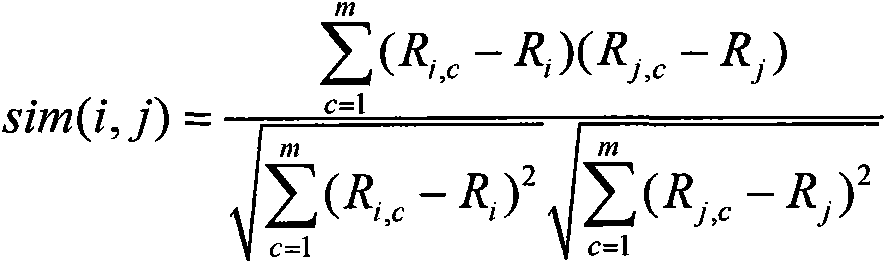Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
112results about How to "Protect private data" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
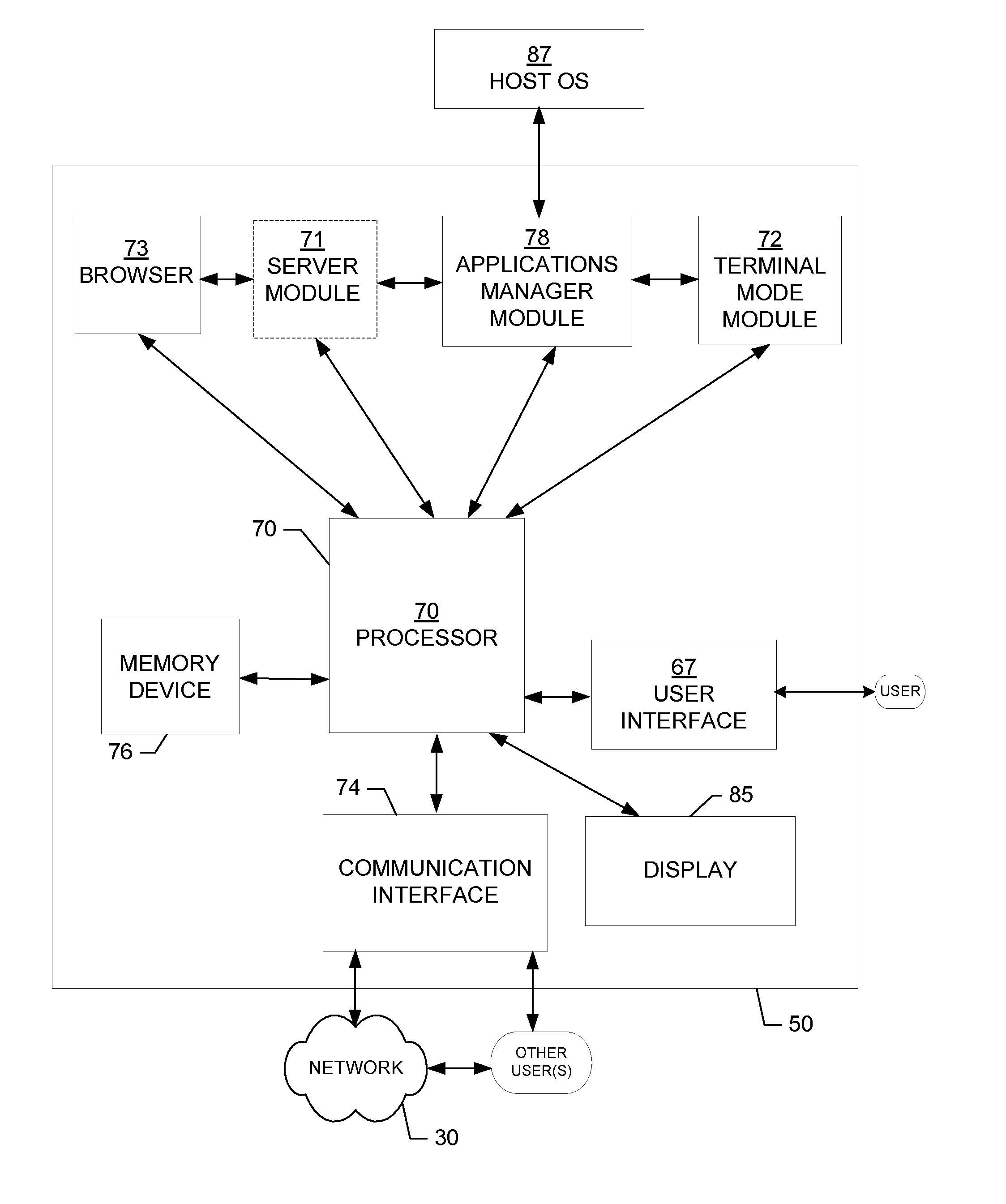
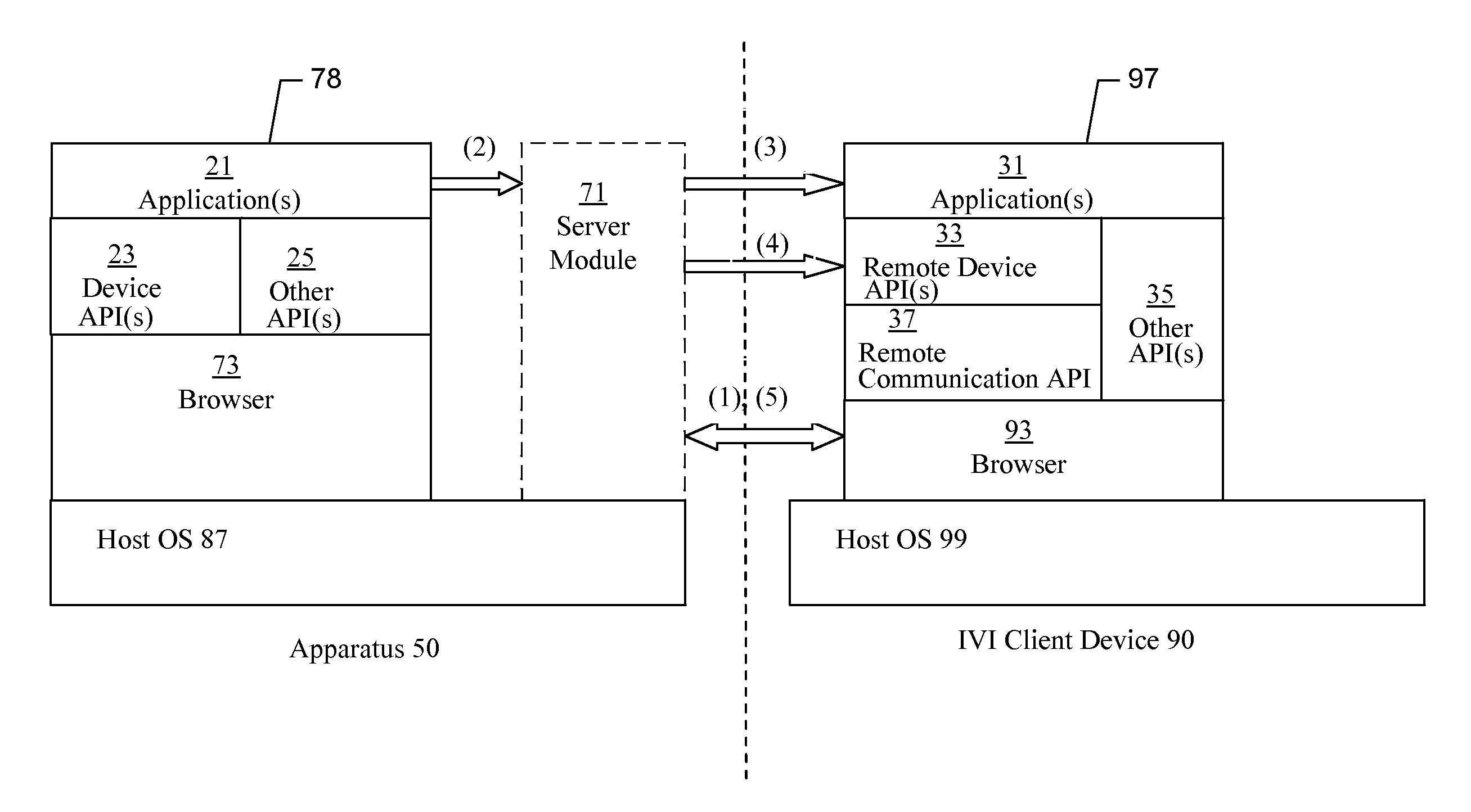
Methods, apparatuses and computer program products for provisioning applications to in vehicle infotainment systems with secured access
ActiveUS20120324482A1Efficient and reliableEfficient and reliable mechanismMultiprogramming arrangementsSoftware deploymentApplication programming interfaceIn vehicle
An apparatus for providing one or more applications to an IVI client device(s) may include a processor and memory storing executable computer code causing the apparatus to at least perform operations including providing an application(s) and associated data to a device in response to receipt of an indication of a selection associated with the application(s). The computer program code may further cause the apparatus to enable the application(s) to access requested data via a plurality of application programming interfaces during execution of the application. The computer program code may further cause the apparatus to provide the requested data to the application in response to receipt of a message(s) generated by a first application programming interface of the interfaces that received a request for the requested data from a second application programming interface of the interfaces. Corresponding methods and computer program products are also provided.
Owner:NOKIA TECHNOLOGLES OY
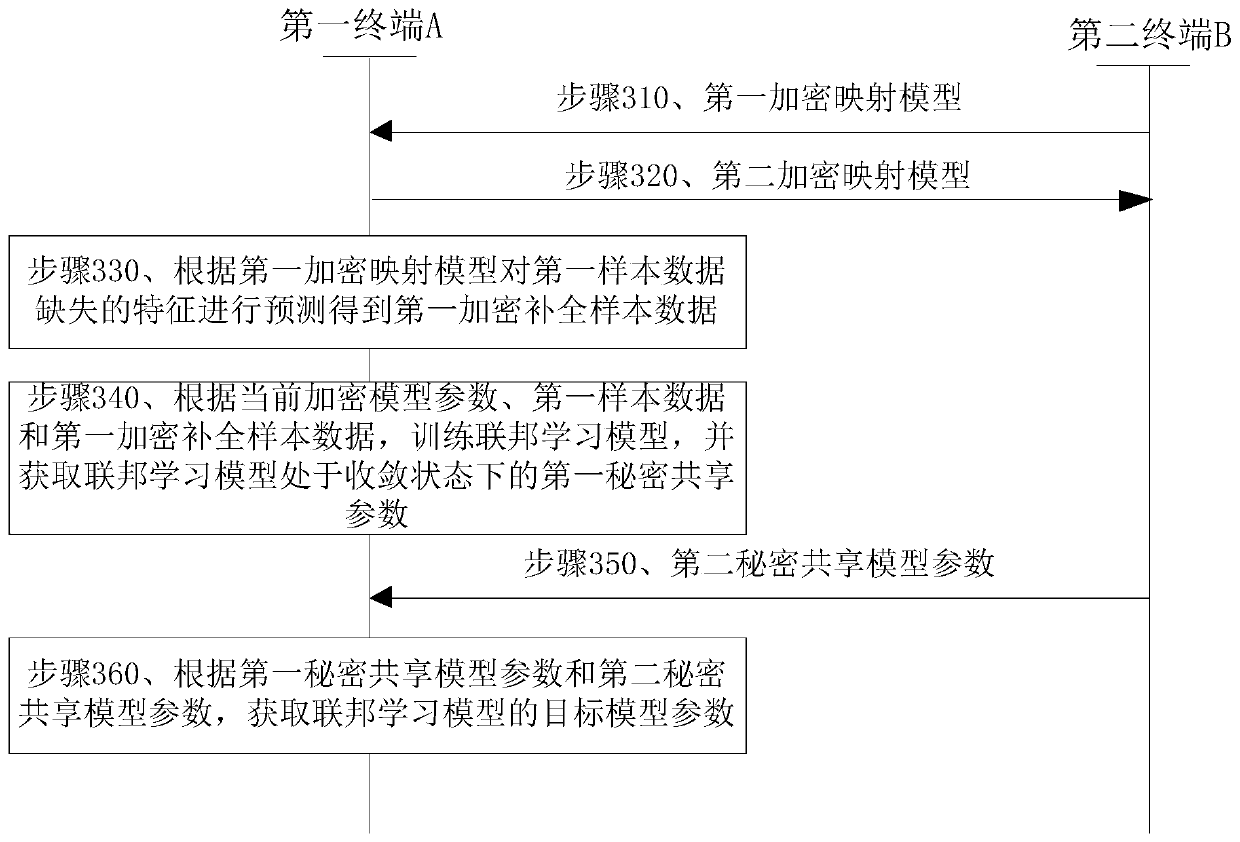
Model parameter training method and device based on federal learning
ActiveCN110288094AImprove experienceProtect private dataMachine learningPattern recognitionModel parameters
The invention discloses a model parameter training method and device based on federal learning. The method comprises the steps of using a first terminal to receive a first encryption mapping model sent by a second terminal; predicting the missing feature of the first sample data according to the first encryption mapping model to obtain the first encryption complement sample data; training a federal learning model according to the current encryption model parameters, the first sample data and the first encryption completion sample data, and obtaining a first secret sharing loss value and a first secret sharing gradient value; and if it is detected that the federal learning model is in a convergence state, obtaining a target model parameter according to the updated first secret sharing model parameter corresponding to the first secret sharing gradient value and a second secret sharing model parameter sent by the second terminal. According to the method, by adopting a secret sharing mode, the training process of the federated learning model does not need the assistance of a second collaborator, and the user experience is improved.
Owner:WEBANK (CHINA)
Method and mobile terminal for multimedia information sharing
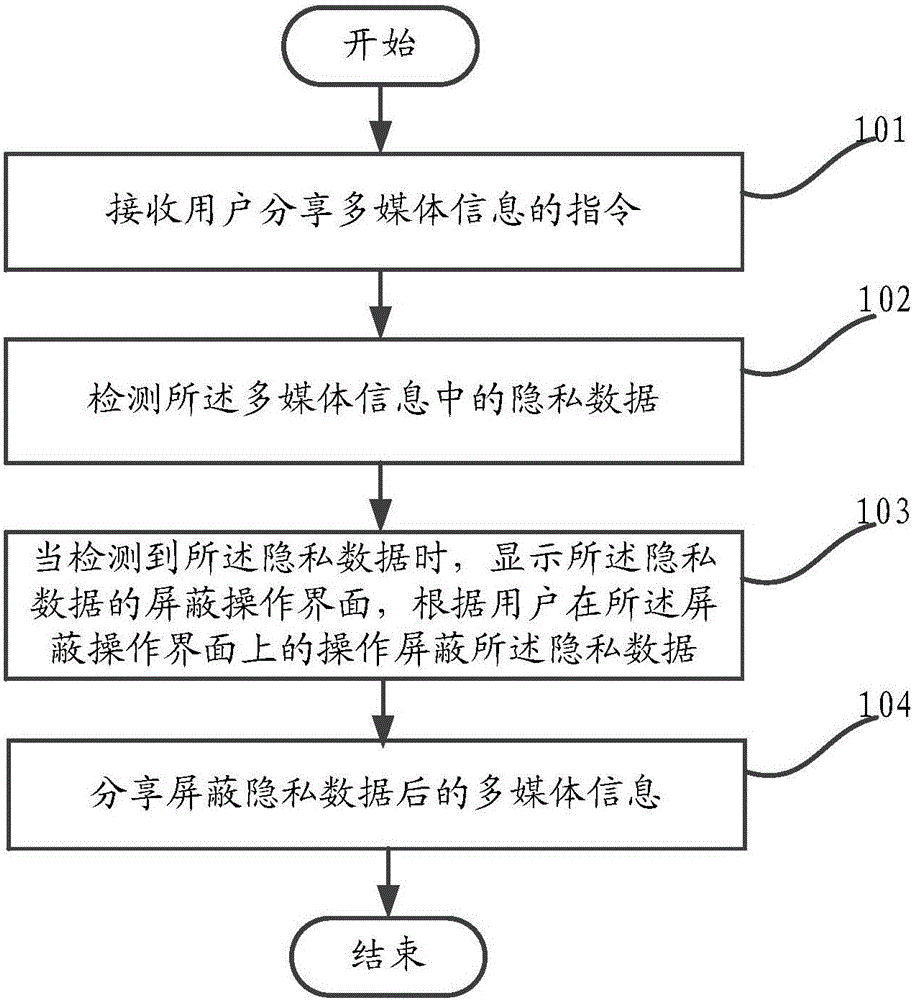
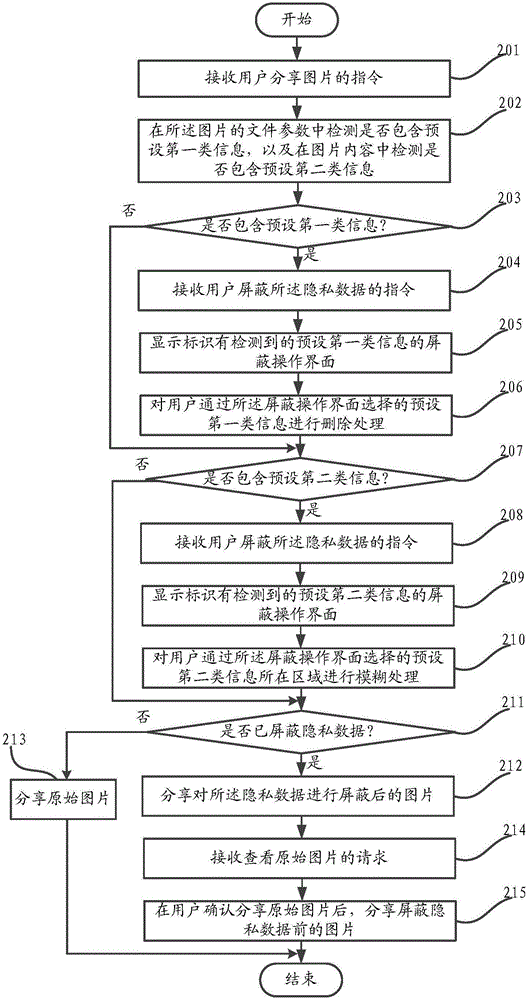
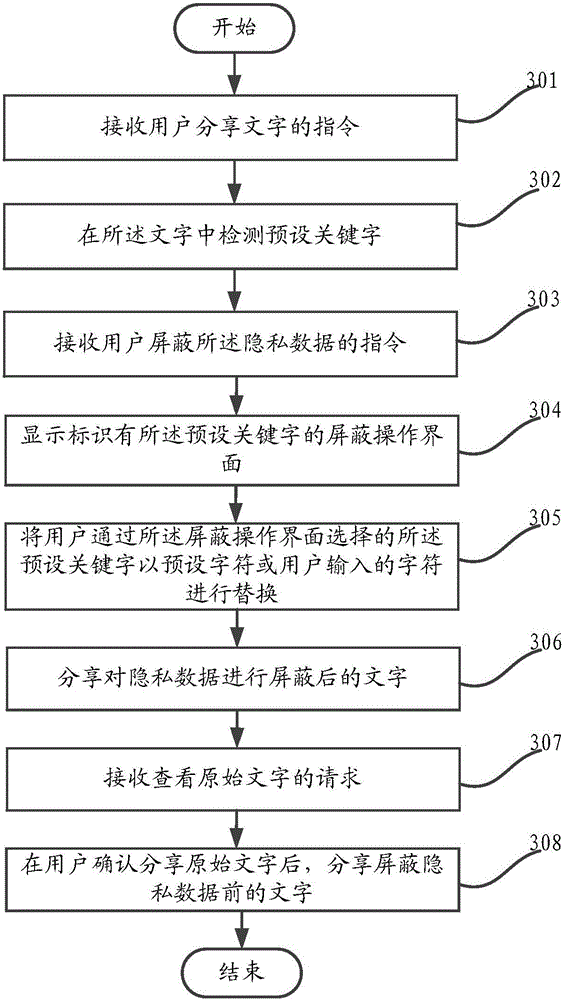
ActiveCN106055996AIncreased Privacy DataProtect private dataDigital data protectionComputer terminalMultimedia information
The invention provides a method for multimedia information sharing and belongs to the technical field of mobile communications. The method for the multimedia information sharing comprises the steps that a user' instruction for sharing multimedia information is received; private data in the multimedia information is detected; a shielding operation interface of the private data is displayed when the private data is detected, and the private data is shielded according to the user's operation on the shielding operation interface; and the multimedia information of which the private data is shielded can be shared. The invention also discloses a relevant mobile terminal. The method for the multimedia information sharing provided by the invention solves the problems in the prior art that efficiency of the multimedia information sharing is low, and the private data in the multimedia information cannot be protected comprehensively. Through automatic detection of the private data and provision of the rapid shielding interface, the efficiency for the multimedia information sharing is increased; and the method and the mobile terminal are applicable to different types of multimedia information and can comprehensively protect the private data in the multimedia information.
Owner:VIVO MOBILE COMM CO LTD
Model parameter determination method and device based on federal learning
The invention discloses a model parameter determination method and device based on federal learning. The method comprises the following steps: a second terminal receiving first encrypted data sent by a first terminal, wherein the first encrypted data is obtained by encrypting label data by the first terminal according to a preset encryption algorithm; according to the first encrypted data, the sample feature data and the current feature parameters of the sample feature data, using a preset algorithm to obtain second encrypted data comprising an encryption gradient value and an encryption loss value, and receiving a first gradient value and a first loss value sent by the first terminal according to the second encrypted data; according to the first gradient value and the current characteristic parameter of the sample characteristic data, obtaining a first characteristic parameter by adopting a preset characteristic parameter algorithm; and if it is detected that the first characteristic parameter is in a convergence state according to the first loss value, determining the first characteristic parameter as a model parameter of the sample model to be trained. According to the method, a third-party collaborator is not needed, and the training efficiency is improved.
Owner:WEBANK (CHINA)
Privacy protection method based on location service in scene of Internet of Things (IOT)
ActiveCN103037306AGuaranteed privacy and securityReduce security risksPayment architectureTransmissionProtocol for Carrying Authentication for Network AccessInternet of Things
Provided is a privacy protection method based on location service in a scene of the Internet of Things (IOT). The privacy protection method based on the location service in the scene of the IOT comprises two privacy protection schemes according to the characteristics on the basis of the location service and the privacy protection level, namely an absolute privacy query scheme for a quite high security level and a query privacy scheme for a quite low security level. Through analysis of application scenes, the secure multi-party computation technology is integrated into IOT location privacy protection, by utilization of technologies such as adding random numbers, using dot product properties, and carrying out homomorphic encryption and oblivious transfer protocols, a dot which is nearest to a query input location in a database to be queried is calculated and found out, different levels of protection measures are taken according to the different application scenes, and therefore the effect that the privacy of query input, query results and contents of the database to be queried is protected is achieved in the absolute privacy protection scheme, and the privacy of the query input and the query results is protected in the query privacy protection scheme.
Owner:NANJING UNIV OF POSTS & TELECOMM
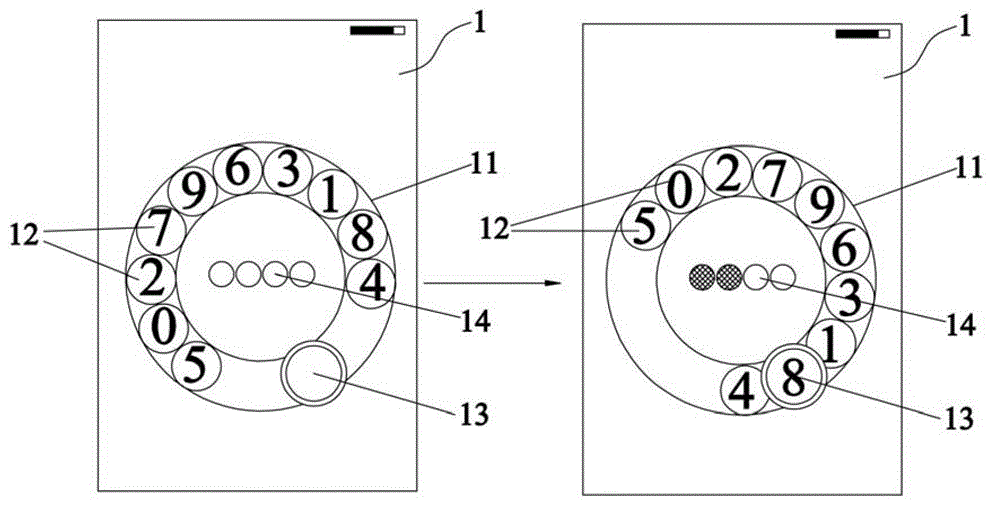
Touch screen unlocking method and system as well as communication terminal
InactiveCN102945118AImprove securityProtect private dataDigital data authenticationInput/output processes for data processingUser FriendlyPassword
The invention discloses a touch screen unlocking method and system as well as a communication terminal; and the touch screen unlocking method comprises the following steps: starting an unlocking interface; inputting at least one password information through the unlocking interface; receiving input password information; when the input password information is matched with a preset unlocking password, unlocking a touch screen and entering a preset application interface; and otherwise, receiving the input password information again. Compared with the prior art, the touch screen unlocking method disclosed by the invention has the advantages as follows: the touch screen is unlocked to enter the preset application interface as long as the password information input by a user through the touch screen is matched with the preset unlocking password on a terminal, so that the traditional direct sliding or down-pulling unlocking is substituted; therefore, the safety of data on the terminal is enhanced; according to the invention, as an unlocking plate, which is touched to rotate, is adopted in the password information inputting method, the unlocking interest is enhanced, so that user-friendly experience value of the user is increased; and moreover, information corresponding to character bits on the unlocking plate is dynamically changed, so that the input concealment is enhanced to guarantee the safety of the data on the terminal.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
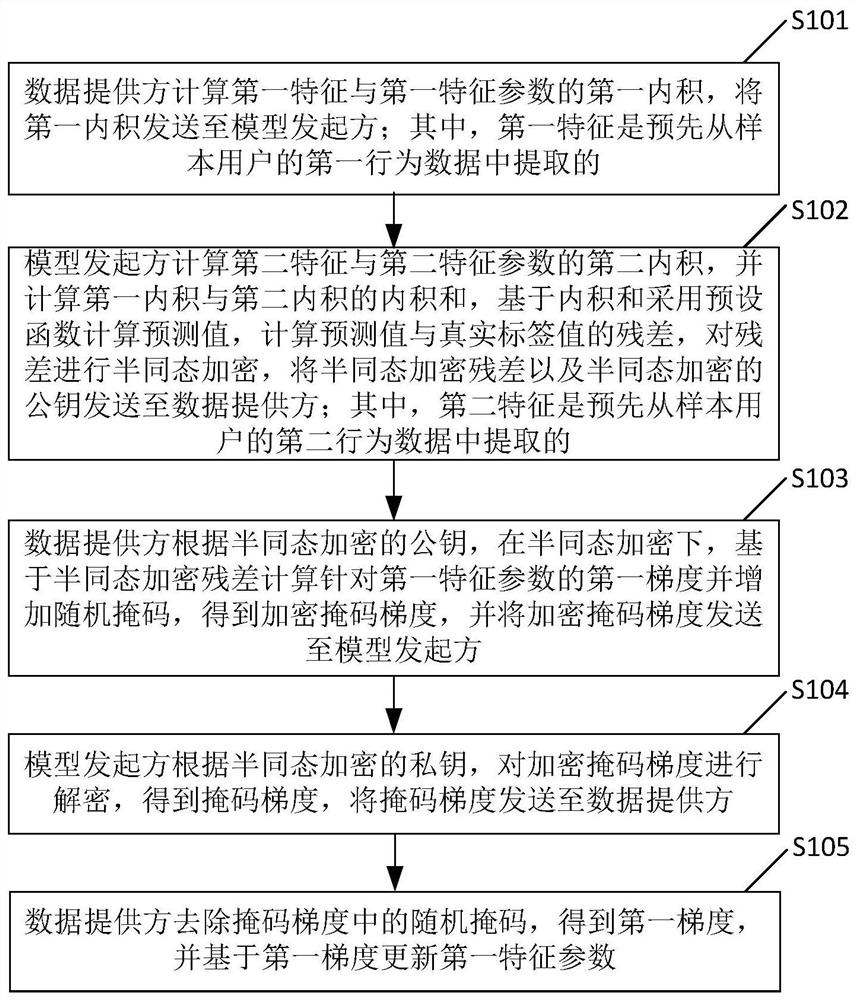
Regression model training method and system without trusted third party in longitudinal federated learning
The embodiment of the invention provides a regression model training method and system without a trusted third party in longitudinal federated learning. A data provider sends a first inner product to a model initiator; the model initiator calculates an inner product sum of the first inner product and the second inner product, calculates a predicted value by adopting a preset function, calculates a residual error between the predicted value and a real label value, performs semi-homomorphic encryption on the residual error, and sends the semi-homomorphic encryption residual error and a semi-homomorphic encryption public key to the data provider; the data provider calculates a first gradient for the first characteristic parameter and adds a random mask under semi-homomorphic encryption; the model initiator decrypts the encrypted mask gradient according to the semi-homomorphic encrypted private key, and sends the mask gradient to the data provider; and the data provider removes the random mask in the mask gradient to obtain a first gradient, and updates the first feature parameter. The training of the regression model in the longitudinal federated learning is completed on the premise of not depending on a third-party mechanism and protecting the privacy data of the two parties.
Owner:深圳市洞见智慧科技有限公司
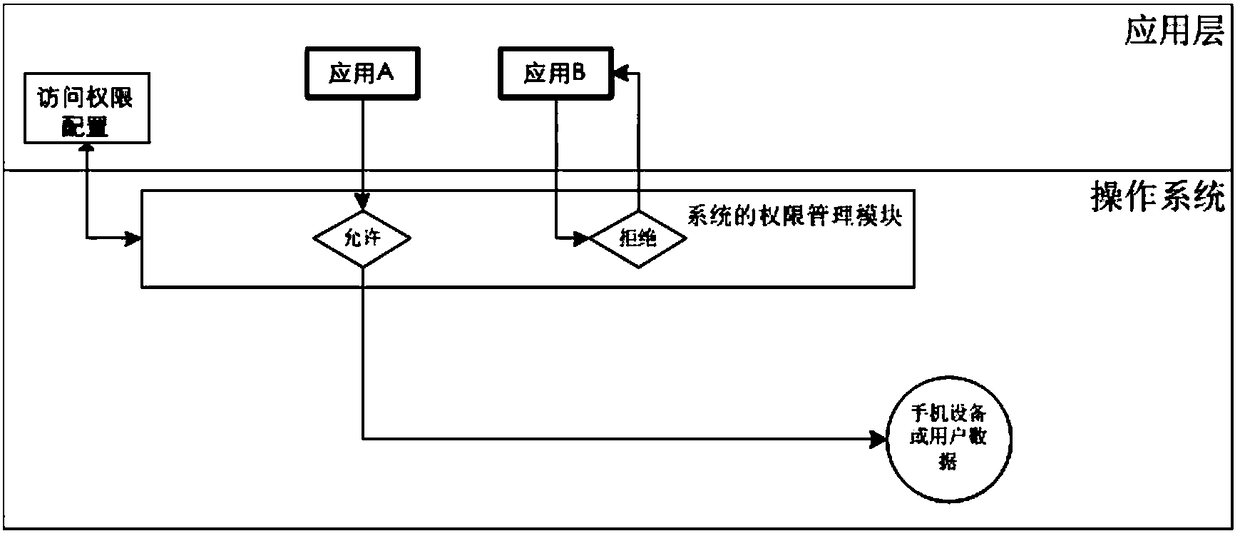
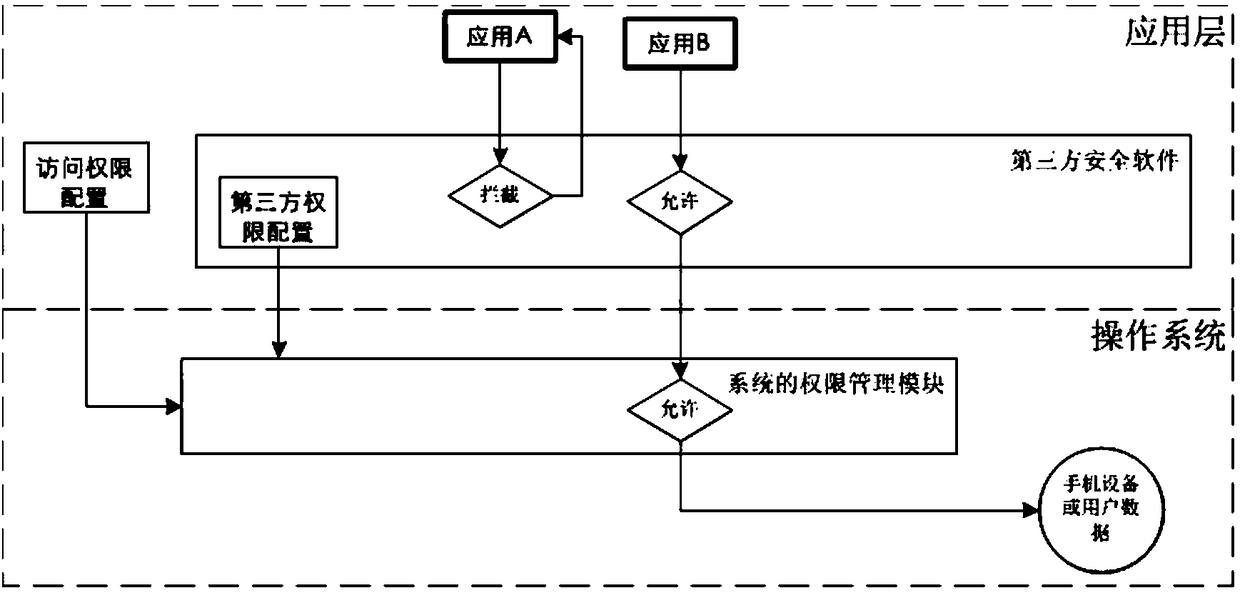
Safety system and safety protection method for mobile terminal
InactiveCN103313238APrevent disclosure or theft of personal informationProtect private informationSecurity arrangementApplication softwareTerminal system
The invention discloses a safety system for a mobile terminal. The safety system comprises a user data isolation module; the user data isolation module comprises a user authority management module and a data protection module and is used for protecting privacy data of a user; the user can enter standby interfaces corresponding to different authority passwords by the aid of the user authority management module; the data protection module is arranged between application and a database interface and is used for managing user data access authority of application programs. The invention further discloses a safety protection method for the mobile terminal. The safety system and the safety protection method have the advantages that the real data can be protected by the system for the mobile terminal, personal information of the mobile terminal is prevented from being revealed or stolen, and the privacy information of the user can be effectively protected.
Owner:TIANYI TELECOM TERMINALS
Message reminding and displaying method applied to multi-user intelligent mobile terminal
InactiveCN105653957AImprove securityProtect private dataDigital data authenticationSubstation equipmentComputer hardwareUser privacy
The invention discloses a message reminding and displaying method applied to a multi-user intelligent mobile terminal. The message reminding method comprises steps of determining whether use environment, where a multi-user intelligent terminal lies is safe after a message is acquired, publically reminding the message if the use environment is safe, and reminding the message in a hidden way if the use environment is not safe. Safety of the use environment, where the current terminal lies is determined before the message is reminded; when the use environment is not safe, the message is reminded in the hidden way, so a user for the current terminal cannot learn content information of the message; only when the use environment is determined to be safe, the message can be reminded in a public way; and therefore, safety of message reminding in the multi-user intelligent mobile terminal can be improved, so user privacy data can be well protected.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
Tamper-proofing method of reputation information based on block chain
ActiveCN106779975ASolve forksProtect private dataBuying/selling/leasing transactionsTransmissionTamper resistanceBlockchain
The invention discloses a tamper-proof method of reputation information based on a block chain. The tamper-proof method is characterized by comprising the first step of building a reputation block chain for storing the reputation information; making a user provide a block to a transaction system when there is a deal in the transaction system, and making the transaction system calculate the reputation value of the block, wherein after finishing the deal, the transaction system returns the transaction information to the reputation block chain, and then the reputation block chain constructs a new block; the second step of checking whether furcations occur in the reputation block chain or not and removing possible furcations in the reputation block chain when the new block is constructed. According to the tamper-proof method of reputation information based on the block chain, the reputation information of a merchant can be authentically recorded, and the reputation information is inalterable. In this way, an intangible reputation degree can be effectively converted into a tangible inalterable reputation value, and thus the reputation of the merchant is more authentic and more reliable.
Owner:HEFEI UNIV OF TECH
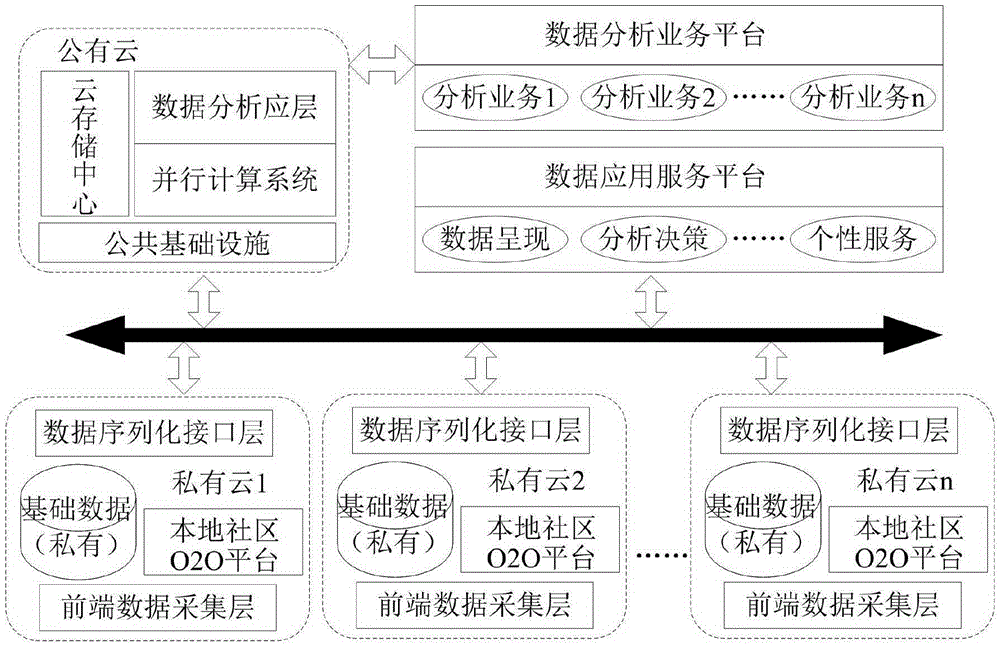
Community O2O-based data analysis system and implementation method thereof
InactiveCN105405047AProtect private dataEasy accessRelational databasesData miningComputing systemsCollections data
The invention relates to a community O2O-based data analysis system and an implementation method thereof. According to the data analysis system, with a hierarchical hybrid cloud computing system adopted as a based, community O2O cloud adopted as private storage resources, public cloud adopted as computing resources, local data requiring analysis are placed in public cloud, after data analysis is completed in the public cloud, results are stored in the O2O private cloud through a local serialization interface. A core process of data analysis and processing includes the following steps that: a community O2O-based hierarchical hybrid cloud computing system is built; a community O2O data serialization interface is built according to data analysis requirements; data collection scripts are deployed; a community O2O-based data analysis system platform is built; and a data analysis platform is deployed. With the community O2O-based data analysis system and the implementation method thereof of the invention adopted, community O2O private data can be protected; virtual storage resources, virtual computing resources and networks can be provided for community O2O platforms; and therefore, merchants can quickly join a community O2O integrity business district.
Owner:GUANGDONG KEHAI TECH DEV CO LTD
Privacy information protection method based on K-means clustering
ActiveCN110233730AProtect private dataPrivacy protectionKey distribution for secure communicationPublic key for secure communicationCiphertextClient-side
The invention discloses a privacy information protection method based on K-means clustering, and the method comprises the steps: carrying out the data encryption of a plurality of clients CUi, obtaining an encrypted ciphertext, and uploading the encrypted ciphertext to a cloud server; the client CUi, the cloud server CSP and the auxiliary cloud server ACSP performing data interaction calculation to obtain a re-encryption key; the cloud server receiving the encrypted ciphertext, re-encrypting the encrypted ciphertext to obtain a re-encrypted ciphertext of the same public key, and converting there-encrypted ciphertext into a Pillier encrypted ciphertext; the cloud server side obtaining the encrypted ciphertext of the Paillier and then calculating clustering; and the cloud server firstly converting the ciphertext of the clustering result into the ciphertext re-encrypted by the bidirectional addition homomorphic agent, then converting the ciphertext into the ciphertext under the public key of the client, and finally returning the ciphertext of the clustering result to the client for decryption. According to the method, the ciphertext of different public keys is clustered, the clustering result under the same public key is converted into the clustering result under different public keys to be returned to the client, and meanwhile, the private data of the client and the privacy of the clustering center are protected.
Owner:JINAN UNIVERSITY
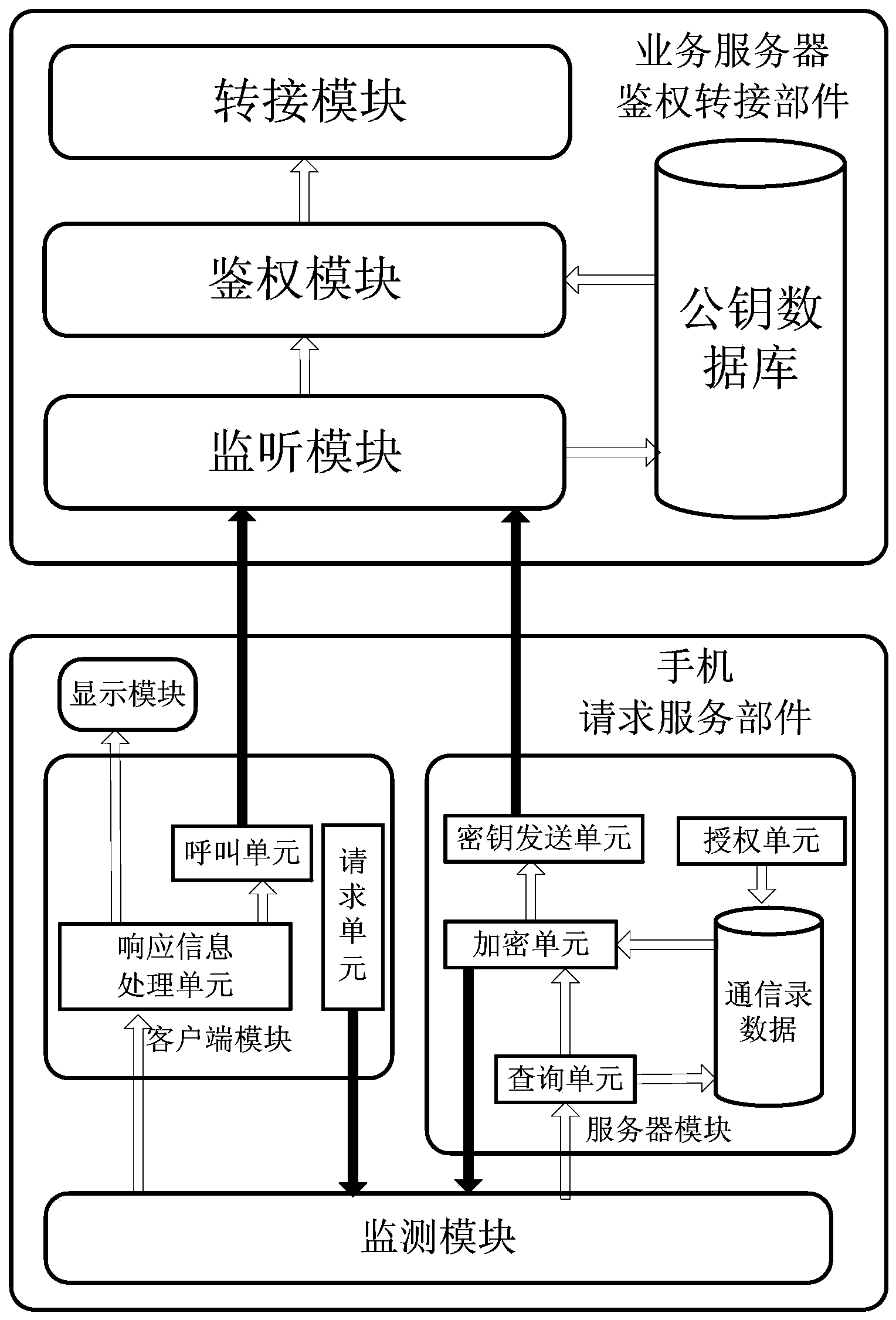
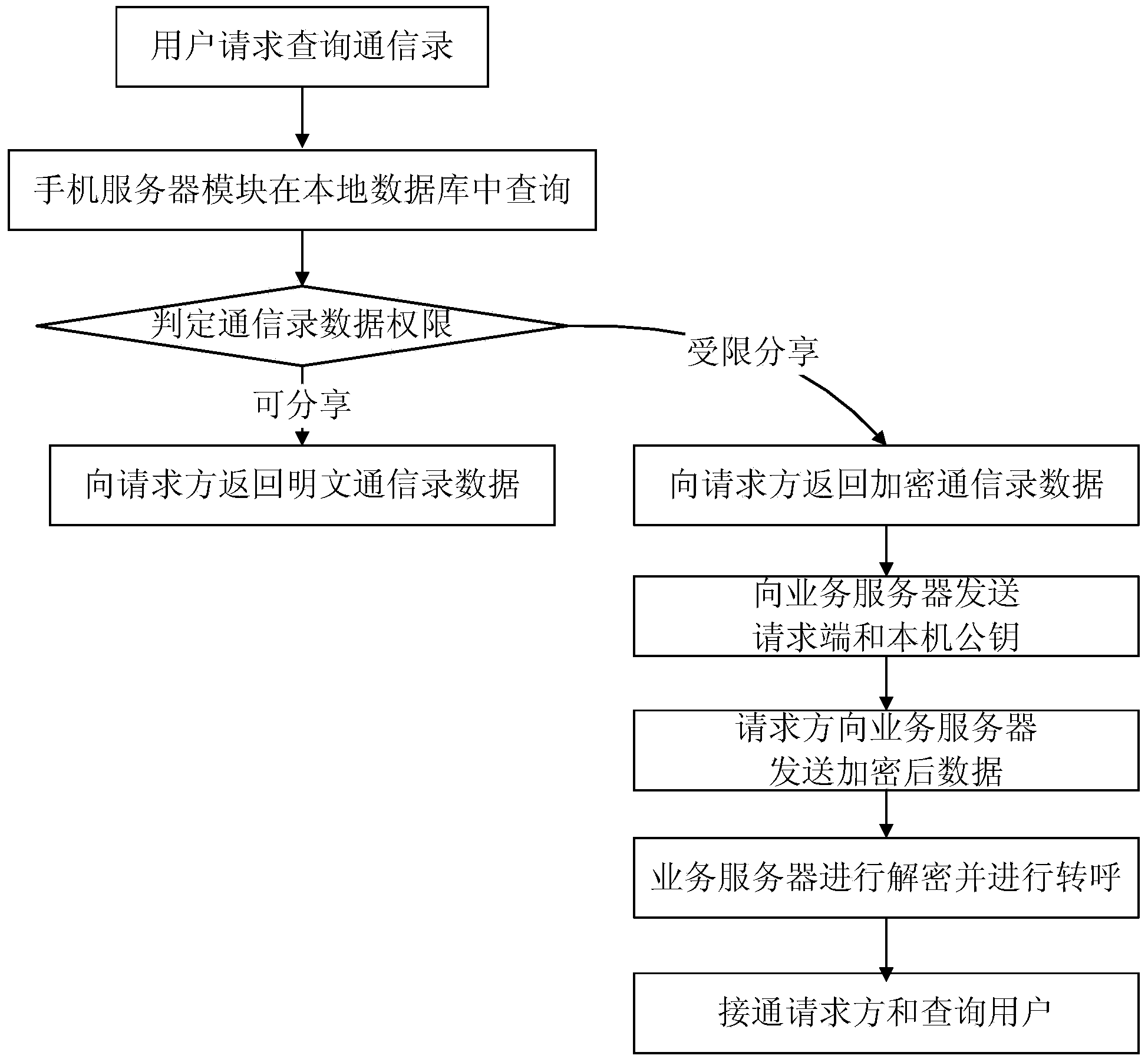
Personal data safety sharing system and method for mobile phone
ActiveCN103401949AProtect private dataImprove communication efficiencyTransmissionSecurity arrangementTransfer procedureInternet privacy
The invention discloses a personal data safety sharing system and a method for a mobile phone. The system comprises a mobile phone provided with a request service component and a core network service server provided with authentication switchover component, wherein the request service component of the mobile phone comprises a monitoring module, a server module, a client module and a display module, and the authentication switchover component of the service server comprises a monitoring module, an authentication module, a call transfer module, and a public key database interactive with the monitoring module and the authentication module. A working method of the system is characterized in that the system divides an authority of contact list data of a user into two kinds, namely a sharable authority and a restricted sharing authority, according to the safety authority set by the user, and makes corresponding different operations according to the different authorities. The mobile phone serves as a server to response sharing requests of other contacts on contact list information, the safety authority is set for personal information, and certain personal privacy information is encrypted by a key technology, so that personal privacy cannot be leaked in a transmission process of the personal privacy information.
Owner:BEIJING UNIV OF POSTS & TELECOMM
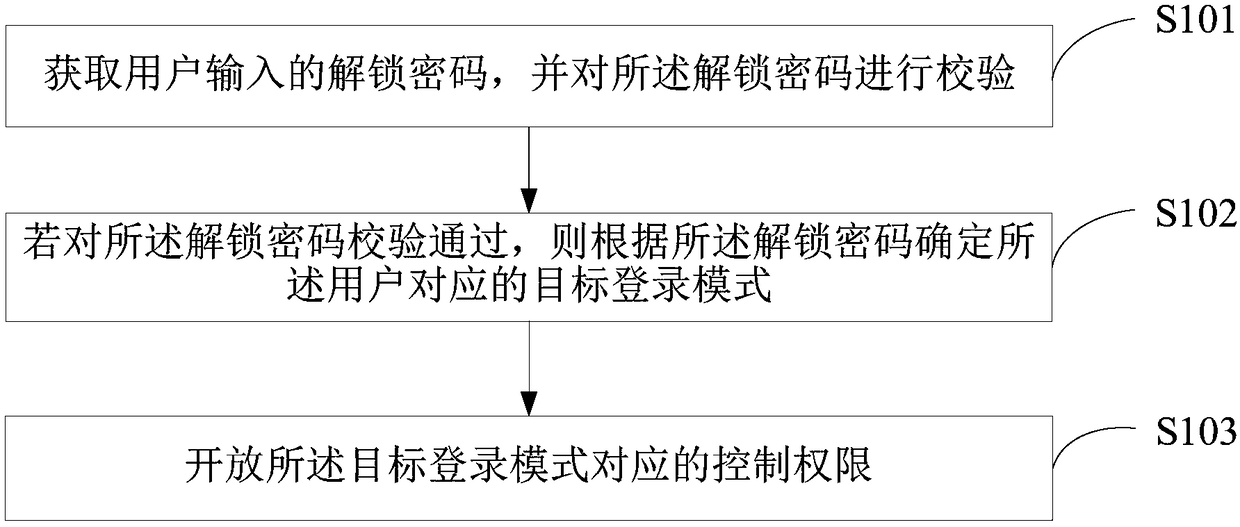
Multi-user login mode realization method, terminal and computer readable storage medium
ActiveCN108171025AProtect private dataReduce development costsDigital data protectionDigital data authenticationLimited accessInternet privacy
Embodiments of the invention disclose a multi-user login mode realization method, a terminal and a computer readable storage medium. The method comprises the steps of obtaining an unlocking password input by a user, and checking the unlocking password; if the check of the unlocking password is passed, determining a target login mode corresponding to the user according to the unlocking password; and opening a control permission corresponding to the target login mode. Different login modes are identified through unlocking passwords to distinguish control permissions; privacy data of the user isprotected; and multiple user modes are realized under the condition of not performing data isolation, so that the development cost can be reduced and a visitor cannot perceive a limited access permission.
Owner:SHENZHEN TRANSSION HLDG CO LTD
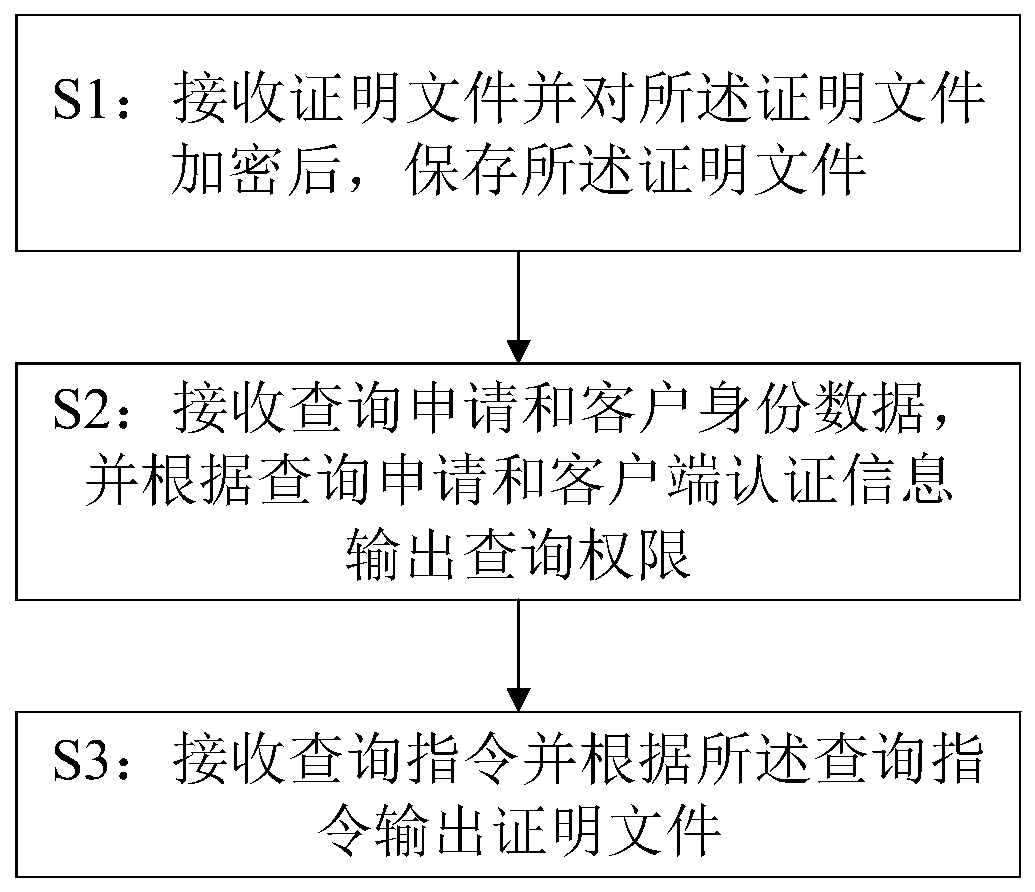
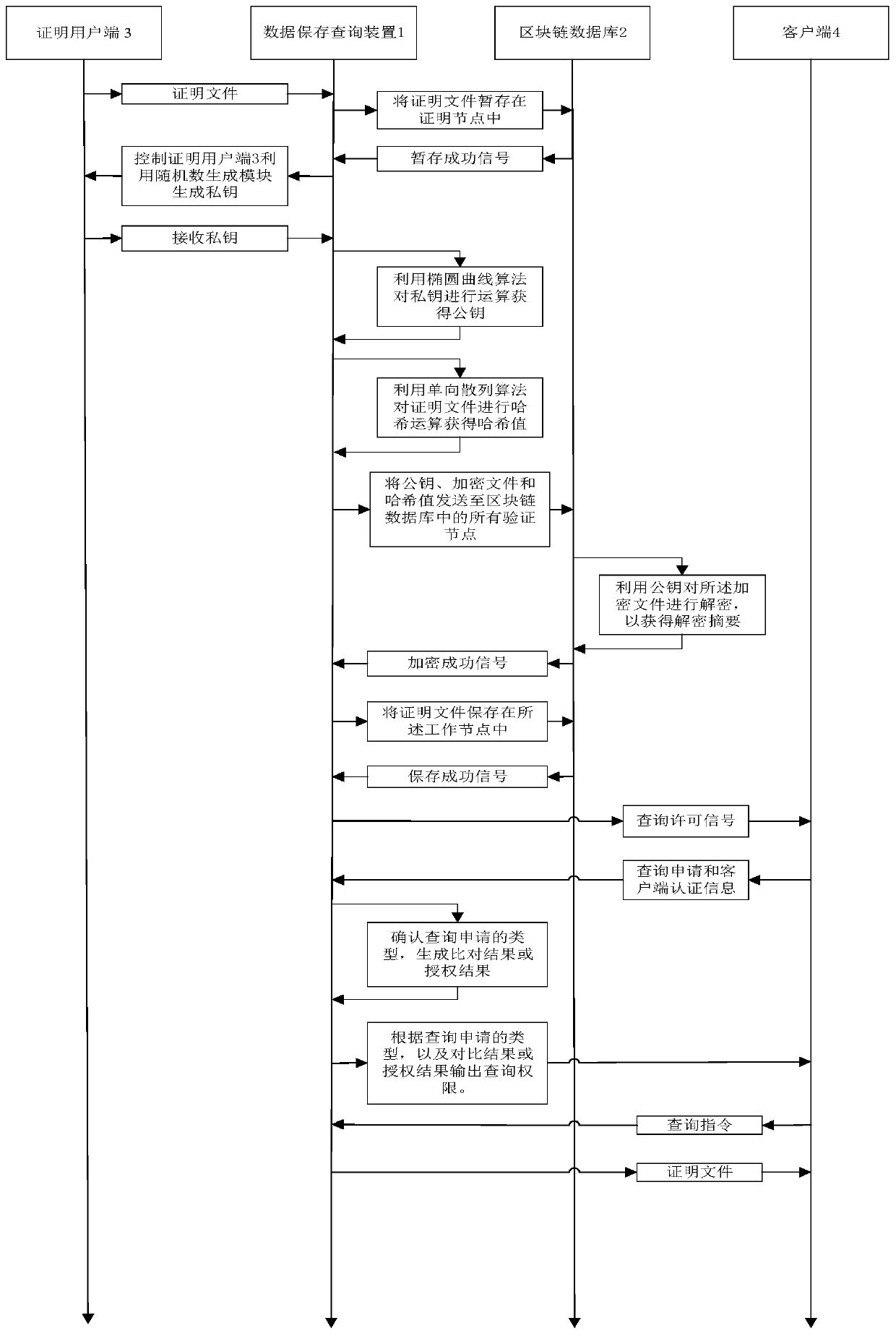
Data storage and query method and device, computer system and readable storage medium
PendingCN109886026ACircumstances Affecting Comprehensive Assessment ResultsImprove creditDigital data protectionTamper resistanceComputerized system
The invention discloses a data storage and query method and device, a computer system and a readable storage medium. By utilizing a block chain database, the block chain database is provided with a plurality of proof nodes, and the method comprises the following steps of receiving a proof file, encrypting the proof file, and storing the proof file; receiving the query application and the client authentication information, and outputting a query authority according to the query application and the client authentication information; and receiving a query instruction and outputting the proof fileaccording to the query instruction. According to the invention, nodes except the block chain database are prevented from tampering the proof file; the comprehensive evaluation result of the company is influenced by counterfeiting and counterfeiting, and meanwhile, the situation that a certain proof node in the block chain database tampers proof files responsible for other proof nodes is also avoided, so that the credit of the comprehensive evaluation result of the company is improved. The method adapts to the requirement of the related party for the proof file of the client, protects the private data, and eliminates the risk of commercial secret leakage.
Owner:PING AN TECH (SHENZHEN) CO LTD
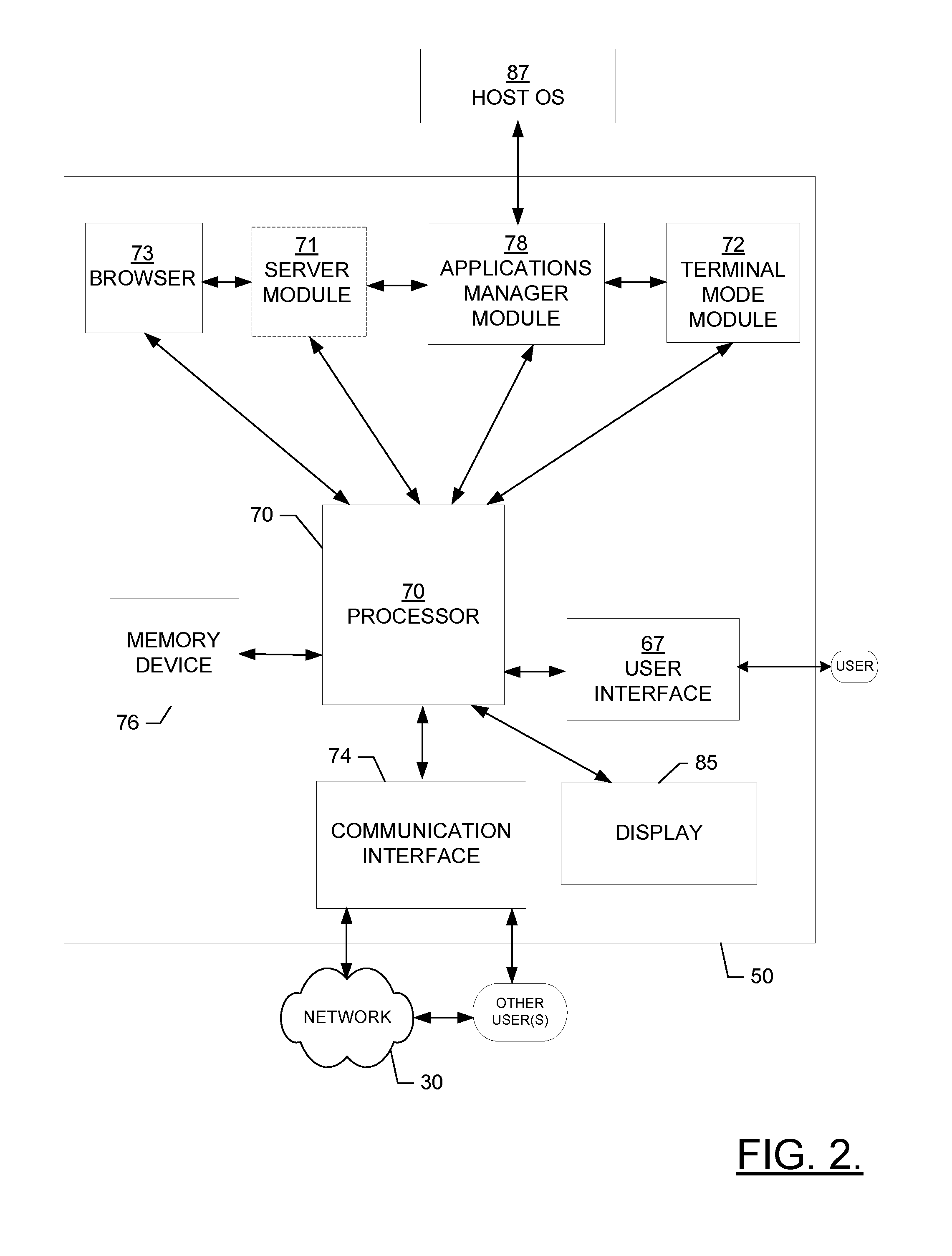
Methods, apparatuses and computer program products for provisioning applications to in vehicle infotainment systems with secured access
ActiveUS8621483B2Efficient and reliableEfficient and reliable provisionProgram controlSoftware deploymentApplication programming interfaceIn vehicle
An apparatus for providing one or more applications to an IVI client device(s) may include a processor and memory storing executable computer code causing the apparatus to at least perform operations including providing an application(s) and associated data to a device in response to receipt of an indication of a selection associated with the application(s). The computer program code may further cause the apparatus to enable the application(s) to access requested data via a plurality of application programming interfaces during execution of the application. The computer program code may further cause the apparatus to provide the requested data to the application in response to receipt of a message(s) generated by a first application programming interface of the interfaces that received a request for the requested data from a second application programming interface of the interfaces. Corresponding methods and computer program products are also provided.
Owner:NOKIA TECHNOLOGLES OY
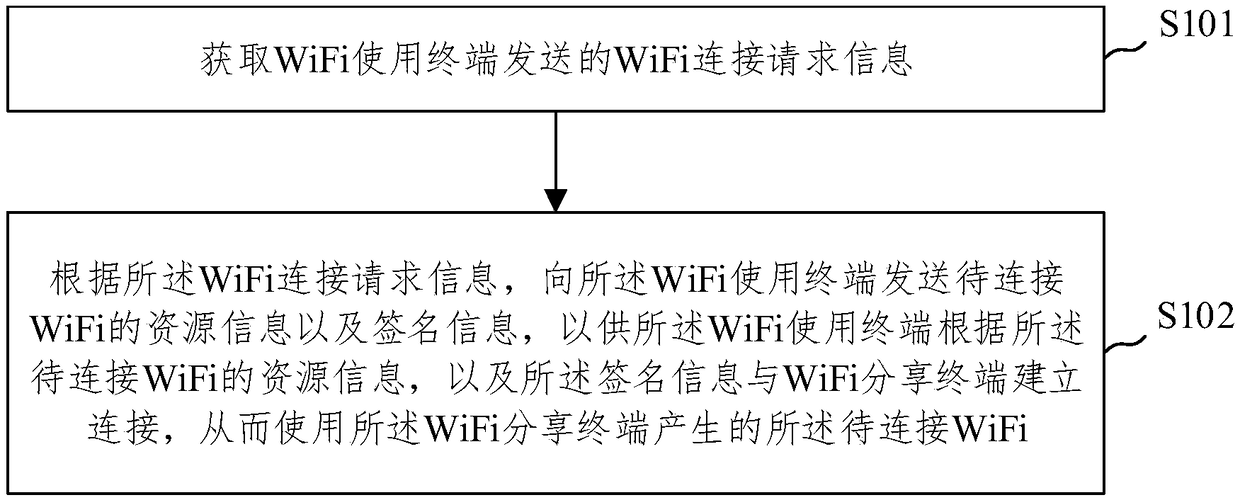
WiFi sharing method and server based on block chain
ActiveCN109168139AImprove securityIncrease usageAccounting/billing servicesTelephonic communicationResource informationUser privacy
The invention provides a WiFi sharing method and a server based on a block chain. The method comprises the following steps: acquiring WiFi connection request information sent by a WiFi using terminal;obtaining WiFi connection request information sent by a WiFi using terminal; obtaining WiFi connection request information from the WiFi using terminal. According to the WiFi connection request information, sending resource information and signature information of WiFi to be connected to the WiFi using terminal, so that the WiFi using terminal establishes a connection with the WiFi sharing terminal according to the resource information of the WiFi to be connected and the signature information, thereby using the WiFi to be connected generated by the WiFi sharing terminal. The invention provides a block chain-based WiFi sharing method and a server, By designing a decentralized form of WiFi sharing platform based on block chain, which improves the security of WiFi sharing network, Compatiblewith public WiFi and private WiFi, WiFi providers are authenticated and WiFi users are billed to make WiFi providers profitable, WiFi resources that motivate WiFi sharing and provide convenience to users are realized, user WiFi information is protected and user privacy data is protected.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Big-data dynamic memory integrity verification method based on lattice
InactiveCN103778387AResist attackPrivacy protectionDigital data protectionDynamic featureQuantum computer
The invention discloses a big-data dynamic memory integrity verification method based on a lattice. The big-data dynamic memory integrity verification method based on the lattice solves the problem that it is difficult for a quantum computer to crack lattice difficulty, high safety is achieved, dynamic change of data is supported, and operation efficiency is high. In order to support the dynamic feature of big data, the Merkle hash tree technology is adopted, and the privacy data of a computing platform can be effectively protected at the same time. In this way, the big-data dynamic memory integrity verification method based on the lattice can be widely applied to scenes relevant to the dynamic integrity verification of the big data.
Owner:SUZHOU INST FOR ADVANCED STUDY USTC
Model-based collaborative filtering method for privacy protection collaborative Web quality-of-service prediction
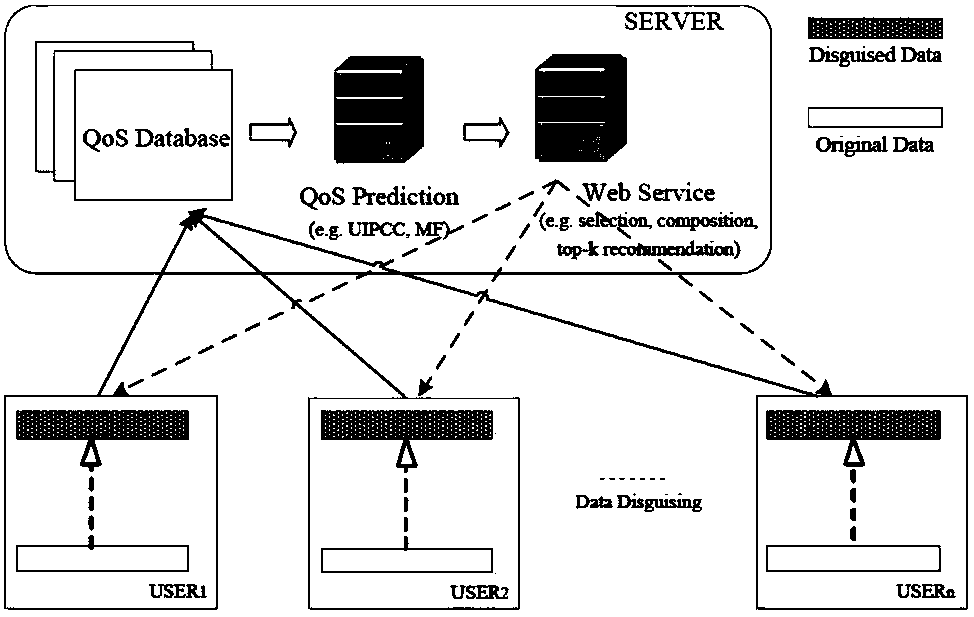
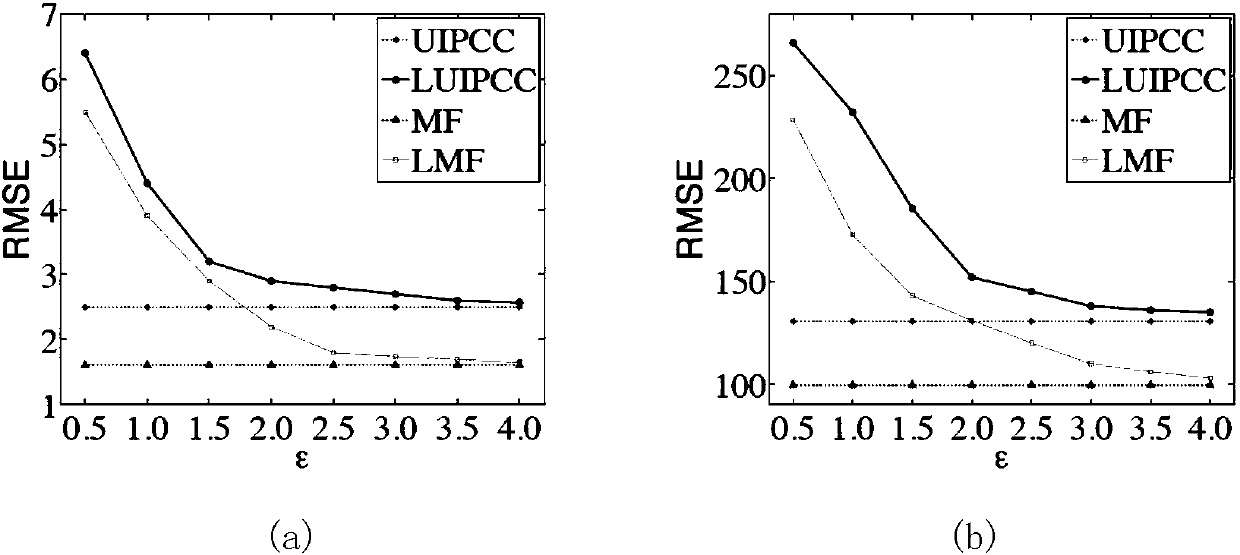
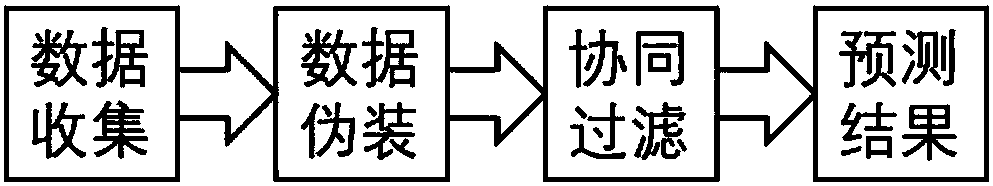
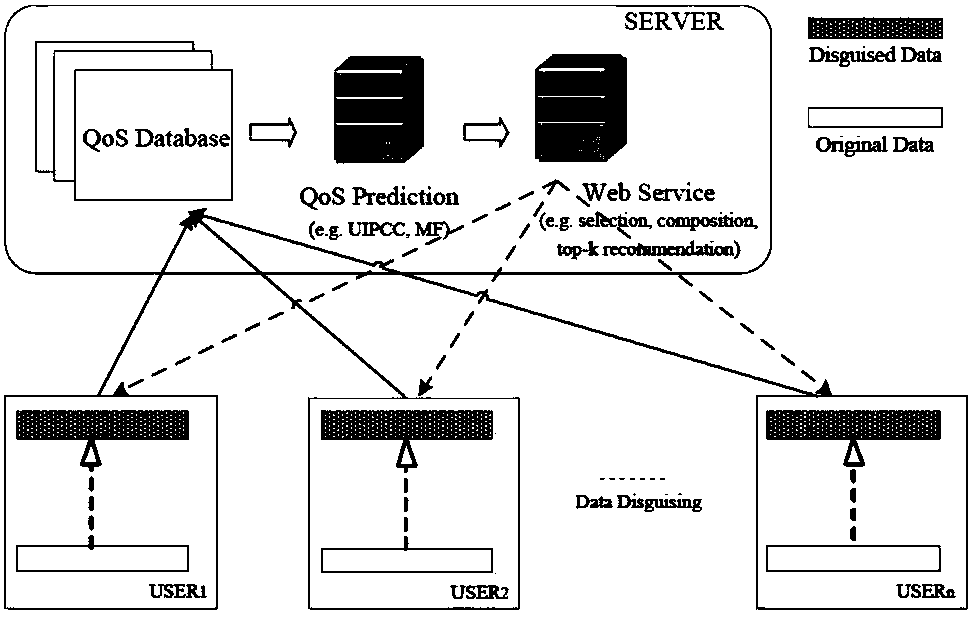
InactiveCN107679415AProtect private dataImprove performanceDigital data protectionData switching networksQuality of serviceWeb service
The invention discloses a model-based collaborative filtering method for privacy protection collaborative Web quality-of-service prediction. The method comprises the following steps of 1, performing data collection: locally collecting quality-of-service values, namely QoS values by users; 2, performing data disguise: disguising the QoS values; 3, performing model-based collaborative filtering on the disguised QoS values; and 4, predicting a result: predicting the result according to the collaboratively filtered QoS values. According to the method, differential privacy is introduced in a collaborative Web QoS prediction framework for the first time, so that the users can get maximum privacy protection by ensuring data availability. An experimental result shows that the method provides secure and accurate collaborative Web QoS prediction, and the model-based collaborative filtering method has superiority in the aspect of capturing a potential structure of QoS data.
Owner:SHENZHEN UNIV
Differential privacy prediction system and method combining privacy protection and Web quality of service
InactiveCN107659444AProtect private dataImprove performanceData switching networksQuality of serviceWeb service
The invention discloses a differential privacy prediction system combining privacy protection and Web quality of service. The system comprises a data collection module, a data hiding module, a collaborative filtering module and a prediction result module; the data collection module is used by each user to collect a quality of service value in local, namely, a QoS value; the data hiding module is used for hiding the collected quality of service value; the collaborative filtering module is used for performing collaborative filtering on the quality of service value hidden by the data hiding module; and the prediction result module is used for predicting a result via the quality of service value filtered by the collaborative filtering module. In addition, the invention further discloses a differential privacy prediction method combining privacy protection and Web quality of service. The differential privacy is imported in a collaborative Web service QoS prediction framework, and thus the user can obtain the maximum privacy protection by ensuring the availability of the data. The experimental results show that the system and method of the invention provide a secure and accurate QoS prediction for cooperative Web services.
Owner:SHENZHEN UNIV
Collaborative filtering recommendation method based on trustful privacy maintenance in personalized search
InactiveCN104156388AAchieve autonomous controlMake up for the lack of privacy protectionPlatform integrity maintainanceSpecial data processing applicationsPersonalized searchUser privacy
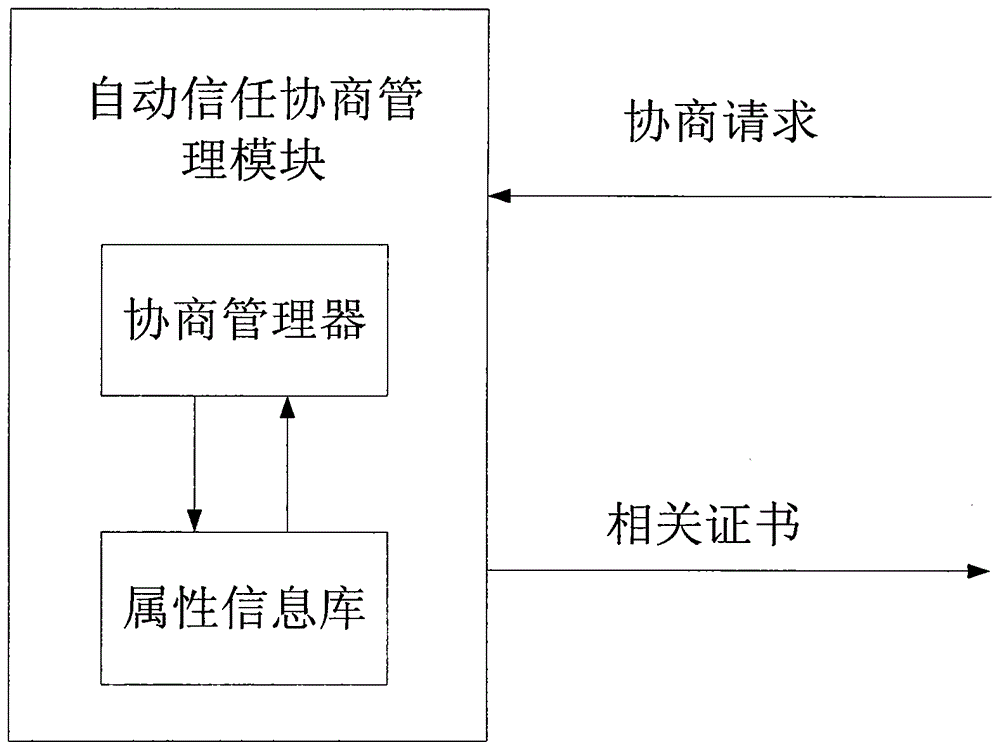
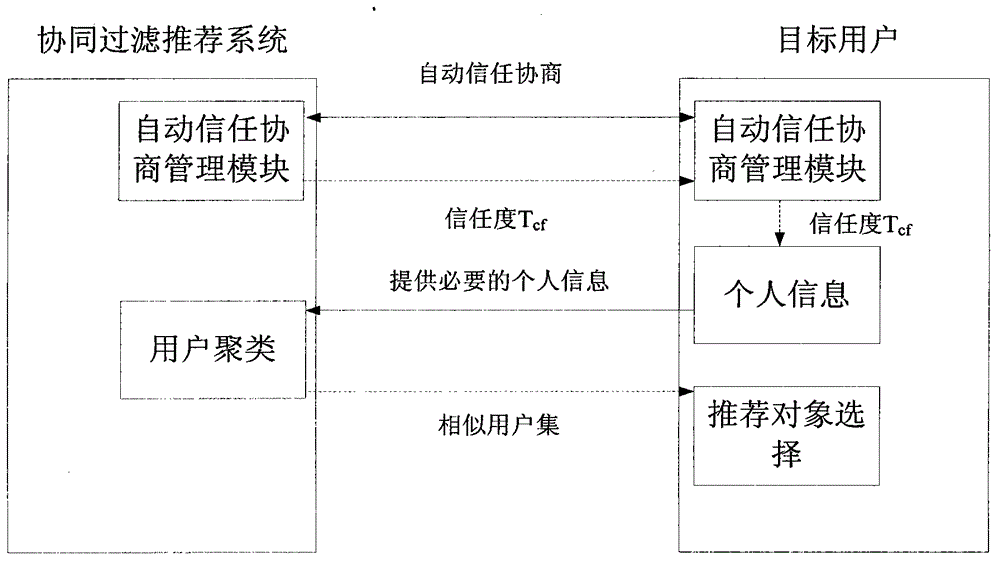
The invention relates to a collaborative filtering recommendation method based on trustful privacy maintenance in personalized search and belongs to the field of computer networks. According to the basic idea, firstly, the trust degree Tcf of a target user to the execution behavior of a collaborative filtering recommendation system is established by means of automatic trust negotiation between the target user and the collaborative filtering recommendation system; the target user judges the degree of disclosure of personal information according to the trust degree Tcf, the collaborative filtering recommendation system collects the personal information provided by the target user and conducts clustering on users to obtain an initial user set with the interest similar to that of the target user; finally, the target user selects a similar user with the trust degree not lower than the Tcf from the user set and makes the similar user as a recommended object. The collaborative filtering recommendation method based on trustful privacy maintenance can overcome the defect that an existing collaborative filtering recommendation method is short of privacy protection in the search and modeling process of personal information, control over the degree of disclosure of the personal information by the target user is achieved, and comprehensive protection is provided for privacy data of the users.
Owner:XIAN UNIV OF POSTS & TELECOMM
Internet site login system based on intelligent equipment monitoring and user identity recognition
ActiveCN110611685AImprove identityIdentity theftInternal/peripheral component protectionDigital data authenticationFull life cycleIdentity recognition
The invention provides an Internet site login system based on intelligent equipment monitoring and user identity recognition. The system comprises a cloud server and clients, and the clients comprisea user client, a maintenance client and a production client. The invention relates to an integrated system for controlling a user to log in an internet site through user identity recognition and binding of hardware features of intelligent equipment and the user identity recognition. Hardware characteristics of the intelligent equipment, all stages of the full life cycle of the intelligent hardware, ownership of a user to the intelligent equipment, login and query states of the user in a cloud server through the equipment, login and use of an internet site and other links can be tracked.
Owner:NANNING ZHISOU INFORMATION TECH
Information processing method and device
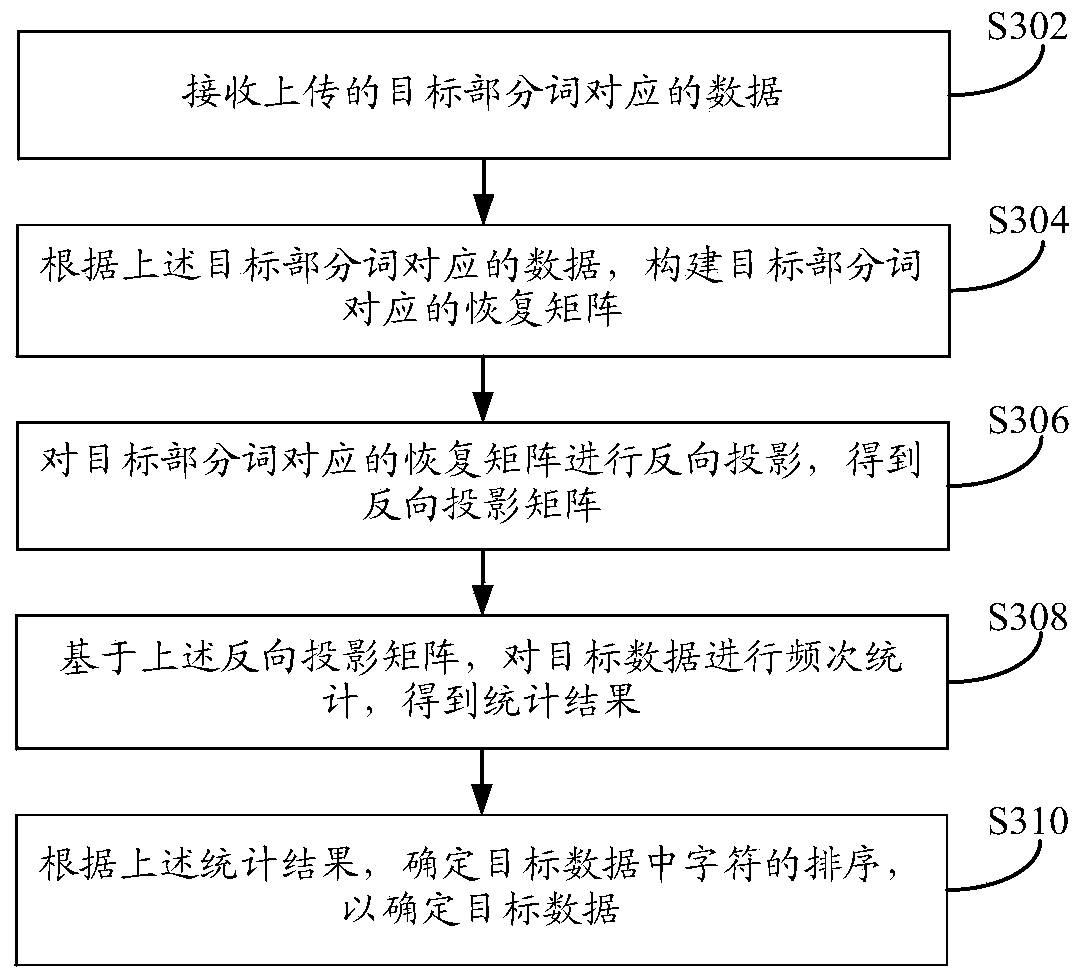
ActiveCN109829320AProtect private dataGood encryptionDigital data protectionText database indexingInformation processingHat matrix
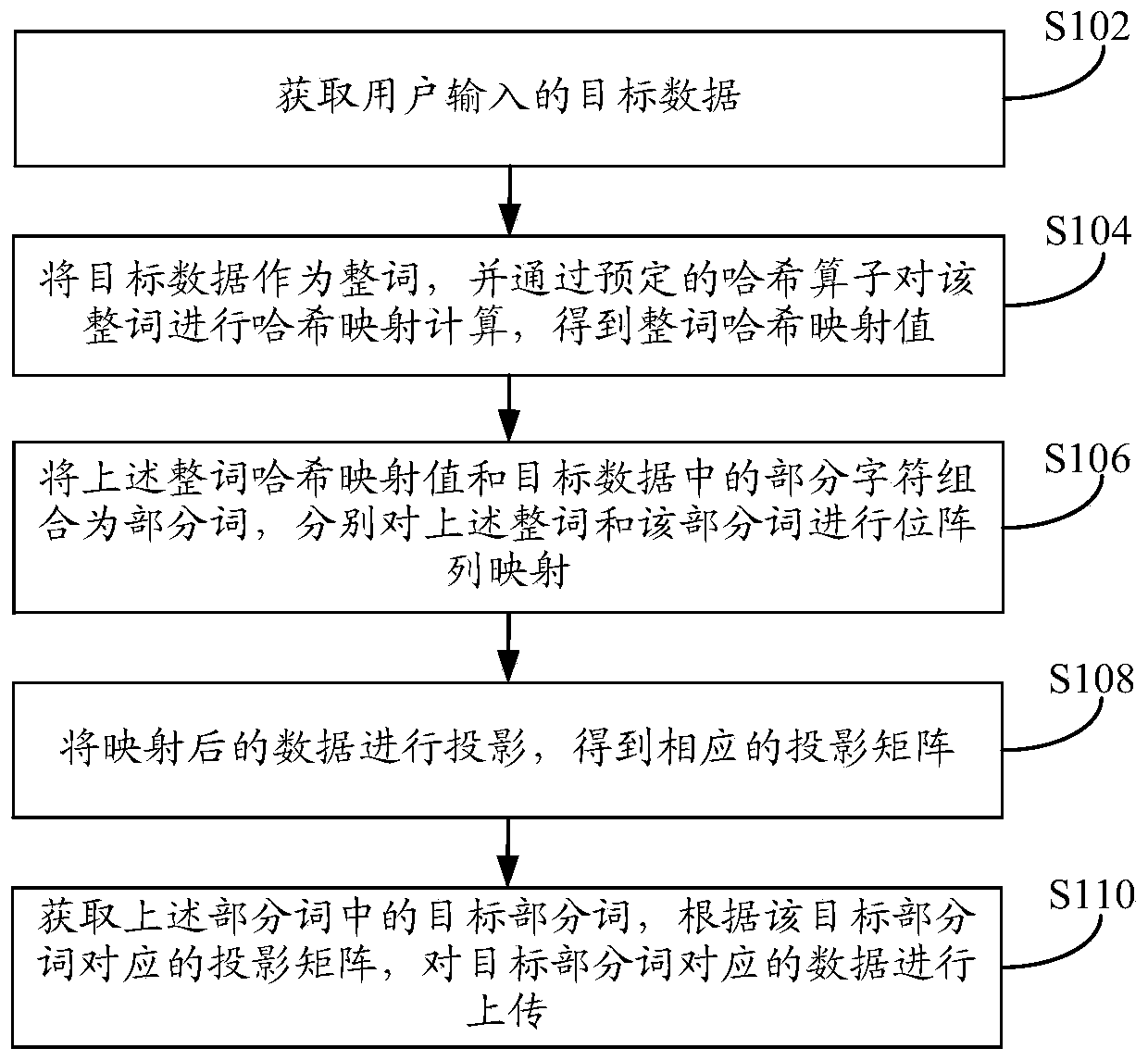
The embodiment of the invention discloses an information processing method and device. The method comprises the steps of obtaining target data input by a user; Taking the target data as a whole word,and performing Hash mapping calculation on the whole word through a predetermined Hash operator to obtain a whole word Hash mapping value; Combining the whole word Hash mapping value and a part of characters in the target data into a part of words, and respectively carrying out bit array mapping on the whole word and the part of words; Projecting the mapped data to obtain a corresponding projection matrix; And obtaining a target part of words in the part of words, and uploading data corresponding to the target part of words according to the projection matrix corresponding to the target part ofwords. According to the embodiment of the invention, the client encrypts the data in a hash mapping and projection manner, and the encryption performance is good, so that the data is safer in the transmission process.
Owner:郑州阿帕斯科技有限公司
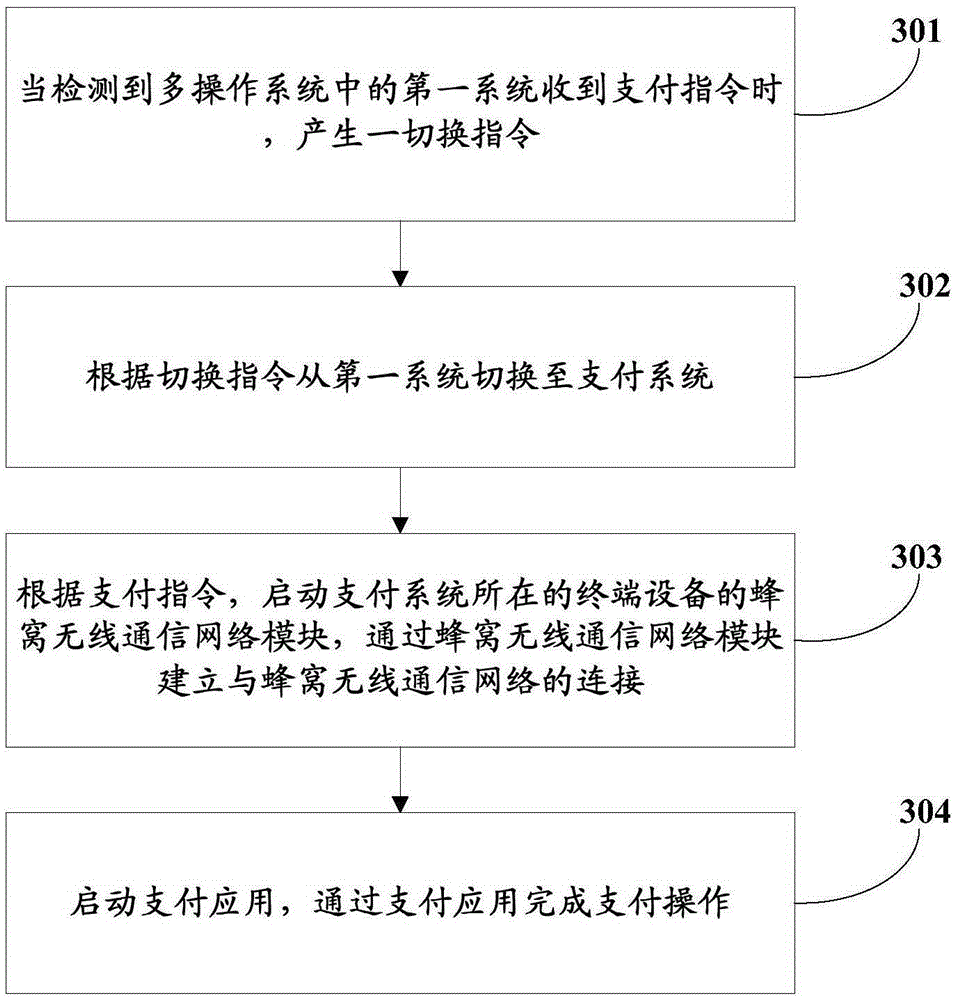
Switching method for multi-operation system and terminal equipment
InactiveCN105825149AProtect private dataImprove securityInternal/peripheral component protectionProtocol authorisationOperational systemTerminal equipment
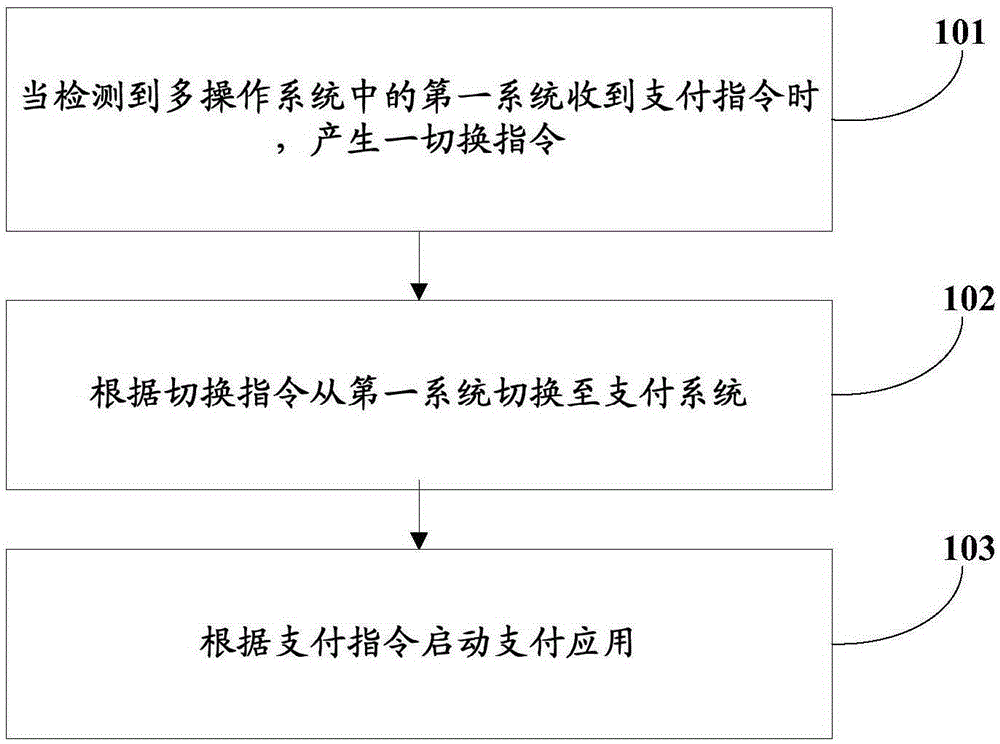
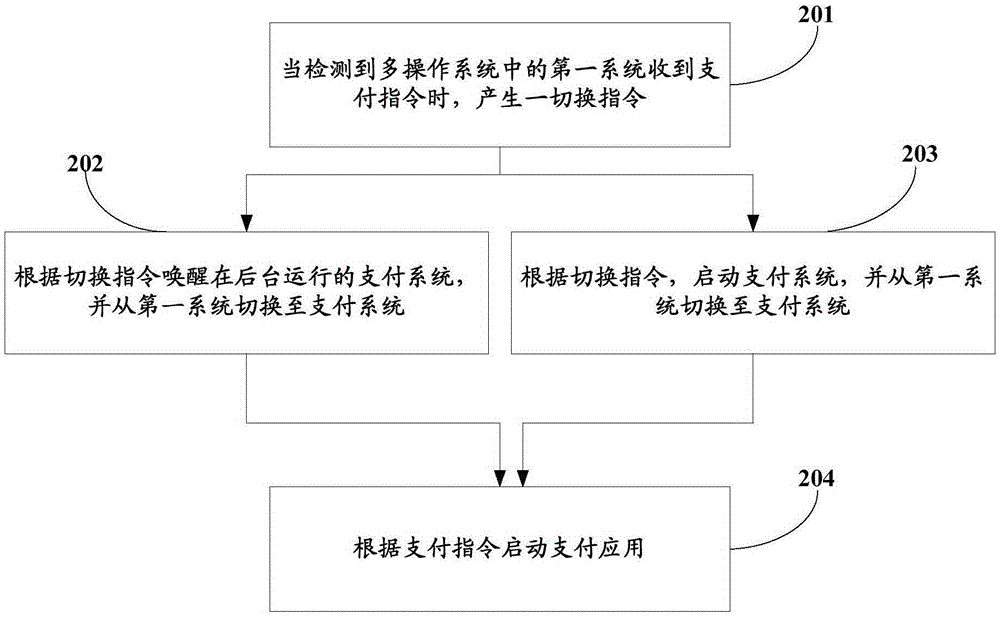
The invention provides a switching method for a multi-operation system and terminal equipment. A payment system for payment application is installed in the multi-operation system. The switching method comprises the following steps: when detecting that a first system in the multi-operation system receives a payment instruction, generating a switching instruction; switching to the payment system from the first system according to the switching instruction; starting the payment application according to the payment instruction. As payment service is defined to be implemented in the payment system in which the payment application is installed, and the payment service cannot be implemented in other operation systems, the problem of payment security in the prior art can be greatly solved for a user, private data of the user can be protected while the user experience is not degraded, the risk that money of the user is stolen is reduced, and the security of the payment system is improved.
Owner:VIVO MOBILE COMM CO LTD
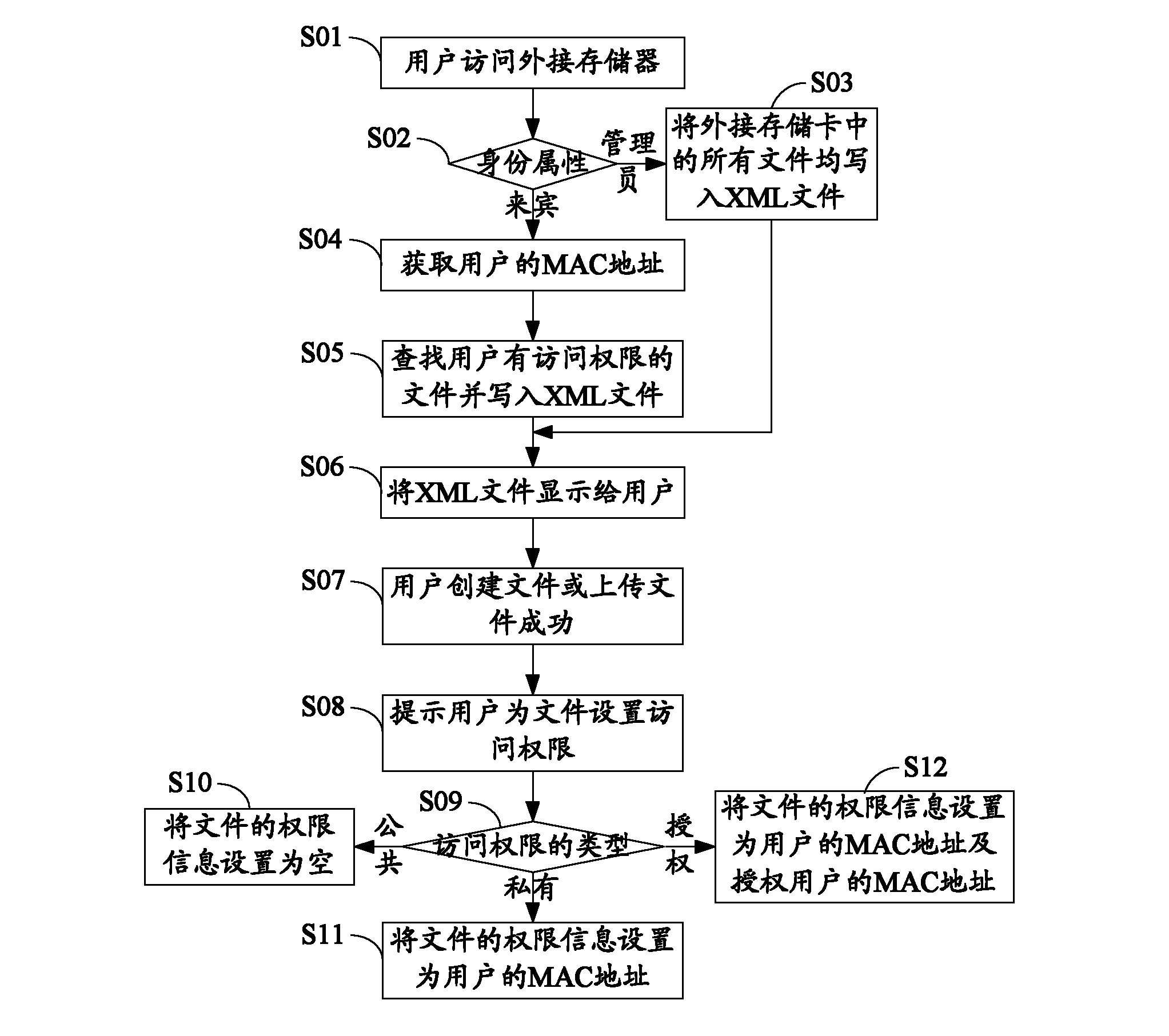
Data card and multi-user access method of external memory card thereof
The invention discloses a data card and a multi-user access method of an external memory card thereof. The multi-user access method comprises the following steps: when a user visits an external memorizer, the data card searches files to which the user has access in the external memorizer according to identity attribute of the user, and the files are shown to the user; when the fact that the user creates a file in the external memory card or successively uploads a file to the external memory card is detected, the user is prompted to set access permission for the file. The data card and the multi-user access method of the external memory card thereof effectively protect private data of the user.
Owner:ZTE CORP
A method and system for protecting personal privacy
PendingCN109426735AImprove compatibilityReliable controlDigital data protectionDigital data authenticationInternet privacyComputer terminal
The invention discloses a method and system for protecting personal privacy, relating to mobile Internet technology. The method for protecting the personal privacy provided herein includes after a mobile terminal receives and permits an application to apply for access to privacy data, if it is determined that access to untrue data is permitted according to a preset configuration, feeding back theconfigured untrue data to the application.
Owner:ZTE CORP
Protection method and device of mobile payment information and mobile payment system
InactiveCN104599124APrevent leakageProtect private dataPayment protocolsInformation CardMobile payment
The invention provides a protection method and a protection device of mobile payment information and a mobile payment system. The protection method of the mobile payment information includes that a card issuer server dynamically updates replacement code information corresponding to information of all payment accounts, stored in the card issuer server; the card issuer server updates a mapping relation between the payment account information stored in the card issuer server and the replacement code information according to the replacement code information after being updated after the card issuer server updates the replacement code information corresponding to the information of all the payment accounts, stored in the card issuer server, at every turn; the card issuer server sends the replacement code information after being updated and the corresponding payment account information to a mobile terminal after the card issuer server updates the replacement code information corresponding to the information of all the payment accounts, stored in the card issuer server, at every turn, and thereby enables the mobile terminal to perform mobile payment according to the replacement code information after being updated. The protection method and the protection device of the mobile payment information and the mobile payment system can prevent the mobile payment information from leaking, and protect intimate data of a user.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
Portable memory devices and method for automatically performing biology identification application program
ActiveCN101034376AProtect private dataInstall without worryInput/output to record carriersDigital data processing detailsElectricityOperational system
The invention relates to a portable storage device and a method of automatic implementation of the biometric recognizing application, the storage unit includes a control module, a memory module and a biosensor. Control module connects with a terminal server, a memory module and a biosensor with electricity. Firmware is stored in control module. Firmware is designed to: memory module is split into at least one biometric application block and a block of confidentiality more than a block. Biometric application block storage has at least one biometric application process; A operating system of the terminal host will regard the biometric application block as a CD-ROM storage device, and close above-CD storage device after self-executing at least one biometric application. At least one biometric application guide a user through a biometric procedures, can be caused by a particular operation. The portable storage device can be used in various mainframe terminals to achieve along with inserts namely, and guide users to process biometric procedures.
Owner:EGIS TECH
Machine learning method, device and system of distributed system, equipment and storage medium
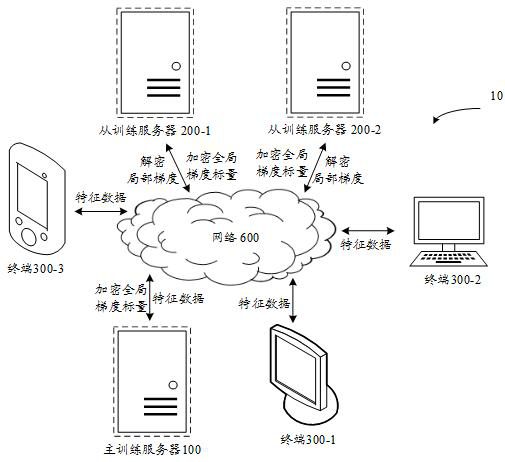
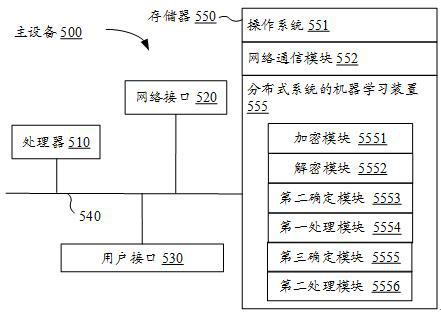
ActiveCN112347500AProtect private dataImprove securityEnsemble learningDigital data protectionFeature dataData storing
The invention provides a machine learning method, device and system of a distributed system, electronic equipment and a computer readable storage medium. An artificial intelligence technology is involved. The method comprises the following steps that: master equipment performs homomorphic encryption on a global gradient scalar of a machine learning model, and sends the obtained encrypted global gradient scalar to slave equipment; the slave equipment determines an encrypted local gradient corresponding to the slave equipment based on the encrypted global gradient scalar, feature data stored bythe slave equipment for the training sample and a local model parameter corresponding to the slave equipment; the master equipment and the slave equipment jointly decrypt the encrypted local gradientcorresponding to the slave equipment to obtain a decryption local gradient corresponding to the slave equipment; and the slave equipment updates a local model parameter corresponding to the slave equipment based on the decrypted local gradient corresponding to the slave equipment. According to the invention, the safety of the training data can be ensured.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Technical document processing method, digital watermark server and processing system
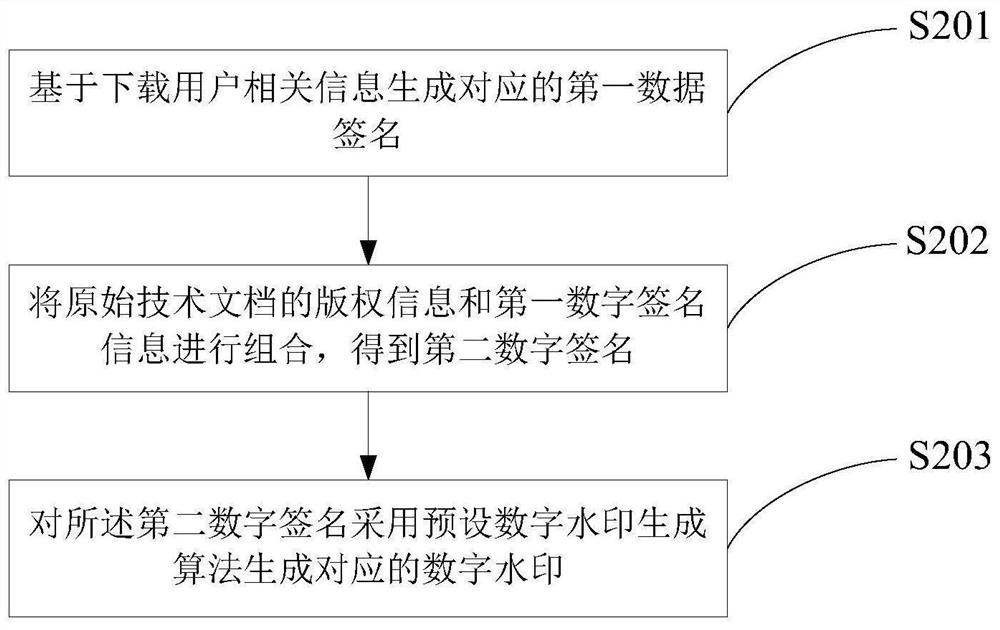
PendingCN113486309ARealize traceabilityProtect private dataDigital data protectionProgram/content distribution protectionDigital signatureUnique identifier
The invention discloses a technical document processing method, a digital watermark server and a processing system. A technical document downloading request is obtained, a corresponding original technical document is obtained according to a unique identifier of the technical document, a corresponding digital signature is generated according to related information of a downloading user, and a corresponding digital watermark is generated based on the digital signature. A target technical document is obtained by embedding a digital watermark into an original technical document, and preset related information of the original technical document and the digital watermark are stored in a block chain system in a corresponding relation mode while the target technical document is sent to a downloading request end for downloading. Because the digital watermark contains the related information of the downloading user, the private data of the downloading user can be effectively protected by storing the digital watermark into the block chain system, when a leaked technical document is found, the digital watermark can be extracted from the technical document to obtain the information of the downloading user, and a leaked person is positioned, so that traceability of the secrete divulger is realized.
Owner:合肥零碳技术有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com