Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
54results about How to "Minimize security risk" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
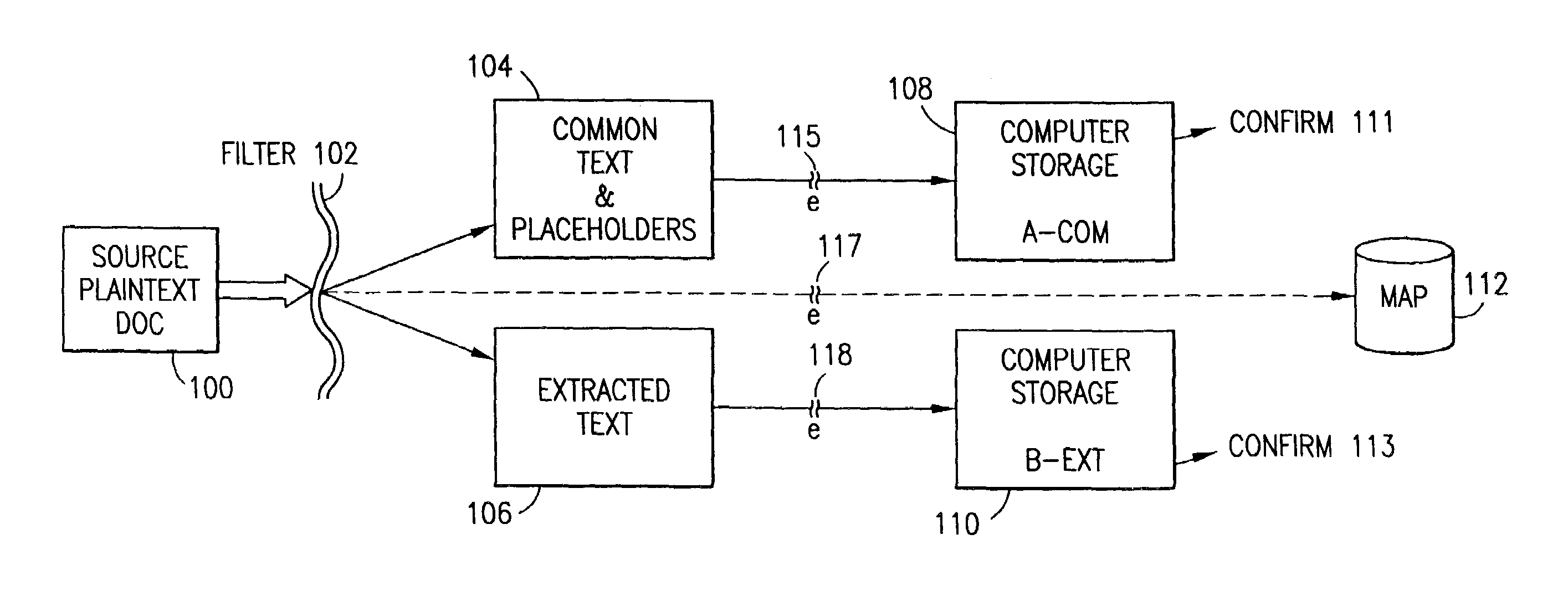
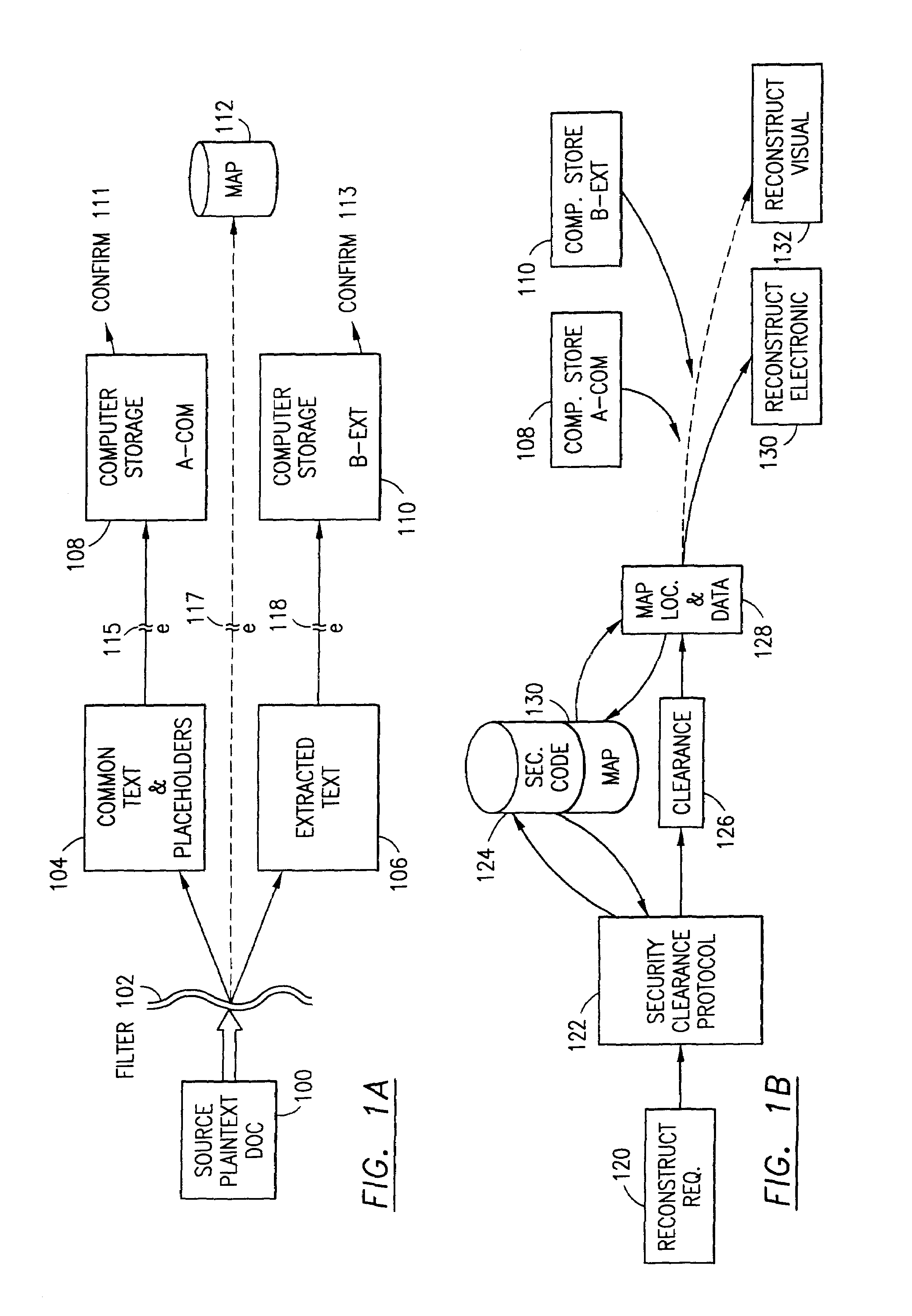
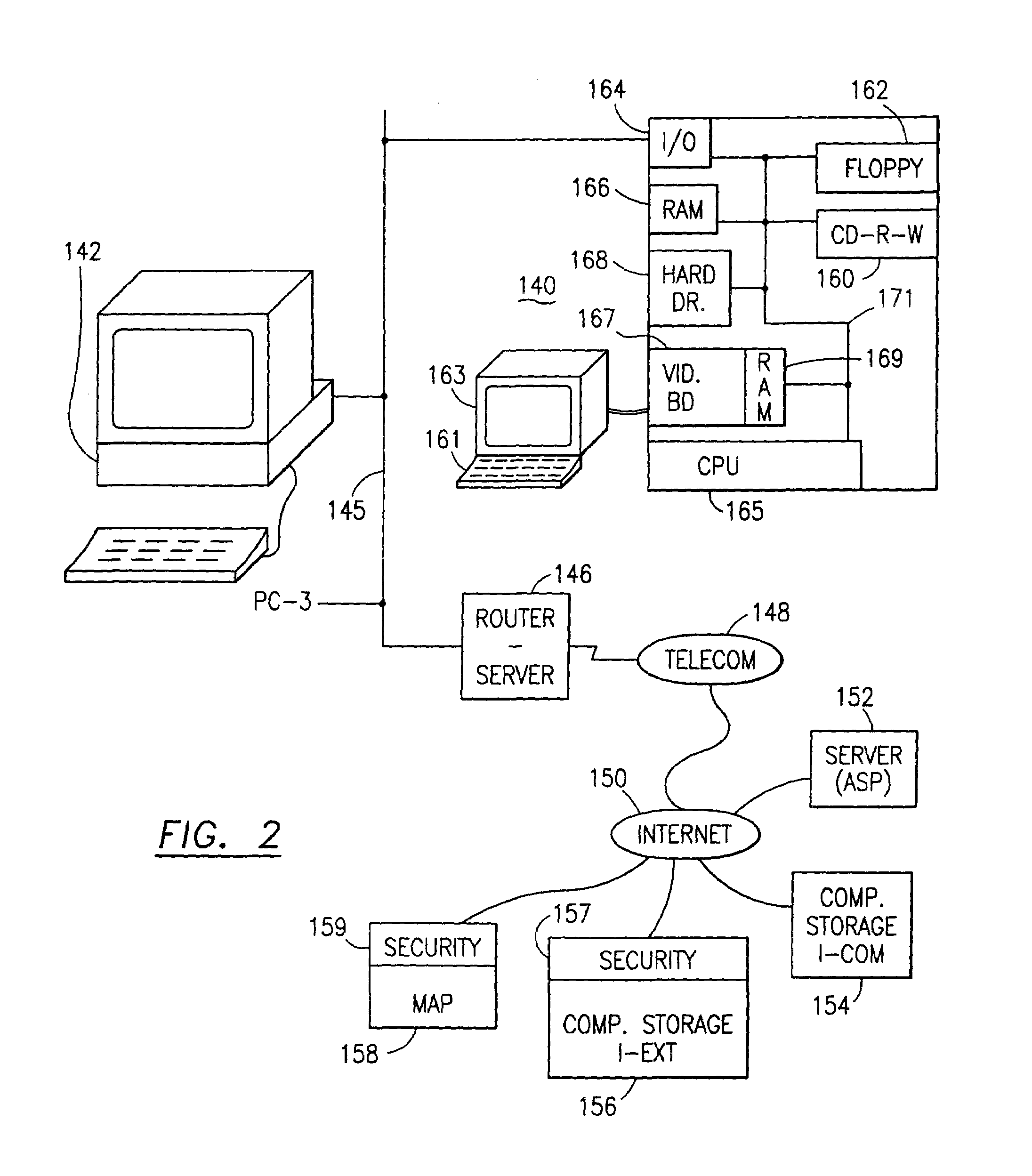
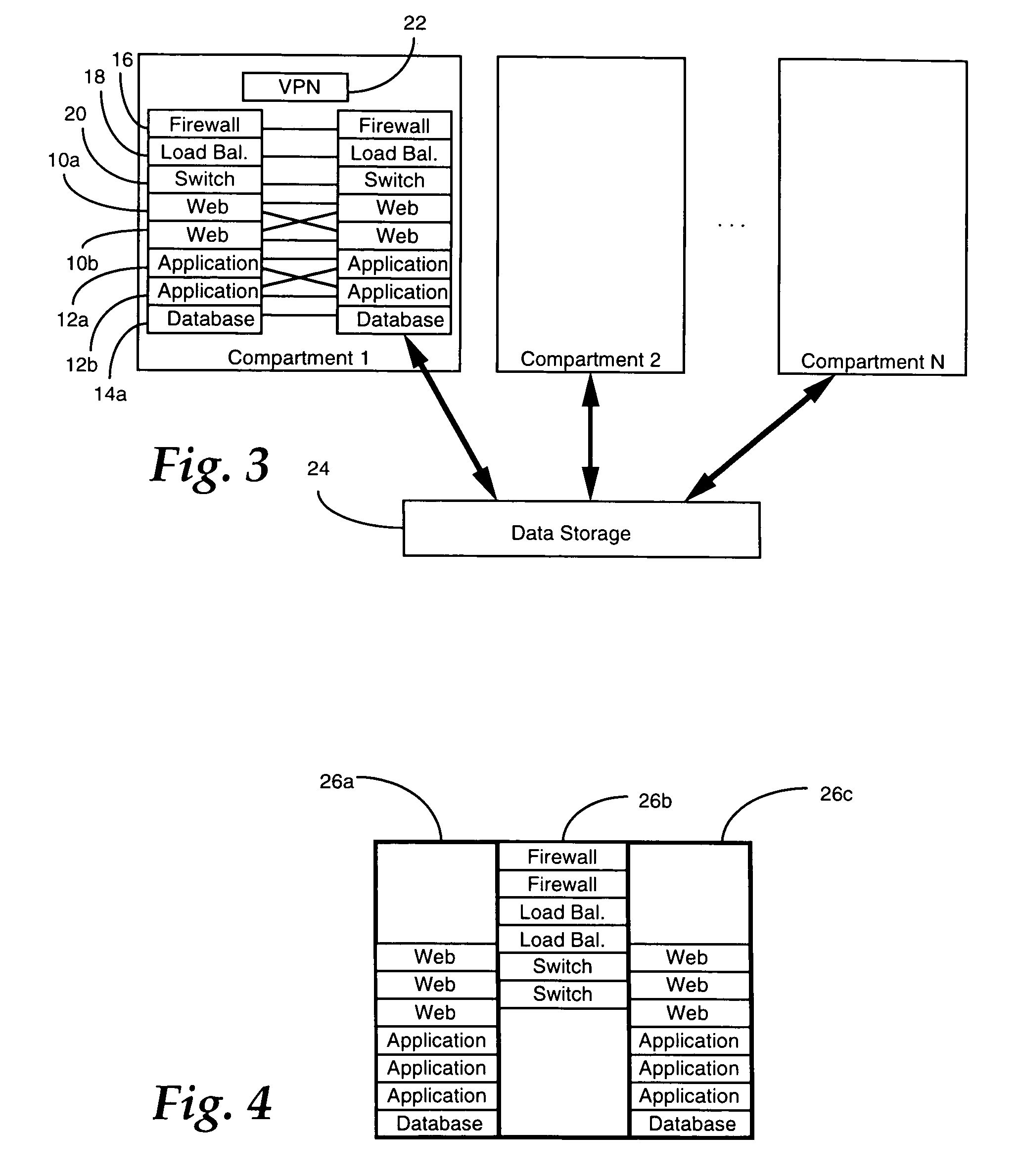
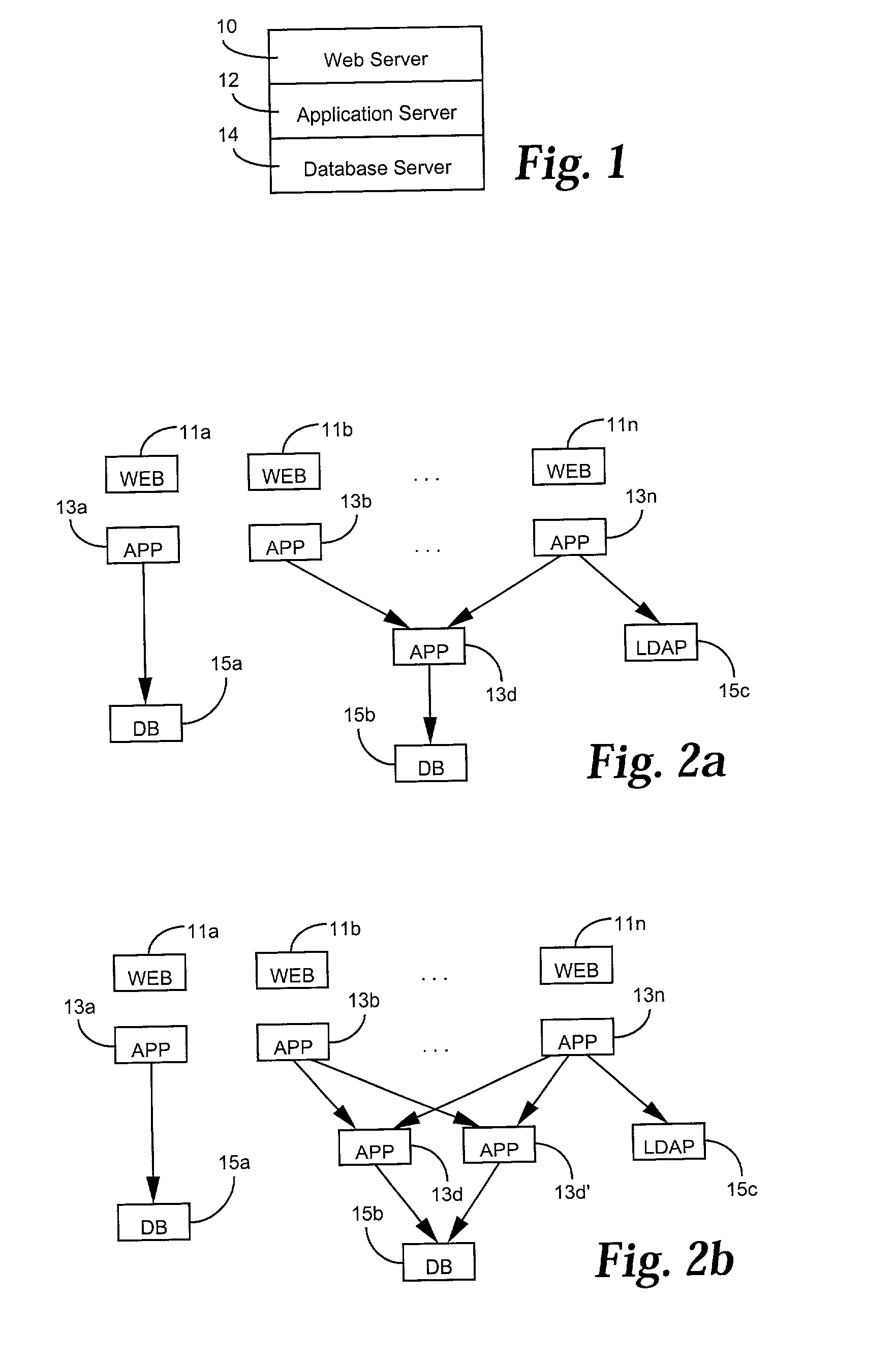
Data security system and method responsive to electronic attacks
ActiveUS7146644B2Ease overhead performanceHigh overhead performanceMemory loss protectionMultiple keys/algorithms usageInformation processingSelf adaptive
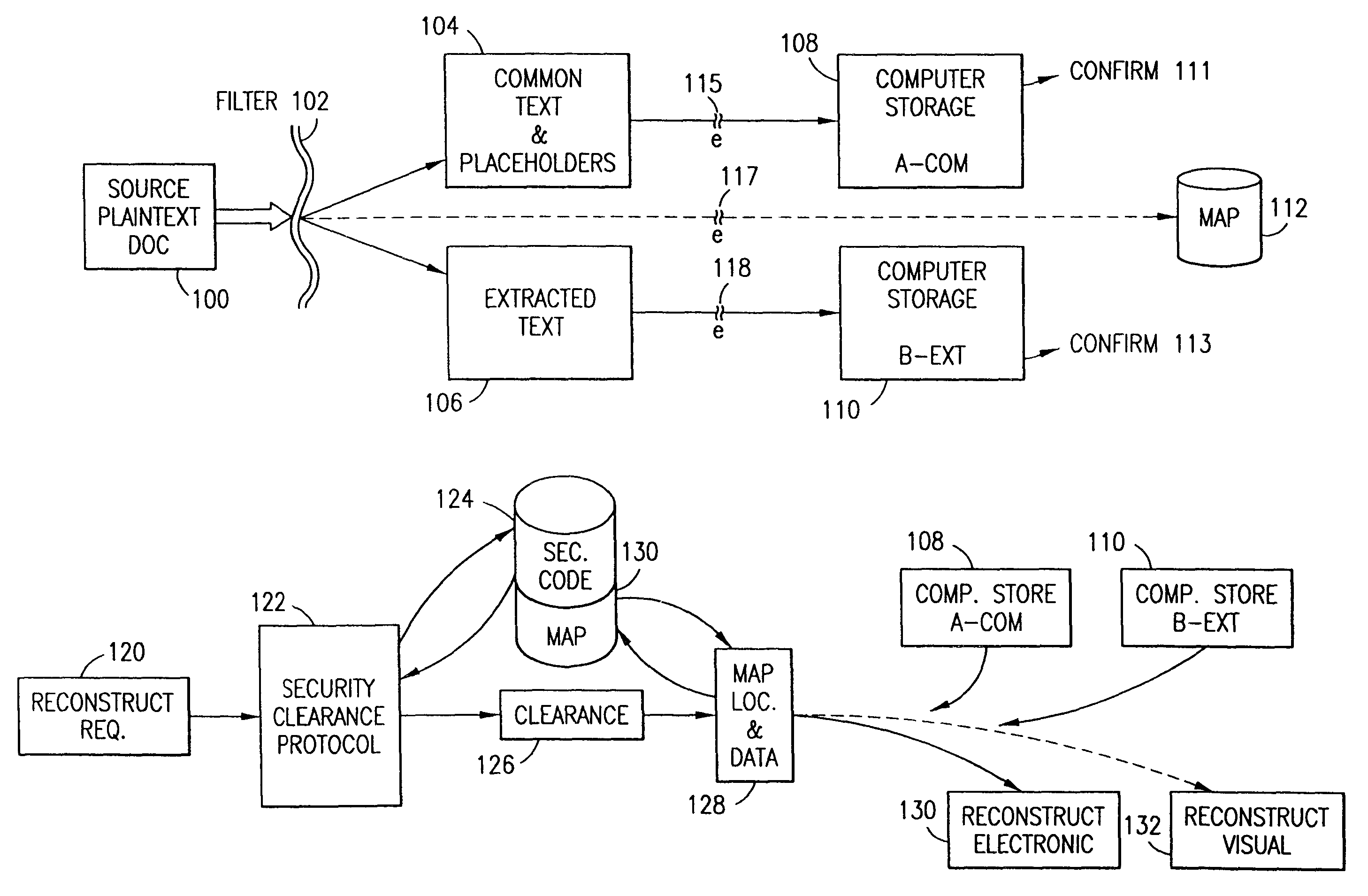
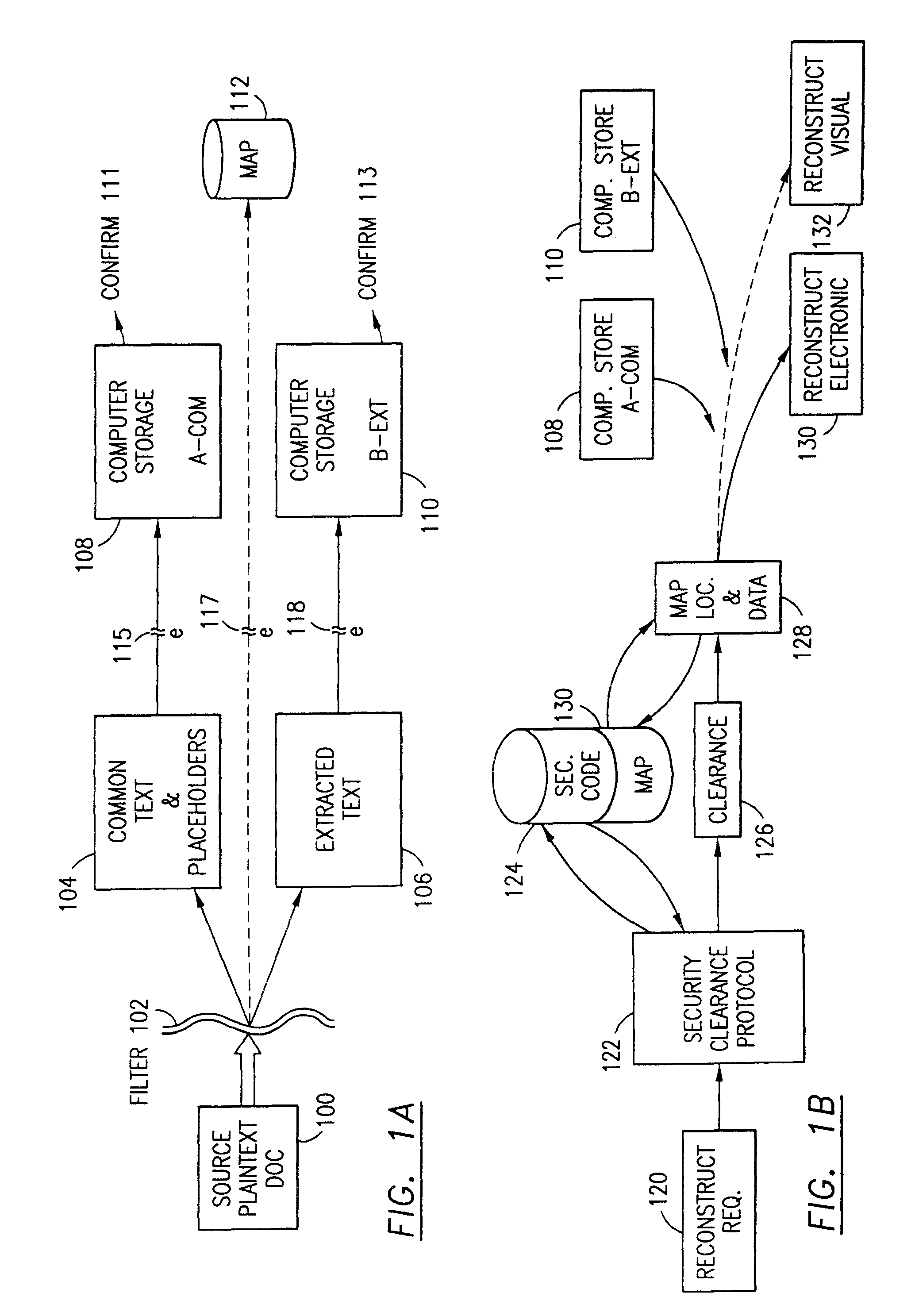
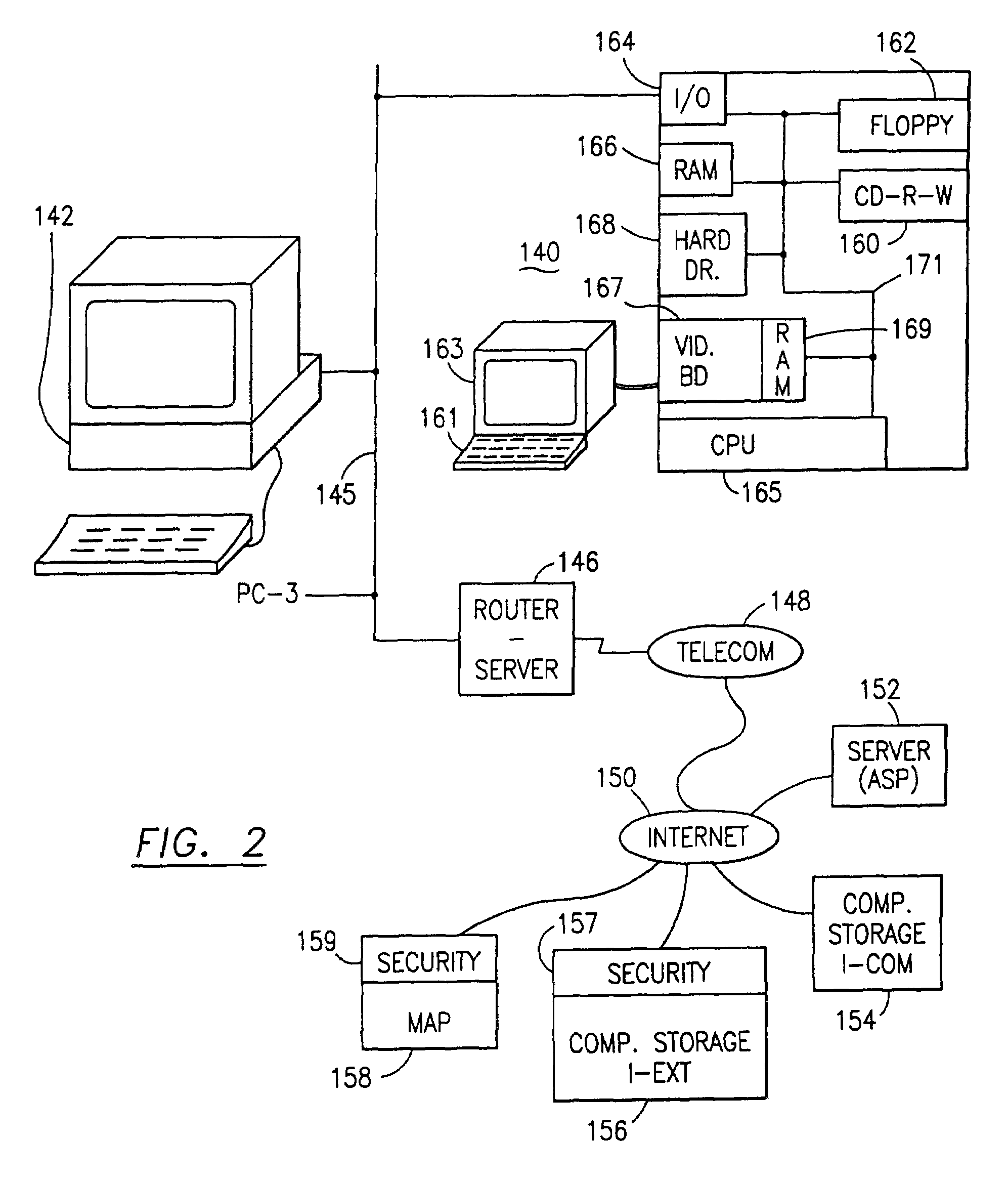
An adaptive method, system and program for securing data against a plurality of electronic and environmental events directed at computers utilizes a hacking monitor which generates attack warnings (such as a hacking warning) dependent upon the severity of the attack. Based upon these warnings, data is filtered to extract security sensitive words etc. and the extract and remainder data (if necessary) is stored in assigned memory. Full or partial reconstruction is permitted, manually or automatically, with a security clearance. Encryption is typically used dependent upon the warning. The information processing system includes a filter which is adjusted based upon the degree of attack warning to extract security sensitive words. A storage system stores extracted data and remainder data (if necessary) based upon the level of the warning and a compiler is used to reconstruct the data in the presence of the appropriate security clearance level.
Owner:DIGITAL DOORS
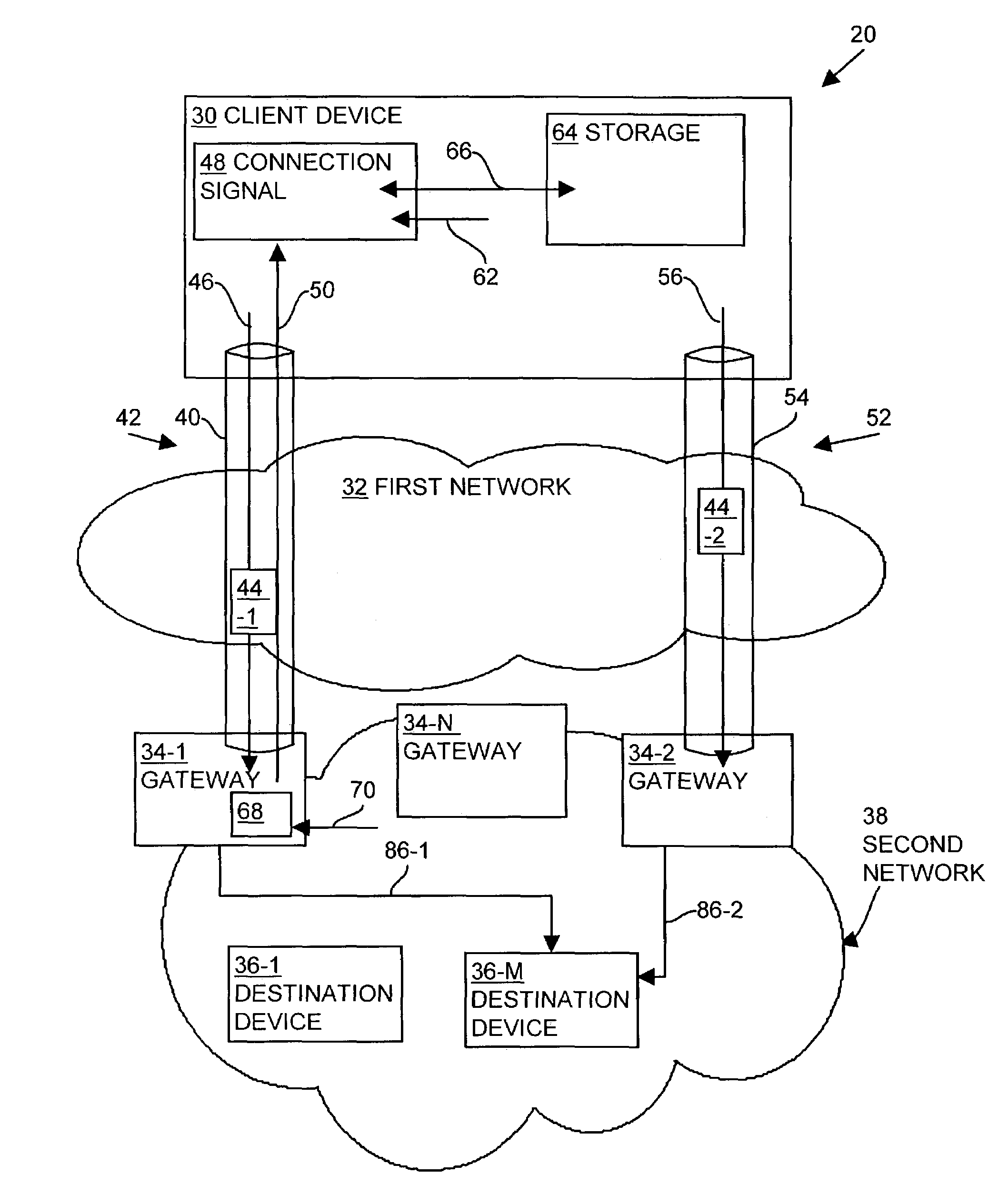
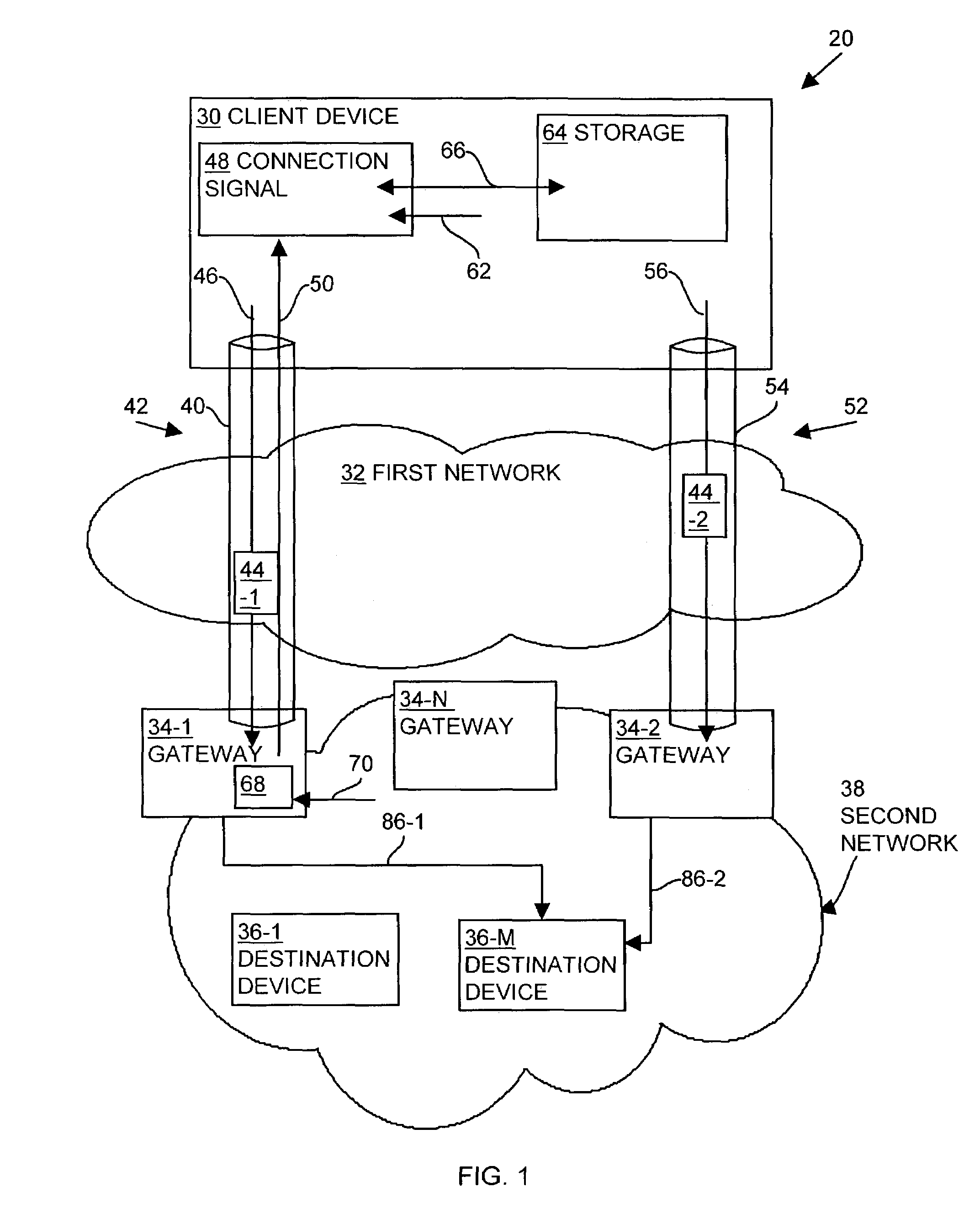
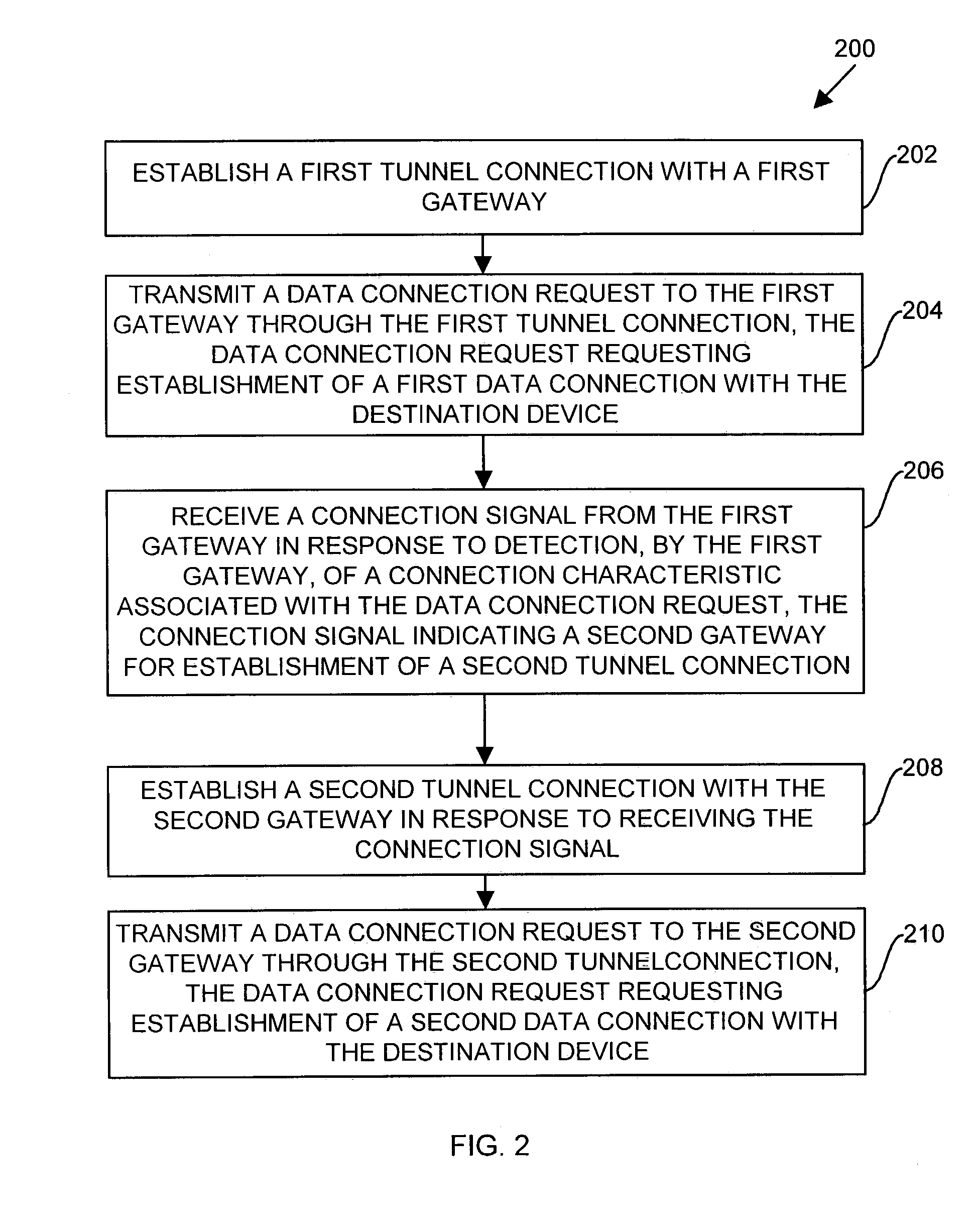
Methods and apparatus for establishing a computerized device tunnel connection
InactiveUS7673048B1Minimize bandwidth utilizationIncrease costError preventionTransmission systemsData connectionTelecommunications
A client device establishes a first tunnel connection or tunnel, through a public network, with a first gateway of a private network and establishes, through the tunnel connection, a data connection with a destination device within the private network. The first gateway monitors or analyzes the geographic locations of the gateways associated with the private network relative to geographic location of the destination device associated with the data connection. Based upon such the monitoring, the first gateway transmits information to the client device relating to establishment of a second tunnel connection or tunnel with a second gateway of the private network. The client device establishes the second tunnel connection with the second gateway and establishes a data connection with the destination device through the second gateway. By establishing the second tunnel connection with the second gateway, the client device utilizes the bandwidth of the public network to exchange data with the destination device, thereby decreasing data transmission costs to the private network and decreasing private network latency.
Owner:CISCO TECH INC
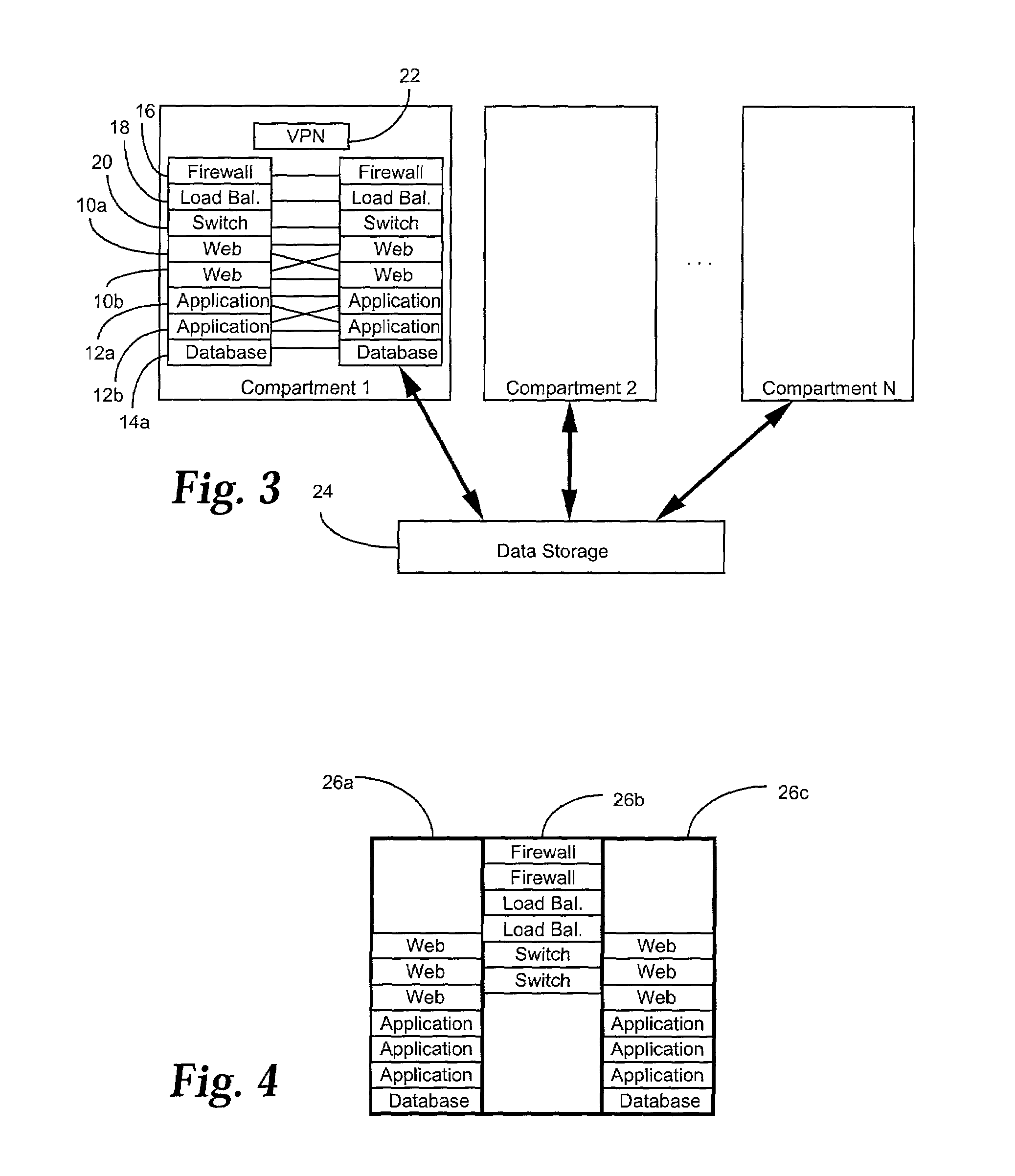
Automated provisioning framework for internet site servers
InactiveUS7124289B1Minimize security riskRepeatability is assuredData processing applicationsDigital computer detailsAuto-configurationComputer hardware
A framework for automatically provisioning computing devices includes a central database system and a central file system. Information stored in the database comprises a model of the individual devices, as well as the interconnections of the devices. The central file system stores the software components to be installed on the devices. When provisioning is carried out, the database sends commands to agents located on each device which cause them to retrieve and install the software components from the file system, and to configure the components according to the stored model.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
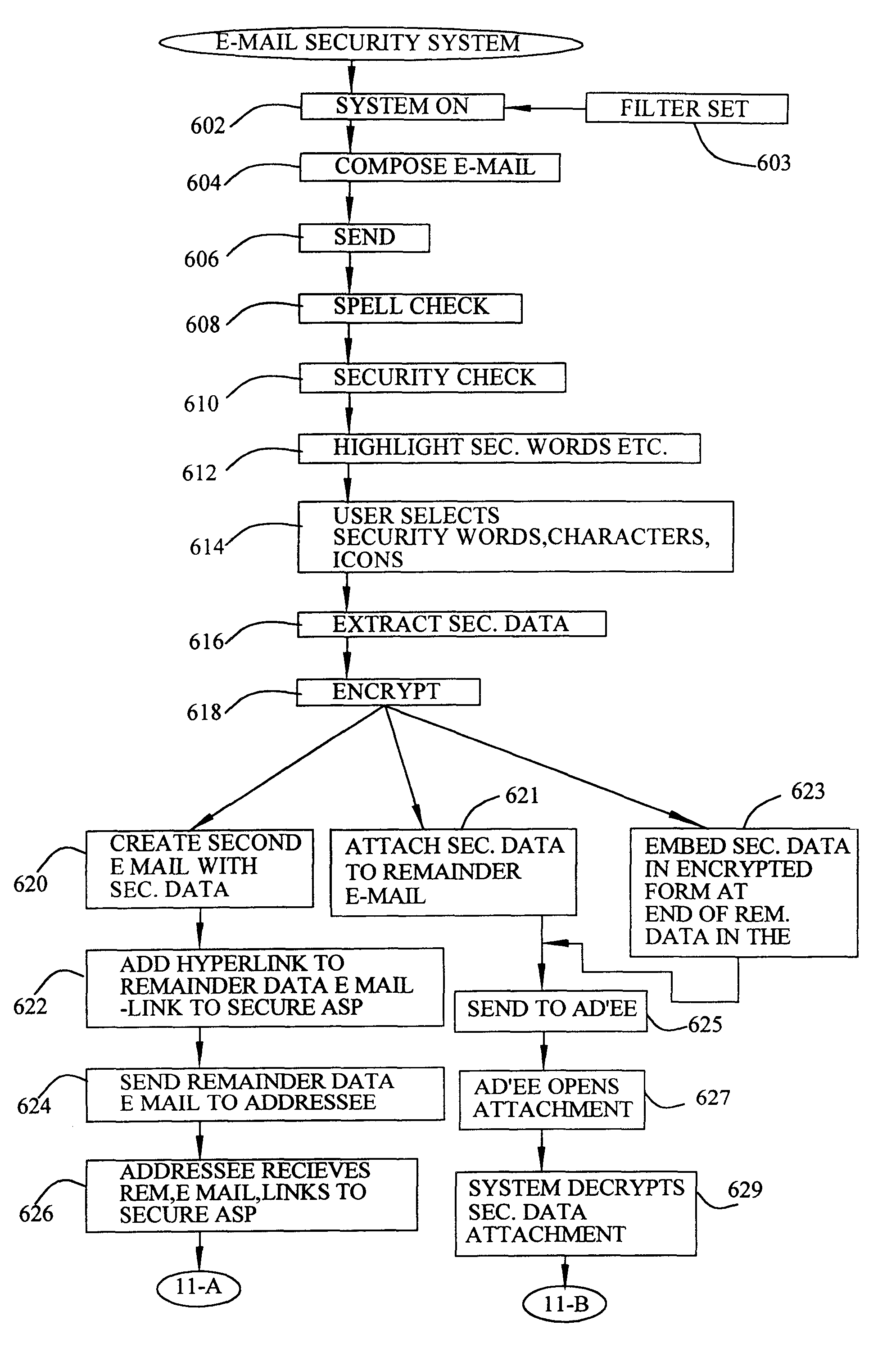
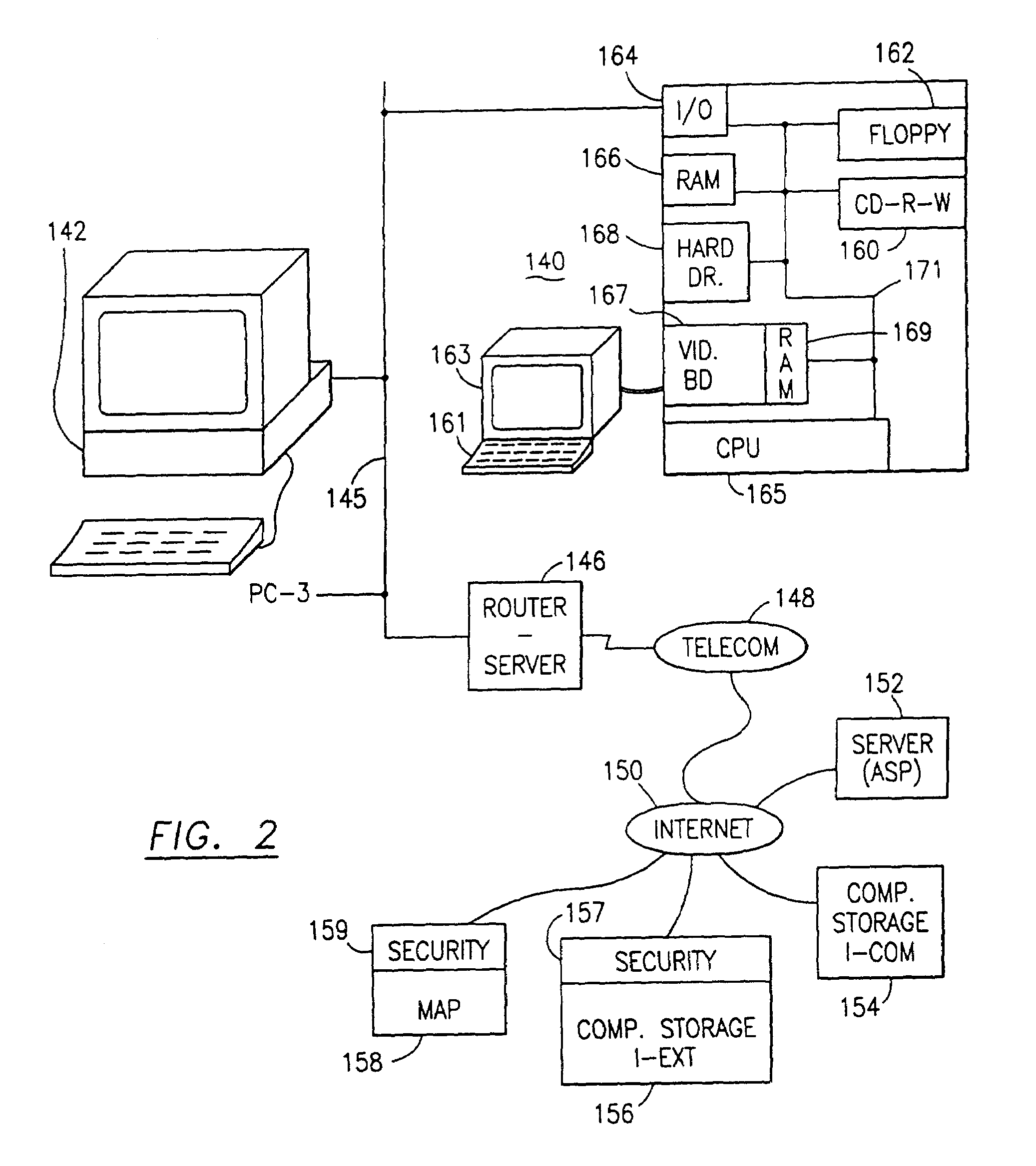
Data security system and method adjunct to e-mail, browser or telecom program
InactiveUS7191252B2Ease overhead performanceHigh overhead performanceDigital data processing detailsUser identity/authority verificationCredit cardInternet privacy
Data security for e-mail or browser-input data operates on identified security sensitive words, characters or icons which are extracted leaving remainder data. Extracted data, in one system, is stored in a remote, extract store in a distributed computer system. Other methods attach an encrypted version of the extract to the email. The browser system operates with an extract store. Remainder data is sent to the addressee or designated web server. The addressee is permitted to retrieve the extracted data from said extract store only in the presence of a security clearance and hence, reconstruct the source e-mail or browser-input data with the extract data. In other systems, the addressee reconstructs the email by decryption and integration. Parsing rather than identifying critical words is an option. The browser method extracts data, facilitates the storage in an extract store, forwards the remainder data to a targeted destination. The financial data or credit card scrubber may use a pop-up window to alert the user to enable the system.
Owner:DIGITAL DOORS
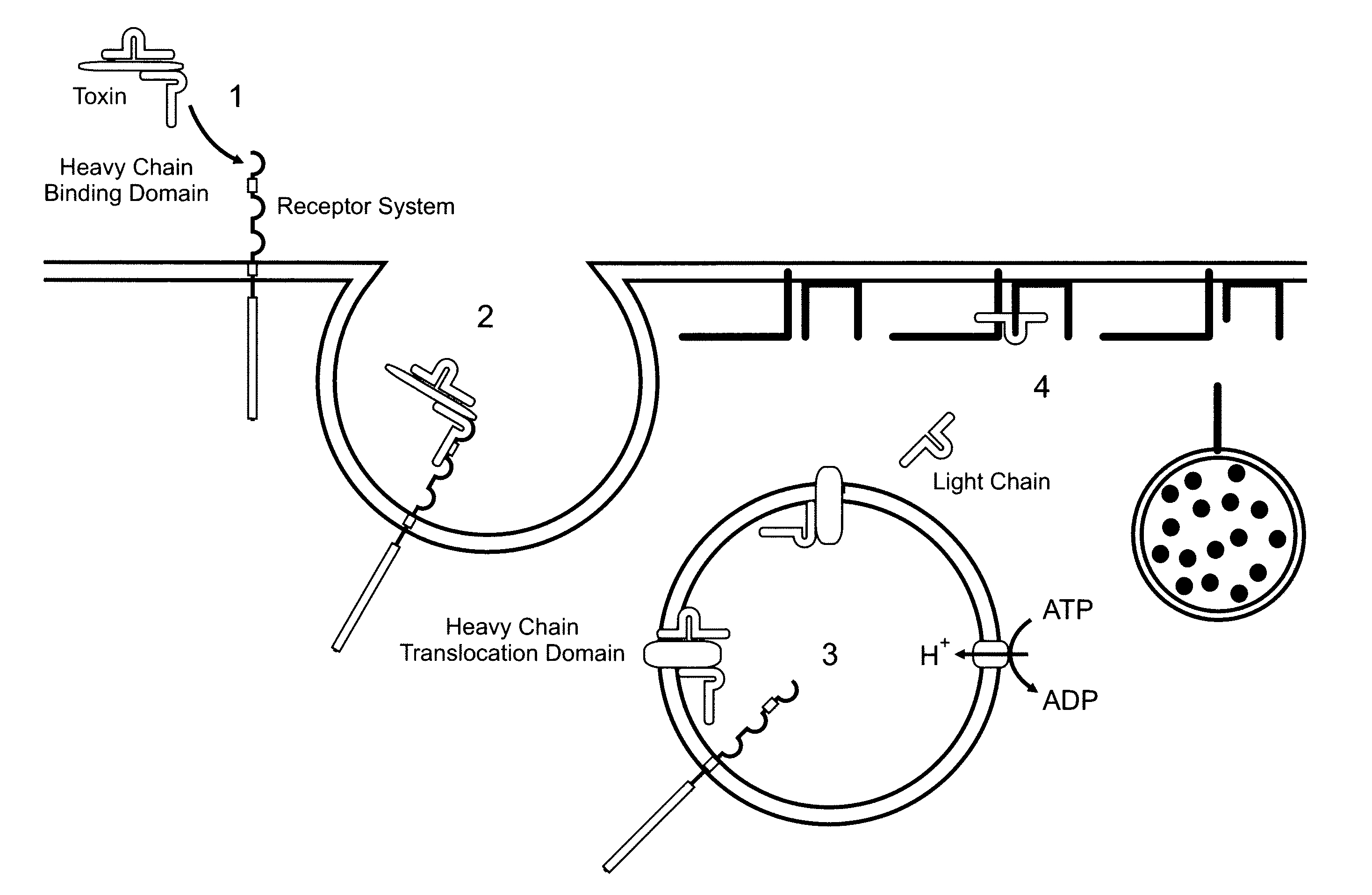
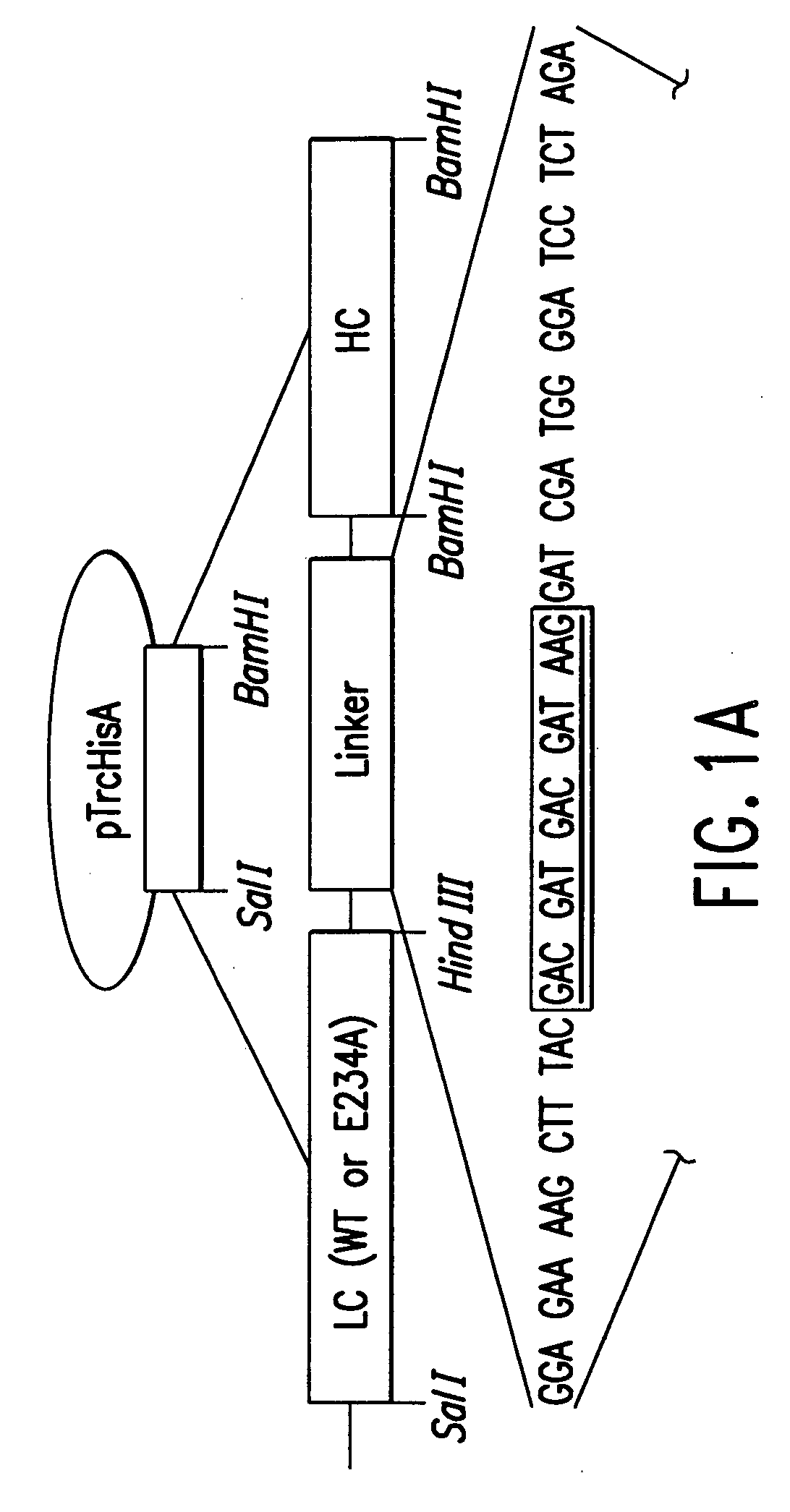
Activatable recombinant neurotoxins
InactiveUS7132259B1Minimize security riskEnhanced efficiency and rateSenses disorderNervous disorderToxinNeurotoxin
The invention provides, in part, compositions comprising activatable recombinant neurotoxins and polypeptides derived therefrom. The invention also provides, in part, nucleic acid molecules encoding such polypeptides, and methods of making such polypeptides and nucleic acid molecules.
Owner:ALLERGAN INC
Automated provisioning of computing networks using a network database model
InactiveUS7131123B2Minimize security riskRepeatability is assuredProgram loading/initiatingMemory systemsAuto-configurationFile system
A framework for automatically provisioning computing devices includes a central database system and a central file system. Information stored in the database comprises a model of the individual devices, as well as the interconnections of the devices. The central file system stores the software components to be installed on the devices. When provisioning is carried out, the database sends commands to agents located on each device which cause them to retrieve and install the software components from the file system, and to configure the components according to the stored model.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Activatable clostridial toxins
InactiveUS20080032931A1Minimize security riskEnhanced efficiency and rateHydrolasesPeptide/protein ingredientsClostridial toxinSaxitoxin
Owner:ALLERGAN INC
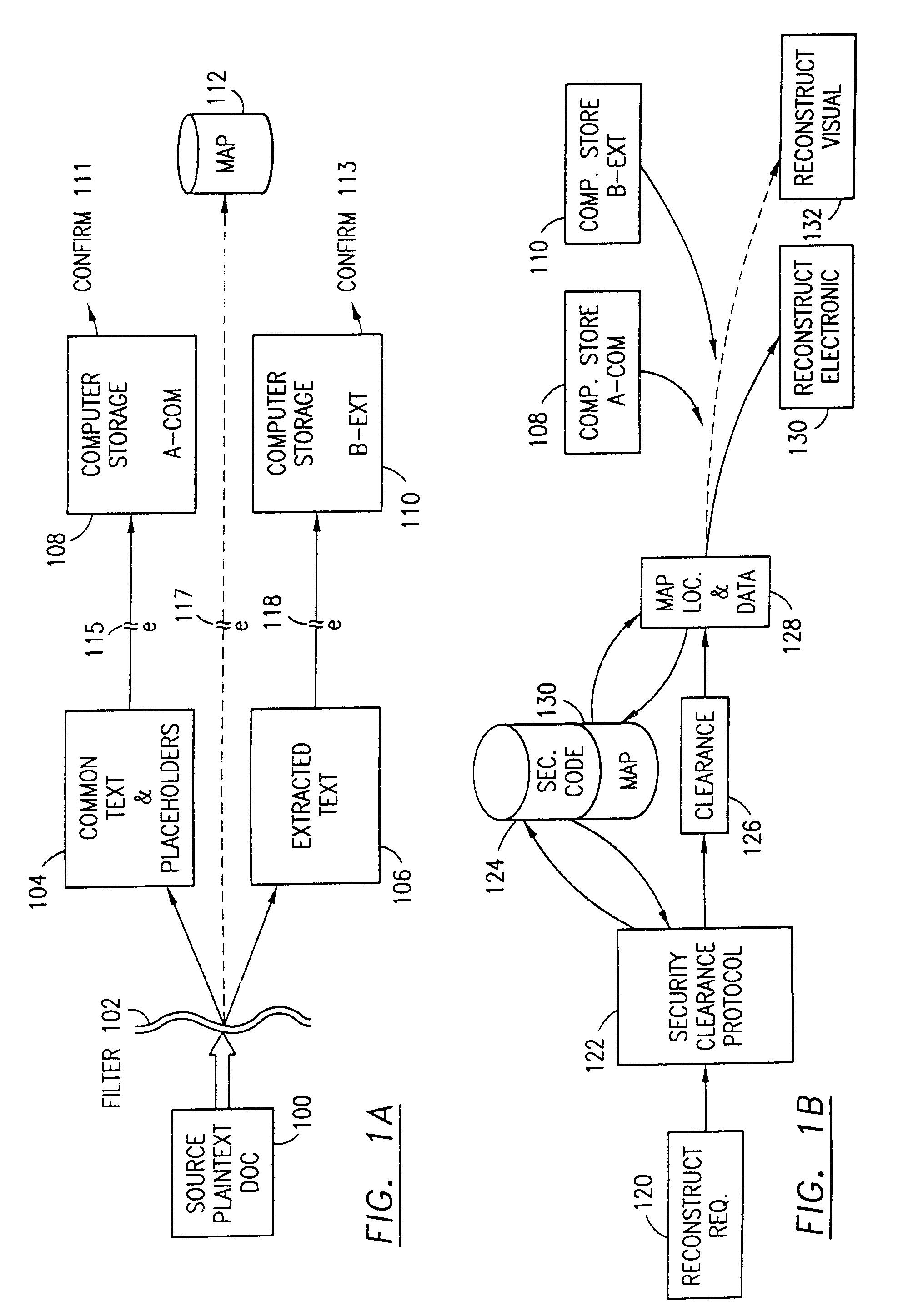
Data security system and method with parsing and dispersion techniques
ActiveUS7349987B2Ease overhead performanceHigh overhead performanceDigital data processing detailsUser identity/authority verificationOriginal dataInternet privacy
A data security having parsing and dispersion aspects enables the user to parse, disperse and reconstruct the original, plain text data or data object, thereby enabling secure storage of the data. The original data may be maintained in its original state, encrypted or it may be destroyed. For example, financial data maintained by an institute, stored as is customary, be parsed with an algorithm, the parsed segments dispersed off-site (that is, separated and stored in extract and remainder stores or computer memories) and away from the financial institute, and, upon appropriate security clearance, the dispersed data can be reconstructed to duplicate the data. Large distribution of parsed data is contemplated by the system. The original data remains stable, operable and immediately useful in its customary storage location (or alternatively destroyed). The secured dispersed data is a back-up of the original data.
Owner:DIGITAL DOORS
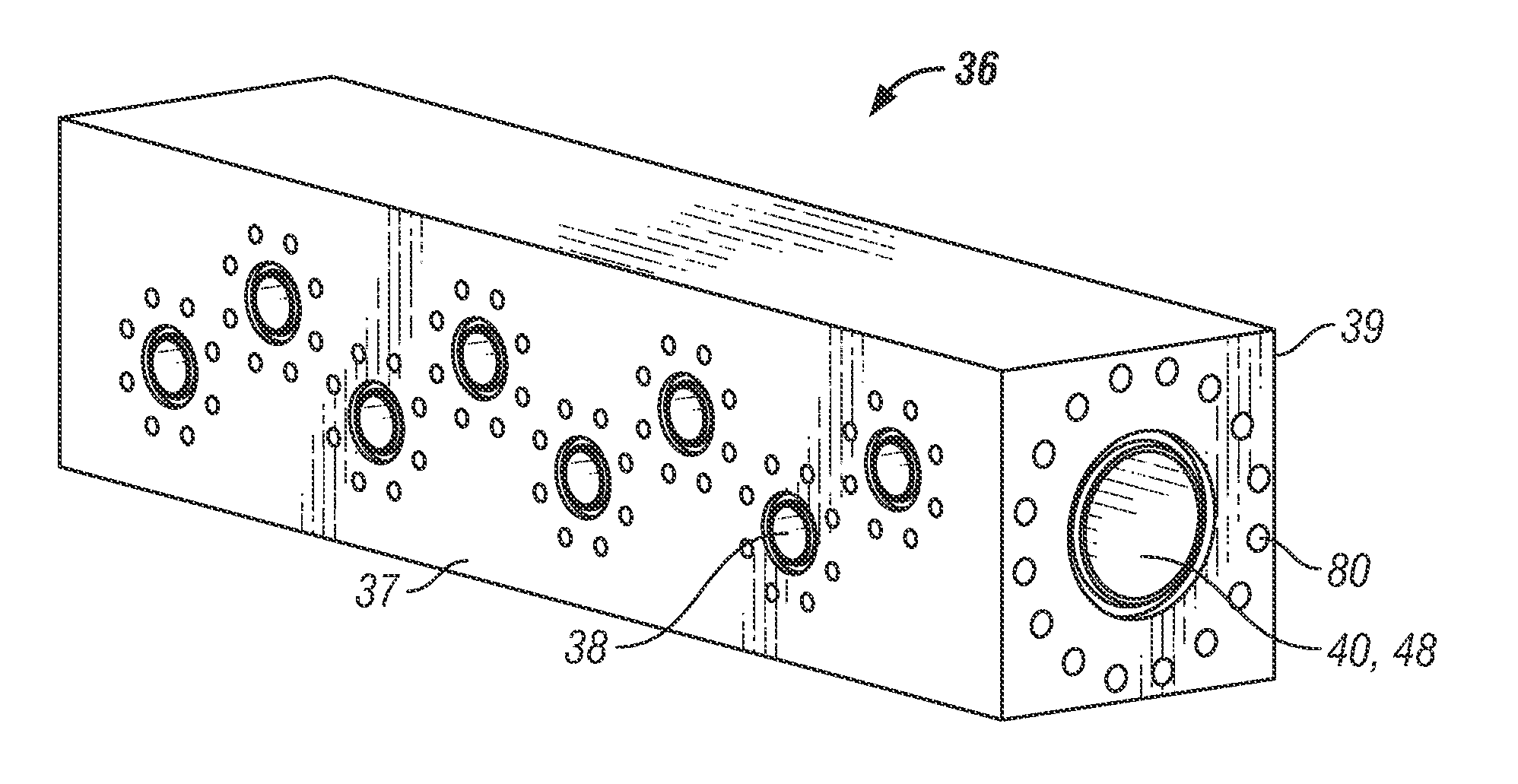
Collection block with multi-directional flow inlets in oilfield applications
The disclosure provides a collection block that aggregates multiple incoming flow lines and provides a consolidated outgoing flow path. The collection block can be remote from a given well that is being fractured to minimize safety risk in operations around the well. The collection block has dual capabilities of being connected to individual incoming flow lines as well as to manifold systems for distributing the out flowing fluids. The one or more inlets can be formed in the collection block at an offset to a centerline of a longitudinal bore through the collection block. In some to embodiments, frac trucks can connect along an extended connection zone that provides the fluids from the truck to the collection block.
Owner:T 3 PROPERTY HLDG
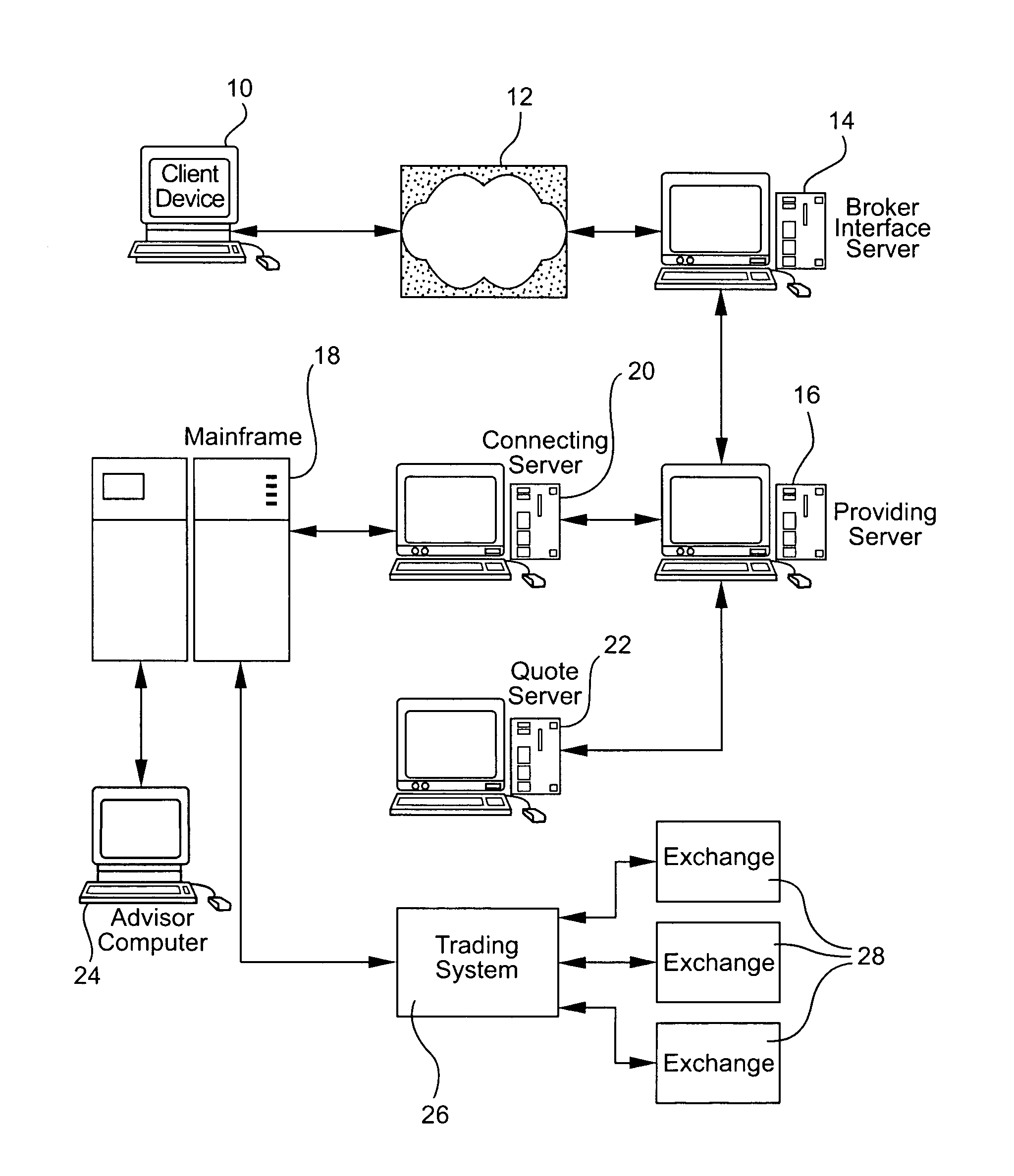
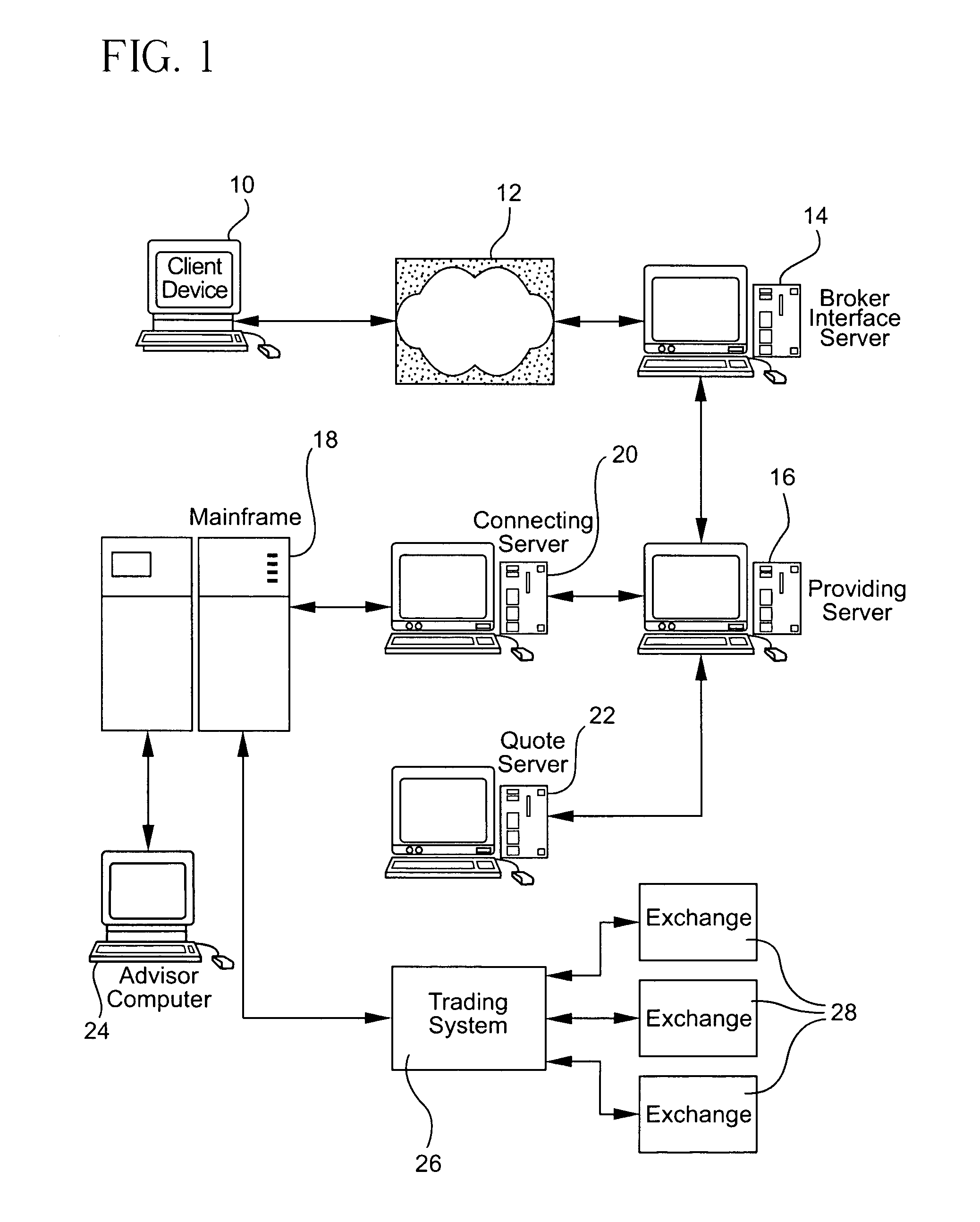
On-line trading system
A computer-based system for trading financial instruments alerts a computer operated by a financial advisor at points where a client interacts with the system. Specifically, in response to the client entering an order to trade a financial instrument, a first alert is transmitted in real-time to the financial advisor's computer including information pertaining to the trade. In the case of validation, in response to the first alert, the user of the financial advisor computer can, in real-time, take action regarding the validated trade prior to execution of the trade. On the other hand, in the case of non-validation, a second alert is transmitted to the financial advisor's computer, and the user of the financial advisor computer can, in real-time, again take action regarding the non-validated trade prior to execution of the trade.
Owner:UBS BUSINESS SOLUTIONS AG
Activatable clostridial toxins
InactiveUS20090018081A1Long duration of therapyOvercome resistanceHydrolasesPeptide/protein ingredientsClostridial toxinNucleic acid
Owner:ALLERGAN INC
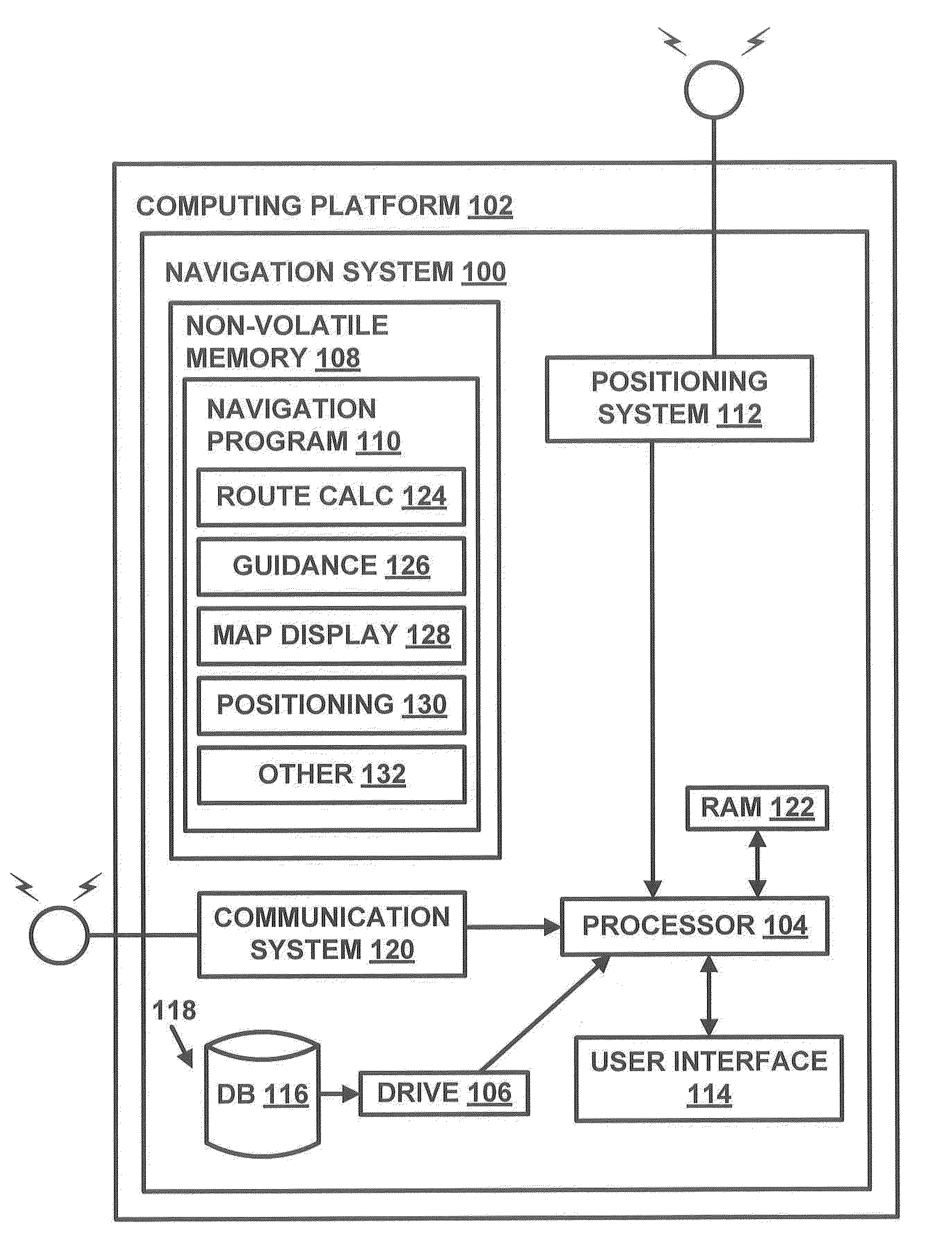
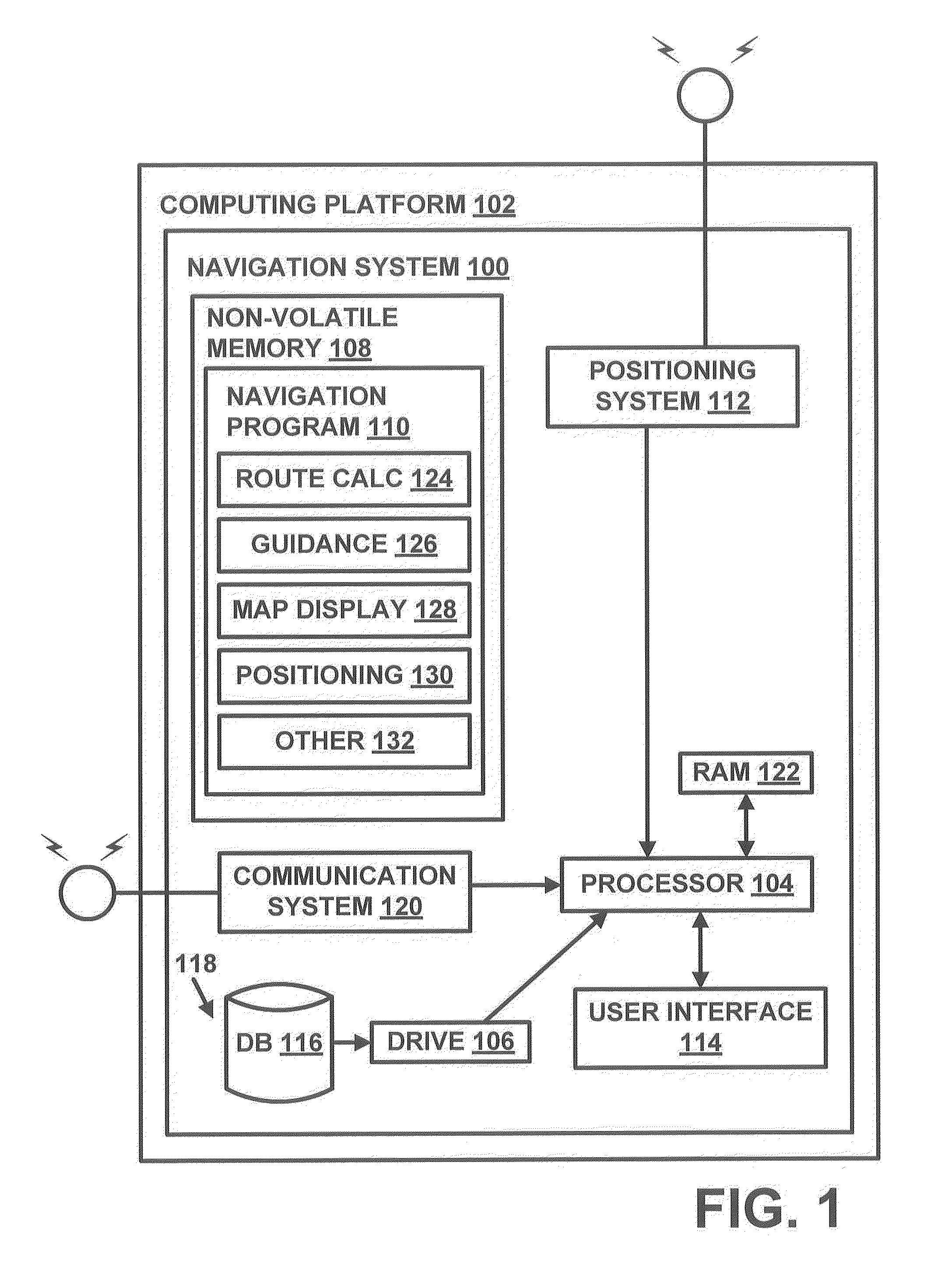
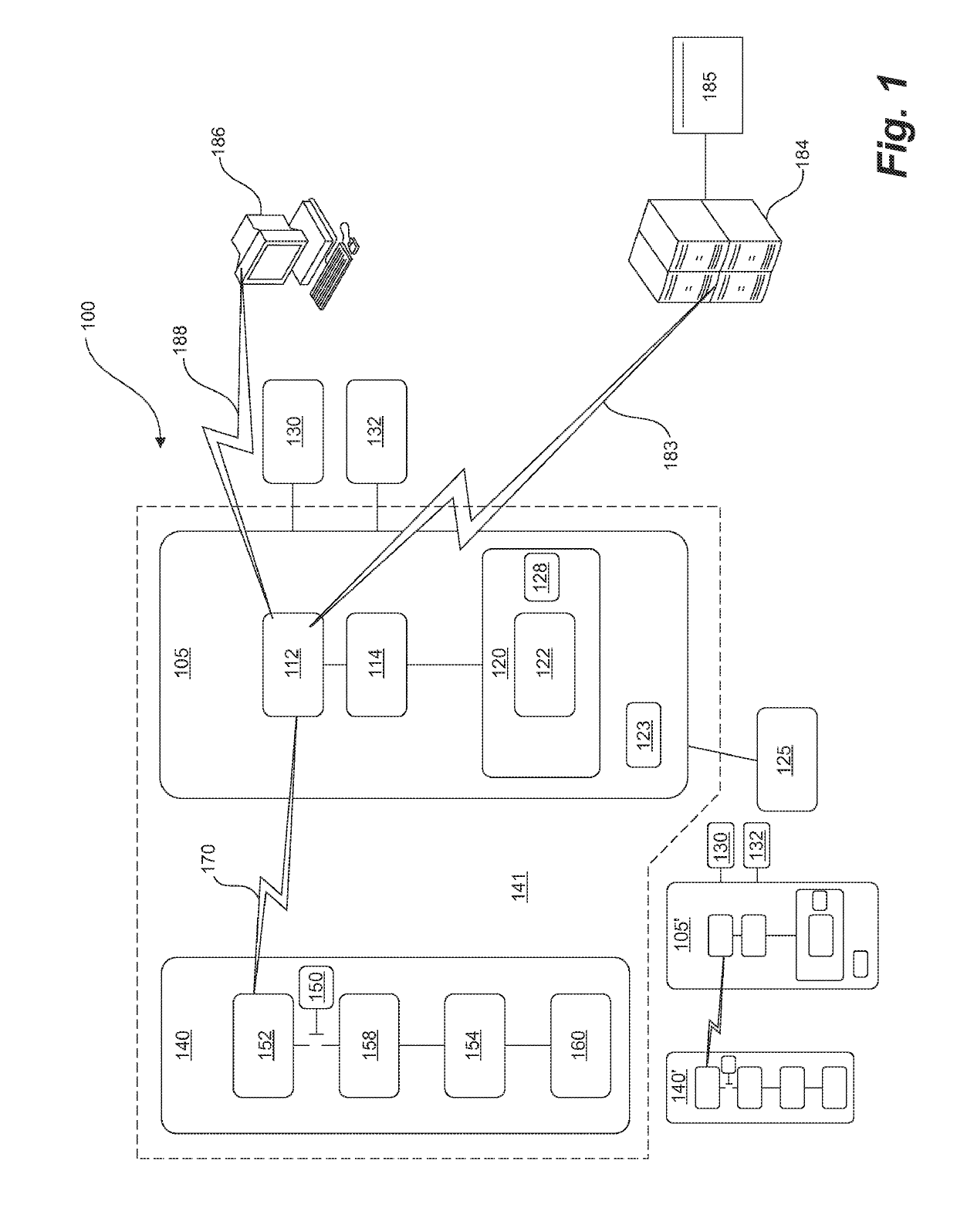
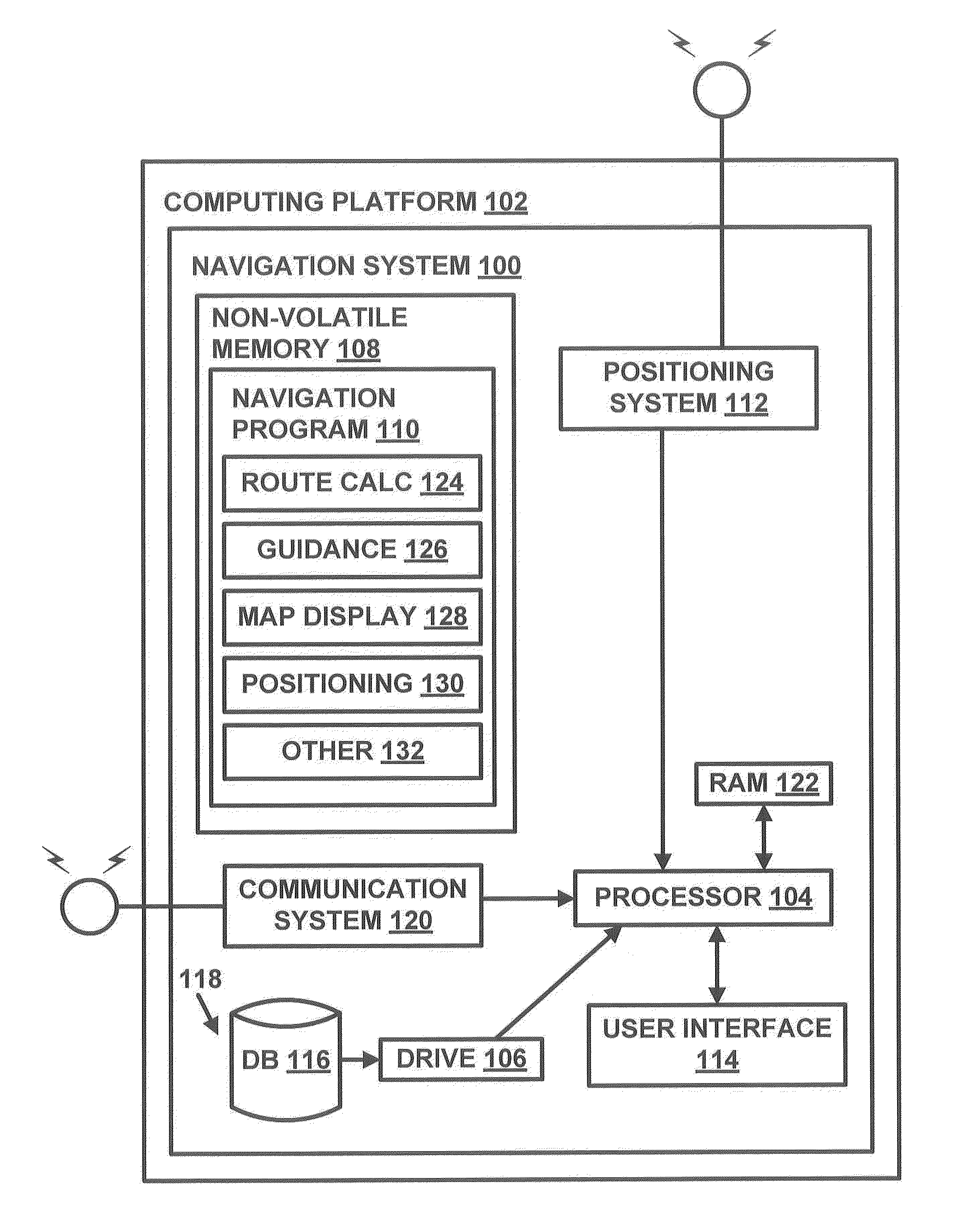
Method of operating a navigation system to provide a pedestrian route
ActiveUS20110246055A1Minimize safety costMinimizes safety costInstruments for road network navigationRoad vehicles traffic controlNavigation systemPedestrian
A computer implemented method of operating a navigation system to provide a pedestrian route is provided. The method comprises receiving a request for a route from an origin to a destination. The method evaluates a plurality of pedestrian paths by accessing data representing the pedestrian paths to determine a safety cost associated with including the pedestrian path in the route. The safety cost indicates a safety risk for the pedestrian. The method provides the route comprising the pedestrian paths that form a continuous navigable route between the origin and the destination that minimize the safety cost.
Owner:HERE GLOBAL BV
Activatable recombinant neurotoxins
InactiveUS20060099672A1Minimize security riskEnhanced efficiency and rateSenses disorderNervous disorderToxinNucleic acid
Owner:ALLERGAN INC
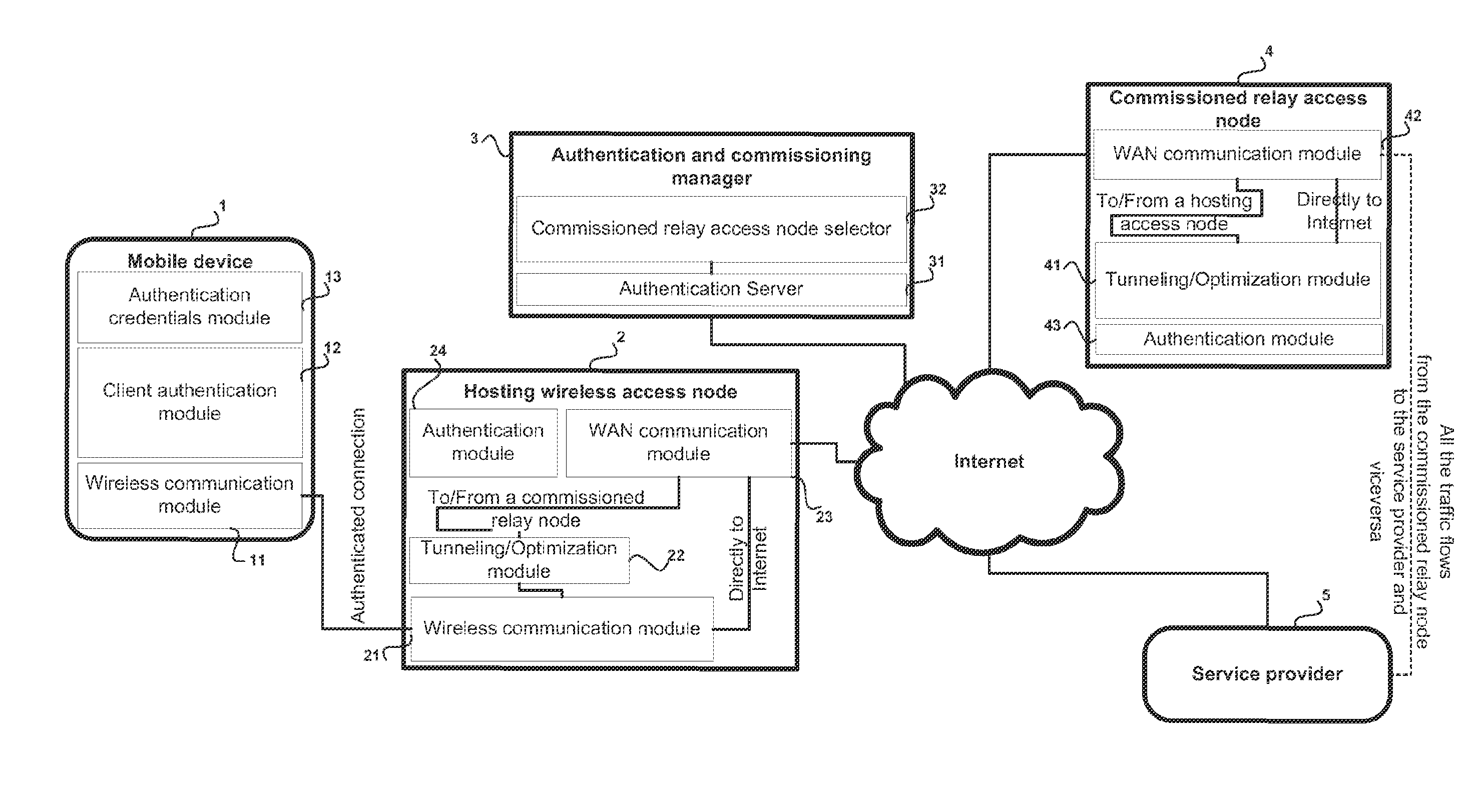
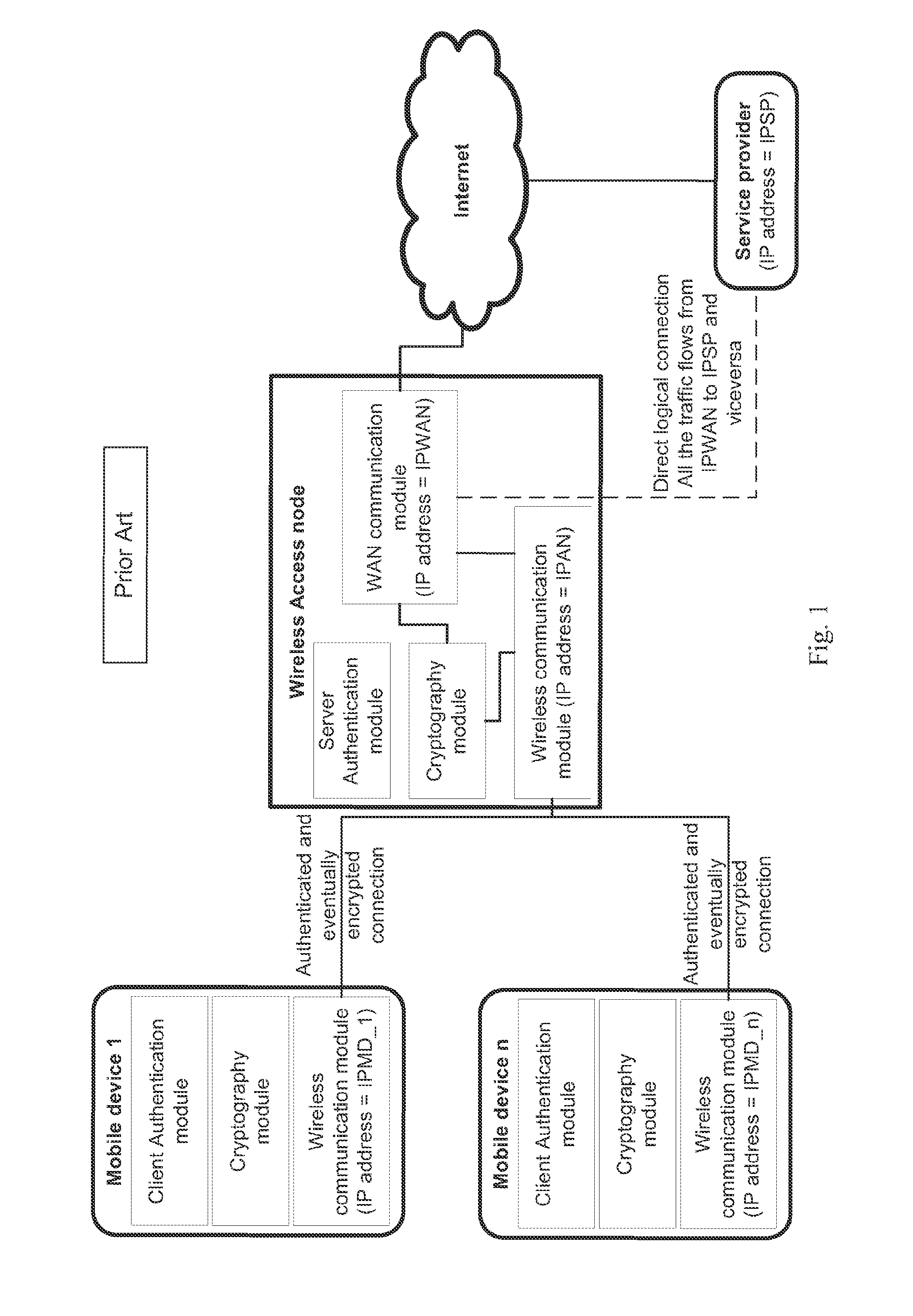
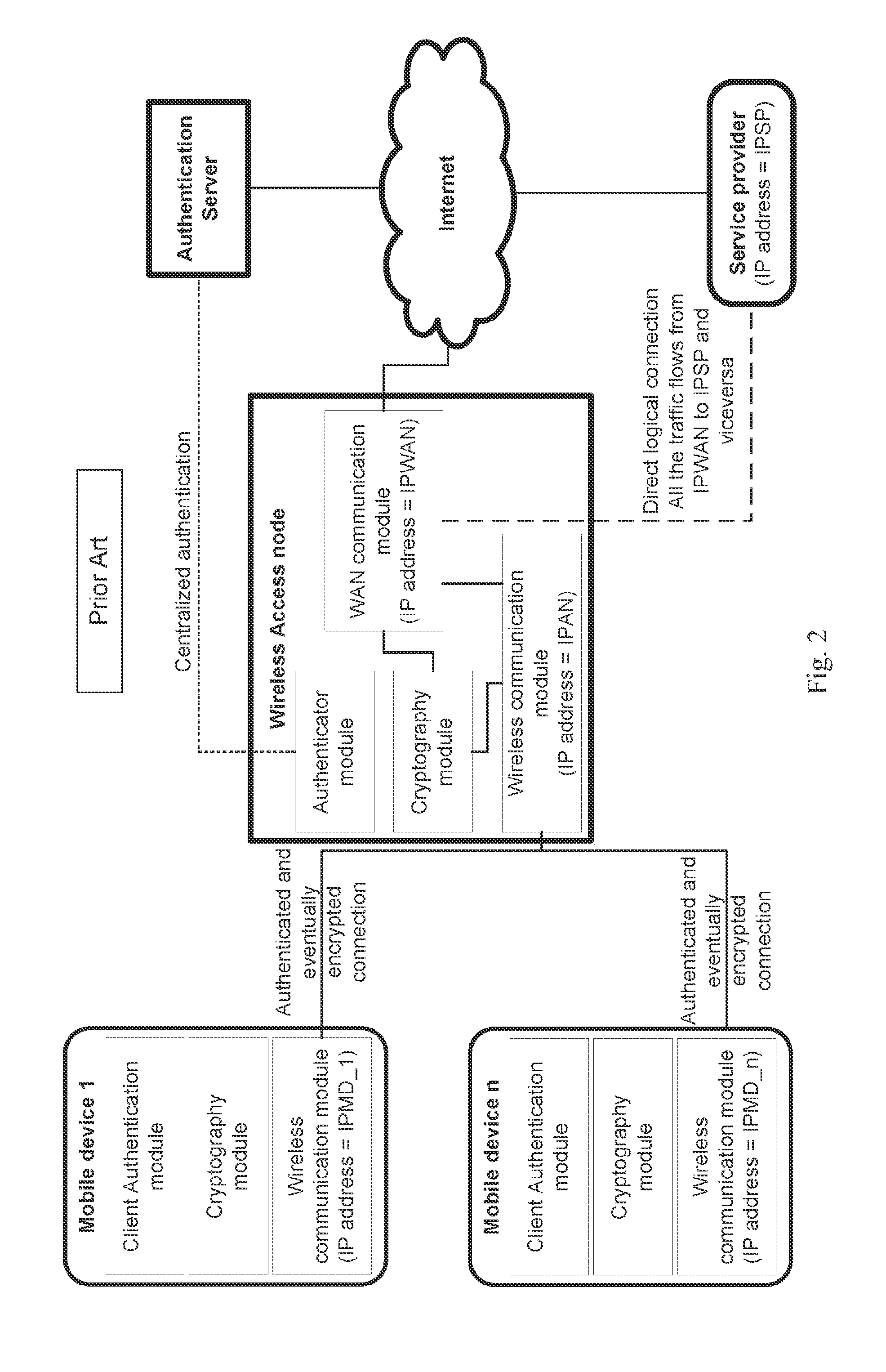
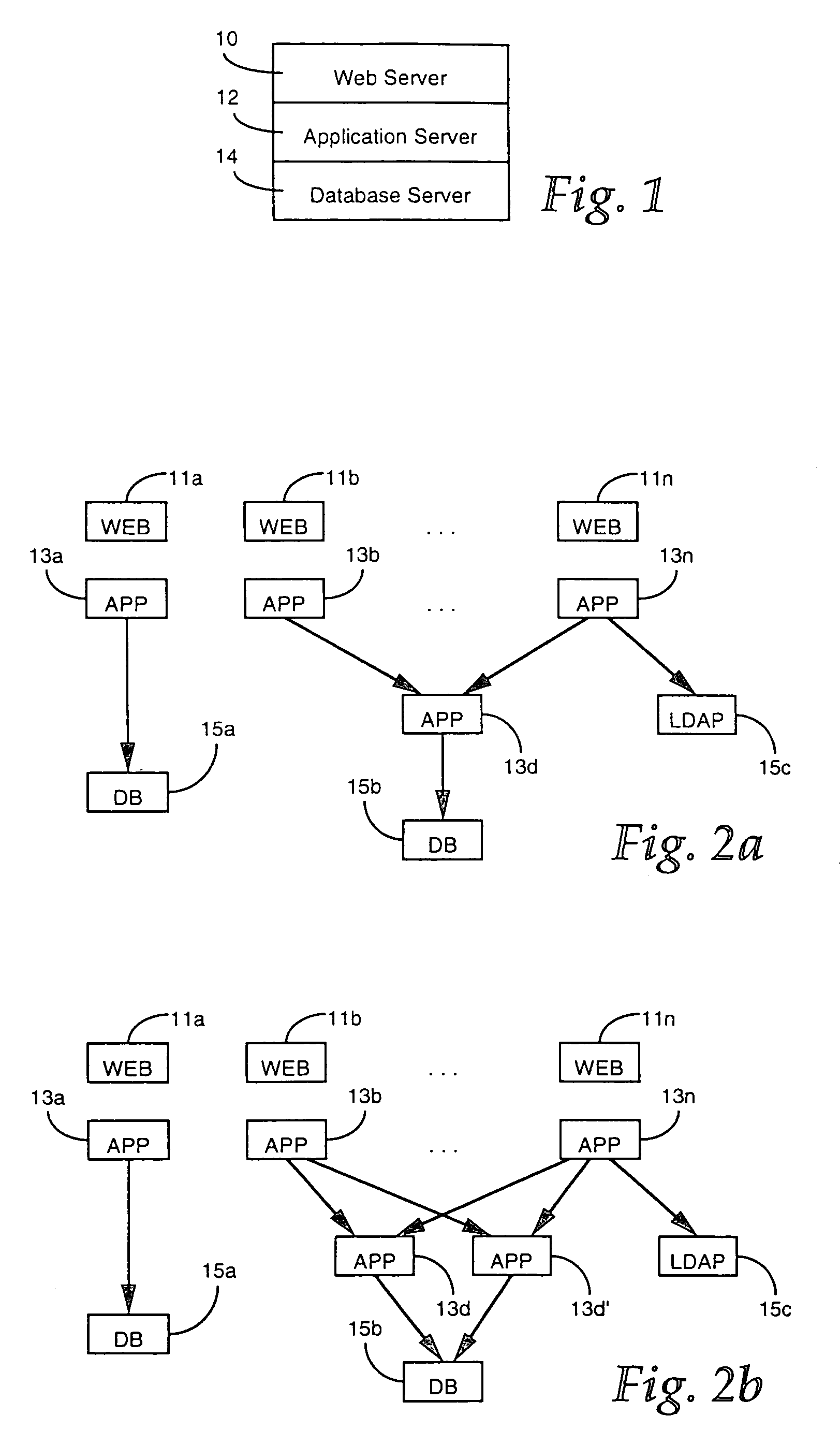
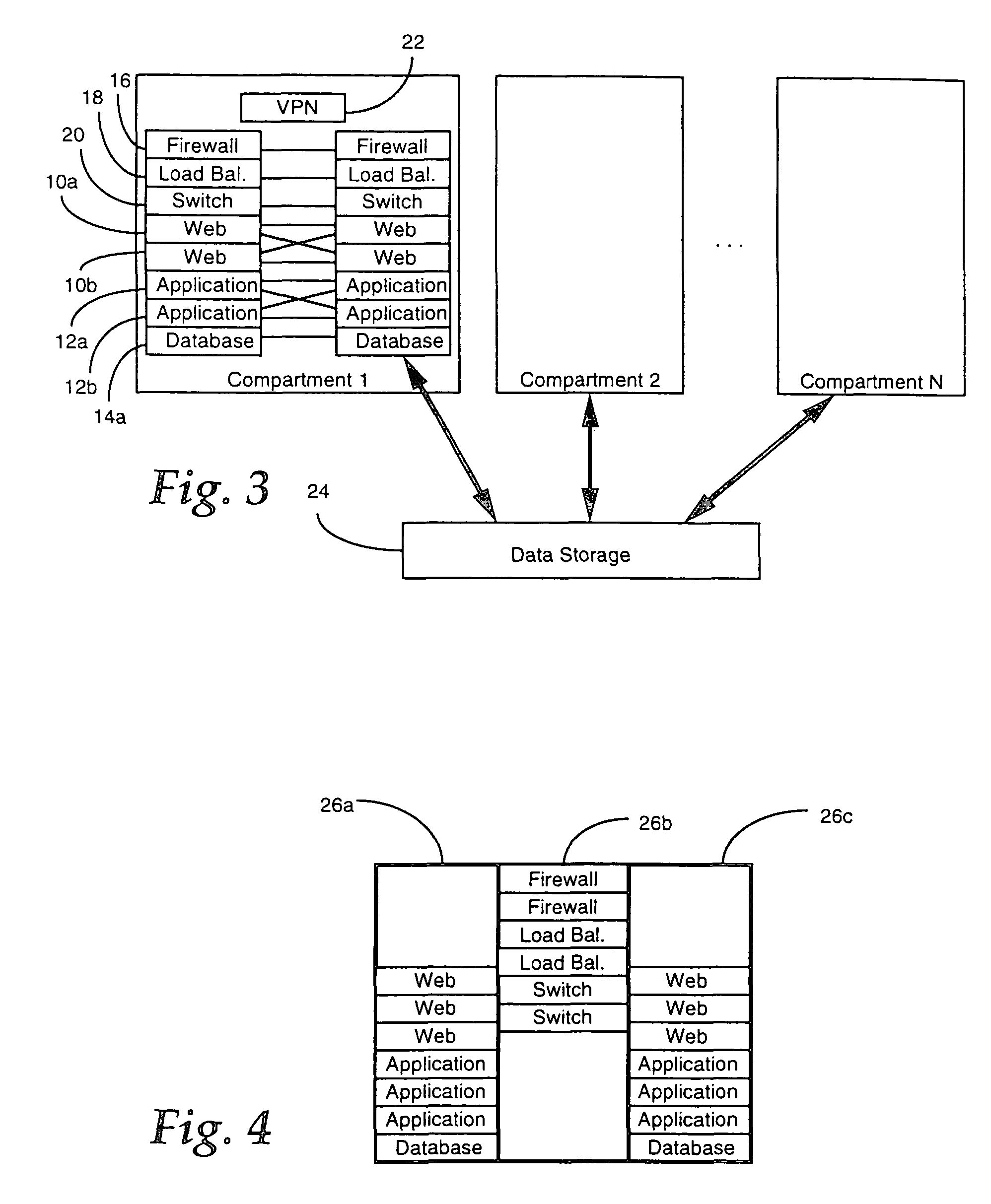
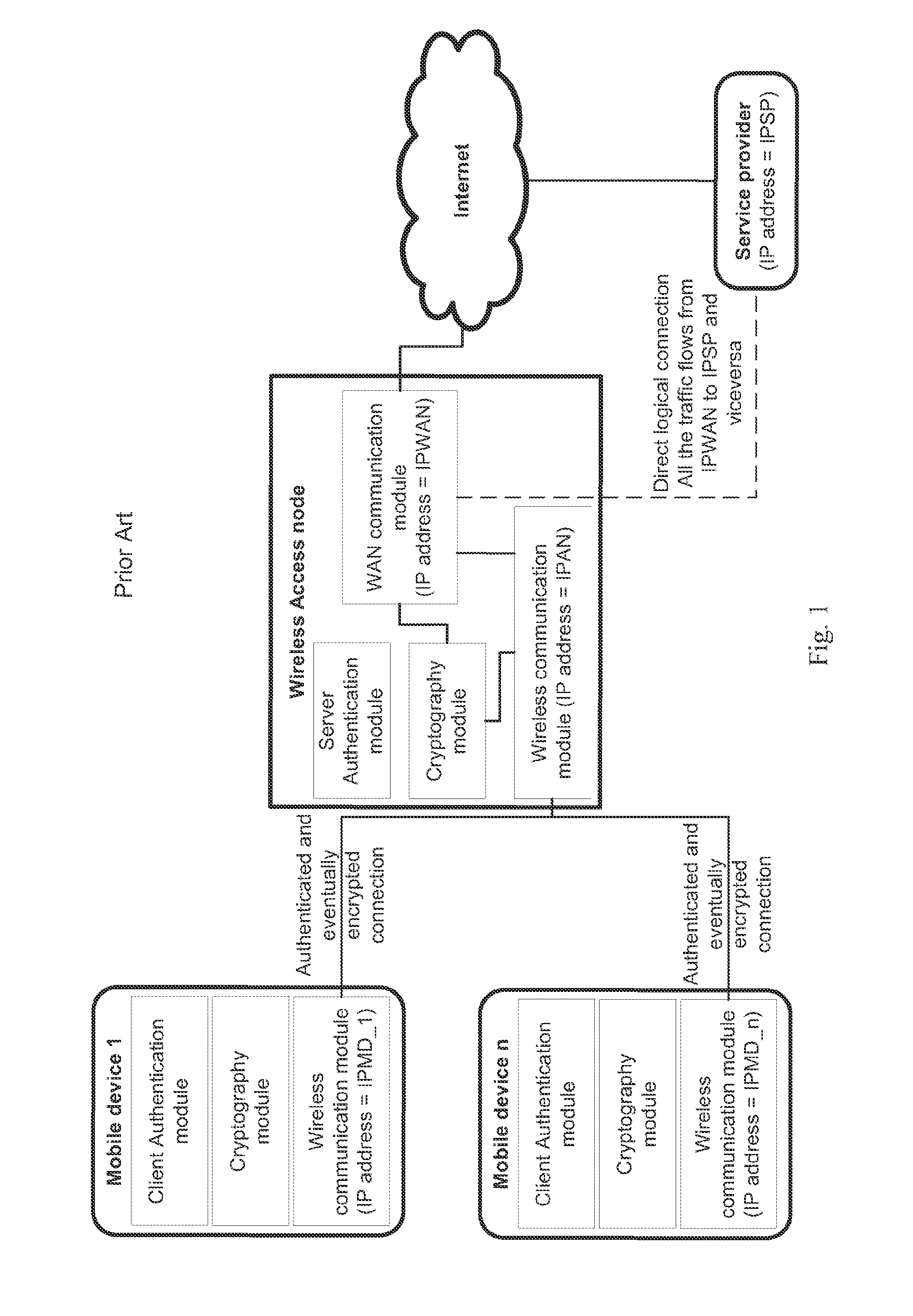
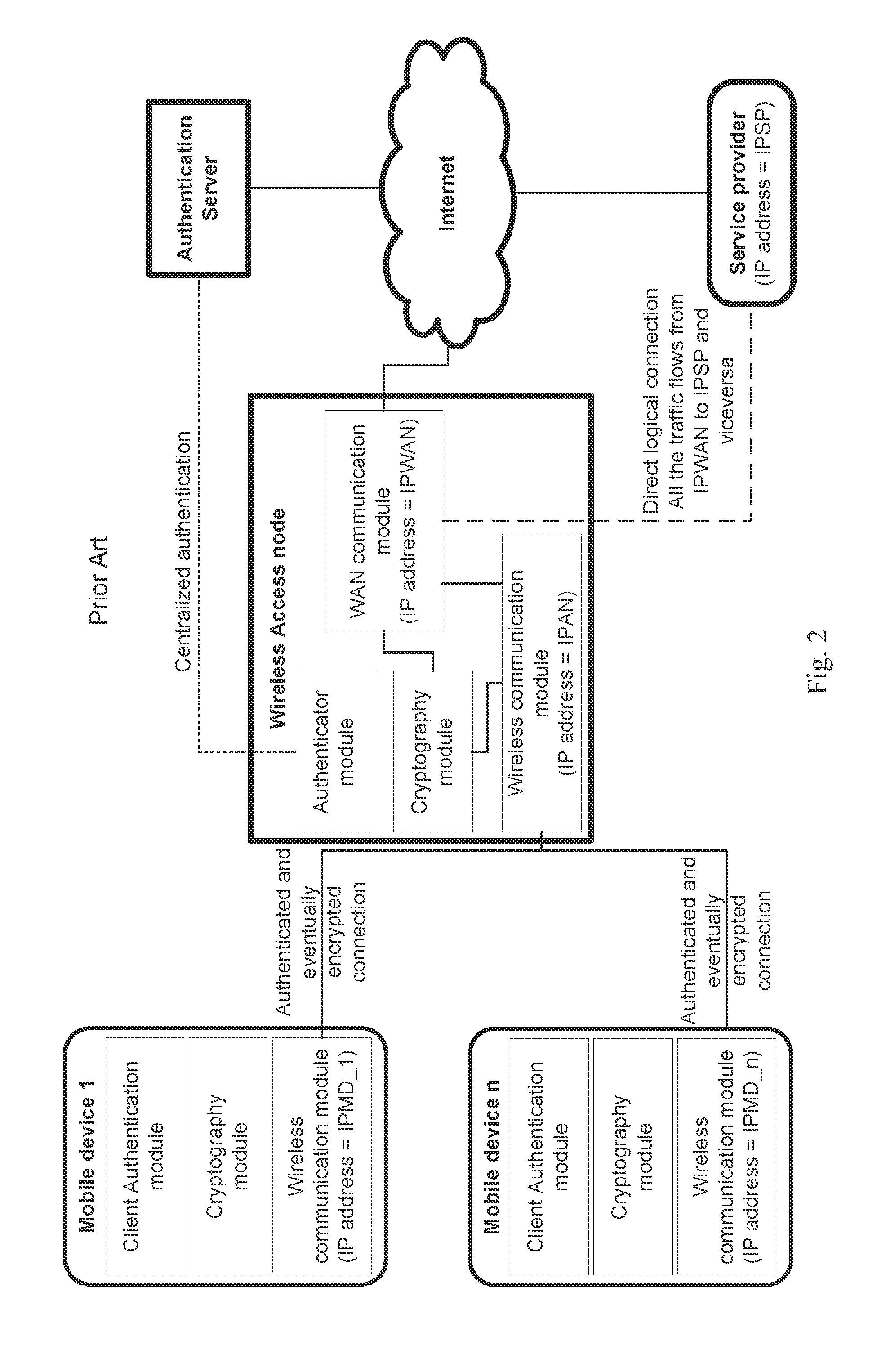
Method and system for wireless connecting a mobile device to a service provider through a hosting wireless access node
ActiveUS20120045060A1Protected from riskPotential security riskUnauthorised/fraudulent call preventionEavesdropping prevention circuitsData transmissionService provider
A method and system for commissioning a wireless connection with a related authentication and the eventual encryption to a remote relay node, whereto an electronic mobile device is connected to a hosting wireless access node for transmitting / receiving data to / from a service provider available on the Internet by means of a commissioned relay access node selected by an authentication and commissioning manager. The data transfer between the mobile device and the service provider is encapsulated into the tunnel between the hosting wireless access node and the commissioned relay access node and is finally forwarded by the commissioned relay access node to the service provider. The service provider thereby is exchanging data with the commissioned relay access node and not directly with the hosting wireless access node.
Owner:PEERTRIBE
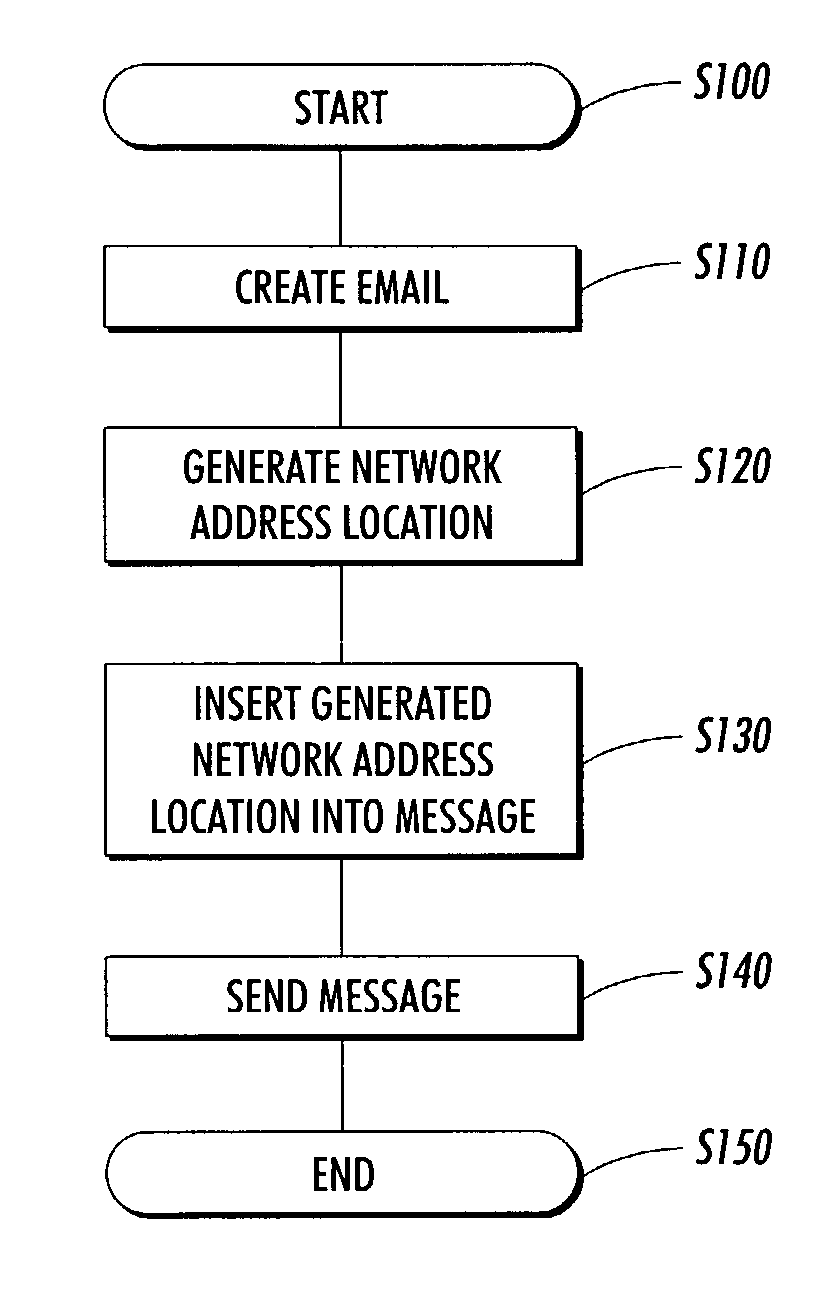
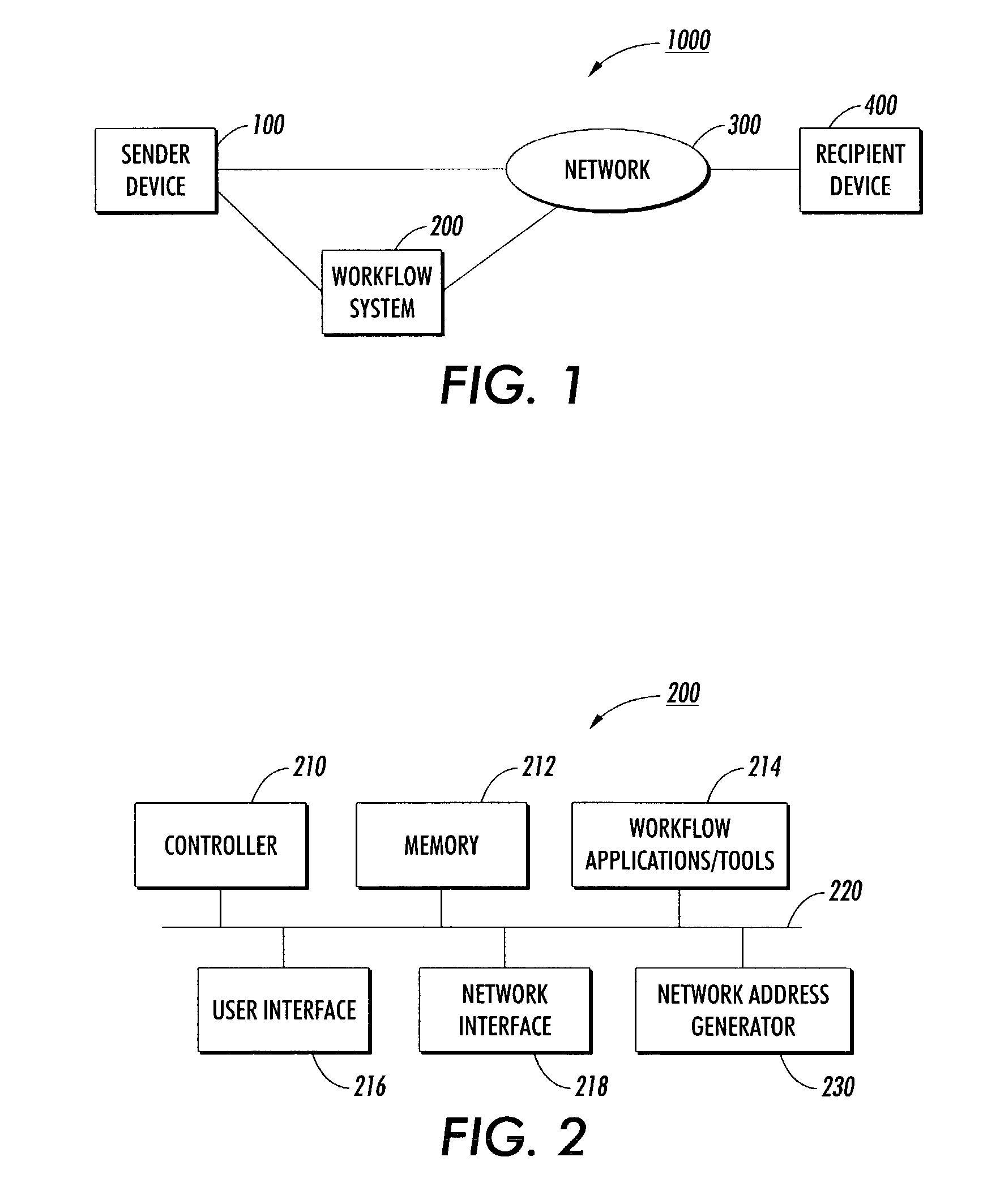
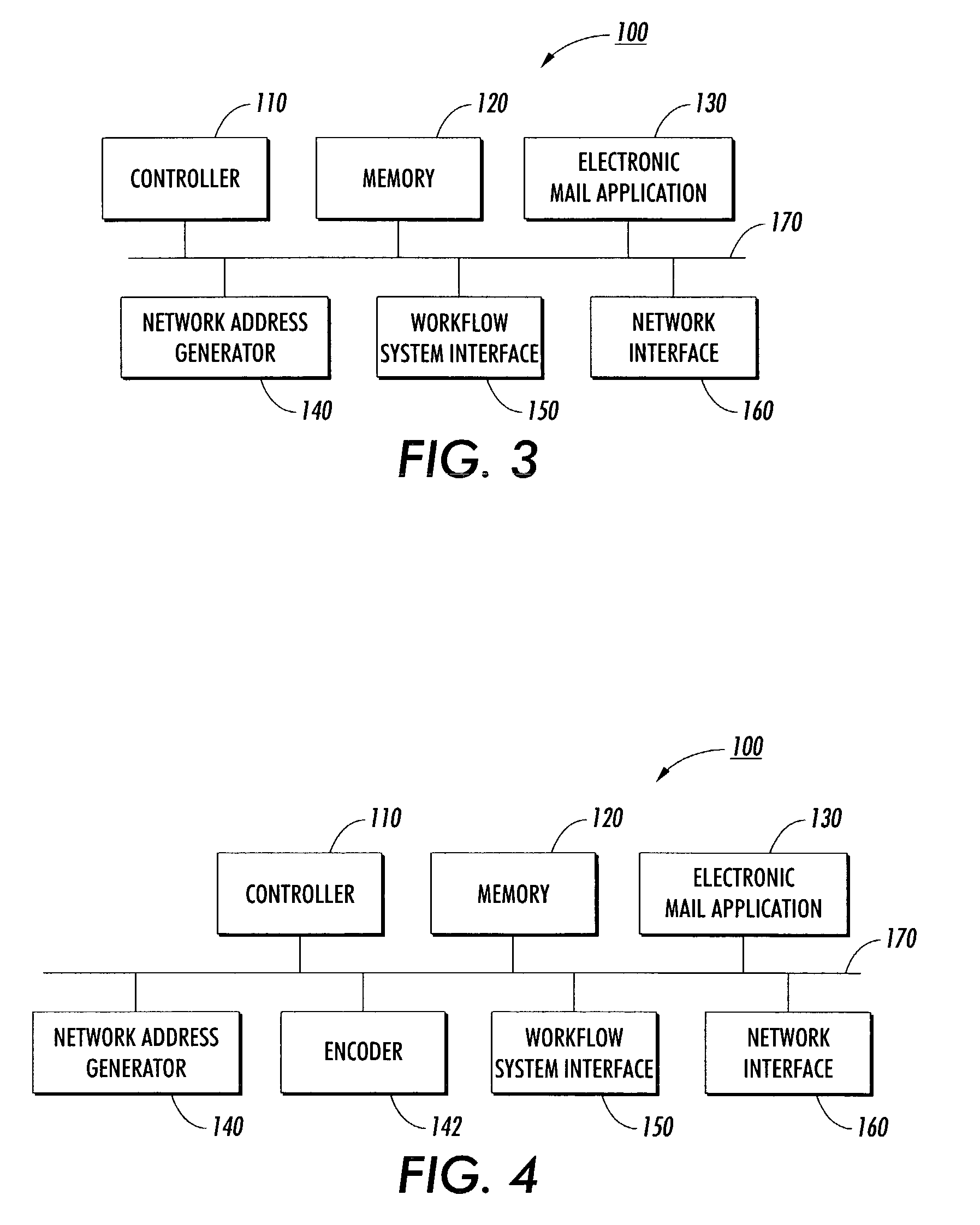
Systems and methods for integrating electronic mail and distributed networks into a workflow system
InactiveUS20030135554A1Minimize security riskDigital data processing detailsMultiprogramming arrangementsEmail addressNetwork addressing
Electronic messages with system-generated network addresses are transmitted to recipients to enable access to specific locations in the workflow system. The network addresses may be used only once, are generated using secure identifications and / or can be generated randomly. These secure identifications can be created by encoding a large number into the network address. The recipient of this network address may be required to himself to the workflow system, for example, as a means for minimizing security risks to the workflow system. The network addresses generated to specific locations within a workflow system are intended for specific recipients but may be shared by the recipients as circumstances require. Electronic mail can be transmitted with specific electronic mail addresses encoded in the electronic mail message. The specific email address can be encoded into a "Reply-to" function. Alternatively, specific email addresses can be embedded into the message portion of the email message.
Owner:PARADISE IP LLC +1
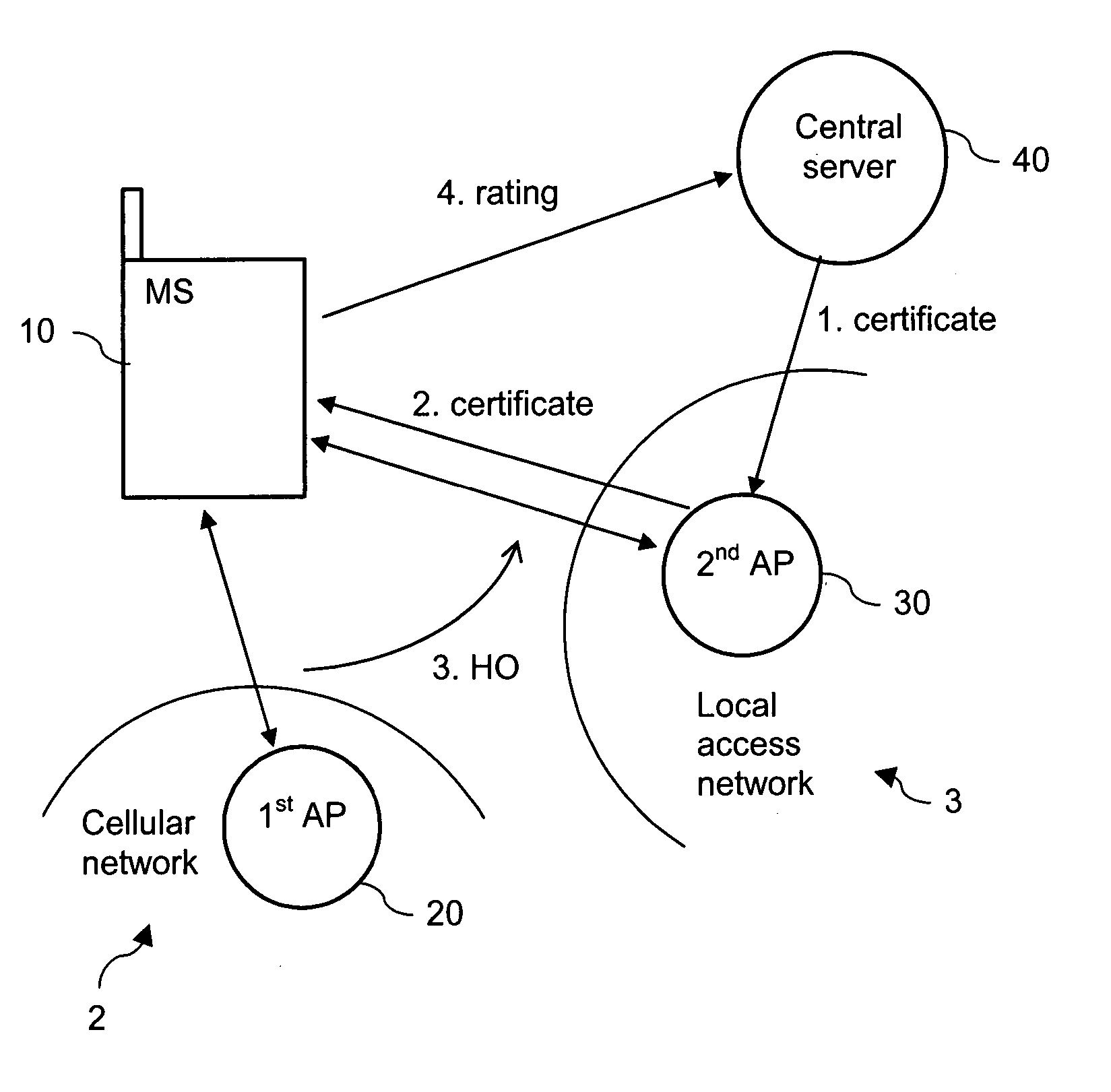
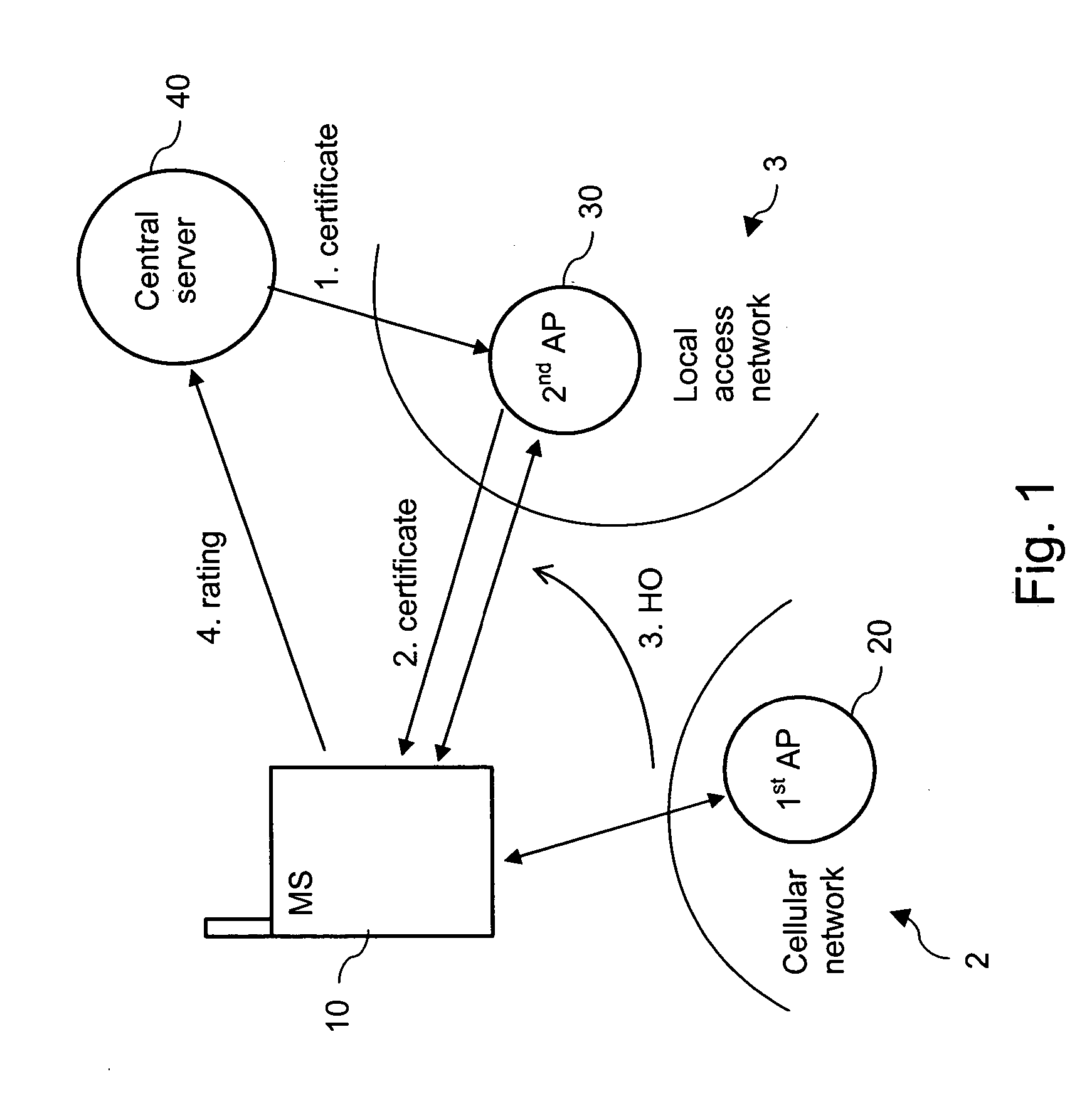
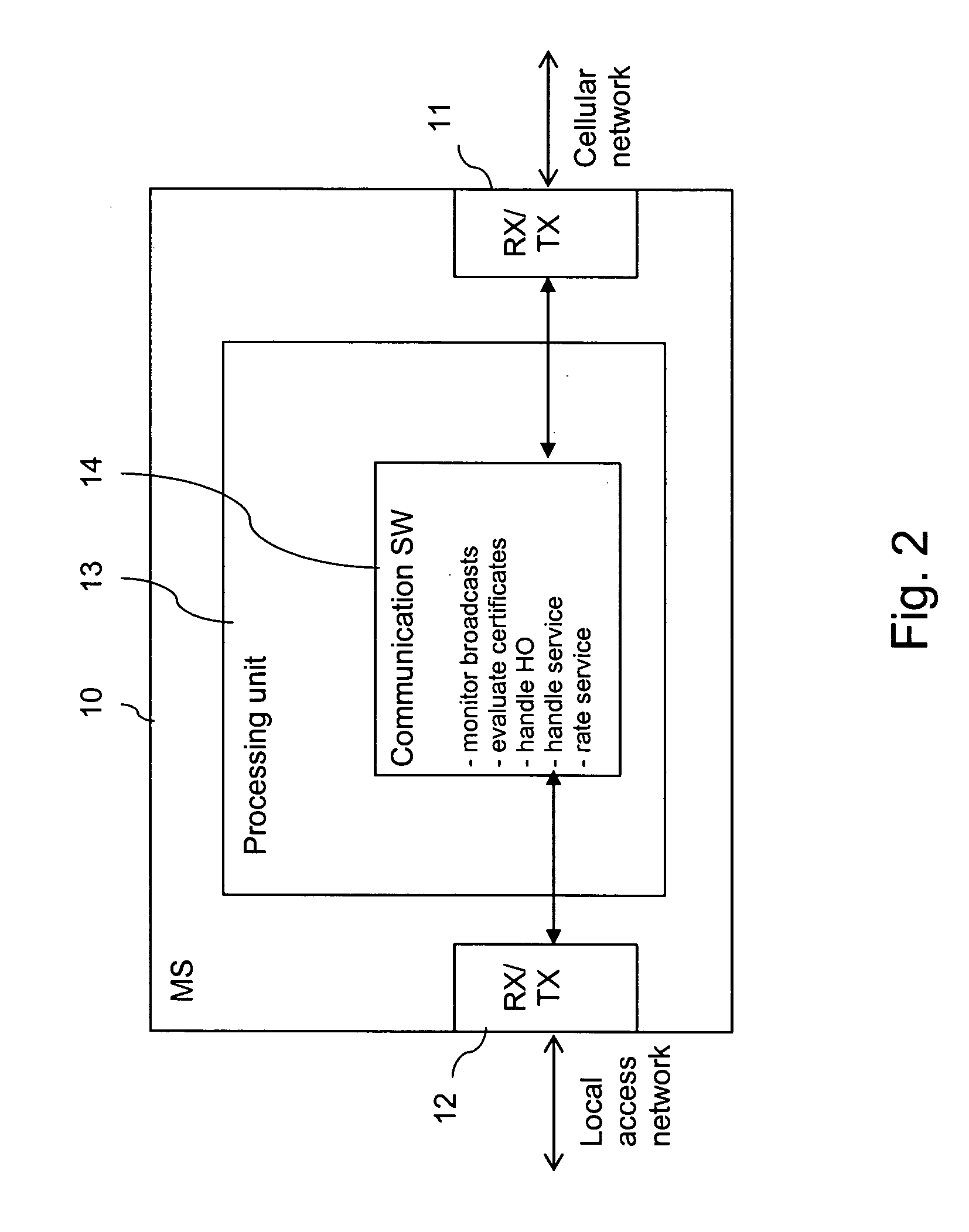
Supporting a decision by a mobile terminal whether to use an available access point
InactiveUS20060246901A1Minimizing impending security riskStreamlining economic operationAssess restrictionNetwork topologiesTelecommunicationsComputer science
Owner:NOKIA CORP
Systems, devices, and methods for reducing safety risk and optimizing energy use
InactiveUS20140316594A1Reduce loadMinimize security riskProgramme controlMechanical power/torque controlReliability engineeringAutomation
The present disclosure is generally directed to reducing a safety risk in an automation system such as an automated electrical system in a structure such as a residential, commercial, or industrial building. More particularly, the present disclosure includes systems, devices, and methods for intelligently monitoring and controlling conditions in components and / or wired connections of an automation system indicative of a potential fire hazard.
Owner:GREEN EDGE TECH
Below main cable work platform support
InactiveUS9103081B1Safely traverseMinimize security riskBridge structural detailsBridge erection/assemblyEngineeringHorizontal bar
A below main cable work platform support for hanging a work platform below a main cable of a suspension bridge and a method of installation thereof. A plurality of supports attach to each band on a main cable. Each support has a pair of struts bolted to the band, the top of each strut on each side of the band, the struts extending downward, connecting to the ends of a horizontal bar that sits between a pair of suspender cables hanging from each band. A work platform is suspended from the horizontal bar and tie down cables extend downward from the bar attaching below to stabilize the platform against wind and uplift. The method includes the step of screwing a single bolt into each side of a cable band for supporting the support therebelow.
Owner:PLATFORM EASY L L C
Limiting exposure to compliance and risk in a cloud environment
ActiveUS20160196446A1Minimizing data security riskMinimize security riskDigital data processing detailsAnalogue secracy/subscription systemsInternet privacyData security
Minimizing data security risks may be provided. A number and type of confidential data in a computing environment may be determined to generate a metric for the type of confidential data in the computing environment. The metric of the type of confidential data may be compared to a predetermined metric for the type. Responsive to determining the metric for the type of confidential data exceeding a predetermined metric for the type, an action may be performed to prevent more entries of the type of confidential data in the computing environment.
Owner:IBM CORP
Rotor hub of a wind turbine generator system
A rotor hub of a wind turbine generator system is provided. A rotor hub of a wind turbine generator system comprises at least two connecting points for respectively receiving a rotor blade. The rotor hub is surrounded by a cladding, the cladding having at least two clearances respectively for a rotor blade. Between the two connecting points for receiving the rotor blades, the spacing between the rotor hub cladding and the rotor hub is set so as to create between the rotor hub cladding and the rotor hub a hollow space that is large enough to allow servicing work on the connecting point between the rotor blade and the rotor hub to be carried out by a worker from there.
Owner:SIEMENS AG
Devices, systems, and methods for securely storing and managing sensitive information
ActiveUS20190163931A1Minimize security riskInput/output to record carriersDigital data protectionComputer securityInformation device
Devices, systems, and methods for storing and managing sensitive information in a connected environment are provided. The system comprises a master controller and a sensitive information storage device (“SIS device”). The SIS device has an island that can be activated by user interaction with the SIS device. In general, the island is deactivated by default and when the island is deactivated, sensitive information that is stored on the SIS device cannot be accessed. Only when the island is activated by user interaction can the stored sensitive information be accessed.
Owner:ELSI INC
Method of operating a navigation system to provide a pedestrian route
ActiveUS9217648B2Low costMinimize security riskInstruments for road network navigationRoad vehicles traffic controlNavigation systemComputer science
A computer implemented method of operating a navigation system to provide a pedestrian route is provided. The method comprises receiving a request for a route from an origin to a destination. The method evaluates a plurality of pedestrian paths by accessing data representing the pedestrian paths to determine a safety cost associated with including the pedestrian path in the route. The safety cost indicates a safety risk for the pedestrian. The method provides the route comprising the pedestrian paths that form a continuous navigable route between the origin and the destination that minimize the safety cost.
Owner:HERE GLOBAL BV
Racing management and information system
InactiveUS20100056238A1Minimize disruptionMinimize any physical changeVideo gamesRemote-control toysInformation systemScoring system
A system that automates the resetting of race field running order following a caution period by collecting data from existing race timing and scoring systems and communicating field reordering instructions directly to racing participants.
Owner:TERRELL II JAMES RICHARD
Limiting exposure to compliance and risk in a cloud environment
ActiveUS20160196445A1Minimizing data security riskMinimize security riskDigital data processing detailsAnalogue secracy/subscription systemsData securityInternet privacy
Minimizing data security risks may be provided. A number and type of confidential data in a computing environment may be determined to generate a metric for the type of confidential data in the computing environment. The metric of the type of confidential data may be compared to a predetermined metric for the type. Responsive to determining the metric for the type of confidential data exceeding a predetermined metric for the type, an action may be performed to prevent more entries of the type of confidential data in the computing environment.
Owner:IBM CORP
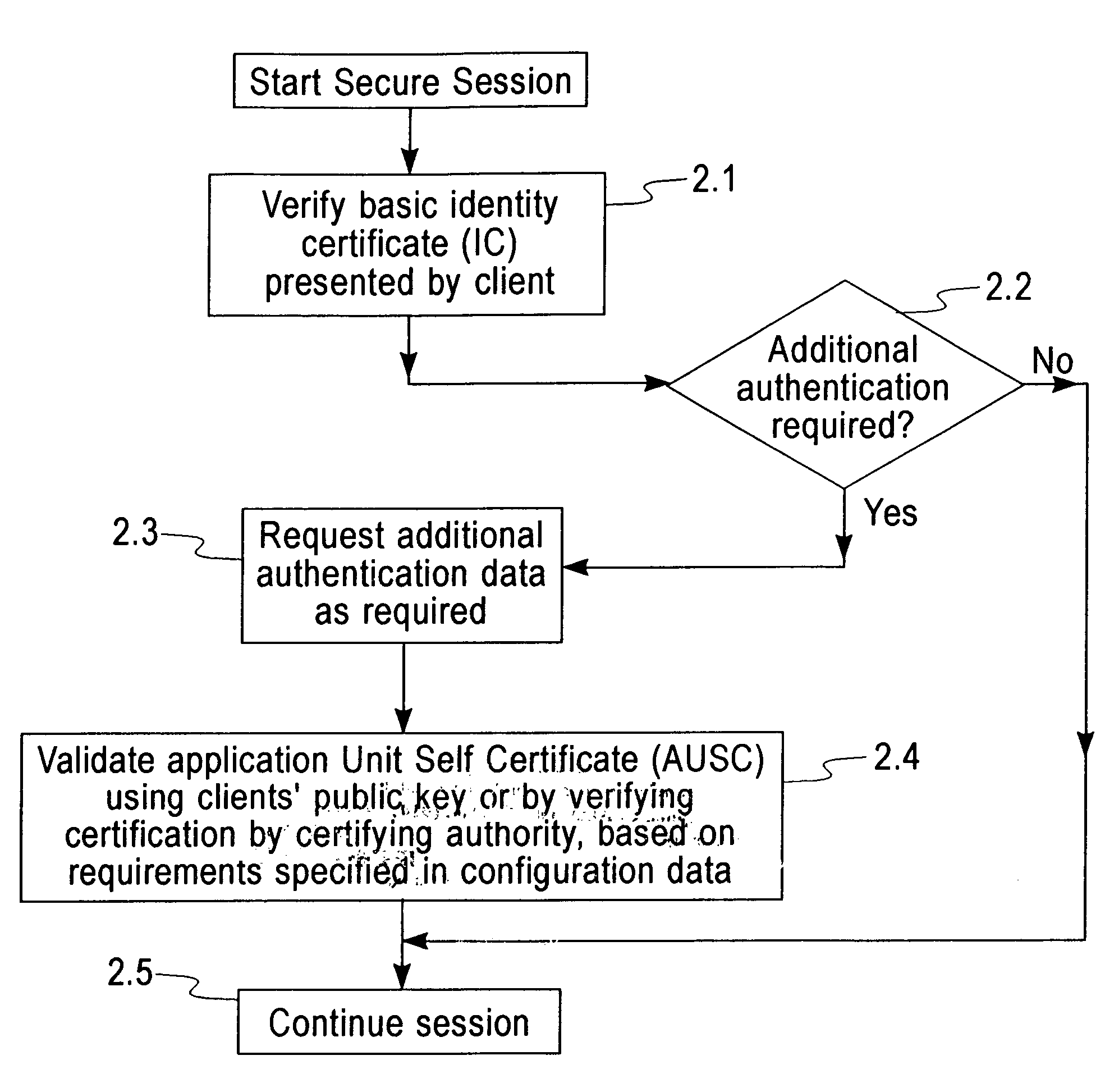
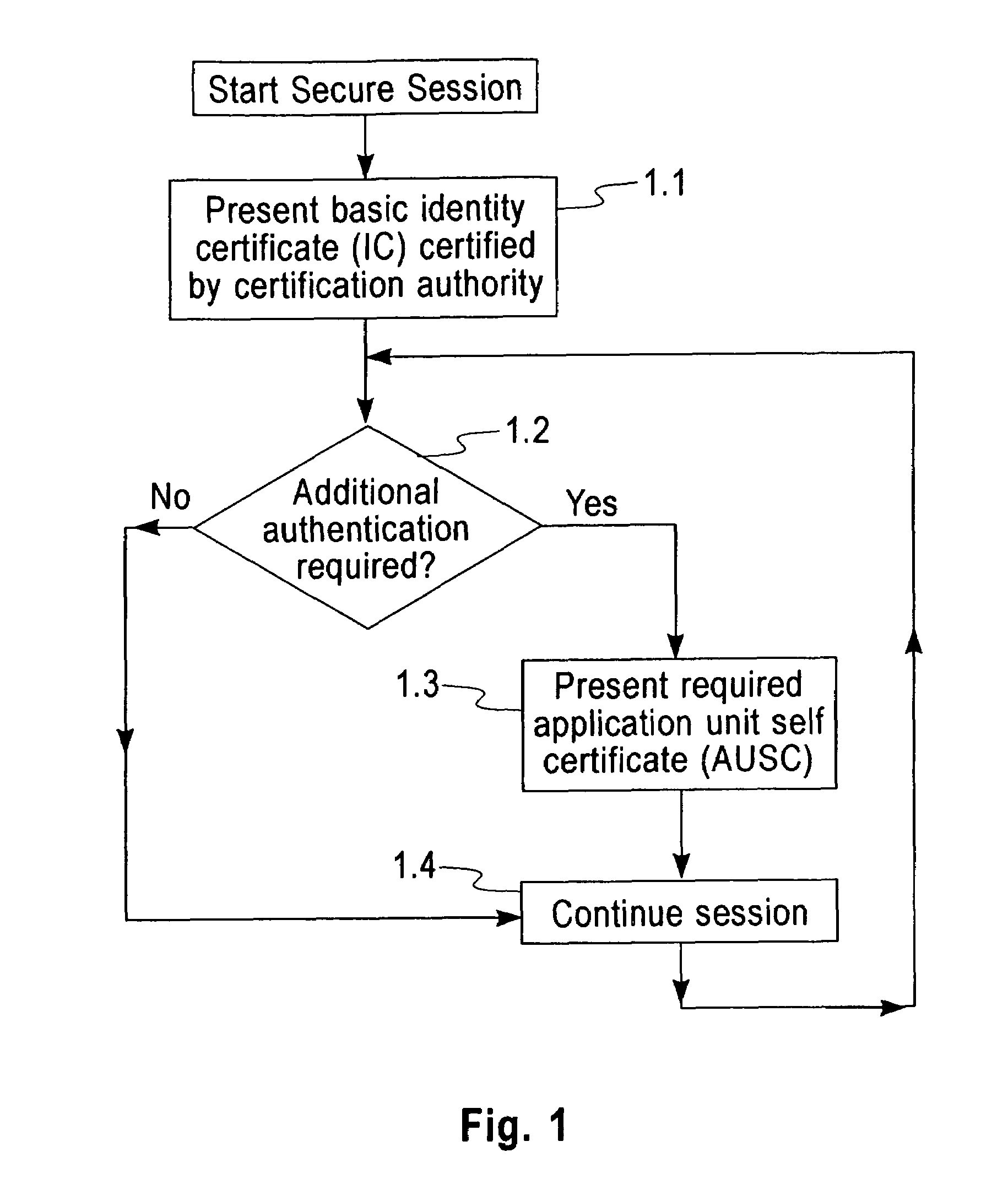
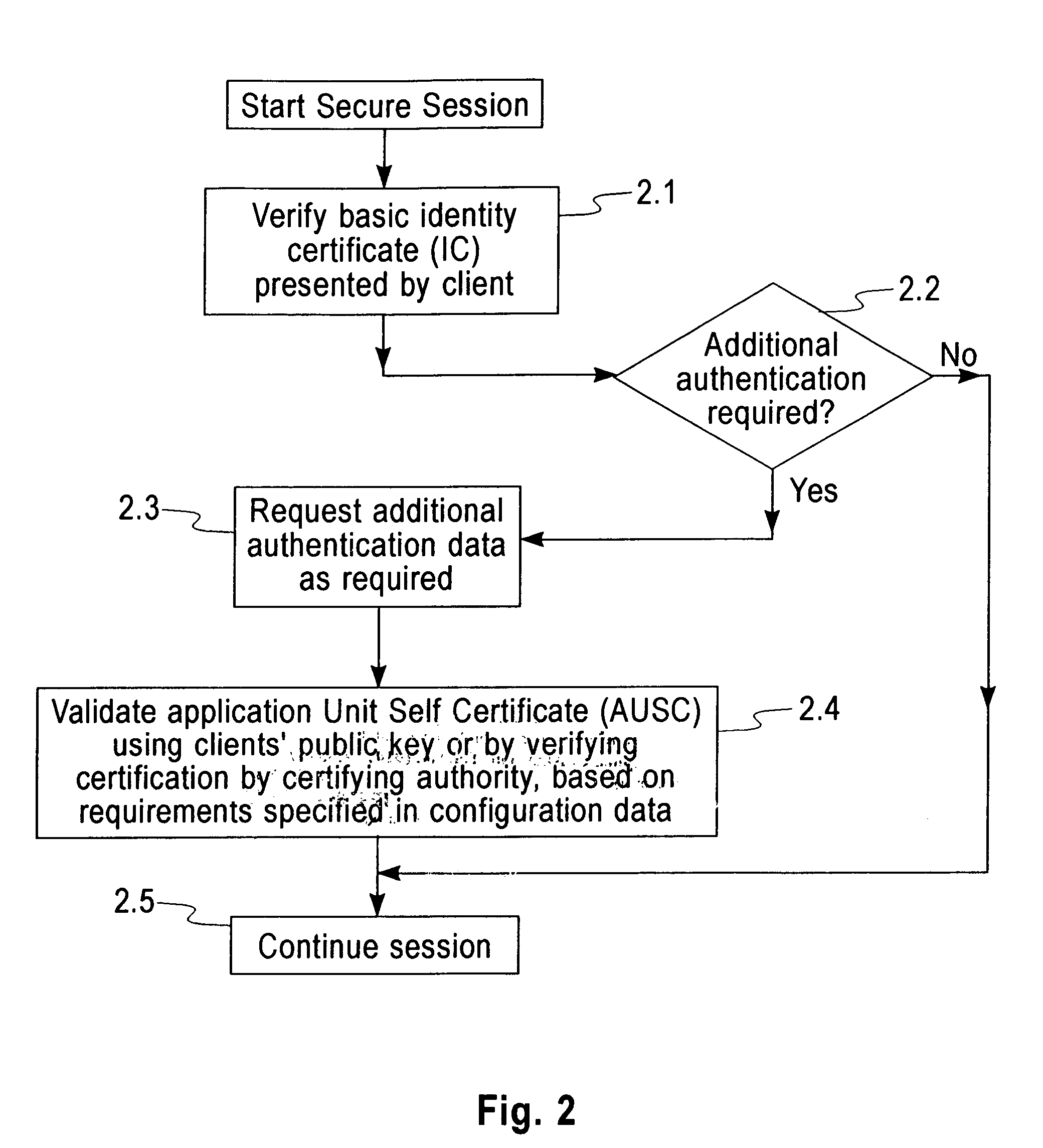
Secure authentication using digital certificates
InactiveUS7395430B2Minimize security riskEliminate riskDigital data processing detailsUser identity/authority verificationSecure authenticationSelective transfer
The present invention provides in a method for providing secure authentication using digital certificates, an improvement to enable the selective transfer of authentication data. The said method comprises presentation of basic authentication data certified by an accepted certifying authority, at the commencement of a secure transaction and transfer of additional individual authentication data units against specific requests, as and when required, thereby eliminating the risks associated with providing any authentication data that is not required for a particular transaction.The instant invention also provides a system and configured computer program product for carrying out the above method.
Owner:IBM CORP
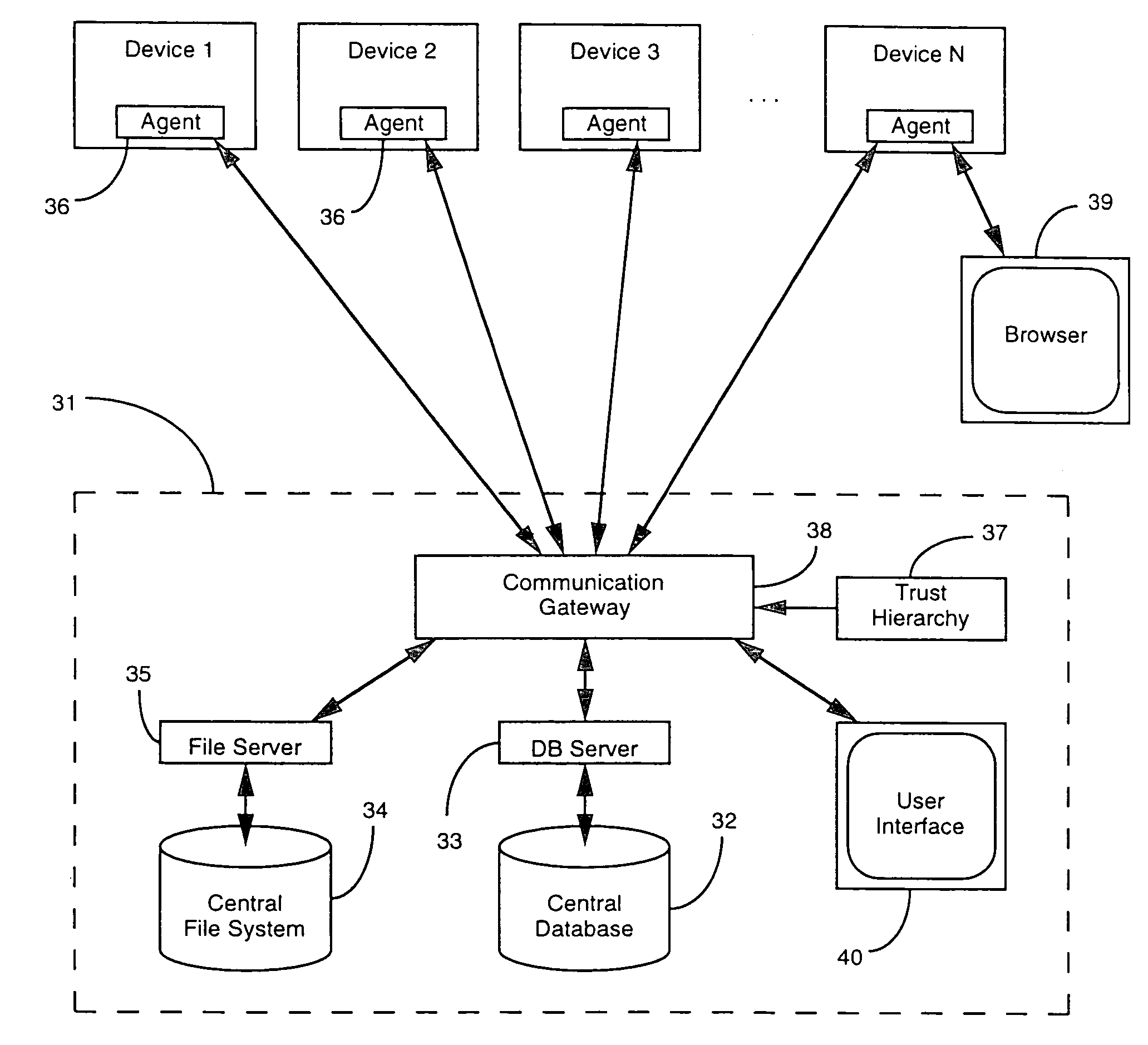
Automated provisioning framework for internet site servers
InactiveUS8250570B2Minimize security riskRepeatability is assuredProgram loading/initiatingMemory systemsComputer hardwareAuto-configuration
A framework for automatically provisioning computing devices includes a central database system and a central file system. Information stored in the database comprises a model of the individual devices, as well as the interconnections of the devices. The central file system stores the software components to be installed on the devices. When provisioning is carried out, the database sends commands to agents located on each device which cause them to retrieve and install the software components from the file system, and to configure the components according to the stored model.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
Method and system for wireless connecting a mobile device to a service provider through a hosting wireless access node
ActiveUS8428264B2Potential security riskReduce decreaseUnauthorised/fraudulent call preventionEavesdropping prevention circuitsService provisionThe Internet
A method and system for commissioning a wireless connection with a related authentication and the eventual encryption to a remote relay node, whereto an electronic mobile device is connected to a hosting wireless access node for transmitting / receiving data to / from a service provider available on the Internet by means of a commissioned relay access node selected by an authentication and commissioning manager. The data transfer between the mobile device and the service provider is encapsulated into the tunnel between the hosting wireless access node and the commissioned relay access node and is finally forwarded by the commissioned relay access node to the service provider. The service provider thereby is exchanging data with the commissioned relay access node and not directly with the hosting wireless access node.
Owner:PEERTRIBE
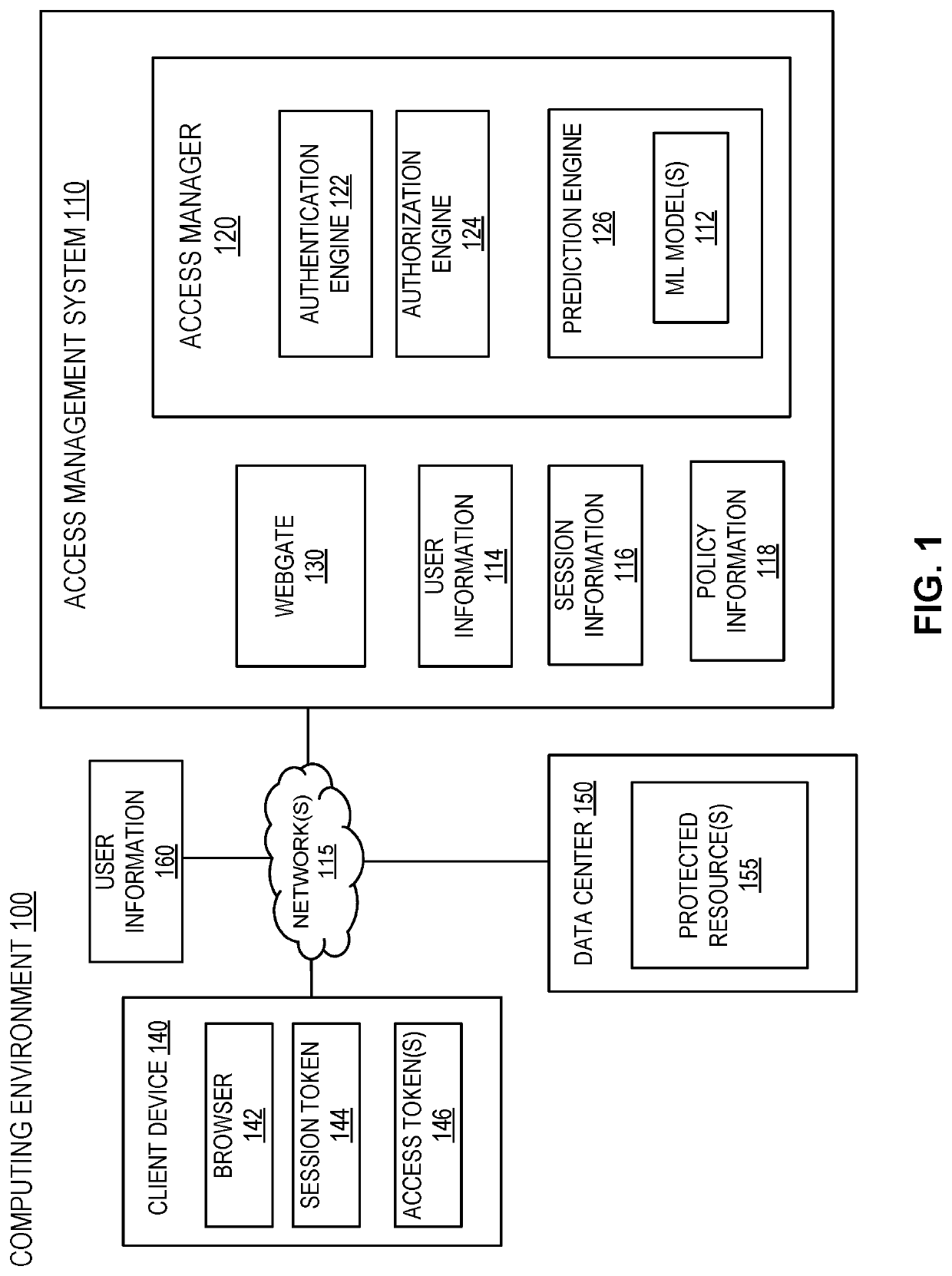
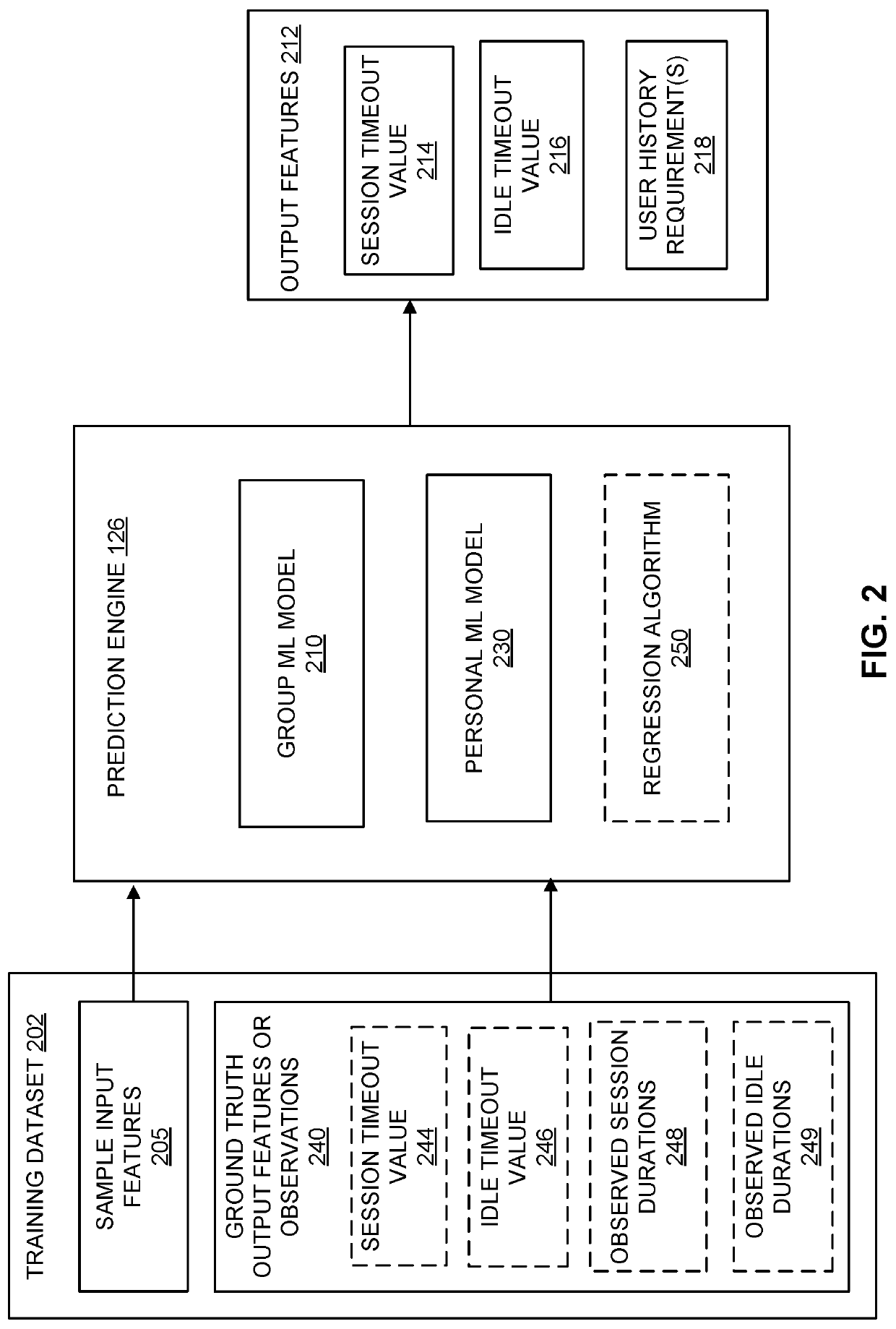
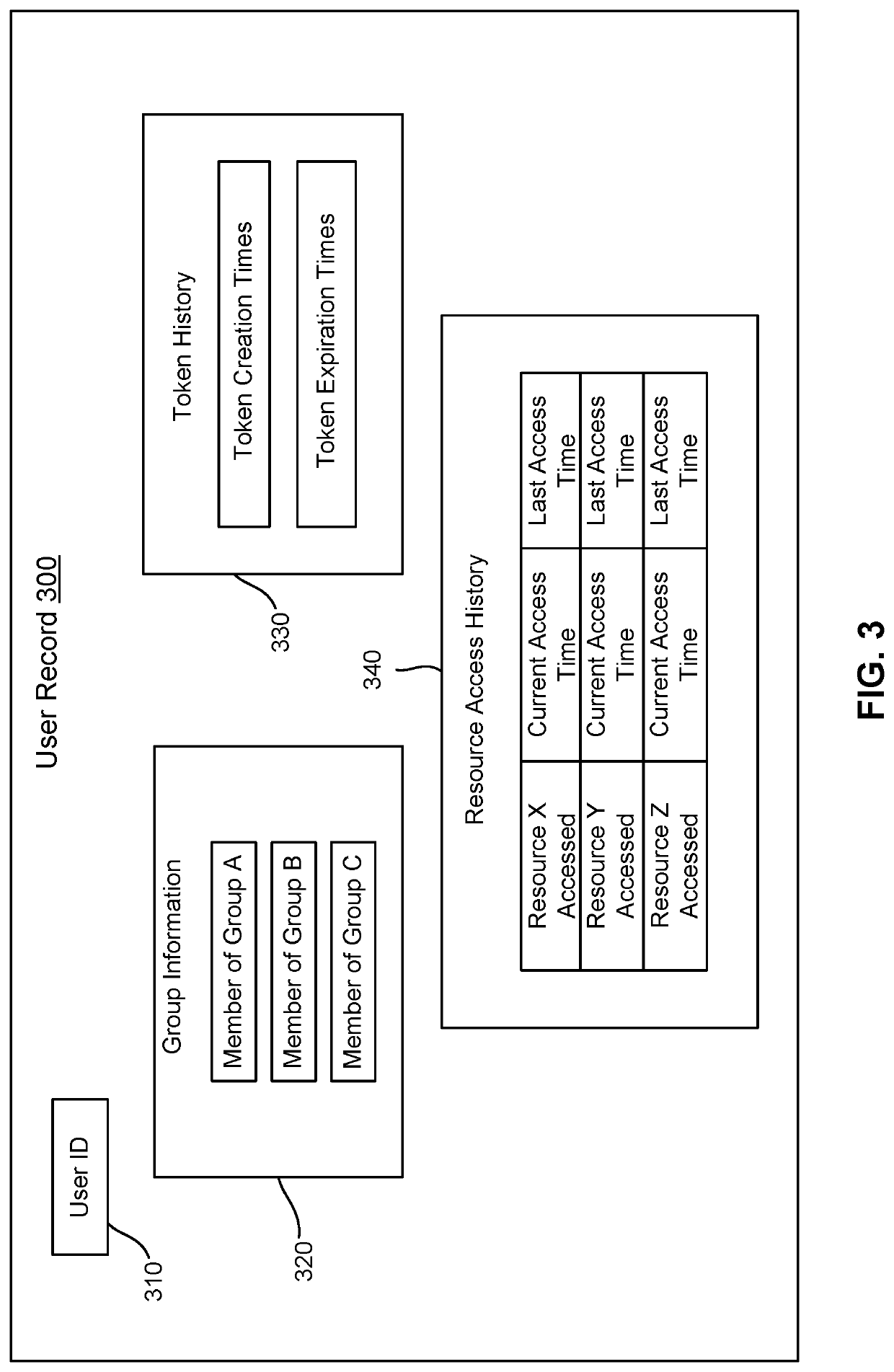
User-specific session timeouts
ActiveUS20210014221A1Risk minimizationPoor user experienceMachine learningTransmissionEngineeringData mining
Techniques for described for generating session-related timeout parameters that are user-specific in value. A user-specific timeout parameter offers several advantages over a static timeout parameter, including minimized the risk of session hijacking, fewer stale sessions to manage, and timeout parameters that more closely match the user's actual behavior. A value for a timeout parameter can therefore depend on information stored for a specific user. The stored information can indicate user behavior observed over a period of time encompassing multiple sessions and / or multiple accesses to the same or different resources. In certain embodiments, a value for a timeout parameter is determined by a prediction engine implemented using a machine learning (ML) model. The ML model may determine the timeout parameter based on information obtained records associated with the user for whom the timeout parameter value is being determined, as well as information from records associated with other users.
Owner:ORACLE INT CORP
Systems, methods, and apparatuses for securely accessing user accounts
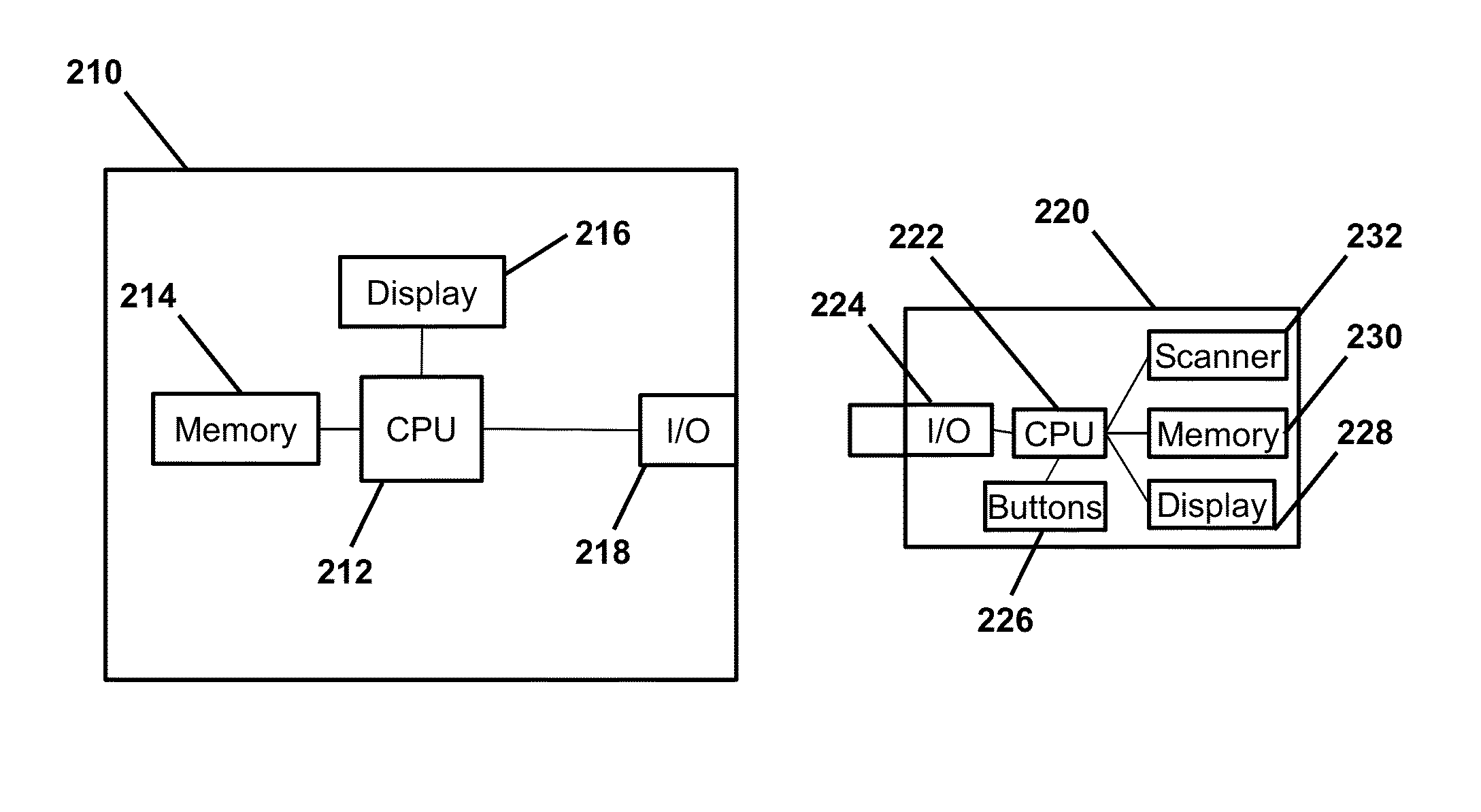
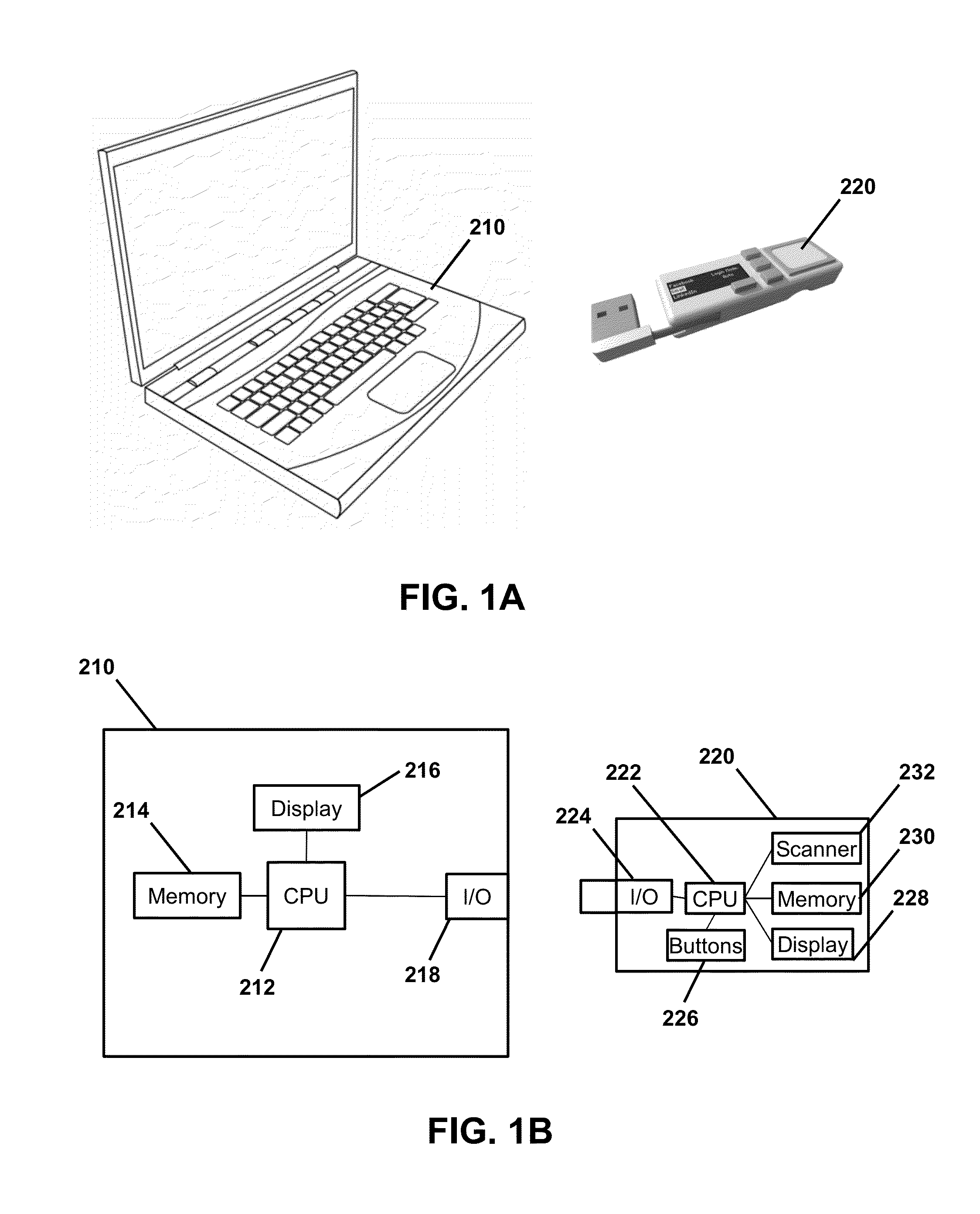
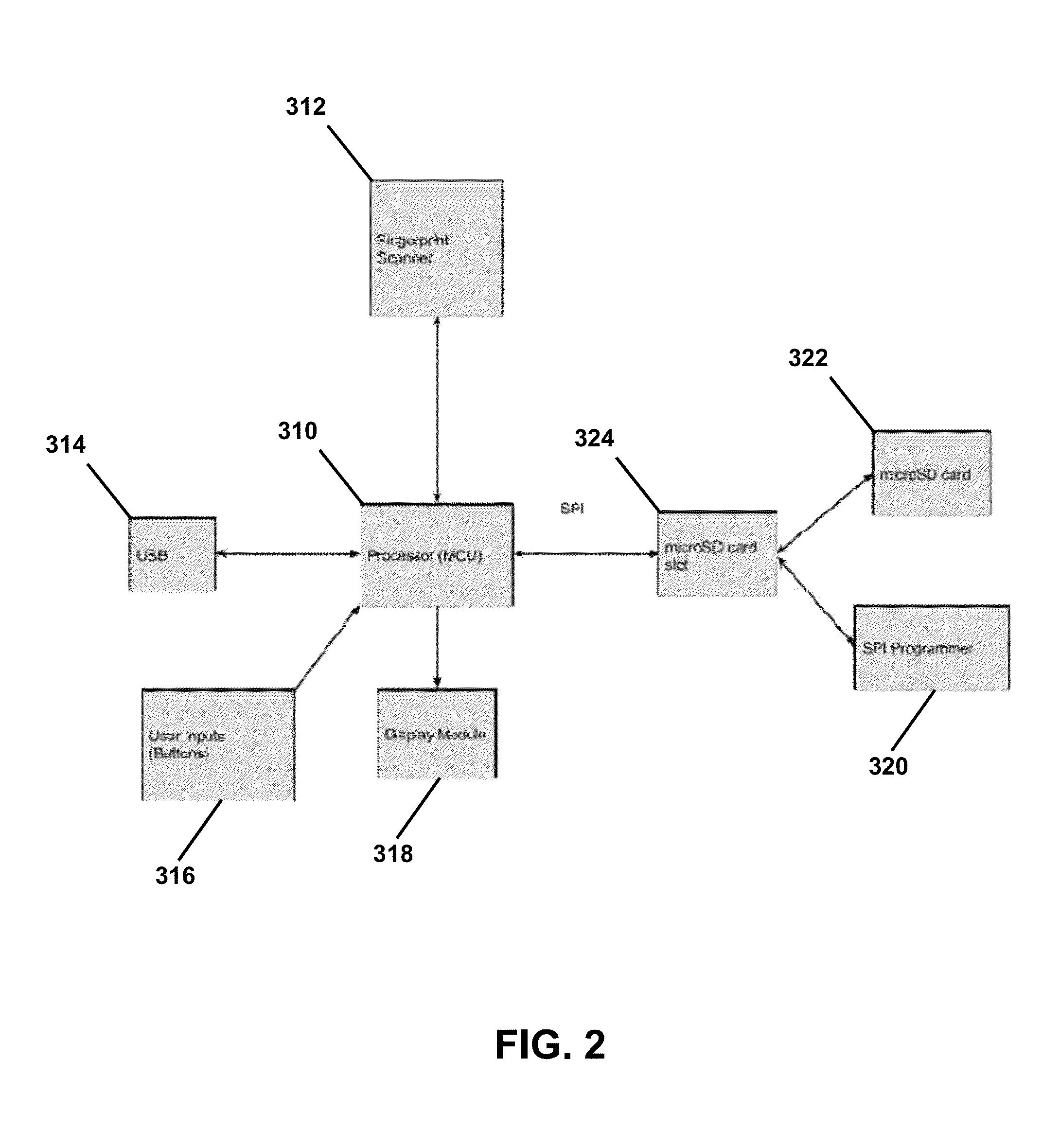
InactiveUS20150333910A1Minimize security riskQuickly and securely logUser identity/authority verificationDigital data authenticationFingerprintInformation field
The systems, methods, and apparatuses of the present disclosure quickly and securely populate account information fields of an account using biometric information, such as fingerprint information. A portable electronic apparatus of the present disclosure includes memory that stores first fingerprint information in association with account information of an account that can be presented by another electronic device through a website or an application running on the other electronic device. The portable electronic apparatus also includes a fingerprint scanner that scans a fingerprint to obtain second fingerprint information, an interface that interfaces with data input interface, such as a keyboard interface, of the other electronic device, and a processor that compares the first fingerprint information with the second fingerprint information, and, if the fingerprint information matches, populates the account information field of the account with the account information via the data input interface of the other electronic device.
Owner:KIRDAHY DYLAN +1
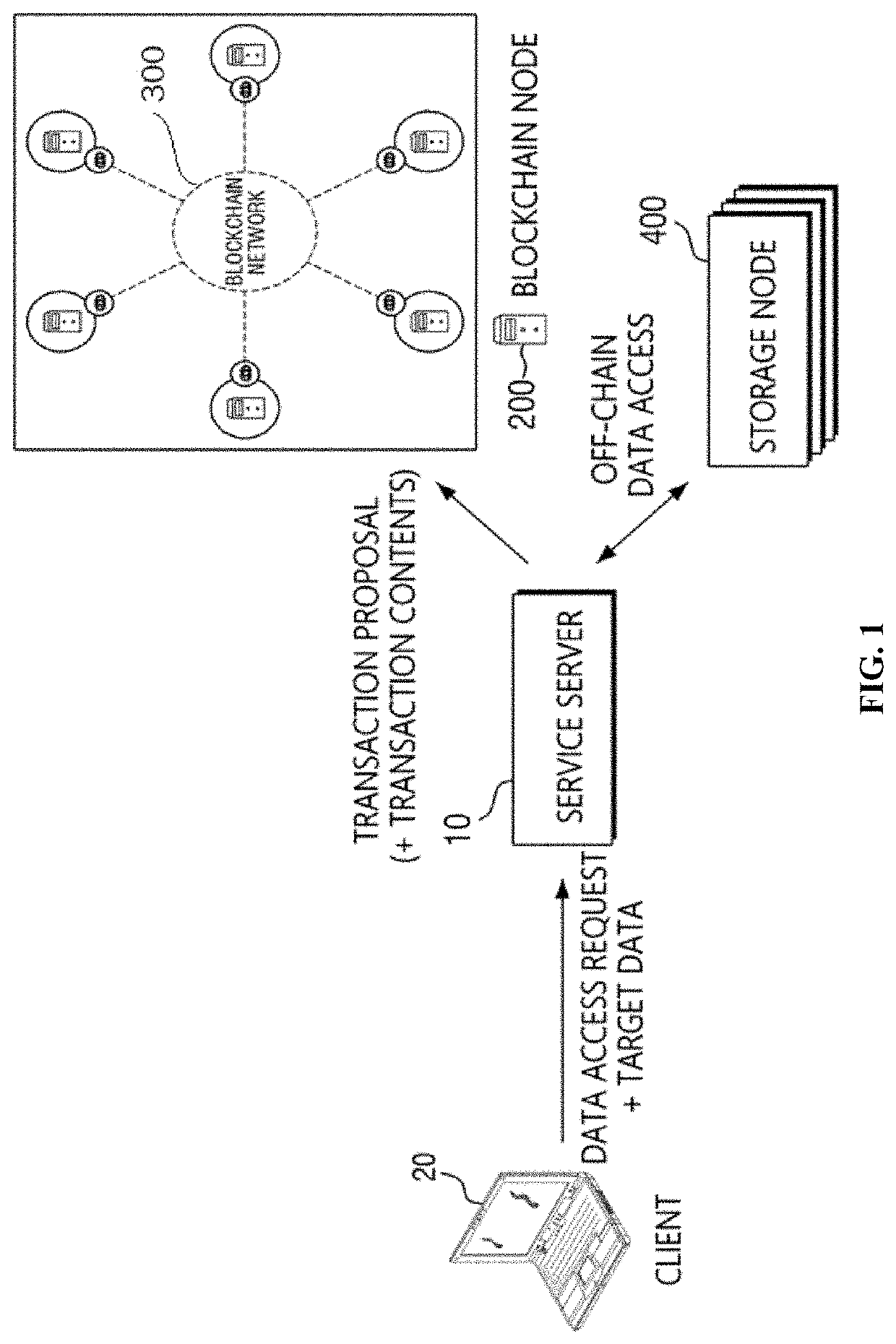
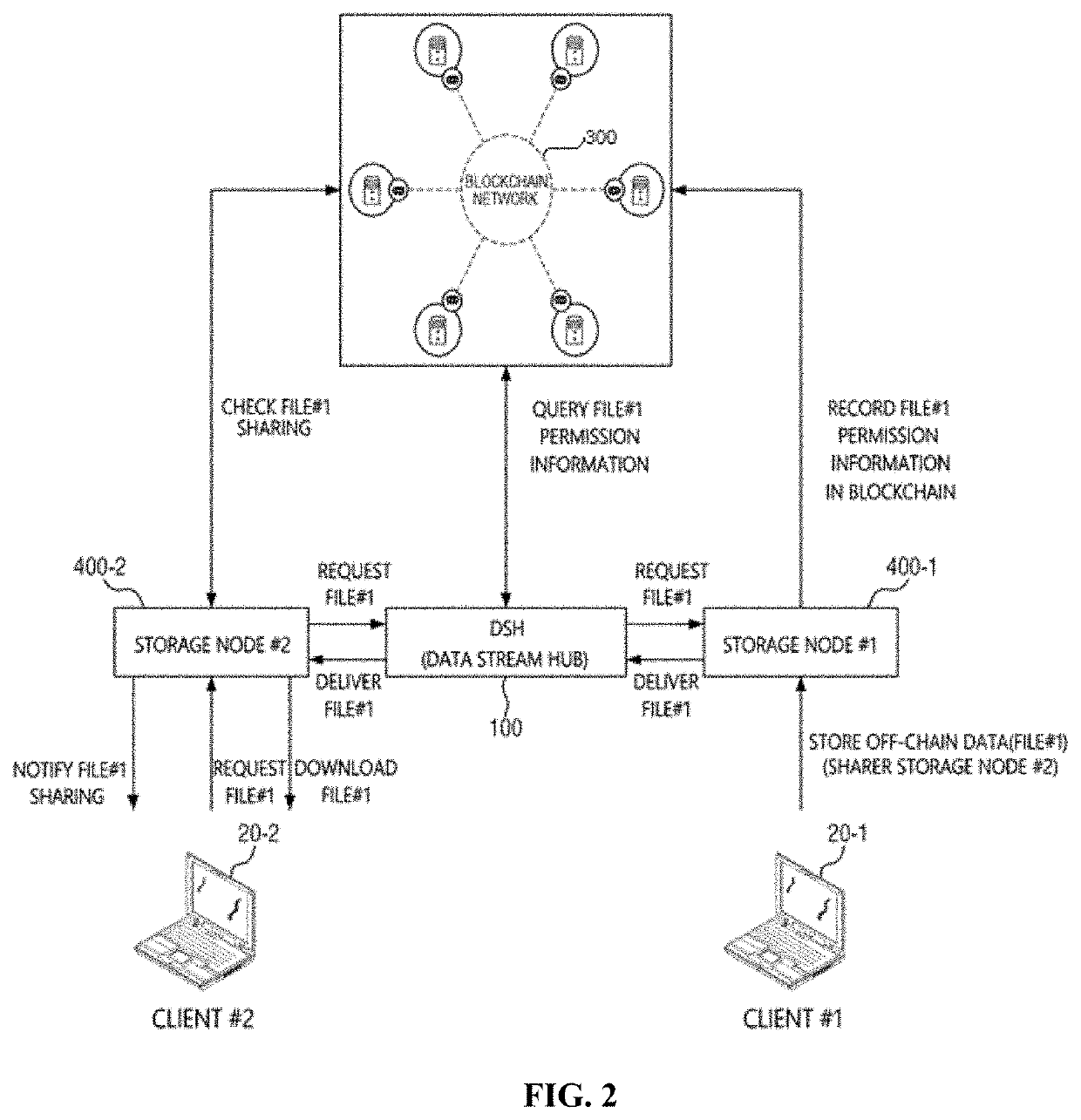
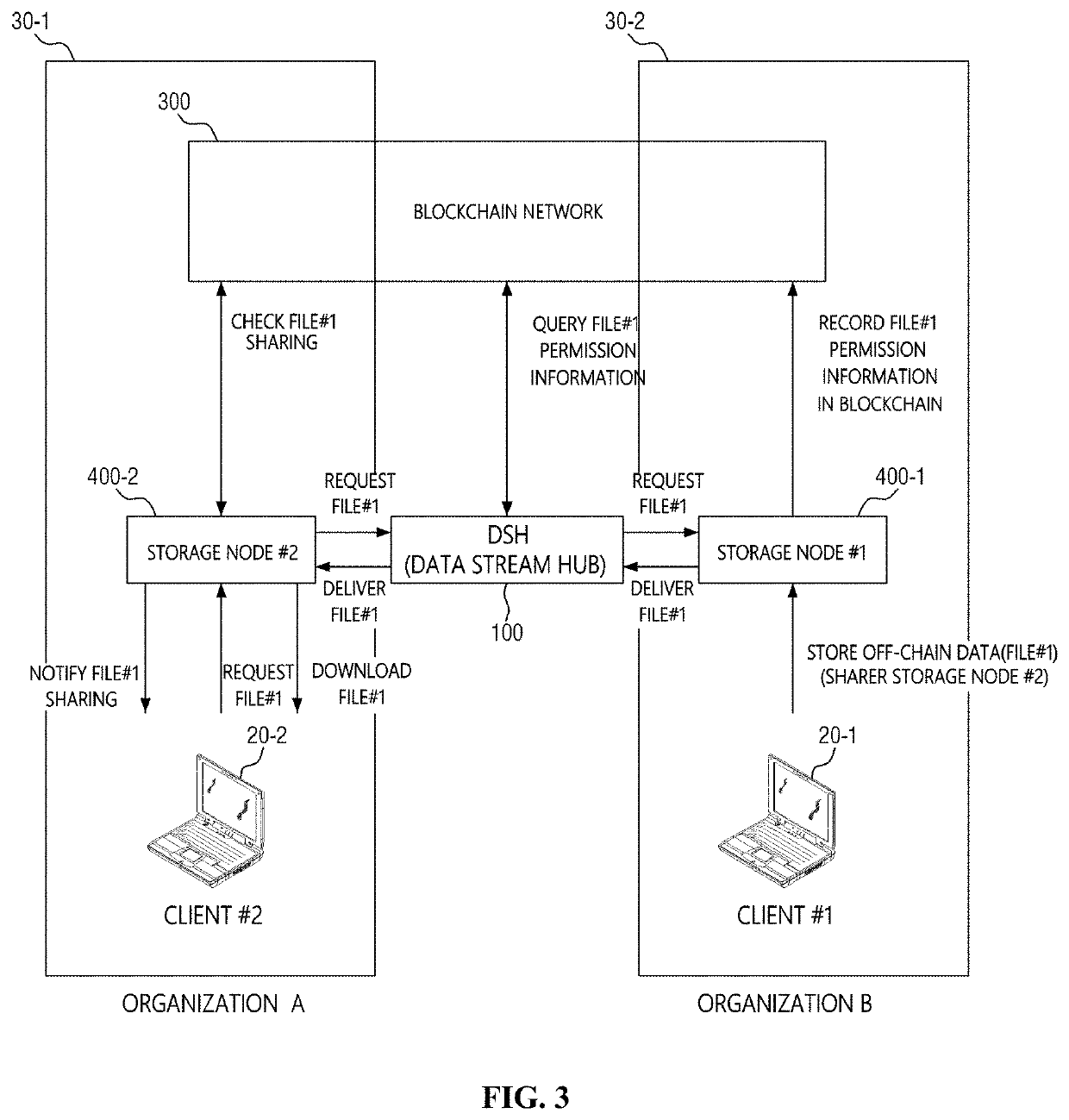
Off-chain data sharing system and method thereof
InactiveUS20210367762A1Ensure reliabilityMinimize security riskEncryption apparatus with shift registers/memoriesDigital data protectionData streamTrunking
An off-chain data sharing system according to an embodiment of the present invention includes a first storage node to store off-chain data, a blockchain node to store a ledger that records permission information of the off-chain data, and a data stream hub to relay data transmission and reception between the first storage node and a second storage node requesting the off-chain data by referring to the permission information.
Owner:SAMSUNG SDS CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com