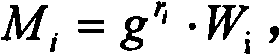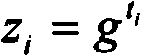Multi-party secret handshaking method in short key environment
A secret handshake and key technology, applied in the field of information security cryptography, can solve the problems of ineffective protection of the privacy of participating users
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
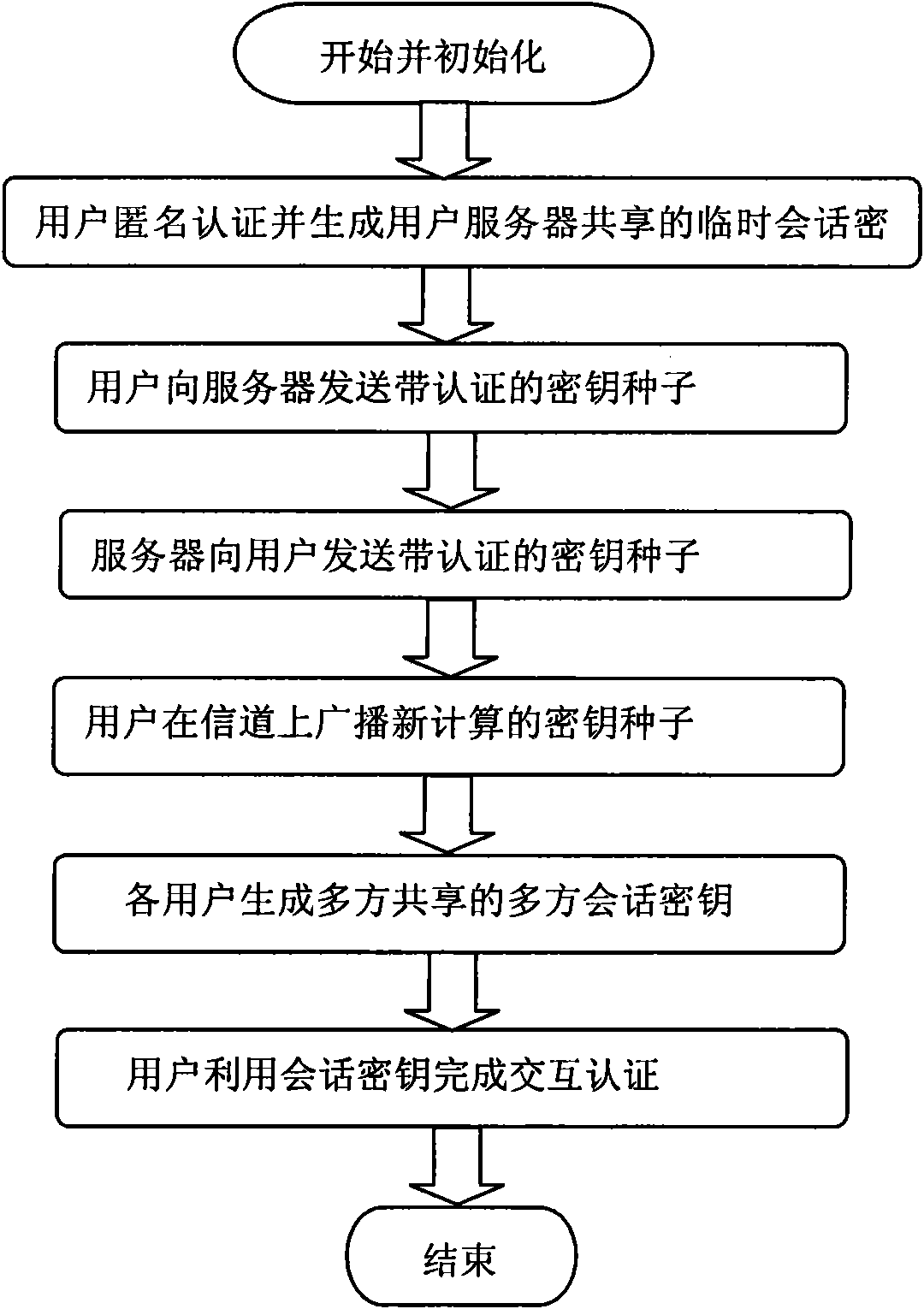
[0018] The multi-party secret handshake method under the short key environment provided by the present invention includes the following six stages: user anonymous authentication stage, key seed sending stage, server distribution stage, multi-party key exchange stage, session key generation stage, and multi-party interactive authentication stage . Such as figure 1 As shown, the specific steps are as follows:
[0019] 1. Start and initialize;
[0020] 2. The user authenticates anonymously and generates a server-oriented session key.
[0021] 3. The user sends the key seed with authentication to the server.
[0022] 4. The server sends the authenticated key seed to the user.
[0023] 5. The user broadcasts the newly calculated key seed on the channel.
[0024] 6. Each user generates a session key shared by multiple parties.
[0025] 7. The user uses the session key to complete interactive authentication.
[0026] In the method, when a user registers on the server, the serv...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com