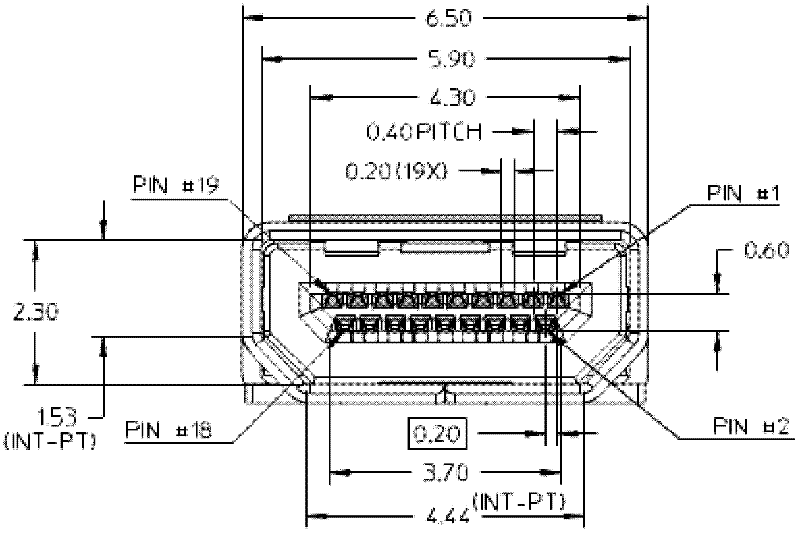
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
332 results about "Function application" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In mathematics, function application is the act of applying a function to an argument from its domain so as to obtain the corresponding value from its range.
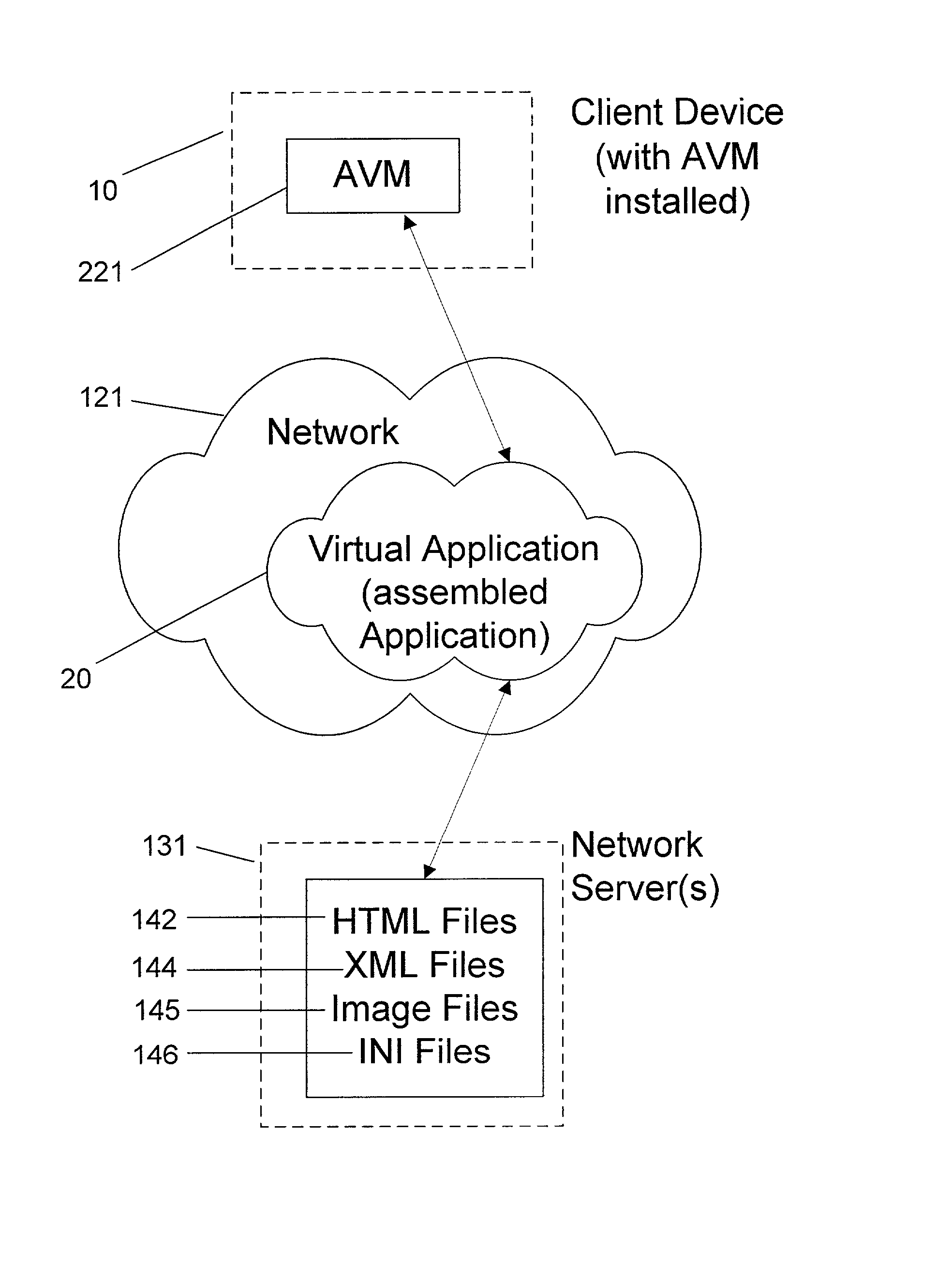
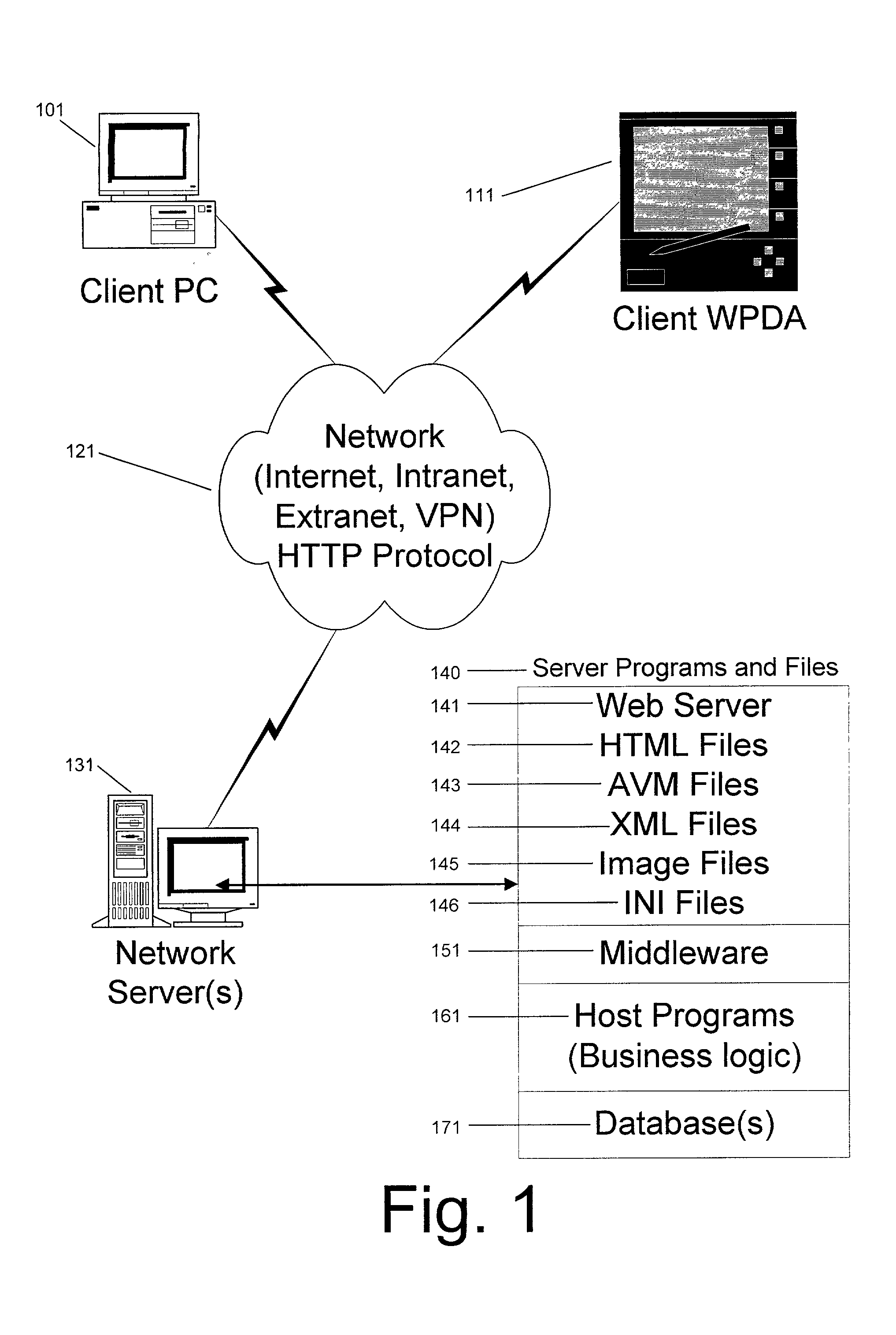
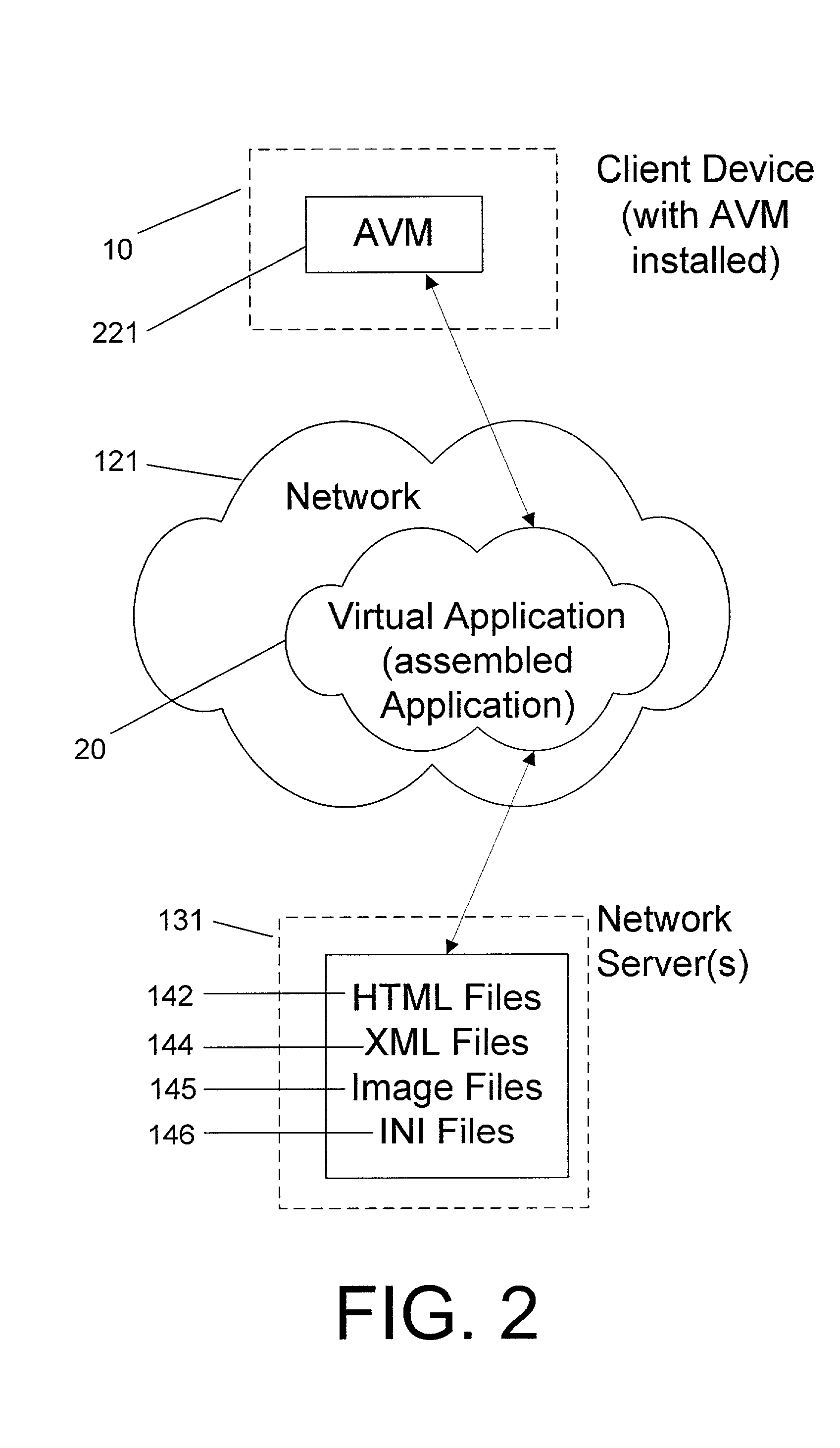
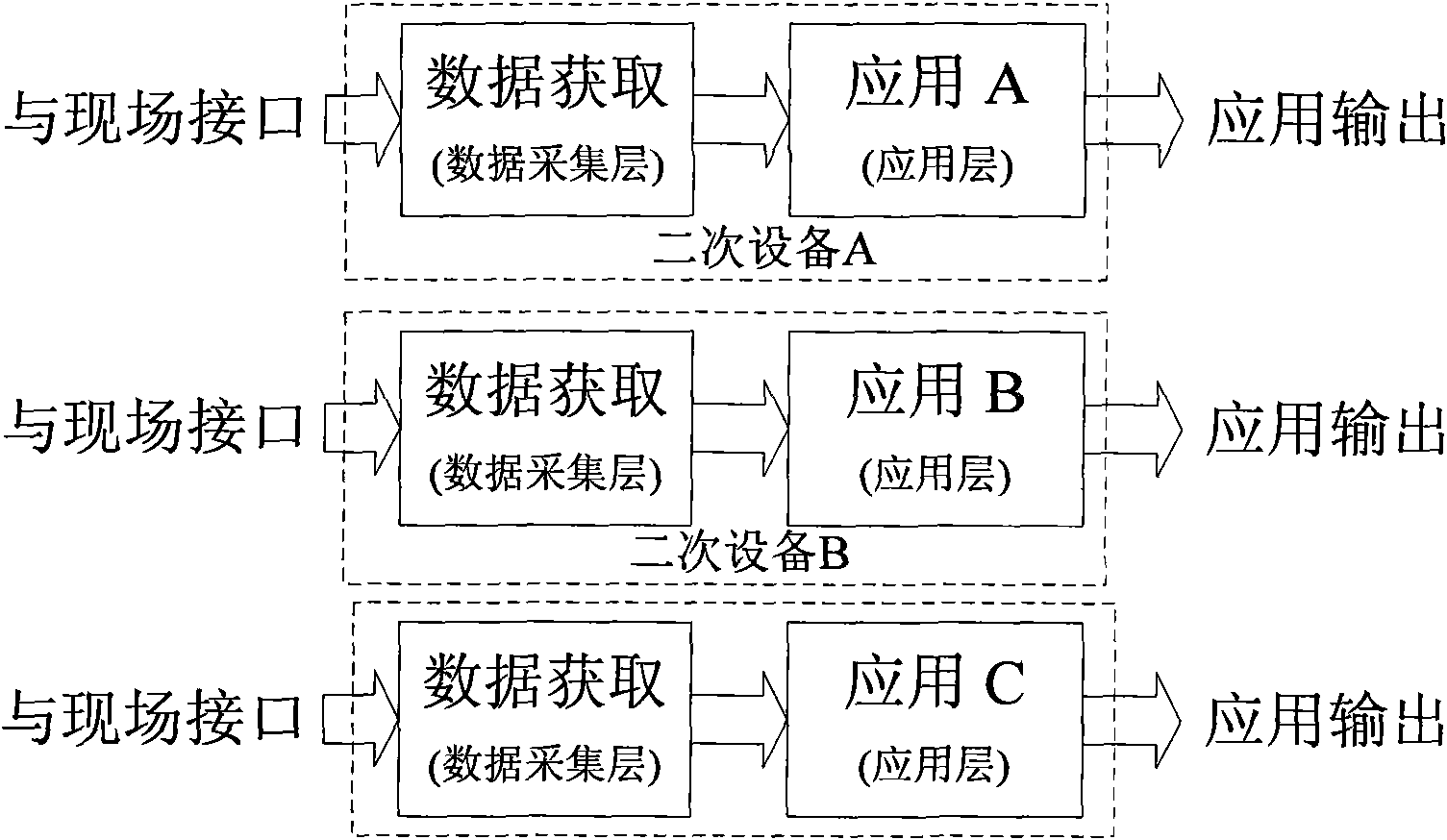
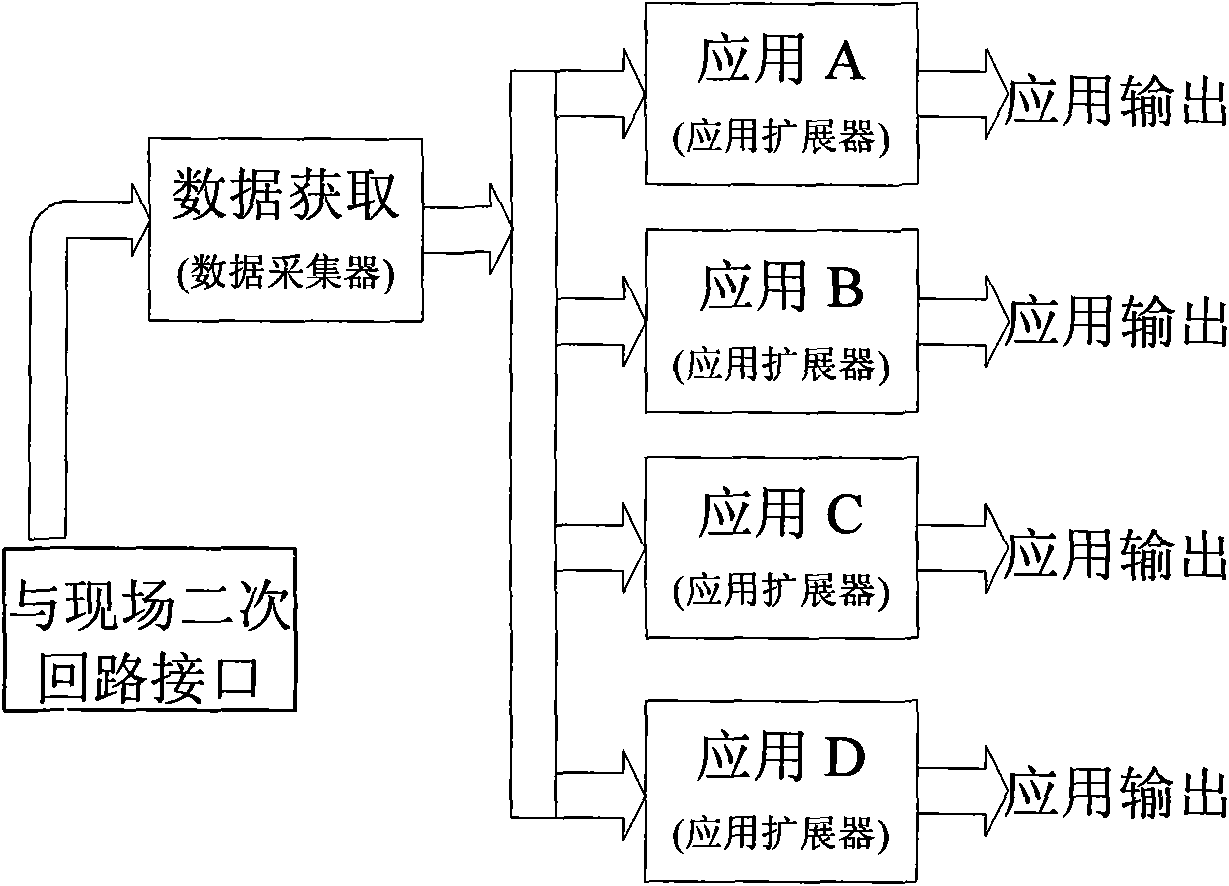
System and method for deploying and implementing software applications over a distributed network
ActiveUS20020129129A1Multiple digital computer combinationsProgram loading/initiatingApplication softwareProgram logic
A system for deploying applications over a distributed network to web-enabled devices uses a server, with stored text files containing application logic, and an application assembler. The application assembler downloads and installs on each web-enabled device. Then, the application assembler downloads one or more text files from the server, retrieves program logic from each of the downloaded text files, and assembles the retrieved program logic into a functioning application. In some instances, a plugin that is downloaded and installed on each web-enabled device is activated by web pages on the server to launch the application assembler.
Owner:DATACLOUD TECH LLC
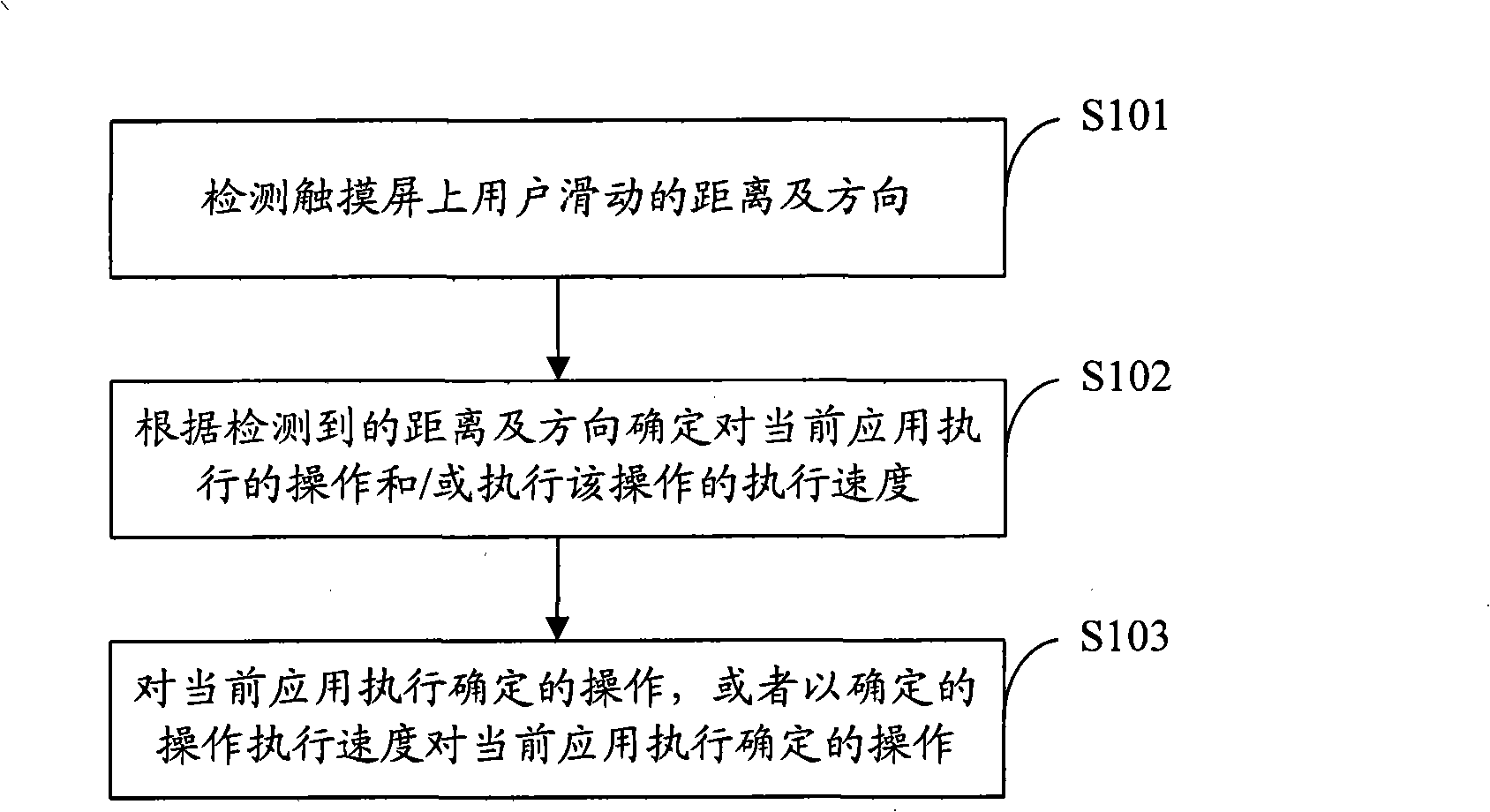
Interaction control method and system based on touch screen
InactiveCN101308440AAchieve accelerationAchieve a controlTelephone sets with user guidance/featuresInput/output processes for data processingInteraction controlTime control
The invention is applied to the field of information technology and provides a touch screen-based interactive control method and a system; the method comprises the following steps: to detect the sliding distance and direction of the user on a touch screen; to determine the operation of the current application implementation and / or the implementation speed for implementing the operation, according to the detected distance and direction; to operate the determination of the current application implementation, or to operate the determination of the current application implementation at a determined operating implementation speed. In an embodiment of the invention, the corresponding functions pre-installed with the system can be continuously implemented through detecting the sliding distance and direction of the user on the touch screen, so as to achieve that the acceleration of the corresponding function application can be controlled through the sliding distance; meanwhile, the purpose of continuously implementing the corresponding function application upon one-time control can be effectively achieved.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
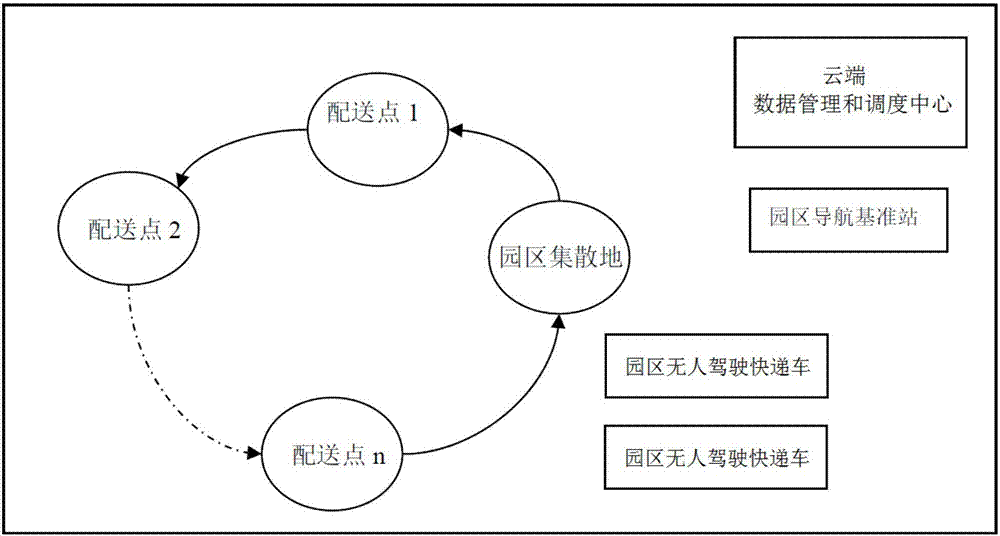
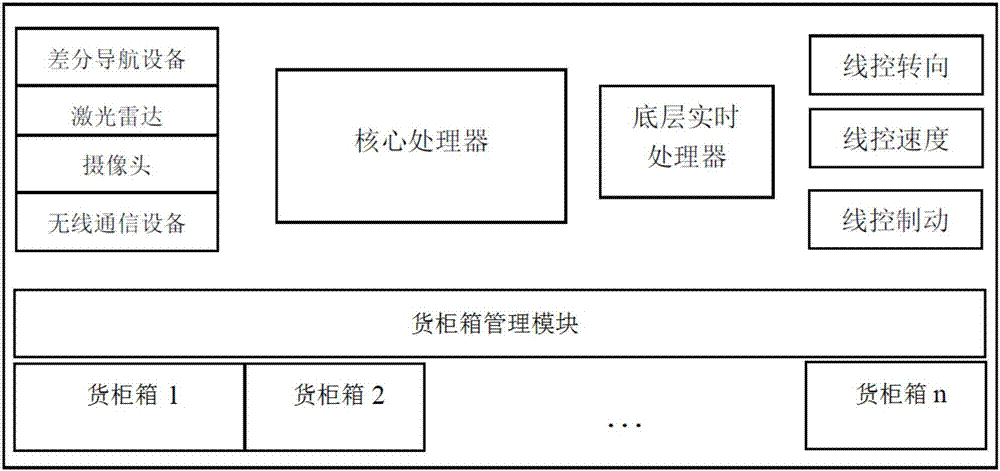
Park unmanned express-delivery vehicle dispensing system and automatic dispensing method thereof
InactiveCN107133771ATroubleshooting automated shipping issuesImprove experienceForecastingIndividual entry/exit registersLogistics managementControl layer
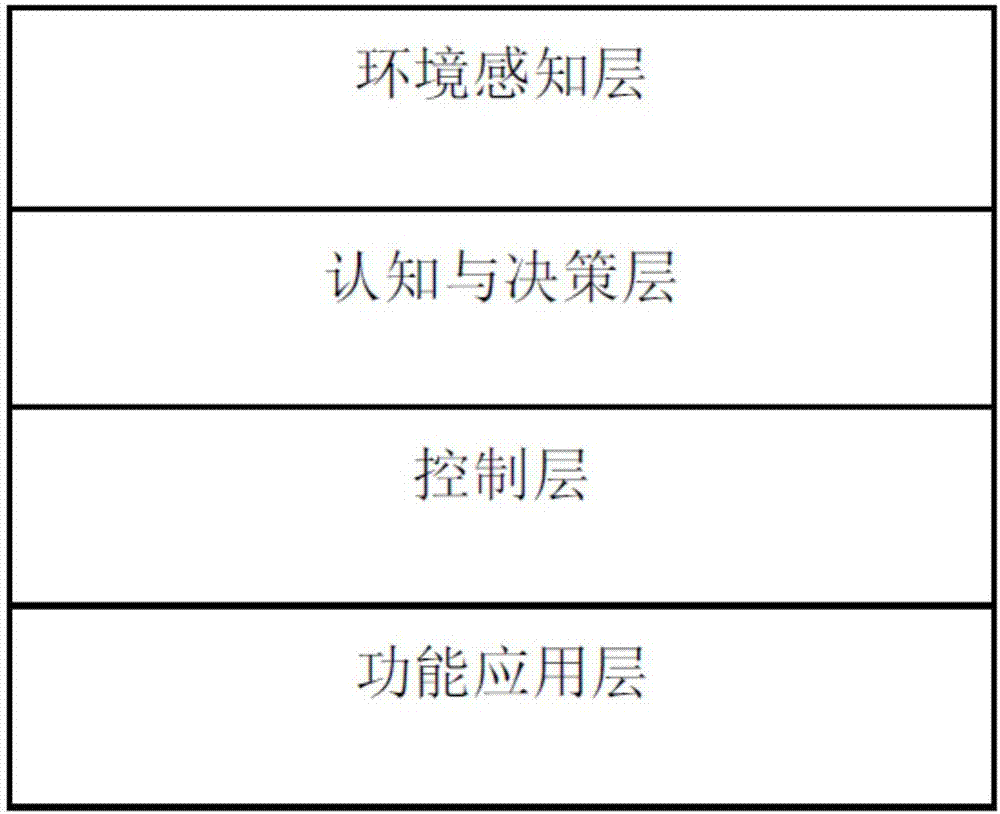
The invention relates to a park unmanned express-delivery vehicle dispensing system and an automatic dispensing method thereof. The system comprises a data management and scheduling center, a park navigation reference station, a park unmanned express-delivery vehicle and wireless communication equipment; and includes an environment sensing layer, a cognition and decision layer, a control layer and a function application layer. The system and method can be used to solve the problems in unmanned logistics automatic dispensing in the last kilometer of a park, district and the like; automatic dispensing schemes from establishment of the automatic dispensing system of the park, the automatic dispensing method, automatic driving of the vehicle, information pushing and identity recognition of an owner of an express are all included; and technical coverage is comprehensive, the system and method are conducive to popularization and application and the user experience is good.
Owner:BEIJING UNION UNIVERSITY
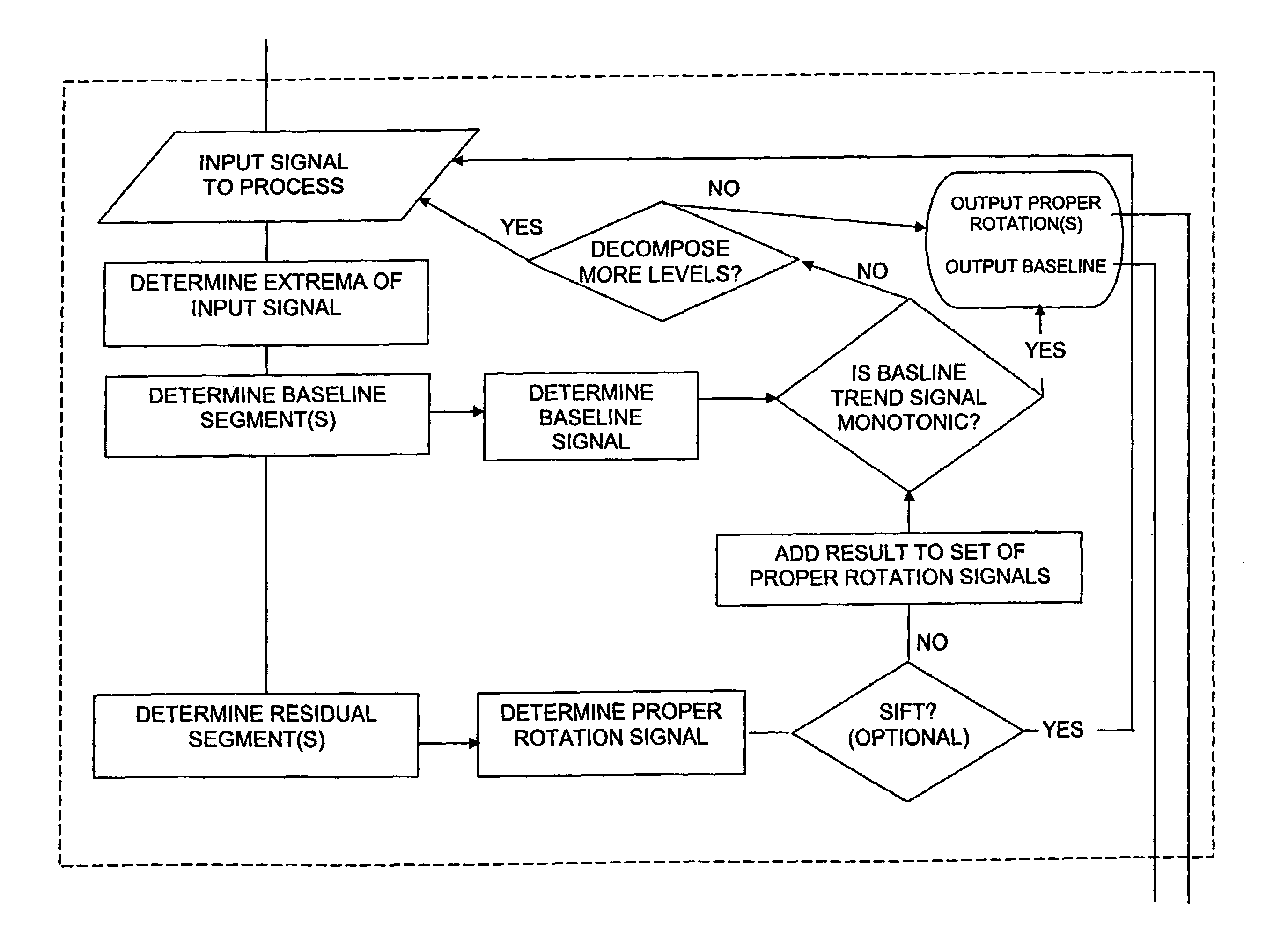
Method, computer program, and system for intrinsic timescale decomposition, filtering, and automated analysis of signals of arbitrary origin or timescale
ActiveUS7054792B2Easy to operateImprove performanceAmplifier modifications to reduce noise influenceTesting/monitoring control systemsTime markDecomposition
A method and system for intrinsic timescale decomposition, filtering, and automated analysis of signals of arbitrary origin or timescale including receiving an input signal, determining a baseline segment and a monotonic residual segment with strictly negative minimum and strictly positive maximum between two successive extrema of the input signal, and producing a baseline output signal and a residual output signal. The method and system also includes determining at least one instantaneous frequency estimate from a proper rotation signal, determining a zero-crossing and a local extremum of the proper rotation signal, and applying interpolation thereto to determine an instantaneous frequency estimate thereof. The method and system further includes determining at least one instantaneous frequency estimate from a proper rotation signal, extracting an amplitude-normalized half wave therefrom and applying an arc sine function to the amplitude-normalized half wave to determine an instantaneous frequency estimate of the proper rotation signal.
Owner:FLINT HILLS SCI L L C
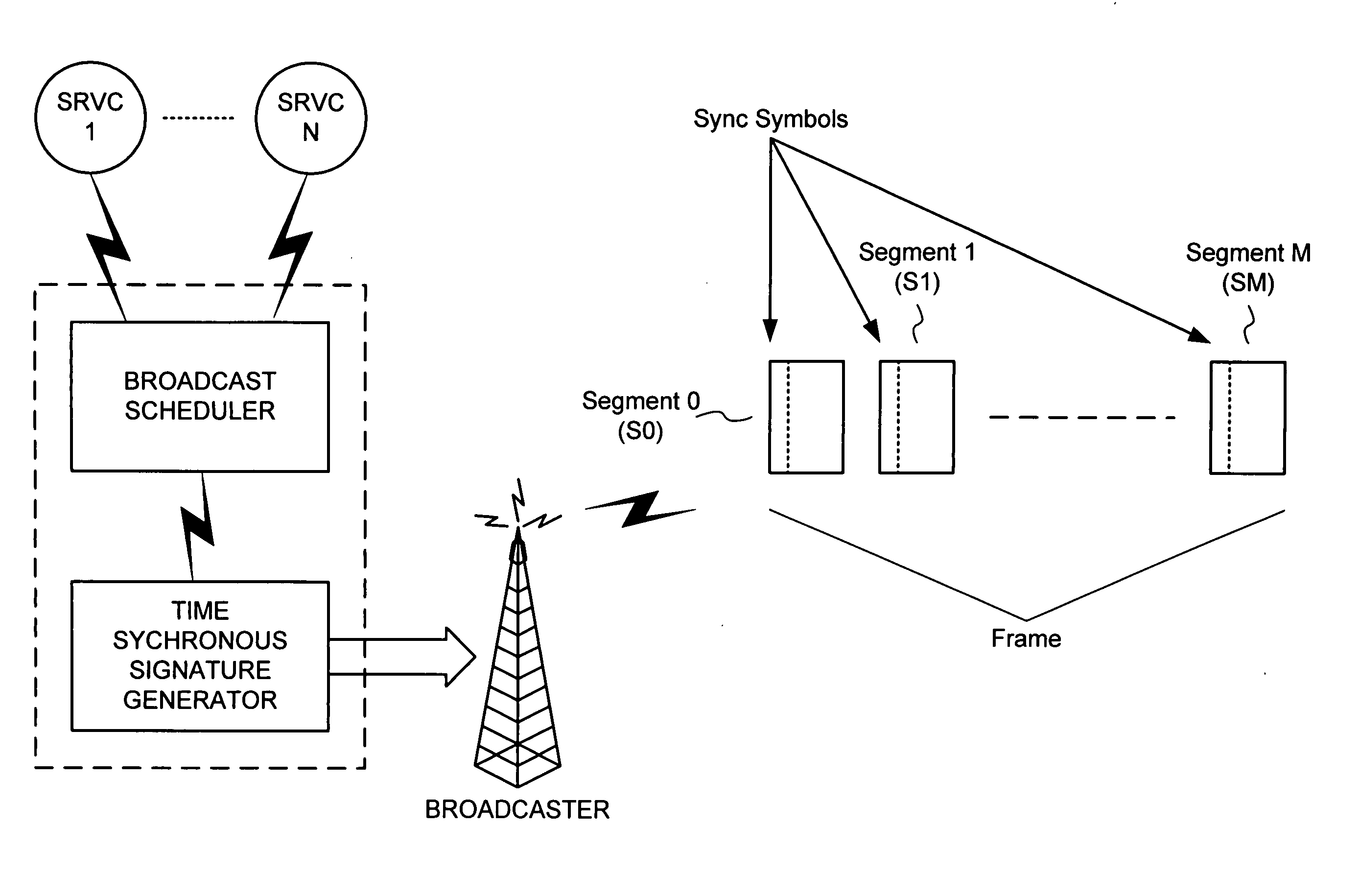
Cheap signatures for synchronous broadcast communication
InactiveUS20050182932A1Keep in syncSynchronising transmission/receiving encryption devicesUser identity/authority verificationHash functionClient-side
A method and system are configured for synchronous broadcast communications by applying signature keys using hashing functions. Each subsequent transmission in a sequence includes a signature key that can be verified by hashing to a preceding signature key from a previous portion of the sequence. The first transmission in the sequence is signed using a signature key that is known by the client device, typically verified using some other mechanism such as asymmetric key signatures. Each client device can utilize an internal counter for the current time or the block number in the transmission sequence to maintain synchronized transmissions in the even that a particular portion of the sequence is missed, and to validate signature keys. Since the signature keys can be validated when they are received but not predicted before they are received, the transmission is difficult to attack while synchronization is maintained.
Owner:MICROSOFT TECH LICENSING LLC
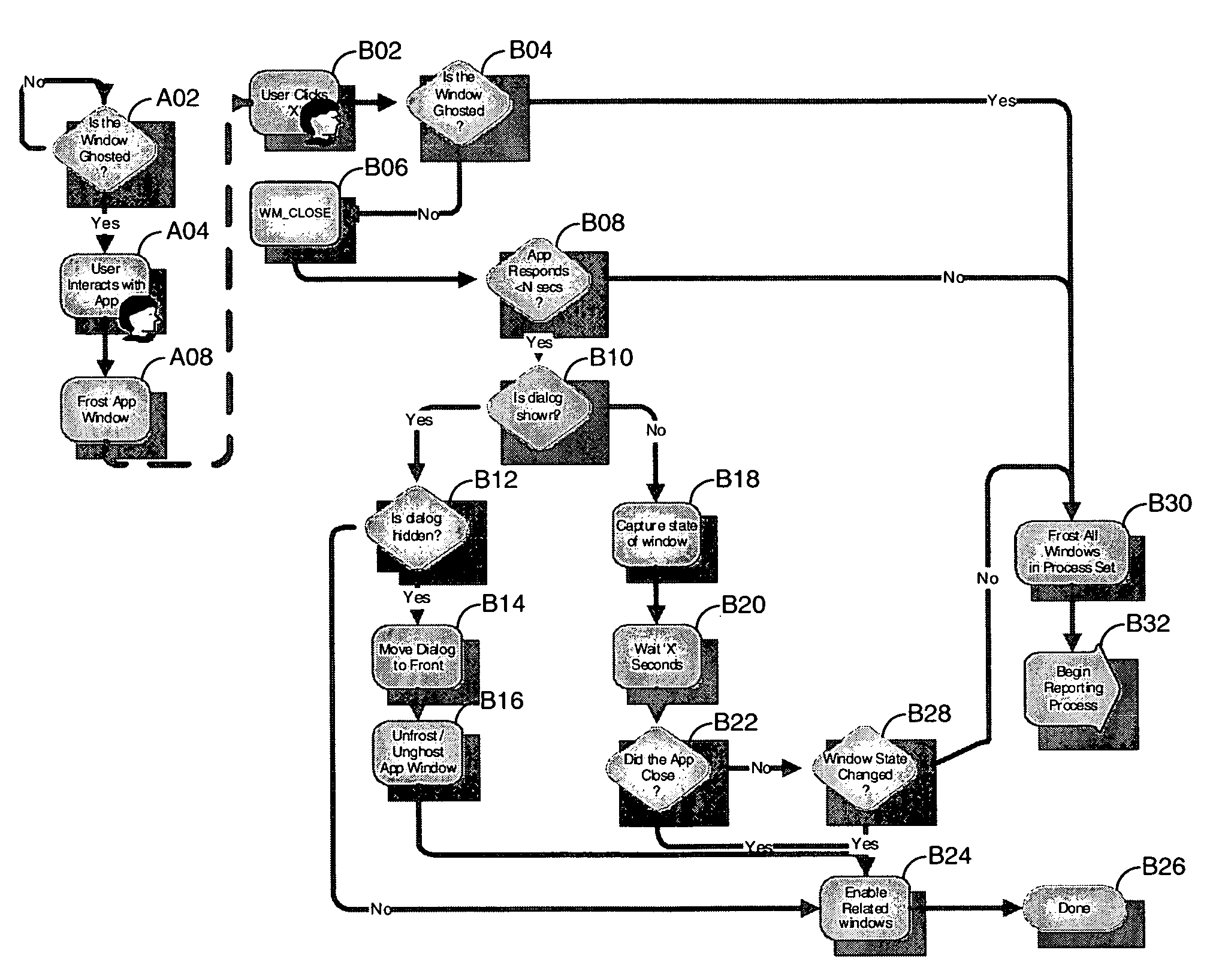
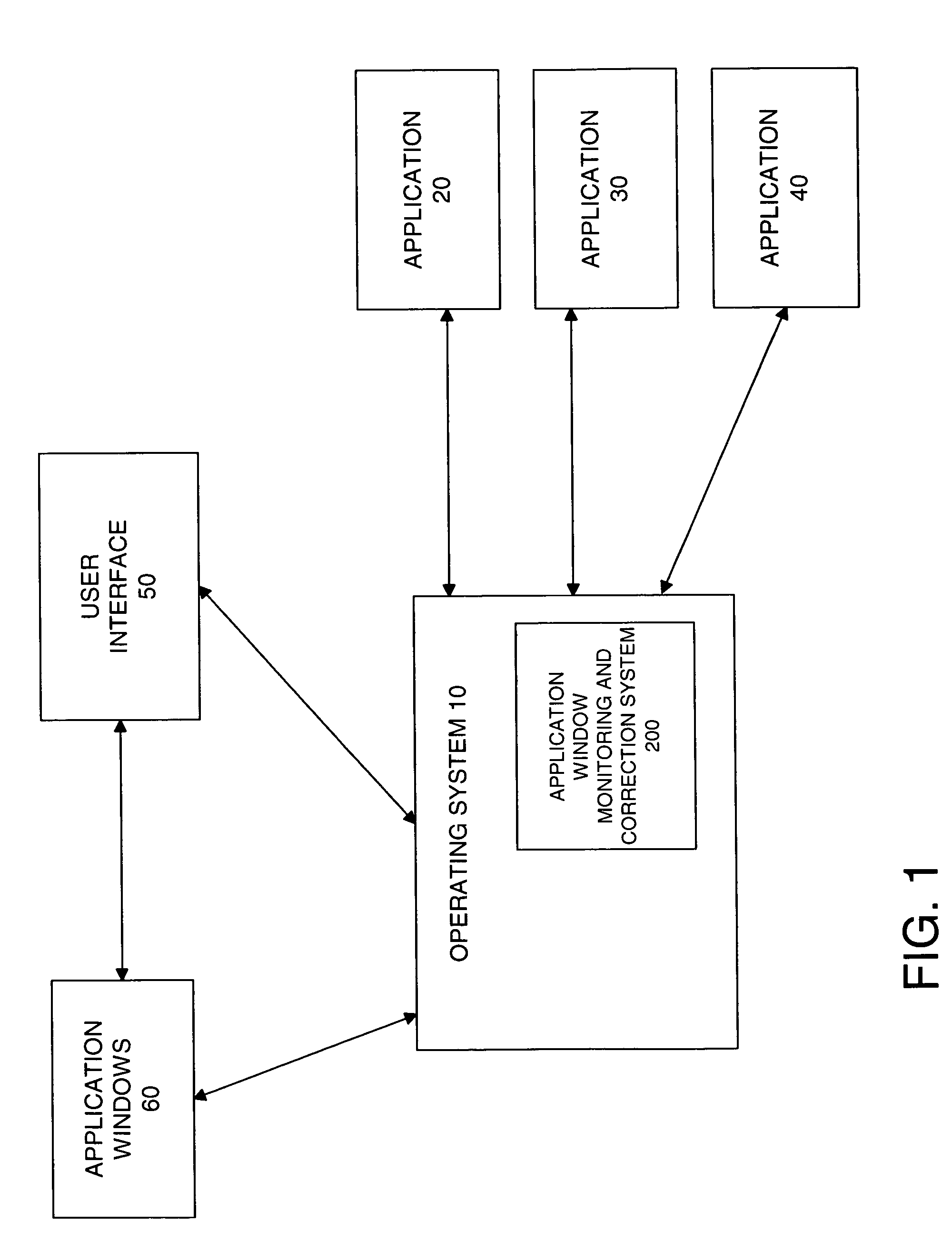
System and method for monitoring application response and providing visual treatment
InactiveUS7386807B2Input/output for user-computer interactionGraph readingVision processingApplication software
Owner:MICROSOFT TECH LICENSING LLC
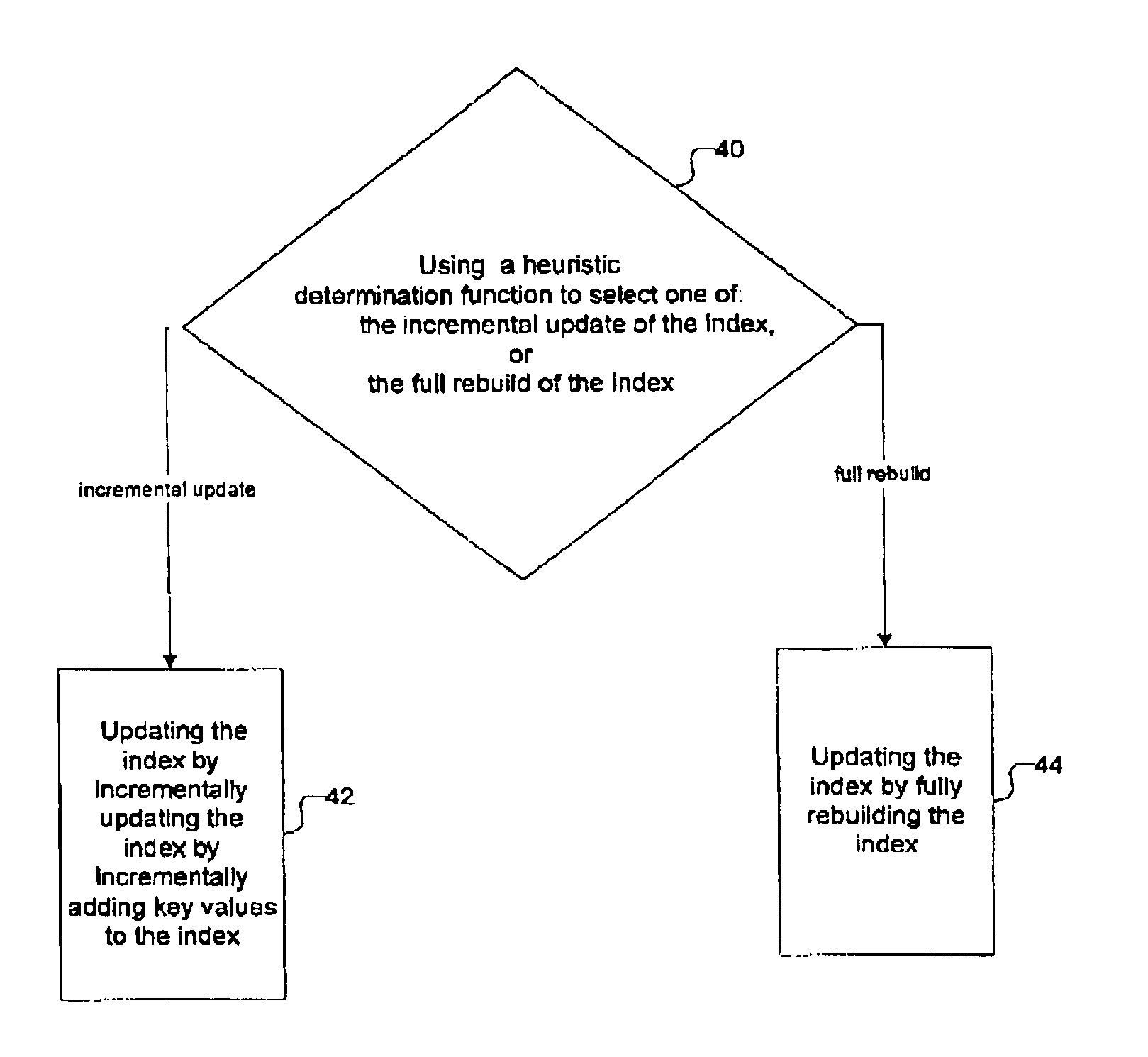
Heuristic-based conditional data indexing
InactiveUS7028022B1Simple systemImprove efficiencyData processing applicationsDigital data information retrievalData setHeuristic
A computer system for the indexing of data in which a heuristic determination function is applied to predict an efficient index updating approach. The system is able to update an index relating to a first data set by incrementally updating the index or by a rebuild of the index at the completion of the addition of a second set of data to the first set of data. The system applies a heuristic determination function to the characteristics of the first set of data, its index, and the second set of data, to predict whether an incremental update or a rebuild update of the index will result in a more efficient rebuild of the data. The system applies this approach to a restore and rollforward recovery or a data load operation to improve the efficiency of these operations.
Owner:TREND MICRO INC
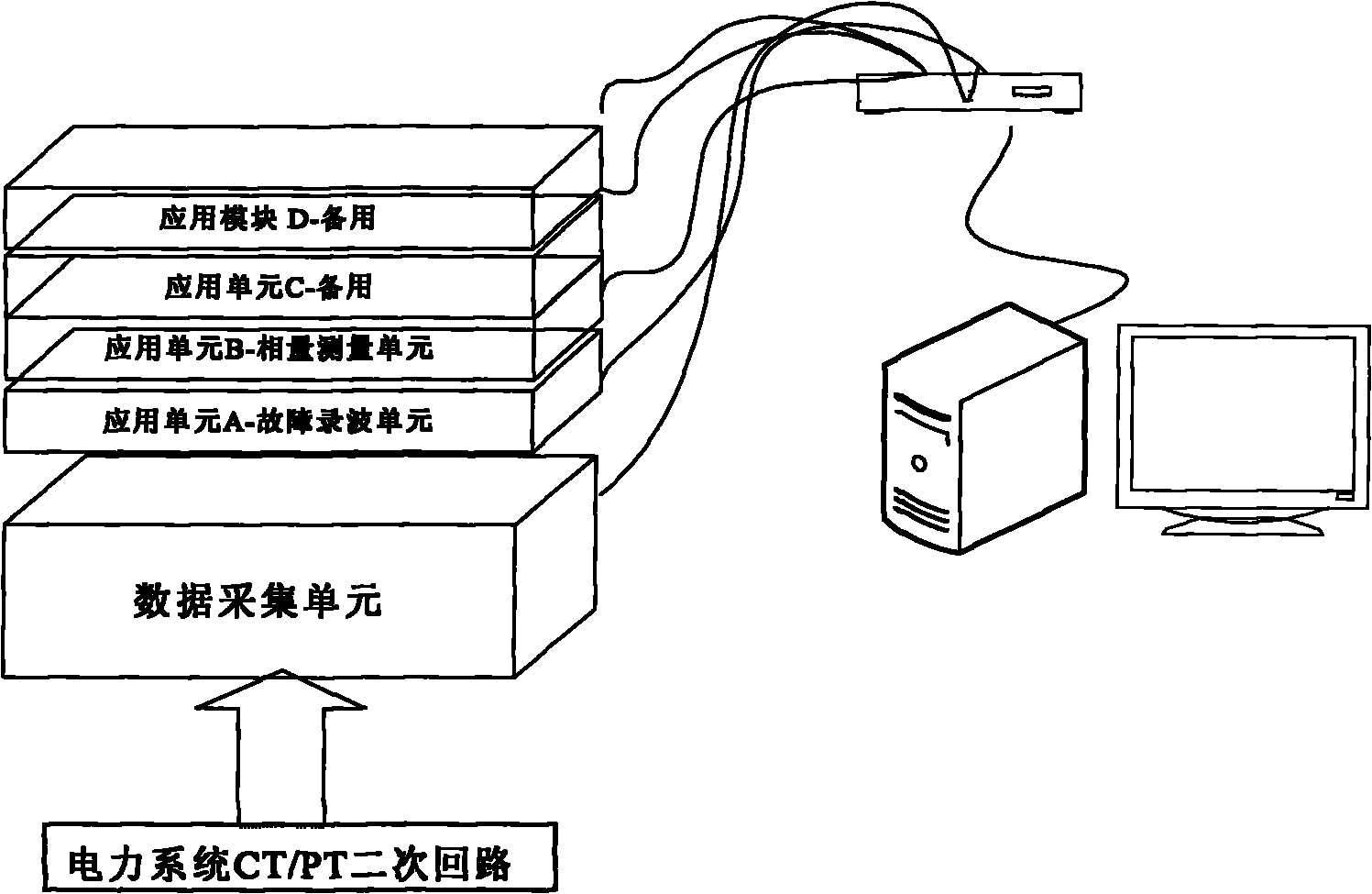
Monitoring method and device of power system
InactiveCN101900777ARealize the whole process monitoringReduce secondary wiringSynchronous motors for clocksFault locationCommunication interfacePrimary station
The invention discloses a monitoring method of a power system, comprising the following steps of: acquiring a running state signal of the power system in real time by a sensor positioned in a power grid; sampling the running state signal by taking a second pulse signal of a satellite synchronous clock as a sampling reference signal and outputting the acquired data to a function application unit of a data application layer through an optical fiber communication interface by a data acquisition unit; and analyzing and processing the acquired data and transmitting the processed result to a main monitoring station through the function application unit. The invention integrates functions of phasor quantity monitoring, fault recording, traveling wave fault location and the like into a monitoring device, considers the expanding demand of a hardware platform on realizing an IEC61850 communication protocol system in the selection of the hardware platform and realizes the monitoring in the whole process of the running state of the power system. The functions realized by the three sets of traditional equipment are realized by one set of equipment, and the secondary wiring is reduced, so that the maintenance cost and the asset investment can be greatly reduced.
Owner:HENNAN ELECTRIC POWER SURVEY & DESIGN INST
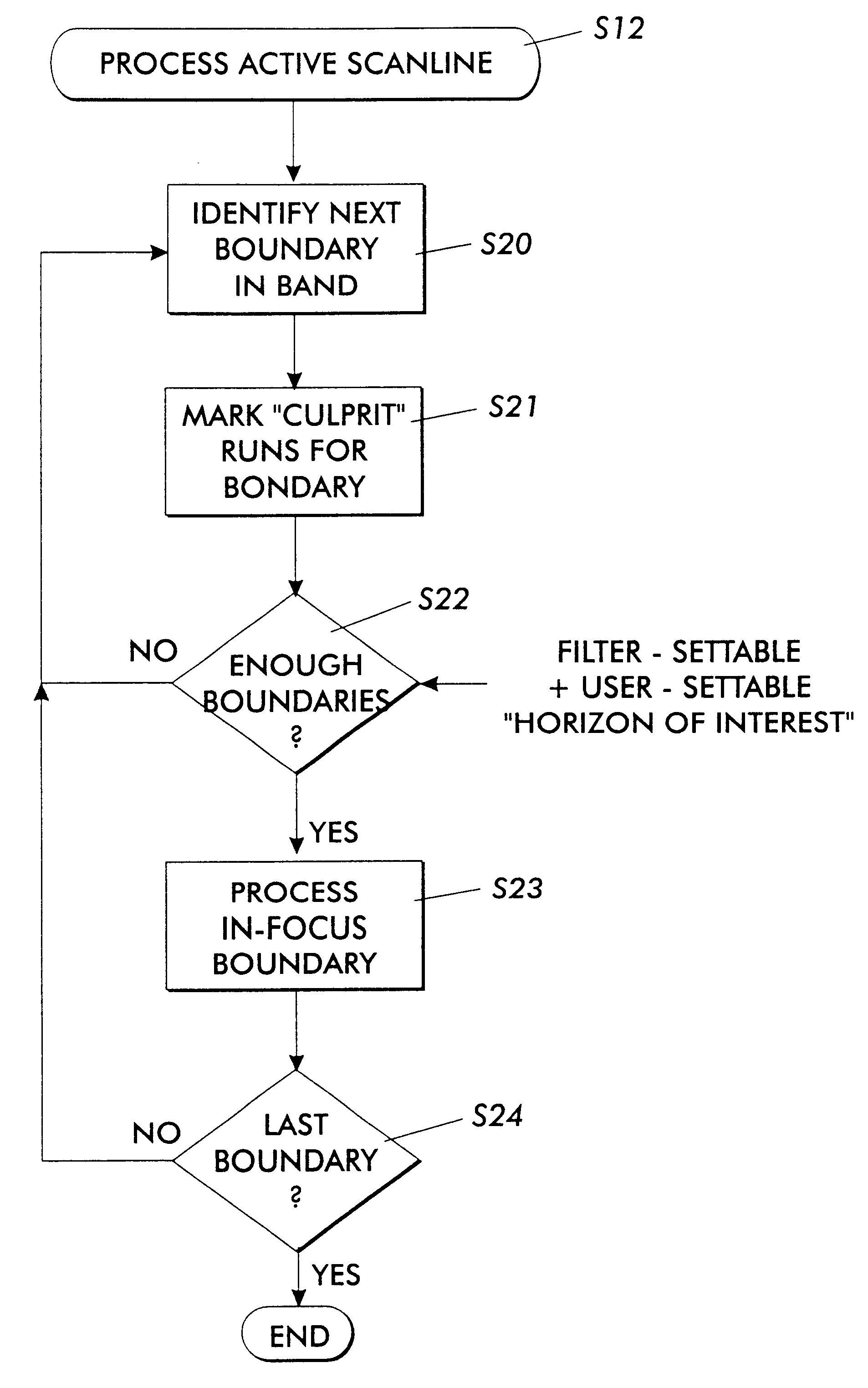
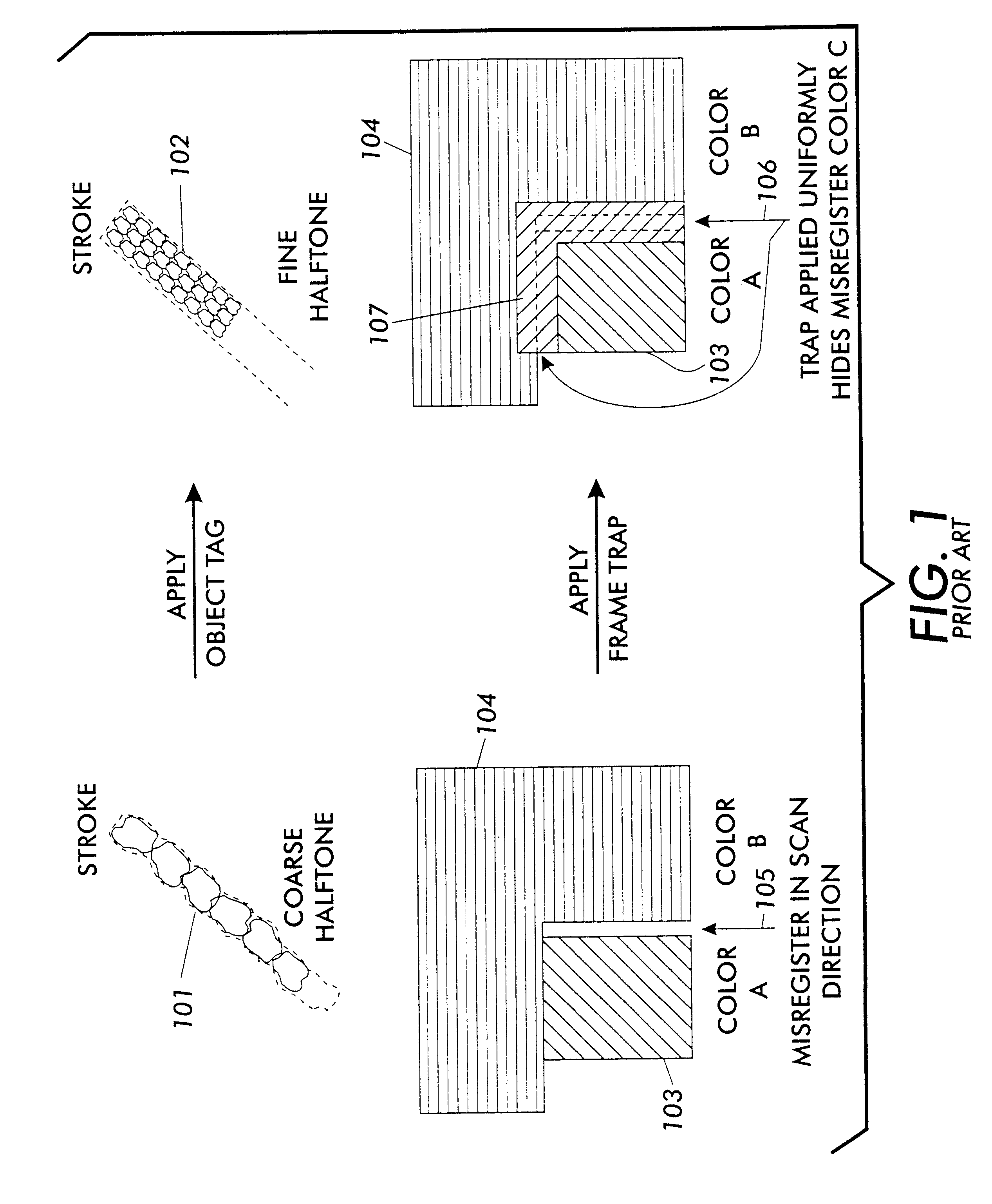
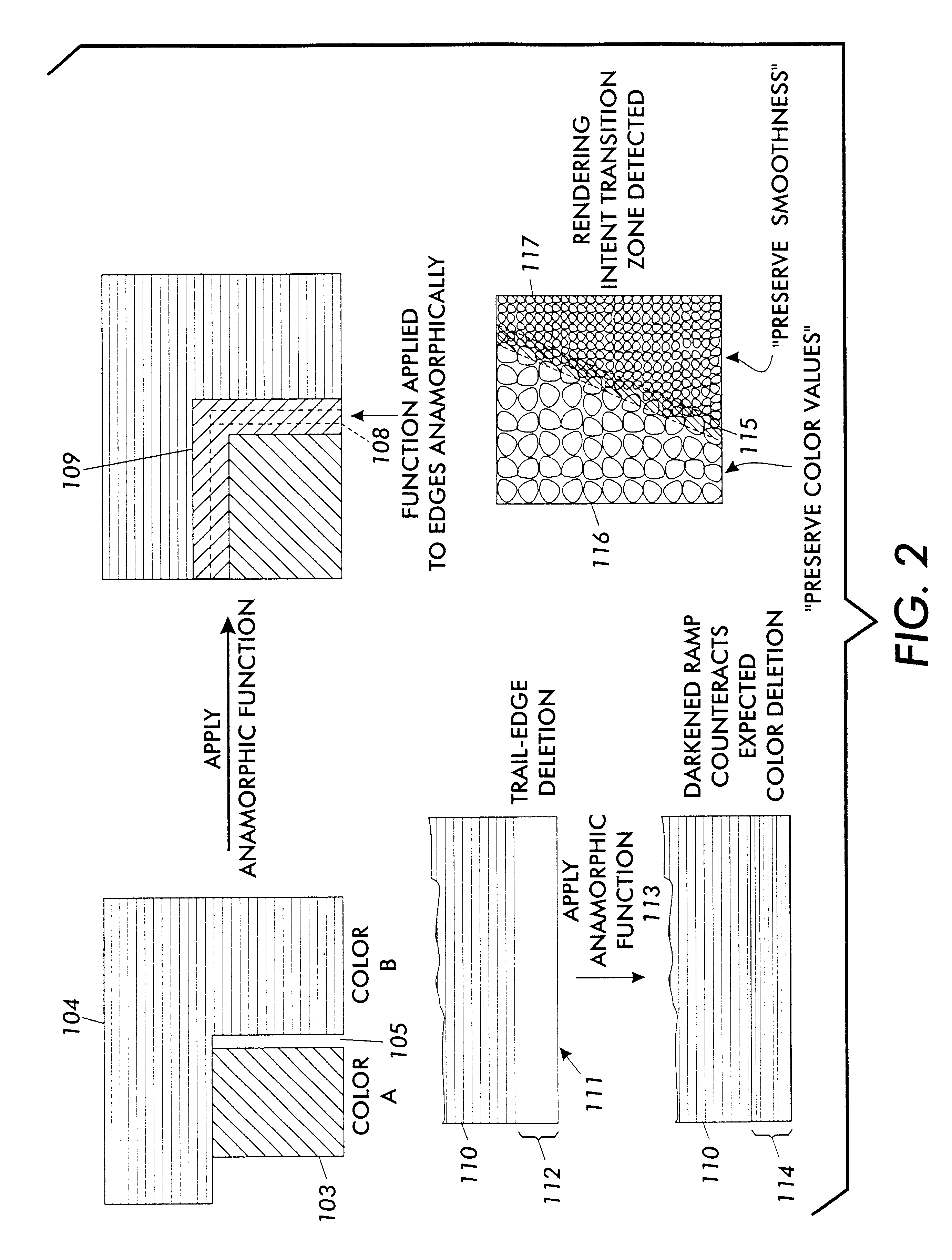
Anamorphic object optimized function application for printer defect pre-compensation
InactiveUS6341020B1Better addressImage enhancementDigitally marking record carriersDigital dataHead movements
Every printing system has characteristic defects which detract from high quality printing. Xerographic printing systems show defects such as banding, mottled colors in large fill areas, trail-edge deletion and starvation where toner concentrations drop at certain color edges, misregistration, and so on. Ink jet printing systems can show ink bleeding, streaking in the direction of head movement, and so on. One approach to reducing printer defects is to refine the electro-mechanics for more precise printing. Another approach which works for predictable defects is to modify the digital data being sent to the printer to pre-compensate for the defect. The prior art does this to a limited extent for individual object types (strokes, fills, images, text, etc.) and for misregistered color edges (trapping). This invention extends the range of edge-related defects that can be both predicted and pre-compensated for. An embodiment of the invention is described which pre-compensates for defects such as trail-edge deletion, starvation, misregistration, halo, etc. by identifying runs of color which meet the criteria likely to cause the effect and applying a function f(edge-distance, object-type) to such runs to modify them appropriately. Both the prediction criteria and the functions applied are anamorphic (the scan direction and process direction are treated differently) and object-optimized (object attributes are taken into account). Further, both prediction criteria and applied correction functions allow user-settable input.
Owner:XEROX CORP
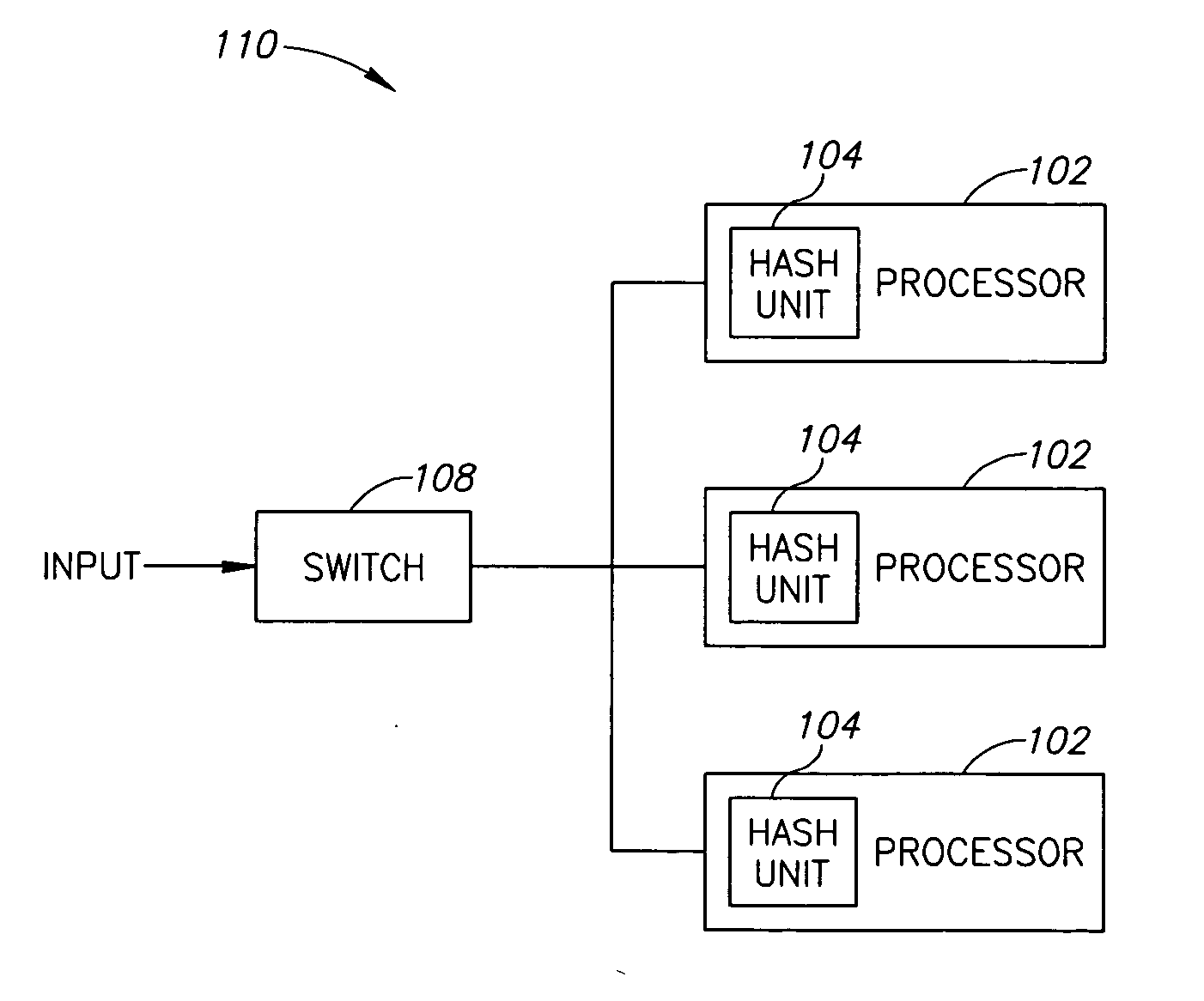
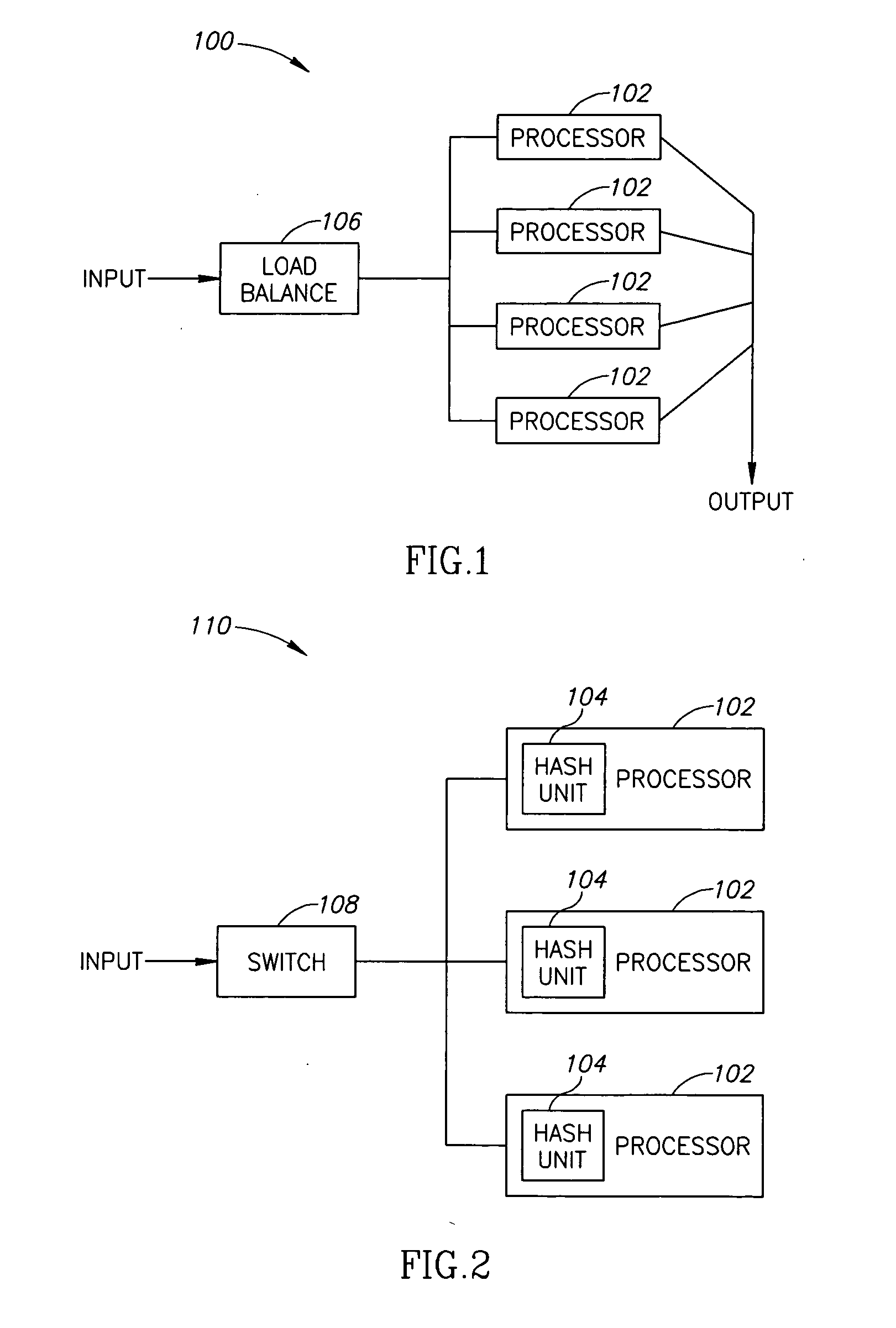
Hash function using arbitrary numbers
InactiveUS20070071233A1User identity/authority verificationSecret communicationHash functionTheoretical computer science
A hash unit, including an input interface adapted to receive an input key, an arbitrary number generator adapted to generate one or more arbitrary numbers, a processor adapted to apply a multi-operand function to an input key received by the input interface together with each of one or more arbitrary numbers generated by the generator so as to generate intermediate results, to mathematically combine the digits of the intermediate results to generate respective short bit results having less than half the bits of the intermediate results and to concatenate the short bit results and an output unit adapted to provide the concatenated short bit results for use as an output hash key.
Owner:ALLOT COMM LTD
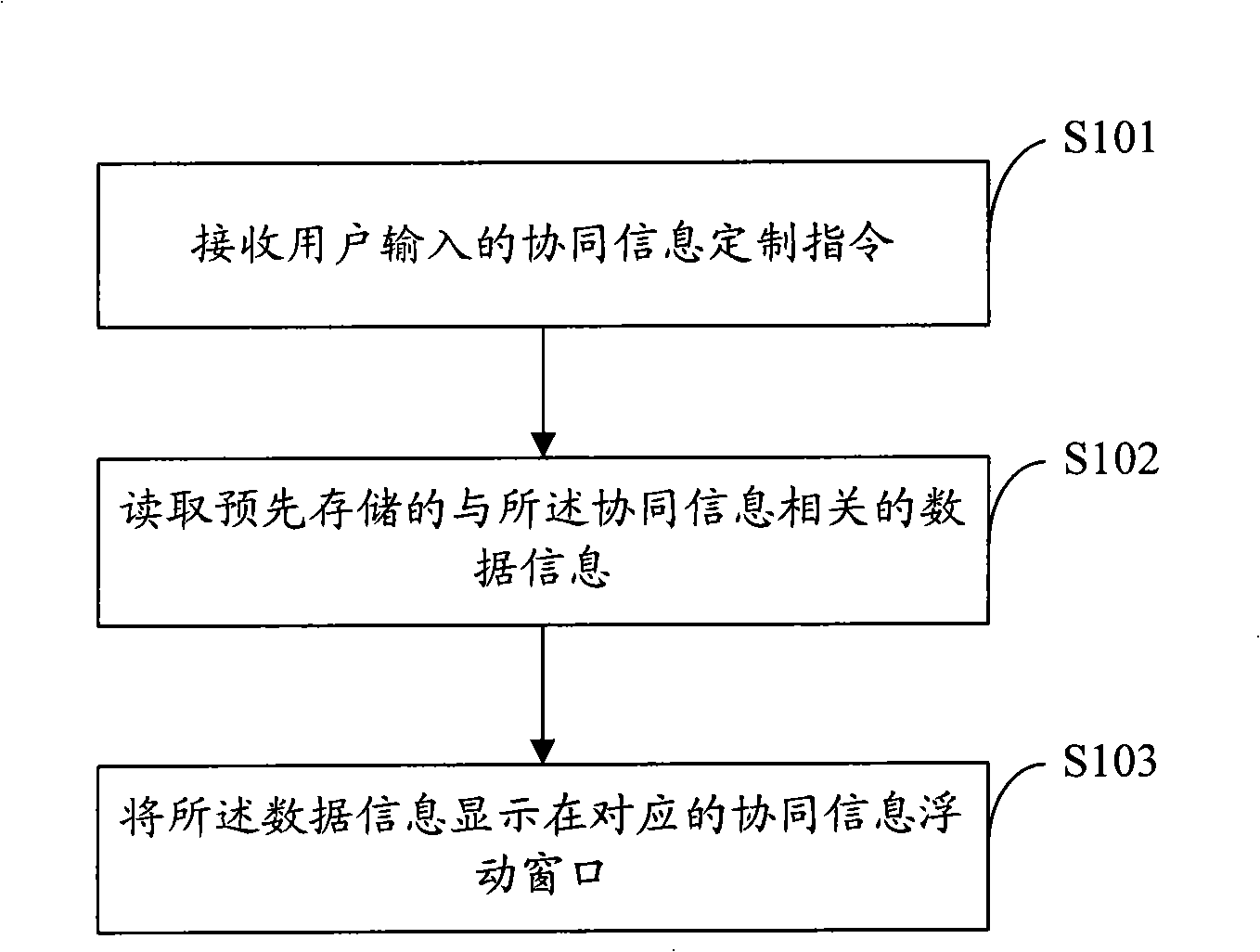
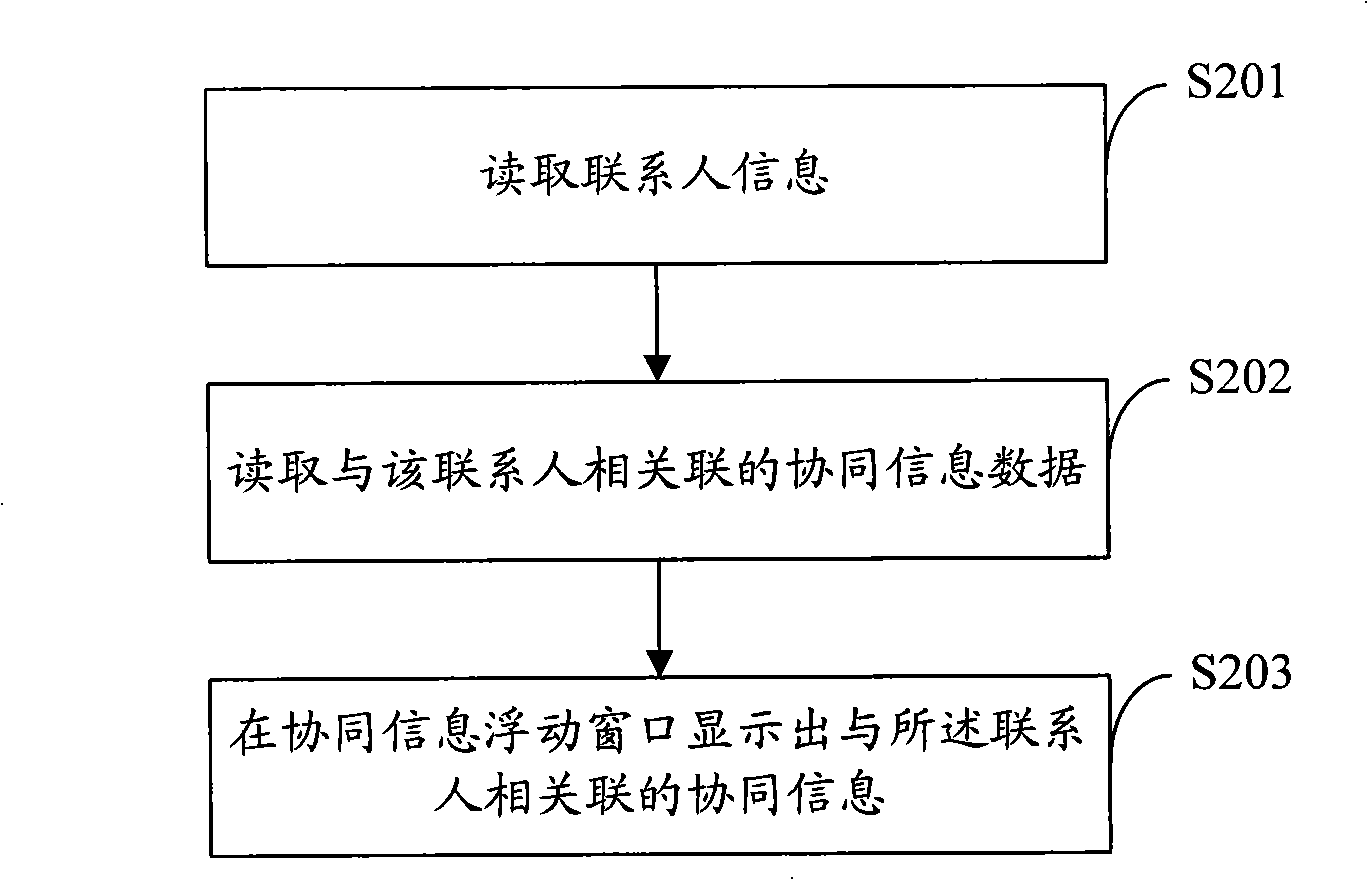
Mobile terminal, its information presentation method and system
InactiveCN101345941AEasy to viewRadio/inductive link selection arrangementsTelephone sets with user guidance/featuresData informationUser input
The invention provides a mobile terminal and information presentation method and system, suitable for a mobile communication domain. The said method comprises: receiving cooperation information customization command input by the customer; reading the prestored data information associated with the cooperation information; displaying the data information on the corresponding cooperation information floating window. In the embodiment of the invention, the cooperation information of self-defining function application is displayed on the interface of the mobile terminal in the way of floating window, and the cooperation information can display the summary information corresponding with the function, therefore the customer can conveniently view information of a plurality of function applications.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
Screenshot processing device and method
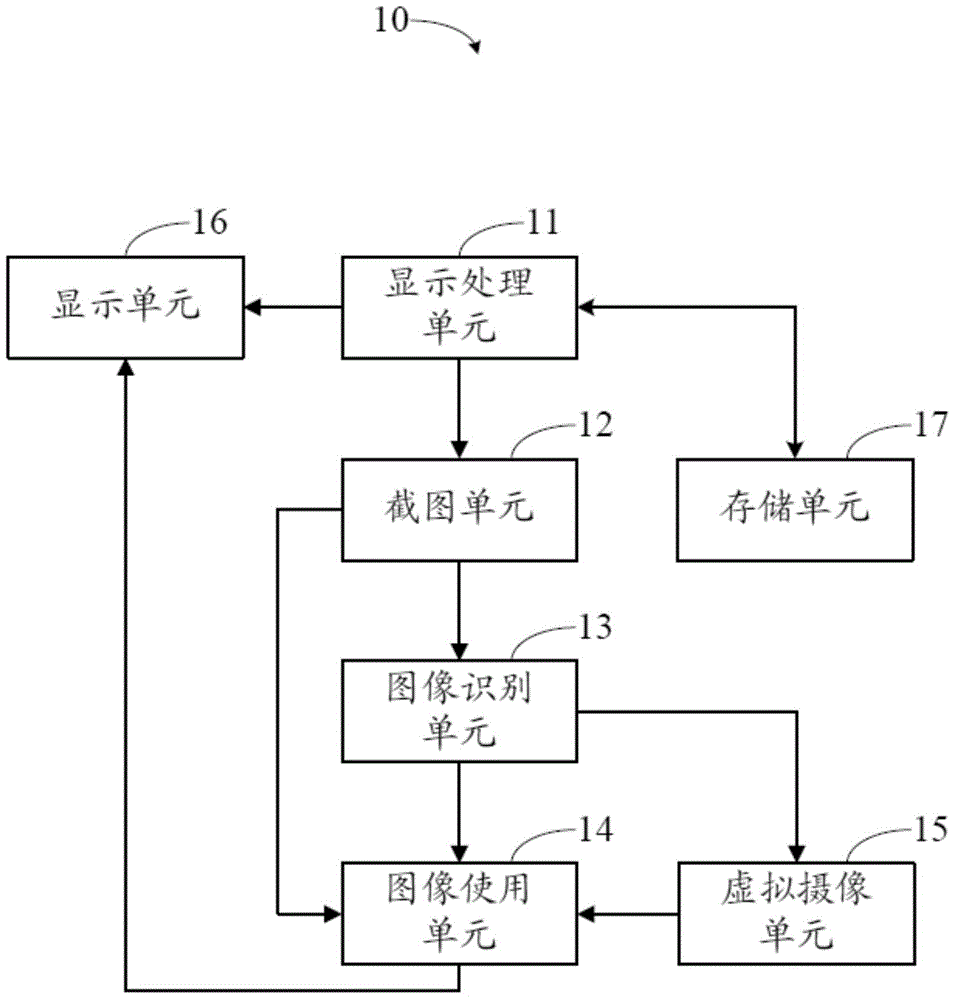
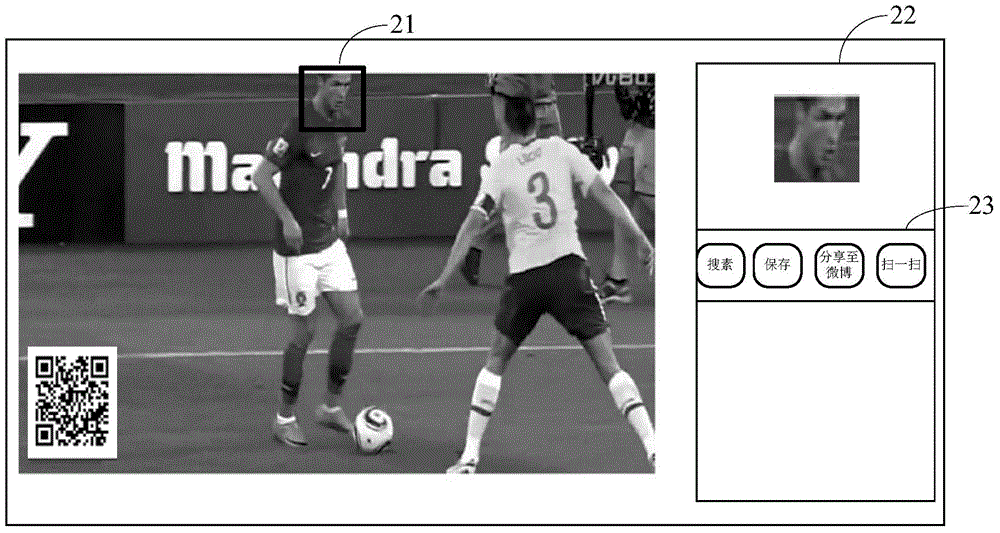
ActiveCN104090762AImprove experienceSpecial data processing applicationsSpecific program execution arrangementsHuman–computer interactionFunction application
The invention provides a screenshot processing device. The screenshot processing device comprises a display processing unit, a display unit, a screenshot unit, an image recognition unit and an image using unit. The display processing unit displays obtained multimedia data through the display unit, receives a screenshot instruction, captures screen data and determines a screenshot area according to operation of a user. The screenshot unit obtains an image in the screenshot area and generates a screenshot completing signal according to the operation of the user. The image recognition unit responds to the screenshot completing signal, recognizes screenshot content and judges the corresponding type. The image using unit responds to the screenshot completing signal, provides a shortcut use menu comprising a plurality of use functions and recognizes the selection of the functions by the user to call a corresponding program to execute the corresponding function. The invention further provides a screenshot processing method. Through the screenshot processing device and method, related function applications are provided according to the screenshot of the user, and the technical effect of foreknowing the intention of the user is achieved.
Owner:FUZHOU ROCKCHIP SEMICON
Server design and method
ActiveUS20080312778A1Low costImprove performanceDigital data processing detailsBroadcast specific applicationsCommunications systemOperational system
A communication system for a vehicle includes a server that includes a real time operating system, at least one cabin function application that runs on the real time operating system, and at least one in-flight entertainment application that runs on another operating system on top of the real time operating system. Thus, an in-operation entertainment system is capable of providing audio and / or visual content to a large number of locations in a cabin of the vehicle, and a cabin function system is capable of providing various cabin applications, e.g., lighting level control, attendant calling, air conditioning control, etc. at different locations in the vehicle cabin in a manner that is isolated and prioritized over the entertainment system.
Owner:THALES AVIONICS INC
System and method for cross domain learning for data augmentation
InactiveUS20110071965A1Digital computer detailsFuzzy logic based systemsMachine learningFunction application
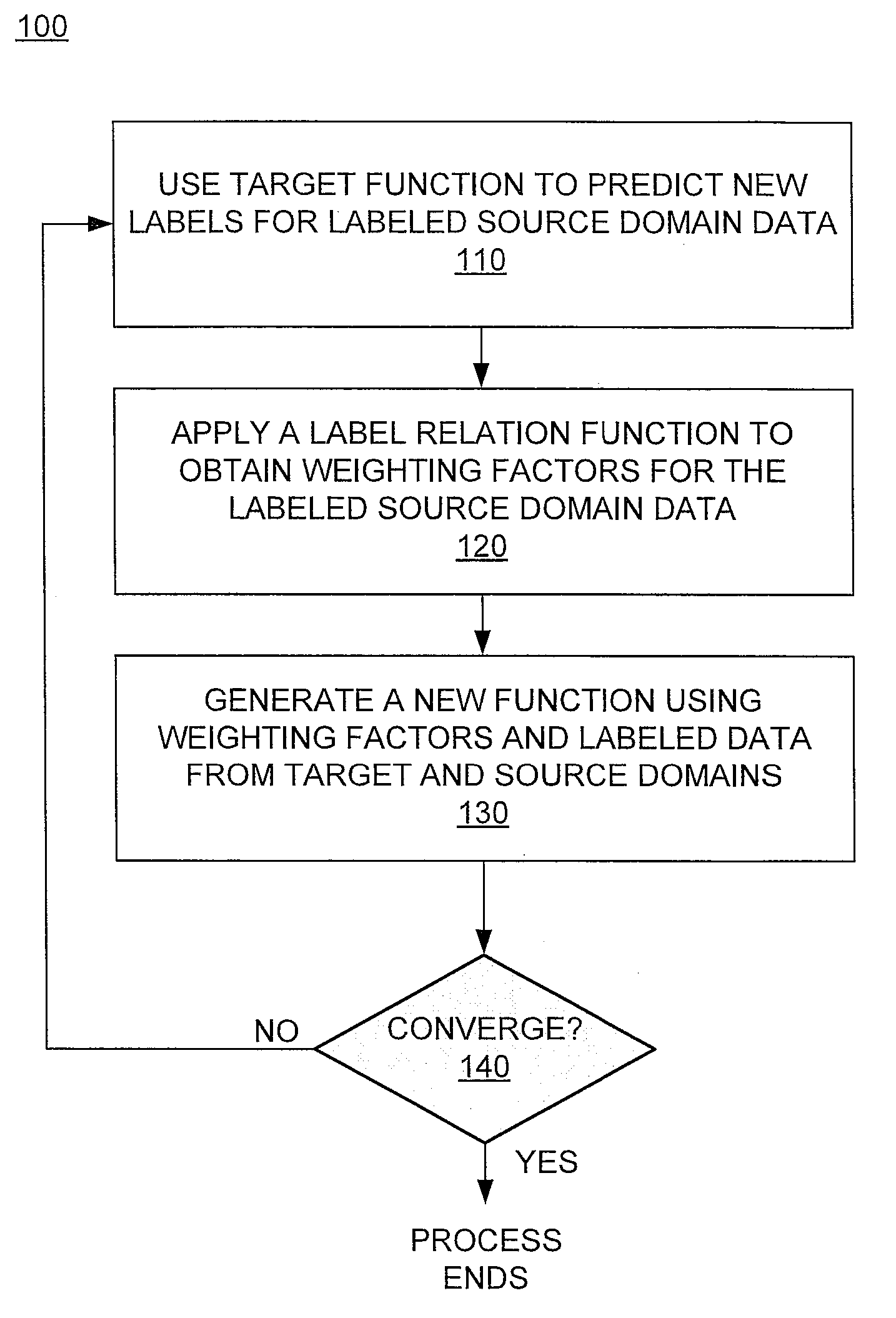
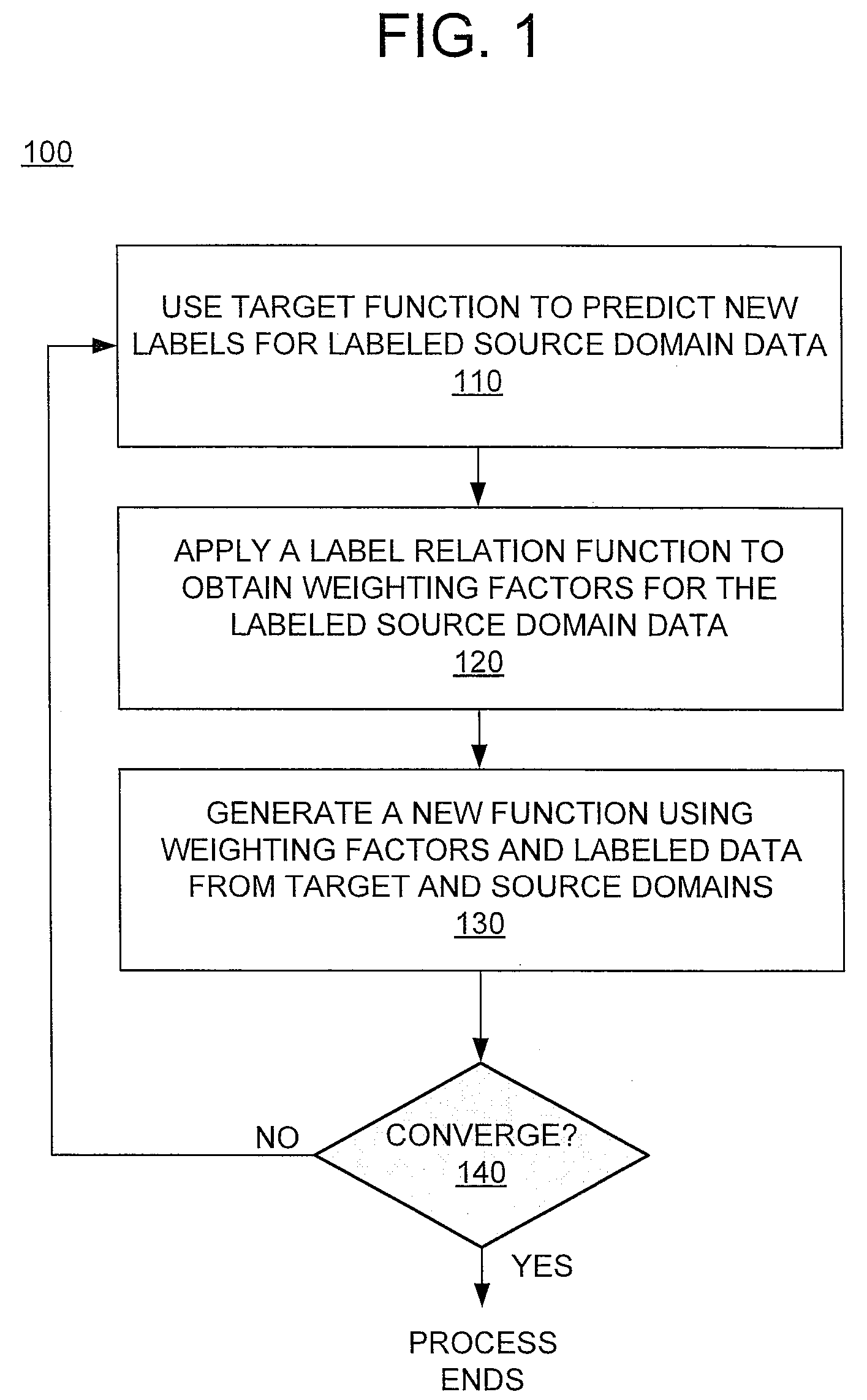
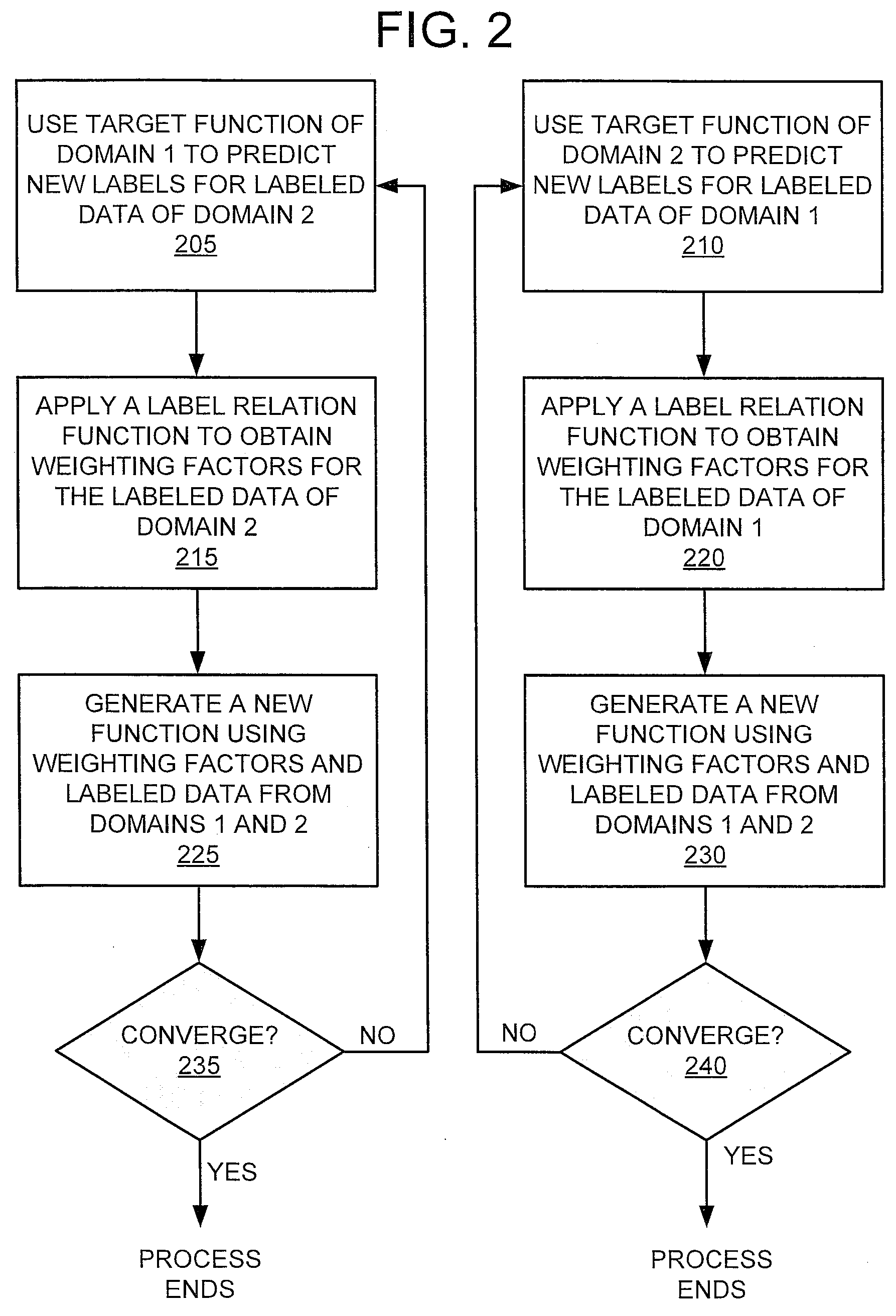
According to an example embodiment, a method comprises executing instructions by a special purpose computing apparatus to, for labeled source domain data having a plurality of original labels, generate a plurality of first predicted labels for the labeled source domain data using a target function, the target function determined by using a plurality of labels from labeled target domain data. The method further comprises executing instructions by the special purpose computing apparatus to apply a label relation function to the first predicted labels for the source domain data and the original labels for the source domain data to determine a plurality of weighting factors for the labeled source domain data. The method further comprises executing instructions by the special purpose computing apparatus to generate a new target function using the labeled target domain data, the labeled source domain data, and the weighting factors for the labeled source domain data, and evaluate a performance of the new target function to determine if there is a convergence.
Owner:STARBOARD VALUE INTERMEDIATE FUND LP AS COLLATERAL AGENT
HDMI multiplexing method, HDMI, and equipped provided with HDMI
ActiveCN102572352ASolve the problem that the function cannot be extended to cause a single functionTelevision system detailsCathode-ray tube indicatorsHigh-definition televisionMultiplexing
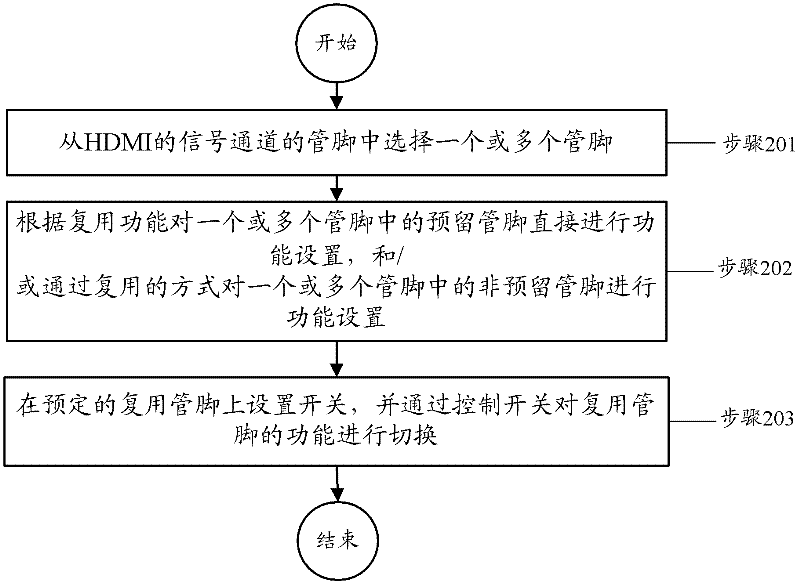
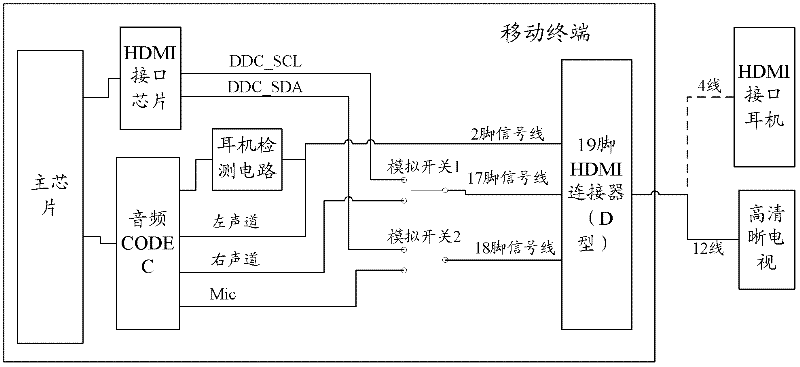
The invention discloses an HDMI (high-definition multimedia interface) multiplexing method, an HDMI, and equipment provided with the HDMI, wherein the method comprises the following steps: one or more pins is (are) selected from pins for signal channel of the HDMI; function setting is directly performed to a reserved pin in the one or more pins according to the multiplexing function, and / or functional setting is performed on a non-reserved pin in the one or more pins in a multiplexing way; and a switch is arranged on a preset multiplexing pin, and then the functions of the multiplexing pin are switched through a control switch. By virtue of the technical scheme provided by the invention, that a terminal HDMI can carry out relevant function application on non-high-definition television when relevant external accessories are connected can be achieved.
Owner:ZTE CORP
Constructions of variable input length cryptographic primitives for high efficiency and high security
ActiveUS7221756B2Improve securityEfficient constructionEncryption apparatus with shift registers/memoriesUser identity/authority verificationComputer hardwareHash function
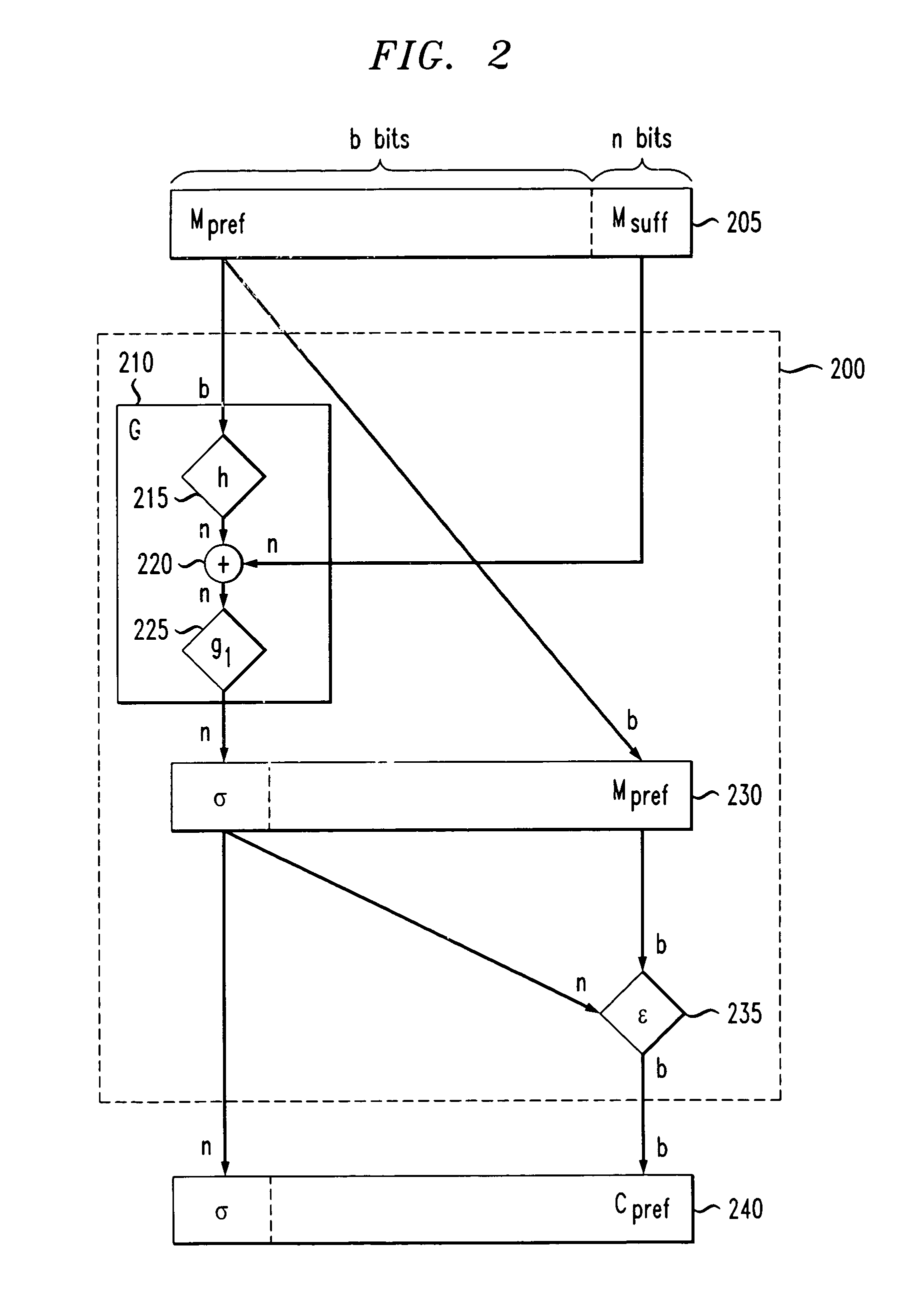
A hash function is applied to a prefix of a VIL input. The output is added to a suffix of the input. A block cipher is applied to results of the addition. An encryption function is performed on the prefix. The final output is the output of the block cipher and the encryption function. In a second encryption technique, a hash function is applied to an input, and the output of the hash function has first and second portions. A block cipher is applied to the second portion. The output of the block cipher is added to the first portion, and a second function is applied to the result of this first addition. The output of the second function is added to the second portion. An inverse hash function is then applied to the output of the first and second additions, creating an encrypted output.
Owner:ALCATEL-LUCENT USA INC
System and method for generating pseudo-random numbers
ActiveUS20070230693A1Random number generatorsSecuring communicationCryptographic hash functionNumber generator
A process and system for generating a pseudo-random number is presented. Input data having entropy is gathered in an Entropy Pool and transformed once by a cryptographic hash function. The transformed data forms the internal state of the pseudo-random number generator. The generator forms the output by applying a second cryptographic hash function to this internal state. Finally, the generator updates the internal state by inputting the current internal state and data from the Entropy Pool into a third cryptographic hash function. The output of the third hash function forms the new internal state of the pseudo-random number generator.
Owner:SAP AG
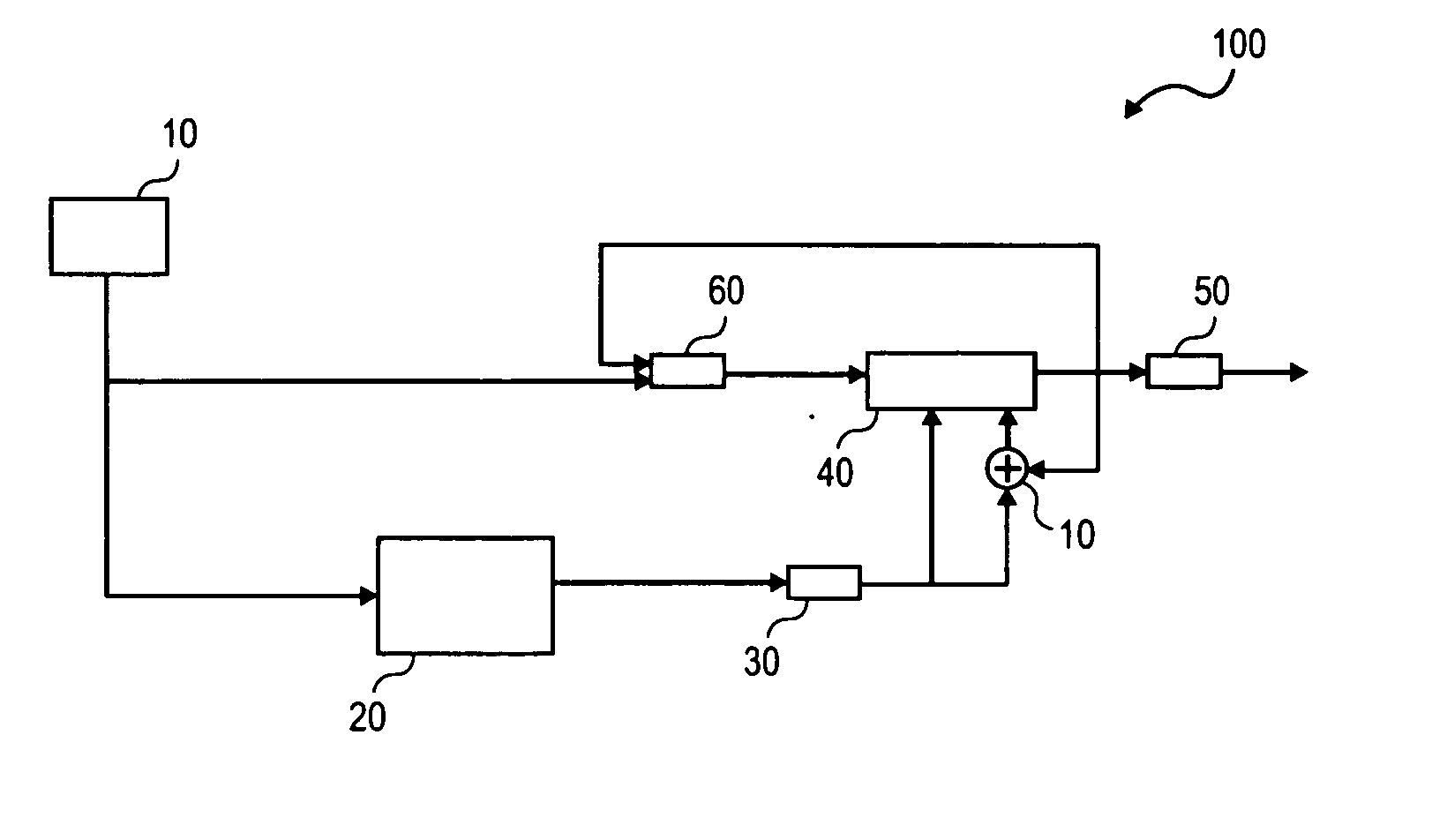
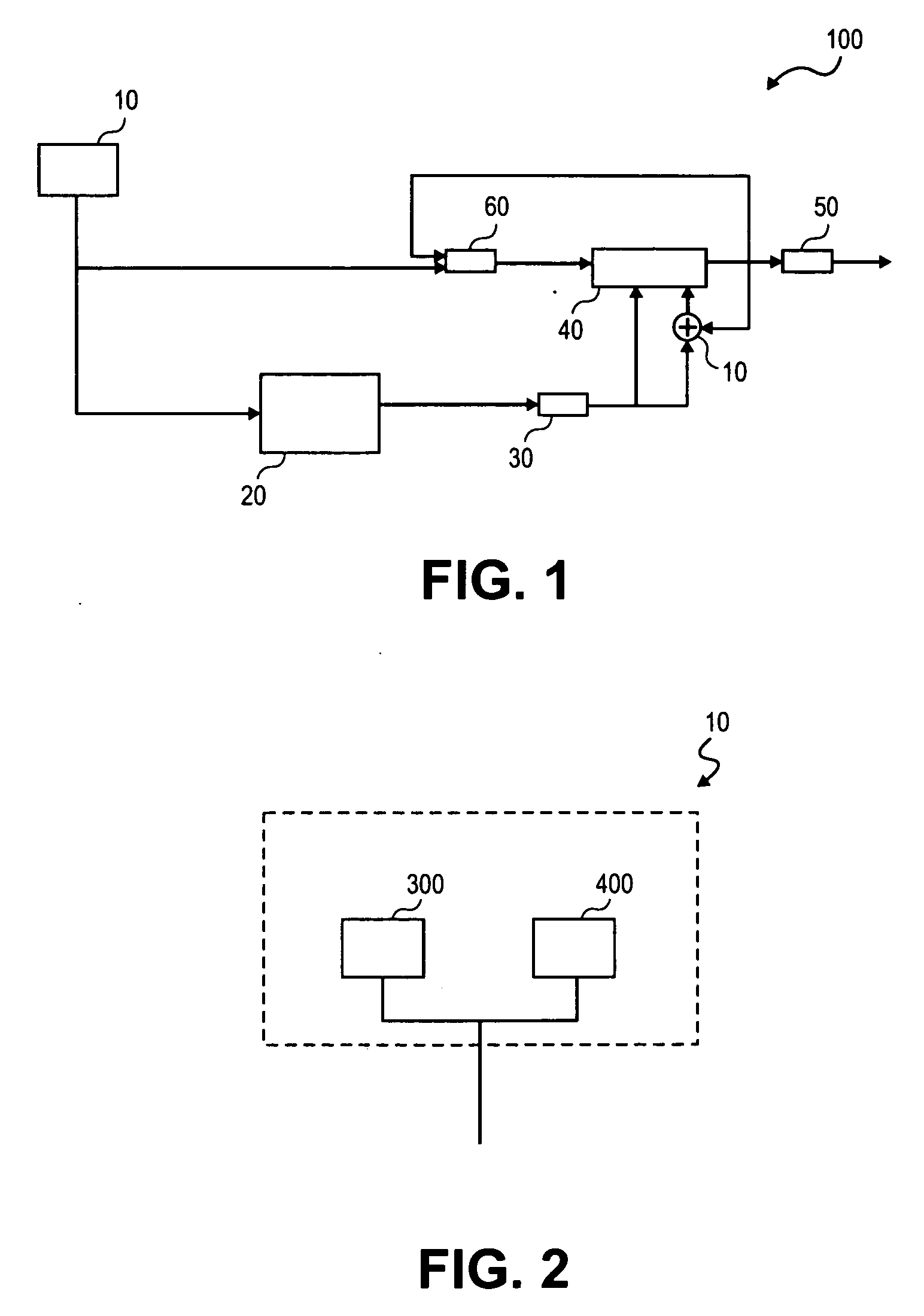
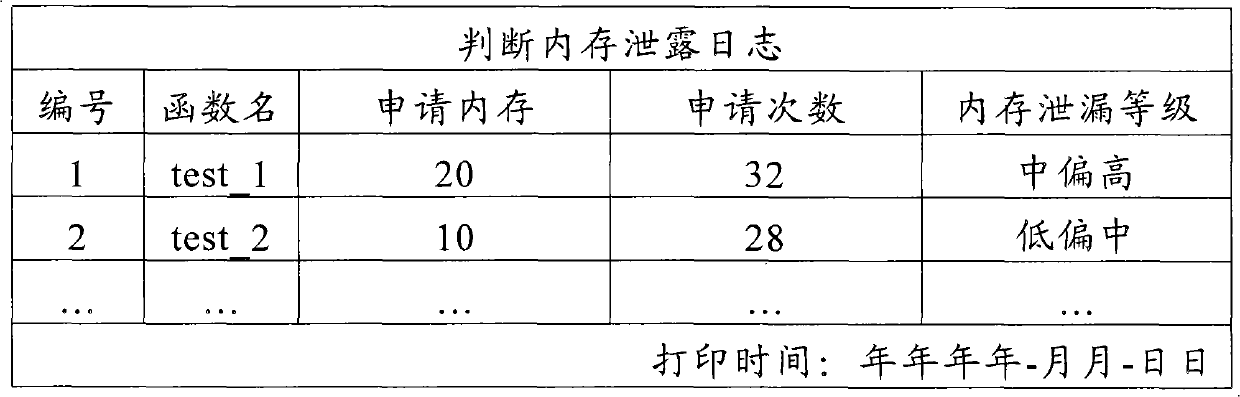
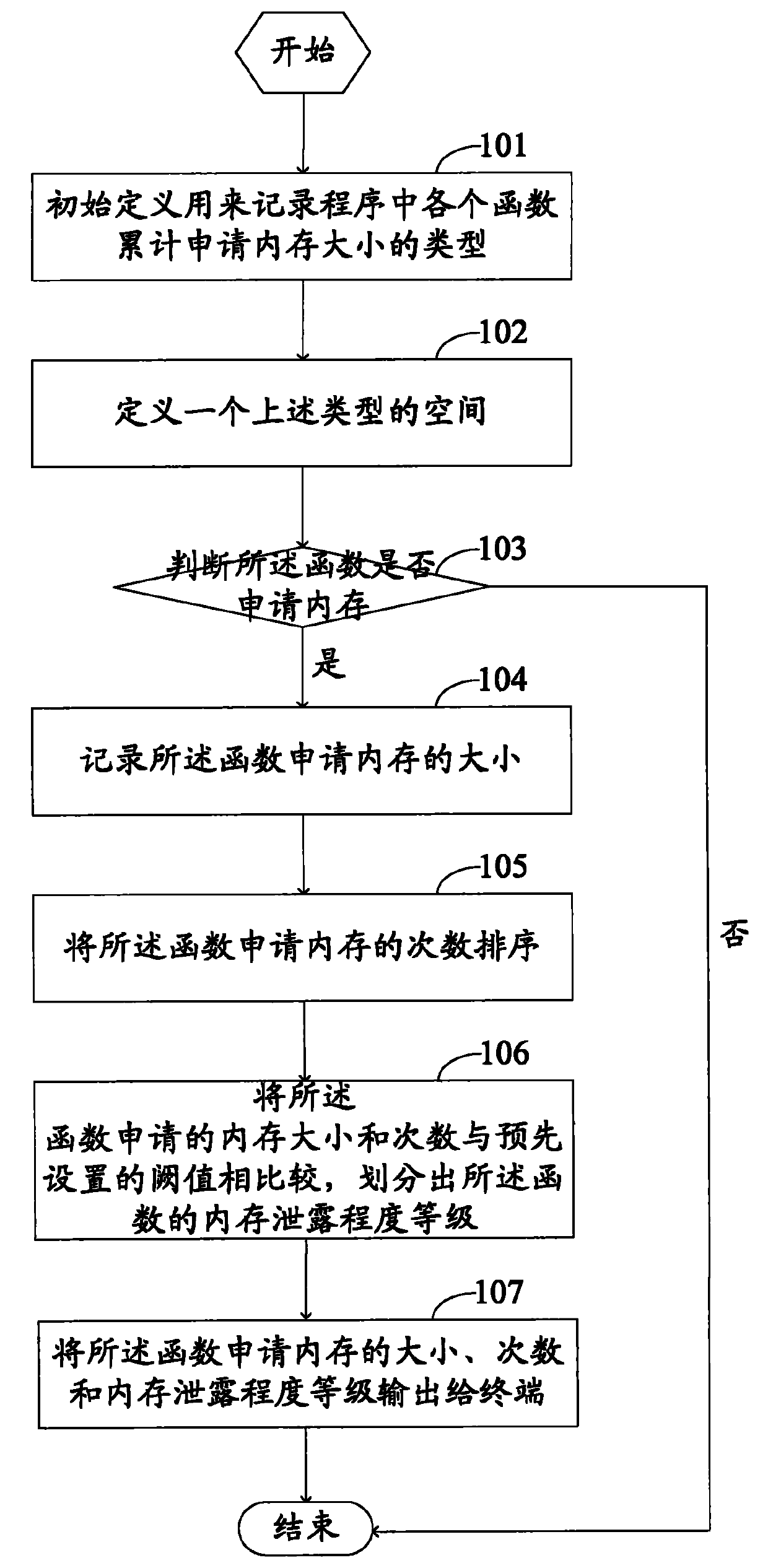
System and method for judging memory leak
The invention provides a method for judging memory leak, comprising the following steps of: when a function application memory is judged aiming at each function in a program, accumulating the memory capacity and the application times of the named function application; when a function release memory is judged, reducing the released memory capacity from the memory capacity of the named function accumulated application and reducing release memory times from accumulated application times; sequencing the memory capacity and the times of the function application in different names in a descending mode by using the memory capacity as priority; ensuring and outputting a level of a memory leak degree according to the memory capacity and the times of the function accumulated application in different names; in addition, the invention provides a system for realizing the method in order to sequence memory distribution and information release according to the memory application times and liberate a programmer from large fussy analytical work.
Owner:BEIJING HAITAI FANGYUAN HIGH TECH
Human face mapping method and device
ActiveCN106570822AAdd application functionsFor maximum editing effectGeometric image transformationComputer visionFunction application
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
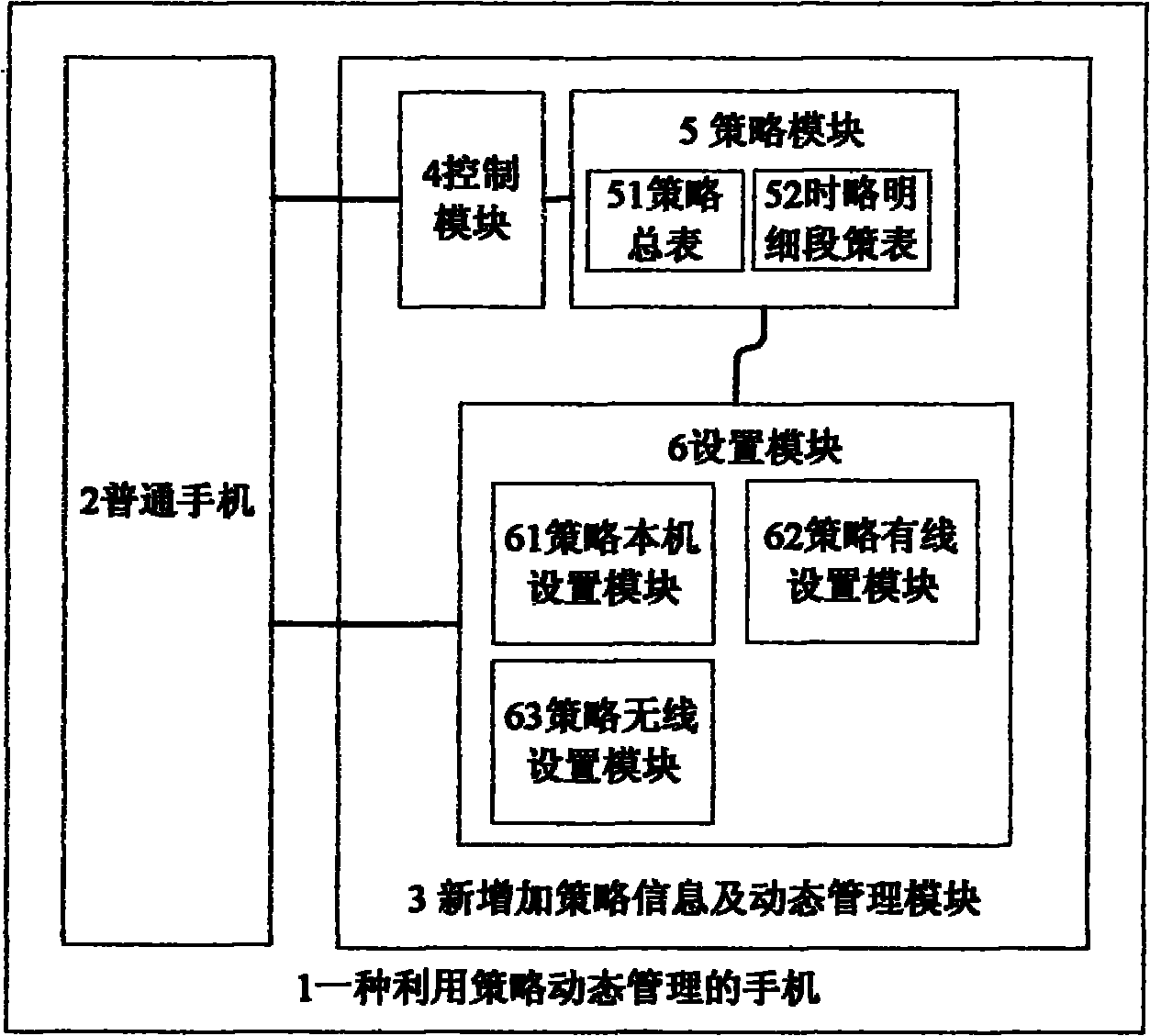
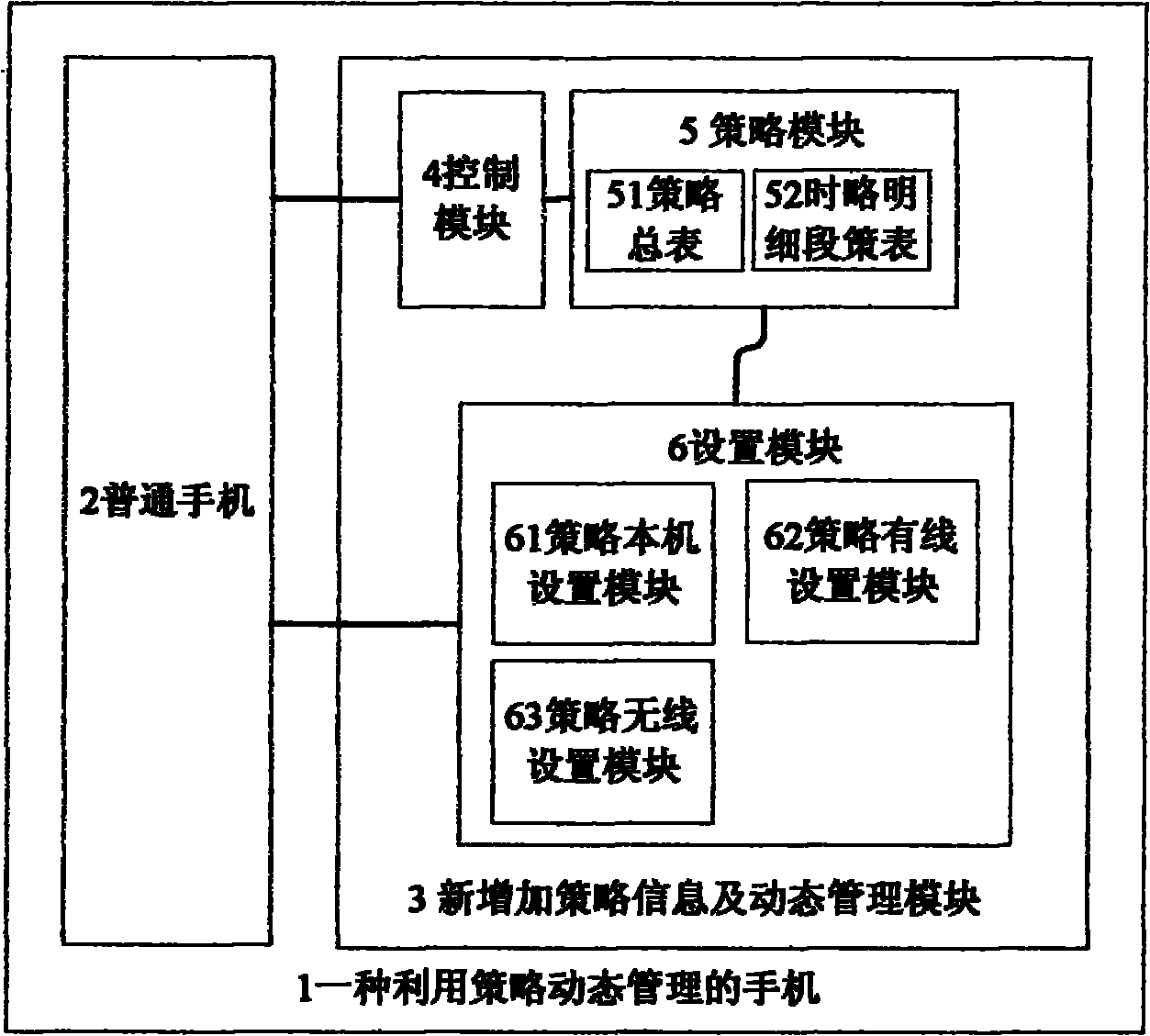
Mobile phone dynamically managed by strategies
InactiveCN101931943ASafe and reasonable to useUse indiscriminatelyWireless network protocolsNetwork data managementDynamic managementMobile phone
The invention relates to a mobile phone, in particular to a mobile phone dynamically managed by strategies. The mobile phone dynamically managed by strategies comprises a strategy module in which a strategy list is stored, a control module and a setting module, wherein the control module dynamically manages the use permission of the integrated function applications in the mobile phone according to strategy attributes; a manager sets the strategy attributes on the mobile phone through the setting module and also can complete the setting from the outside in a wireless or wired way; when a user operates the function applications on the mobile phone, an judgment on the use permission of the function application is made, and use is permitted if a time interval is open, or the use is forbidden if the time interval is closed; at the open or closed time interval, whether the current time is at the open time interval is continuously detected, if the current time is at the open time interval, the use is permitted, or the use is forbidden; and the function application which runs currently is checked regularly and stops running when entering the closed time interval. The mobile phone enables parents to individually configure the function application in the mobile phone and the use time intervals permitted to be used according to the actual condition of students, so that teenagers can use the mobile phone more healthily and rationally.
Owner:袁程
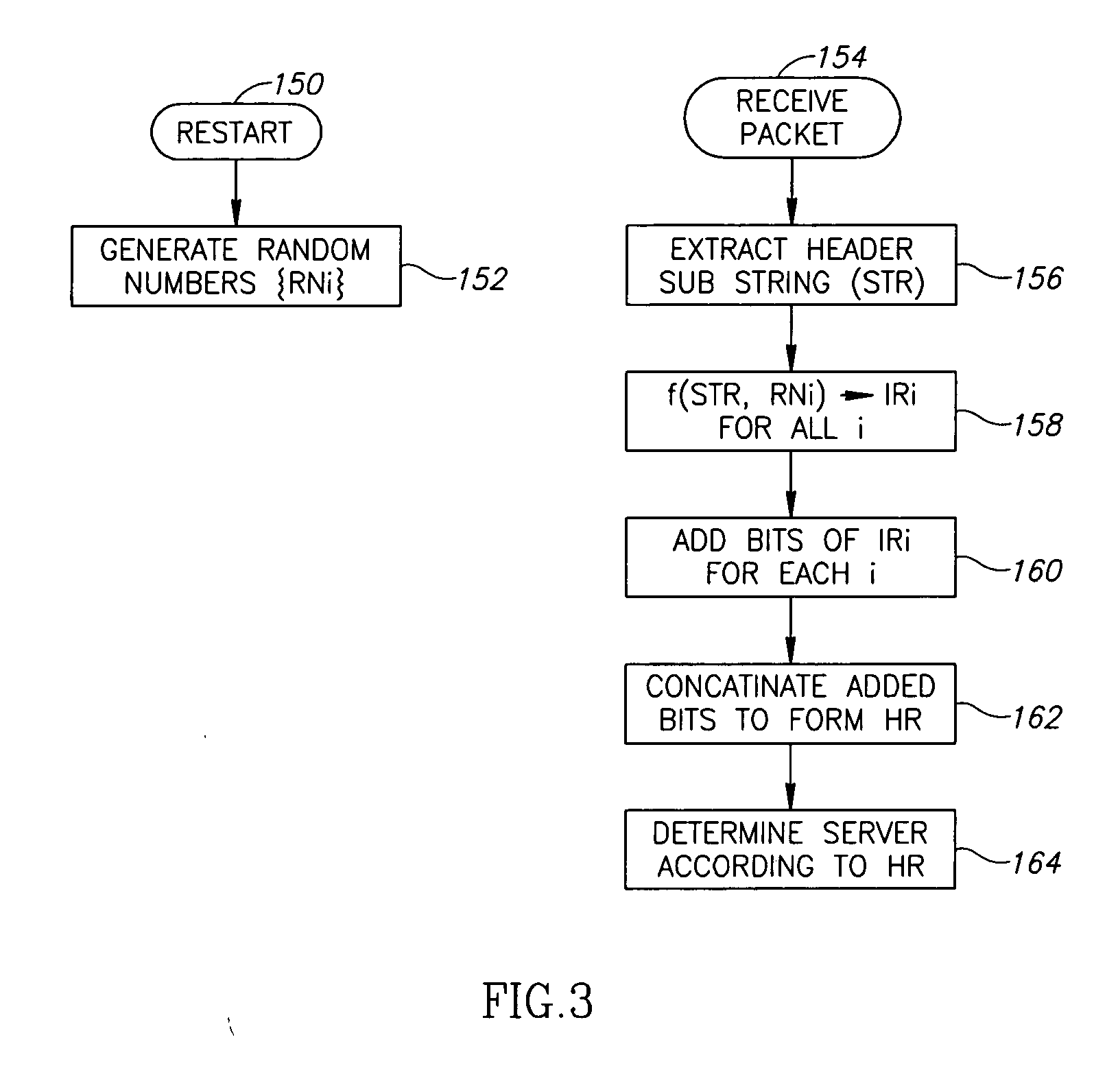
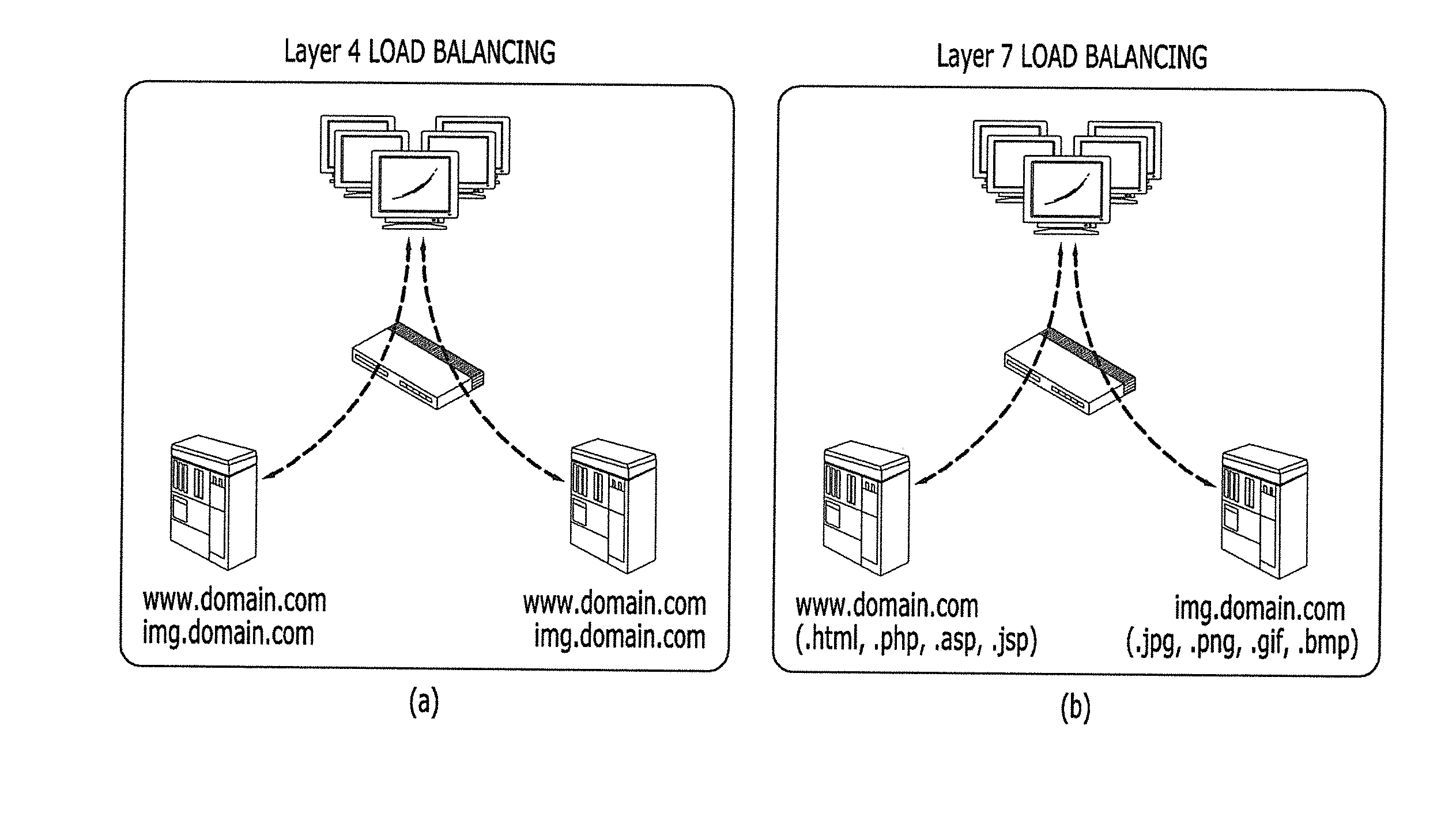
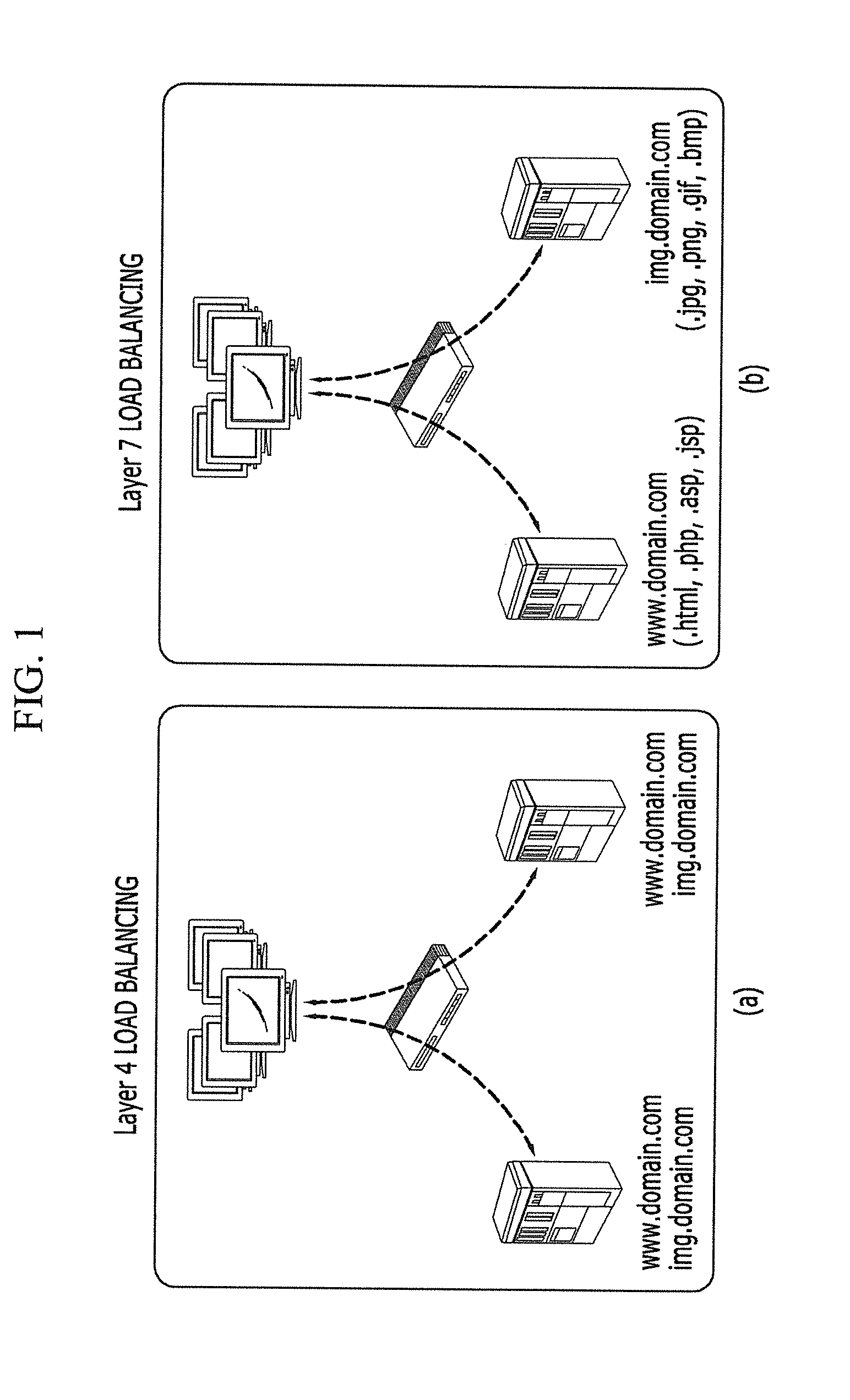
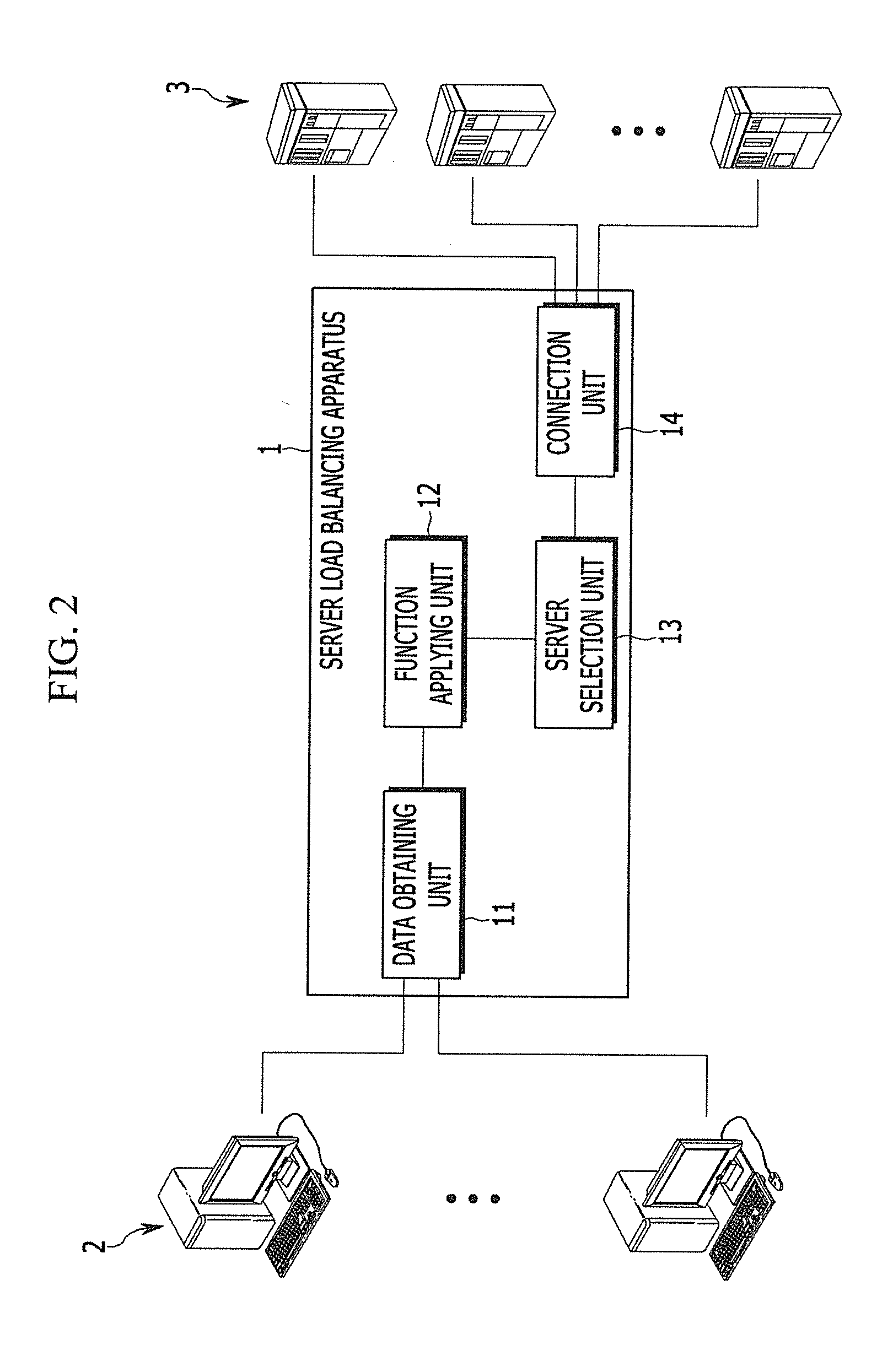
Method and apparatus for processing server load balancing by using the result of hash function
ActiveUS20140337417A1Effective distributionIncrease the number ofTransmissionHash functionClient-side
For load balancing of a plurality of servers, a server load balancing apparatus selects a hash source from a uniform resource locator (URL) input from a client, and applies a predetermined hash function to the hash source. The server load balancing apparatus selects a server from among the plurality of servers according to a hash value based on the hash result of the hash function application.
Owner:SOLBOX INC
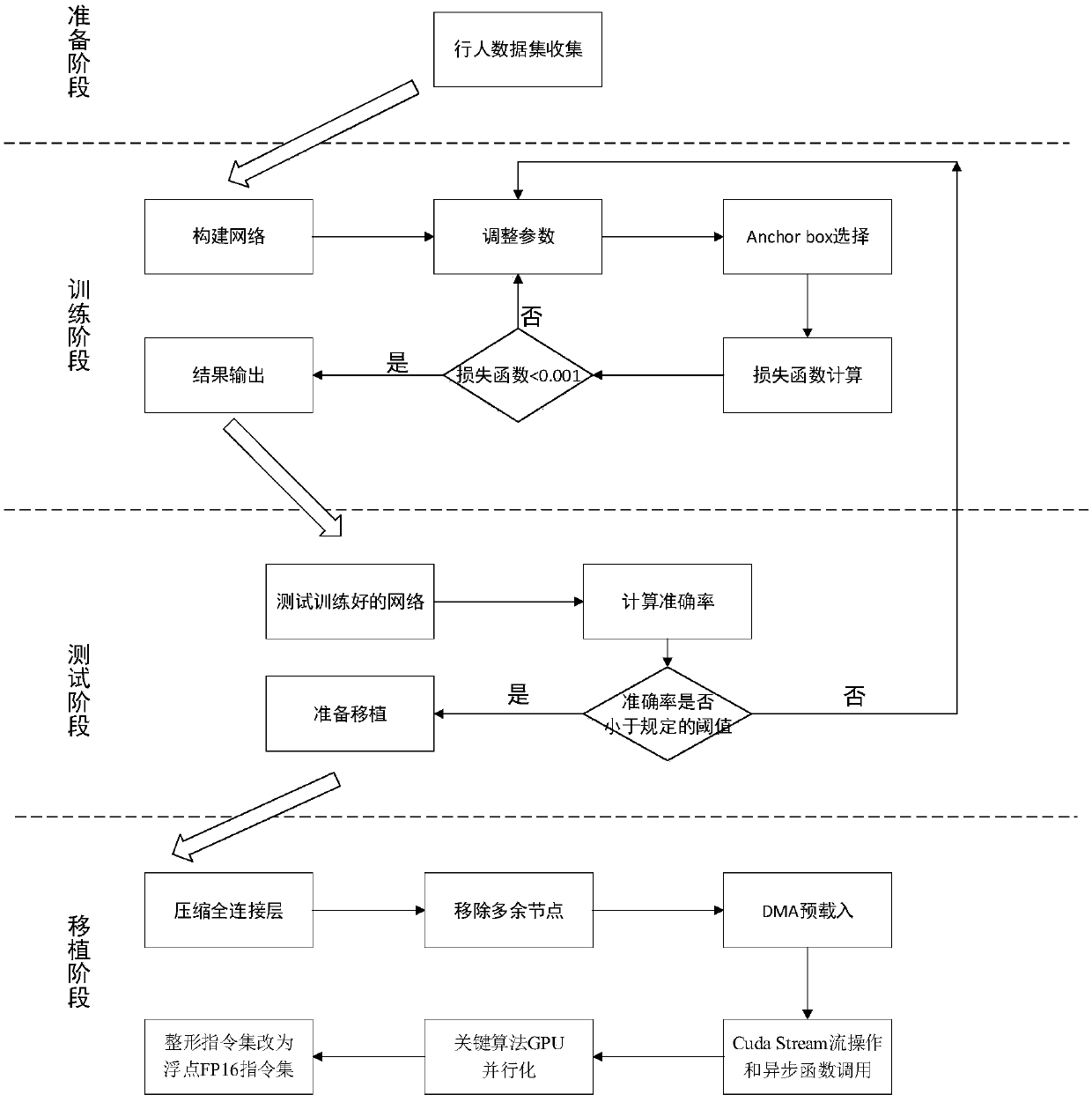
Deep learning pedestrian detection method based on embedded terminal
InactiveCN108805070AObvious speed advantageReduce complexityCharacter and pattern recognitionManual annotationData set
The invention discloses a deep learning pedestrian detection method based on an embedded terminal. The method comprises the steps that first, at a sample preparation stage, an existing automatic driving dataset is acquired, or manual annotations obtained after a fixed camera and a mobile camera shoot videos are collected; second, at a training stage, a large quantity of training images are used totrain parameters of a constructed convolutional neural network so as to complete detection feature learning; third, at a test stage, a large quantity of test images are input into the trained convolutional neural network, and a detection result is obtained; and fourth, at a porting stage, code level optimization and porting into the embedded terminal are performed. According to the method, the 18-layer convolutional neural network is adopted to perform pedestrian feature learning, and the method has an innovative advantage compared with a traditional machine learning method; and an optimization strategy for the embedded terminal is also proposed, the network scale and algorithm complexity are further reduced, and the method is suitable for ADAS function application.
Owner:合肥湛达智能科技有限公司
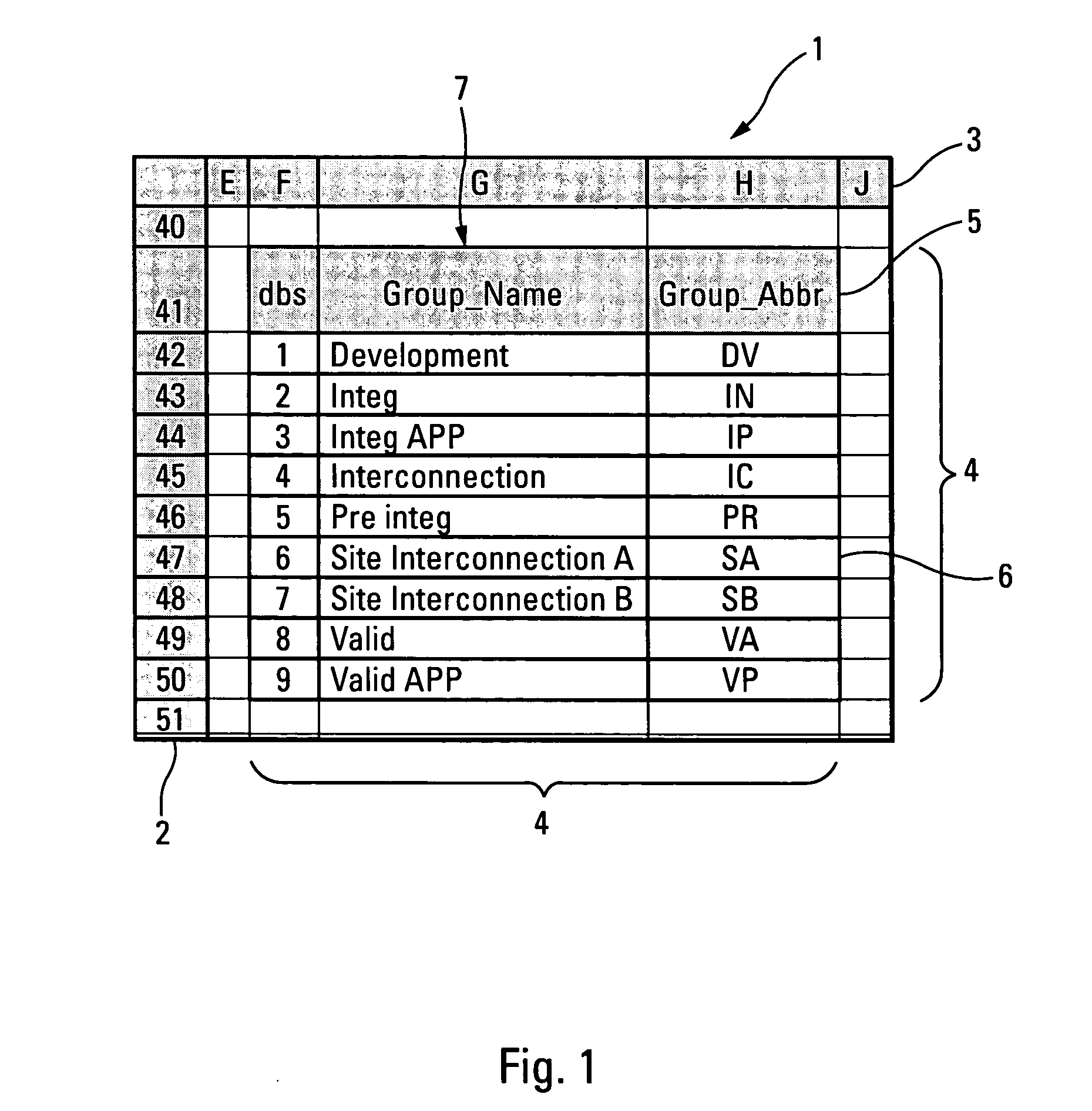
Method of updating a database created with a spreadsheet program
InactiveUS20050149482A1Database updatingDigital data processing detailsElectronic formSources of error
The present invention concerns a method of updating a database created with a spreadsheet program, for example with the Excel computer program. The manipulation of databases in a spreadsheet program may be a source of errors and lack user-friendliness to ensure that it is efficiently used. The main object of the invention is to ensure a uniformity and to facilitate the task of a user in the creation and maintenance of such a database. Accordingly, the object of the invention is an updating method. The data of the database are located in a first range of cells, and update parameters are located in a second range of cells. At least one updating function is applied to a determined set of cells of the first range of cells, each updating function using update parameters contained in determined cells of the second range of cells.
Owner:THALES SA
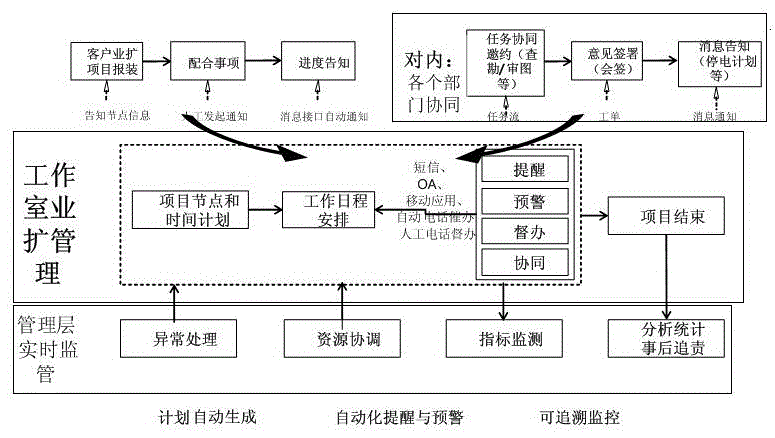
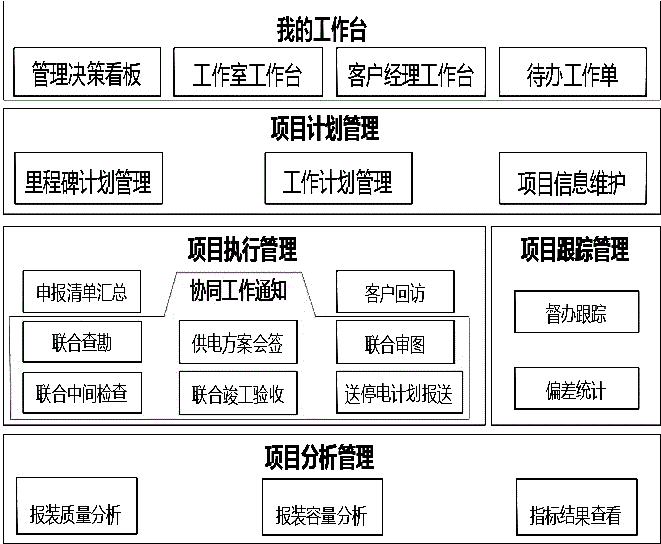
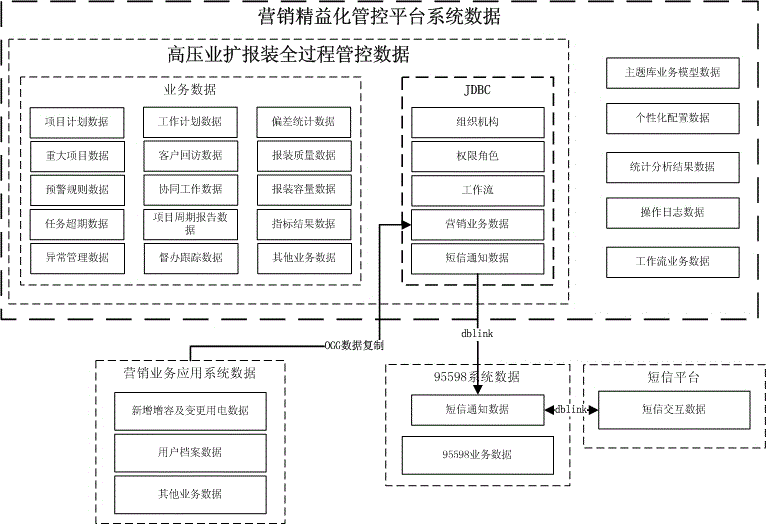
High-voltage business expansion overall process management and control system of power marketing
InactiveCN105427091AImprove capacity completionImprove return visit satisfaction rateOffice automationProject trackingCo operative
The invention discloses a high-voltage business expansion overall process management and control system of power marketing, and relates to a management and control system. Business expansion management work is one of the traditional core businesses of a power supply enterprise, the work developing and finishing situation of the business expansion management work directly affects the brand image and the client service level of the power supply enterprise, and a situation that the business expansion management work is manually carried out can not meet development requirements along with the increase of data. The high-voltage business expansion overall process management and control system comprises a workbench function application module, a project plan management module, a project execution management module, a project tracking management module, a mobile terminal synergy APP (Application) module and a project analysis management module. The technical scheme is cooperated with a management responsibility to develop a business expansion multi-department united cooperative flow and establish a projectized plan management mechanism, a traditional business expansion mode is optimized and improved to develop the overall process management and control of each link of the high-voltage business expansion and realize milestone node management so as to shorten the power connection time of a client, improve the volume completion rate of the high-voltage business expansion and the client review satisfaction rate of the high-voltage business expansion.
Owner:STATE GRID ZHEJIANG HANGZHOU XIAOSHAN POWER SUPPLY CO +2
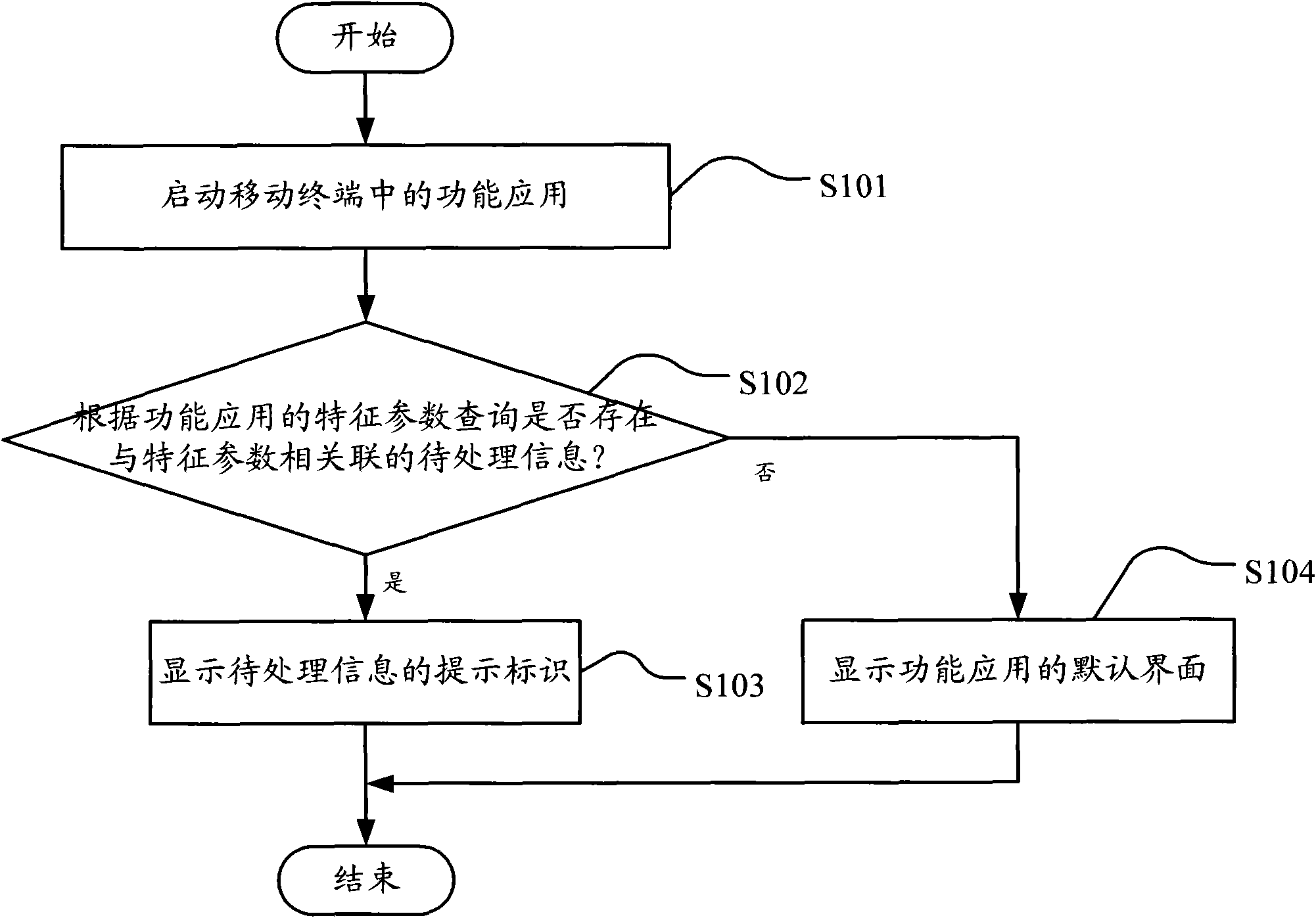
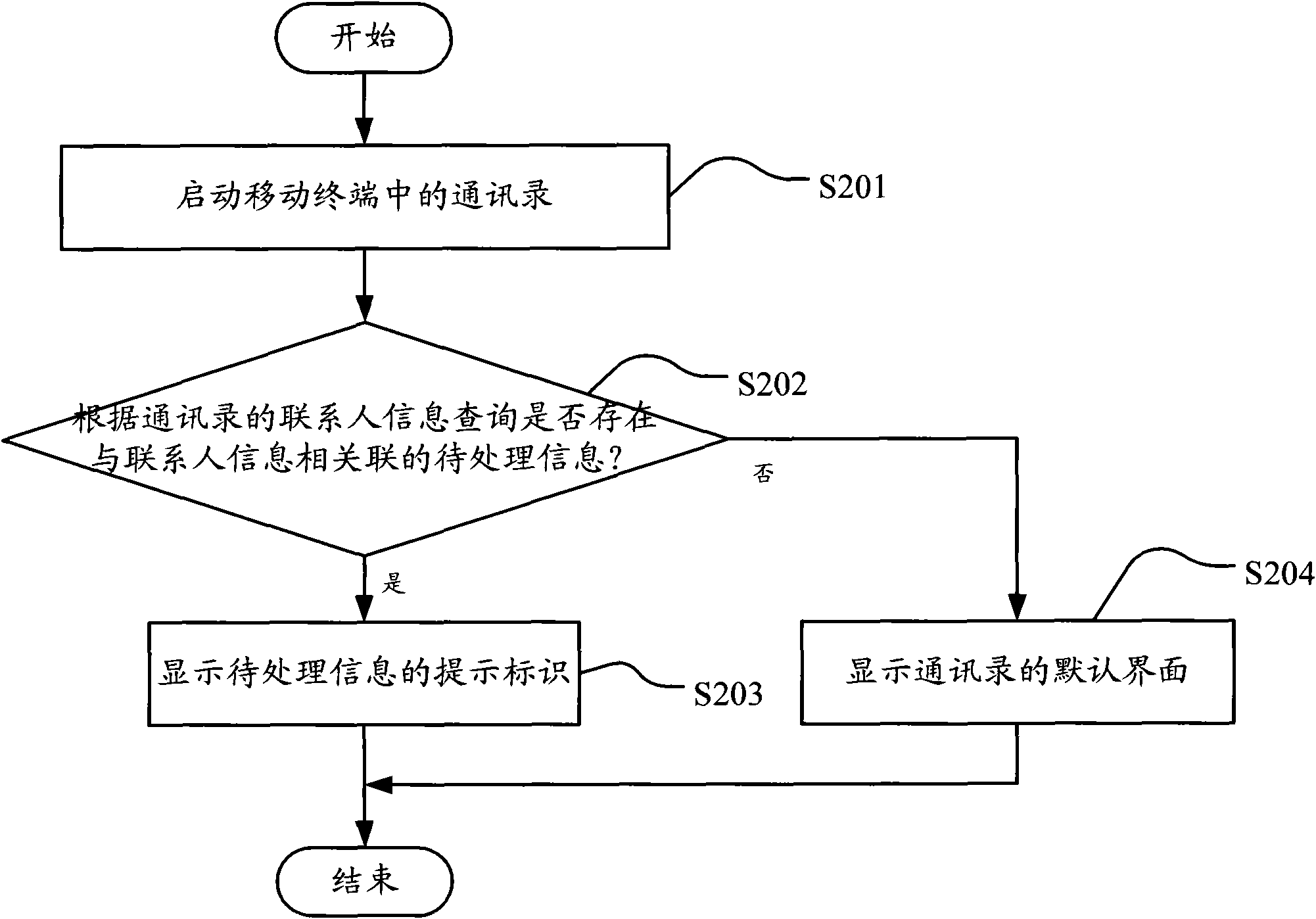
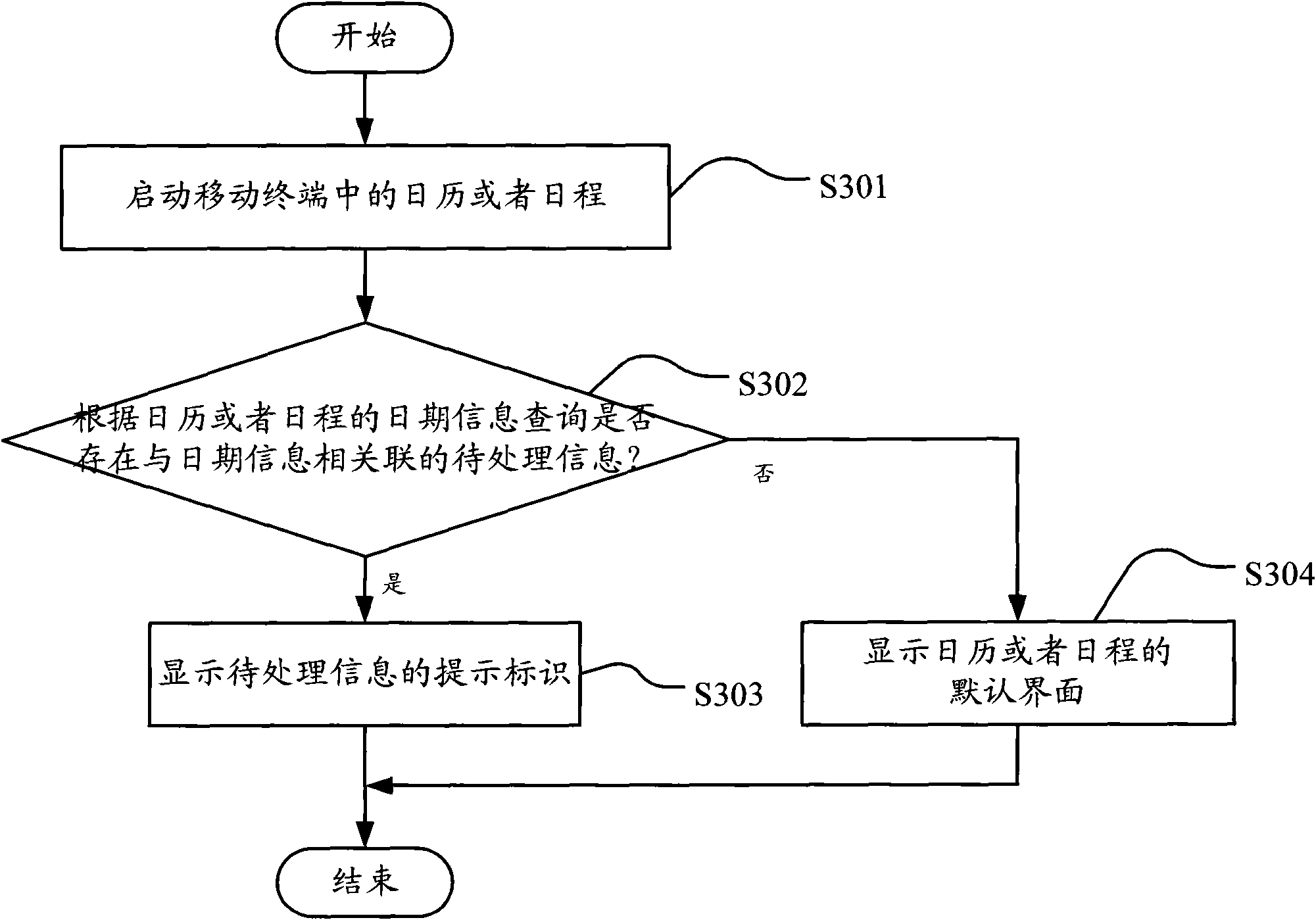
Method and device for giving prompt for information in mobile terminal
InactiveCN101977270AQuick searchConvenient querySubstation equipmentFeature parameterProcess information
The embodiment of the invention discloses a method and a system for giving a prompt for information in a mobile terminal. In the invention, the method comprises the following steps of: starting the function application in the mobile terminal; querying whether the characteristic parameter-related information to be processed exists according to the characteristic parameters of the function application; and if the information exists, displaying the prompting identifier of the information to be processed. In the embodiment of the invention, the information to be processed is queried and a user is promoted according to the characteristic parameters of the function application, so that the user can check the related information to be processed quickly and conveniently through a uniform interface, and convenience is brought to the user for instantly acquiring the information to be processed.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
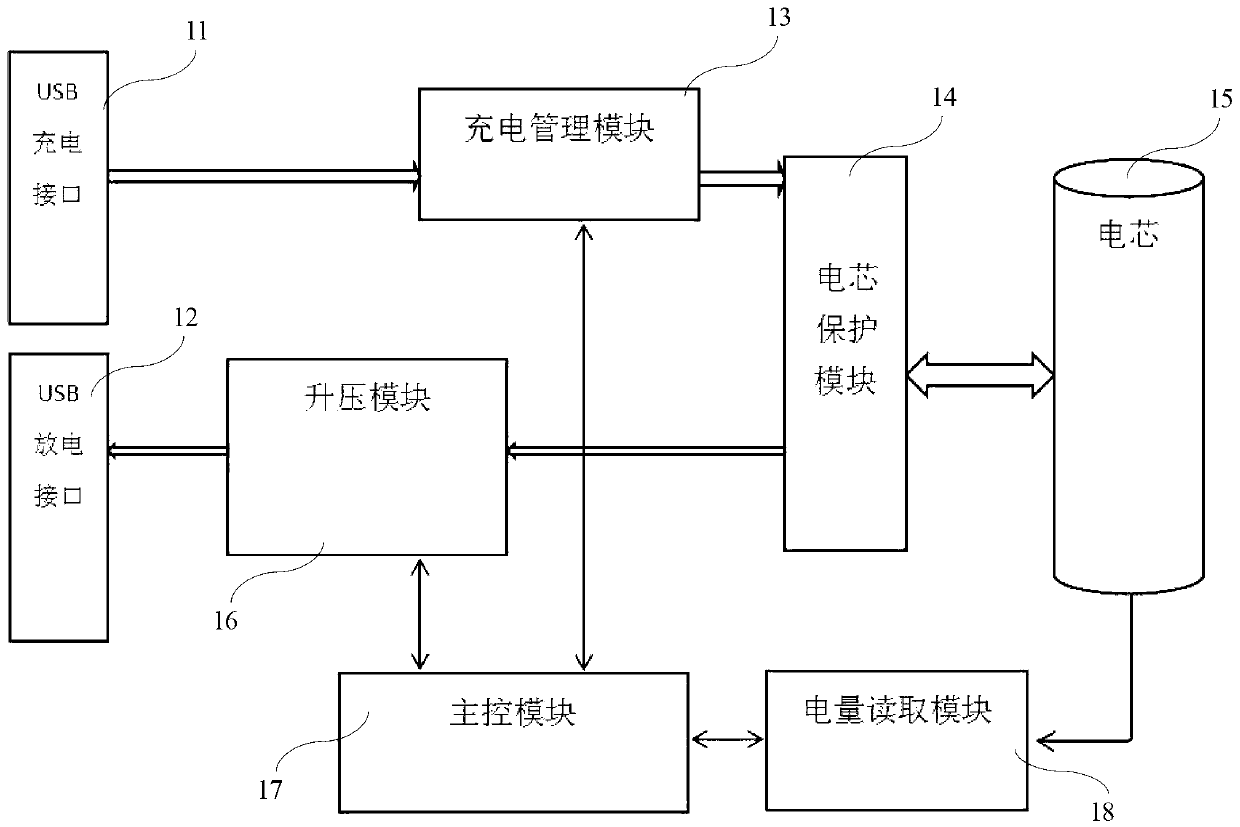
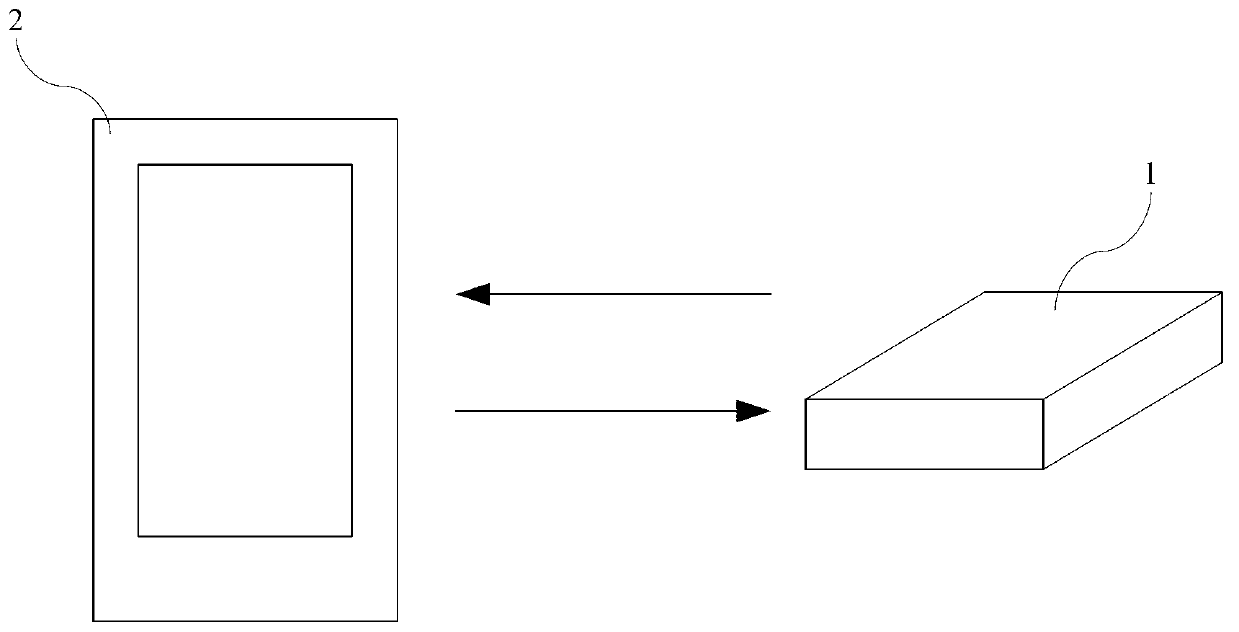
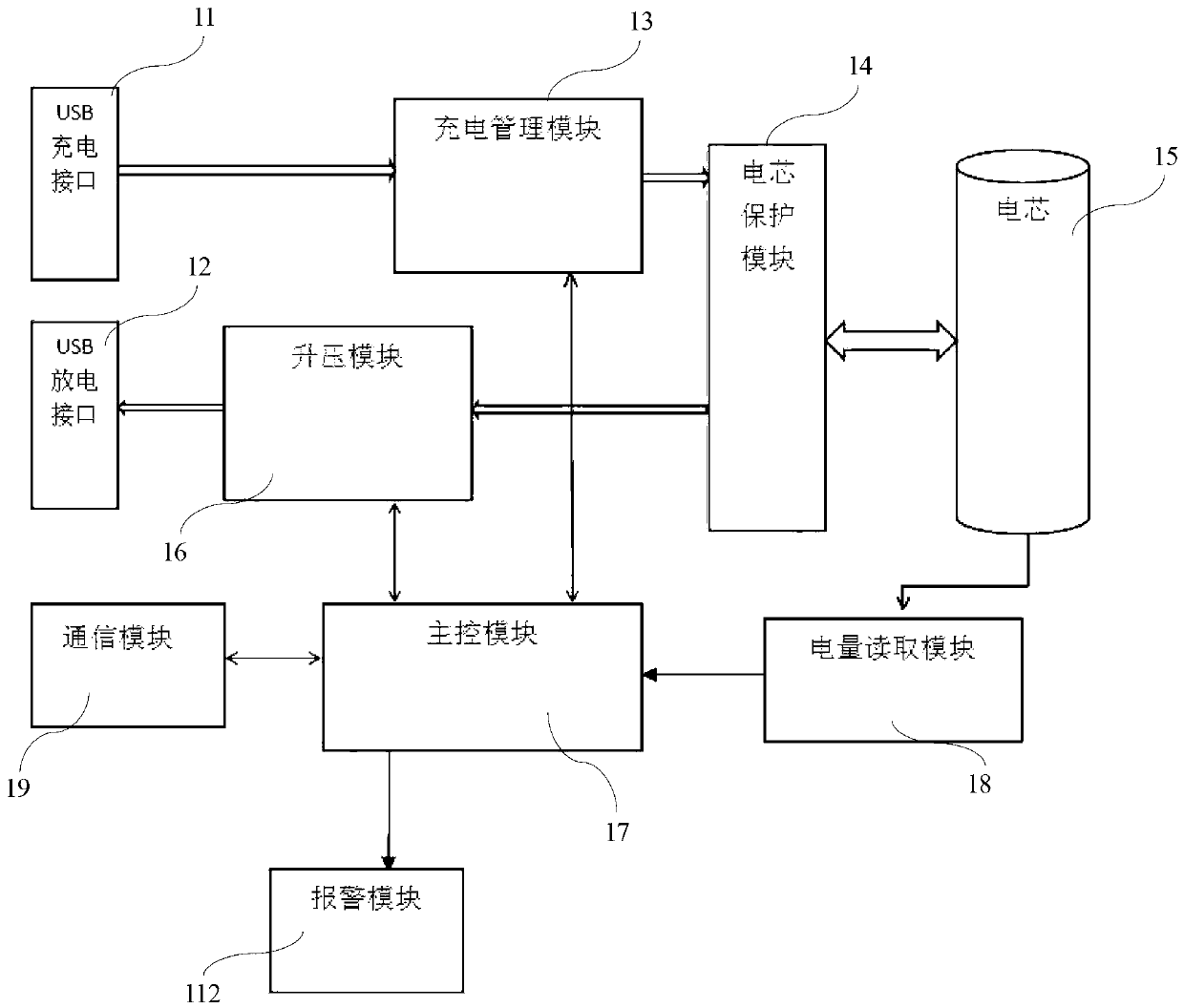
Mobile power supply and extended function application method thereof
InactiveCN103346598AEasy to understandEstimated healthBatteries circuit arrangementsNear-field systems using receiversWireless communication protocolEngineering
The invention discloses a mobile power supply and an extended function application method of the mobile power supply. Due to the fact that a communication module is arranged on the mobile power supply and the communication module and a communication module built in an external mobile device follow the same wireless communication protocol, wireless communication connection can be set up between the mobile power supply and the external mobile device so that command or data transmission can be conducted and then application of various extended functions is achieved. Due to the adoption of the extended function application method of the mobile power supply, the mobile power supply has the advantages of being capable of providing the practical electric quantity or other information of a batter cell inside the power supply in real time, enabling the external mobile device to be controlled in a remote mode through the mobile power supply, and giving an alarm when the connection is broken and thus preventing the mobile power supply or the mobile device from being lost.
Owner:上海网罗电子科技有限公司
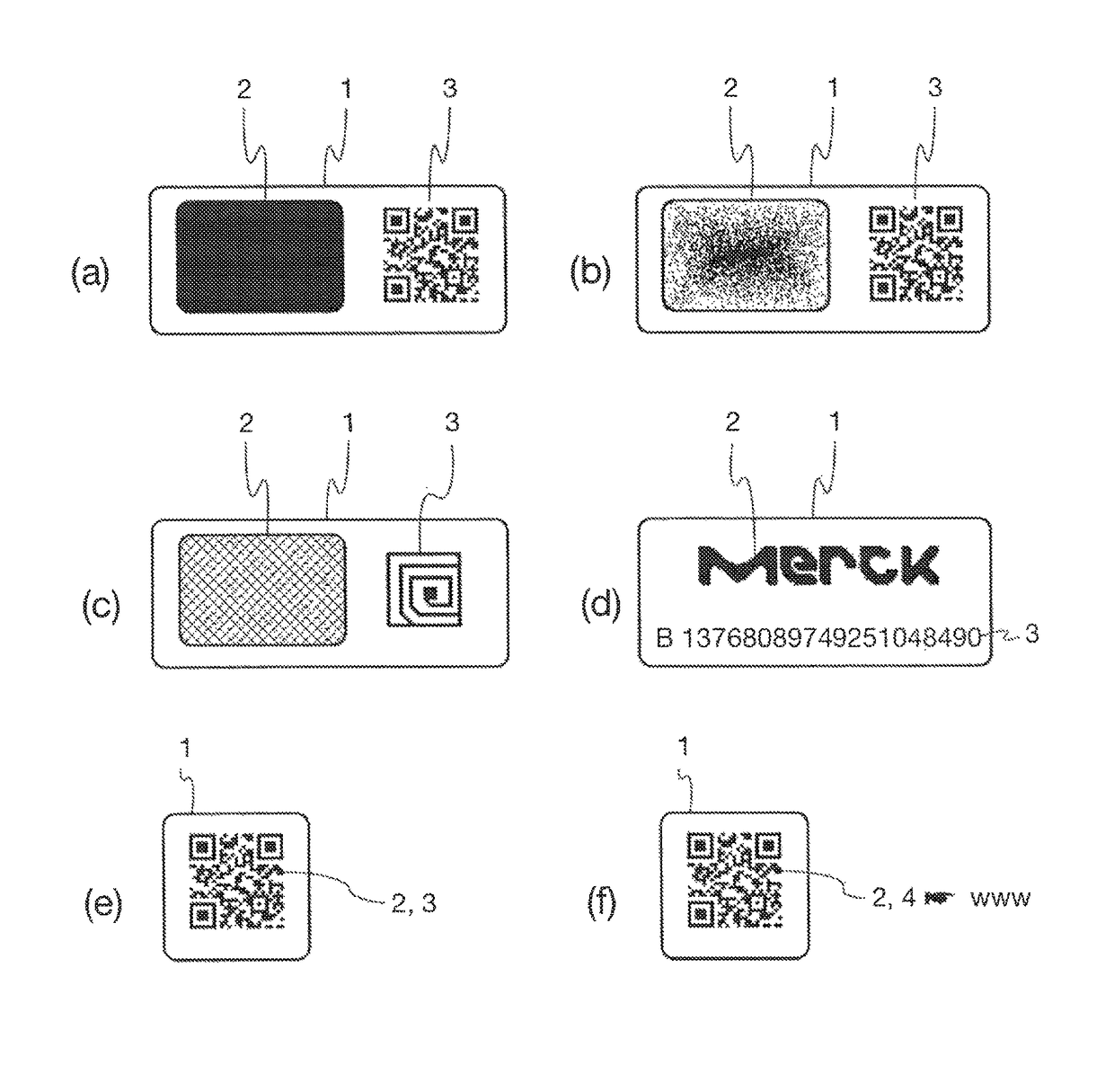
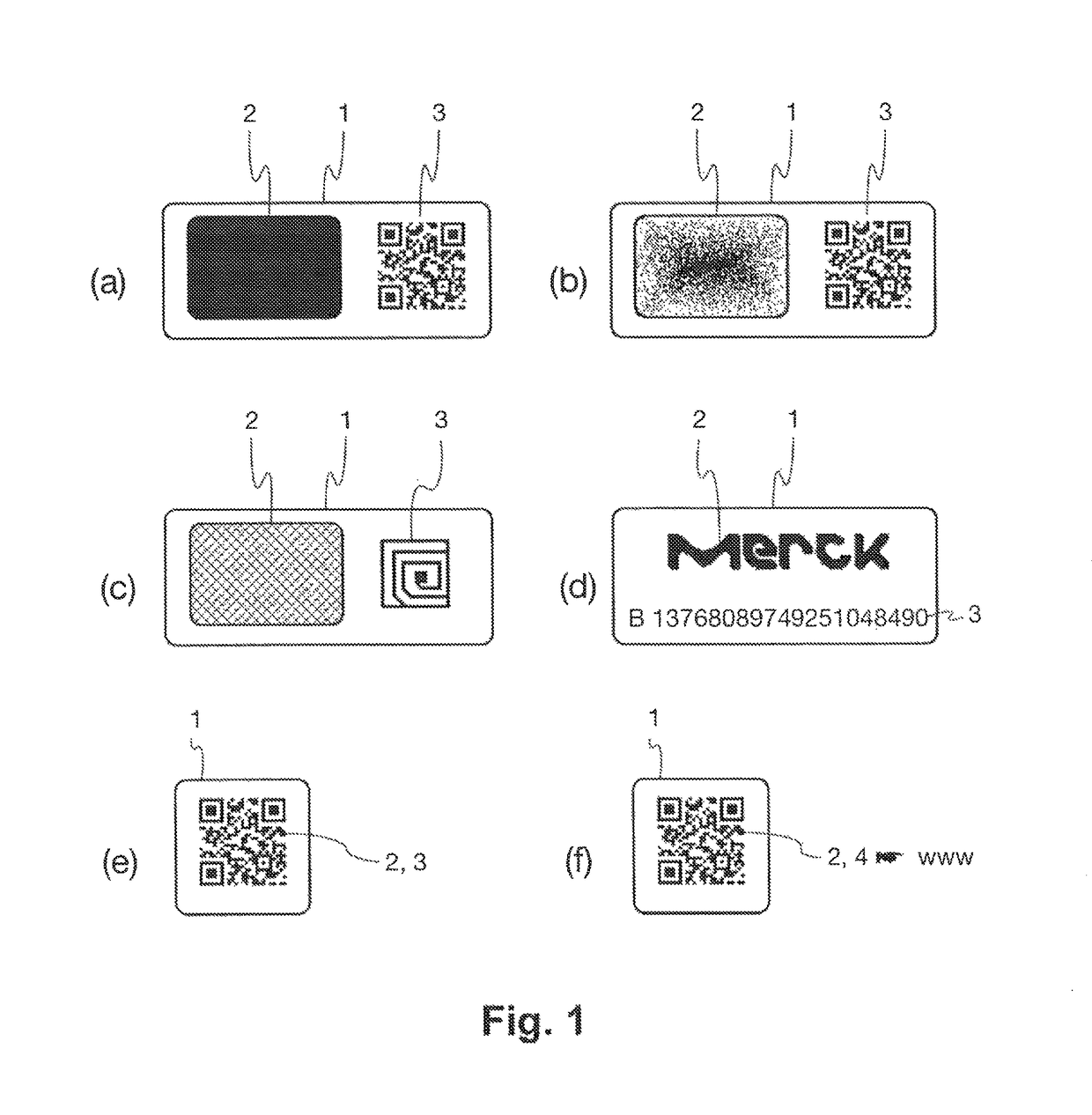
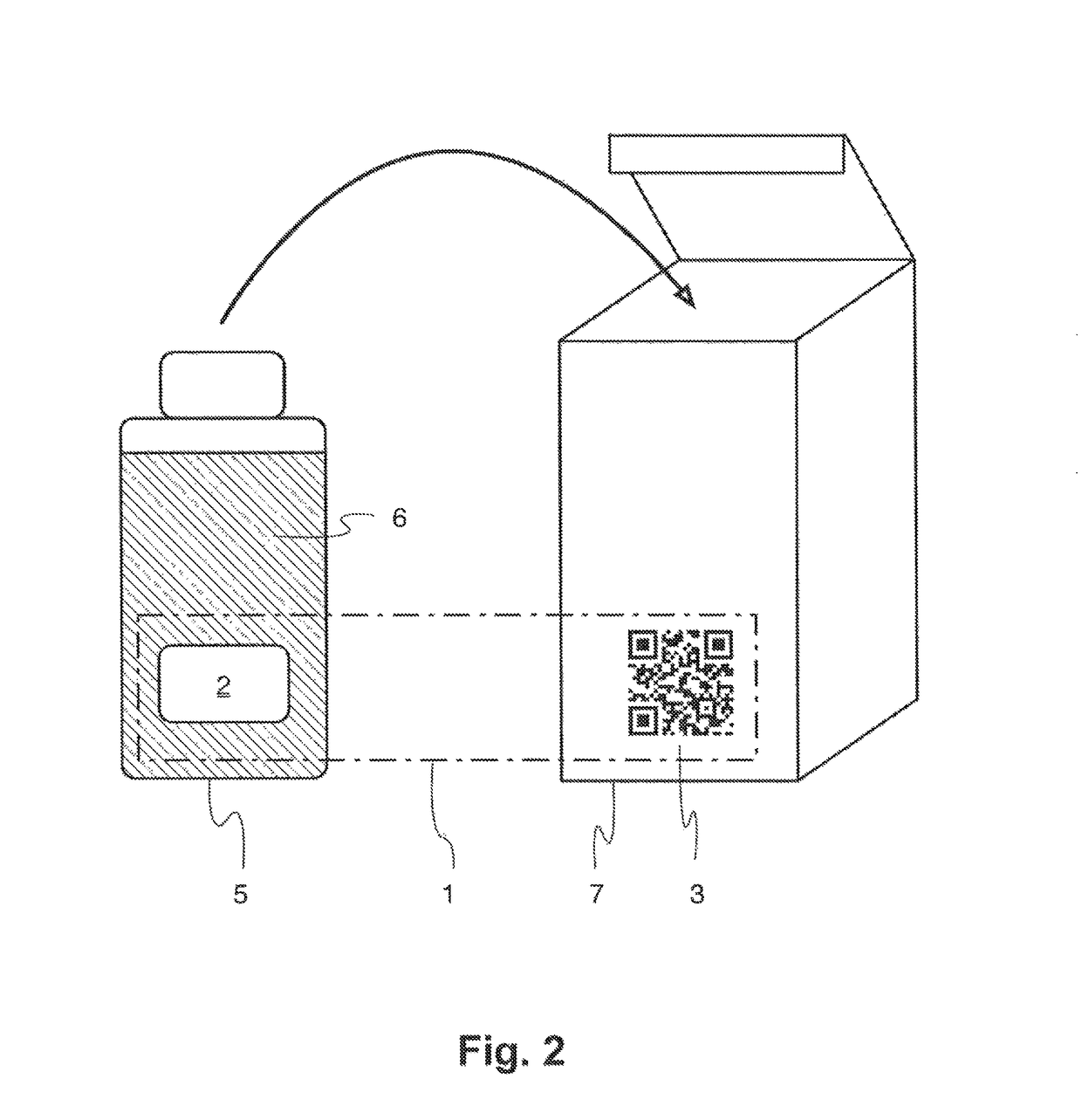
Reader device for reading a marking comprising a physical unclonable function
ActiveUS10002277B1Efficient readingVerify authenticityEncryption apparatus with shift registers/memoriesCoding/ciphering apparatusSecurity solutionCryptographic hash function
The present invention relates to the field of anti-counterfeit protection of products. Specifically, the invention is directed to a method of reading with a reader device a marking comprising a physical unclonable function, PUF, and a corresponding reader device. In particular, such reader device marking can be used in connection with or can form a component of a multi-component security system, in particular of an anti-counterfeit protection system, which is also disclosed herein as part of an overall security solution for anti-counterfeit protection. The method comprises a stimulation step, wherein a physical challenge according to a predetermined challenge-response authentication scheme corresponding to the PUF is created and applied to a PUF; a detection step, wherein a response generated by the PUF in accordance with the challenge-response authentication scheme in reaction to the challenge is detected and a digital signal representing the response is generated; a processing step, wherein the digital signal is processed in order to generate a hash value of the response by application of a predetermined cryptographic hash function to the digital signal; and an output step, wherein data representing the generated hash value as a first reading result is output.
Owner:MERCK PATENT GMBH
Method and system for generation of cryptographic keys for use in cryptographic systems
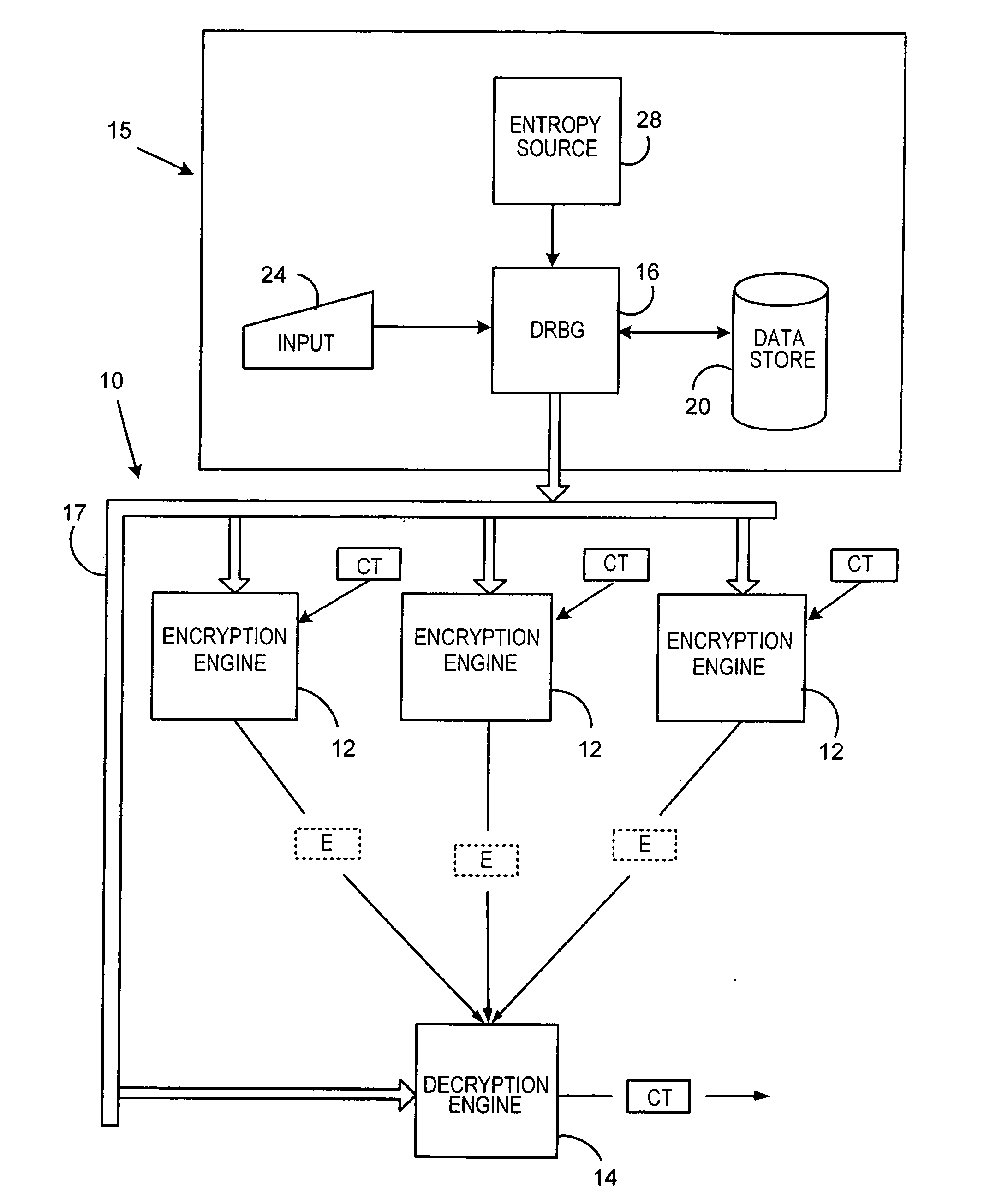
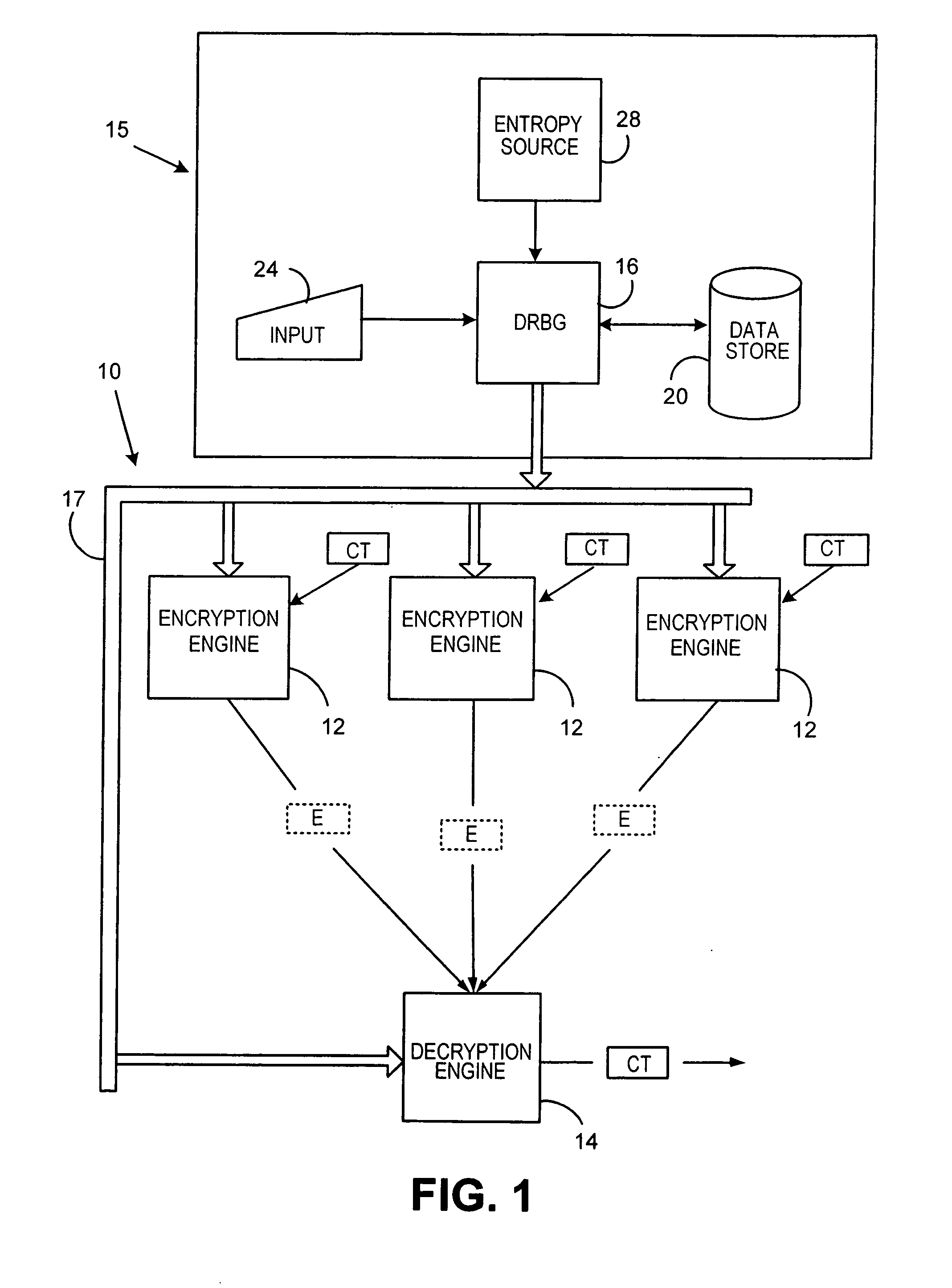
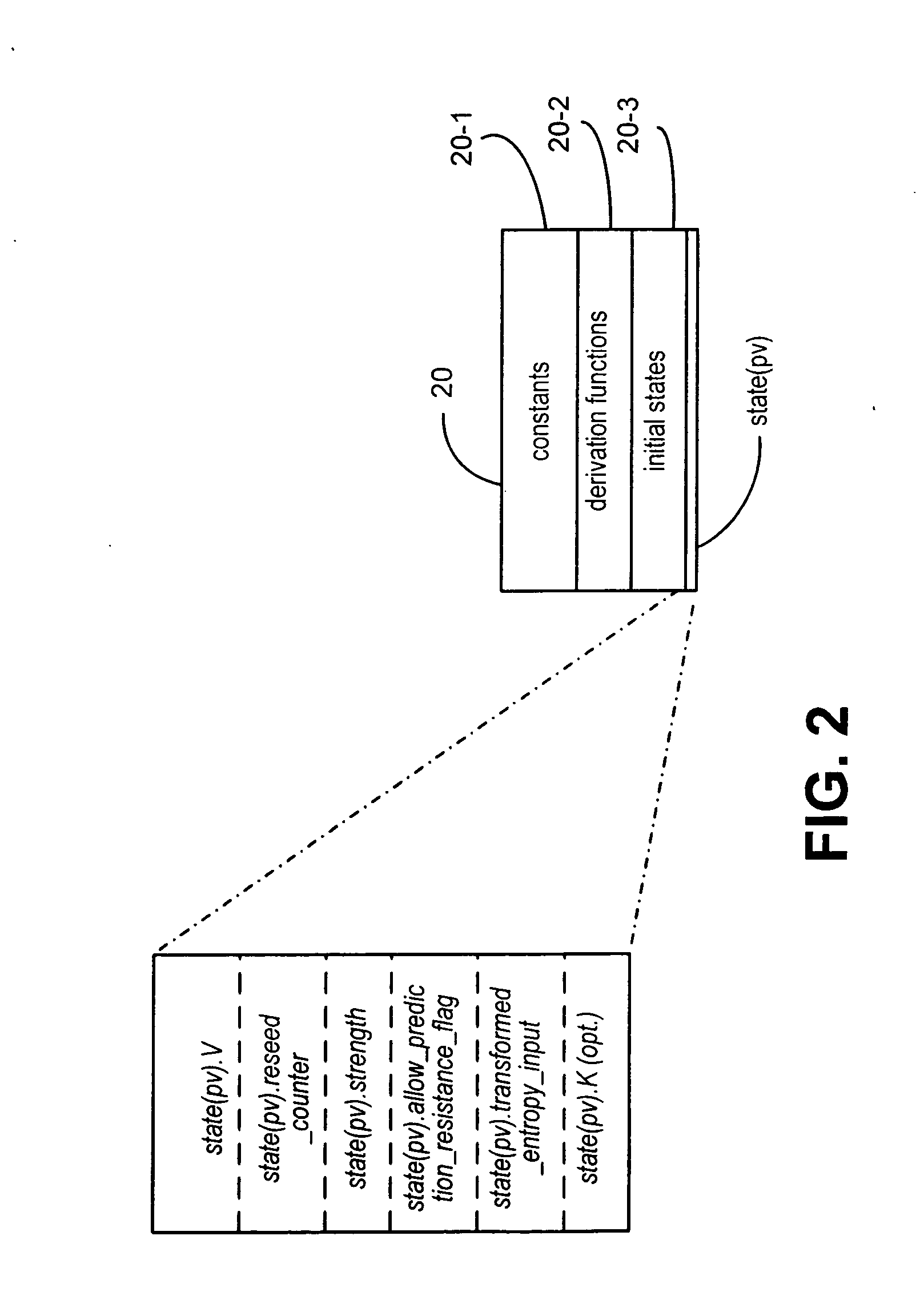
A method and deterministic random bit generator system operating in accordance with the method, for generating cryptographic keys and similar secret cryptographic inputs which are hard to guess. A entropy is input from an entropy source; and an initial seed is generated as a function of the entropy input. When a request to generate a cryptographic key is received a temporary seed is generated by applying the function to the seed. The requested cryptographic key is generated by applying a second function to the temporary seed; and output. A new seed is then generated by applying a third function to the temporary seed. In one embodiment of the subject invention all three functions are carried out by applying the same operator to appropriate inputs. In another embodiment of the subject invention new entropy is incorporated into the seed from time to time.
Owner:PITNEY BOWES INC
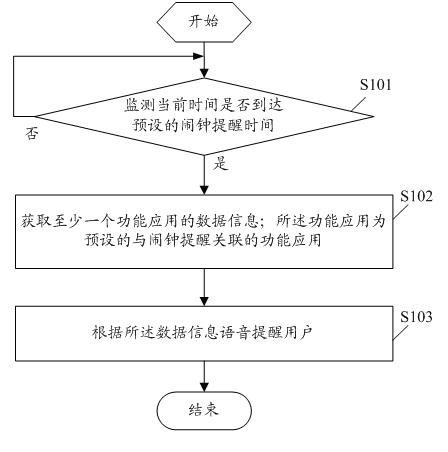
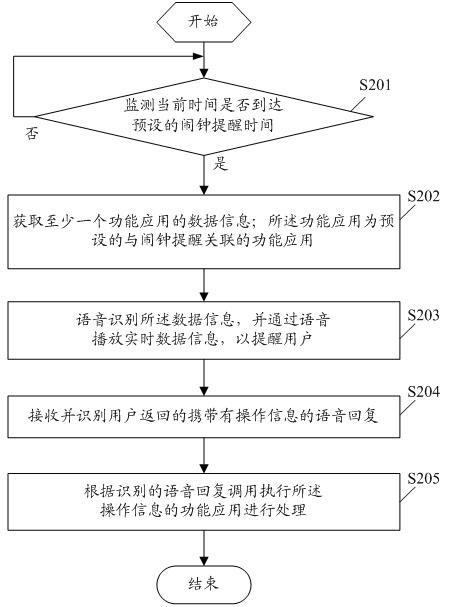
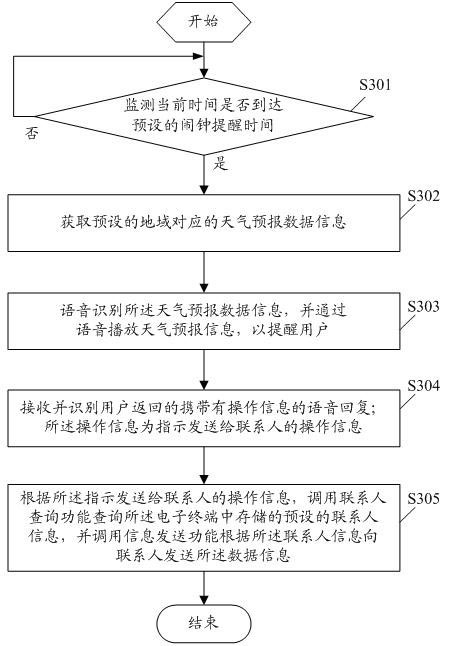
Method for realizing alarm clock reminding on electronic terminal and electronic terminal
InactiveCN102082855AAdd funImprove experienceAutomatic exchangesMessaging/mailboxes/announcementsData informationInterconnection
The embodiment of the invention discloses a method for realizing alarm clock reminding on an electronic terminal, which comprises the following steps: monitoring whether the current time achieves preset alarm clock reminding time or not; if so, acquiring data information of at least one function application, wherein the function application is the function application which is preset and related to the alarm clock reminding; and reminding a user through voice according to the data information and performing voice interaction with the user. The embodiment of the invention further discloses the electronic terminal. By adopting the method and the electronic terminal, the problem that the alarm clock reminding function in the prior art is boring and single can be effectively solved, other function applications can be automatically called for reminding treatment by associating the alarm clock reminding with other function applications, intelligentization and interconnection of the alarm clock reminding are realized, the transaction processing function which is more convenient and faster can be provided for business people, and fun and experience of the user in the use of the electronic terminal are greatly improved.
Owner:DONGGUAN YULONG COMM TECH +1
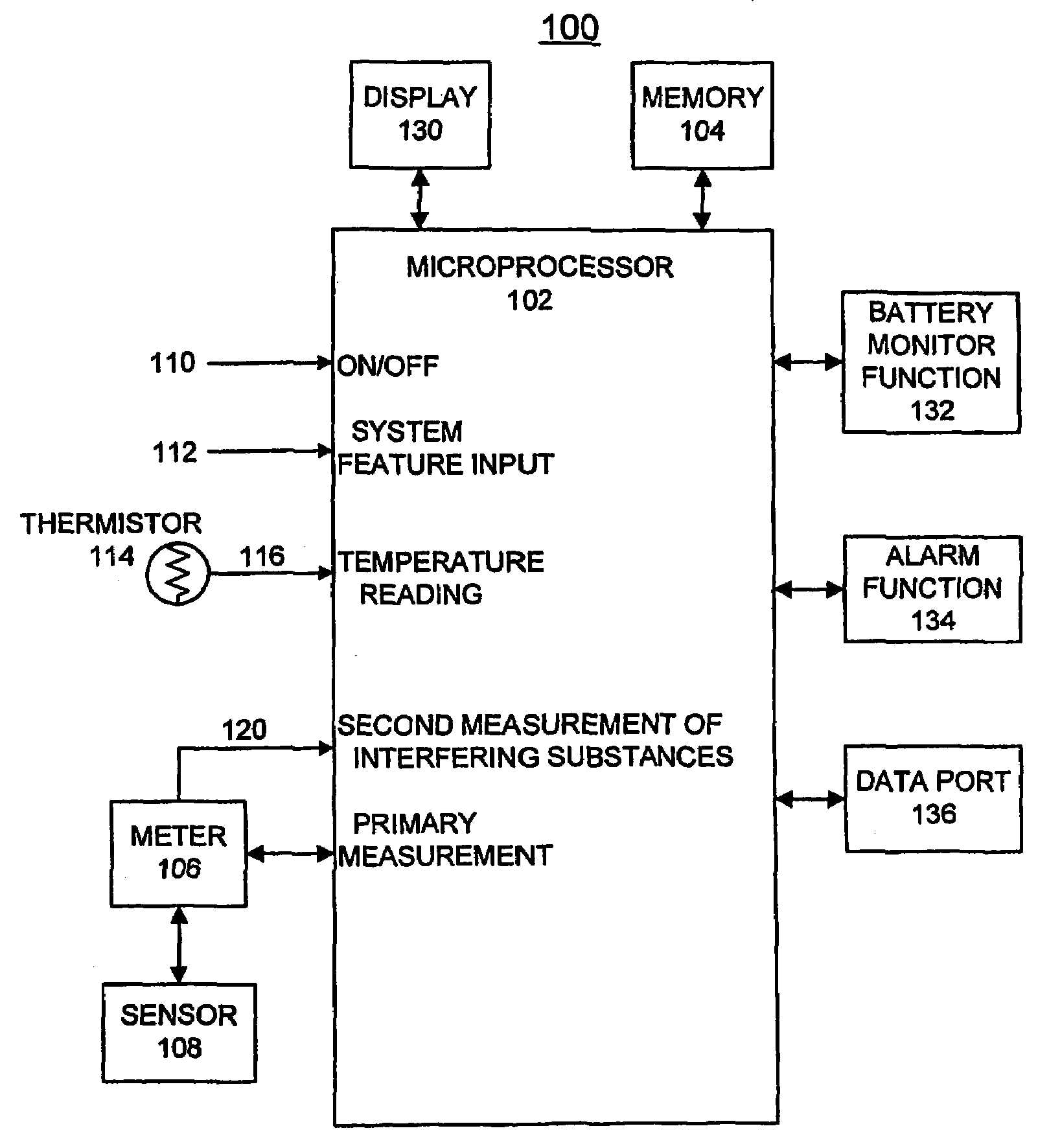
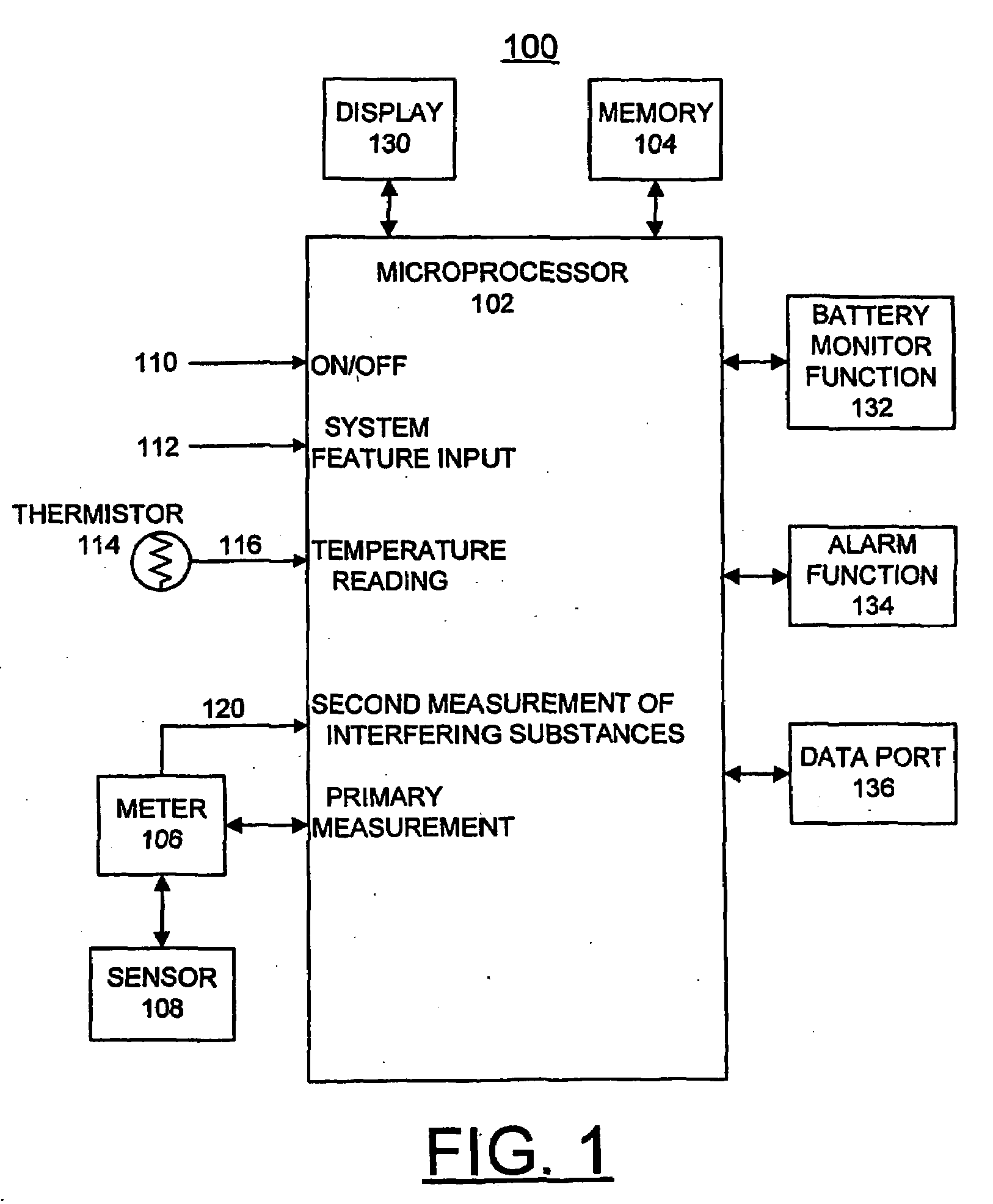
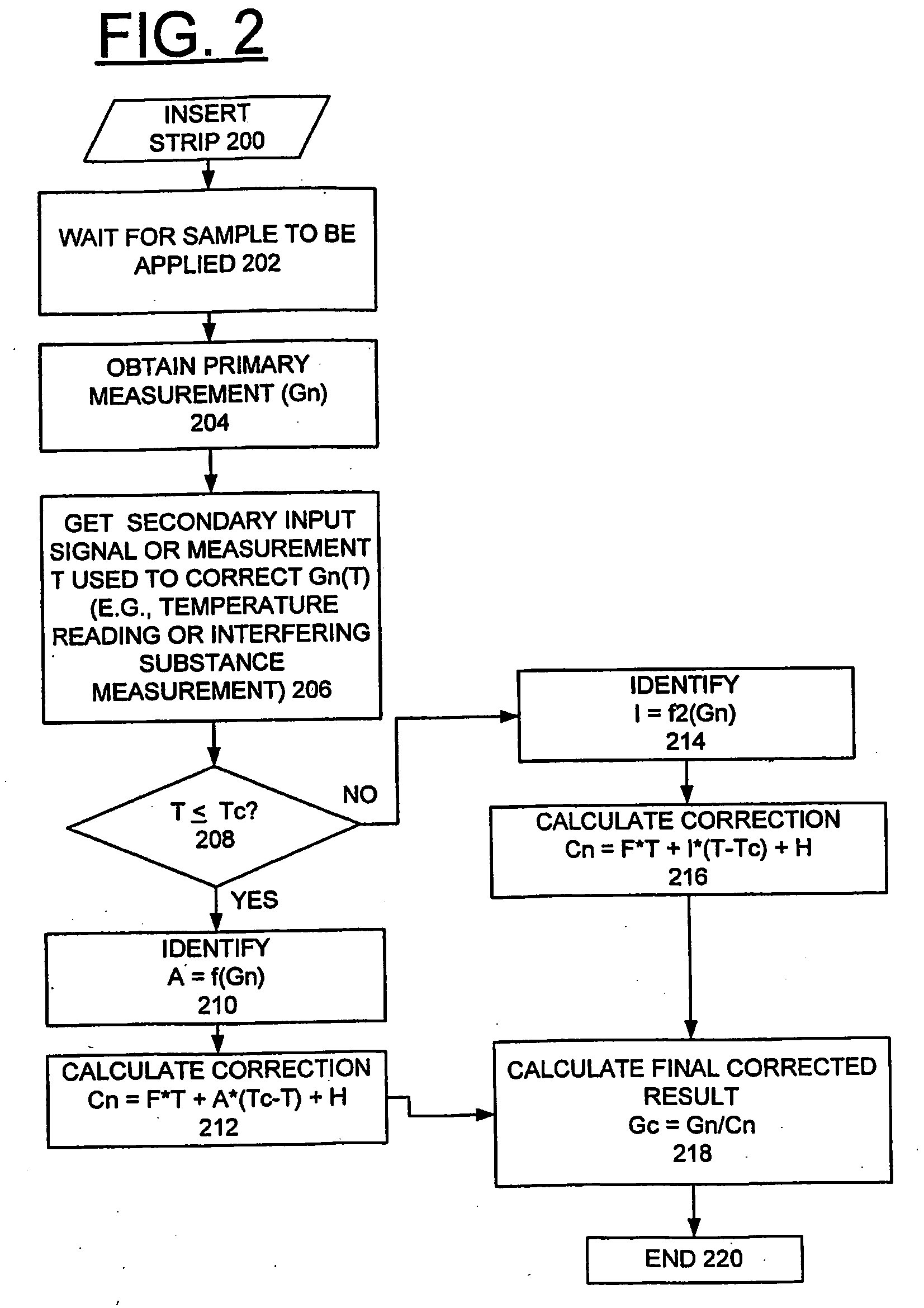
Method and Apparatus for Implementing Threshold Based Correction Functions for Biosensors
InactiveUS20080274447A1Minimize interferenceMicrobiological testing/measurementMaterial analysis by electric/magnetic meansAnalyteEngineering
A biosensor system, method and apparatus are provided for implementing threshold based correction functions for biosensors. A primary measurement of an analyte value is obtained. A secondary measurement of a secondary effect is obtained and is compared with a threshold value. A correction function is identified responsive to the compared values. The correction function is applied to the primary measurement of the analyte value to provide a corrected analyte value. The correction method uses correction curves that are provided to correct for an interference effect. The correction curves can be linear or non-linear. The correction method provides different correction functions above and below the threshold value. The correction functions may be dependent or independent of the primary measurement that is being corrected. The correction functions may be either linear or nonlinear.
Owner:ASCENSIA DIABETES CARE HLDG AG
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com