Static-analysis-assisted symbolic execution vulnerability detection method
A technology of symbolic execution and static analysis, which is applied in the field of identification and detection of software vulnerabilities, can solve the problems of wasting computing time and resources, increasing the false negative rate, limiting the efficiency of vulnerability detection, etc., and achieve the goal of reducing computing time and resources and improving efficiency Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
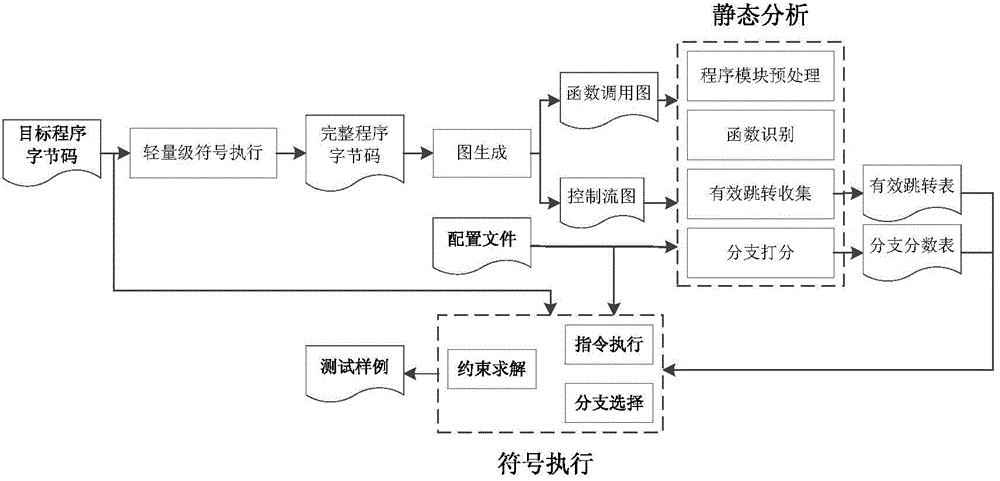
[0028] figure 1Shown is the general flowchart of this method. The input of this method is divided into two parts: target program bytecode and configuration file. The bytecode of the target program is obtained by compiling the C / C++ source program with Clang, the front end of the LLVM 3.1 compiler system. Users can define sensitive operations that may cause software vulnerabilities in the configuration file as the target of this detection, and define corresponding security constraints for each sensitive operation. If the sensitive operation can violate the security constraints in the execution environment, the sensitive operation is considered as a triggerable program vulnerability. The output of this method is a test sample of the program input. By executing the test sample, the current execution environment can be reached and sensitive operations can be triggered to violate the security constraints.
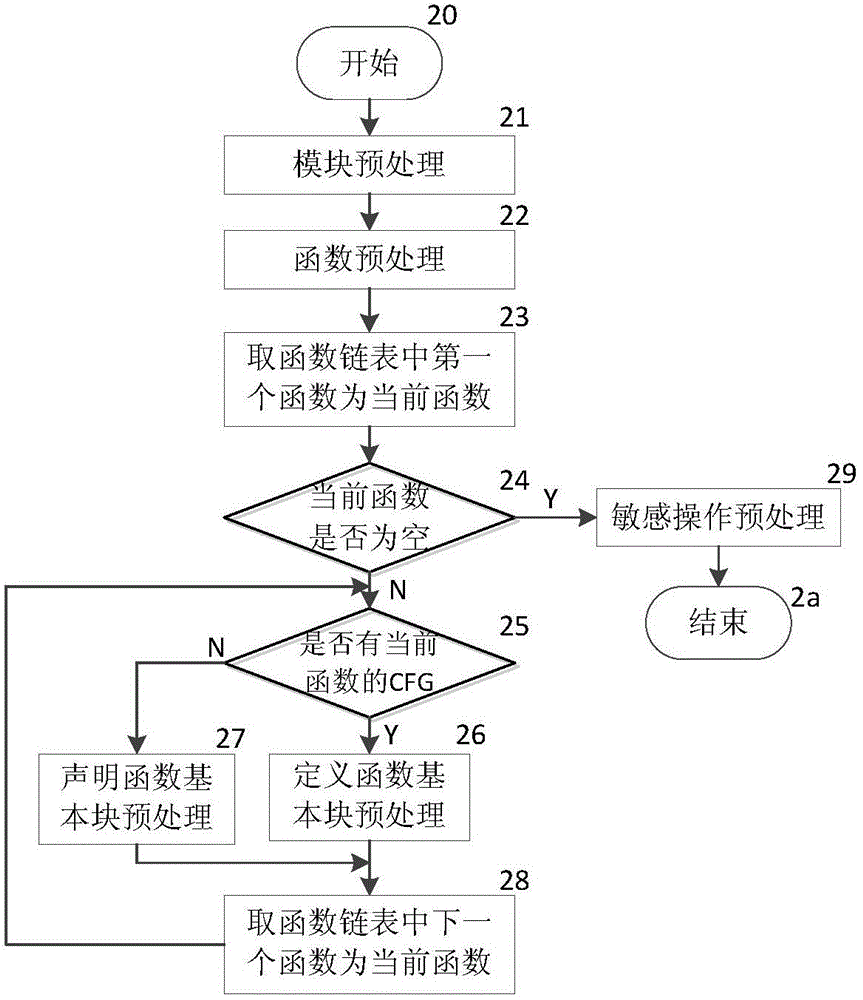
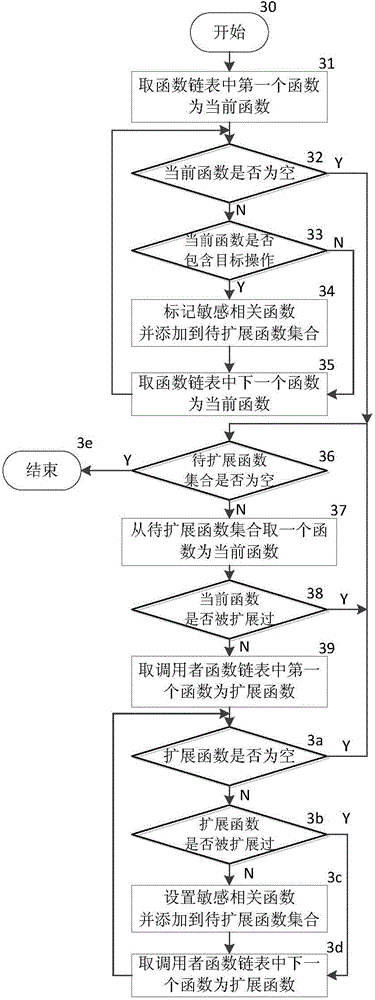
[0029] First, the lightweight symbolic execution process uses the symbol...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com