Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1415results about How to "Improve method" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
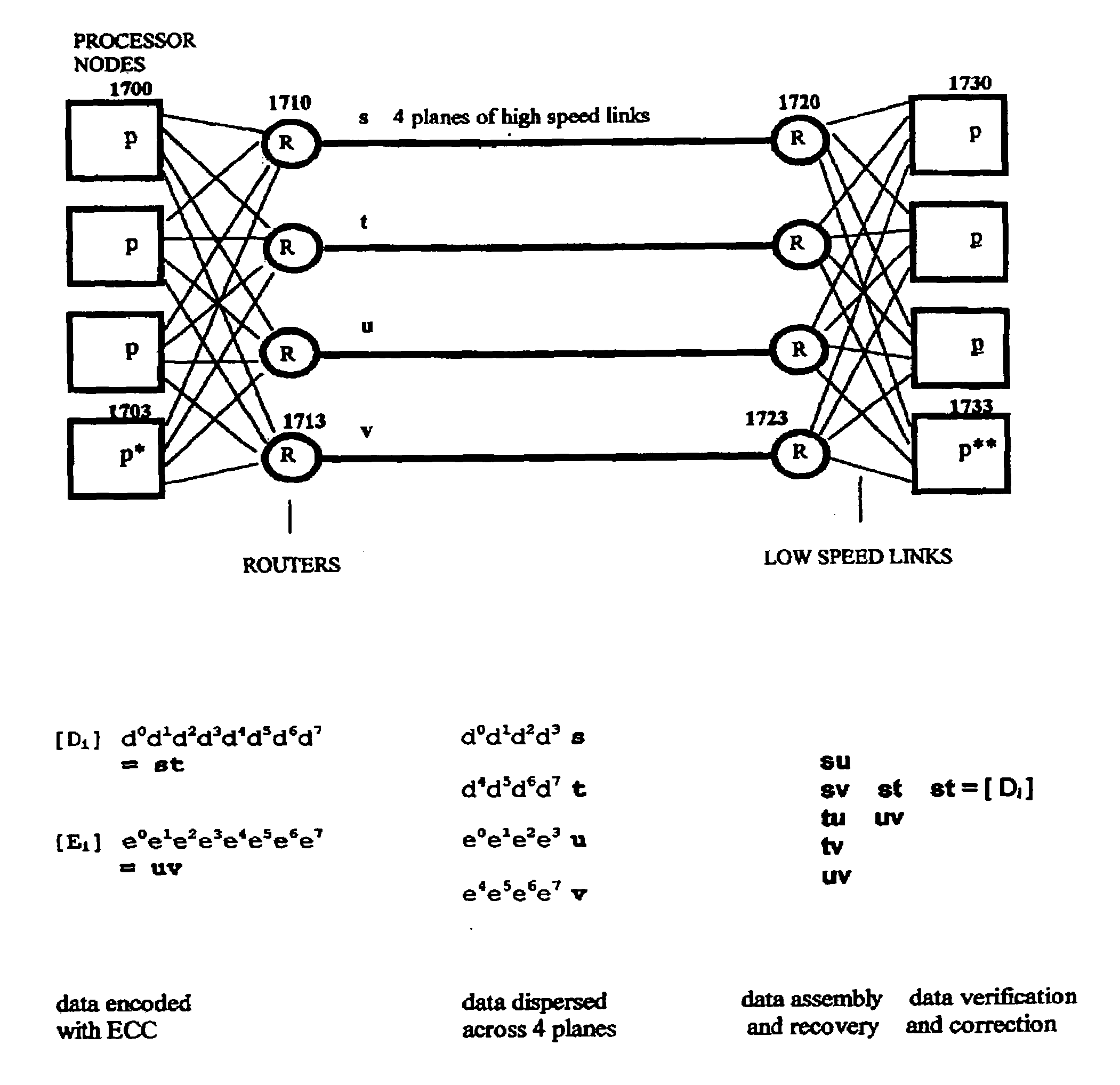
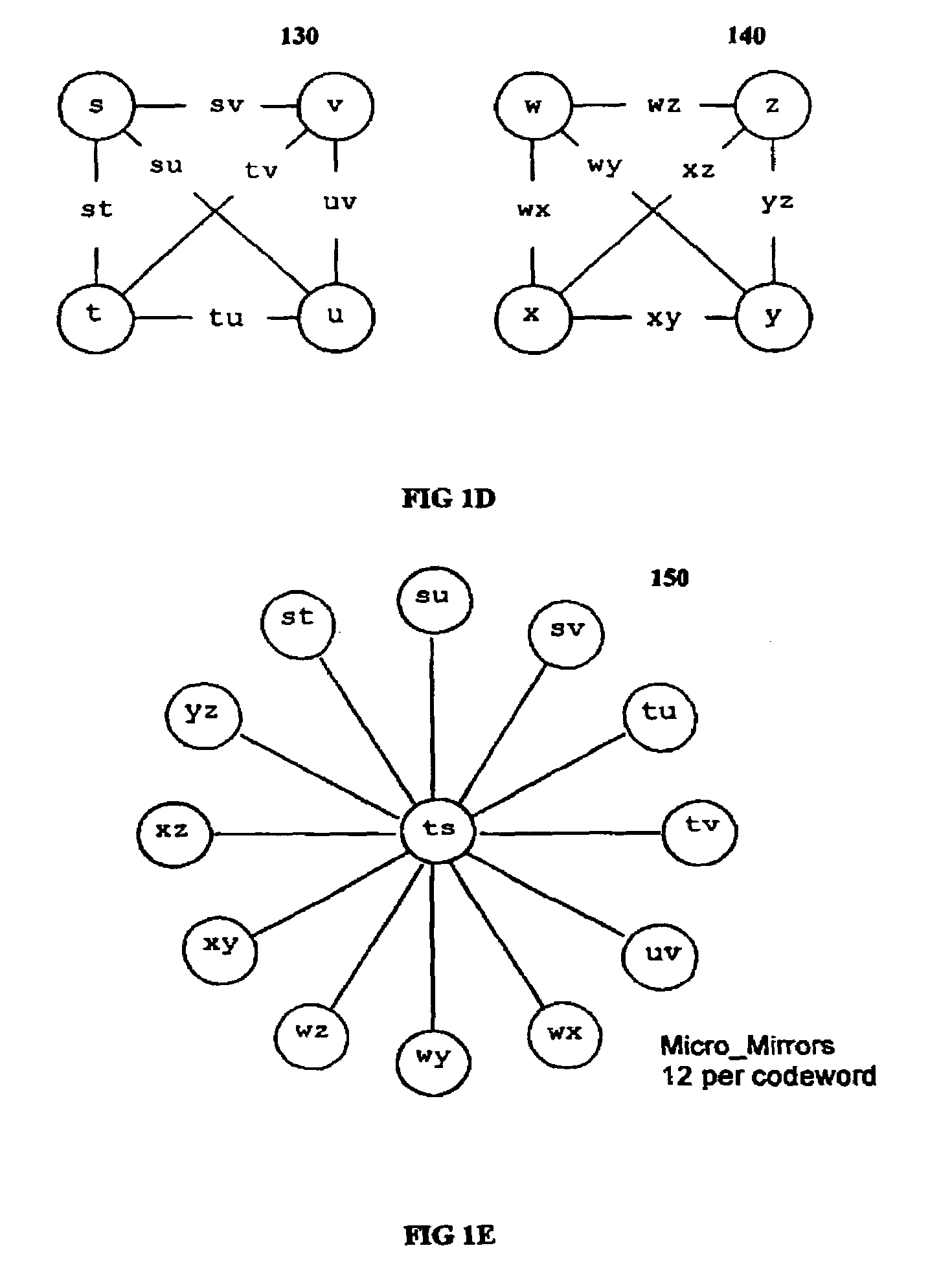
Multi-dimensional data protection and mirroring method for micro level data
ActiveUS7103824B2Detection errorLow common data sizeCode conversionCyclic codesData validationData integrity
The invention discloses a data validation, mirroring and error / erasure correction method for the dispersal and protection of one and two-dimensional data at the micro level for computer, communication and storage systems. Each of 256 possible 8-bit data bytes are mirrored with a unique 8-bit ECC byte. The ECC enables 8-bit burst and 4-bit random error detection plus 2-bit random error correction for each encoded data byte. With the data byte and ECC byte configured into a 4 bit×4 bit codeword array and dispersed in either row, column or both dimensions the method can perform dual 4-bit row and column erasure recovery. It is shown that for each codeword there are 12 possible combinations of row and column elements called couplets capable of mirroring the data byte. These byte level micro-mirrors outperform conventional mirroring in that each byte and its ECC mirror can self-detect and self-correct random errors and can recover all dual erasure combinations over four elements. Encoding at the byte quanta level maximizes application flexibility. Also disclosed are fast encode, decode and reconstruction methods via boolean logic, processor instructions and software table look-up with the intent to run at line and application speeds. The new error control method can augment ARQ algorithms and bring resiliency to system fabrics including routers and links previously limited to the recovery of transient errors. Image storage and storage over arrays of static devices can benefit from the two-dimensional capabilities. Applications with critical data integrity requirements can utilize the method for end-to-end protection and validation. An extra ECC byte per codeword extends both the resiliency and dimensionality.
Owner:HALFORD ROBERT
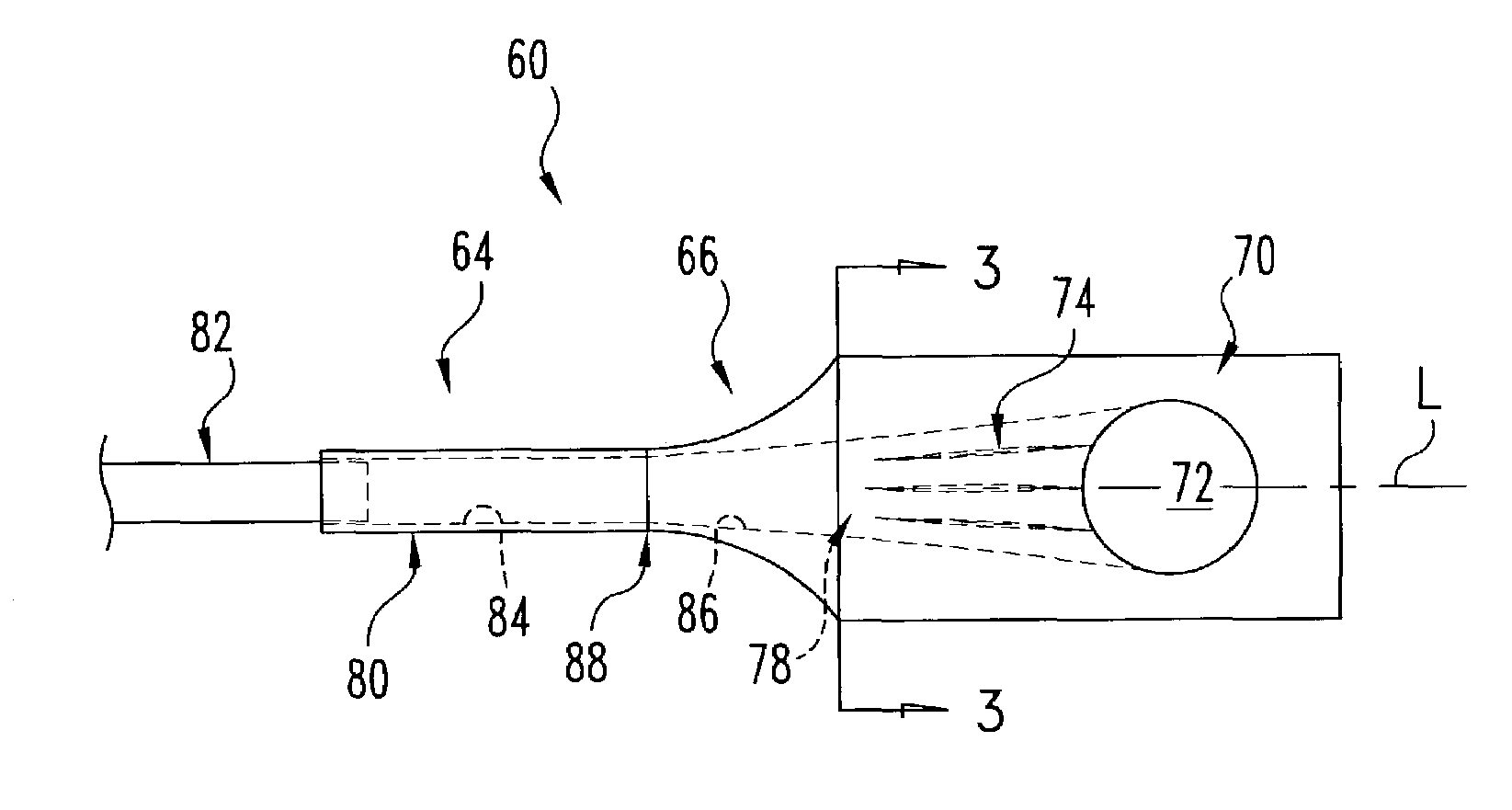
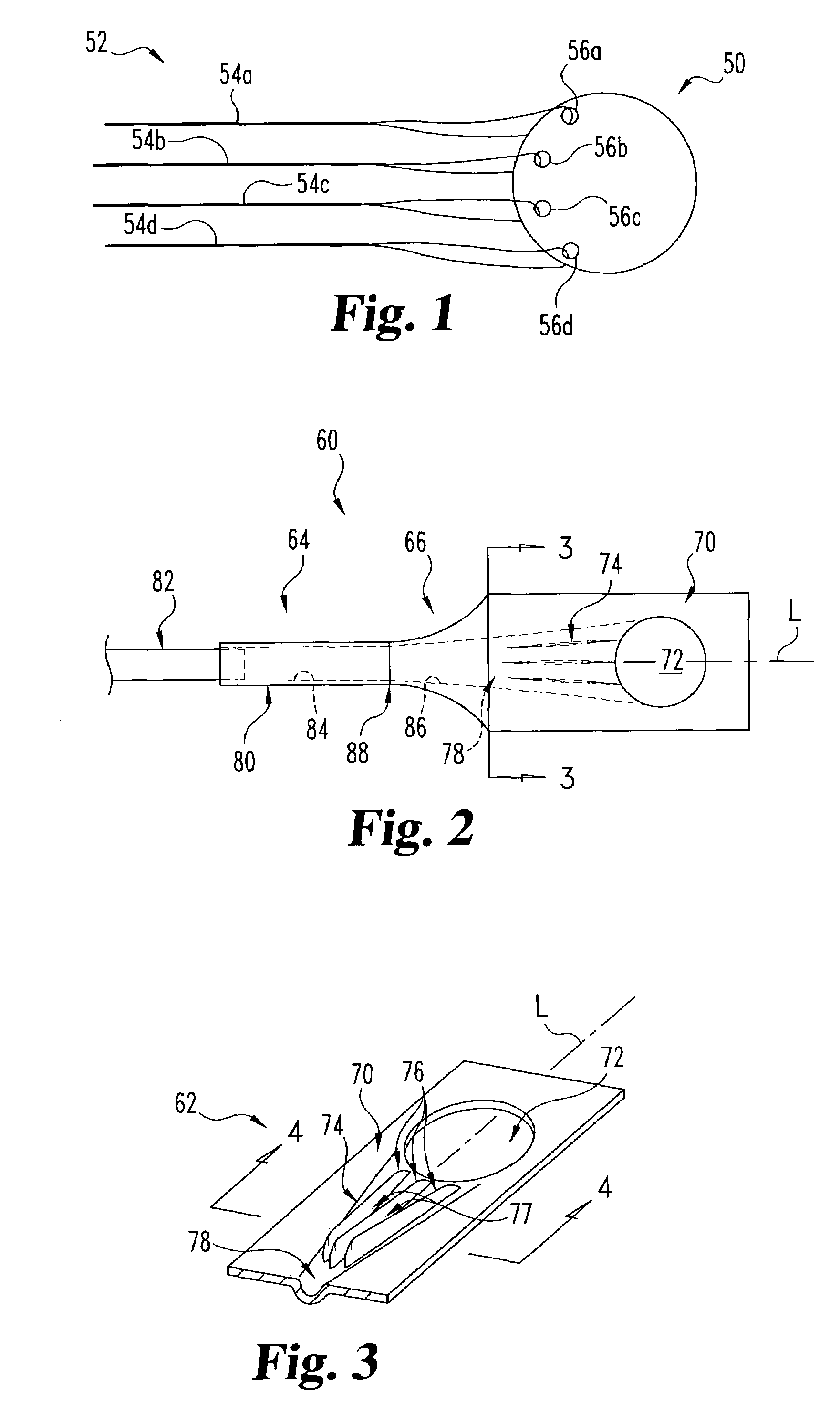
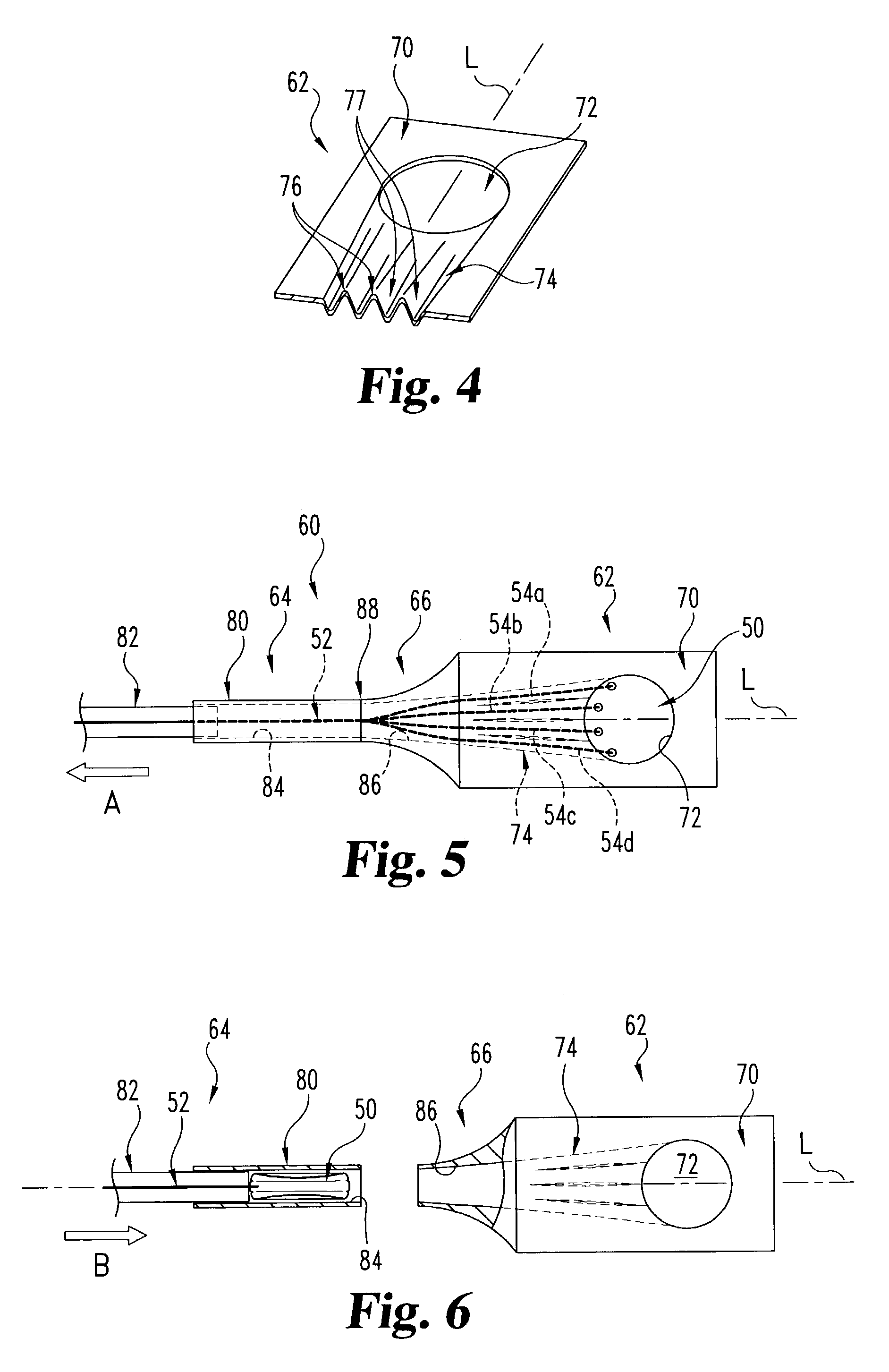
Method of and system for reading visible and/or invisible code symbols in a user-transparent manner using visible/invisible illumination source switching during data capture and processing operations
ActiveUS8408468B2Avoiding shortcoming and drawbackWithout complexityCharacter and pattern recognitionHybrid readersComputer scienceComputer graphics (images)
Method of and system for reading visible and / or invisible code symbols in a user-transparent manner using visible / invisible illumination switching during data capture and processing operations.
Owner:METROLOGIC INSTR
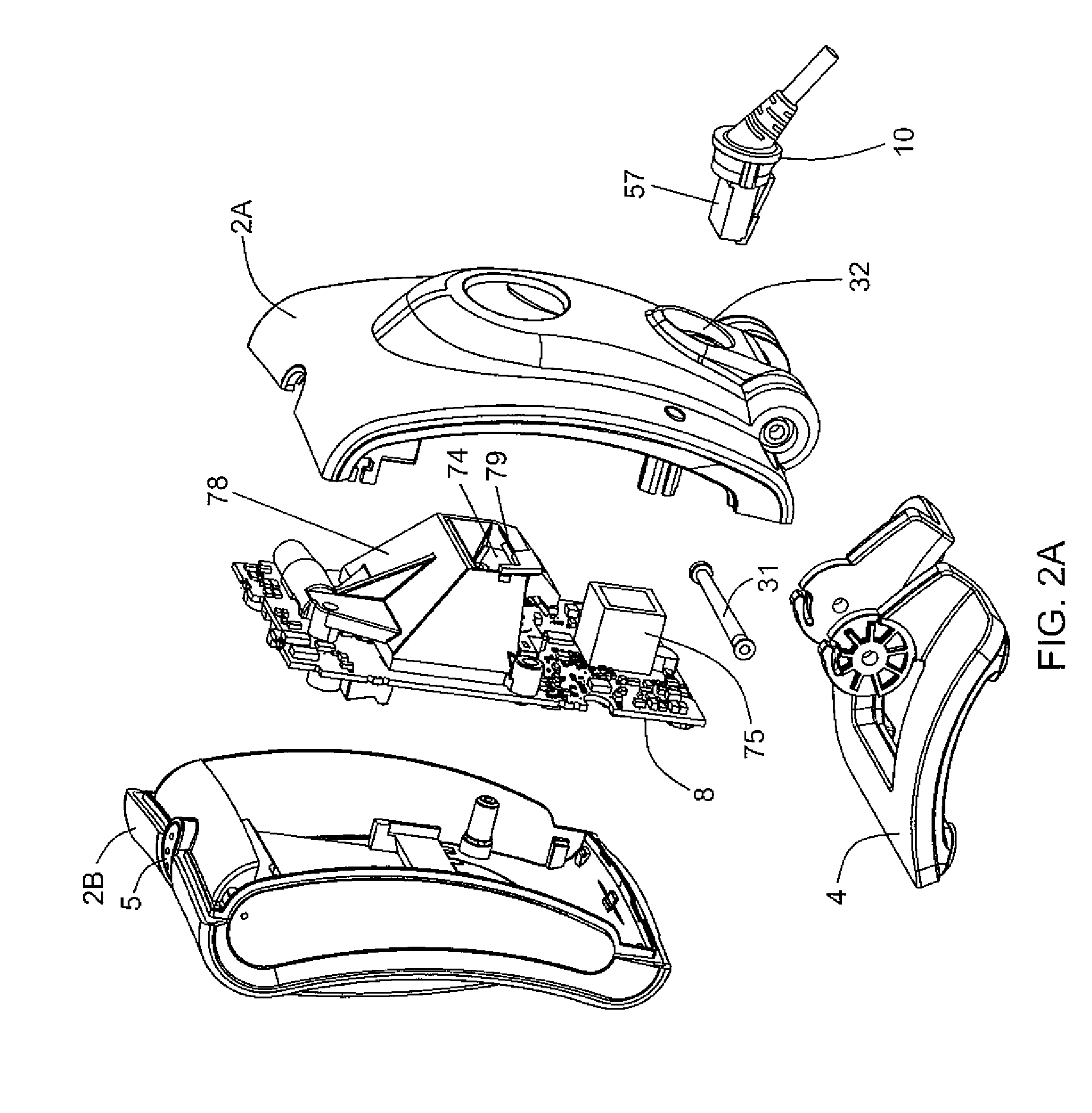
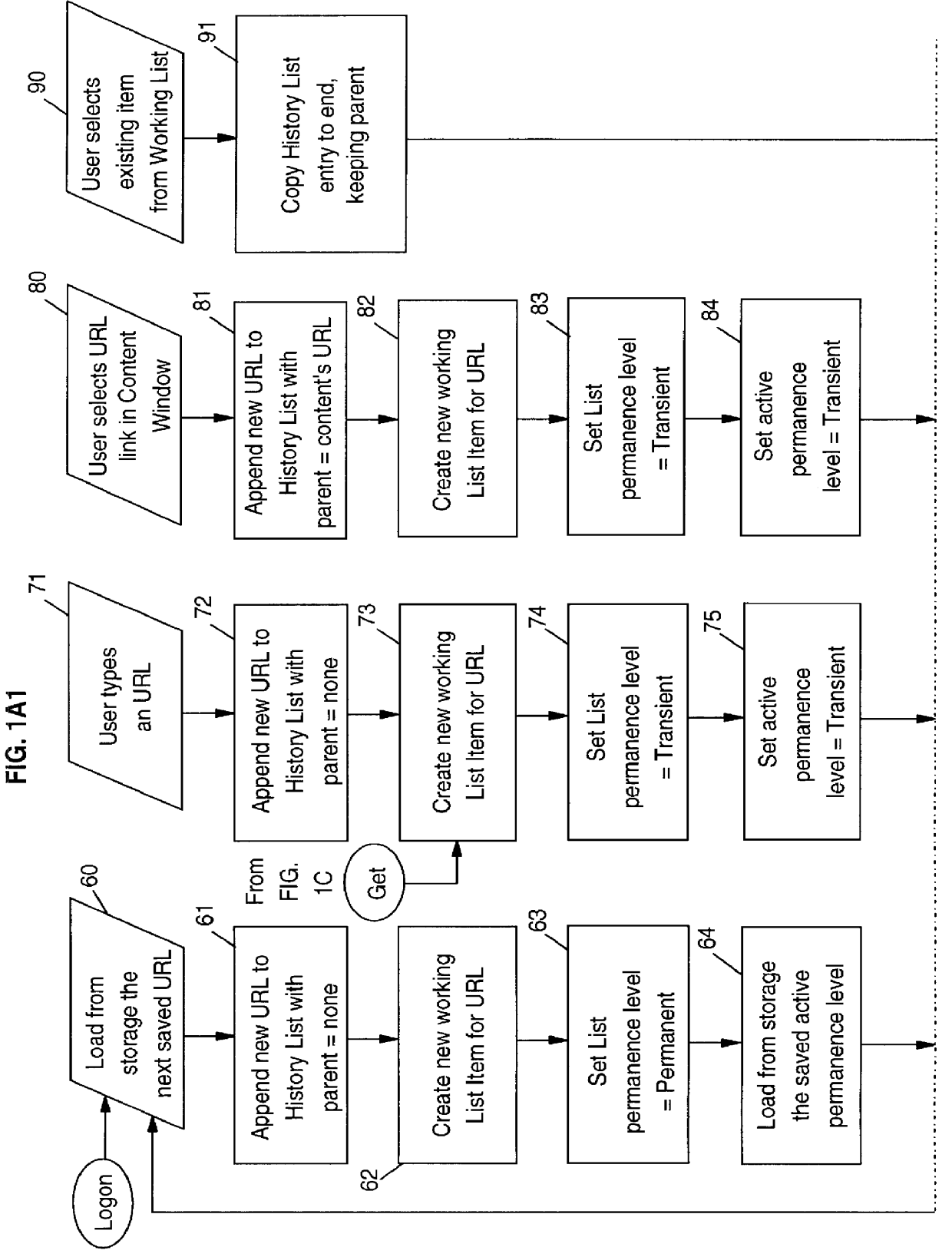
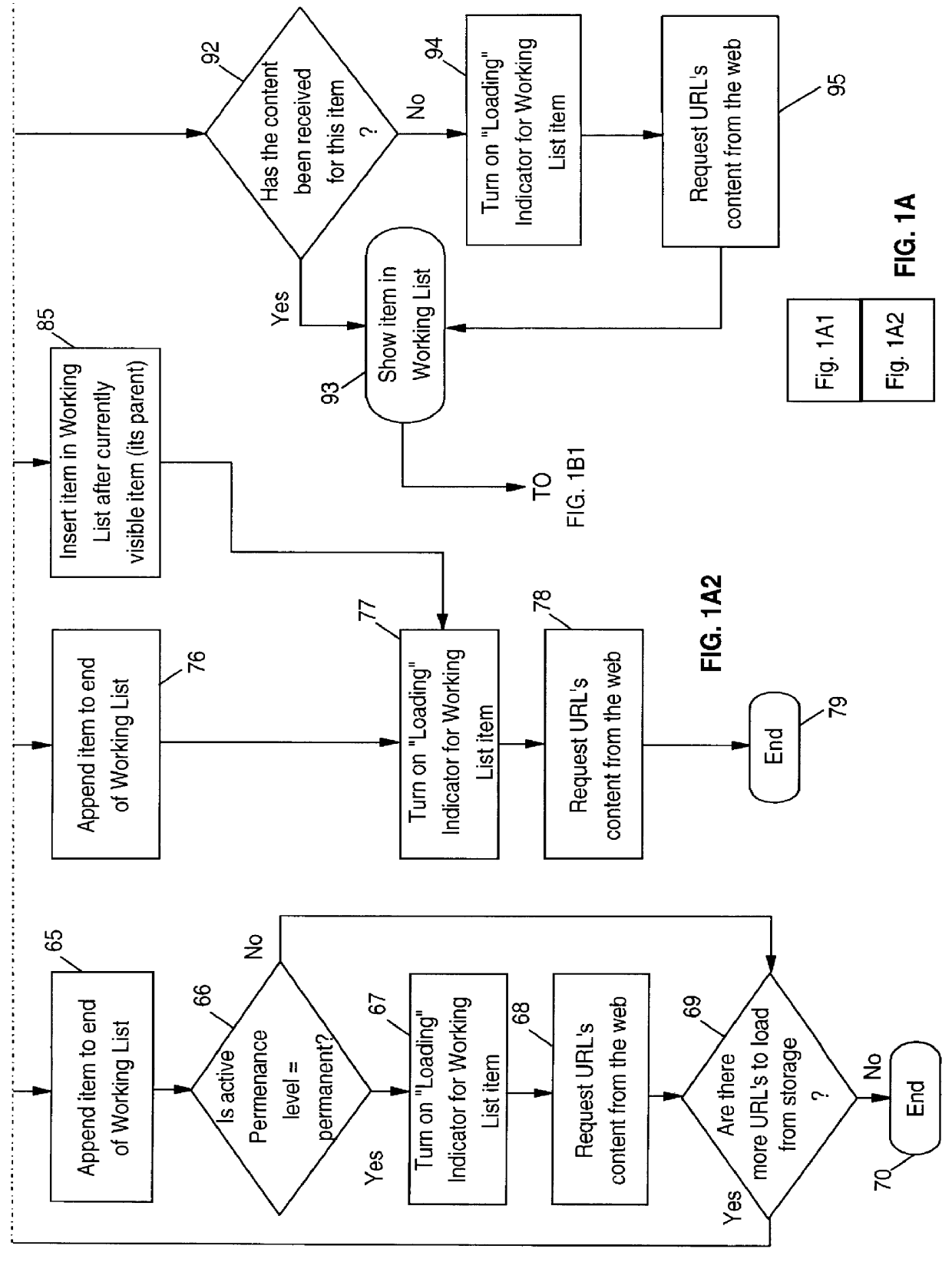
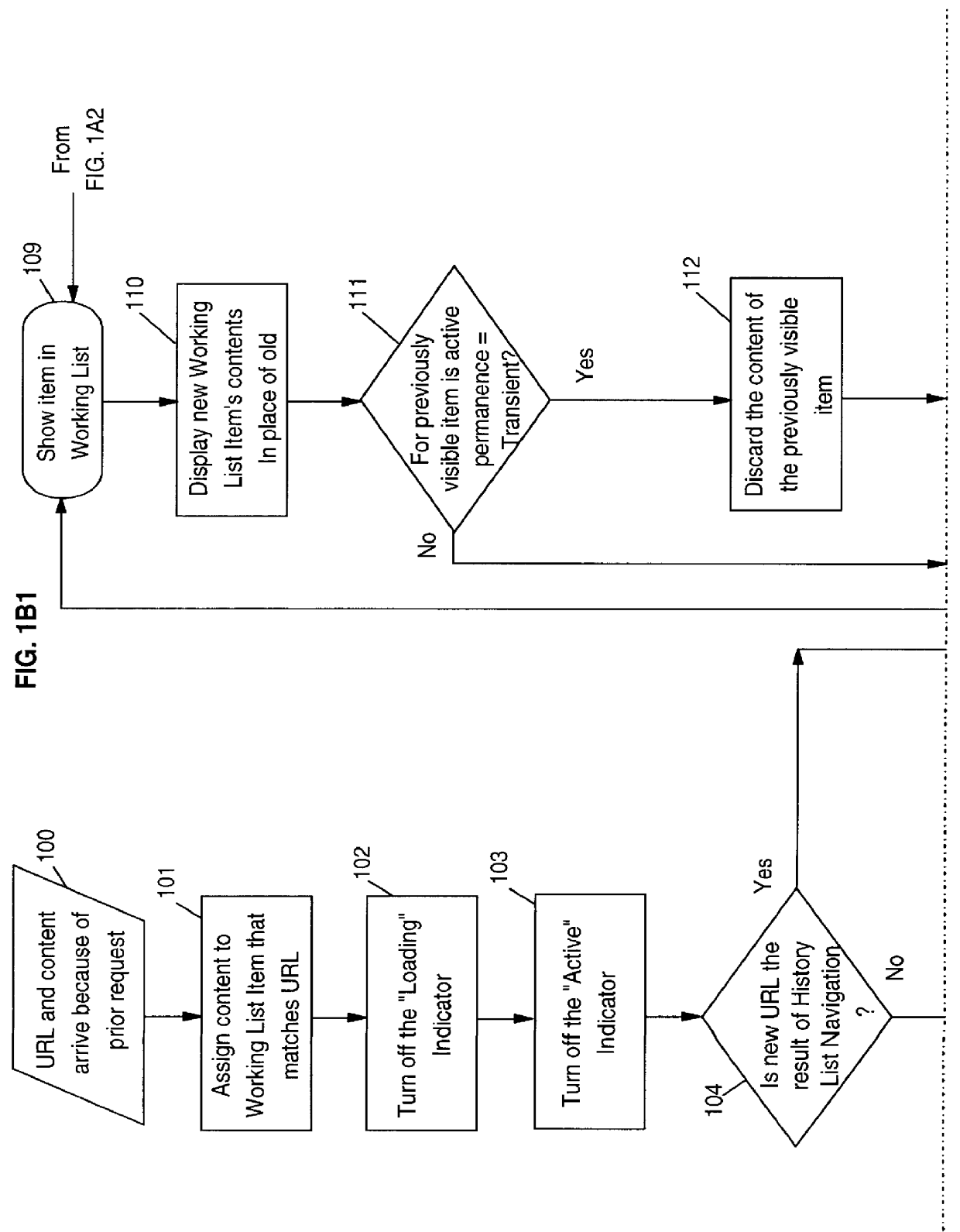
Browser and plural active URL manager for network computers
InactiveUS6049812AImprove methodSpecial data processing applicationsSecuring communicationActivity StatusWorking environment
A network browser is provided with working list maintenance and creation facility which contains an indicator for each URL's listing duration level of permanence for controlling how long a URL will be kept or maintained in the working list and also includes an activity duration permanence level indicator for controlling how long the URL will be kept active. This enables the browser to maintain multiple, concurrently active URLs and thereby enable the browser to provide the functional emulation of a desktop working environment to the user.
Owner:WISTRON CORP
Instrumentation and method for delivering an implant into a vertebral space
InactiveUS7081120B2Improved instrumentationImprove methodInternal osteosythesisBone implantRelative displacementIntervertebral disk
Instrumentation and method for delivering an implant into an intervertebral disc space, including a die member configured to transition the implant from an initial configuration to a deformed configuration having a reduced lateral profile suitable for insertion into the intervertebral disc space in a minimally invasive manner. In one embodiment, the die member includes an opening sized to receive the implant while in the initial configuration, and wherein relative displacement between the implant and the die member causes the implant to transition toward the reduced-profile deformed configuration. In a specific embodiment, the opening comprises an axial passage including a first portion having a rectangular cross-section corresponding to a substantially planar initial configuration of the implant, and a second portion having a circular cross-section corresponding to a substantially cylindrical deformed configuration of the implant.
Owner:WARSAW ORTHOPEDIC INC
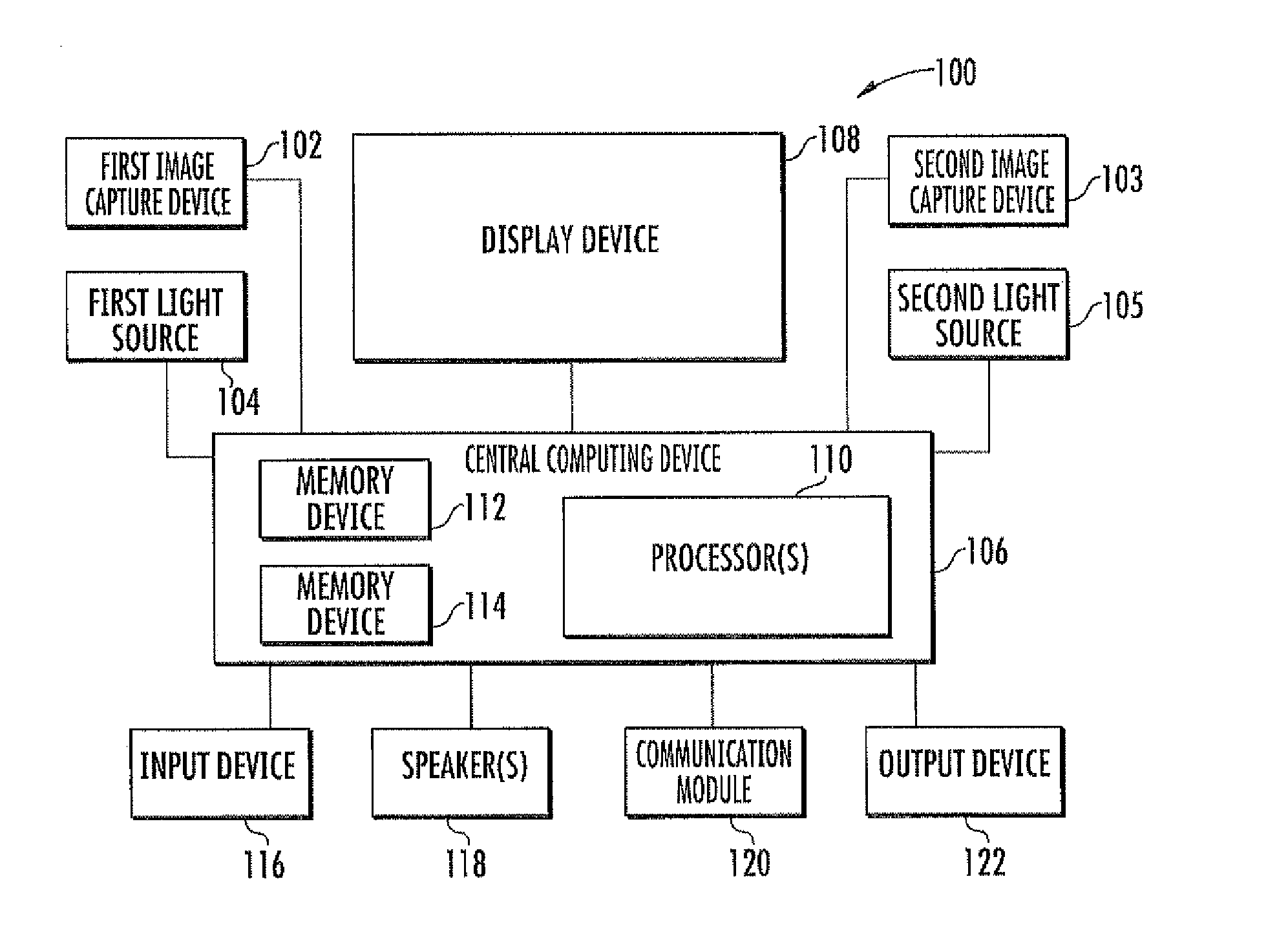
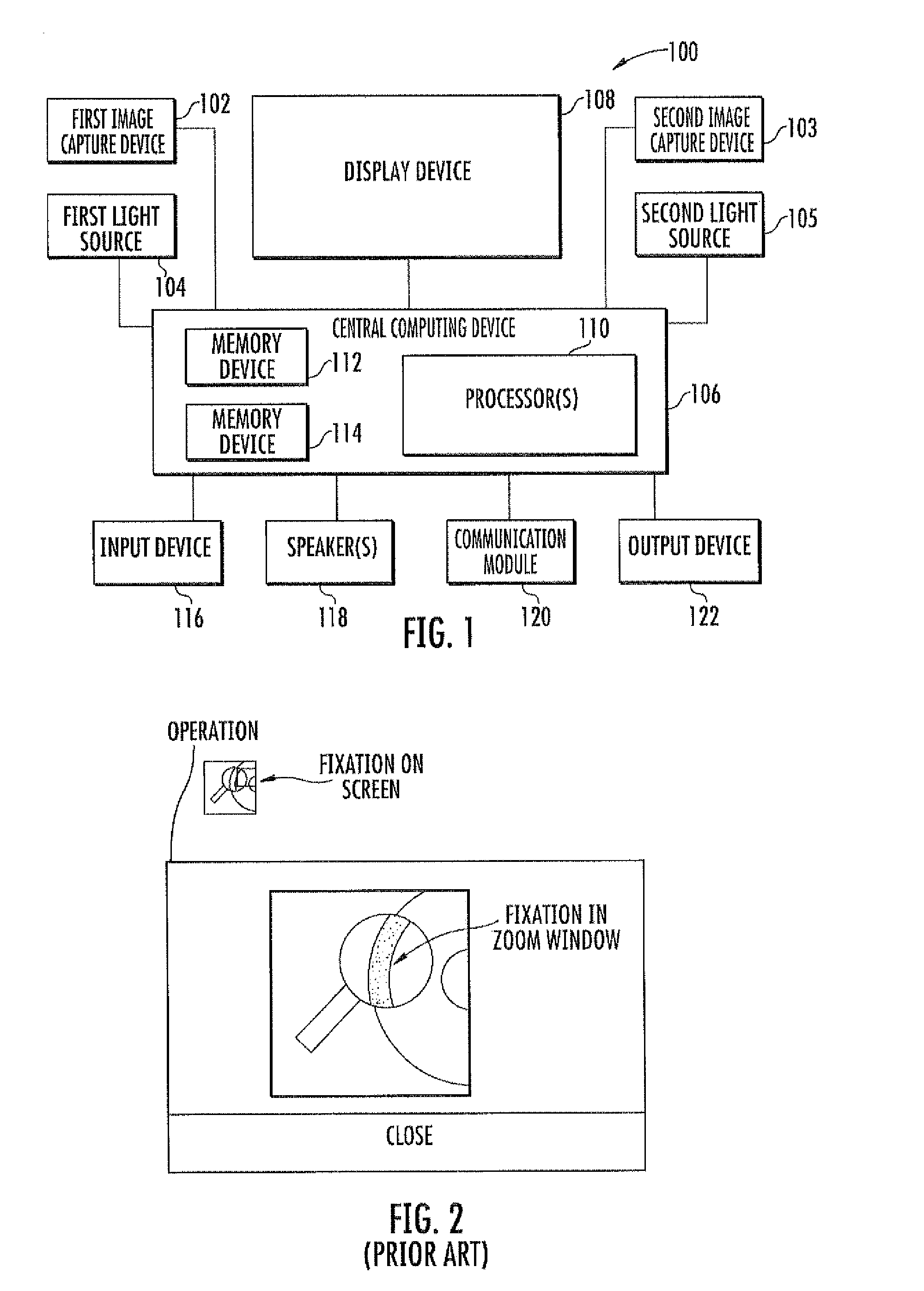
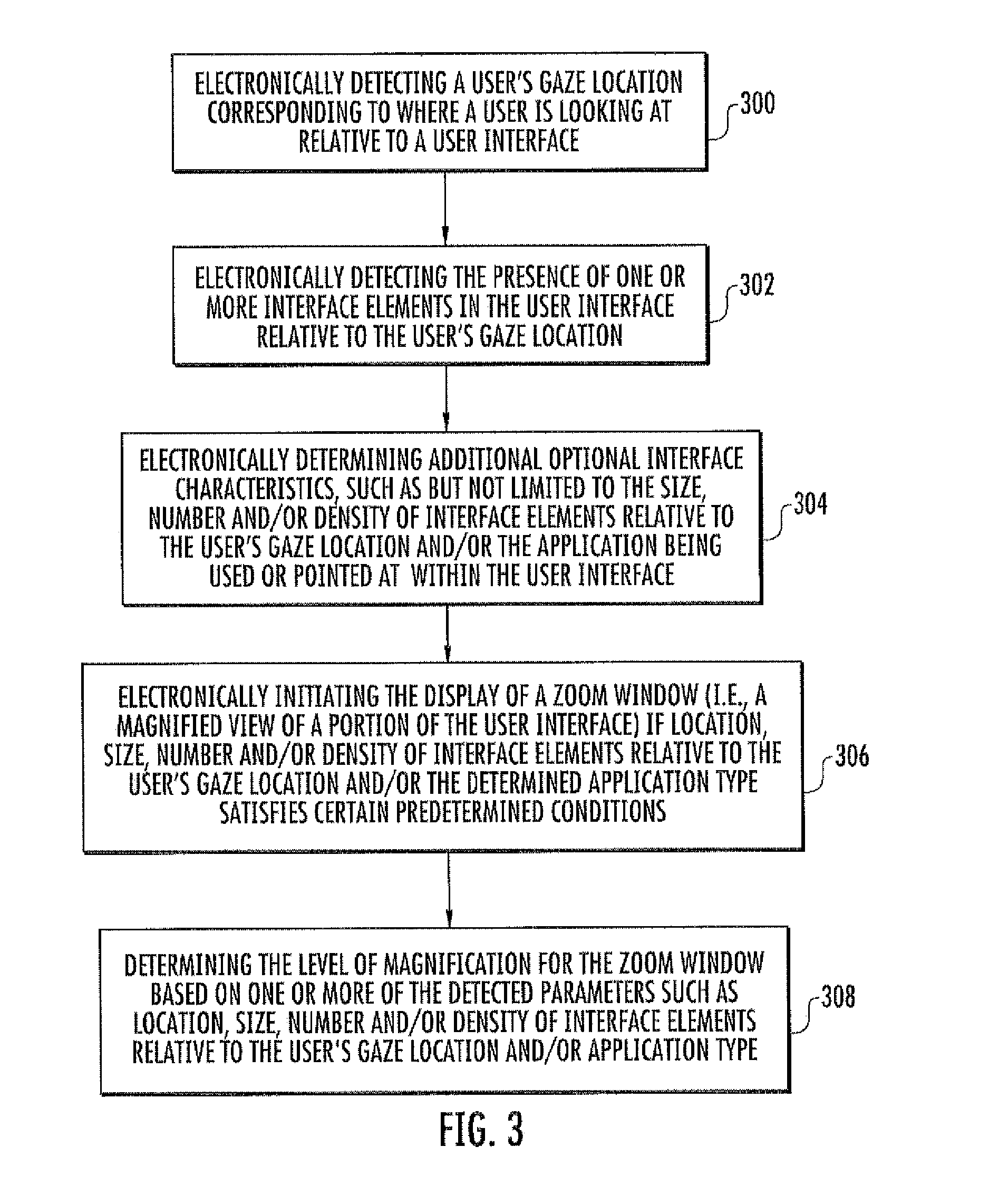
Calibration free, motion tolerent eye-gaze direction detector with contextually aware computer interaction and communication methods
InactiveUS20120105486A1Improved eye tracking systemImprove methodAcquiring/recognising eyesColor television detailsHuman–computer interaction
Eye tracking systems and methods include such exemplary features as a display device, at least one image capture device and a processing device. The display device displays a user interface including one or more interface elements to a user. The at least one image capture device detects a user's gaze location relative to the display device. The processing device electronically analyzes the location of user elements within the user interface relative to the user's gaze location and dynamically determine whether to initiate the display of a zoom window. The dynamic determination of whether to initiate display of the zoom window may further include analysis of the number, size and density of user elements within the user interface relative to the user's gaze location, the application type associated with the user interface or at the user's gaze location, and / or the structure of eye movements relative to the user interface.
Owner:DYNAVOX SYST
Contract based enterprise application services
InactiveUS20050108169A1Improve methodComputer security arrangementsMarketingService contractService-level agreement
The invention includes systems and methods of facilitating interaction between service consumers and services providers based on service contracts. These service contracts are established by considering preferences, capabilities or limitations of each service consumer and at least one characteristic of each service provider. Once the preferences, capabilities or limitations of a service consumer are determined these may be used to automatically established individualized service contracts with a variety of service providers. The services contracts may include contract terms relating to data format, communication protocol, security, data logging, load balancing, service level agreements, service quality, performance requirements, or the like.
Owner:SOFTWARE AG
Method for treating skin and underlying tissue
InactiveUS7189230B2Reduce the amount requiredSmall sizeElectrotherapyPneumatic massageSkin surfaceMedicine
A method for treating a tissue site couples an energy delivery surface of an electromagnetic energy delivery device with a skin surface. An underlying tissue area beneath the skin surface is created. The cooling creates a reverse thermal gradient, where a temperature of the skin surface is less than a temperature of the underlying tissue area. Energy is delivered from the energy delivery device to the underlying tissue area. The energy delivery modifies the underlying tissue area and decreases irregularities of the skin surface.
Owner:THERMAGE INC
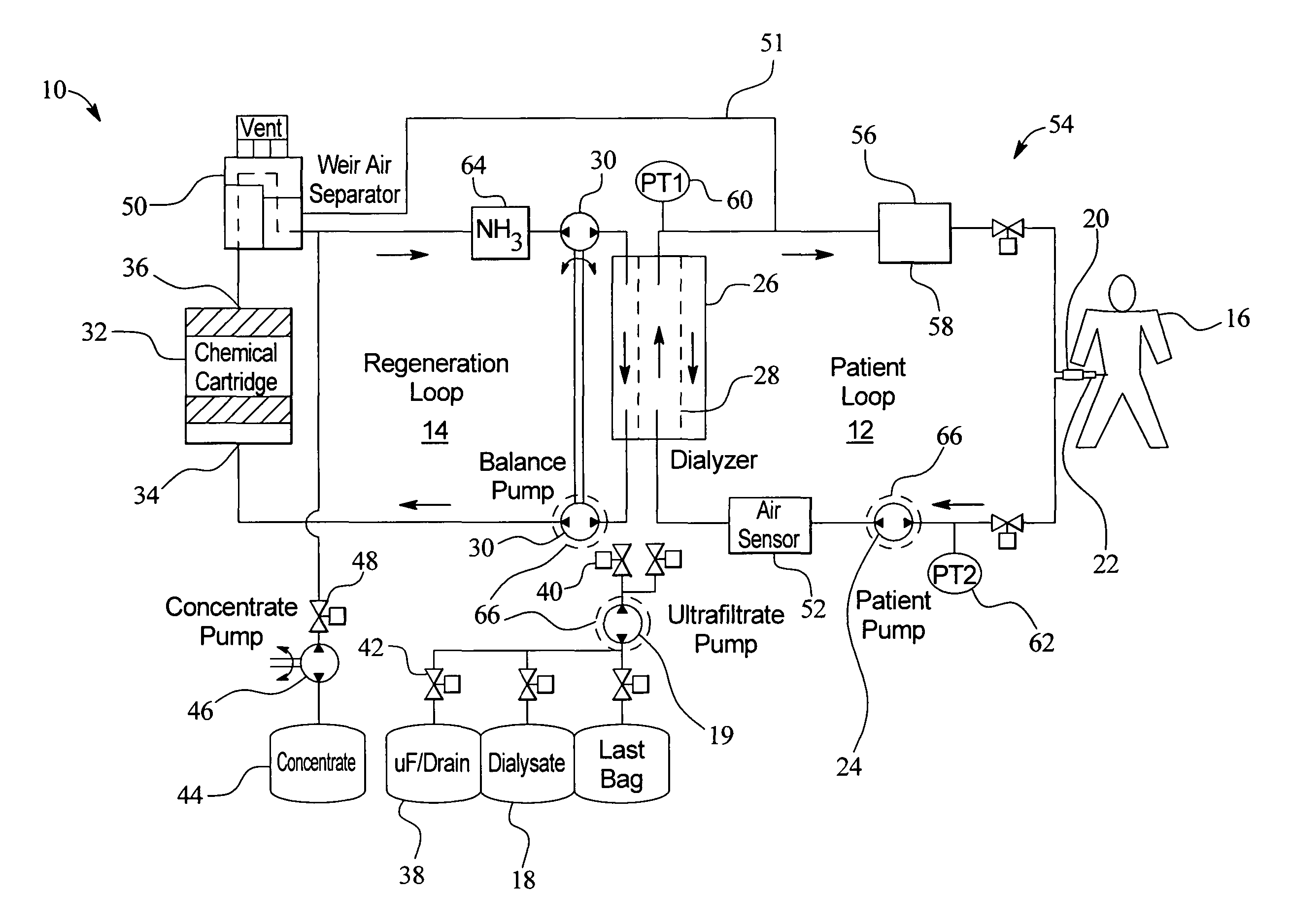
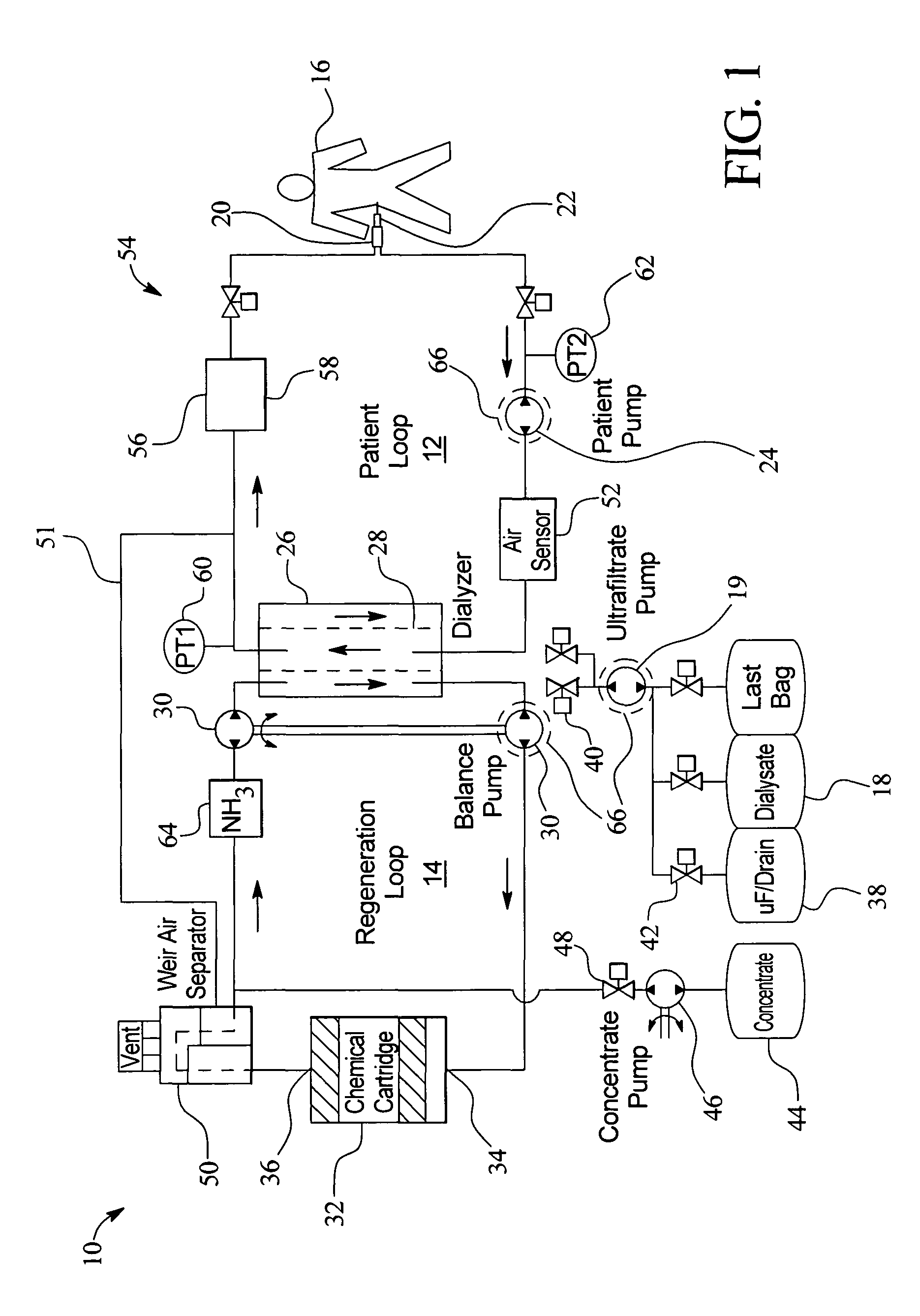
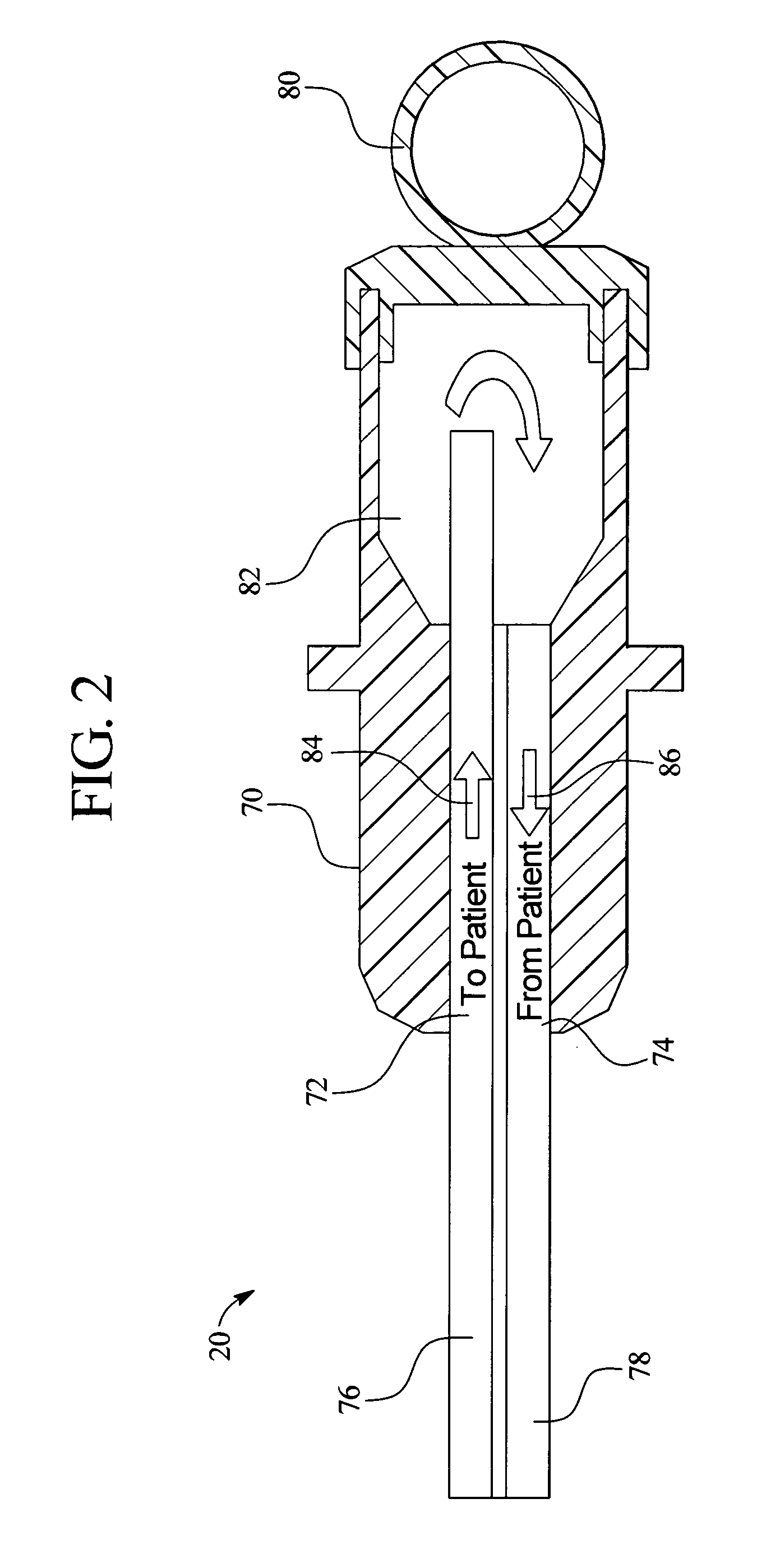
Systems and methods for performing peritoneal dialysis
ActiveUS7867214B2Strengthen the systemImprove methodSolvent extractionIon-exchanger regenerationMetabolic wasteSorbent
In a peritoneal dialysis embodiment of the present invention, spent dialysate from the patient's peritoneal cavity passes, along a patient loop, through a dialyzer having a membrane that separates waste components from the spent dialysate, wherein the patient loop returns fresh dialysate to the patient's peritoneal cavity. The waste components are carried away in a second regeneration loop to a regeneration unit or sorbent cartridge, which absorbs the waste components. The regeneration unit removes undesirable components in the dialysate that were removed from the patient loop by the dialyzer, for example, excess water (ultrafiltrate or UF), toxins and metabolic wastes. Desirable components can be added to the dialysate by the system, such as glucose and electrolytes. The additives assist in maintaining the proper osmotic gradients in the patient to perform dialysis and provide the necessary compounds to the patient.
Owner:BAXTER INT INC
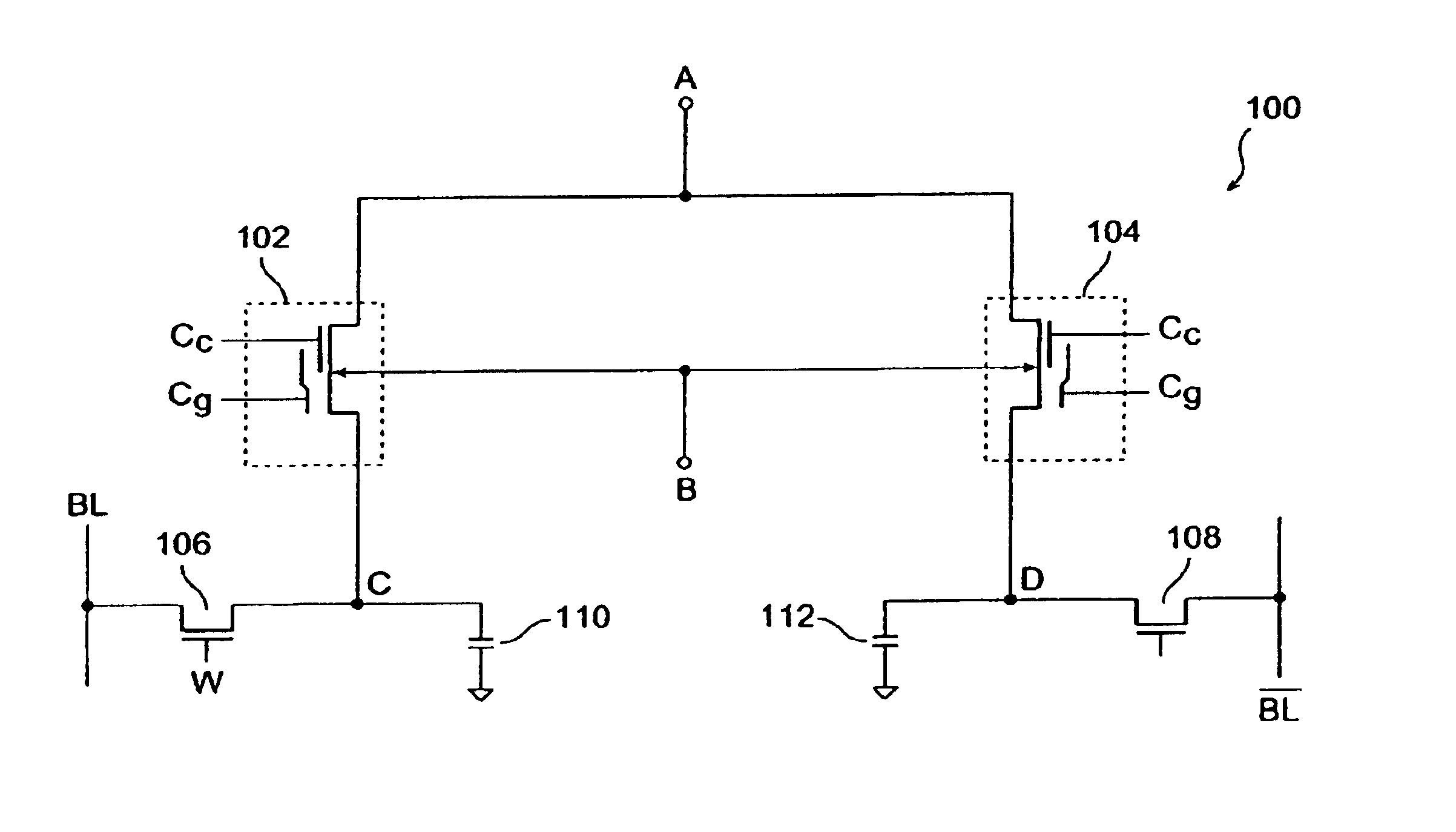
Non-volatile differential dynamic random access memory
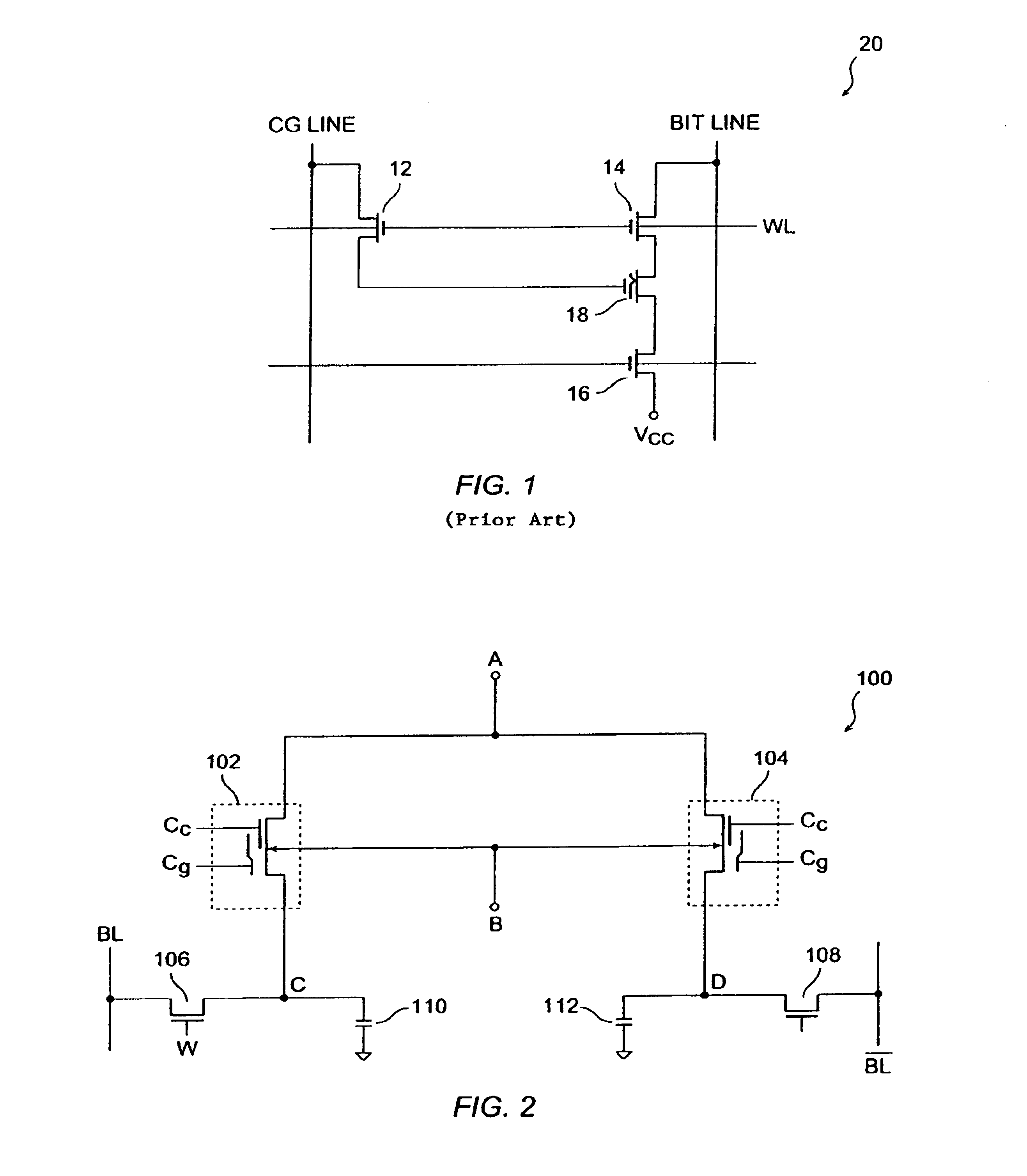
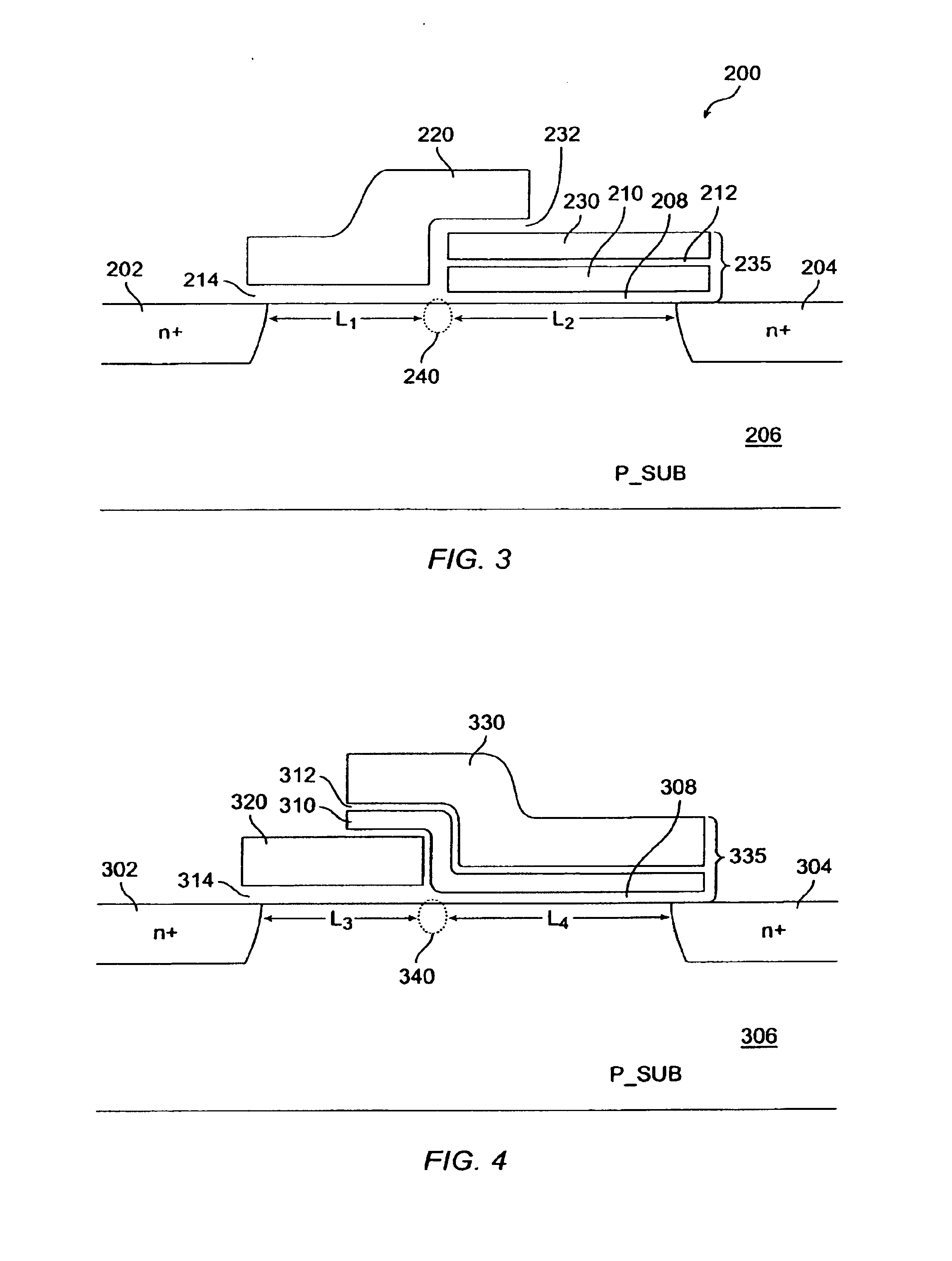
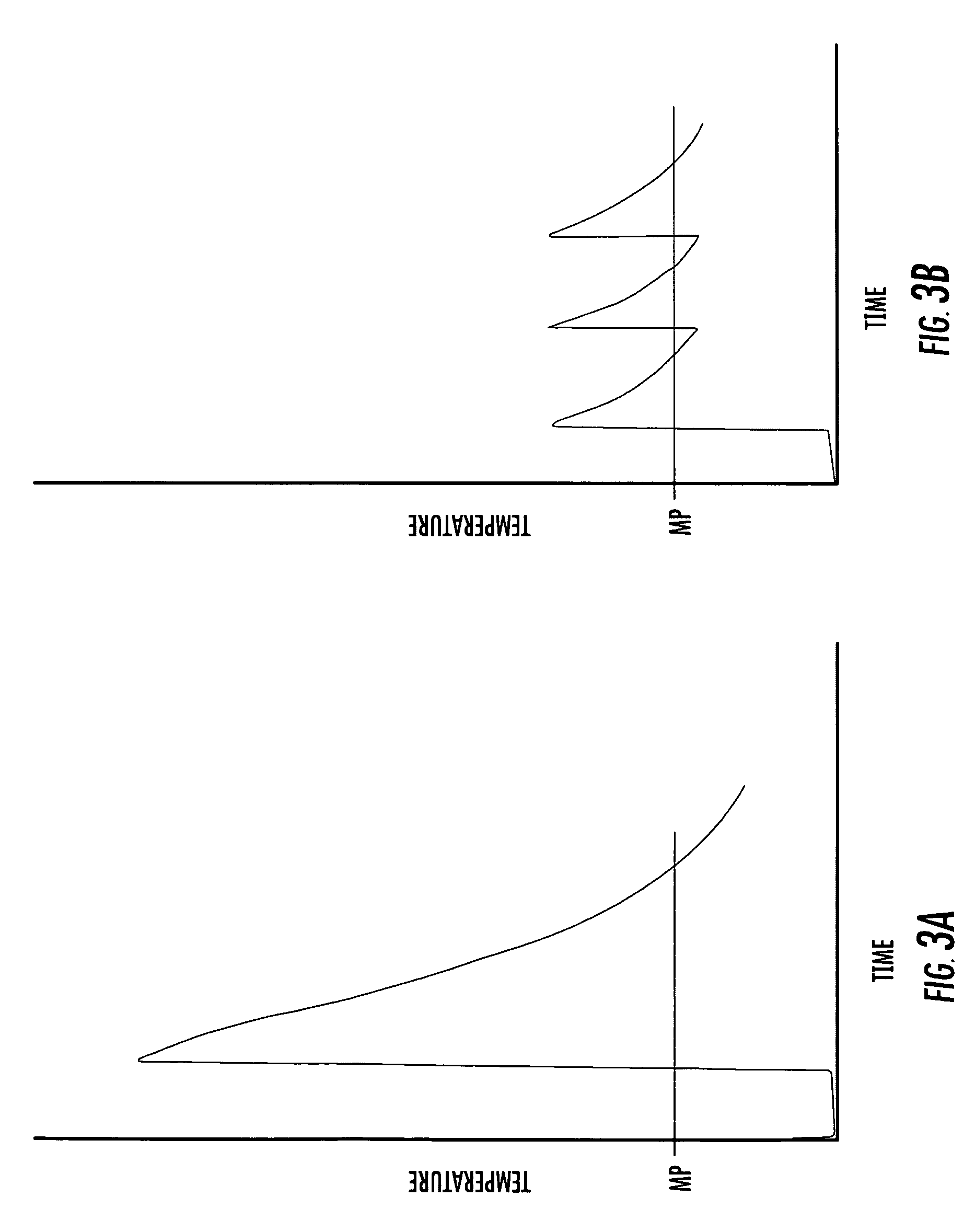
In accordance with the present invention, a memory cell includes a pair of non-volatile devices and a pair of DRAM cells each associated with a different one of the non-volatile devices. Each DRAM cell further includes an MOS transistor a capacitor. The DRAM cells and their associated non-volatile devices operate differentially and when programmed store and supply complementary data. The non-volatile devices are erased prior to being programmed. Programming of the non-volatile devices may be done via hot-electron injection or Fowler-Nordheim tunneling. When a power failure occurs, the data stored in the DRAM are loaded in the non-volatile devices. After the power is restored, the data stored in the non-volatile devices are restored in the DRAM cells. The differential reading and wring of data reduces over-erase of the non-volatile devices.
Owner:O2IC
Display device and method of driving the same
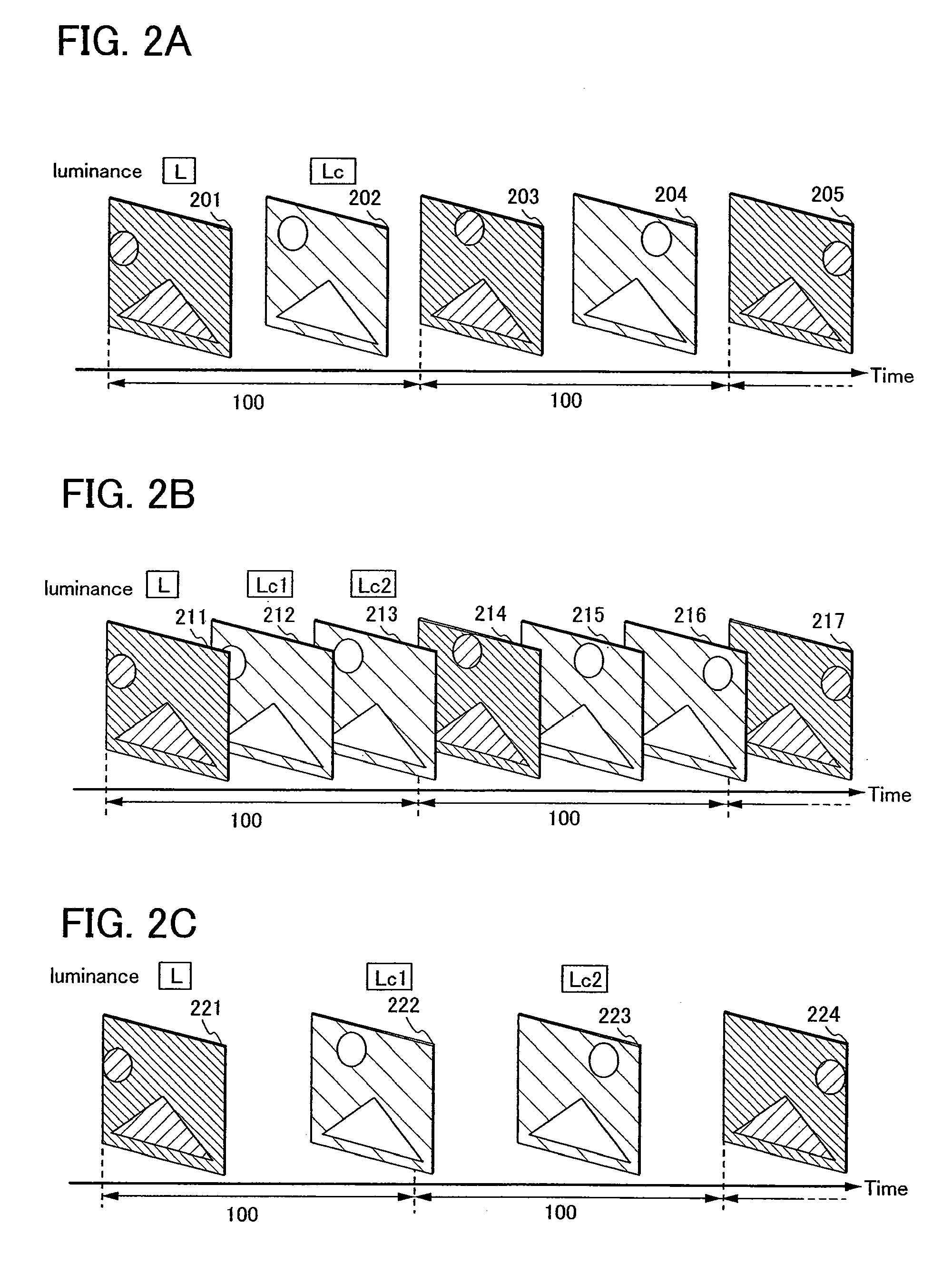
InactiveUS20080068359A1Decrease in luminanceIncreased power consumptionSolid-state devicesCathode-ray tube indicatorsHuman eyeIntermediate state
The present invention solves the motion blur of moving images in hold-type display devices. An amount of a moving image is detected from image data included in frames and an image at the intermediate state between an image of the current frame and an image of the next frame is made as an interpolation image. Thus, the movement of the image can follow the movement of human eyes and the luminance of the interpolation image is changed, and thus, display can be made close to pseudo impulse type display. In this manner, hold-type display devices without motion blur and methods of driving the hold-type display devices can be provided.
Owner:SEMICON ENERGY LAB CO LTD
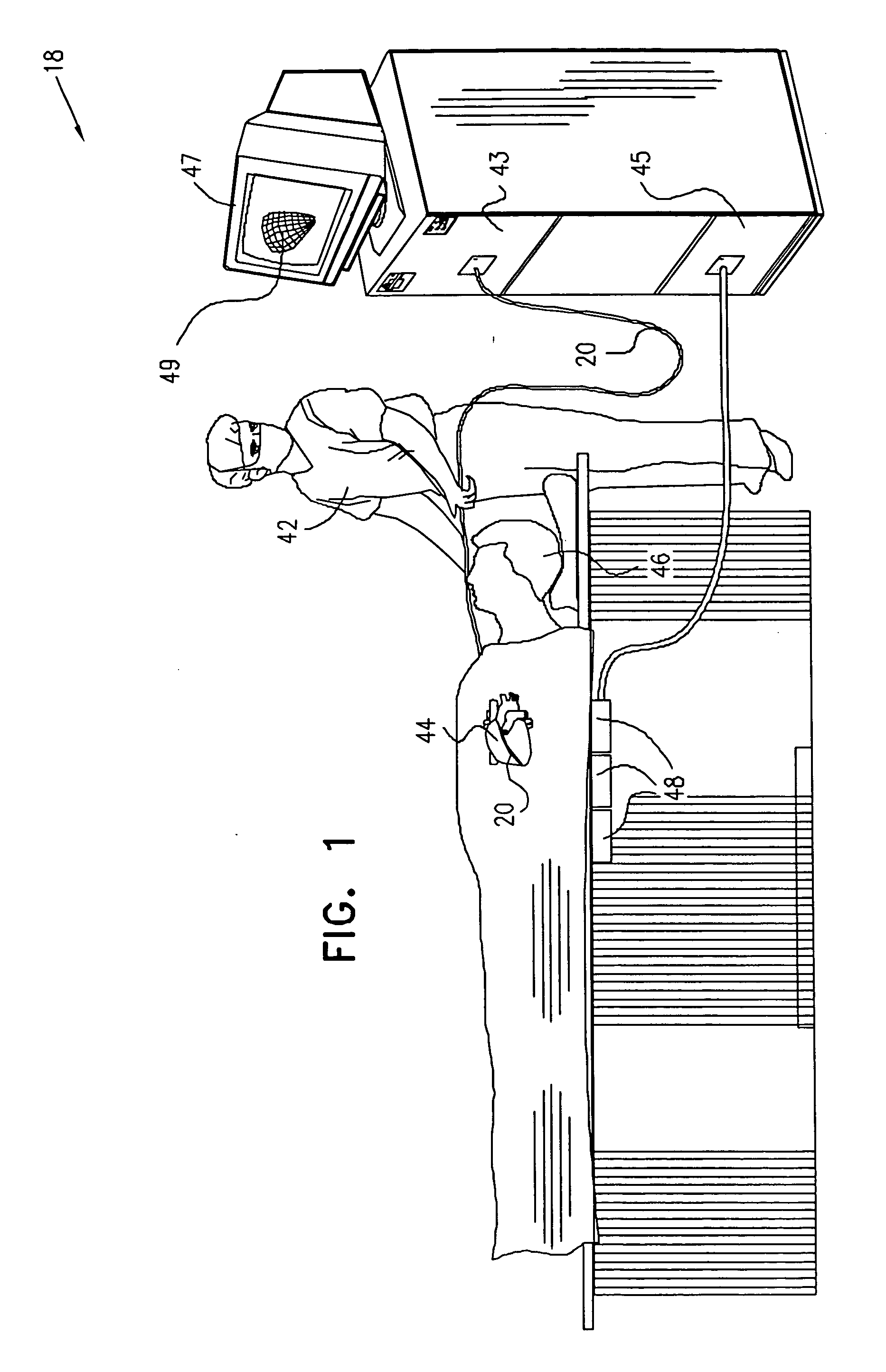
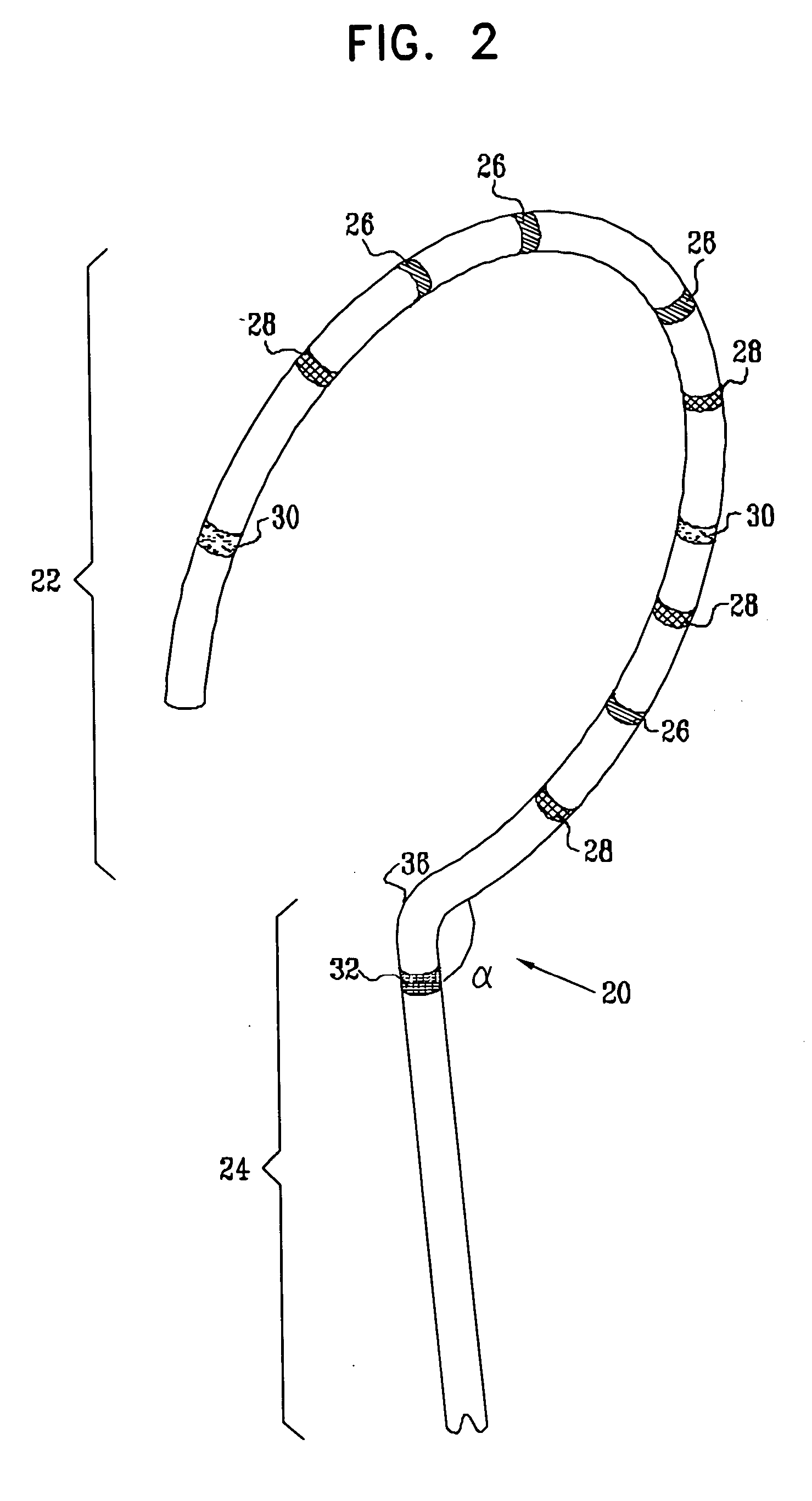
Lasso for pulmonary vein mapping and ablation
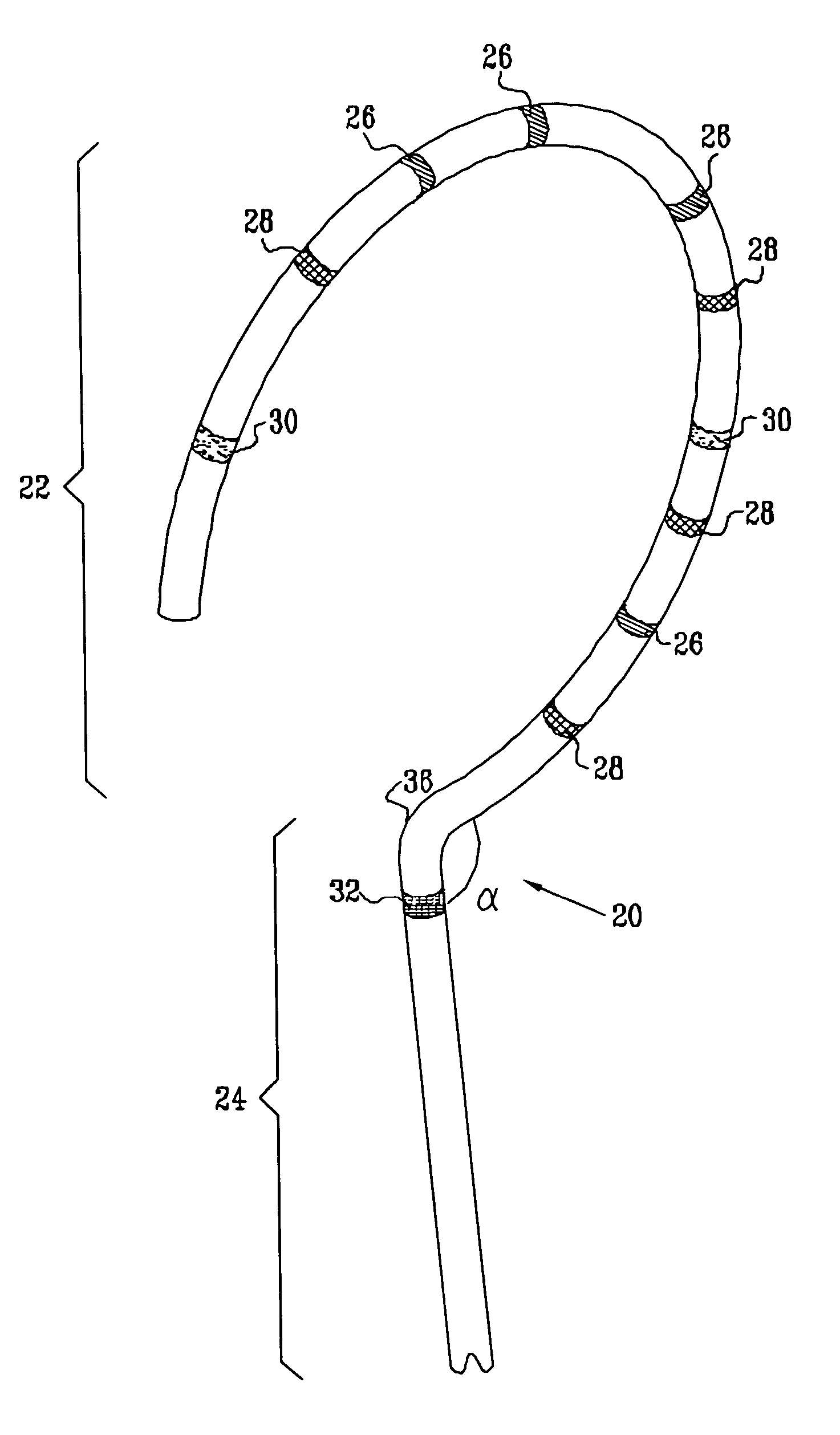
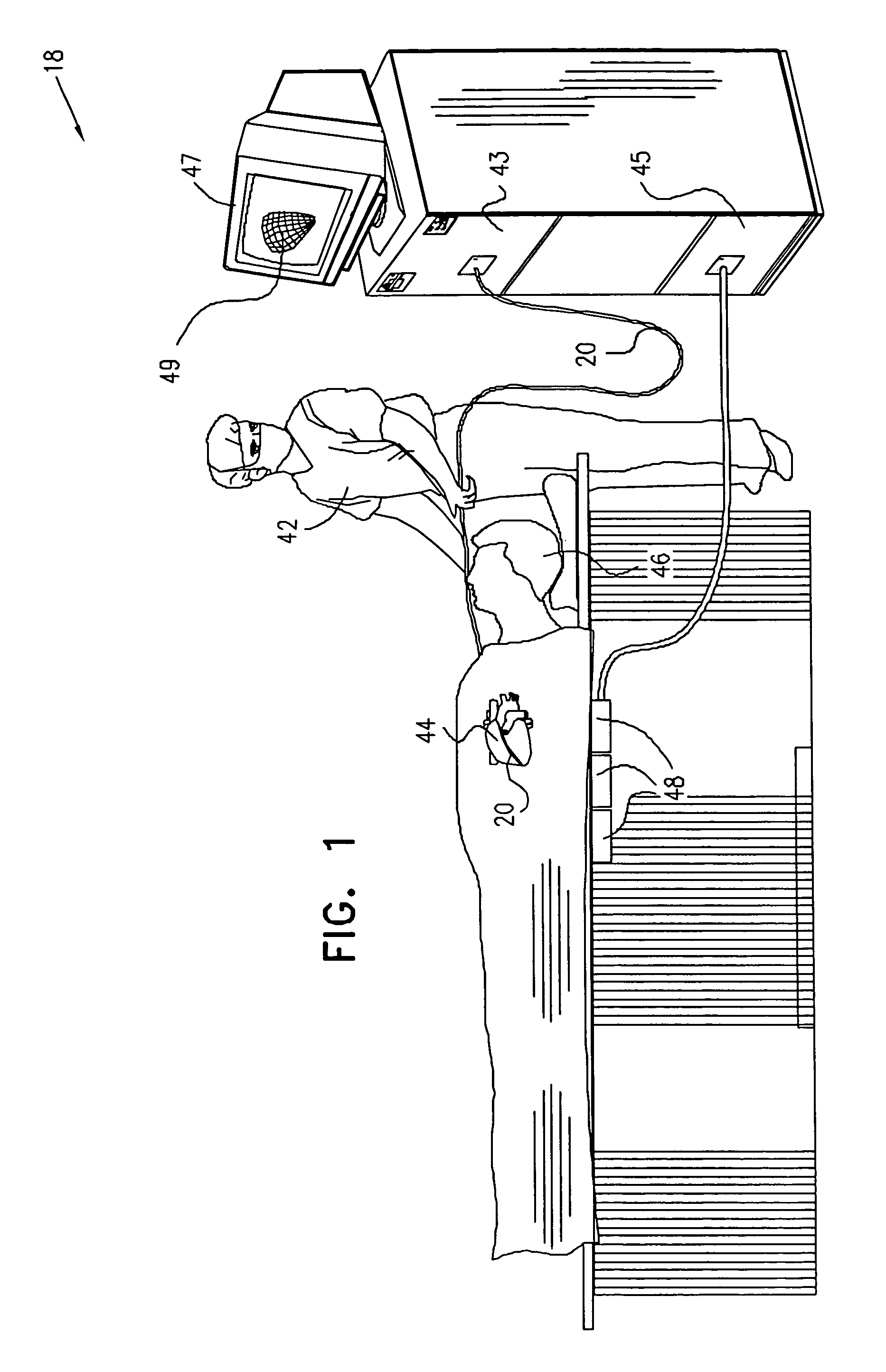
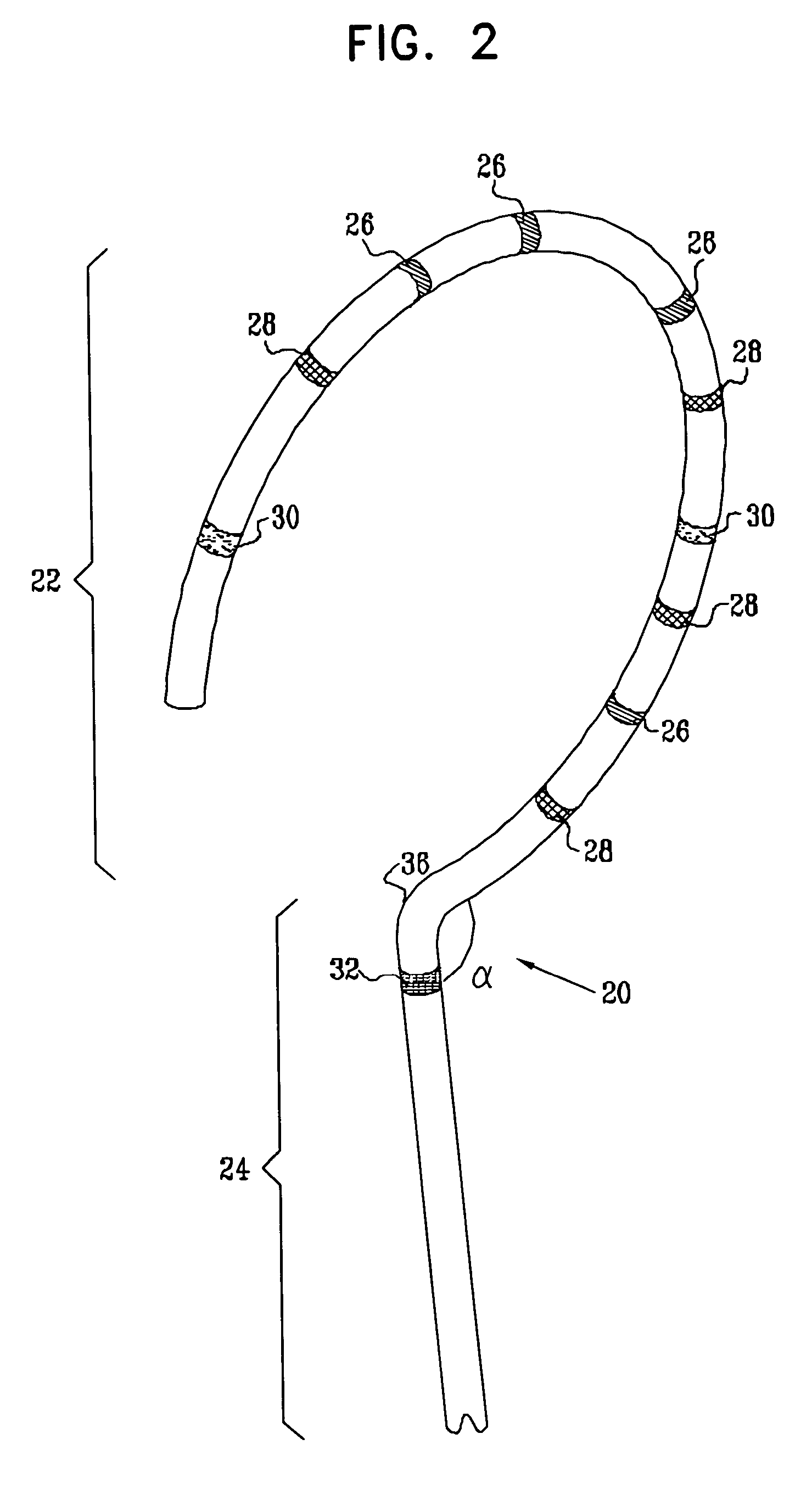
InactiveUS6973339B2Improve accuracyShorten the timeInternal electrodesDiagnostic recording/measuringVeinMedicine
Owner:BIOSENSE WEBSTER INC
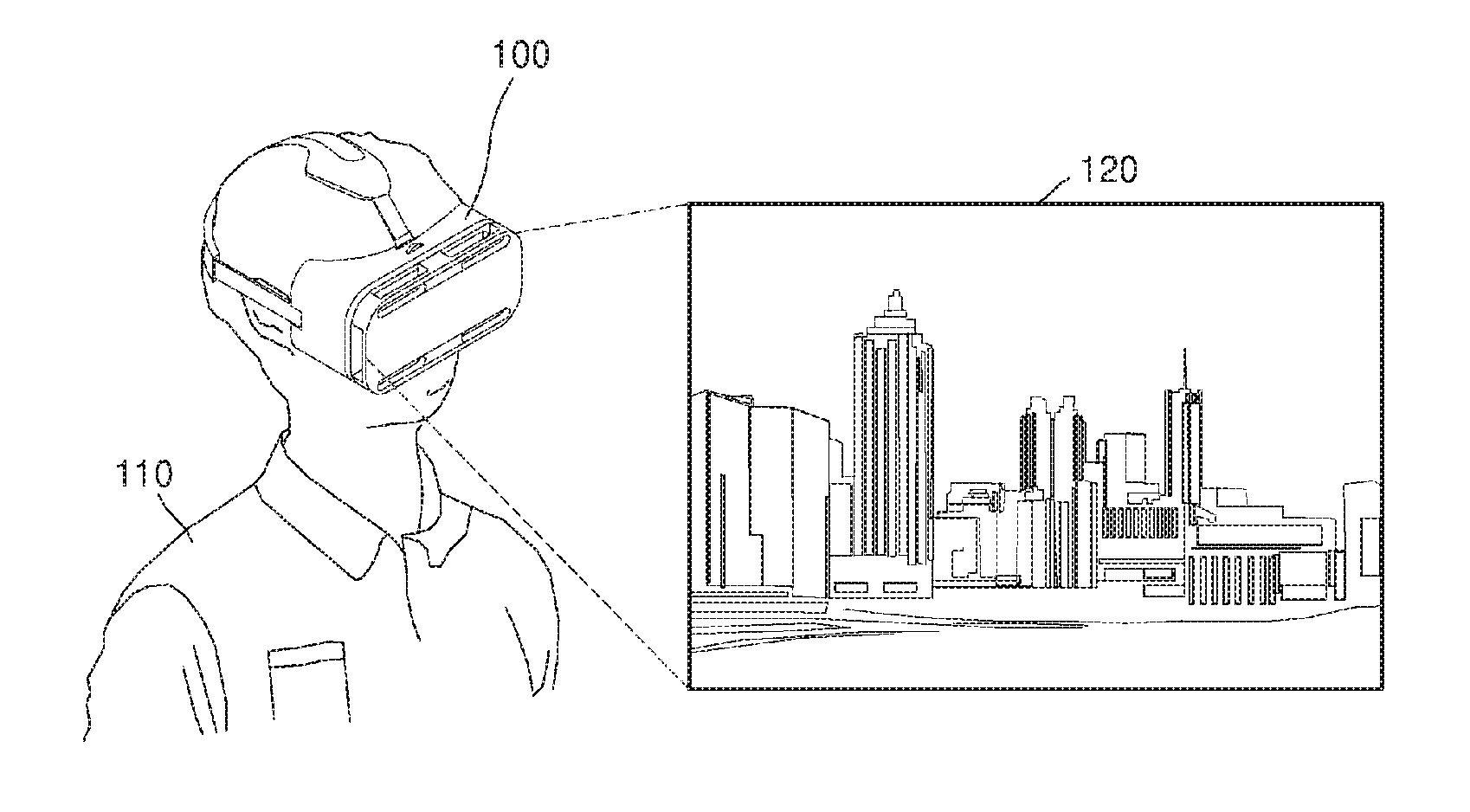
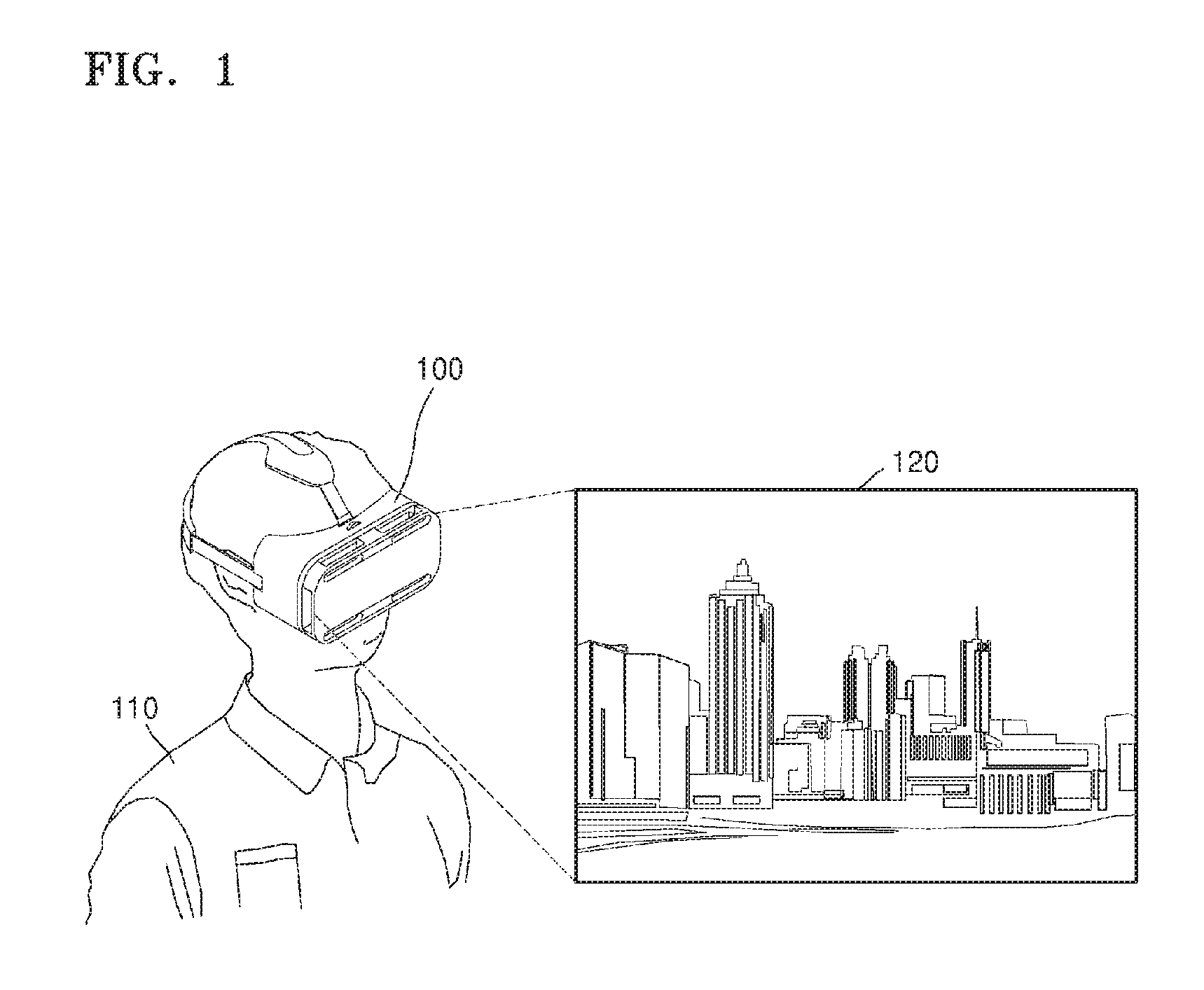
Virtual reality display apparatus and display method thereof
InactiveUS20170061696A1Add display methodImprove immersionImage analysisSteroscopic systemsObject basedVirtual reality
A virtual reality display apparatus and display method thereof are provided. The display method includes displaying a virtual reality image; acquiring object information regarding a real-world object based on a binocular view of the user; and displaying the acquired object information together with the virtual reality image.
Owner:SAMSUNG ELECTRONICS CO LTD
System and method for heating biological tissue via RF energy
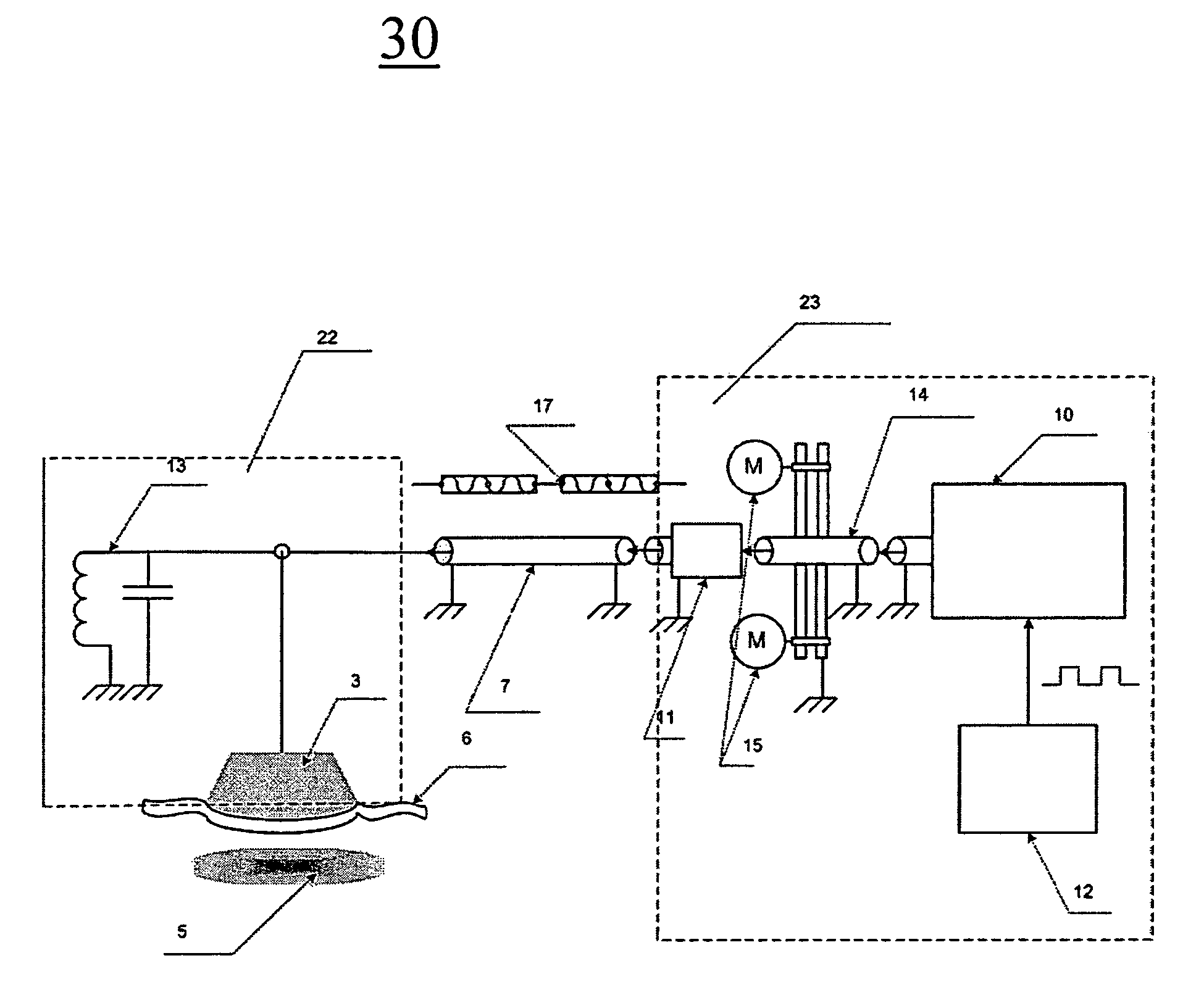
InactiveUS7630774B2Reduce the temperatureSimple methodElectrotherapyControlling energy of instrumentImpedance matchingThermal treatment
A system 30 and method(s) 100 for thermal treatment of a selected target within a subject is disclosed. System 30 includes RF source 10, phase shifter 14, impedance matching network 11 and resonator 13. Applicator 3 conveys output signal 17 from energy source 10 through surface 6 of biological tissue 4 to predetermined energy dissipation zone 5 after output 17 has been processed by the phase shifter 14, IMN 11 and resonator 13. Stationary water molecules 1, such as those in fat cells, are heated. System 30 is operative to heat a volume of biological tissue beneath the biological tissue surface 6 such that surface 6 of biological tissue 4 is maintained at a lower temperature than predetermined energy dissipation zone 5 without a cooling device. The invention is useful in selective heating of cellulite bodies as a means of treating cellulite.
Owner:ALMA LASERS LTD
Process for preparing arene selectivity by enhancing methanol aromatizatian and process for preparation of catalyst thereof
ActiveCN101550051AImprove methodHigh yieldMolecular sieve catalystsHydrocarbon by hydrocarbon and non-hydrocarbon condensationMolecular sieveFixed bed
The invention relates to a process for preparing arene selectivity by enhancing methanol aromatizatian. The process uses methanol as raw material, compositely modifies HZSM-5 molecular sieve catalyst by active ions like Ga, Zn, Cu, Cr and Ag for catalyzing methanol aromatizatian, employs the fixed bed continuous process or the floating bed continuous process, wherein the reaction pressure is 0.1-3.5MPa; the reaction temperature is 380-500 DEG C; the space velocity of raw material liquid is 0.1-10.0 h; and N2 space velocity is 120-800 h. The advantages of the invention lie in collocation combination of mixing ion modification, and arene selectivity reaches to 70%.
Owner:TIANJI COAL CHEM IND GROUP +1
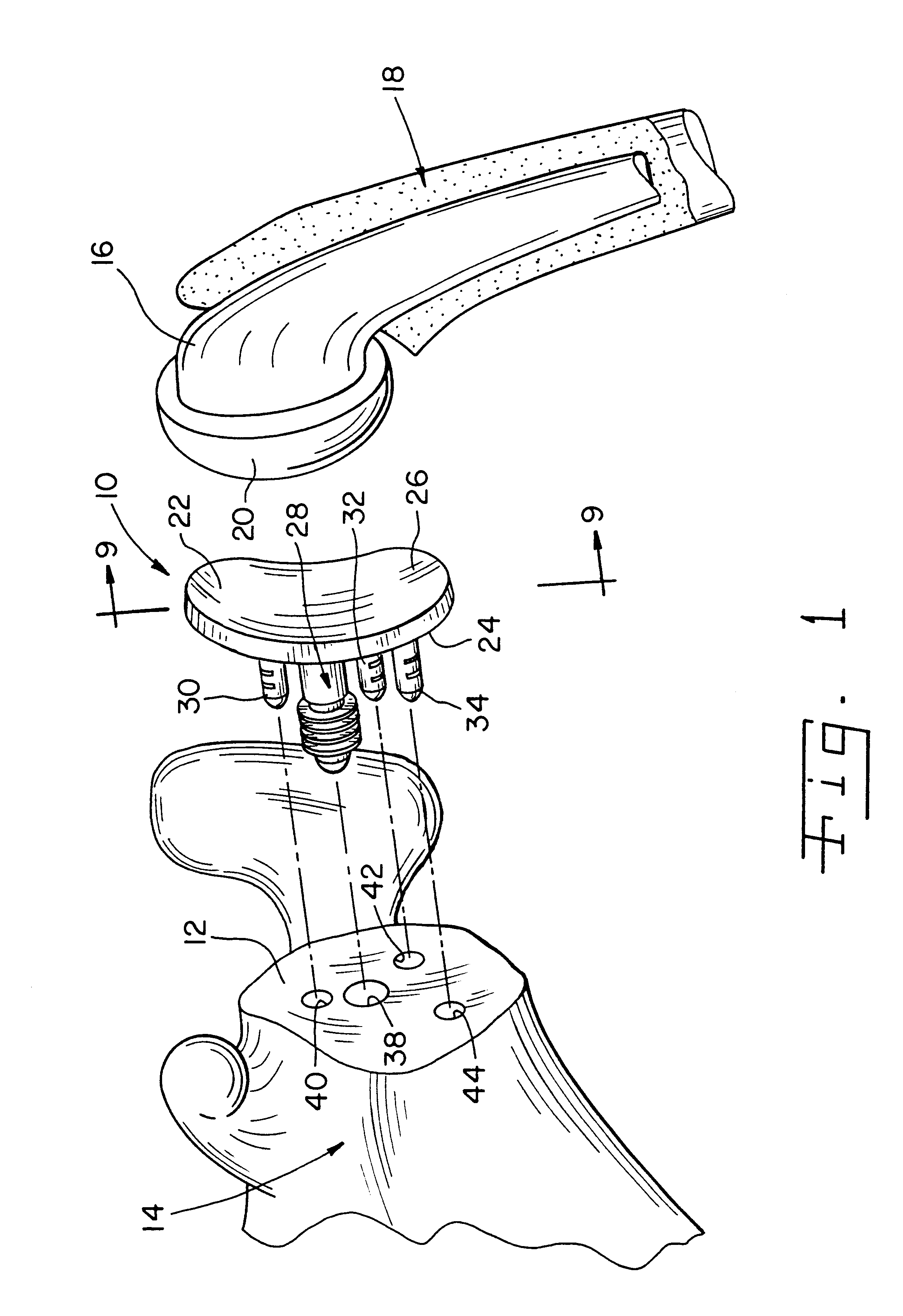
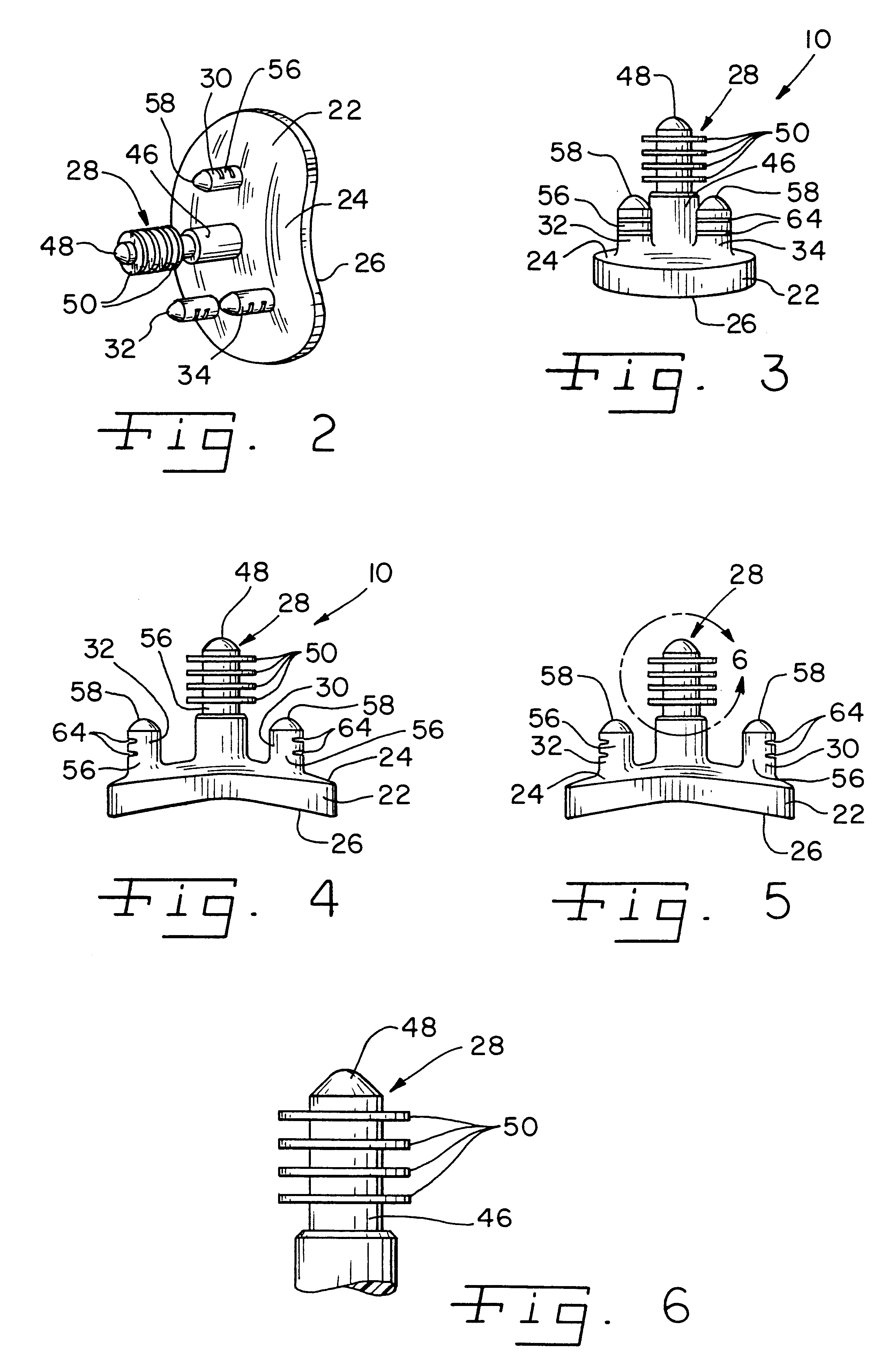
Apparatus and method for securing a cementless glenoid component to a glenoid surface of a scapula
A glenoid component for securement to a glenoid surface of a scapula so as to provide a bearing surface for a head portion of a humerus includes a body portion having a first surface configured to contact the glenoid surface of the scapula and a second surface configured to receive the head portion of the humerus. The glenoid component also includes an anchor peg extending from the first surface of the body portion for penetrating the glenoid surface of the scapula so as to secure the body portion to the glenoid surface of the scapula. The anchor peg has a first end portion and a second end portion with the first end portion of the anchor peg being secured to the first surface of the body portion, and the second end portion of the anchor peg having a number of fins secured thereto. The glenoid component also includes a first stabilizing peg extending from the first surface of the body portion for penetrating the glenoid surface of the scapula so as to prevent movement of the body portion relative to the glenoid surface of the scapula. A method of securing a glenoid component to a glenoid surface of a scapula so as to provide a bearing surface for a head portion of a humerus is also disclosed.
Owner:DEPUY PROD INC
Droplet Actuator Configurations and Methods
InactiveUS20100307917A1Easy to useFacilitates of propertyElectrostatic separatorsSludge treatmentEngineeringActuator
Droplet actuators for conducting droplet operations, such as droplet transport and droplet dispensing, are provided. In one embodiment, the droplet actuator may include a substrate including, droplet operations electrodes arranged for conducting droplet operations on a surface of the substrate; and reference electrodes associated with the droplet operations electrodes and extending above the surface of the substrate. Other embodiments of droplet actuators and methods of loading and using such droplet actuators are also provided.
Owner:ADVANCED LIQUID LOGIC
Solid-state imaging device, method for processing signal of solid-state imaging device, and imaging apparatus
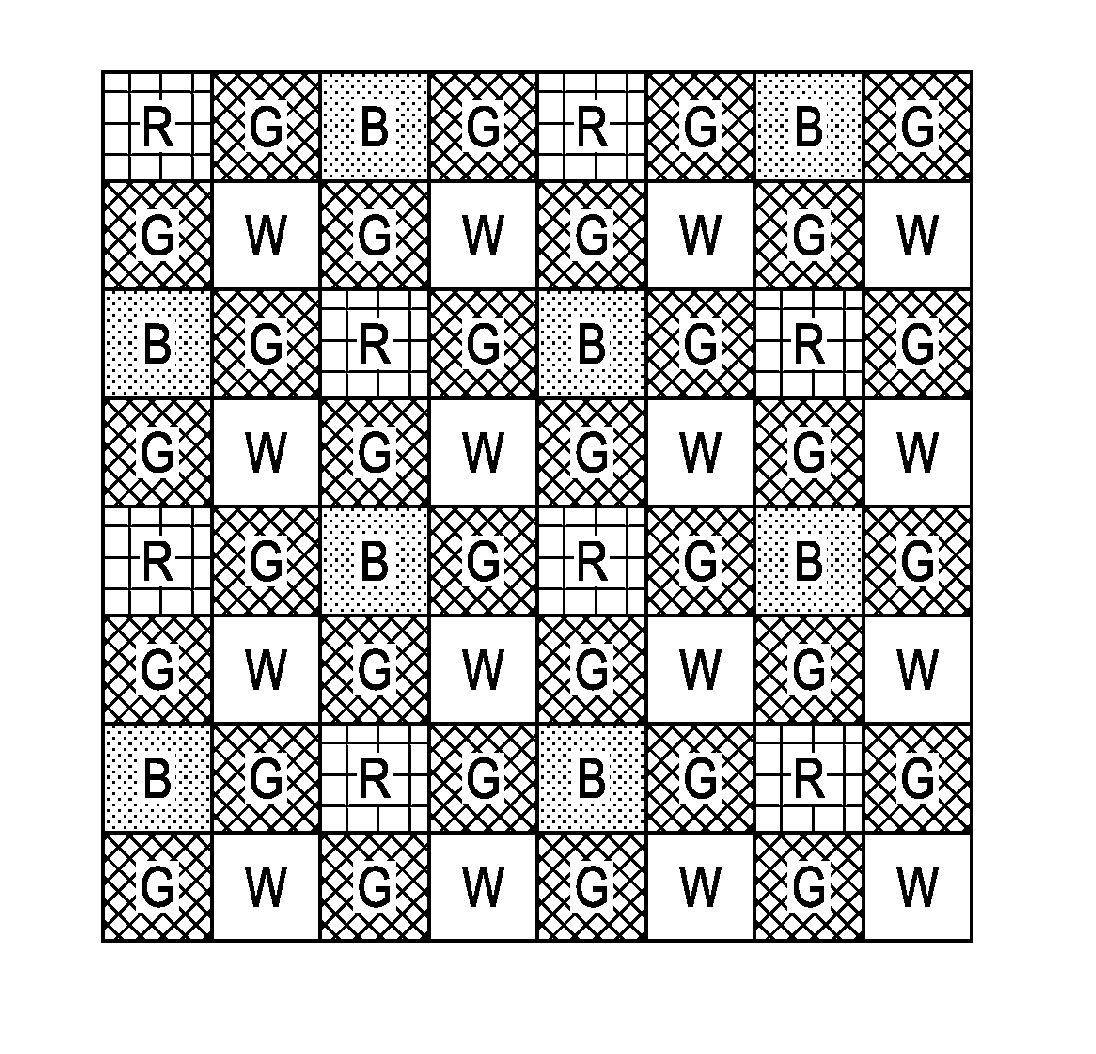
InactiveUS20100141812A1High sensitivityHigh strengthTelevision system detailsImage analysisCheckerboard patternComputer science
A solid-state imaging device includes a color filter unit disposed on a pixel array unit including pixels two-dimensionally arranged in a matrix and a conversion processing unit disposed on a substrate having the pixel array unit thereon. The color filter unit has a color arrangement in which a color serving as a primary component of a luminance signal is arranged in a checkerboard pattern and a plurality of colors serving as color information components are arranged in the other area of the checkerboard pattern. The conversion processing unit converts signals that are output from the pixels of the pixel array unit and that correspond to the color arrangement of the color filter unit into signals that correspond to a Bayer arrangement and outputs the converted signals.
Owner:SONY CORP
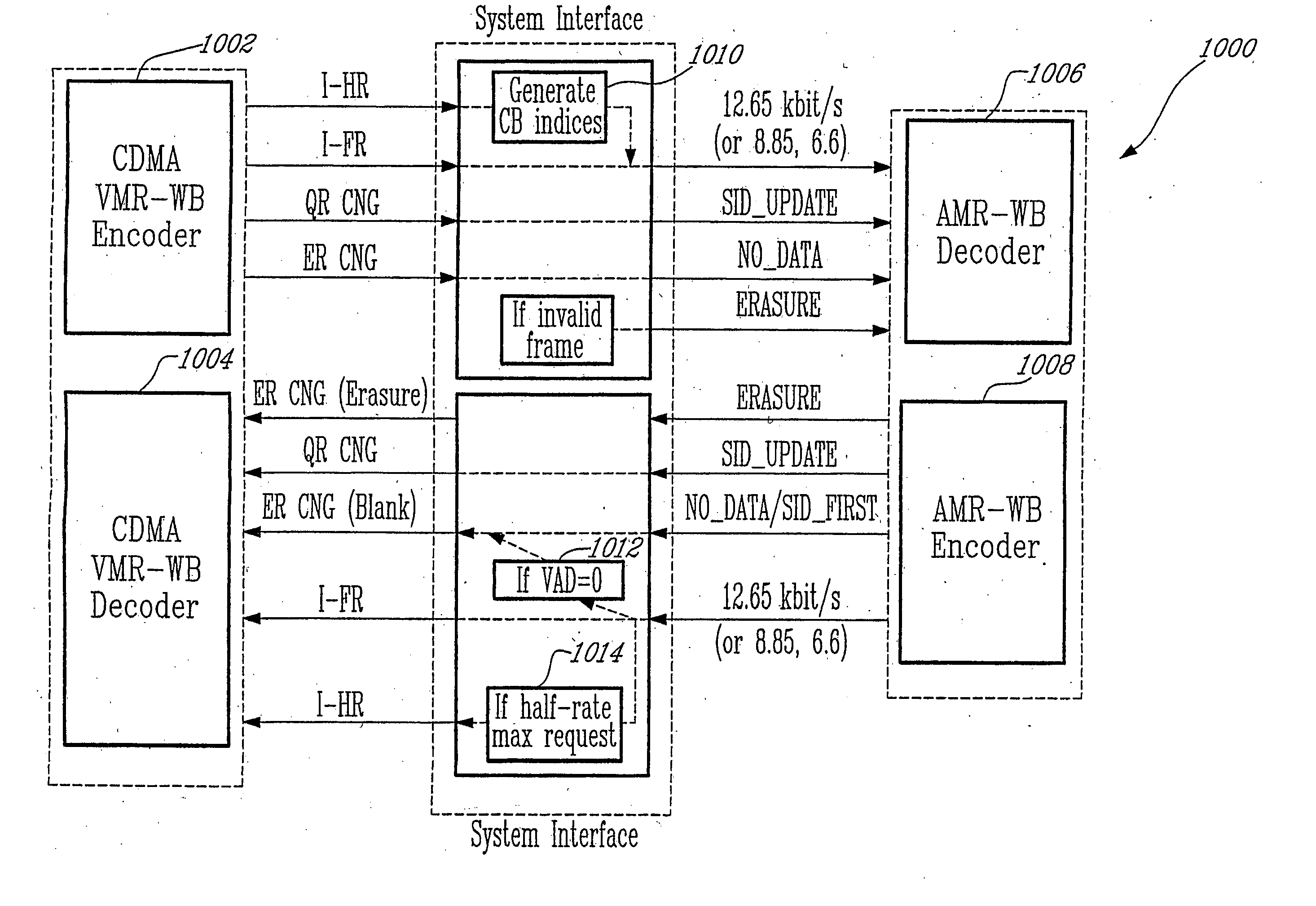
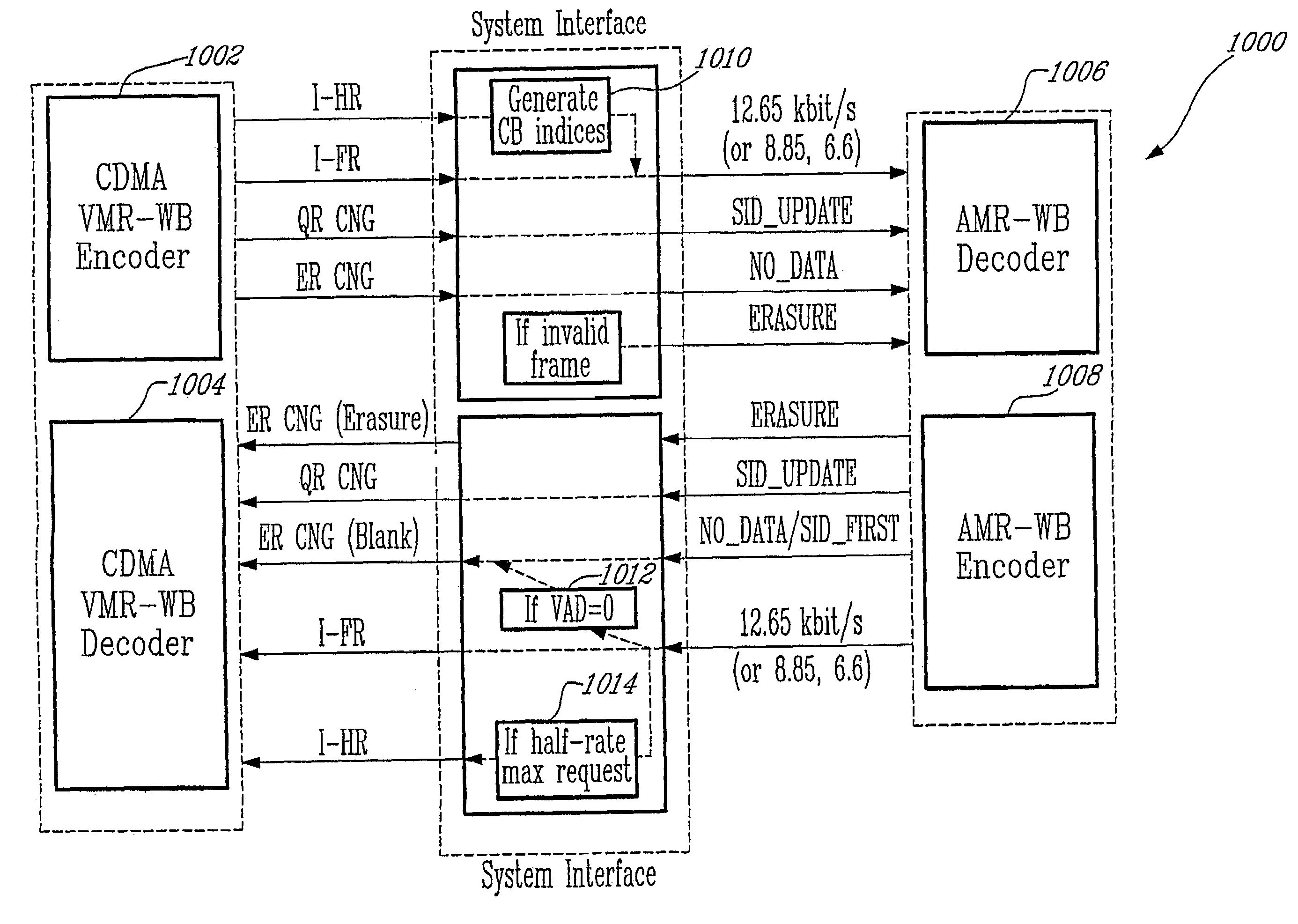
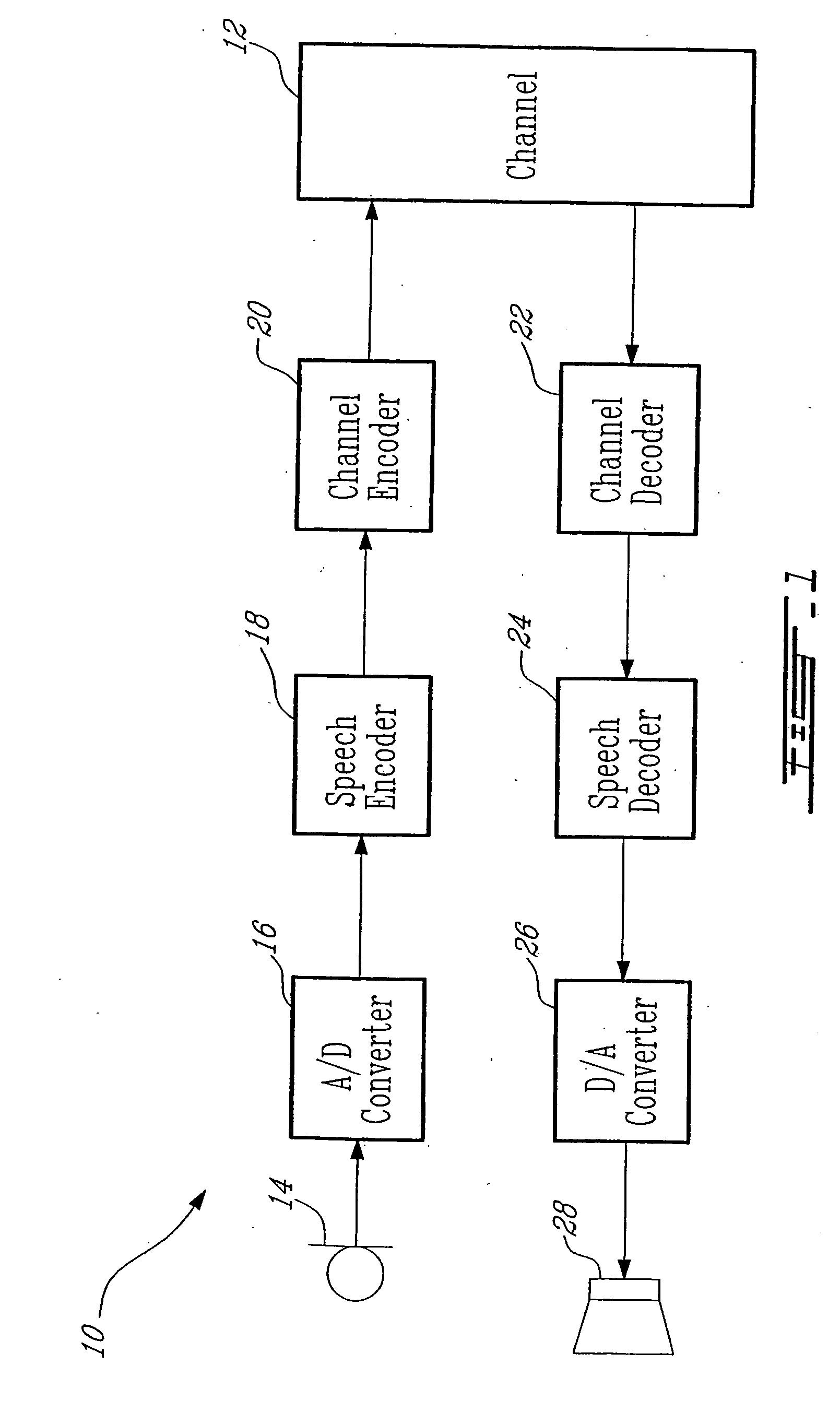
Method for interoperation between adaptive multi-rate wideband (AMR-WB) and multi-mode variable bit-rate wideband (VMR-WB) codecs
ActiveUS20050267746A1Improve classificationImprove methodSpeech analysisFluid pressure measurementBit allocationFull Rate
A source-controlled Variable bit-rate Multi-mode WideBand (VMR-WB) codec, having a mode of operation that is interoperable with the Adaptive Multi-Rate wideband (AMR-WB) codec, the codec comprising: at least one Interoperable full-rate (I-FR) mode, having a first bit allocation structure based on one of a AMR-WB codec coding types; and at least one comfort noise generator (CNG) coding type for encoding inactive speech frame having a second bit allocation structure based on AMR-WB SID_UPDATE coding type. Methods for i) digitally encoding a sound using a source-controlled Variable bit rate multi-mode wideband (VMR-WB) codec for interoperation with an adaptative multi-rate wideband (AMR-WB) codec, ii) translating a Variable bit rate multi-mode wideband (VMR-WB) codecsignal frame into an Adaptive Multi-Rate wideband (AMR-WB) signal frame, iii) translating an Adaptive Multi-Rate wideband (AMR-WB) signal frame into a Variable bit rate multi-mode wideband (VMR-WB) signal frame, and iv) translating an Adaptive Multi-Rate wideband (AMR-WB) signal frame into a Variable bit rate multi-mode wideband (VMR-WB) signal frame are also provided.
Owner:NOKIA TECHNOLOGLES OY
Tire temperature and pressure monitoring sensors and systems
InactiveUS7075421B1Avoid degradationInhibit wearOptical signallingTyre measurementsMonitoring systemRadio frequency
A tire monitoring system providing tire status and notifying or warning the vehicle operator of early detection of imminent tire failure and performance degradation; thus improving safety by preventing blowouts from occurring, lengthening tire life by encouraging preventive maintenance, and improving fuel mileage by encouraging the operator to fill the tire to its proper pressure or repair it. The system monitors temperature of the rim of the wheel to which the tire is attached, such temperature being transmitted to the vehicle operator or other interested parties via means such as radio frequency.
Owner:TUTTLE JOHN R
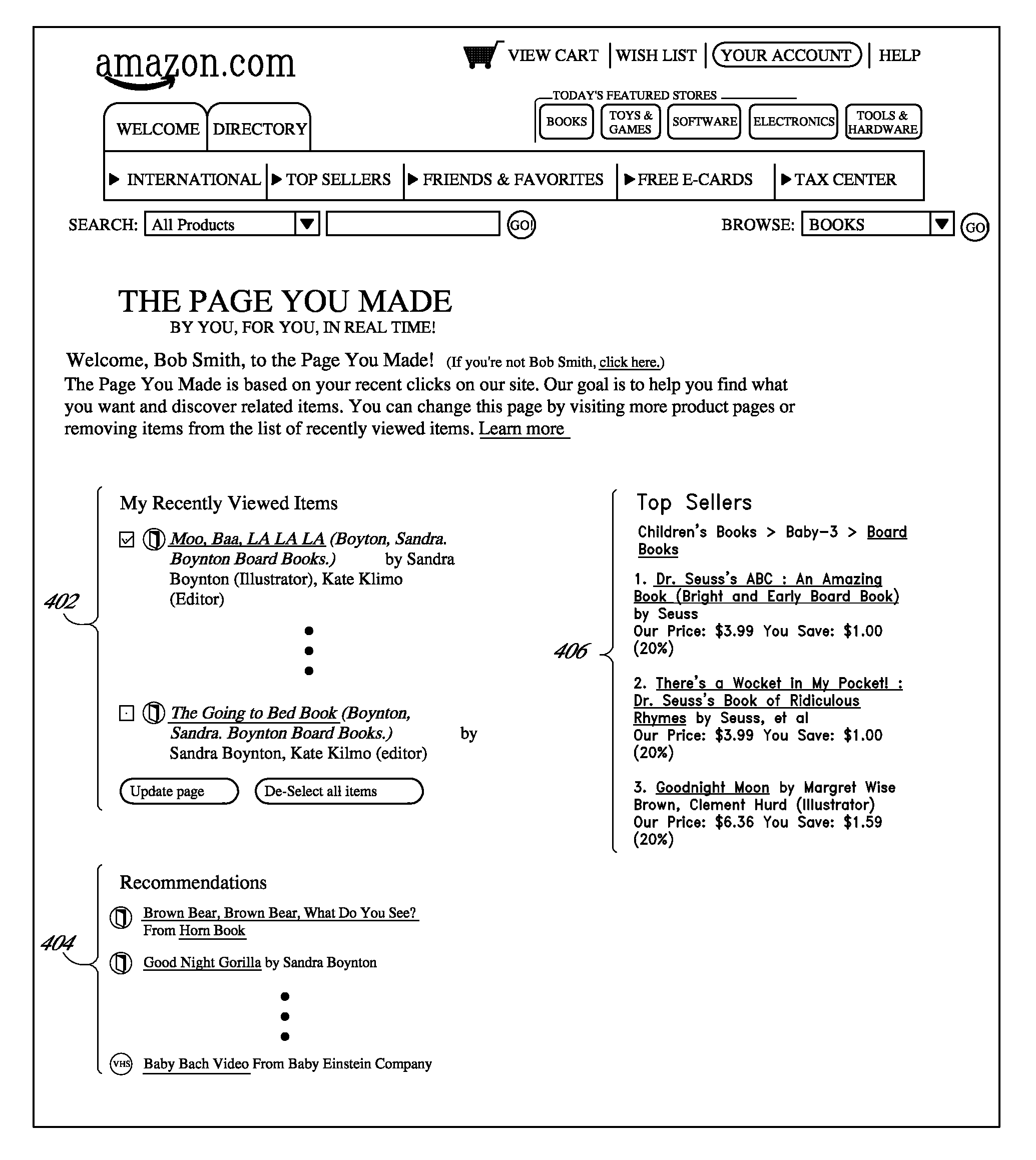
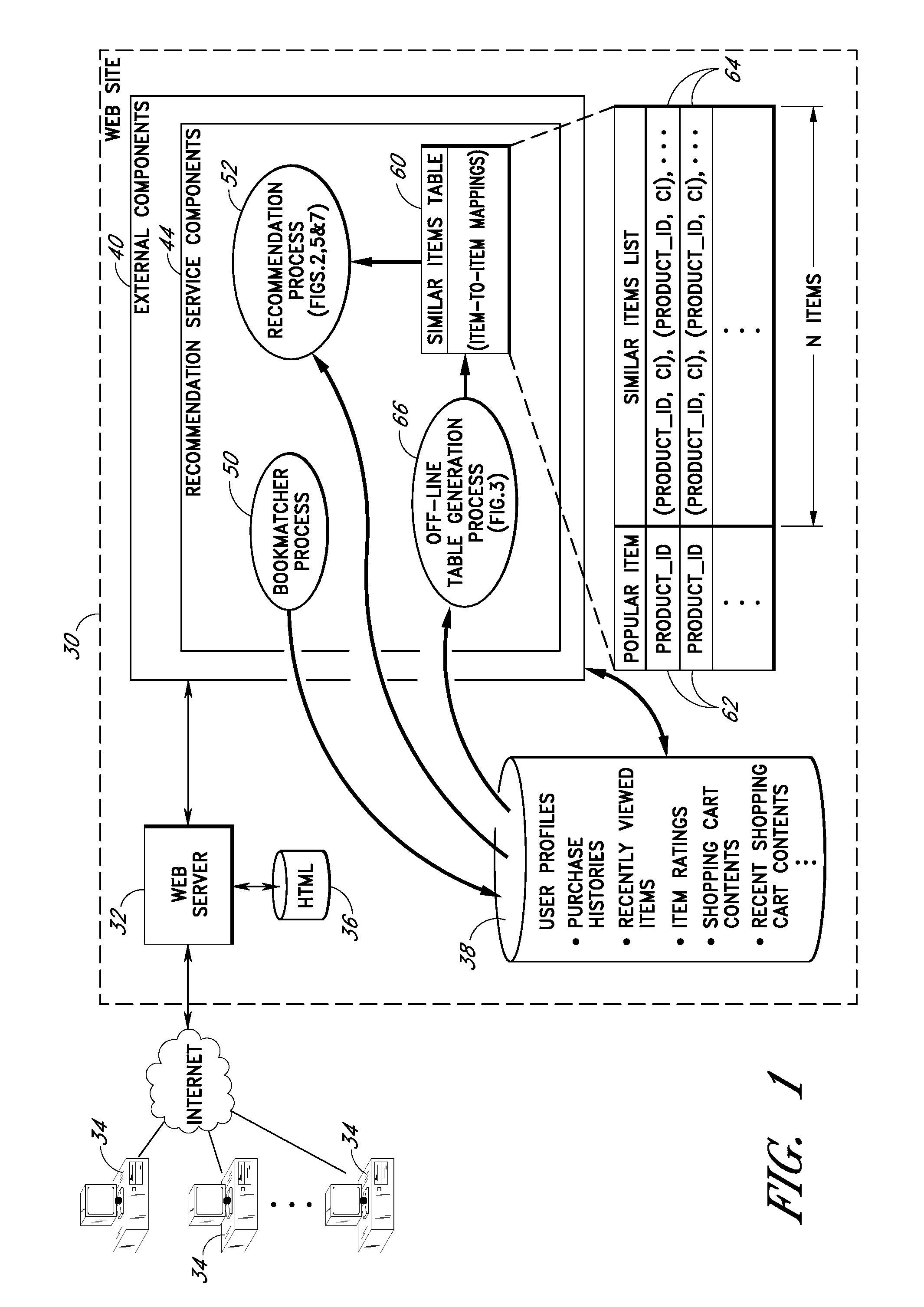
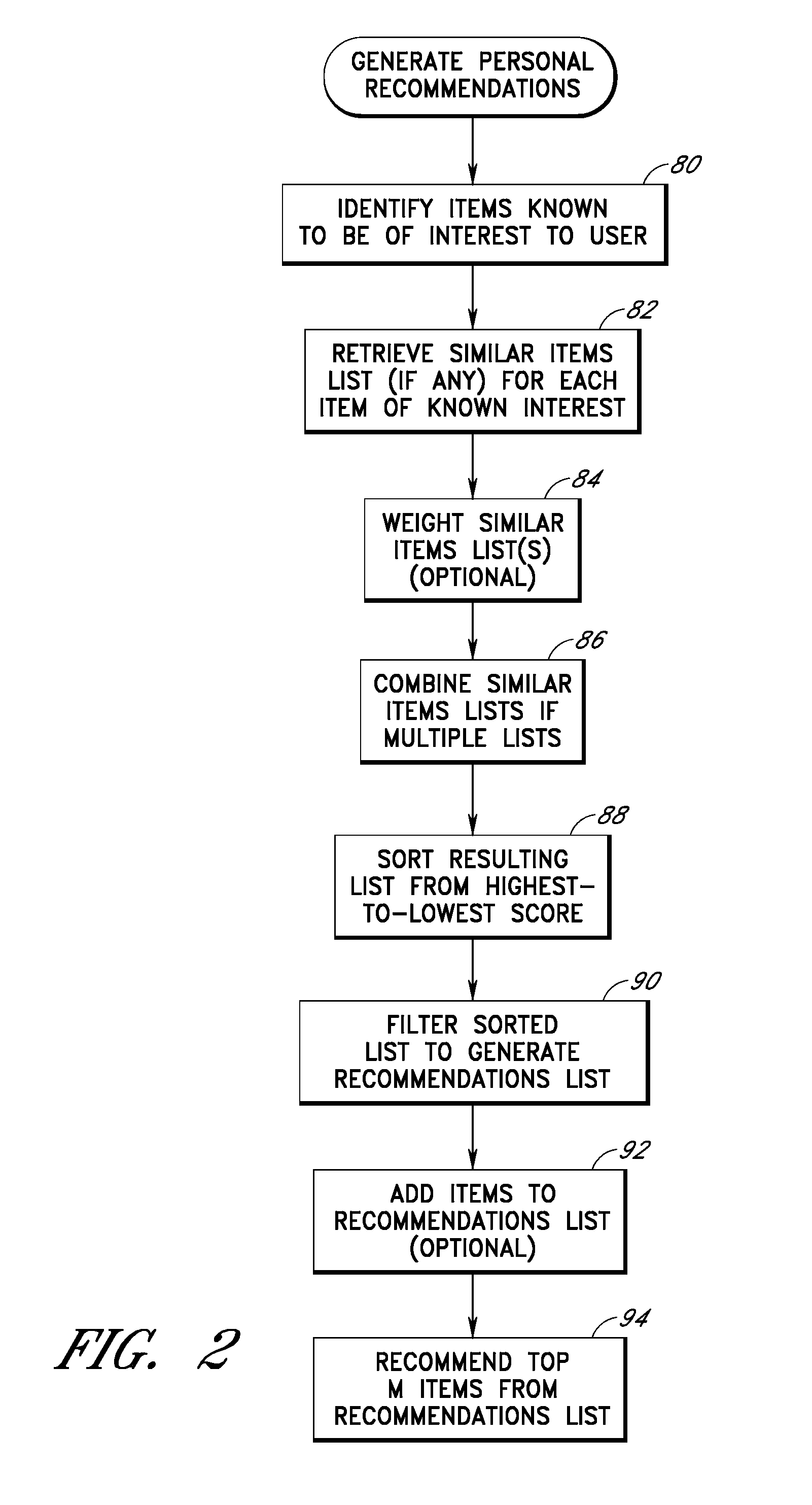
User interface and methods for recommending items to users
ActiveUS20100191619A1Without sacrificing breadthQuick buildMarketingInput/output processes for data processingGeneration processUser interface
Improved user interfaces and methods are provided for presenting item recommendations to a user when the user selects an item to add to an electronic shopping cart. In response to the user's selection, a page generation process generates and returns a page that includes a condensed shopping cart portion and a recommendations portion. The condensed shopping cart portion displays the contents of the shopping cart, but omits some of the item information and / or controls provided on a shopping cart page, thereby preserving more screen real estate for the display of item recommendations. The condensed shopping cart portion also includes a link to the shopping cart page.
Owner:AMAZON TECH INC
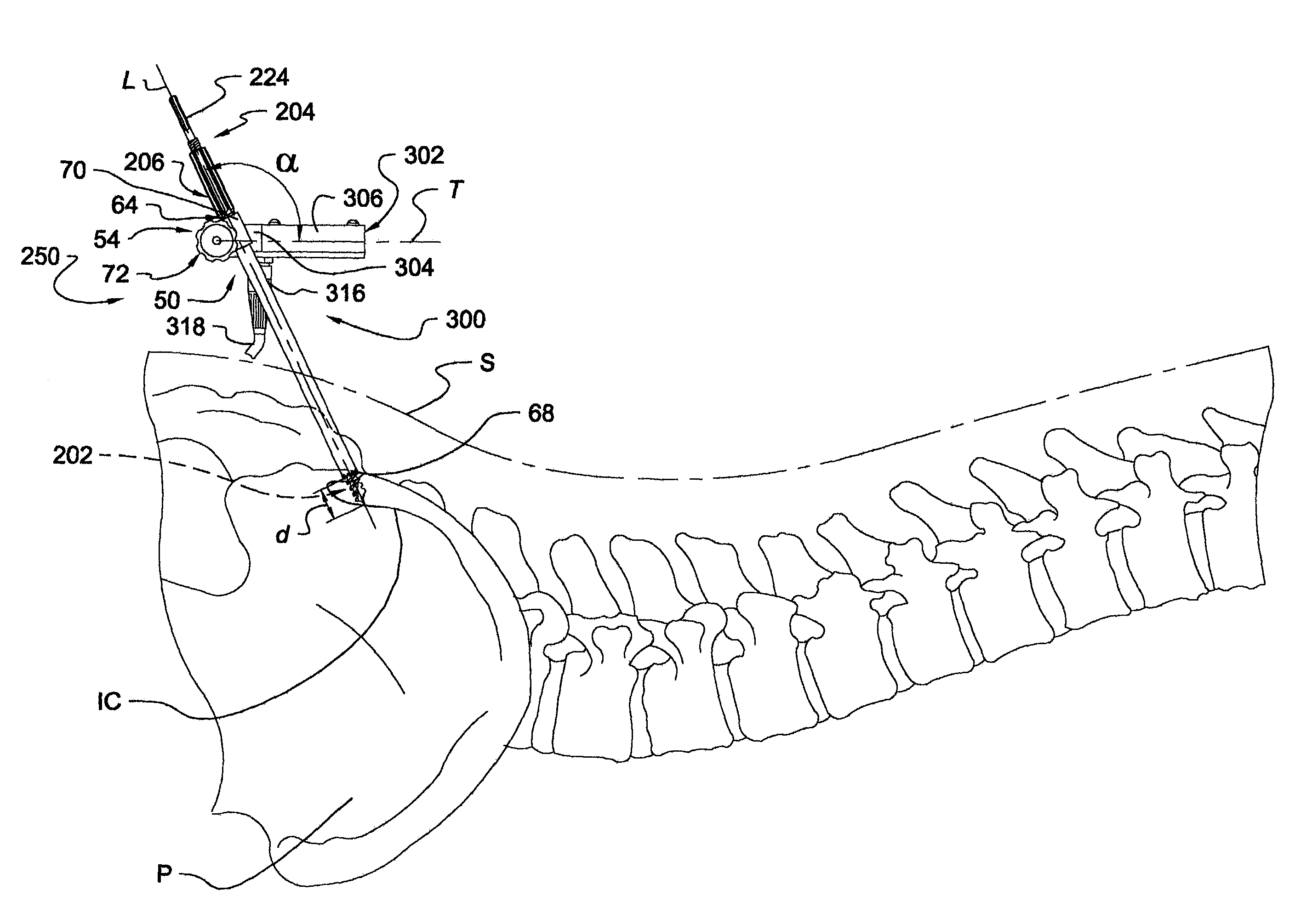
Instrumentation and method for mounting a surgical navigation reference device to a patient
ActiveUS6993374B2Improved instrumentationImprove methodSuture equipmentsDiagnostic markersSpinal columnIliac region
Instrumentation and methods are provided for mounting a surgical navigation reference frame to a patient for performing an image-guided surgical procedure on an anatomical component. In one embodiment of the invention, a trocar is positioned within a cannula to form an insertion device adapted for percutaneous introduction into the patient. A bone anchor having a bone engaging portion is inserted through the cannula and is anchored to bone. The bone anchor cooperates with the cannula to form a mounting device adapted for coupling with the surgical navigation reference frame. In one embodiment of the invention, an image-guided surgical procedure is performed at a location remote from the anchoring location. In a specific embodiment, an image-guided surgical procedure is performed adjacent the spinal column, with the bone engaging portion of the bone anchor anchored to the iliac region of the pelvic bone, and more specifically to the iliac crest of the pelvic bone.
Owner:WARSAW ORTHOPEDIC INC
Method for interoperation between adaptive multi-rate wideband (AMR-WB) and multi-mode variable bit-rate wideband (VMR-WB) codecs
InactiveUS7203638B2Improve classificationImprove methodSpeech analysisFluid pressure measurementUltra-widebandBit allocation
A source-controlled Variable bit-rate Multi-mode WideBand (VMR-WB) codec, having a mode of operation that is interoperable with the Adaptive Multi-Rate wideband (AMR-WB) codec, the codec comprising: at least one Interoperable full-rate (I-FR) mode, having a first bit allocation structure based on one of a AMR-WB codec coding types; and at least one comfort noise generator (CNG) coding type for encoding inactive speech frame having a second bit allocation structure based on AMR-WB SID_UPDATE coding type. Methods for i) digitally encoding a sound using a source-controlled Variable bit rate multi-mode wideband (VMR-WB) codec for interoperation with an adaptative multi-rate wideband (AMR-WB) codec, ii) translating a Variable bit rate multi-mode wideband (VMR-WB) codecsignal frame into an Adaptive Multi-Rate wideband (AMR-WB) signal frame, iii) translating an Adaptive Multi-Rate wideband (AMR-WB) signal frame into a Variable bit rate multi-mode wideband (VMR-WB) signal frame, and iv) translating an Adaptive Multi-Rate wideband (AMR-WB) signal frame into a Variable bit rate multi-mode wideband (VMR-WB) signal frame are also provided.
Owner:NOKIA TECH OY
Lasso for pulmonary vein mapping and ablation
ActiveUS20050033135A1Improve accuracyShorten the timeInternal electrodesDiagnostic recording/measuringVeinMedicine
A method is provided for electrical mapping of a pulmonary vein of a heart, including introducing into the heart a catheter having a curved section and a base section, the base section having a distal end attached to a proximal end of the curved section. At a location on the curved section, a first position signal is generated having fewer than six dimensions of position and orientation information. At a vicinity of the distal end of the base section, a second position signal is generated having six dimensions of position and orientation information. The method also includes measuring, at one or more locations on the curved section, an electrical property of the pulmonary vein.
Owner:BIOSENSE WEBSTER INC
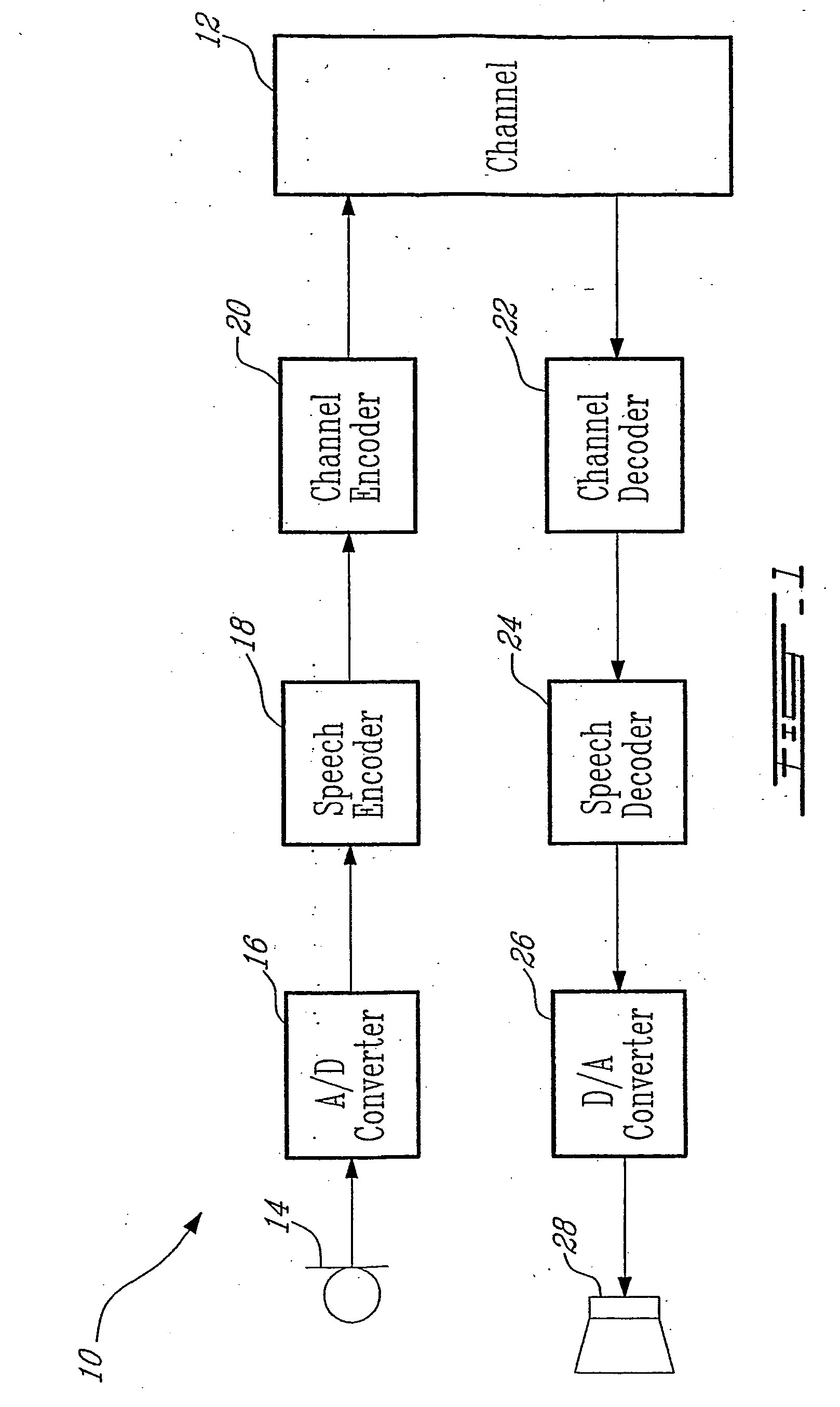
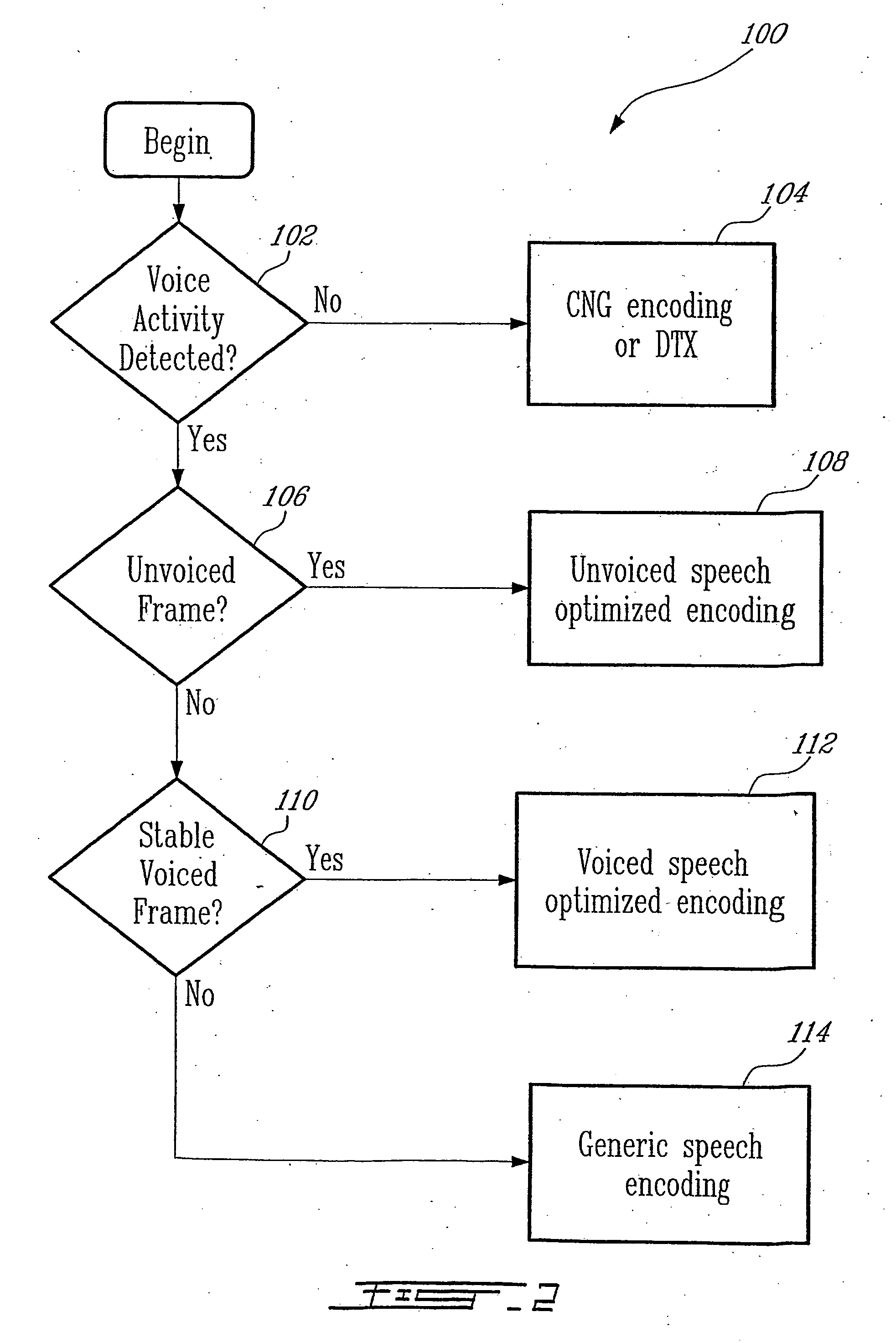
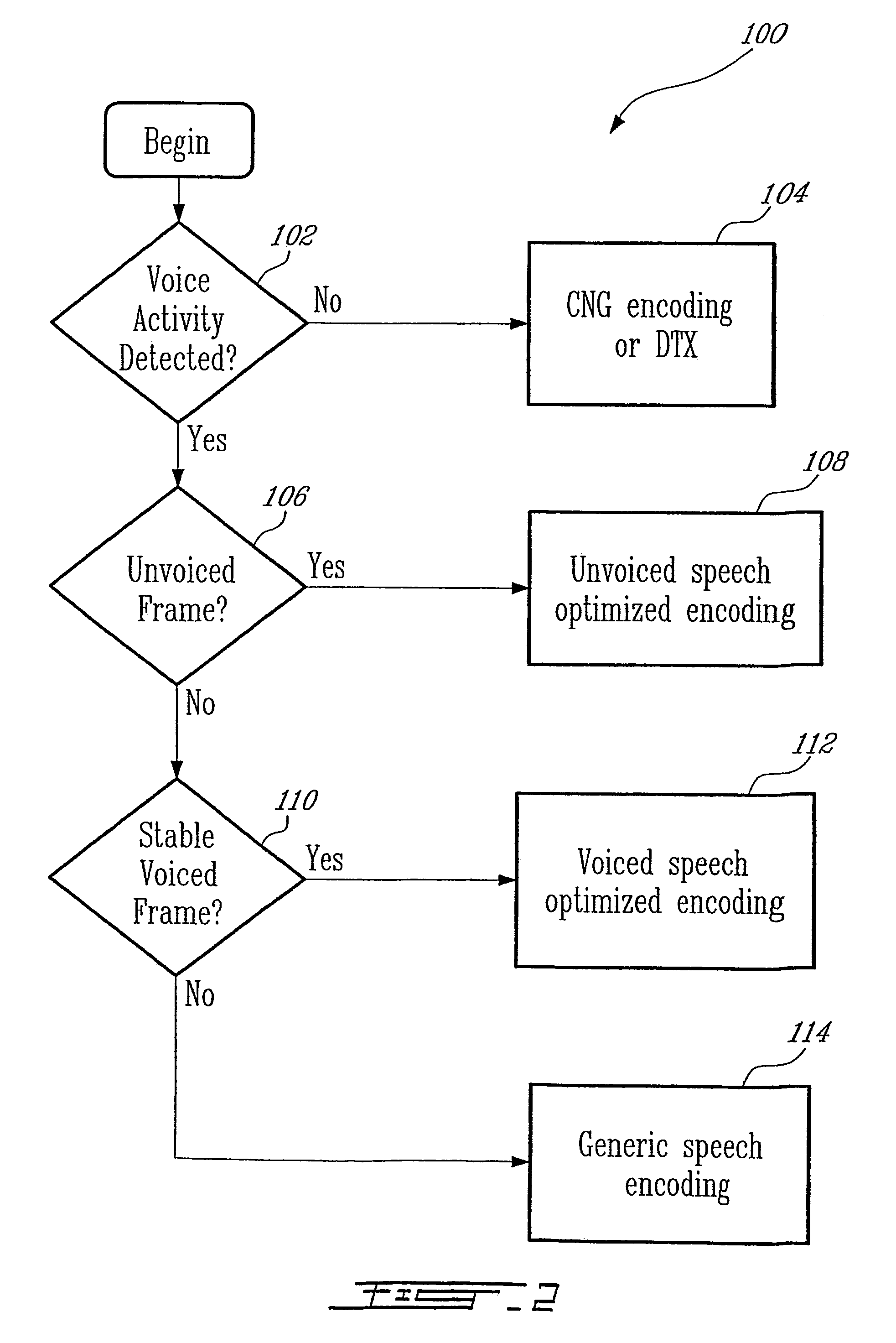
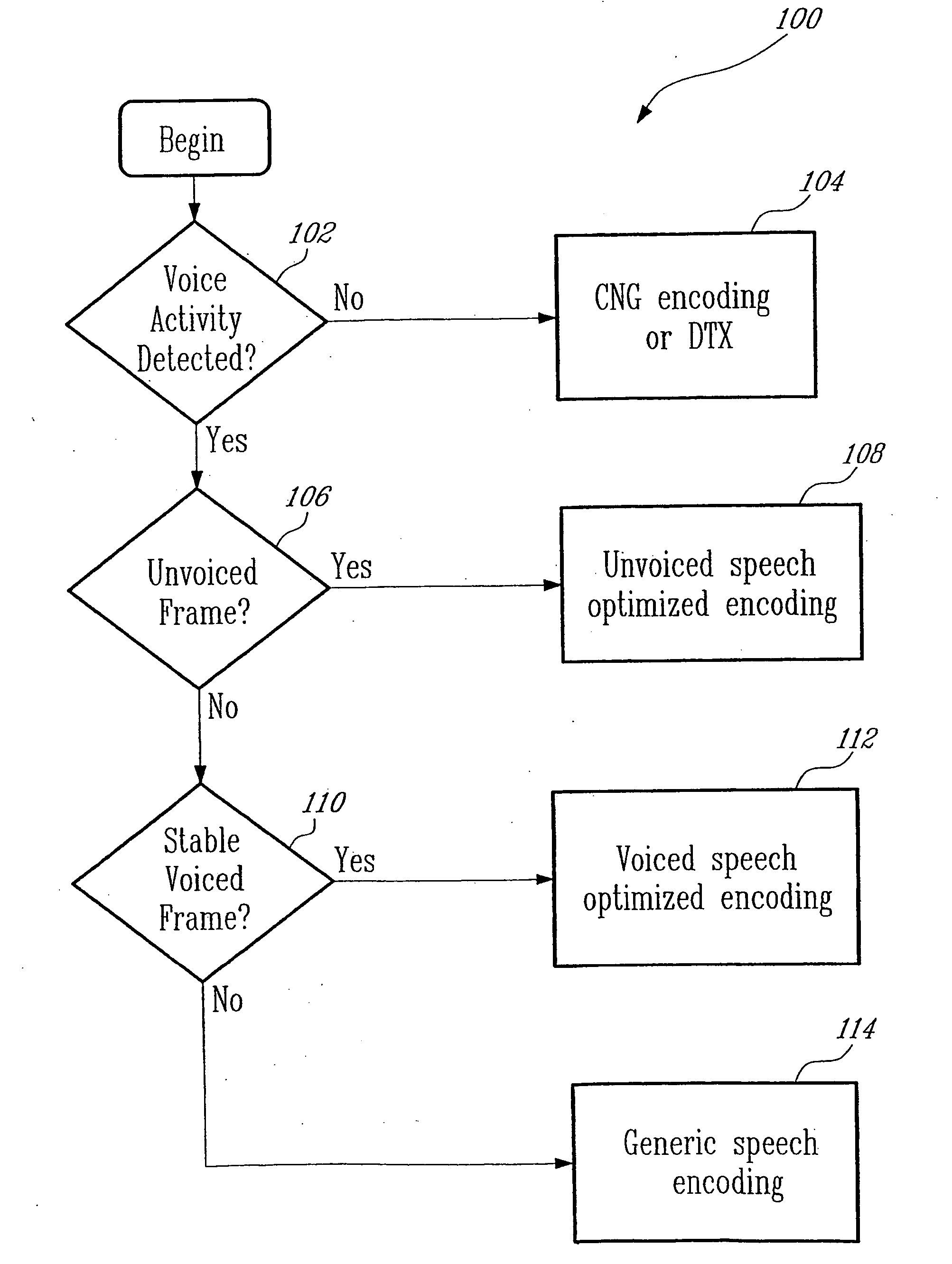
Methods and devices for source controlled variable bit-rate wideband speech coding
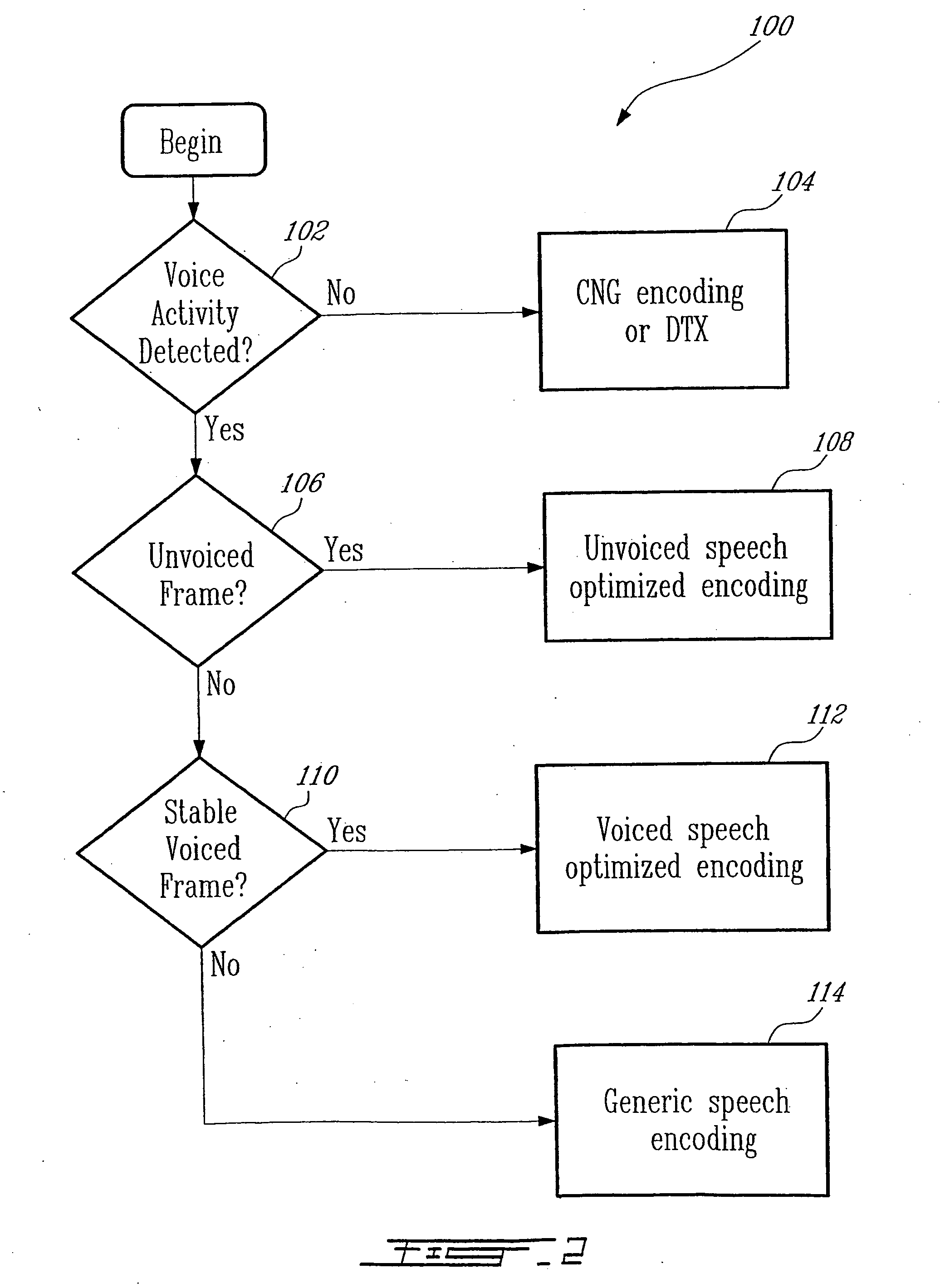
ActiveUS20050177364A1Improve methodImproved signal classificationSpeech analysisControl variableSubjective quality
Speech signal classification and encoding systems and methods are disclosed herein. The signal classification is done in three steps each of them discriminating a specific signal class. First, a voice activity detector (VAD) discriminates between active and inactive speech frames. If an inactive speech frame is detected (background noise signal) then the classification chain ends and the frame is encoded with comfort noise generation (CNG). If an active speech frame is detected, the frame is subjected to a second classifier dedicated to discriminate unvoiced frames. If the classifier classifies the frame as unvoiced speech signal, the classification chain ends, and the frame is encoded using a coding method optimized for unvoiced signals. Otherwise, the speech frame is passed through to the “stable voiced” classification module. If the frame is classified as stable voiced frame, then the frame is encoded using a coding method optimized for stable voiced signals. Otherwise, the frame is likely to contain a non-stationary speech segment such as a voiced onset or rapidly evolving voiced speech signal. In this case a general-purpose speech coder is used at a high bit rate for sustaining good subjective quality.
Owner:NOKIA TECHNOLOGLES OY
Universal forms engine
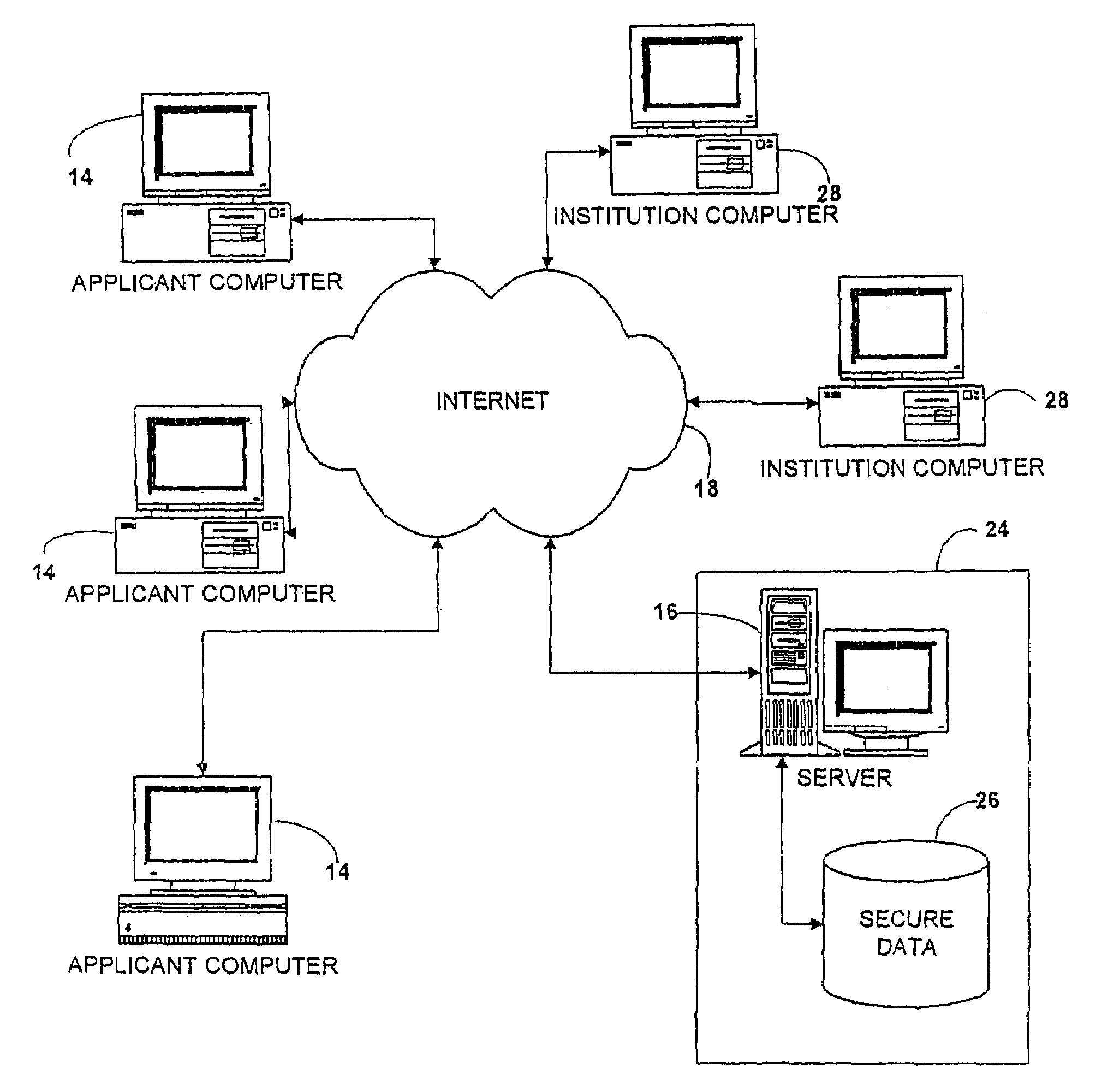
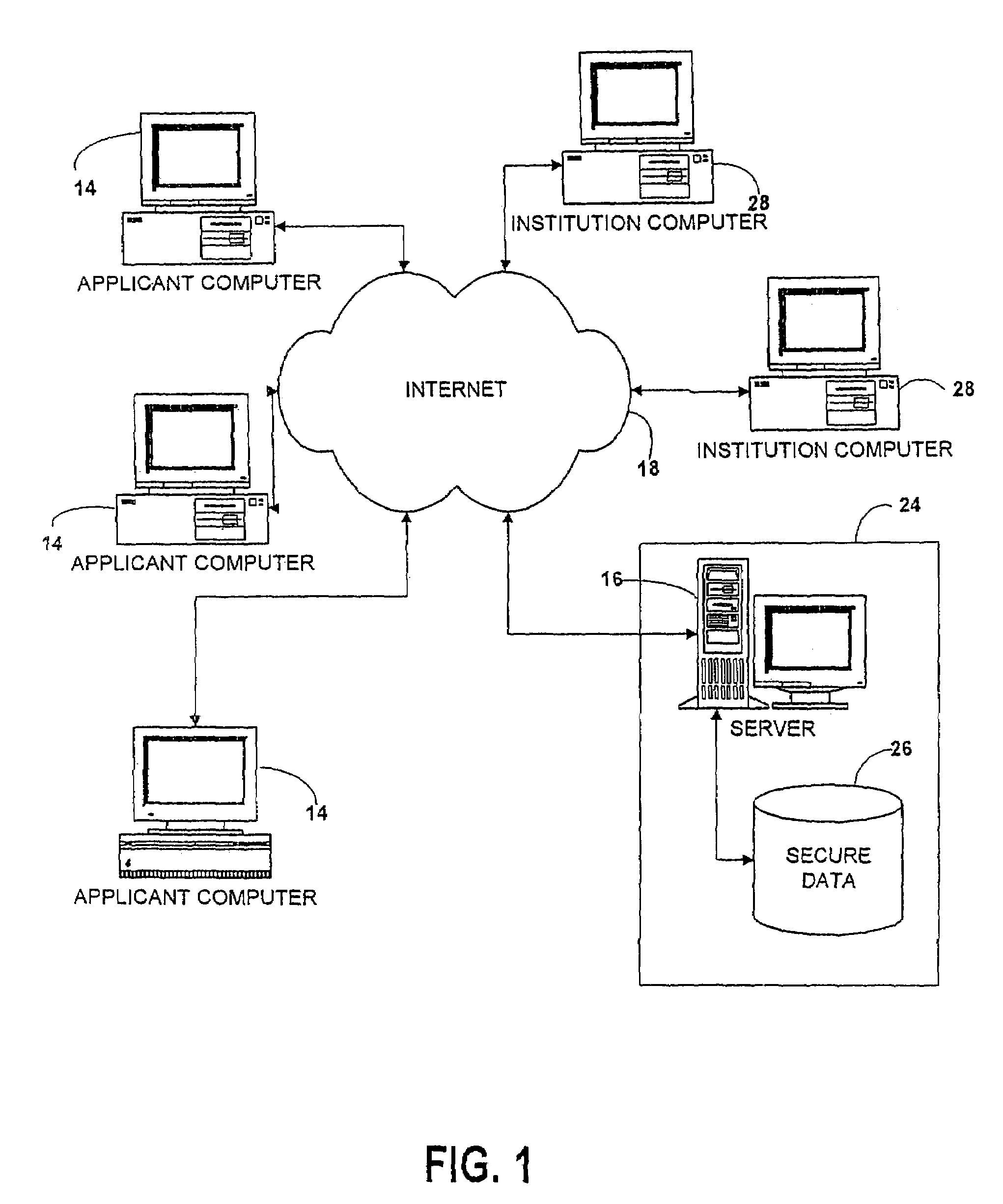
InactiveUS7376891B2Simple methodSpeed up the processData processing applicationsNatural language data processingData validationThird party
A forms engine allows data sharing between customizable on-line forms, such as college admissions applications. Before applying, an applicant opens an account with a third party application servicer. After the applicant completes an application for one institution, the data is saved in a data base and automatically populates fields in subsequent application forms. The form for each institution is created from a form description file. Each form is branded for its institution and forms for different institutions differ in appearance and content so that the presence of the third party servicer is transparent to the applicant.The system is extensible without programming, allowing new applicant attributes to be readily incorporated into the system and allowing the content and appearance of the application to be readily changed by changing the description file. The use of aliases for applicant attributes permits data to be readily shared between forms even though labeled and arranged differently on different forms. Information stored about each attribute allows the specification of data validation rules and data sharing and grouping rules, as well as dependency rules that permit application page content to depend on applicant's responses on a previous page.
Owner:COLLEGENET
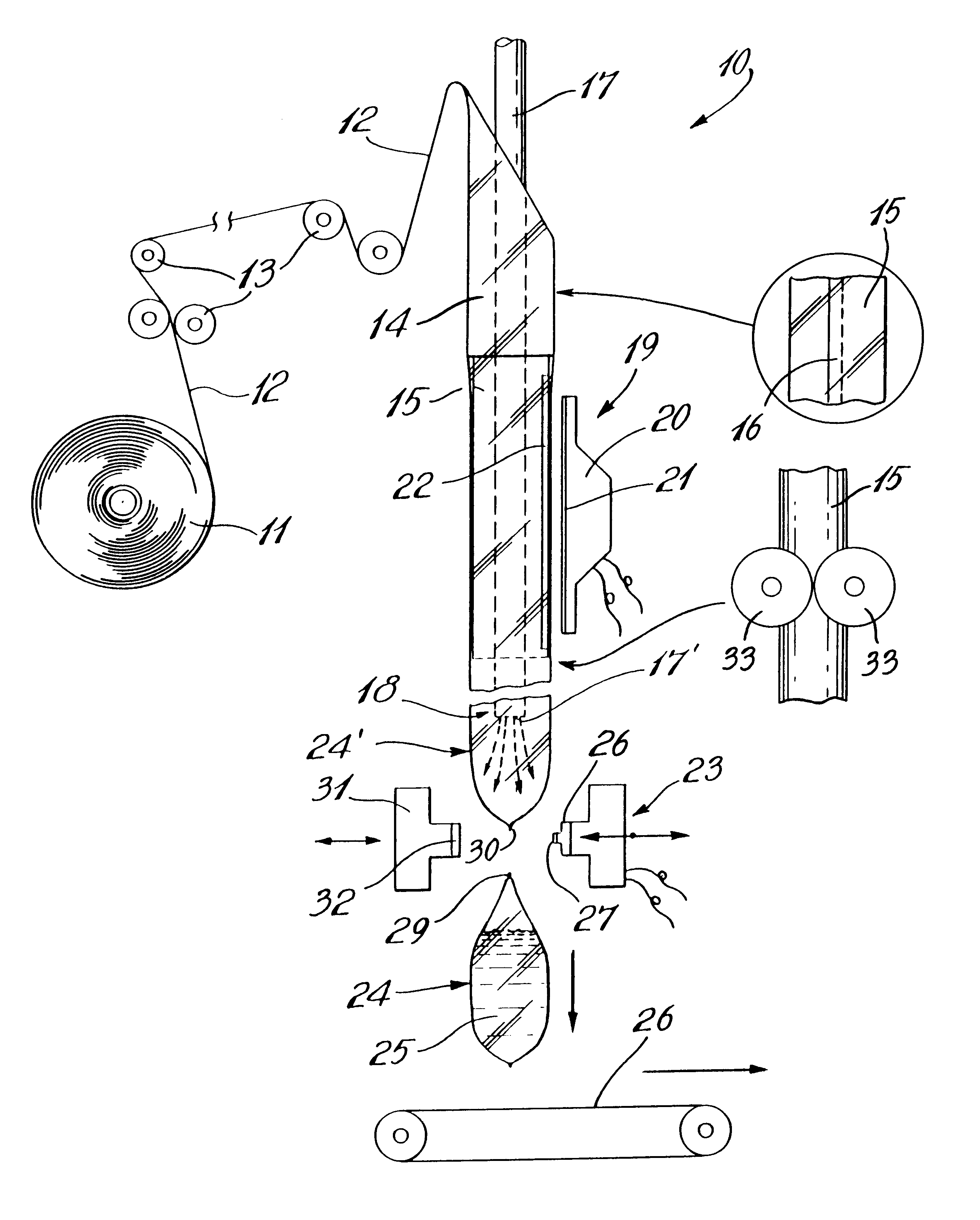
High-speed pouch forming, sealing and filling machine, method of operation, and multi-layer film therefore
InactiveUS6237308B1Improve methodImprove throughputSynthetic resin layered productsWrapper twisting/gatheringPuncture resistanceEngineering
The multi-layer film structure having an inner sealing layer which comprises metallocene resin, a core which includes polypropylene copolymer and an outer layer and wherein the multi-layer film structure has a thickness within a range between about 50 and 70 microns (2.0-2.75 mil). By utilizing this thin film with specific properties the sealers may be operated at lower temperatures thereby resulting in an energy saving and they produce seals having improved seal strength of 30% to 50% as compared with known prior mono-layer polyethylene film. The seal initiation temperature is reduced by 10° C. to 15° C. and the film exhibits an improved machine direction tensile strength of 25% to 40% and an improvement of 30% to 50% in puncture resistance as compared with a 76 microns (3 mil) mono-layer polyethylene film. This results in a reduction in the sealing cycle time and an increase in the throughput of the machine. This results in a liquid pouch having a substantial improvement in drop test performance, puncture resistance and seal strength. The machine accomplishes better seals with less energy, requires less downtime for roll changes and maintenance and increase throughput.
Owner:GLOPAK INC
Controlled densification of fusible powders in laser sintering
ActiveUS7569174B2Heat dissipationSimple methodAdditive manufacturing apparatusAuxillary shaping apparatusHigh energyTime segment
The invention relates to a method producing parts using laser sintering wherein a fusible powder is exposed to a plurality of laser scans at controlled energy levels and for time periods to melt and densify the powder and in the substantial absence of particle bonding outside the fusion boundary. Strength is improved up to 100% compared to previous methods. An example includes a relatively high energy initial scan to melt the powder followed by lower energy scans controlled to densify the melt and separated in time to dissipate heat to the surrounding part cake. The rate and extent to which the powder particles are fused together can be controlled so that each successive scan can be used to fuse the particles together in discreet incremental steps. As a result, the final dimensions of the part and its density and mechanical properties can be improved compared to conventional methods and part growth avoided.
Owner:3D SYST INC
Two step lateral flow assay methods and devices
ActiveUS20070020768A1Easy to optimizeEasy to detectEnzymologyDisease diagnosisAntigenLateral flow immunoassay
Lateral flow assay devices and methods for detecting a first member of a specific binding pair in a sample which comprises a plurality of nonspecific binding pair members are adapted for two step determinations. In one embodiment, a two step lateral flow assay method for identifying IgE antibodies in a sample comprises applying a sample to a sample port of a device, wherein the device is adapted to deliver the sample to a lateral flow matrix having a plurality of IgE antigen species immobilized at respective positions at a first location The two step method further comprises allowing the sample to travel along the lateral flow matrix through the immobilized plurality of IgE antigen species to a second location downstream of the first location, applying liquid buffer to the lateral flow matrix to mobilize labeled reagent which is adapted to bind anti-IgE antibody and is dried on the lateral flow matrix at a location upstream of the delivery of the filtered sample to the lateral flow matrix, and allowing labeled reagent mobilized by the liquid buffer to travel along the lateral flow matrix through the immobilized plurality of IgE antigen species to a location downstream of the first location. Further embodiments comprise additional lateral flow immunoassay devices and methods for identifying IgE antibodies in a sample.
Owner:PHADIA AB
Advanced quad flat no lead chip package having a protective layer to enhance surface mounting and manufacturing methods thereof
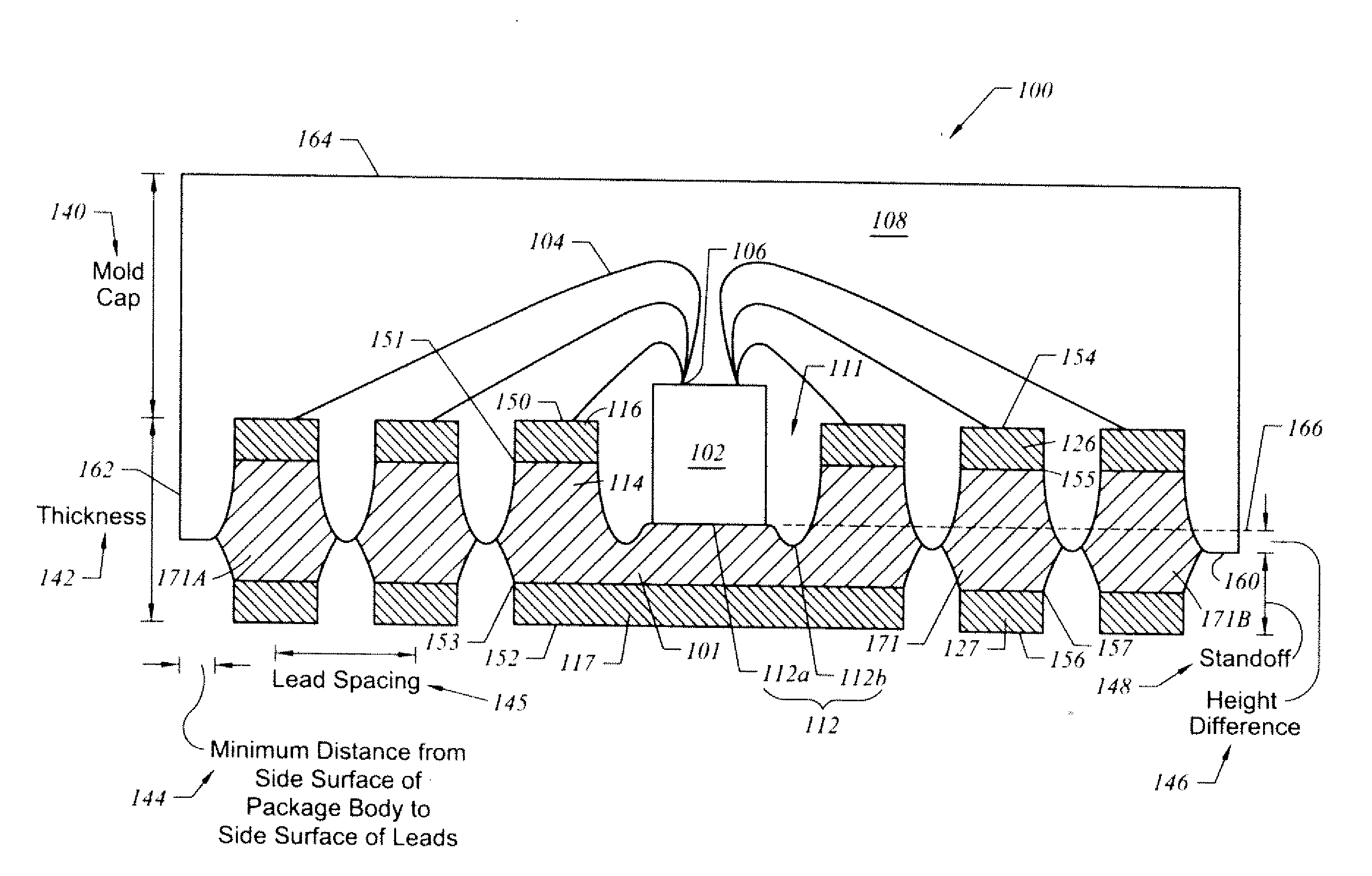
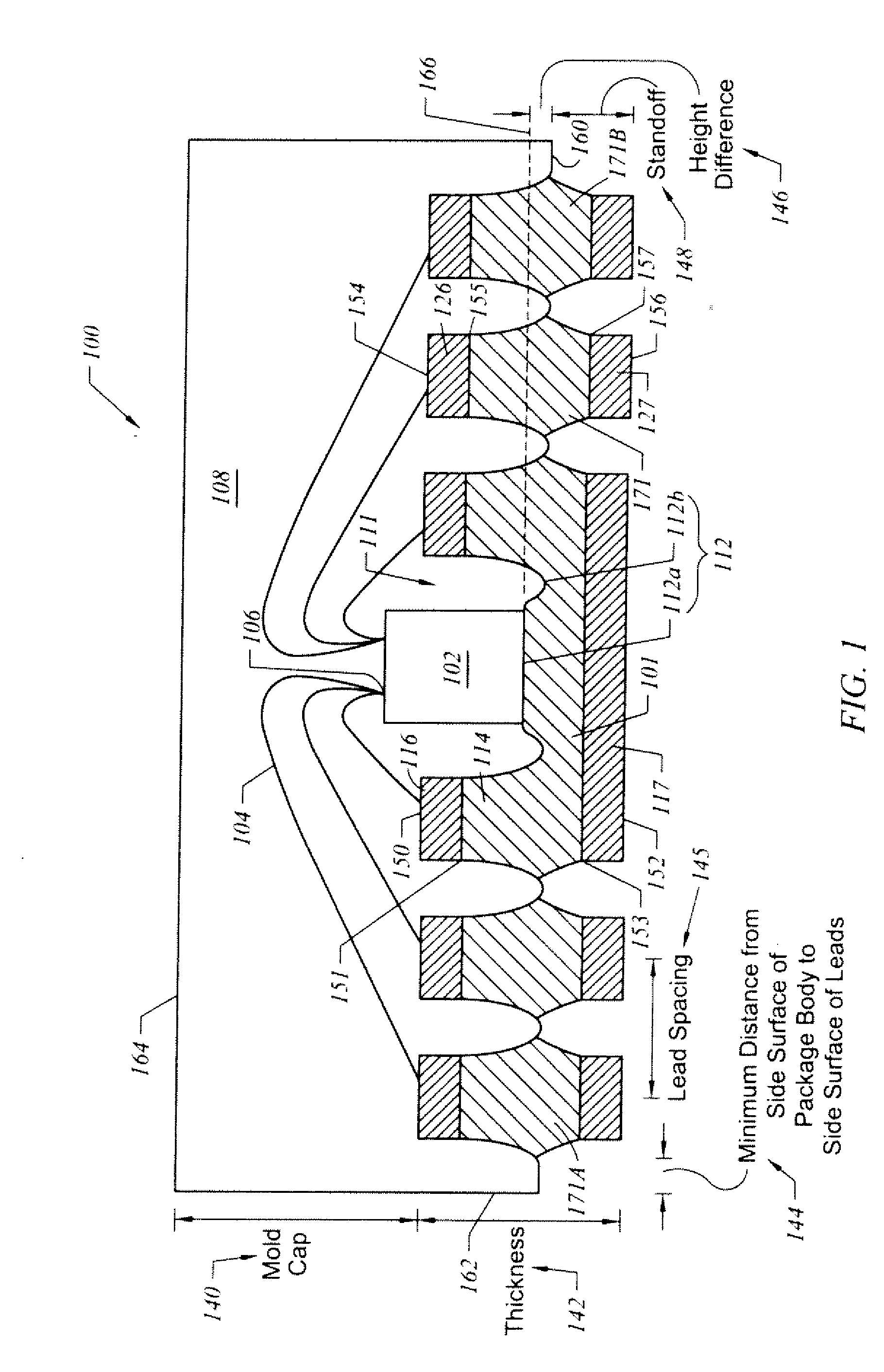
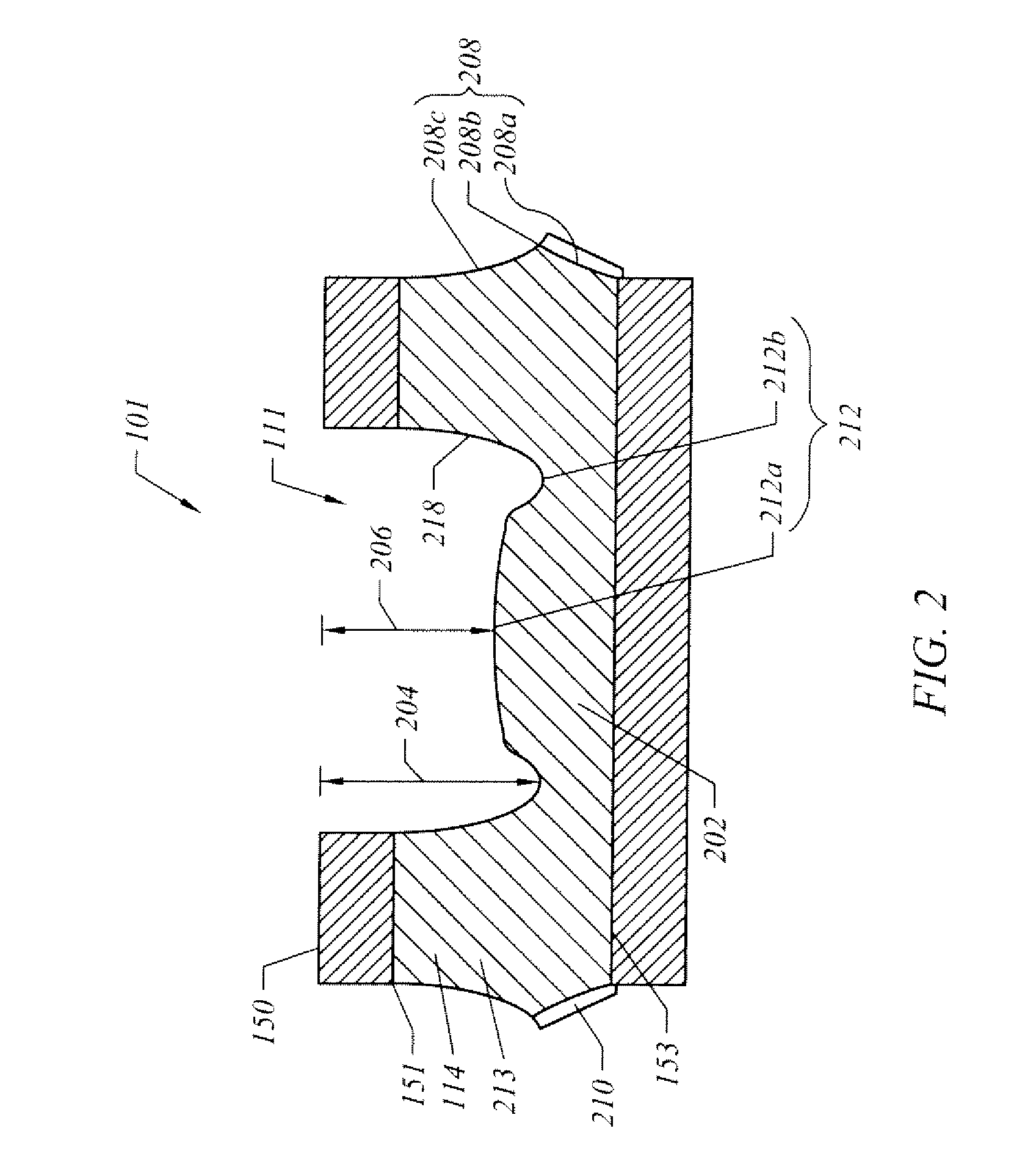
ActiveUS20090230526A1Improve methodFine surfaceSemiconductor/solid-state device detailsSolid-state devicesSurface mountingSemiconductor package
A semiconductor package and related methods are described. In one embodiment, the package includes a die pad, multiple leads, a chip, a package body, and a protective layer. The die pad includes an upper sloped portion, a lower sloped portion, and a peripheral edge region defining a cavity with a cavity bottom. Each lead includes an upper sloped portion and a lower sloped portion. The chip is disposed on the cavity bottom and is coupled to the leads. The package body is formed over the chip and the leads, substantially fills the cavity, and substantially covers the upper sloped portions of the die pad and the leads. The lower sloped portions of the die pad and the leads at least partially extend outwardly from a lower surface of the package body. The protective layer substantially covers the lower sloped portion and the lower surface of at least one lead.
Owner:ADVANCED SEMICON ENG INC
Integrated rail system and method for making and using same
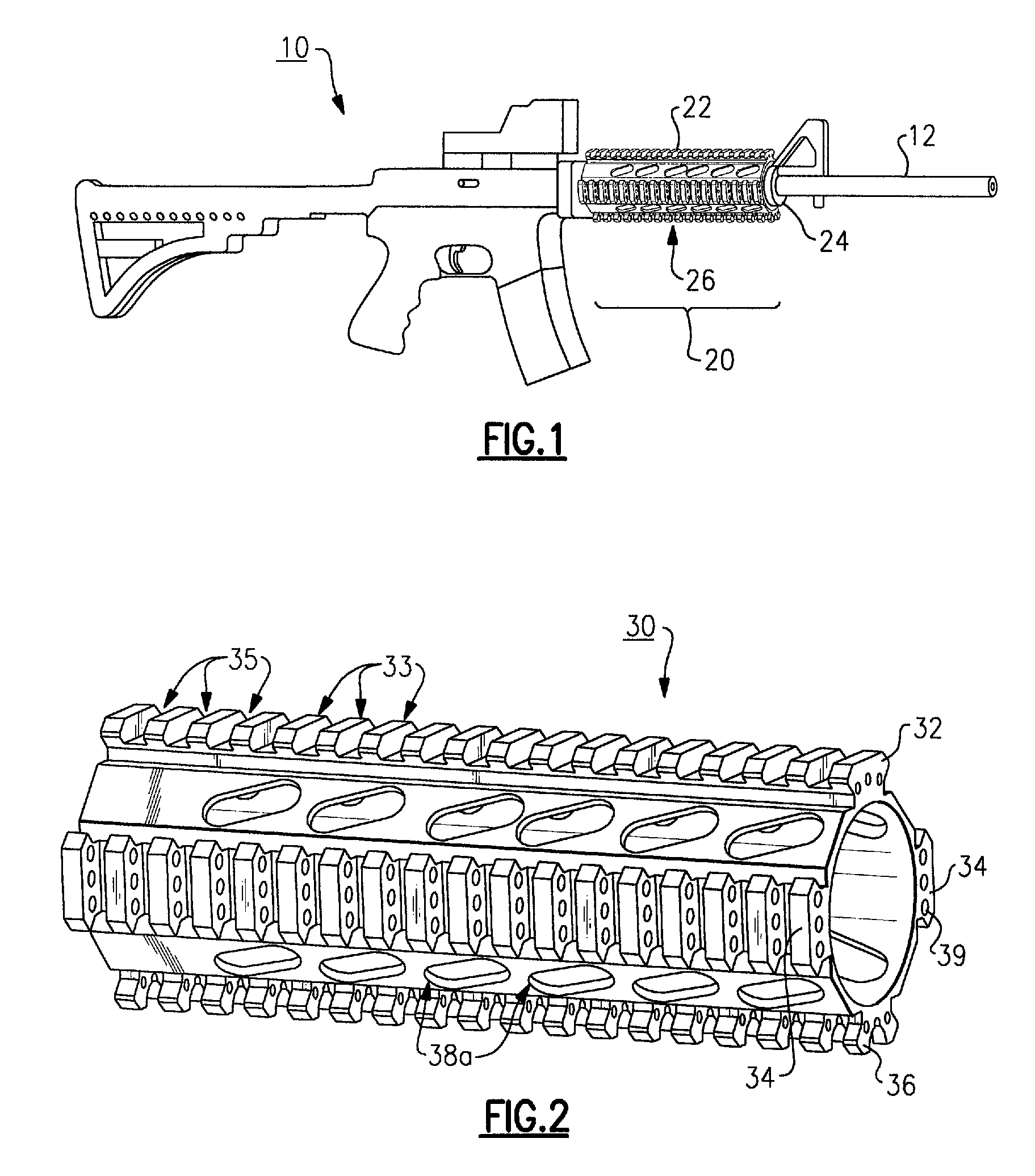
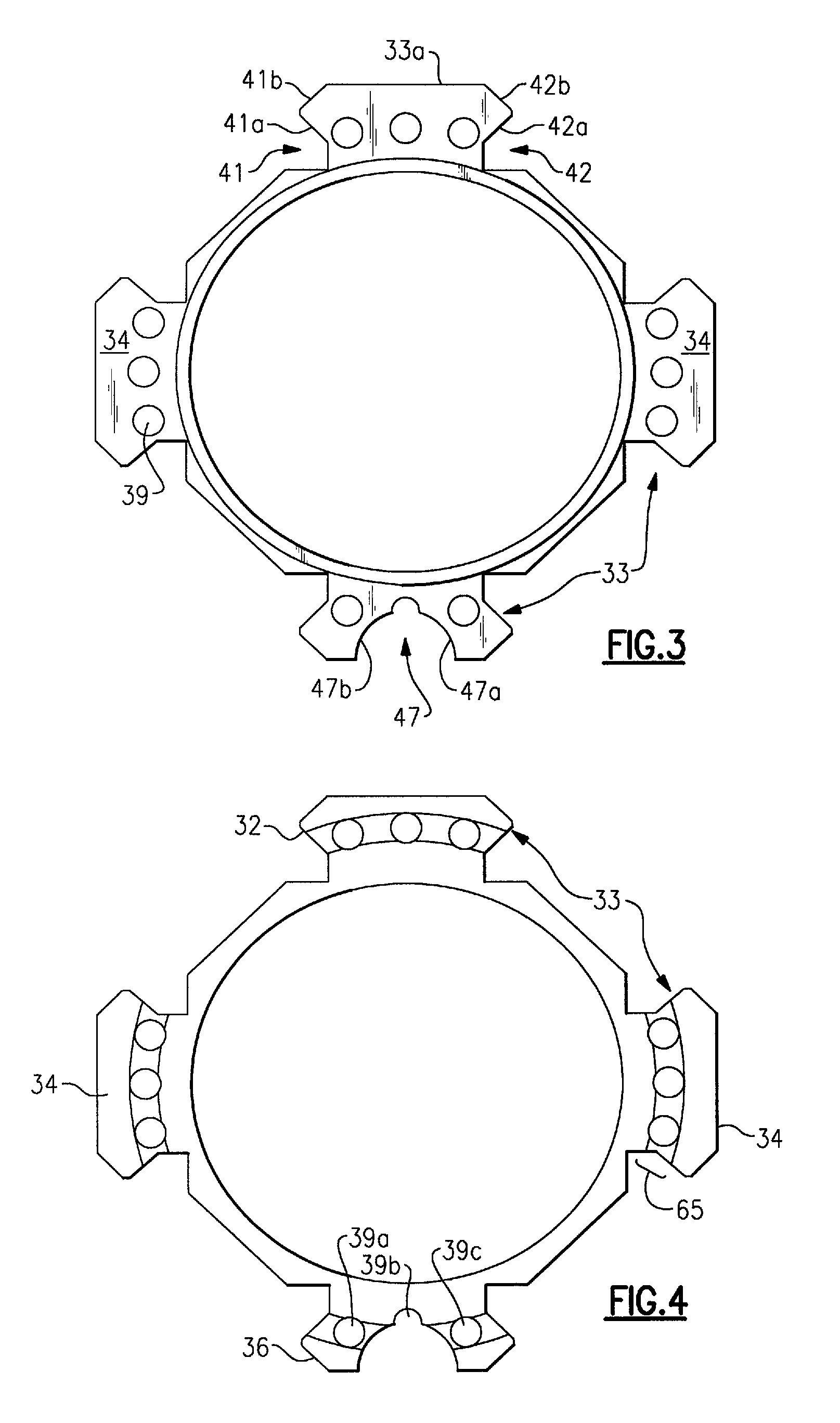
InactiveUS8028460B2Improve methodImprove protectionLine/current collector detailsCartridge extractorsEngineeringSystem construction
Embodiments of the application can include an integrated rail system construction for a firearm with transverse ribs or tabs (e.g., picatinny rail) to include an undercut or slot at a front and / or rear face to cooperate with mounting structure for a detachable accessory. Embodiments of a rail structure can include a channel to pass wires used to power accessories mounted to the rail. Embodiments of the application can include methods for manufacturing an integral rail system.
Owner:THE OTIS PATENT TRUST
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com