Storage method, restoration method and operation method of ordered and derivable large-data files
An operation method and big data technology, applied in the field of cloud storage, can solve problems such as easy leakage of private information, achieve the effect of reducing encryption workload and improving data processing efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
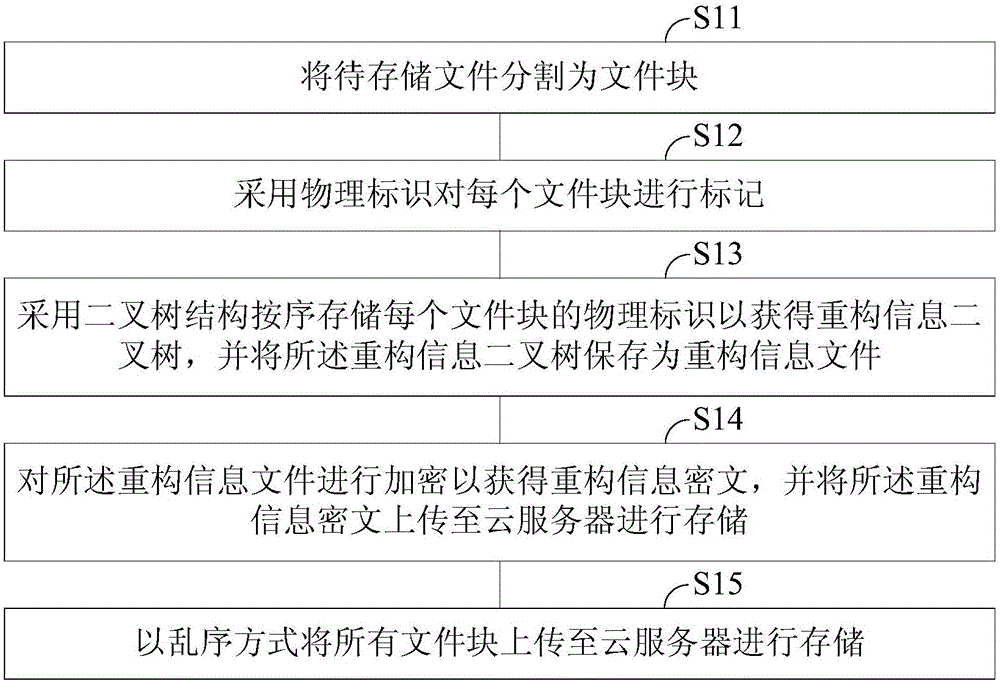
[0022] figure 1 It is a schematic flow chart of the method for storing ordered and deducible large data files in this embodiment, and the method for storing orderly and deducible large data files includes:
[0023] Step S11, dividing the file to be stored into file blocks.
[0024] First of all, it is necessary to generate orderly system parameters in the cloud server that can deduce the safe storage of large data files. The system parameters include a large prime number p, an intrinsic root g of the large prime number p, and define a hash function that maps any character string to the remaining cluster Select the hash function international standard SHA-3 from arbitrary-length strings to fixed-length strings, denoted as h(x). After the system parameters are generated in the cloud server, the orderly deducible big data files to be protected are selected through the client, that is, the files to be stored are determined and the files to be stored are divided. It should be n...
Embodiment 2
[0043] Based on the method for storing ordered and deducible large data files provided in Embodiment 1, this embodiment provides a recovery method for ordered and deducible large data files, and the method provided in Embodiment 1 for the ordered and deducible large data files storage. figure 2 It is a schematic flowchart of the method for recovering ordered and deducible large data files in this embodiment, and the method for restoring orderly and deducible large data files includes:
[0044] Step S21, download the ciphertext of the reconstruction information corresponding to the file to be restored and decrypt it to obtain the binary tree of the reconstruction information corresponding to the file to be restored. Specifically, the file where the data to be read is located is selected from the cloud file directory of the cloud server, and the file is the file to be restored. Further, multiple files to be restored can be selected. Download the reconstructed information ciph...
Embodiment 3
[0050] image 3 is a schematic flow chart of the file block insertion operation in this embodiment, and the file block insertion operation includes:
[0051] Step S31, download and decrypt the reconstructed information ciphertext corresponding to the operation file to obtain a binary tree of reconstructed information corresponding to the operation file. This step is similar to step S21 in Embodiment 2, and will not be repeated here.
[0052] Step S32, dividing the file to be inserted into file blocks to be inserted. Specifically, a segment of continuous data to be inserted into the operation file is imported through the client, that is, the file to be inserted is imported, and the file to be inserted is divided into one or more files to be inserted according to a method similar to step S11 in Embodiment 1. file blocks.
[0053] Step S33, marking each file block to be inserted with a physical identifier. This step is similar to step S12 in Embodiment 1, that is, a hash value ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com