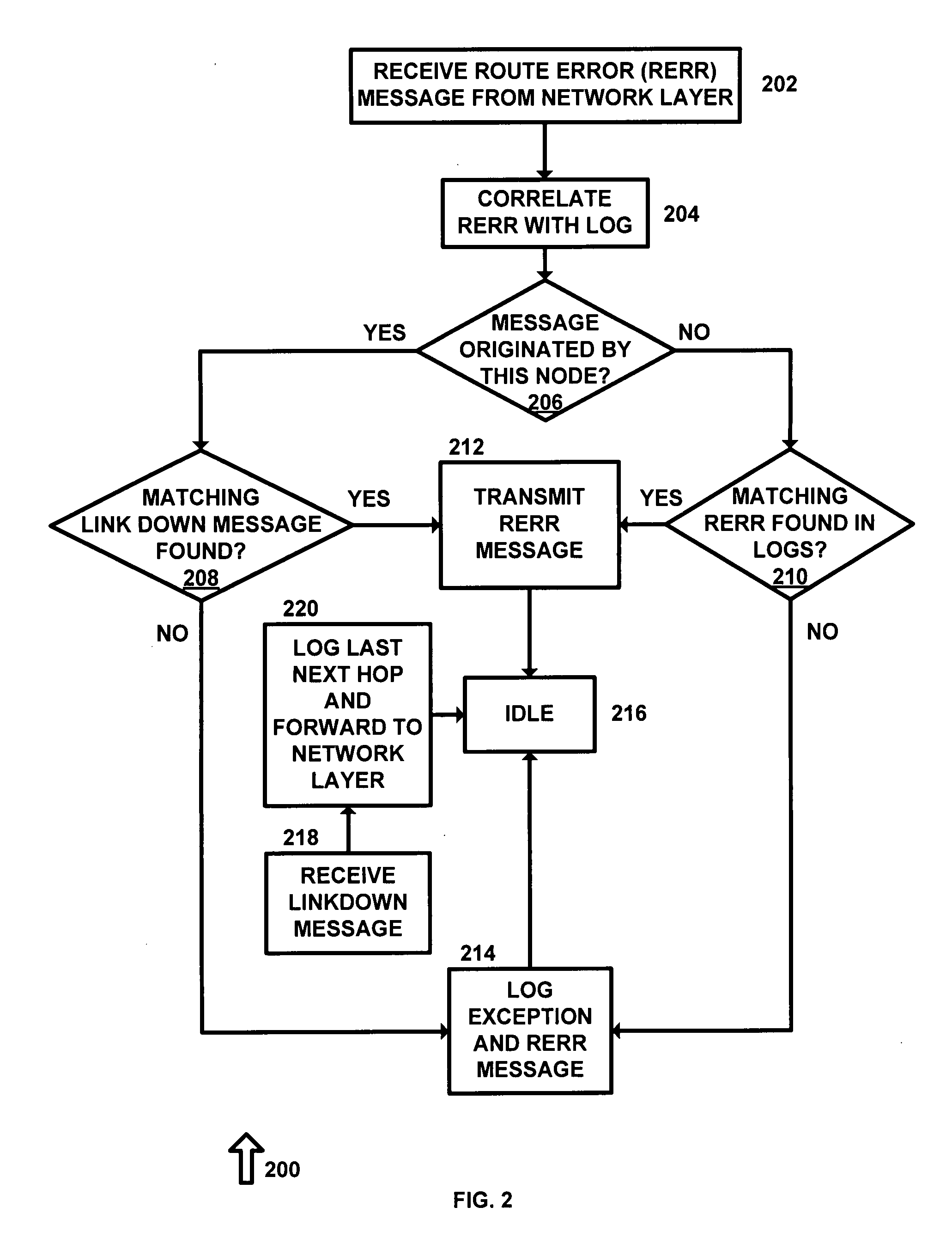
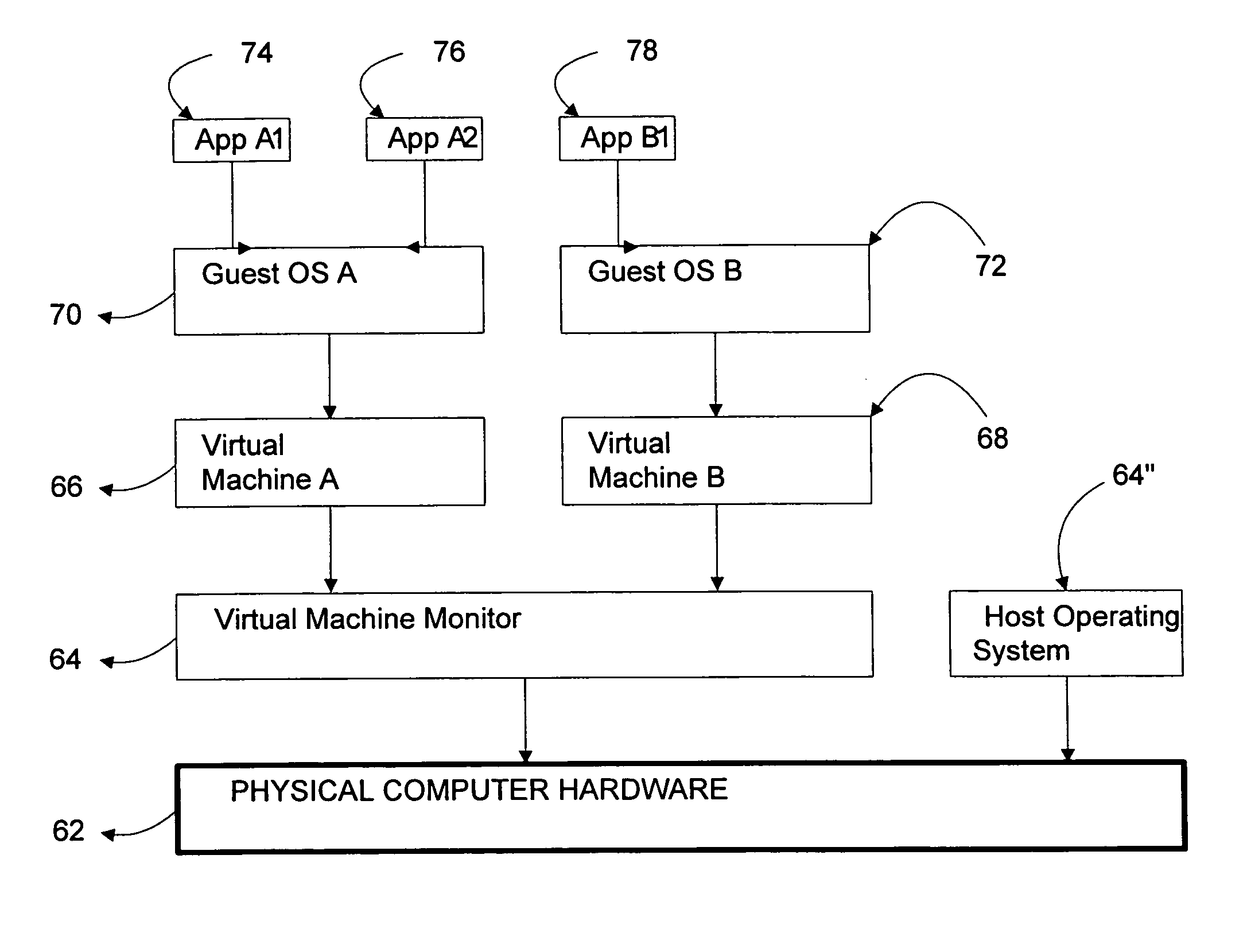
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
102 results about "High assurance" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
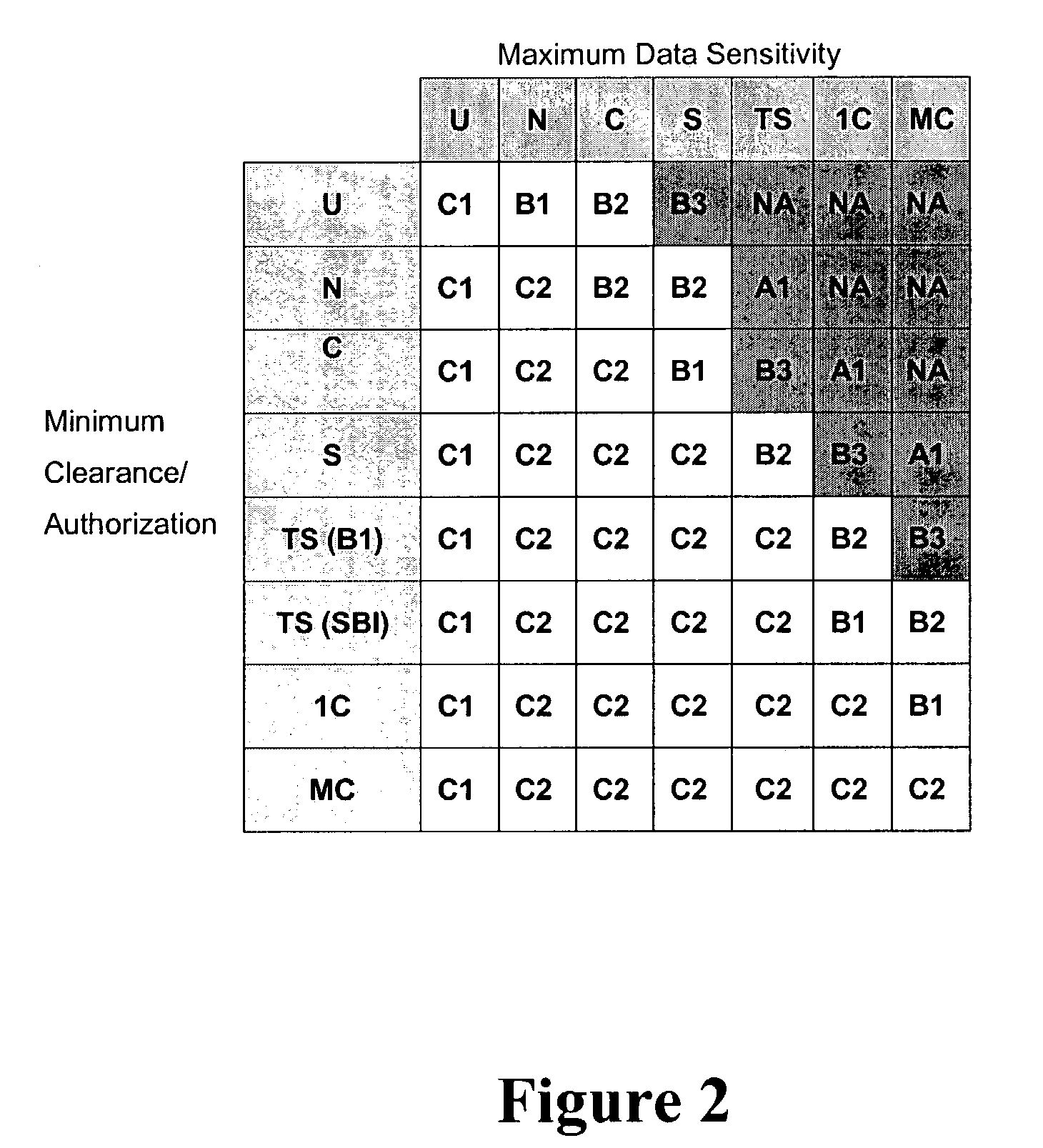
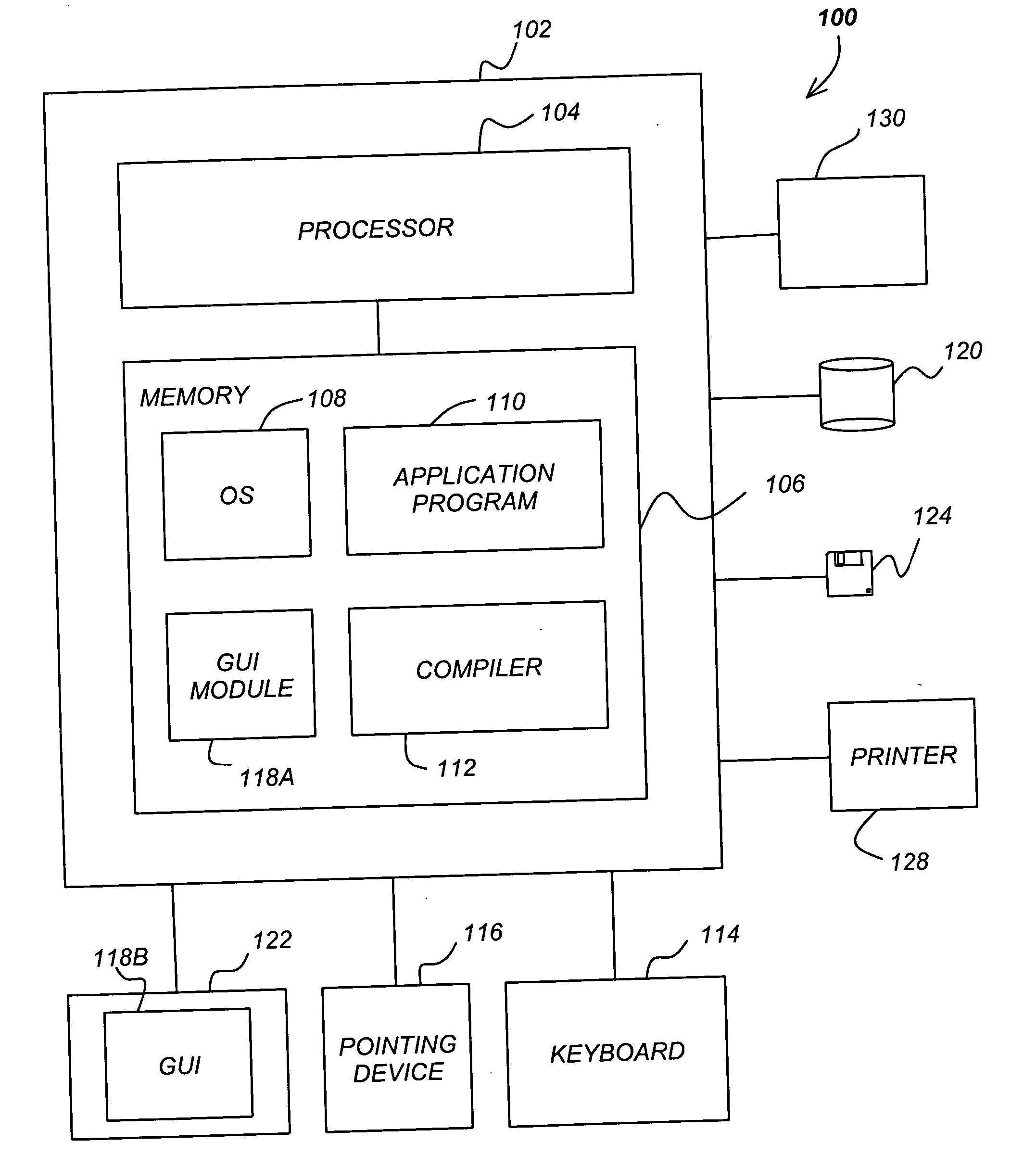
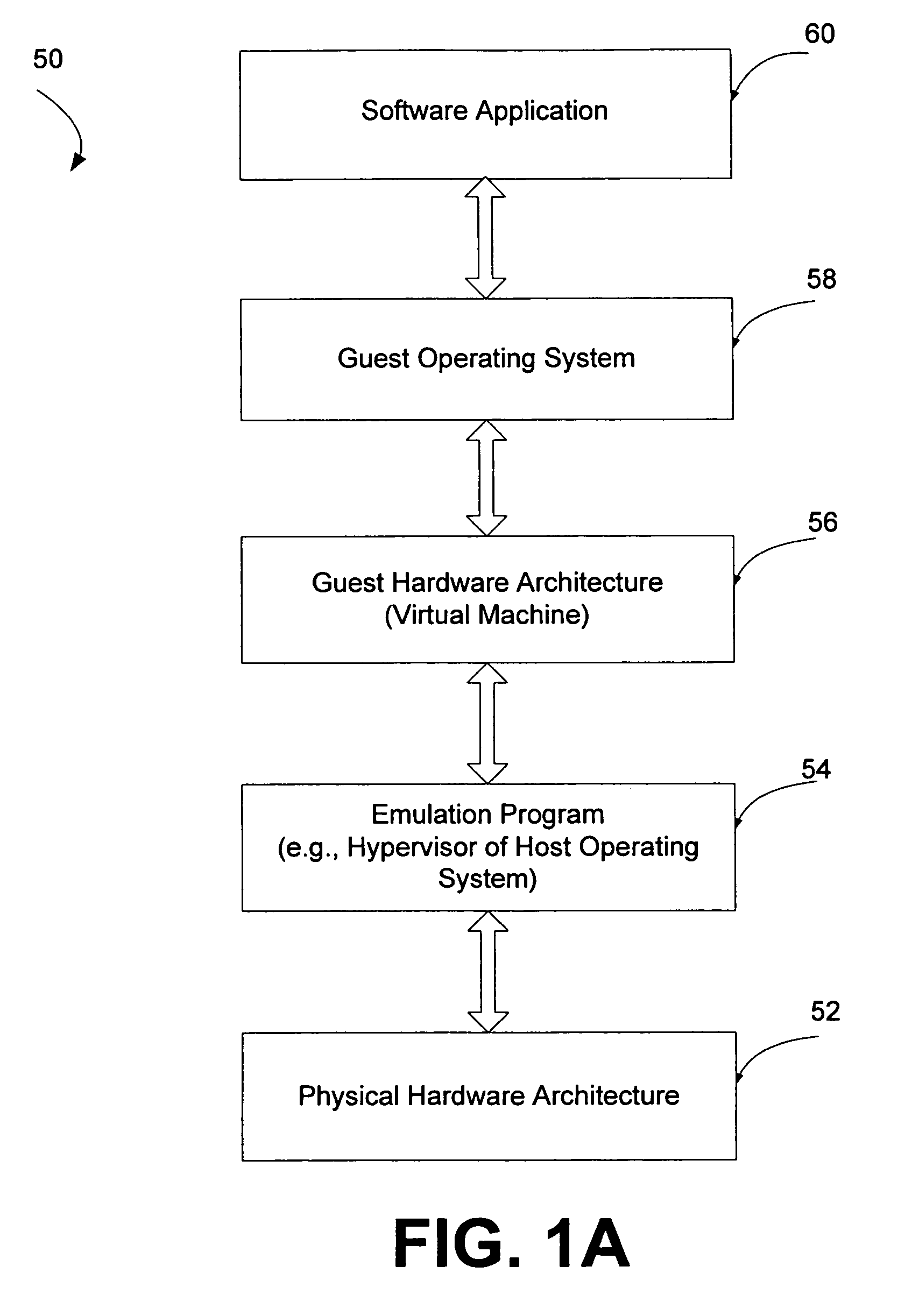
Method and apparatus for providing secure access control for protected information
InactiveUS20070136603A1Quick fixComputer security arrangementsSecuring communicationInternet privacyHigh assurance
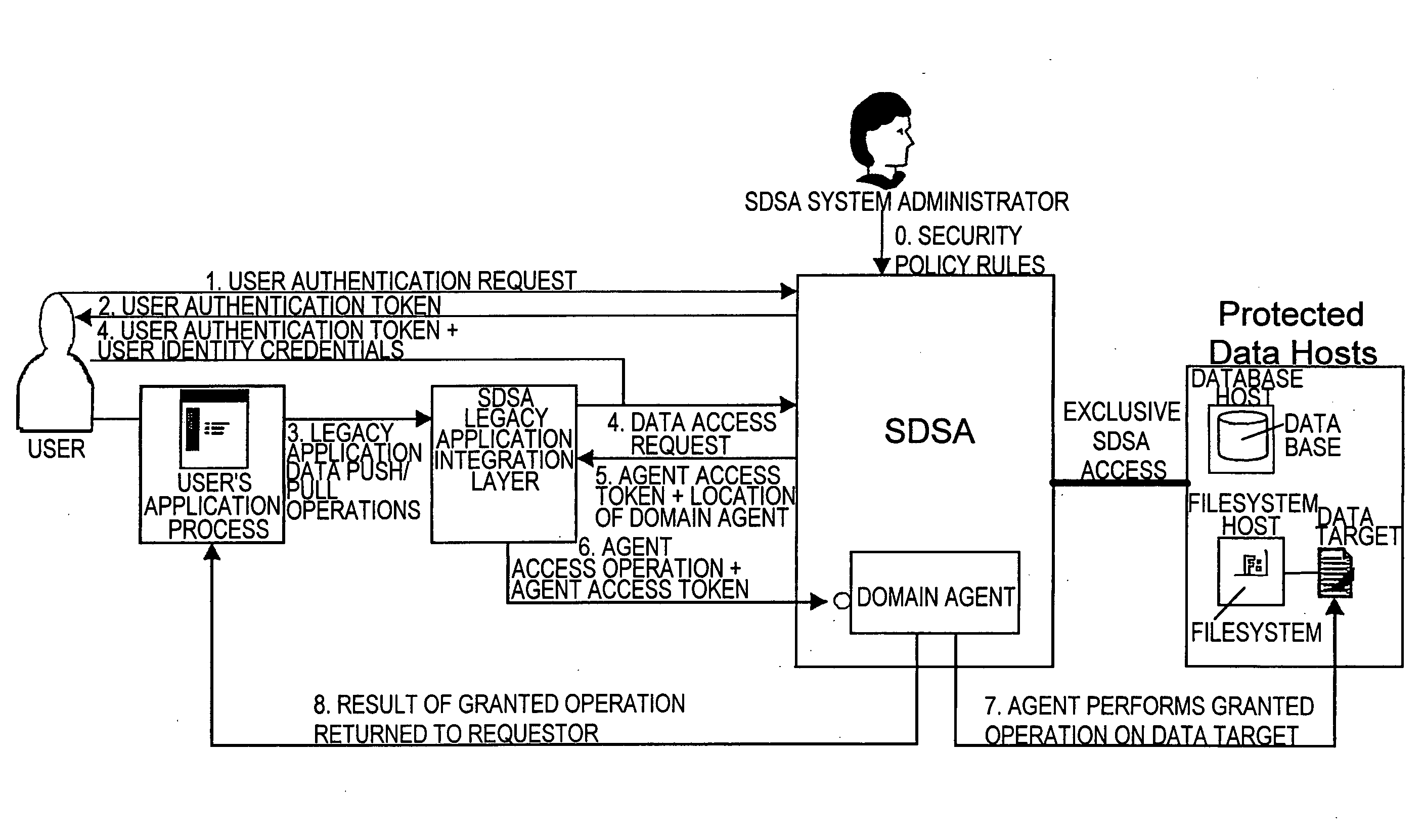
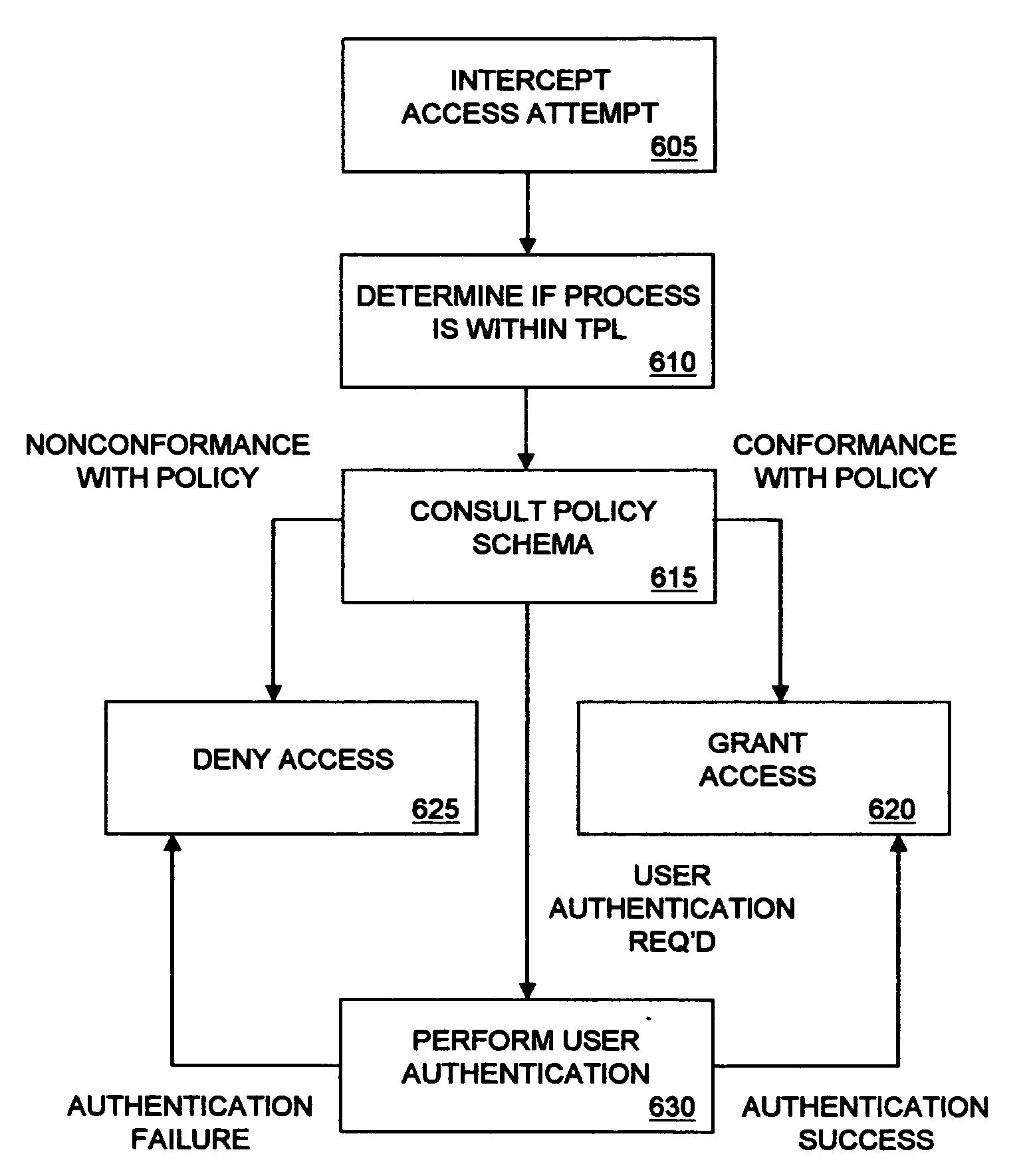
There are provided methods and apparatuses for processing requests from requestors, methods and apparatuses for transmitting indicia representative of information from a first domain to a second domain, methods comprising, and apparatuses for, determining whether a requestor is authorized to perform a desired operation on a target comprising at least one element which comprises an information set of indicia and arrangements of stored data, as well as computer-readable media having computer-executable commands for performing the same. In some aspects of the present invention, there are provided high-assurance data security apparatuses and methods, in particular, user data protection via enforcement of policy-based access control.
Owner:SENSIS CORPORATION
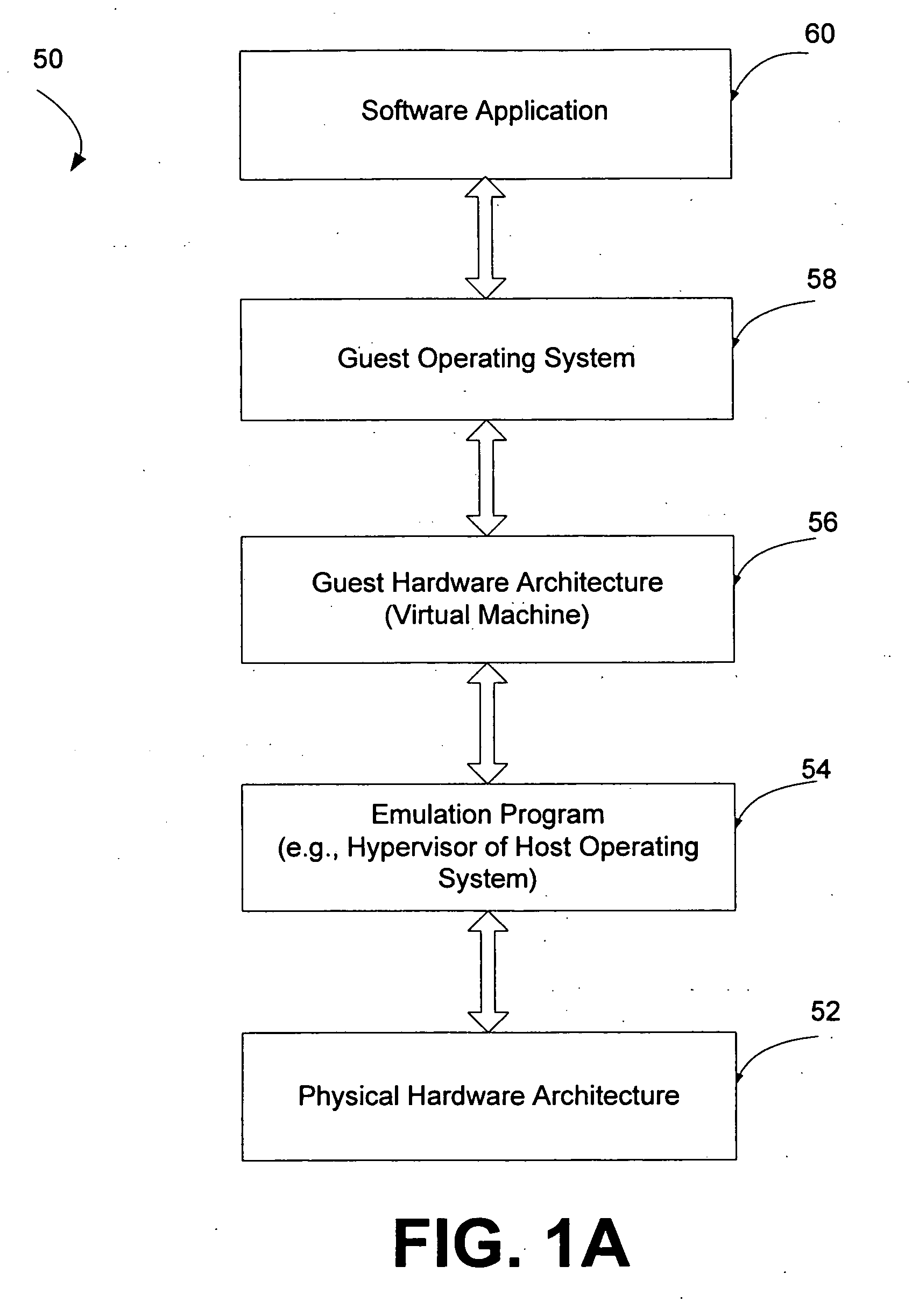
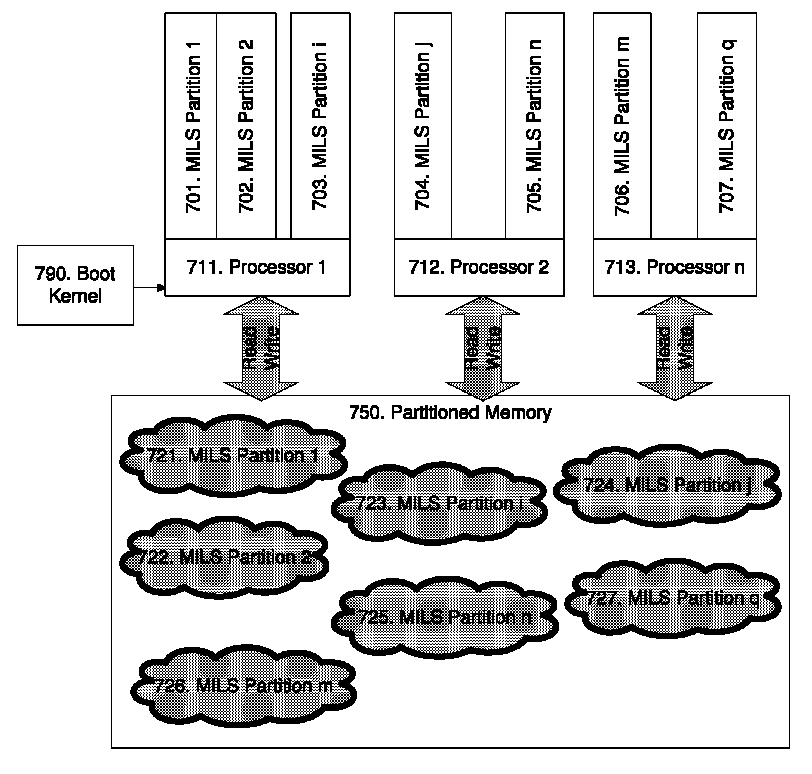
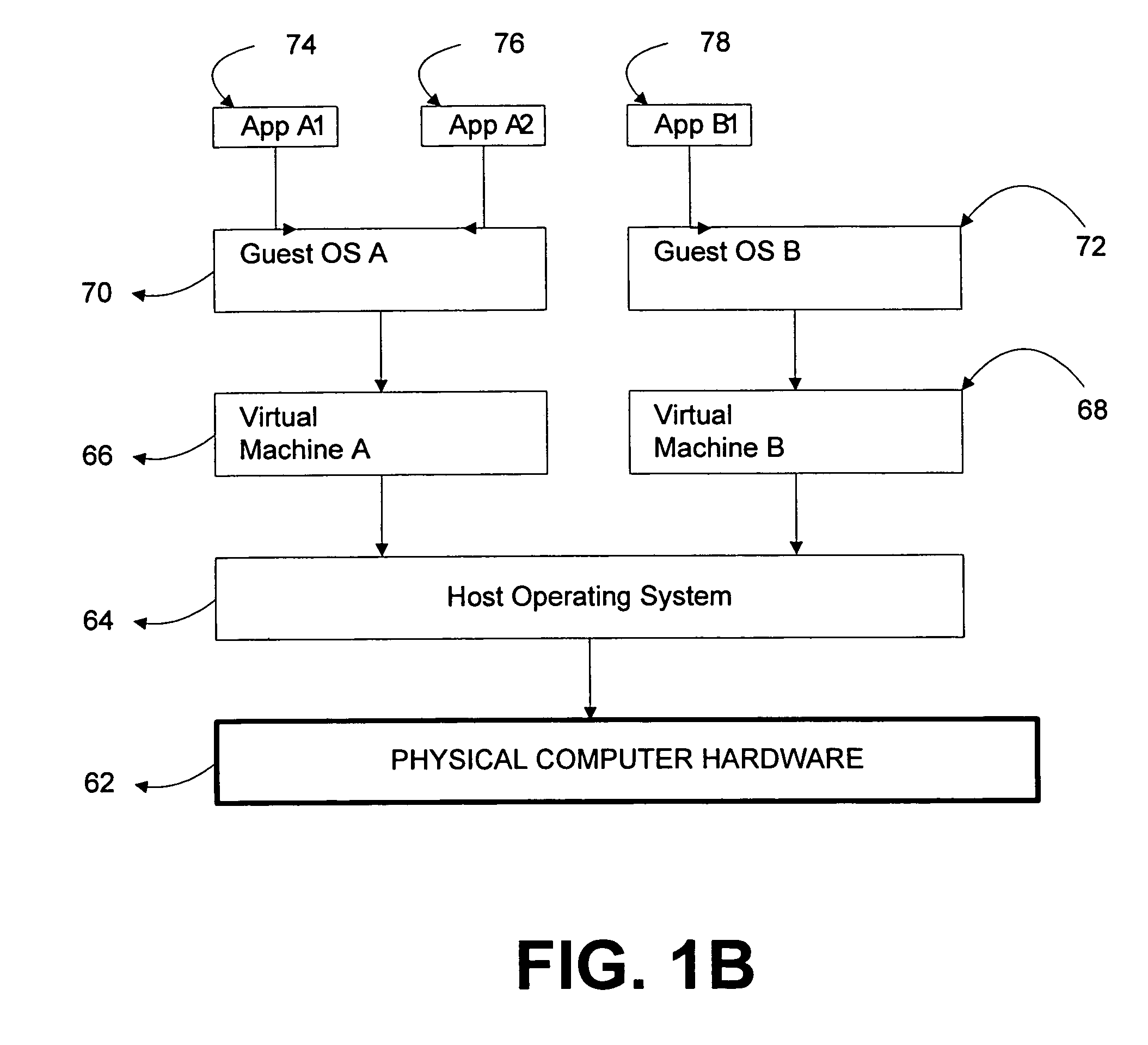
Local secure service partitions for operating system security
ActiveUS20060236127A1Guaranteed growthSmall sizeVolume/mass flow measurementUnauthorized memory use protectionOperational systemOperating system security
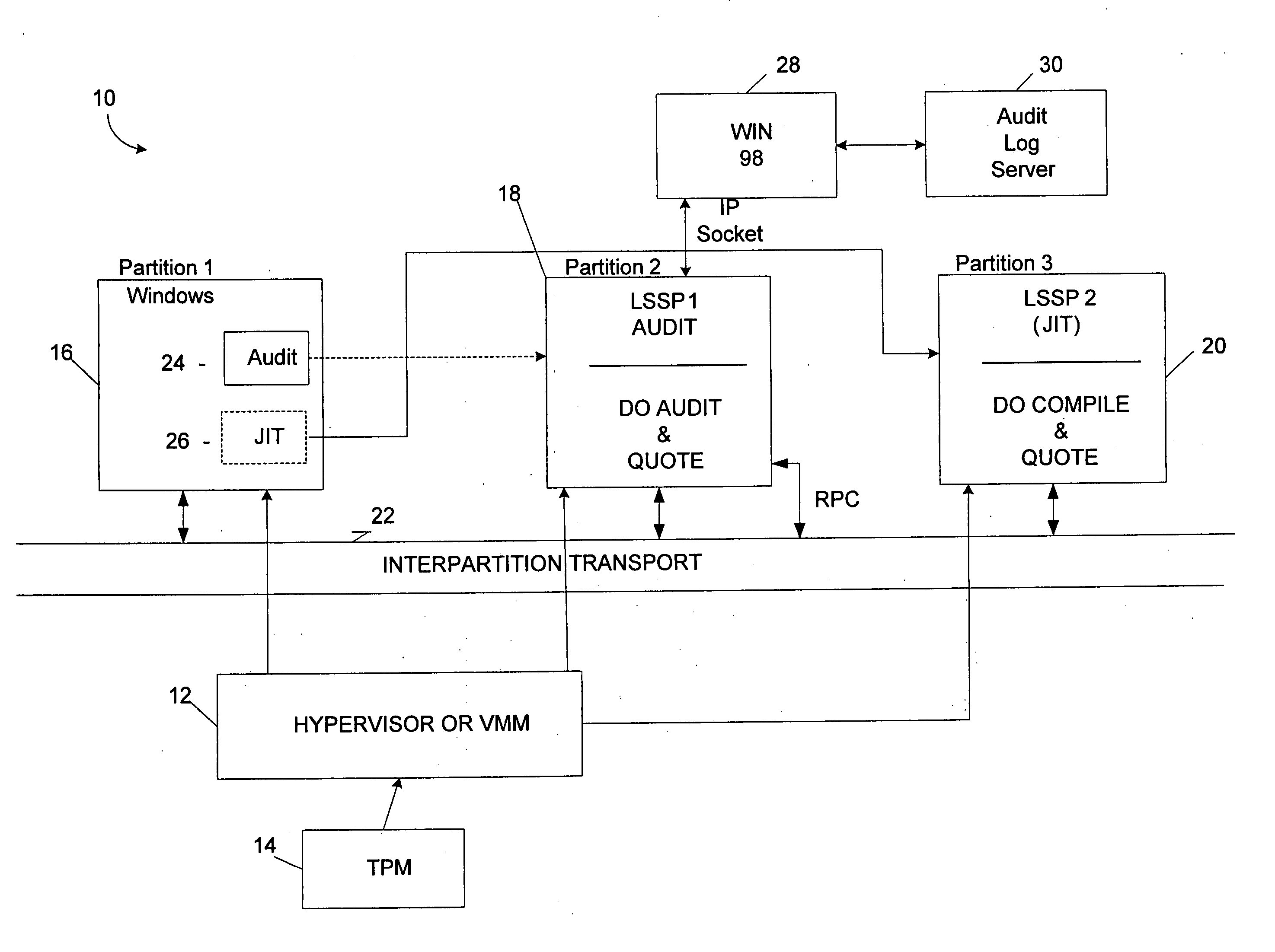
Systems and methods provide multiple partitions hosted on an isolation technology such as a hypervisor where at least one of the partitions, a local secure service partition (LSSP), provides security services to other partitions. The service partitions (LSSPs) host those high assurance services that require strict security isolation, where the service can be shared across partitions and accessed even when the user is not connected to a network. The LSSP also can certify the results of any computation using a key signed by a TPM attestation identity key (AIK), or other key held securely by the hypervisor or a service partition. The LSSPs may be configured to provide trusted audit logs, trusted security scans, trusted cryptographic services, trusted compilation and testing, trusted logon services, and the like.
Owner:MICROSOFT TECH LICENSING LLC
Achieving high assurance connectivity on computing devices and defeating blended hacking attacks
ActiveUS7490350B1Improve integrityAttack is still possibleMultiple digital computer combinationsInternal/peripheral component protectionCommunications systemPrivate network
System and techniques for protecting wireless communication systems from blended electronic attacks that may combine wireless and computer attacks. One embodiment is an integrated hardware and software firewall / protection system that provides a protection scheme that may include an additional functional processing layer between the hardware firewall and a mobile terminal. This additional functional processing layer performs an extra layer of communications and security processing, including such features as management of Internet Connection Firewall (ICF) functions, key generation for firewall and virtual private network (VPN) functions, and packet inspection and filtering.
Owner:TECNICA
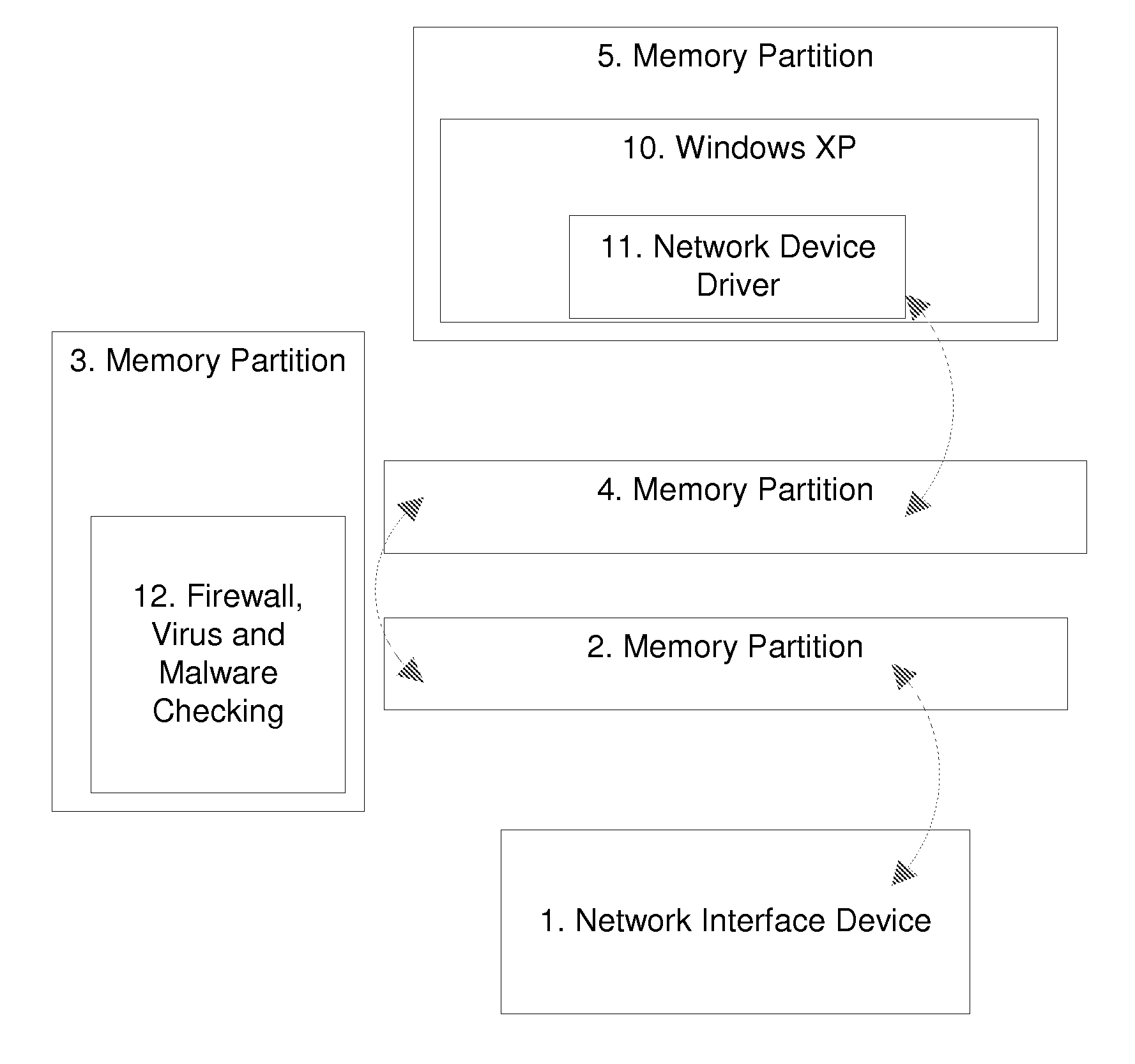
Methods and Systems for Achieving High Assurance Computing using Low Assurance Operating Systems and Processes
ActiveUS20080016313A1Improve protectionImprove securityDigital data processing detailsUnauthorized memory use protectionOperational systemTerm memory
A computing system contains and uses a partitioning microkernel (PMK) or equivalent means for imposing memory partitioning and isolation prior to exposing data to a target operating system or process, and conducts continuing memory management whereby data is validated by security checks before or between sequential processing steps. The PMK may be used in conjunction with an Object Request Broker.
Owner:TECNICA
Trusted enclave for a computer system
ActiveUS20080077994A1High assurance protectionAvoid system resourcesDigital data processing detailsUser identity/authority verificationSoftware systemComputerized system
A trusted enclave for a software system of a computer node provides relatively high assurance protection of a section of the software system. The trusted enclave attempts to stop malware from compromising parts of the software system within the trusted enclave. If a software system process outside the trusted enclave becomes compromised, the compromised process may be prevented from compromising software system resources within the trusted enclave. Compromise of a process or resource of the software system refers to, for example, malware access, alteration or control of the process or resource.
Owner:APPGUARD LLC
Trusted computer system
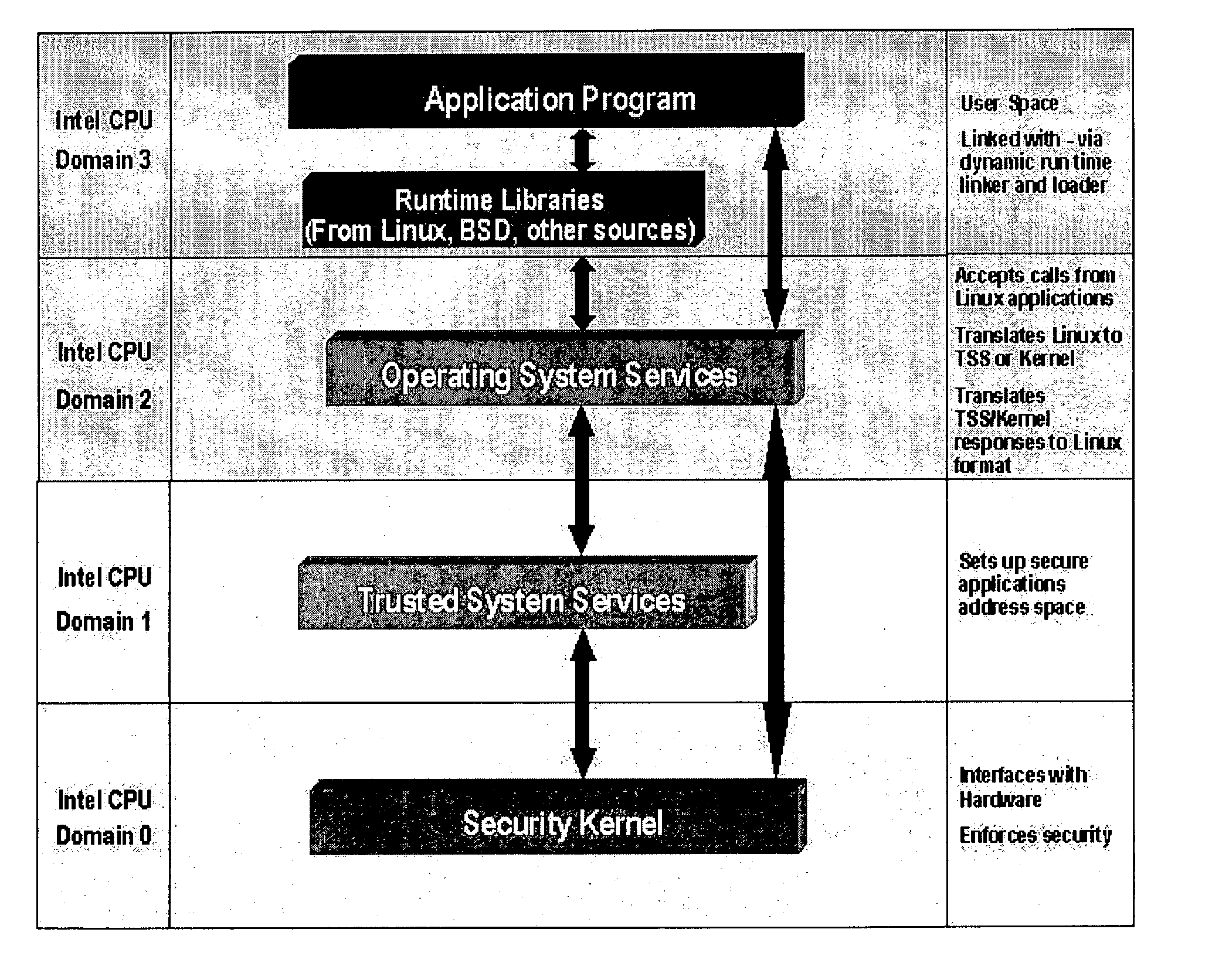
InactiveUS7103914B2Improve robustnessHigh level of assuranceMemory loss protectionDigital data processing detailsOperational systemGNU/Linux
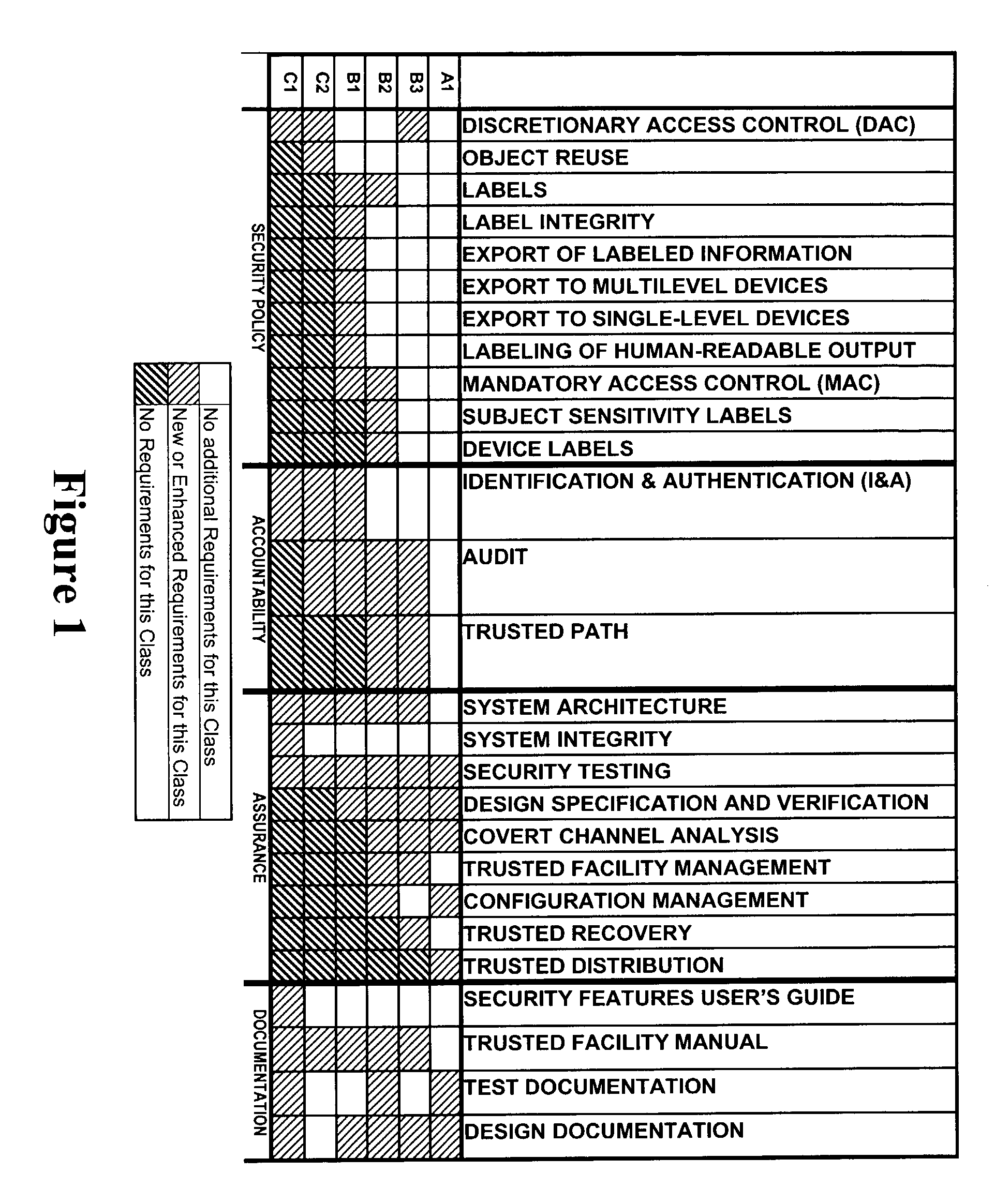
A trusted computer system that offers Linux® compatibility and supports contemporary hardware speeds. It is designed to require no porting of common applications which run on Linux, to be easy to develop for, and to allow the use of a wide variety of modern development tools. The system is further designed to meet or exceed the Common Criteria EAL-5 or higher rating through incorporation of required security features, as well as a very high level of assurance for handling data at a wide range of sensitivity (e.g., classification) levels in a wide range of operational environments. This is achieved through the implementation of a well-layered operating system which has been designed from the ground up to enforce security, but which also supports Linux operating system functions and methods.
Owner:BAE SYST INFORMATION & ELECTRONICS SYST INTERGRATION INC +1
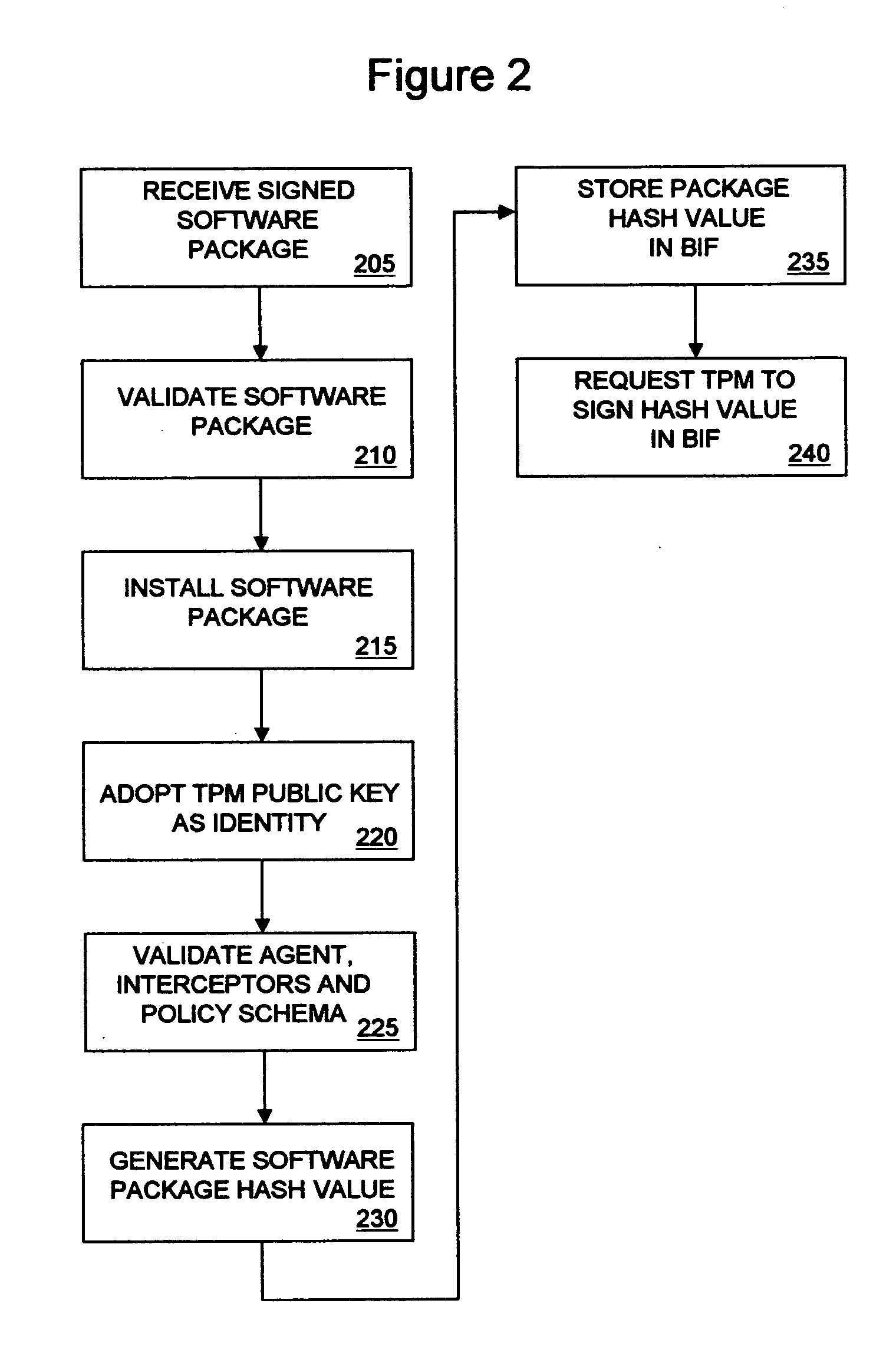
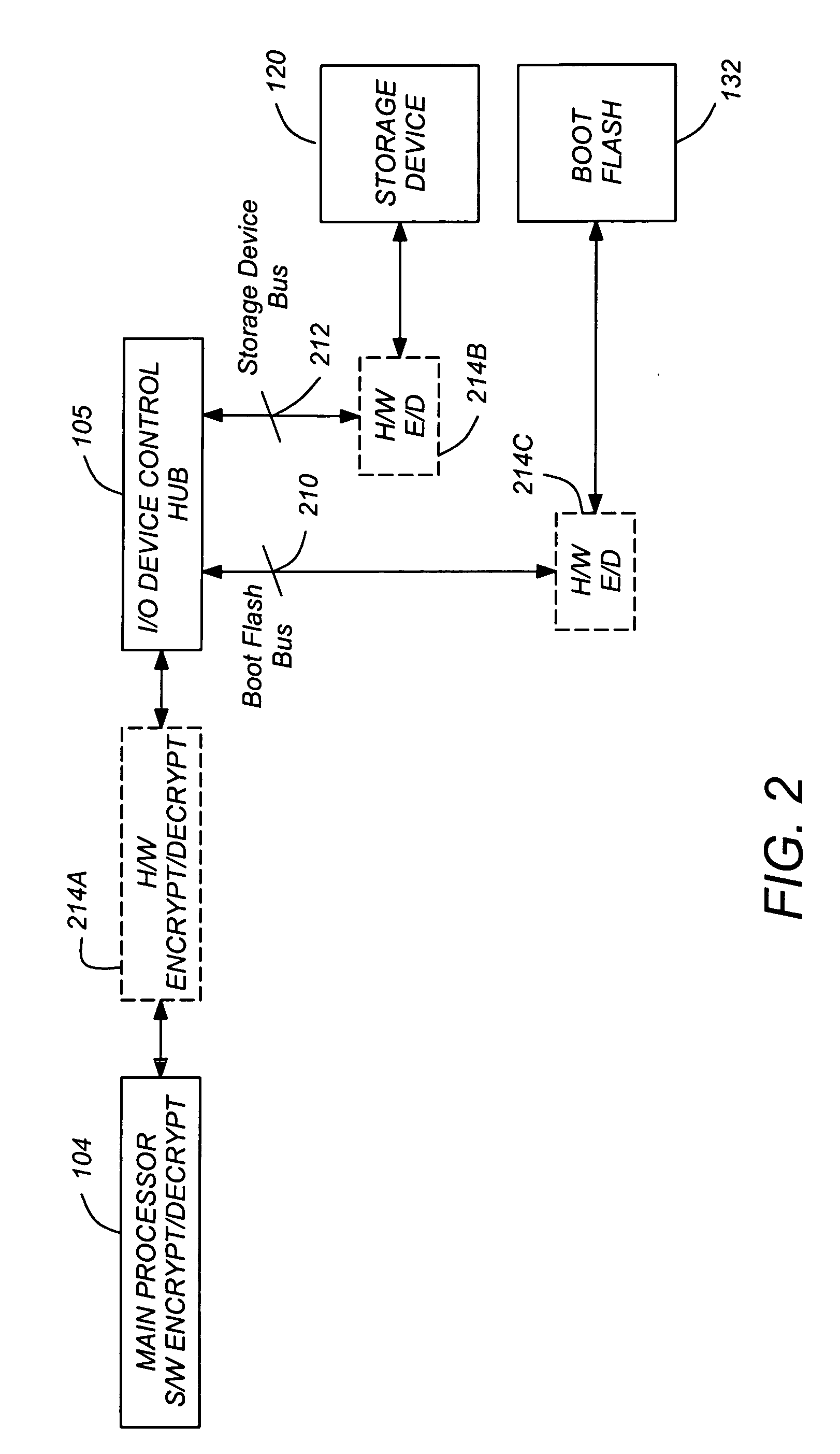
High-assurance secure boot content protection
InactiveUS20060026417A1Safe storageHardens” the encryption processDigital computer detailsComputer security arrangementsHard disc driveMaster processor
A method and apparatus for high assurance boot processing is disclosed. A trusted processor is used to authenticate a trusted boot program and in conjunction with a selector, to provide the authenticated boot program to a boot memory where it can be accessed by a main processor to execute the bootup sequence. The trusted processor also provides a command for the main processor to write a data sequence to a hard drive or similar device, and monitors the data written by the main processor to verify that the data has not been tampered with or otherwise compromised.
Owner:INFORMATION ASSURANCE SYST +1
Multi-level security software architecture
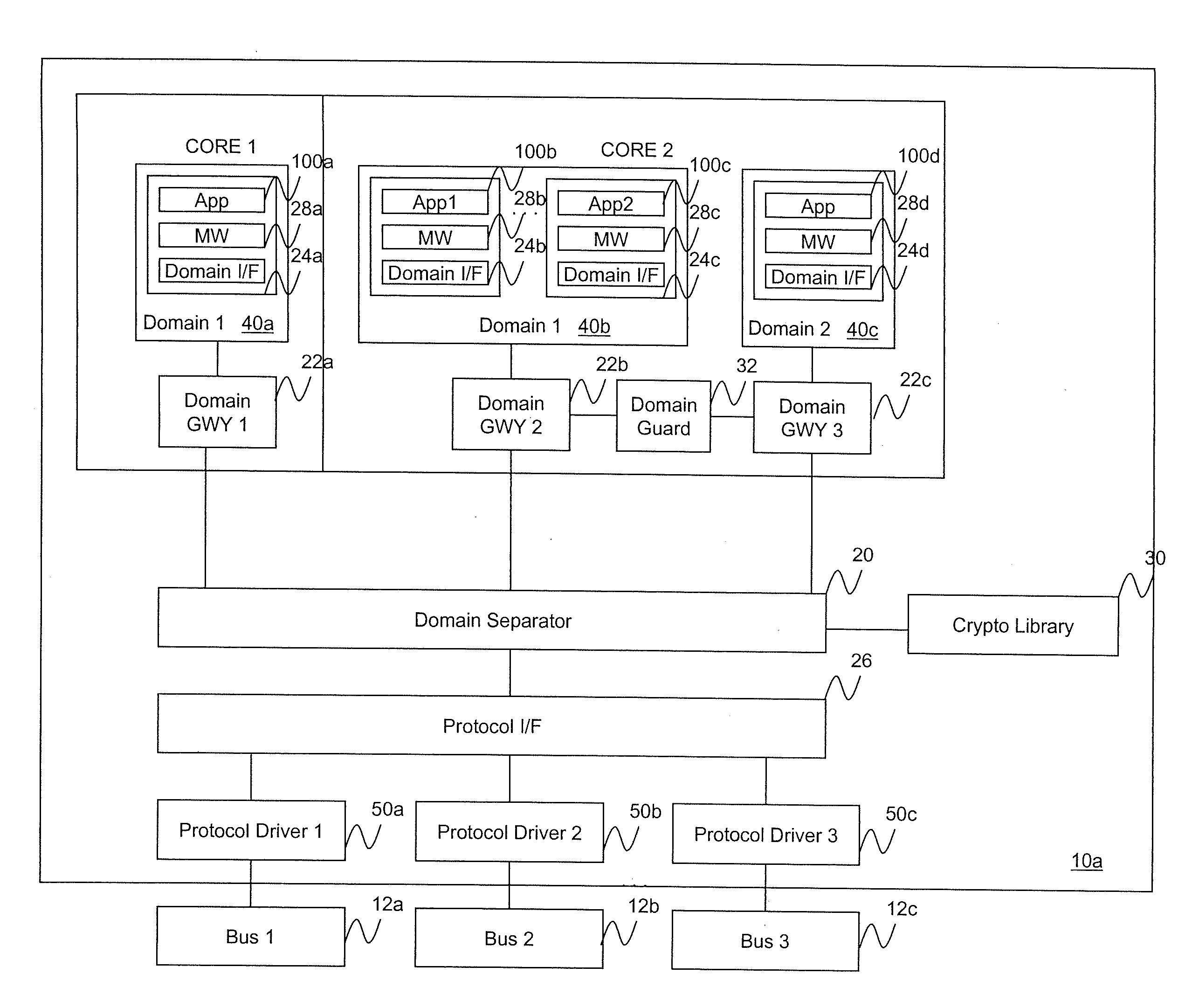
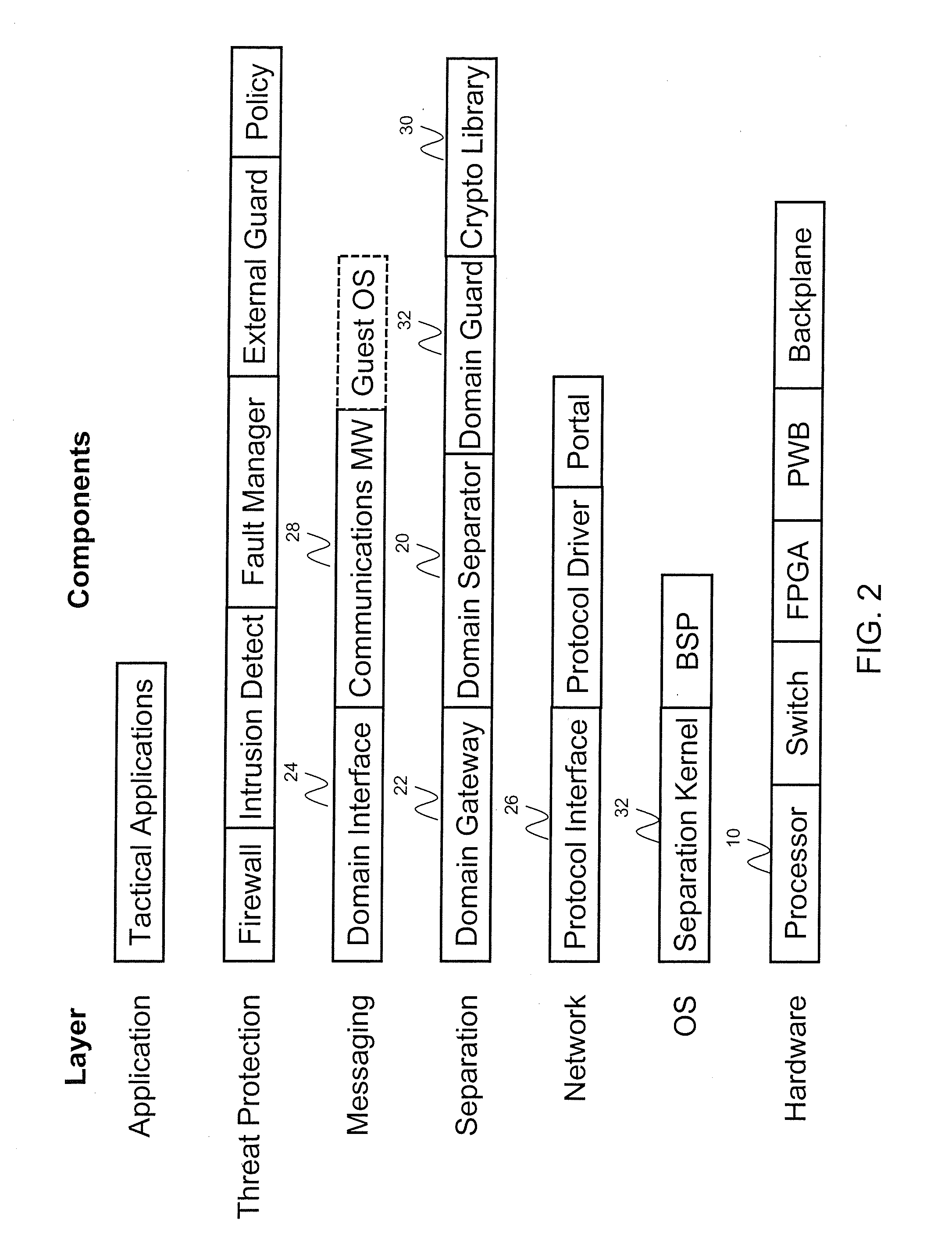
ActiveUS20120066509A1Unauthorized memory use protectionHardware monitoringSecurity softwareFull data
A multi-level security software architecture includes various components configured to provide full data separation across multiple processors while limiting the number and size of high assurance components. The architecture includes a domain separator for ensuring that messages exchanged between domains that are distributed on different microprocessors are securely routed between domain members. The domain separator verifies a message label including a domain identifier provided by a domain gateway and cryptographically binds the message label to each message via cryptographic keys. This prevents misrouting messages caused by accidental or malicious corruption of message labels. Additionally, the domain separator can encrypt messages as necessary to enforce data separation on shared network buses. The domain separator is also responsible for managing the cryptographic keys used to label or encrypt messages.
Owner:FORCEPOINT FEDERAL
System for handling processed meat and poultry products
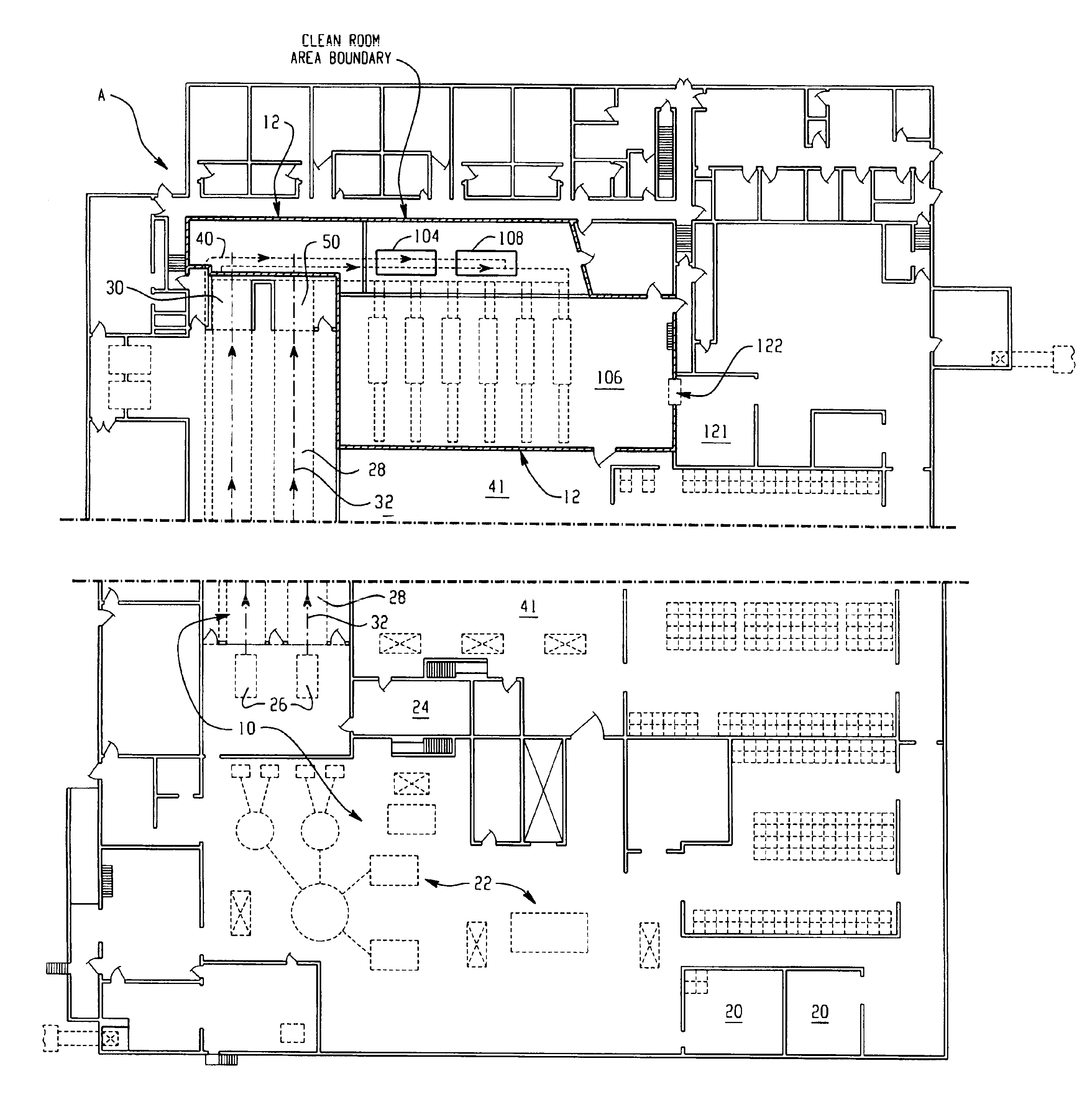
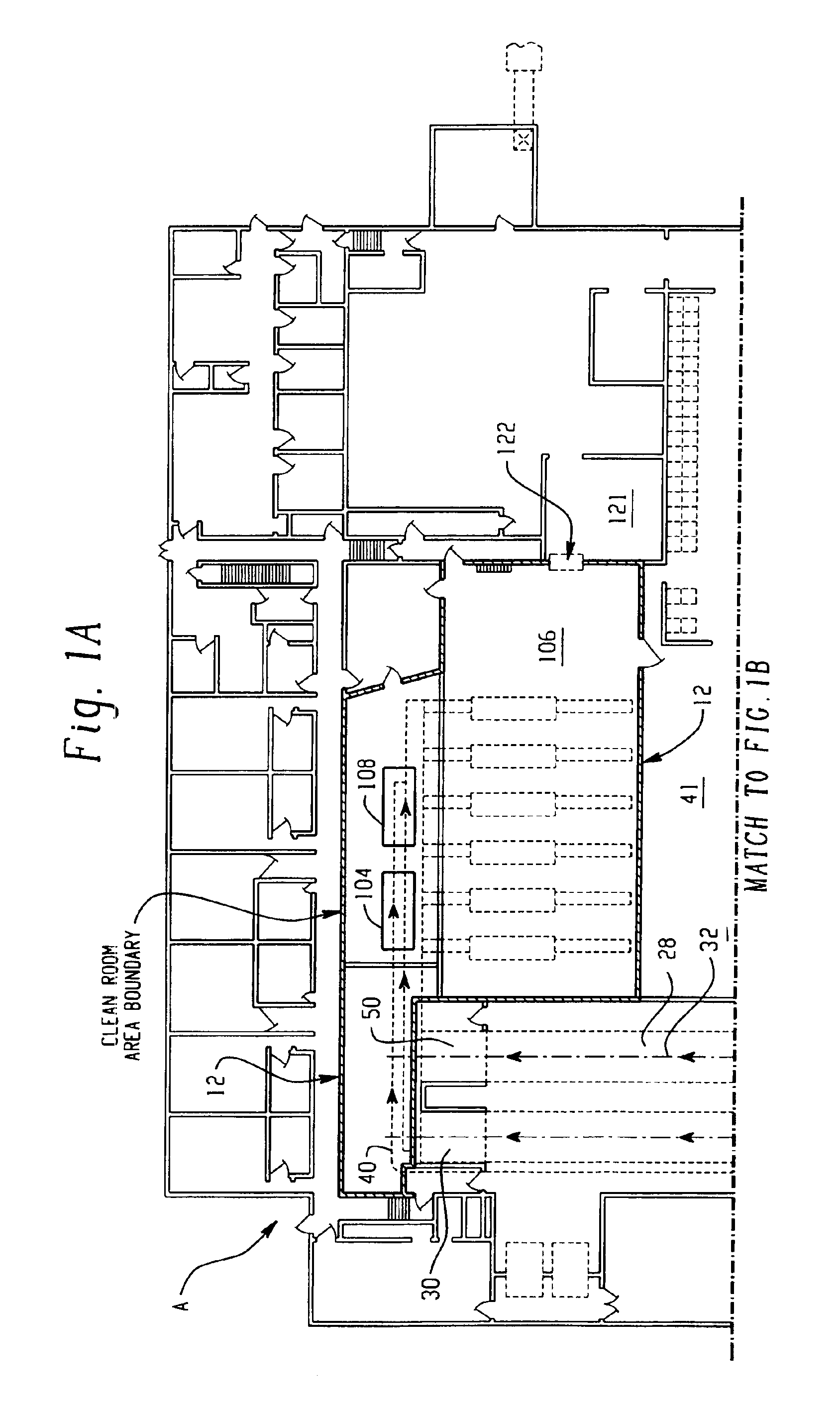
InactiveUS6964788B2Apparent advantageObvious advantagesMeat/fish preservation using liquidsSausage casingsPathogenic microorganismPoultry product
Food products, such as precooked meats, sausages, and the like are microbially decontaminated in their cooking packages to remove surface microorganism contamination from the packages. The cooking packages are removed and the food products optionally subjected to further processing, such as slicing, and then packaged in aseptic packaging. The microbial decontamination step, further processing and packaging are carried out in a clean room which is maintained to a high level of sterilization or disinfection to minimize or eliminate contamination of the food products with pathogenic microorganisms such as Listeria Monocytogenes. The food products thus leave the packaging plant with a much higher assurance of food safety than is found in a conventional packaging plant.
Owner:STERIS CORP
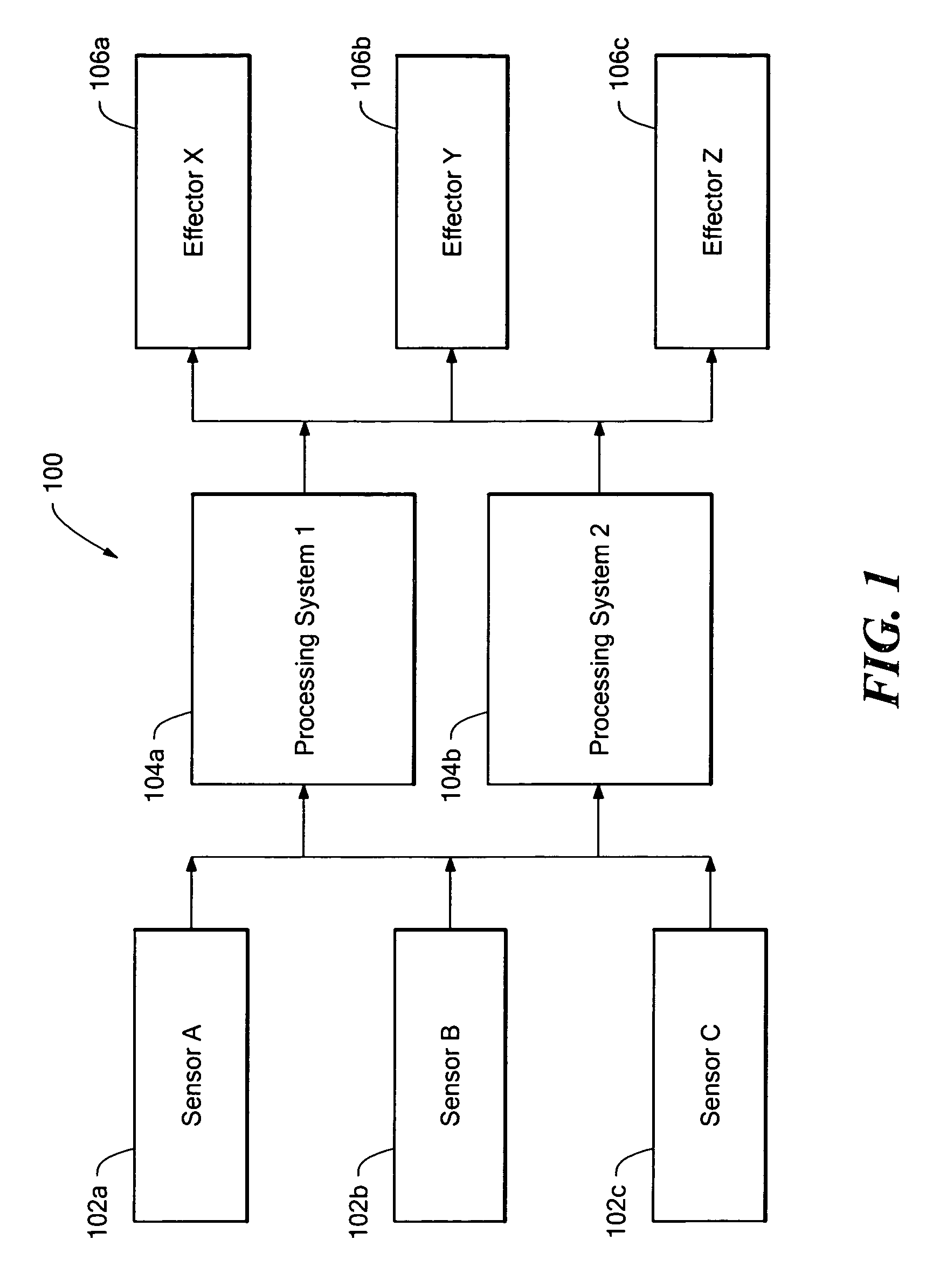
Methods and apparatus for processor system having fault tolerance
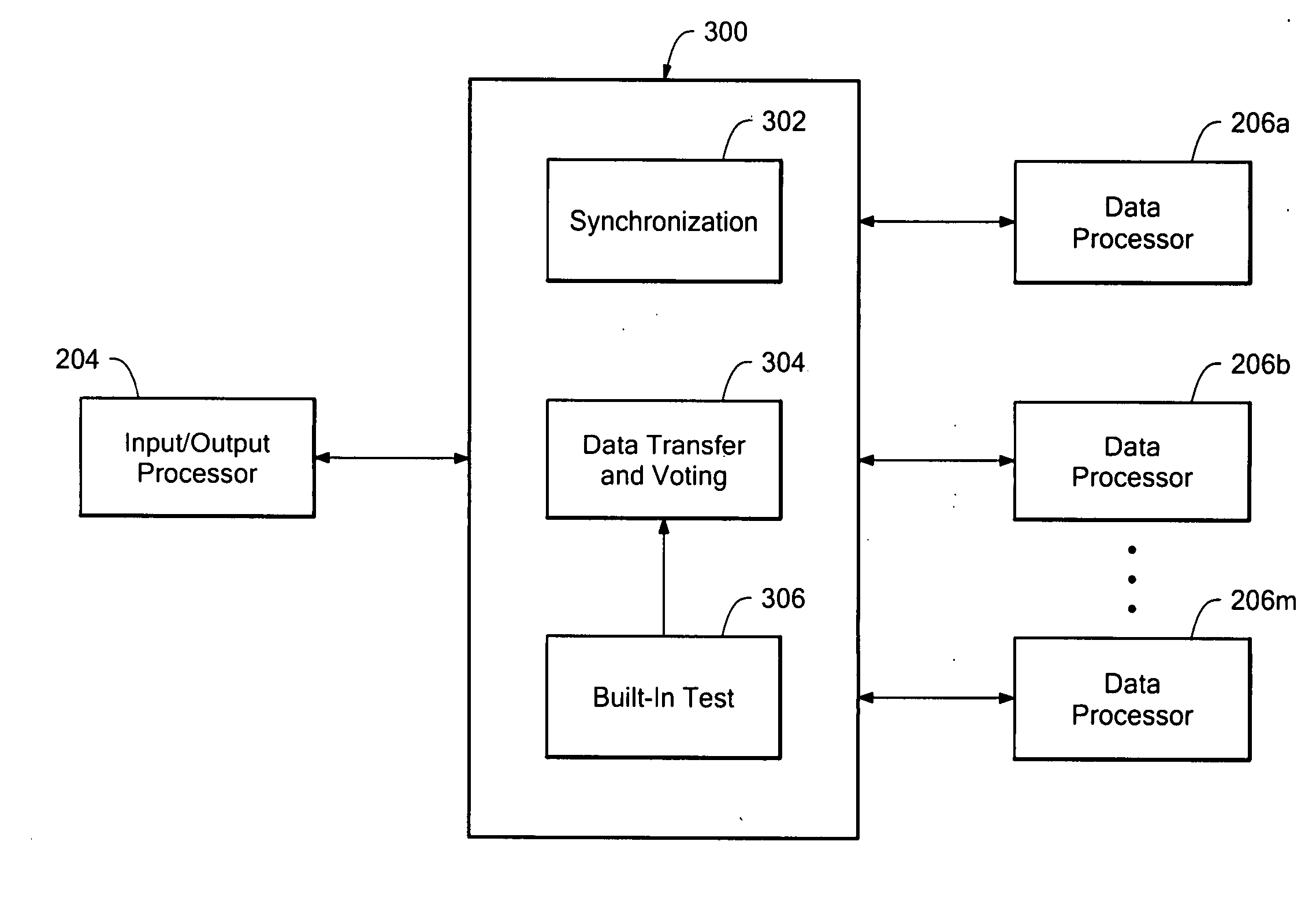
ActiveUS20070033511A1Easy to refreshEasy to upgradeError preventionDigital data processing detailsFault toleranceHandling system
A high assurance processing system includes a plurality of data processors coupled in parallel, a bridge coupled to the input / output processor, and an input / output processor coupled to the bridge for coupling to a sensor and an effector. Sensor data passes to the bridge through the input / output processor for processing by the parallel data processors, which generate redundant effector data for comparison by the bridge to detect errors. If data matches are found, data is transmitted to the effector.
Owner:RAYTHEON CO
Trusted enclave for a computer system
ActiveUS7712143B2Digital data processing detailsUser identity/authority verificationSoftware systemComputerized system
A trusted enclave for a software system of a computer node provides relatively high assurance protection of a section of the software system. The trusted enclave attempts to stop malware from compromising parts of the software system within the trusted enclave. If a software system process outside the trusted enclave becomes compromised, the compromised process may be prevented from compromising software system resources within the trusted enclave. Compromise of a process or resource of the software system refers to, for example, malware access, alteration or control of the process or resource.
Owner:APPGUARD LLC
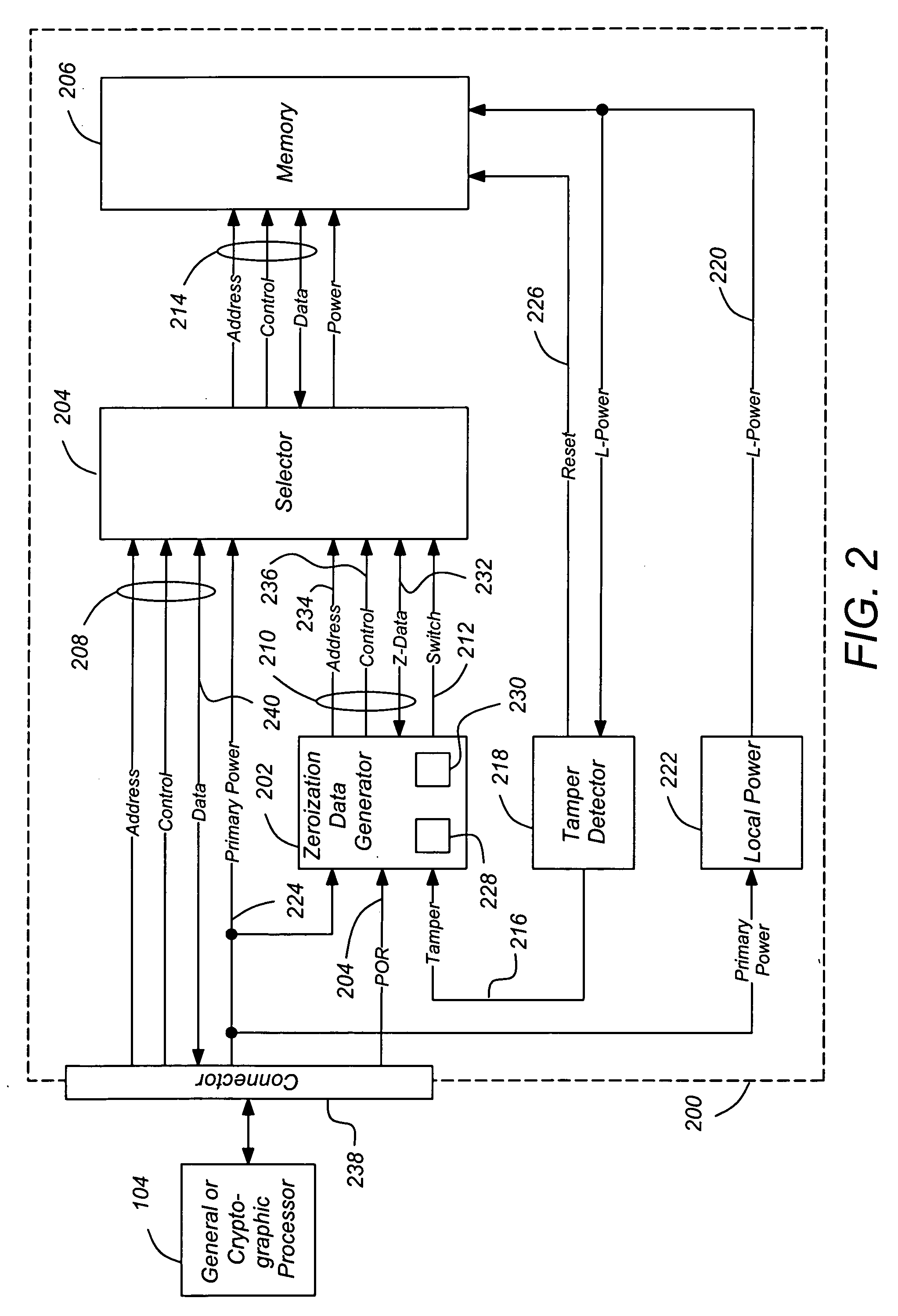
High-assurance processor active memory content protection
ActiveUS20060023486A1High assurance data zeroizationData recoveryDigital storageInternal/peripheral component protectionActive memoryTerm memory
A method and apparatus for preventing compromise of data stored in a memory by assuring the deletion of data and minimizing data remanence affects is disclosed. The method comprises the steps of monitoring the memory to detect tampering, and if tampering is detected, generating second signals having second data differing from the first data autonomously from the first processor; providing the generated second signals to the input of the memory; and storing the second data in the memory. Several embodiments are disclosed, including self-powered embodiments and those which use separate, dedicated processors to generate, apply, and verify the zeroization data.
Owner:SAFENET
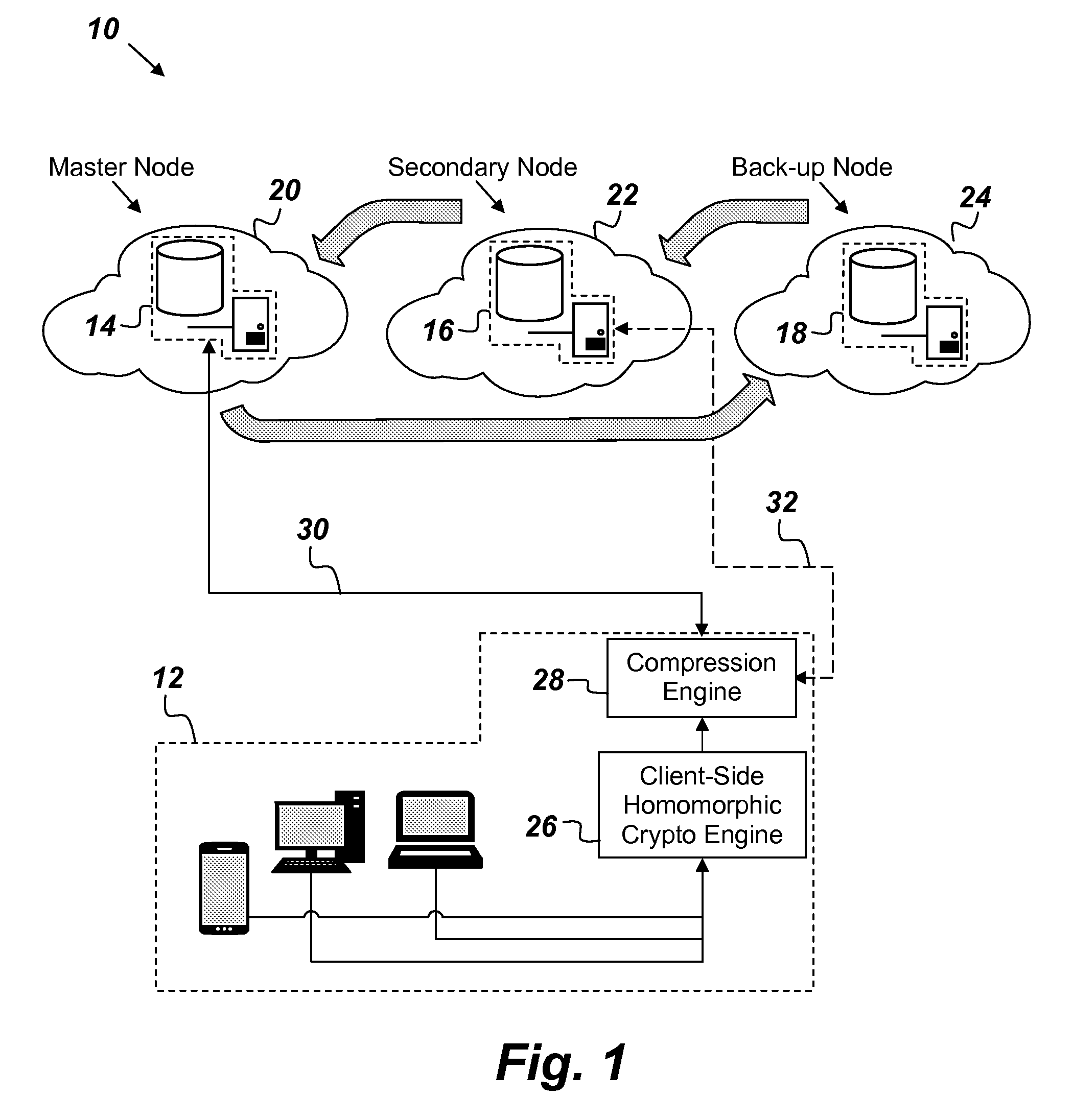
System and Method for High-Assurance Data Storage and Processing based on Homomorphic Encryption
ActiveUS20160323098A1Quality of serviceLower quality of serviceKey distribution for secure communicationSoftware simulation/interpretation/emulationQuality of serviceClient-side
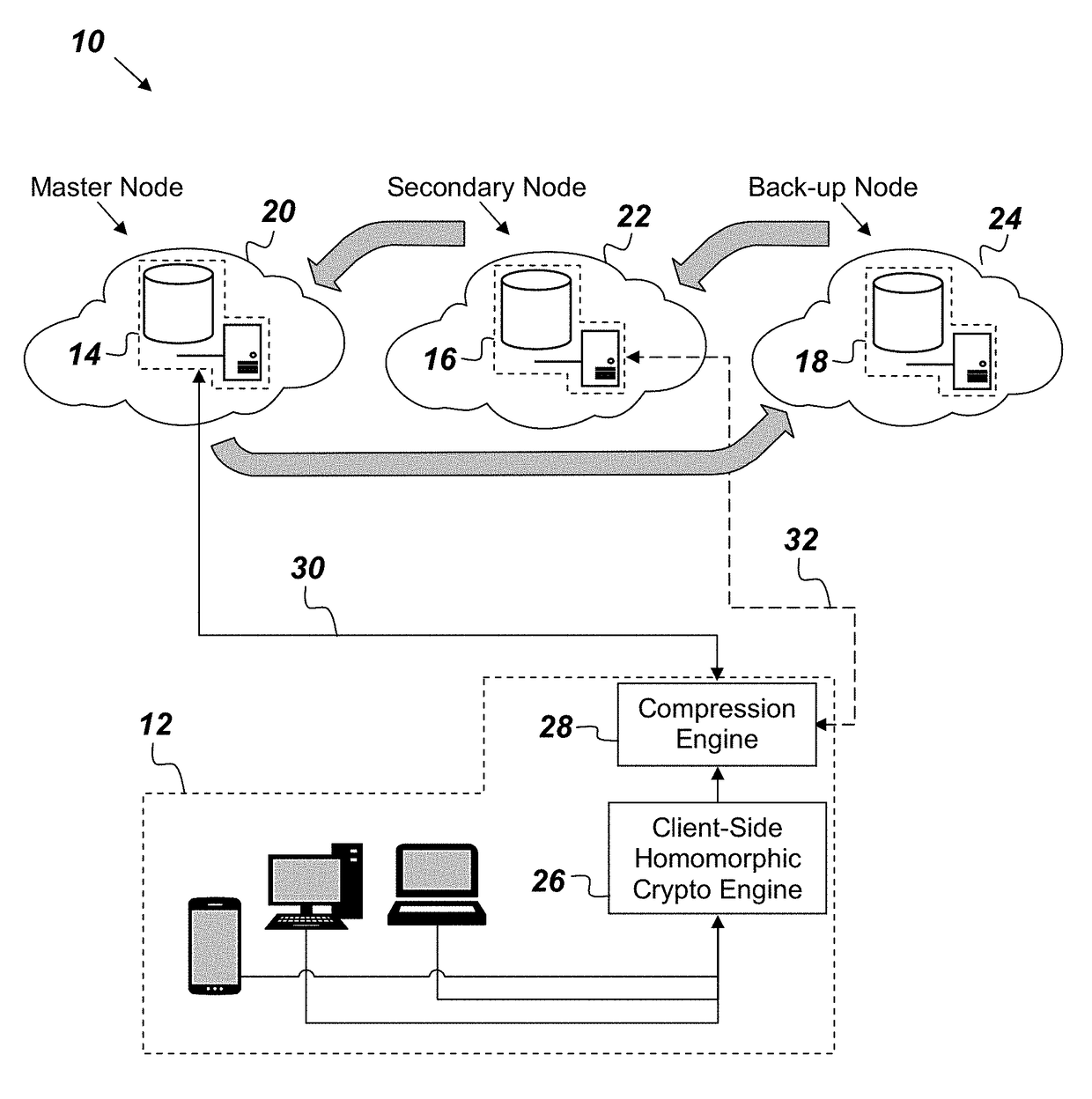
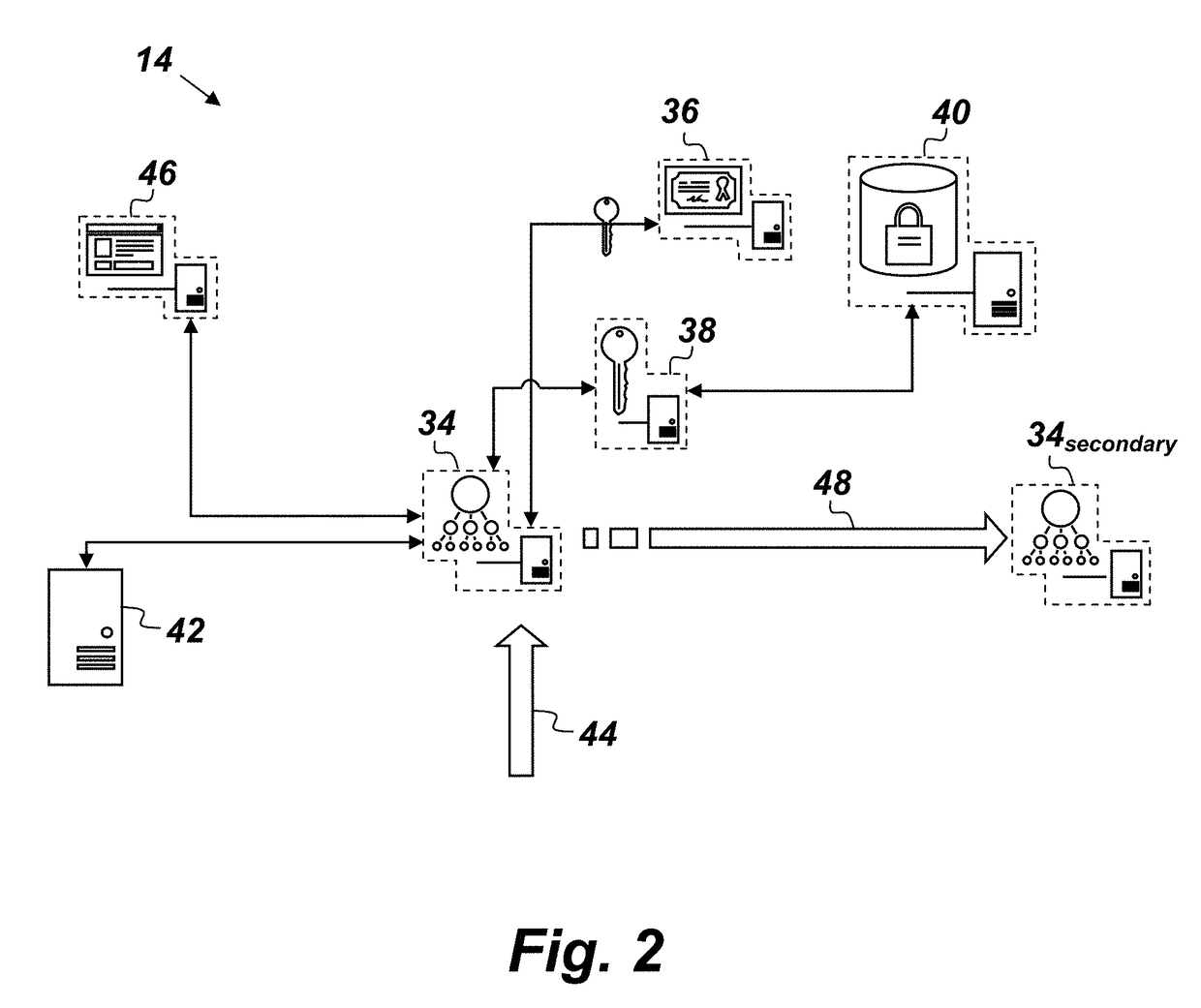
A key value storage (KVS) system comprising: a client-side agent configured to encrypt data; three nodes hosted respectively in three cloud service providers, wherein each node comprises: a management node configured to receive encrypted data from the client-side agent, a homomorphic encryption (HE) key manager configured to fetch a public key of a given object in the KVS system, a homomorphic encryption and processing engine configured to execute commands over the encrypted data without decrypting it, a homomorphic memory store, a hypervisor configured to monitor performance of the management node in order to assess the quality of service of the management node; and wherein each node serves on a rotating basis in a master node role, a secondary node role, or a back-up node role, wherein the nodes rotate their roles when the master node's hypervisor detects a reduced quality of service of the master node's management node.
Owner:THE UNITED STATES OF AMERICA AS REPRESENTED BY THE SECRETARY OF THE NAVY
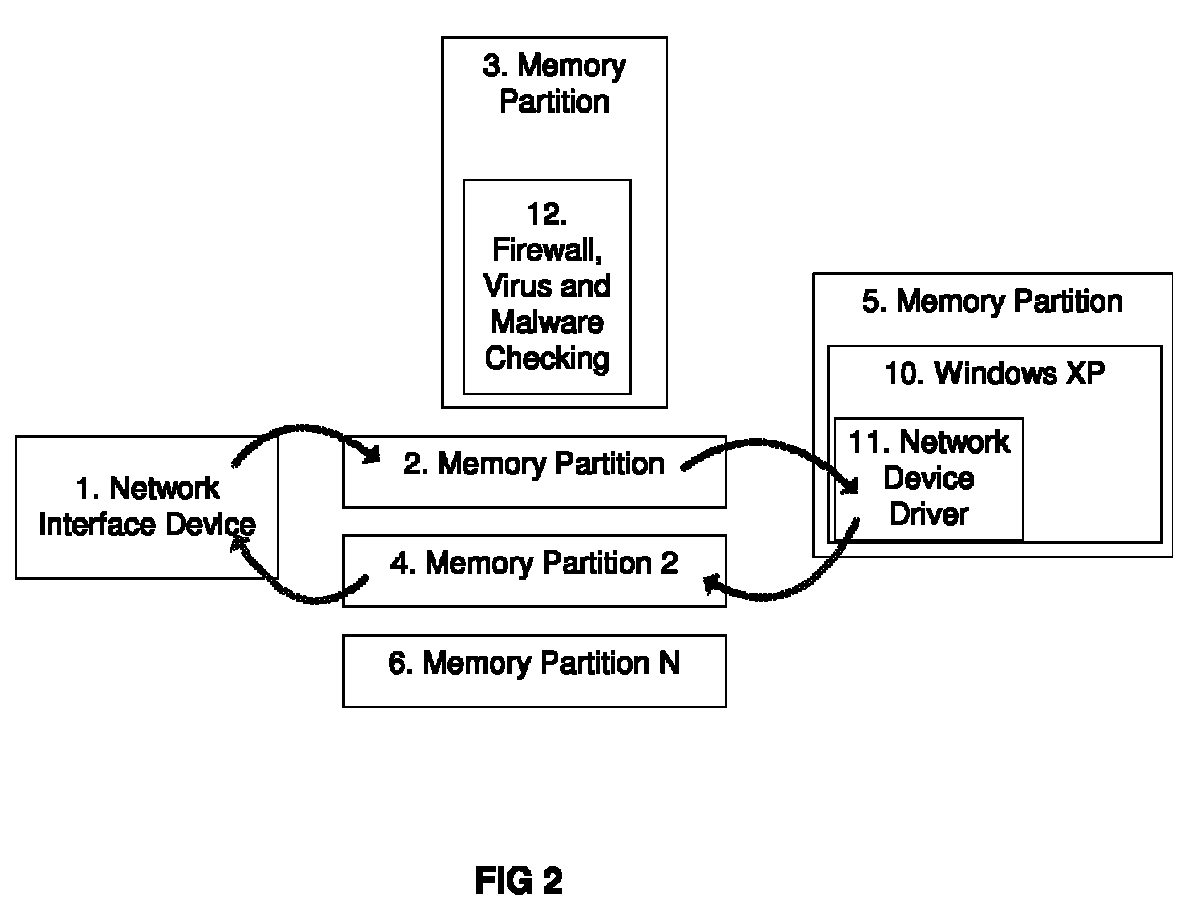
High-assurance file-driven content filtering for secure network server
ActiveUS20070204337A1Solve problemsMemory loss protectionError detection/correctionFiltering rulesComputer science
A server for transferring data between networks. The server is programmed to perform the following steps: (a) creating a receiving process, a filtering process and a forwarding process, the filtering process being dictated by a file that specifies filtering rules, wherein: (b) the receiving process receives data transmitted from a source host; (c) the filtering process filters the transmitted data based on the filtering rules; and (d) the forwarding process forwards only filtered data to a destination host.
Owner:THE BOEING CO
Methods and systems for achieving high assurance computing using low assurance operating systems and processes
ActiveUS7840763B2Improve protectionImprove securityDigital data processing detailsUnauthorized memory use protectionOperational systemSecurity check
A computing system contains and uses a partitioning microkernel (PMK) or equivalent means for imposing memory partitioning and isolation prior to exposing data to a target operating system or process, and conducts continuing memory management whereby data is validated by security checks before or between sequential processing steps. The PMK may be used in conjunction with an Object Request Broker.
Owner:TECNICA
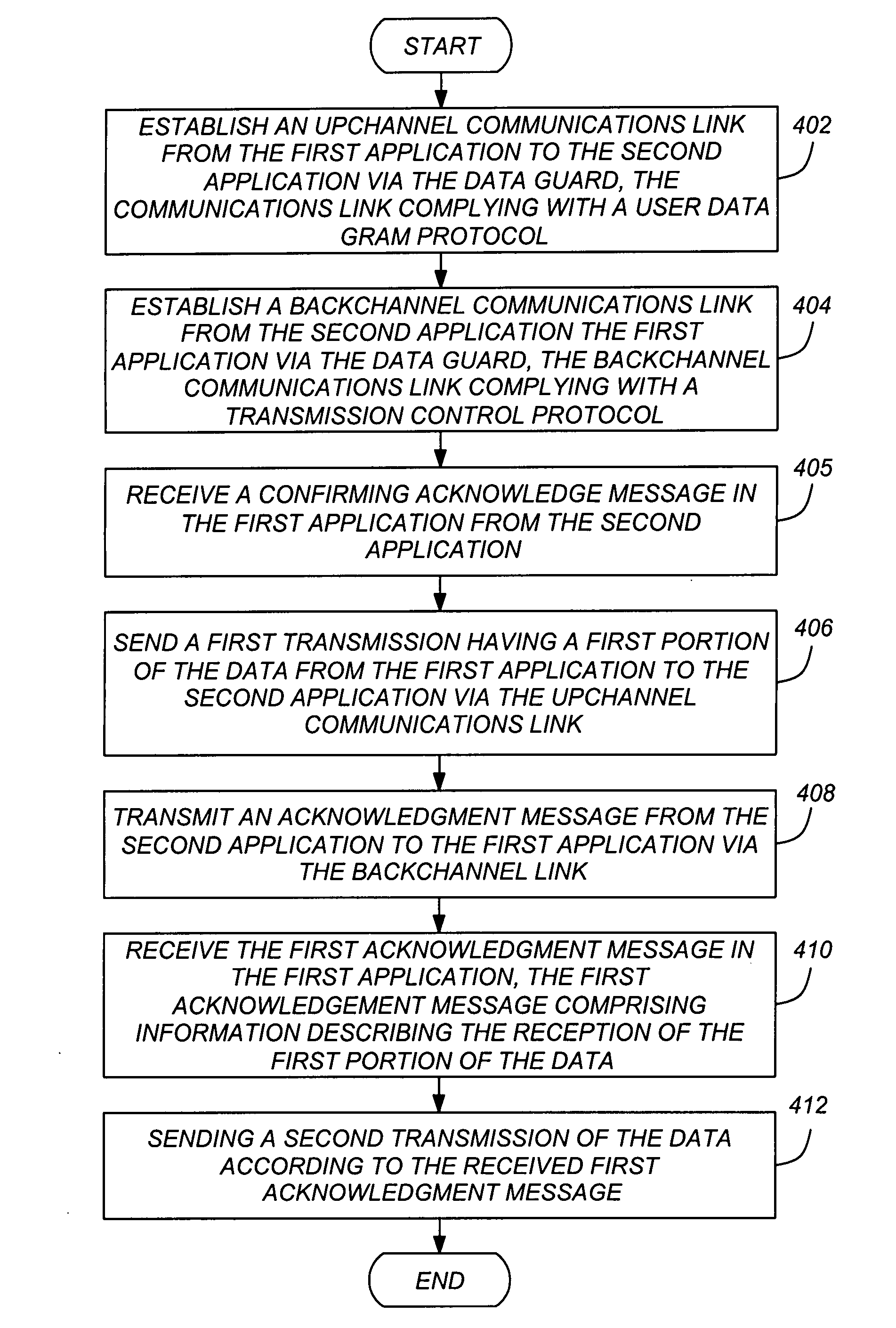
Method and apparatus for reliable, high speed data transfers in a high assurance multiple level secure environment
ActiveUS20080301799A1Inexpensively addedImprove securityComputer security arrangementsMultiple digital computer combinationsCommunication linkBackchannel
A method, apparatus for passing data from a first application at a first security level to a second application in a second security level higher than the first security level is disclosed. A backchannel communications link is established between the first application and the second application, and the backchannel link is used to transmit information such as an acknowledgement message to from the second application to the first application.
Owner:THE BOEING CO
Integration of high-assurance features into an application through application factoring
ActiveUS20050091661A1Better at ensuring correct behavior of their hosted environmentsTransformation of program codeDigital data processing detailsChain of trustApplication software
Application factoring or partitioning is used to integrate secure features into a conventional application. An application's functionality is partitioned into two sets according to whether a given action does, or does not, involve the handling of sensitive data. Separate software objects (processors) are created to perform these two sets of actions. A trusted processor handles secure data and runs in a high-assurance environment. When another processor encounters secure data, that data is sent to the trusted processor. The data is wrapped in such a way that allows it to be routed to the trusted processor, and prevents the data from being deciphered by any entity other than the trusted processor. An infrastructure is provided that wraps objects, routes them to the correct processor, and allows their integrity to be attested through a chain of trust leading back to base component that is known to be trustworthy.
Owner:MICROSOFT TECH LICENSING LLC
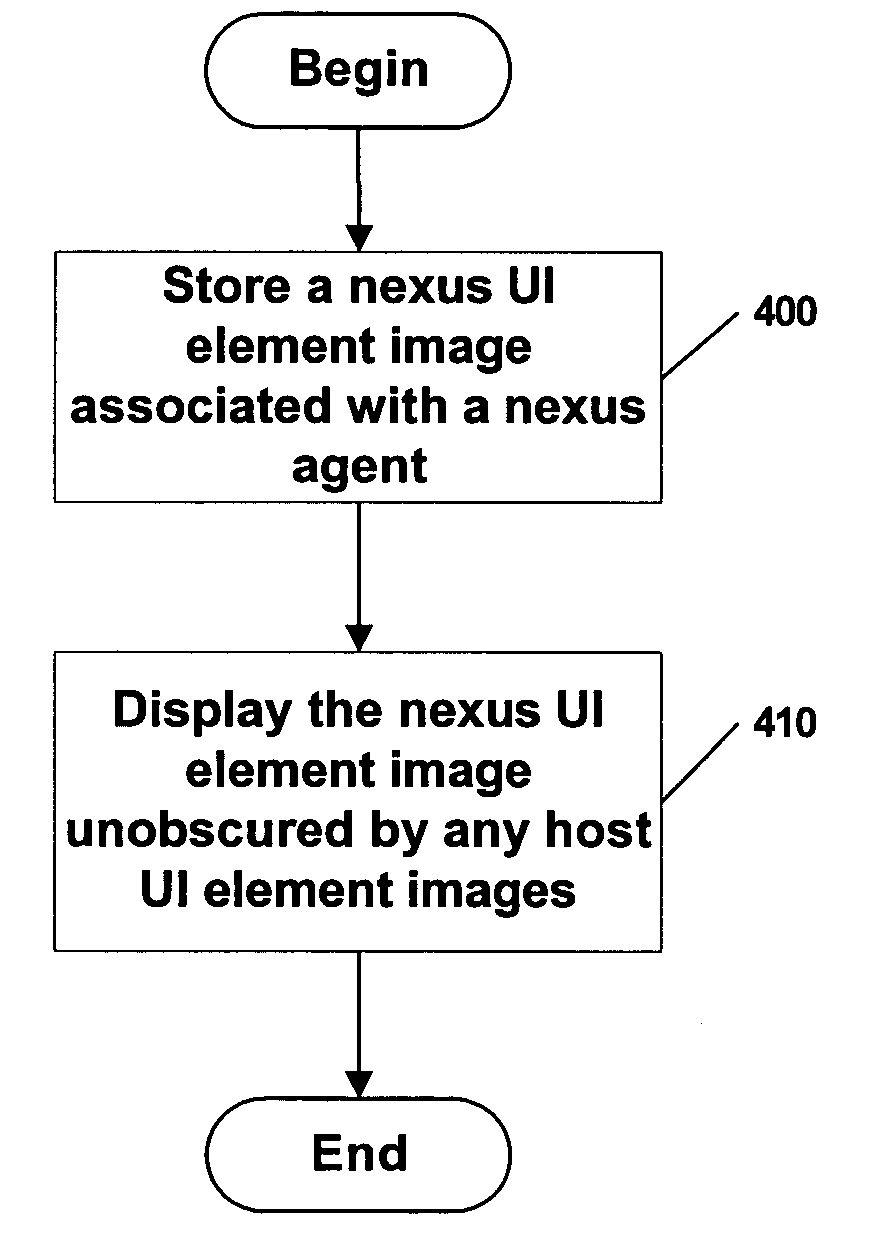
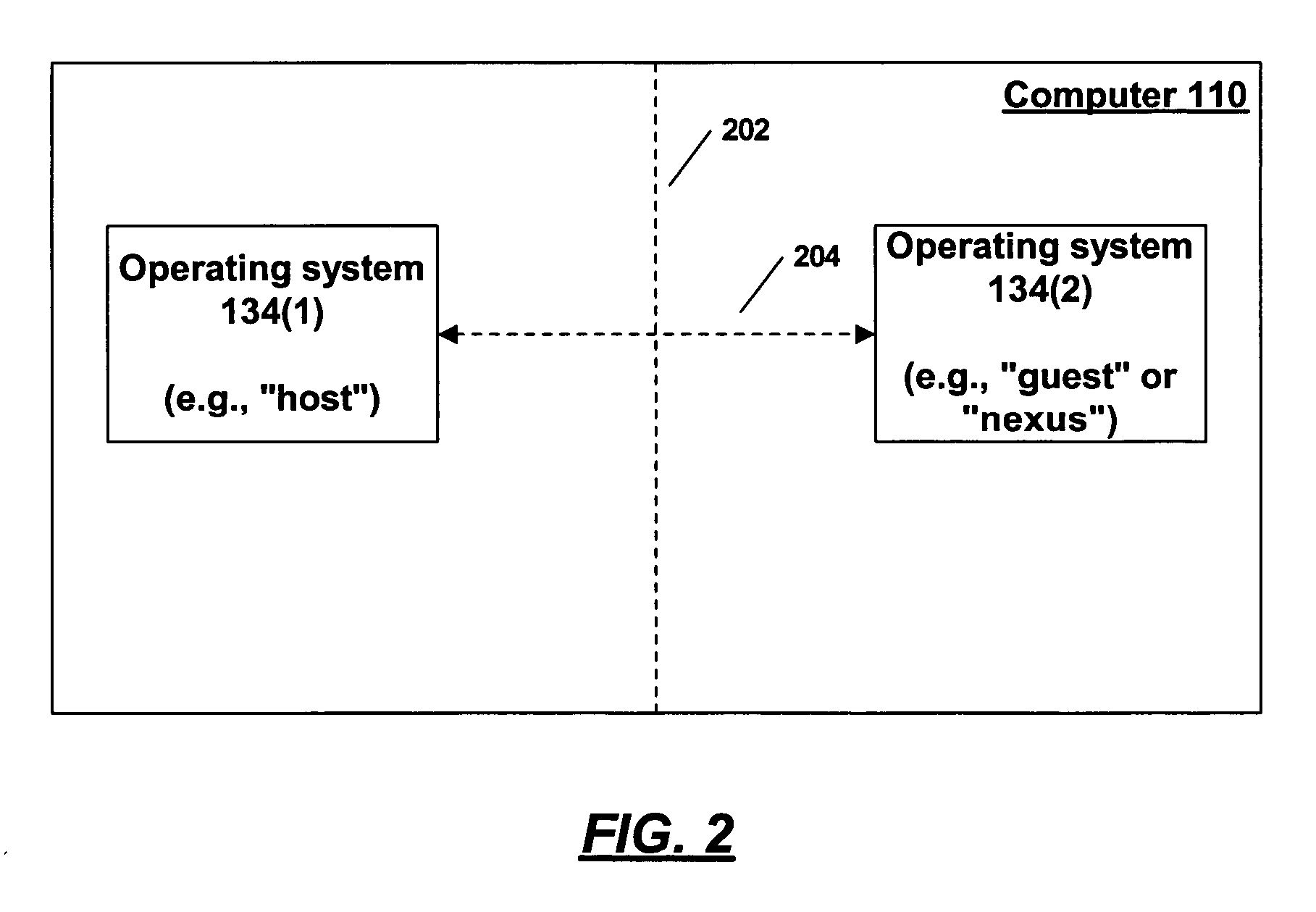
Providing a graphical user interface in a system with a high-assurance execution environment
ActiveUS20050091486A1Maintain securityProgram control using stored programsDigital data processing detailsGraphicsOperational system
Techniques are disclosed to provide security for graphical user interface elements being displayed in a system in which a first, host operating system is used along with a second, high assurance operating system, where the first system provides at least some of the infrastructure for the second system. Graphical user interface elements associated with the high-assurance operating system are prevented from being obscured and from any partial transparency. Additionally, a piece of secret information is stored which can be displayed upon command by graphical user interface elements associated with the high-assurance operating system. Coordinating certain elements of the display of all graphical user interface elements associated with the high assurance operating system also helps to identify legitimate elements associated with the high assurance operating system, as opposed to impostor elements which are not. Where a windowing system is used, public title information is furnished to a host operating system windowing system to identify a window owned by a process running on a high-assurance operating system. Private title information associated with the same window is used only in the high assurance operating system.
Owner:MICROSOFT TECH LICENSING LLC
System having parallel data processors which generate redundant effector date to detect errors
ActiveUS7272681B2Easy to refreshEasy to upgradeError preventionDigital data processing detailsData matchingParallel computing
A high assurance processing system includes a plurality of data processors coupled in parallel, a bridge coupled to the plurality of data processors, and an input / output processor coupled to the bridge for coupling to a sensor and an effector. Sensor data passes to the bridge through the input / output processor for processing by the parallel data processors, which generate redundant effector data for comparison by the bridge to detect errors. If data matches are found, data is transmitted to the effector.
Owner:RAYTHEON CO
Providing secure input to a system with a high-assurance execution environment
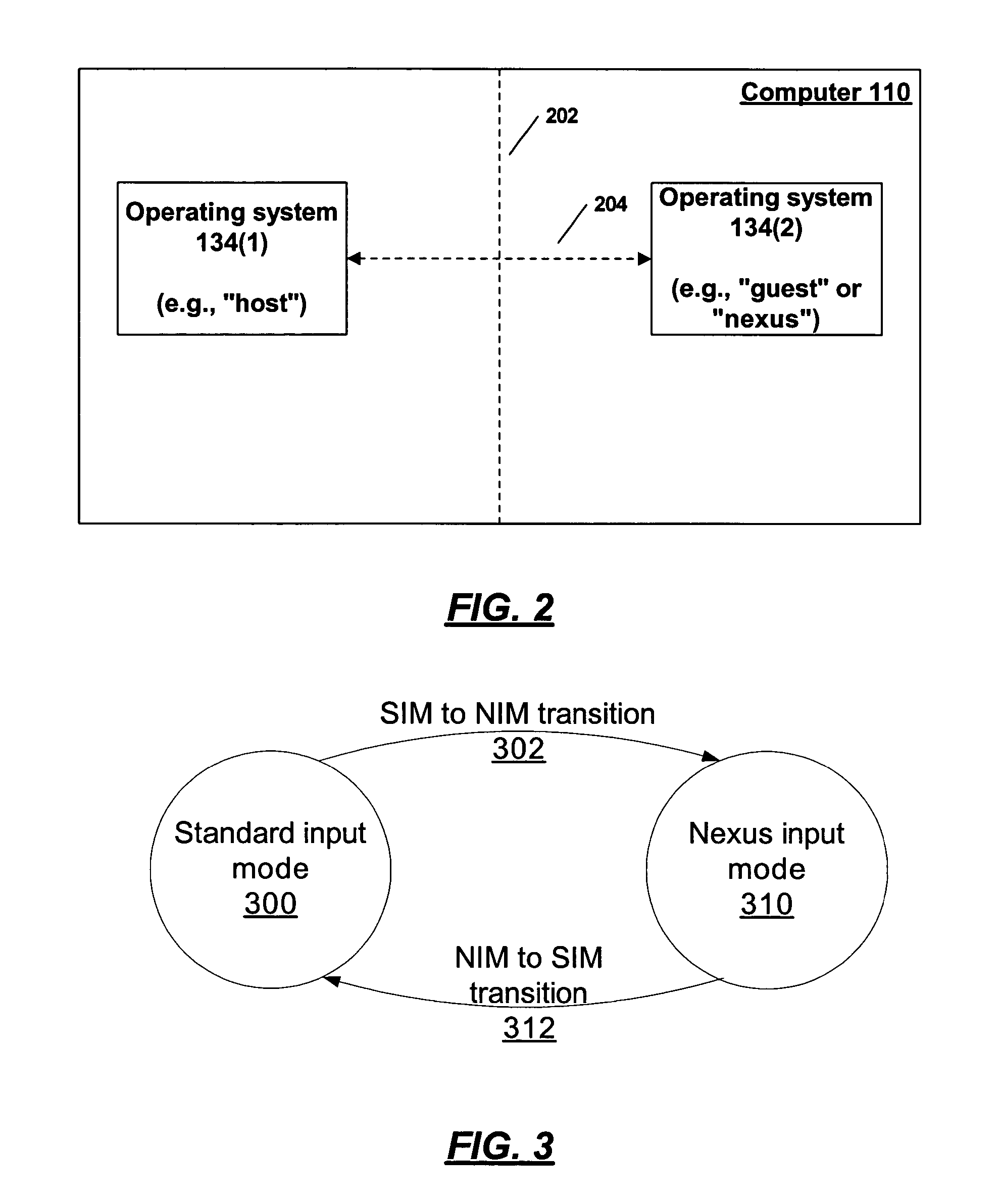
InactiveUS20050091530A1Digital data processing detailsMultiprogramming arrangementsGraphicsOperational system
Techniques are disclosed to provide security for user input in which a first, host operating system is used along with a second, high assurance operating system, where the first system provides at least some of the infrastructure for the second system. Two modes are presented. In a first mode, user data is passed to the host operating system. In a second mode, user data is retained in the second operating system for the use of the second operating system or processes running on the second operating system. Transitions between the nodes can be accomplished according to hypothecated user actions such as keystroke combinations, or when the user performs an action which indicates a programmatic activation of a process running in the second operating system. Where shadow graphical elements are run by the first operating system to indicate the location of graphical elements from processes running on the second operating system, this programmatic activation may be indicated by programmatic activation of a shadow graphical element.
Owner:MICROSOFT TECH LICENSING LLC
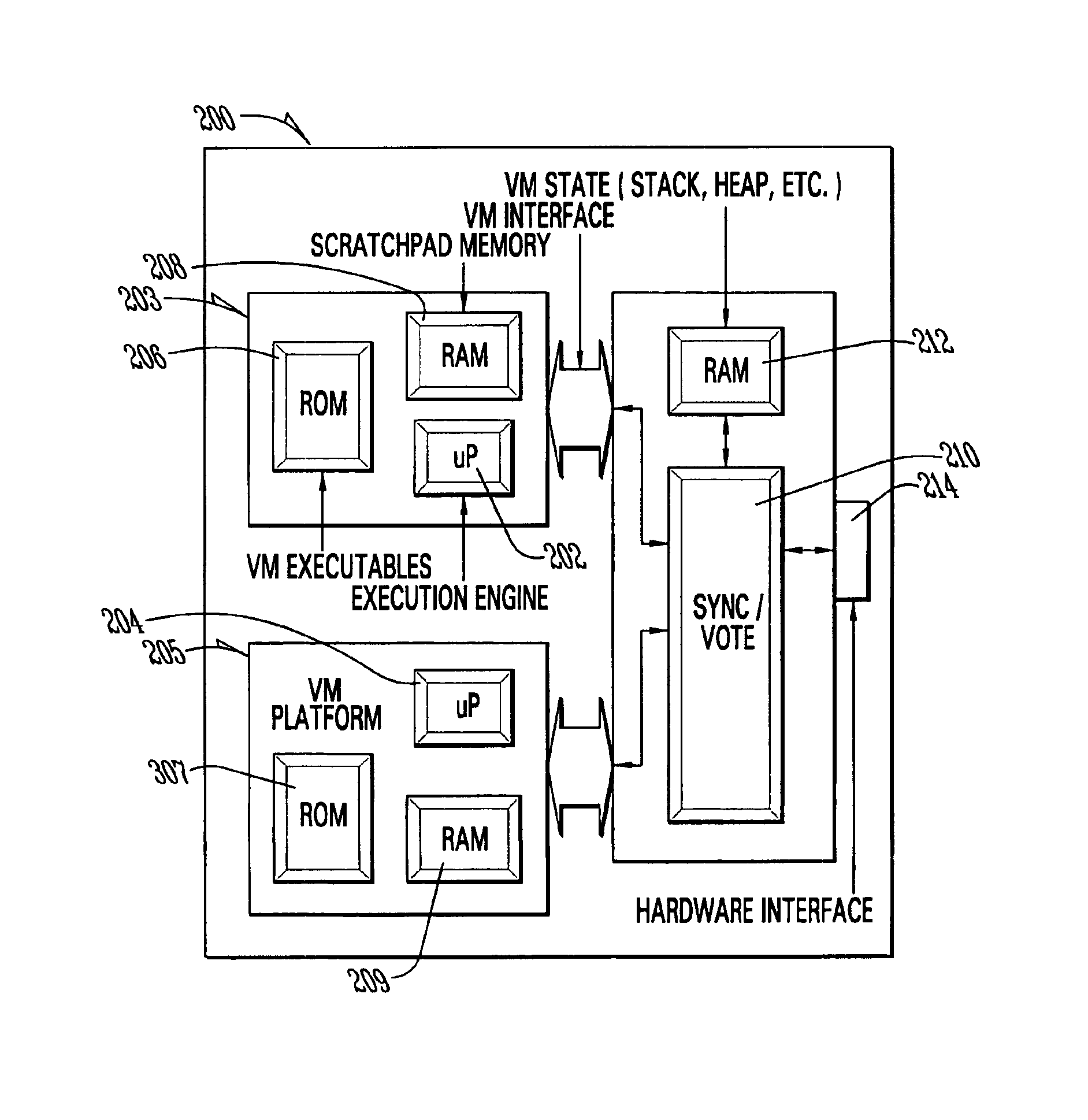
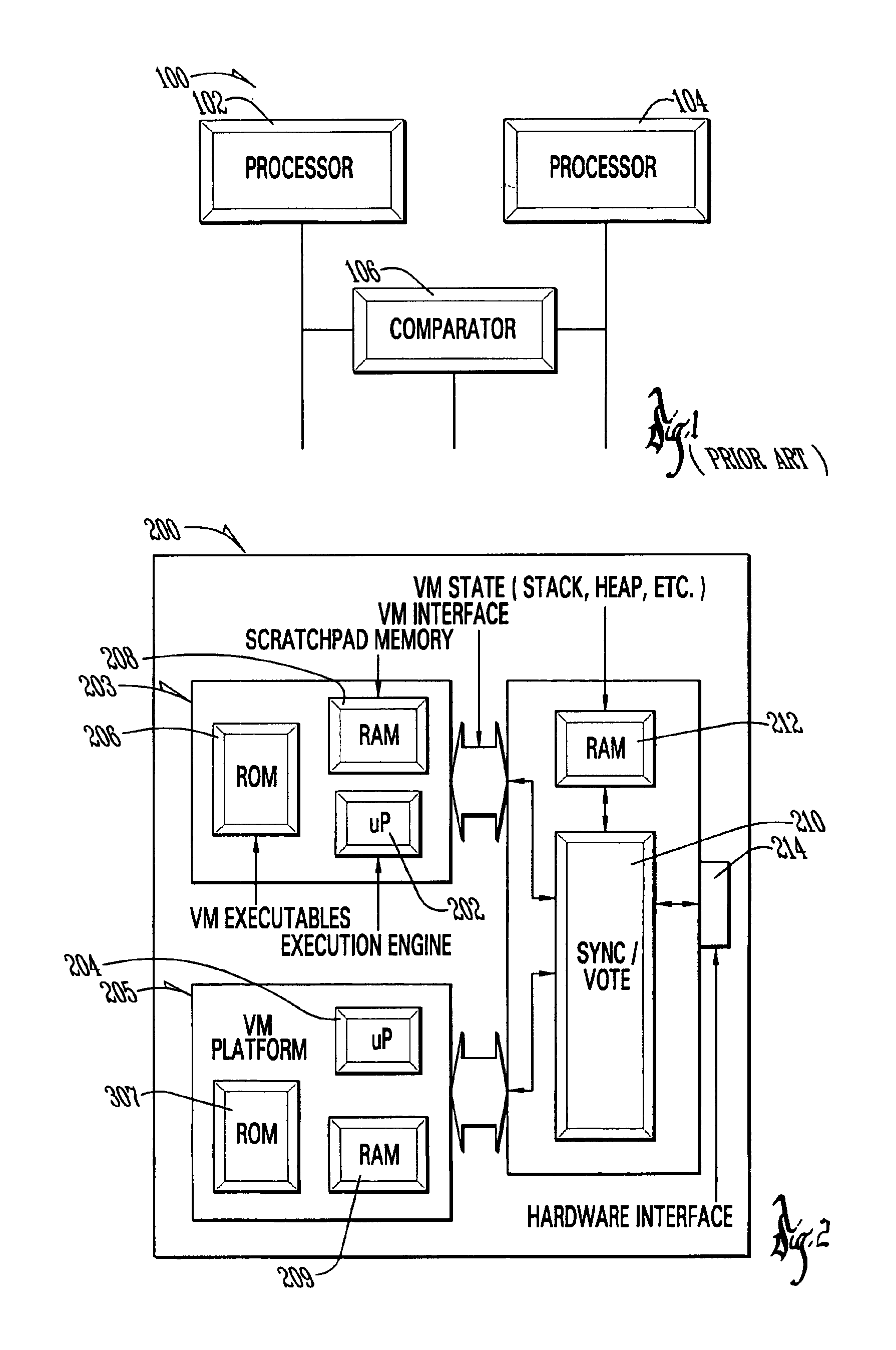
Method and apparatus for high assurance computing using virtual machines on general purpose computing resources
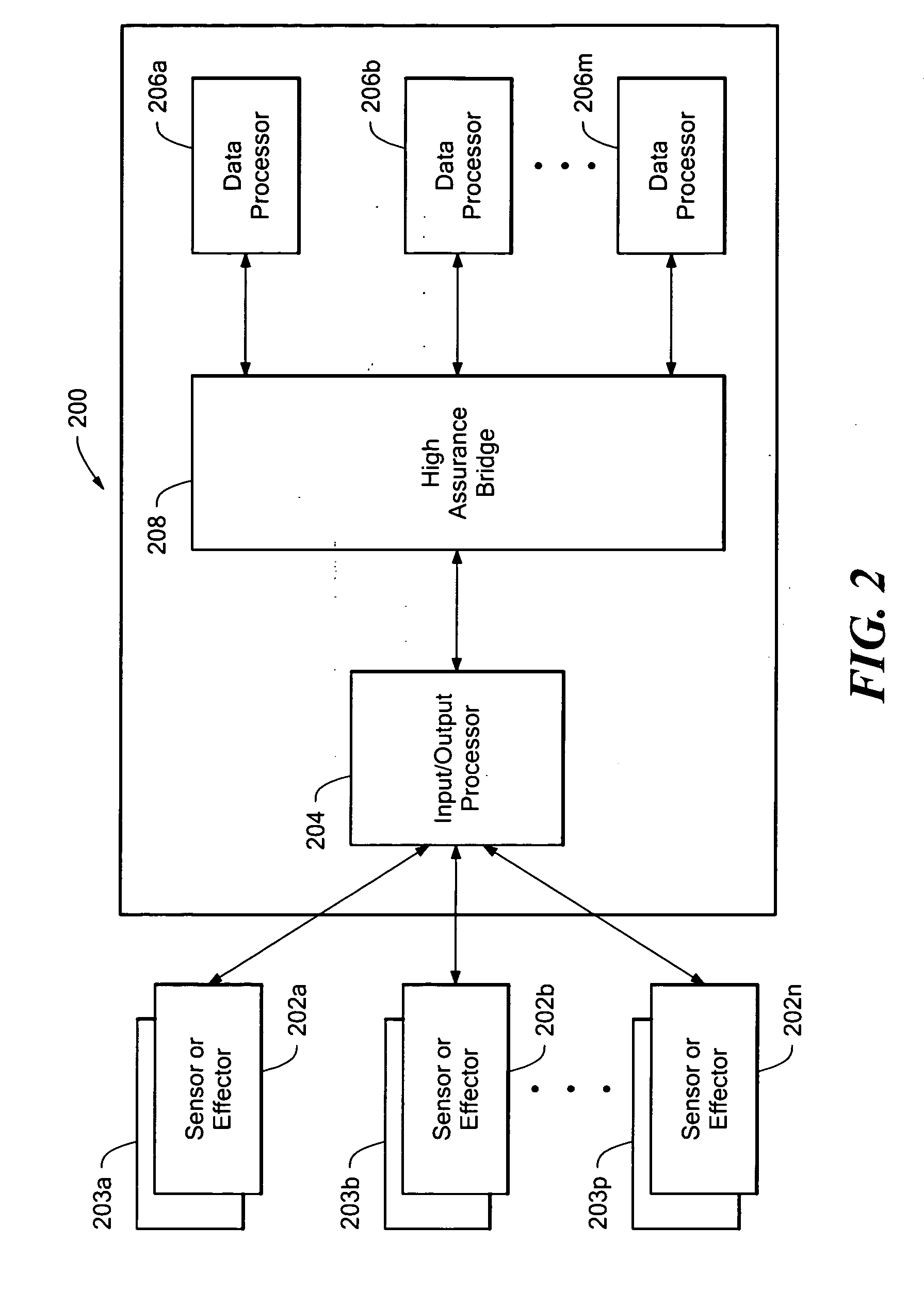
InactiveUS6895582B1Improve the level ofEliminate needDigital data processing detailsNavigation instrumentsGeneral purposeAviation
A system and method for enhancing the integrity of an avionics system which uses a pair dissimilar general purpose microprocessors, each running a virtual machine, compiled for its respective processor, from a common original source file; the virtual machines running on a subset of the instructions for each microprocessor and thereby avoiding conditions known or likely to result in defects; the virtual machines running a single or identical avionics program and then voting the results of this simultaneous redundant execution to arrive at an enhanced assurance level; providing written claims to the FAA that an enhanced assurance level is achieved.
Owner:ROCKWELL COLLINS INC
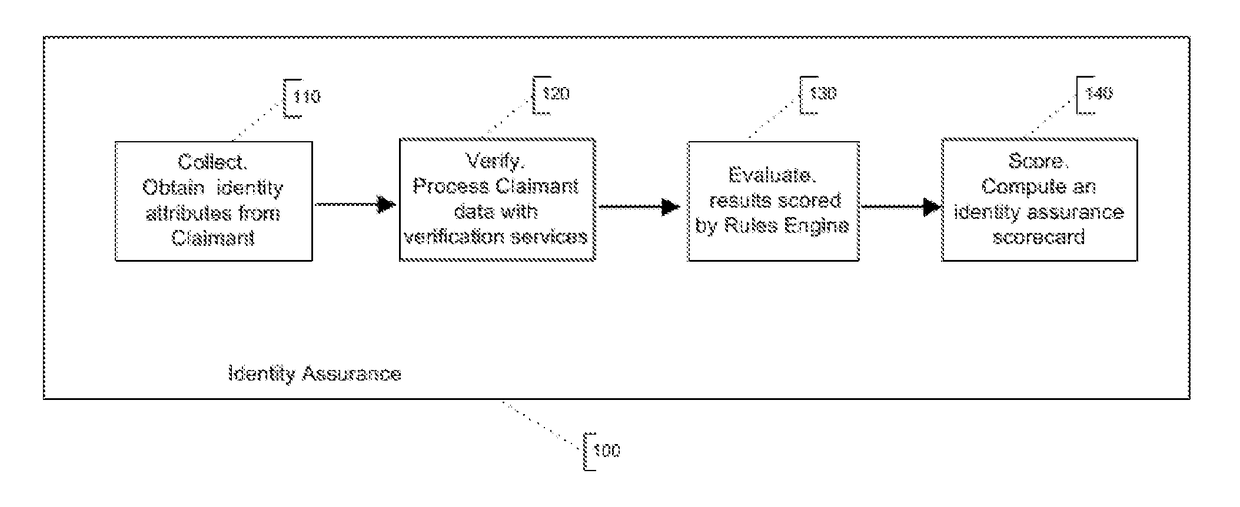
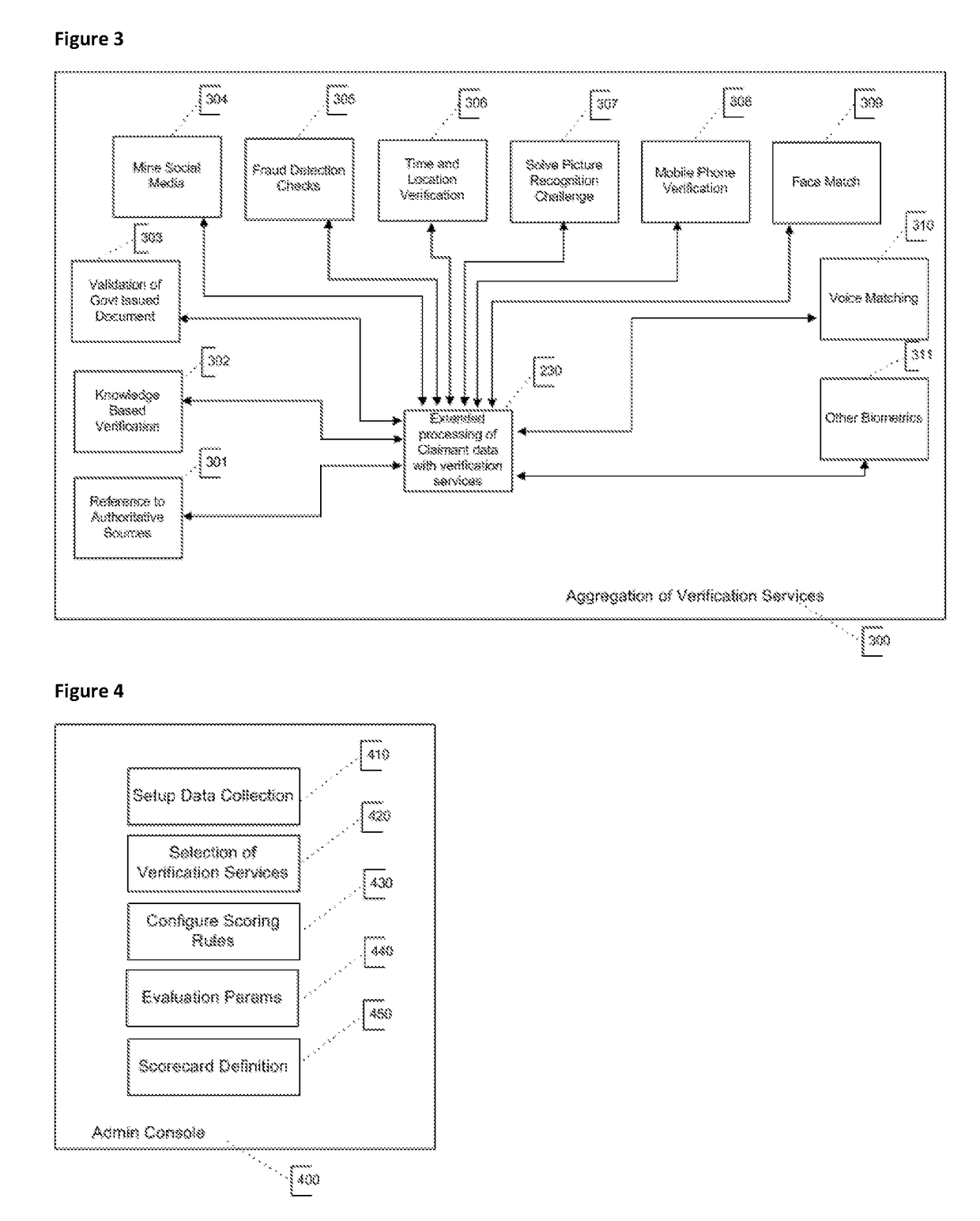
High Assurance Remote Identity Proofing
InactiveUS20180124047A1Guaranteed growthConfidenceData processing applicationsDigital data authenticationInternet privacyE-commerce
Remote identity proofing is the process of uniquely verifying an individual who is a party to an online transaction. This presents an enormous challenge to the secure delivery of government services as well as online commerce. The degree of difficulty is compounded when attempting to remotely authenticate for the first time a previously unknown individual. The High Assurance Remote Identity Proofing method introduces a holistic approach to solving this problem. A rich collection of identity data, when evaluated by multiple verification methods, can be aggregated to an identity assurance score, which is a measure of the uniqueness and authenticity of a claimed identity and ultimately provides a high assurance that someone attempting to remotely verify his or her identity is who he or she claims to be.
Owner:FISHER DAVID L +3
High assurance segregated gateway interconnecting different domains
ActiveUS20170070507A1Different level of securityNetwork connectionsElectric digital data processingData formatHigh assurance
A gateway having an architecture authorizing bidirectional communication between applications located in different domains and presenting a high assurance level of protection. The gateway interconnects a first and second domain. The gateway comprises an internal protocol, first and second protocol adapters hosted within the first and second domains and configured to make a conversion between application data formatted according to an applicative protocol relative to the two domains and gateway data formatted according to the gateway internal protocol, and a security module hosted on a separate platform to communicate with the first and second protocol adapters via first and second data links according to the gateway internal protocol. The first and second protocol adapters and security module are each physically segregated and the security module comprises functional blocs configured to authorize secure bidirectional flow of gateway data along two different and separate unidirectional paths between the two protocol adapters.
Owner:AIRBUS OPERATIONS (SAS)
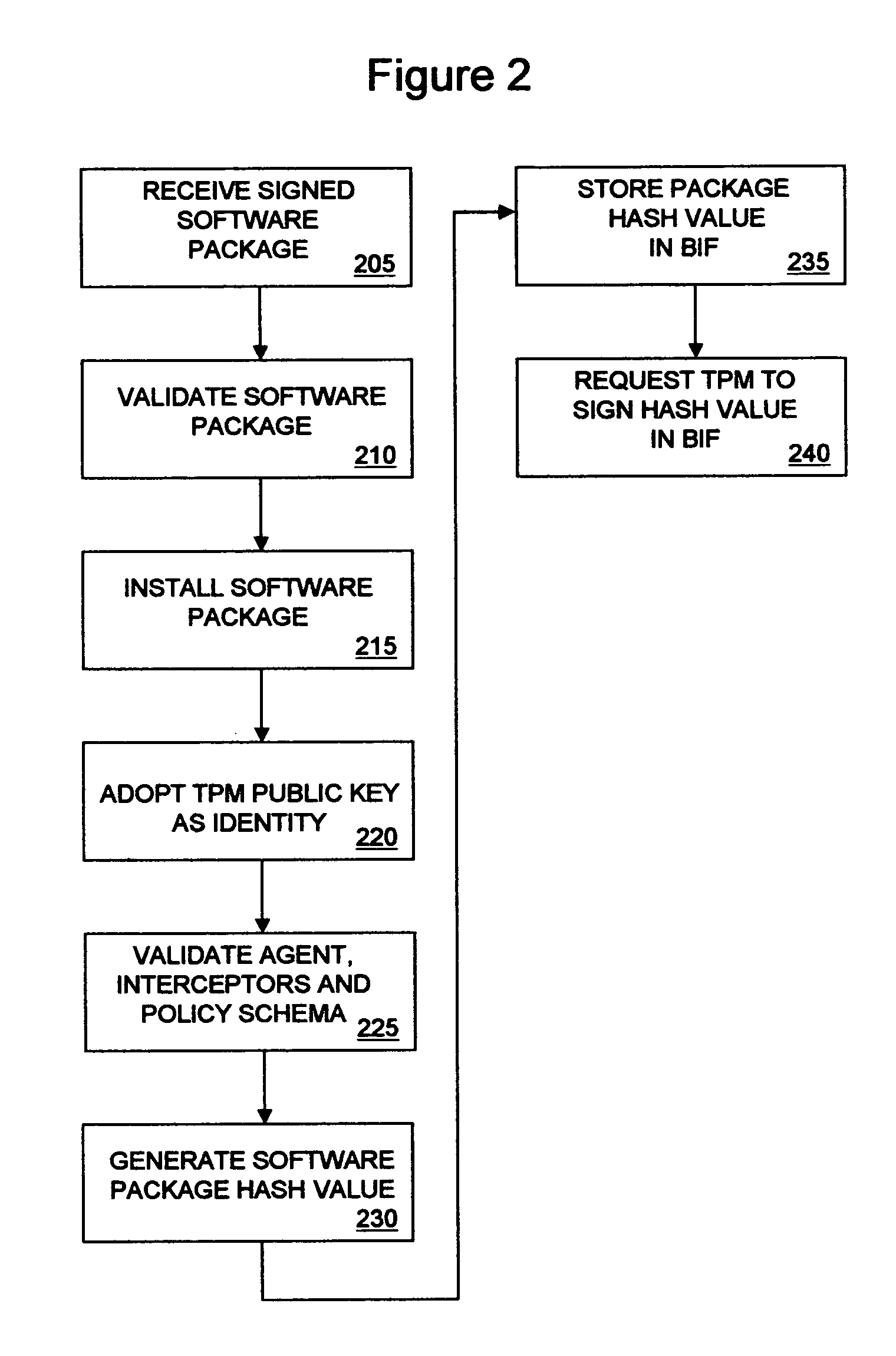
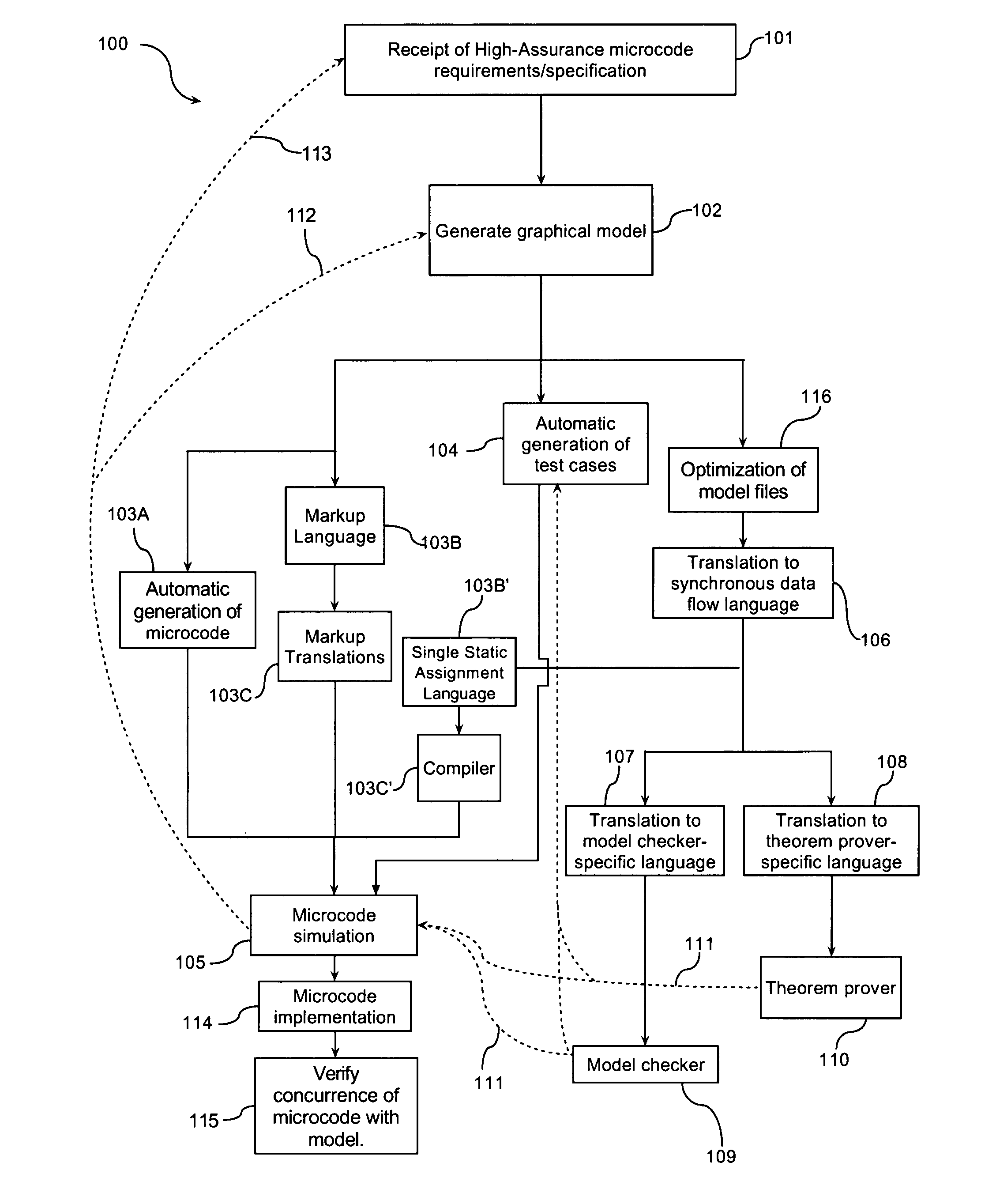
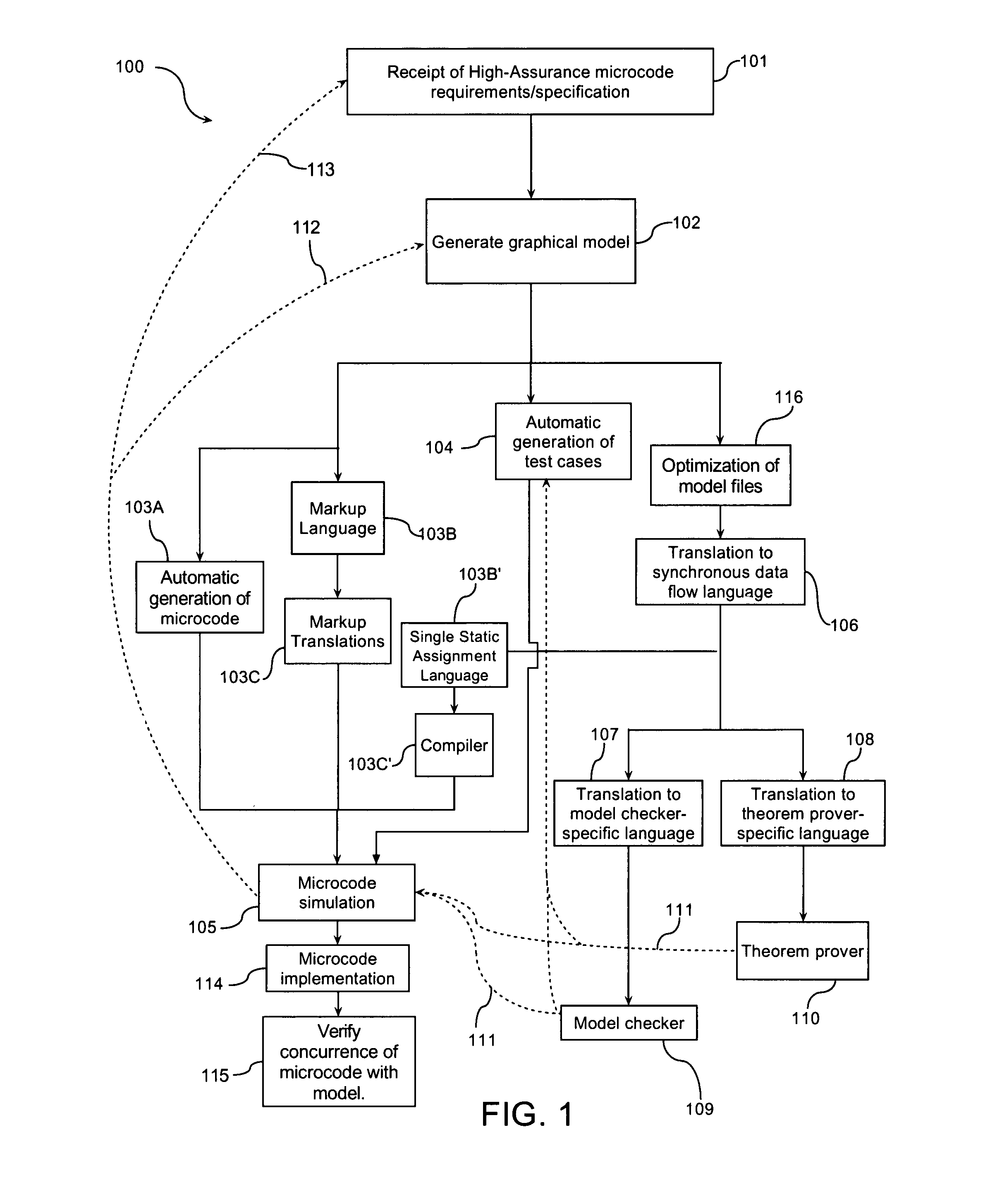
Method and system for the development of high-assurance microcode
The present invention is a methodology for developing high-assurance microcode. The method may comprise one or more of the following steps: (a) receiving a plurality of requirements detailing intended behavior of microcode (b) creating a model of microcode behavior; (c) generating microcode based on the model; (d) generating test cases based on the model; (e) simulating the behavior of the microcode; (f) translating the model into a verification tool-specific format; and (g) formally verifying the model using a verification tool.
Owner:ROCKWELL COLLINS INC
System and method for high-assurance data storage and processing based on homomorphic encryption
ActiveUS9729312B2Key distribution for secure communicationSoftware simulation/interpretation/emulationQuality of serviceClient-side
A key value storage (KVS) system comprising: a client-side agent configured to encrypt data; three nodes hosted respectively in three cloud service providers, wherein each node comprises: a management node configured to receive encrypted data from the client-side agent, a homomorphic encryption (HE) key manager configured to fetch a public key of a given object in the KVS system, a homomorphic encryption and processing engine configured to execute commands over the encrypted data without decrypting it, a homomorphic memory store, a hypervisor configured to monitor performance of the management node in order to assess the quality of service of the management node; and wherein each node serves on a rotating basis in a master node role, a secondary node role, or a back-up node role, wherein the nodes rotate their roles when the master node's hypervisor detects a reduced quality of service of the master node's management node.
Owner:THE UNITED STATES OF AMERICA AS REPRESENTED BY THE SECRETARY OF THE NAVY
Tamper-resistant communication layer for attack mitigation and reliable intrusion detection
ActiveUS20080317002A1Reduce attackDifficult to compromiseCircuit switching systemsNetwork connectionsNetworking protocolNetwork attack
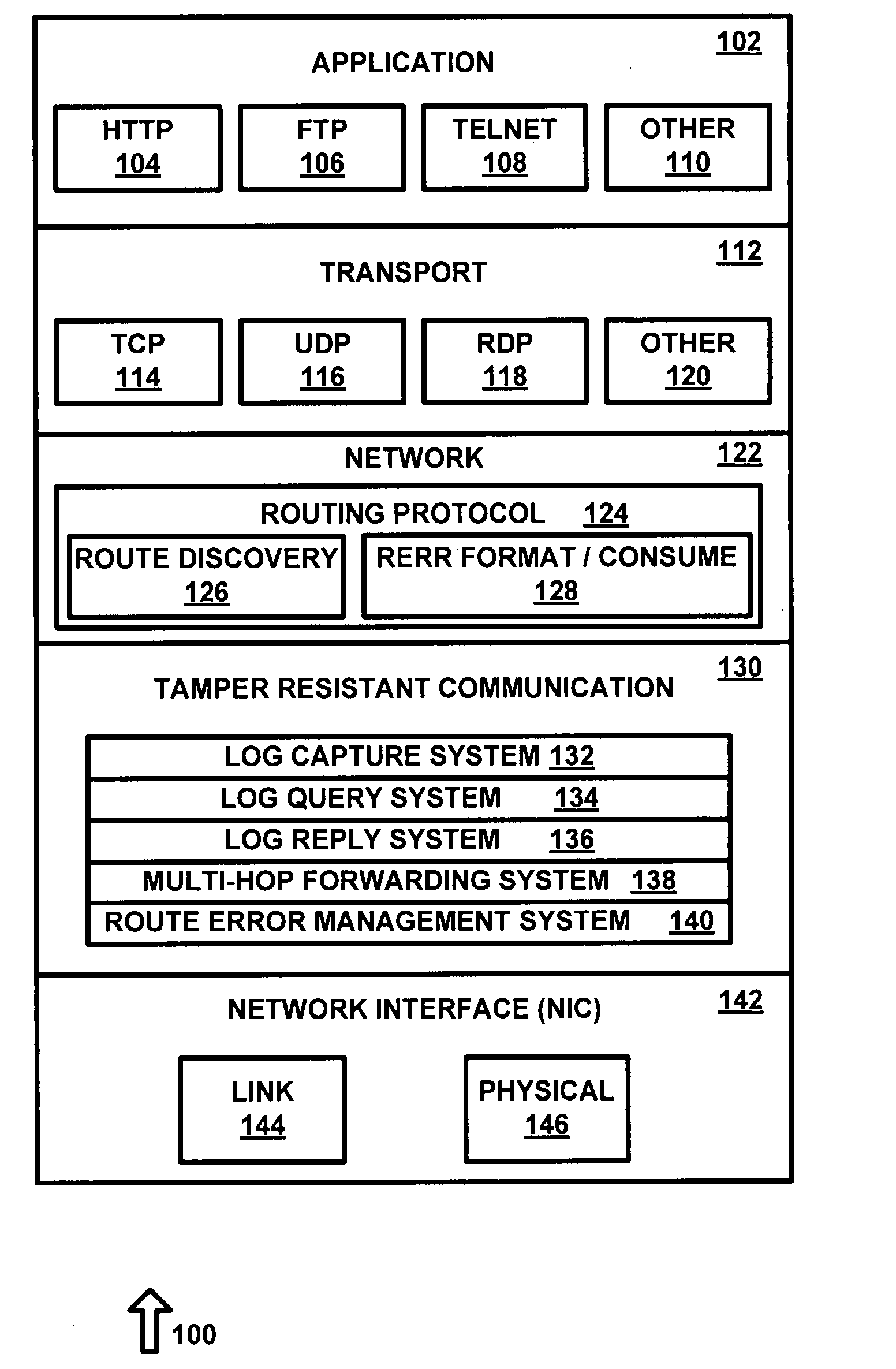
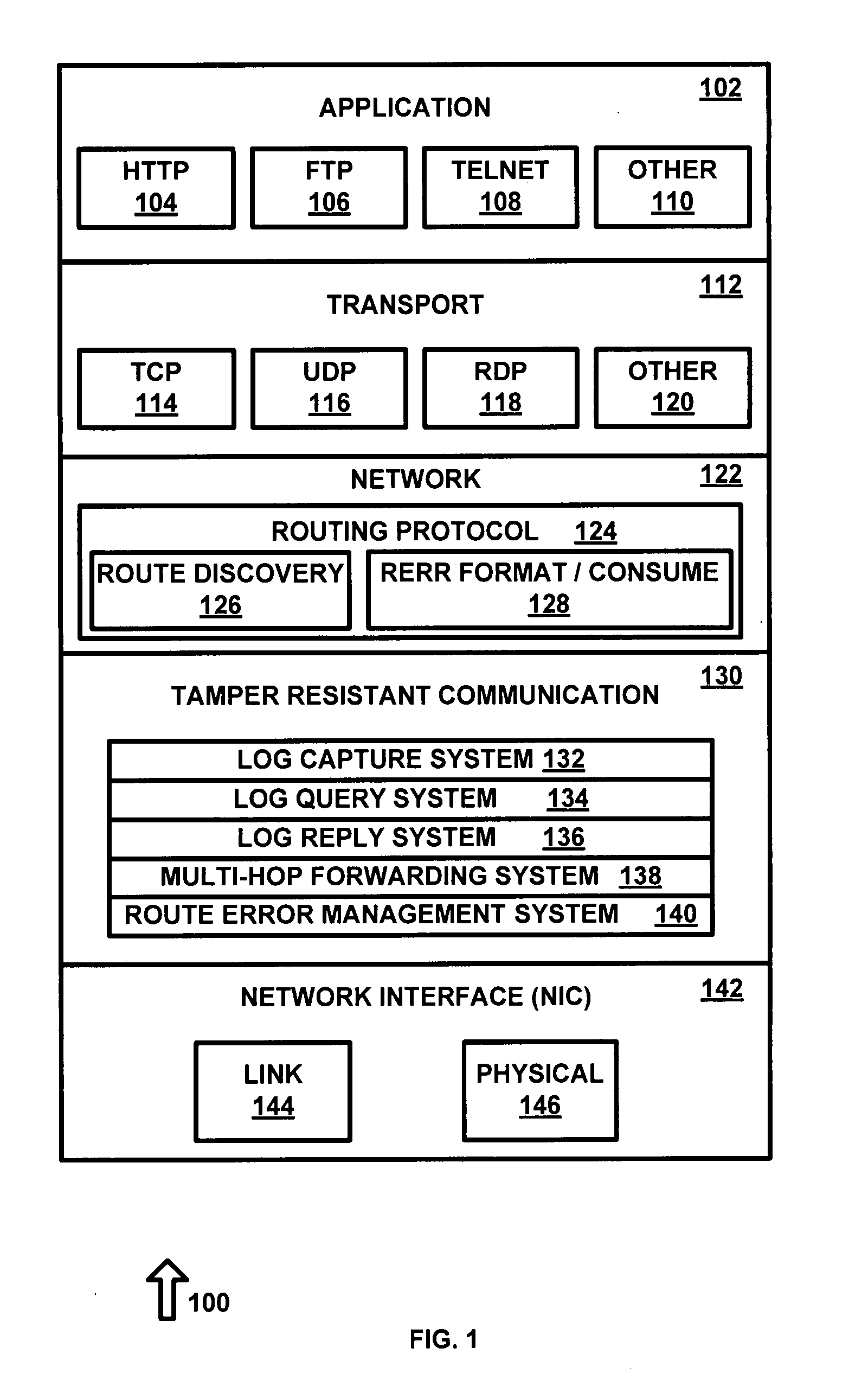
A Tamper-Resistant Communication layer (TRC) adapted to mitigate ad hoc network attacks launched by malicious nodes is presented. One embodiment of the invention utilizes TRC, which is a lean communication layer placed between a network layer and the link layer of a network protocol stack. All aspects of the network protocol stack, with the exception of the routing protocol and data packet forwarding mechanism in the network layer, are unchanged. TRC takes charge of certain key functions of a routing protocol in order to minimize network attacks. Additionally, TRC implements highly accurate self-monitoring and reporting functionality that can be used by nodes in the network to detect compromised nodes. TRC of a node controls its ability to communicate with other nodes by providing non-repudiation of communications. The tamper-resistant nature of TRC provides high assurance that it cannot be bypassed or compromised.
Owner:BOARD OF RGT THE UNIV OF TEXAS SYST
Providing secure input to a system with a high-assurance execution environment
Techniques are disclosed to provide security for user input in which a first, host operating system is used along with a second, high assurance operating system, where the first system provides at least some of the infrastructure for the second system. Two modes are presented. In a first mode, user data is passed to the host operating system. In a second mode, user data is retained in the second operating system for the use of the second operating system or processes running on the second operating system. Transitions between the nodes can be accomplished according to hypothecated user actions such as keystroke combinations, or when the user performs an action which indicates a programmatic activation of a process running in the second operating system. Where shadow graphical elements are run by the first operating system to indicate the location of graphical elements from processes running on the second operating system, this programmatic activation may be indicated by programmatic activation of a shadow graphical element.
Owner:MICROSOFT TECH LICENSING LLC
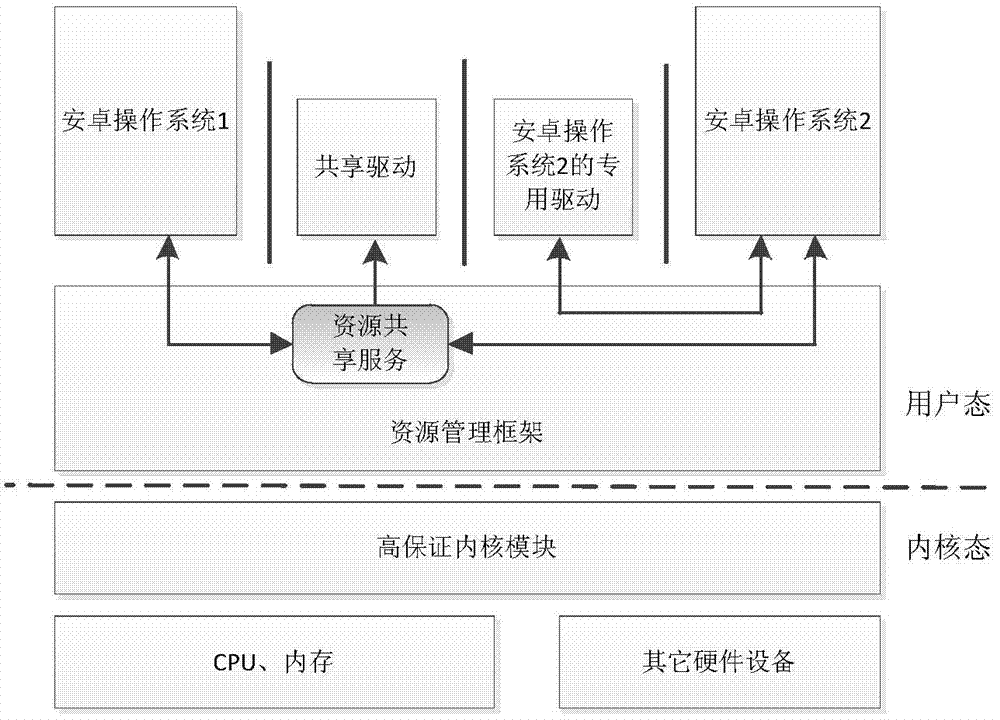
Mobile terminal operation system based on high-assurance kernel module and realization method of mobile terminal operation system
ActiveCN104850787AAchieve isolationImprove securityPlatform integrity maintainanceResource managementComputer terminal
The invention discloses a mobile terminal operation system based on a high-assurance kernel module and a realization method of the mobile terminal operation system. The mobile terminal operation system comprises a mobile terminal operation sub-system module, a high-assurance kernel module, and a resource management frame module, wherein the mobile terminal operation sub-system module comprises at least two mobile terminal operation sub-systems, each mobile terminal operation sub-system is corresponding to a relevant user interface; the high-assurance kernel module is used for accessing all hardware resources of the mobile terminal and providing a basic safety mechanism for the running of the mobile terminal operation sub-system module; the resource management frame module is used for accessing partial hardware resource of the mobile terminal and providing the basic resource management service for the mobile terminal operation sub-system module. The high-assurance kernel module is divisionally designed, and the access to the hardware source is managed, so that the security of the mobile terminal operation system can be well improved.
Owner:DATA COMM SCI & TECH RES INST
Local secure service partitions for operating system security
ActiveUS8619971B2Small sizeGuaranteed growthError detection/correctionVolume/mass flow measurementOperational systemOperating system security
Systems and methods provide multiple partitions hosted on an isolation technology such as a hypervisor where at least one of the partitions, a local secure service partition (LSSP), provides security services to other partitions. The service partitions (LSSPs) host those high assurance services that require strict security isolation, where the service can be shared across partitions and accessed even when the user is not connected to a network. The LSSP also can certify the results of any computation using a key signed by a TPM attestation identity key (AIK), or other key held securely by the hypervisor or a service partition. The LSSPs may be configured to provide trusted audit logs, trusted security scans, trusted cryptographic services, trusted compilation and testing, trusted logon services, and the like.
Owner:MICROSOFT TECH LICENSING LLC
Method to construct a high-assurance ipsec gateway using an unmodified commercial implementation
ActiveUS20100131750A1Unauthorized memory use protectionHardware monitoringComputer hardwareSecure communication
A system and method of providing secure communications is provided. Messages are encrypted or decrypted in protected memory of a processor. Outbound messages from a secure network are prepared for encryption by adding a header outside of the protected memory and then encrypted in the protected memory. The encryption is performed by retrieving a key from a key cache as designated by rules in the header. The encrypted message is sent to the unsecure network. An inbound message from an unsecure network that is received in unprotected memory is sent to a decryption module in protected memory. The inbound message is decrypted using a key designated in its header and retrieved from the key cache. The decrypted message is returned to the unprotected memory, where it is stripped of the encryption header and then sent to its destination within the secure network.
Owner:MOTOROLA SOLUTIONS INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com