Cipher key generation system and method based on RSA cryptographic algorithm
A cryptographic algorithm and key generation technology, which is applied in the field of key generation system based on RSA cryptographic algorithm, can solve the problems of large amount of calculation, affecting the speed of key generation, and insufficient probability, etc., to achieve high security and high practicability , the effect of increasing the generation speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] The present invention will be further described below in conjunction with the accompanying drawings.
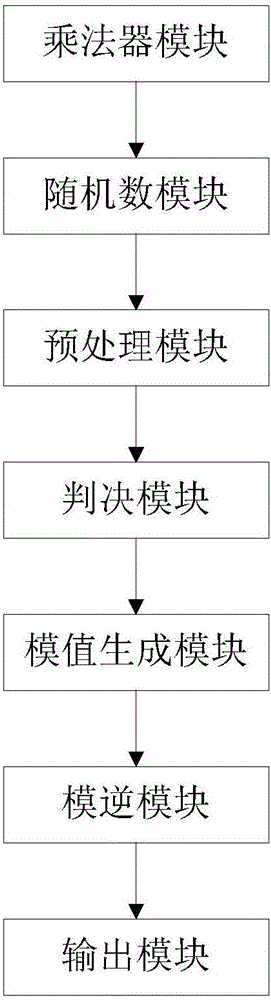
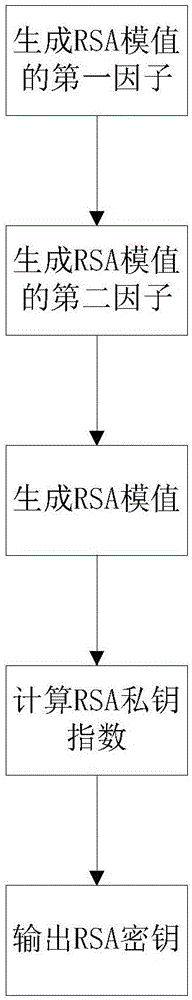
[0035] Refer to attached figure 1 , The system of the present invention includes a multiplier module, a random number module, a preprocessing module, a decision module, a modulus value generation module, a modulus inversion module, and an output module.
[0036] The multiplier module is used to calculate the product of all prime numbers within 500.
[0037] The random number module is used to randomly generate a 512-bit integer.
[0038] The preprocessing module is used to calculate the product of all prime numbers within 500 and the greatest common divisor of the generated integers.
[0039] The judging module is used to perform Miller-Rabin primality test on mutually prime integers.
[0040] The modulus generation module is used to calculate the modulus of RSA.
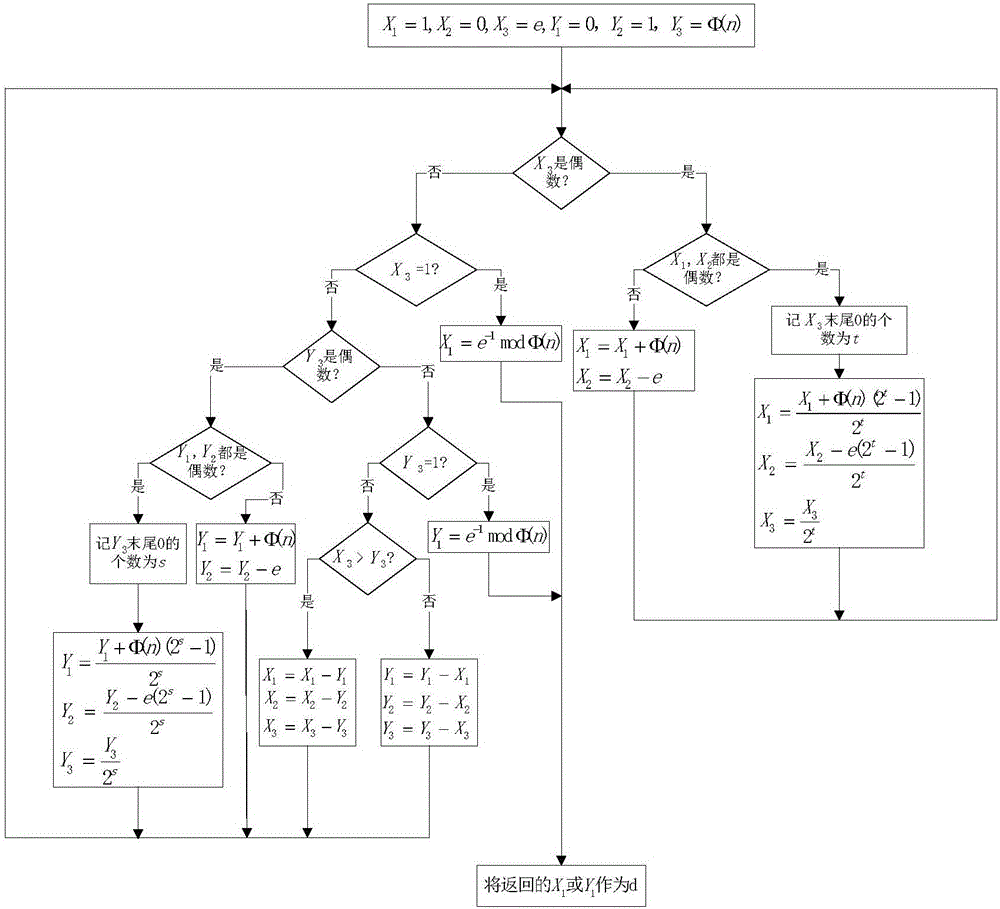
[0041] The modular inverse module is used to calculate the RSA private key index.
[0042] The outpu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com