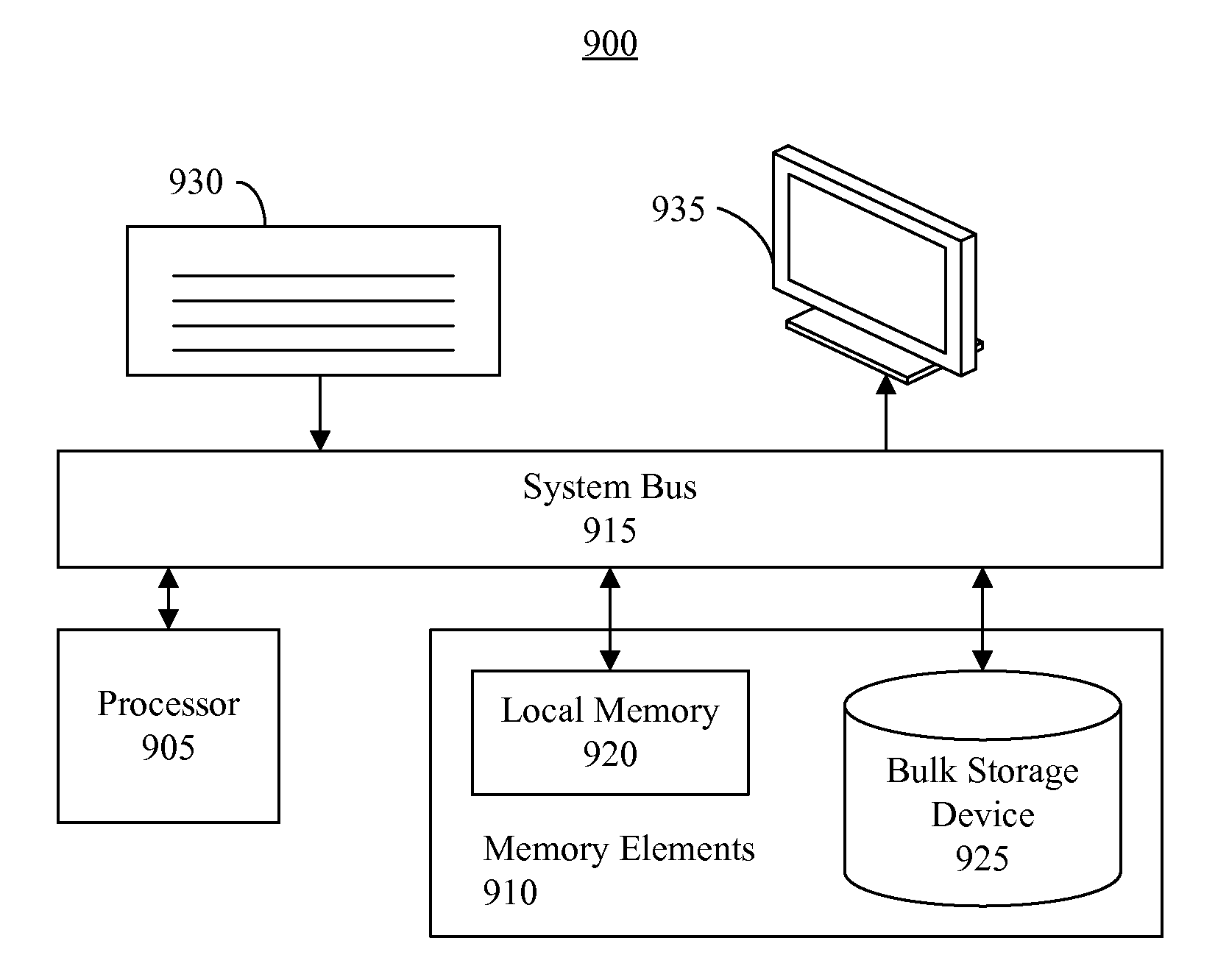
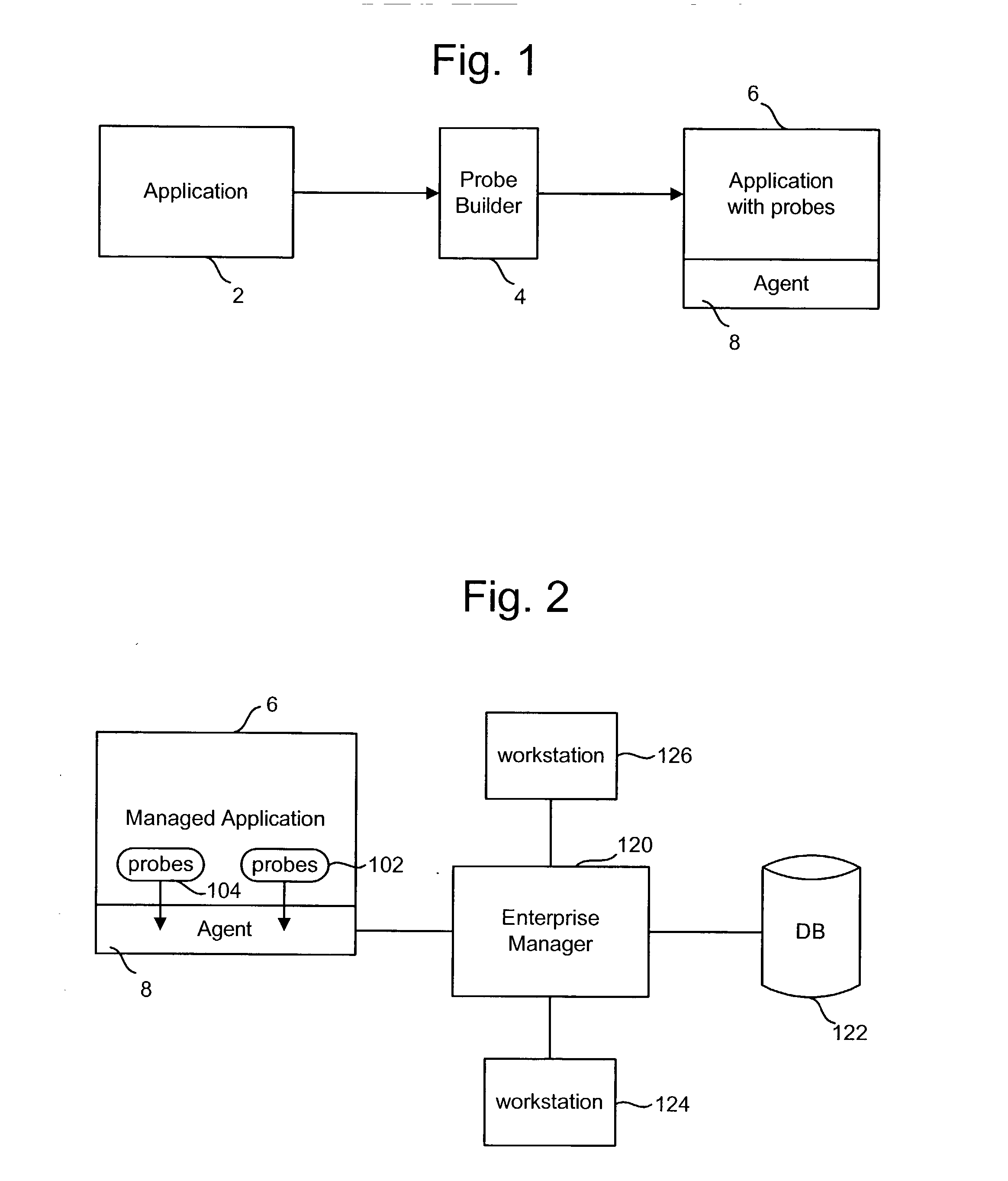
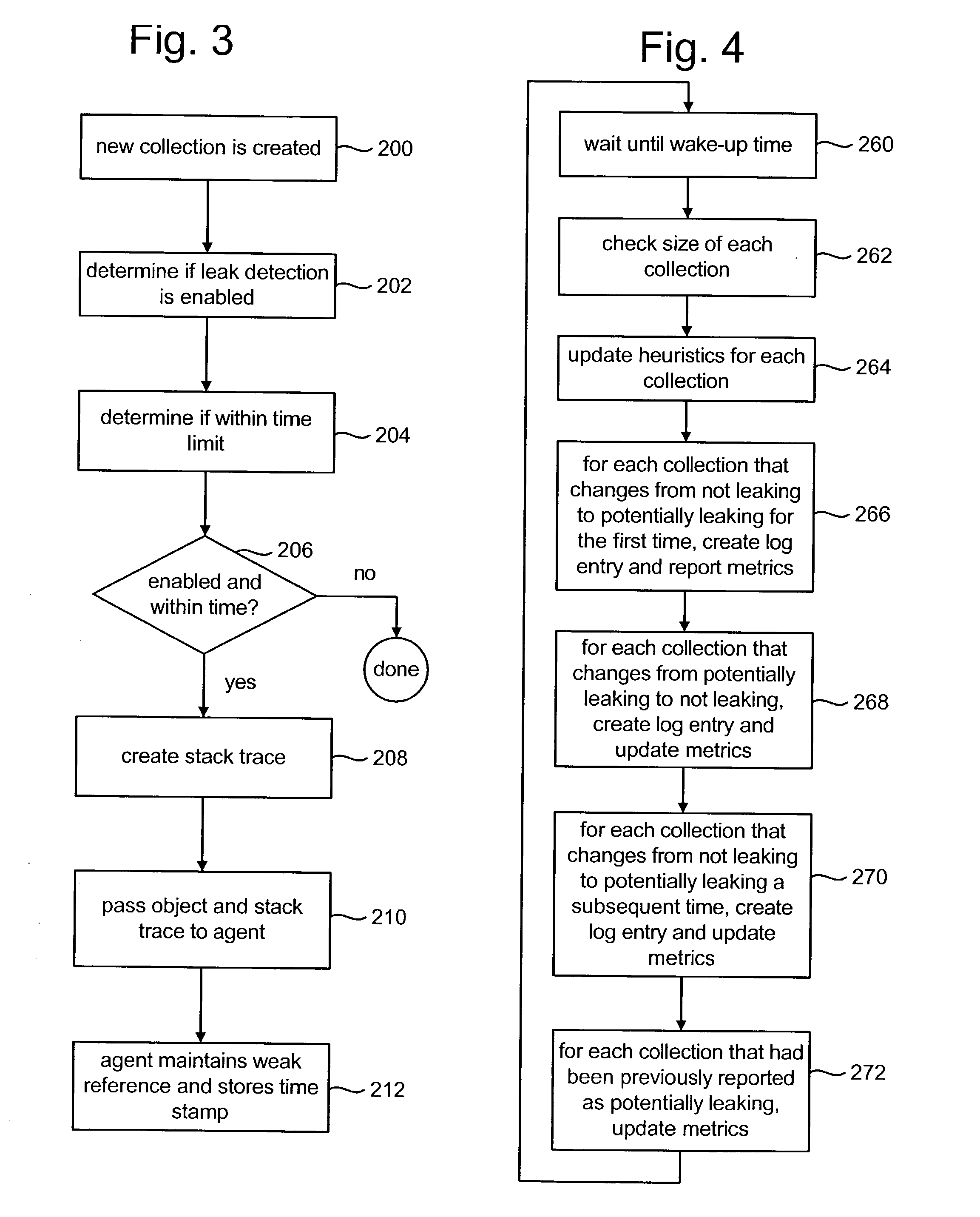
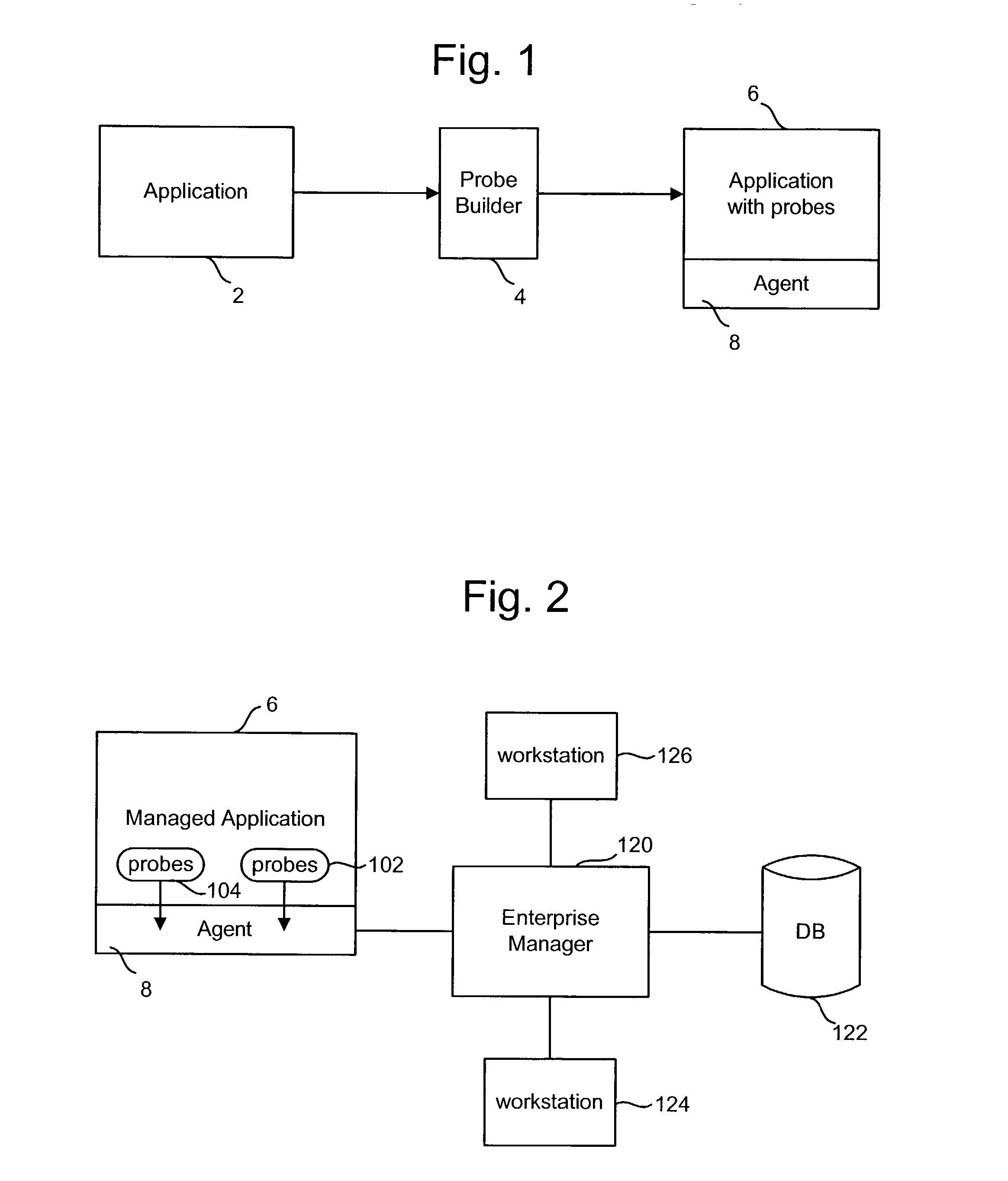
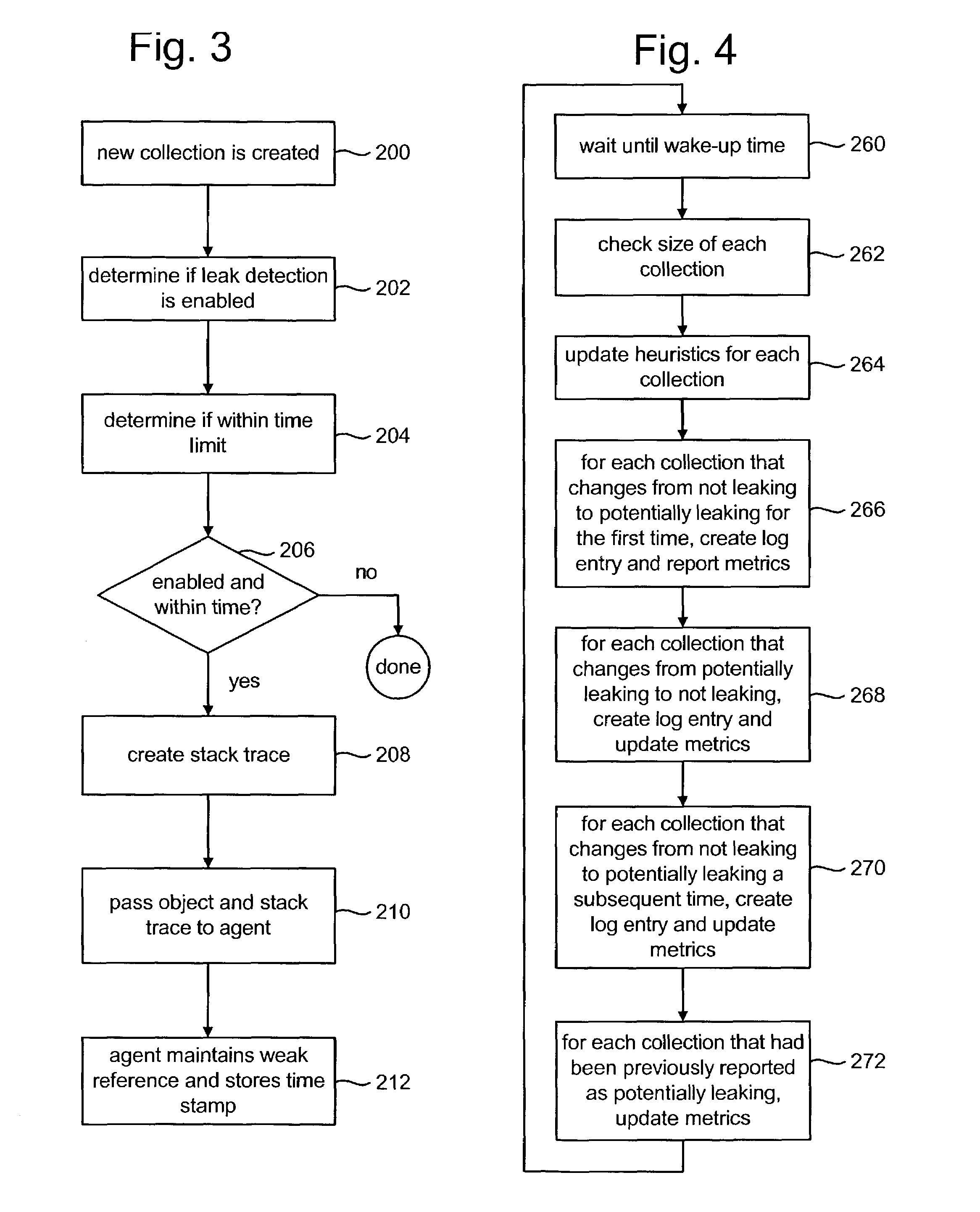
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
395 results about "Memory leak" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In computer science, a memory leak is a type of resource leak that occurs when a computer program incorrectly manages memory allocations in such a way that memory which is no longer needed is not released. A memory leak may also happen when an object is stored in memory but cannot be accessed by the running code. A memory leak has symptoms similar to a number of other problems and generally can only be diagnosed by a programmer with access to the programs' source code.
Automated product defects analysis and reporting
InactiveUS20070074149A1Well formedError detection/correctionDigital computer detailsSoftware faultData mining
An automation infrastructure which automatically analyzes software faults and / or bugs related to a product defect is provided. More particularly, the system can automatically analyze and detect symptoms in the forms of crash dump, memory leak, corruption and test issues etc. In accordance therewith, aspects can automatically search for and locate existing defect reports, if such existing reports are available. Moreover, aspects can automatically report new defects in a defect tracking database or other tracking mechanism.
Owner:MICROSOFT TECH LICENSING LLC
Memory control method for embedded systems
ActiveCN102915276AImprove distribution efficiencyAdd status monitoringMemory adressing/allocation/relocationComputer architectureParallel computing
The invention provides a memory control method for embedded systems. The method includes: applying for memory in an operating system, and using part of the memory as a memory pool and the other part as a reserved memory area; establishing a cache for each thread by pool management of the memory pool and thread caching technology; subjecting the reserved memory area to management by TLSF (two-level segregated fit) algorithm; dividing the memory pool into memory blocks different in size, connecting the memory blocks in the same size to form a double linked list, adding a memory management unit for each memory block, and placing the memory management unit and the memory blocks in different memory areas respectively; and establishing a memory statistical linked list for each thread to connect the memory blocks applied by the thread so as to facilitate troubleshooting of memory leak. In addition, a memory coverage checking mechanism is added without increasing cost of the memory control method.
Owner:WUHAN POST & TELECOMM RES INST CO LTD
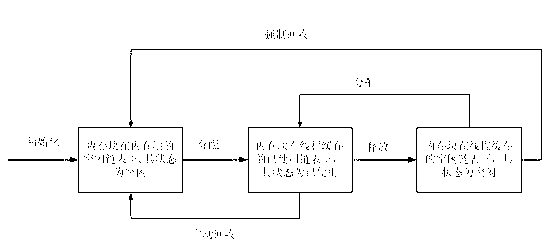
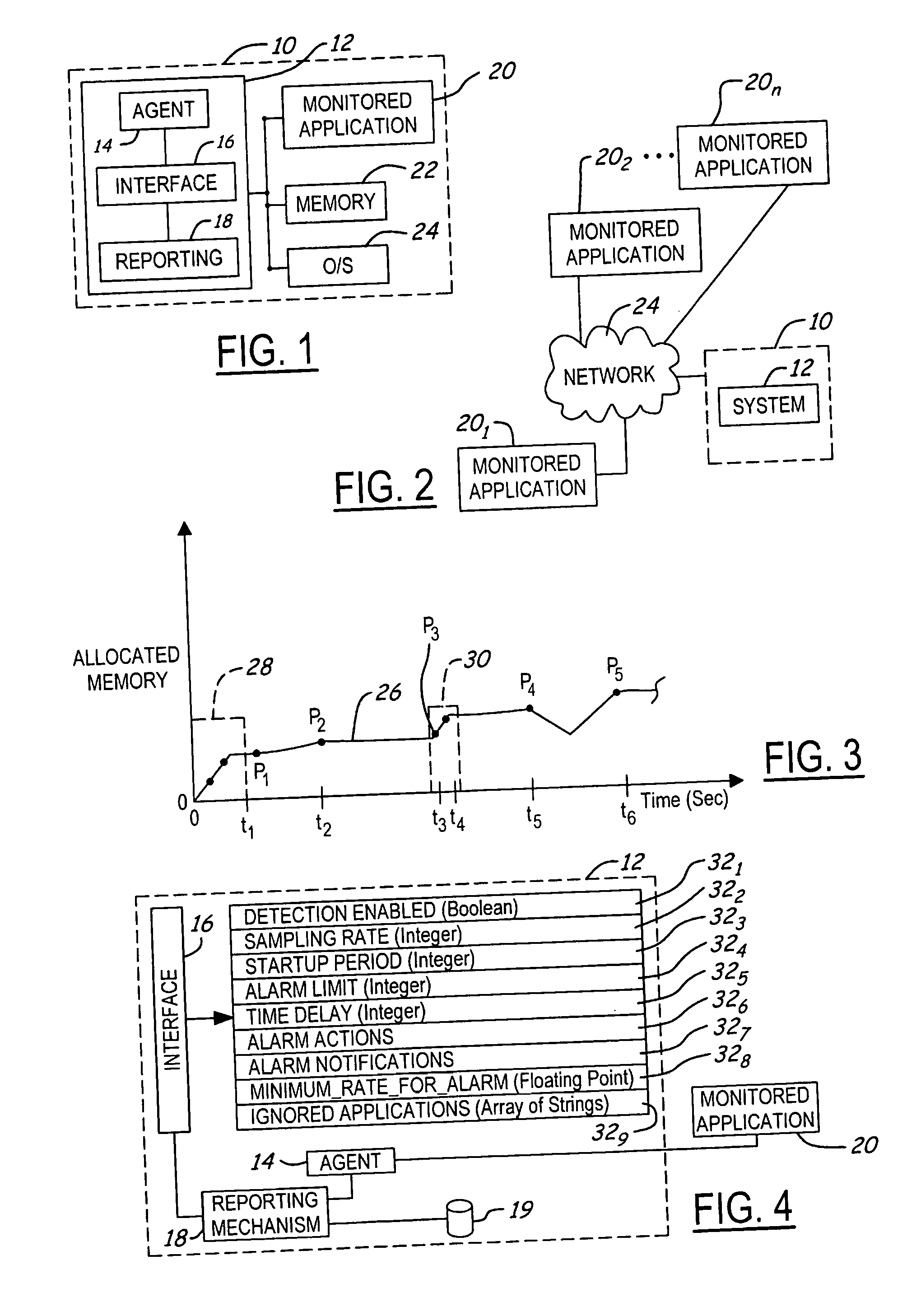
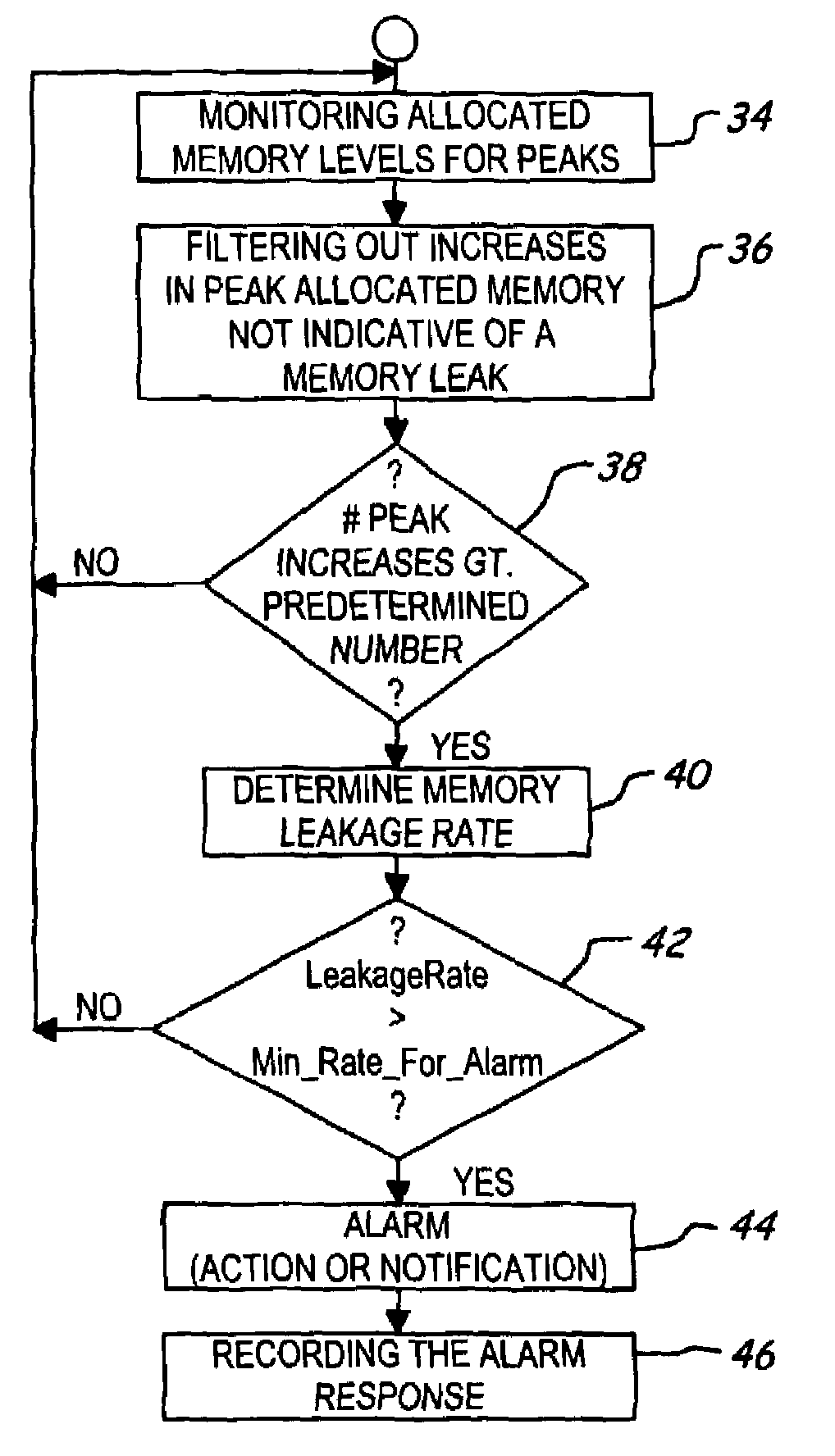
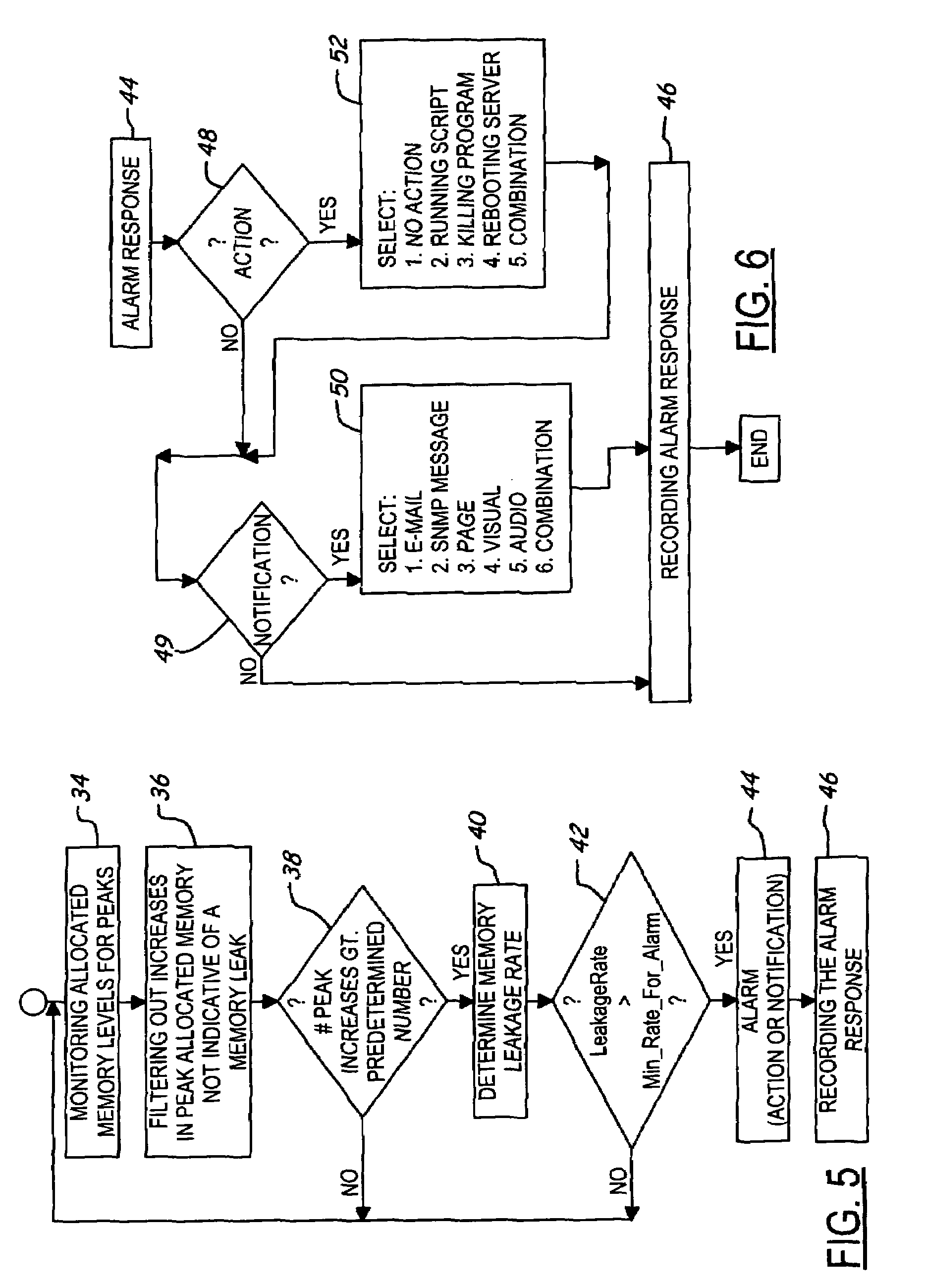
Apparatus and method for detecting memory leaks
A system and method for detecting memory leaks includes a monitoring agent, a user interface for configuring operating parameters and a reporting mechanism. The monitoring agent determines allocated memory levels of a monitored application at a sampling frequency and determines when a then-existing “peak” memory level has increased. The monitored application is determined to be leaking memory when a determined number of increases in the peak allocated memory level are detected. The determined number may be fixed ahead of time or may be calculated dynamically based on user specified parameters. When a given memory leakage rate is exceeded, an alarm response is taken, which may be either a specified notification of the alarm or an action. Certain increases in the peak allocated memory levels are ignored as not necessarily being indicative of a memory leak condition, such as during startup of the program or between rapidly, closely-occurring increases in the peak allocated memory level.
Owner:LAKESIDE SOFTWARE LLC
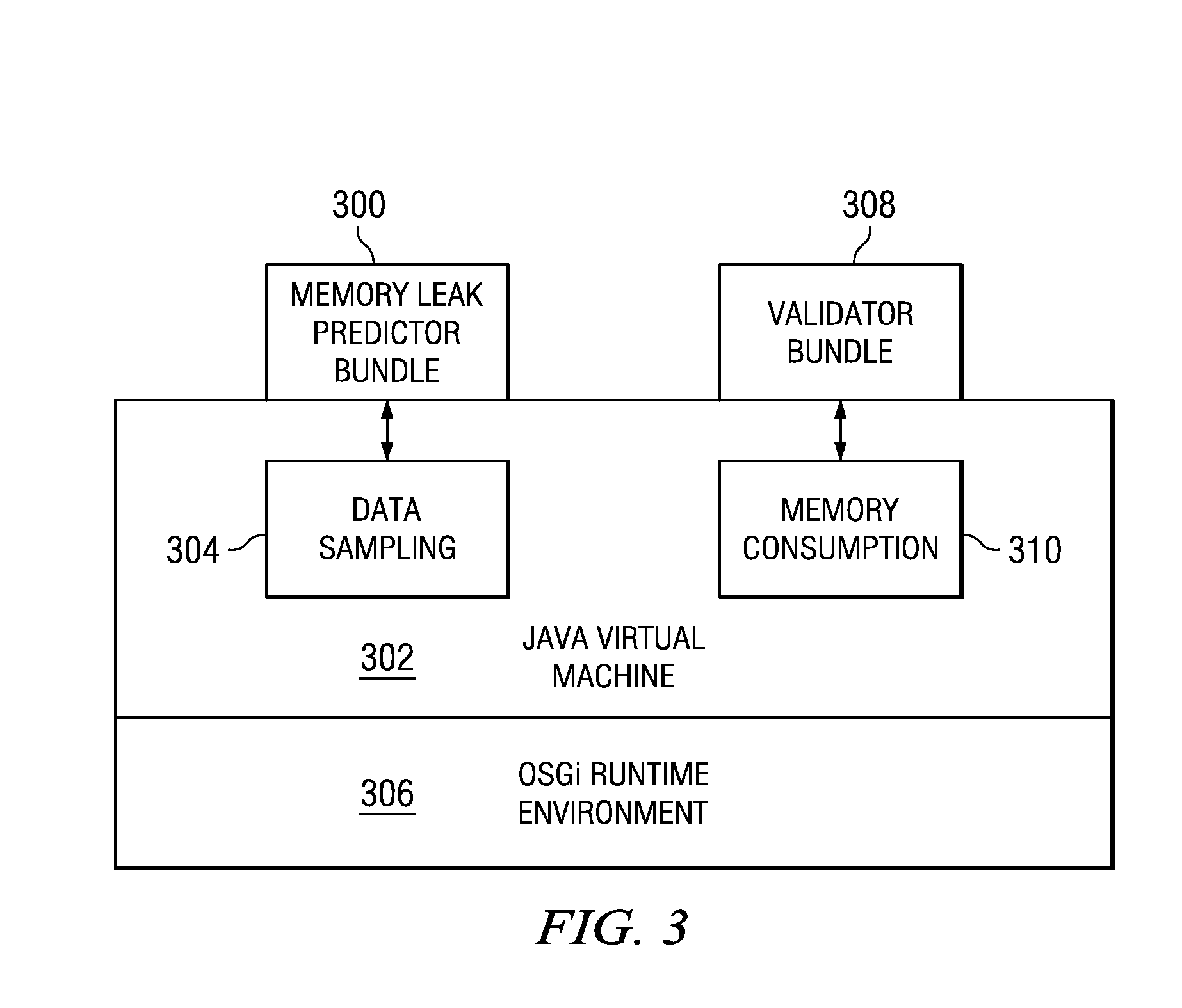
Method and Apparatus to Anticipate Memory Exhaustion in an Open Services Gateway Initiative Environment
A computer implemented method, computer program product, and data processing system for predicting a future status of a memory leak. A first set of data including memory consumption data is received at a software bundle. The software bundle is operating in an open services gateway initiative environment. Responsive to a determination that a memory leak exists, the first set of data is analyzed to predict a future status of the memory leak. The future status is stored, as stored data, in a storage device.
Owner:IBM CORP
Identifying memory leaks in computer systems
InactiveUS20060206885A1Non-redundant fault processingSpecific program execution arrangementsObject basedAnalysis data
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
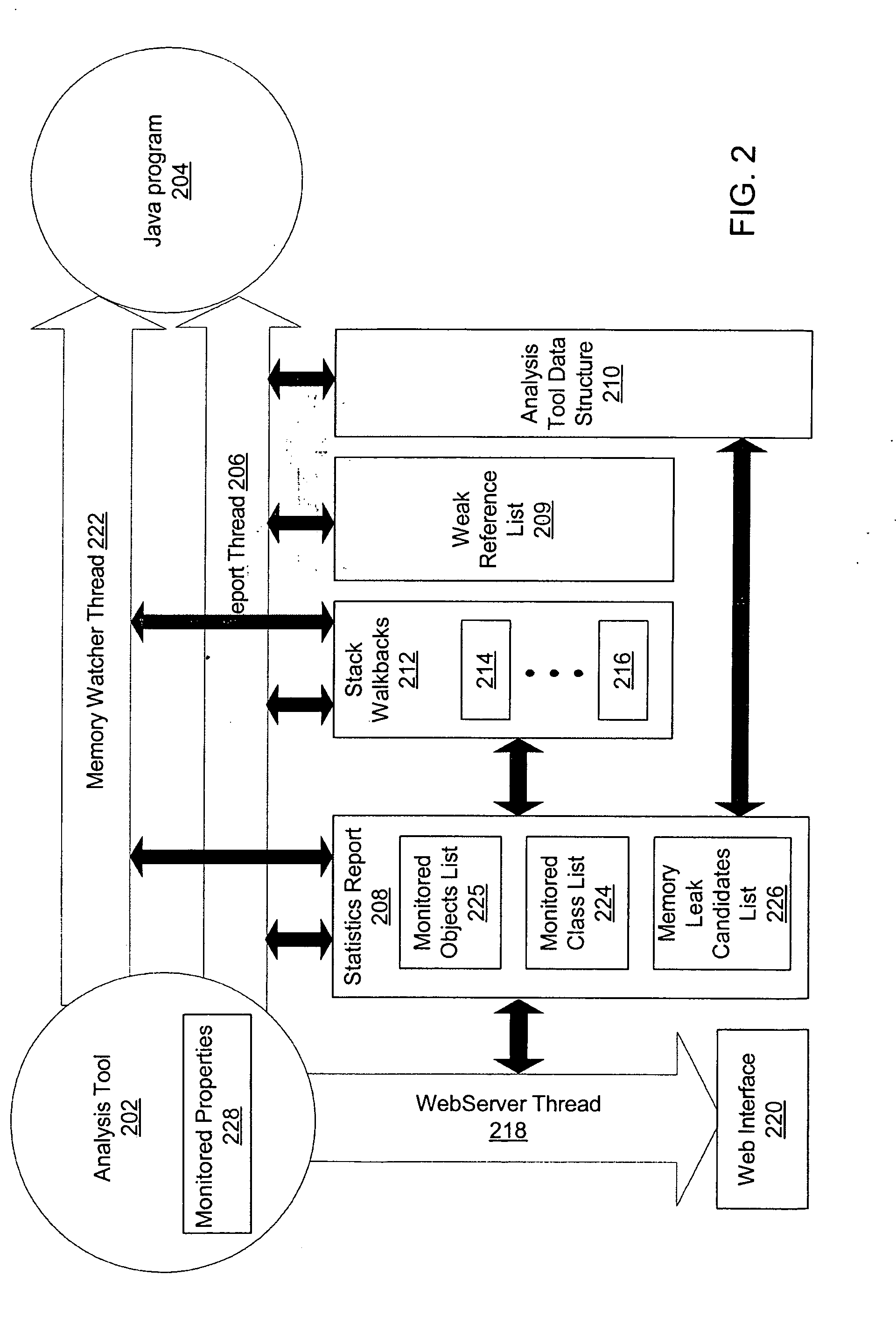
Method, system and article for detecting memory leaks in Java software
InactiveUS20050204342A1Error detection/correctionSpecific program execution arrangementsObject ClassSoftware system
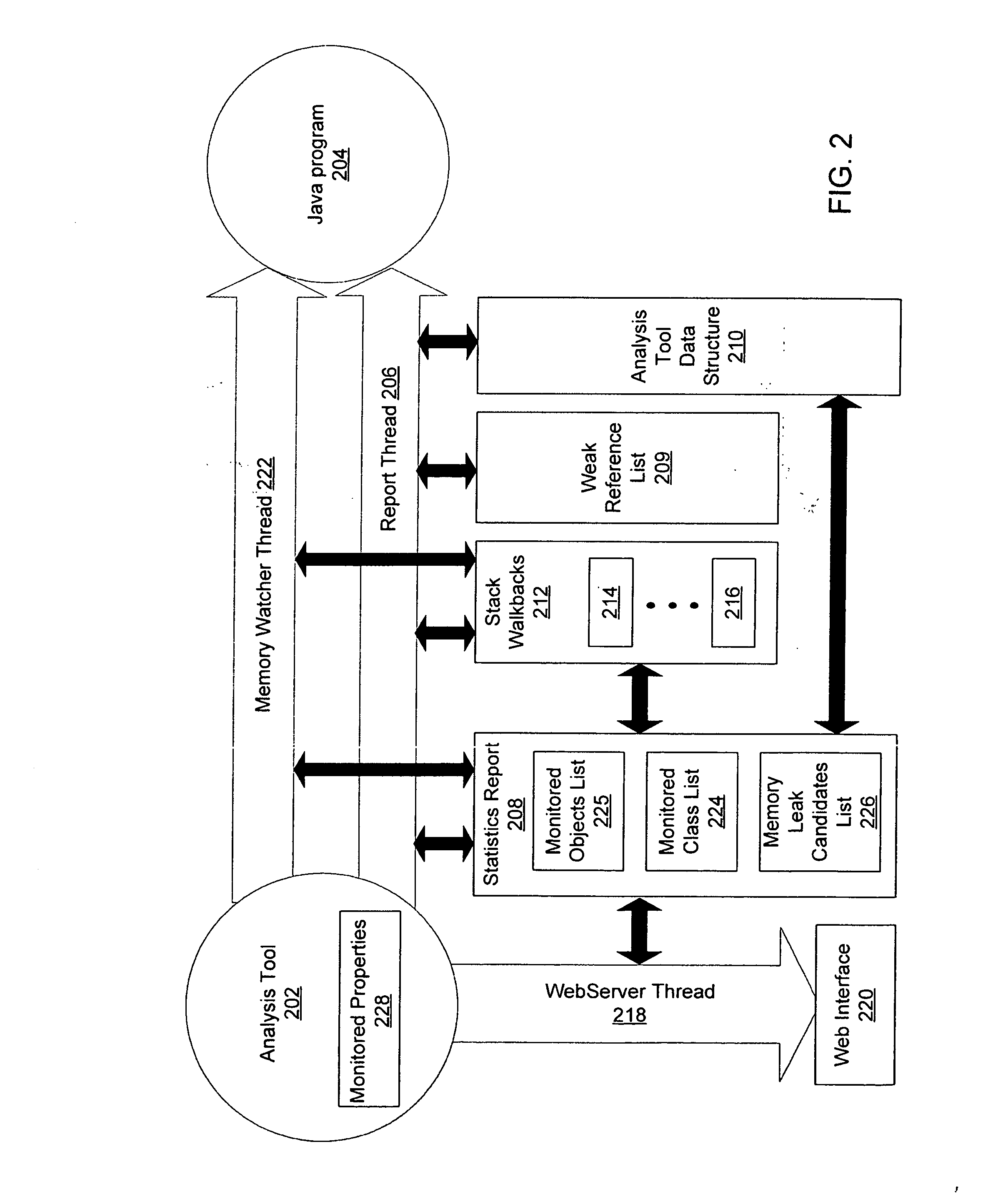
An analysis tool for specifically identifying the cause and location of object memory leaks within a large software system is provided. The analysis tool transparently adds multiple processing threads that collaborate to identify sources of potential memory leaks in the software being analyzed. These threads provide notifications of object classes executing in the software that have had excessive instance counts or have exceeded the average lifetime of an object, thereby providing the analysis tool operator sufficient information to make a final determination of objects that are possible candidates for memory leaks. Once the cause and location of the object memory leaks are ascertained, the analysis tool operator may analyze the memory leaks, and subsequently modify the software to reduce or eliminate the memory leaks.
Owner:IBM CORP
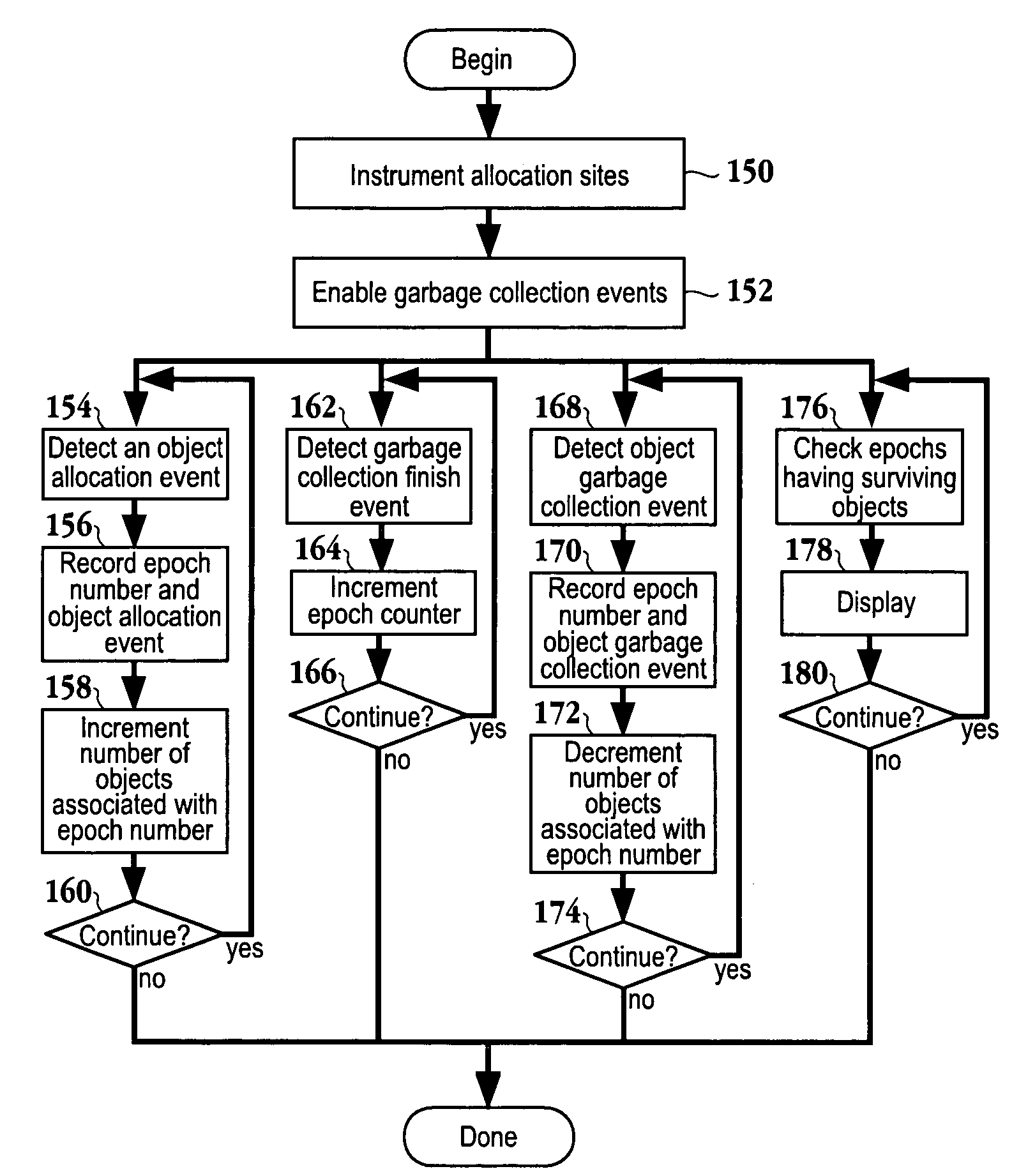
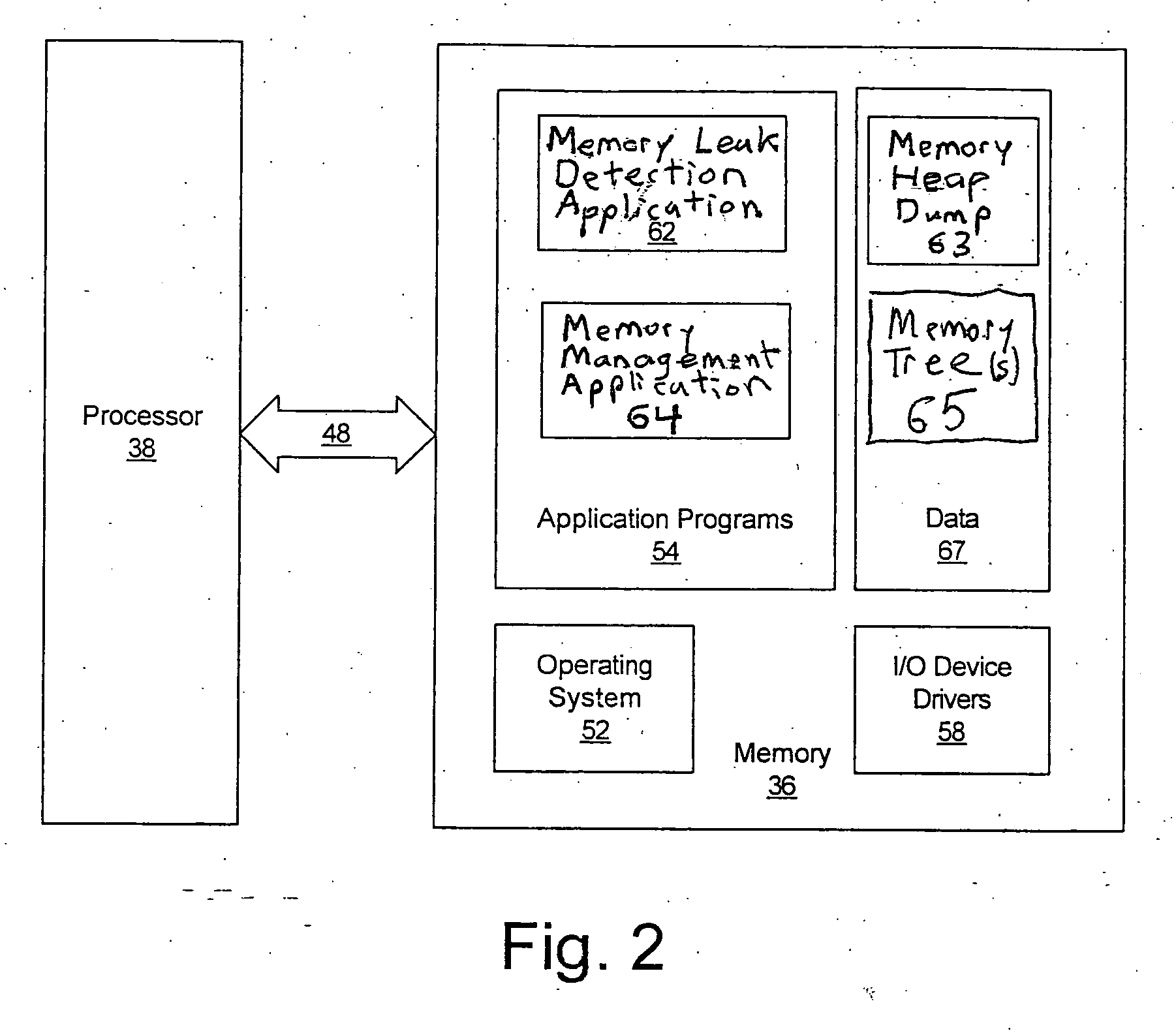
Method for monitoring heap for memory leaks
A low overhead method for identifying memory leaks is provided. The low overhead method includes a) detecting completion of a garbage collection cycle; and b) identifying a boundary between used objects in memory and free memory space. The steps of a) and b) are repeated and then it is determined if there is an existing memory leak based upon evaluation of boundary identifiers. A computer readable media and a system for identifying memory leaks for an object-oriented application are also provided.
Owner:ORACLE INT CORP
Conservative garbage collection and access protection
ActiveUS20130007073A1Memory architecture accessing/allocationSpecial data processing applicationsRefuse collectionWaste collection
A method of memory management can include creating an initial root set of pointers for a program during execution of the program and performing a marking process by iteratively marking referred objects of each pointer of the root set and expanding the root set with filtered, encoded pointers. The method also can include identifying each non-live object for any marked object as red-marked and performing, using a processor, a re-marking process on the root set in which red-marked objects are excluded. Each object of the root set not marked can be designated as including a memory leak.
Owner:IBM CORP
Automated product defects analysis and reporting
An automation infrastructure which automatically analyzes software faults and / or bugs related to a product defect is provided. More particularly, the system can automatically analyze and detect symptoms in the forms of crash dump, memory leak, corruption and test issues etc. In accordance therewith, aspects can automatically search for and locate existing defect reports, if such existing reports are available. Moreover, aspects can automatically report new defects in a defect tracking database or other tracking mechanism.
Owner:MICROSOFT TECH LICENSING LLC
Memory leak diagnosis
InactiveUS20090328007A1Software testing/debuggingSpecific program execution arrangementsParallel computingRanking
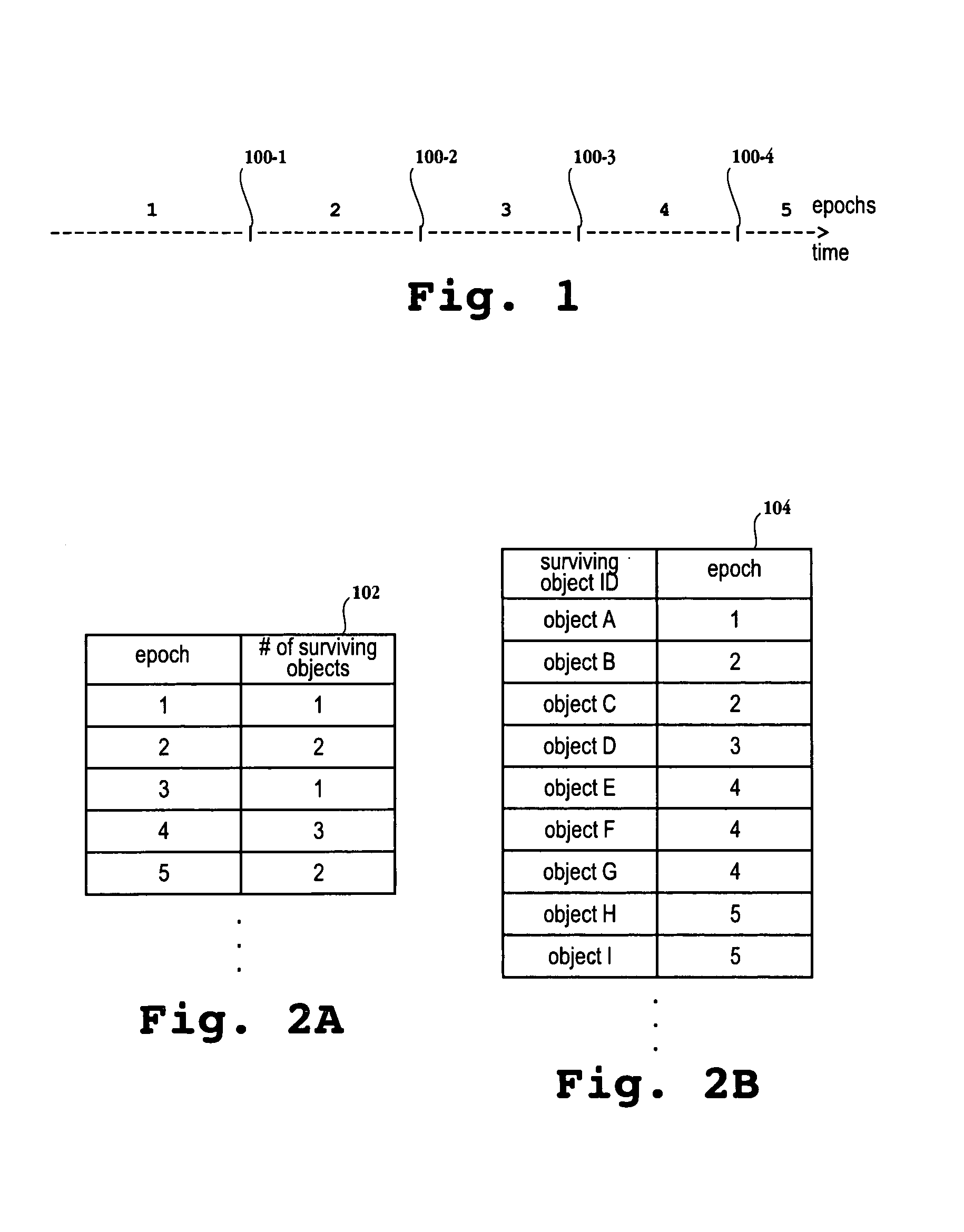
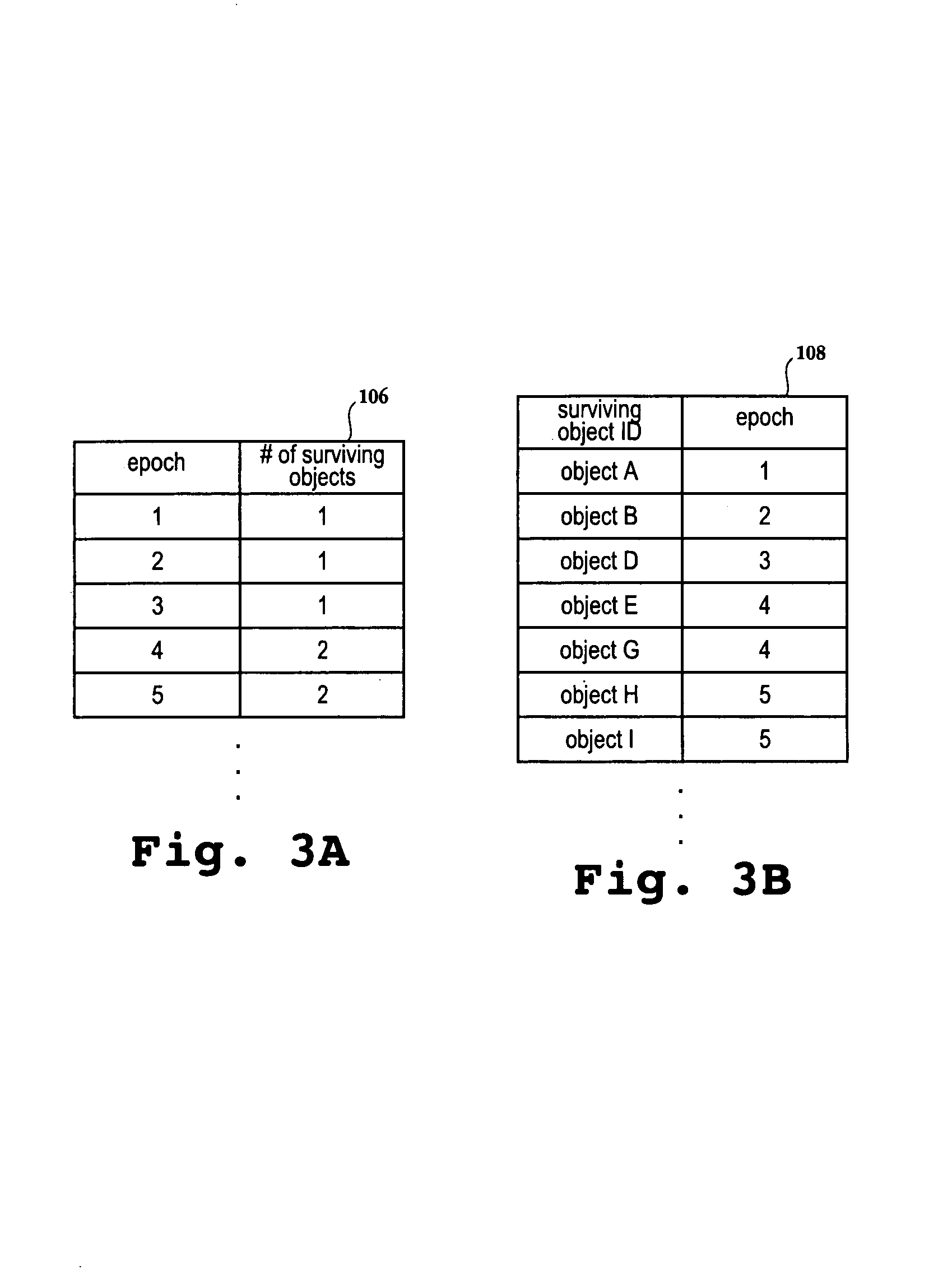
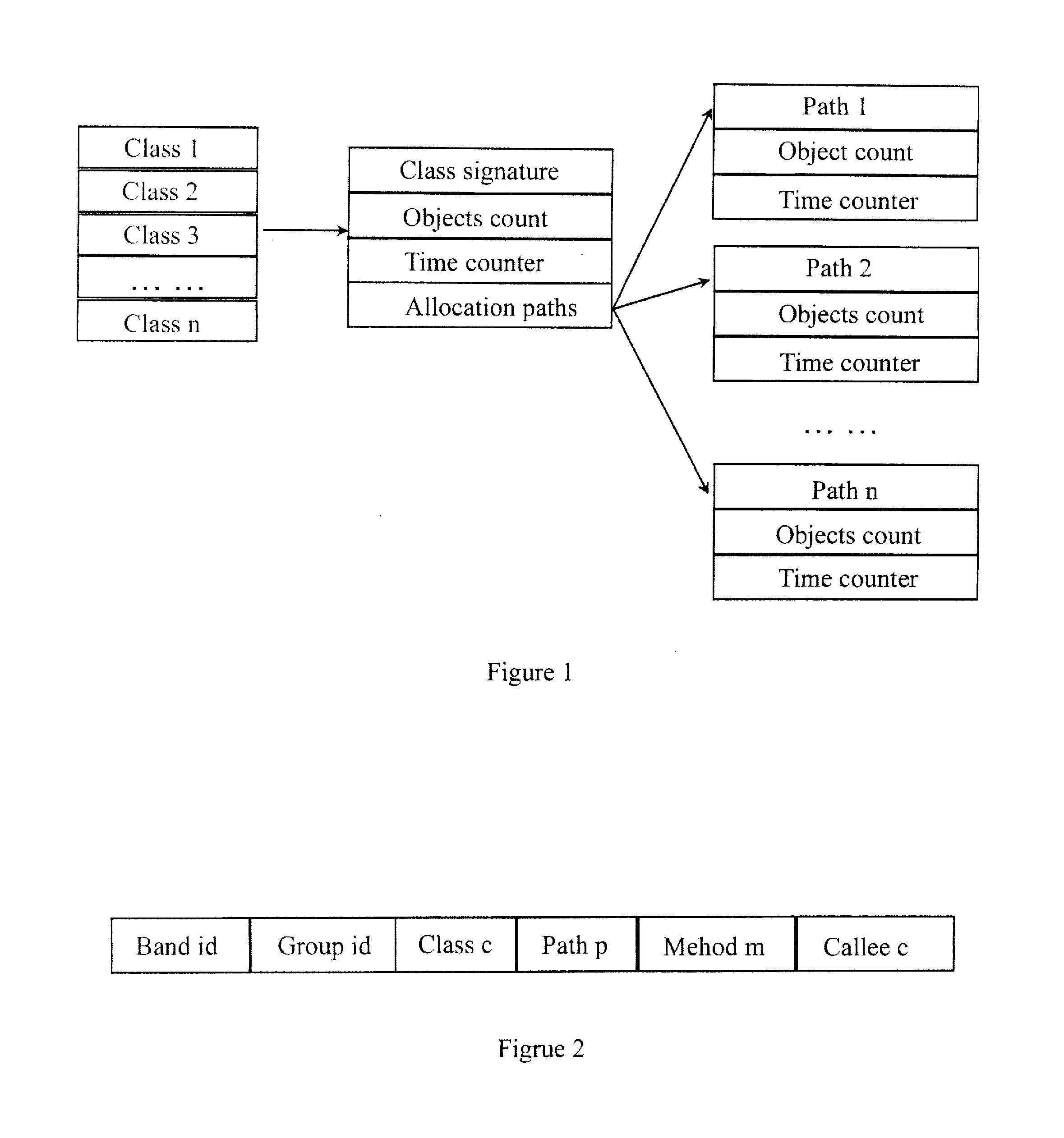
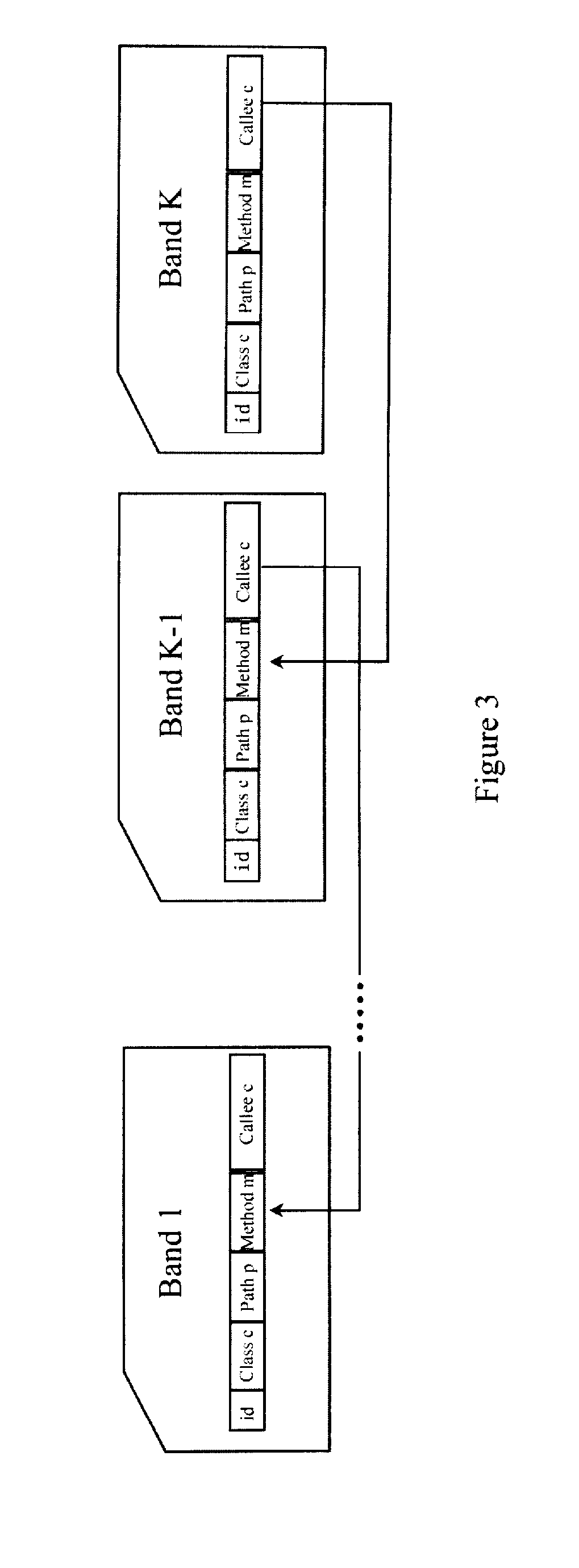
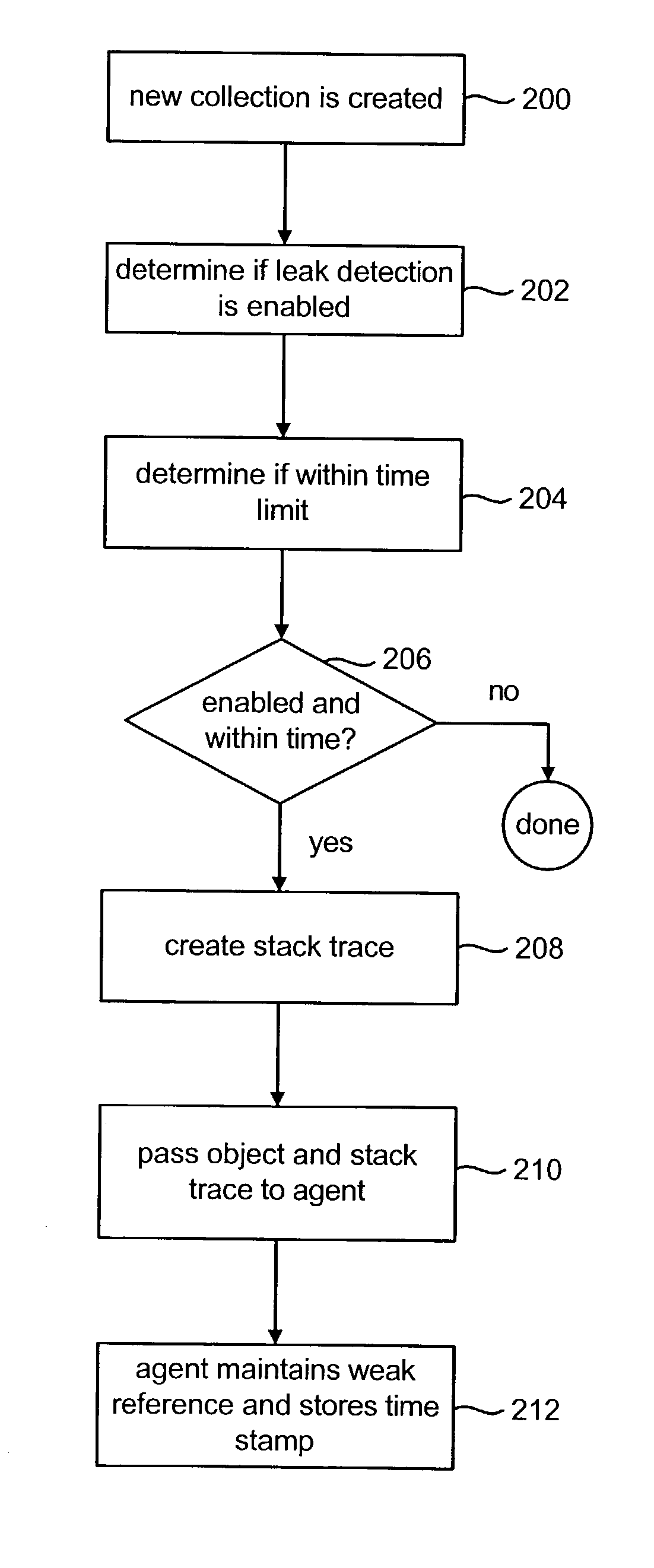
A method and an apparatus for diagnosing memory leak. The method includes: tracing the allocation of objects; recording allocation paths and allocation time of each object; giving to each object one unique identifier (ID) corresponding to an allocation path; determining the allocation path to which each object belongs; organizing the objects which are allocated but still not collected, and counting the age generations of the objects of the similar type according to the allocation time of each object; ranking the allocation paths according to the age generations of the surviving objects; and analyzing the ranking of the allocation paths, in which the allocation path with higher rank is more probable to introduce memory leaks. Thus, the suspicious allocation path possibly incurring memory leaks is selected and reported to the user for analysis.
Owner:IBM CORP
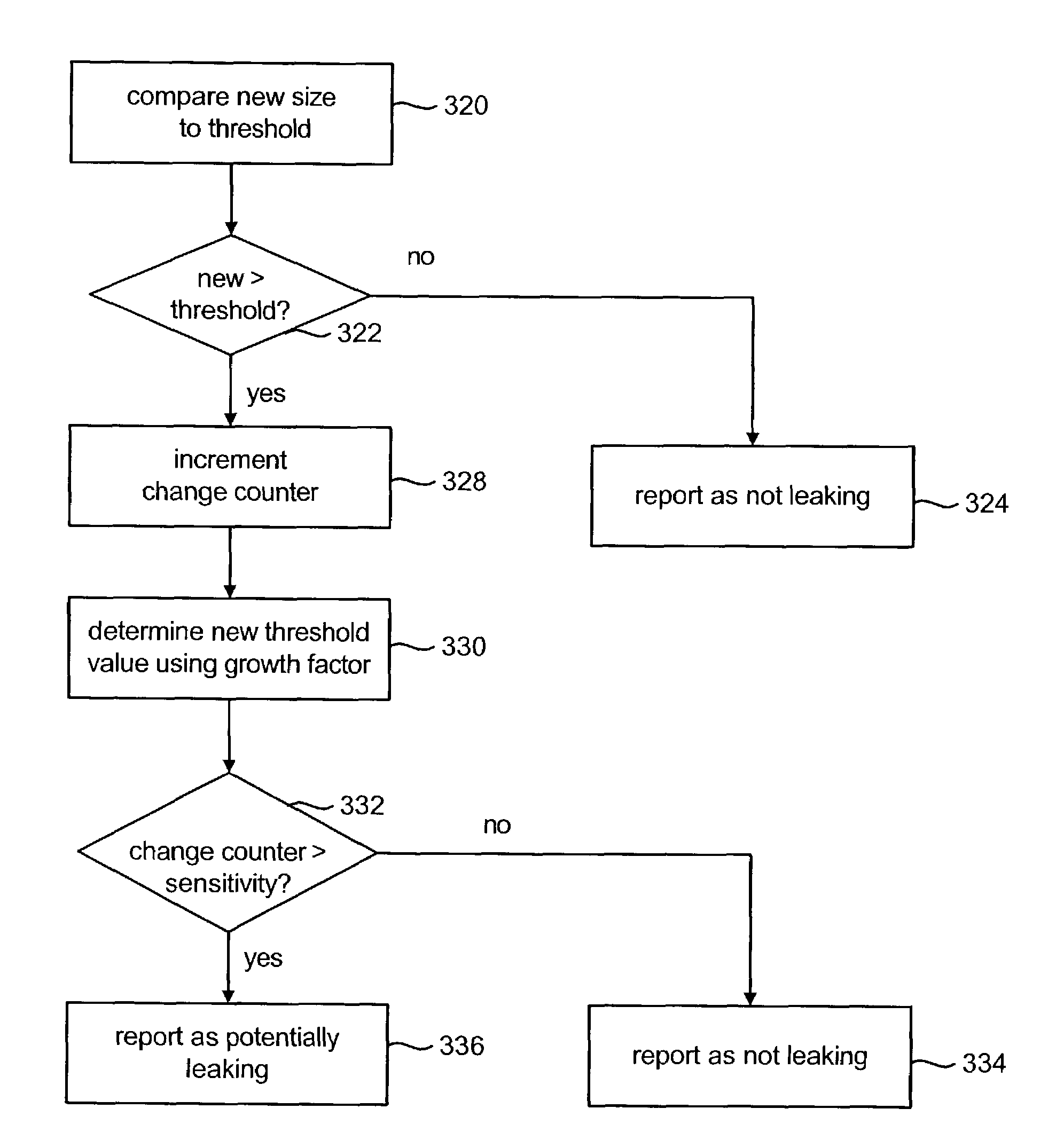
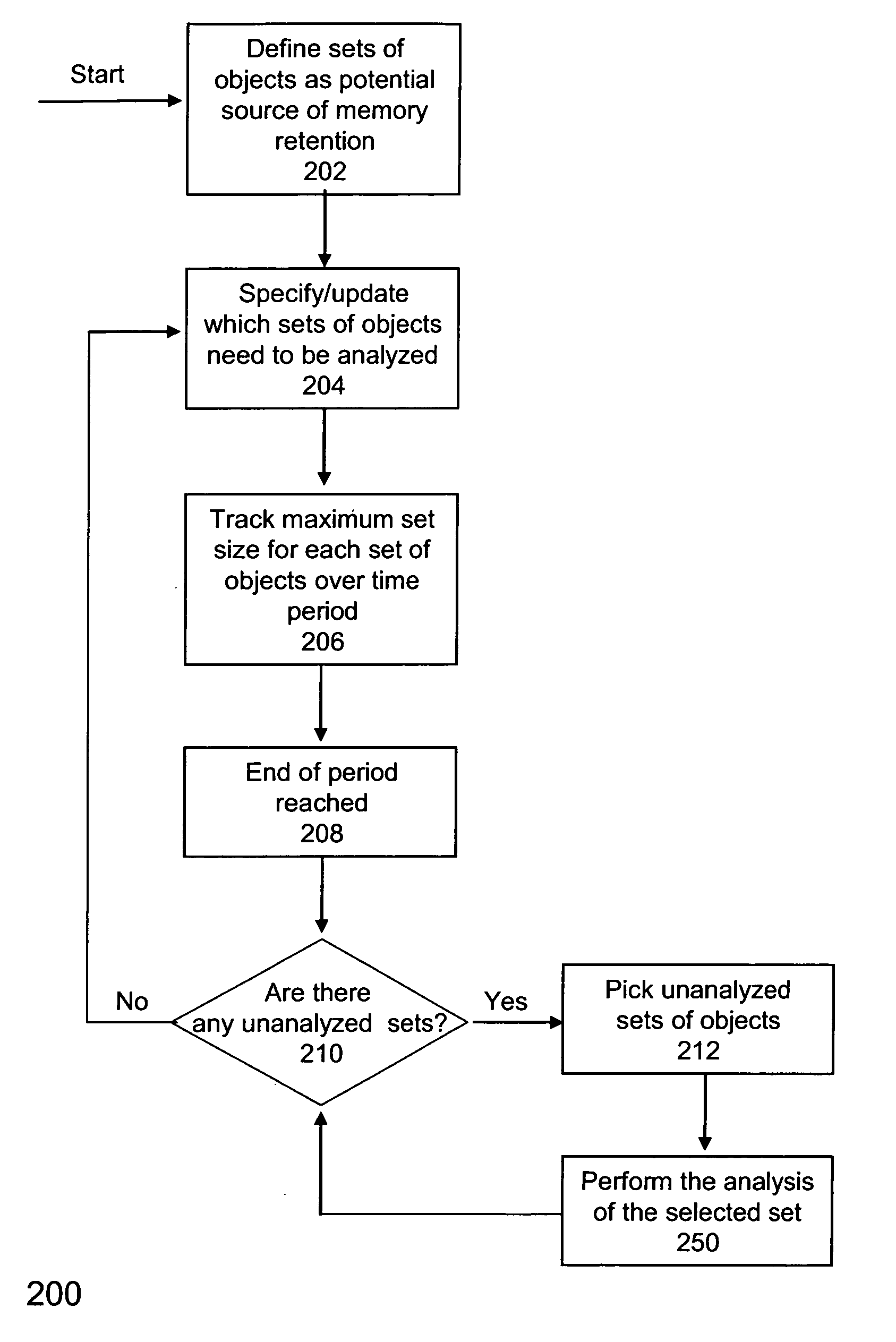
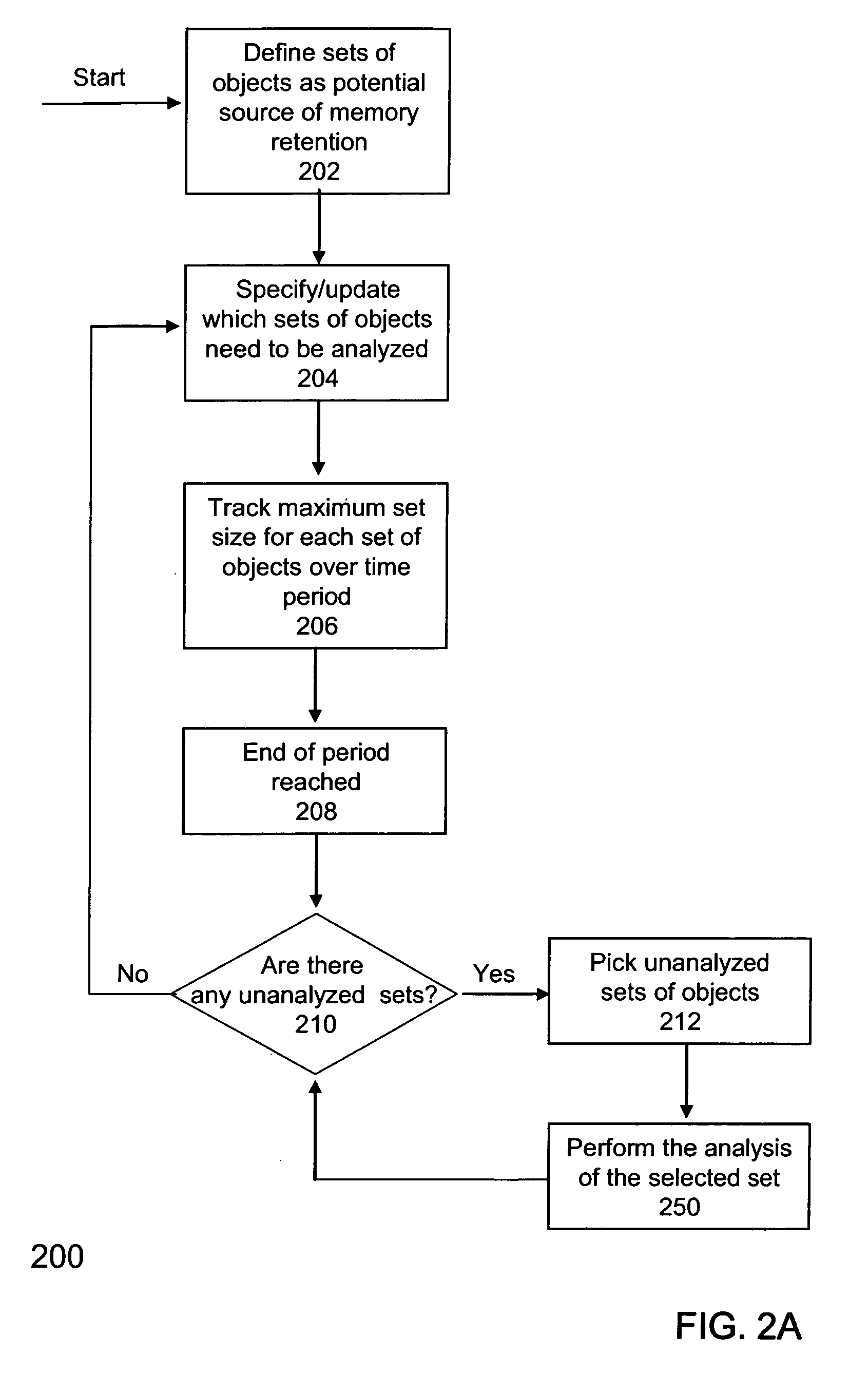
Locating potential sources of memory leaks
ActiveUS20040078540A1Error detection/correctionSpecific program execution arrangementsMemory leakOperating system
Potential sources of memory leaks are identified by tracking the size of groups of stored items and determining based on the growth pattern of the groups whether the groups of stored items are potential sources of memory leaks. An example of a group of stored items is an instance of a Java collection. If the growth pattern of a particular group of stored items indicates that it may be the source of a memory leak, that group is reported to a user and will continue to be tracked.
Owner:CA TECH INC
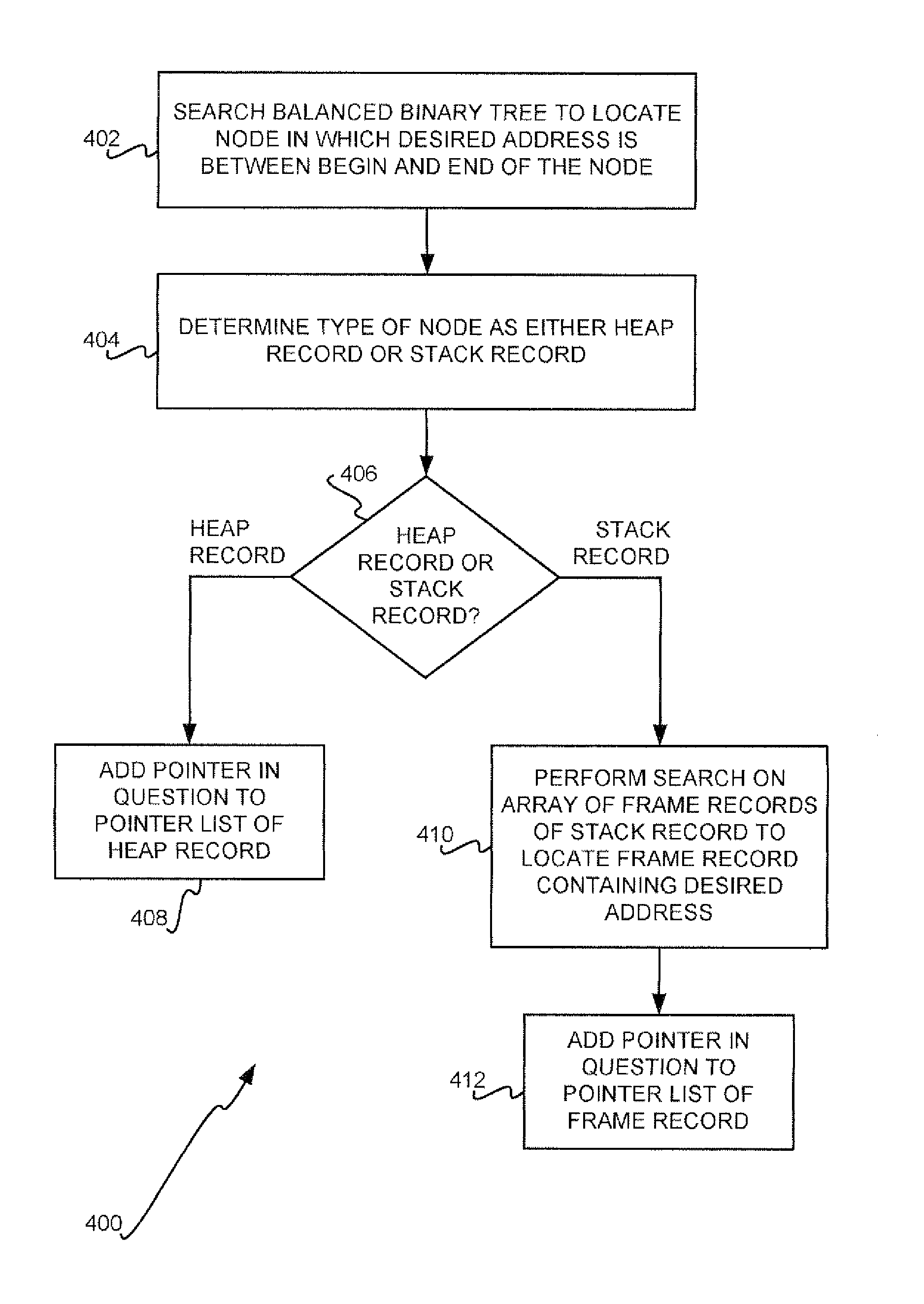
Detecting Dangling Pointers and Memory Leaks Within Software
InactiveUS20080301646A1Error detection/correctionSpecific program execution arrangementsParallel computingBinary tree
Dangling pointers and memory leak locations within software are detected. As the software allocates and deallocates memory, lists of pointers referencing the memory, and pointer status, are maintained. As the software writes new addresses within pointers and reads addresses referenced by the pointers, the pointer lists are maintained to determine whether the pointers are dangling and to detect memory leak locations. A balanced binary tree having a number of nodes can be maintained. The nodes represent heap or stack records. Each heap record corresponds to heap memory that has been allocated and has a list of pointers referencing the heap memory. Each stack record corresponds to a stack within which a stack frame is allocated each time a function is entered. The stack record has frame records corresponding to the stack frames. Each frame record has a list of pointers referencing the corresponding stack frame.
Owner:IBM CORP
Locating potential sources of memory leaks
InactiveUS7234080B2Reduce system overheadEasy to monitorHardware monitoringSoftware testing/debuggingMemory leakOperating system
Potential sources of memory leaks are identified by tracking the size of groups of stored items and determining based on the growth pattern of the groups whether the groups of stored items are potential sources of memory leaks. An example of a group of stored items is an instance of a Java collection. If the growth pattern of a particular group of stored items indicates that it may be the source of a memory leak, that group is reported to a user and will continue to be tracked.
Owner:CA TECH INC
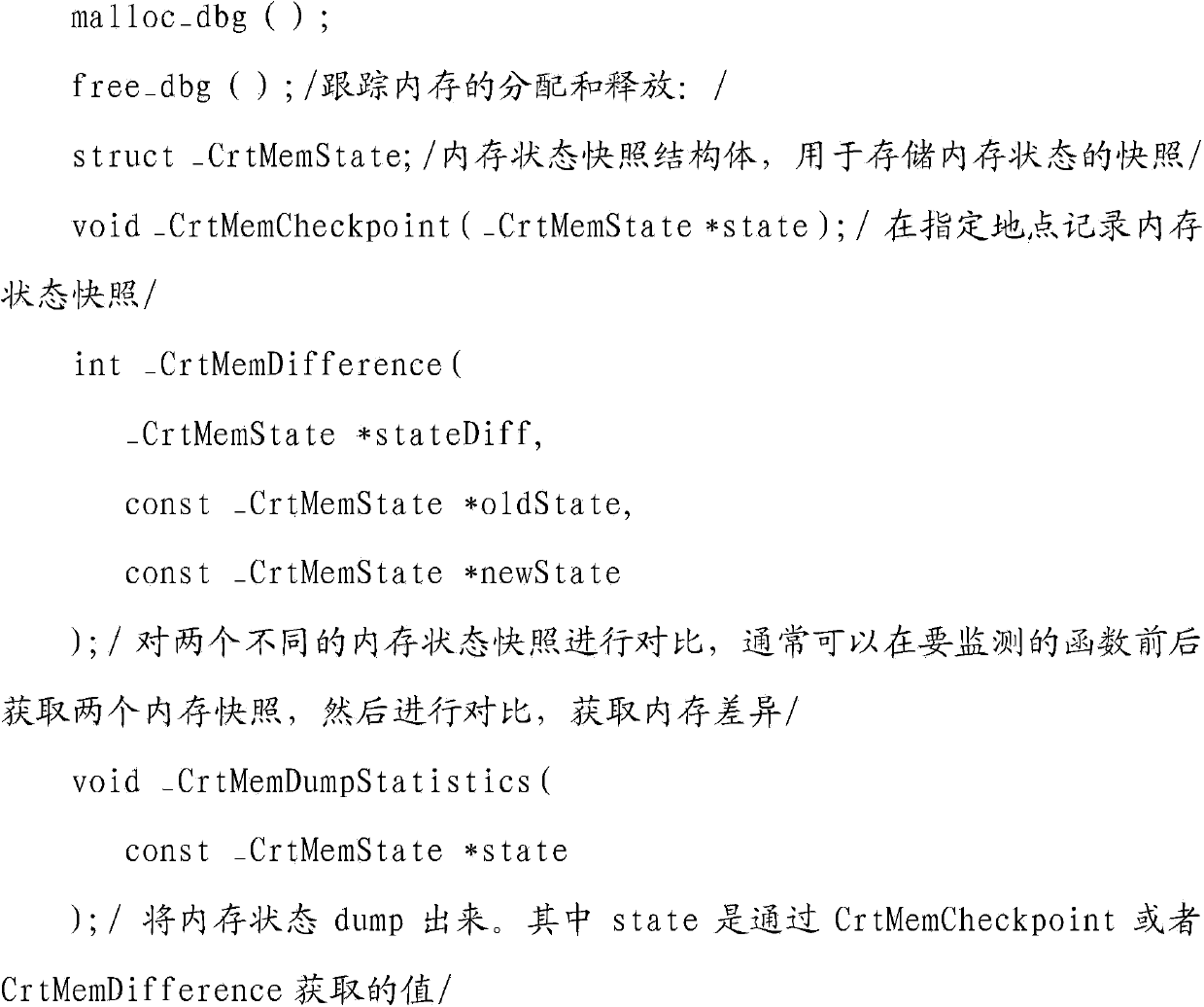
Method for checking sofeware memory leak
The invention discloses a kind of examining method for software memory leakage. The method confirms the memory block which is applied by the application at first and the occupied time of different memory blocks, when the application runs, it records the applying and releasing information of the memory, and finds the memory block which is not released and exceeds the time, it ascertains the memory leakage point of the application; the examination to the memory leakage of application with the method has little impact on the application, it's easy to be realized and low cost, it applies to the long-term examination for the memory leakage, and helps to find the leakage fault emerged in actual application environment.
Owner:HUAWEI TECH CO LTD
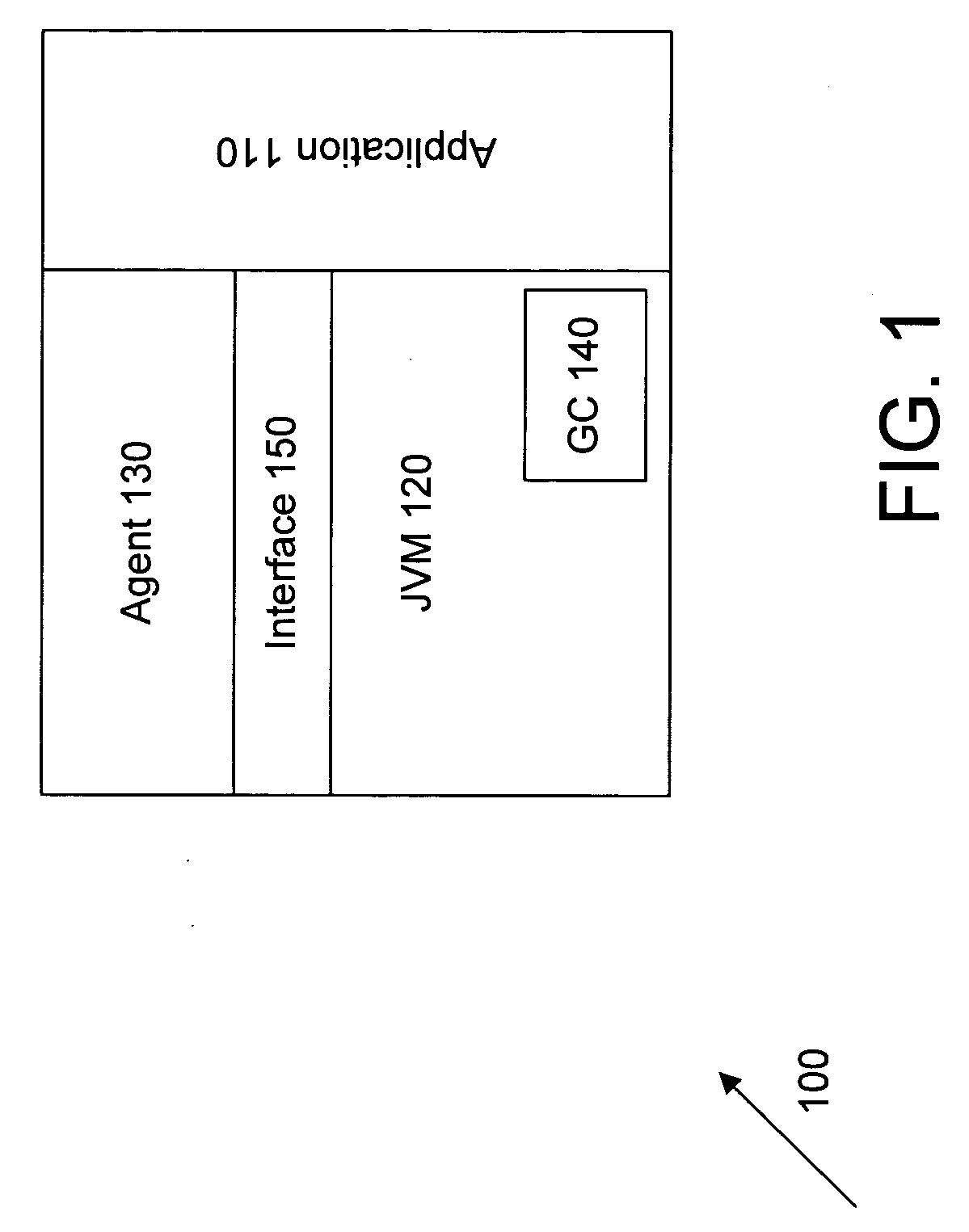
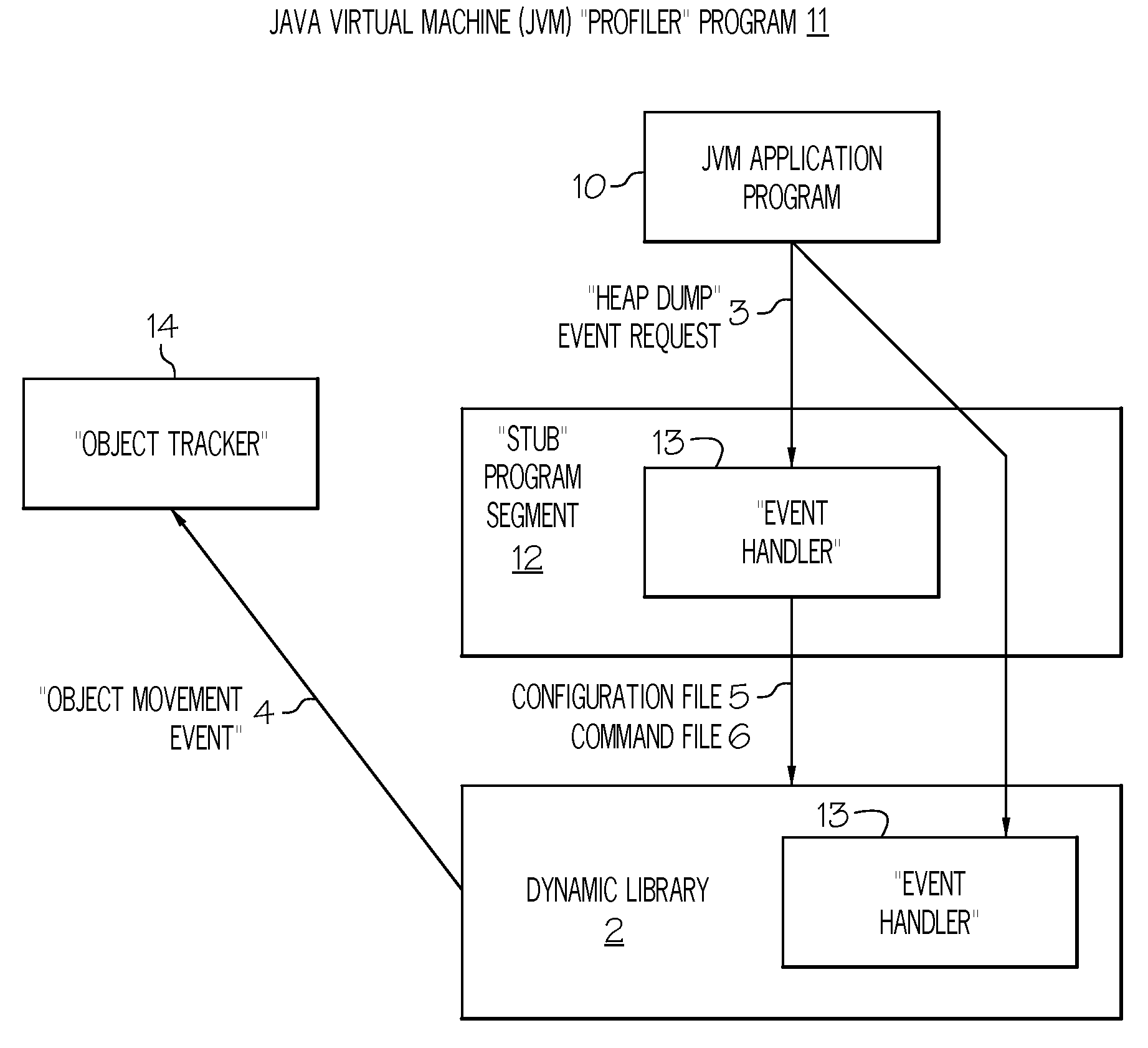
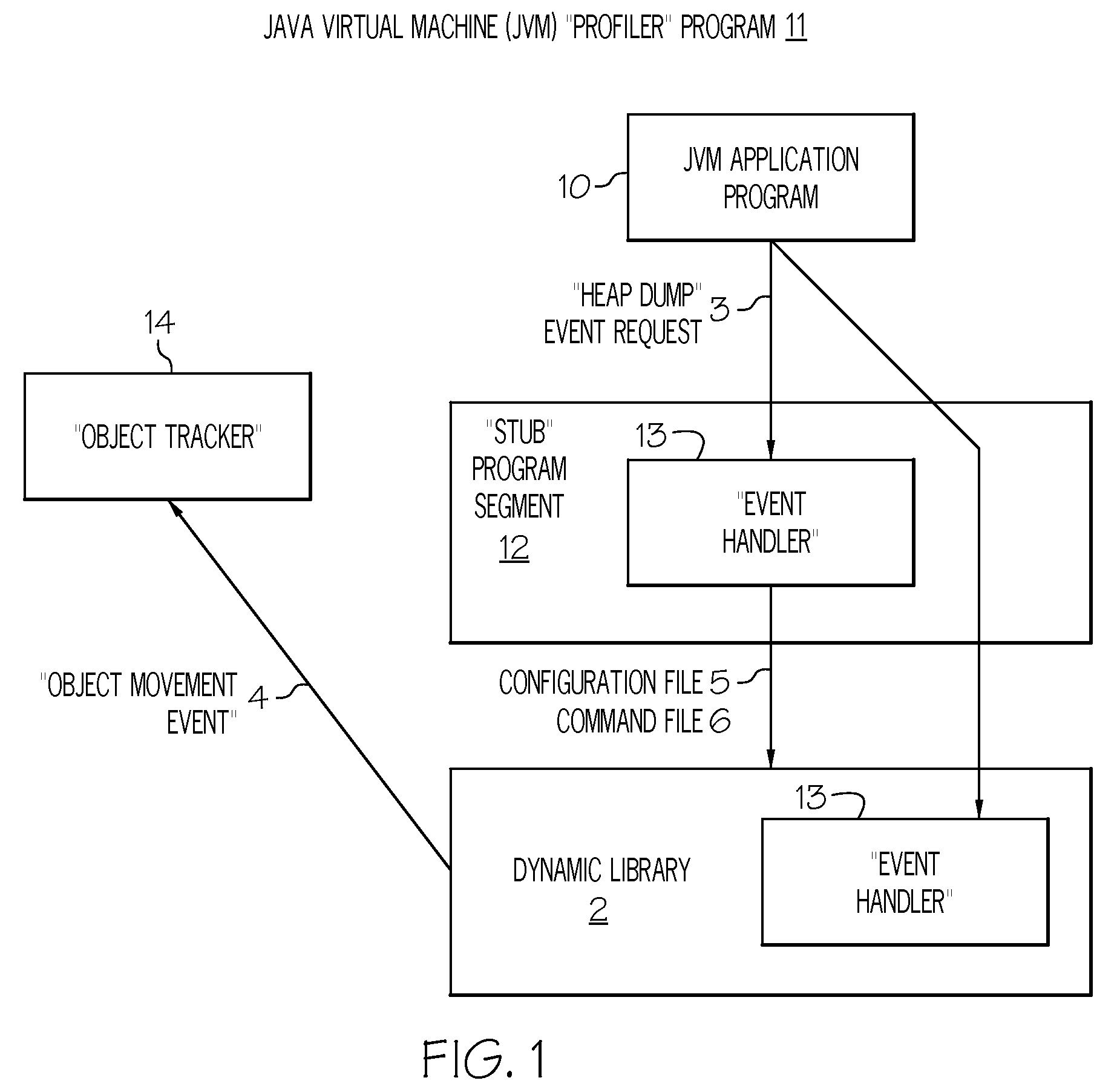
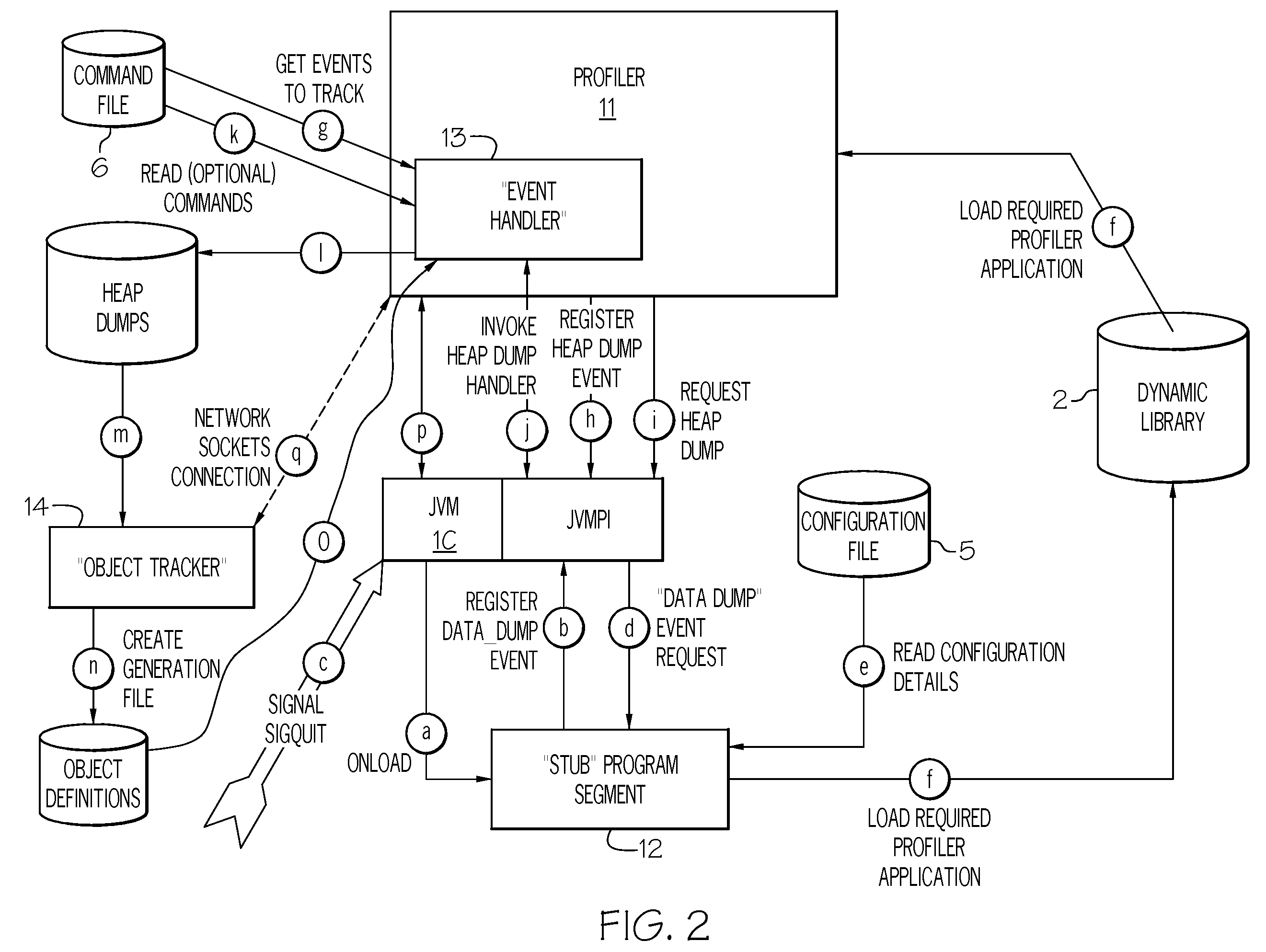
Method and system for analyzing memory leaks occurring in JAVA virtual machine data storage heaps
InactiveUS20080209404A1Error detection/correctionSpecific program execution arrangementsProgram segmentParallel computing
An invention is disclosed for analyzing memory leaks occurring in Java Virtual Machine (JVM) data storage, consisting of a dynamically modifiable JVM “profiler” and an “object tracker” tool for analyzing the output from the profiler. Specifically, a method and system is disclosed for programming a JVM profiler used to analyze and correct memory leaks in stored data heaps, consisting of a program segment (or “stub”) initialized by the JVM application program interface to determine the parameters to be passed to the main profiler memory leak analysis program logic, which is then initialized by the stub to examine a minimal number of “heap dumps” in order to identify data elements or objects for the existence and / or correction of memory leaks. Updated information on data elements or objects can be requested from the profiler as needed by use of the object movement tracking option to record the details of subsequent changes in data memory storage status once a heap dump has been obtained.
Owner:IBM CORP
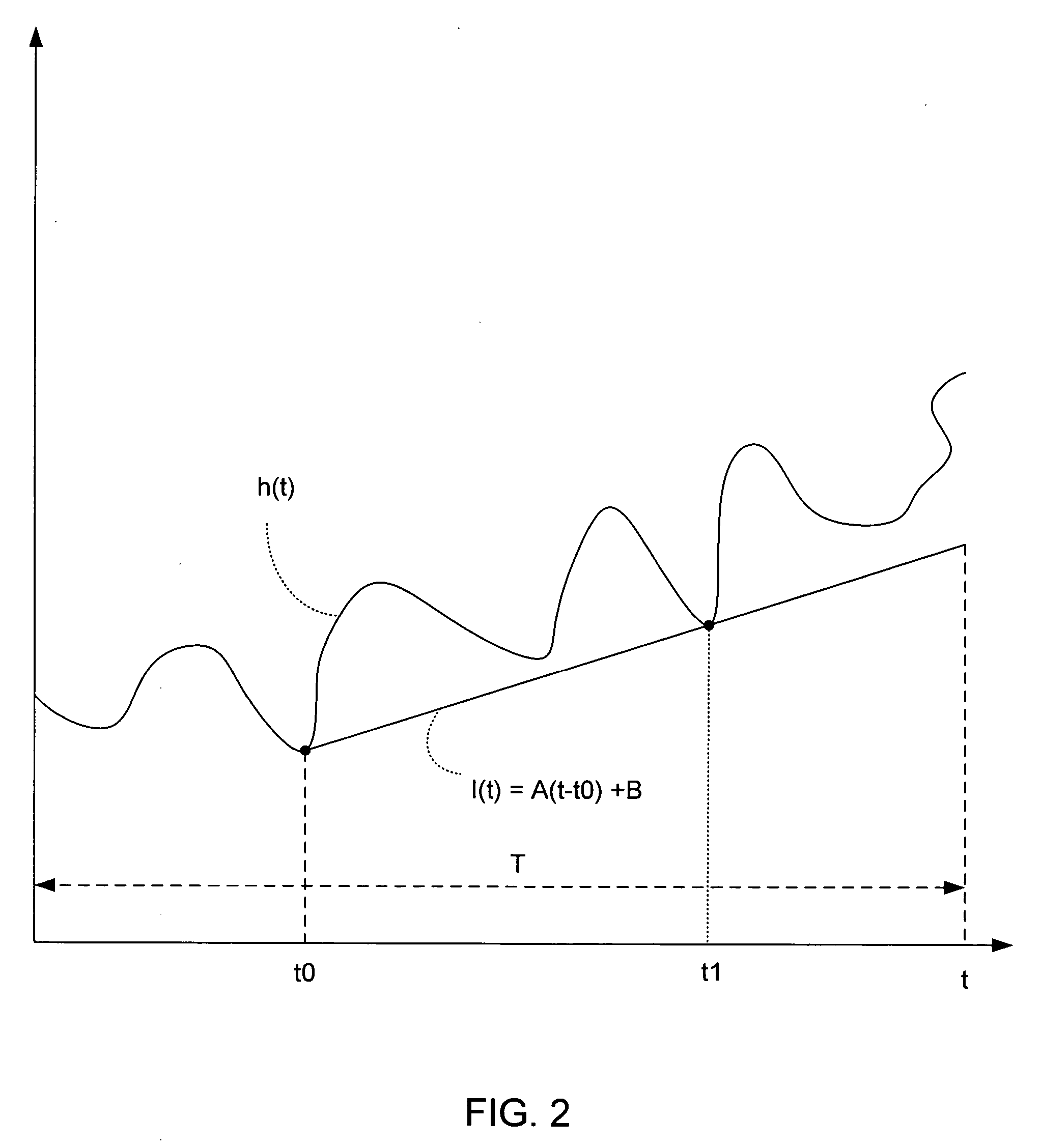
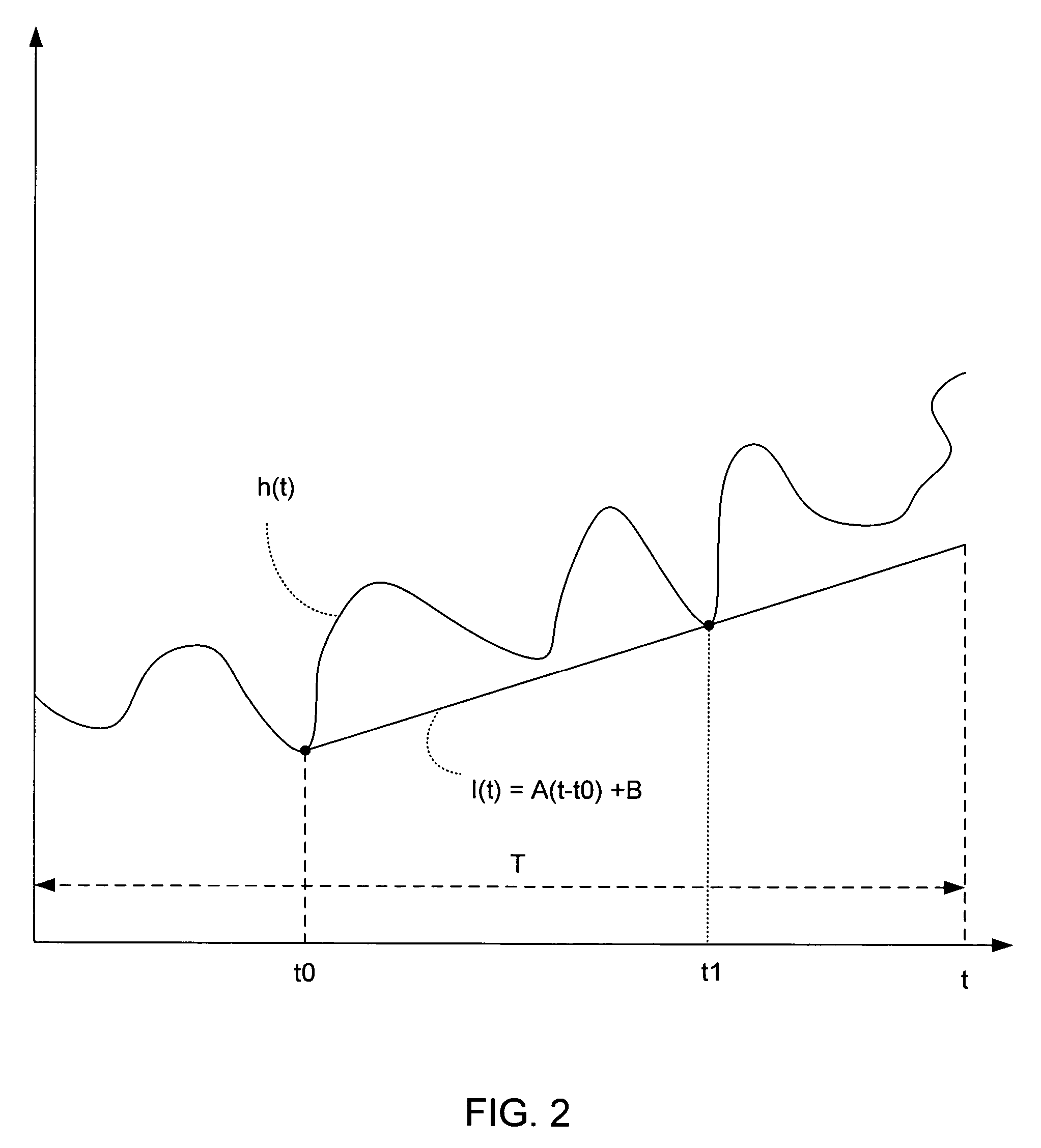
Identifying sources of memory retention
ActiveUS20070067758A1Reduce overheadMultiprogramming arrangementsNon-redundant fault processingMemory retentionParallel computing
One embodiment relates to a method for identifying sources of memory retention in an executing application. A size of a set of objects is tracked over multiple periods. A period is determined to be a growth period if the size for the set of objects increases above a previous maximum size, and the number of growth periods is counted. The set of objects is flagged as having potential undesired object retention (a memory leak) if the number of growth periods is greater than a threshold number. Other embodiments are also disclosed.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP +1
Method and system for predicting memory leaks from unit testing
InactiveUS20060085156A1Resistance/reactance/impedenceSpecial data processing applicationsTerm memoryUnit testing
A method for predicting memory leak in a computer program. The method includes acquiring a reference to a tested unit included in the computer program for preventing static data objects from being deallocated; repeatedly executing the tested unit for more than once; tracking which objects in the tested unit are allocated in a corresponding executing time; performing garbage collection; tracking which objects are deallocated during the garbage collection; comparing the object allocations to the object deallocations; and determining if every execution of the tested unit allocates memory that cannot be deallocated.
Owner:PARASOFT
Memory leakage management
ActiveUS20060095427A1Enhance memory leakage managementAttenuate memory leakageMemory architecture accessing/allocationError detection/correctionParallel computingMemory leak
Owner:META PLATFORMS INC
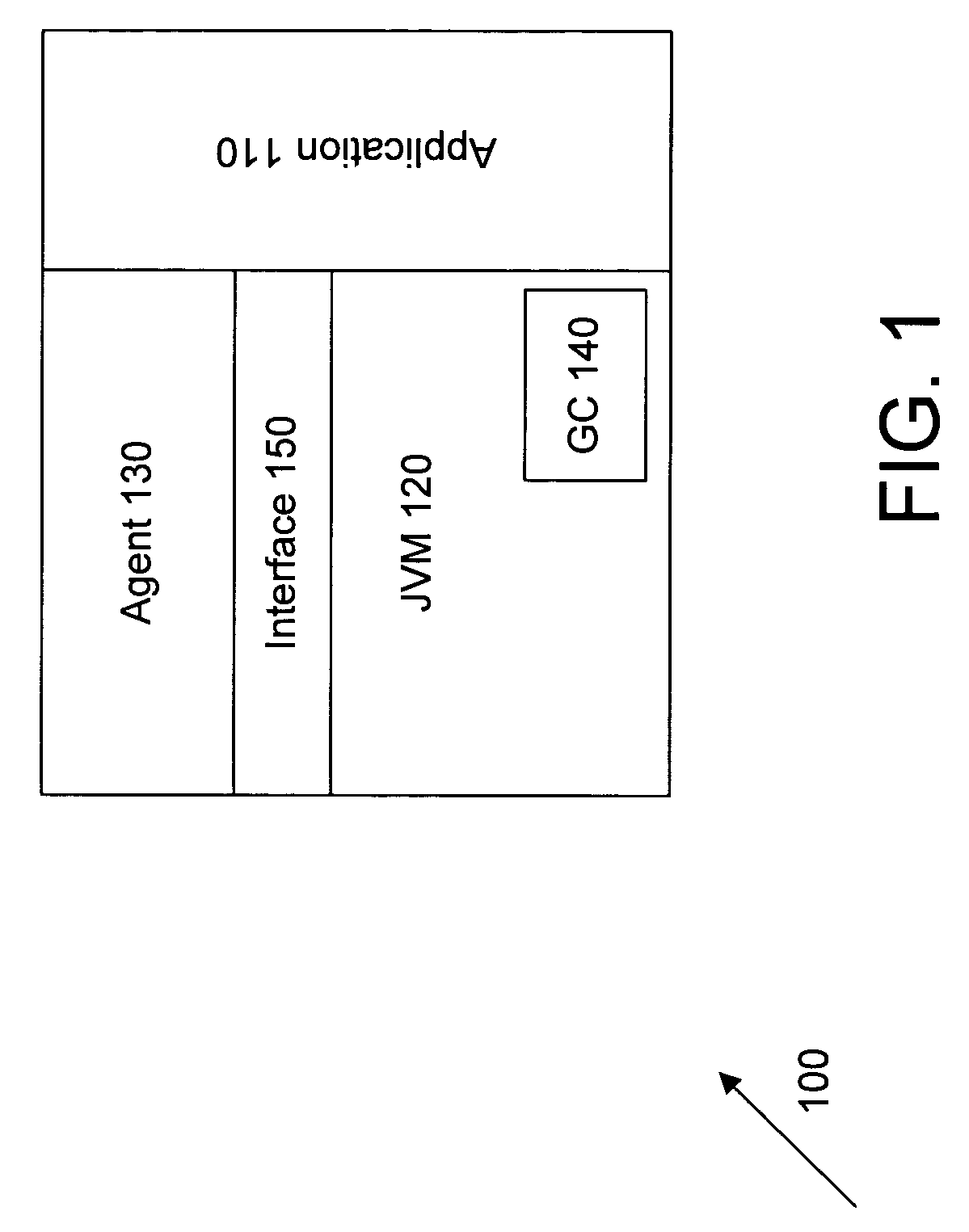
Method and system to optimize JAVA virtual machine performance
InactiveUS20080046673A1Improve resource utilizationImprove application stabilityError detection/correctionSpecific program execution arrangementsParallel computingDEVS
A method to assist a software developer in optimizing performance of a Java virtual machine (Jvm) is disclosed. The method includes creating a model to predict future usage of heap memory by the Jvm. In response to the time series analysis model having an upward trend of heap memory usage, advising the developer to review a heap dump to determine if a possible memory leak exists. In response to the time series analysis model having a horizontal asymptote at a predicted future time, advising the developer to specify the maximum limit of heap memory as a function of the horizontal asymptote. In response to a heap exhaustion error, which indicates a requested usage of heap memory by the Jvm greater than a maximum limit of heap memory, determining a likely cause of the heap exhaustion error, and advising the developer to take appropriate actions to optimize the Jvm performance.
Owner:IBM CORP
Methods, systems and computer program products for detecting memory leaks
InactiveUS20060212852A1Error detection/correctionSpecific program execution arrangementsParallel computingMemory leak
Methods of detecting a memory leak may include identifying a largest ChildNode of a ParentNode; and comparing a total size of the ParentNode to a total size of the largest ChildNode of the ParentNode. If the total size of the ParentNode is significantly larger than the total size of the largest ChildNode of the ParentNode, a possible memory leak area may be identified. Related systems and computer program products are also discussed.
Owner:IBM CORP
Identifying memory leaks in computer systems
InactiveUS7434206B2Non-redundant fault processingSpecific program execution arrangementsObject basedComputerized system
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Mobile memory divulgence protection method and system
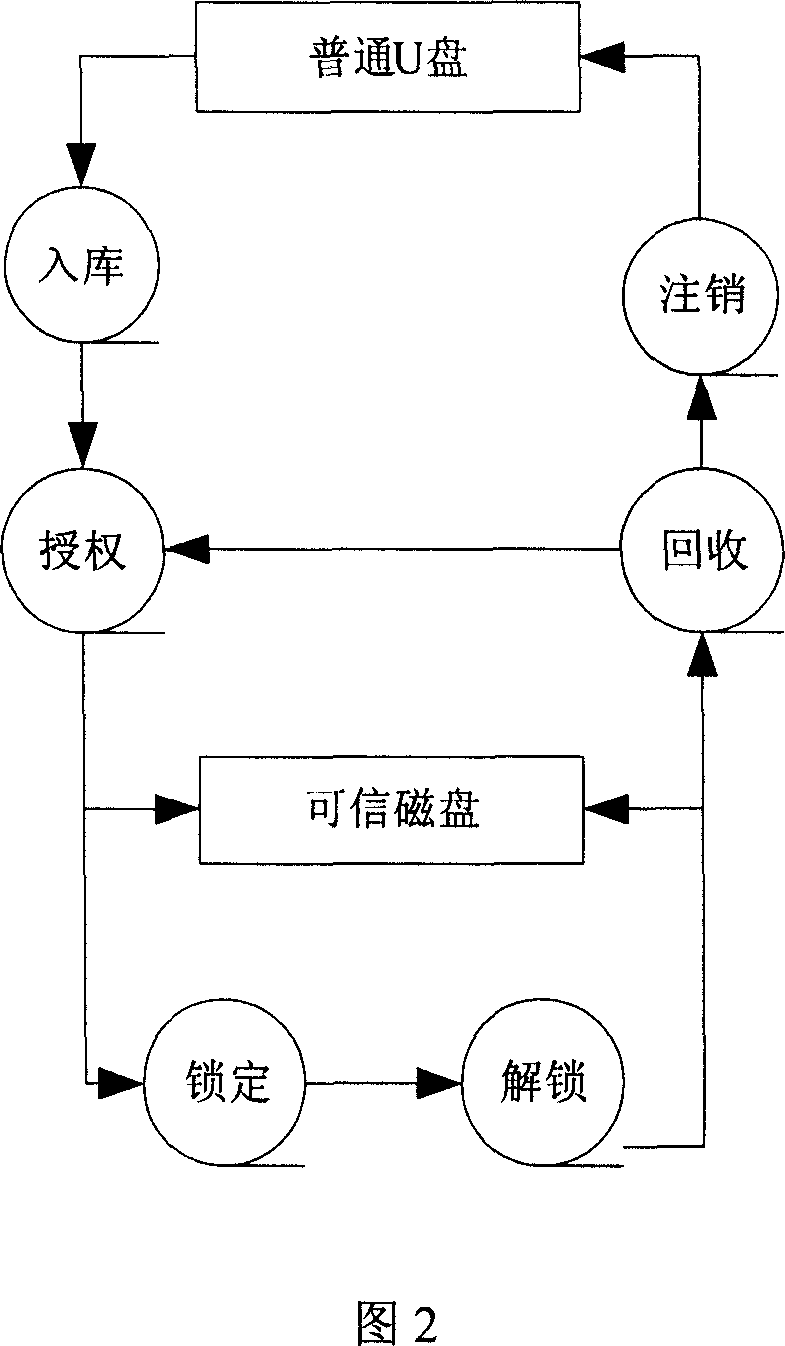
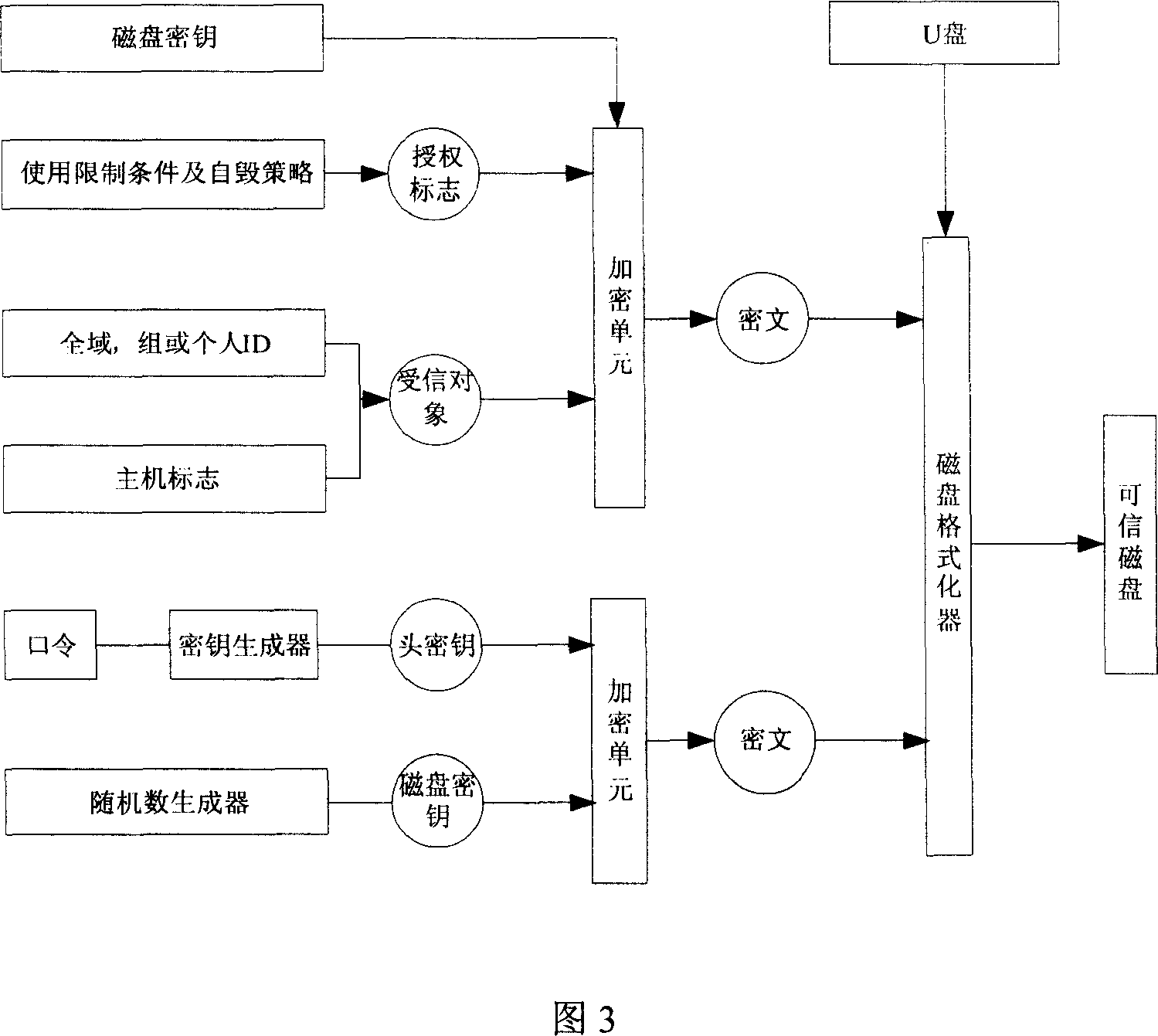
InactiveCN101079008AEasy to manageReach protectionUnauthorized memory use protectionInternal/peripheral component protectionCiphertextFloppy disk
The invention discloses a method of shifting memory leaking secret protection and system to realize the method, which is characterized by the following: utilizing virtual disk technique; adopting disk grade bridging method; proceeding encryption for the data in the common memory through the virtual disk with special pattern; storing the data on the shifting memory with cryptogram style; loading the virtual disk before reading or writing data; proceeding order checkout and user identification proved; non-loading without right order or special form; assuring the safety of the data in the shifting memory; setting the system as three module of server, warranting center and custom terminal. This invention can be used to various memories such as flash memory, shifting hard disk, soft disk and so on.
Owner:CHINA NAT SOFTWARE & SERVICE
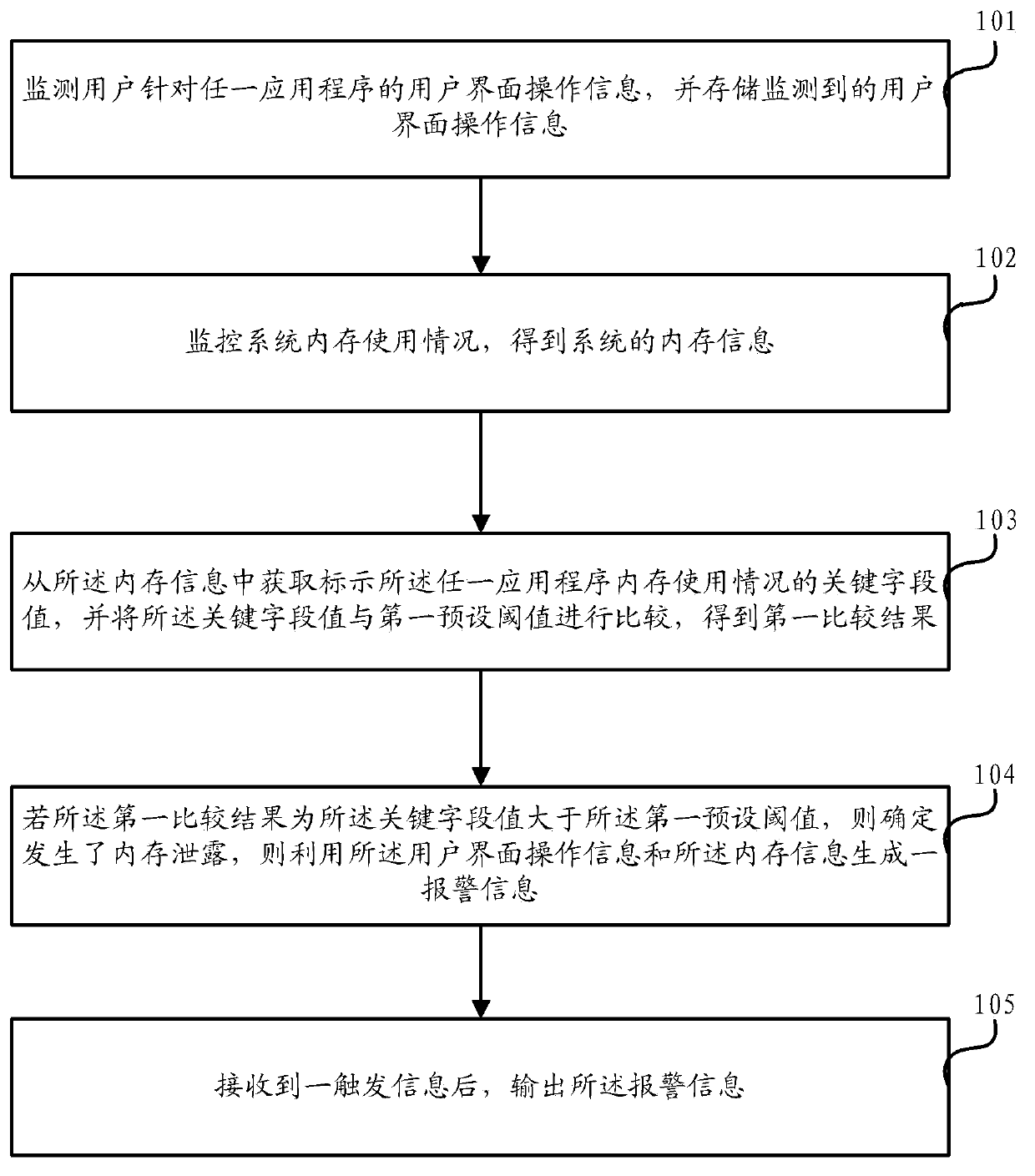
Method and device for monitoring leakage of memory
The invention discloses a method and a device for monitoring leakage of a memory. The method comprises the following steps of monitoring the operation information of a user interface of a user on an application program, and storing the monitored operation information of the user interface; monitoring the usage condition of the memory of a system, and obtaining the information of the memory of the system; obtaining the key field value for indicating the usage condition of the memory in the application program from the information of the memory; if the first comparison result indicates that the key field value is greater than the first preset threshold, determining the occurrence of leakage of the memory, and utilizing the operation information of the user interface and the information of the memory to generate alarming information; after receiving triggering information, outputting the alarming information. The method and the device have the advantage that the particular operation scene which occurs during the leakage of the memory can be determined, and the corresponding LOG information is analyzed, so a developer can quickly locate the use problem of the memory in the program.
Owner:LENOVO (BEIJING) LTD
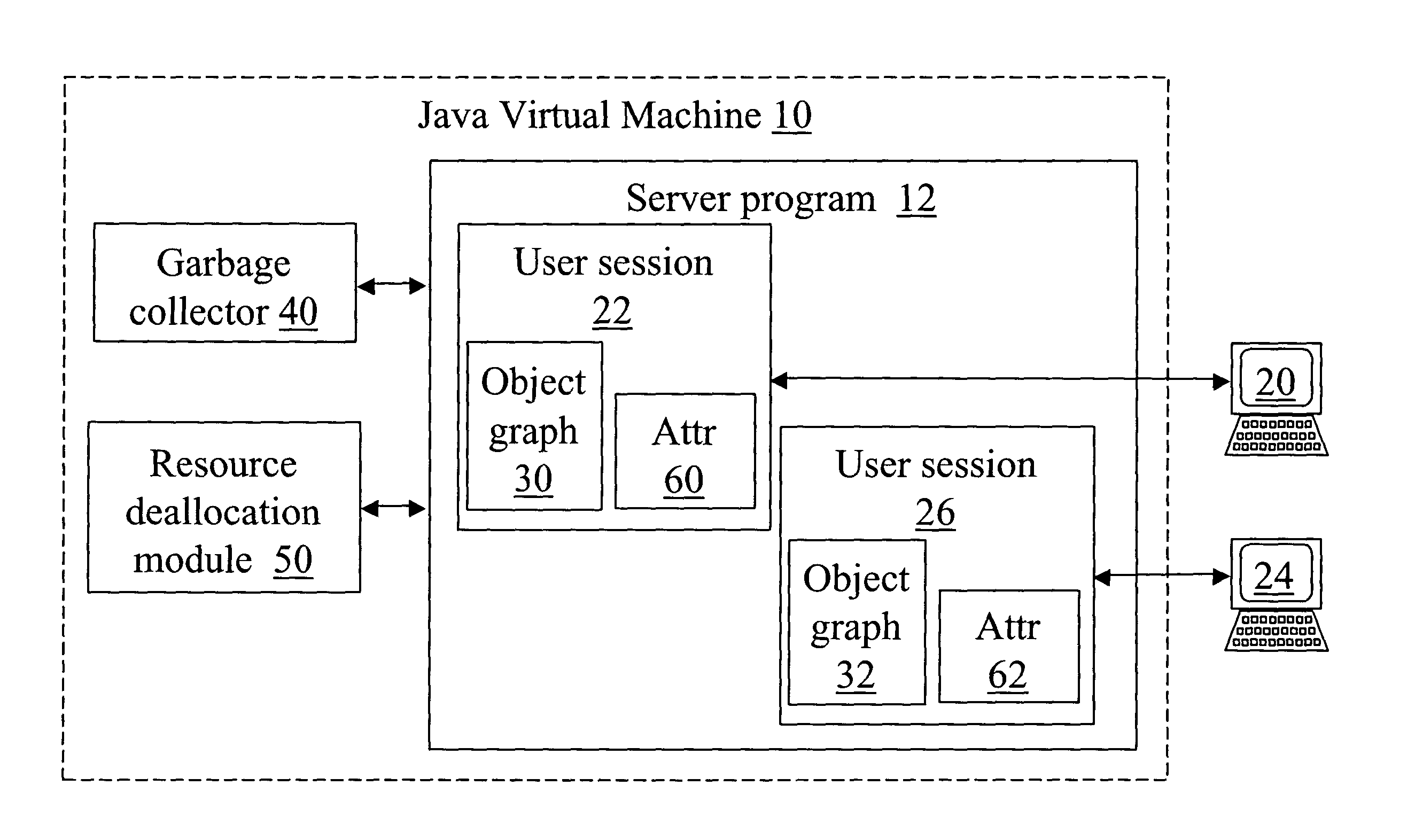
Method and system for resolving memory leaks and releasing obsolete resources from user session data
A software program (12) is configured to initiate, process, and terminate user sessions (22, 26). A resource deallocation module (50) is linked to the software program (12) to deallocate allocated external resources of each object of a user session responsive to an impending termination of said user session. An automatic memory management module (40) is invoked by the software program with respect to said user session subsequent to the deallocation performed by the resource deallocation module (50) and prior to the termination of said user session.
Owner:IBM CORP
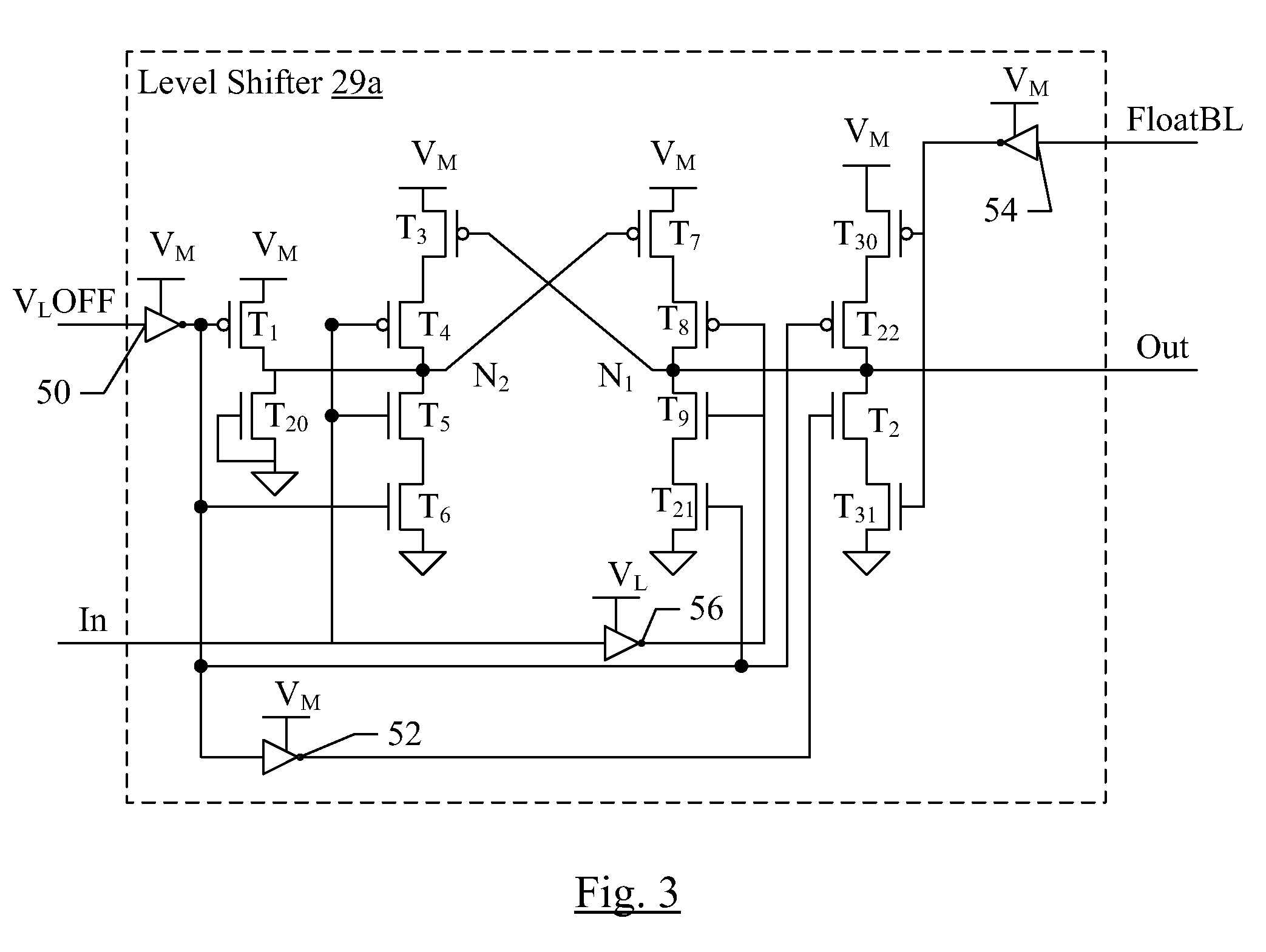
Leakage and NBTI Reduction Technique for Memory
In one embodiment, an integrated circuit includes a logic circuit and a memory circuit that includes multiple bit lines and bit line precharge circuits. The memory circuit may include level shifters for control signals generated from logic circuit inputs, and particularly there may be one or more level shifters that generate precharge enable signals to control the bit line precharge circuits. The level shifters for the bit line precharge circuits may also be controlled, during periods of time that the memory circuit is idle, by an input control signal (FloatBL herein). If the FloatBL signal is asserted, the bit line precharge circuits may be disabled to float the bit lines. In some embodiments, the FloatBL signal may also disable bit line bit line hold circuits on the bit lines. In some embodiments, when the memory circuit is exiting an idle state, the bit line precharge circuits may be enabled in a staggered fashion.
Owner:APPLE INC
Method and device for monitoring memory
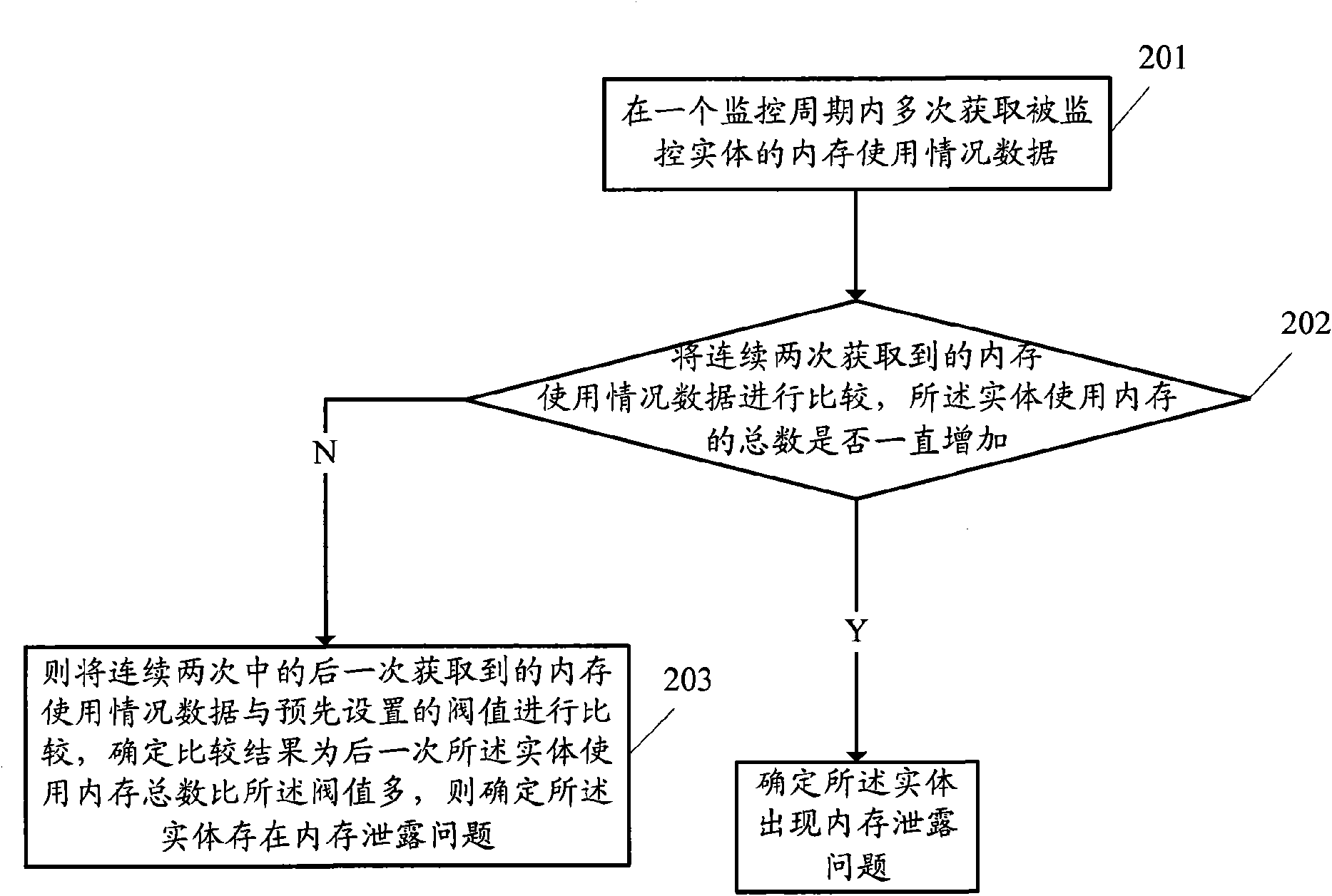
ActiveCN101599048AMemory leak monitoringObvious memory leak problemSoftware testing/debuggingData switching networksMemory leakOperating system
The invention discloses a method and a device for monitoring memory, which are used for monitoring memory usage of an entity using the memory. Memory usage data of the entity to be monitored is saved in a memory cell of memory usage data; and the memory usage data of the entity to be monitored changes along with the memory usage of the entity to be monitored. The method comprises the following steps: acquiring the memory usage data of the entity to be monitored for a plurality of times from the memory cell of the memory usage data and comparing the memory usage data acquired from two consecutive times in a monitoring cycle; and if the total memory usage of the entity of the latter time is always larger than that of the former time in each acquired comparison result, confirming the phenomenon of memory leak in the entity. The method and the device provided by the invention can timely discover the problem of imperceptible memory leak in a system.
Owner:BEIJING ZHIGU TECH SERVICE
Embedded system test method
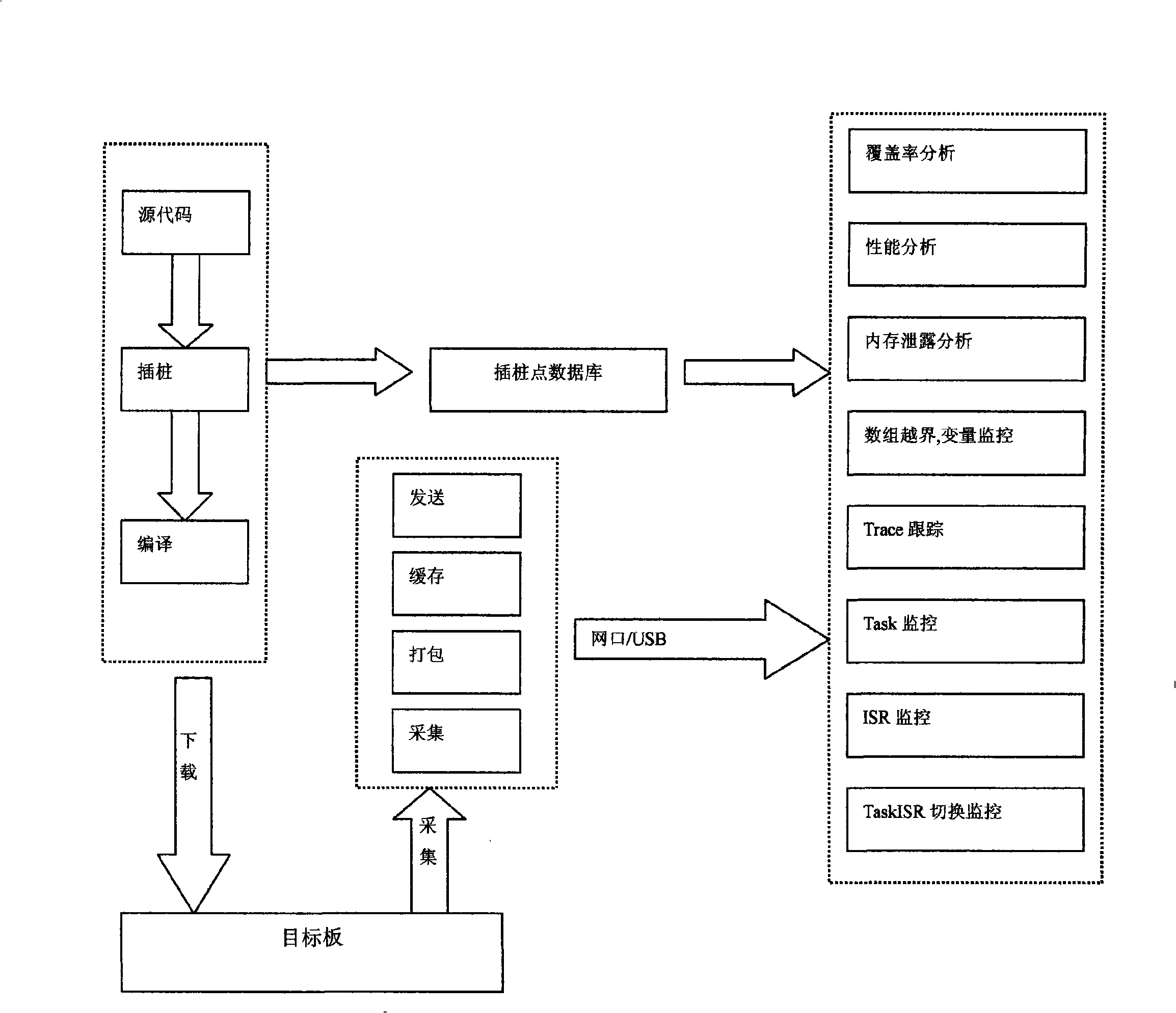
InactiveCN101408862AAccurate samplingAddressing the downsides of testingSoftware testing/debuggingSystem testingData acquisition
The invention relates to an embedded system testing method. Hardware and assistance software are adopted; firstly, pile pitching is carried out on a source code, a sentence is inserted in a specific place, then a pile pitching document is compiled and downloaded; when a target board operates to a pile pitching point, a bus presents specific signals, the auxiliary hardware of a data acquisition unit acquires the signals of the pile pitching points; subsequently, the acquisition point information is packed and sent to a testing result analyzing software for result analysis, thus the embedded system testing is realized. The testing includes coverage analysis, performance analysis, memory leak analysis, array out-of-range, variable control, trace following, Task monitoring, ISR monitoring, TaskISR switching monitoring, etc.
Owner:李周
Apparatus and method for detecting memory leaks
A system and method for detecting memory leaks includes a monitoring agent, a user interface for configuring operating parameters and a reporting mechanism. The monitoring agent determines allocated memory levels of a monitored application at a sampling frequency and determines when a then-existing “peak” memory level has increased. The monitored application is determined to be leaking memory when a determined number of increases in the peak allocated memory level are detected. The determined number may be fixed ahead of time or may be calculated dynamically based on user specified parameters. When a given memory leakage rate is exceeded, an alarm response is taken, which may be either a specified notification of the alarm or an action. Certain increases in the peak allocated memory levels are ignored as not necessarily being indicative of a memory leak condition, such as during startup of the program or between rapidly, closely-occurring increases in the peak allocated memory level.
Owner:LAKESIDE SOFTWARE LLC
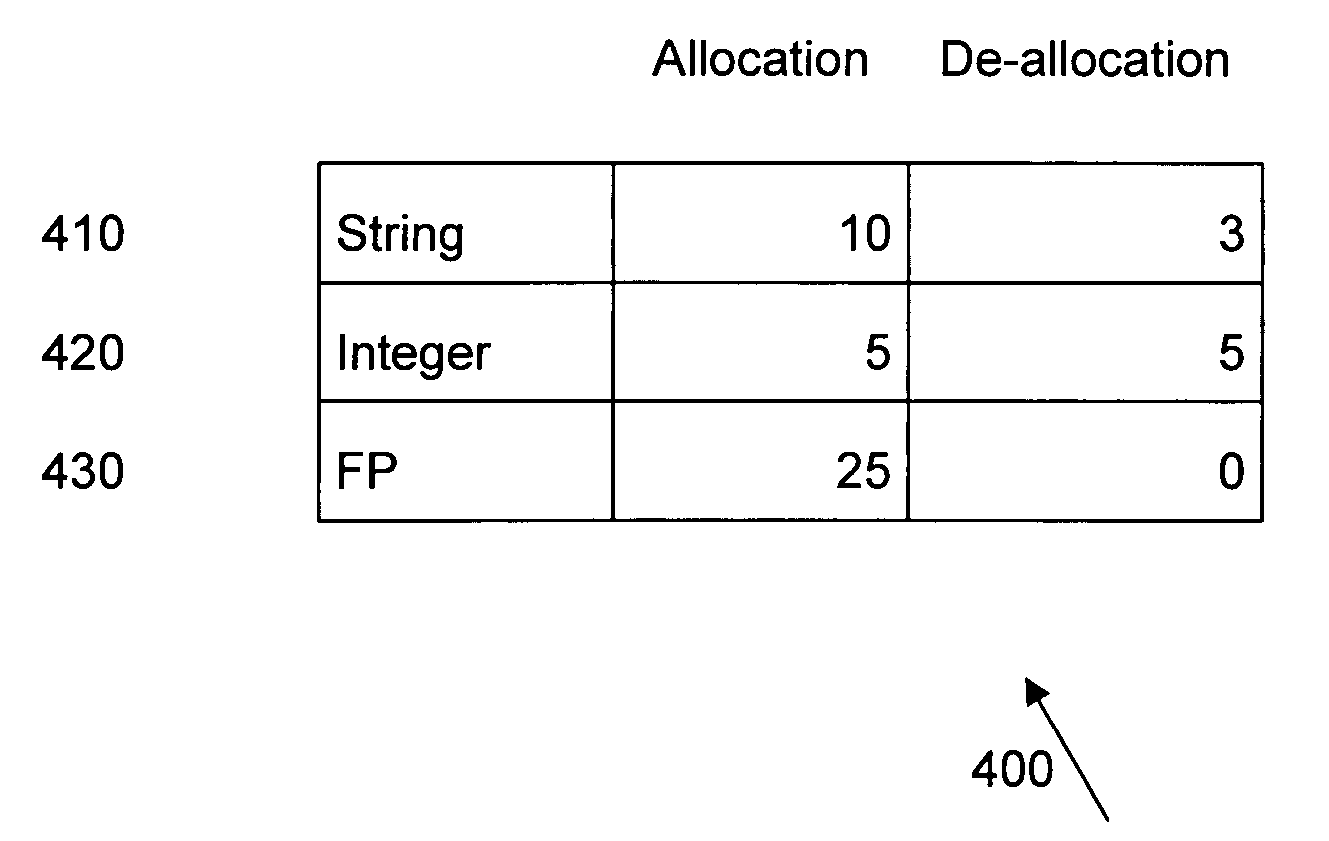
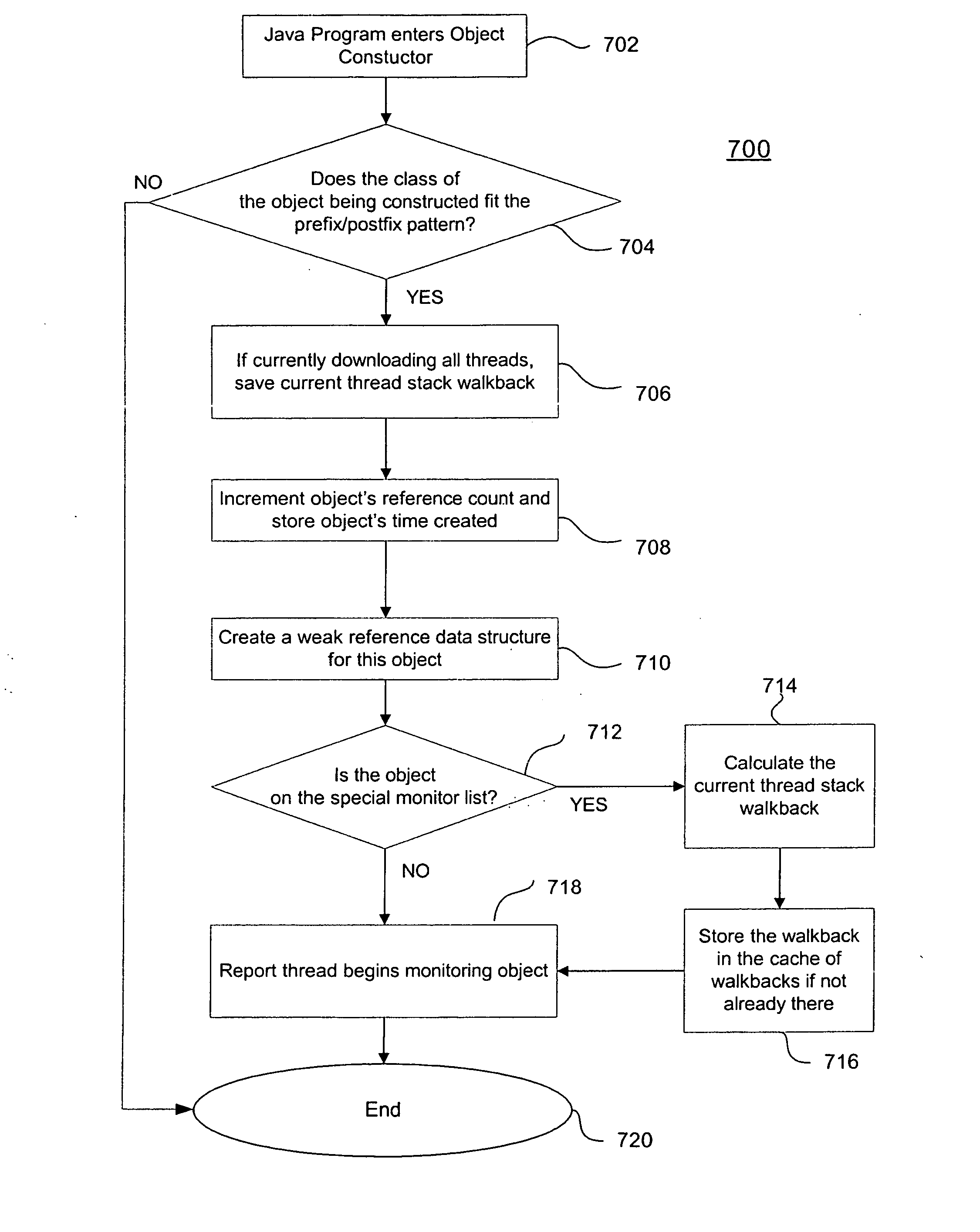
Method, system and article for detecting critical memory leaks causing out-of-memory errors in Java software
InactiveUS20050204341A1Error detection/correctionSpecific program execution arrangementsObject ClassSoftware system
An analysis tool for specifically identifying the cause and location of critical memory leaks within a large software system is provided. The analysis tool transparently adds multiple processing threads that collaborate to identify sources of potential memory leaks in the software being analyzed. These threads provide notifications of object classes executing in the software that have had excessive instance counts or have exceeded the average lifetime of an object. A stack walkback is performed on objects being monitored as an out-of-memory condition approaches and while there is still sufficient memory available to unwind and store the stack walkback. By saving the stack walkbacks just prior to the out-of-memory failure, the analysis tool operator is thereby provided sufficient information to make a final determination of objects that are possible candidates for memory leaks and subsequently modify the software to reduce or eliminate the memory leaks.
Owner:IBM CORP
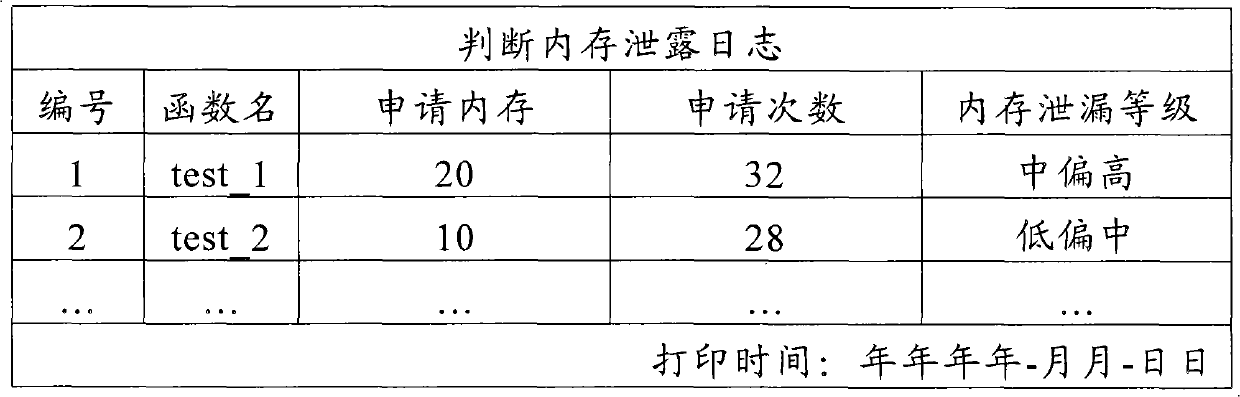
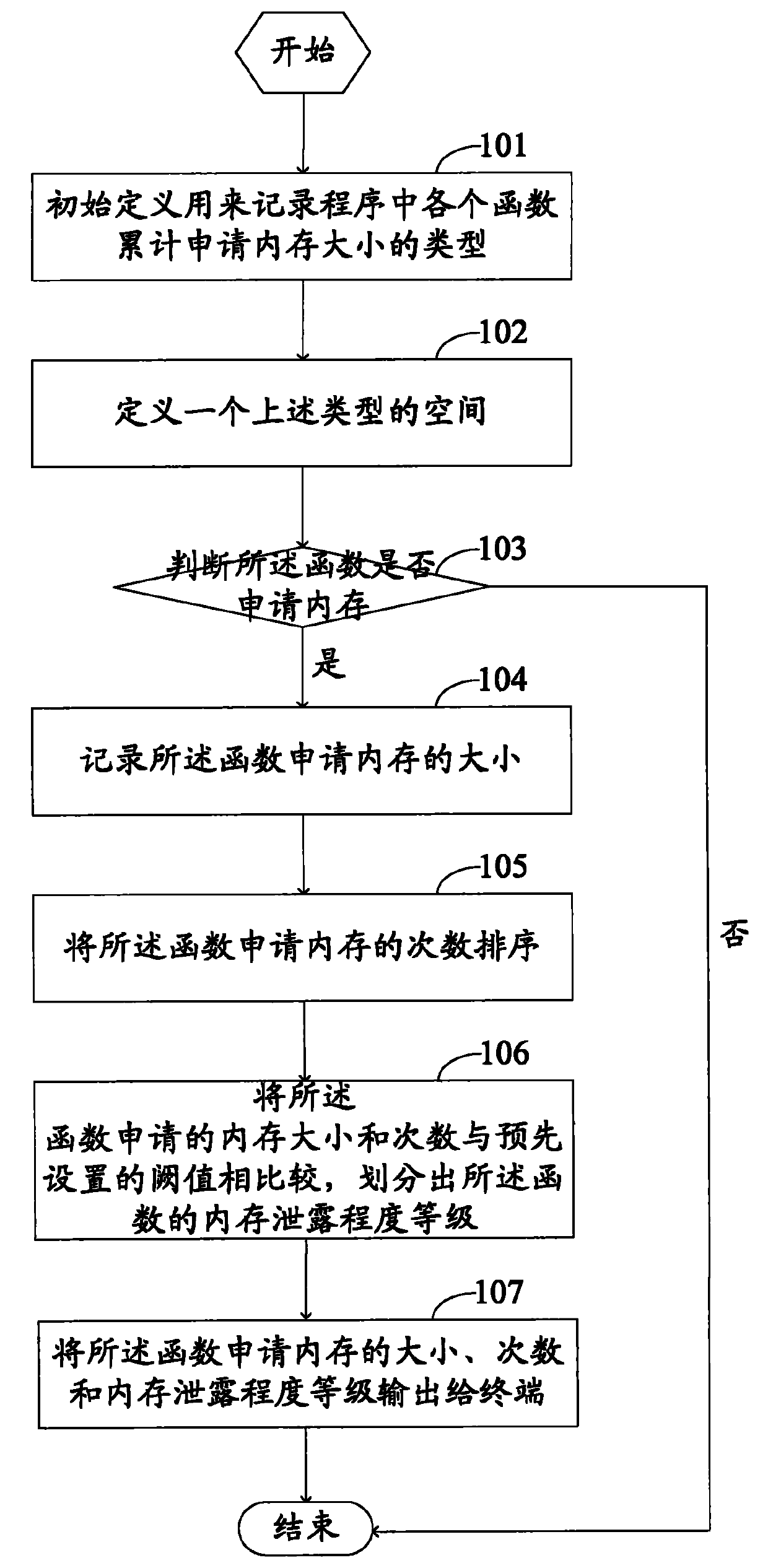
System and method for judging memory leak
The invention provides a method for judging memory leak, comprising the following steps of: when a function application memory is judged aiming at each function in a program, accumulating the memory capacity and the application times of the named function application; when a function release memory is judged, reducing the released memory capacity from the memory capacity of the named function accumulated application and reducing release memory times from accumulated application times; sequencing the memory capacity and the times of the function application in different names in a descending mode by using the memory capacity as priority; ensuring and outputting a level of a memory leak degree according to the memory capacity and the times of the function accumulated application in different names; in addition, the invention provides a system for realizing the method in order to sequence memory distribution and information release according to the memory application times and liberate a programmer from large fussy analytical work.
Owner:BEIJING HAITAI FANGYUAN HIGH TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com