Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
660results about How to "Flexible management" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
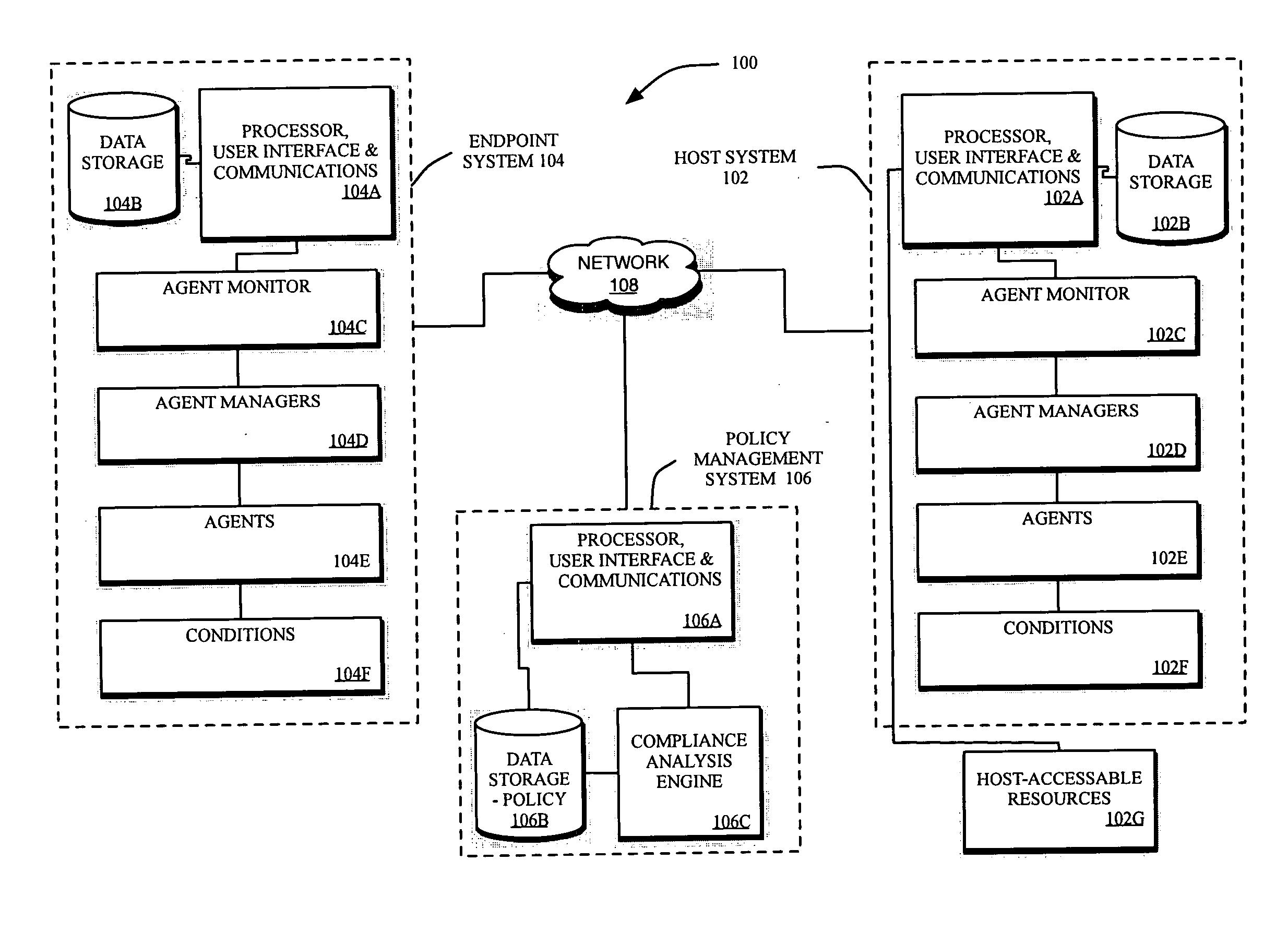
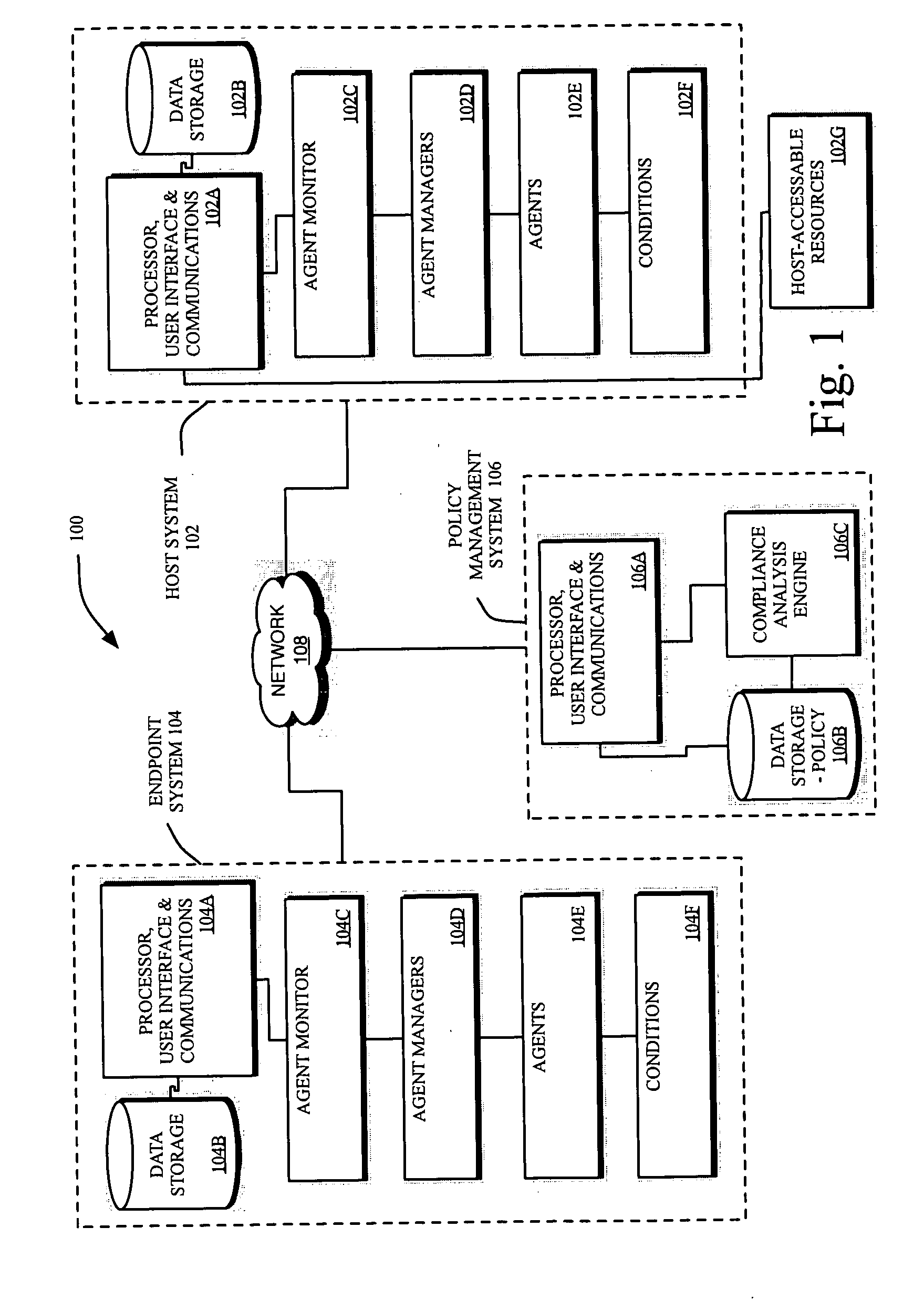
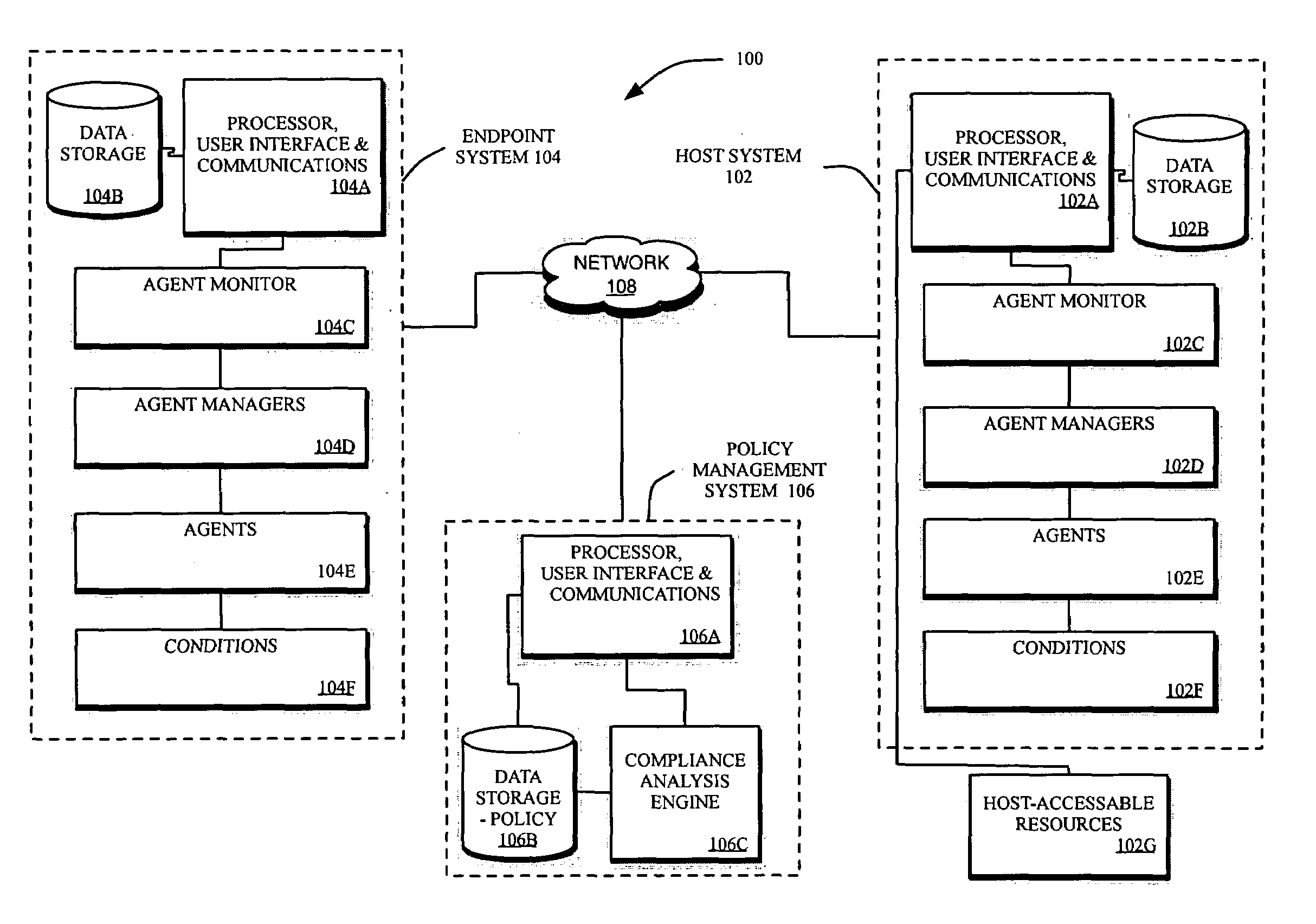
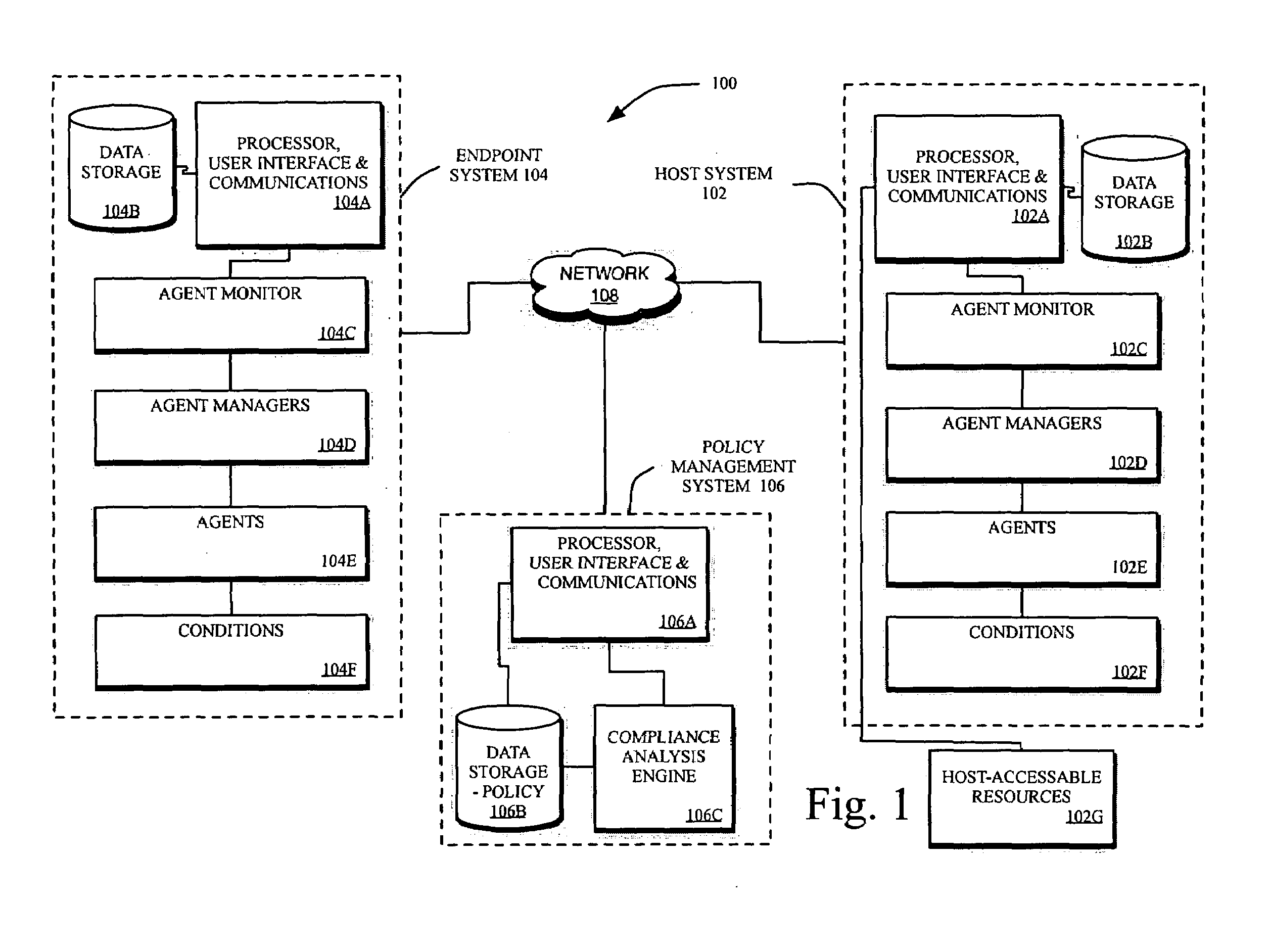
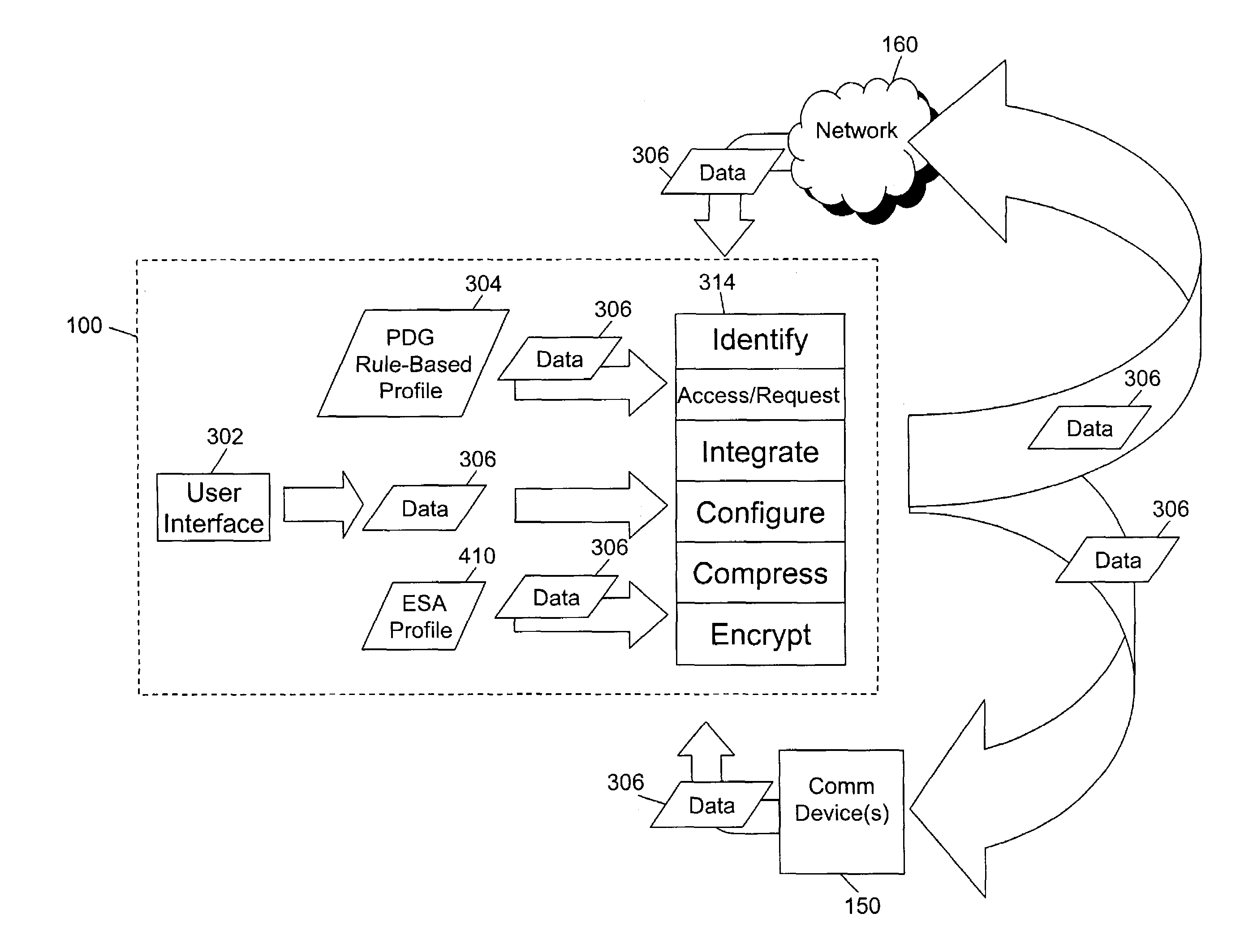
Method and systems for controlling access to computing resources based on known security vulnerabilities
InactiveUS20070143851A1Flexible managementRandom number generatorsUser identity/authority verificationSecurity bugSoftware
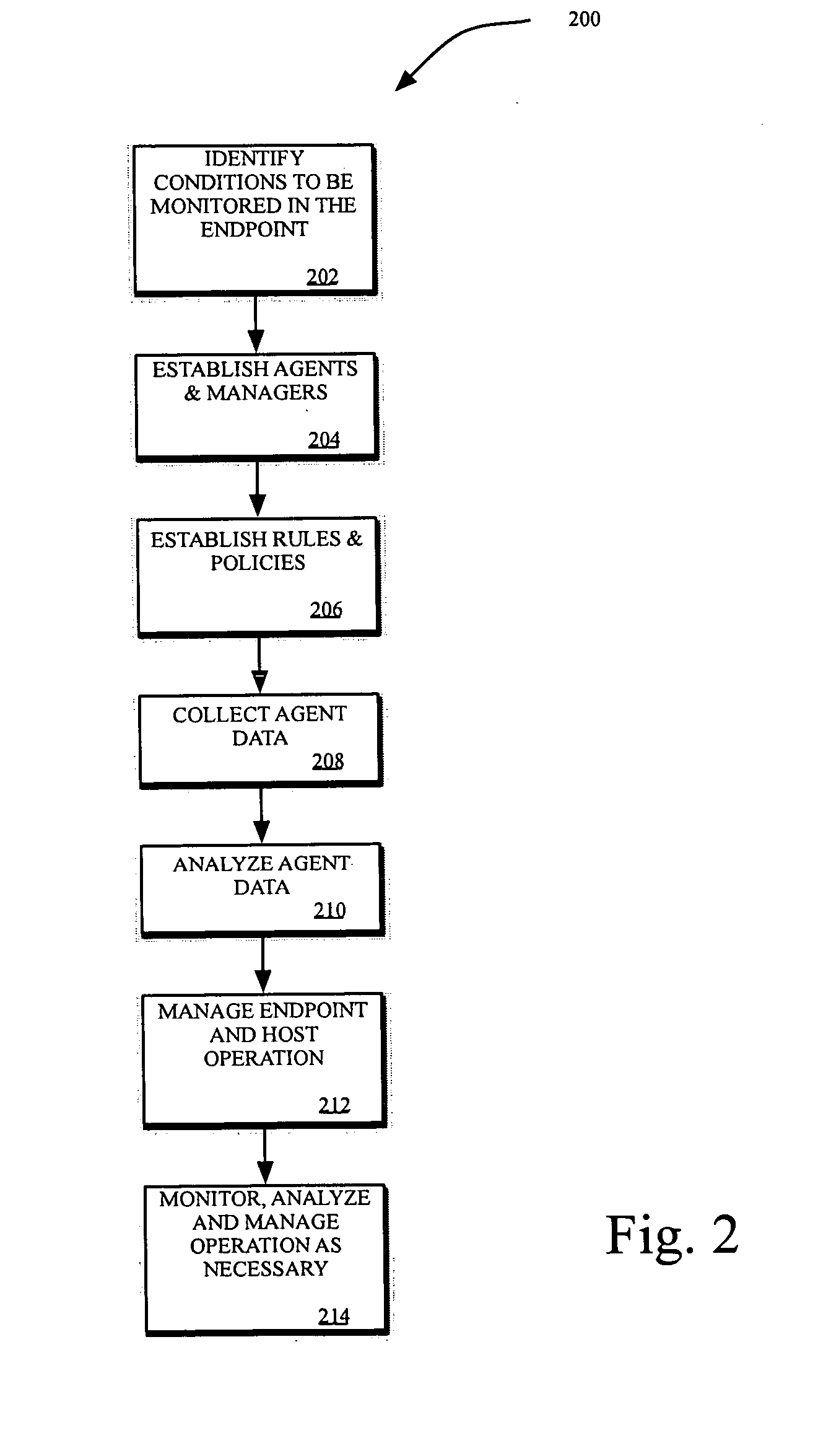
Methods and systems are provided for fine tuning access control by remote, endpoint systems to host systems. Multiple conditions / states of one or both of the endpoint and host systems are monitored, collected and fed to an analysis engine. Using one or more of many different flexible, adaptable models and algorithms, an analysis engine analyzes the status of the conditions and makes decisions in accordance with pre-established policies and rules regarding the security of the endpoint and host system. Based upon the conditions, the policies, and the analytical results, actions are initiated regarding security and access matters. In one described embodiment of the invention, the monitored conditions include software vulnerabilities.
Owner:DAEDALUS BLUE LLC
Methods and systems for intelligently controlling access to computing resources
InactiveUS20070143827A1Flexible managementDigital data processing detailsUser identity/authority verificationComputational resourceSuitability model
Methods and systems are provided for fine tuning access control by remote, endpoint systems to host systems. Multiple conditions / states of one or both of the endpoint and host systems are monitored, collected and fed to an analysis engine. Using one or more of many different flexible, adaptable models and algorithms, an analysis engine analyzes the status of the conditions and makes decisions in accordance with pre-established policies and rules regarding the security of the endpoint and host system. Based upon the conditions, the policies, and the analytical results, actions are initiated regarding security and access matters. In one described embodiment of the invention, the monitored conditions include software vulnerabilities.
Owner:DAEDALUS BLUE LLC
System and method for multiple virtual teams
ActiveUS8060875B1Flexible managementMultiprogramming arrangementsMultiple digital computer combinationsNetwork conditionsVirtual team
A system and method for assigning virtual machines to network interfaces. A first virtual machine is assigned to a network interface according to a first rule and a second virtual machine is assigned to a network interface according to a second rule. The assignment rules are dependent on network conditions as determined through at least one of the network interfaces. The first rule and the second rule may specify assignments differently, such that the same network conditions may result in different assignments for the first and second virtual machines.
Owner:VMWARE INC
Information processing apparatus, information processing method, and computer program
InactiveUS20060184532A1Flexible managementStill image data retrievalStatic indicating devicesInformation processingComputer graphics (images)
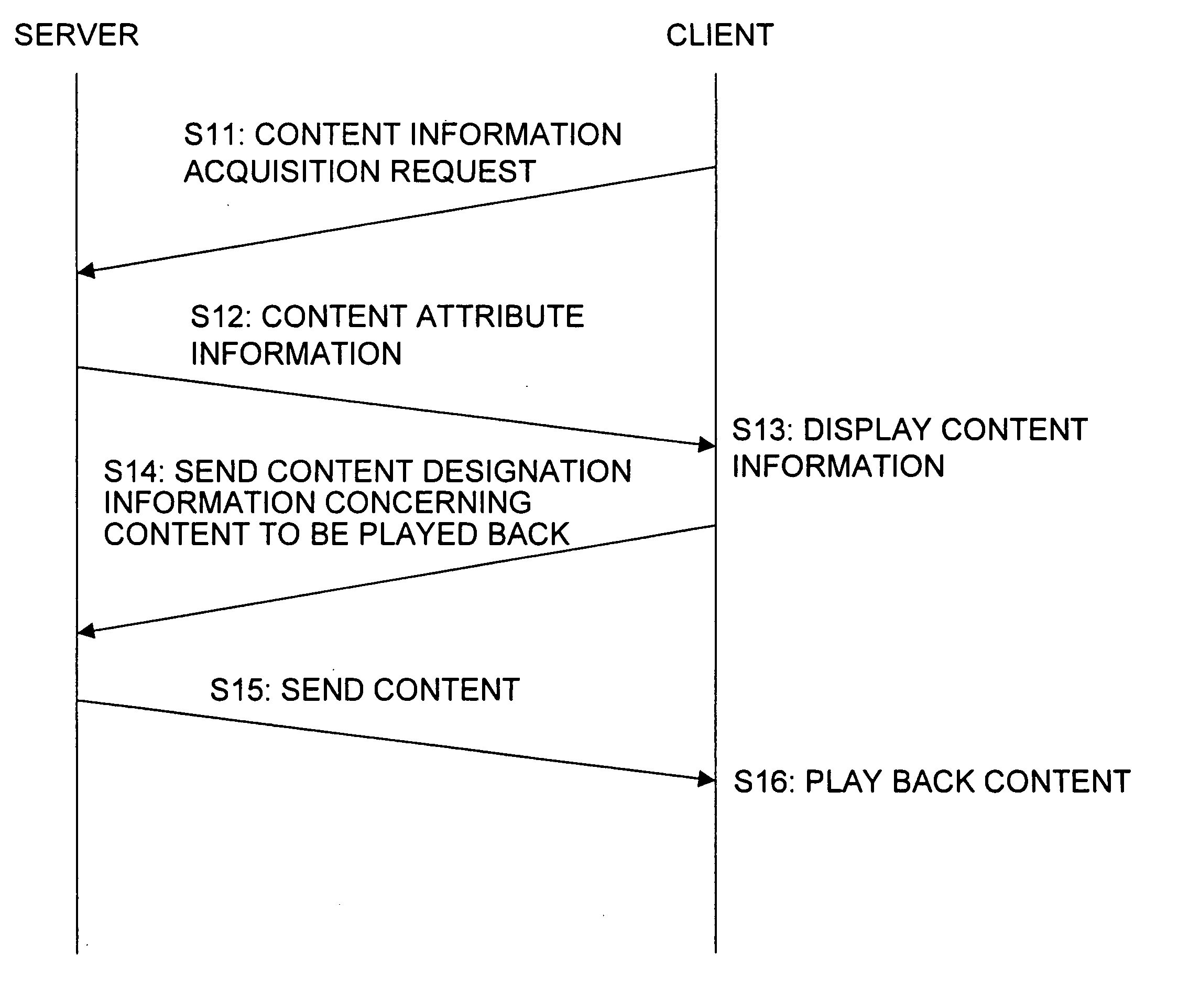
To provide an apparatus and method for efficiently displaying image content, which is sent and received between a server and a client, in a correct direction. An image content providing server stores, as property information, original angle information indicating correct directions of image content as metadata of the image content. The server generates content information including the original angle information and sends the generated content information to a client. This allows the client to understand the correct direction of the image content received from the server, and to obtain and display image data in the correct direction by performing rotation processing in the client device based on the obtained information or to request the server to perform the rotation processing.
Owner:SONY CORP
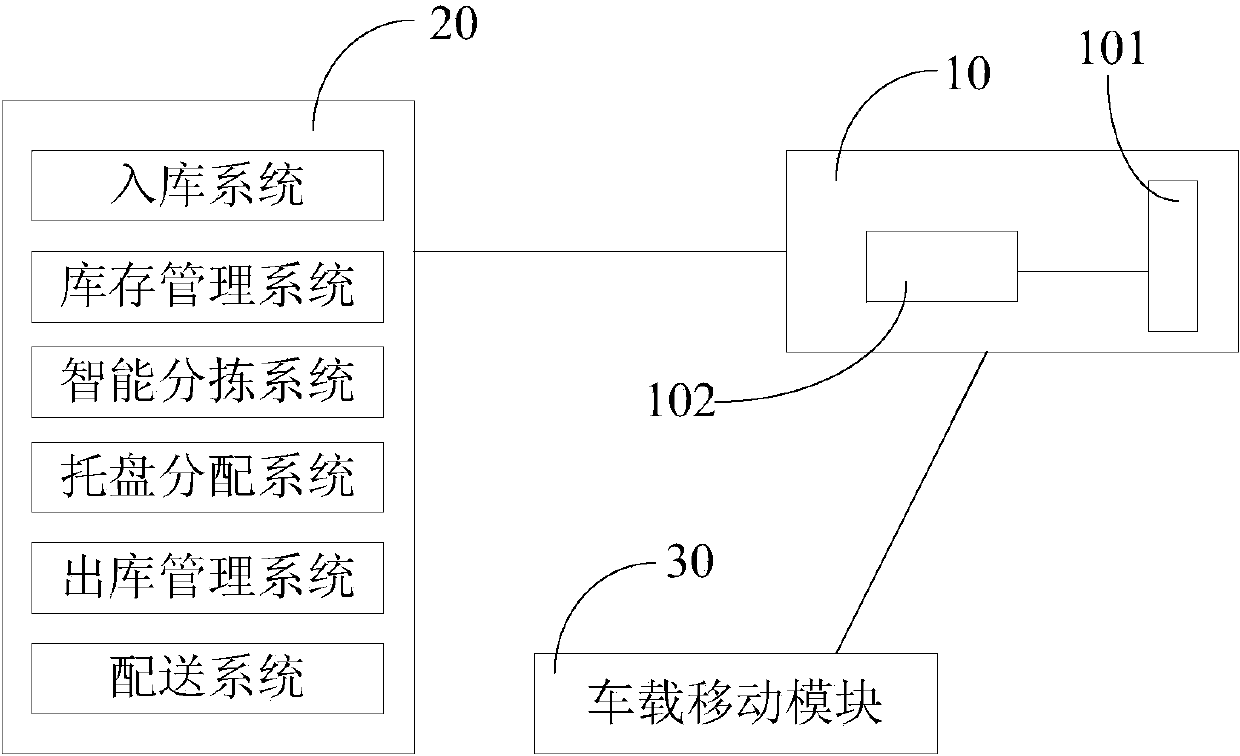
Radiofrequency identification (RFID) based intelligent logistics managing system
InactiveCN103593751AEfficient informatizationFlexible managementLogisticsEmbedded systemStorage garage
The invention relates to an RFID based intelligent logistics managing system, which belongs to the field of logistics management, and used for managing logistics information of cargoes with RFID tags. The logistics managing system comprises a logistics control system, a storage system arranged in a warehouse and a vehicle-mounted mobile module, wherein the logistics control system is connected with the storage system and the vehicle-mounted mobile module via a communication network to realize commutation between the logistics control system and the storage system or the vehicle-mounted mobile module, each of the storage system and the vehicle-mounted storage system is equipped with an RFID reader, the RFID readers read information of the RFID tags, and the RFID information is transmitted to the logistics control system. According to the RFID based intelligent logistics managing system, logistics information can be managed in a highly-efficient, automatic, informationized, networked, intelligent and flexible manner.
Owner:CHINA CONSTR EIGHT ENG DIV CORP LTD
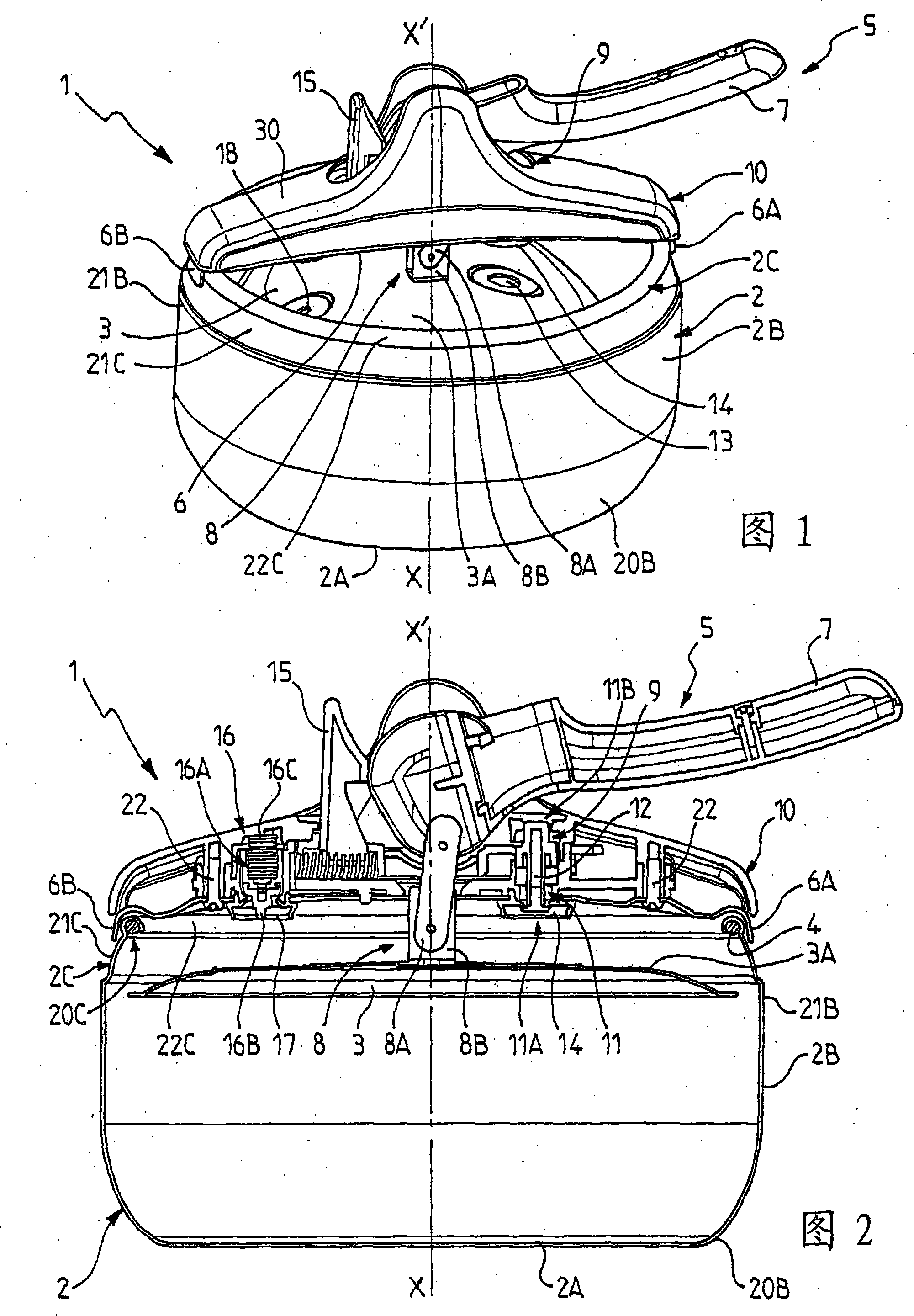
Pressure-cooking device with improved construction and corresponding manufacturing method
ActiveCN101209179ASimple structureFast and cheap to constructPressure-cookersEngineeringMechanical engineering
Owner:SEB SA
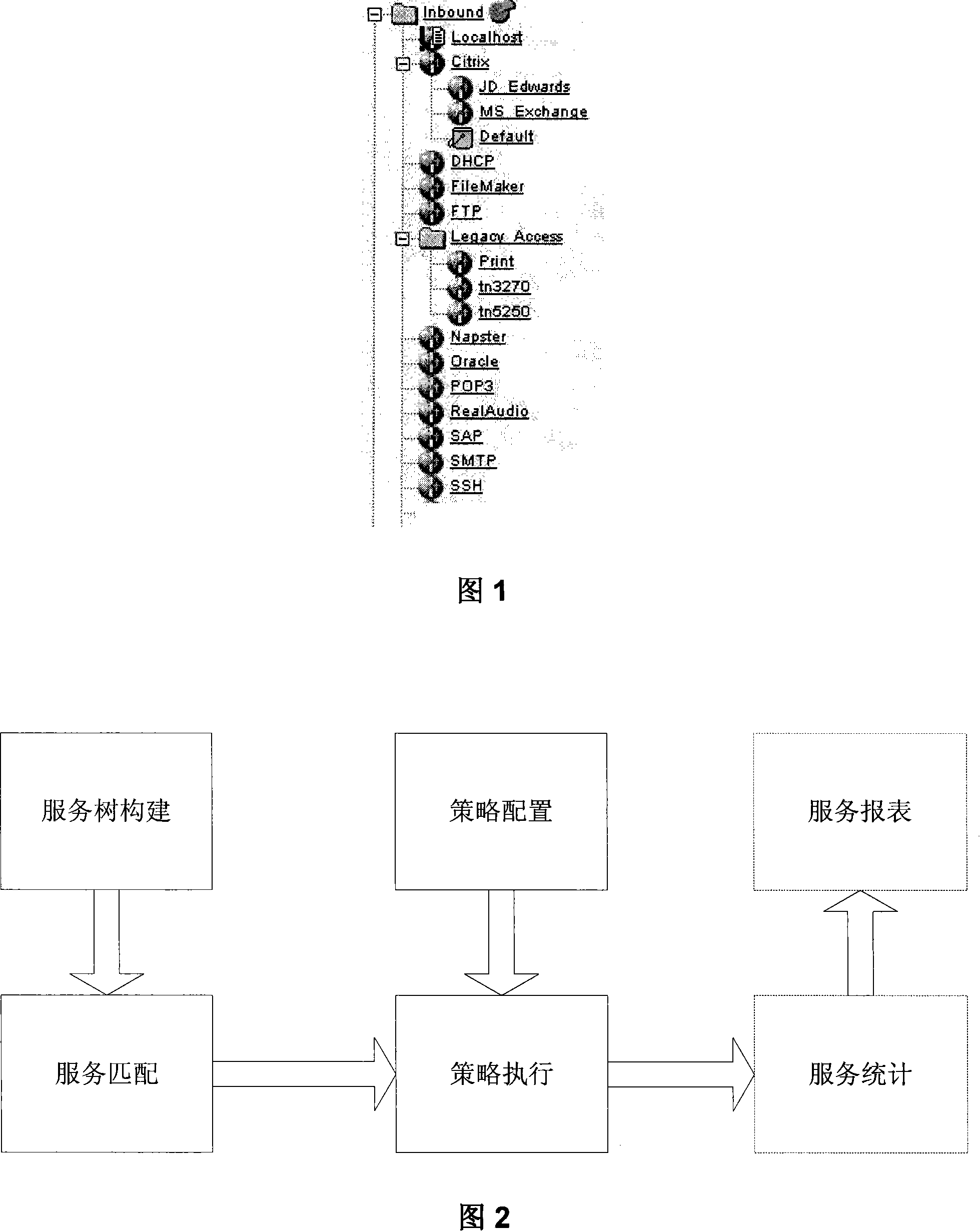
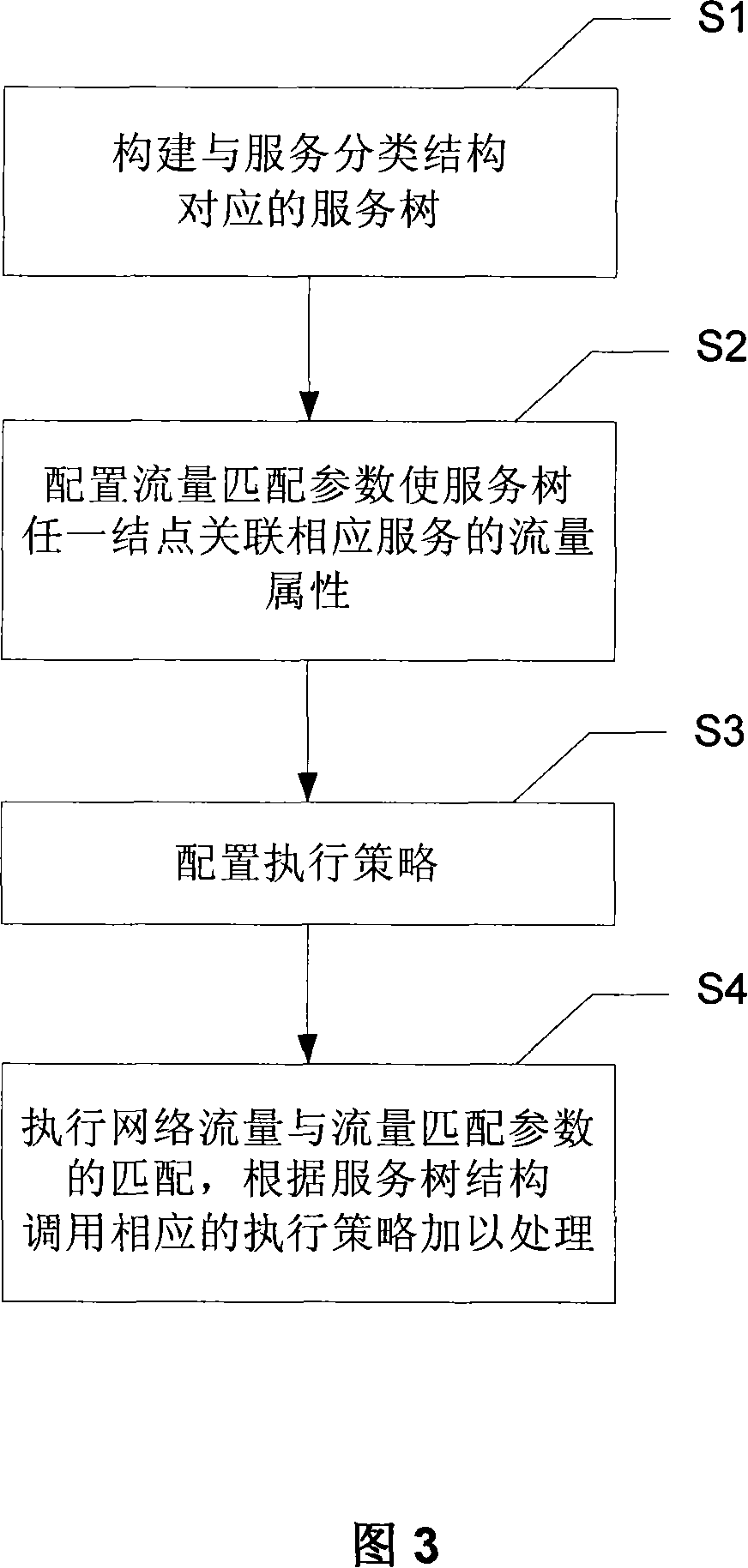
Network flux classification processing method and apparatus
ActiveCN101119321AReduce configuration workloadHigh portabilityData switching networksTraffic volumeWorkload
The present invention discloses a network flow assorting and processing method which comprises the steps as follows: building a service tree that is corresponding with the service assorted structure; allocating the parameters that matches with flow making either node of the service tree relating to the flow attribution of corresponding service; allocating the executing strategy, wherein any executing strategy comprises a plurality of strategy rules and each strategy rule defines a processing action of a service node; as for the received net flow, executing the matching that matches with the flow matching parameters and invoking corresponding executing strategy to process according to matching result and the structure of the service tree. The present invention also discloses a net flow assorted processing device. The present invention can reduce the allocating workload of managing the net flow and increase the transplant performance of the net flow management. Besides, the net flow management can be more efficiency and flexible.
Owner:NEW H3C TECH CO LTD
Methods, Systems, and Products for Virtual Personalized Networks
ActiveUS20080232295A1Easy accessEasy to shareInformation formatDigital computer detailsPersonalizationComputer science
Owner:IOT INNOVATIONS LLC
Network privilege management method, device and system
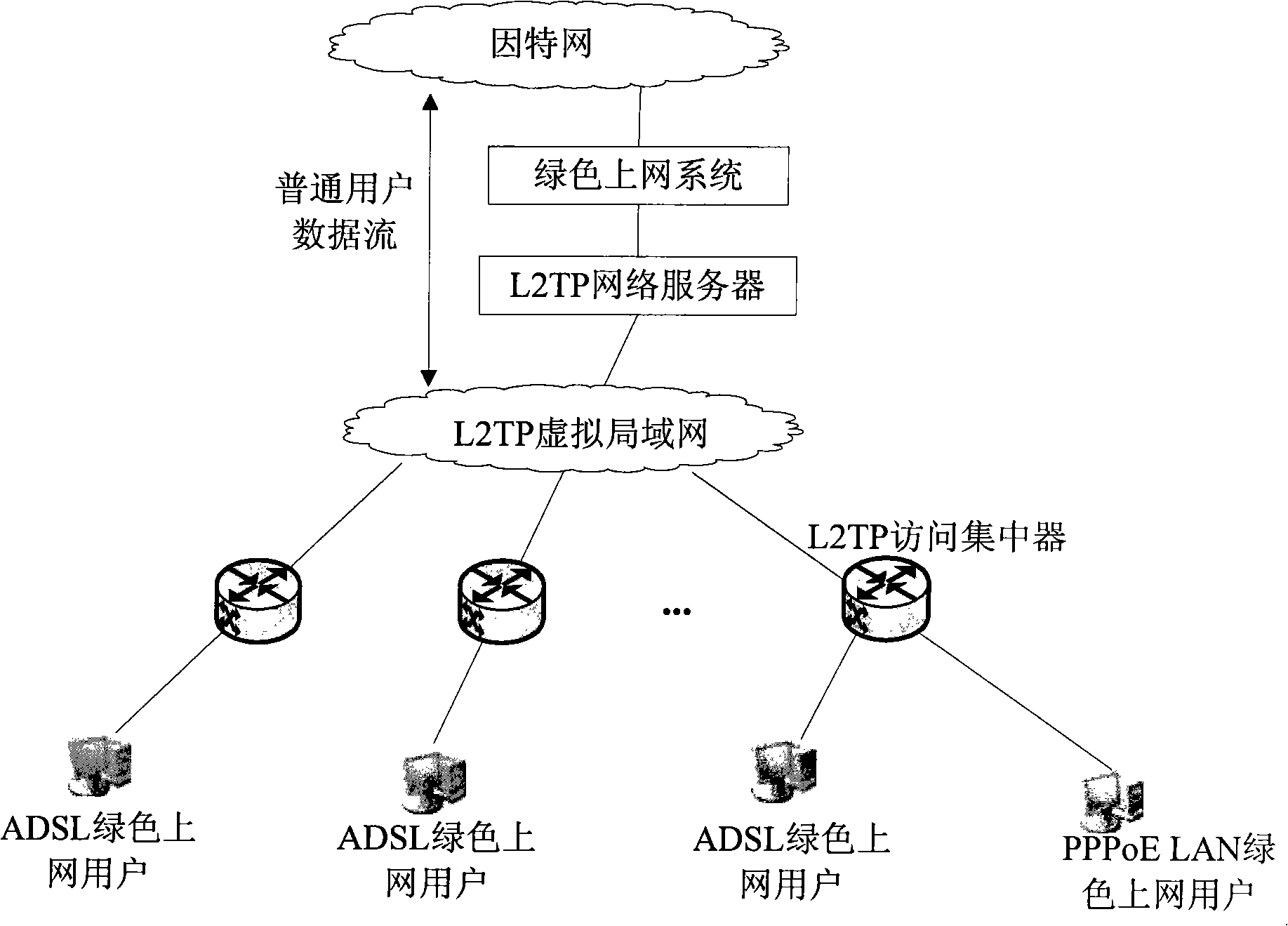
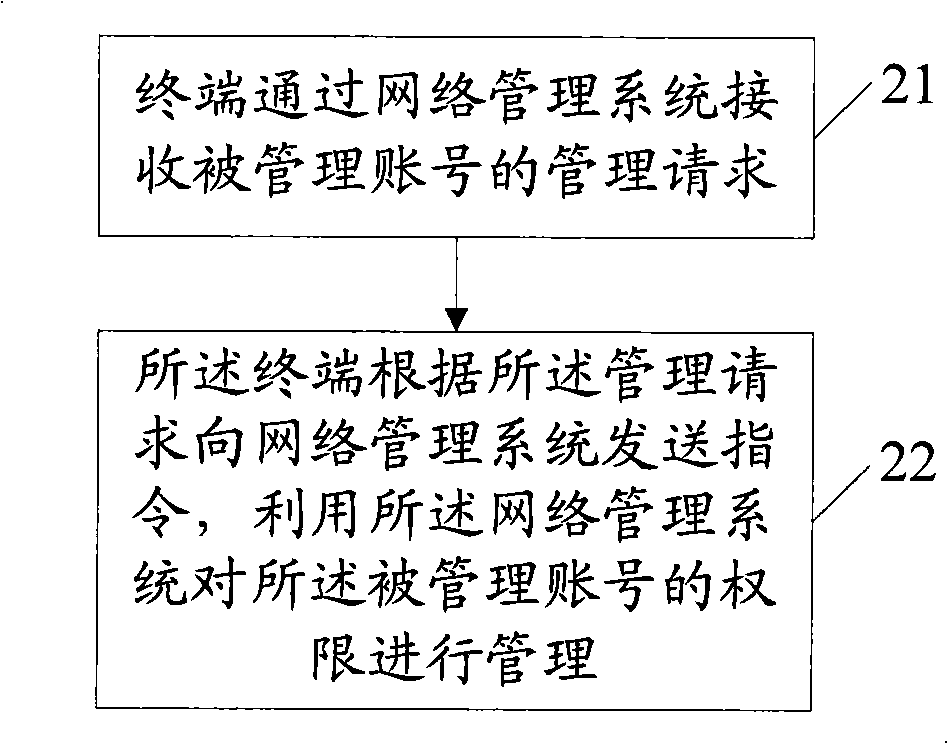
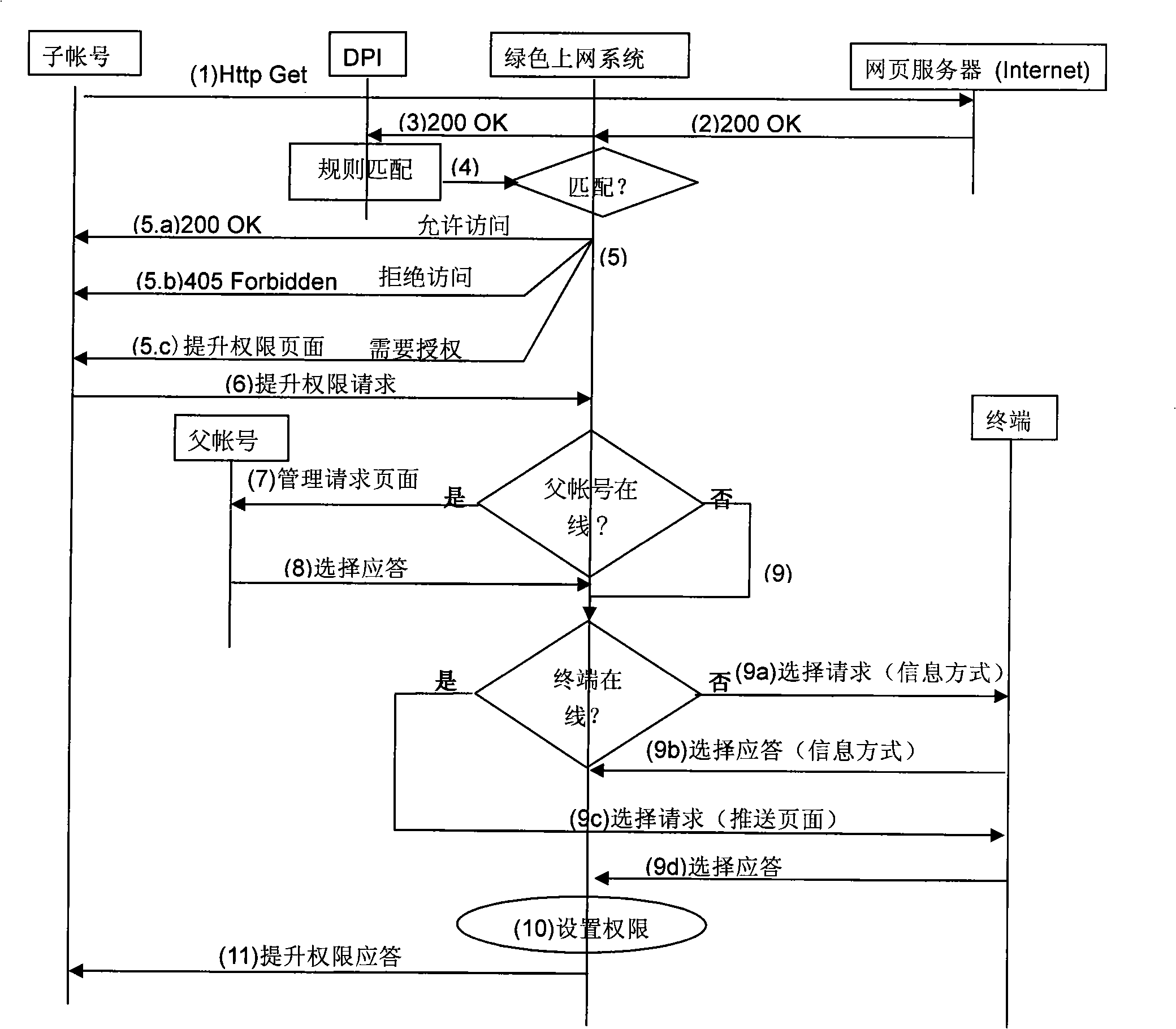
InactiveCN101515868AEasy to manageFlexible managementTelephonic communicationData switching networksTelecommunications networkRights management
The invention discloses a network privilege management method, device and system, relates to telecommunication network technology, can make terminal manage managed account anytime and anywhere, and realizes convenient and flexible management for the managed account. The network privilege management method provided by the embodiment of the invention includes steps that the terminal receives management request of the managed account through a network management system; and the terminal sends instruction to a green networking system to manage the managed account. The invention is suitable for any scene needing account monitoring.
Owner:HUAWEI TECH CO LTD
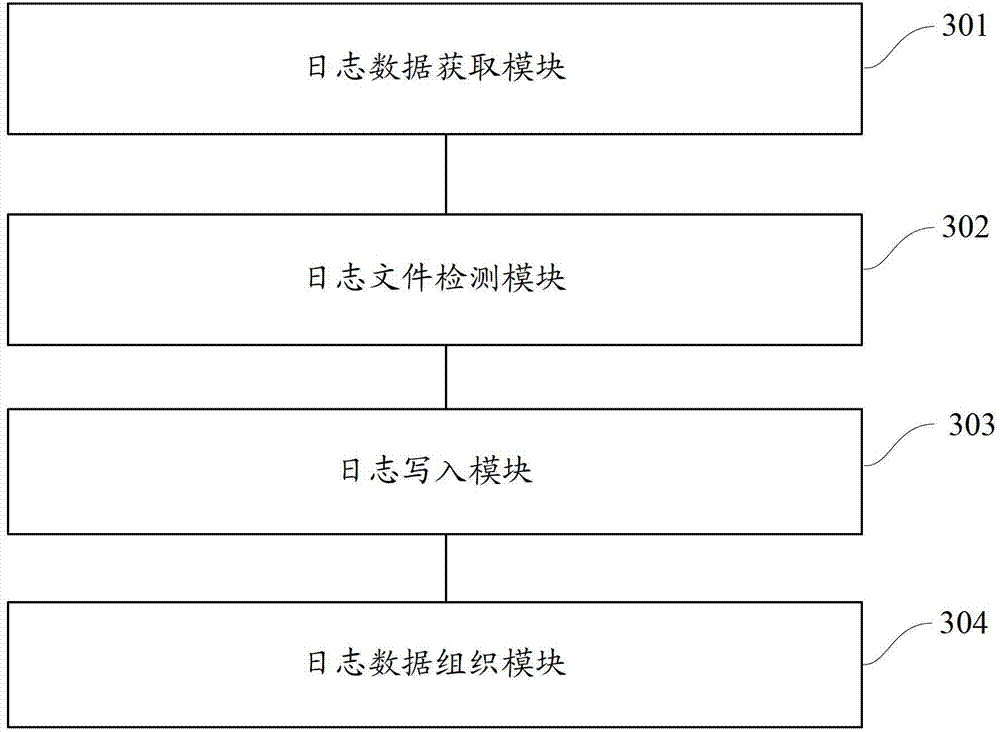
Method and device for log recording
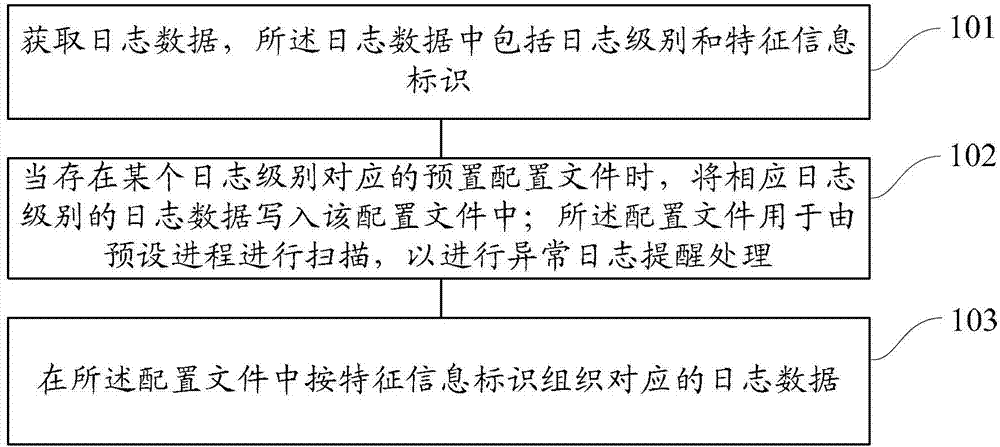
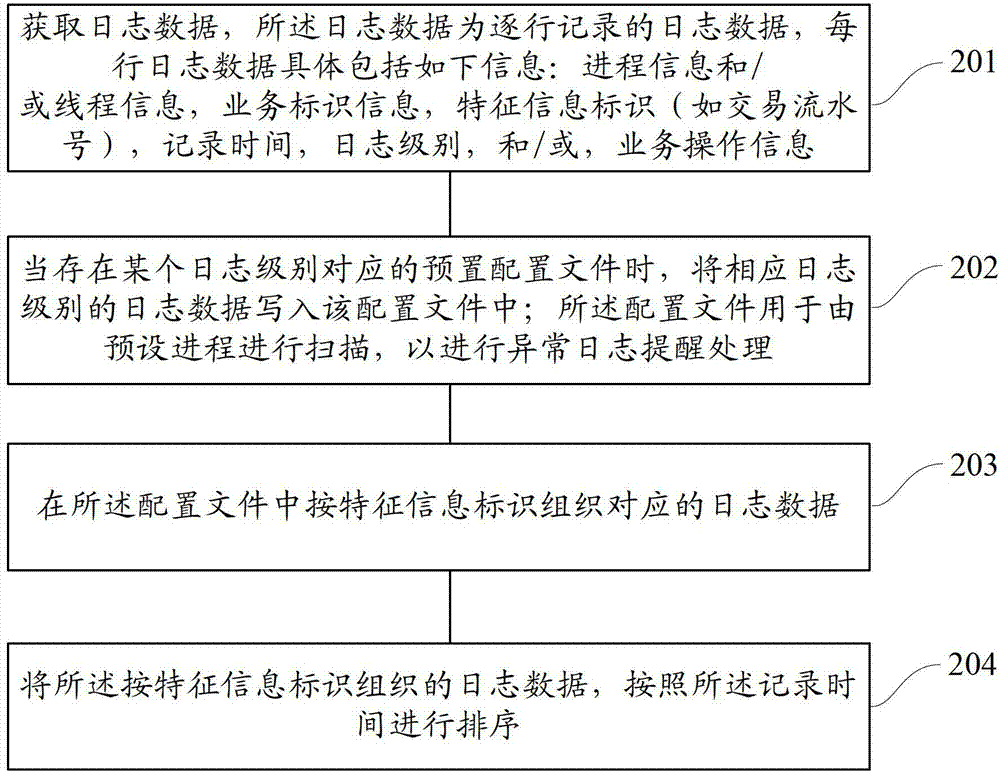
ActiveCN102902764AImprove efficiencySave storage spaceError detection/correctionSpecial data processing applicationsOperating systemLog data
The invention discloses a method and a device for log recording. The method comprises obtaining log data which comprise log levels and characteristic information identifications; writing the log data of corresponding log levels in a configuration file when the preset configuration file corresponding to a certain log level exists; enabling the configuration file to be used for scanning by using a preset progress to conduct unusual log reminding treatment; organizing corresponding log data in the configuration file according to the characteristic information identifications. The method and the device can improve efficiency for locating logs and reporting unusual logs while reducing occupation of log data storage resources.
Owner:BEIJING QIHOO TECH CO LTD +1
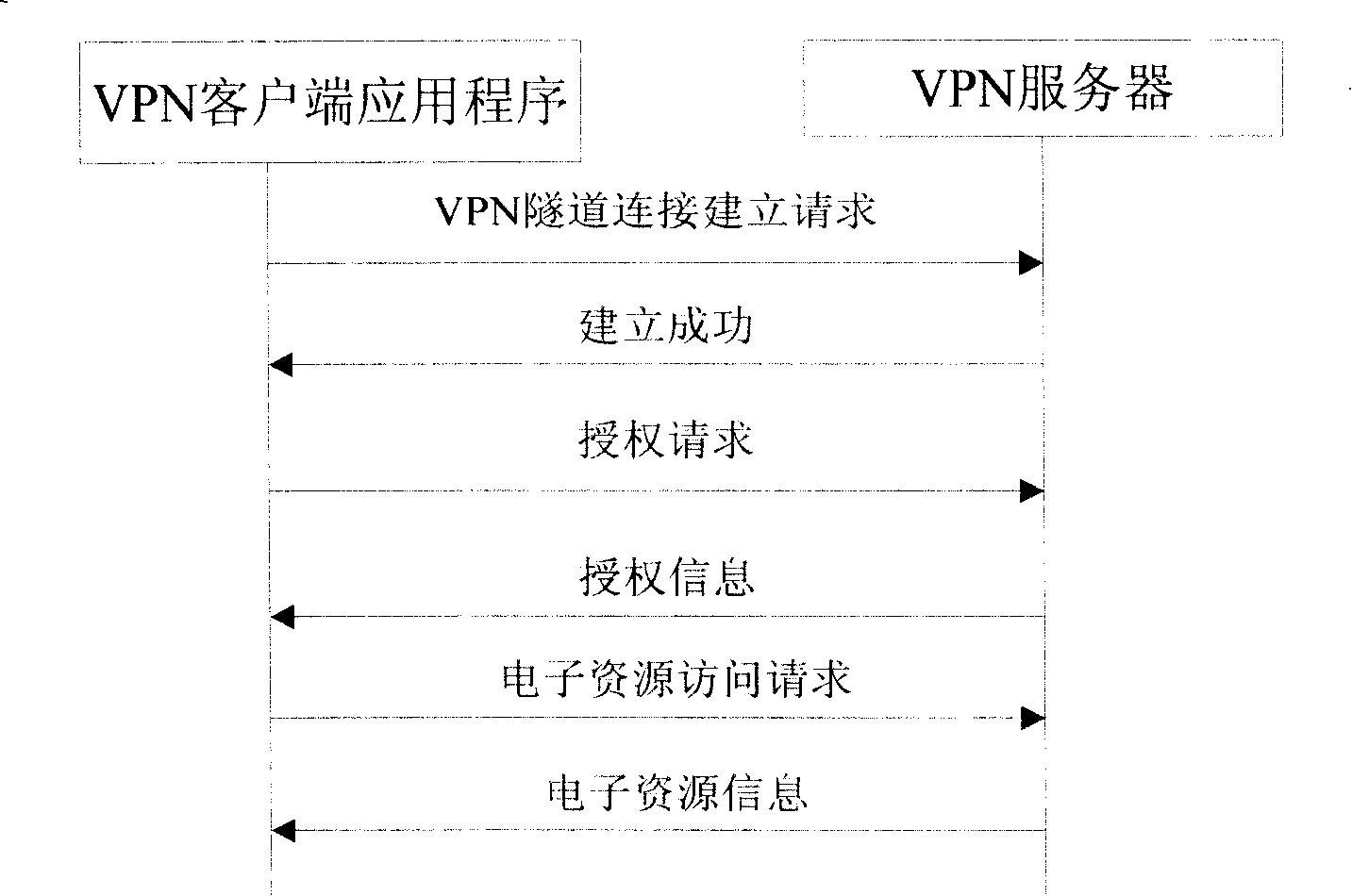
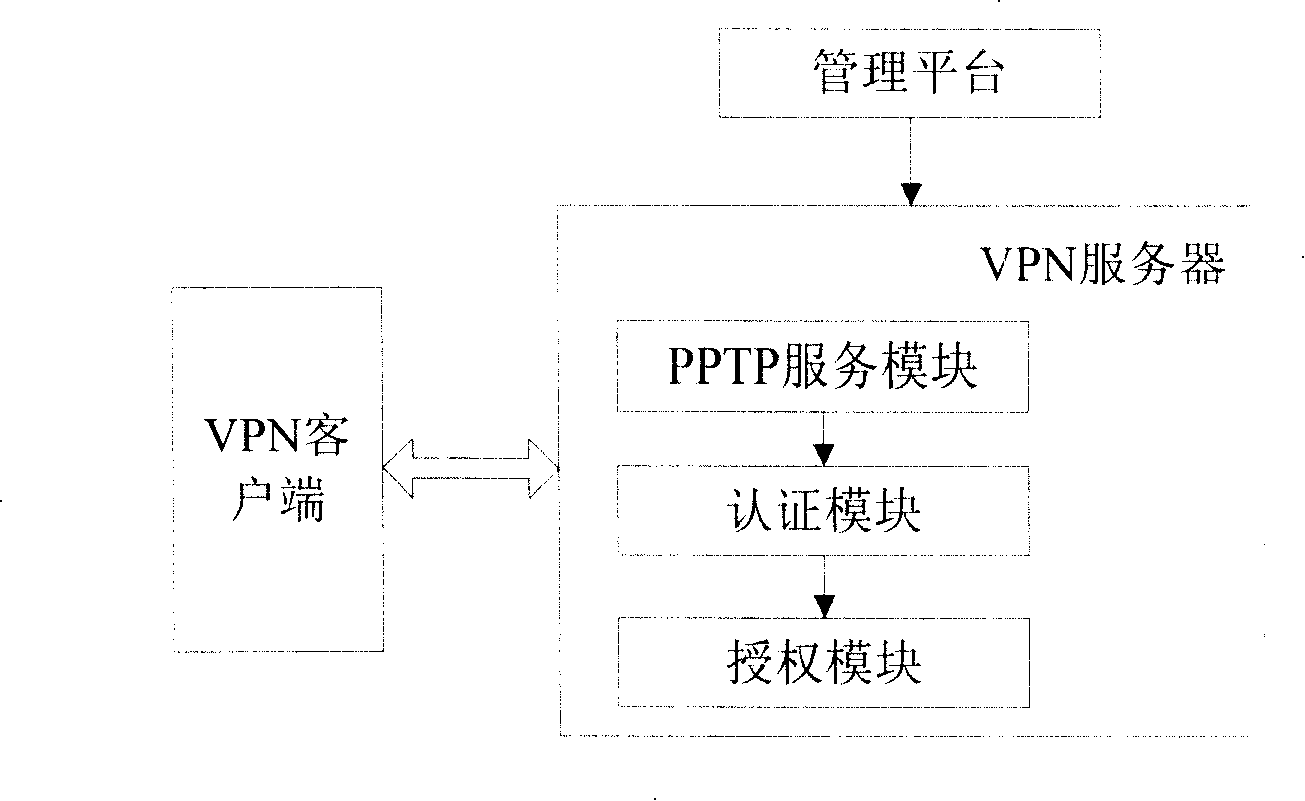
Method and system for remote access to campus network resources
The invention discloses a method for realizing remote access of campus network resource and a system thereof, relating to technology of remote access of the Internet. The invention is invented to solve the problem that users not in the campus network can not access the campus network resource currently. In the invention, through adopting an application program of a VPN client terminal, a request of the establishment of a virtual special tunnel connection is sent to a VPN server; the VPN server verifies the request of the establishment of the virtual special tunnel connection and after the request is qualified, the VPN server returns a response of the successful establishment of the virtual special tunnel connection to the VPN client terminal; the VPN client sends an authorization request to the VPN server and according to an access right of the VPN client terminal, the VPN server returns an authorization message to the VPN client terminal; the VPN client terminal analyzes the received authorization message and according to the authorization message to access electronic resource in the campus network through the virtual special tunnel. The invention realizes the goal that the users outside the campus network can access the campus network resource safely.
Owner:PEKING UNIV FOUNDER GRP CO LTD +1
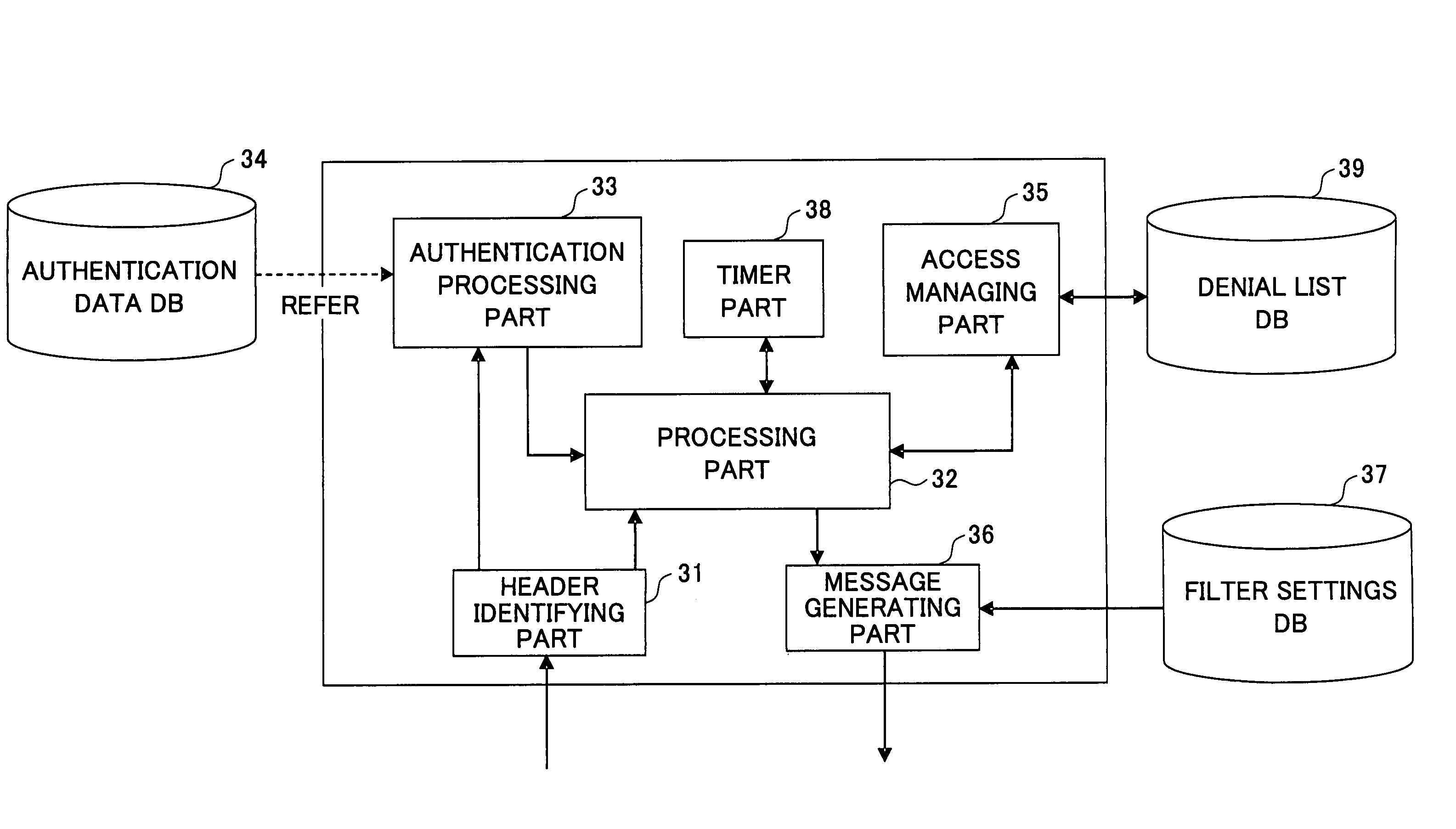
Access management method and access management server
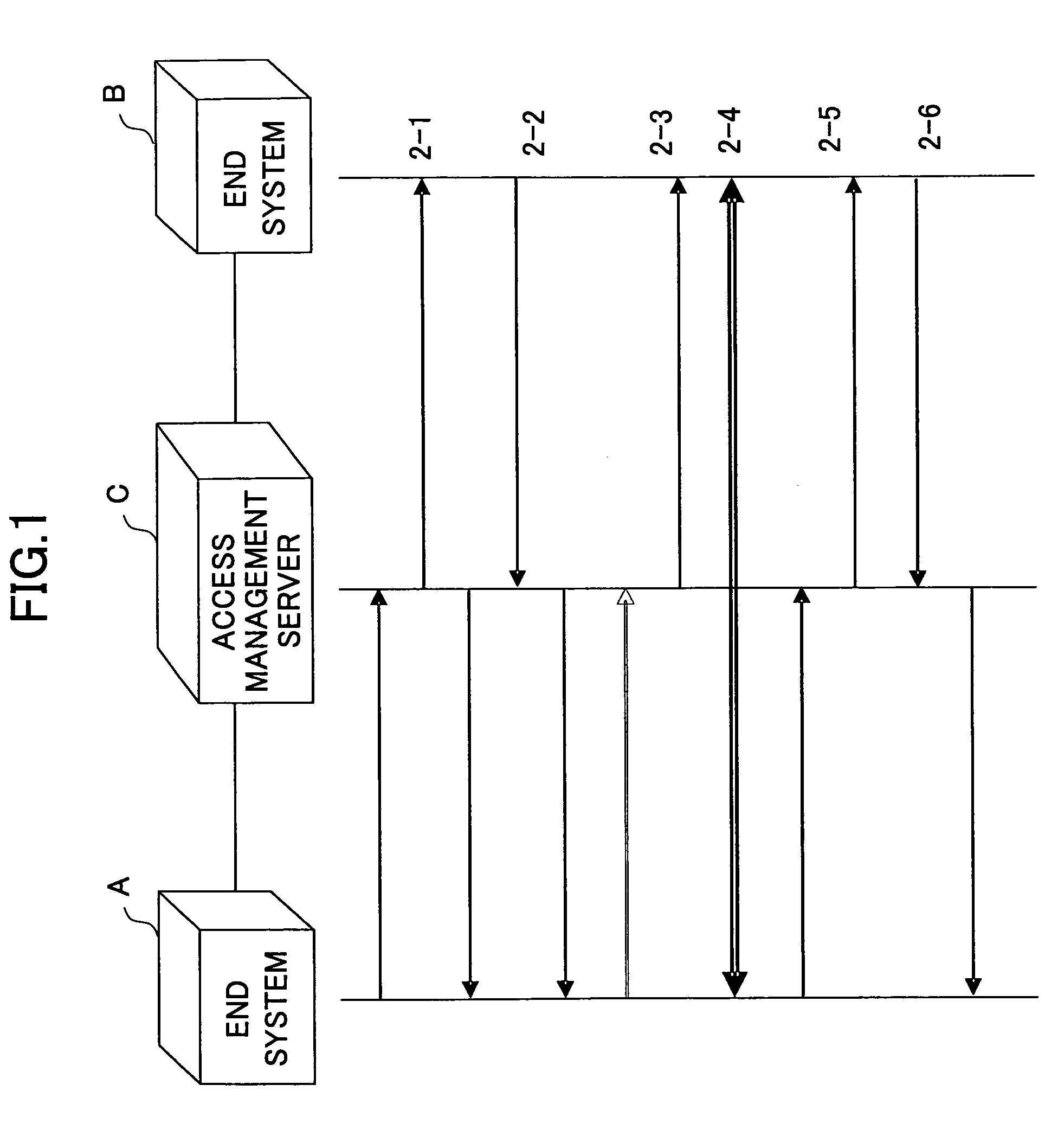
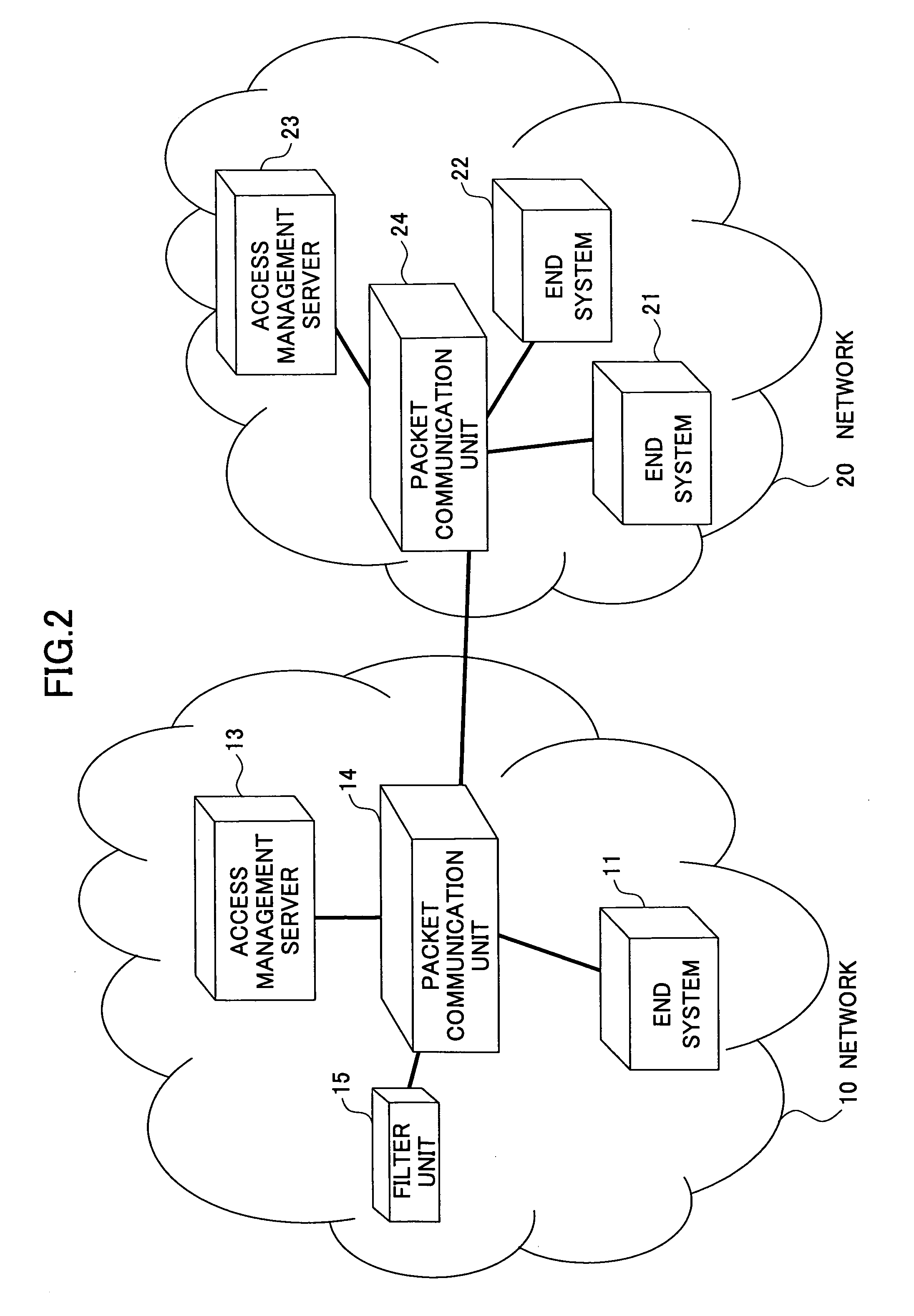
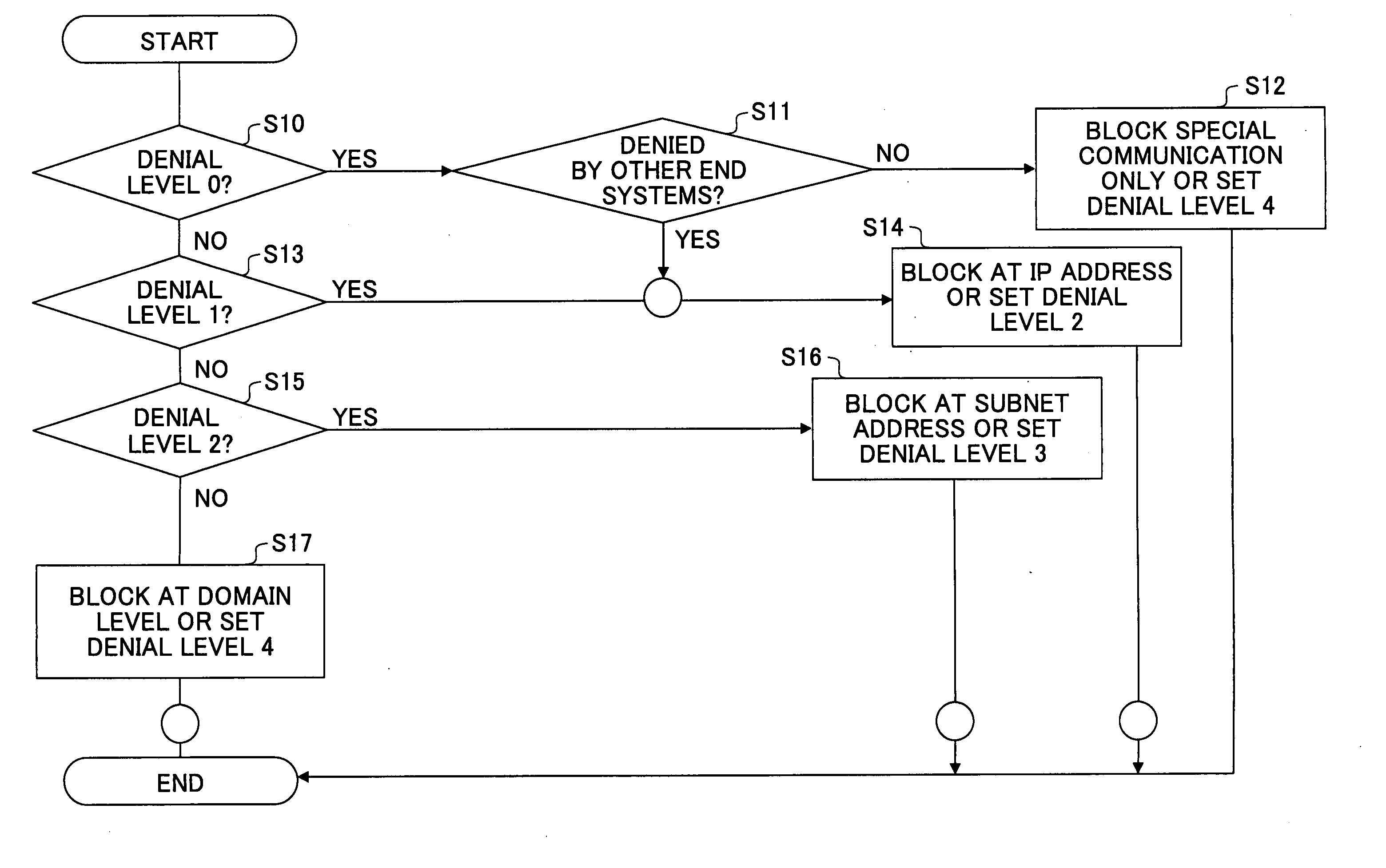
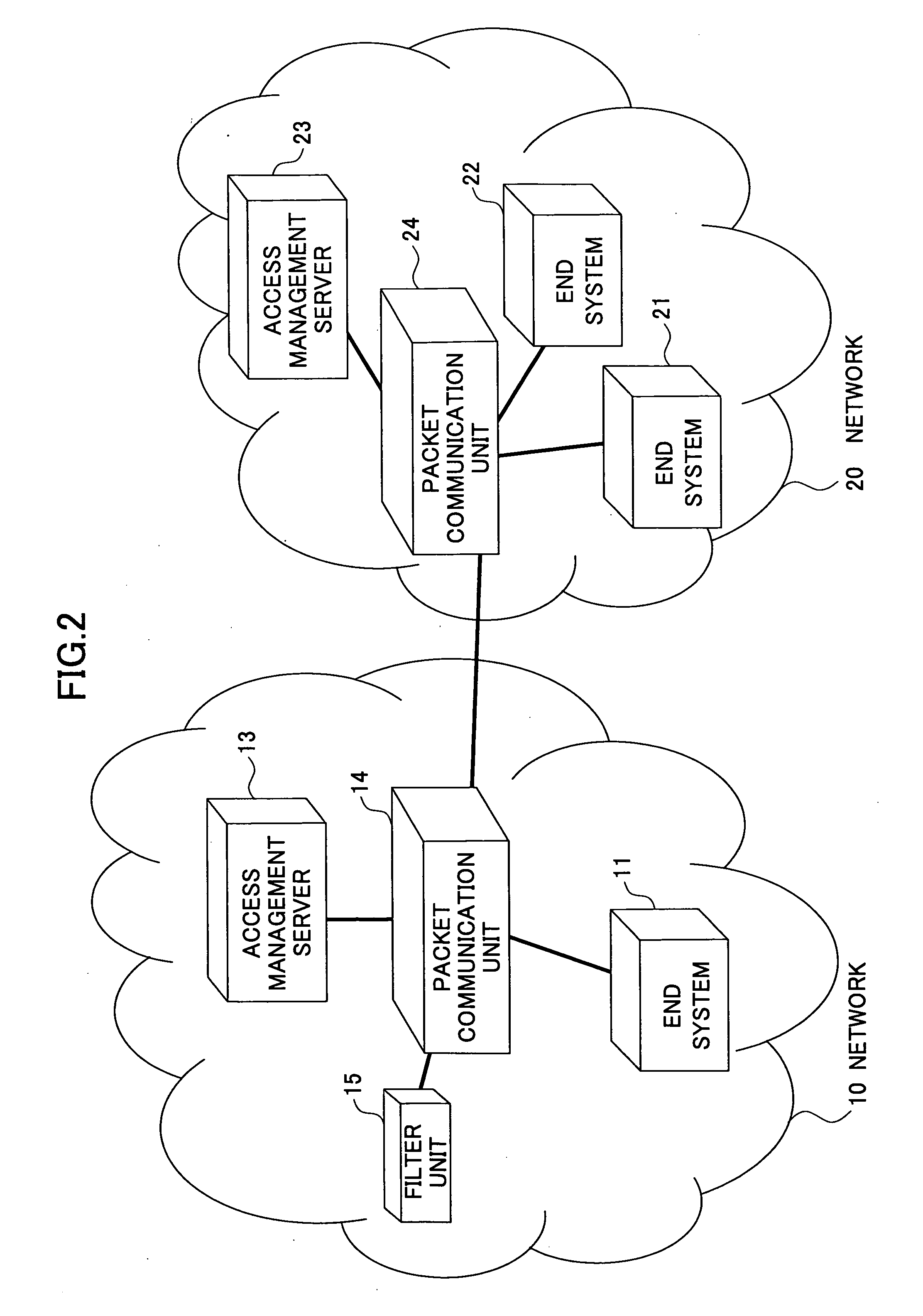
InactiveUS7508767B2Avoid attackFlexible managementError preventionTransmission systemsPacket communicationEnd system
In an access management method in a network including at least one end system, a packet communication unit for routing, and an access management server including an authentication function, a communication partner is authenticated for each session and a communication permitted by a communication partner is permitted by the access management server. A packet meeting a condition of a denied packet being denied by the communication partner is discarded by the packet communication unit.
Owner:FUJITSU LTD
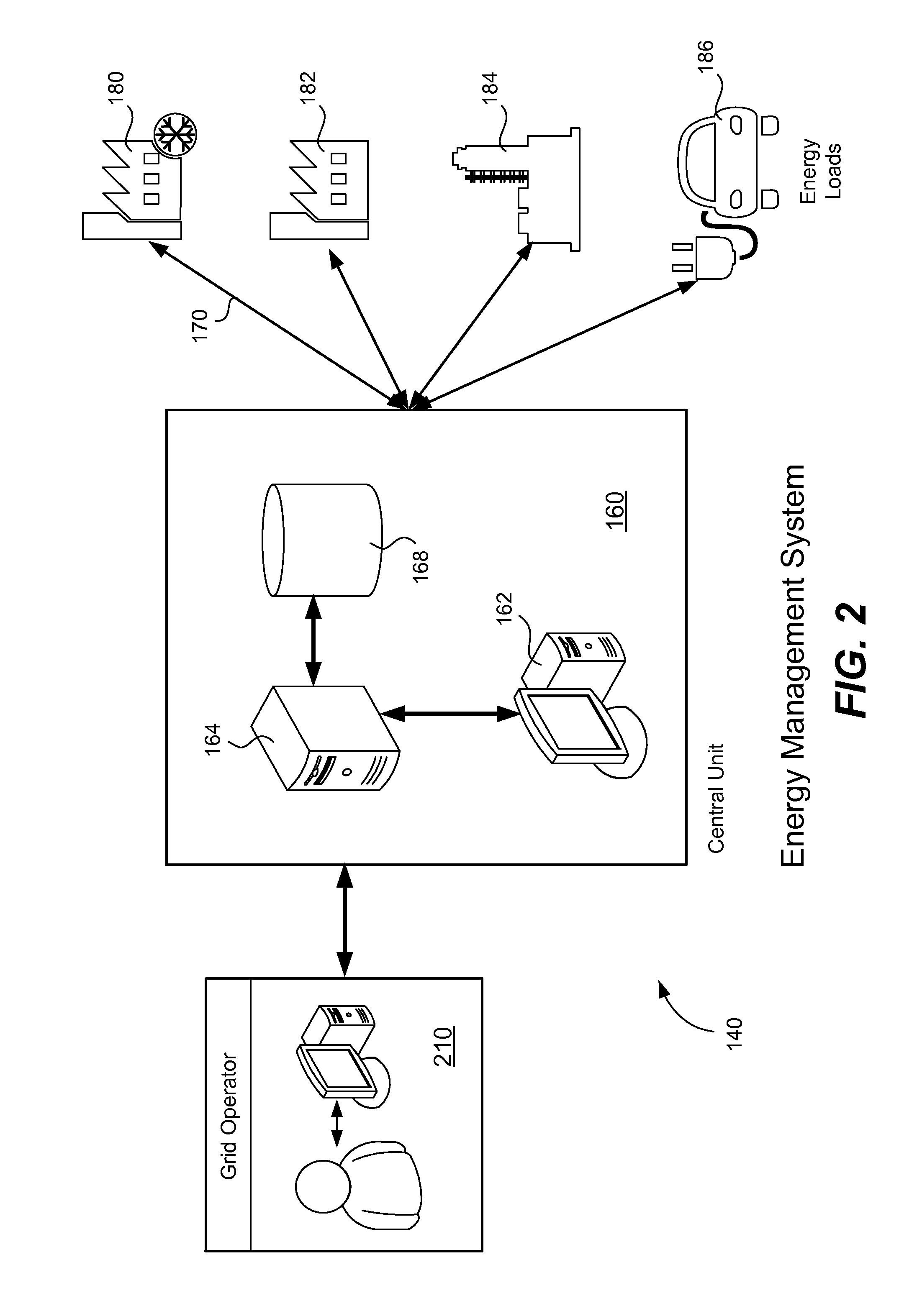
Portfolio managed, demand-side response system
ActiveUS20150112501A1Responding rapidly and reliablyReduce (or increase) powerMechanical power/torque controlLevel controlGrid operatorPower grid
A central site, using grid operator requirements to reduce portfolio power according to frequency decreases within a frequency band, determines the optimal frequency triggers at which each load within a portfolio should reduce power and by how much power. Power availability of each load is optimized. These triggers and individual load power reductions are periodically dispatched from the central site to the individual loads. Each load detects when a frequency deviation occurs and is able to independently and rapidly reduce its power consumption according to the triggers and corresponding power reductions it received previous to the frequency deviation. Reliance upon the central site to detect a frequency deviation and then to dispatch power reductions in real time is not needed. The system also detects frequency increases and directs a portfolio of loads to consume more power. The system applies to energy loads and detection of a grid signal in general.
Owner:RESTORE
Data permission management method, data permission management system and service management system
ActiveCN105912949AEasy to manage and maintainFlexible managementDigital data protectionSpecial data processing applicationsService systemRights management
The invention discloses a data permission management method, a data permission management system and a service management system and relates to the field of computer technologies. The method disclosed by the invention comprises the steps that the data permission management system receives a user's data access request intercepted by the service system; through analysis of the data access request, an object to be accessed by the user is acquired; access permission information of the object to be accessed by the user is searched in permission configuration information; and the access permission information is integrated with the data access request, and then the integrated information and request are returned to the service system, so that the service system can continue processing the data access request with the access permission information. According to the invention, uniform and centralized management of data permissions of each service system can be implemented by the data permission management system; and management and maintenance become convenient.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
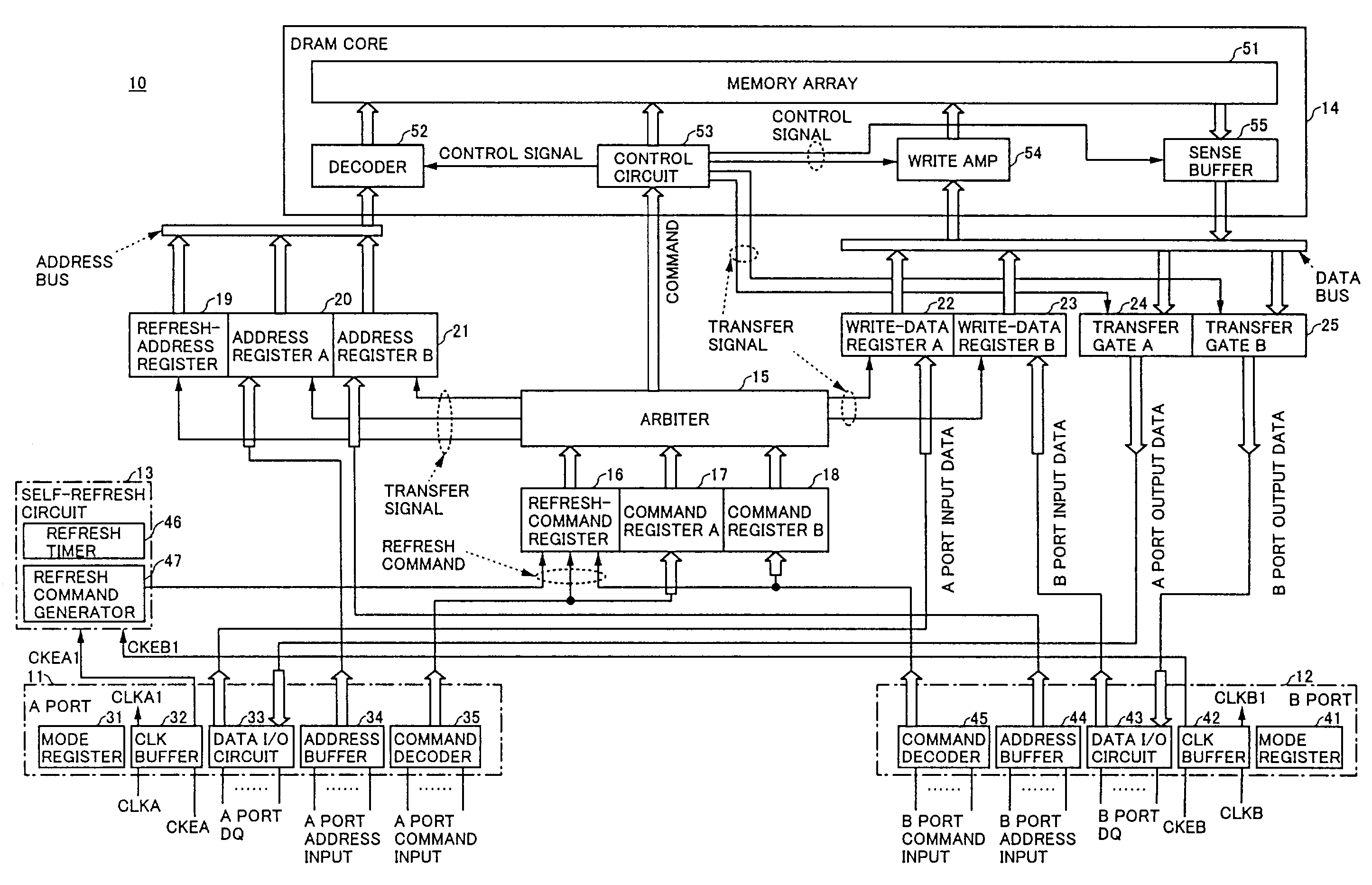
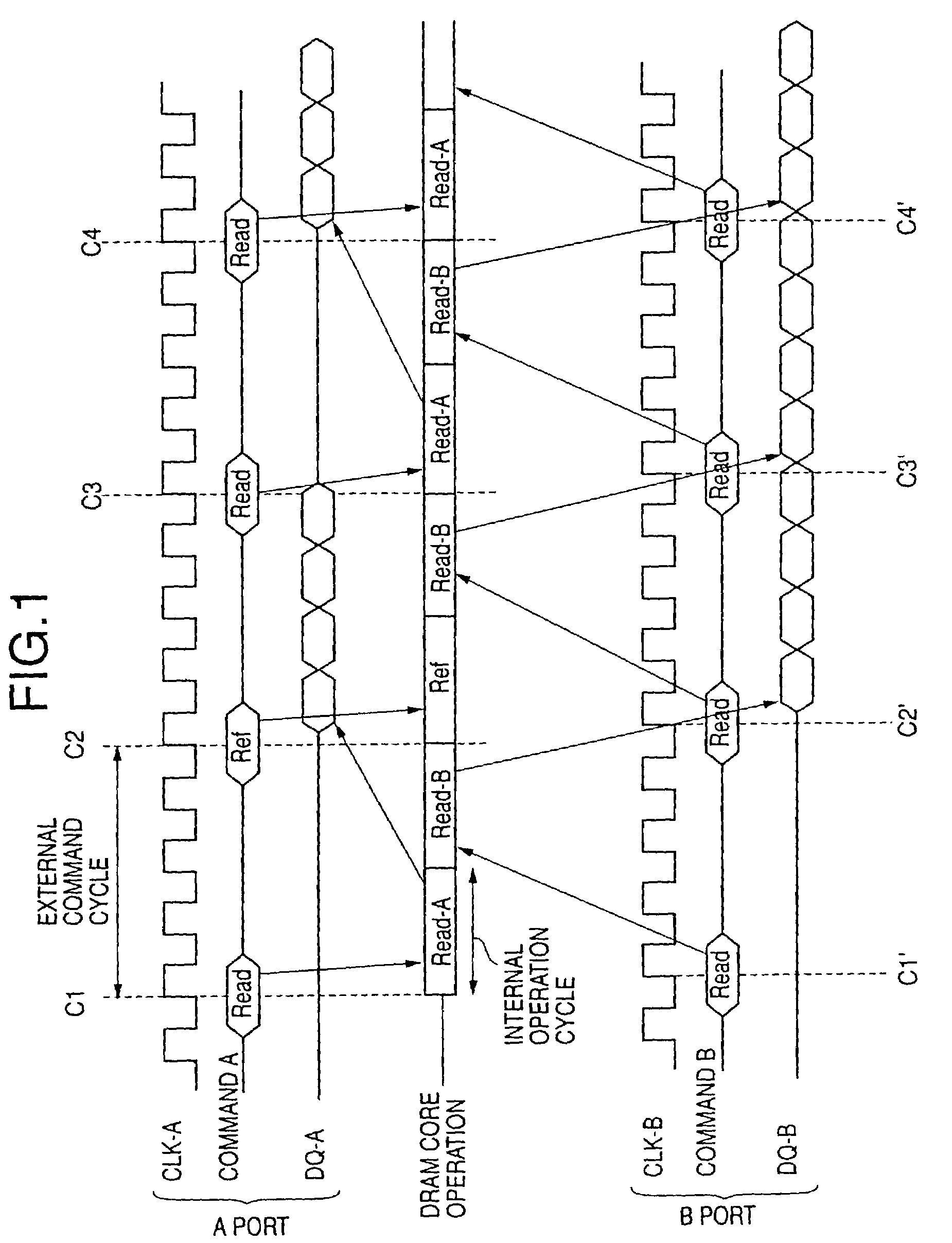
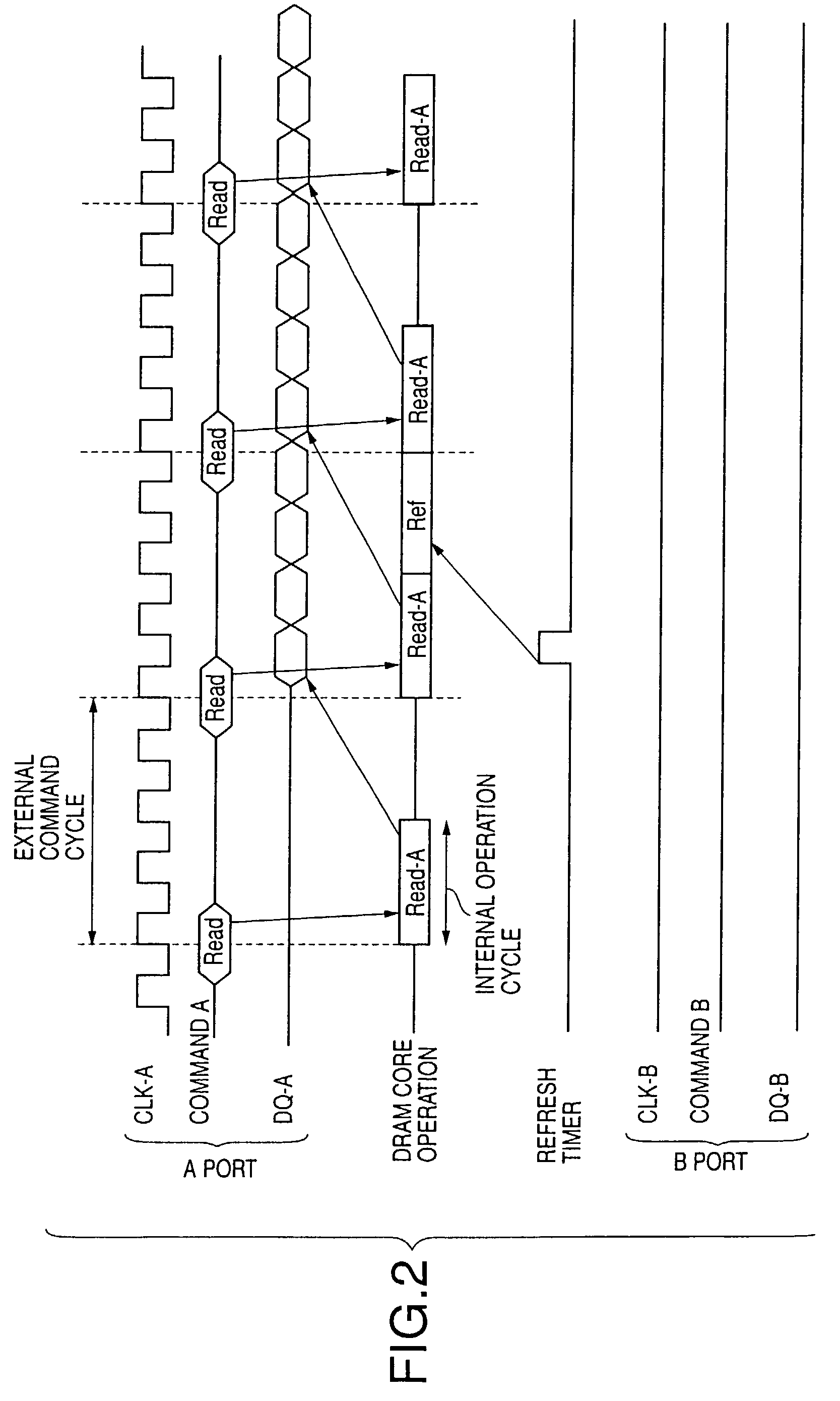
Multi-port memory based on DRAM core
A semiconductor memory device includes a plurality of N external ports, each of which receives commands, and an internal circuit which performs at least N access operations during a minimum interval of the commands that are input into one of the external ports.
Owner:SOCIONEXT INC
Random Access Mode Control Method and Entity
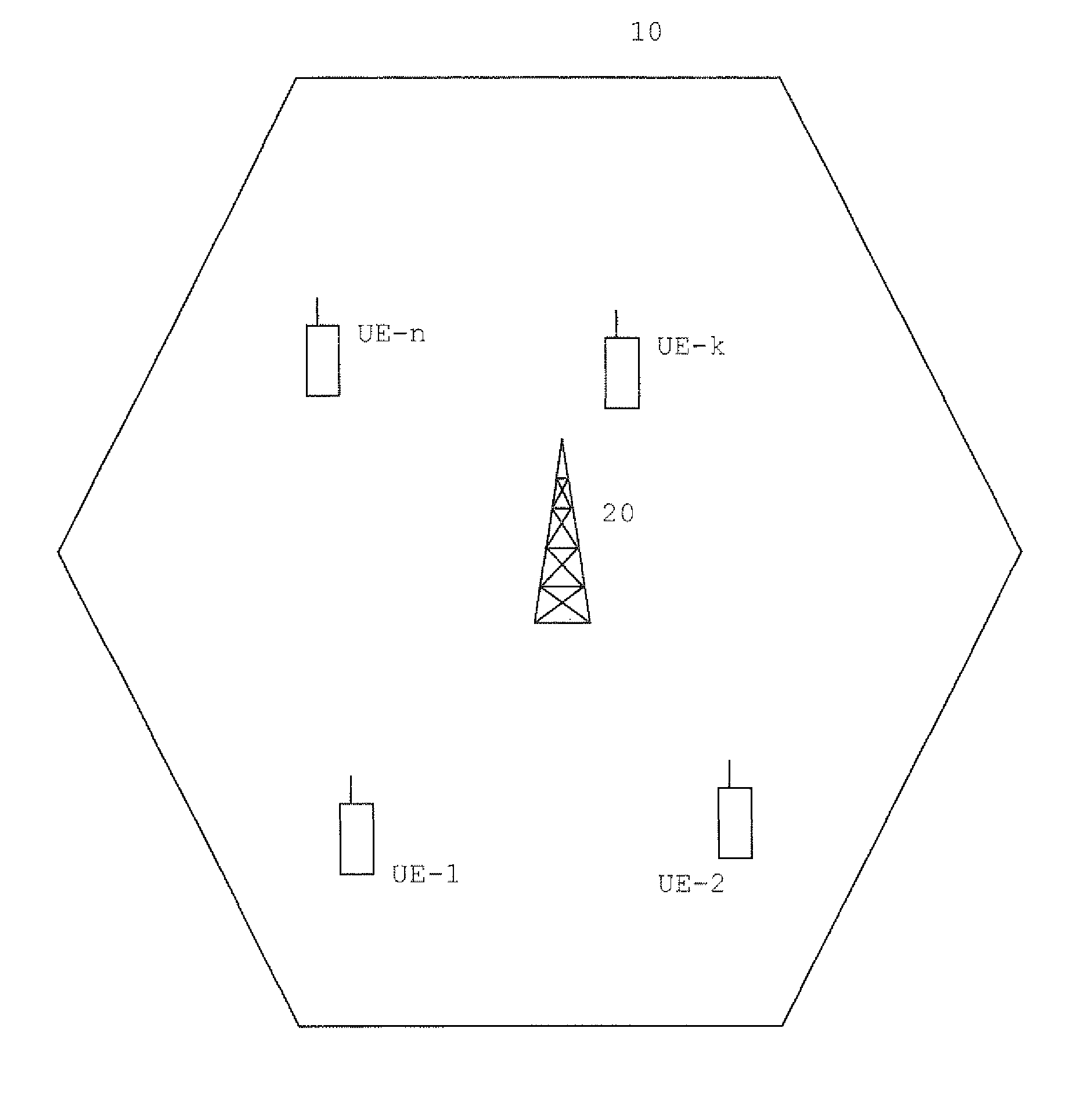
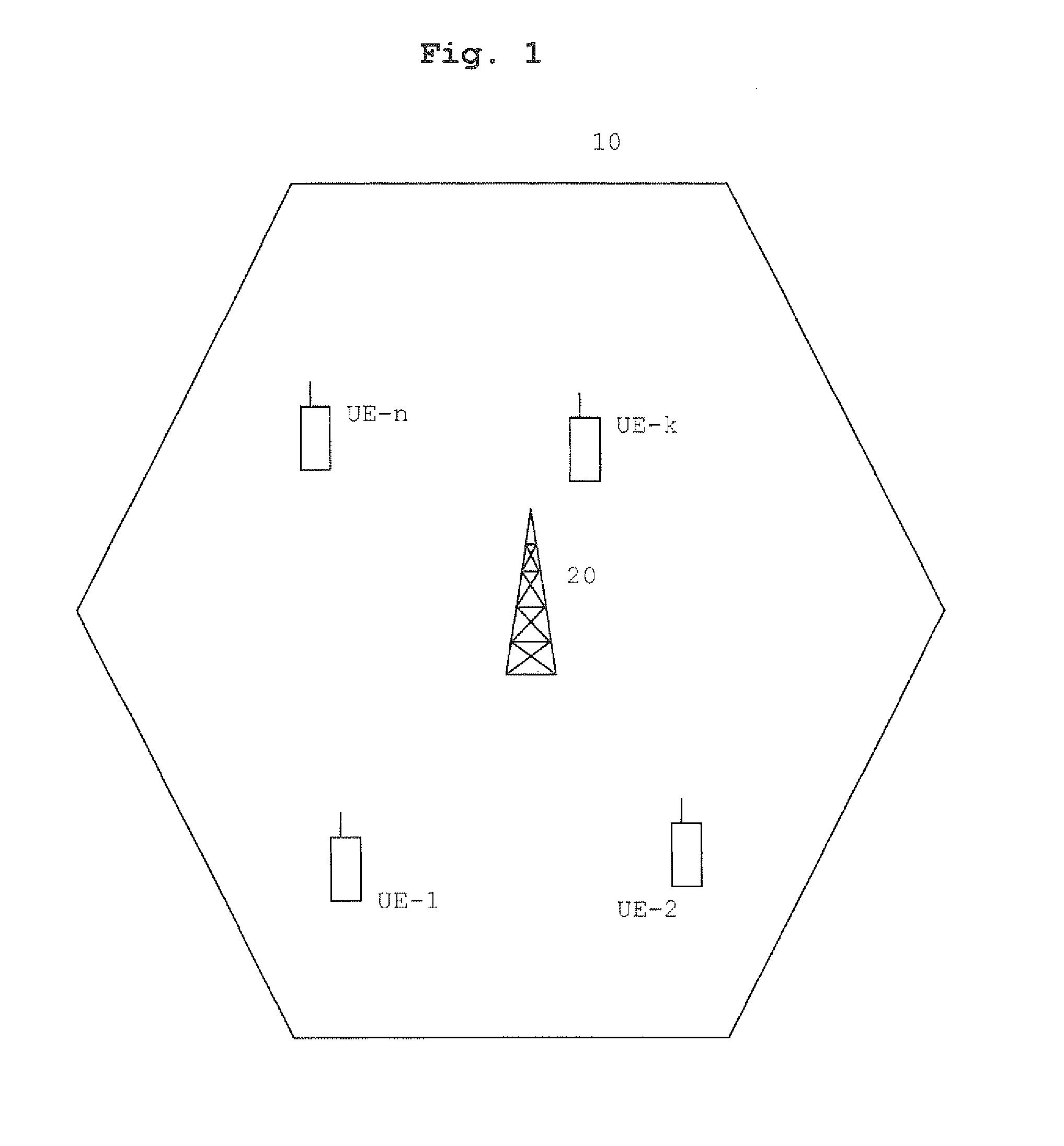
InactiveUS20110086658A1Flexible managementOptimal utilisationModulated-carrier systemsCode division multiplexRandom access memoryMode control
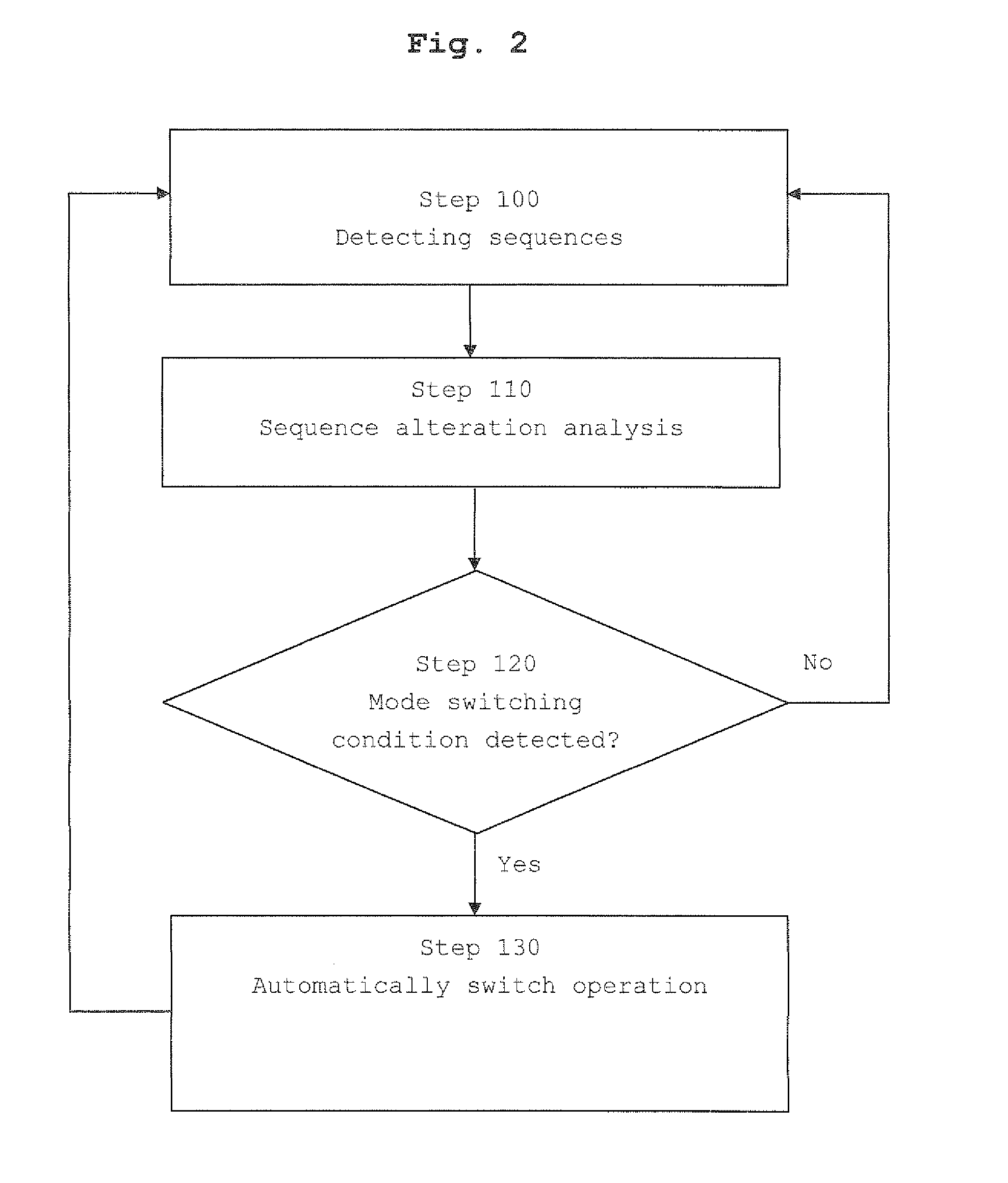
A method of controlling a random access mode in a cell of a cellular communication system, said cell being operable in a first random access mode associated with a first set of random access identification sequences or in a second random access mode associated with a second set of random access identification sequences / said random access identification sequences to be used by terminals (UEI . . . UEn) performing a random access operation in said cell, where said second set of random access identification sequences is arranged for avoiding misidentifications due to sequence alterations occurring in transmissions from said terminals (UEI . . . -UEn), the method comprising: performing a sequence alteration analysis based on the an output of a random access identification sequence detector in a network entity, and if a mode switching condition is determined on the basis of the sequence alteration analysis, automatically switching operation of said cell from one of said random access modes to the other of said random access modes.
Owner:TELEFON AB LM ERICSSON (PUBL)
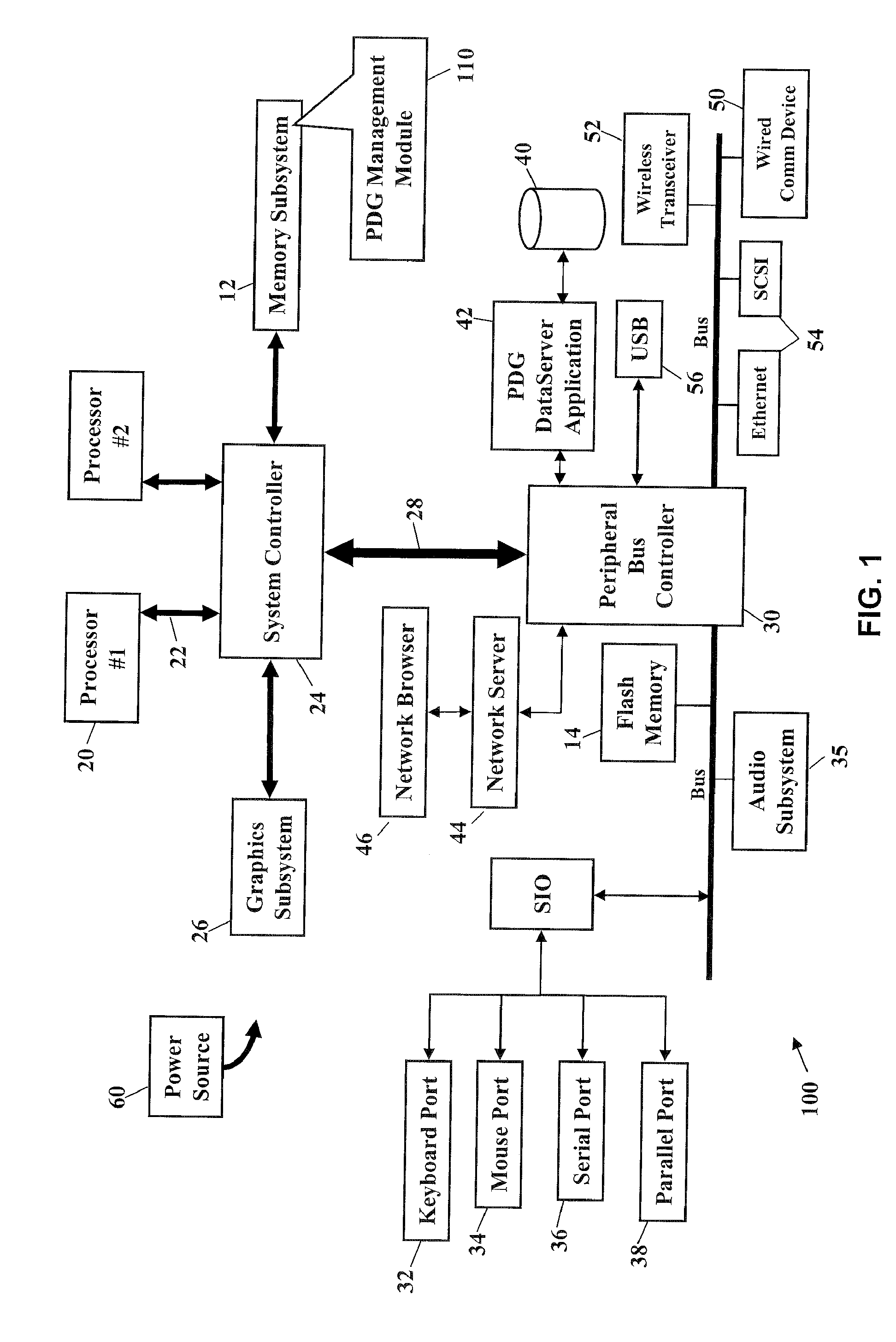
Firmware automatic configuration system and method for substrate management controller
InactiveCN1641568AFlexible replacementFlexible managementSpecial data processing applicationsSpecific program execution arrangementsBaseboardMakefile
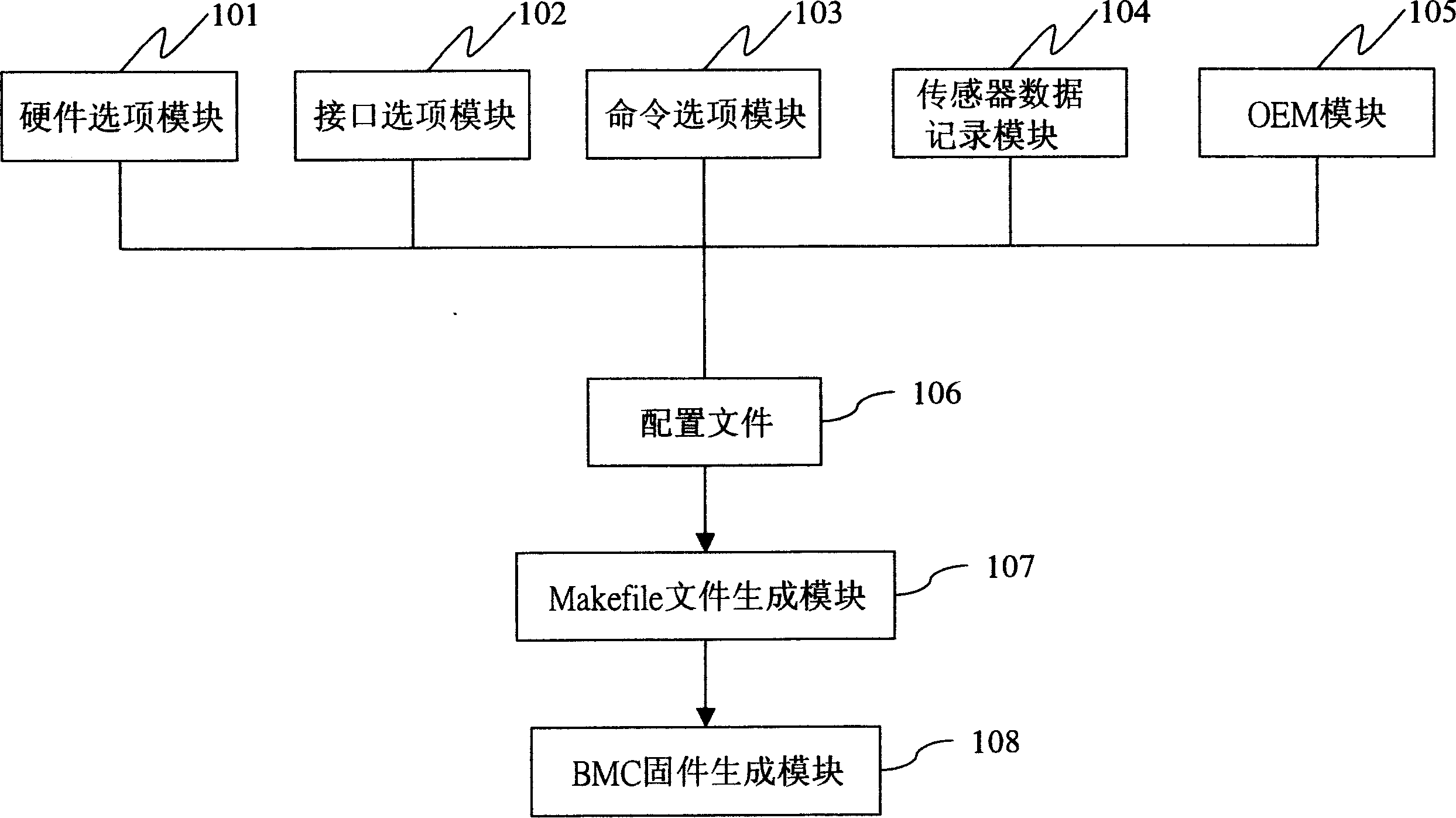
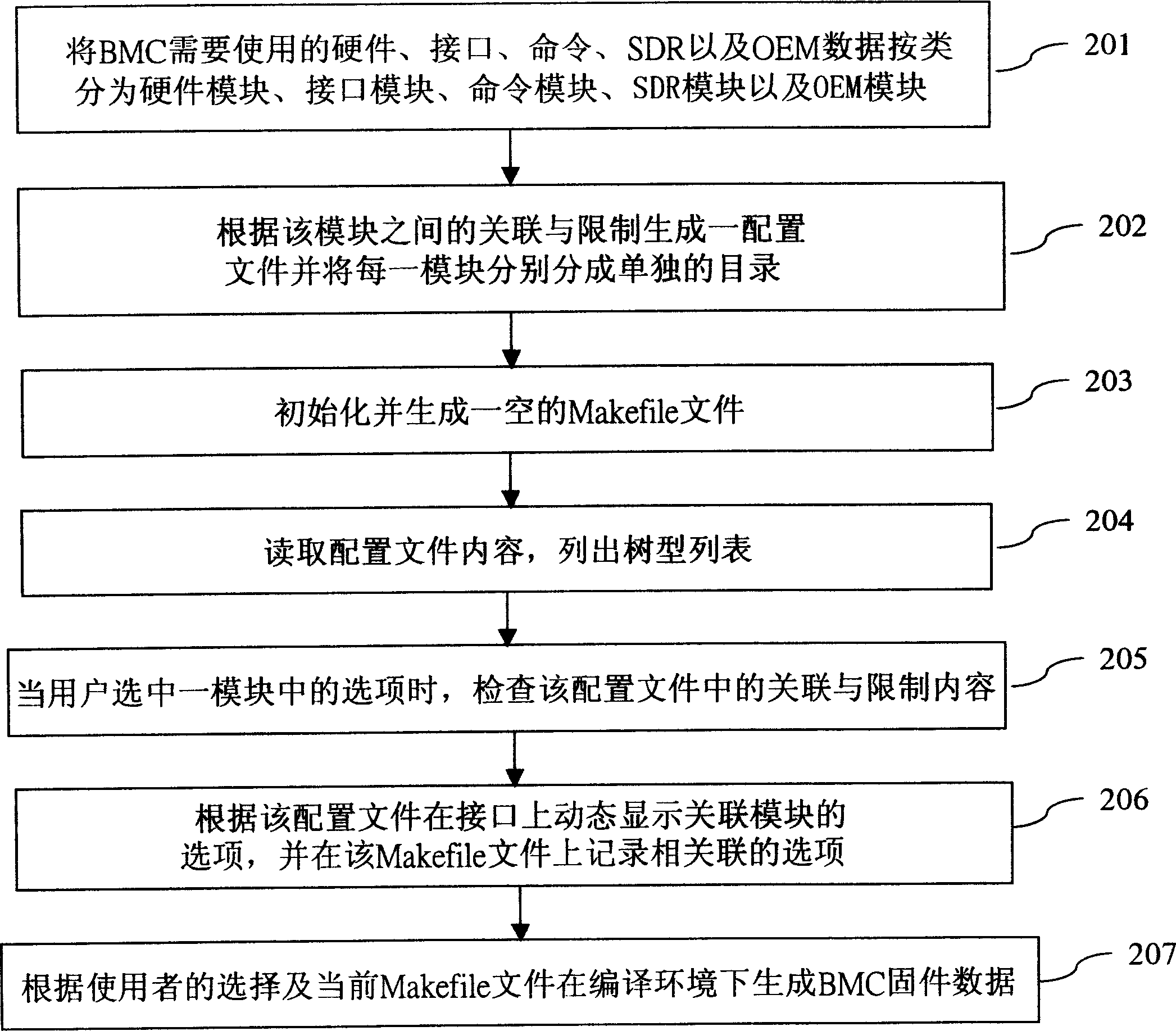
The invention discloses a firmware automatic configuration system of baseboard managing controller. It packages the hardware module, interface module, command module, SDR module and OEM module according to species. Then, a configuration file would be created and separated catalog of every module would be gained. A Makefile would be created after initializing. Reading content of the configuration file, when user chooses an option in a module, checking the configuration file and dynamic display the option of the relate module on the interface and register the relative option on the Makefile. Finally, BMC firmware data would be created and automatically finish the configuration of BMC firmware according to the invention.
Owner:INVENTEC CORP
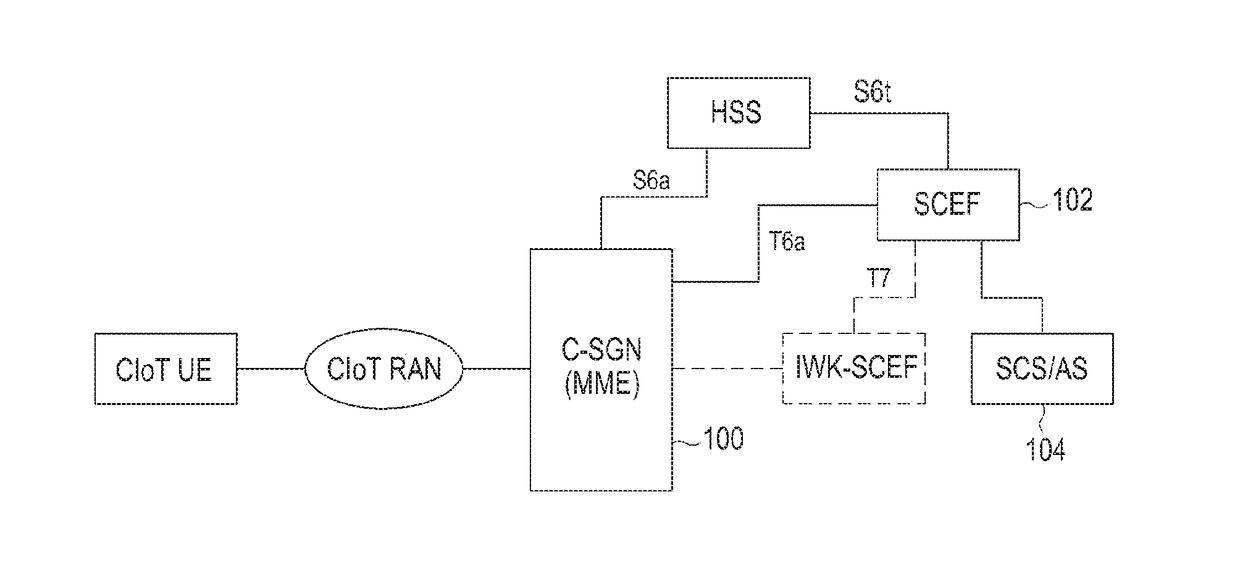
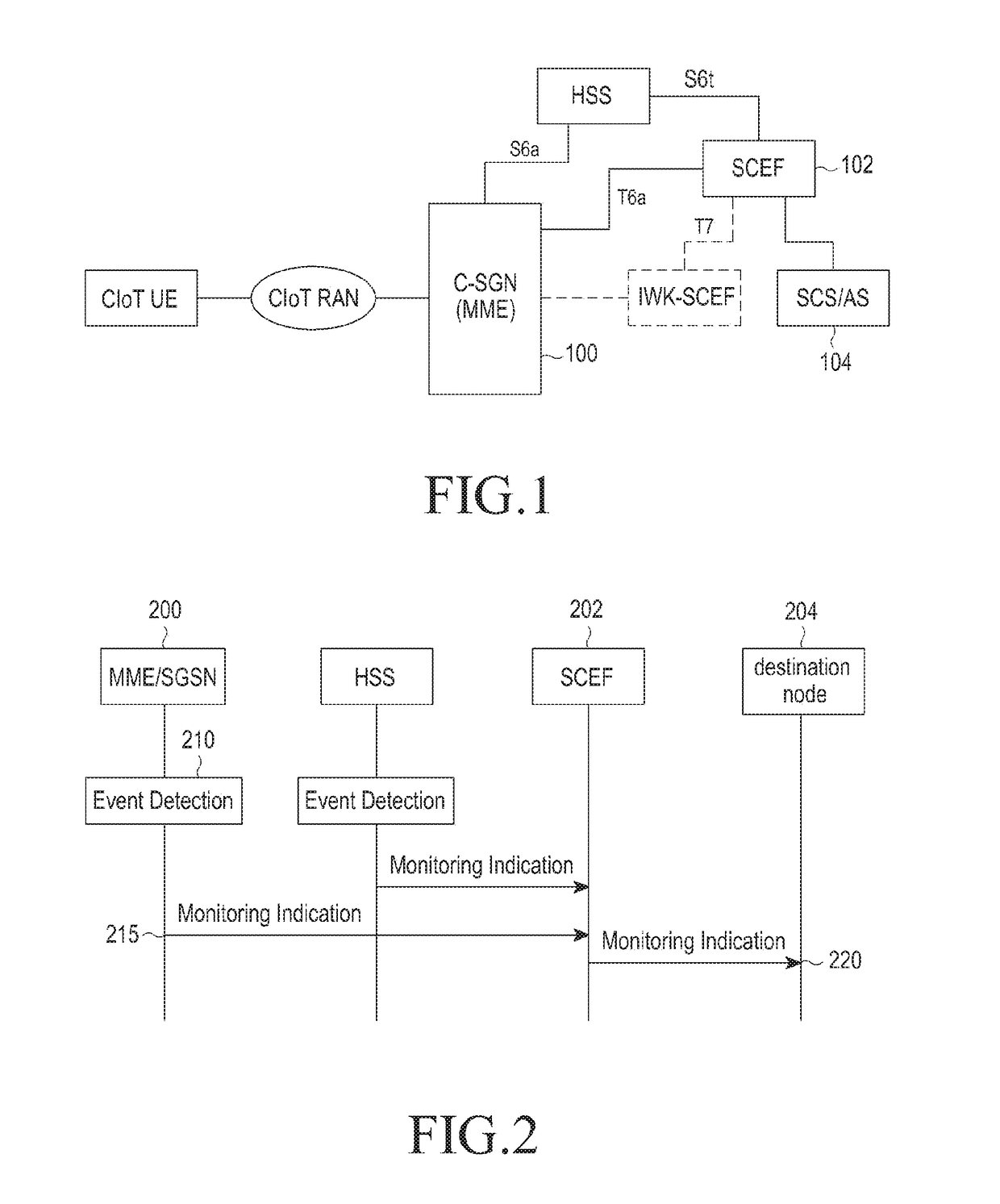
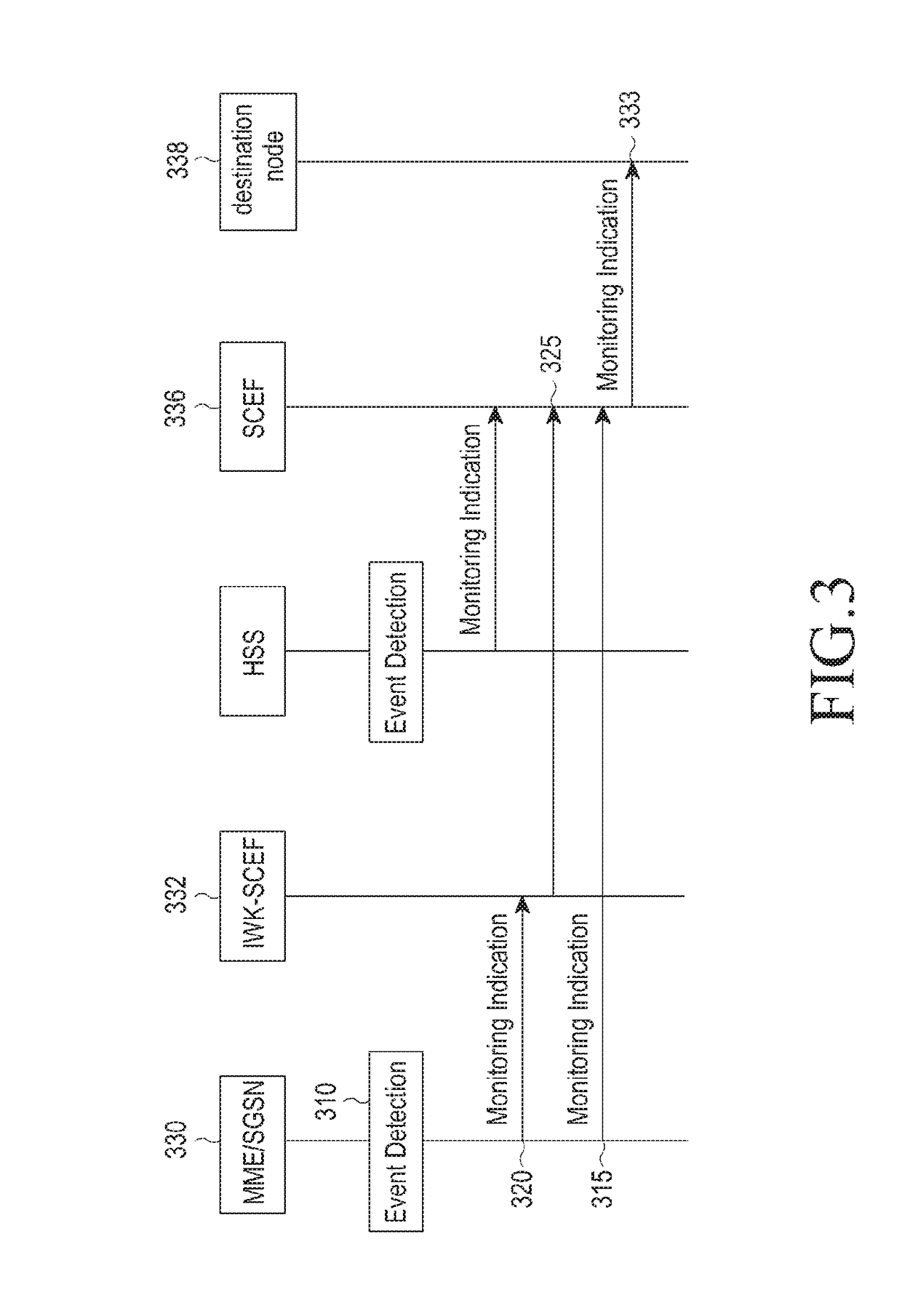
Method for transmitting data in ciot system and device therefor
ActiveUS20180332462A1Promote recoveryAccurately reflectNetwork traffic/resource managementMachine-to-machine/machine-type communication serviceCellular communication systemsComputer terminal
The present disclosure provides a method whereby a mobility management entity (MME) in a cellular communication system transmits uplink data, the method comprising: receiving uplink data from a terminal; determining if the received uplink data is an Internet Protocol (IP) packet by examining the uplink data; transmitting the uplink data to a destination node via a packet data network (PDN) if the uplink data is an IP packet; and transmitting the uplink data to the destination node via a service capability exposure function (SCEF) if the uplink data is not an IP packet, wherein the uplink data comprises an indicator for indicating whether the uplink data is an IP packet.
Owner:SAMSUNG ELECTRONICS CO LTD
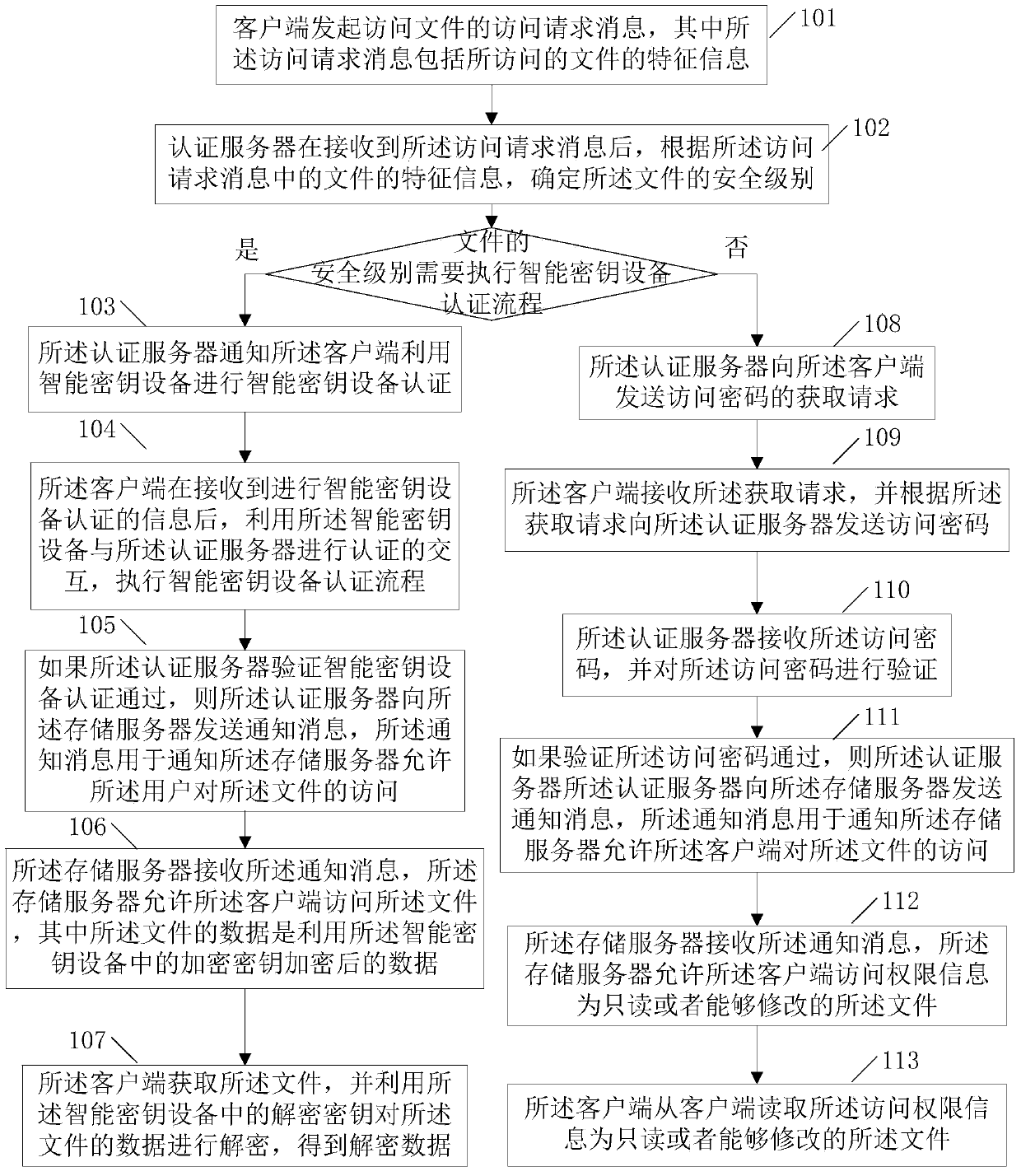
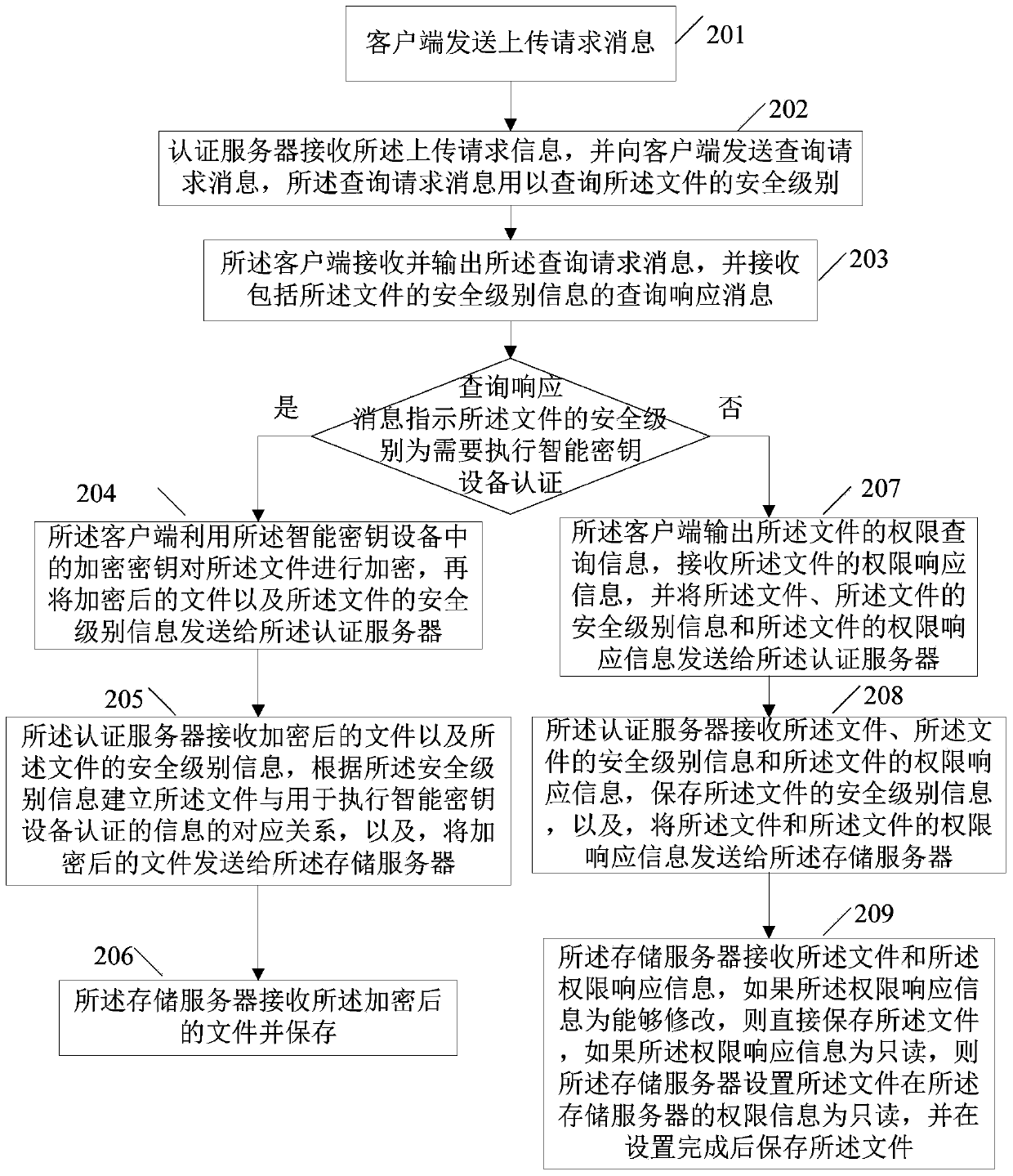
Method for accessing and uploading data in data storage system
ActiveCN103701611AEnsure safetyReduce operation and maintenance costsUser identity/authority verificationDigital data protectionData storage systemEngineering
The invention provides a method for accessing and uploading data in a data storage system. The method of accessing data comprises the following steps: a client side initiates an access request message for access to a file; an authentication server determines the security level of the file according to feature information of the file in the access request message after receiving the access request message; if the security level of the file requires to carry out a smart key equipment certification process, the authentication server informs the client side of utilizing smart key equipment to carry out the smart key equipment certification process; after receiving information for the smart key equipment authentication, the client side carries out the smart key equipment authentication process; if the authentication server approves the smart key equipment authentication, the authentication server sends a notification message to a storage server; the storage server allows the client side to access to the file; the client side acquires the file, and decrypts the data of the file by utilizing a decryption key in the smart key equipment, so as to obtain the decrypted data.
Owner:TENDYRON CORP
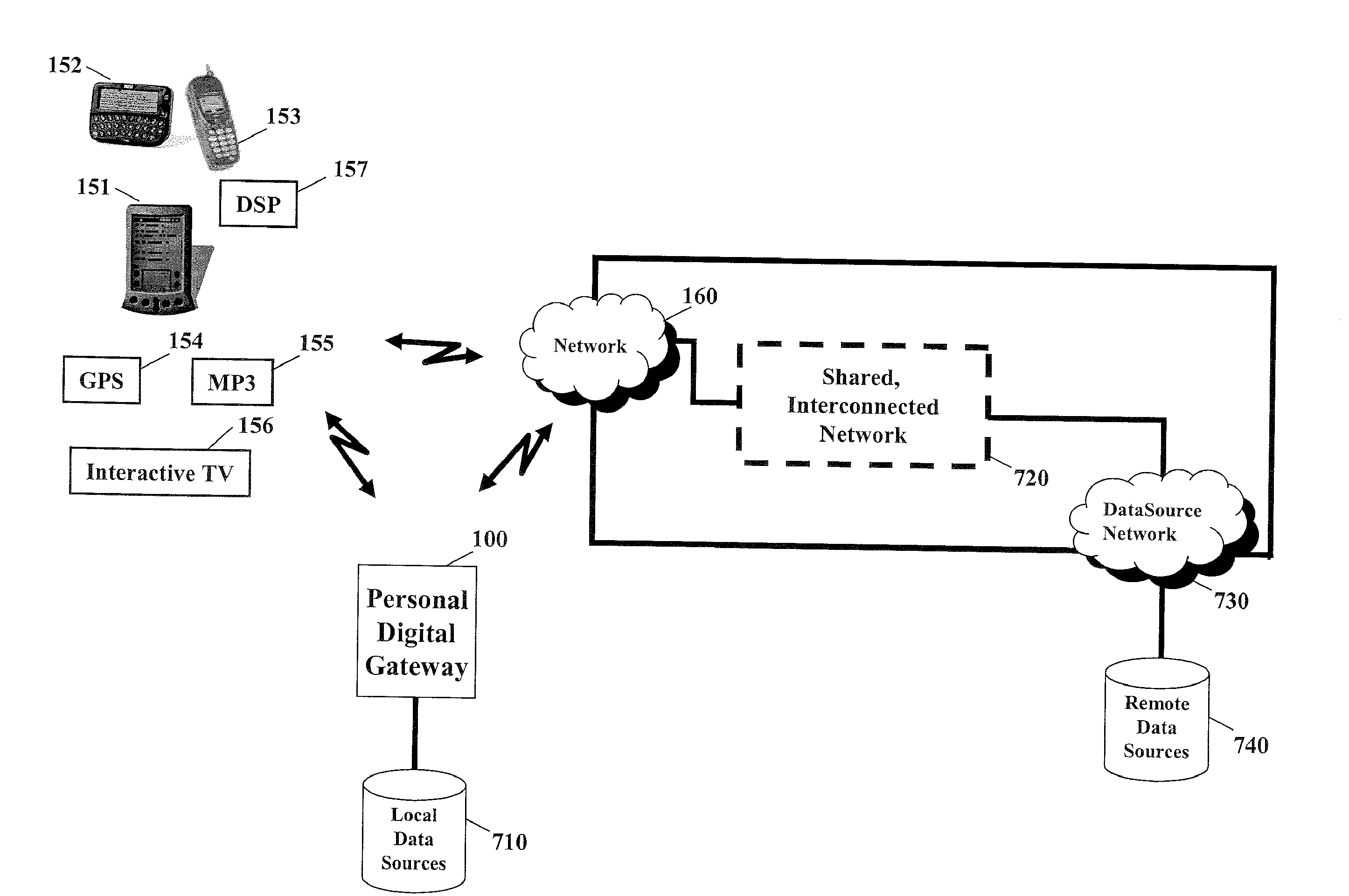
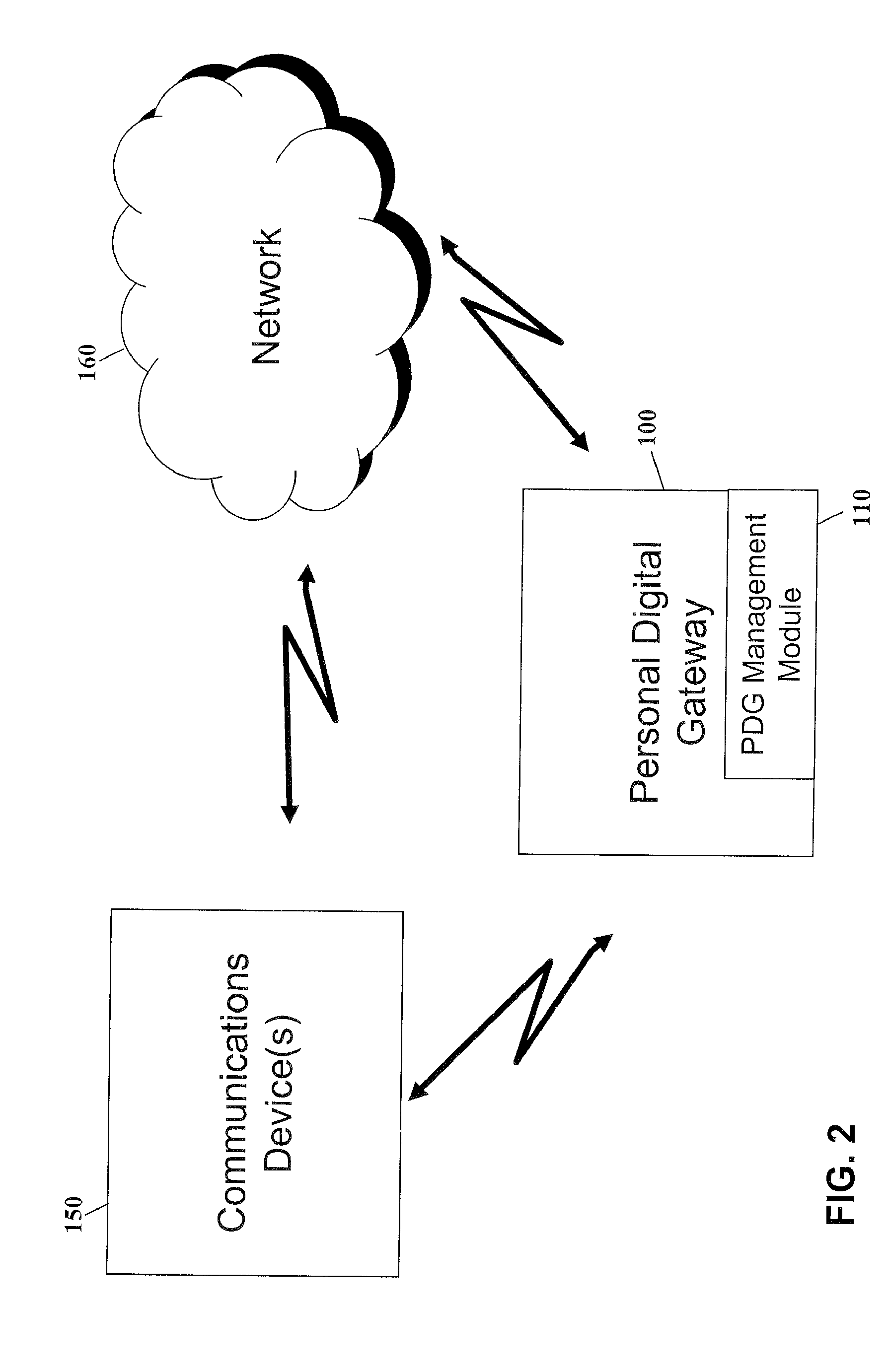
Multi-path gateway communications device
ActiveUS7263102B2Easy accessImprove securityTime-division multiplexMultiple digital computer combinationsPersonalizationTelecommunications
Owner:IOT INNOVATIONS LLC
Access management method and access management server
InactiveUS20060007868A1Avoid attackFlexible managementError preventionTransmission systemsPacket communicationEnd system
In an access management method in a network including at least one end system, a packet communication unit for routing, and an access management server including an authentication function, a communication partner is authenticated for each session and a communication permitted by a communication partner is permitted by the access management server. A packet meeting a condition of a denied packet being denied by the communication partner is discarded by the packet communication unit.
Owner:FUJITSU LTD
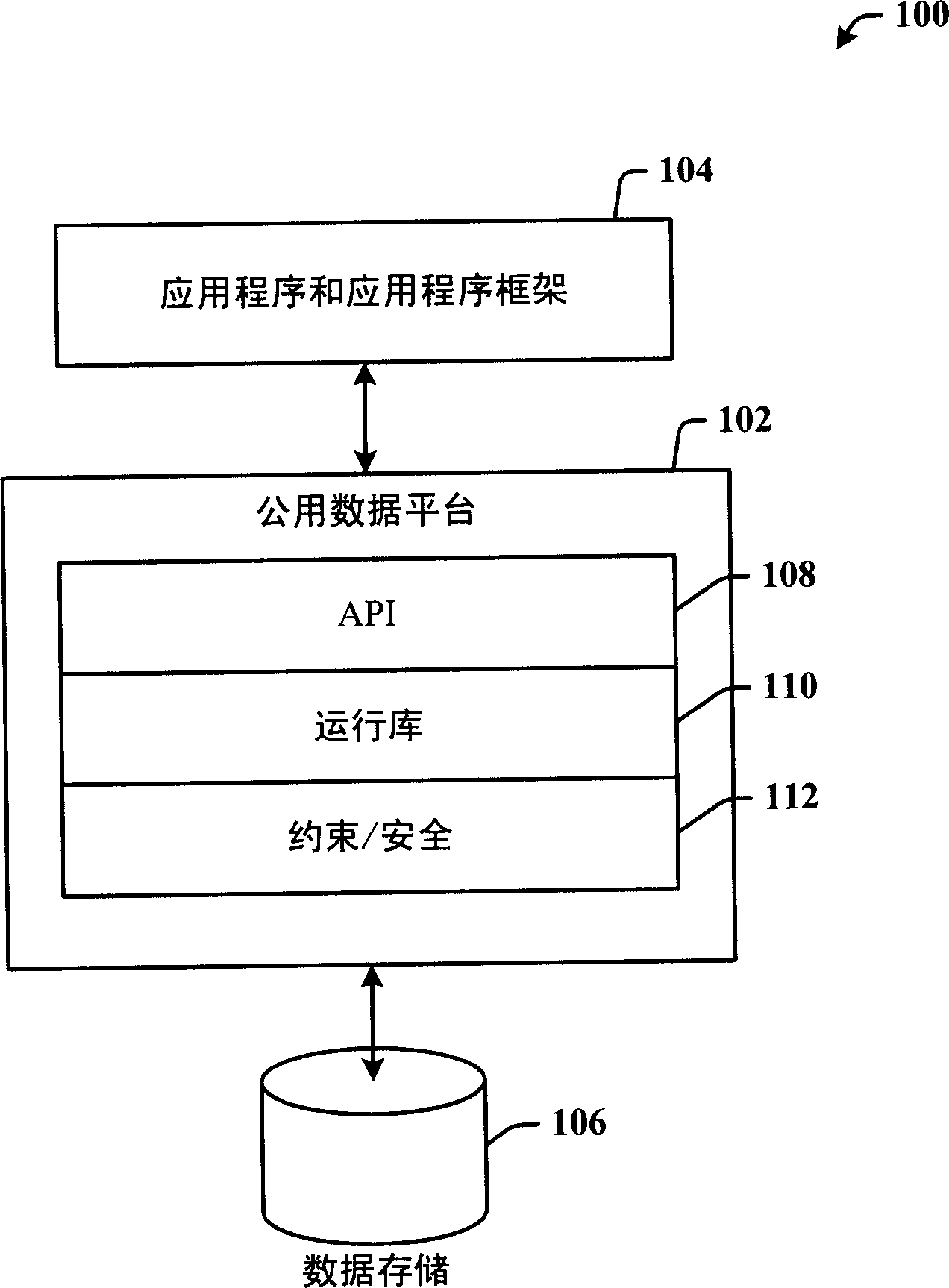
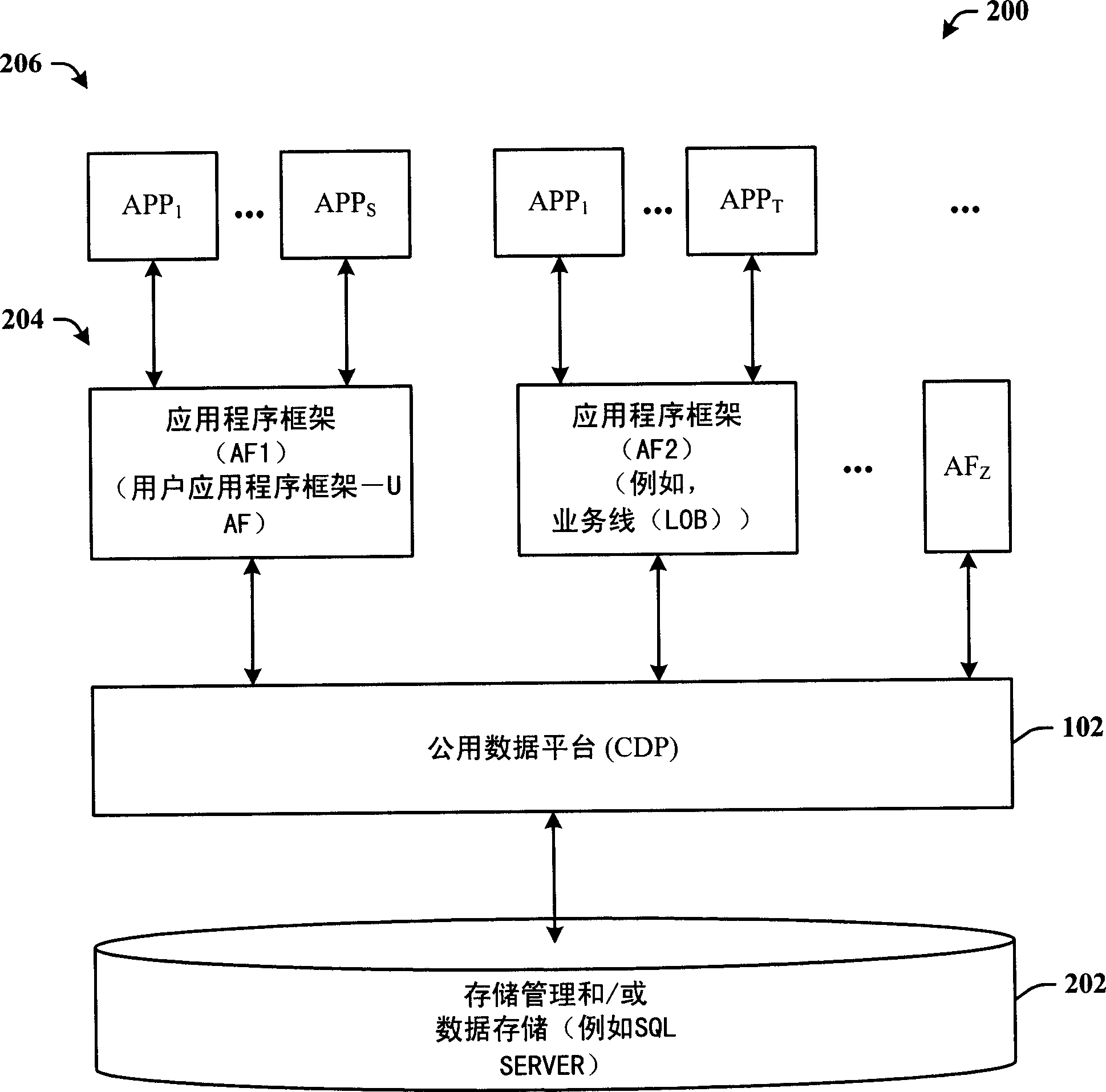
Platform for data services across disparate application frameworks
ActiveCN1828527ARich storageEasy to organizeVehicle arrangementsComputing modelsData platformUnstructured data
Data management between a common data store and multiple applications of multiple disparate application frameworks. A data storage component is provided that facilitates the storage of data, which data includes structured, semi-structured, and unstructured data. A common data platform interfaces to the data storage component to provide data services accessible by a plurality of disparate application frameworks, which data services allow a corresponding application of the different frameworks to access the data.
Owner:MICROSOFT TECH LICENSING LLC
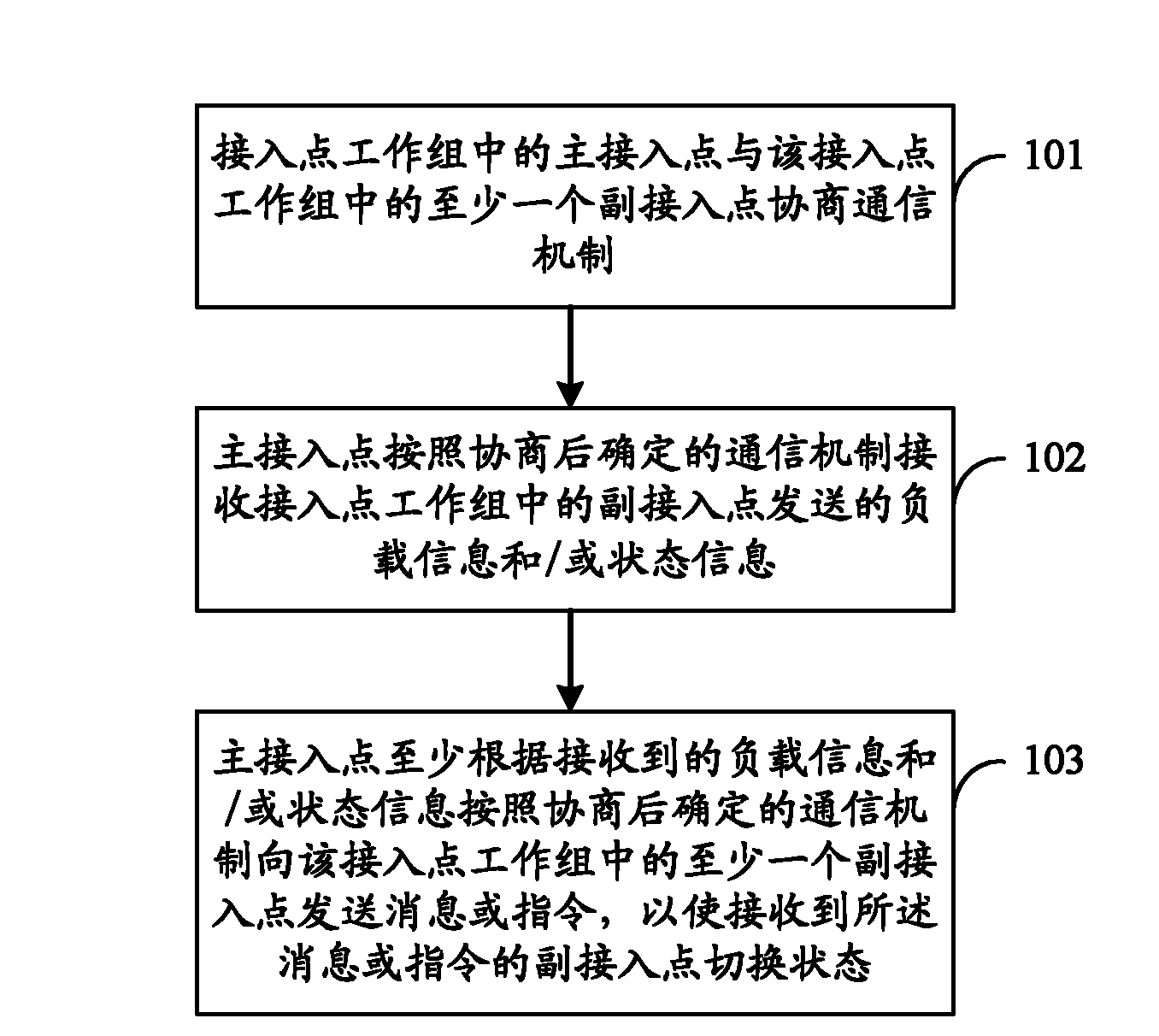
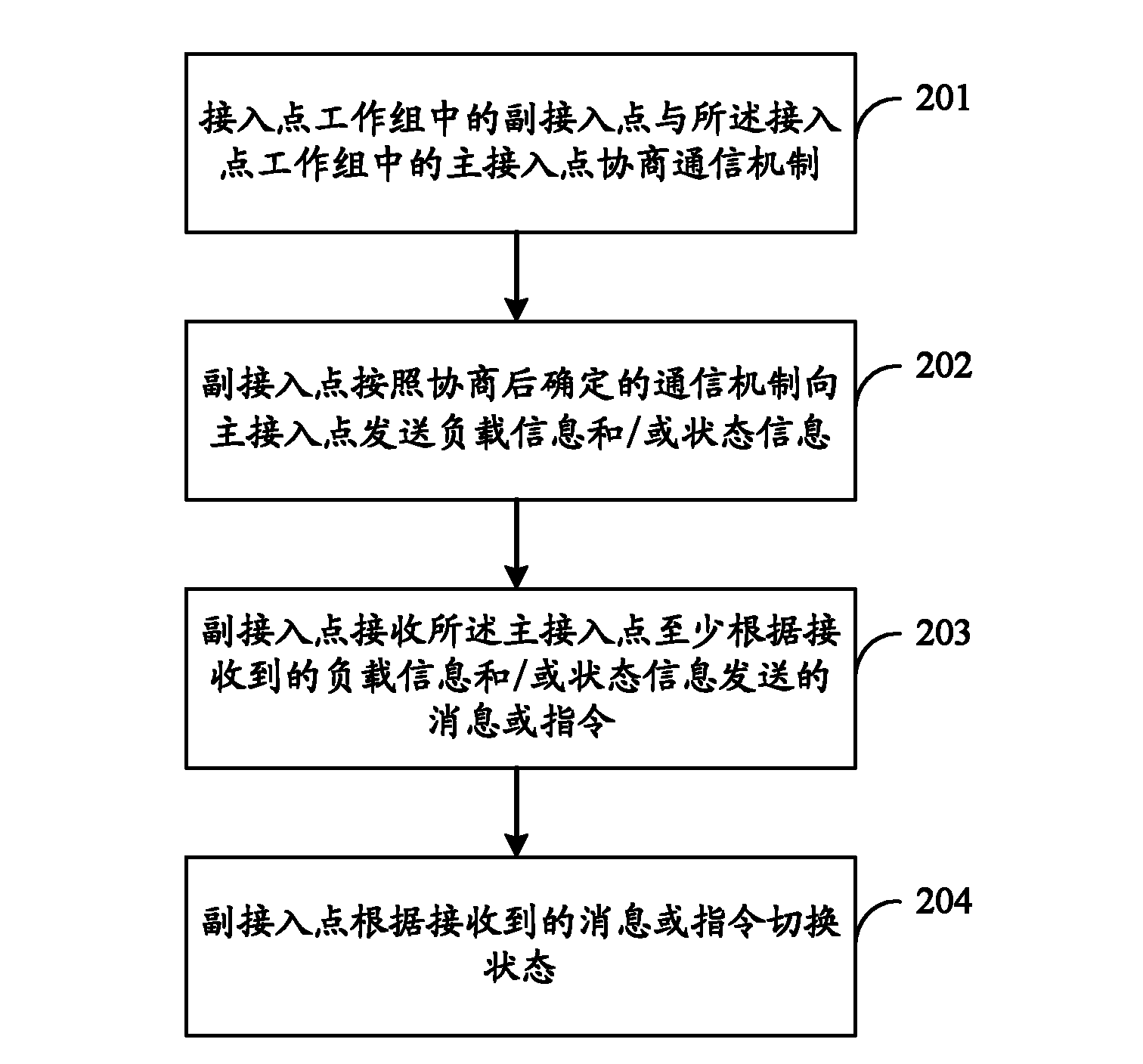
Access point and method for managing access point working group
InactiveCN102761938AFlexible managementMeet needsPower managementAssess restrictionTelecommunicationsComputer science
Owner:HUAWEI DEVICE CO LTD
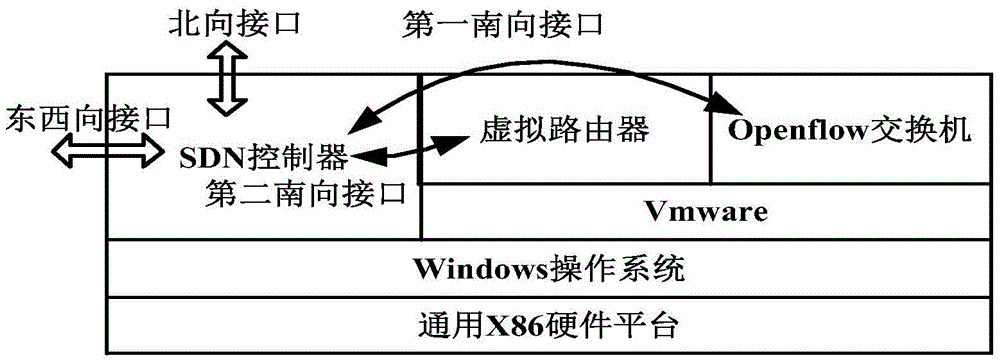
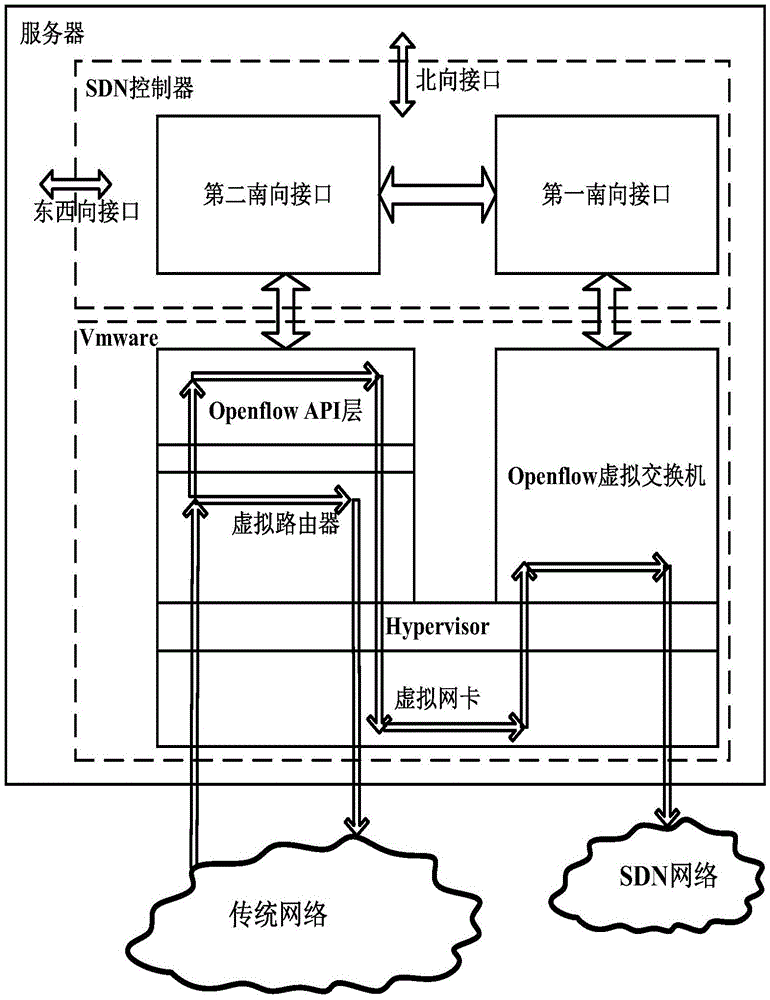
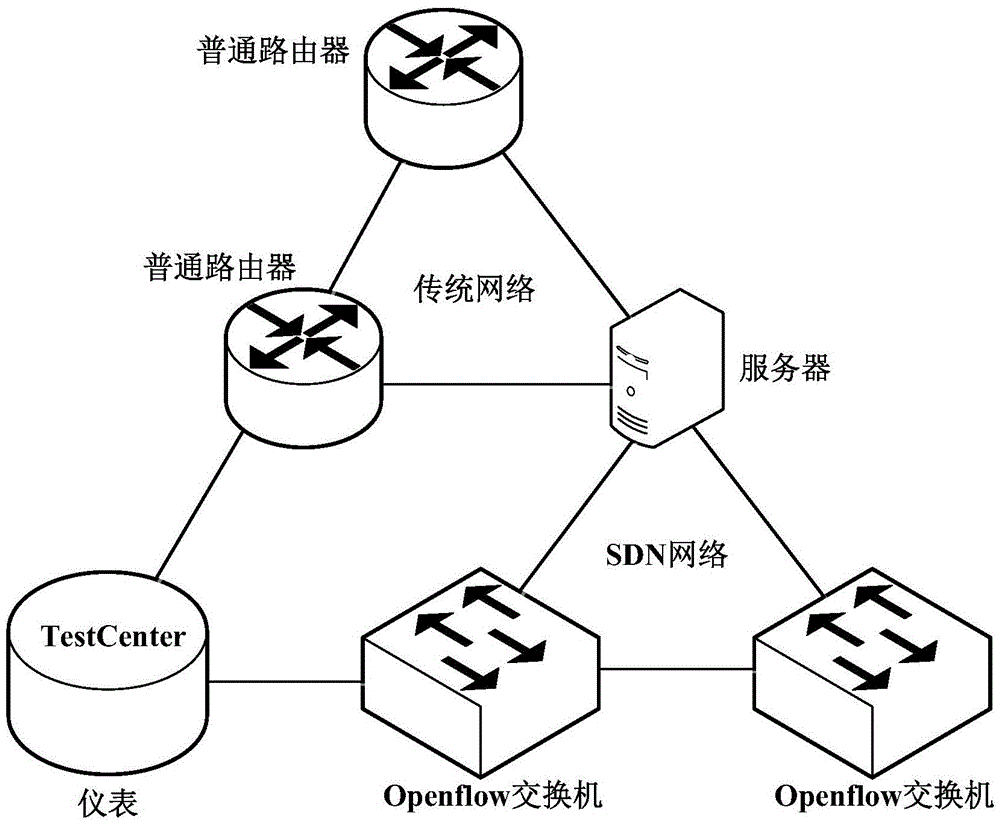
SDN (Software Defined Network) platform based on router virtualization and implementation method
ActiveCN105681191ARealize traffic interworkingGood data plane performanceData switching networksSoftware simulation/interpretation/emulationData virtualizationSoftware
The invention discloses an SDN (Software Defined Network) platform based on router virtualization and an implementation method, and relates to the field of virtualization technology, SDNs and cloud computation. The SDN platform comprises a virtual router, an Openflow switch and an SDN controller, wherein the SDN controller comprises an eastbound-westbound interface, a northbound interface, a first southbound interface and a second southbound interface; the second southbound interface is used for controlling data packet forwarding of the virtual router, and recording flow entry information of the virtual router; the first southbound interface is used for learning routing topology and a flow table of the second southbound interface in order to control rapid forwarding of the Openflow switch; and an application programming interface (API) layer based on an Openflow protocol is encapsulated on an integrated code layer of the virtual router. Through adoption of the SDN platform based on the router virtualization and the implementation method, high data forwarding performance and routing performance between an SDN network and a conventional network can be realized. The virtual router has the characteristics of high functional extensibility and high flexibility, and can be applied to the cloud computation easily.
Owner:FENGHUO COMM SCI & TECH CO LTD
Method and apparatus for encapsulating a virtual filer on a filer
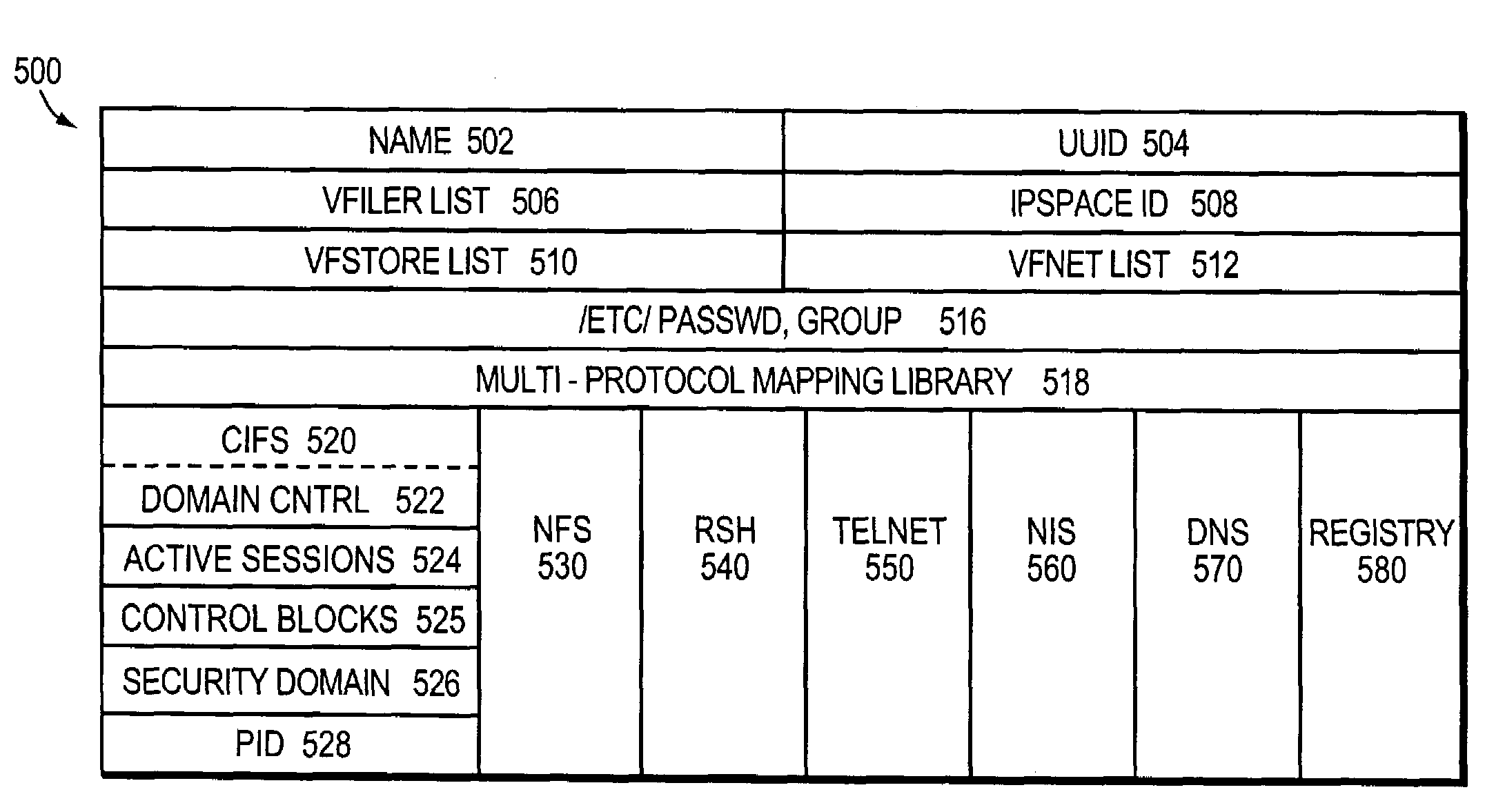
InactiveUS7269696B2Maximum flexibilityFine granularityDigital computer detailsMultiprogramming arrangementsOperational systemFile system
An architecture provides the ability to create and maintain multiple instances of virtual servers, such as virtual filers (vfilers), within a server, such as a filer. A vfiler is a logical partitioning of network and storage resources of the filer platform to establish an instance of a multi-protocol server. Each vfiler is allocated a subset of dedicated units of storage resources, such as volumes or logical sub-volumes (qtrees), and one or more network address resources. Each vfiler is also allowed shared access to a file system resource of a storage operating system. To ensure controlled access to the allocated and shared resources, each vfiler is further assigned its own security domain for each access protocol. A vfiler boundary check is performed by the file system to verify that a current vfiler is allowed to access certain storage resources for a requested file stored on the filer platform.
Owner:NETWORK APPLIANCE INC
Method for constructing problem difficulty level based on big data as well as device and service equipment
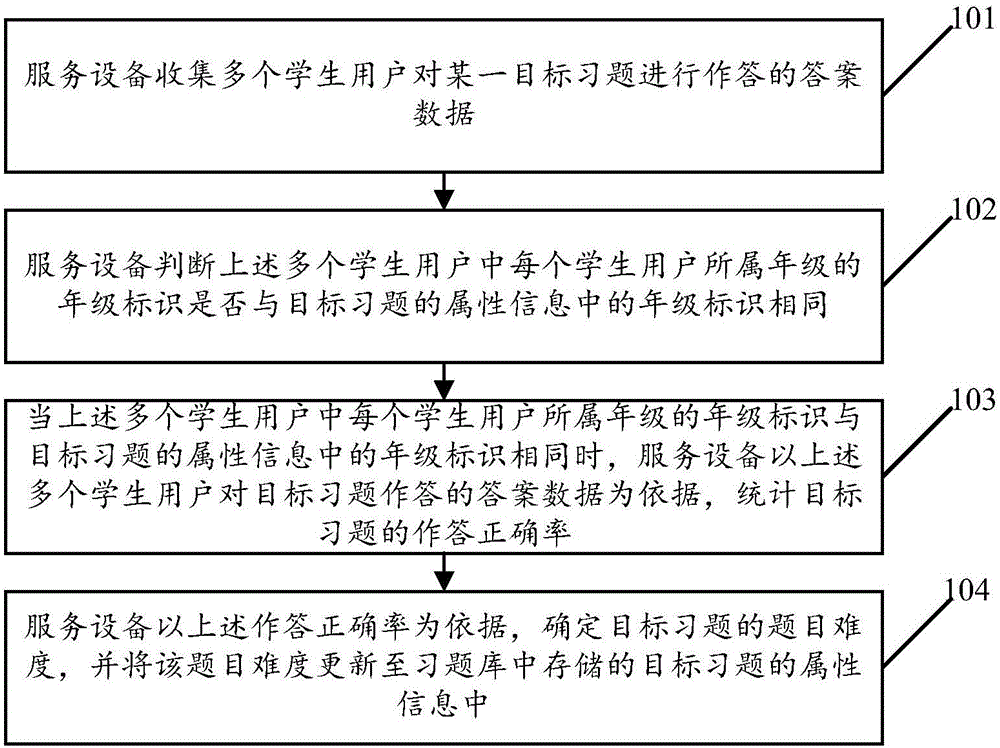
ActiveCN106781785AFlexible managementData processing applicationsElectrical appliancesData scienceBig data
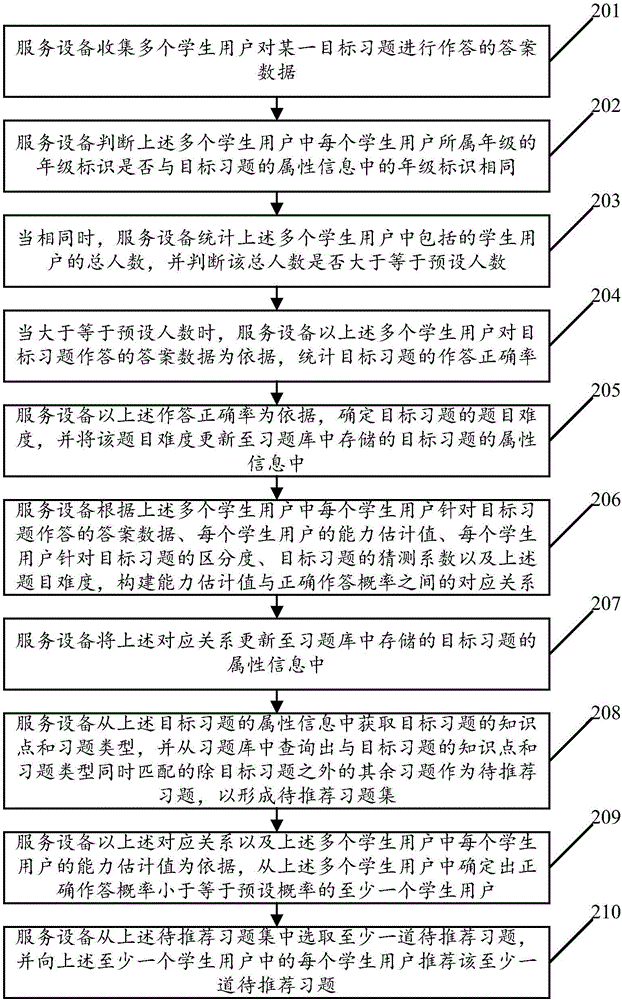
The embodiments of the invention relate to the technical field of computers, and disclose a method for constructing a problem difficulty level based on big data as well as a device and service equipment. The method comprises the following steps: collecting answer data for multiple student users to answer a certain target exercise; judging a grade identifier indicating the grade of each student in the multiple student users is same as that in attribute information of the target exercise or not; and when the grade identifier indicating the grade of each student in the multiple student users is same as that in the attribute information of the target exercise, calculating the answering accuracy of the target exercise on the basis of the answer data for the multiple student users to answer the target exercise; and determining the problem difficulty level of the target exercise on the basis of the calculated answering accuracy, and updating the determined problem difficulty level into the attribution information of the target exercise. By implementing the embodiments of the invention, the problem difficulty level of an exercise can be objectively defined, and dynamic and flexible management of the defined problem difficulty level can be achieved.
Owner:GUANGDONG XIAOTIANCAI TECH CO LTD
Method and system for testing performance parameter between random two terminal systems in IP network
InactiveCN101013975AReliable methodResolve Entity DownloadsData switching networksDatabase serverCommunication control
The invention discloses one method and system to realize the test on any two end systems property parameters in IP network in any place, which comprises the following steps: firstly downloading test programs to central register and manager person sets control strategy and sends test through browser; test servo starts mobile probe for test and sending test message to signal station to fulfill test result into data servo to display results.
Owner:中国人民解放军理工大学指挥自动化学院
Edge side assembler
InactiveUS7224698B2Improve abilitiesEasy accessDigital data processing detailsData switching by path configurationPersonalizationComputer network
Owner:IOT INNOVATIONS LLC +1
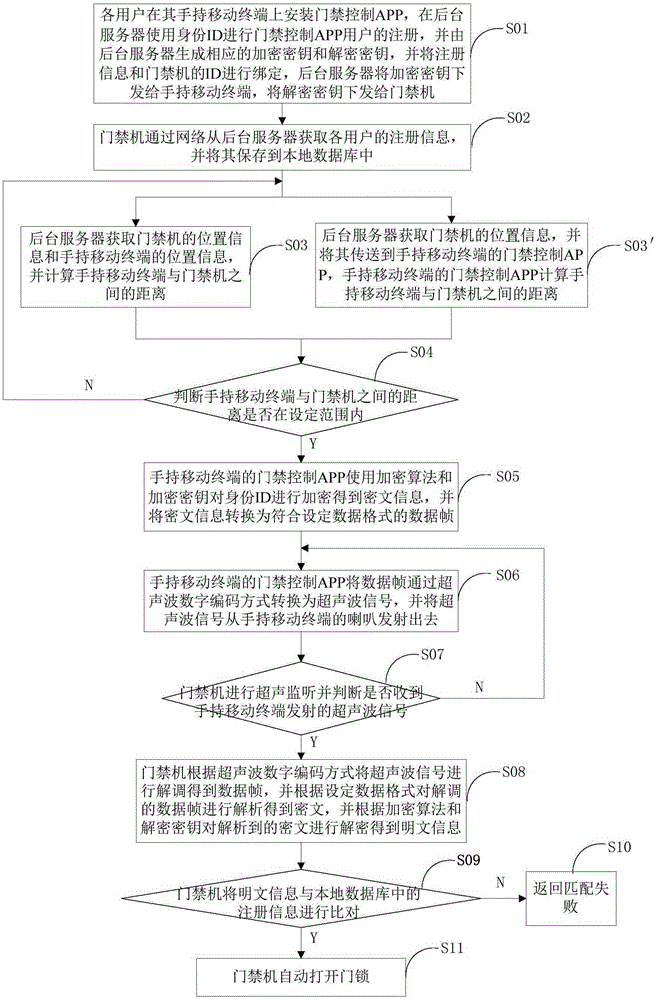
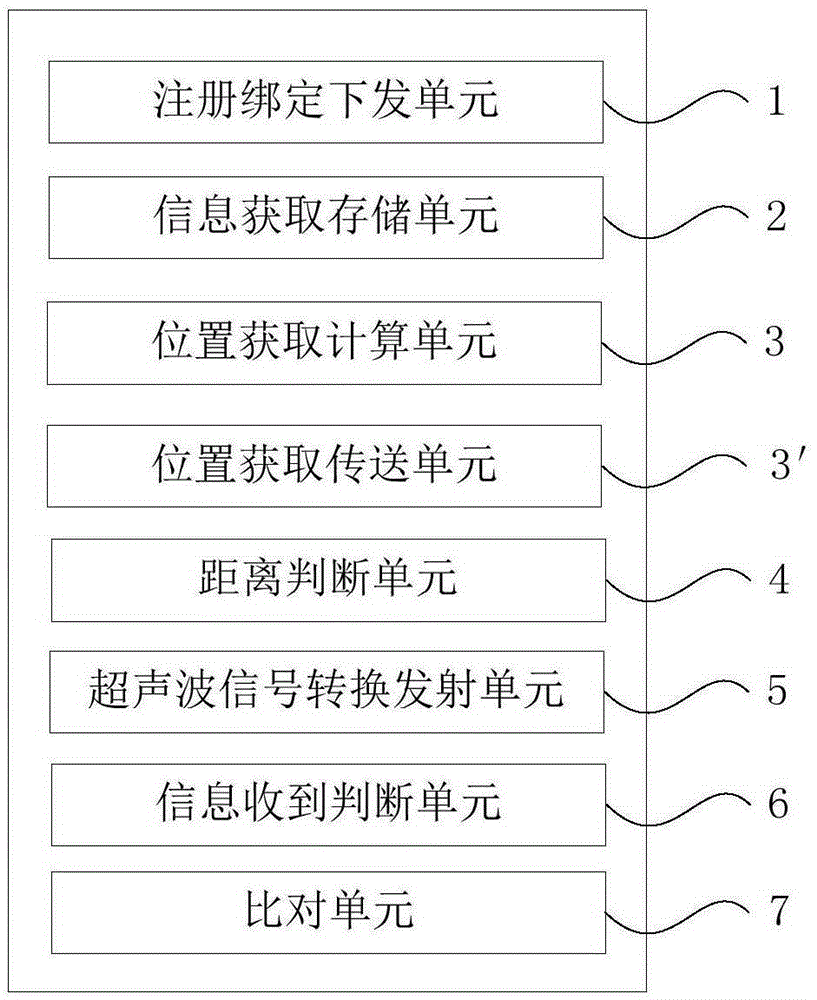
Method and device for identifying access control identity based on ultrasonic waves
ActiveCN105303659AImprove securityFlexible managementSonic/ultrasonic/infrasonic transmissionTelephonic communicationHand heldComputer terminal
The invention provides a method and a device for identifying access control identity based on ultrasonic waves. The method comprises the following steps of enabling each user to install an access control APP (application) at a hand-held mobile terminal, and use the ID (identity) to register as the user of the access control APP; generating an encrypting key and a decrypting key; enabling an access control machine to obtain the information of the users, and storing into a local database; when the distance between the hand-held mobile terminal and the access control machine is controlled within the setting range, using an encrypting algorithm and the encrypting key to encrypt the ID to obtain encrypting information, converting the encrypting information into a data frame, converting the data frame into an ultrasonic signal by an ultrasonic digital encoding type, transiting the ultrasonic signal via a loudspeaker, enabling the access control machine to receive the ultrasonic signal and convert the ultrasonic signal into the data frame, demodulating, and decrypting to obtain a plain text; if the plain text is matched with the information of the local database, automatically opening a door. The method and the device for identifying the access control identify based on the ultrasonic waves have the beneficial effects that the safety is higher, the use cost is reduced, and the reliability is higher.
Owner:SHENZHEN YUDI TECH CO LTD
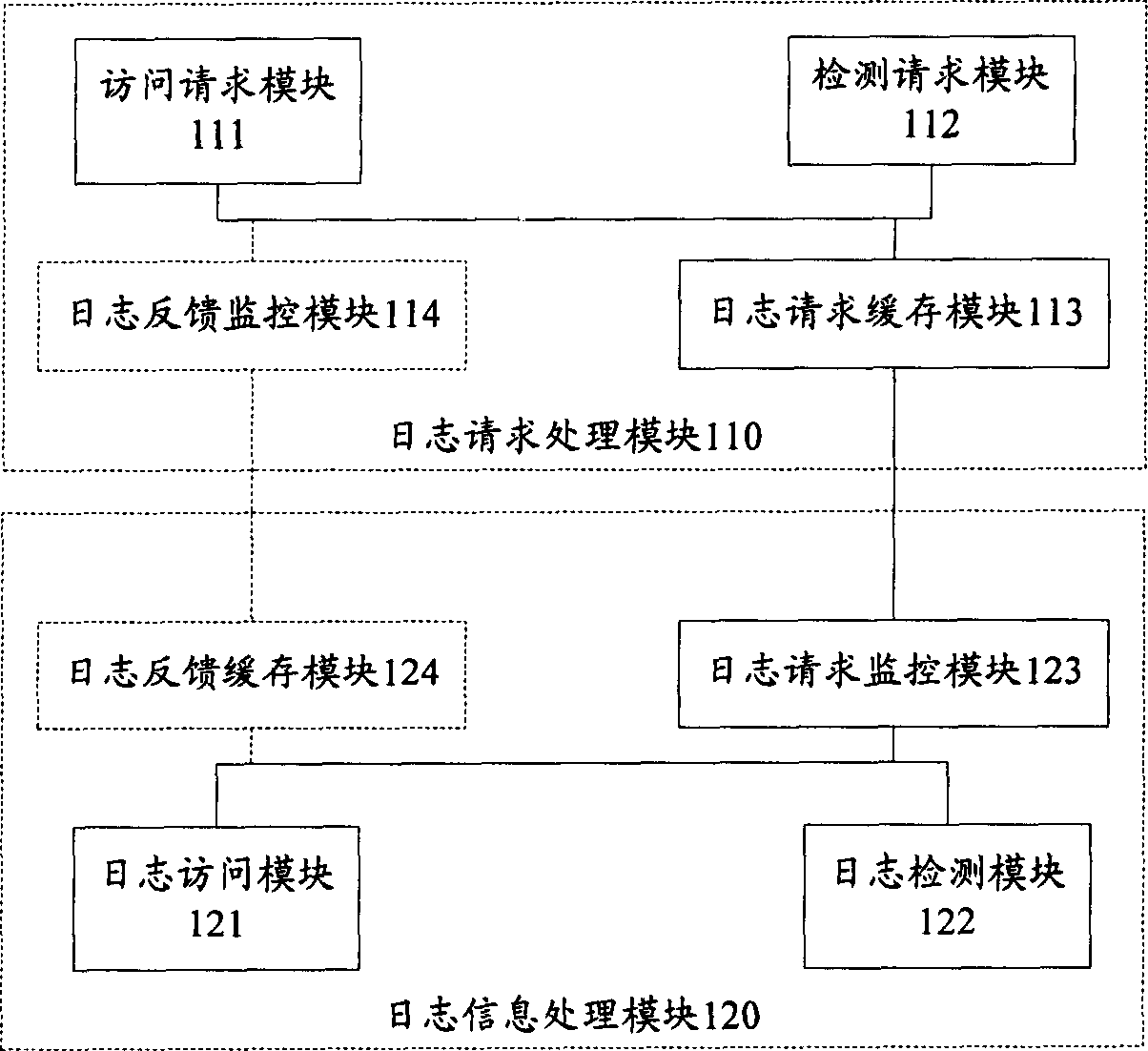
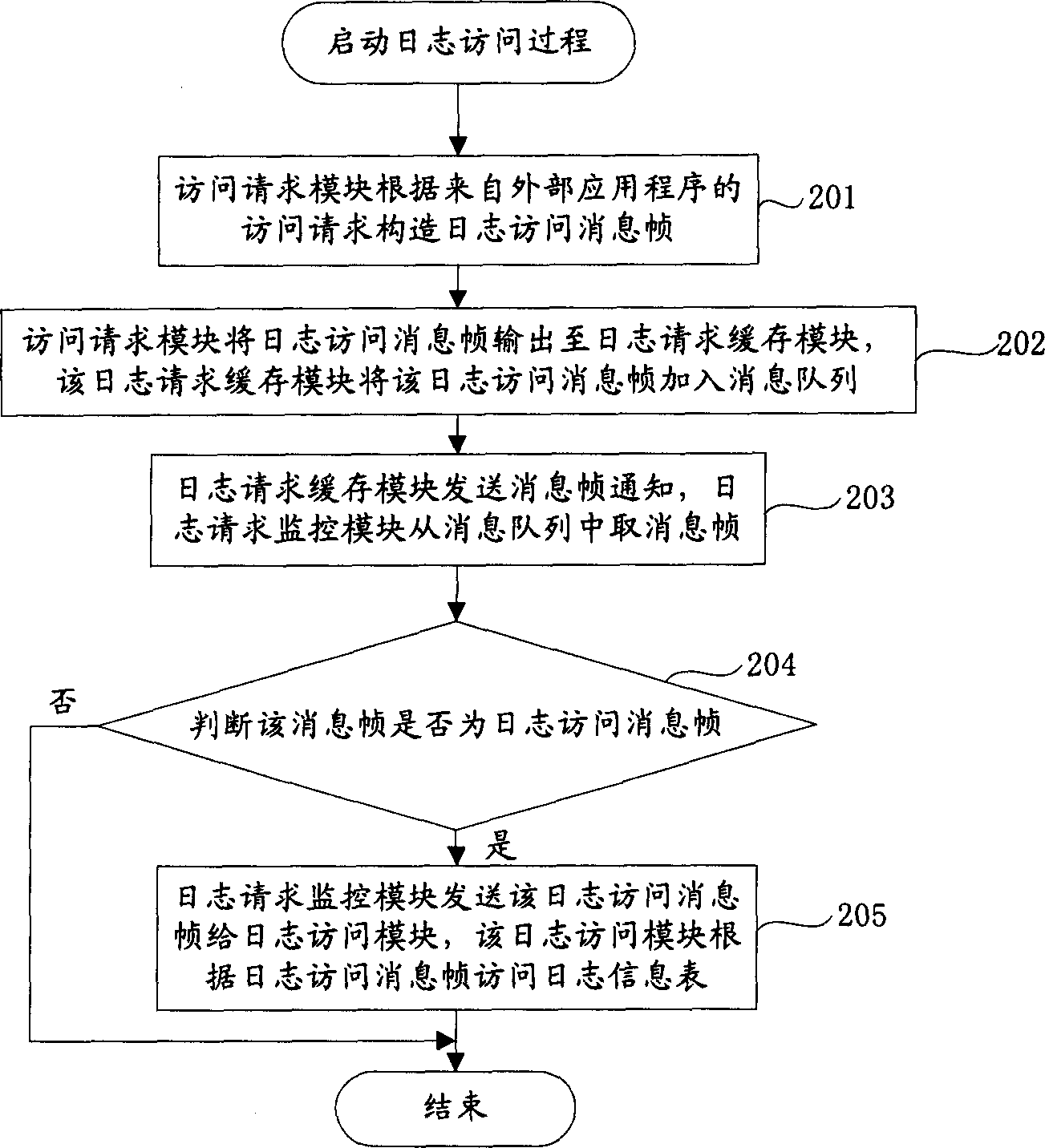
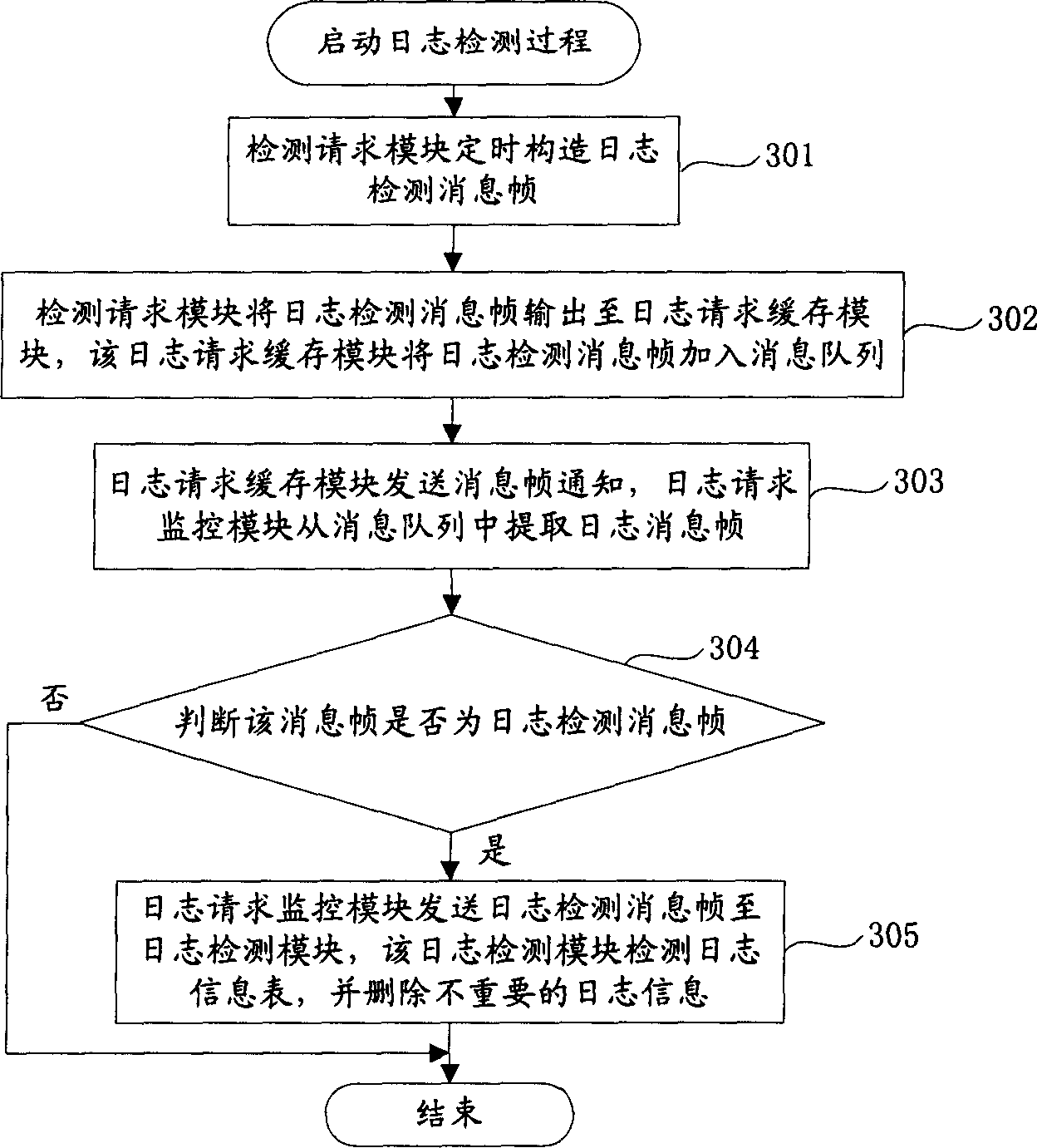
Log information management method and system
InactiveCN1815451AFlexible managementEasy to manageRedundant operation error correctionProcess moduleManagement system
The method divides log information management system into log request process module and log information process module. Log detection process of the method includes (1) the log request process module constructs and outputs log detection request to the log information process module; (2) after detecting the log detection request, the log information process module detects stored state of log information in log information base, determines whether the detected stored state of log information exceeds prearranged configured threshold of log stored state; if yes, deleting log information with attribute being as unimportant in log information base; otherwise, ending current process. The invention realizes detection of log information, deletes unimportant log information automatically.
Owner:HUAWEI TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com