Method and system for controlling access authority of information safety equipment
A technology of information security and access rights, applied in computer security devices, instruments, digital data authentication, etc., to achieve competitive and widely used effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
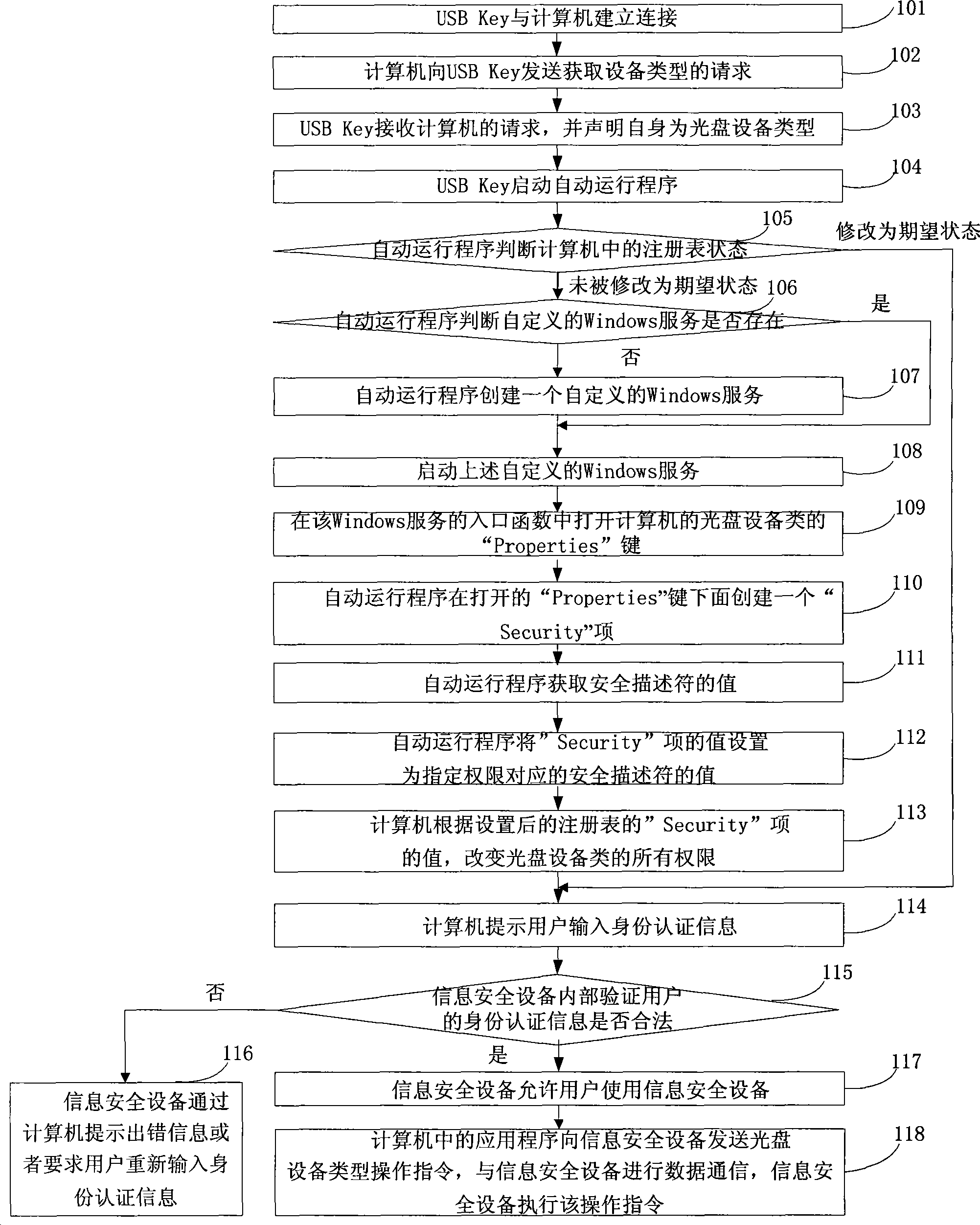
[0088] see figure 1 , the embodiment of the present invention provides a method for controlling the access authority of information security equipment. The method provided by the embodiment of the present invention is applicable to the operating system platforms of Windows 2000 and above. To facilitate the description of the embodiment of the present invention, the information security equipment described Specifically, take the USB Key as an example. For details, see the following:
[0089] Step 101, USB Key establishes connection with computer;
[0090] Wherein, the connection relationship between the USB Key and the computer is established by inserting the USB Key into the computer through the USB interface.
[0091] Step 102, the computer sends a request to obtain the device type to the USB Key;
[0092] Step 103, the USB Key receives the request from the computer, and declares itself as an optical disc device type;
[0093] Wherein, in step 103 of this embodiment, the i...
Embodiment 2
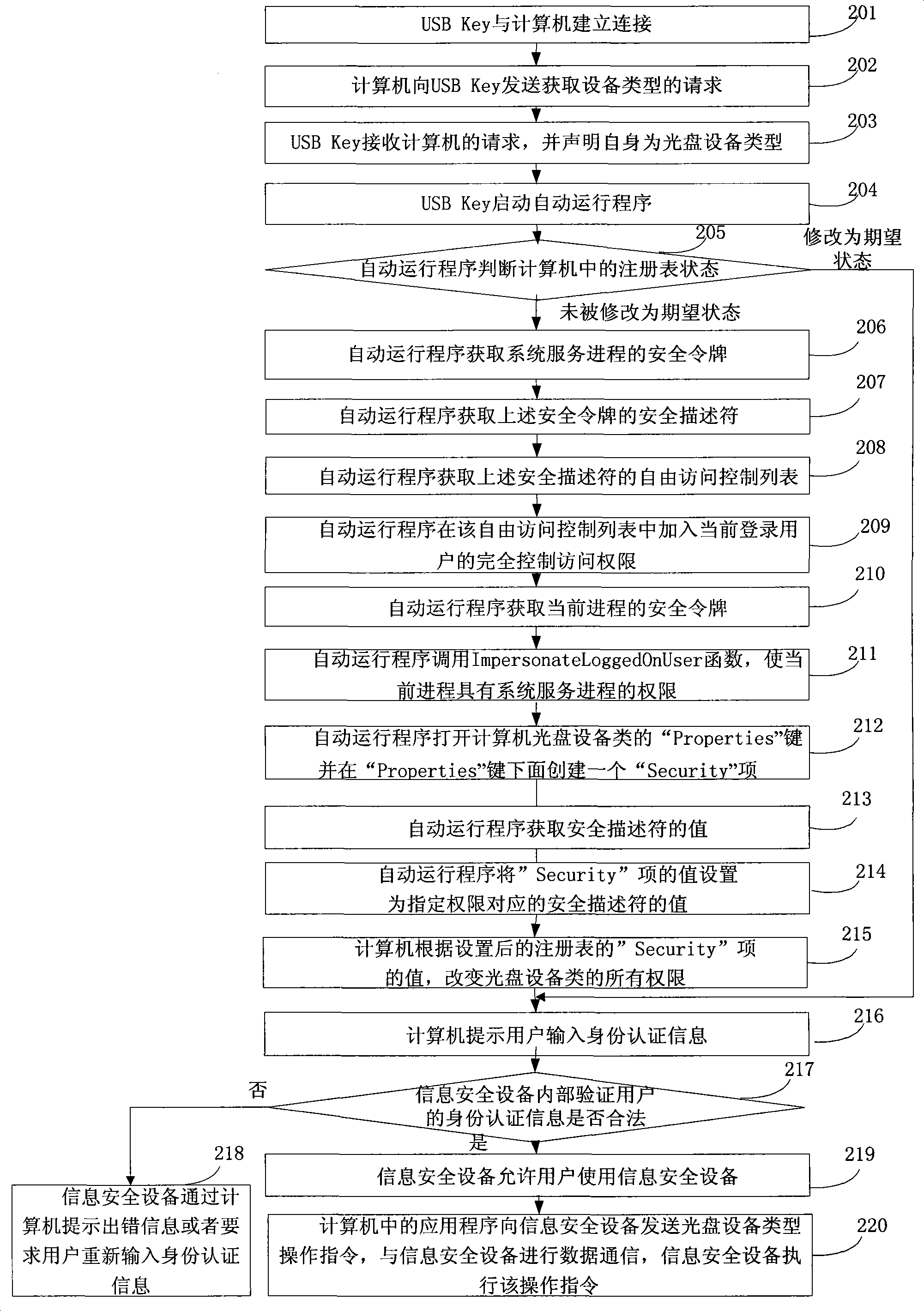
[0142] see figure 2 , the embodiment of the present invention provides a method for controlling the access authority of an information security device. When the access authority is elevated, the embodiment of the present invention implements it by means of a security token. The method provided by the embodiment of the present invention is applicable to Windows 2000 / XP / 2003 operating system, still using the information security device as an example of a USB Key, the specific content is as follows:
[0143] Step 201, USB Key establishes connection with computer;
[0144] Step 202, the computer sends a request to obtain the device type to the USB Key;
[0145] Step 203, the USB Key receives the request from the computer, and declares itself as an optical disc device type;
[0146] In step 203 of this embodiment, the information security device USB Key declares itself as an optical disc device type by reporting the device descriptor to the computer as an optical disc device de...
Embodiment 3
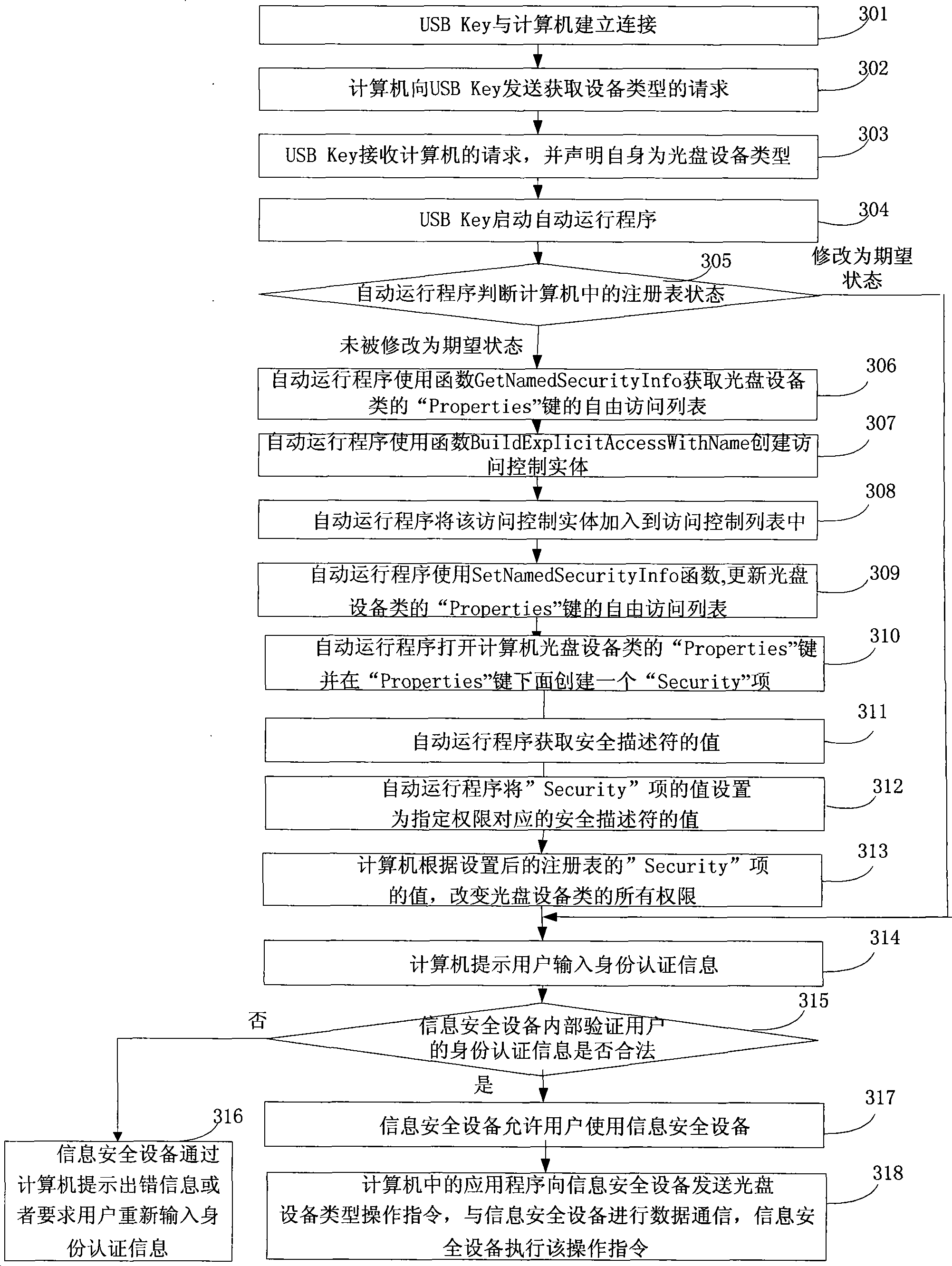
[0193] see image 3 , the embodiment of the present invention provides a method for controlling the access authority of an information security device. When the access authority is increased in the embodiment of the present invention, it is realized by using a function to obtain the free access list of the "Properties" key of the optical disc device class. The method provided by the embodiment of the invention is applicable to the Windows 2000 / XP / 2003 operating system, and the information security device is still specifically described as a USB Key as an example. The specific content is as follows:
[0194] Step 301, USB Key establishes connection with computer;
[0195] Step 302, the computer sends a request to obtain the device type to the USB Key;
[0196] Step 303, the USB Key receives the request from the computer and declares itself as an optical disc device type;
[0197] In step 303 of this embodiment, the information security device declares itself as an optical dis...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com