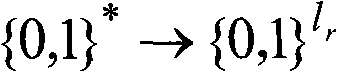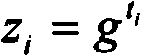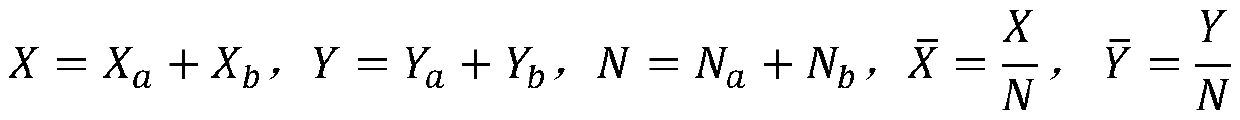Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
106results about How to "Guaranteed not to be leaked" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Method and device for medical information sharing privacy protection based on blockchain technology
InactiveCN106682530AAvoid privacyUse constraintsDigital data protectionInformation sharingPrivacy protection
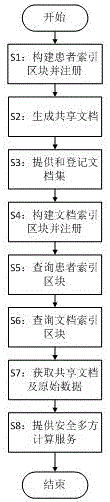
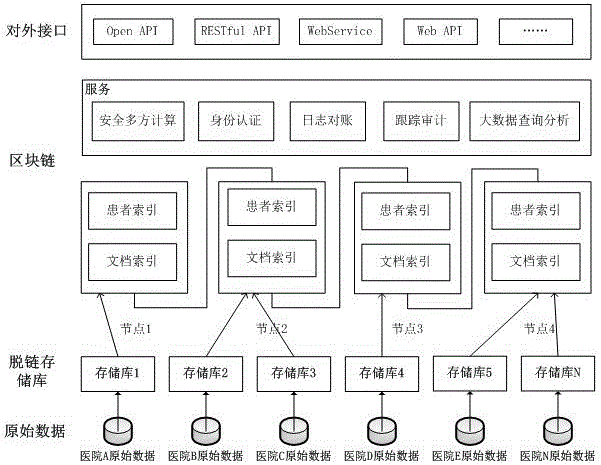
The invention discloses a method and device for medical information sharing privacy protection based on a blockchain technology. According to the method, in aspects of privacy protection based on a blockchain technology, medical data on-chain and off-chain storage and forced privacy protection safety multiparty calculation, illegal medical data obtaining, use and tampering are avoided, and medical information sharing, big data analysis and utilization and patient privacy protection are implemented. The device comprises a data storage module, a service module provided based on the blockchain technology and a call service module provided externally, wherein a three-layer data storage frame is adopted for the data storage module; and the service module provided based on the blockchain technology mainly comprises forced privacy protection safety multiparty calculation. The method and device for medical information sharing privacy protection based on the blockchain technology are mainly applied to the fields of method and device for medical information sharing privacy protection based on a blockchain technology and medical big data analysis and the like, and technical guarantee is also provided for patient privacy protection while medical information sharing is achieved based on the blockchain technology.
Owner:HANGZHOU DIANZI UNIV
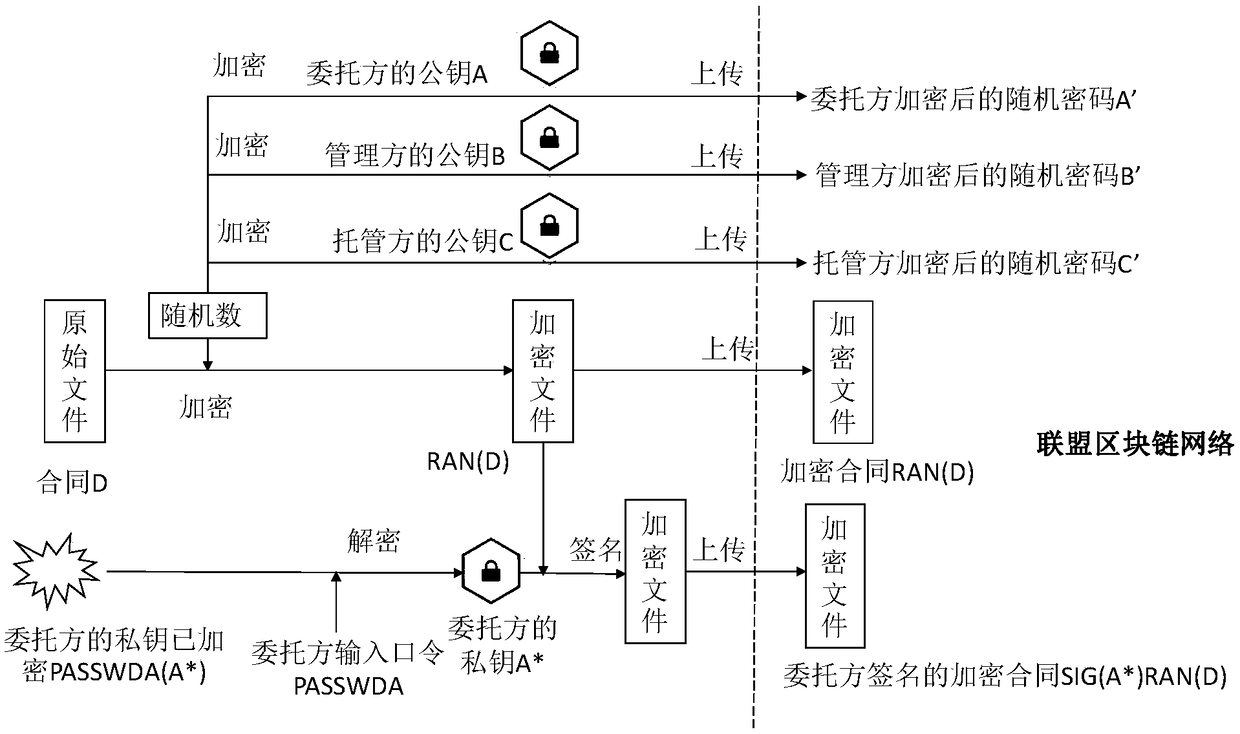
A contract signing system based on multi-party consensus of alliance chains
ActiveCN109377198ASolve the cumbersome processPrevent modification of dataOffice automationChain systemBlockchain
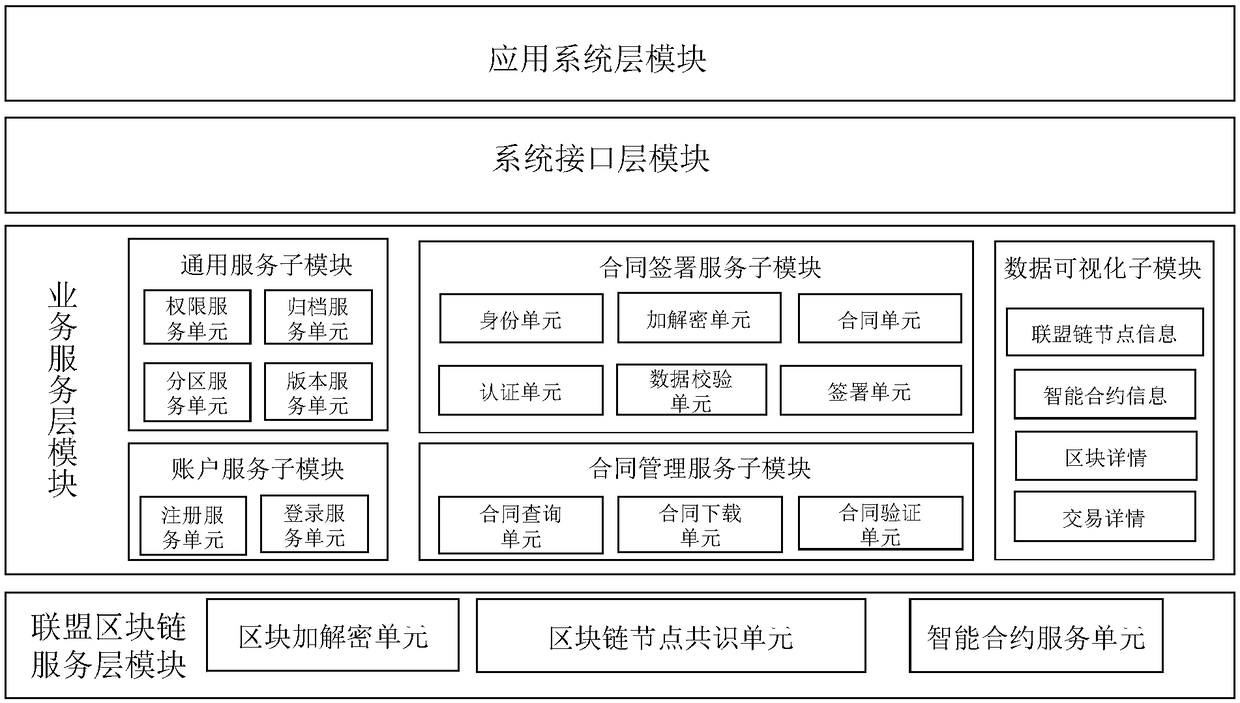
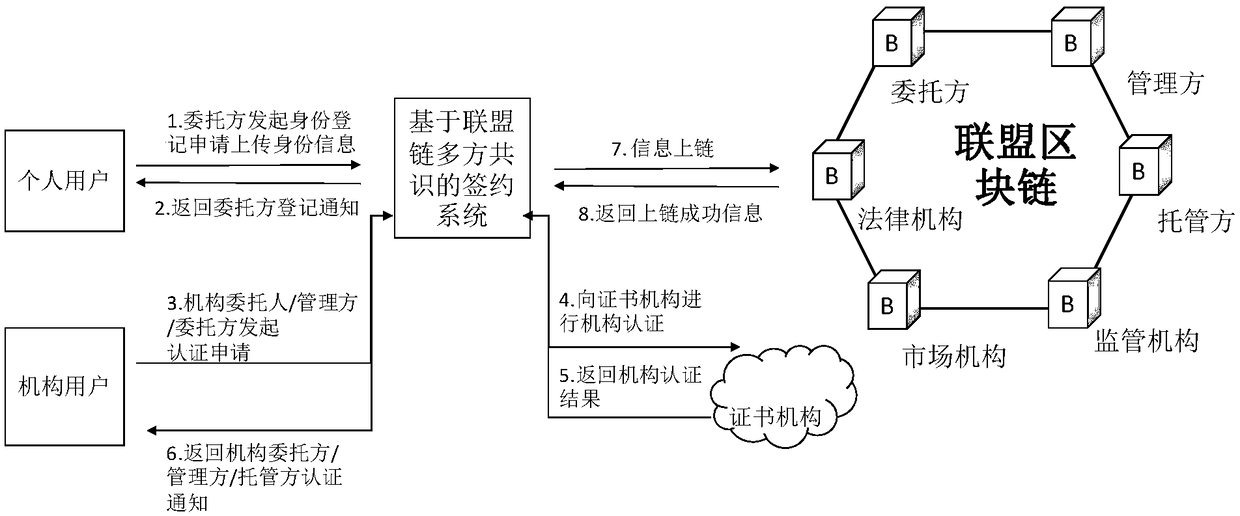
The invention discloses a signing system based on multi-party consensus of alliance chains, aiming at providing infrastructure of private fund industry, providing a private fund online signing management system based on alliance chain system, supporting multi-party participation and consensus, encrypting and verifying data for private fund entrusting party, management party and custodian party. The technical scheme is as follows: the contract signing scheme realized by the contract signing system of the invention, in which encryption sharing and multiple independent signatures are carried outsimultaneously, cannot only ensure that the electronic contract is not leaked on the block chain, but also can effectively verify whether the contract is tampered with or not. Moreover, the block chain multi-party consensus algorithm in the system of the invention can efficiently complete the minimum consensus of four nodes and prevent malicious nodes from modifying data. In addition, the heterogeneous contract storage design in the system of the invention can combine the traditional database system and the block chain system to realize the classified storage of the data on the chain and underthe chain, which is convenient for the local search and inquiry and ensures that the commercial secrets are not disclosed.
Owner:上海金融期货信息技术有限公司
Method for protecting mobile terminal privacy based on voiceprint recognition
InactiveCN102231277AEliminate dependenciesRemoval of Difficult Restrictions on CollectionSpeech recognitionRecognition algorithmSpeech sound
The invention discloses a method for protecting mobile terminal privacy based on voiceprint recognition. The method comprises the following steps: analysis and extraction of voice message characteristics, model training and voiceprint recognition. In the method, the efficiency of the voiceprint recognition is high, and the performances and the recognition efficiency of the voiceprint recognition are not associated with the texts and the language. The voice length of a speaker is not required specially, and only voice messages in minutes are required so as to acquire the voice feature messages of the speaker, thereby carrying out the model training and the recognition. Applications of a voiceprint recognition algorithm in the intelligent mobile terminal have the advantages of high stability and recognition accuracy, and a voice feature model which is trained occupies small memory space of the intelligent mobile terminal. The method can be utilized to preferably protect the private information of a user in the intelligent mobile terminal and avoid the private information from being revealed and stolen when a mobile phone is lost.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Session message processing method and device
ActiveCN109639828AFlexible and intelligent interactionSafe interactionTransmissionVirtual userMessage processing
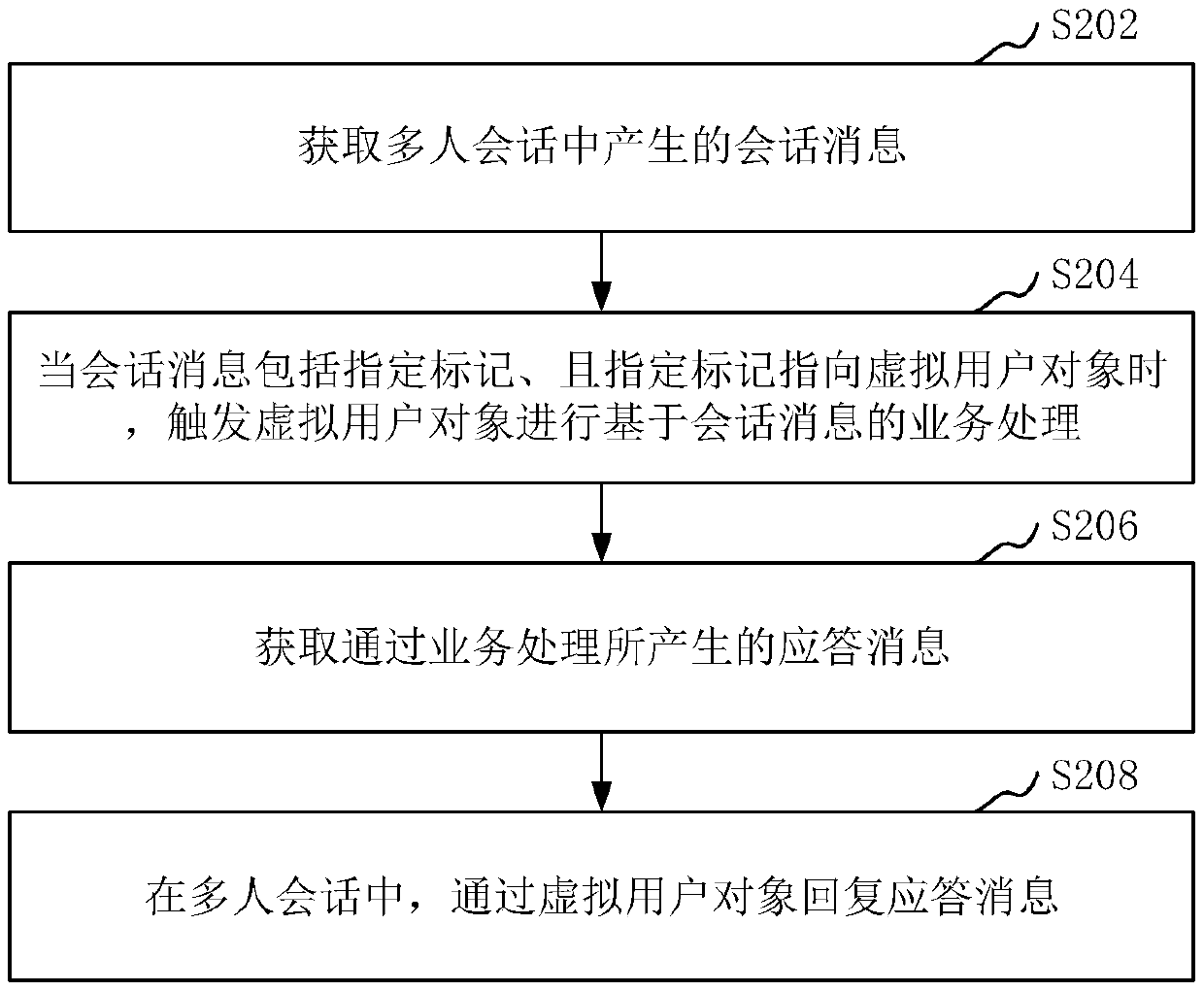
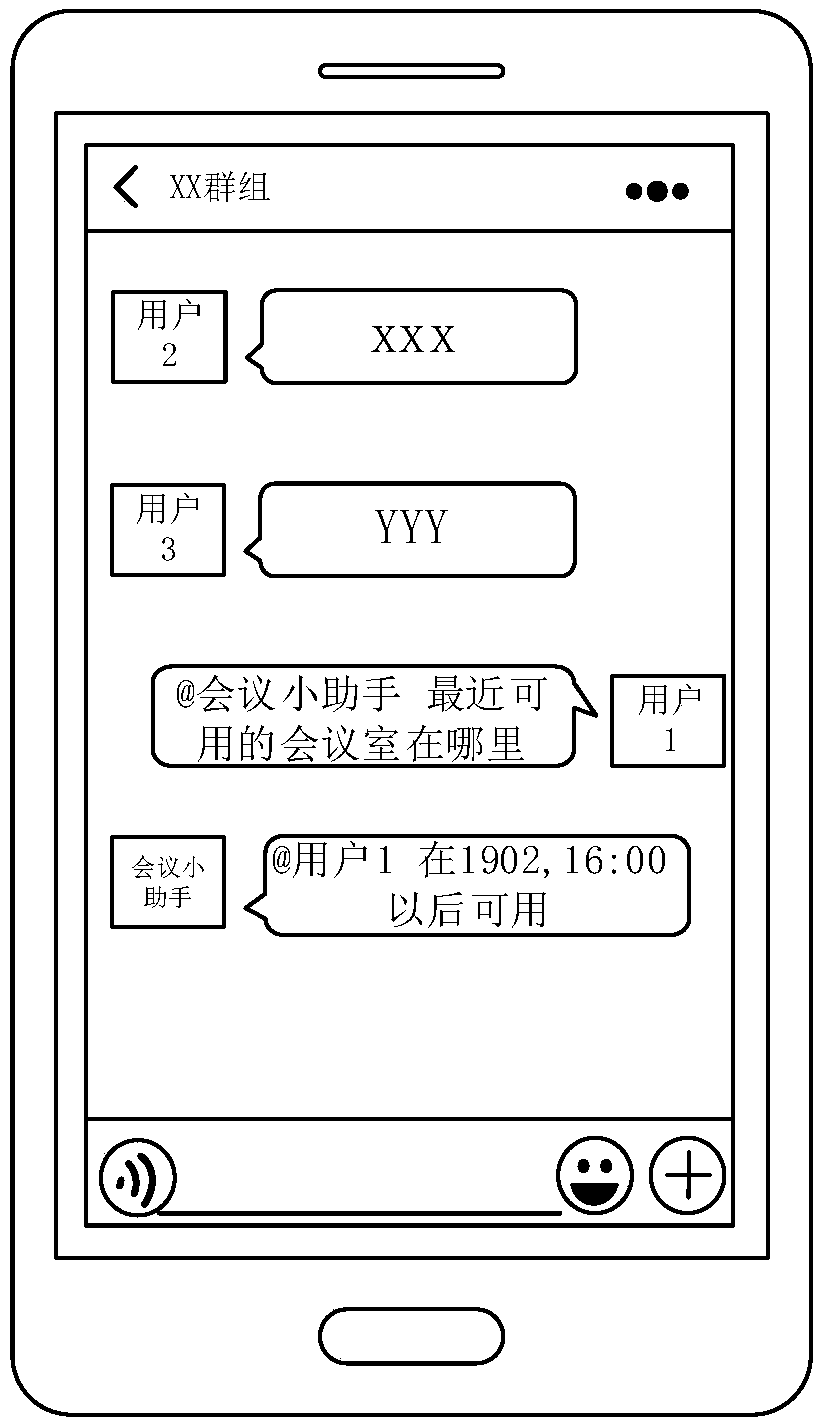
The invention relates to a session message processing method and device, computer readable storage medium and computer equipment. The method comprises the steps of acquiring a session message generated in a multi-user session; when the session message comprises a specified mark, and the specified mark points to a virtual user object, triggering the virtual user object to perform business treatmentbased on the session message; acquiring a response message generated via the business treatment; and in the multi-user session, replying to the response message via the virtual user object. Accordingto the scheme provided by the invention, the flexibility of interaction with the virtual user object can be improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
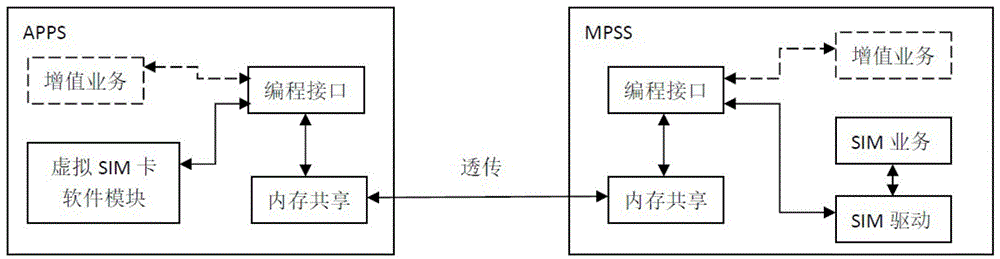
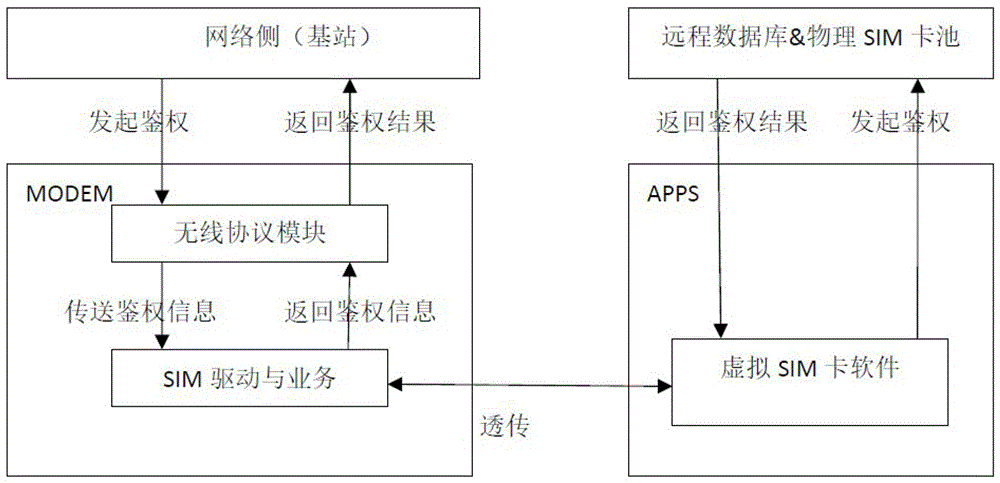
Virtual SIM card system and method of using virtual SIM card by mobile terminal
ActiveCN106851617AImprove securityReduce development and maintenance costsSecurity arrangementNetwork data managementSoftwareComputer hardware
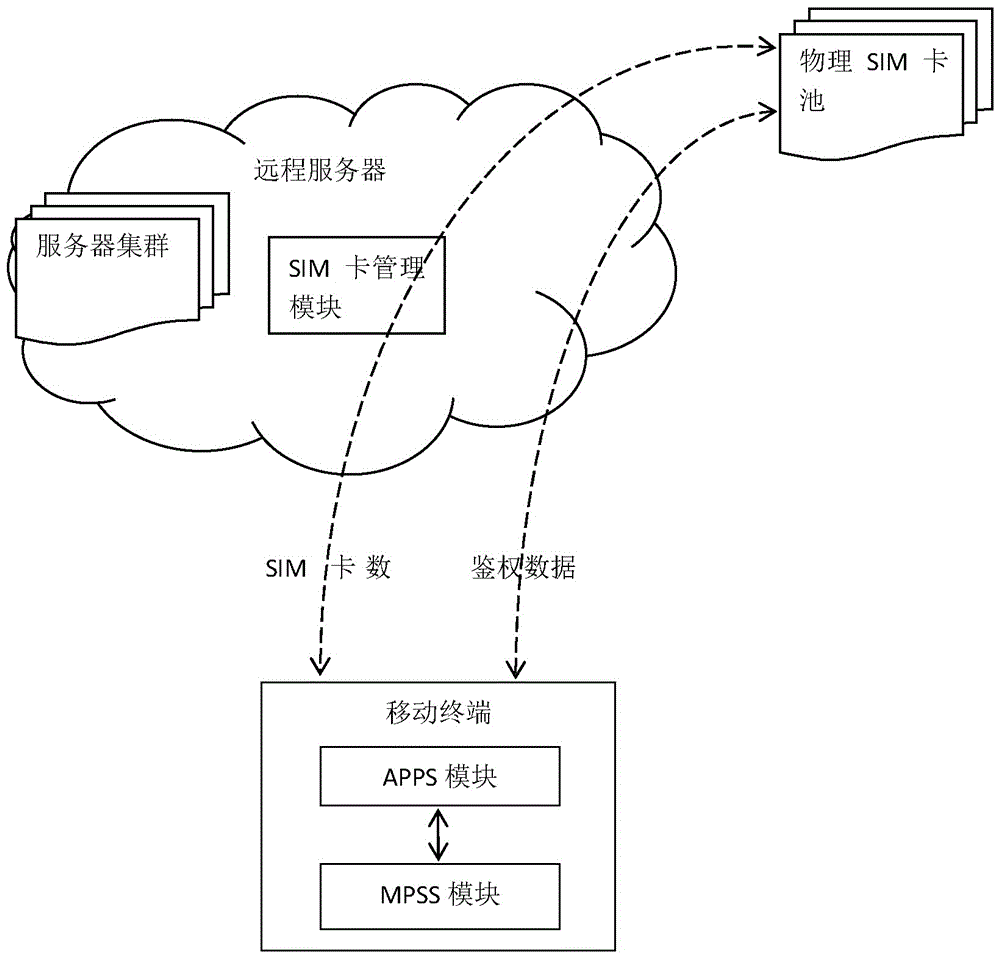
The invention discloses a virtual SIM card system and a method of using a virtual SIM card by a mobile terminal. The virtual SIM card system comprises a physical SIM card pool, and an SIM card management module for managing and distributing physical SIM card information. The mobile terminal which communicates with the SIM card management module comprises a high-pass LTE chip with double communication channels and a global roaming card for reporting the current position to the SIM card management module through one communication channel; an APPS module of the high-pass LTE chip receives the information of corresponding physical SIM card through the other communication channel, obtain authentication data from the corresponding physical SIM card through the SIM card management module and then transmits the authentication data to the MPSS module of the high-pass LTE chip in an unvarnished transmission manner; and the MPSS module communicates with the base station at the currently located position to finish functions of the corresponding physical SIM card. Through a software number reading method, corresponding virtual SIM cards are provided for users without depending on hardware, and the cost is saved.
Owner:SHENZHEN DIMIOR TECH CO LTD
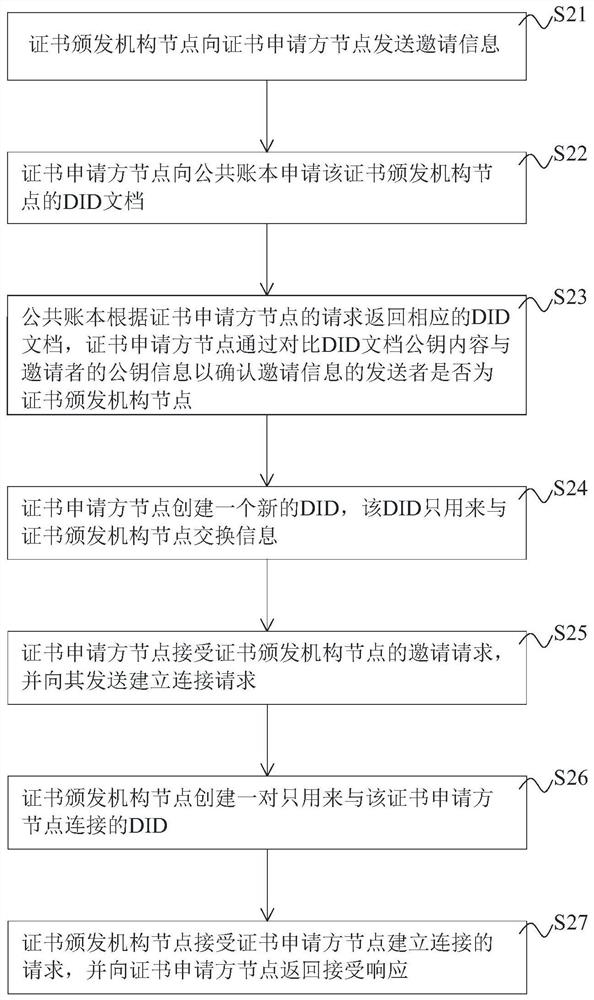
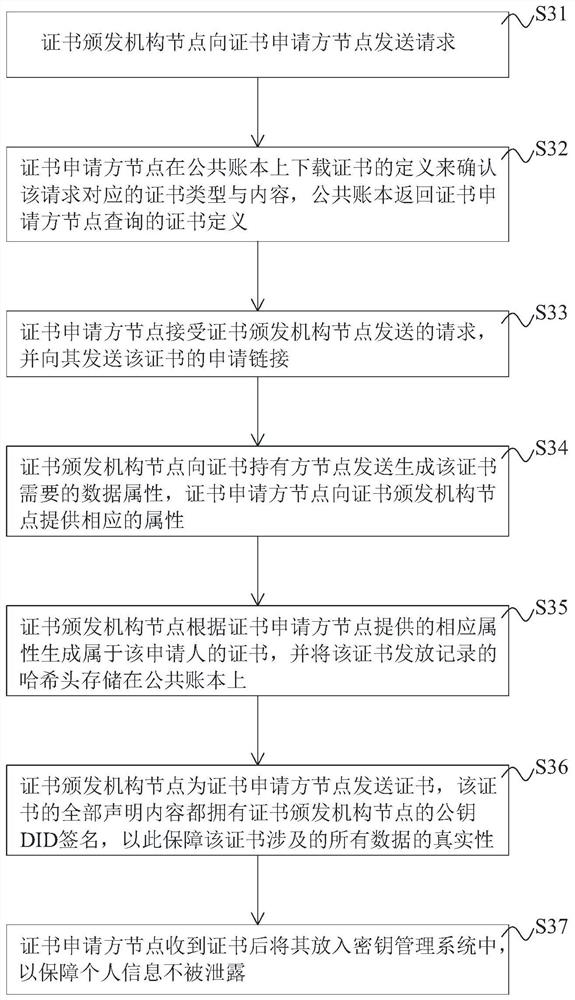
Digital certificate management method and system based on block chain, equipment and storage medium
ActiveCN113014392ARaise the barSolve forgeryEncryption apparatus with shift registers/memoriesUser identity/authority verificationSecure communicationGeneration process
The invention discloses a digital certificate management method and system based on a block chain, equipment and a storage medium, in the method, a certificate template can be issued only after passing through a registration program, strict management and control are carried out from the root of certificate issuing, the certificate template and a sending record of each certificate can be traced, and the problem of certificate counterfeiting is thoroughly solved, the certificate inspection cost can be reduced, and the certificate inspection efficiency is improved. Before a certificate is issued and verified, a secure connection needs to be established between an applicant and an issuer and between a holder and a verifier, and the adopted DID technology provides a basis for secure communication and increases the security of certificate transmission. Besides, the certificate verifier can complete validity verification of the certificate based on the verifiable declaration provided by the holder, and the generation process of the verifiable declaration is combined with cryptographic technologies such as zero-knowledge proof and Merkel tree to selectively disclose certificate attributes, so that the privacy of the certificate holder can be ensured not to be leaked, and the security is improved.
Owner:HUNAN UNIV
Storage method, restoration method and operation method of ordered and derivable large-data files
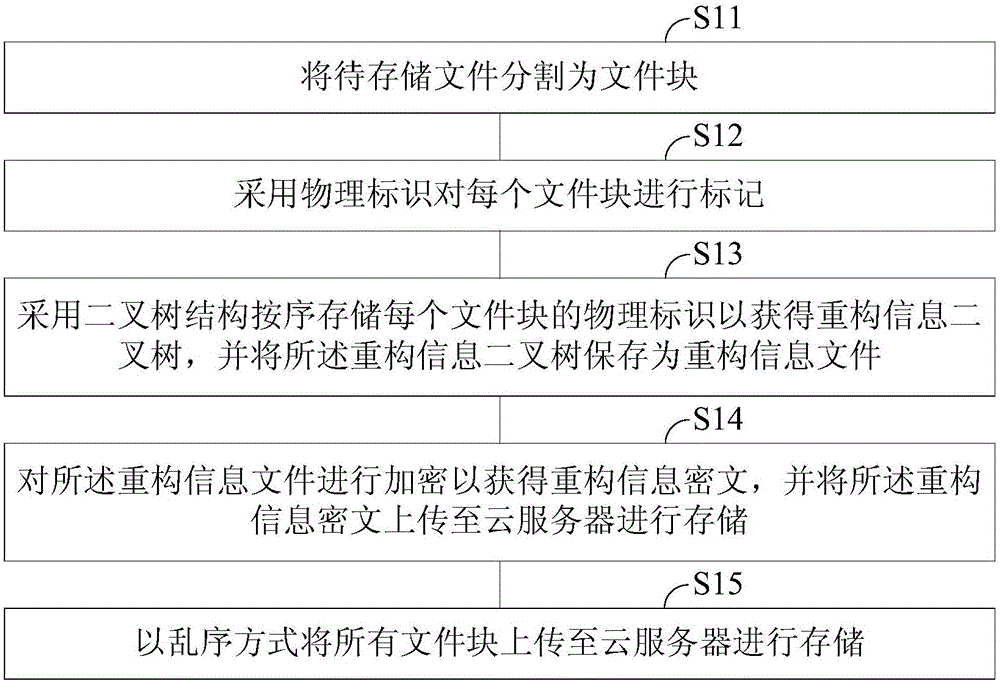
ActiveCN105760781AGuaranteed not to be leakedImprove data processing efficiencyDigital data protectionTransmissionRestoration methodCiphertext
The invention discloses a storage method, a restoration method and an operation method of ordered and derivable large-data files. The storage method comprises the following steps: segmenting the files to be stored into file blocks; marking each file block by adopting a physical identifier; storing the physical identifier of each file block in order by adopting a binary tree structure so as to obtain a reconstructed information binary tree, and storing the reconstructed information binary tree as a reconstructed information file; encrypting the reconstructed information file so as to obtain reconstructed information ciphertext and uploading the reconstructed information ciphertext to a cloud server for storage; and uploading all the file blocks to the cloud server for storage in a disordered manner. According to the storage method, the restoration method and the operation method disclosed by the invention, no leakage of privacy information hidden in the ordered and derivable large-data files is guaranteed, and all data in the ordered and derivable large-data files does not need to be encrypted.
Owner:SICHUAN NORMAL UNIVERSITY
Online banking transaction method, device and system, and mobile terminal
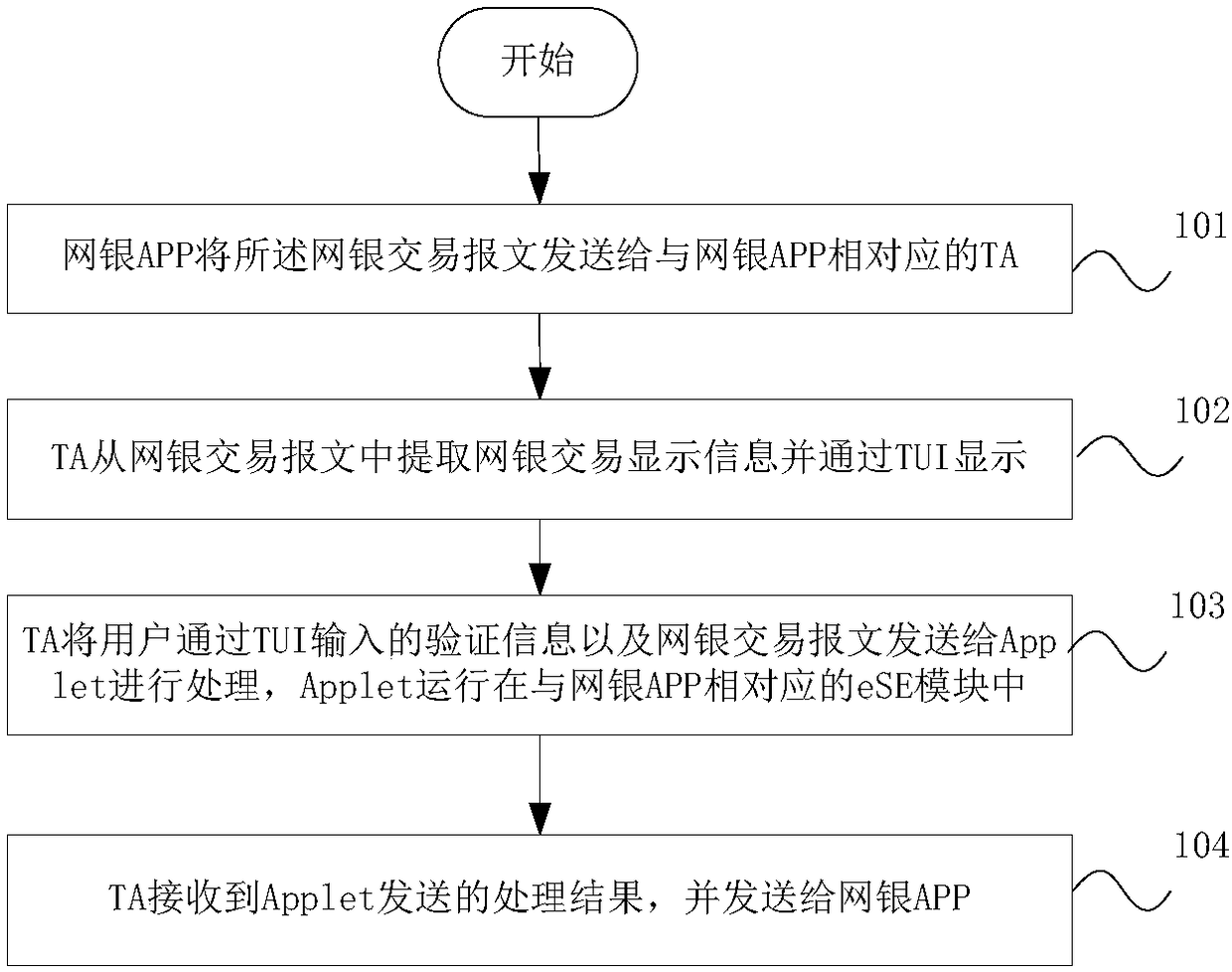
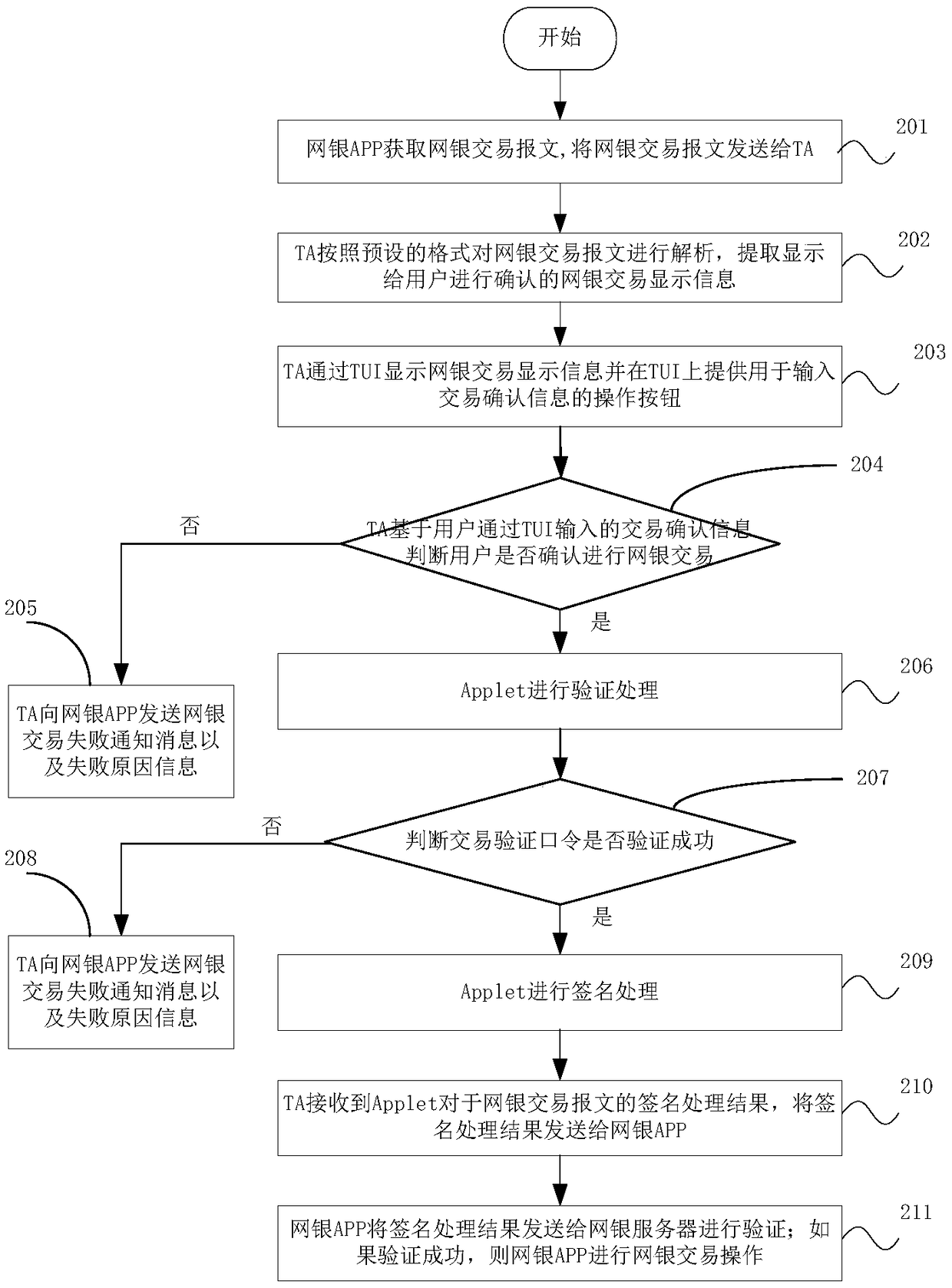
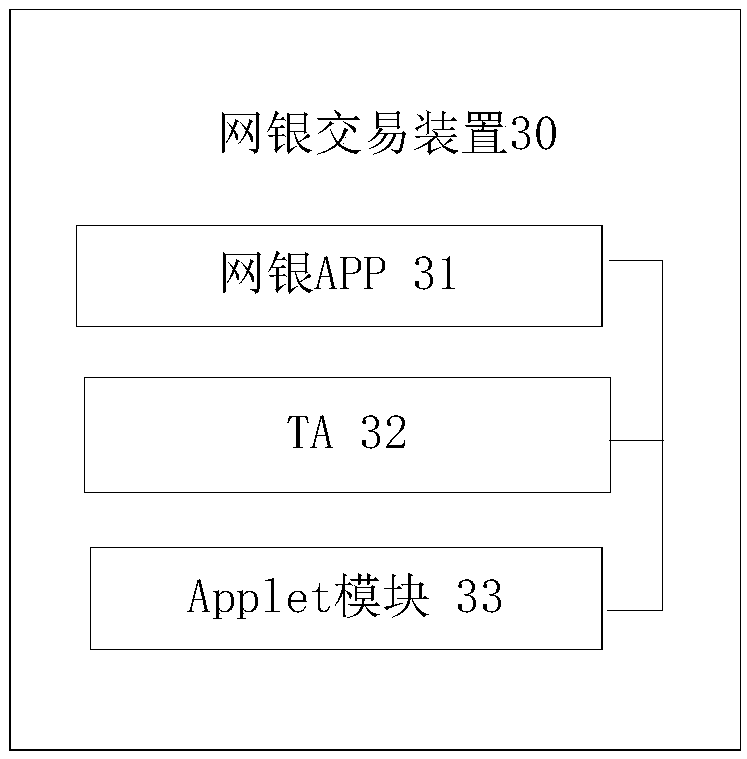
InactiveCN108229956AGuaranteed not to be leakedGuaranteed correctnessProtocol authorisationPasswordUser interface
The embodiment of the invention discloses an online banking transaction method, device and system, and a mobile terminal. The method comprises the following steps that: an online banking APP (Application) sends an online banking transaction message to a corresponding TA (Trusted Application); the TA extracts online banking transaction display information from the online banking transaction message, and the online banking transaction display information is displayed through a TUI (Trusted User Interface); and the TA sends verification information input through the TUI and the online banking transaction message to Applet in an SE (Safety Element) module to be processed, and the TA sends a processing result to the online banking APP. By use of the method, the device, the system and the mobileterminal, the user can confirm transaction information in the trusted UI environment, and the correctness of transaction information can be guaranteed; a password is input in the trusted UI environment, and the password can prevent from being leaked; the user can identify the authenticity of the trusted UI environment through reserved information; and the storage and the use of a private key arerestricted in the SE, the private key can prevent from being leaked, and online banking transaction safety is guaranteed.
Owner:WATCHDATA SYST +1
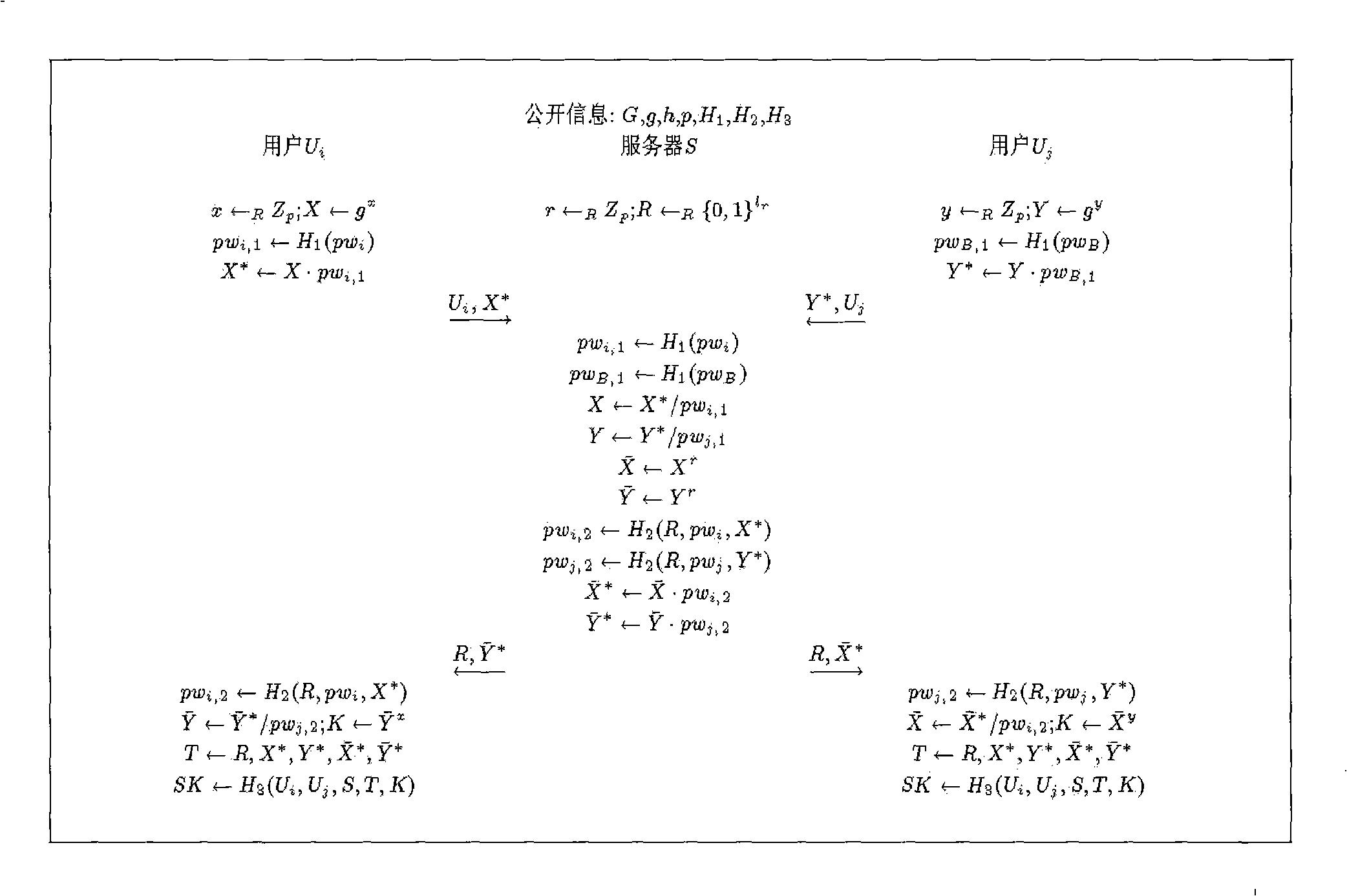
Method for switching three-partner key with privacy protection based on password authentication
InactiveCN101282216AGuaranteed not to be leakedEffective protectionUser identity/authority verificationClient-sidePrivacy protection
The present invention relates to an authenticated key exchange technique, and discloses a three-party password-based authenticated key exchange method which is provided with a privacy protection. The method comprises the following steps: an initialization step, exchanging the reserved information by two client subscribers which prepare to do key exchange; a client initialization stage, ciphering the information respectively by two client subscribers which prepare to do key exchange with the respective passwords and sharing passwords in the server and transmitting to the server together with the non-ciphered information; a server procession stage, when the server receives the request information from the client, using an oblivious transfer mechanism for processing these information and generating different returning information aiming at each one in two client subscribers, and then respectively transmitting these information to corresponding client subscriber; a client authorization step, when the client receives the returning information of the server, adopting a mechanism of normal key exchange for processing the returned information based on the password itself in order to generate the seed of the conversation key, and generating the authorization information with the seed of the conversation key for transmitting to the subscriber of the other side; and a conversation key generating step, if the authorization information from the subscriber of the other side is authorized, generating the conversation key with the seed of the conversation key. Compared with prior art, the plan not only realizes the three-party password-based authenticated key exchange, but also simultaneously and effectively protects the privacy information comprising identity and participation action of the client subscriber which participates the key exchange.
Owner:INST OF INFORMATION ENG CAS
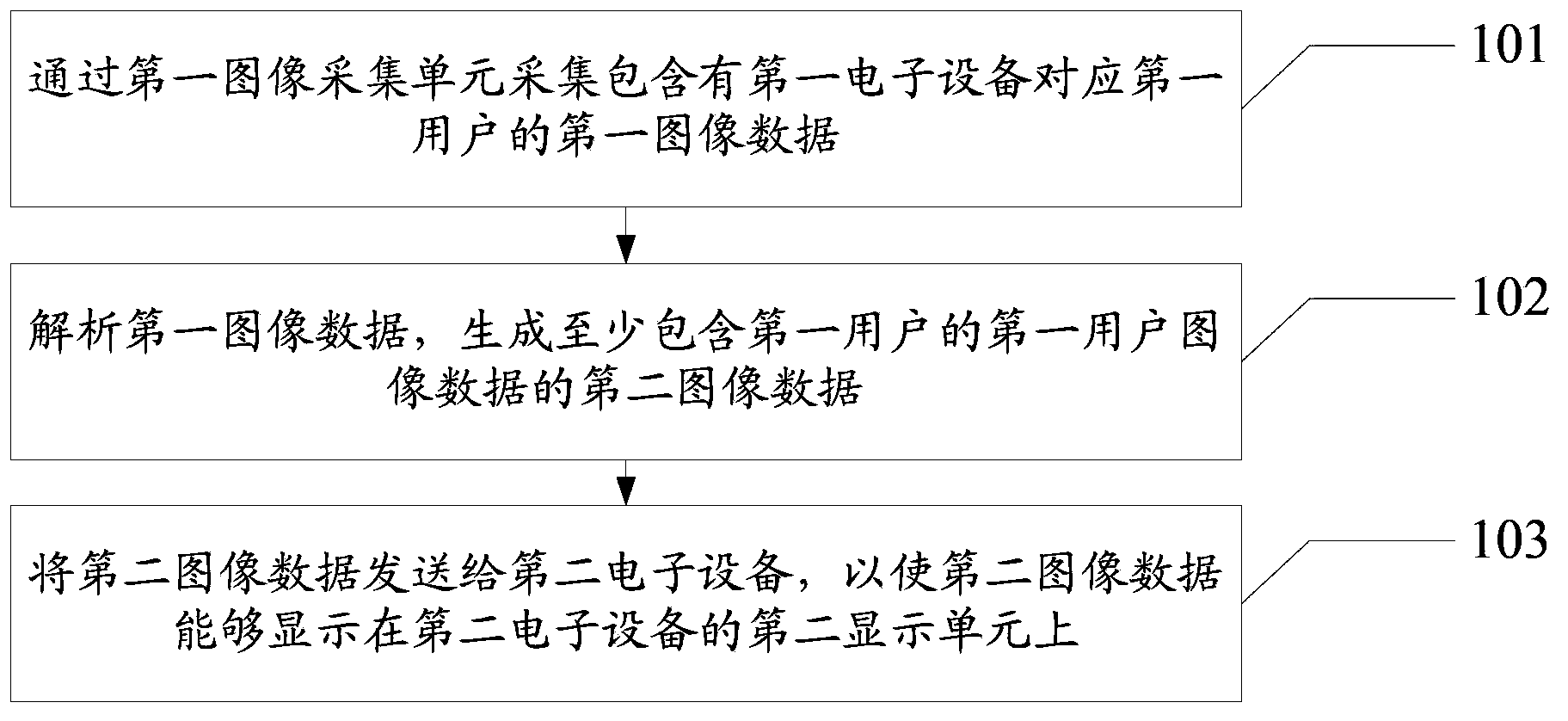
Information processing method and electronic equipment
ActiveCN104079860AReduce data volumeFast data transferTwo-way working systemsSelective content distributionInformation processingInteraction device
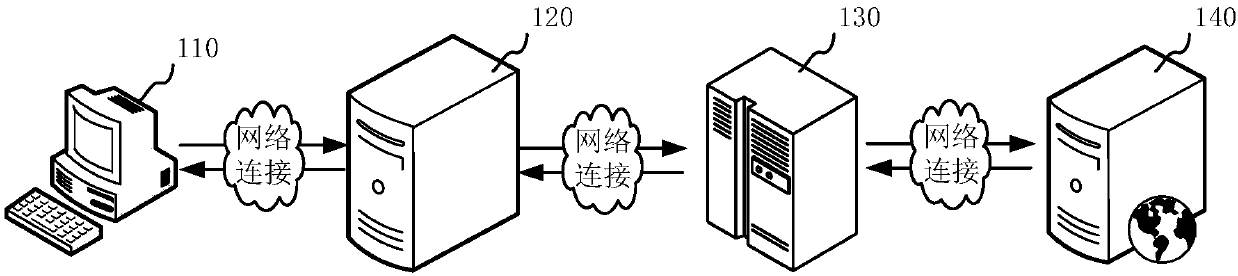
An embodiment of the invention provides an information processing method and electronic equipment. The information processing method comprises the following steps of: collecting first image data including a first user corresponding to first electronic equipment, analyzing the first image data, generating second image data at least including first user image data of the first user, wherein the data size of the second image data is smaller than the data size of the first image data, and transmitting the second image data to second electronic equipment so as to display the second image data to a second display unit of the second electronic equipment. According to the information processing method and the electronic equipment, the technical problem of slower data transmission speed caused by occupation of more network bandwidths by the data due to larger data size transmission between interactive devices in the prior art can be solved.
Owner:LENOVO (BEIJING) LTD
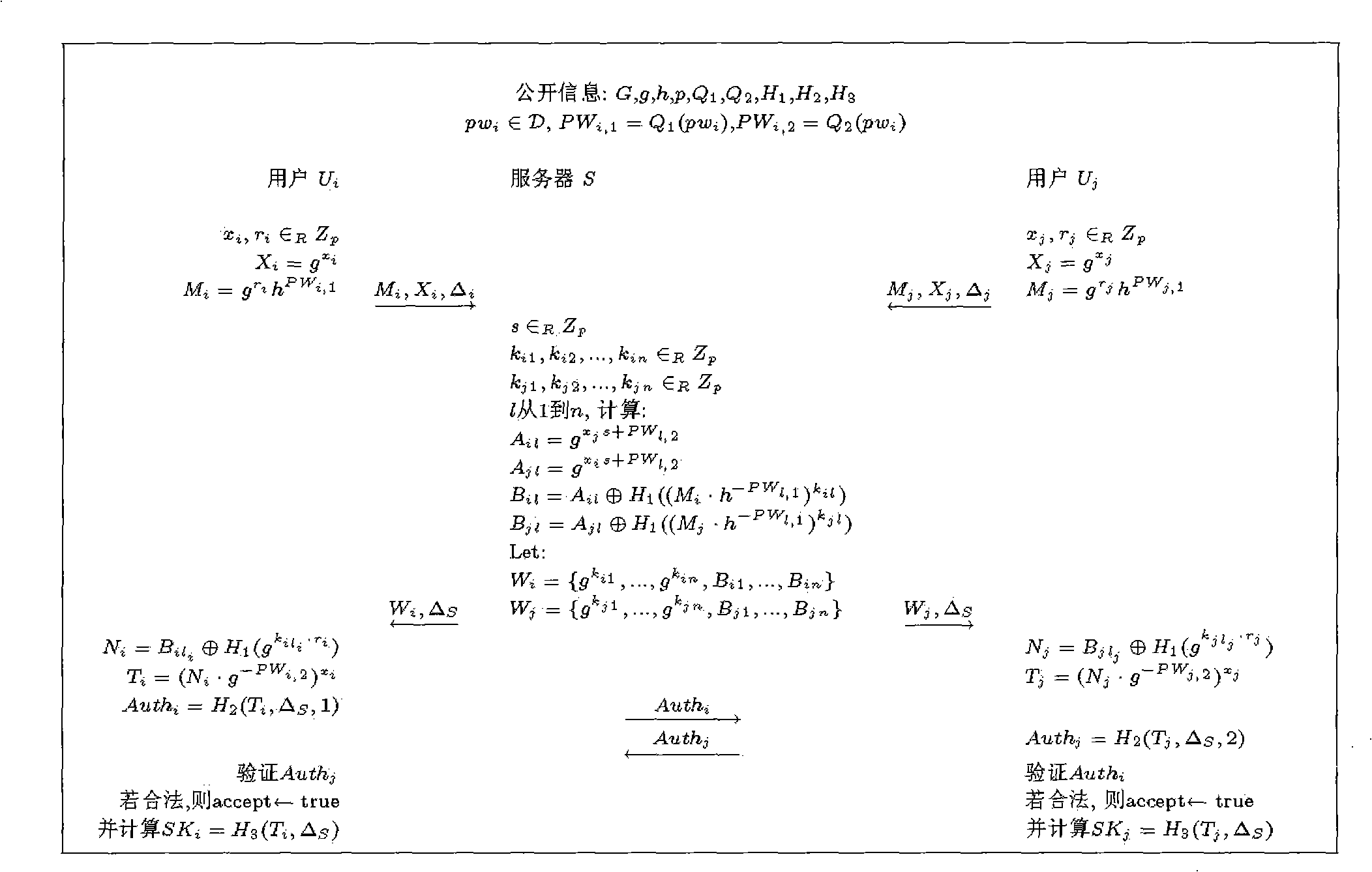
Multi-party secret handshaking method in short key environment
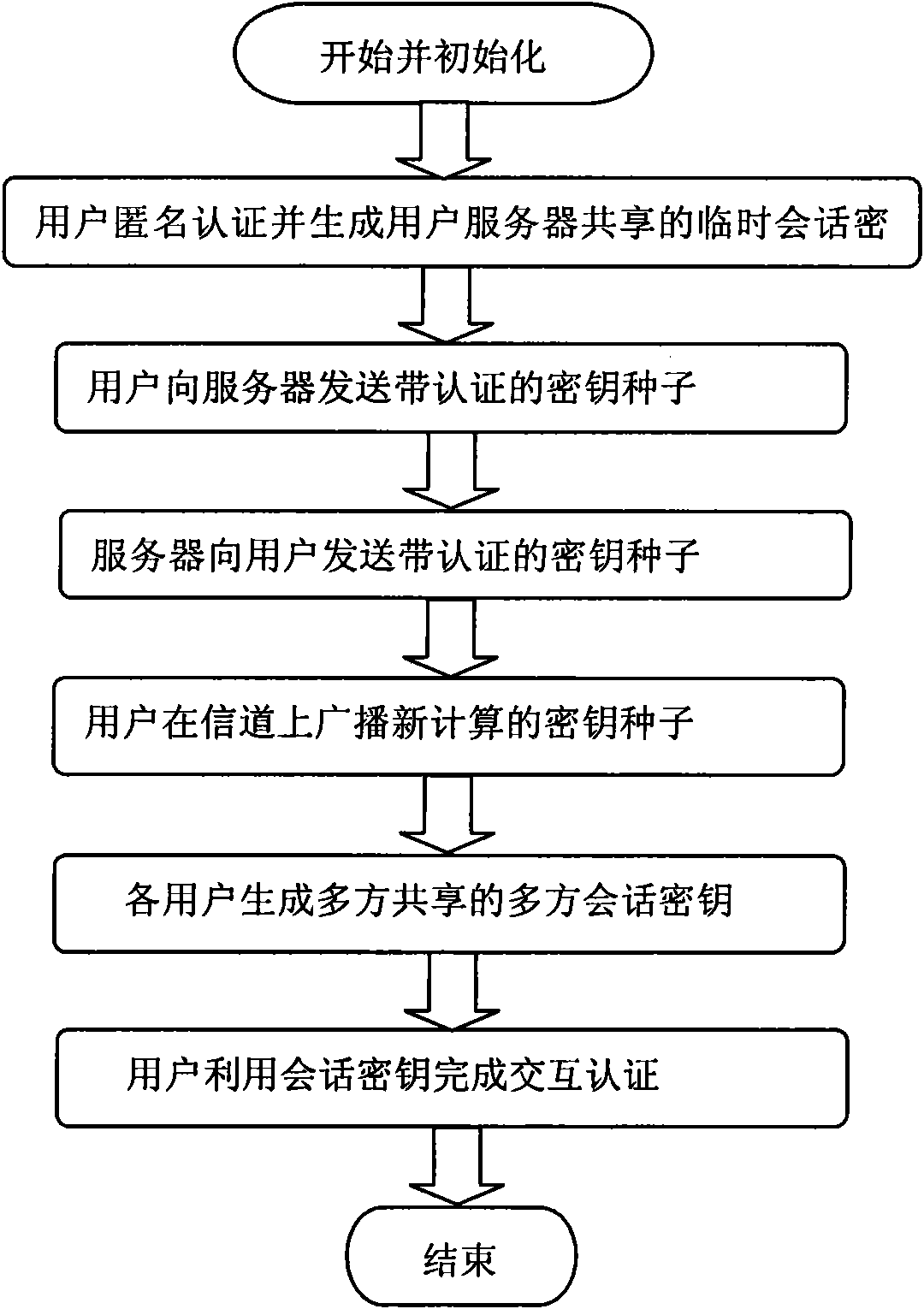
InactiveCN101908961AImplementation is not leakedGuaranteed not to be leakedUser identity/authority verificationKey exchangeUser privacy
The invention provides a multi-party secret handshaking method in short key environment, which belongs to the field of information security cryptology. The method comprises the following steps: (1) starting and initializing; (2) a user anonymously authenticates and generates a temporary conversation key shared with a server; (3) the user transmits a key seed with authentication to the server; (4) the server transmits a key seed with authentication to the user; (5) the user broadcasts a newly calculated key seed on the channel; (6) the users generate a multi-party shared conversation key; and (7) the users complete the interactive authentication by utilizing the conversation key. The method overcomes the defect that the prior multi-party secret handshaking method is dependent on the basic facilities of the public key, and the defect that the prior key exchanging method based on short key authentication can not effectively protect the privacy of the participating users. The invention realizes multi-party secret handshaking, effectively protects the privacy information, including identity and participation behavior of the participating users, and also realizes secure key exchange based on short key.
Owner:BEIJING JIAOTONG UNIV
Enhanced mixed physical isolation method
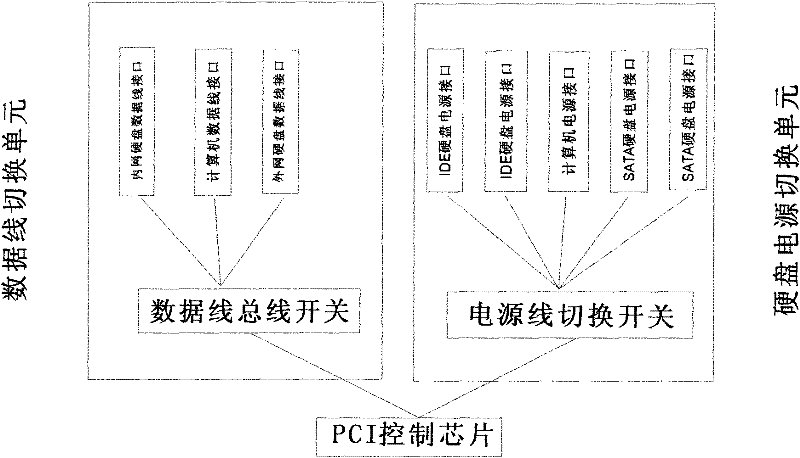
The invention relates to a network isolation method for a peripheral component interconnect (PCI) bus of a computer, which is implemented by a PCI bus interface, a PCI control chip, a network switching unit and a hard disk switching unit. By adopting a mode of bus control, a control signal on the PCI bus is read by a CH364P chip, physical isolation of internal and external networks can be realized by a computer user only using a physical isolation card and hard disk memory equipment, and the user can connect only a set of network within same time, so that the different networks cannot be interconnected, the physical isolation of the networks is realized finally, danger brought by attacks among the networks is avoided effectively, and the safety of the networks is ensured.
Owner:张建华 +2
Method and system for preventing information leakage in smart home
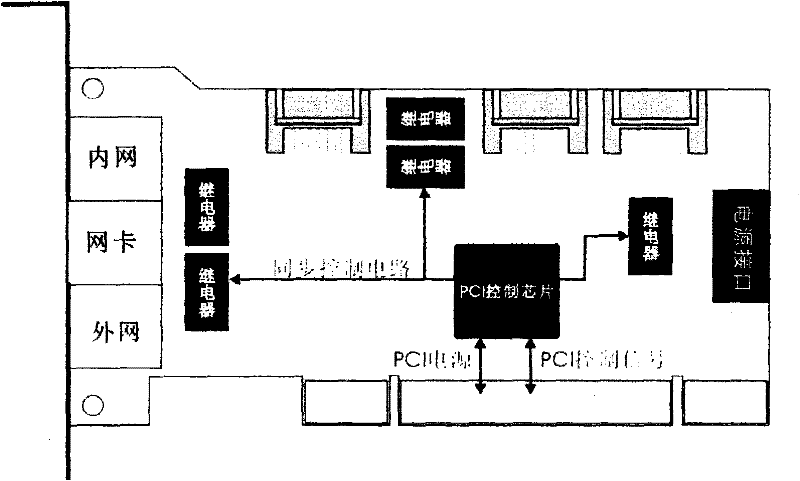
ActiveCN106789378AGuaranteed not to be leakedEnsure safetyHome automation networksInformation transmissionAmbient data
The invention relates to a method for preventing information leakage in smart home. The method comprises the following steps of (S1) configuring a custom information transmission protocol among smart home equipment, a server and a user terminal; (S2) dividing a data storage area special for storing various data acquired during an operation process of various smart home equipment in the server; carrying out hardware encryption on the data storage area; storing unique identification numbers of the smart home equipment and the user terminal in the server; (S3) carrying out type division on various smart home data acquired during the operation process of various smart home equipment, wherein the smart home data comprises environment data, behavior data, user state data, and smart home equipment operation state data; (S4) carrying out safety degree grading on the smart home data; configuring permission grade information corresponding to different domestic consumers according to different smart home data types.
Owner:山西君和科技有限公司
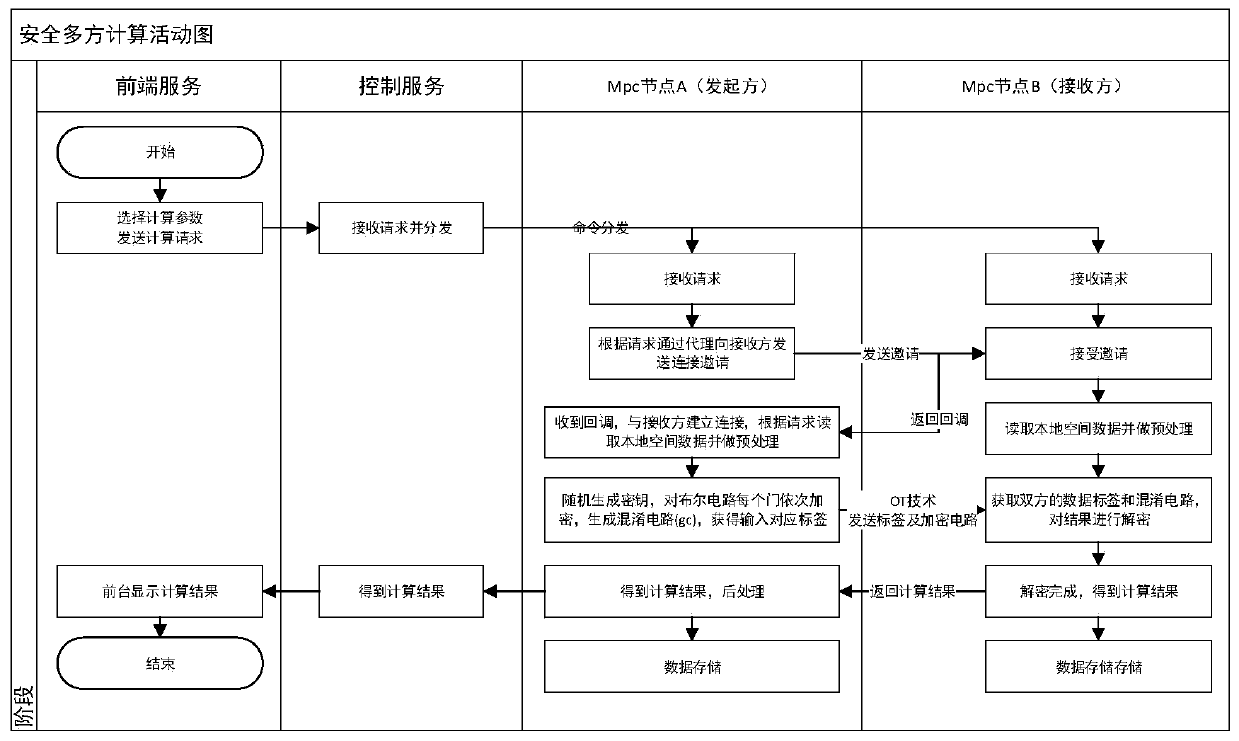
Implementation method of geographic weighted average center based on secure multi-party computation
ActiveCN110166446ATroubleshoot leak-prone technical issuesGuaranteed not to be leakedTransmissionNODALSecure multi-party computation
The invention discloses an implementation method of geographic weighted average center based on secure multi-party computation, which comprises the following steps: splitting a realized algorithm, taking a part which can be locally processed as a preprocessing part, and taking a part which needs to be interactively computed by two parties as an MPC computing part; designing a metadata table and anode information table; and realizing a data preprocessing step in the java program; firstly locally processing respective data according to needs by two computation parties to obtain weighted sums ofX coordinates and Y coordinates of local elements, namely Xa, Ya, Xb and Yb; calculating the weight sum and recording the weight sum as Na and Nb; and initiating MPC calculation by the initiator A torealize the following algorithms: X = Xa + Xb, Y = Ya + Yb and N = Na + Nb, and obtaining the result and sharing and performing post-processing by the two parties. And in the process, the double-transmission data are not leaked, so that the privacy of the data is effectively protected.
Owner:JUZIX TECH SHENZHEN CO LTD +1
Switching median filtering based encrypted image denoising method
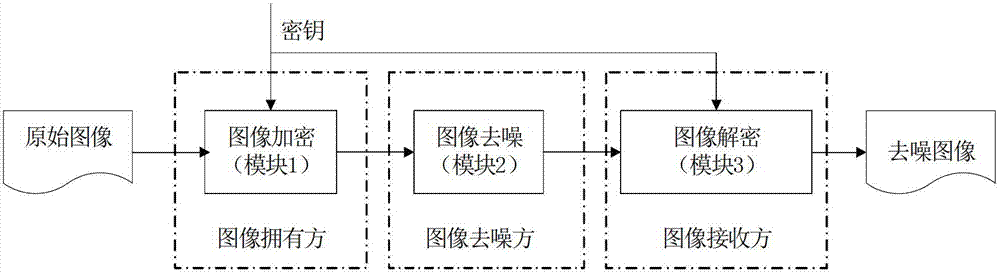
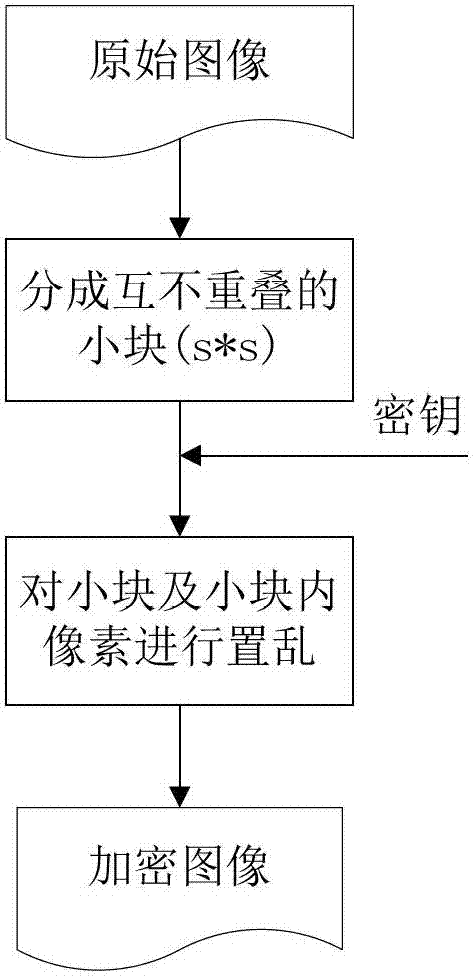
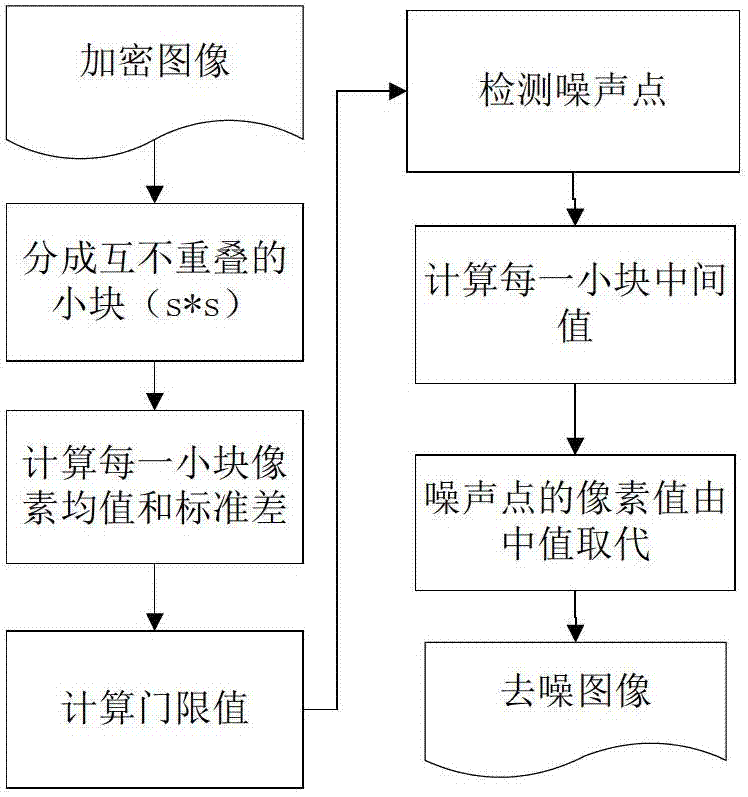
InactiveCN102903082AQuality improvementGuaranteed not to be leakedImage enhancementUser identity/authority verificationImage denoisingPattern recognition
The invention discloses a switching median filtering based encrypted image denoising method, which belongs to the field of multimedia information security and image processing. The method involves an image owning party, an image denoising party and an image receiving party, the image owning party has a noisy image, and hopes to denoise the image by the image denoising party and then transmit the image to the image receiving party, but because the image owning party distrusts the image denoising party, after the image is encrypted, the image owning party transmits the image with covered contents to the image denoising party to process. The method comprises the following steps: firstly, carrying out encryption on the image by using a particular image encryption method, and due to the particularity of the encrypted image, carrying out denoising processing on the image by using a non-traversing switching median filtering; firstly, dividing the image into blocks, and finding the mean value, standard deviation and mid-value of each block; then, obtaining a threshold according to the standard deviation, and determining a noise point; and finally, replacing the pixel value of the noise point with the mid-value. The method disclosed by the invention not only effectively realizes the image denoising, but also protects the information security of images.
Owner:CHONGQING UNIV
Fog collaborative cloud data sharing method based on attribute-based encryption
ActiveCN110611662AReduce overheadReduce resource consumptionKey distribution for secure communicationPersonalizationData information
The invention discloses a fog collaborative cloud data sharing method based on attribute-based encryption. The method comprises the following steps: 1, initializing a system; the authorization mechanism generates a system public key, a system master key, a private key of the cloud service provider, a public key of the fog node and a private key of the fog node; 2, performing data encryption; the user encrypts the shared data based on the shared content key and then sends the encrypted shared data to the fog node; 3, performing data preprocessing; the fog node receives ciphertext data transmitted from a user, and outputs a preprocessed classification result and indexes of related data information entries; 4, re-encrypting the data; the fog node operates an algorithm, re-encrypts the shareddata based on a professional access strategy, and encrypts related professional entries corresponding to each piece of data; 5, performing data decryption; as long as the attributes of the cloud service provider can meet personalized and professional access policies, the cloud service provider can decrypt the shared ciphertext. According to the method, professional information classification and effective data analysis of the shared data can be conveniently realized.
Owner:已未来(北京)通信科技有限公司
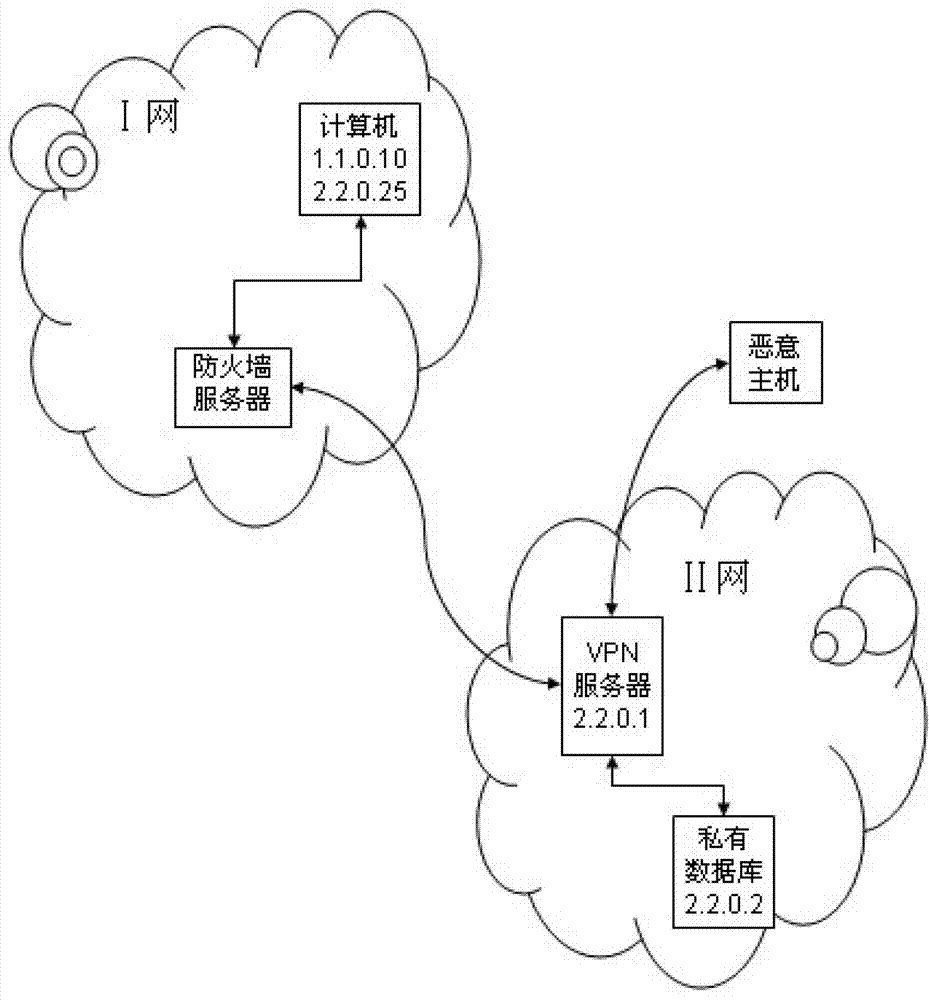
Solution for potential safety hazards in VPN (virtual private network)
ActiveCN102833271AEnsure Security PolicyGuaranteed not to be leakedNetworks interconnectionPlaintextData stream
The invention discloses a solution for potential safety hazards in a VPN (virtual private network), which comprises the following steps that: A, a firewall server detects that whether a ciphertext of packet header information of an encryption part of a data packet in a VPN tunnel is in a black and white list corresponding to a destination IP address in plaintext packet header information thereof; B, if the obtained result in the step A is that the ciphertext is not in the black and white list, the firewall server inquires firewalls according to the destination IP (internet protocol) address so as to obtain eligible FDD (firewall decision diagram) branches; C, the firewall server converts the inquiring results obtained in the step B into an OBDD (ordered binary decision diagram), and saves the OBDD and corresponding inquiring conditions; D, the firewall server encrypts and confuses each node of the OBDD obtained in the step C, and sending the OBDD to a VPN server; E, the VPN server decrypts the received OBDD so as to obtain destination node information, and the ciphertext of an exclusive-or data packet of the information is sent to the firewall server; and F, the firewall server executes a firewall strategy, and adds the ciphertext in the step A into the black and white list corresponding to the destination IP address. The firewall securely executes the firewall strategy for a data stream in the VPN tunnel, and the encrypted data is not leaked.
Owner:GUILIN UNIV OF ELECTRONIC TECH
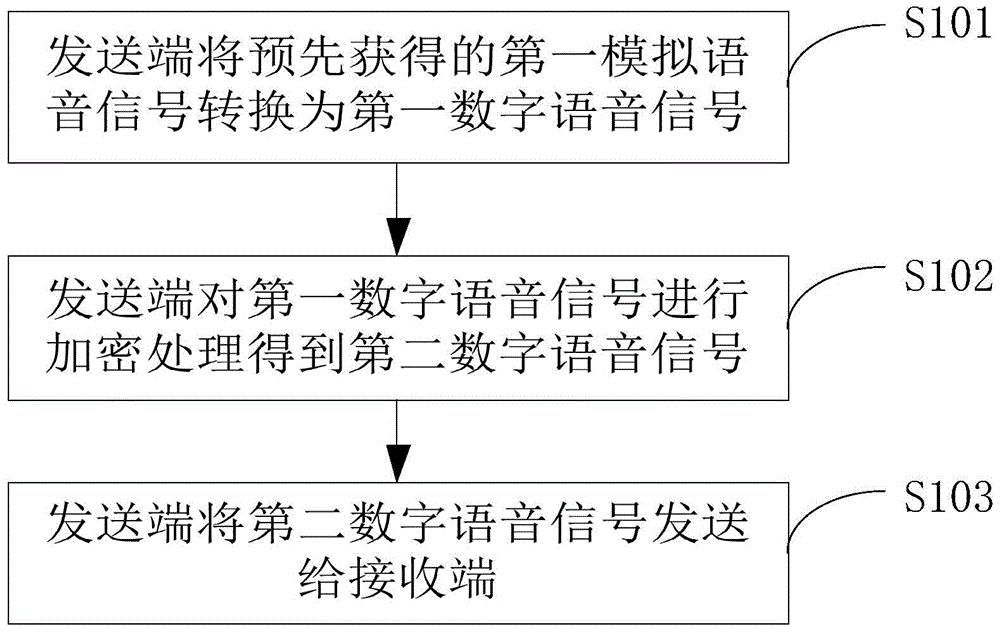
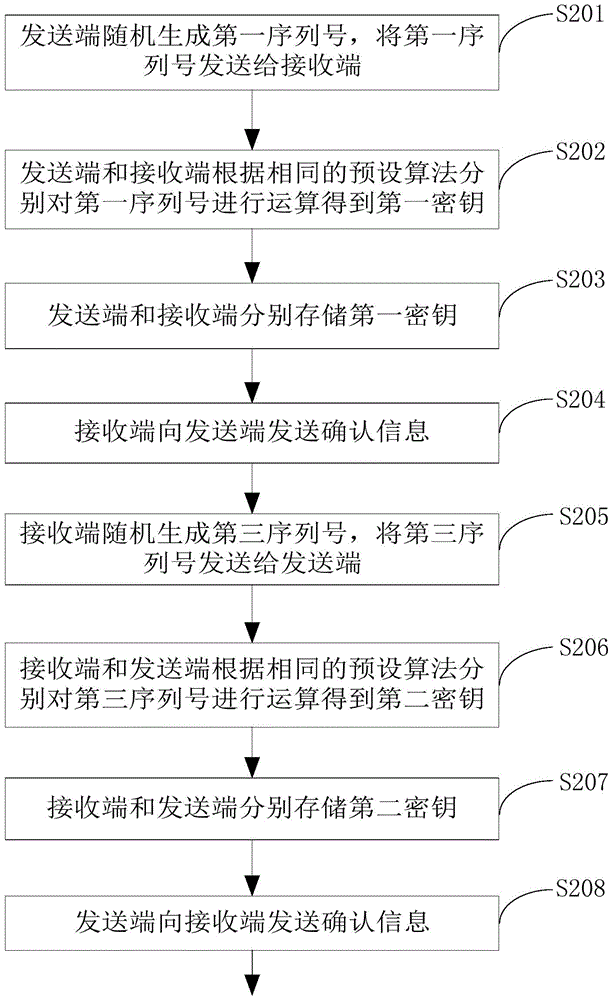
Voice communication method and device
InactiveCN105050082AEnsure safetyGuaranteed not to be leakedTransmissionSecurity arrangementTelecommunicationsVoice communication
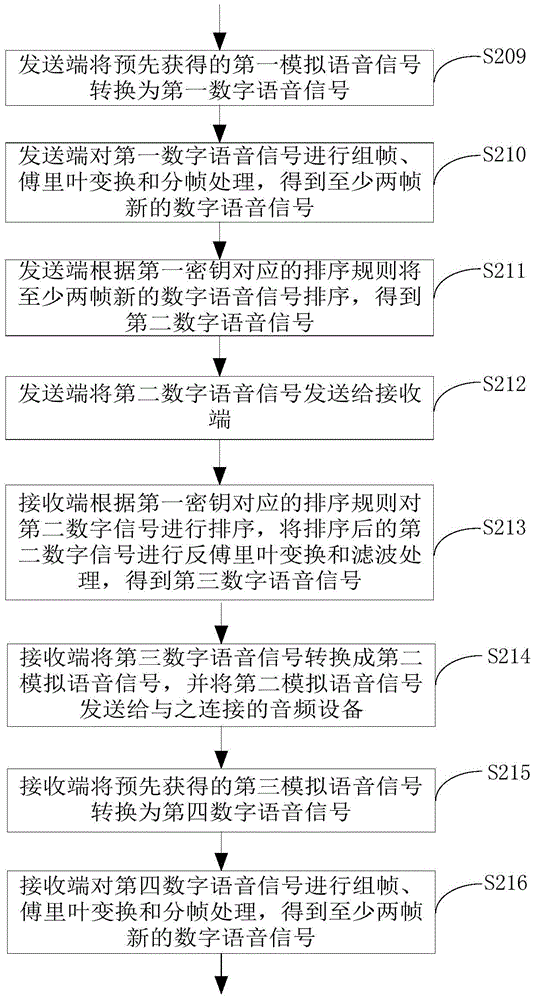
The embodiment of the invention provides a voice communication method and device and belongs to the communication technical field. The voice communication method is applied to the voice communication device. The voice communication device includes a transmitting end and a receiving end; the transmitting end and the receiving end are connected with each other through a communication network; and the transmitting end and the receiving end pre-store first keys. The method includes following steps that: the transmitting end converts first analog voice signals into first digital voice signals and performs encryption processing on the first digital voice signals so as to obtain second digital voice signals; the transmitting end transmits the second digital voice signals to the receiving end; the receiving end performs decryption processing on the second digital voice signals according to the first keys so as to obtain third digital voice signals; and the receiving end converts the third digital voice signals into second analog voice signals. With the voice communication method provided by the invention adopted, the security of voice communication can be effectively ensured, and the data and privacies of users will not leak assuredly.
Owner:CHENGDU HUIYAN TECH CO LTD
Mobile terminal self-destroying method and apparatus as well as mobile terminal
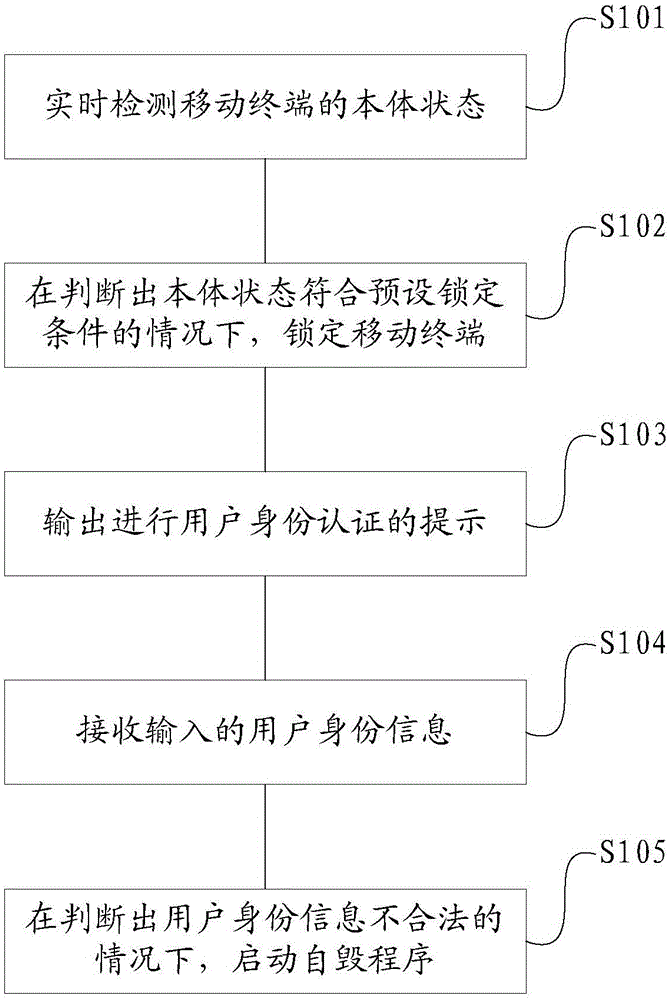
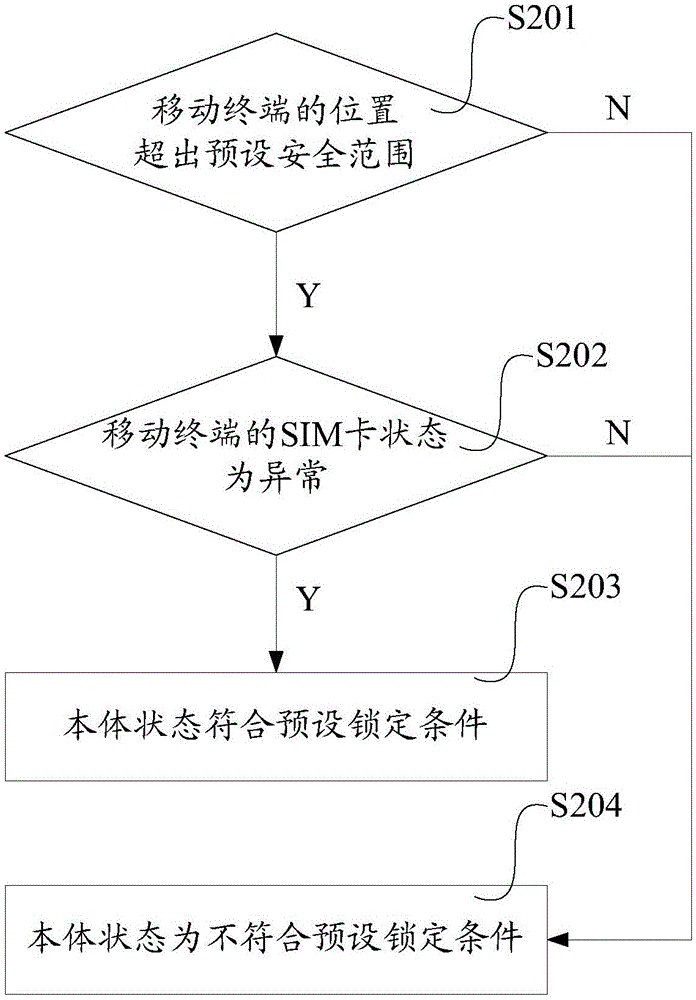
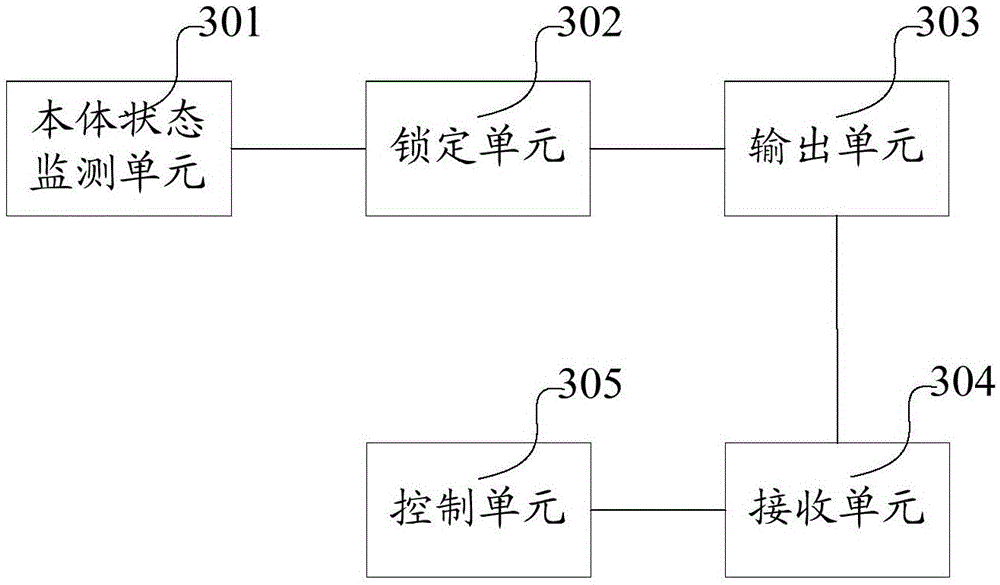
InactiveCN105631351ASelf-destructAvoid reuseDigital data protectionDigital data authenticationComputer scienceAuthentication
The invention provides a mobile terminal self-destroying method and apparatus as well as a mobile terminal. The method comprises the steps of detecting a body state of the mobile terminal in real time; when it is judged that the body state meets a preset locking condition, locking the mobile terminal; outputting a prompt of performing user identity authentication; receiving input user identity information; and when it is judged that the user identity information is illegal, starting a self-destroying program. According to the mobile terminal self-destroying method disclosed by the invention, the key point of triggering a self-destroying program is that the body state meets the locking condition and the user identity information is illegal, and the body state is acquired by the mobile terminal in real time and does not depend on other devices, so that the stability of the method is fully reflected, the method is not influenced by an actual environment, and the self destruction of the mobile terminal can be realized in any condition.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
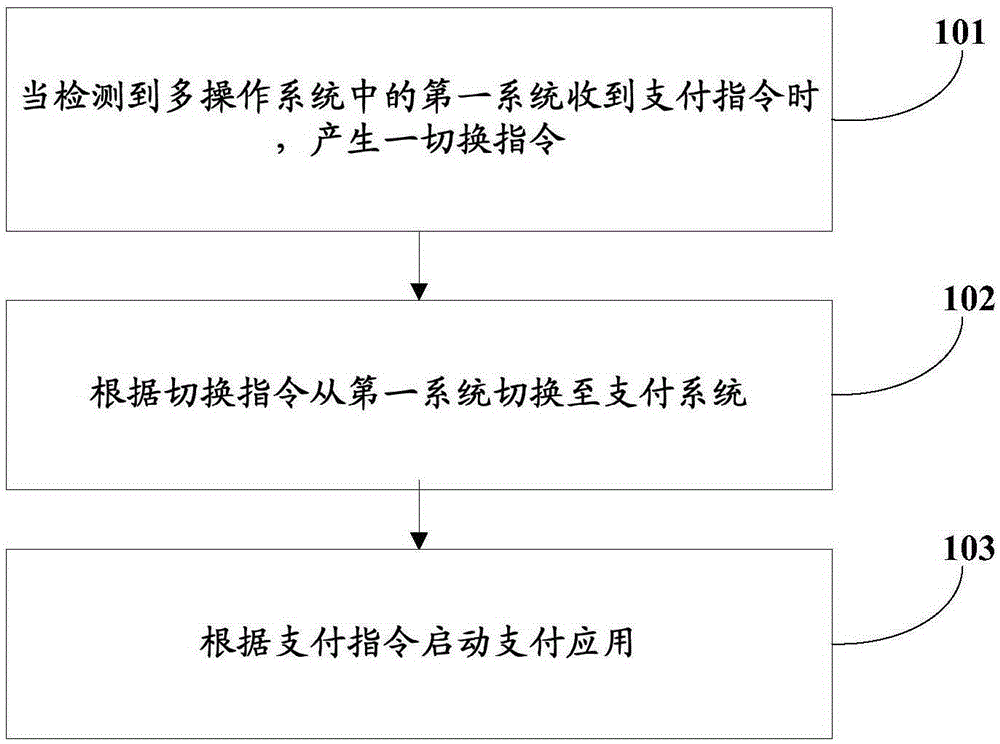
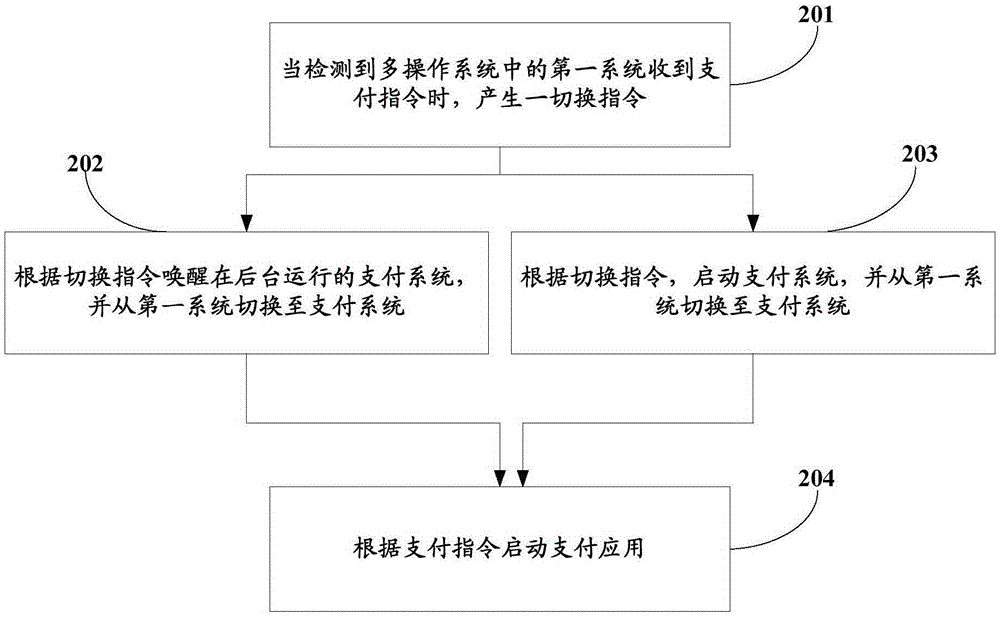
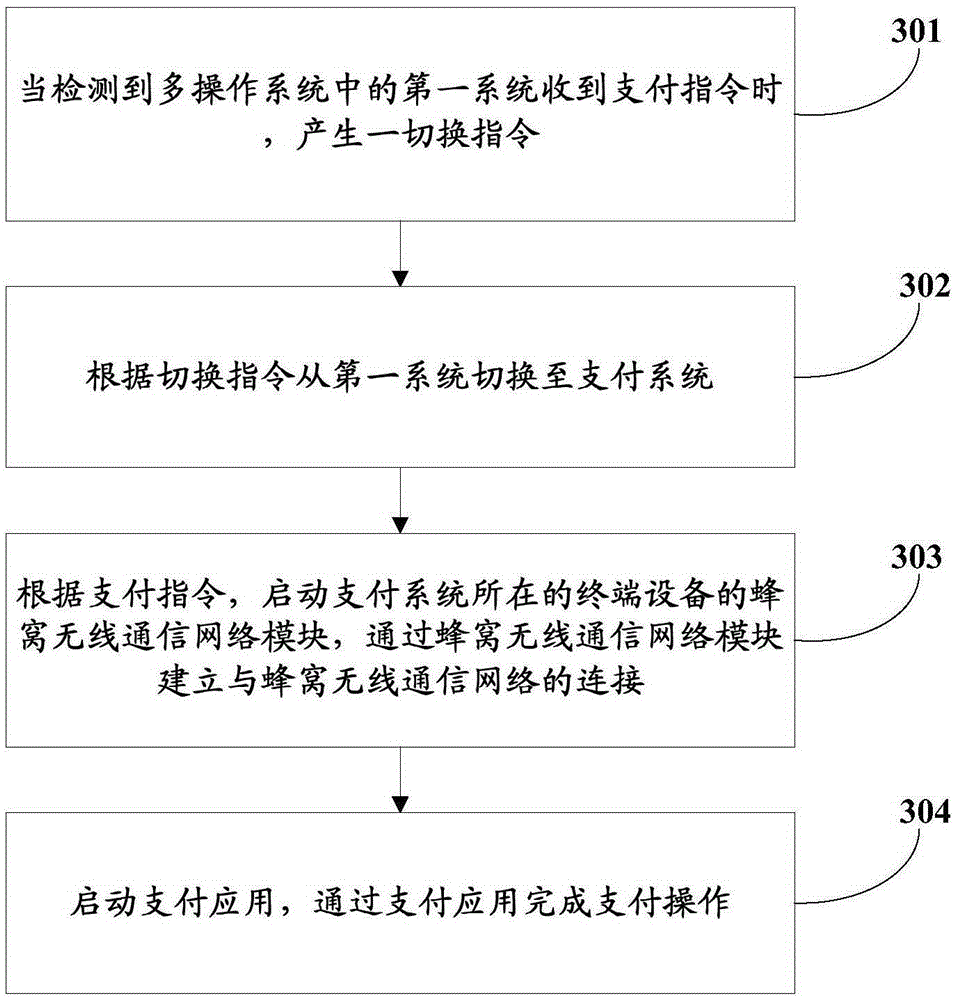
Switching method for multi-operation system and terminal equipment
InactiveCN105825149AProtect private dataImprove securityInternal/peripheral component protectionProtocol authorisationOperational systemTerminal equipment
The invention provides a switching method for a multi-operation system and terminal equipment. A payment system for payment application is installed in the multi-operation system. The switching method comprises the following steps: when detecting that a first system in the multi-operation system receives a payment instruction, generating a switching instruction; switching to the payment system from the first system according to the switching instruction; starting the payment application according to the payment instruction. As payment service is defined to be implemented in the payment system in which the payment application is installed, and the payment service cannot be implemented in other operation systems, the problem of payment security in the prior art can be greatly solved for a user, private data of the user can be protected while the user experience is not degraded, the risk that money of the user is stolen is reduced, and the security of the payment system is improved.
Owner:VIVO MOBILE COMM CO LTD
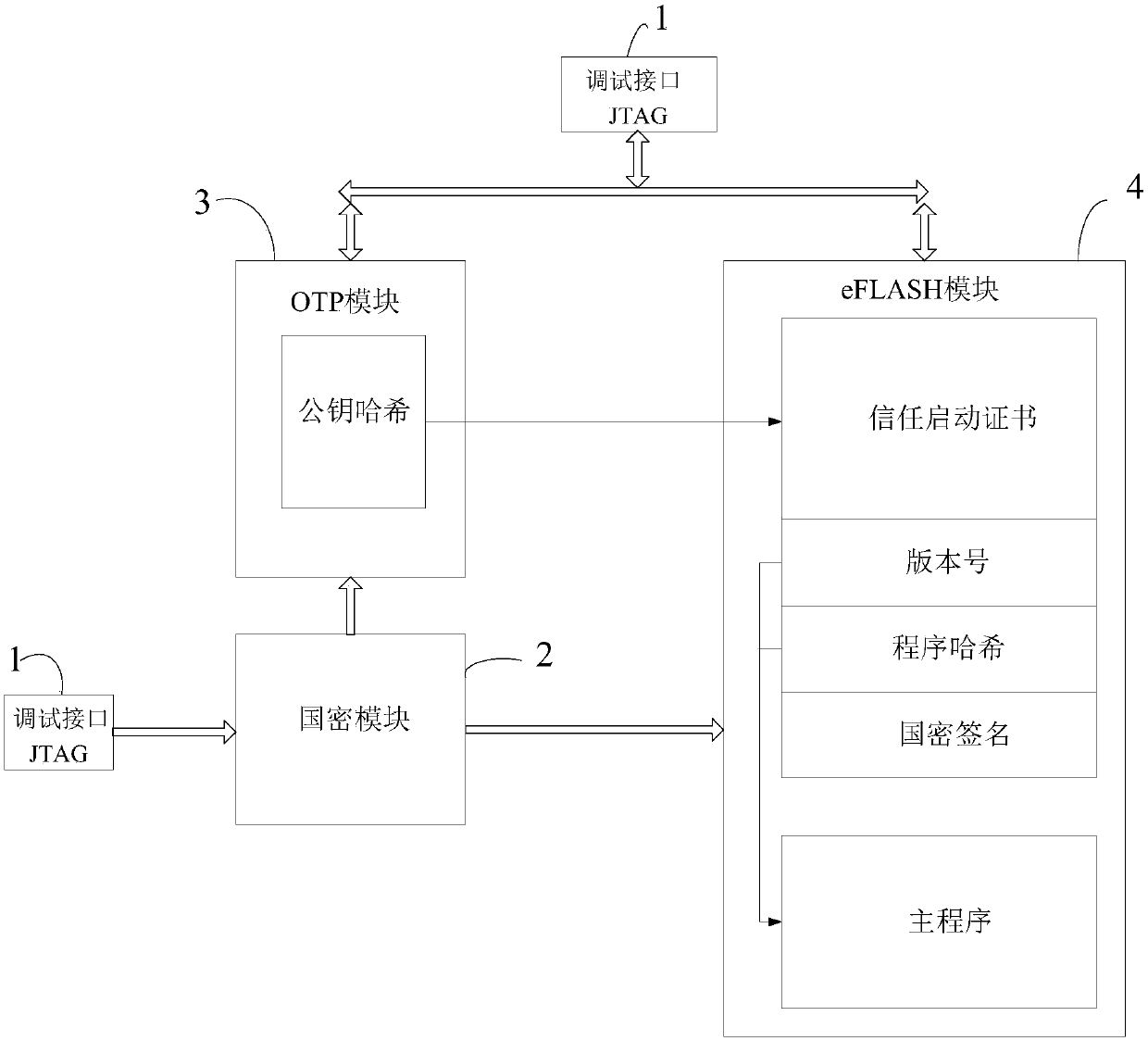
An identity recognition method and system based on a national cryptographic algorithm
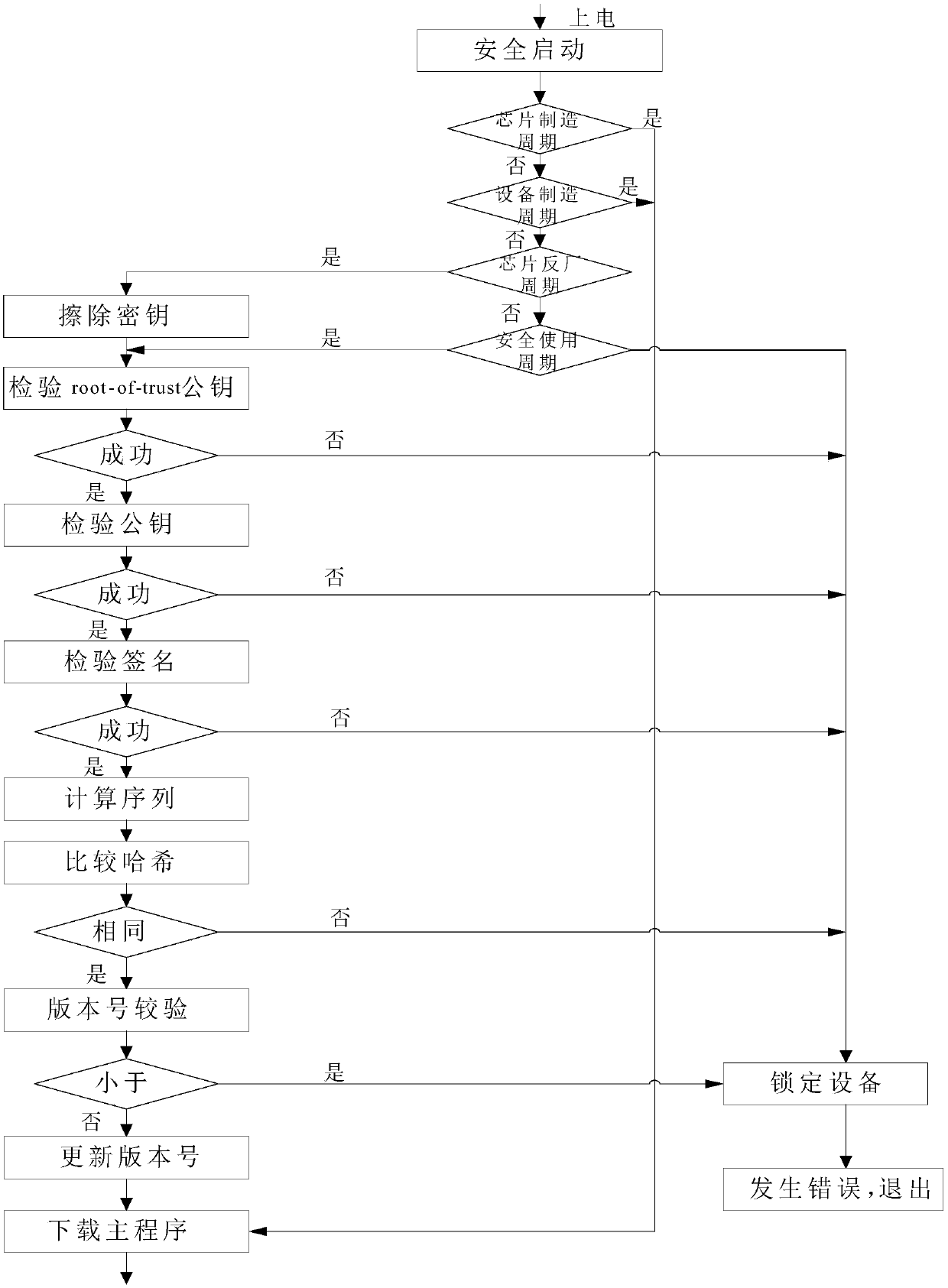
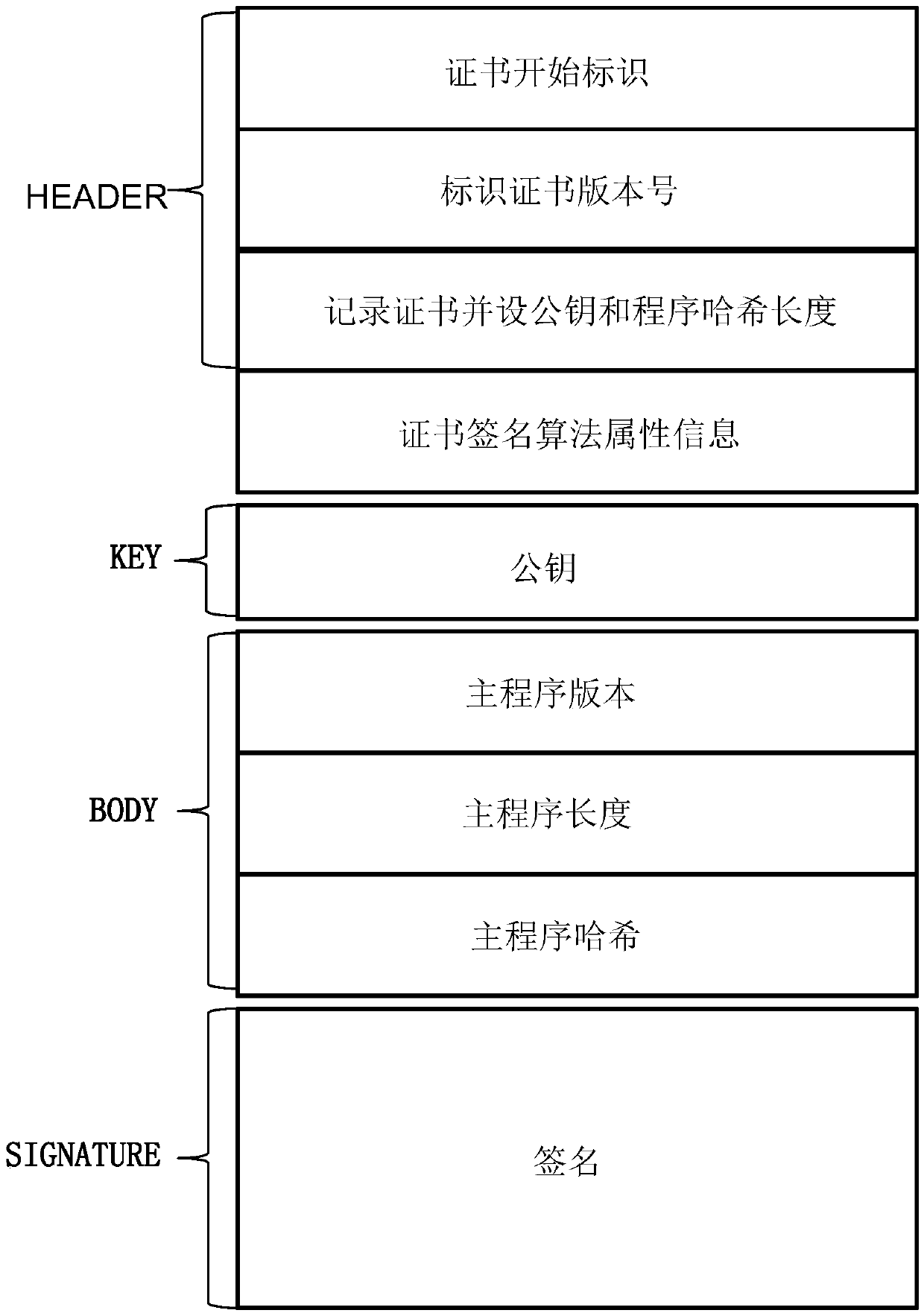
ActiveCN109583162AImprove experienceGuaranteed not to be leakedDigital data authenticationEncryptionSecurity level
The invention discloses an identity recognition method and system based on a national cryptographic algorithm, and the method comprises the steps: transmitting a program and storage data through a debugging interface, the storage data comprising a public key, a private key, a program, a signature, and the like, and the program comprising a main program; Public key Hash is encrypted through a national cryptographic algorithm and then stored in an OTP module, and a private key, a signature and the like are encrypted through the national cryptographic algorithm and then stored in an eFLASH moduletogether with a main program. Comparing a public key hash of the OTP module with a result obtained by performing hash operation on a public key in the eFLASH module to verify the public key, and considering that the public key is legal when the comparison result is consistent; When the public key is legal, the private key is compared with the signature according to the sequence obtained by executing the main program to verify the private key, and when the comparison result is consistent, it is considered that the private key is legal and passes through the signature. According to the scheme,the problems of low security level and the like in the prior art are solved, and the security level is improved through multi-level encryption.
Owner:上海芯钛信息科技有限公司
Multifunctional near field communication integrated system and method
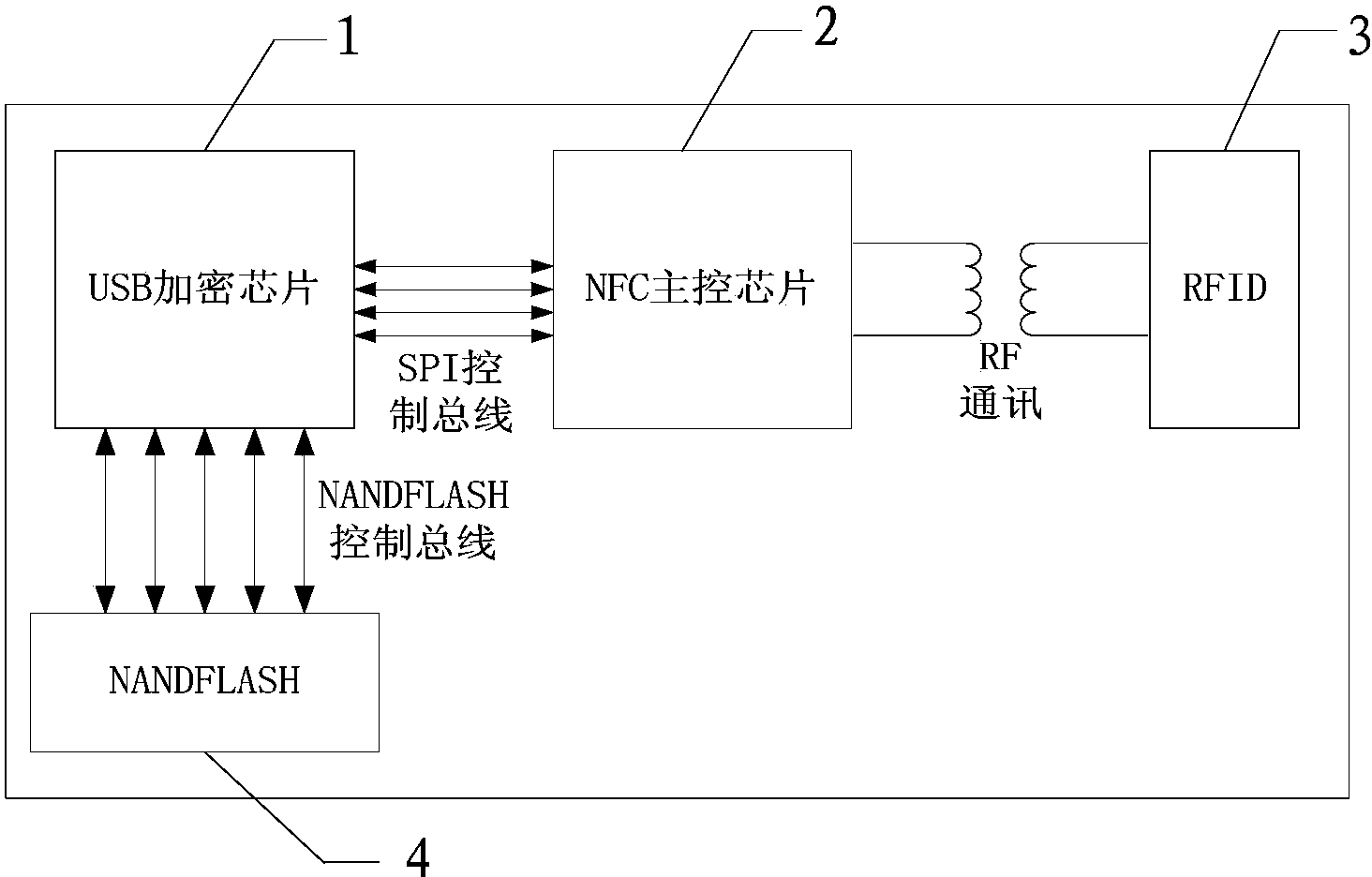
InactiveCN103532598AReduce in quantityConsistent informationNear-field systems using receiversInternal/peripheral component protectionType conversionCard reader
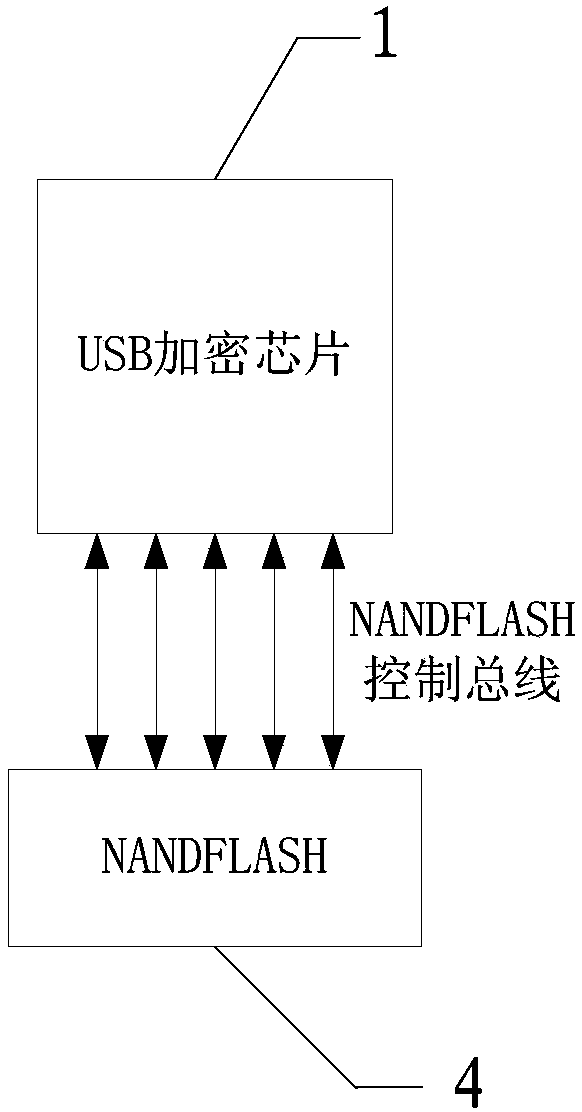
The invention relates to a multifunctional near field communication integrated system and a multifunctional near field communication integrated method, which are applicable to near field communication equipment. The multifunctional near field communication integrated system comprises a USB (universal serial bus) encryption chip, an NFC (near field communication) master control chip and an RFID (radio frequency identification) chip; the USB encryption chip is connected with the NFC master control chip through an SPI (serial peripheral interface) control bus, and the NFC master control chip is communicated with the RFID chip through the RF (radio frequency) communication mode; the USB encryption chip is used for realizing the function of a card-issuing card reader; the NFC master control chip is used for realizing the communication type conversion, and the contact communication is converted into non-contact communication; the RFID chip is used for realizing the function of a non-contact card; the USB encryption chip is connected with a PC (personal computer) host through the USB interface, and the PC host carries out read-write authentication and data modification on the RFID chip through the USB encryption chip and the NFC master control chip. With the adoption of the multifunctional near field communication integrated system and the multifunctional near field communication integrated method, the number of cards and USB flash disks carried by users is reduced, the integrated system is convenient and feasible, can be used for issuing cards and also can be used as a card.
Owner:刘宏伟
Residential building entrance guard security system and method based on edge calculation
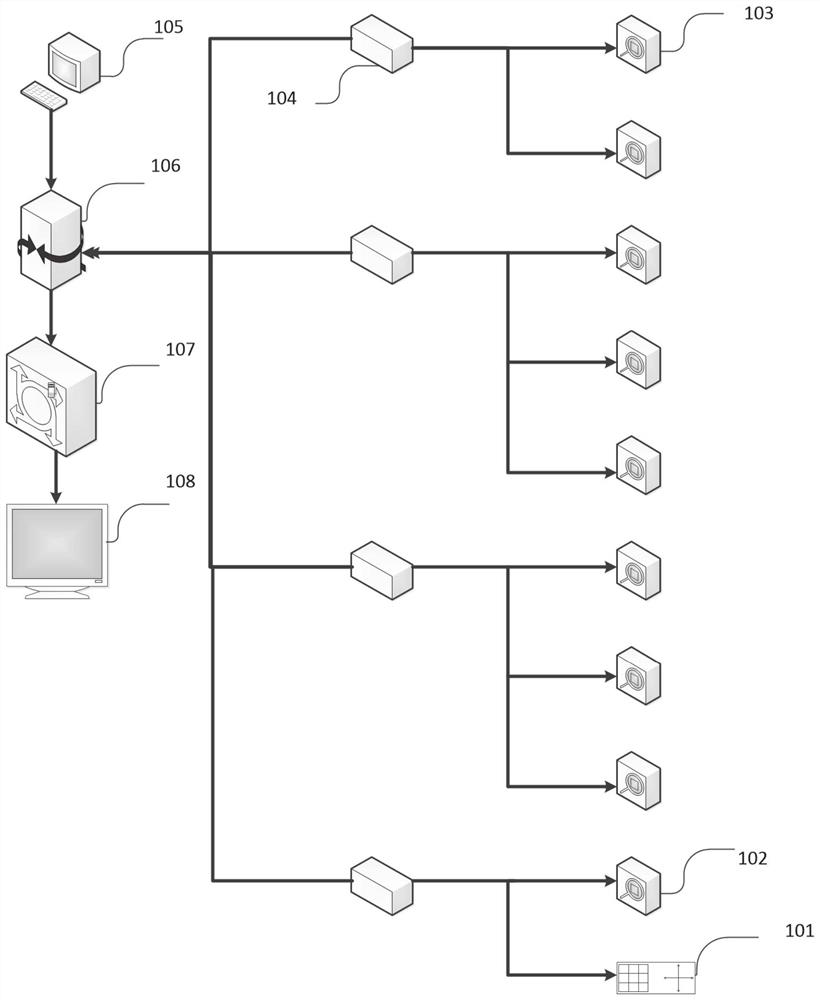
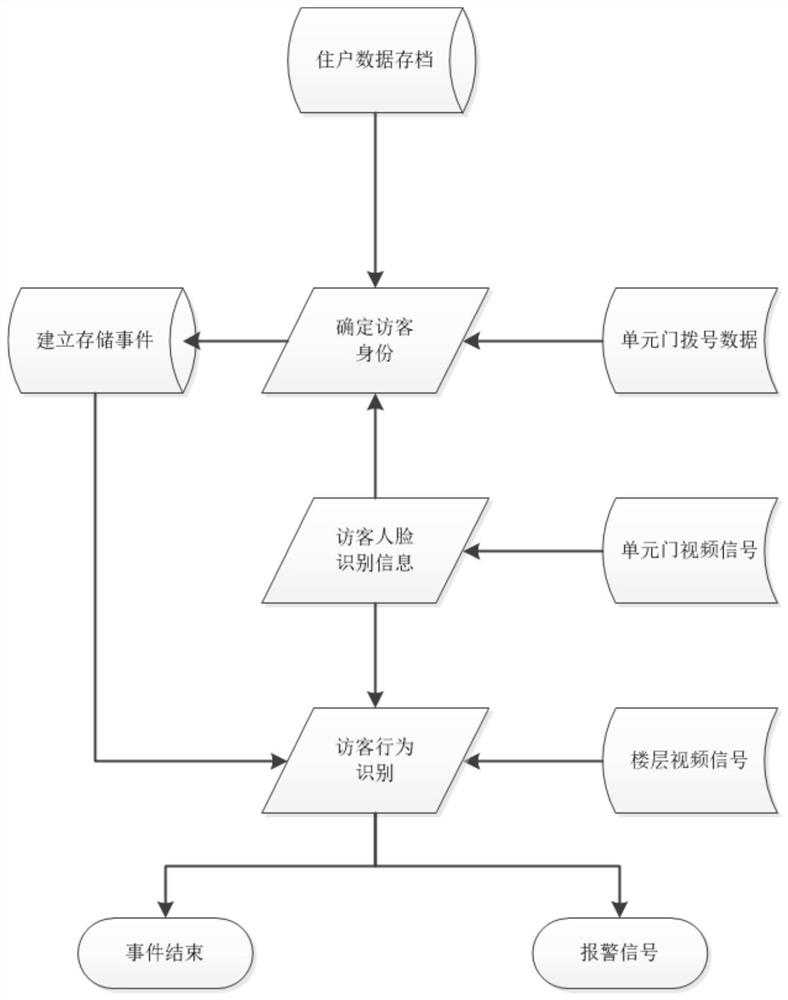
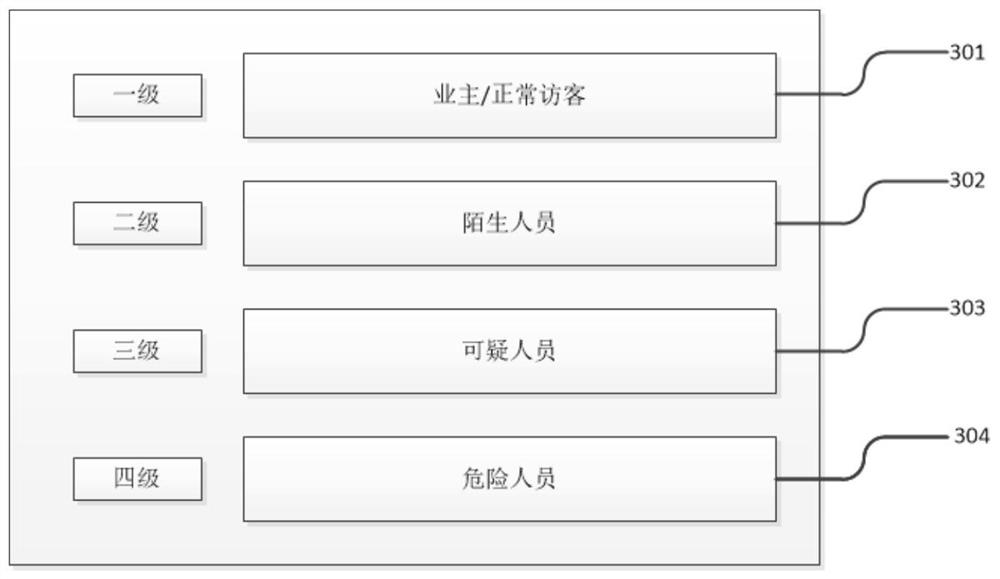
PendingCN112383615AGood real-time performanceGood confidentialityTelevision system detailsColor television detailsComputer securityEngineering
The invention provides a residential building entrance guard security system and method based on edge computing. The residential building entrance guard security system comprises an edge computing node, an edge server and a cloud server, the edge computing node serves as a local device and is configured to receive visitor visiting information and image information of visitors, establish events, conduct face recognition, people number recognition and behavior recognition on the visitors and classify danger levels of the events. The edge server communicates with at least one edge computing node,receives and screens all levels of events uploaded by the edge computing node, and uploads screened event information to the cloud server; and the cloud server is configured to issue information to owners involved in the screened events.
Owner:SHANDONG JIANZHU UNIV
Information leakage preventing method and system based on internet of things
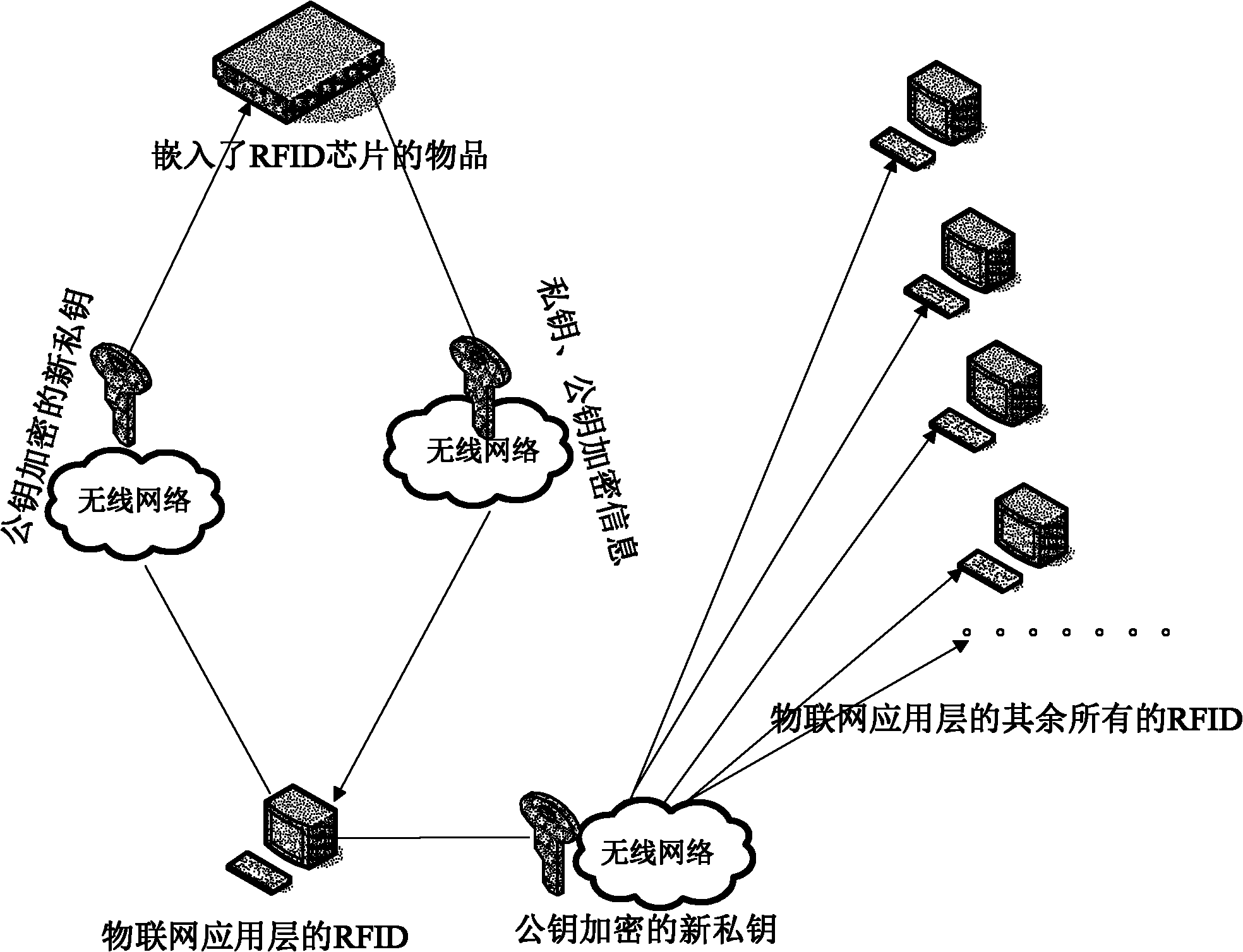
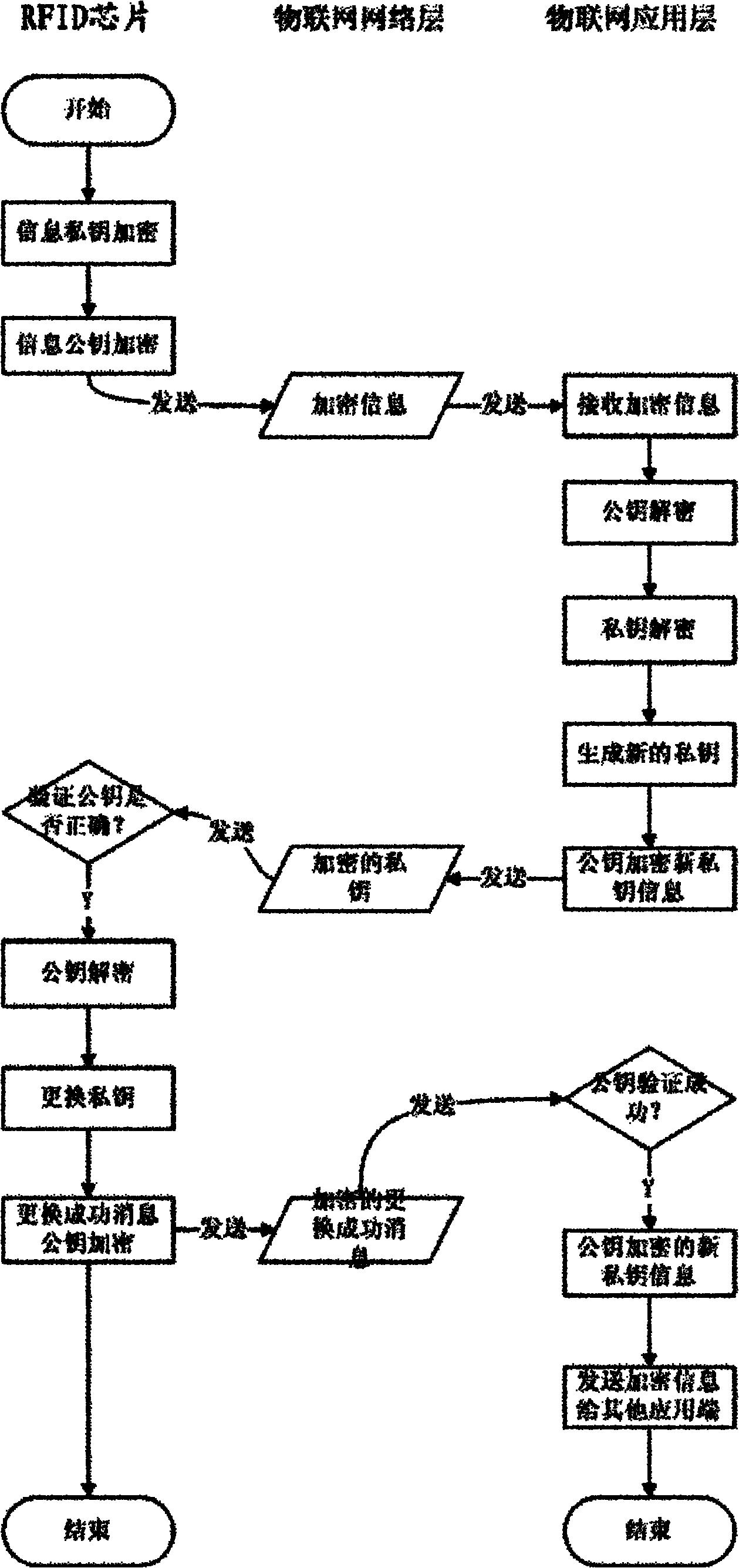
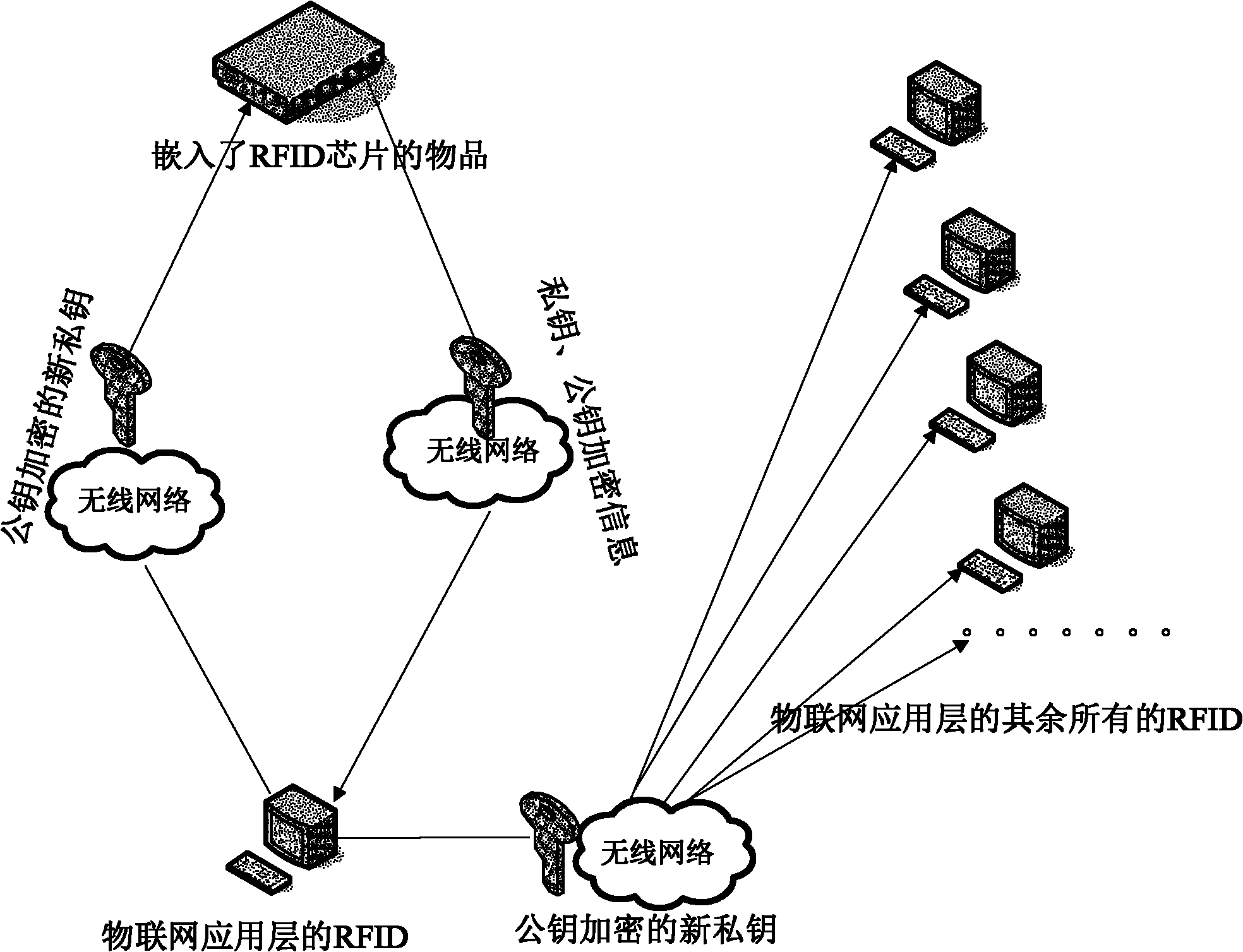
ActiveCN102065094APrevent leakageProtection securitySensing record carriersTransmissionPasswordThe Internet
The invention discloses an information leakage preventing method and system based on the internet of things. An RFID (Radio Frequency Identification Device) chip responder and a reader of an application layer of the internet of things, which are mutually communicated and arranged in the internet of things; and the RFID chip responder stores an electronic carrier of identifying information of things in the internet of things. The method comprises the following steps that the RFID chip responder encrypts a private key and a public key and then transmits encrypted information to the reader of the application layer of the internet of things by a network layer of internet of things; the reader of the application layer of the internet of things decrypts the public key and the private key and generates a new private key every time; and the reader of the application layer of the internet of things encrypts and forwards the new generated private key to the RFID chip responder and readers of other application layers of the internet of things by using the public key. The invention protects the safety of data in the internet of things and prevents the leakage of information by a public key and private key encrypting mechanism. In the whole process of realization, the dynamic replacement of the private key not only further protects information safety but also improves the difficulty of password cracking.
Owner:WUXI CINSEC INFORMATION TECH
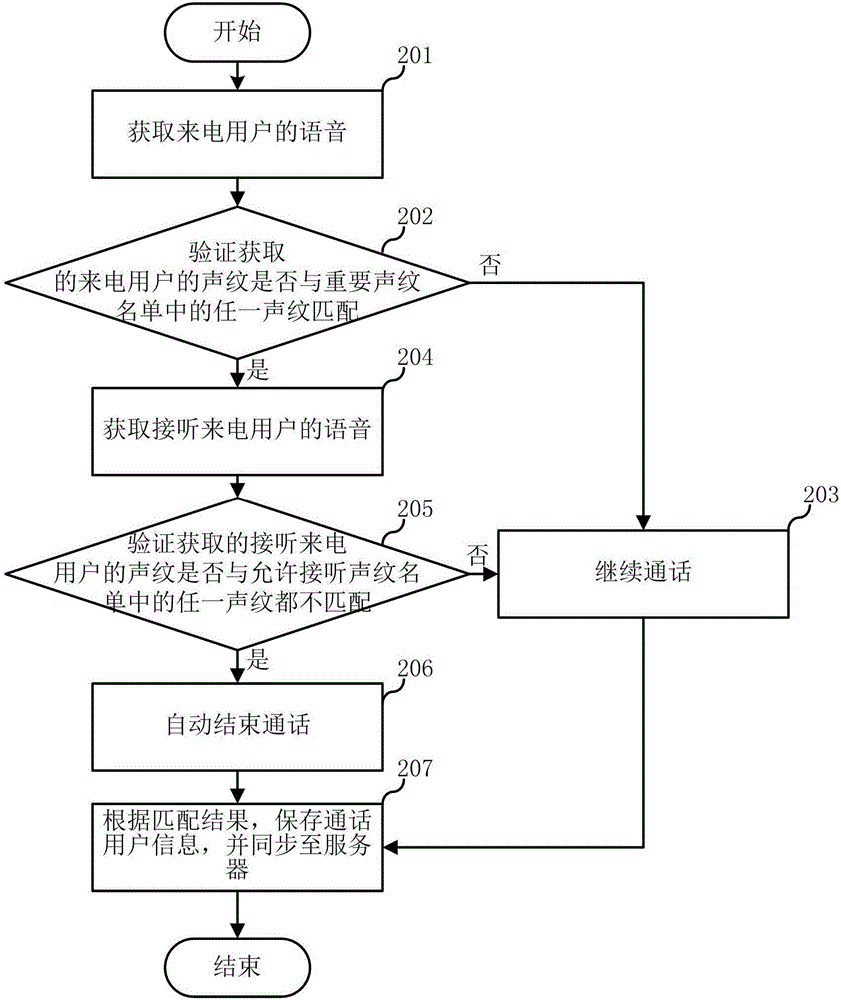
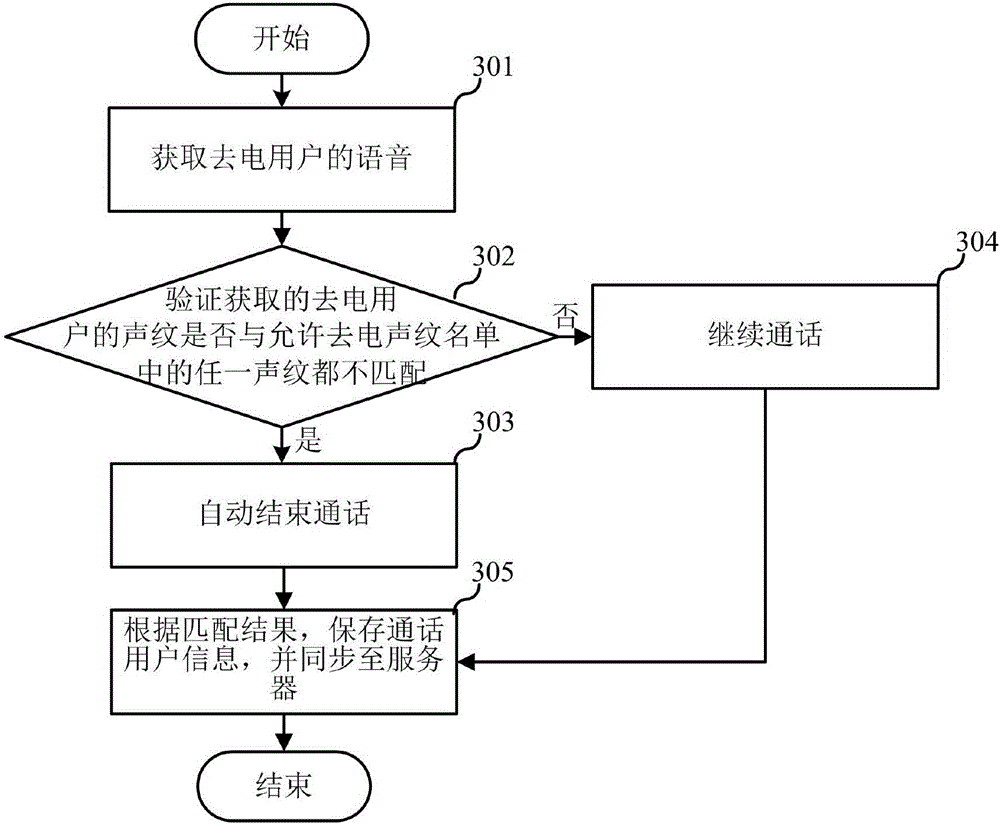
Call control method and apparatus
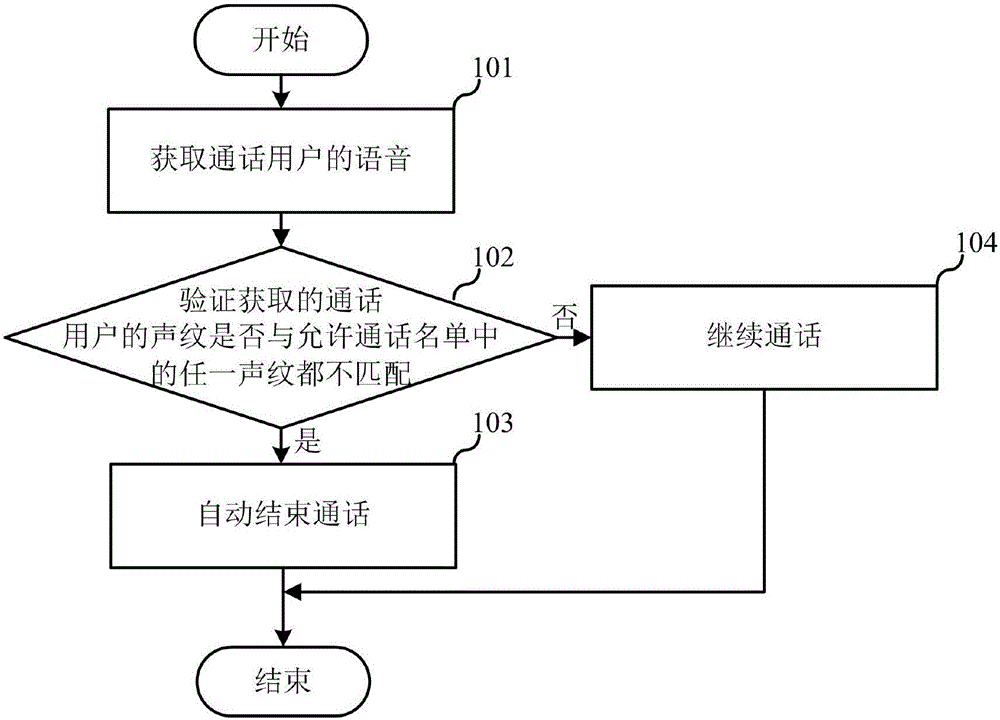
InactiveCN107181851APrevent fraudImprove security and confidentialityUnauthorised/fraudulent call preventionUser identity/authority verificationSpeech soundCall control
The embodiment of the invention relates to the technical field of communication, and discloses a call control method and apparatus. The call control method is applied to a terminal, and includes the steps: when the terminal is in the call state, acquiring the voice of a user; and when the acquired voiceprint of the call user is not matched with any one voiceprint in the list allowing calls, automatically ending the call, wherein the list allowing calls include any one or any combinations: an important voiceprint list, a list allowing answering the voiceprints, and a list allowing out-going call voiceprint. The call control method and apparatus can prevent the incoming call of important contacts from answering by the other, thus guaranteeing that the important information is not leaked out, and can prevent lawless persons defraud the contact stored in the terminal address list by using the terminal, thus avoiding bringing unnecessary trouble and loss to the user and other people.
Owner:SHANGHAI YUDE TECH CO LTD
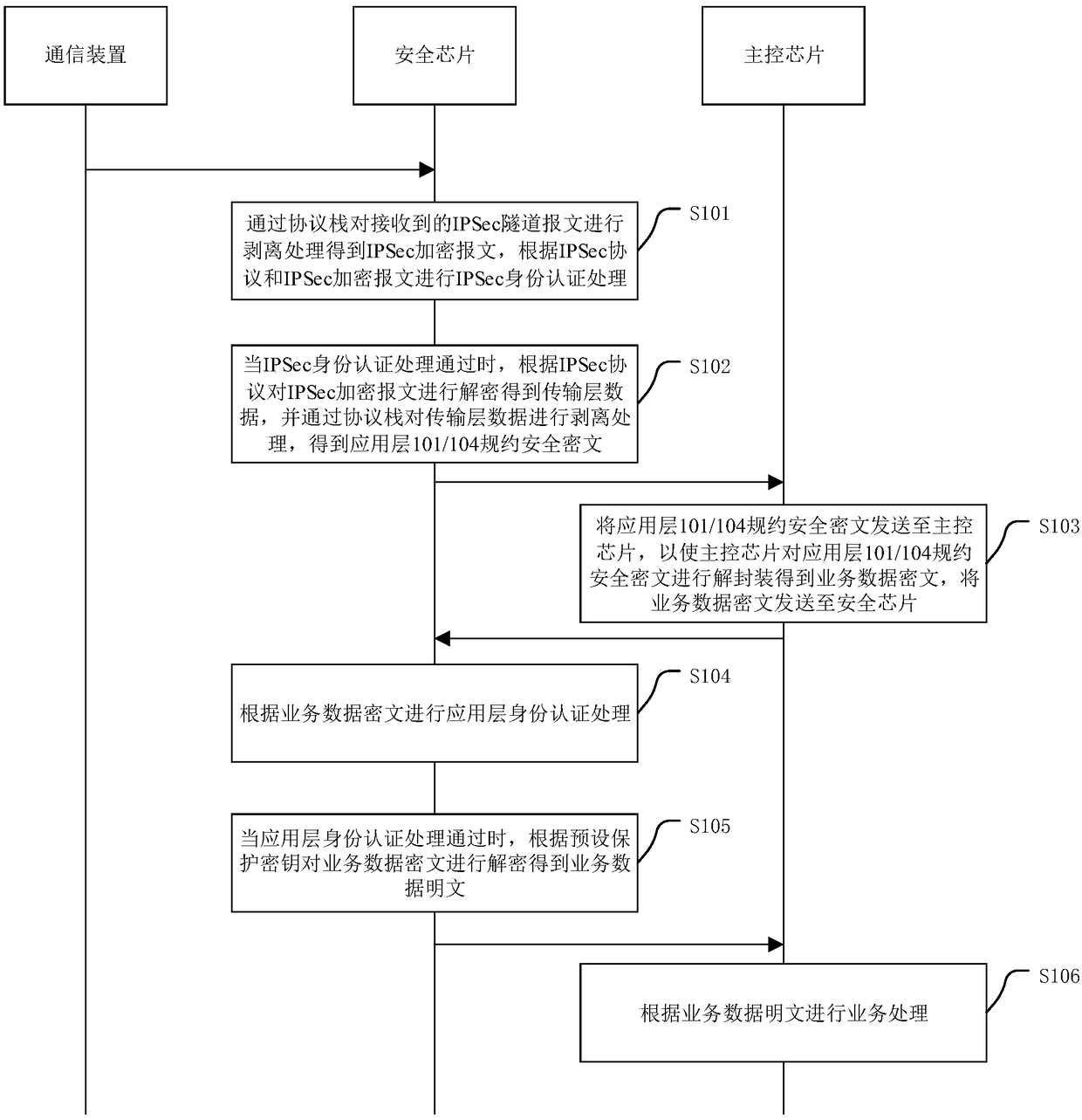
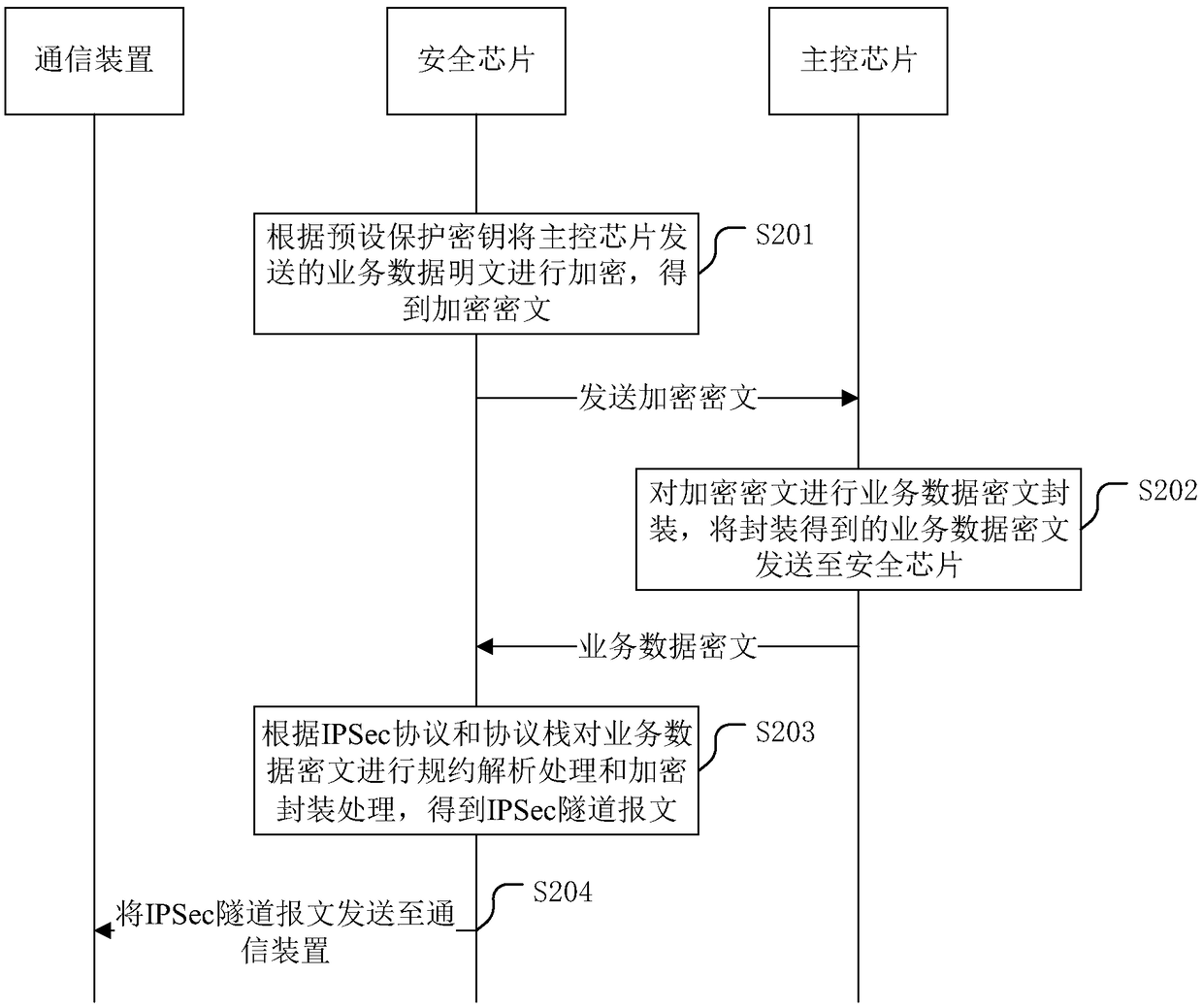
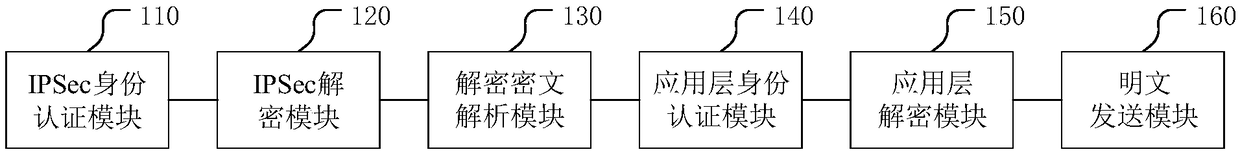
Double encryption-based service data processing method for power distribution terminal
ActiveCN108900540AGuaranteed not to be leakedAvoid malicious intrusionTransmissionDistribution power systemData decryption
The application discloses a double encryption-based service data processing method for a power distribution terminal. According to the method, received massages are processed by means of IPSec protocol authentication and decryption, and an identity authentication operation and a data decryption operation are performed at an application layer, so that data is prevented from being leaked, a power distribution system network is not maliciously invaded, the messages received by the power distribution terminal are sent by safe equipment, and the situations such as malicious attacks caused by data communication between masquerading equipment and the power distribution terminal can be avoided. The dual protection of a network layer and the application layer is realized in a process of service data processing of the power distribution terminal, so that the security protection performance of the power distribution terminal is improved, and the situations of the malicious attacks are avoided. The application also discloses a data encryption method of the power distribution terminal, a service data processing system, a data encryption system, the power distribution terminal and a computer readable storage medium, which have the beneficial effects.
Owner:ELECTRIC POWER RESEARCH INSTITUTE, CHINA SOUTHERN POWER GRID CO LTD +1
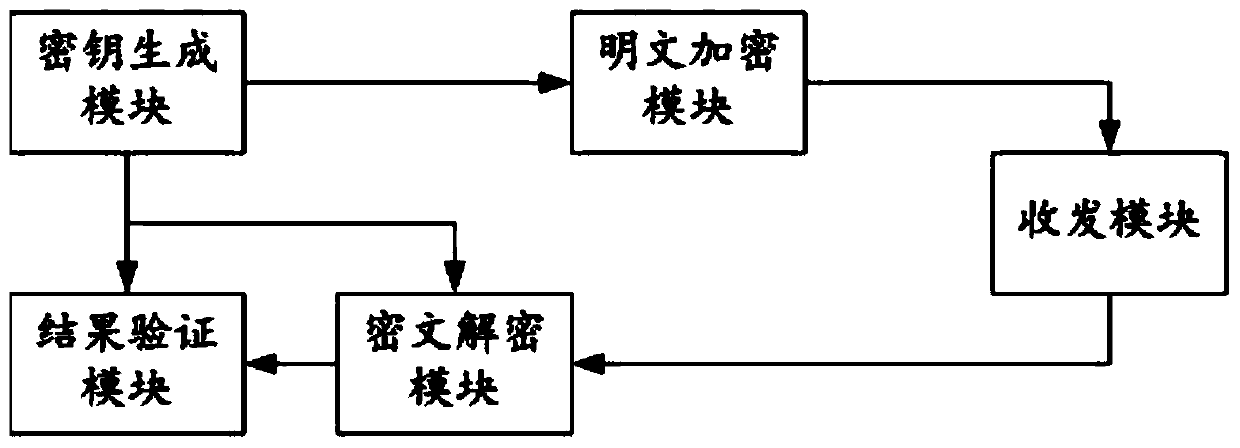
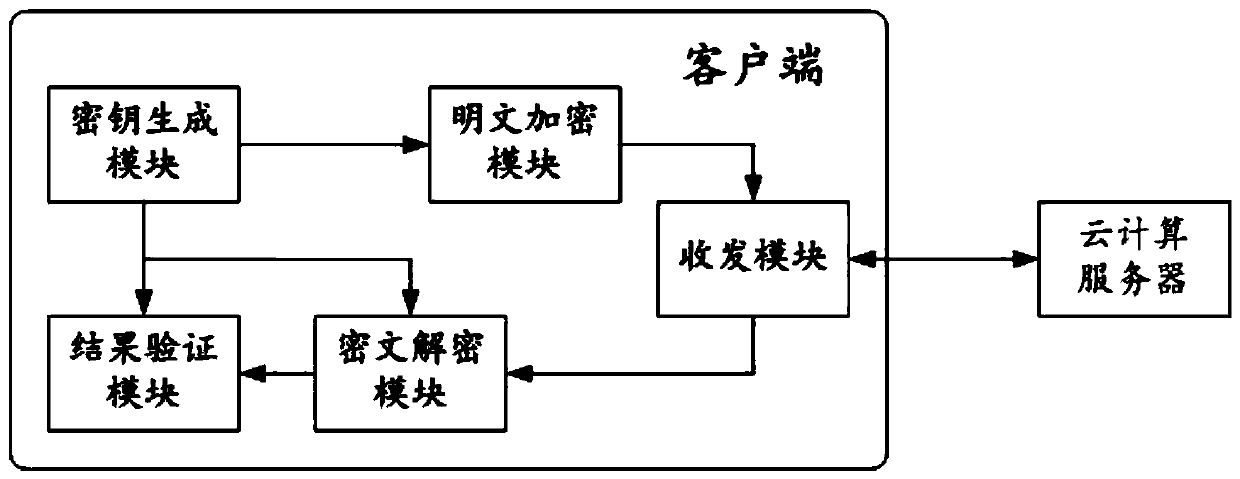
Verifiable outsourcing computing method for realizing safety and high efficiency of large-scale matrix multiplication, client and cloud computing system
ActiveCN110826089AGuaranteed not to be leakedImprove verification efficiencyDigital data protectionIndustrial engineeringOutsourcing computation
The invention relates to the technical field of cloud computing, and discloses a verifiable outsourcing computing method for realizing the safety and high efficiency of large-scale matrix multiplication, a client and a cloud computing system. According to the present invention, a new outsourcing calculation protocol suitable for calculating a large-scale matrix multiplication result is provided, the client with less computing resources / weak computing power can outsource the multiplication operation of the matrix to the cloud server with a large number of computing resources with less computingexpenditure under the premise of ensuring that the sensitive matrix data is not leaked when facing the large-scale matrix multiplication operation, and the safe and reliable verification about a matrix multiplication result is provided for the client, so that the requirements of the outsourcing computation for safety (verifiability), privacy and high efficiency are met, and the method is convenient to apply and popularize practically. Compared with an existing related protocol, the probability that the verification scheme passes through a guessing result is lower, and the verification schemedoes not depend on an original plaintext matrix and the random verification times, and the verification efficiency is also higher.
Owner:SICHUAN UNIV
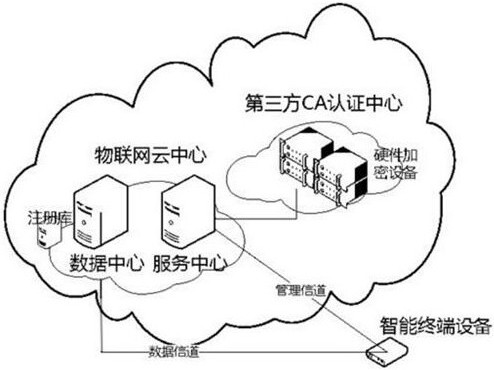
Intelligent safety system for Internet-of-things terminal of power enterprise
An intelligent safety system for an Internet of Things terminal of power enterprise mainly comprises an intelligent terminal device, a third-party CA authentication center and an Internet of Things cloud center, wherein the intelligent terminal device is responsible for uploading identity information data, generating a temporary asymmetric secret key, verifying the identity of the Internet of Things cloud center, and storing the digital certificate into local hardware equipment; the Internet of Things cloud center is provided with a data center and a service center of intelligent terminal equipment, provides identity authentication service and key-related security authentication service, and interacts with a third-party CA authentication center; the third-party CA authentication center provides a digital certificate signing and issuing service. According to the invention, the intelligent equipment in the Internet of Things in a power enterprise is integrated into the Internet of Things, so the private key of the terminal with the hardware encryption chip is prevented from being leaked, and the problem of key strength of the terminal adopting a soft encryption mode is solved.
Owner:辽宁丰沃新能源有限公司
Method and device for sharing VPN and terminal device
InactiveCN106535094AQuick shareGuaranteed not to be leakedAssess restrictionConnection managementTerminal serverPrivate network
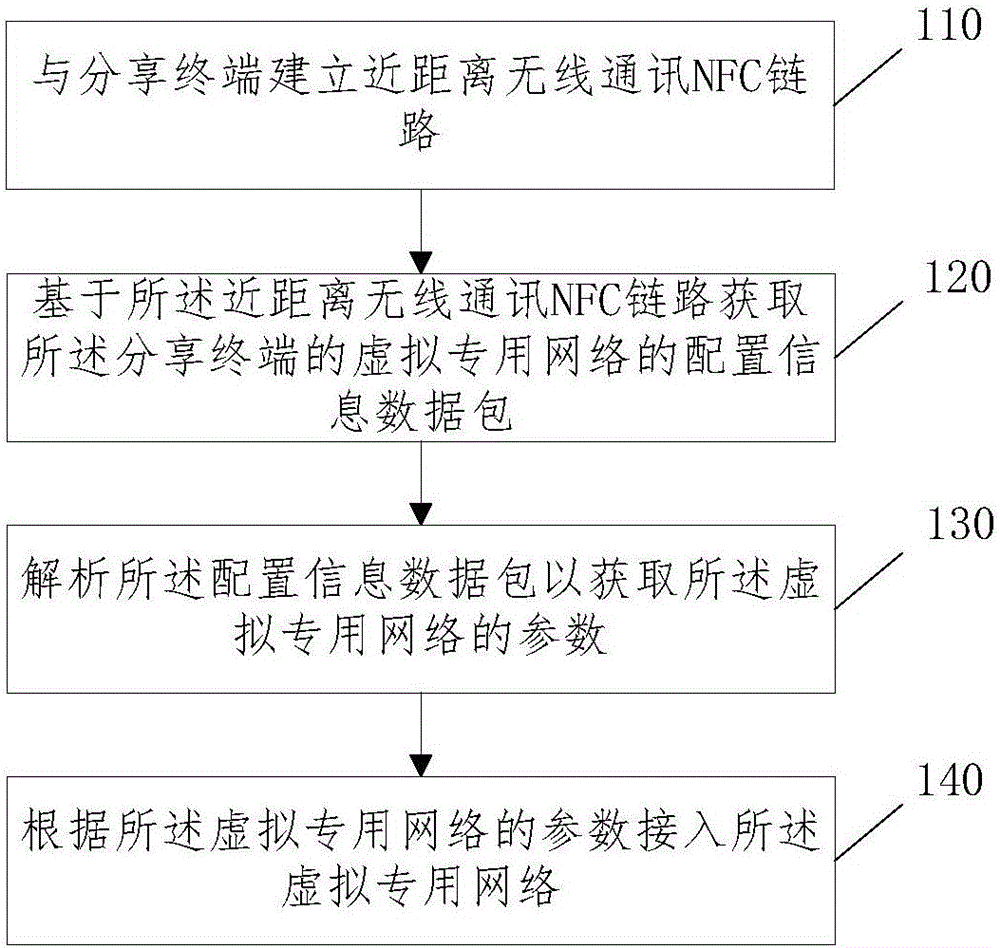
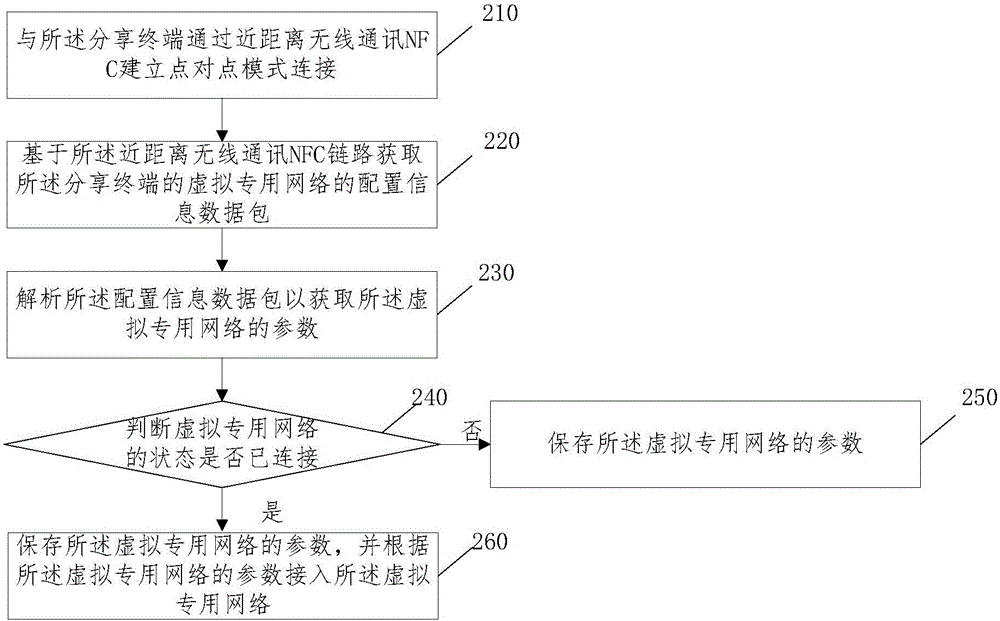
The invention discloses a method and a device for sharing a VPN (Virtual Private Network) and a terminal device, and relates to the technical field of short-range wireless communication. The method comprises the steps of establishing an NFC (Near Field Communication) link with a sharing terminal; obtaining a configuration information data packet of the VPN of the sharing terminal based on the NFC link; analyzing the configuration information data packet to obtain parameters of the VPN; and accessing the VPN based on the parameters of the VPN. According to the scheme of the invention, rapid sharing of the VPN not only can be realized, but personal sensitive information also can be guaranteed to be not easy to leak. Therefore, the problems in the prior art that the sharing operation of the VPN is relatively complex and the personal sensitive information is easy to leak are solved.
Owner:LETV HLDG BEIJING CO LTD +1
Management method for transaction processing in management system
InactiveCN107506902AGuaranteed fair dealingGuaranteed not to be leakedPayment architectureOffice automationWorkloadTransaction processing system
The invention discloses a management method for transaction processing in a management system. The method comprises: a transaction submitter assigns a user / employee to carry out processing; and otherwise, a transaction processing request is assigned to a preset assignee and the assignee assigns an assigned user / employee to carry out processing according to a content a transaction processing request submitted by the transaction submitter. According to the invention, the function of assigning a user / employee to carry out processing is provided for the transaction submitter and the transaction can not be transferred, so that the transaction privacy is protected from being leaked and thus the fair transaction processing is guaranteed. Because the independent individual role is used as an assignee, when the assignee resigns or is transferred to another position, only a newly-appointed assignee needs to be associated to an assigned role to obtain current all transactions automtaically, so that the transaction transferring workload is reduced; moreover, the seamless docking is realized, transaction assignment lagging or missing is avoided, and thus the emergency event can be dealt with timely and a negative effect that is caused on the employee's enthusiasm because the transaction submitted by the employee can not be responded timely is eliminated.
Owner:CHENGDU QIANNIUCAO INFORMATION TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com