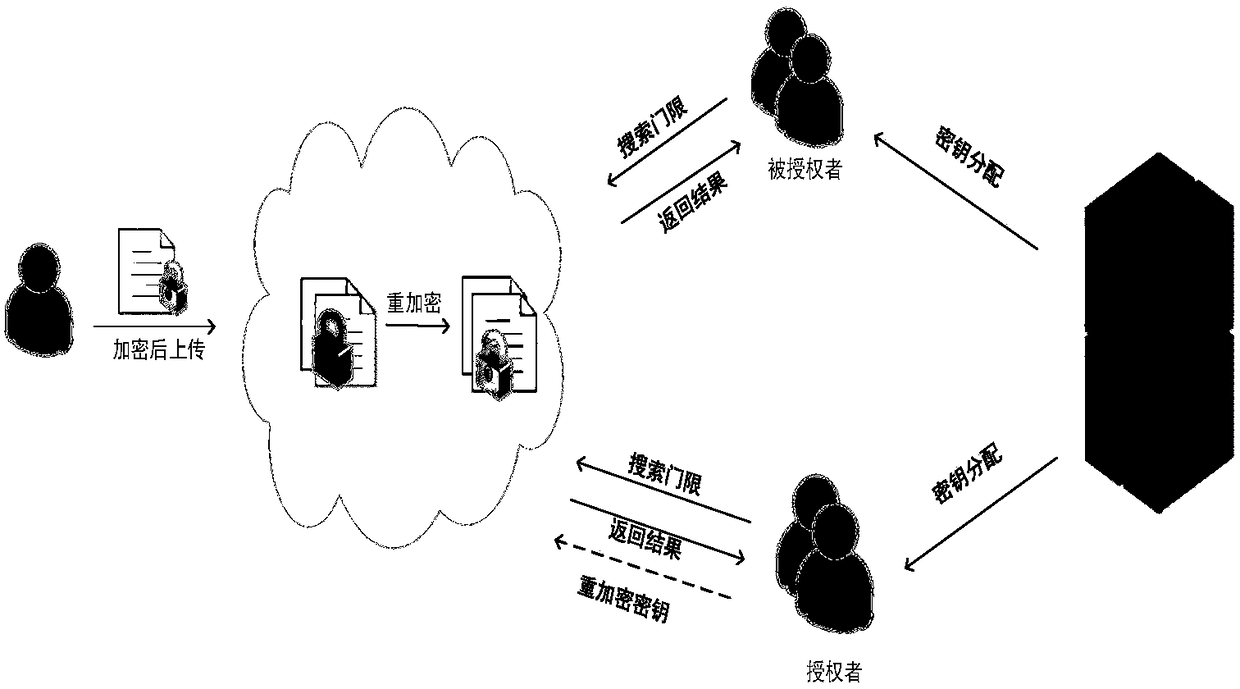
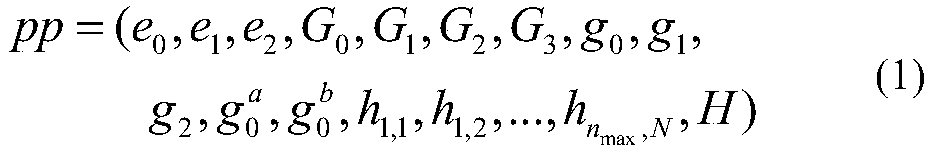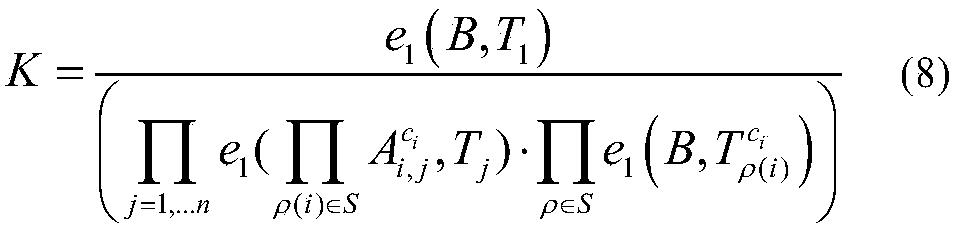Permission sharing model by medical cloud search
A cloud search and permission technology, applied in the field of searchable encryption, which can solve the problem of access policies relying on authorization centers, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0046] 1 Basic concept description
[0047] 1.1 Bilinear Mapping
[0048] Definition 1 bilinear map. G and G T are two multiplicative cyclic groups of order p. Bilinear map e:G×G→G T ,g,g T Respectively G, G T The generator of , satisfying the following properties at the same time:
[0049] Bilinear: there exists e(g a , g b )=e(g,g) ab ,in
[0050] • Non-degenerate: There exists g∈G such that e(g,g)≠1.
[0051] Computability: yes e(u,v) can be calculated efficiently.
[0052] 1.2 Difficult Problem Hypothesis
[0053] Definition of n-multilinear map: Given a security parameter l and a l-bit prime number p, an n-multilinear map is composed of n p-order groups (G 0 ,G 1 ,...,G n-1 ) and n-1 mappings e i :G 0 ×G i →G i+1 (i=0,...n-2) composition. The n-multilinear map should satisfy the following properties, for (i=0,...n-2):
[0054] · If g ∈ G 0 for G 0 generator, then g i+1 = e i (g 0 , g i ) is G i+1 generator of .
[0055] Satisfy
[005...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com