Method and systems for controlling access to computing resources based on known security vulnerabilities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] As used here in, examples and illustrations, as well as descriptive terminology such as “exemplary” and “illustrative” and variants thereof, are descriptive and non limiting.
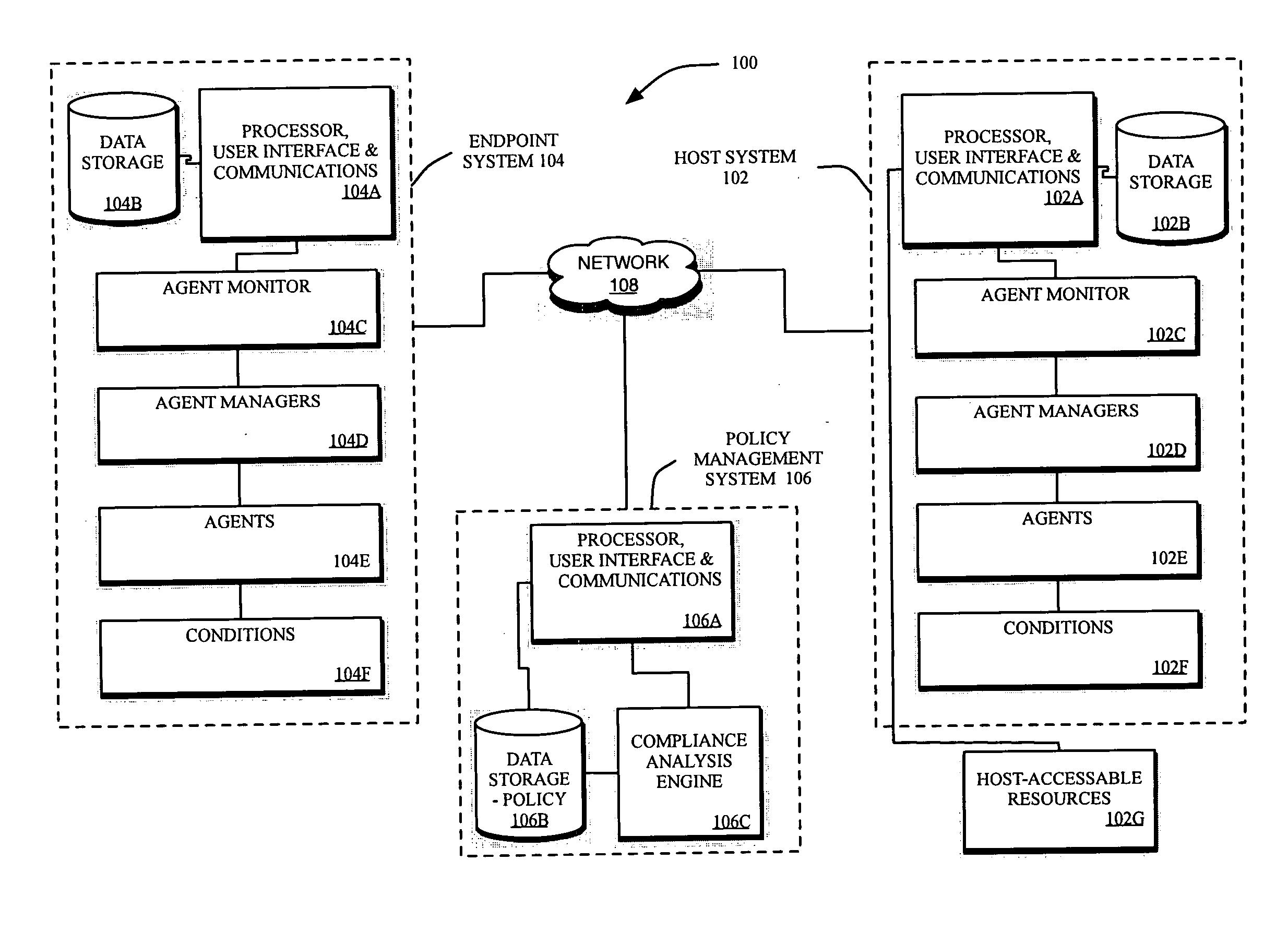
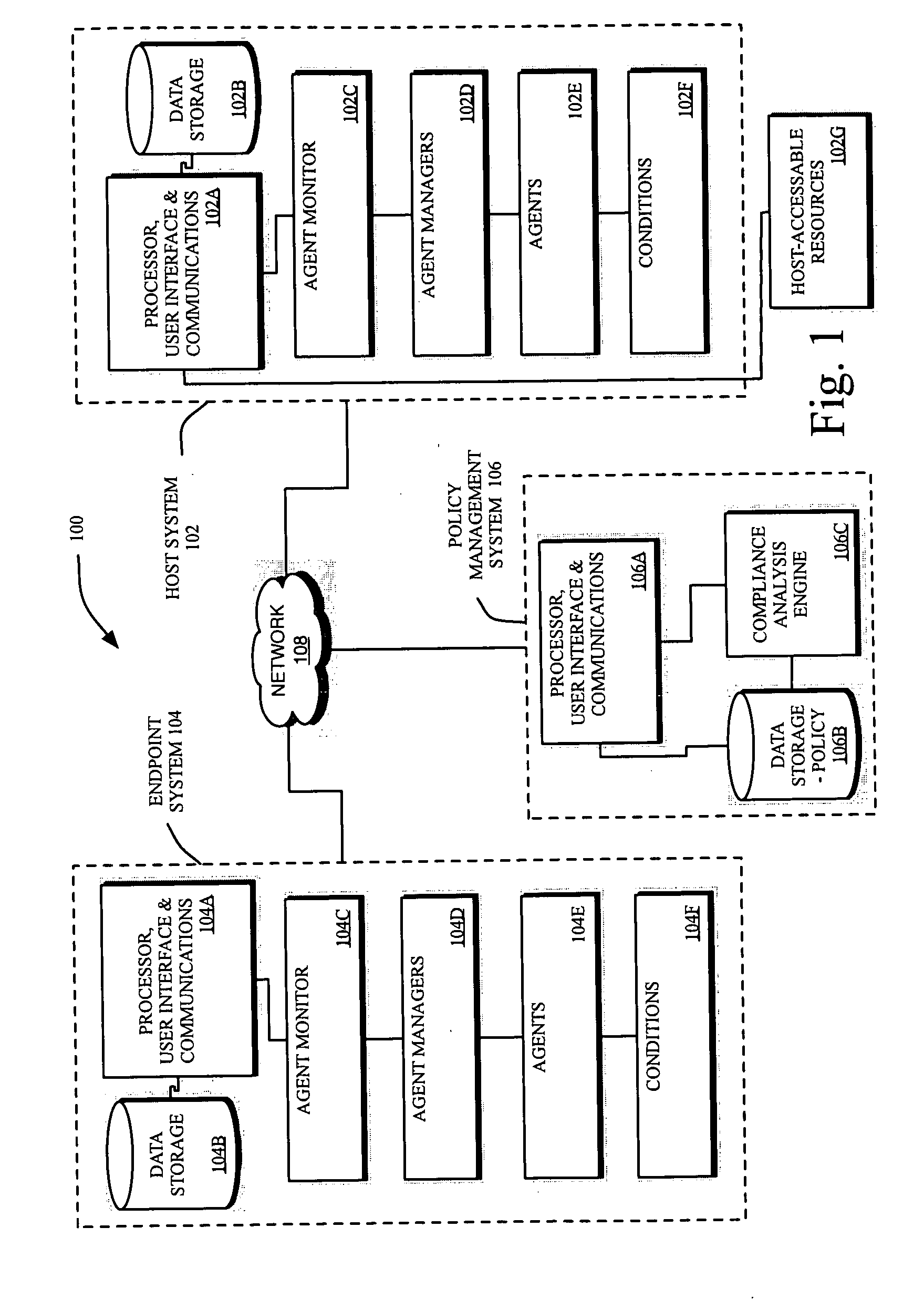
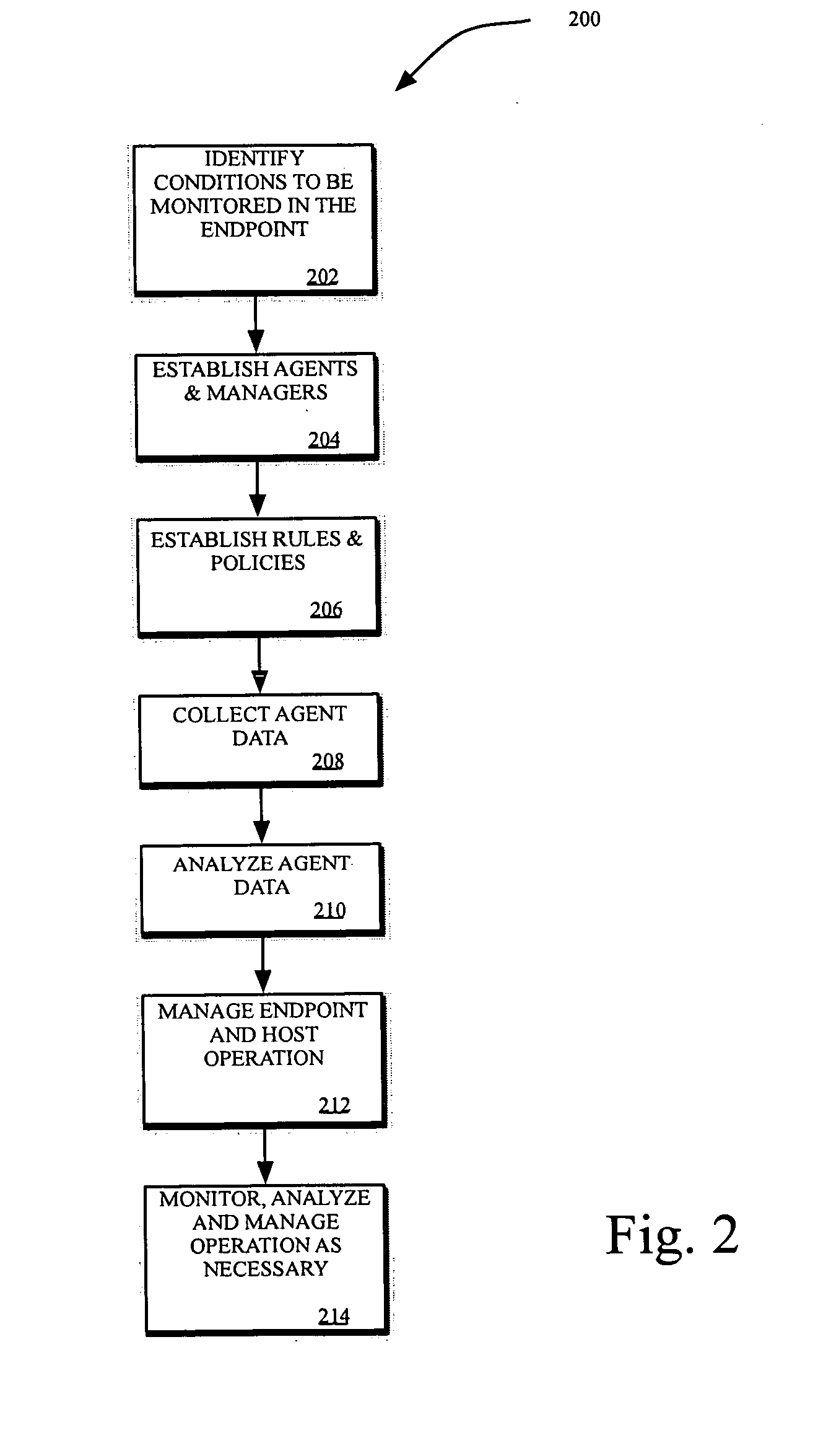
[0029] For purposes of describing the present invention, the following specification is arranged topically, in accordance with the following topics: [0030] Overview [0031] Description Of The System [0032] Establishing Agents And Managers [0033] Establishing Rules And Policies [0034] Administrator Policy Configuration [0035] Integration With Vulnerability Scoring Systems [0036] Analyzing Agent—Collected Condition Data [0037] EndPoint Compliance Assessment Algorithms [0038] Matrix Analysis Algorithm [0039] Business Rules—Based Analytical Model For Policy Enforcement [0040] Boolean Table—Based Analytic Model For Policy Enforcement [0041] Scoring—Based Analytical Model For Policy Enforcement [0042] Individual Agent Score Threshold Analysis And Enforcement [0043] Composite Agent Scoring, Threshold Analysis An...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com