Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
377 results about "Enterprise information system" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
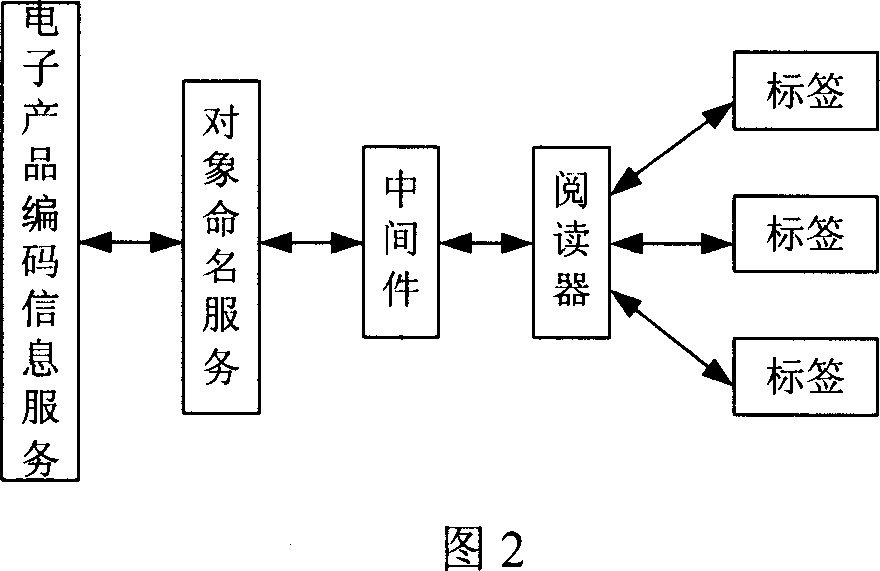
An enterprise information system (EIS) is any kind of information system which improves the functions of enterprise business processes by integration. This means typically offering high quality of service, dealing with large volumes of data and capable of supporting some large and possibly complex organization or enterprise. An EIS must be able to be used by all parts and all levels of an enterprise.
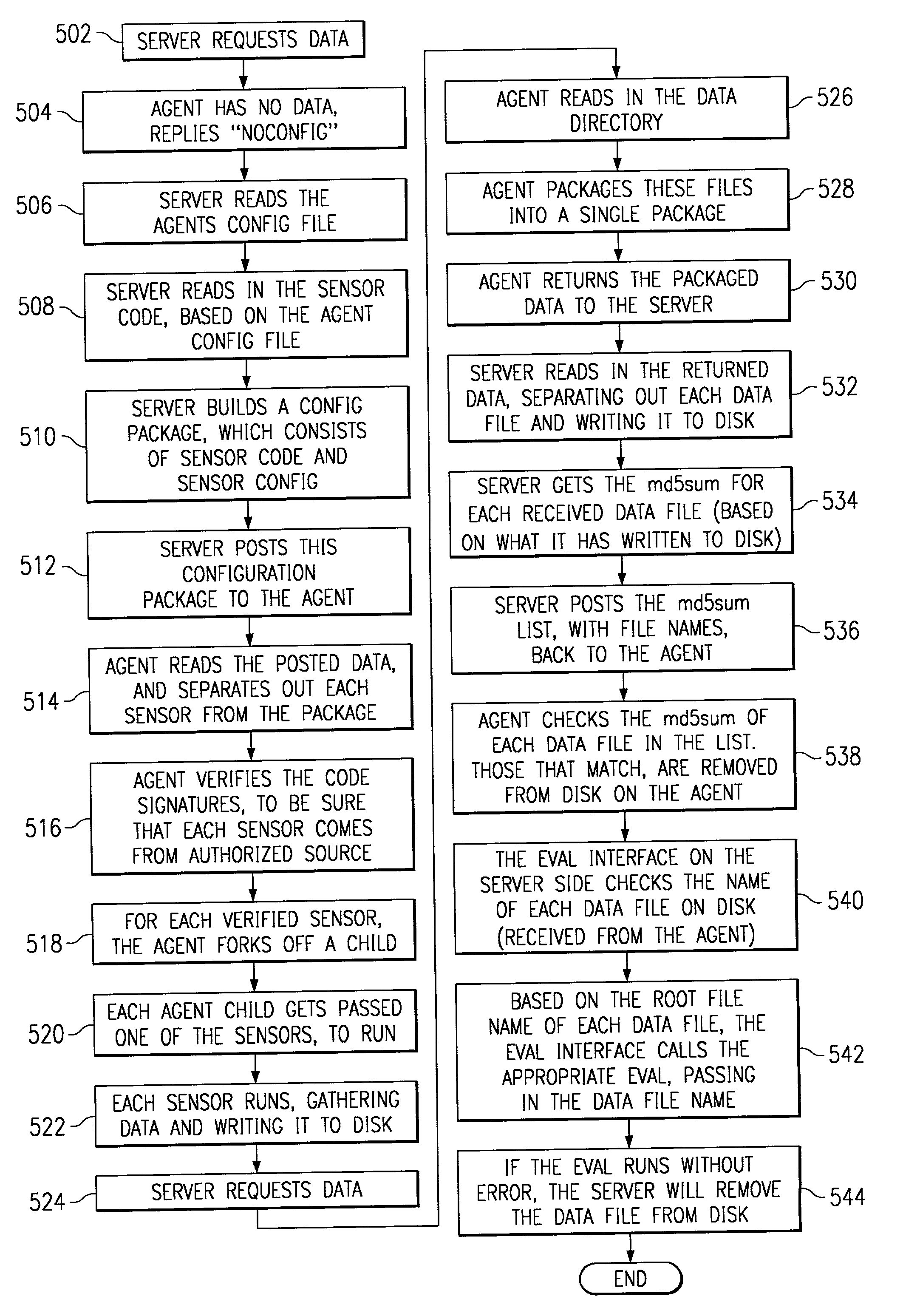
Scalable system for monitoring network system and components and methodology therefore
InactiveUS20020078382A1Memory loss protectionDigital computer detailsScalable systemSecurity software
The present invention is a security software methodology and system that takes an internal approach to mitigating security risks from authorized and unauthorized users. The security software system uses the methodology of monitoring, in great detail, any configuration changes made to information systems within a network. These systems and applications include web servers, firewalls, proxy servers, log servers, intrusion detection software systems, routers and any other device or application which can be considered a part of the enterprise information system infrastructure.
Owner:SECURITY & INTRUSION DETECTION RES LABS
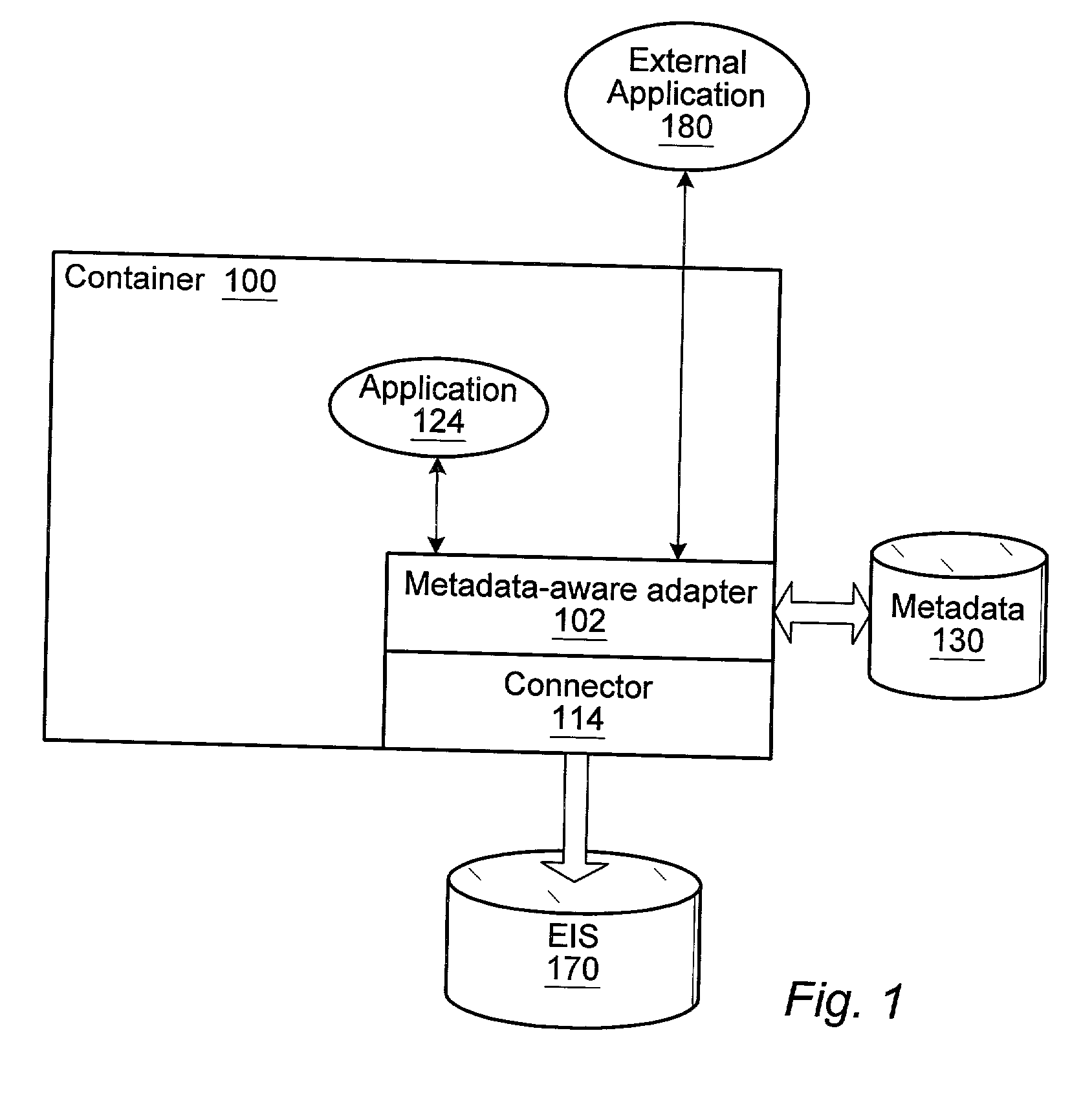
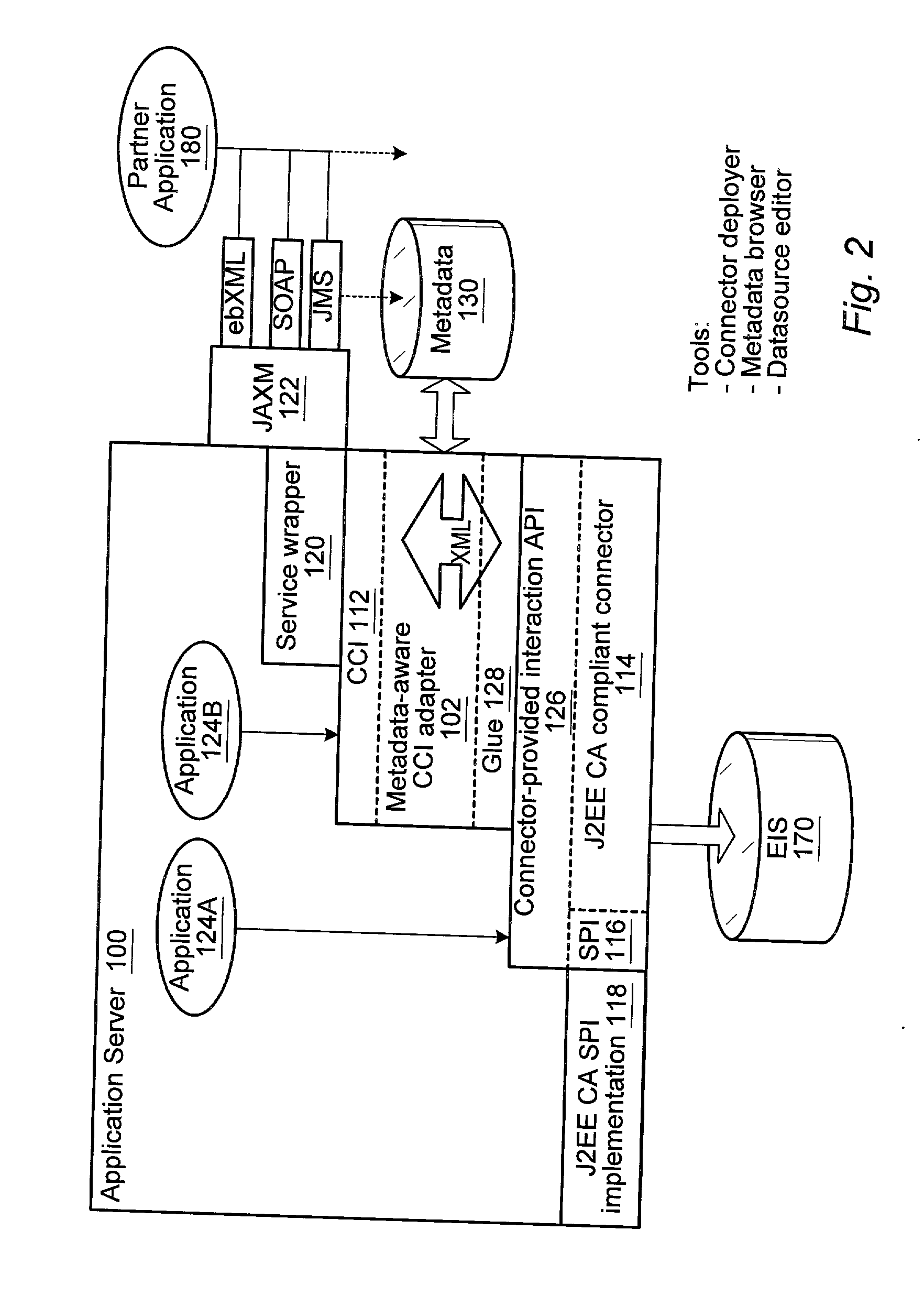
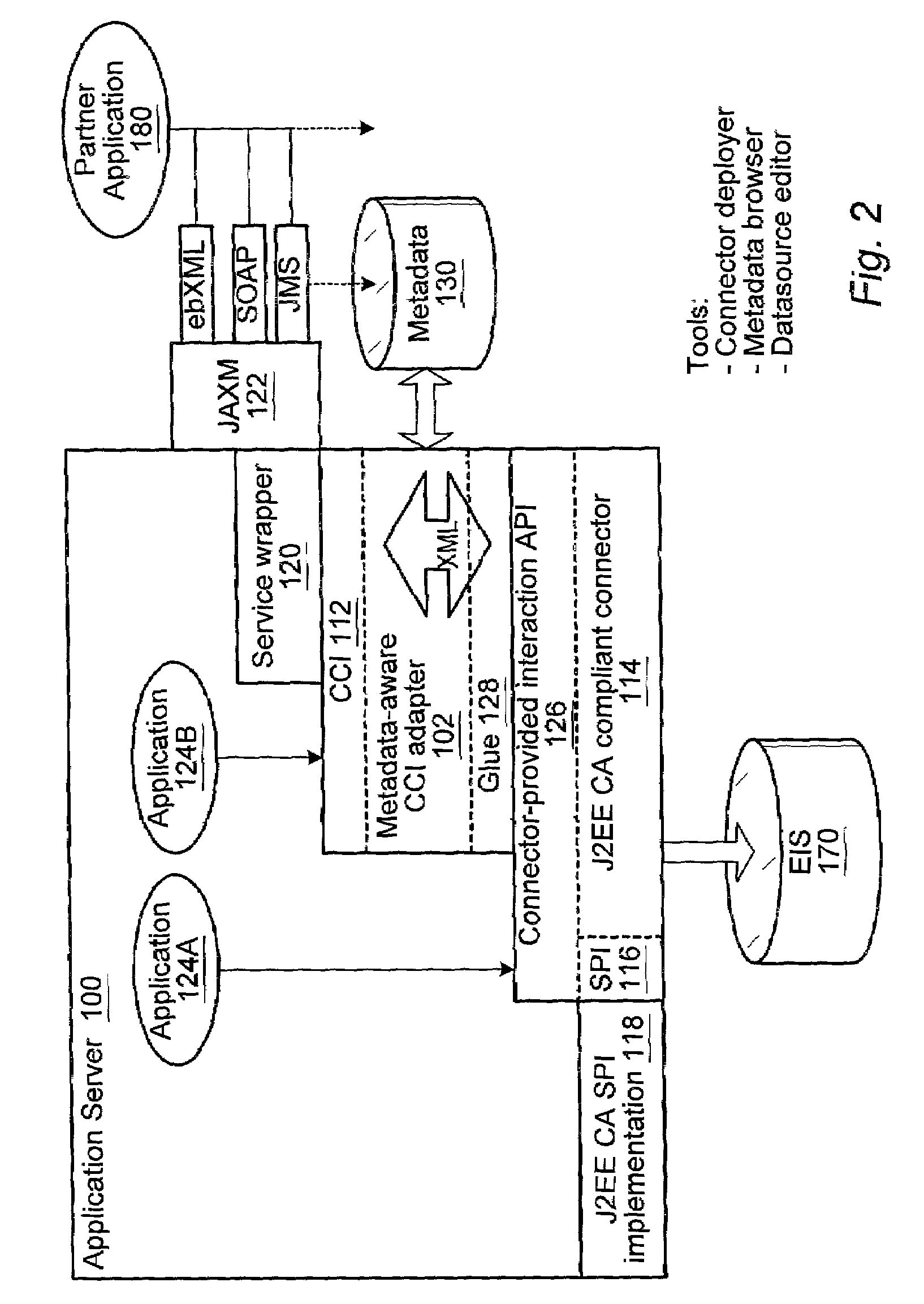
Metadata-aware enterprise application integration framework for application server environment
ActiveUS20030018832A1Data processing applicationsDistributed object oriented systemsEnterprise application integrationApplication server
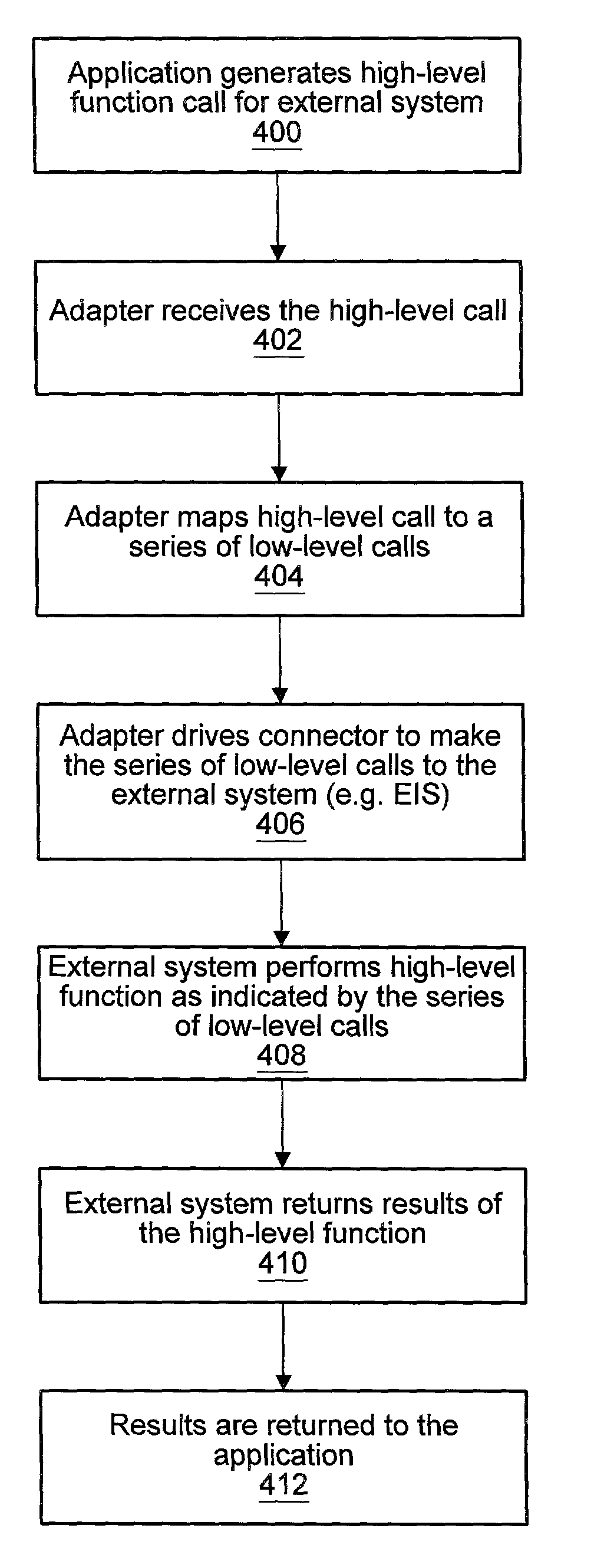
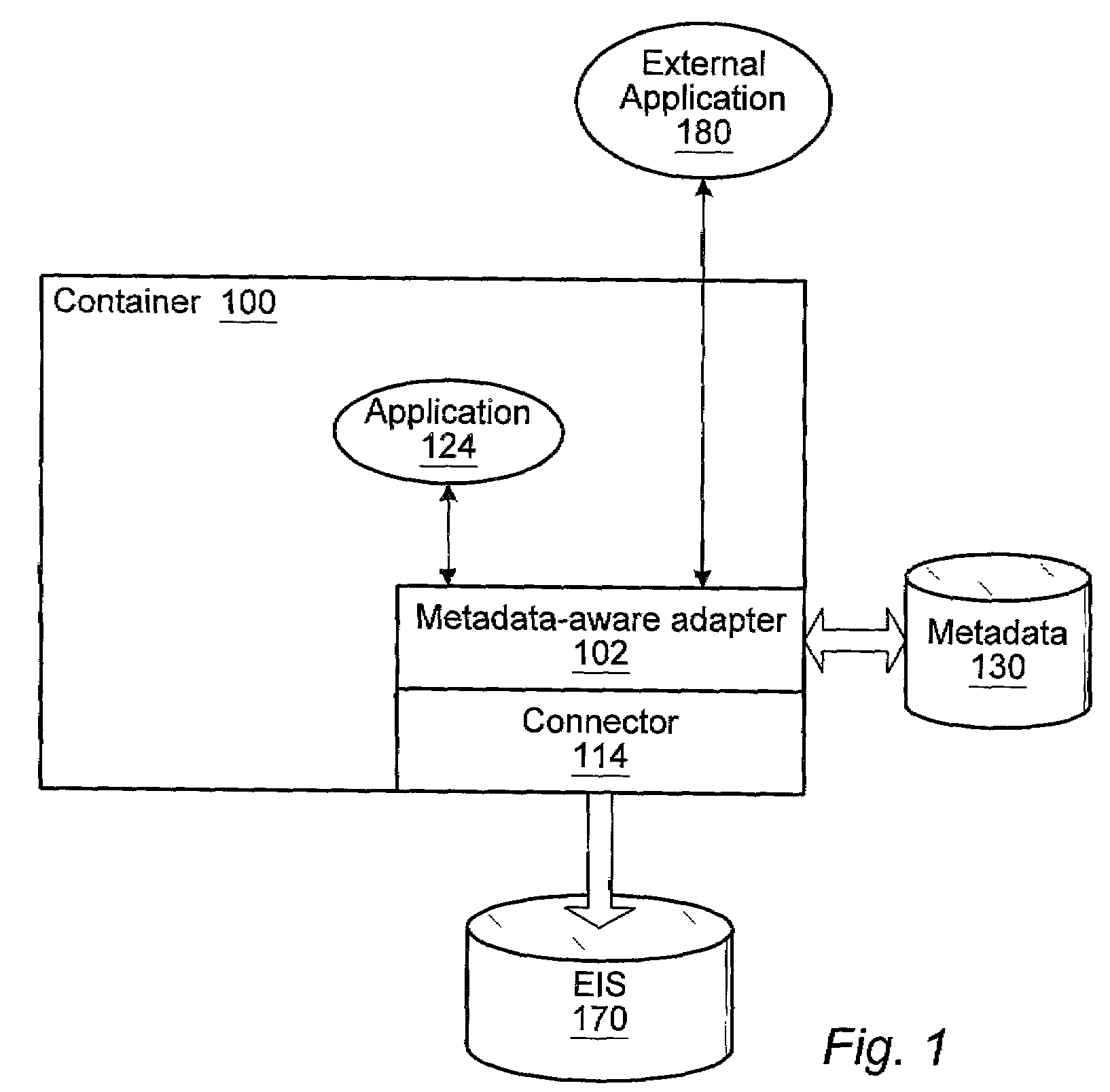
A metadata-aware Enterprise Application Integration (EAI) framework for an application server environment. The framework allows the connector writer to connect to a system using a low-level API. The framework provides a space in a connector in which to define high-level functions. Using the framework, the user can mine metadata for the functions and generate a description of each high-level function that can be dropped into the framework and appear as a high-level function invokable through the connector. This high-level function manifestation, when invoked, drives the low-level API provided by the connector. An adaptive layer may wrap a native Common Client Interface (CCI) exposed by a connector to provide an abstract connector that allows a higher-level abstraction of external Enterprise Information Systems (EIS). The adaptive layer may interpret metadata to model an external EIS as a logical data source. The adaptive layer may be referred to as a metadata-aware CCI adapter.
Owner:ORACLE INT CORP
Distributed Asset Management System and Method
ActiveUS20090007098A1Highly independentMultiple digital computer combinationsProgram loading/initiatingData sourceApplication software
Owner:CONNECTIF SOLUTIONS
Connection architecture for a mobile network
InactiveUS20070027832A1Key distribution for secure communicationSpatial transmit diversityMobile deviceMobile Web
A real-time communication architecture establishes a continuous connection between an enterprise network and a communication management system. The connection is continuously held open allowing mobile devices real-time access to enterprise email systems. The real-time communication architecture can support an entire enterprise email system or individual email users. The foregoing and other objects, features and advantages of the invention will become more readily apparent from the following detailed description of a preferred embodiment of the invention which proceeds with reference to the accompanying drawings.
Owner:SEVEN NETWORKS INC
Metadata-aware enterprise application integration framework for application server environment
ActiveUS7152090B2Data processing applicationsDigital data processing detailsEnterprise application integrationApplication server
A metadata-aware Enterprise Application Integration (EAI) framework for an application server environment. The framework allows the connector writer to connect to a system using a low-level API. The framework provides a space in a connector in which to define high-level functions. Using the framework, the user can mine metadata for the functions and generate a description of each high-level function that can be dropped into the framework and appear as a high-level function invokable through the connector. This high-level function manifestation, when invoked, drives the low-level API provided by the connector. An adaptive layer may wrap a native Common Client Interface (CCI) exposed by a connector to provide an abstract connector that allows a higher-level abstraction of external Enterprise Information Systems (EIS). The adaptive layer may interpret metadata to model an external EIS as a logical data source. The adaptive layer may be referred to as a metadata-aware CCI adapter.
Owner:ORACLE INT CORP
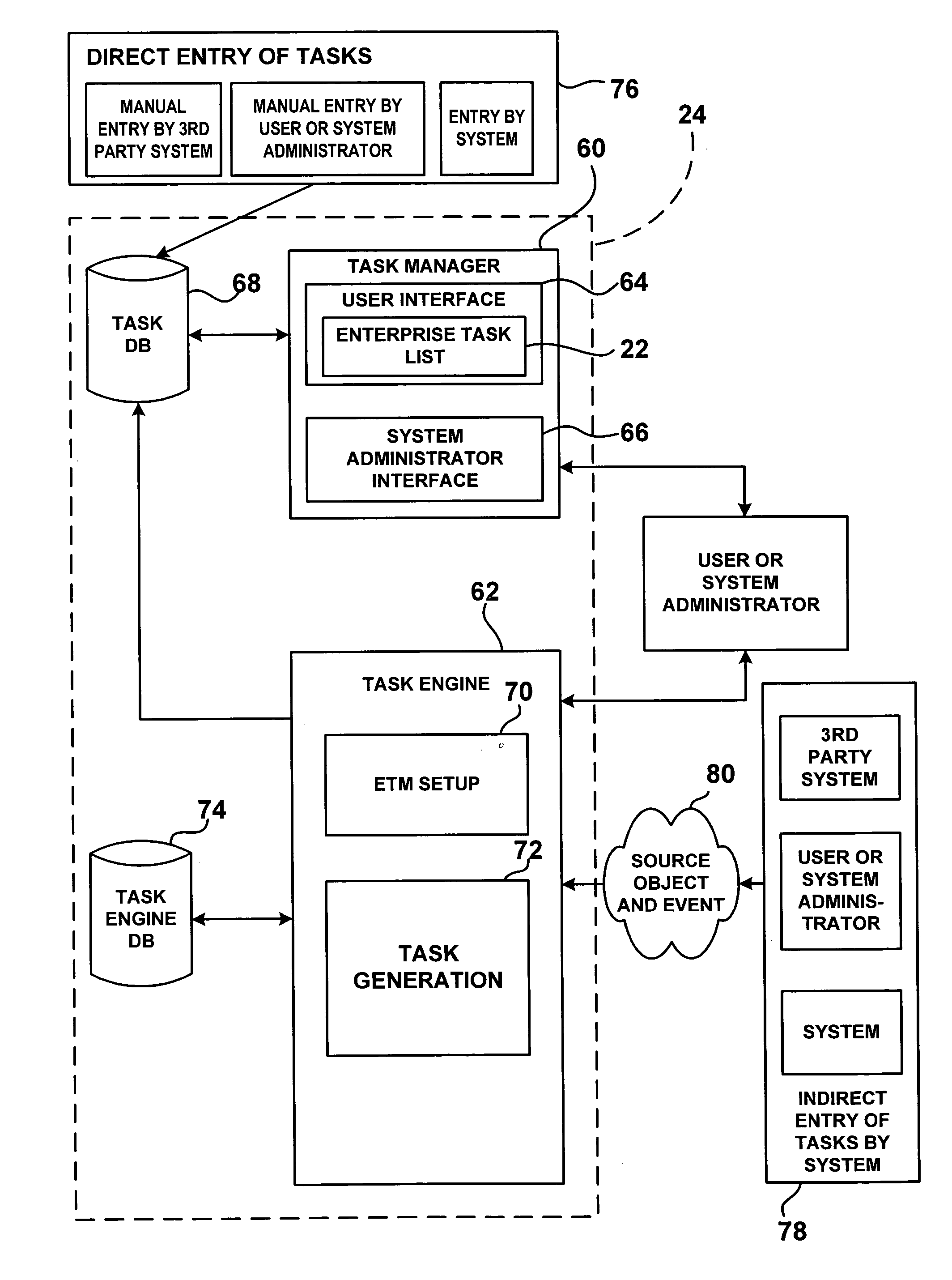
Enterprise task manager
ActiveUS20050028158A1Automatically performMultiprogramming arrangementsSpecific program execution arrangementsTask managementUser interface
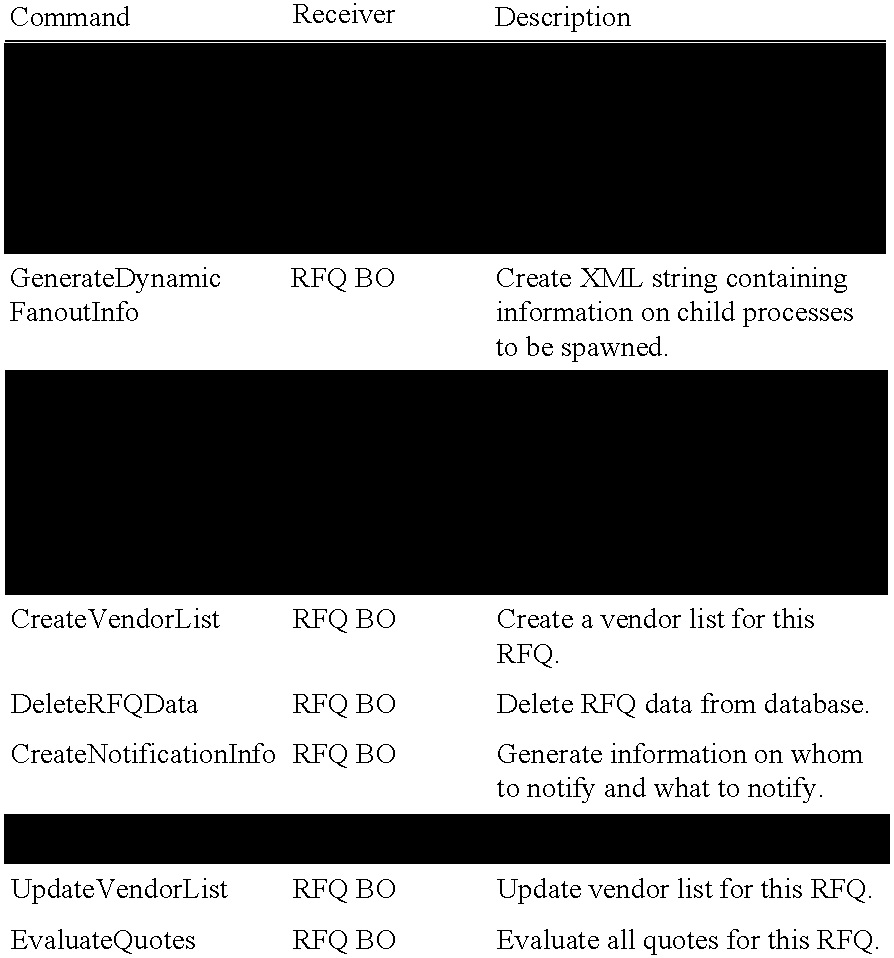
An enterprise task management system (24) for managing data maintenance tasks across multiple applications. System (24) includes a task manager module (60) and a task engine module (62). Task manager module (60) includes two primary graphical user interfaces: a user interface (64) and a system administrator interface (66). User interface (64) includes an enterprise task list (22), a preview text box (96), and an instructions text box (100). Task engine module (62) includes the following sub-modules: ETM system setup (70) and task generation (72). Another aspect of the present invention is a system architecture for centrally managing the creation of tasks. Additional aspects of the present invention include a method of generating data maintenance tasks within an enterprise information system, a method of populating task data fields using task templates, and a method of automatically generating and performing tasks within system (24).
Owner:IDX INVESTMENT CORP
Method and system for business program and service planning, delivery and management
InactiveUS20130339099A1Facilitate establishmentFacilitate recordationResourcesService planningStructured communication
Methods and systems for structured communications between business planners to capture and profile a planning and management method as well as tasks, results, and performance indicators for tracking the achievement of a business strategy, goal, or mandate are outlined for an enterprise or an enterprise and its partner organizations. The systems and methods can be used to accelerate the configuration of management information systems and / or enterprise information systems in accordance with those profiles for the purposes of planning, delivering and managing programs and services.
Owner:AIDROOS DAOOD
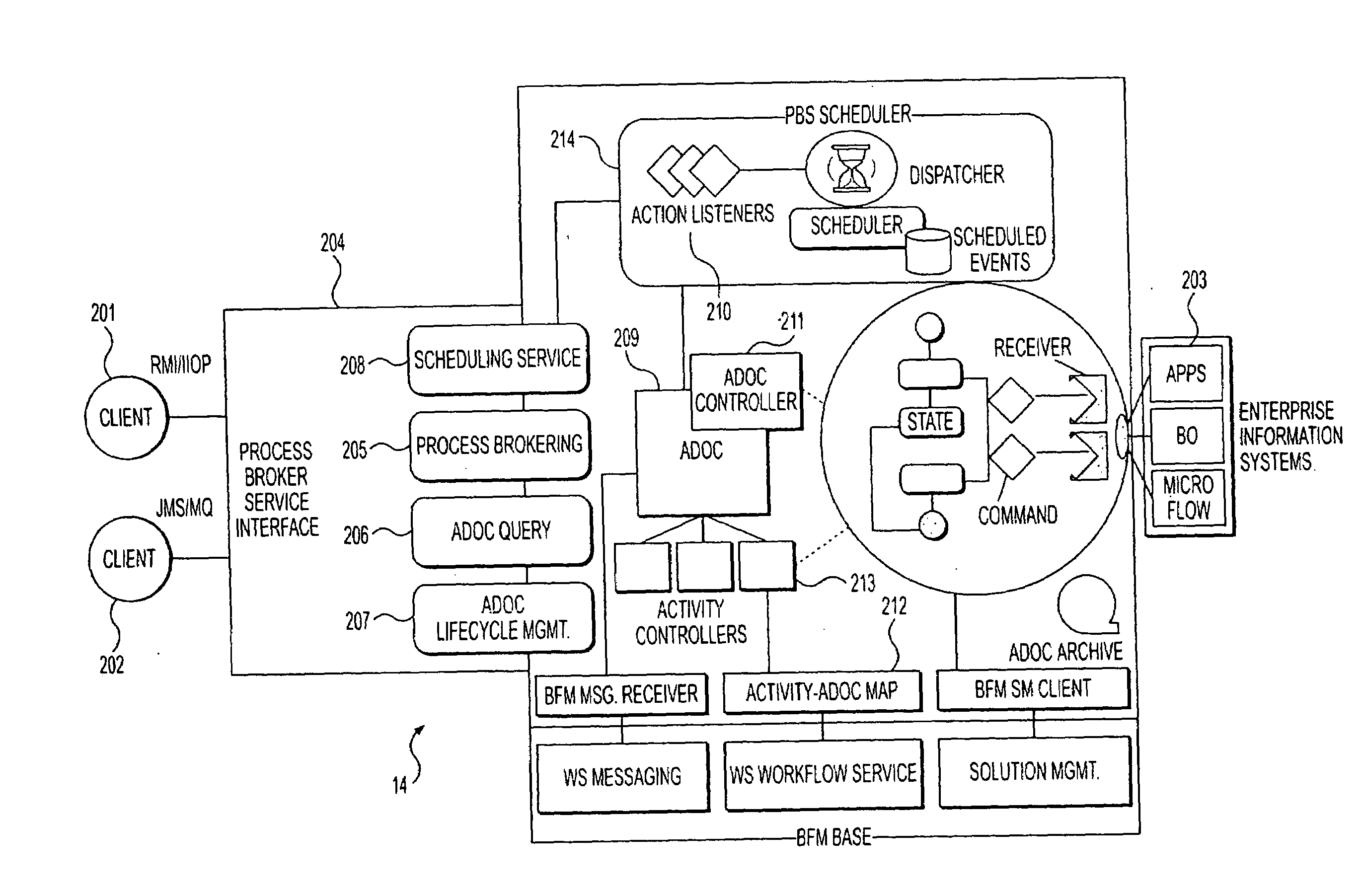
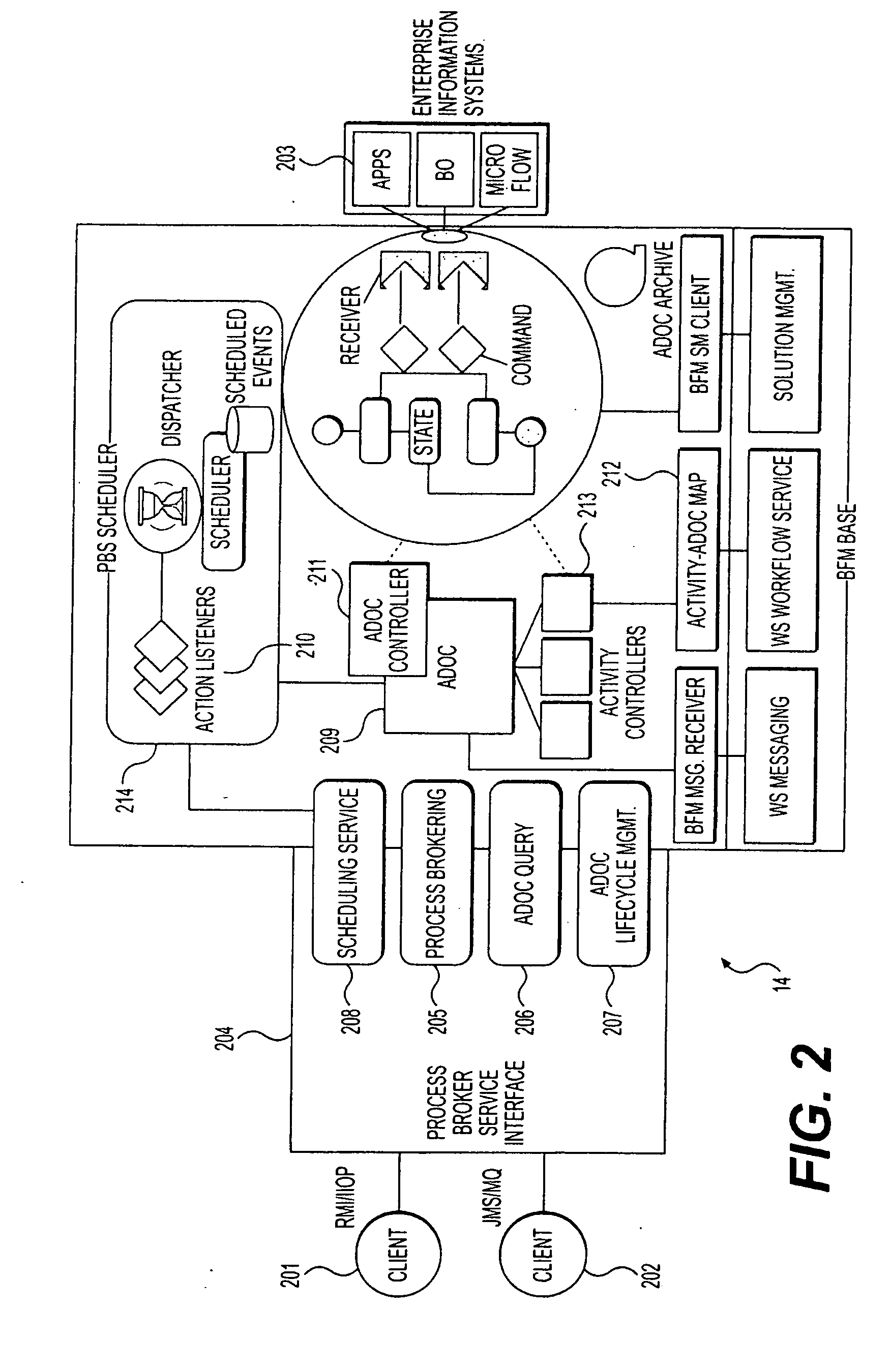
Method and system for process brokering and content integration for collaborative business process management
InactiveUS20030187743A1FinanceMultiple digital computer combinationsApplication softwareBusiness process management
Process Brokering Services (PBS) are implemented though the concept of Adaptive Documents to facilitate electronic commerce (e-commerce). PBS provides a single point of process control over the various fragmented execution flows and brings together the elements for process integration (views, content, flows) in a unified, scalable architecture on an industry standard platform. The two principal functions of the PBS are brokering of multiple business processes encapsulated in various back-end systems including workflow engines and business applications, and aggregating content from multiple enterprise information systems in the business context and managing the shared access to this based on the roles of the participants. The dynamic services provided by PBS are accessible to clients through the PBS Interface.
Owner:IBM CORP
System and method for providing highly available processing of asynchronous service requests
ActiveUS7222148B2Overcome deficienciesData processing applicationsMultiple digital computer combinationsClient-sideApplication software
Highly-available processing of an asynchronous request can be accomplished in a single transaction. A distributed request queue receives a service request from a client application or application view client. A service processor is deployed on each node of a cluster containing the distributed request queue. A service processor pulls the service request from the request queue and invokes the service for the request, such as to an enterprise information system. If that service processor fails, another service processor in the cluster can service the request. The service processor receives a service response from the invoked service and forwards the service response to a distributed response queue. The distributed response queue holds the service response until the response is retrieved for the client application.
Owner:ORACLE INT CORP
Extensible multi-dimensional framework
InactiveUS20080040364A1Easy to implementEasy to modifyOffice automationSpecial data processing applicationsDevelopment teamMulti dimensional
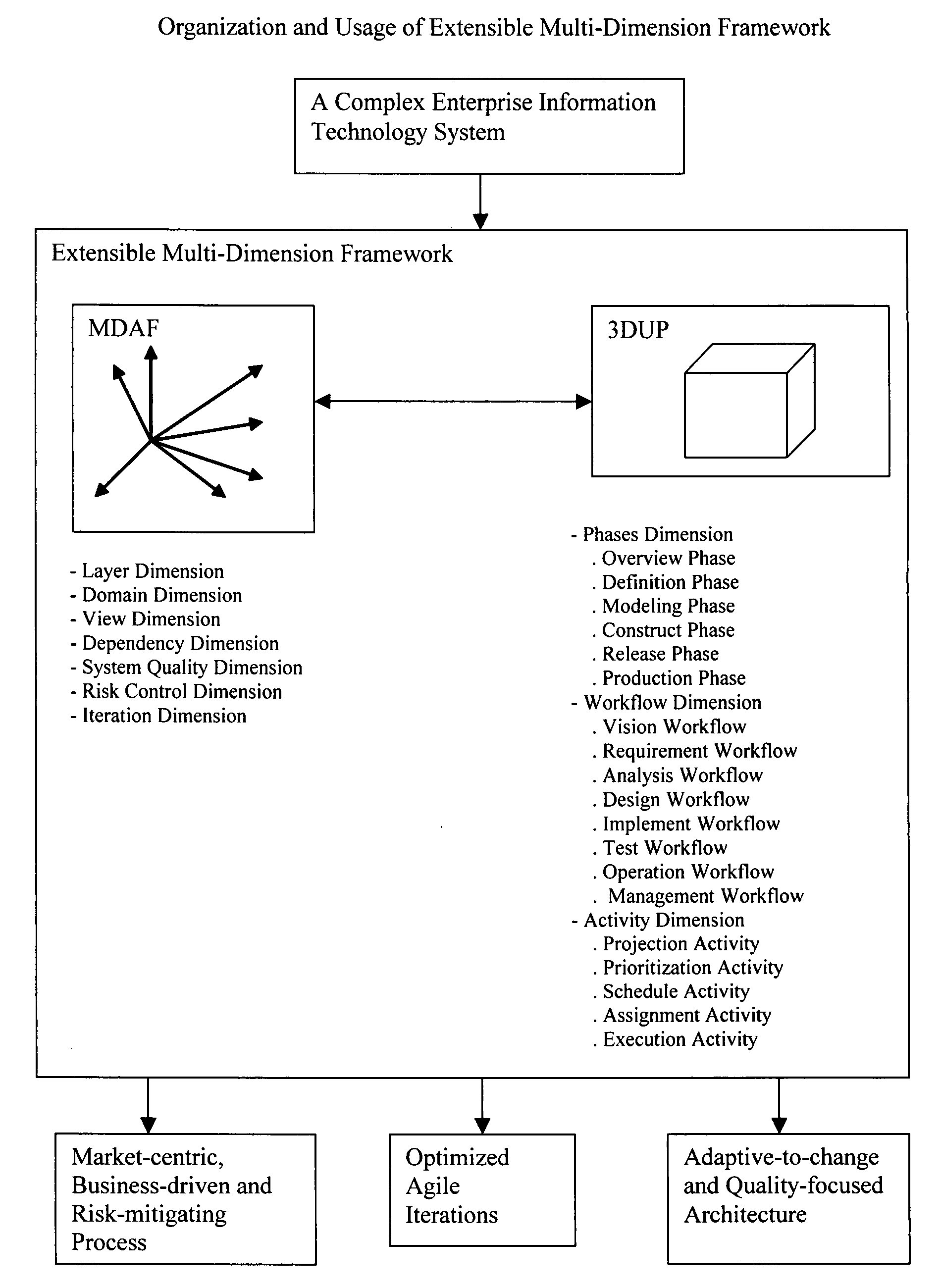
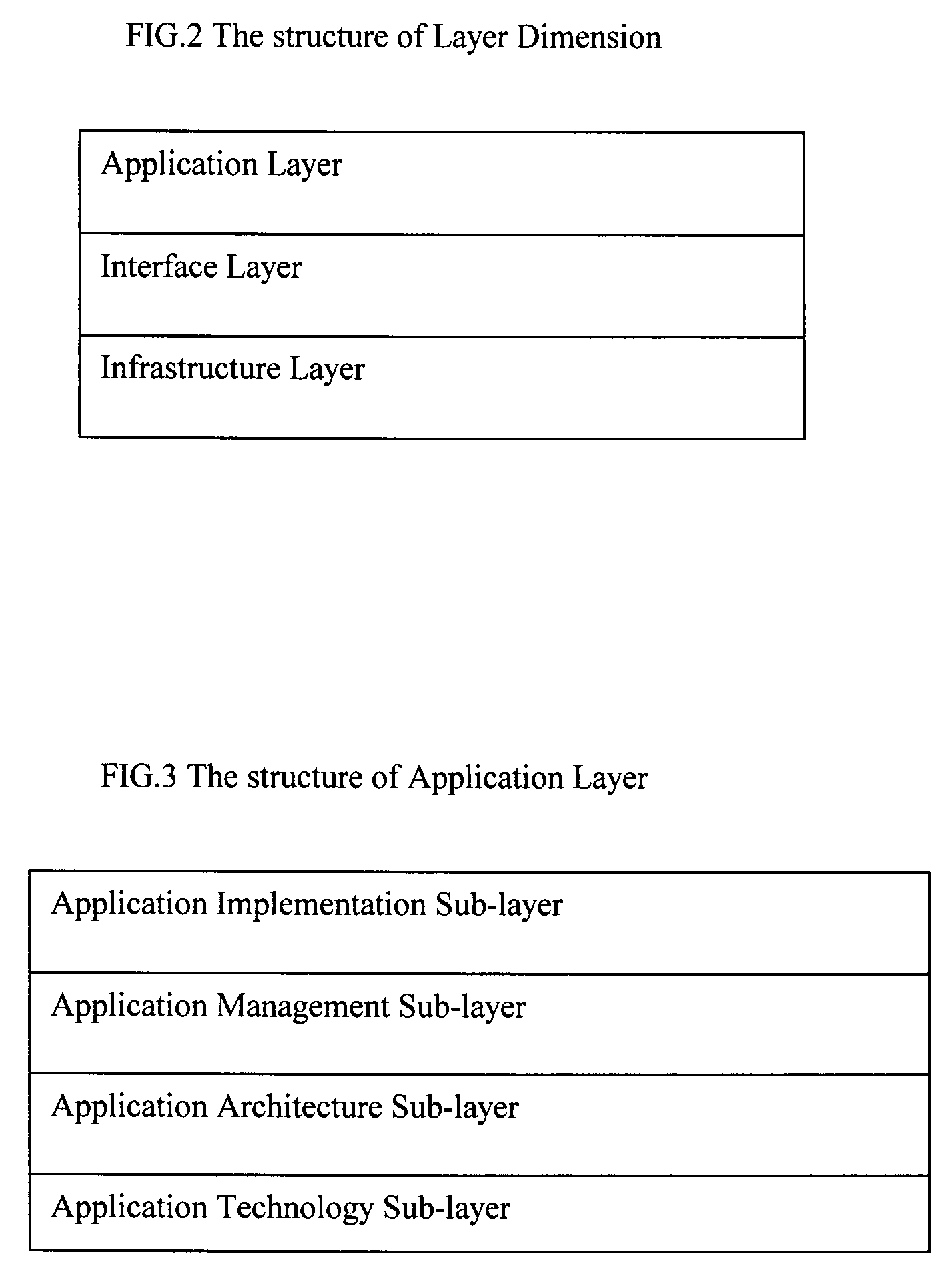
Extensible Multi-Dimensional Framework (EMDF) is a system engineering framework for designing, developing and managing enterprise information technology systems. It includes two parts: multi-dimensional architecture framework (MDAF) and three-dimensional unified process (3DUP). MDAF includes comprehensive concepts for modeling an enterprise information technology system. 3DUP provides an iterative system development process. EMDF addresses an enterprise information technology system as a single entity. By projecting this entity on intertwined MDAF dimensions through the 3DUP lifecycle, all logical or physical elements encompassed in the entity will be exposed and captured in well-organized artifacts defined in MDAF. These elements are then prioritized and scheduled in a set of agile iterations. The iterations will be planned in parallel projects implemented by multiple development teams. During a long-term system development lifecycle, some elements may change. The dimensions included in MDAF provide a flexible framework to adjust system architectures, iterations and projects in order to adapt to such changes. The key deliverables of EMDF include an adaptive-to-change quality-focused architecture, optimistic agile iterations, and a market-centric business-driven risk-mitigating process.
Owner:LI DI
Extracting Enterprise Information Through Analysis of Provenance Data
Techniques are disclosed for extracting information through analysis of provenance data. For example, a computer-implemented method of extracting information regarding an execution of an enterprise process comprises the following steps. Provenance data is generated, wherein the provenance data is based on collected data associated with an actual end-to-end execution of the enterprise process and is indicative of a lineage of one or more data items. A provenance graph is generated that provides a visual representation of the generated provenance data, wherein nodes of the graph represent records associated with the collected data and edges of the graph represent relations between the records. At least a portion of the generated provenance data from the graph is analyzed so as to extract information about the execution of the enterprise process based on the analysis.
Owner:IBM CORP
Industrial controlling network safety protecting method
ActiveCN103036886AGuaranteed real-time diagnosisReduce severityTransmissionIndustrial securityControl system
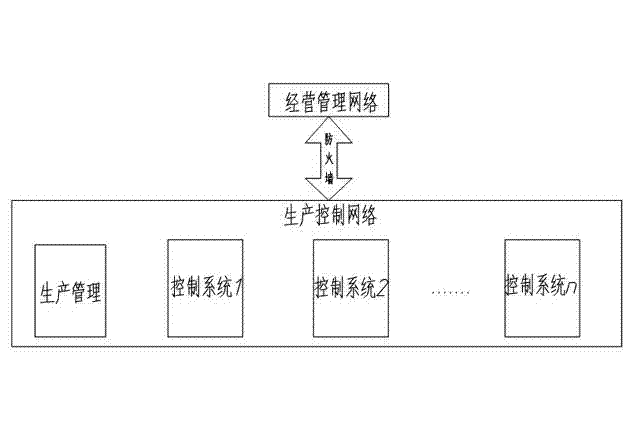
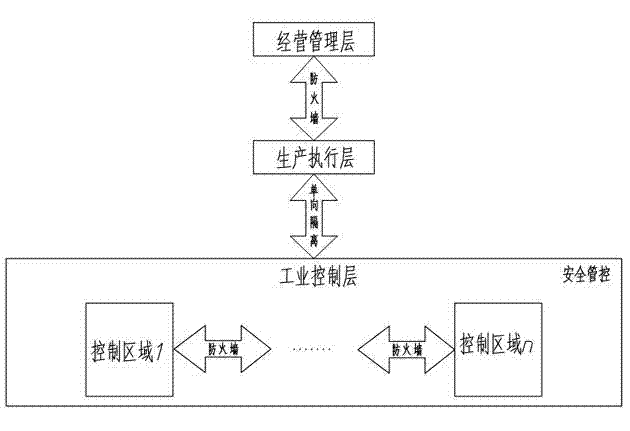
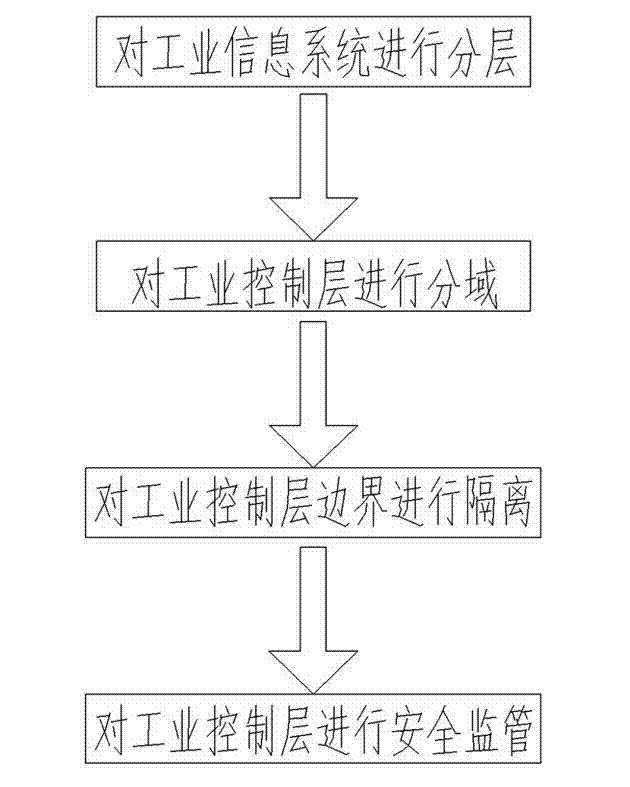
The invention discloses an industrial controlling network safety protecting method. The industrial controlling network safety protecting method is capable of improving industrial controlling network safety, convenient to communicate, capable of preventing external attack and invasion, and effectively protecting industrial controlling system and safety of industrial equipment. The industrial controlling network safety protecting method comprises the steps as below: processing an information system of an industrial enterprise in hierarchy; adopting safety protecting strategy procedures for data exchanging of the industrial controlling hierarchies; dividing the industrial controlling hierarchies into a plurality of automated unit regions and using a firewall for region separation; blocking potential communication ways of a production executive hierarchy to the industrial controlling hierarchy; adopting an industrial safety management platform module to build the center of configuration, management, analysis, warning and auditing of the industrial controlling hierarchy. The industrial controlling network safety protecting method is applied to the field of industrial controlling network.
Owner:珠海市鸿瑞信息技术股份有限公司
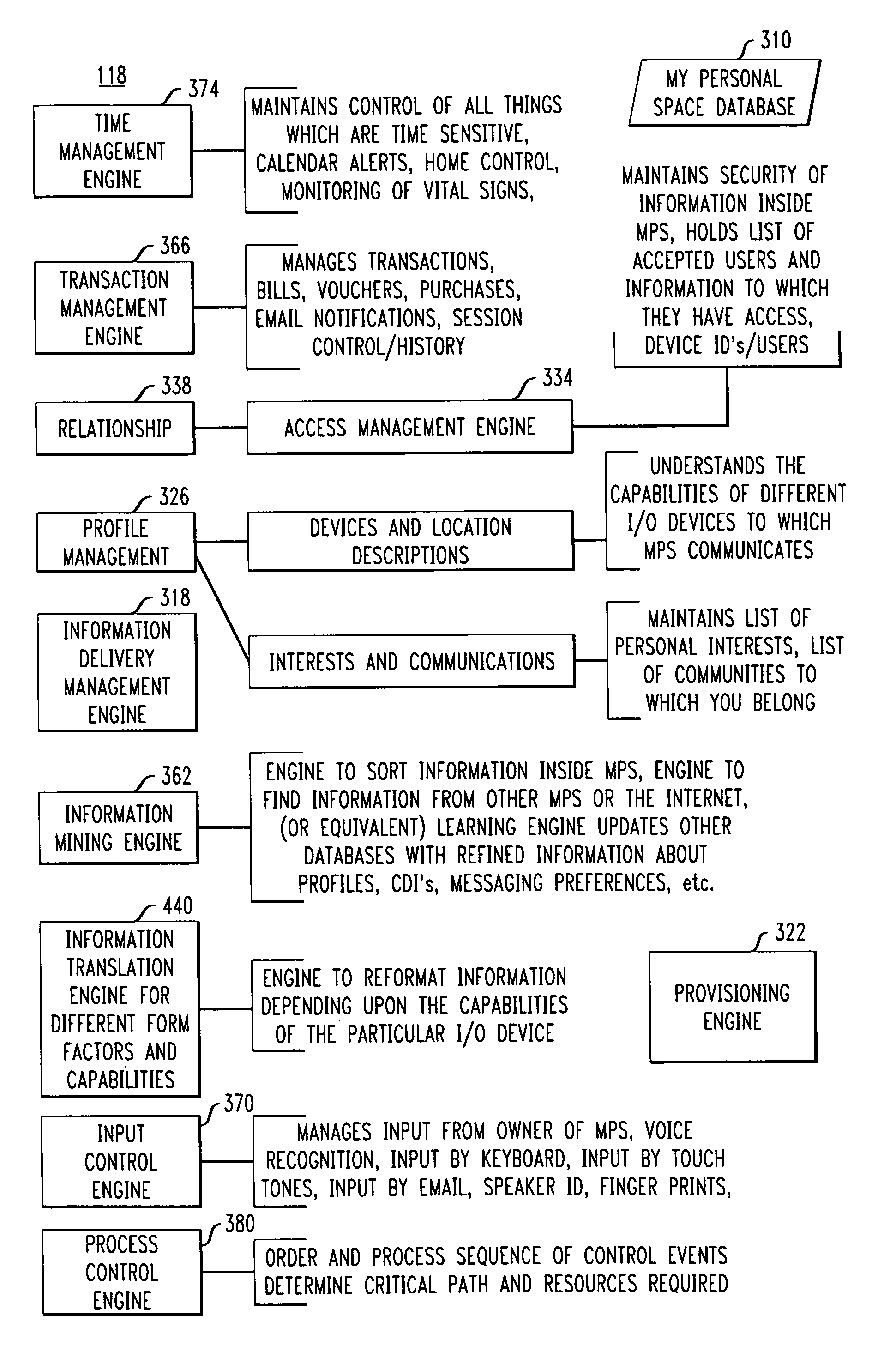
Enterprise information and communication system having a transaction management engine for managing bills vouchers purchases and email notifications
An information and communication system uses an web page like environment or “Personal Space” to integrate a plurality of communication and monitoring functions. Home or enterprise automation components are linked together via wired or unwired network links and accessed via the Personal Space. Communications services are accessed through a wide variety of devices and facilitated by the Personal Space. Databases are built and used to customize user services. User profiles and system use patterns are compared and analyzed to continuously improve system performance.
Owner:ALCATEL-LUCENT USA INC +1
Task request processing method and device and enterprise information system
ActiveCN106095585AImprove securityImprove stabilityResource allocationEnterprise integrationDistributed computing
The invention provides a task request processing method and device and an enterprise information system. The method comprises the steps that any background server receives a task request message sent by an enterprise service bus; a task is generated according to the received task request message, and the task is added to a task table in a database; the any background server in an idle state captures the unexecuted task from the task table and executes the captured task in a thread pool. The task request processing process is broken up into two processes capable of being executed independently by two different servers. For the same task request, execution is conducted according to a normal execution sequence; task execution is conducted when corresponding background servers are in an idle state, tasks are executed by means of the thread pool, in this way, it is well guaranteed that tasks can be executed, the safety and stability of the background servers are improved, and customer experience is improved.
Owner:CHINA CONSTRUCTION BANK
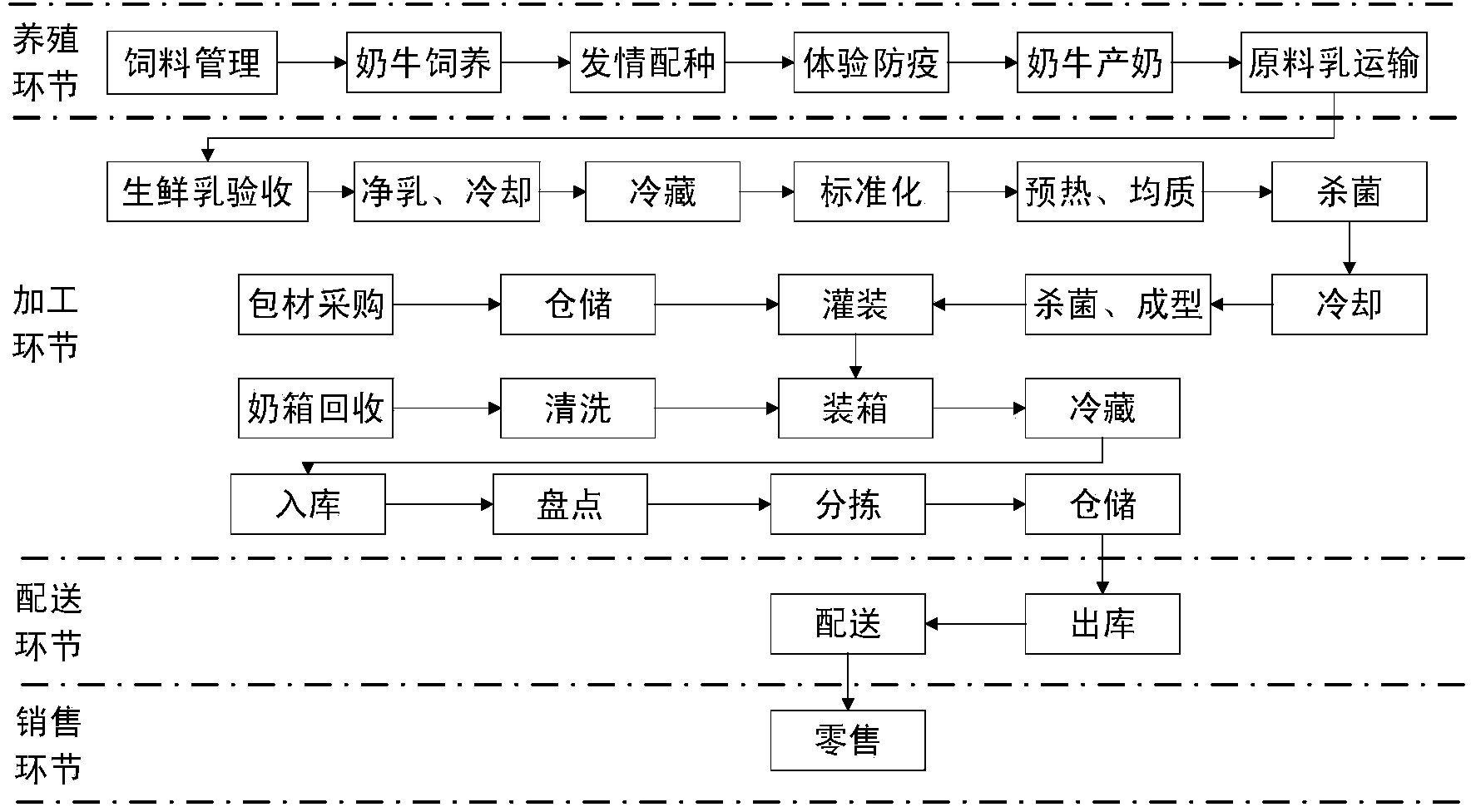
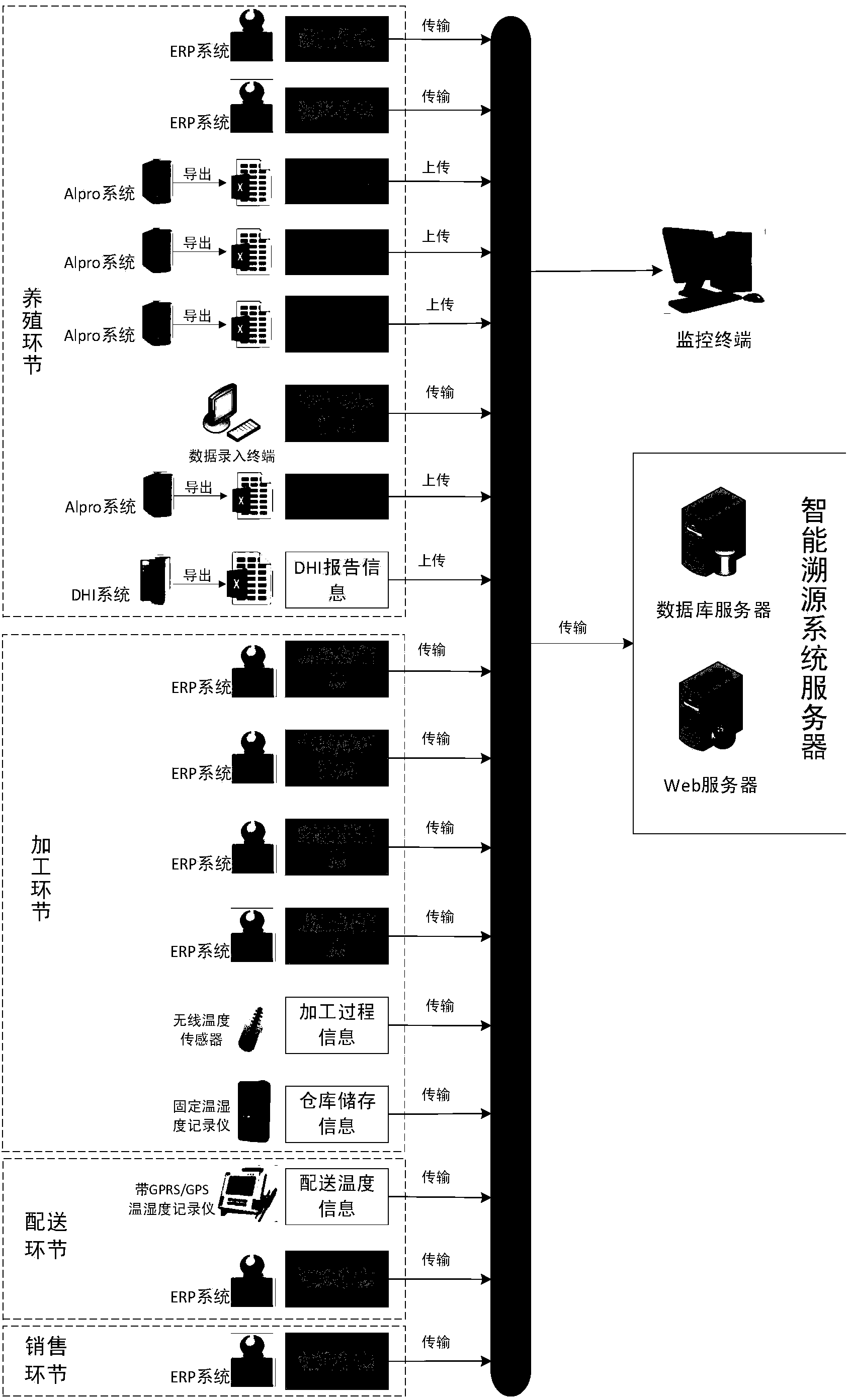
Dairy product quality safety full-life-circle intelligent traceability method based on Internet of things
The invention discloses a dairy product quality safety full-life-circle intelligent traceability method based on the Internet of things. The method comprises the following steps: the step S1 in which various cow breeding information is acquired in the breeding link; the step S2 in which various material and processing information is acquired in the processing link; the step S3 in which the raw milk and finished milk temperature information is acquired in the distribution link; the step S4 in which the order, customer and distribution information is acquired in the marketing link; the step S5 in which a traceability method in which a two-dimensional bar code and a traceability code are combined is adopted, wherein the two-dimension code is used on a large package, and the traceability code is used on a small package, and a traceability platform is established to perform traceability. According to the traceability method of the invention, an appropriate technology is selected when the enterprise actual situation is taken into account, and at the same time, the existing enterprise information system is used to acquire most of the traceability information, so that a lot of equipment and labor cost can be reduced. Additionally, the intelligent traceability system can be used to realize the visualization of the whole dairy product supply chain, so great utilization values can be provided for dairy product enterprises and supervision departments to facilitate the enterprises and the supervision departments to find problems timely, so that the loss can be effectively reduced.
Owner:SOUTH CHINA UNIV OF TECH +2
System and method for single sign-on
InactiveUS20060271689A1Low costLow-cost implementationMultiple digital computer combinationsDigital data authenticationSystem engineerInformation system
The single sign-on is implemented without requiring knowledge of a lower layer such as HTTP and HTML by using a single sign-on module which stores knowledge to store single sign-on and a single sign-on server which analyzes log-in communication of an EIS (Enterprise Information System) and selects and executes an applicable single sign-on module. Since the single sign-on can be implemented without requiring knowledge of a lower layer such as HTTP and HTML from a system engineer, the single sign-on can be implemented in a short period and at low cost.
Owner:HITACHI LTD
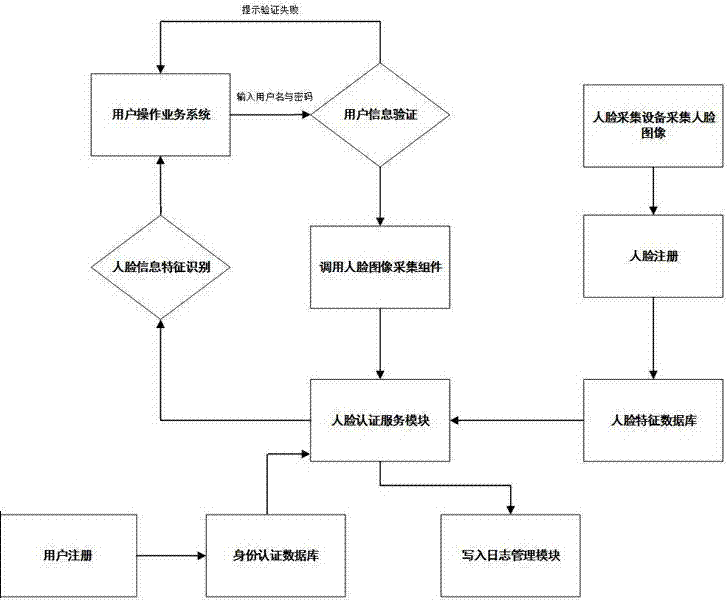
User identity reliably-verifying system based on face identification and using method thereof
InactiveCN104765998AImprove the protective effectPrevent intrusionCharacter and pattern recognitionDigital data authenticationApplication serverDatabase server
The invention relates to a user identity reliably-verifying system based on face identification and a using method thereof. The system comprises a database server, a face identification server, an application server, a user terminal computer and a face acquisition device, wherein the database server, the face identification server, the application server and the user terminal computer are all connected to an interchanger for data transmission, and the output end of the face acquisition device is connected with the user terminal computer. The enterprise user identity reliably-verifying system is established by means of the fan identification technology, a face identification authentication service port and a face identification component are flexibly integrated for an enterprise information system to be used, and a safe and reliable identity verifying service is provided when an enterprise user logs in the information system or conducts key business operation.
Owner:STATE GRID CORP OF CHINA +1
Automatic creation and transmission of data originating from enterprise information systems as audio podcasts
ActiveUS8229937B2Digital data processing detailsNatural language data processingPersonal computerBackground process
Owner:SAP AG
Credit data management system supporting complex enterprise environment and credit data management method
InactiveCN104299105AIncrease authenticityImprove reliabilityResourcesSpecial data processing applicationsInformation analysisData warehouse
The invention relates to a credit data management system supporting complex enterprise environment and a credit data management method. The credit data management system comprises a user applying module, a data acquiring module, a data processing module, a data warehouse, a data analyzing model managing module, an analysis evaluating module and a credit managing module. The credit data management system solves the problems of integration, standardization, management and analysis of enterprise data under the complex enterprise environment, processes and converts dispersive and nonstandard enterprise information, makes data more standard and be integrated into the data warehouse and provides support for credit evaluation for enterprises. Meanwhile, the invention provides a method more suitable for the credit data management system to achieve enterprise credit data analysis and evaluation based on external data handling, and efficiency of enterprise information analysis and evaluation accuracy are improved.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
System and method for enterprise application interactions
ActiveUS7350184B2Digital data processing detailsMultiprogramming arrangementsApplication softwareClient-side
An application view control can allow users of a software tool to interact with Enterprise applications using simple Java APIs. This can allow a user who is not an expert in the use of a given Enterprise system to utilize its capabilities in a manner a Java programmer can understand. A developer can invoke application view services both synchronously and asynchronously, and can subscribe to application view events. The developer can use simple Java objects in both the service and event cases. The developer need not understand XML, or the particular protocol or client API for the Enterprise application, such as an Enterprise Information System (EIS).
Owner:ORACLE INT CORP
Security attack alarm positioning system based on Spark big data platform of Tachyou
InactiveCN105207826AEfficient use ofImprove good performanceData switching networksReal time analysisData platform
The invention discloses a security attack alarm positioning system based on a Spark big data platform of Tachyou and belongs to the field of big data and information security. The system comprises an acquisition module, a security attack alarm positioning module and a view module. The acquisition module gathers log information in an enterprise information system, preprocesses and pushes the log information to the security attack alarm positioning module in real time, the security attack alarm positioning module performs real-time analysis to generate alarm information, and sends the alarm information to a view front end page. Compared with the prior art, the security attack alarm positioning system can solve the problem that a large number of logs are difficult to analyze in real time and has excellent practicality and value of popularization and application.
Owner:NANJING LIANCHENG TECH DEV
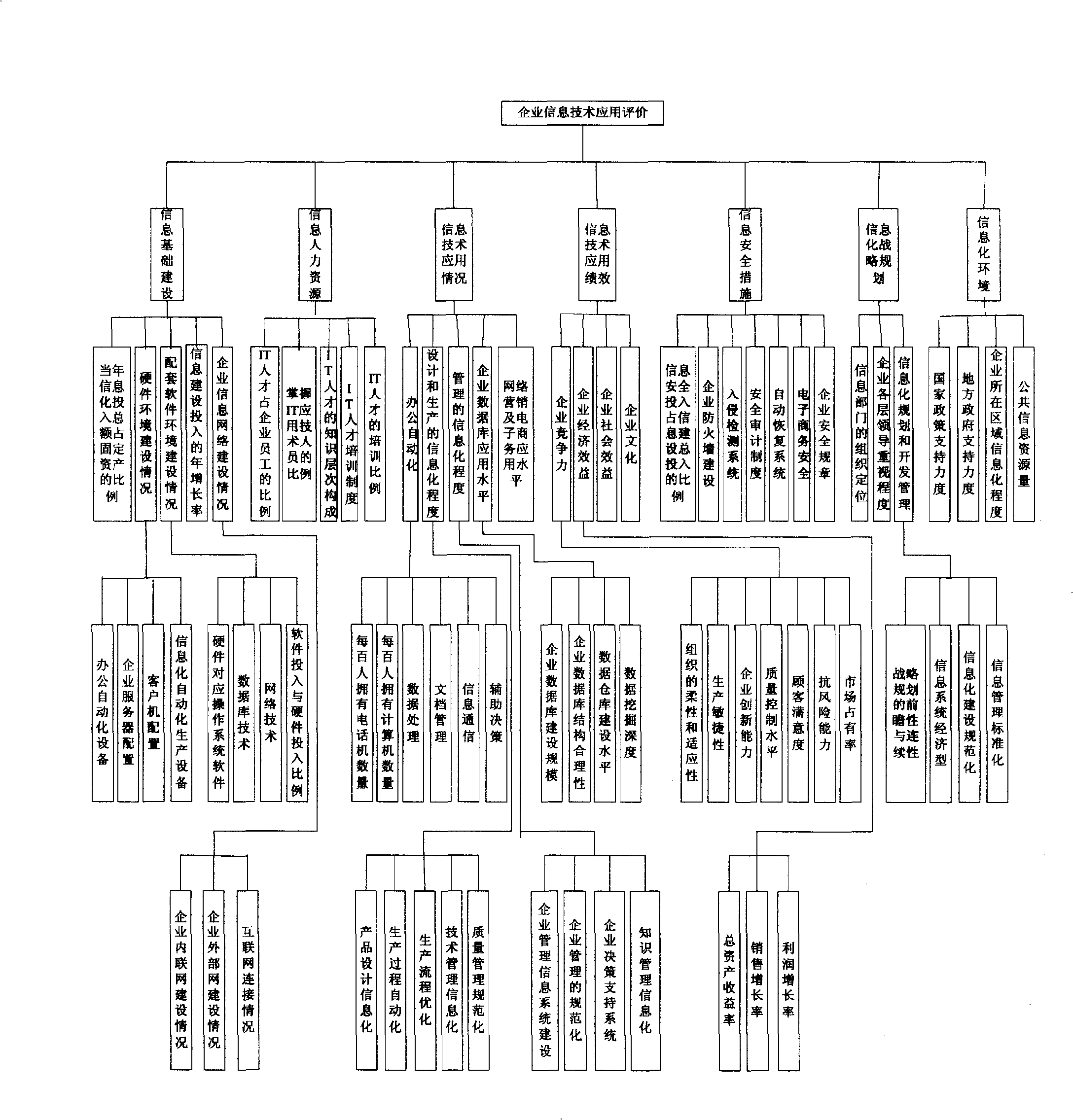
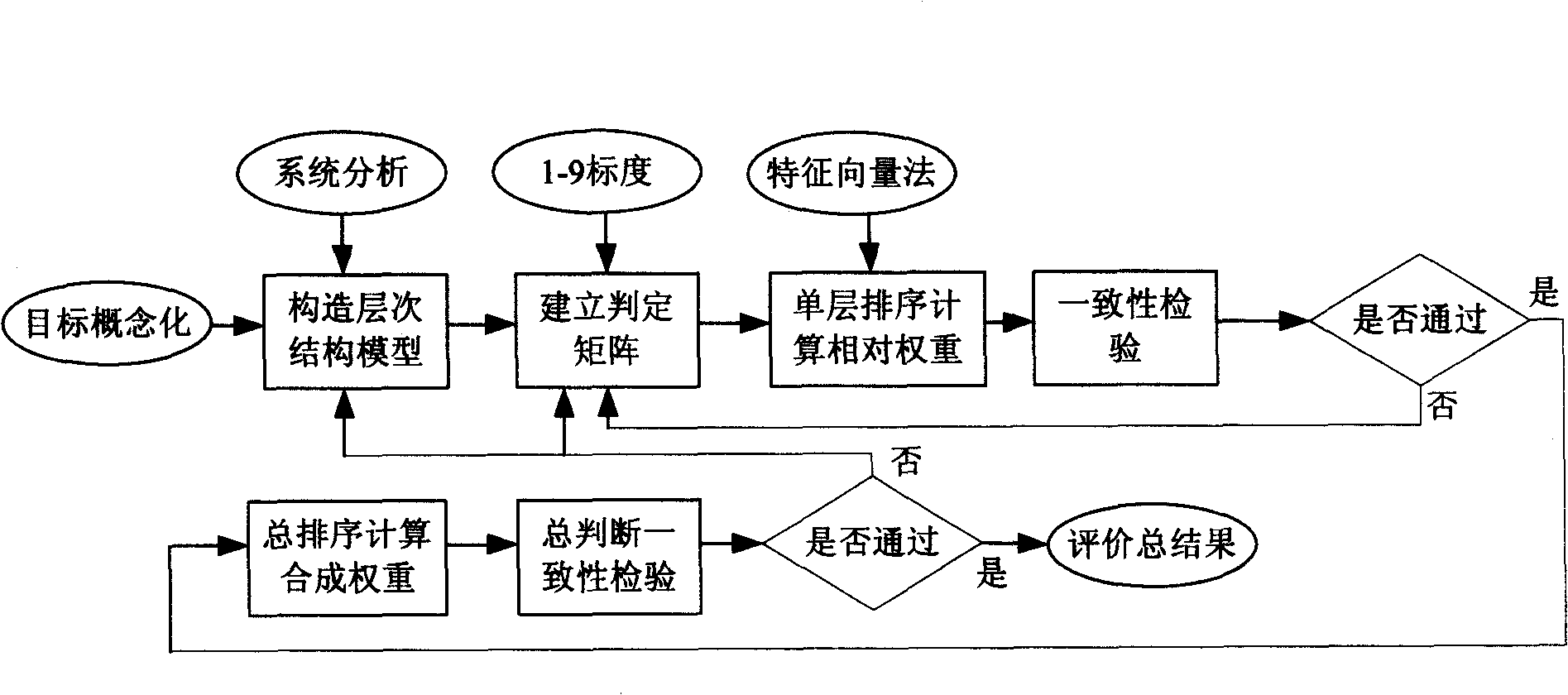
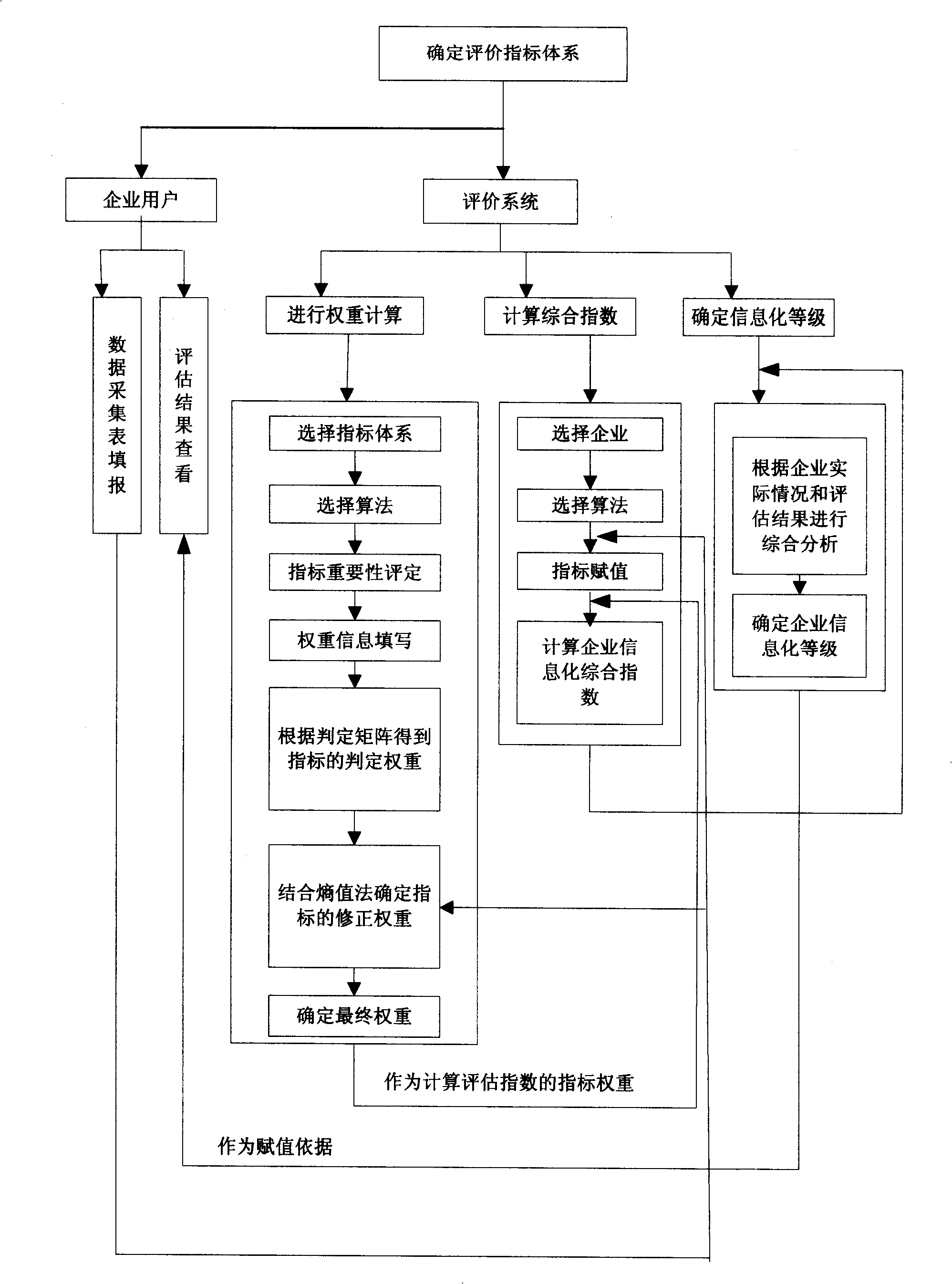
Method and system for evaluating degree of application of enterprise information technology
The invention relates to a method and a system for evaluating the degree of application of an enterprise information technology. The evaluation method comprises the step of establishing an evaluation index system, the step of giving values to evaluation indexes, the step of determining the relative importance of each evaluation index, the step of determining the weight of each index in the system, the step of calculating an evaluation exponent of the degree of the application of the enterprise overall information technology and other steps. The invention realizes the evaluation of the degree of the application of the enterprise-oriented information technology, avoids the subjectivity caused by scoring by experts in the traditional method and ensures the relative objectivity and the accuracy of the evaluation result by the method of being combined with actual quantitative data. The invention enables enterprises to carry out reasonable and accurate positioning of the own information level and avoid the waste caused by blind investment and is simultaneously conductive to finding weak links during the own information construction for the enterprises and leading the enterprises to carry out the targeted improvements.
Owner:ZHEJIANG NORMAL UNIVERSITY
Method and System for Process Brokering and Content Integration for Collaborative Business Process Management
Process Brokering Services (PBS) are implemented though the concept of Adaptive Documents to facilitate electronic commerce (e-commerce). PBS provides a single point of process control over the various fragmented execution flows and brings together the elements for process integration (views, content, flows) in a unified, scalable architecture on an industry standard platform. The two principal functions of the PBS are brokering of multiple business processes encapsulated in various back-end systems including workflow engines and business applications, and aggregating content from multiple enterprise information systems in the business context and managing the shared access to this based on the roles of the participants. The dynamic services provided by PBS are accessible to clients through the PBS Interface.
Owner:INT BUSINESS MASCH CORP
Detection of access point location errors in enterprise localization systems
ActiveUS20100329123A1Error preventionFrequency-division multiplex detailsLocalization systemLikelihood-ratio test
Method and apparatus for validating location information associated with an access point (AP) in a wireless local area network (WLAN) by subjecting neighborhood node proximity information retrieved from an AP and neighborhood node location information retrieved from a database to a likelihood ratio tests (LRT). The neighborhood node proximity information retrieved from an AP comprises a list of nodes exhibiting at the AP a signal strength above a threshold level T, or link quality information associated with those nodes having a signal received by the AP.
Owner:1BAR NET LTD
Method and system for quickly converting enterprise information system into mobile application
InactiveCN104268739ASave time and costSave development costMultiprogramming arrangementsOffice automationHTML5Middleware
The invention discloses a method and system for quickly converting an enterprise information system into a mobile application. The method includes the steps that a client application sends a request to server Java middleware, wherein the client application is a combination of a html5 file and a native container; the Java middleware conducts kernel processing after receiving the request, a database or an interface or a page of the corresponding enterprise information system are requested through a unified data bus; the unified data bus collects data from the enterprise information system through database drive or interface drive or page drive, and the data are converted into data of a JSON format and sent to the client application, wherein keys in the data of the JSON format are custom tags; the client application receives and analyzes the data of the JSON format, and a user interface is generated, wherein the custom tags are adopted in html5 dynamic data in the user interface. By the adoption of the scheme, the development difficulty can be lowered, the cross-platform development time and the cross-platform development cost are saved, the enterprise information system can be quickly converted into the mobile application, and developers do not need to provide too many or permanent technical supports.
Owner:蓝信移动(北京)科技有限公司
J2EE enterprise information system (EIS) common object request broker architecture (CORBA) connector
InactiveUS20050028164A1Multiprogramming arrangementsMultiple digital computer combinationsApplication serverEnterprise integration
Connections between a Java 2 enterprise edition (J2EE) application server and a common object request broker architecture (CORBA) enterprise information system are managed. A resource adapter is integrated with the application server. The resource adapter includes an encapsulated CORBA interface to the enterprise information system. Additionally, a persistent CORBA connection is established between the application server and the enterprise information system.
Owner:SBC KNOWLEDGE VENTURES LP
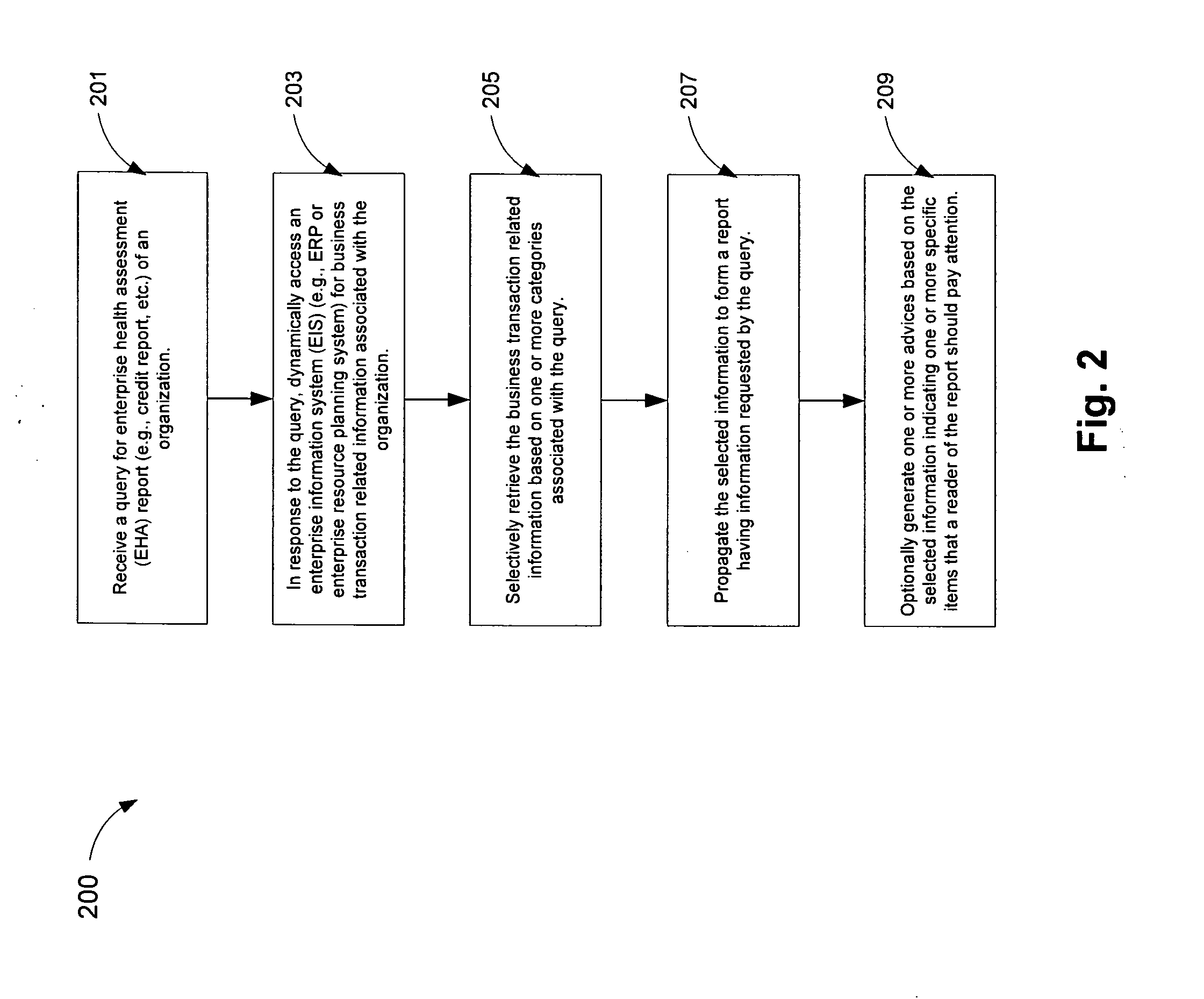
Method and apparatus for enterprise operation assessment
A method and an apparatus for automatic generation of an enterprise operation health assessment of an organization by dynamically accessing an associated enterprise information system are described. The assessment may be initiated in response to a query over a network. Business transaction information during course of operations within the organization may be retrieved according to one or more requirements of the enterprise operation health assessment report based on the received query. In addition, an advisory report may be generated based on the enterprise operation health assessment report according to one or more rules.
Owner:SAP AG
Method and system for obtaining context information of workflow in computing environment generally referred to
InactiveCN1959724ARealize automatic executionResourcesWorkflow management systemComplex event processing
A method for obtaining context information of work stream in pan-calculation environment includes utilizing complicated event processing engine in work stream server based on complicated event processing rule to carry out extracting and regathering on event information formed by enterprise physical environment and activity pretreated and obtained by electronic countermark identifier under pan-calculation environment prepared by Internet work stream station, information unit and identifying unit; then structuring them to form composite event being used to pick up context from.
Owner:TSINGHUA UNIV
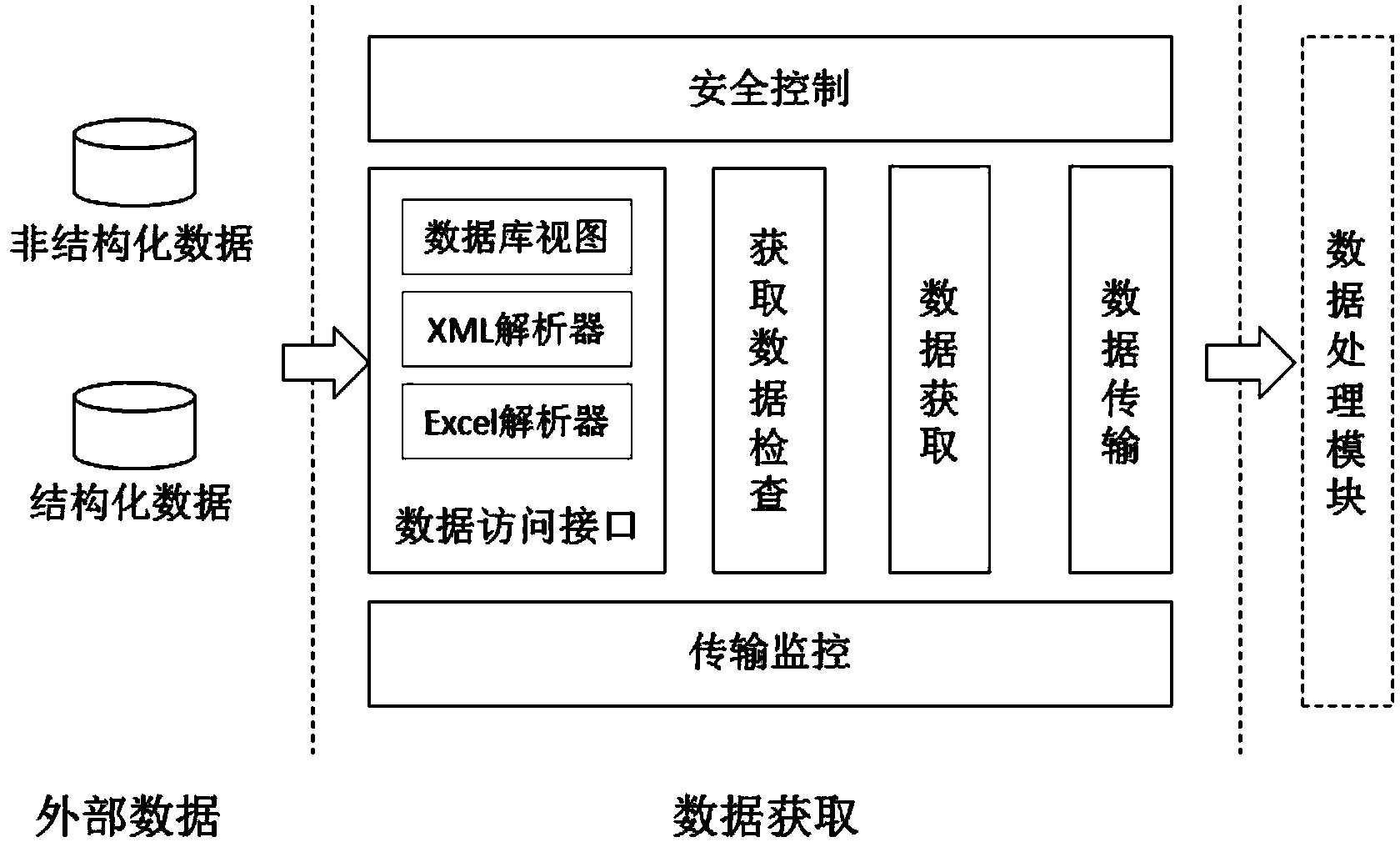
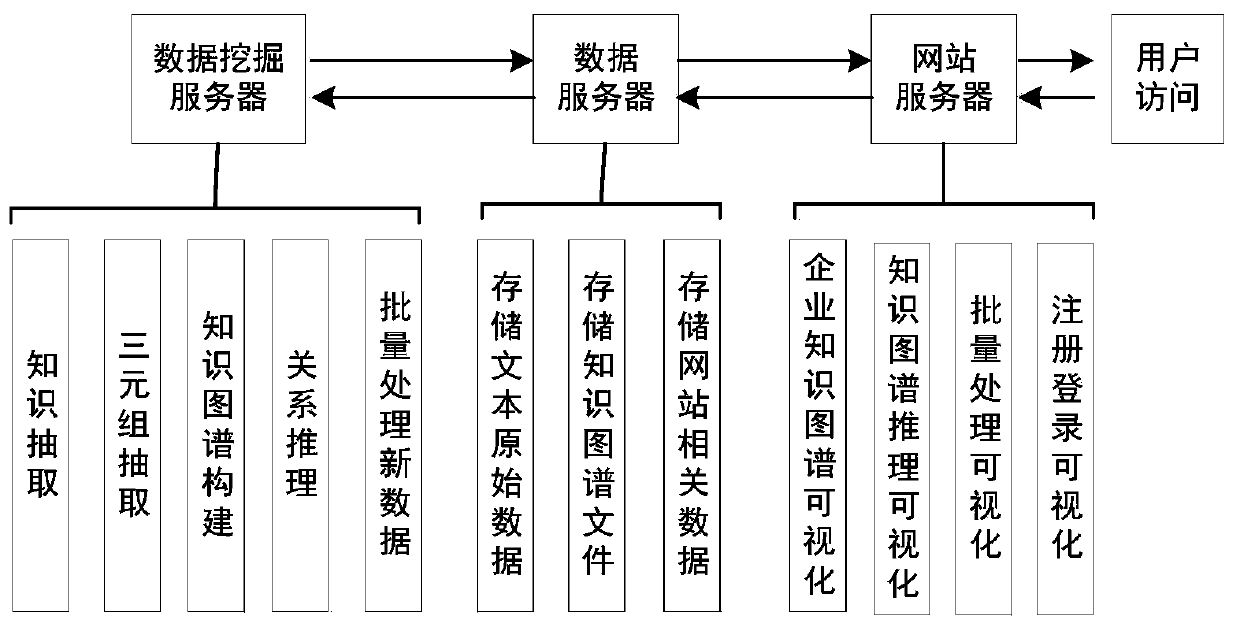
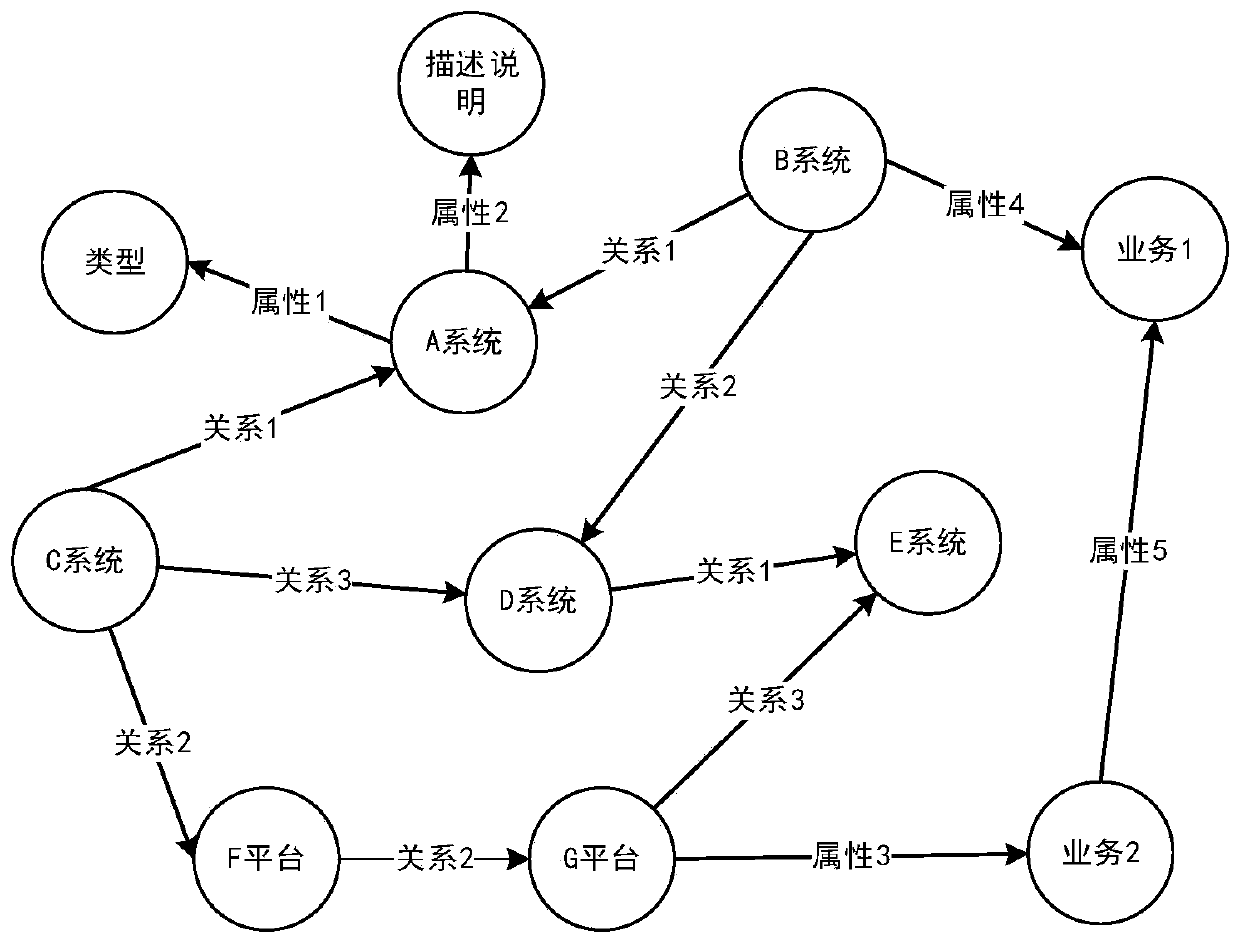
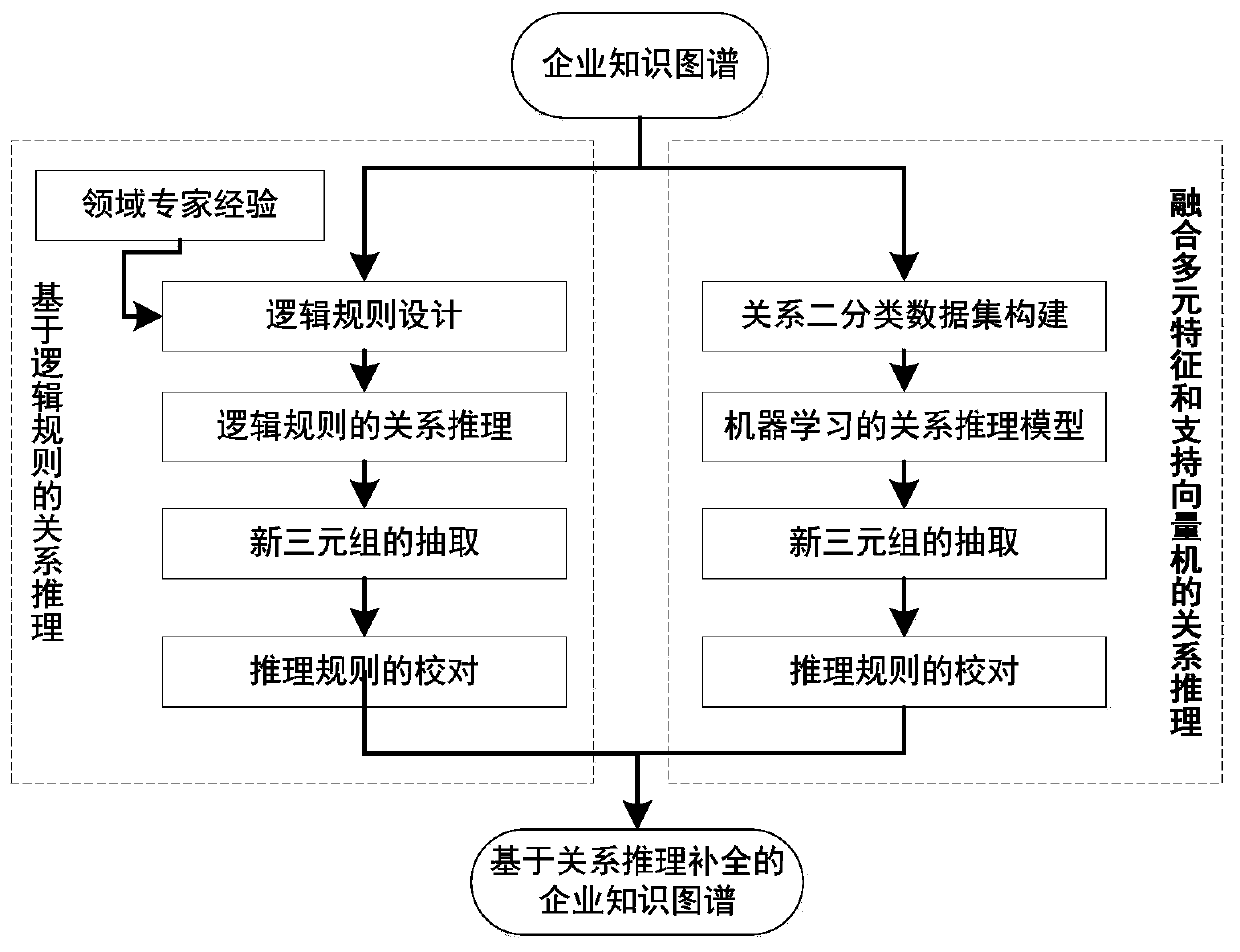
Information system management method based on knowledge graph
The invention discloses an information system management method based on a knowledge graph. According to the method, multi-source heterogeneous data such as technical documents, test analysis reports,operation log data and user feedback generated in design and actual operation of an enterprise informatization system are utilized, entities and relations in the data are extracted by comprehensivelyutilizing iteration rules and a machine learning algorithm, and a knowledge graph of the enterprise information system is constructed. On the basis of the extracted triple data, logic rules and machine learning are combined to realize relationship reasoning of the knowledge graph, a hidden relationship of an enterprise internal information system is mined, existing knowledge graph data is supplemented and perfected, and finally, a webpage is designed by utilizing a B / S mode to visually display the knowledge graph of the enterprise internal information system. The knowledge graph visually andcomprehensively displays the composition structure of each information system of the enterprise, helps enterprise decision makers and technical management personnel to macroscopically master the interaction relationship of the internal information systems of the enterprise, and promotes healthier and more stable development of internal informatization construction of the enterprise.
Owner:XI AN JIAOTONG UNIV
Apparatus, system, and method for automated identity relationship maintenance
An apparatus, system, and method are disclosed for automatically maintaining identity relationships among disparate enterprise information systems. The apparatus comprises a synchronization hub comprising an identity relationship repository, a relationship service module, a consistency module, and an adjustment module. The relationship service is configured to access a target relationship entry using a unique key from a source business object, wherein the source business object is representative of changes made in a source enterprise information system. The various components and modules of the synchronization hub cooperate to determine identity relationships that need updating and to propagate identity relationship changes to one or more destination enterprise information servers.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com