Double-domain elliptic curve dot product hardware accelerator
A hardware accelerator and elliptic curve technology, applied in electrical components, public keys for secure communication, digital transmission systems, etc., can solve problems such as slow computing speed, and achieve the effect of improving efficiency and high flexibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
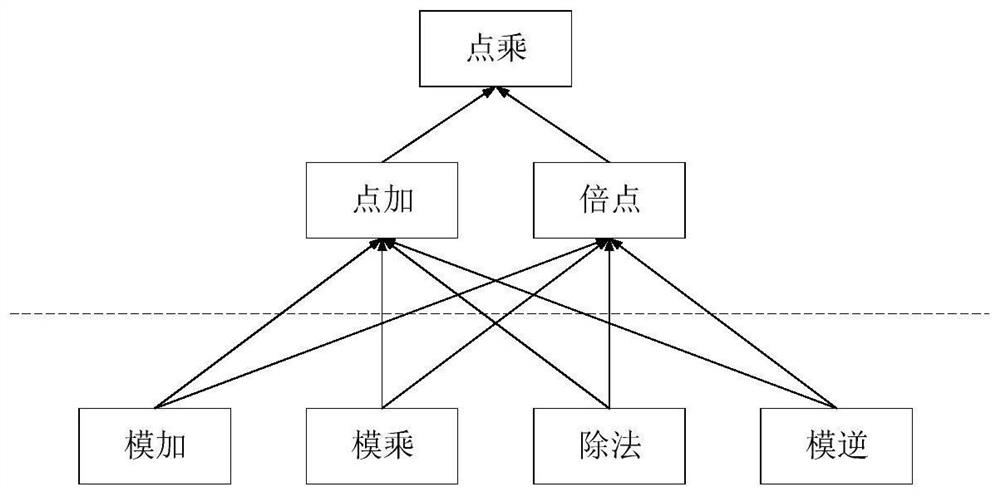
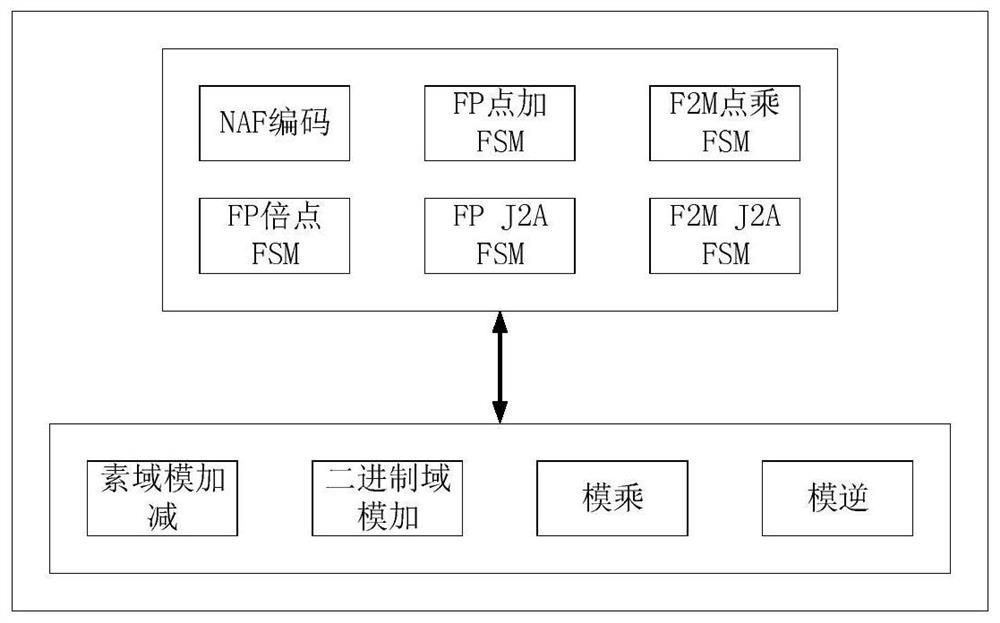
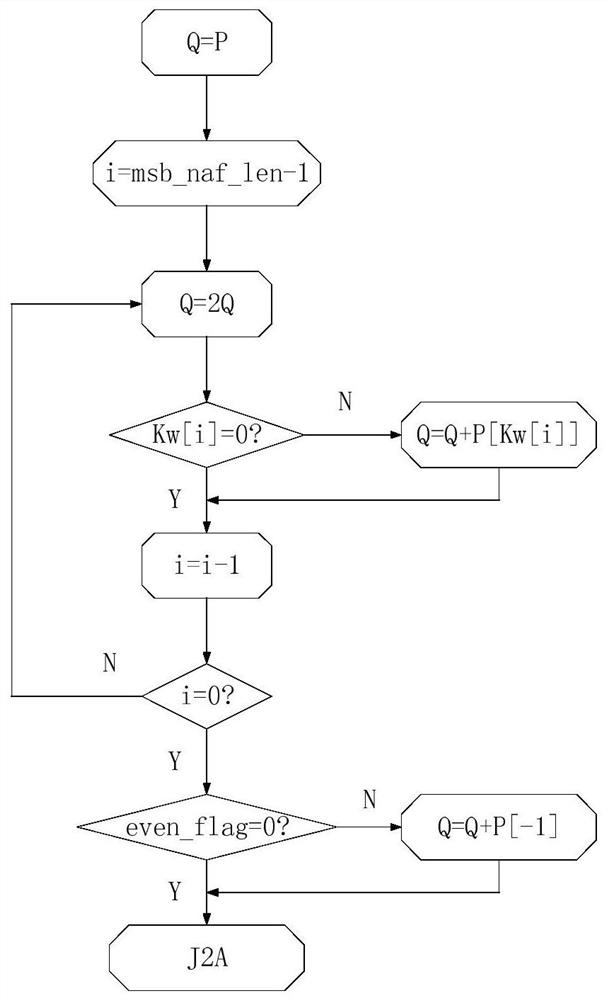
[0012] The implementation steps of the present invention will be described in detail below in conjunction with the accompanying drawings. The structure diagram of the elliptic curve point multiplication accelerator is attached Figures 1 to 3 As shown, the modular operation includes three basic dual-domain modular operations: modular reduction, modular multiplication, and modular inversion. The prime number field point operation layer includes doubling and point addition, which are completed by calling different modular operations through the state machine. Prime number field point multiplication It is completed by calling the state machine of doubling and dot adding, and the dot multiplication of binary domain is completed by calling different modulo operations through the state machine.
[0013] Among them, all point operations and modulo operations are implemented by hardware to improve the speed of ECC operations.
[0014] In one example, the Montgomery modular multiplica...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com