An identity recognition method and system based on a national cryptographic algorithm
A national secret algorithm and identification technology, applied in the field of identification methods and systems based on the national secret algorithm, can solve the problems of low security protection level and low user experience.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
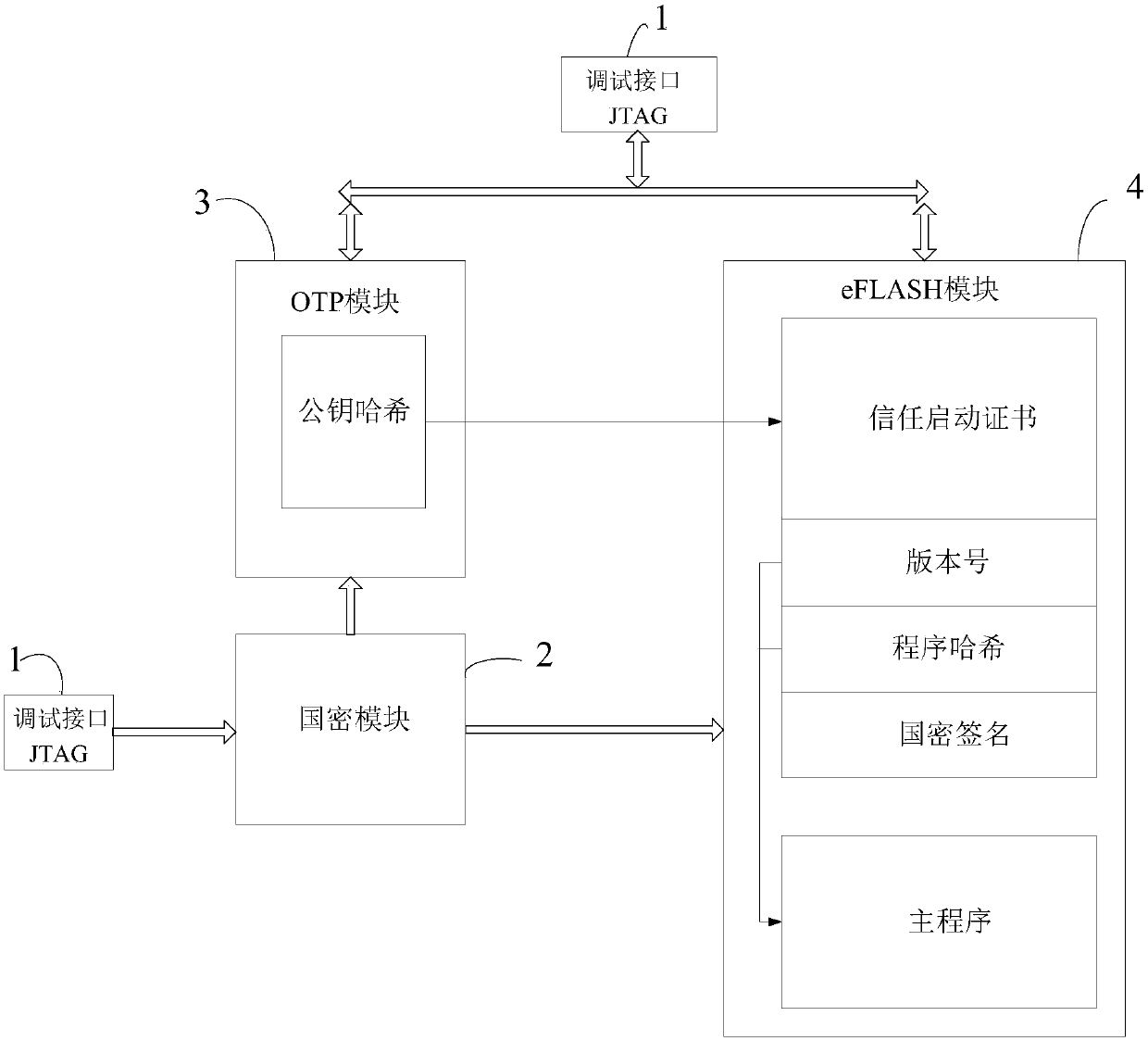
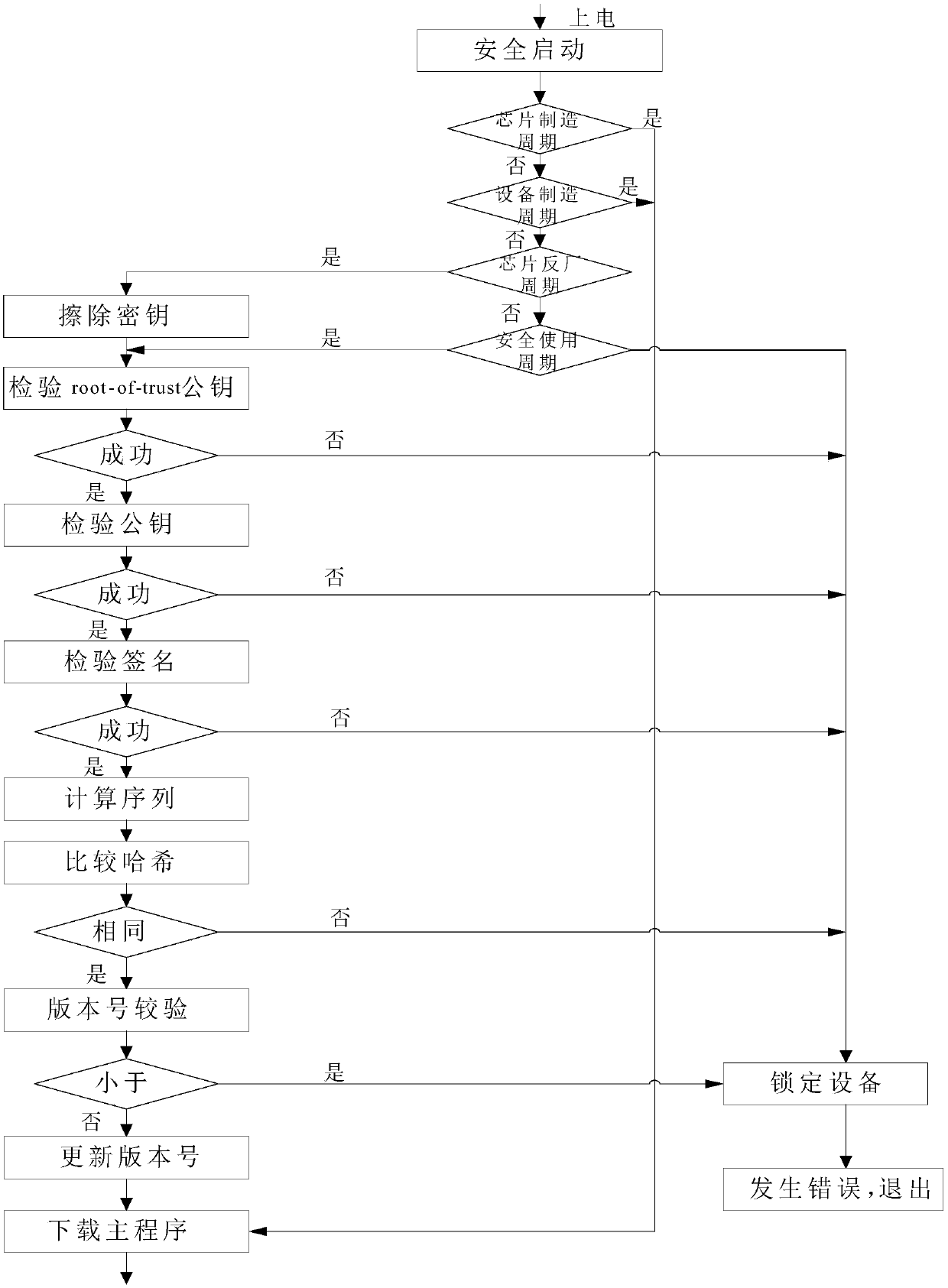
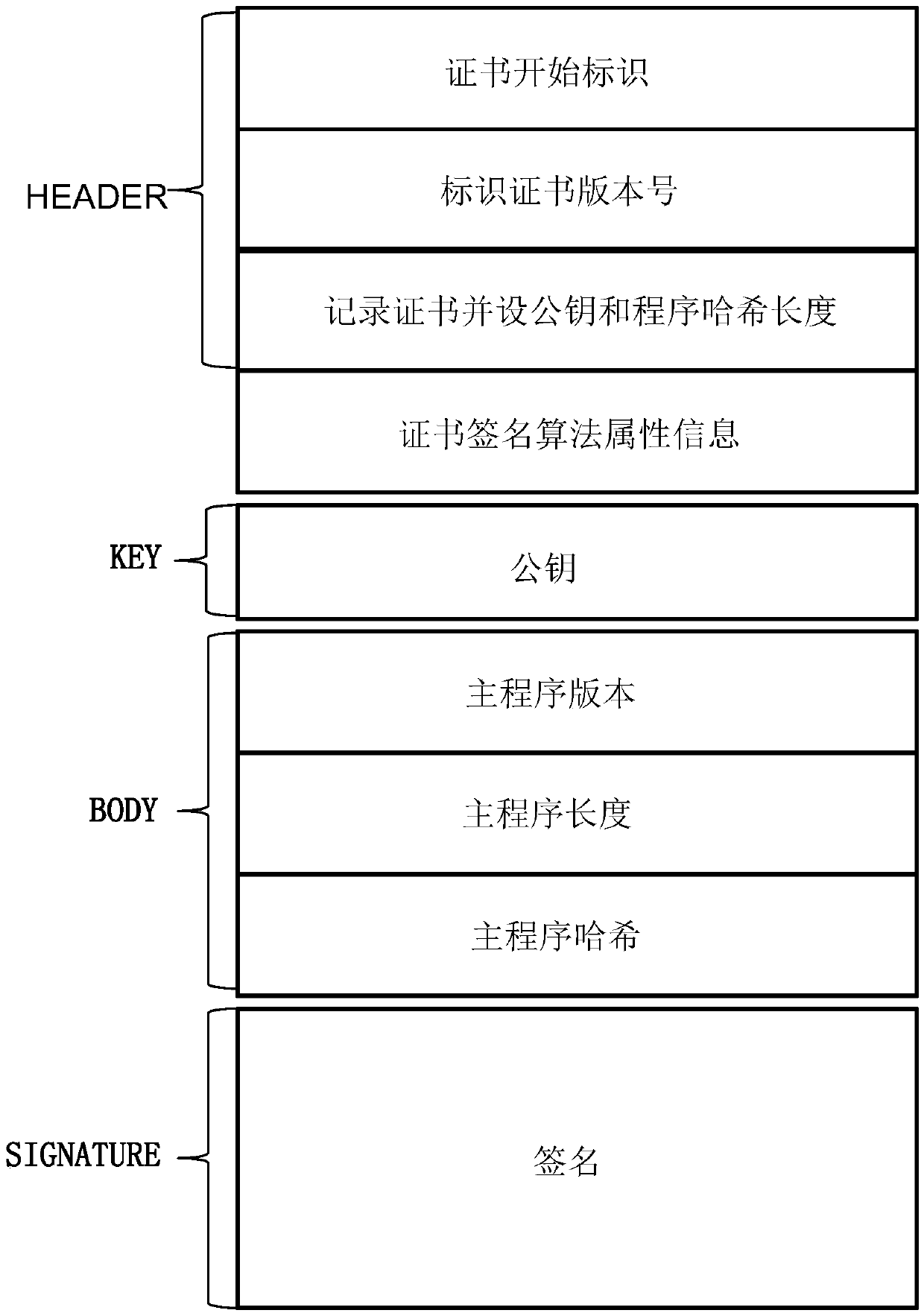
[0030] Please refer to Figure 1 to Figure 3 , the present invention provides a kind of identification method based on national secret algorithm, comprises the following steps:
[0031] Step 1, transmit program and store data through debug interface 1, described store data comprises public key, private key and signature, and described program comprises main program; Debug interface 1 is JTAG communication interface for example;
[0032] Step 2, the hash of the public key is stored in the OTP module 3 after being encrypted by the national secret algorithm, and the private key and signature, and other keys are stored in the eFLASH module 4 together with the main program after being encrypted by the national secret algorithm;
[0033] National secret algorithms such as SM2, SM3, SM4, etc. The public key and private key can choose different specific algorithms according to the system configuration;
[0034] In a preferred embodiment of the present invention, the public key in ste...
Embodiment 2
[0061] see figure 1 , Figure 4 , the embodiment of the present invention is also an identity recognition system based on a national secret algorithm, including a chip, and the chip is internally integrated with: a debugging interface 1, a national secret module 2, an otp module 3, and an eflash module 4, wherein:
[0062] The debugging interface 1 is used to access the otp module and the eflash module according to the control instructions of the control logic module;
[0063] The national secret module 2 is used to encrypt and decrypt the data through the debugging interface;
[0064] The otp module 3 is used to store the public key hash encrypted by the national secret module, control related data and other manufacturer information, etc.;
[0065] The eflash module 4 is used to store the main program and the public key encrypted by the national secret module, related function keys, private keys and signatures;
[0066] The control process is to execute some initialization...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com