Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
723results about How to "Easy to scan" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
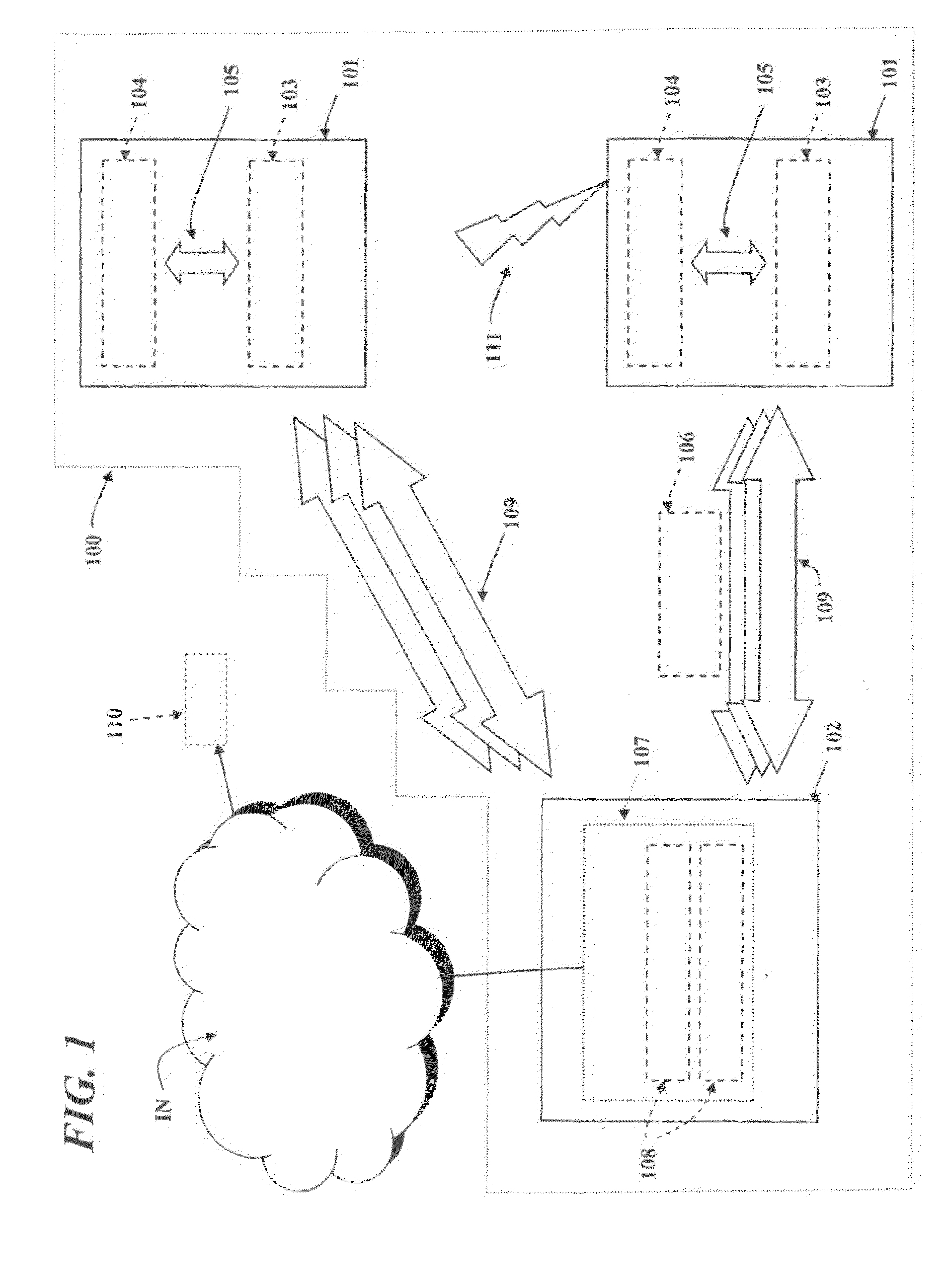
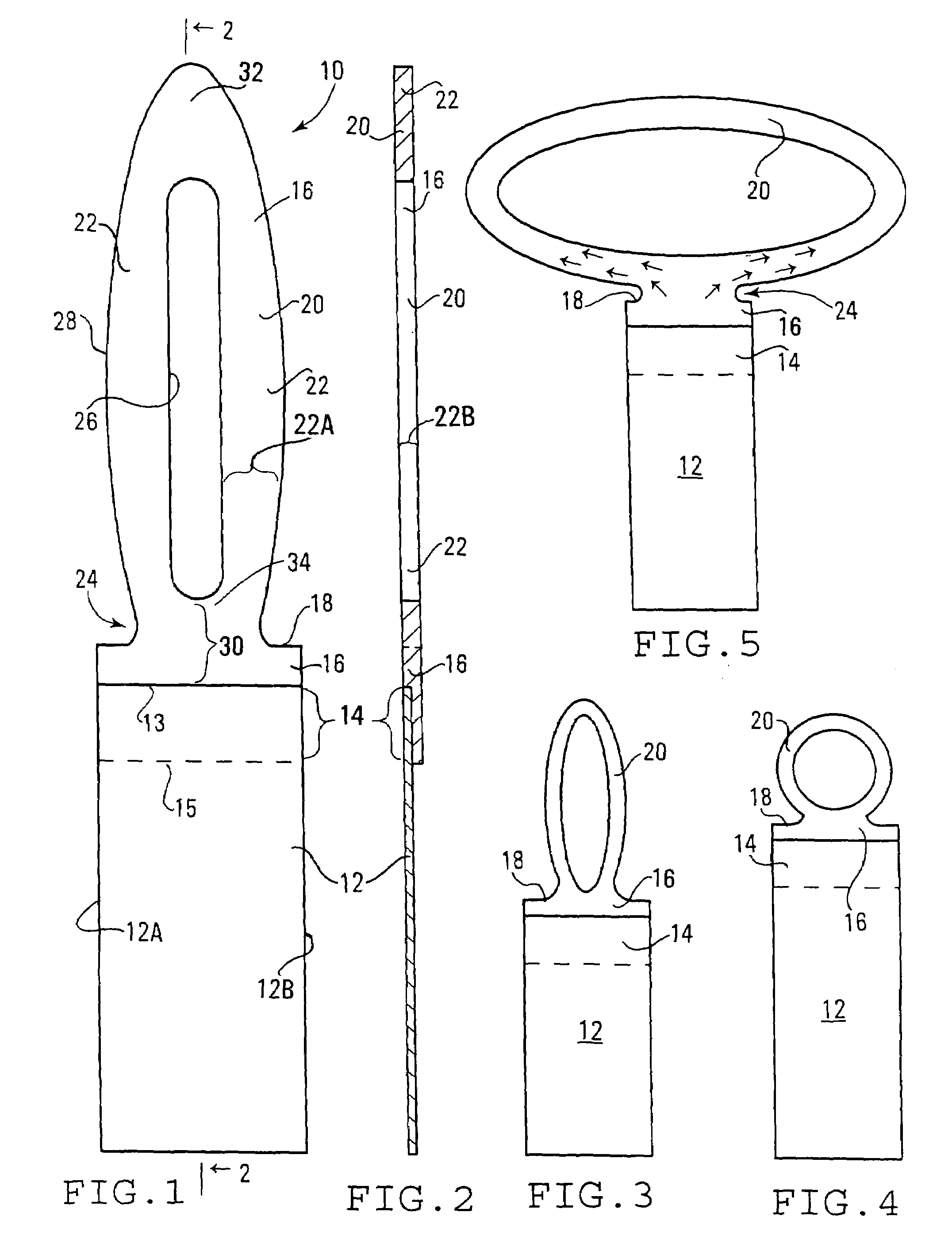
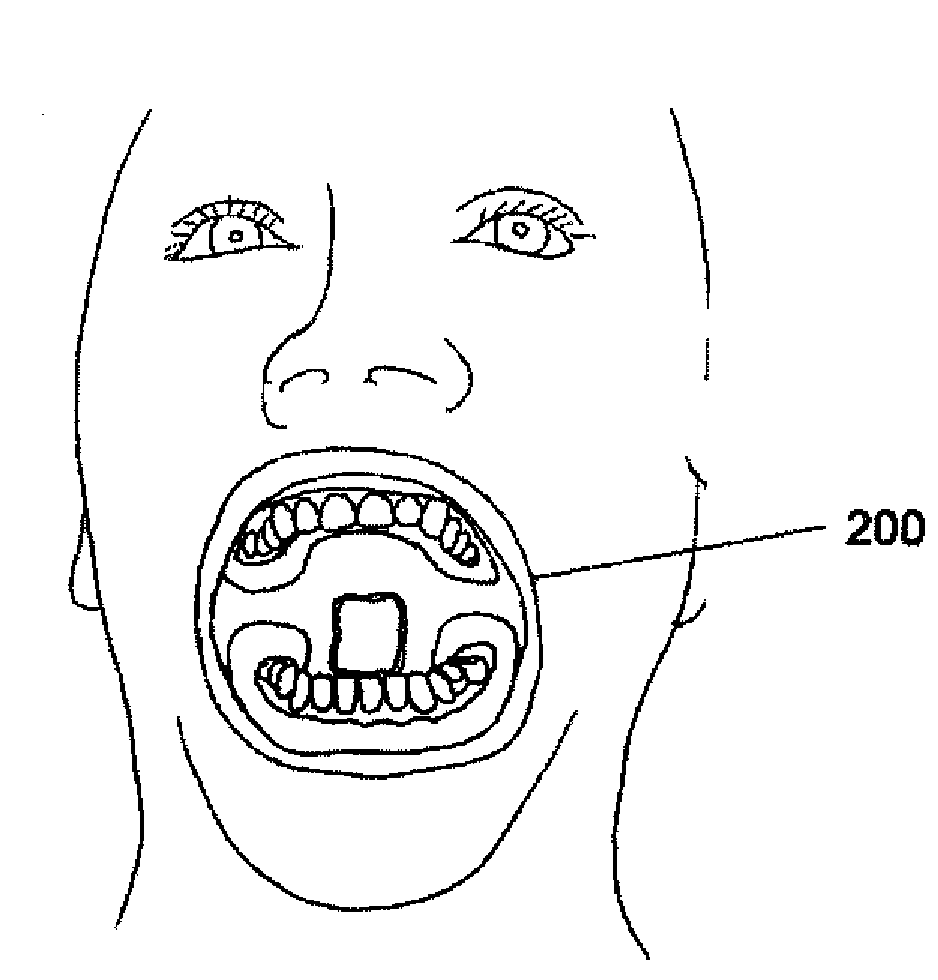
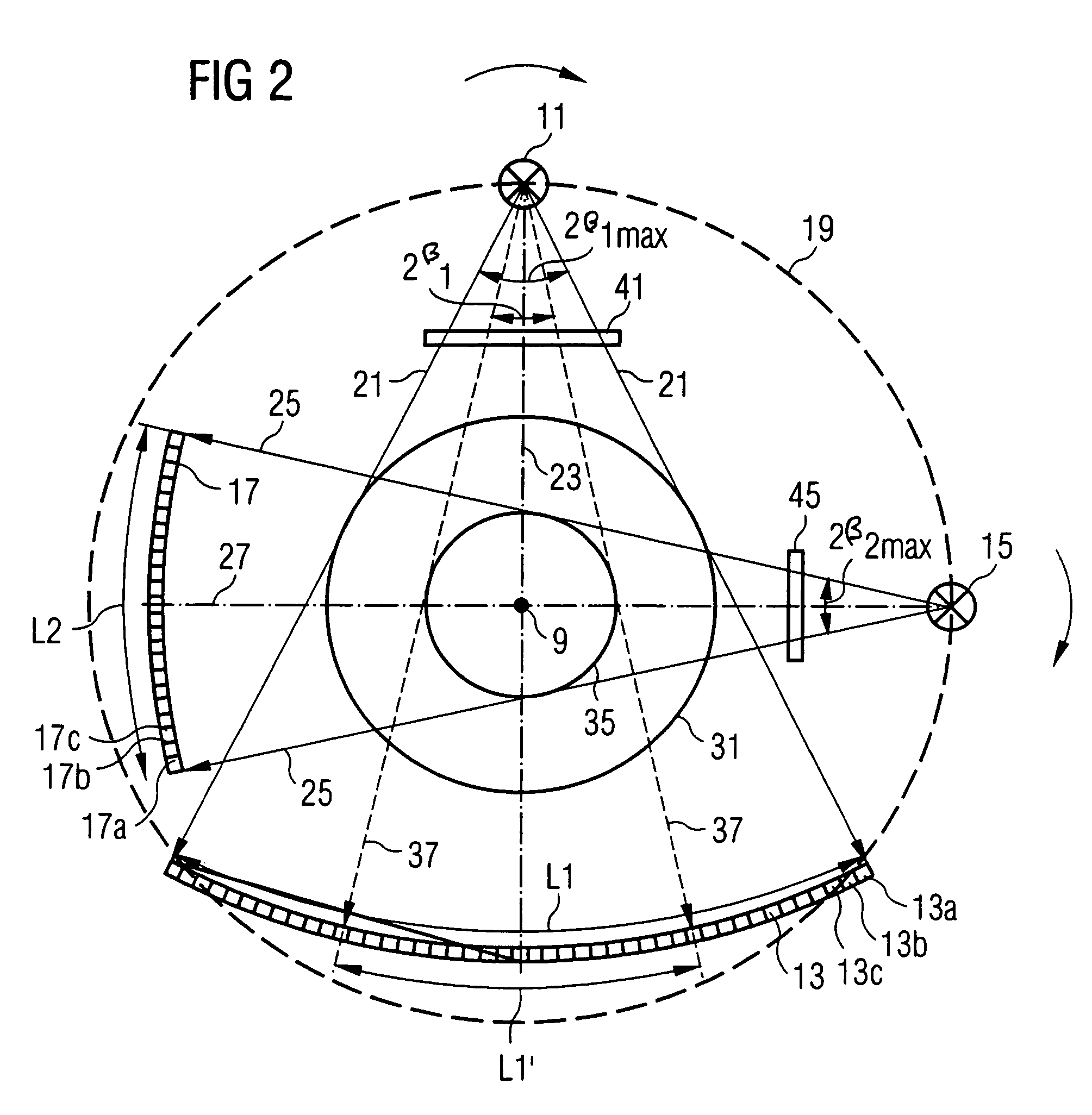
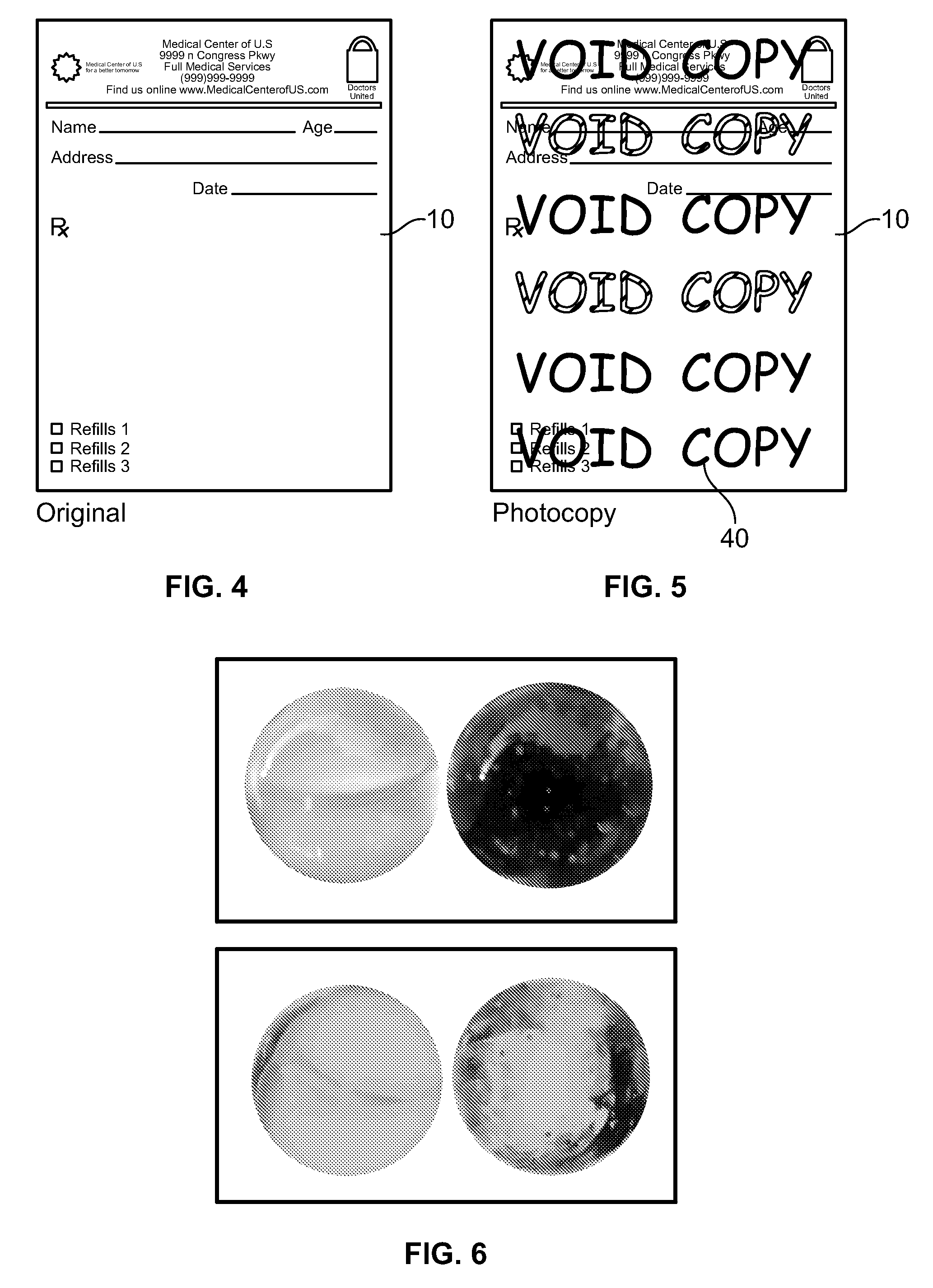
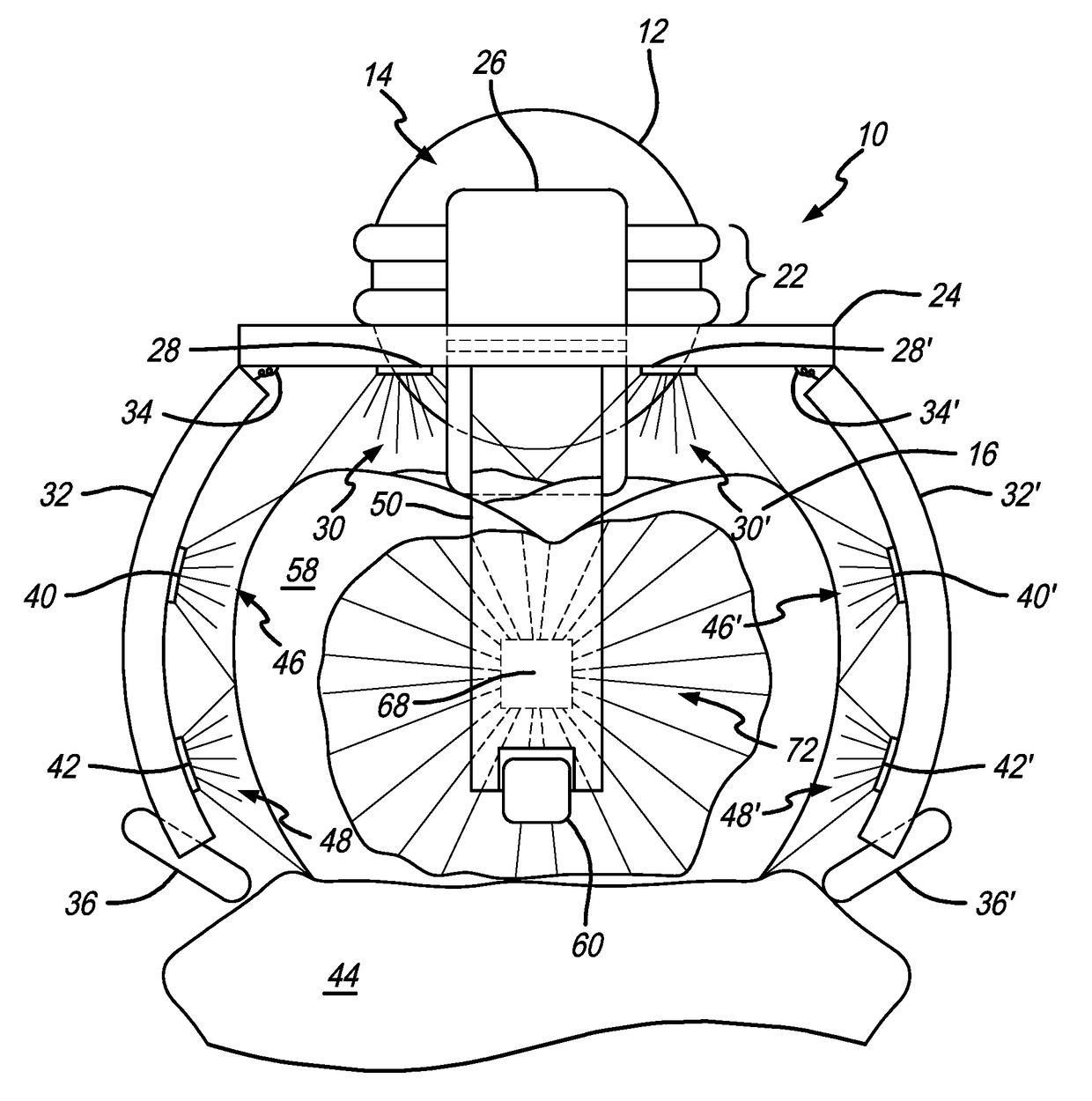
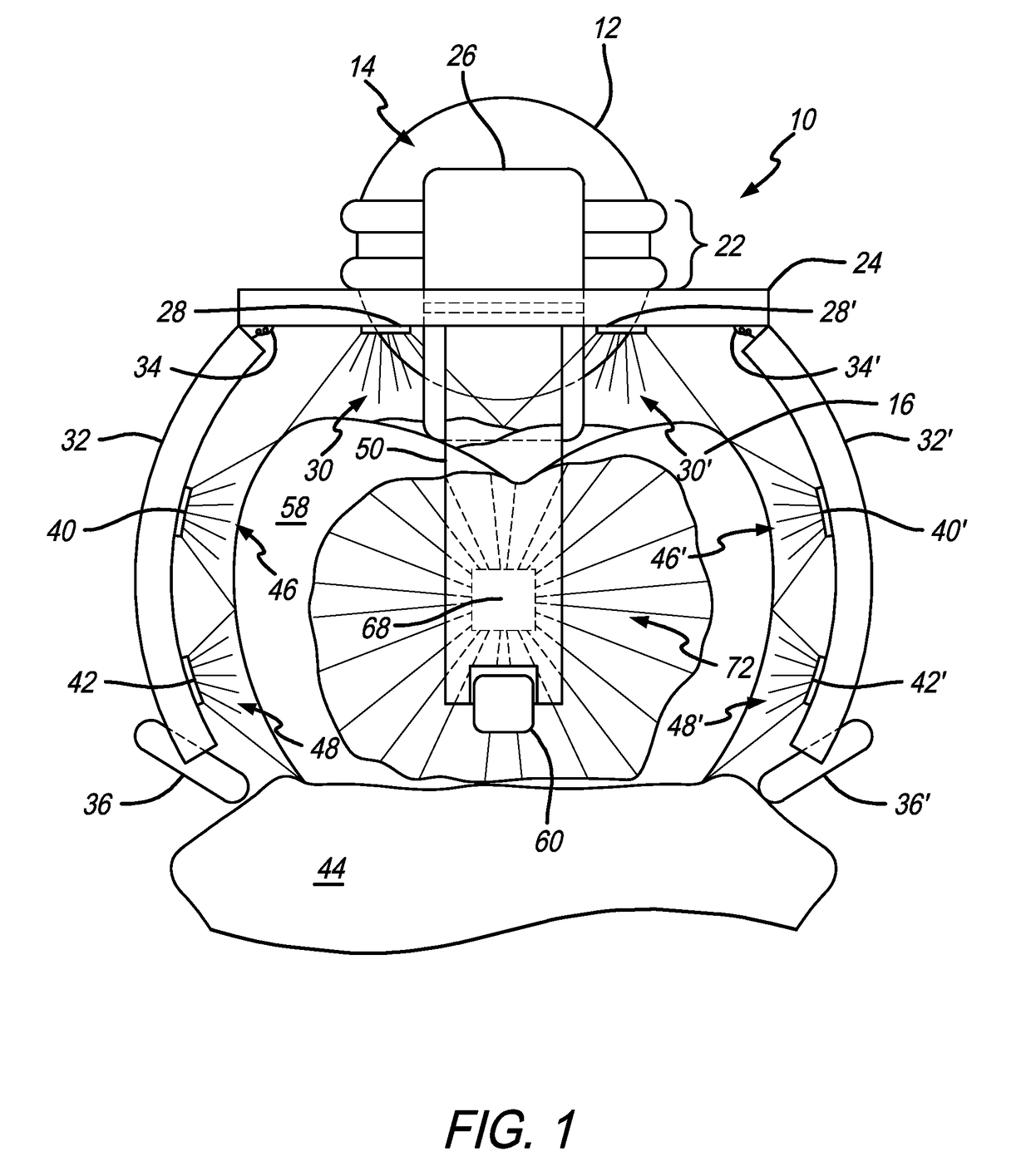
Method and apparatus for three-dimensional optical scanning of interior surfaces
InactiveUS20030164952A1Easy to produceHigh precision scan dataAdditive manufacturing apparatusOtoscopesEar canalOptical scanning
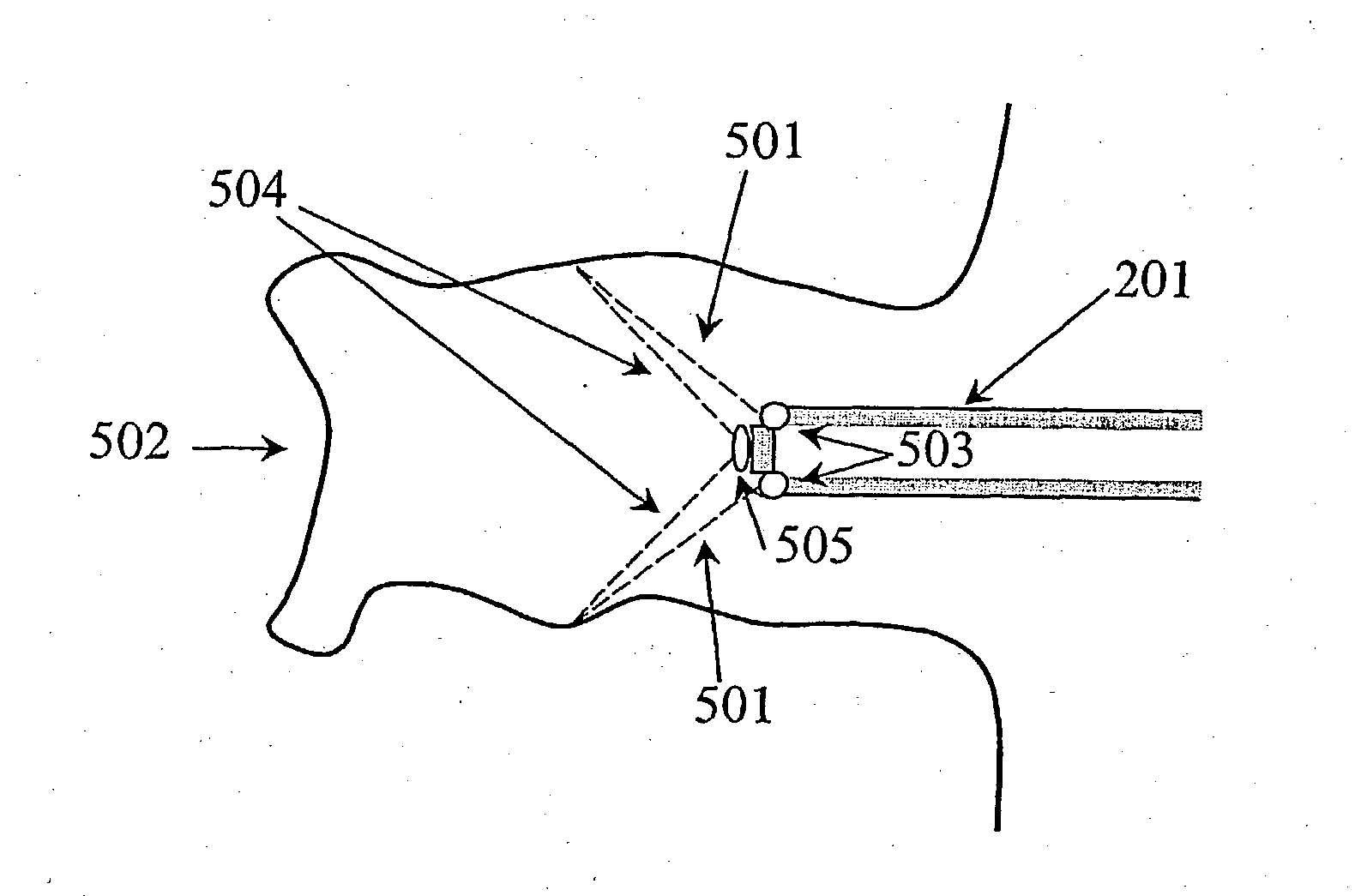
The invention concerns the three-dimensional scanning of interior surfaces or cavities of limited dimensions or with restricted accessibility by providing a probe-shaped non-contact adpated to perform a scan 360° around the axis of the probe and a method for scanning. The invention furthermore relates to the creation of high precision three-dimensional replicas of real objects using 3-D scan data obtainable with the scanner according to the invention. Furthermore, the invention relates to a specific embodiment for scanning the human ear and ear canal.
Owner:3SHAPE AS
Method and System for Mobile Network Security, Related Network and Computer Program Product
ActiveUS20090144823A1Easy to scanReduce overheadMemory loss protectionUnauthorized memory use protectionUser deviceDevice status
A honeypot system for protecting a mobile communication network against malware includes one or more user-less mobile devices including a monitoring module for monitoring the events conveying software applications in the associated mobile device as well as a controller client module that emulates human-like interaction with the user-less devices as a function of the events monitored. The system controllably performs, for the applications conveyed by the events monitored, one or more of the following steps: i) installing the application on the device; ii) executing the application installed on the device; and iii) de-installing the application from the- device. After any of these steps, the state of the device is checked in order to detect if any anomalous variation has occurred in the state of the device indicative of the device being exposed to the risk of malware. If any anomalous variation is detected, the system issues a malware alert message.
Owner:TELECOM ITALIA SPA
Method and apparatus for three-dimensional optical scanning of interior surfaces
InactiveUS7625335B2High precision scan dataEasy to combineAdditive manufacturing apparatusOtoscopes3d scanningOptical scanning
Owner:3SHAPE AS
Scanning apparatus and method
InactiveUS7313264B2Shorten the timeLow costCharacter and pattern recognitionUsing optical meansComputer graphics (images)Structured light
A scanning apparatus and method for generating computer models of three-dimensional objects comprising means for scanning the object to capture data from a plurality of points on the surface of the object so that the scanning means may capture data from two or more points simultaneously, sensing the position of the scanning means, generating intermediate data structures from the data, combining intermediate data structures to provide the model; display, and manually operating the scanning apparatus. The signal generated is structured light in the form of a stripe or an area from illumination sources such as a laser diode or bulbs which enable data for the position and color of the surface to be determined. The object may be on a turntable and may be viewed in real time as rendered polygons on a monitor as the object is scanned.
Owner:3D SCANNERS LTD
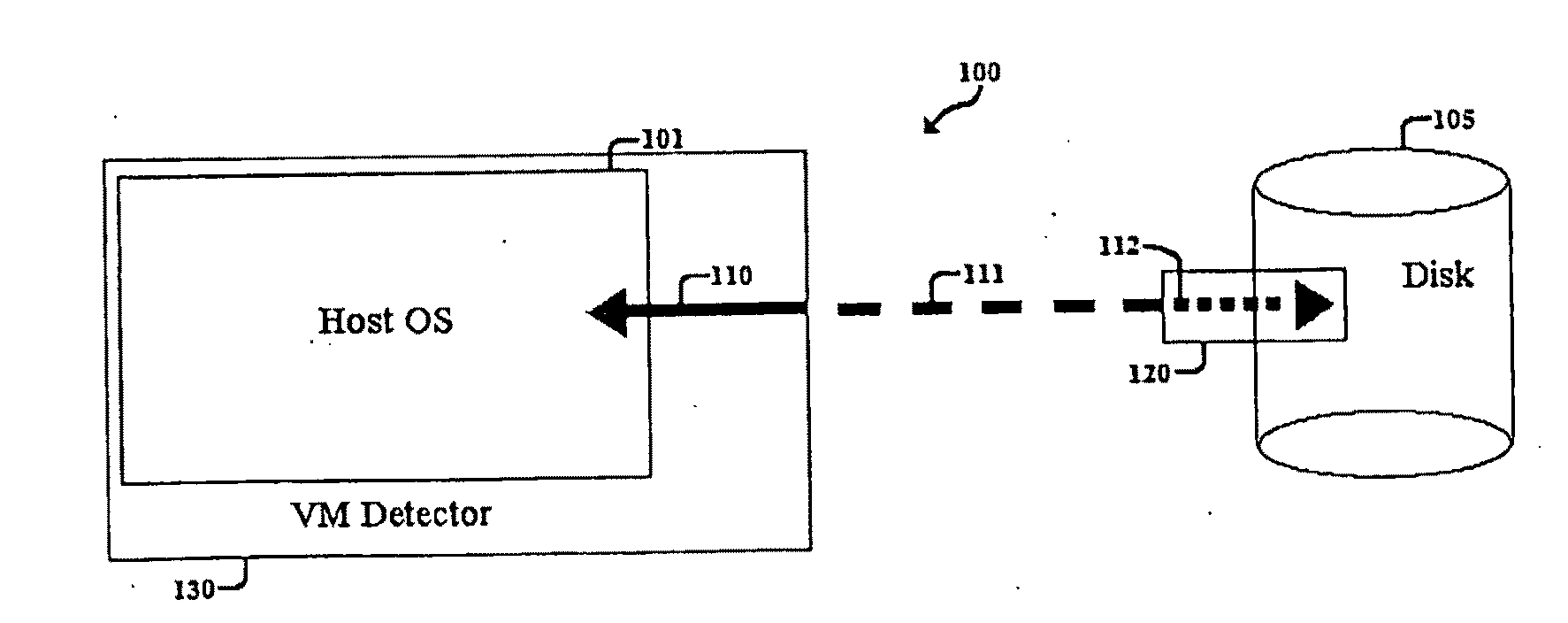
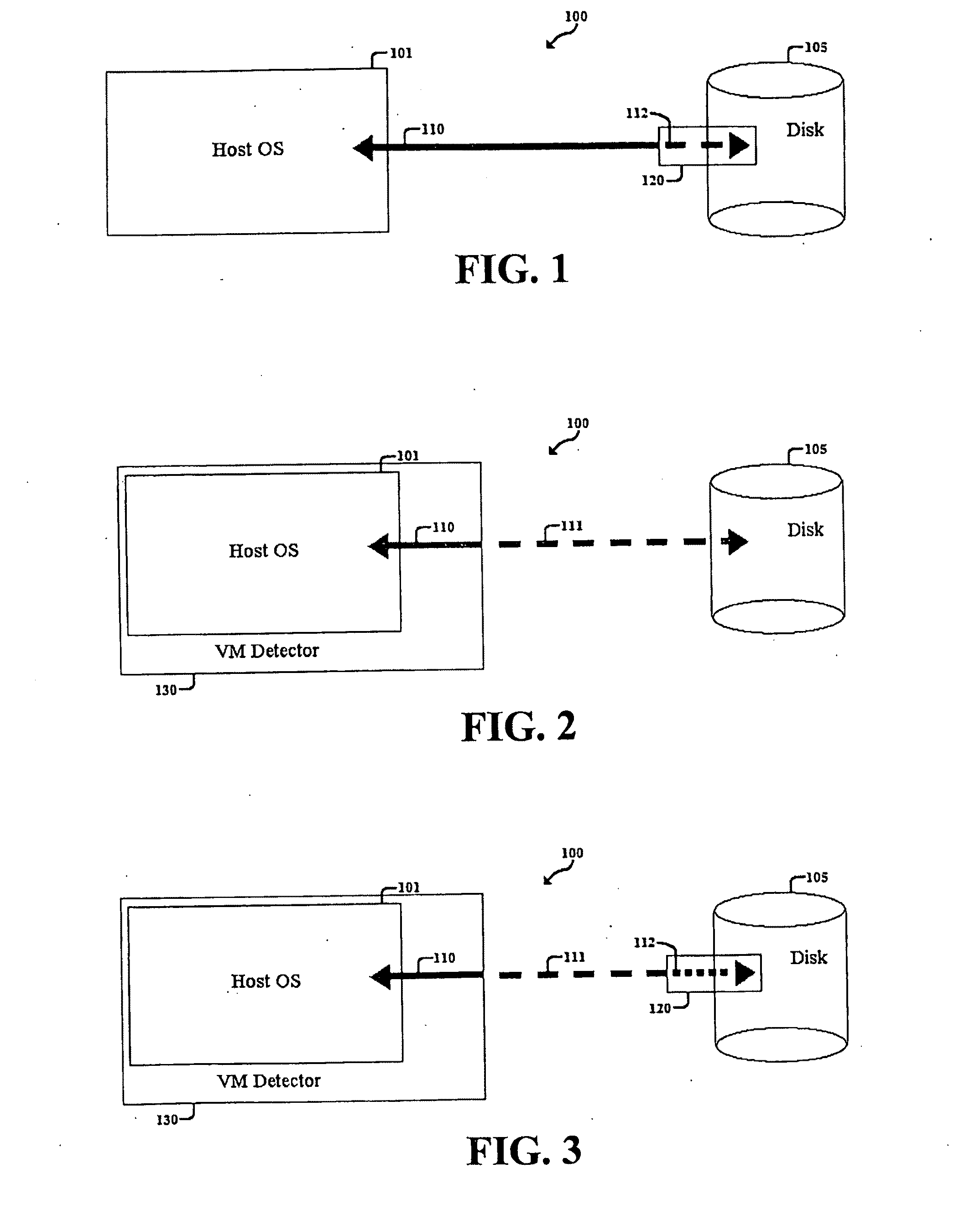
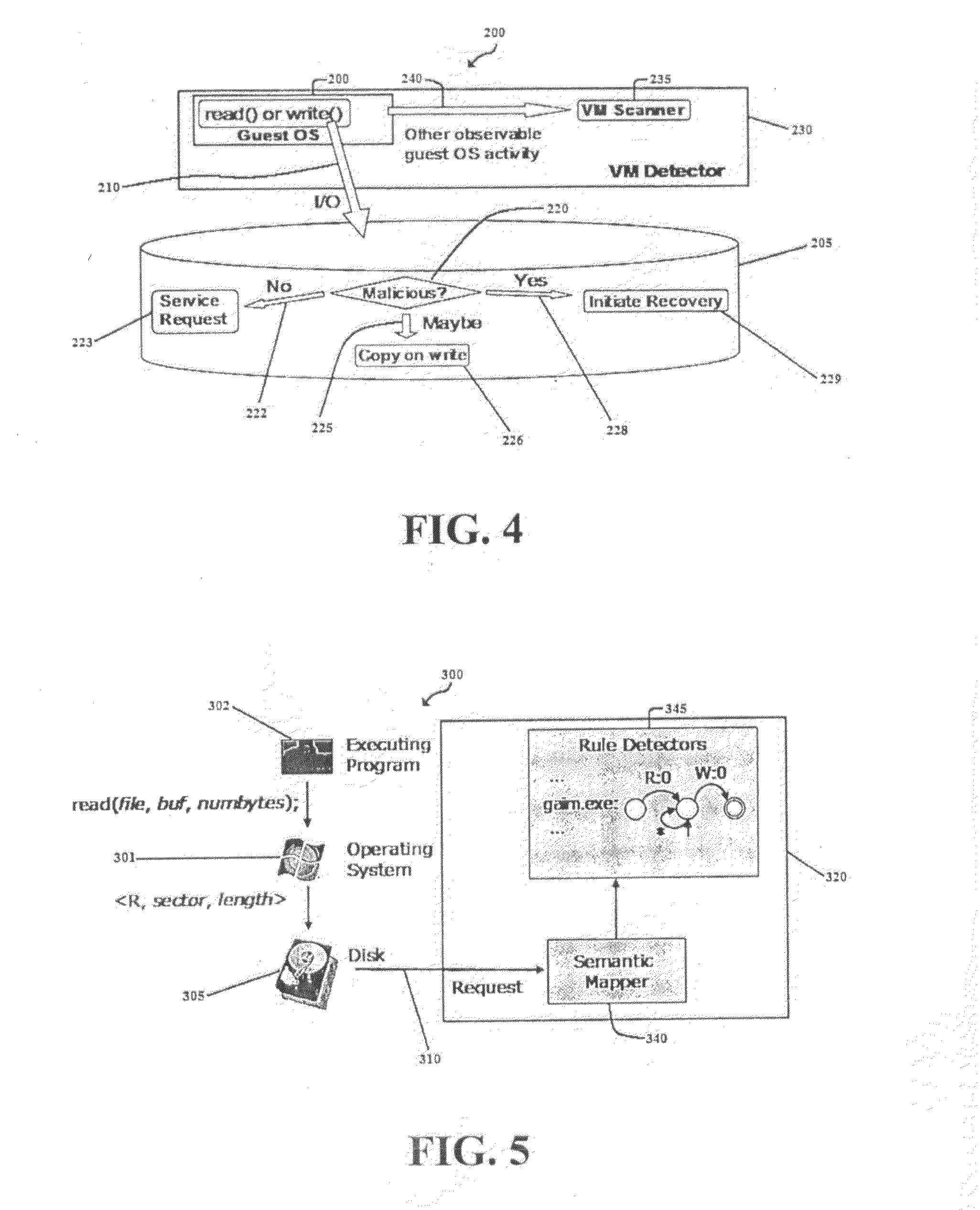
Method, System, and Computer Program Product for Malware Detection, Analysis, and Response
InactiveUS20110047618A1Reduce the burden onMinimal performance overheadMemory loss protectionError detection/correctionOperational systemMalware
A method, system, and computer program product for detecting malware from outside the host operating system using a disk, virtual machine, or combination of the two. The method, system, and computer program product detects malware at the disk level while computer files in the host operating system are in actual program execution by identifying characteristic malware properties and behaviors associated with the disk requests made. The malware properties and behaviors are identified by using rules that can reliably detect file-infecting viruses. The method, system, and computer program product also uses the disk processor to provide accelerated scanning of virus signatures, which substantially decreases overhead incurred on the host operating system by existing malware detection techniques. In the event that malware is detected, the method, system, and computer program product can respond by limiting the negative effects caused by the malware and help the system recover to its normal state.
Owner:UNIV OF VIRGINIA ALUMNI PATENTS FOUND
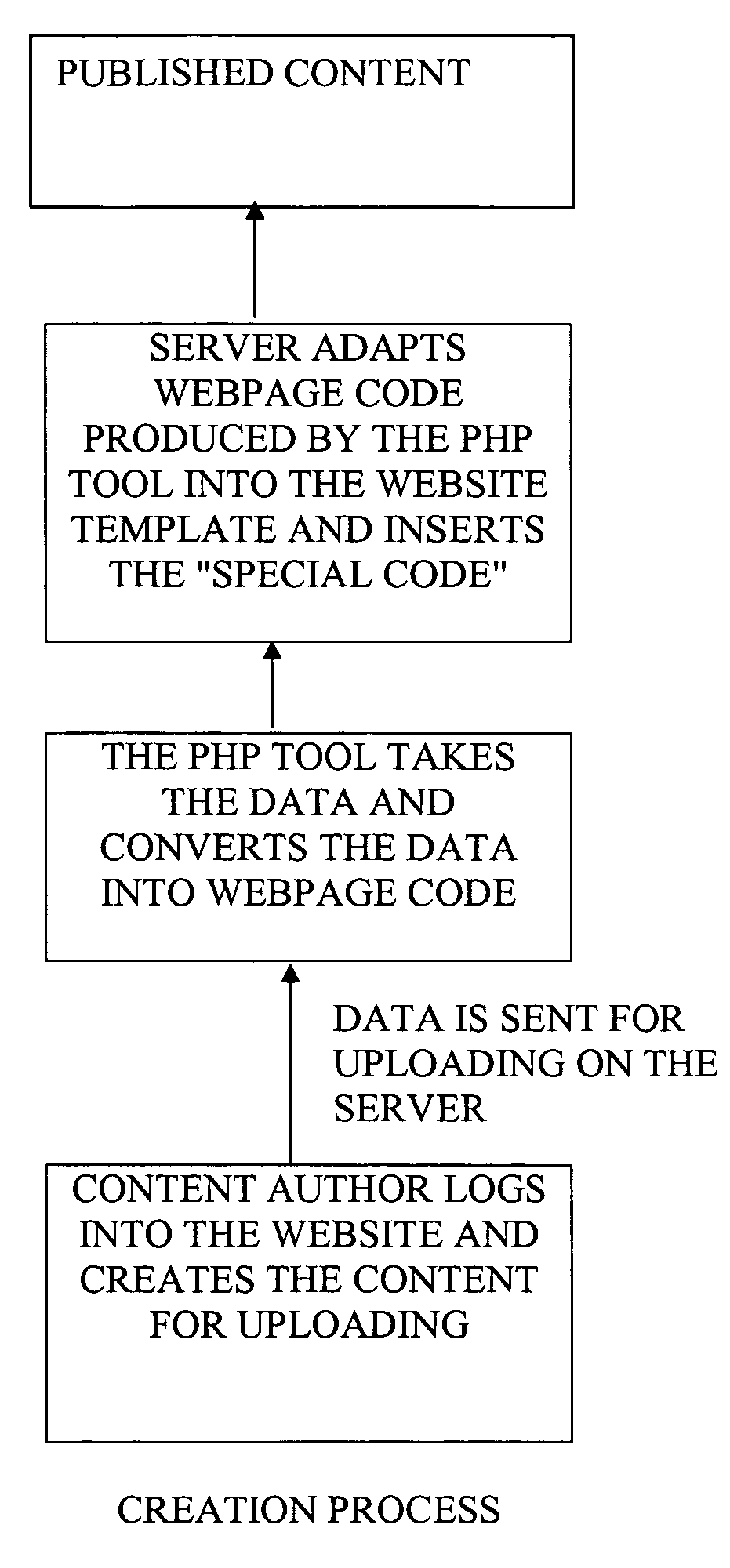
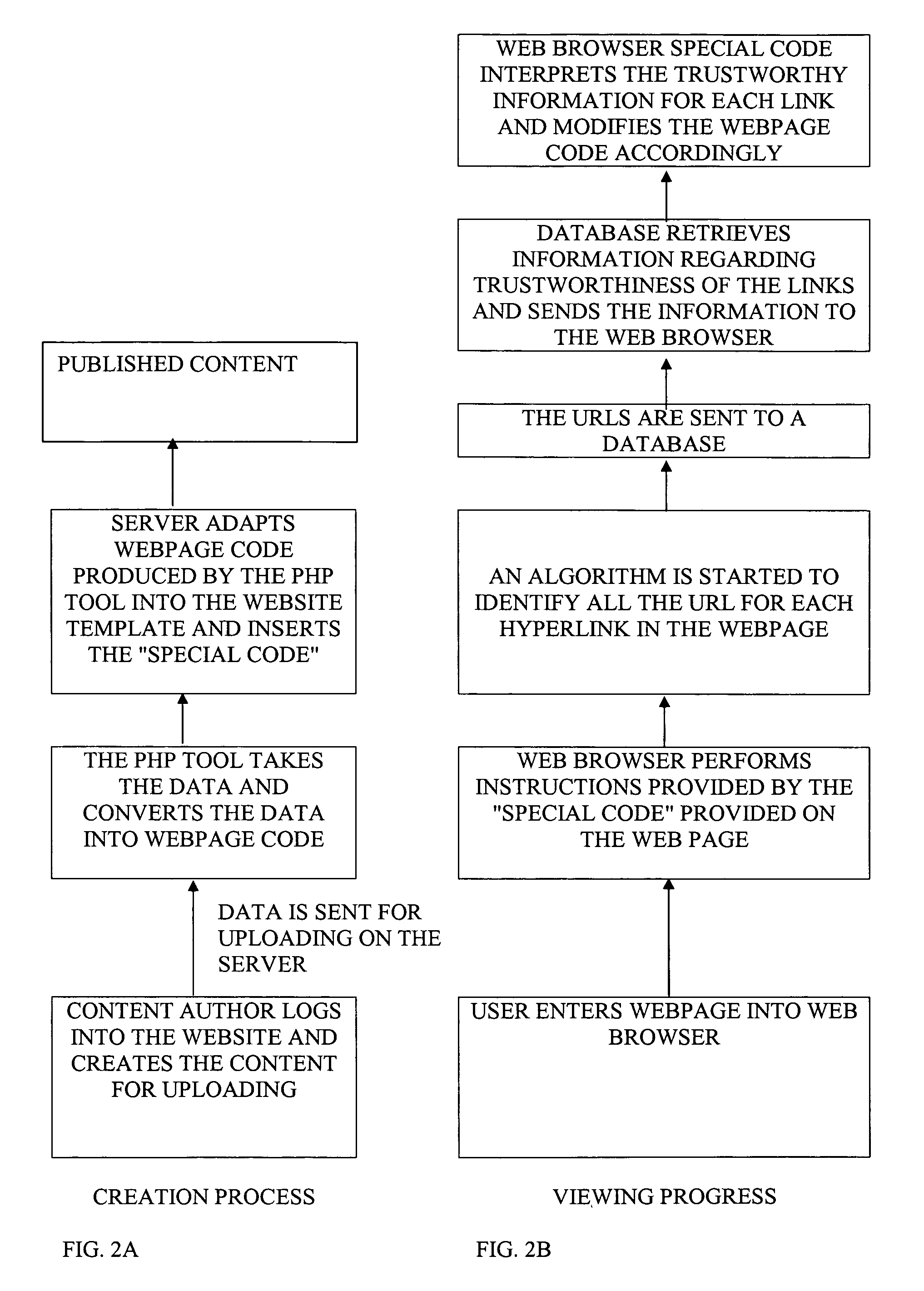
Website content regulation
ActiveUS20100017880A1Simple processReduce loadMemory loss protectionError detection/correctionWeb siteHyperlink
A method of facilitating the scanning of web pages for suspect and / or malicious hyperlinks that includes receiving at a content hosting website, user generated content. A web page or web page containing said content is then generated and, in the web page source code is included a detection code segment or a link from which a detection code segment can be downloaded. The detection code segment is executable by a web browser or web browser plug-in to scan the web page(s), or cause the web page(s) to be scanned, for suspect and / or malicious links.
Owner:FINJAN LLC
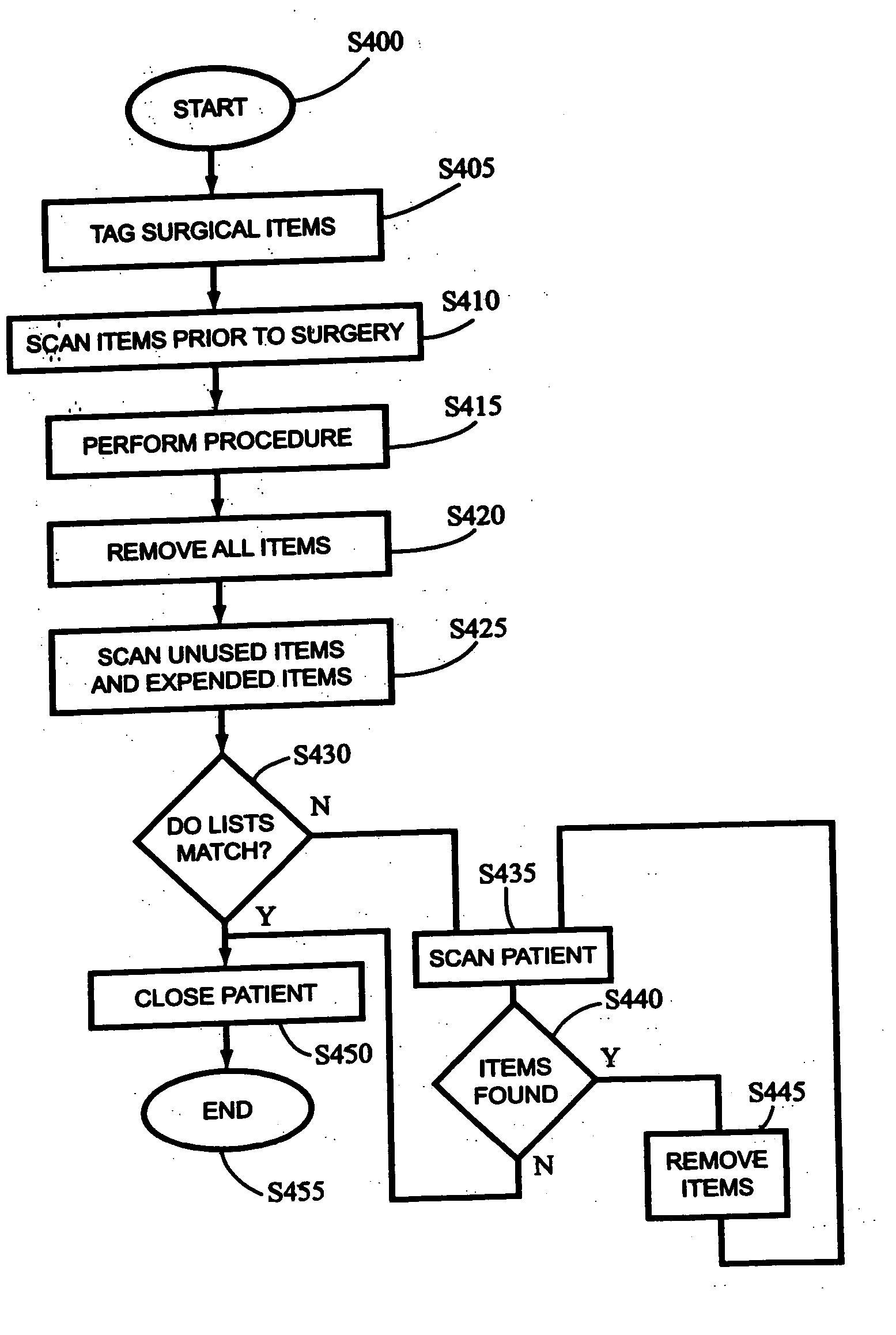
Systems and methods of accounting for surgical instruments and disposables
A system and method for the preventing unintended surgical instruments and surgical disposables from remaining in the body cavity of a patient post surgically. Individual items are tagged with an RFID transponder tag preferably at the time of manufacture. Then, after an operation is complete, but prior to would closure, the body of the patient is scanned using an RFID reader device, such as, a hand held reader device to detect the presence of any latent RFID tags. As long as no tags are identified it is presumed that the body cavity is free of any unintended items. This avoids sponge counting and other overhead intensive methods of accounting for surgical items during a surgical procedure.
Owner:WARSAW ORTHOPEDIC INC
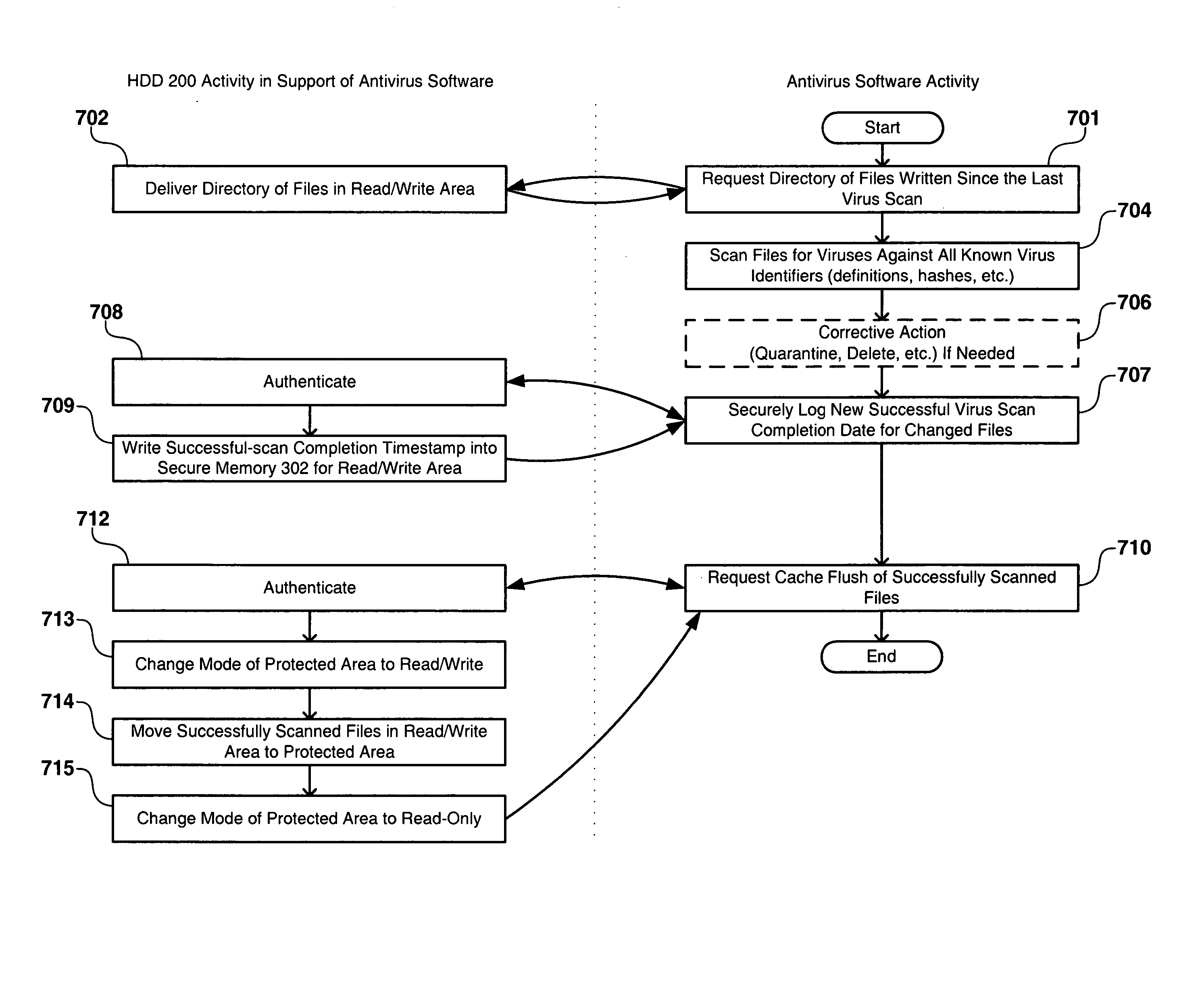
Secure storage tracking for anti-virus speed-up
ActiveUS20060021032A1Reduce scan timeEfficient and secureMemory loss protectionError detection/correctionAnti virusVirus
A computer system includes a security subsystem which is able to trustfully track which files or storage areas of a storage device have been altered since a last virus scan. The trusted information can then be used to accelerate scans for undesirable code or data such as viruses and invalid or corrupt registry entries. In the case of viruses, files or storage areas which have been altered are scanned against a super-set of virus definitions. Unaltered files or storage areas are scanned against a subset of virus definitions.
Owner:LENOVO PC INT
Storage conversion for anti-virus speed-up
ActiveUS20060021041A1Reduce scan timeEfficient and secureMemory loss protectionError detection/correctionAnti virusVirus
A computer system includes a security subsystem which is able to trustfully track which files or storage areas of a storage device have been altered since a last virus scan. The trusted information can then be used to accelerate scans for undesirable code or data such as viruses and invalid or corrupt registry entries. In the case of viruses, files or storage areas which have been altered are scanned against a super-set of virus definitions. Unaltered files or storage areas are scanned against a subset of virus definitions.
Owner:LENOVO PC INT
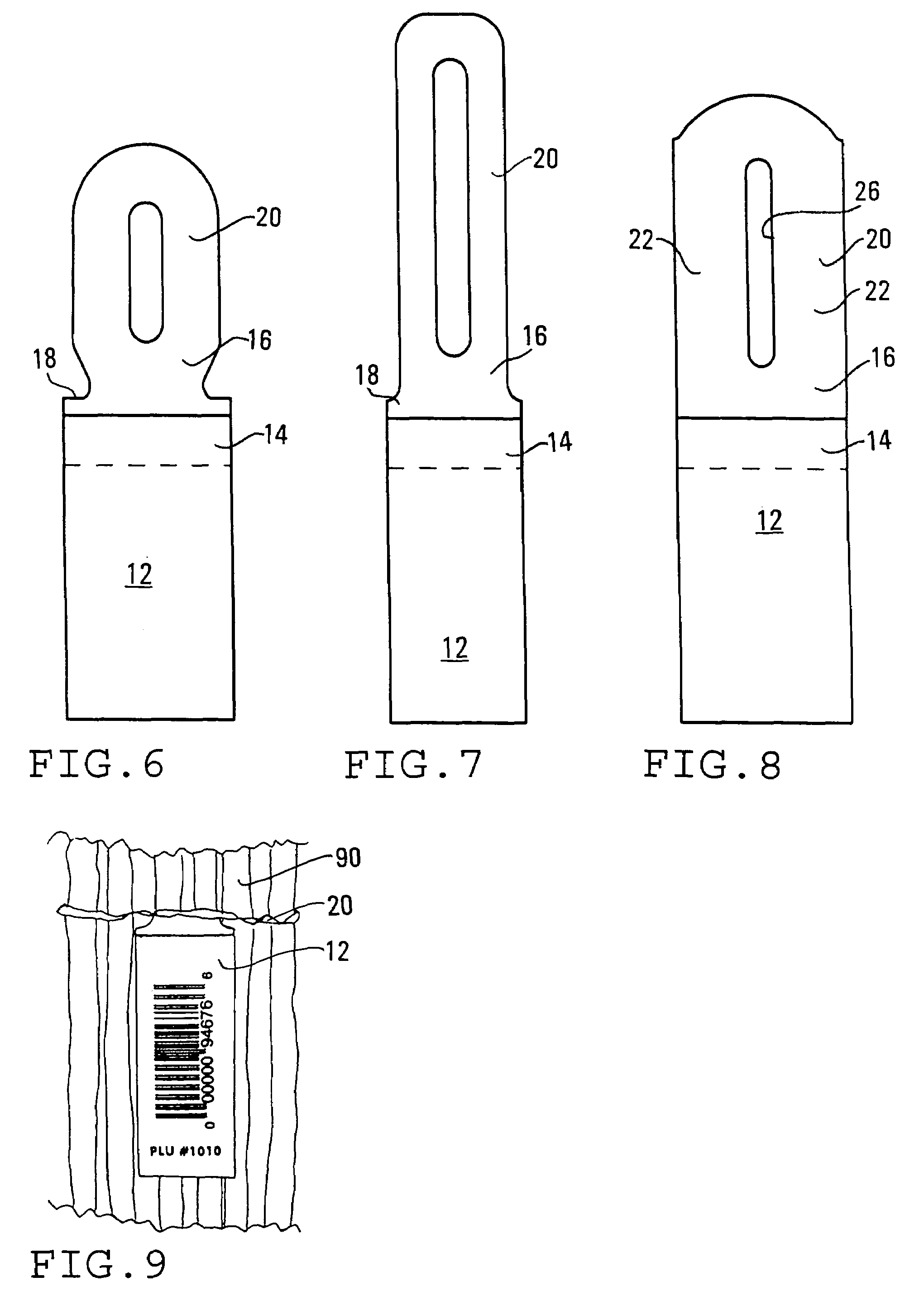
Merchandise labeling
Owner:BEDFORD IND INC
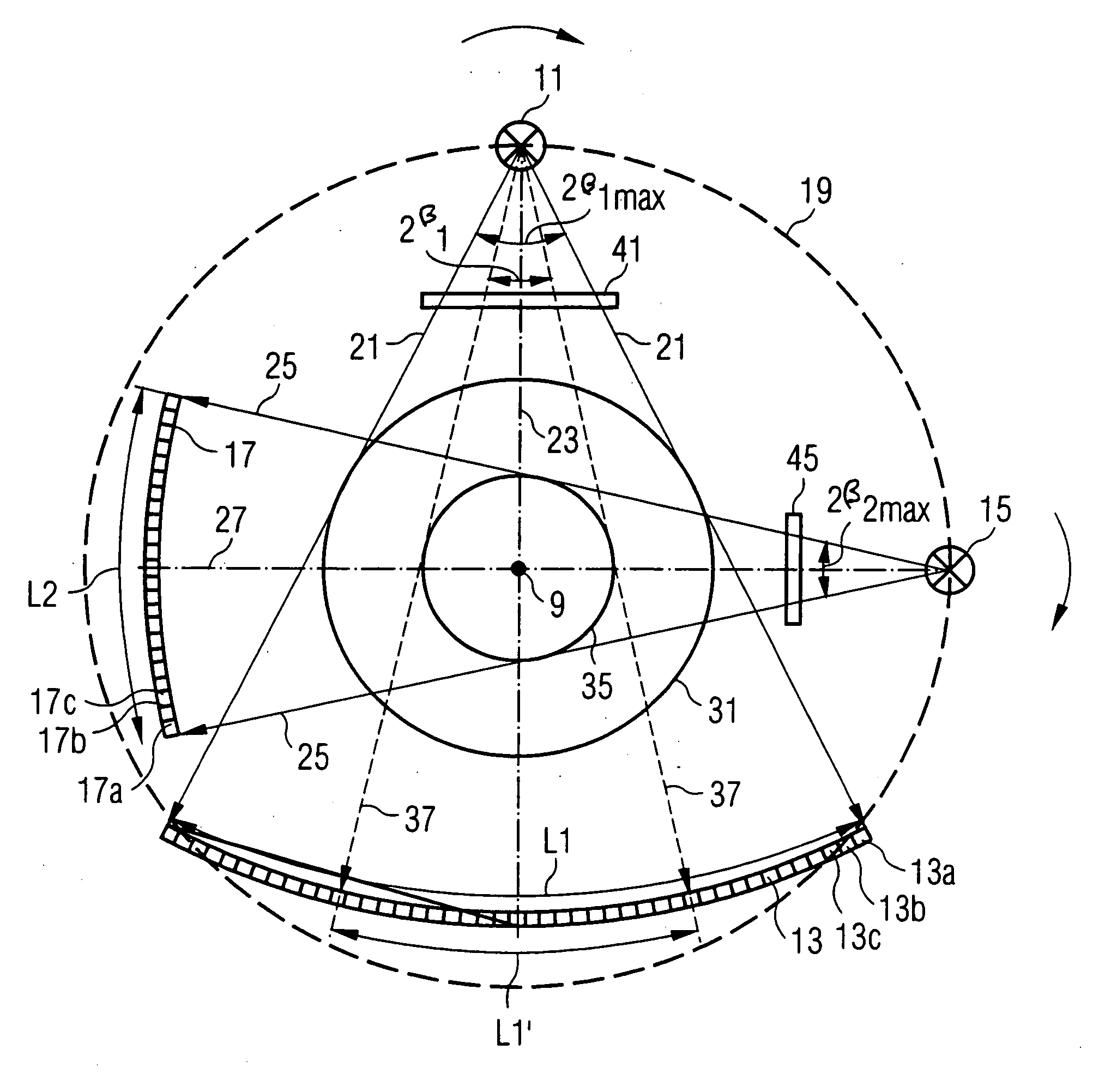
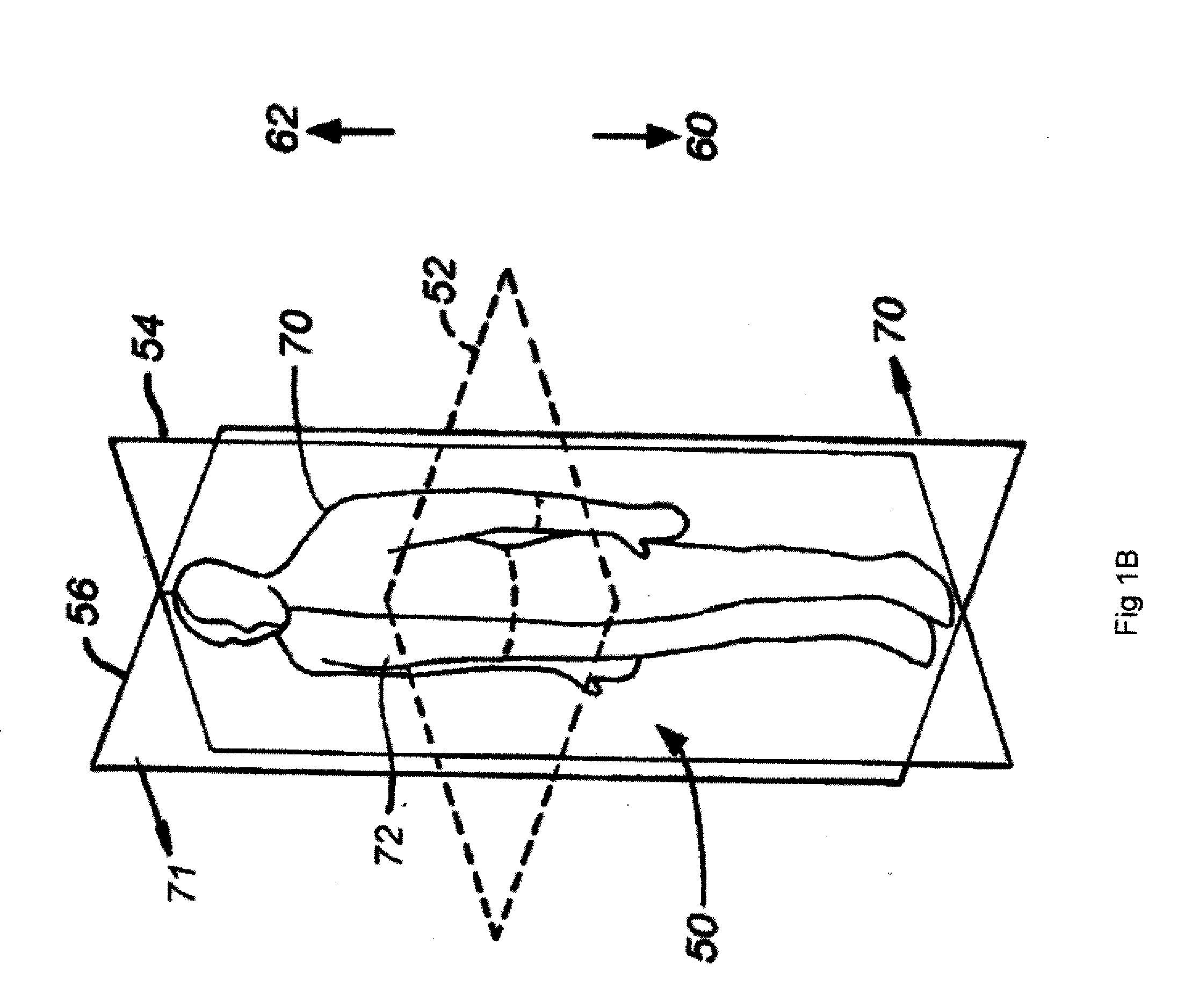
Imaging tomography apparatus with at least two radiator-detector combinations
ActiveUS20050089134A1High resolutionLarge regionRadiation/particle handlingComputerised tomographsSoft x rayTemporal resolution
An imaging tomography apparatus, in particular an x-ray computed tomography apparatus, has two acquisition systems capable of rotating around a common rotation axis. Each of the acquisition systems has a radiator as well as a detector. The maximum measurement fields scanned by the two acquisition systems given rotation around the rotation axis are of different sizes, or can be adjusted to different sizes. In particular, the lengths of both detectors measured in the azimuthal direction—are of different sizes. The tomography apparatus can be fashioned to scan the entire body cross-section of an examination subject or of a patient with conventional temporal resolution, and to scan detail region, such as a heart region, with an increased temporal resolution or accelerated data acquisition rate in comparison to a device with only one acquisition system.
Owner:SIEMENS HEALTHCARE GMBH
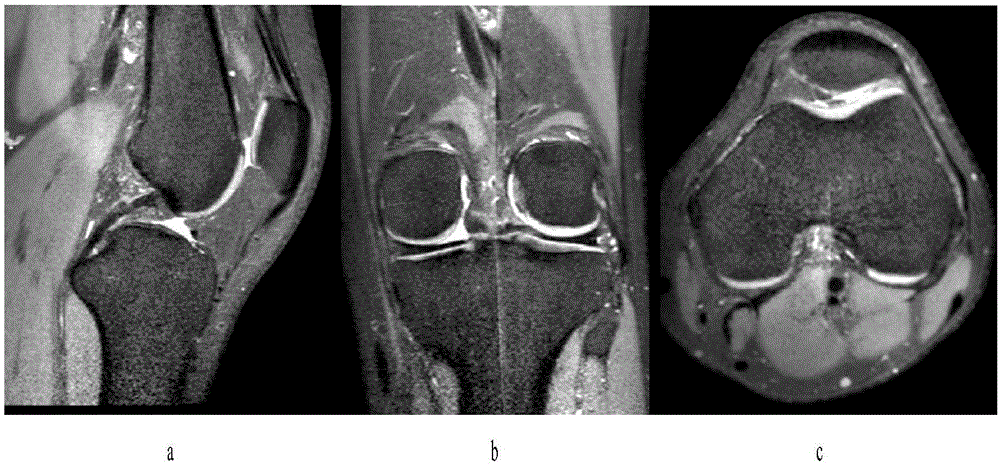
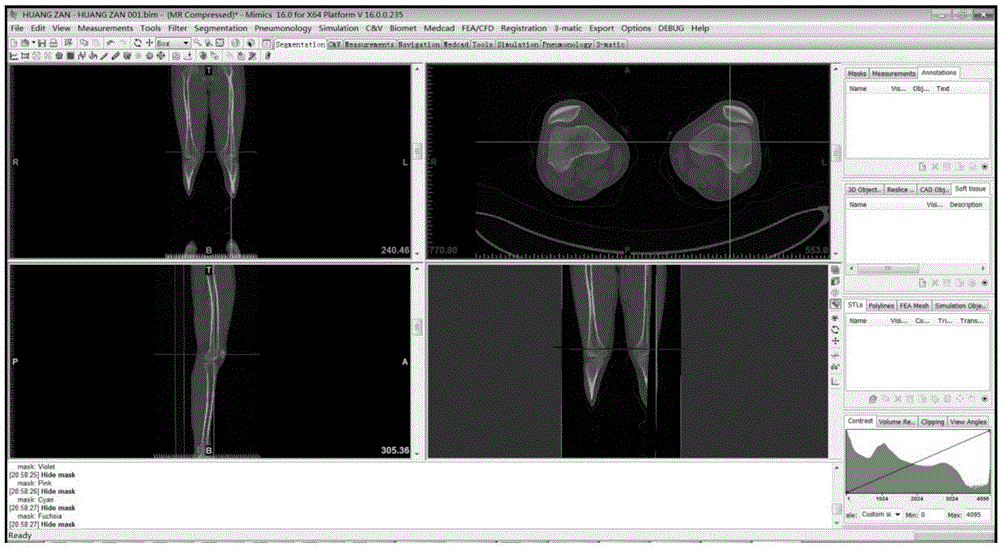
Method for establishing human knee joint three-dimensional simulation model in combination with CT (Computed Tomography) and MRI (Magnetic Resonance Imaging)
InactiveCN105139442AEasy to scanClear imageInput/output processes for data processing3D modellingThree dimensional modelFemur
The invention relates to a method for establishing a human knee joint three-dimensional simulation model in combination with CT (Computed Tomography) and MRI (Magnetic Resonance Imaging), and belongs to the technical field of medical images. The method comprises six steps of CT image acquisition, MRI image acquisition, data storage, CT two-dimensional image importing and three-dimensional model establishment, MRI two-dimensional image importing and three-dimensional model establishment, and knee joint anatomy simulation model registration and modification. The method combines the advantages of CT and MRI scanning, so that the scanning is convenient and fast, the images are clear, the dissection relation is definite, the density resolution is very high, and the scanning range is very wide. According to the method, two sets of images are registered through a three-dimensional image registration technology, three-dimensional coordinate systems of two types of images are unified by fitting point cloud contours and anatomical feature points of femurs, tibias and fibulas, and registration is performed through a registration module to obtain a double-lower-limb full-length knee joint three-dimensional digital model with structures of bones, cartilages, meniscuses, ligaments, muscle tendons and the like.
Owner:FIRST AFFILIATED HOSPITAL OF KUNMING MEDICAL UNIV
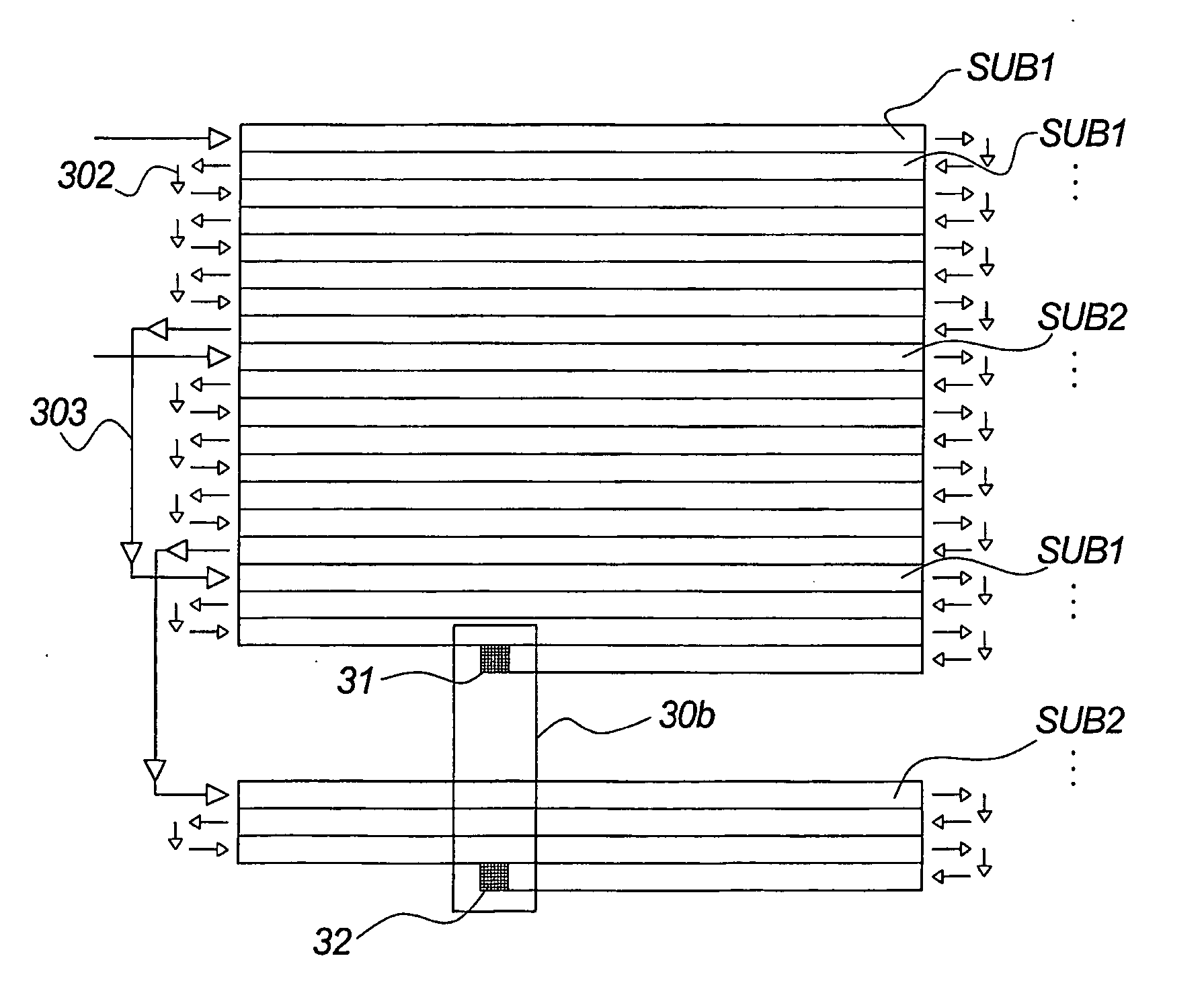
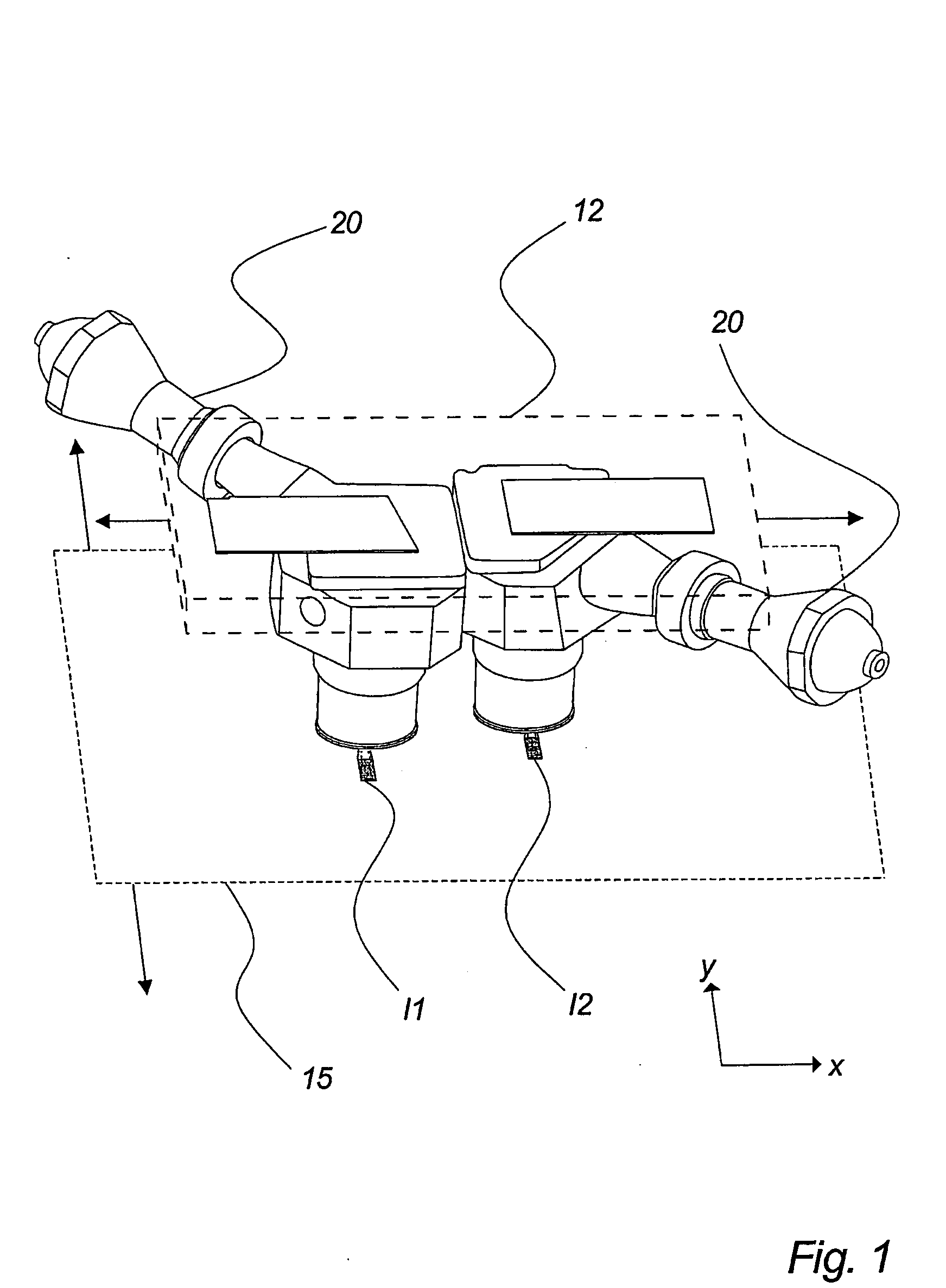
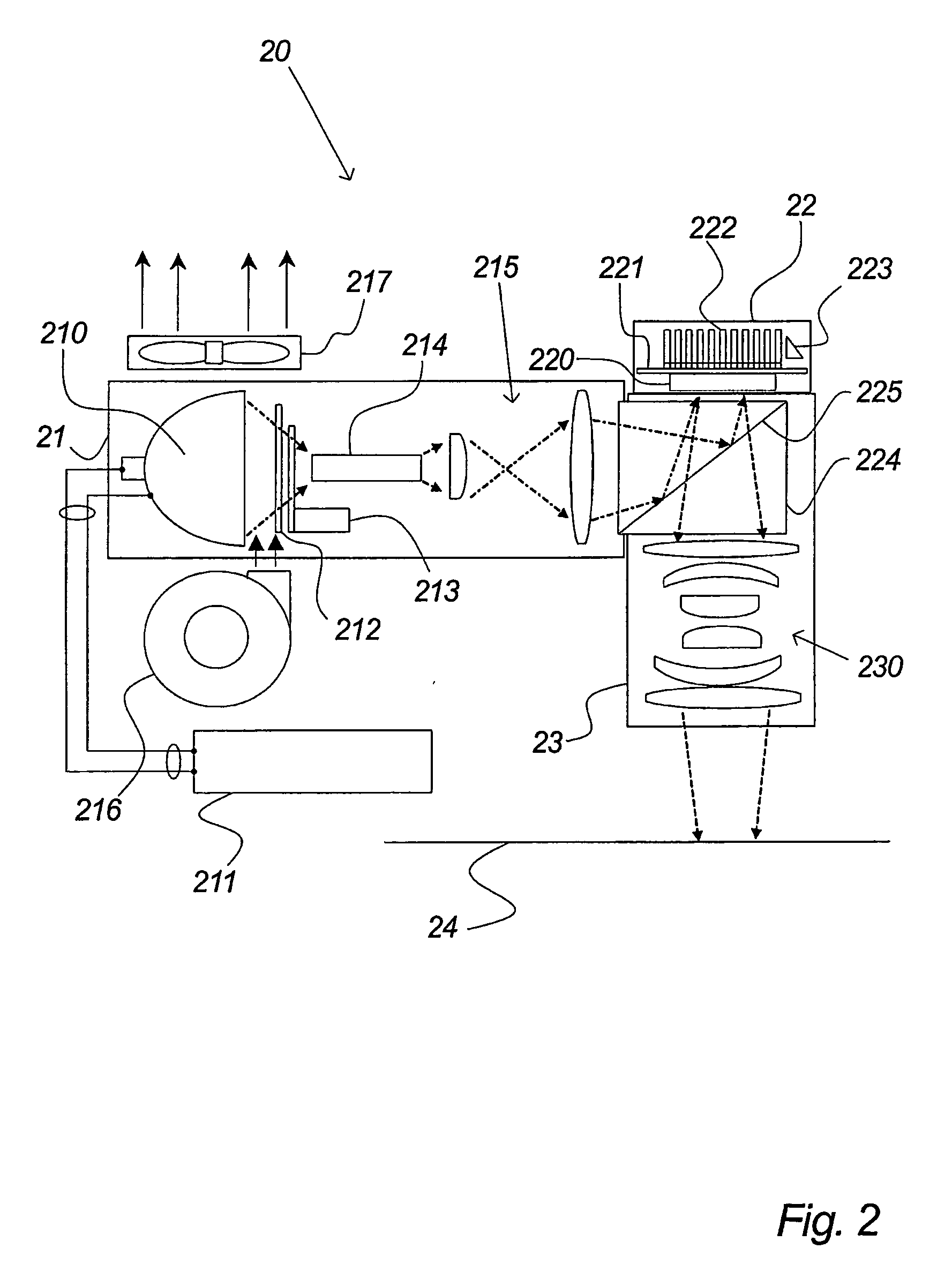
Light modulating engine
InactiveUS20050168789A1Effective scanning areaSolve the slow scanning speedTelevision system detailsProjectorsSpatial light modulatorLight emitter
The invention relates to a light illumination apparatus comprising at least one exposure head (12) and at least two light modulating arrangements (20), each of said two light modulating arrangements (20) comprising a spatial light modulator (31, 32) and an associated light emitter arranged for illumination of an illumination surface (15) via said spatial light modulator (31, 32), each of said two light modulating arrangements (20) being digitally controlled, said apparatus comprising means for performing a relative movement between said at least one exposure head and said illumination surface (15) in at least one direction (x;y).
Owner:SIGN TRONIC
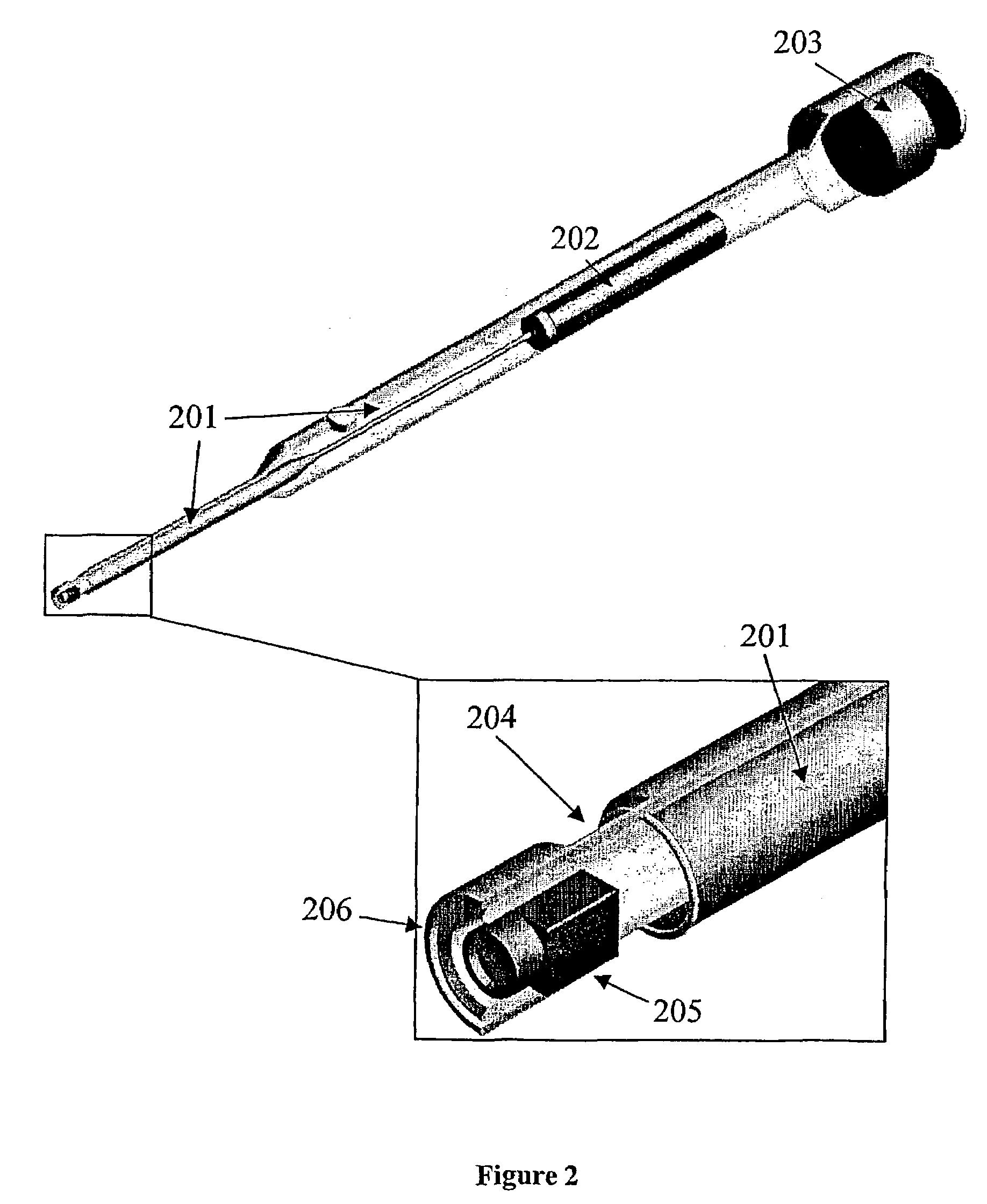
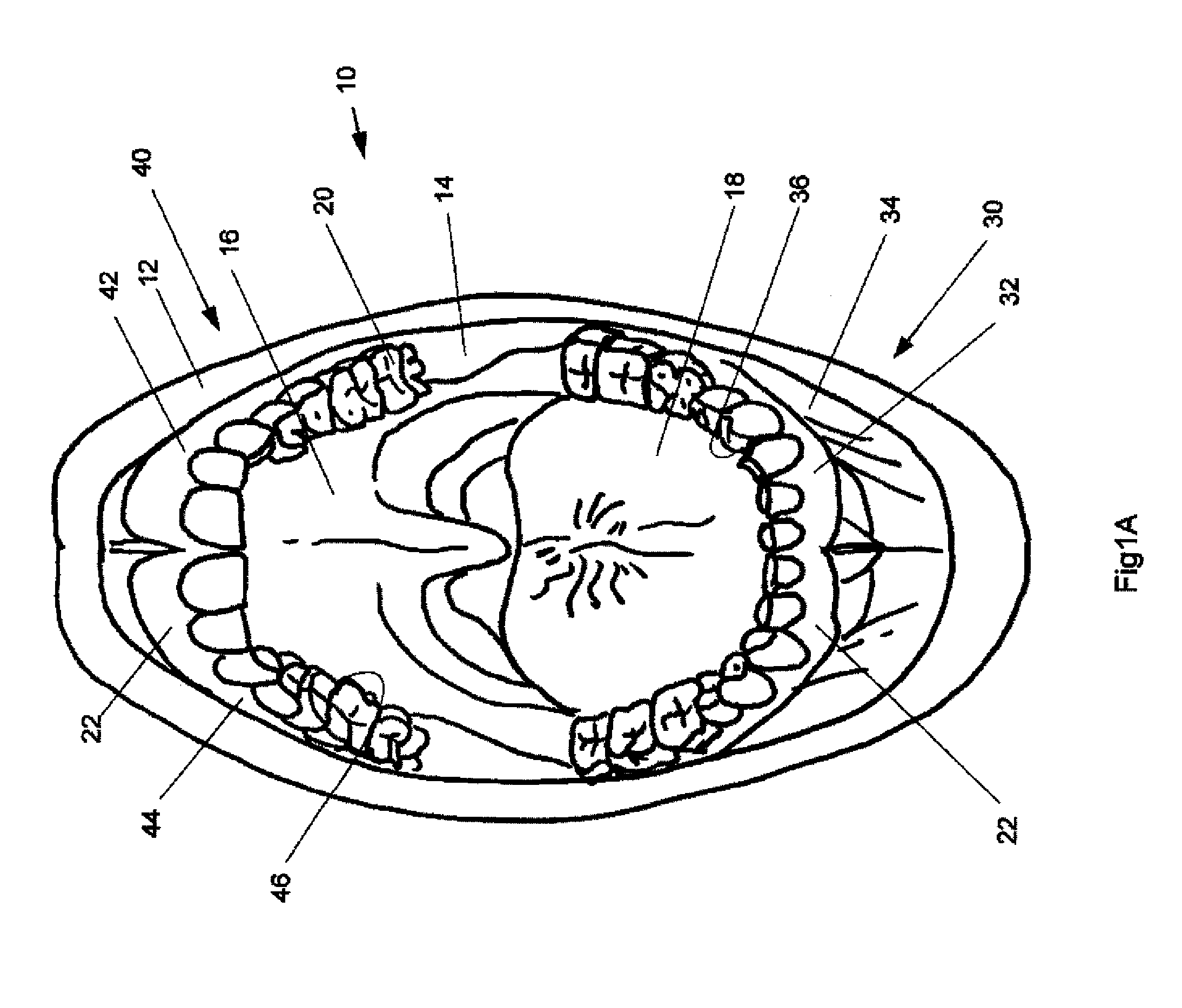
Methods, devices, systems, assemblies, and kits for tissue retraction in an oral cavity
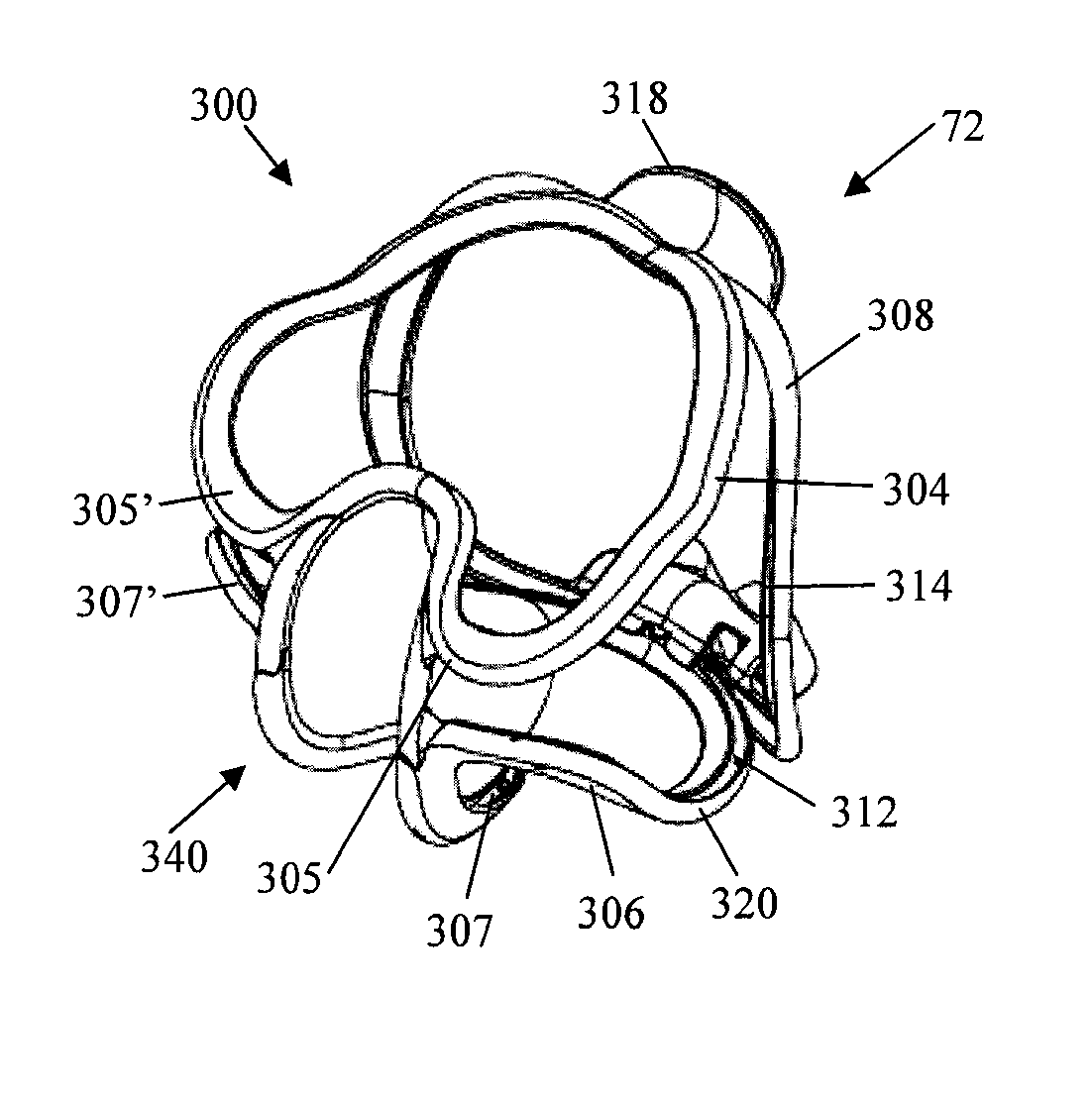
InactiveUS20090081611A1Improve accessibilityEfficient separationImpression capsSurgeryVisibilityDentistry
Provided herein is a retraction device for retracting soft tissue from the dental surfaces in the oral cavity of a patient. The retraction device is comprised of a topology conformable structure, where the topology conformable structure is adaptable to be delivered to the oral cavity in a constrained shape. The device can then undergo a conformation change in the oral cavity, where the device transforms into its unconstrained shape. The unconstrained shape of the device creates a useable working field in the oral cavity. The useable working field can provide increased accessibility to and / or visibility within the oral cavity. Also provided herein are methods for using the device and kits.
Owner:ULTRADENT PROD INC
Imaging tomography apparatus with at least two radiator-detector combinations
ActiveUS7016455B2High resolutionLarge regionRadiation/particle handlingComputerised tomographsSoft x rayTemporal resolution
An imaging tomography apparatus, in particular an x-ray computed tomography apparatus, has two acquisition systems capable of rotating around a common rotation axis. Each of the acquisition systems has a radiator as well as a detector. The maximum measurement fields scanned by the two acquisition systems given rotation around the rotation axis are of different sizes, or can be adjusted to different sizes. In particular, the lengths of both detectors measured in the azimuthal direction—are of different sizes. The tomography apparatus can be fashioned to scan the entire body cross-section of an examination subject or of a patient with conventional temporal resolution, and to scan detail region, such as a heart region, with an increased temporal resolution or accelerated data acquisition rate in comparison to a device with only one acquisition system.
Owner:SIEMENS HEALTHCARE GMBH
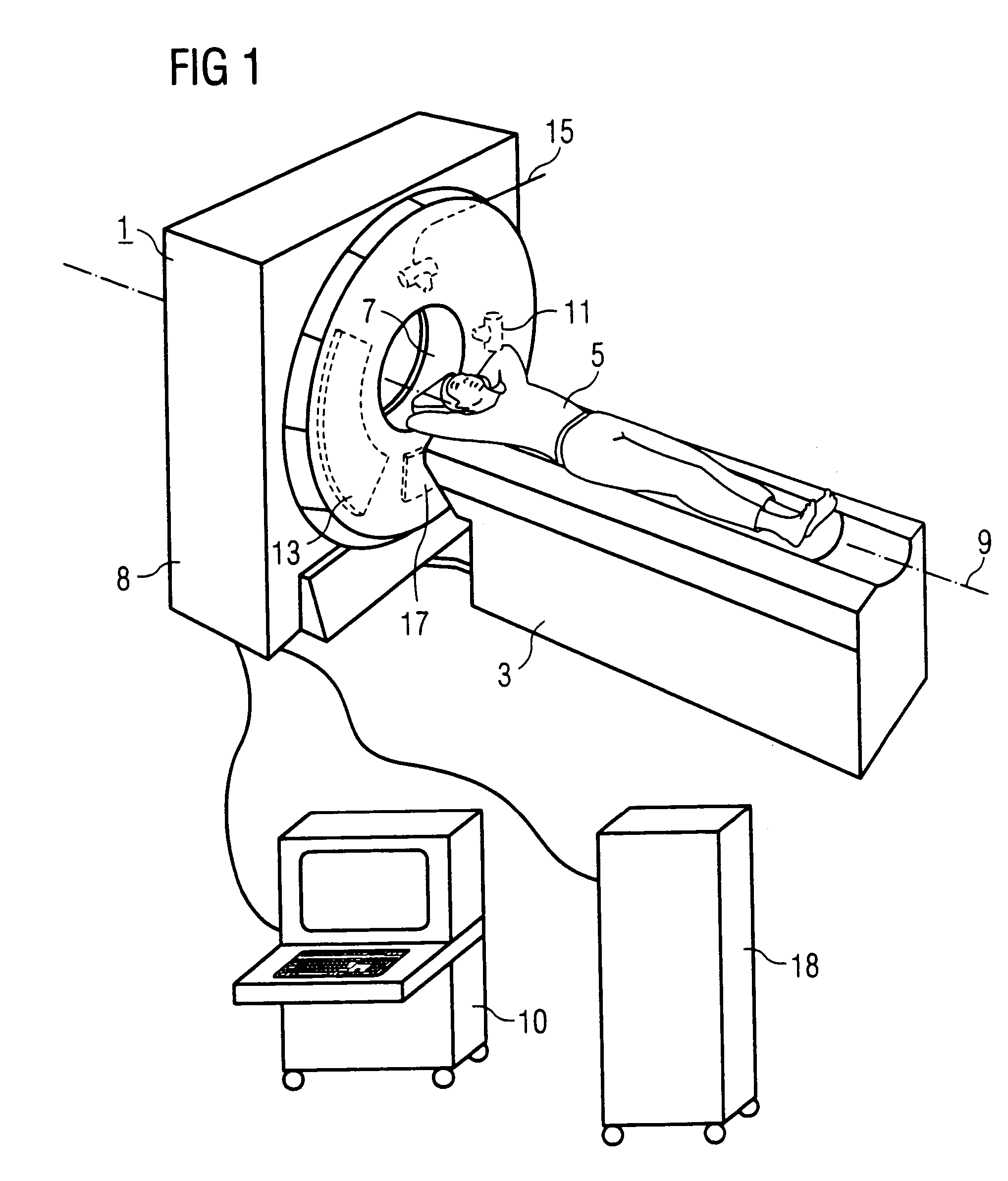
Small-sized bedside CT (computed tomography) scanner
ActiveCN105232076ALow costReduced fan angle requirementsComputerised tomographsTomographyCt scannersX-ray
The invention discloses a small-sized bedside CT (computed tomography) scanner. The small-sized bedside CT scanner comprises a frame, a rotating component, an imaging system and a drag chain component. The imaging system is provided with an X-ray source module and a detector module which are arranged on the same sidewall of the rotating component symmetrically along the axial center, the X-ray source module is connected with the rotating component through a rotating shaft, and the detector module is used for receiving emergent rays from the X-ray source module correspondingly in a translational motion manner. The drag chain component straddles the sidewall of the frame, the straddling length is not more than the semi-perimeter of the frame, one end of the drag chain component is fixed on the frame while the other end thereof is arranged on the sidewall of the frame movably along with the rotating component, and a cable is connected with a power supply and the imaging system through the drag chain component. The small-sized bedside CT scanner mainly solves the technical problem that an existing CT scanner has extremely high requirements on worksite floors.
Owner:SUZHOU INST OF BIOMEDICAL ENG & TECH CHINESE ACADEMY OF SCI
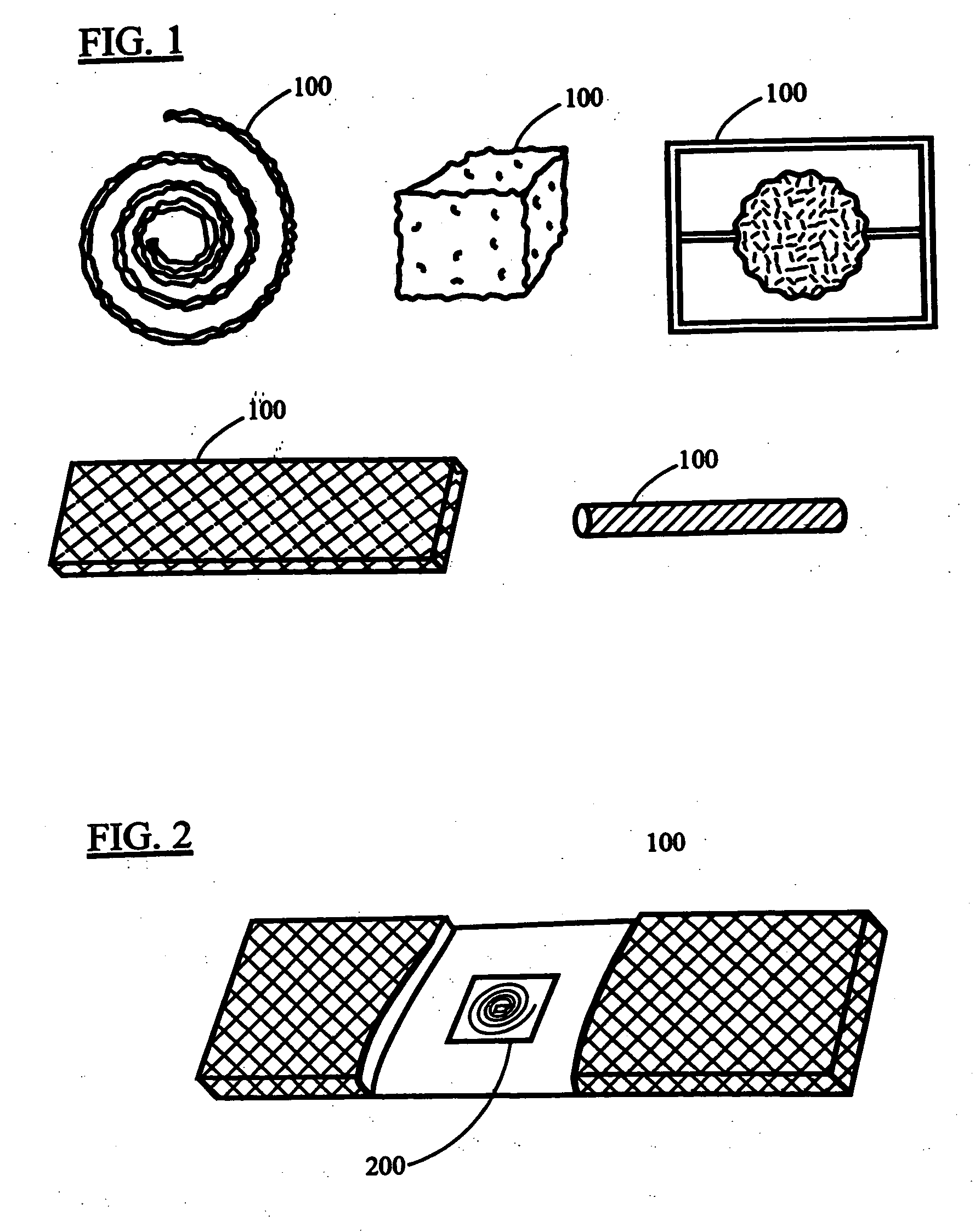
Radio frequency detectable medical supplies
InactiveUS20060065739A1Eliminate needEasy to scanAbsorbent padsRecord carriers used with machinesLaparotomy spongeRe entry
A medical supply such as an operating room towel, laparotomy sponge, gauze pad, bandage, or swab with radio frequency detectable material which eliminates the need for re-entry into a patent after operating in situations where medical supplies are missing. The patent can be easily scanned with a handheld scanner to determine if the medical supply was accidentally left inside the patient. If no RF detectable material is observed, unnecessary re-entry into the patient is prevented. The radio frequency detectable material is incorporated into the medical supply as a tag, in the handle, as a handle, stitched to the medical supply, woven into the medical supply, or sewn into a seam in the medical supply. An identifier on the medical supply indicates that the medical supply is an RF detectable medical supply. In addition to preventing unnecessary re-entry, scanning for RF detectable material is much safer than scanning for x-ray detectable material.
Owner:FALLS WILLIAM HALLEN JR +1
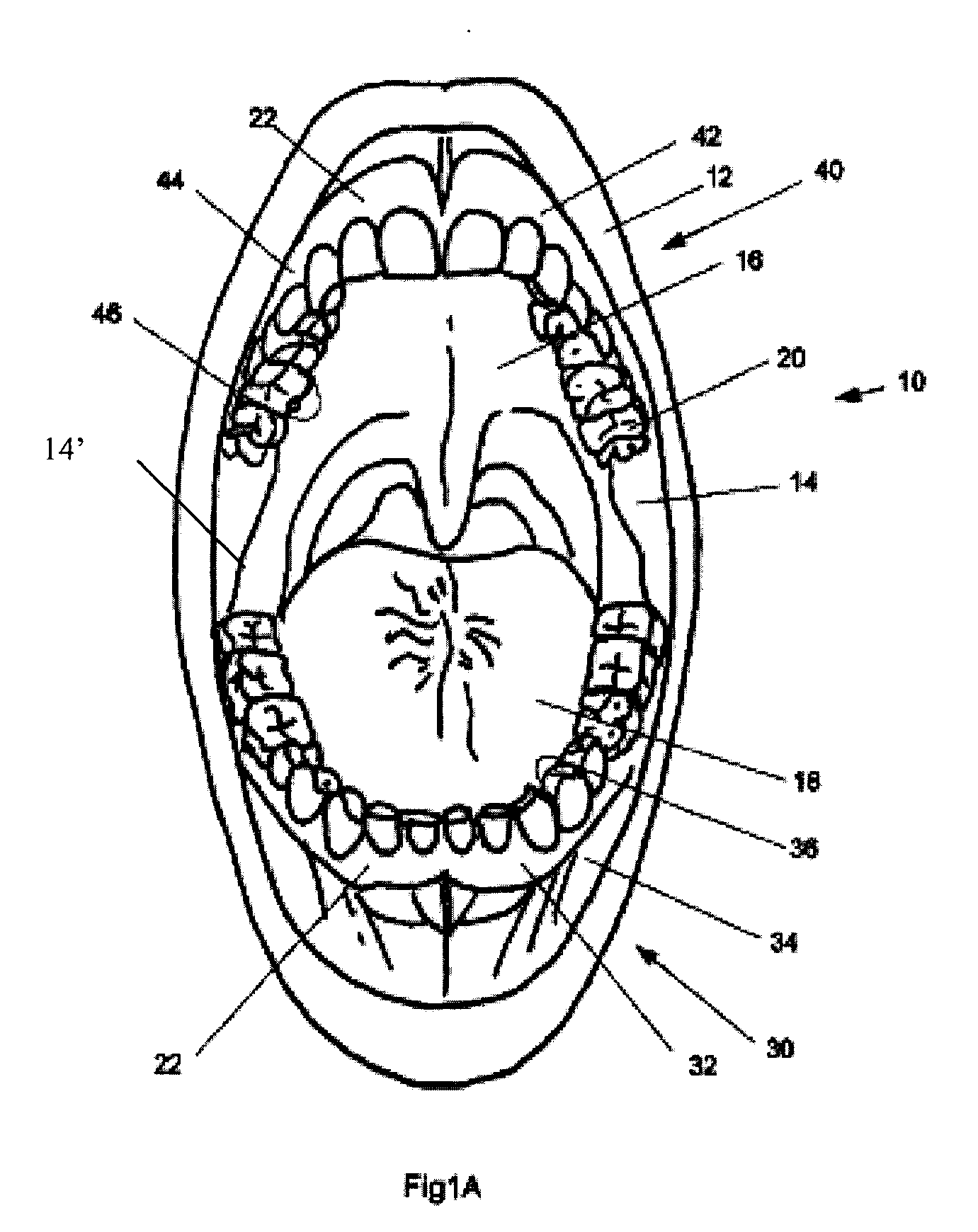
Method of dental microscopic procedure
InactiveUS20070098237A1Easily scan a specific tooth, surrounding teethEasy to scanImpression capsData processing applicationsSurgical mirrorOptical axis
A method of dental microscopic procedure, using a digital surgical scope, includes steps for selecting a function of the digital surgical scope to perform, obtaining the corresponding images from the image data taking device or the image data processing / storing device, processing the images by the image data processing / storing device, and displaying the images on the displays. The dental surgical procedure is done by seeing the images displayed on the screen. The digital surgical scope includes a microscope lens assembly for magnifying an optical image of an object and an in-line illumination device for illuminating the object along the same optical axis and from the same direction of the microscope lens assembly. The image data processing / storing device is for manipulating the image taken by the microscope lens assembly and the image data taking device.
Owner:YOO BEN +3
3D printing machine with three-dimensional figure feedback system and printing method of 3D printing machine
InactiveCN105666877AHigh precisionImprove printing efficiencyAdditive manufacturing apparatusGraphicsControl system
The invention discloses a 3D printing machine with a three-dimensional figure feedback system and a printing method of the 3D printing machine. The 3D printing machine comprises a rack, a printing platform, a printing spray head, a material box, a feeding device, a drive device, a control system, a computer, a support mounted on the outer side of the drive device and a 3D scanner which is arranged on the support and used for scanning a printed article. In the product forming process, the 3D scanner is used for scanning a semi-finished workpiece or a blank, the three-dimensional profile of the workpiece is obtained and compared with a three-dimensional model of a target product through graphics operation, the motion path and printing parameters of the printing machine are adjusted according to a result, and therefore feedback control of the printing process is achieved, and the 3D printing forming precision and the printing efficiency are improved.
Owner:MATERIAL INST OF CHINA ACADEMY OF ENG PHYSICS
Reading machine
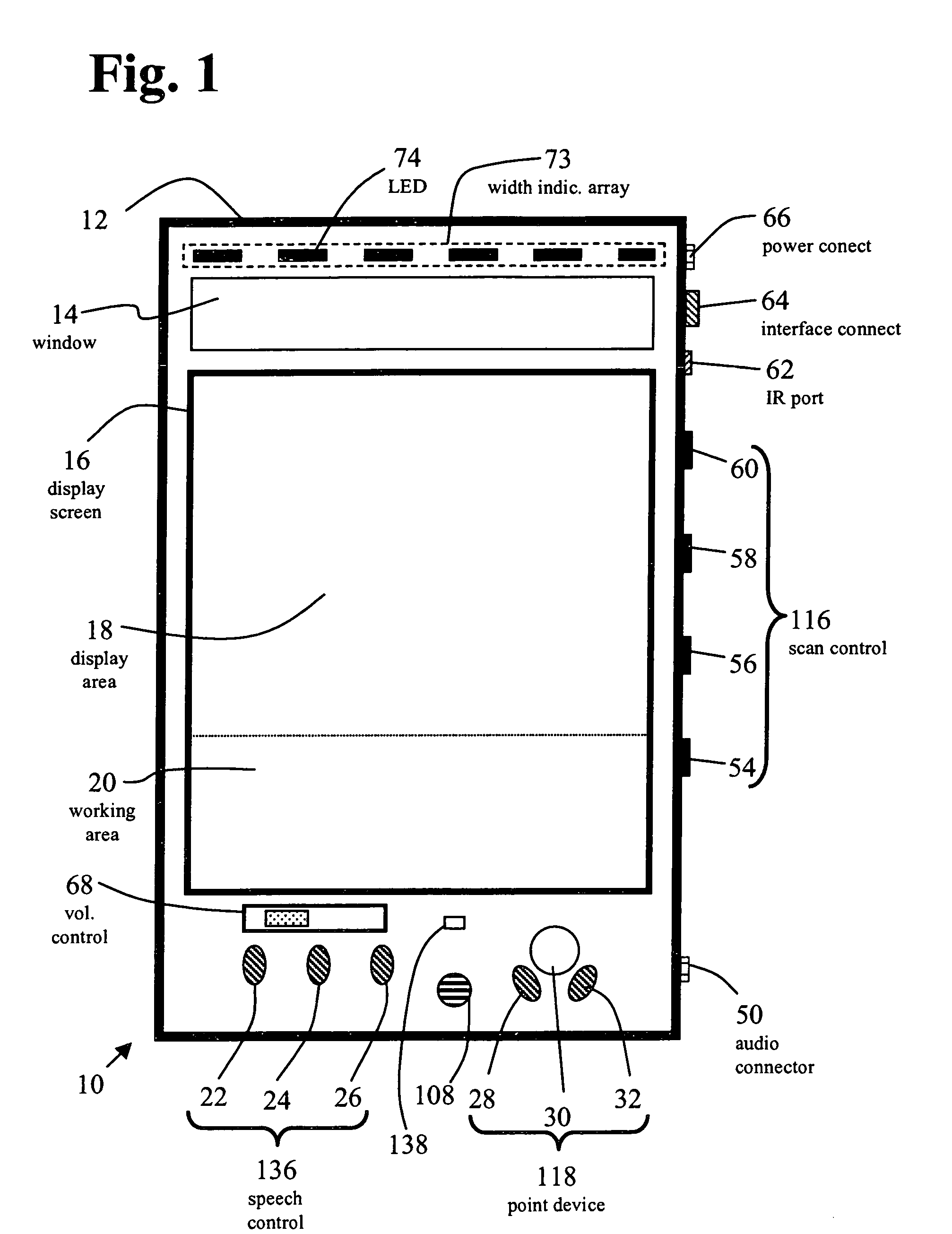
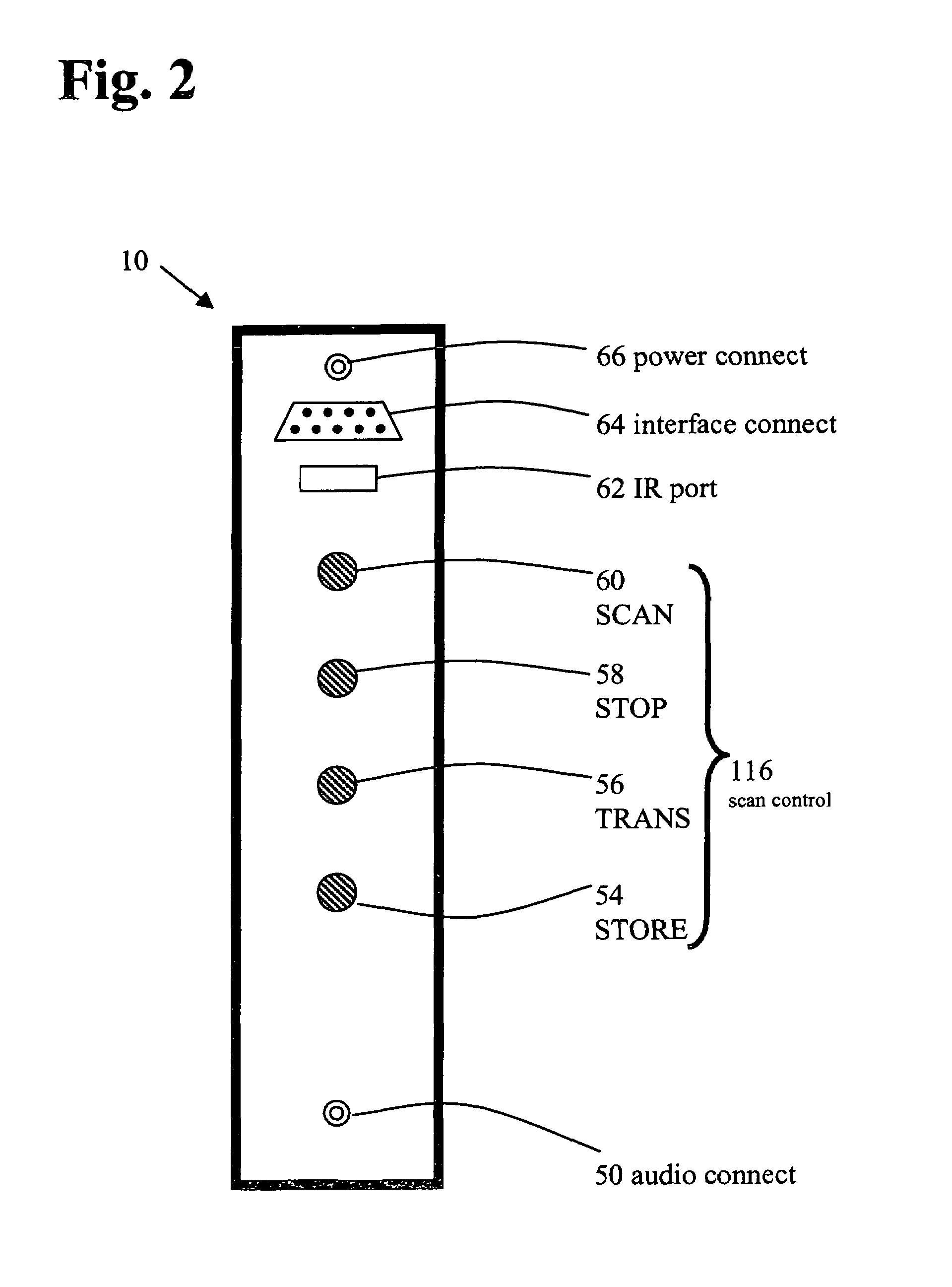
InactiveUS6965862B2Permit note takingEasy to scanCharacter and pattern recognitionSpeech synthesisSpoken languageHeadphones
A portable reading machine has a scanner for scanning an image comprising text. The scanner has a scanning area occupying a maximum width and an active width defined by a scanning width limiting mechanism adjustable to a preselected width. A photoreceptive element forms an electronic representation of a portion of the image within the active width. The electronic representation is converted to a digital character string corresponding to the active image text. A speech system outputs the digital character string as ordinary spoken language voiced through a speaker or headset.
Owner:SCHULLER CARROLL KING
Methods, devices, systems, assemblies, and kits for tissue retraction in an oral cavity
ActiveUS20130230822A1Improve accessibilityEfficient separationImpression capsSurgeryVisibilityDentistry
Provided herein is a retraction device for retracting soft tissue from the dental surfaces in the oral cavity of a patient. The retraction device is comprised of a topology conformable structure, where the topology conformable structure is adaptable to be delivered to the oral cavity in a constrained shape. The device can then undergo a conformation change in the oral cavity, where the device transforms into its unconstrained shape. The unconstrained shape of the device creates a useable working field in the oral cavity. The useable working field can provide increased accessibility to and / or visibility within the oral cavity. Also provided herein are methods for using the device and kits.
Owner:ULTRADENT PROD INC
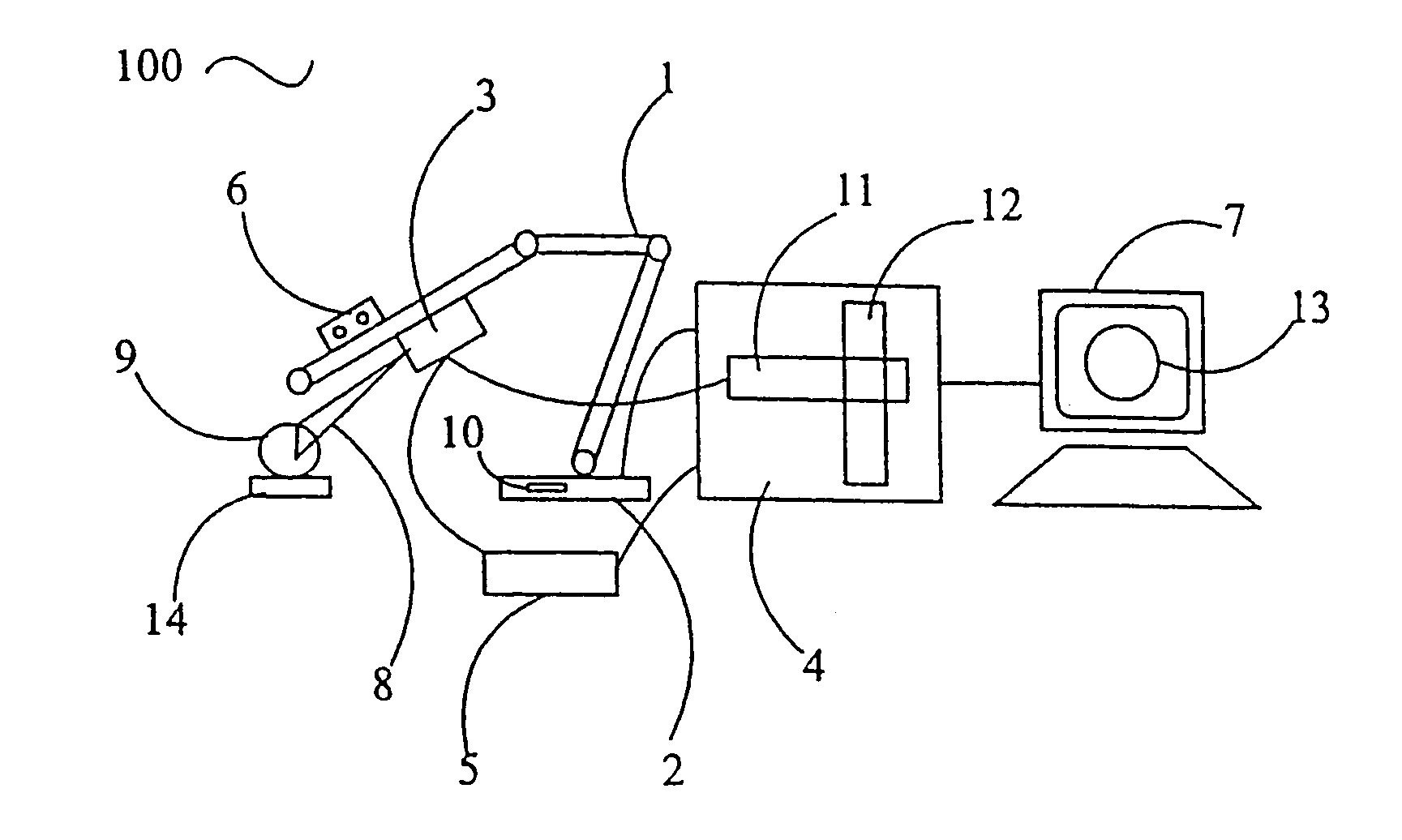
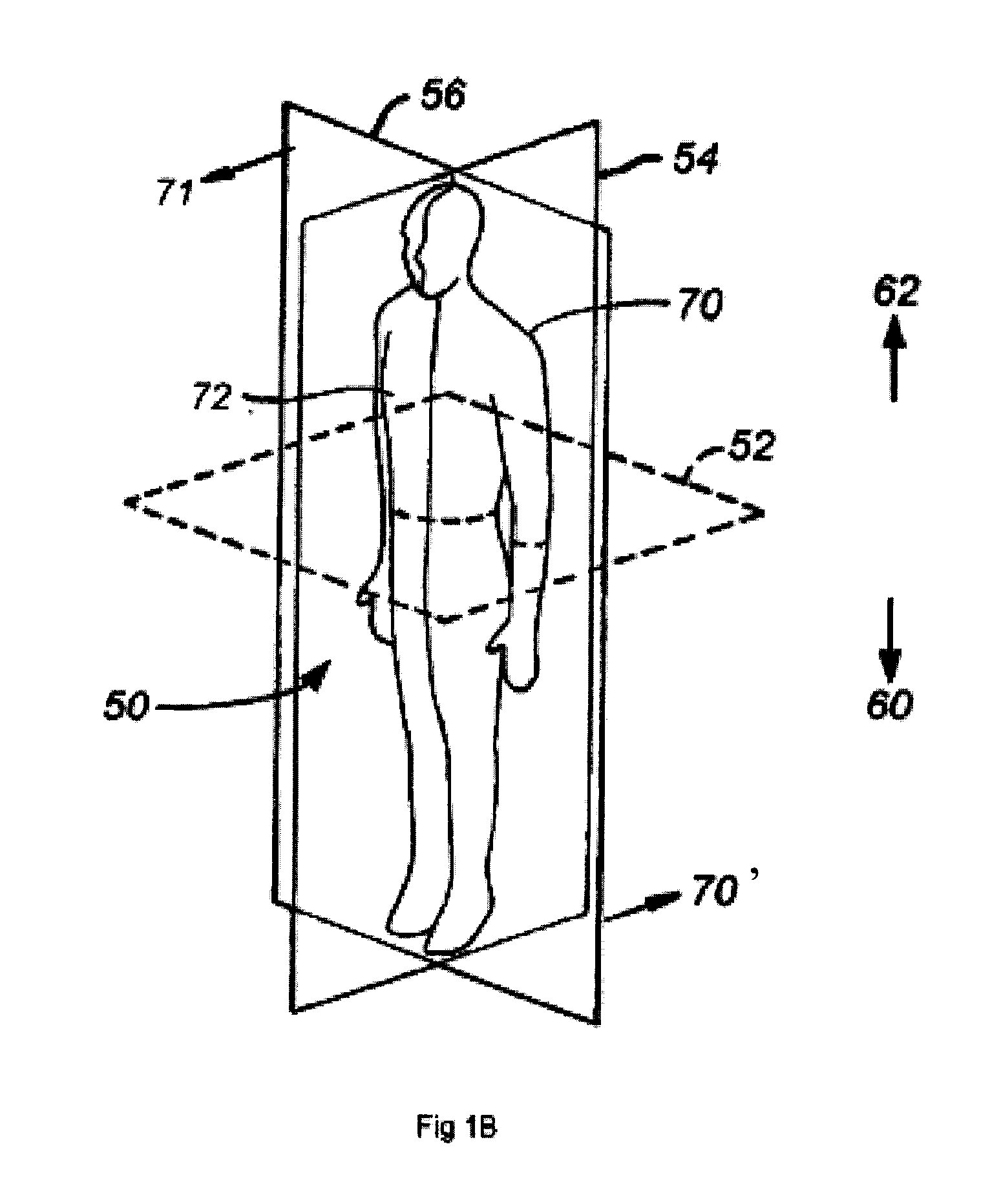
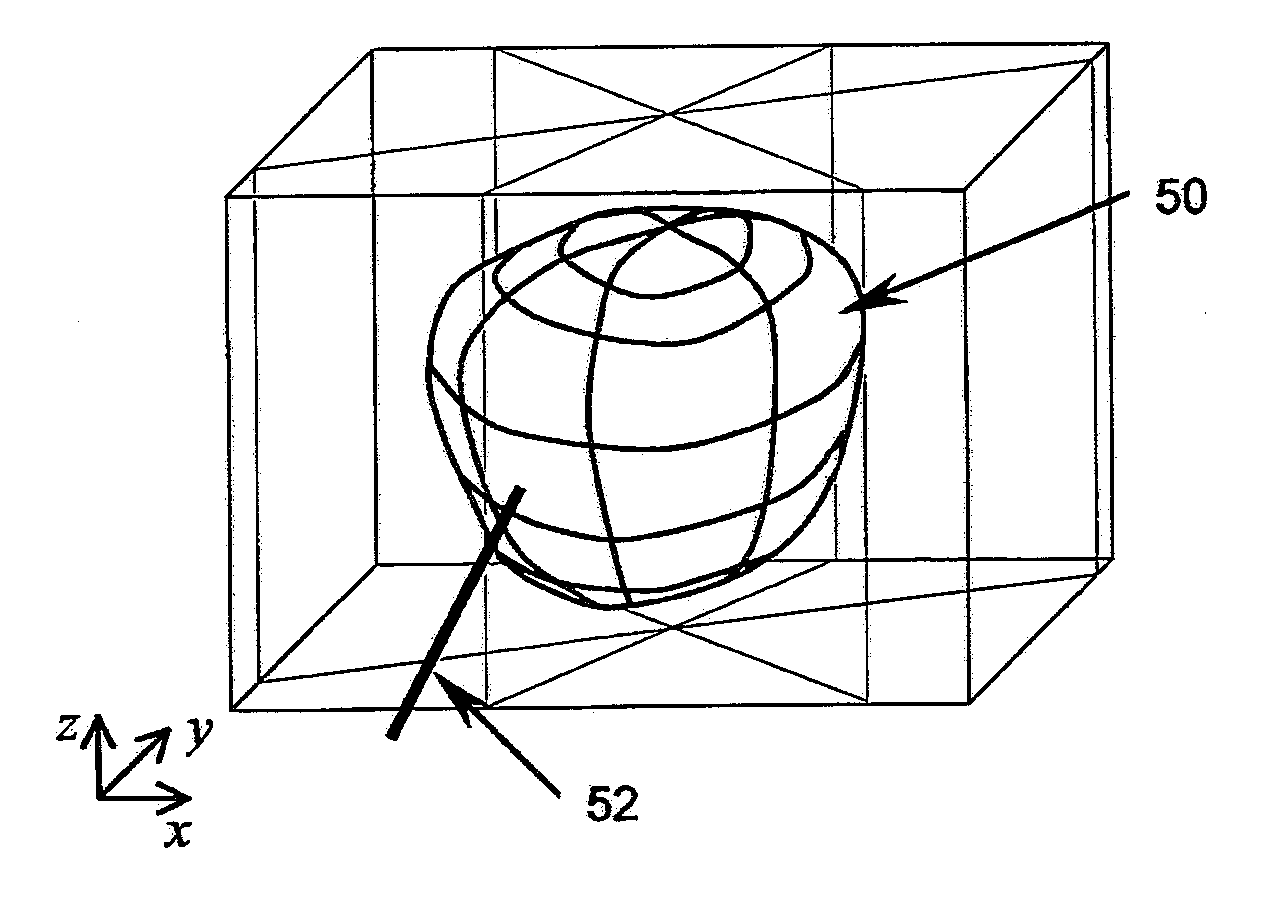
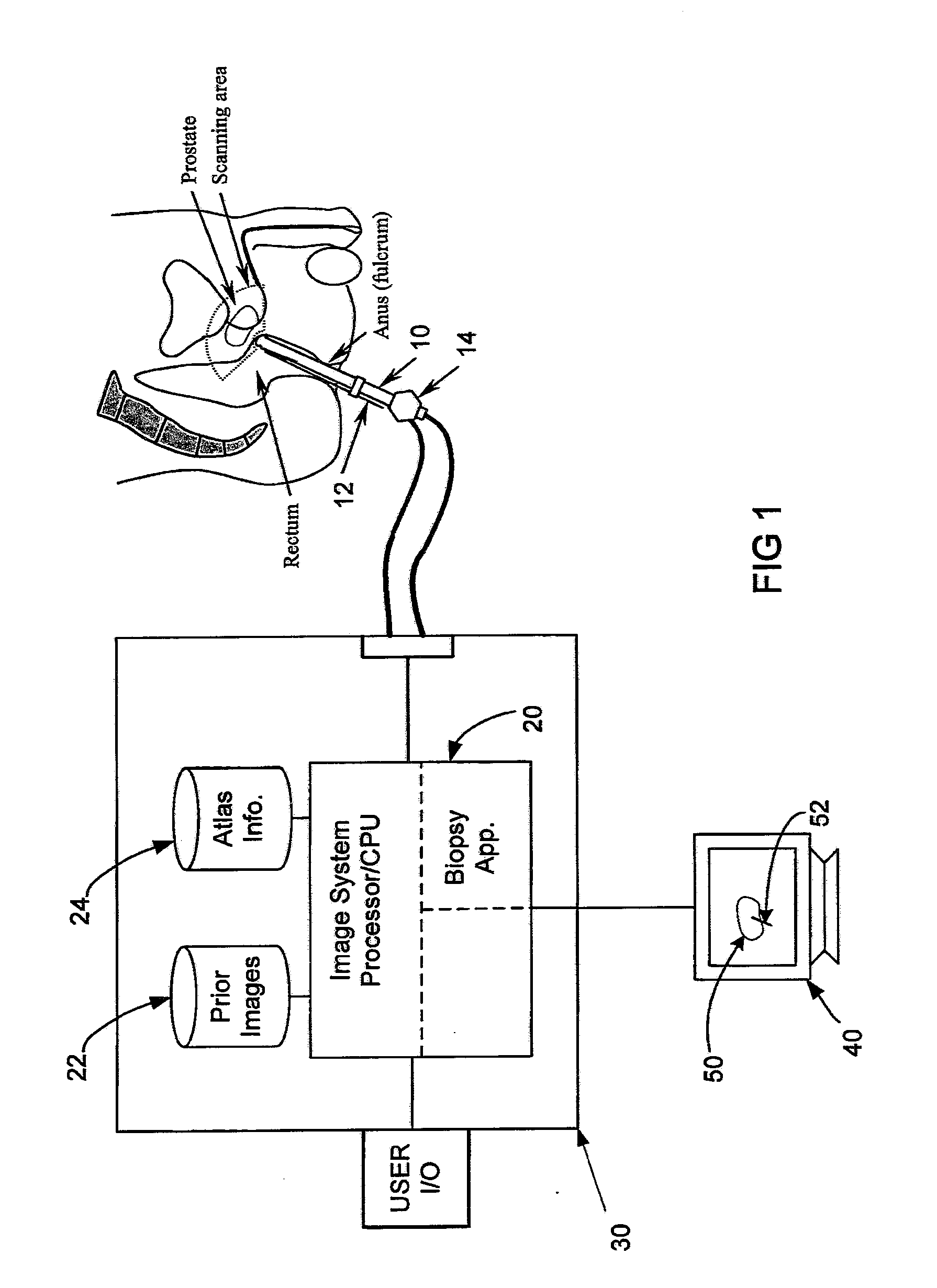
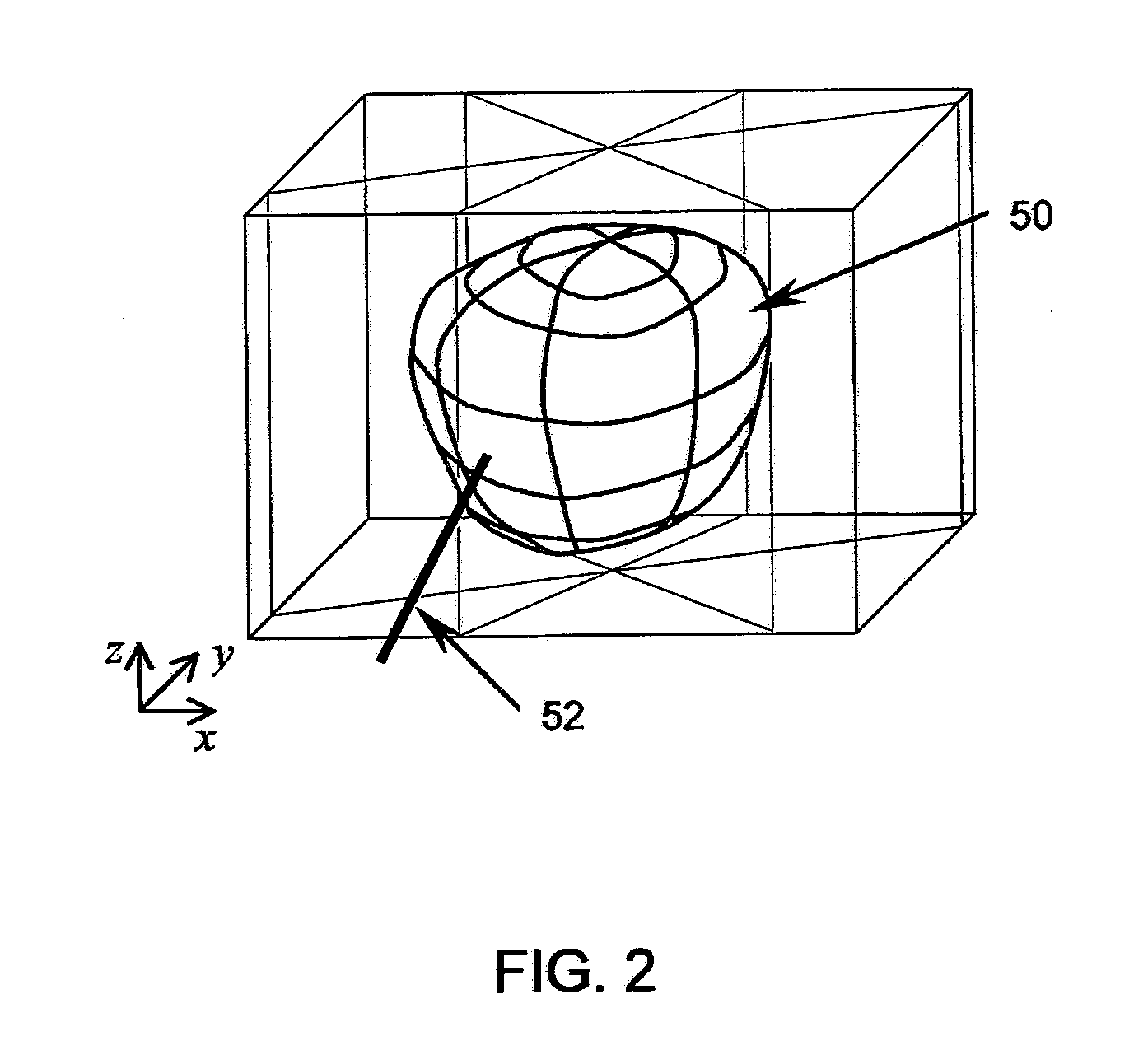
System and method for prostate biopsy
InactiveUS20100172559A1Easy to planEasy to explainImage enhancementImage analysisInsertion depthTransducer
The invention presents tools to improve a 3-D image aided biopsy or treatment procedure for prostate gland by providing additional functionality and additional visual cues on an output image of the prostate, which may be generated substantially in real-time. The tools include i) the identification of various parts of prostate to classify as per regular classification in pathological reports, ii) Computing and displaying the insertion depth of needle with respect to a selected target point during the procedure, iii) Computing and displaying the distance from needle tip to prostate surface following a procedure and, iv) Calibration for misalignment of a 2-D imaging transducer when used under tracked motion for a procedure.
Owner:EIGEN INC
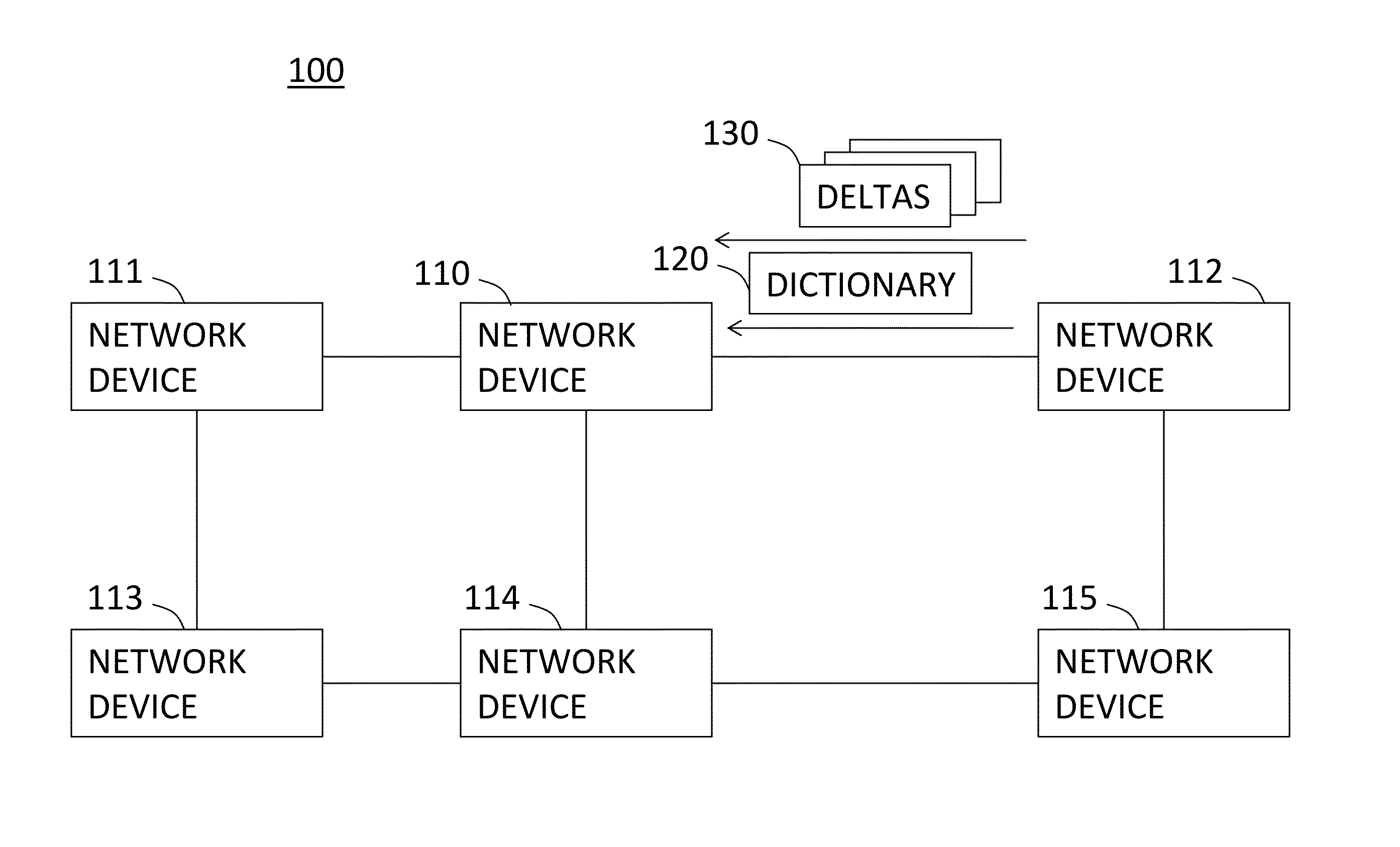
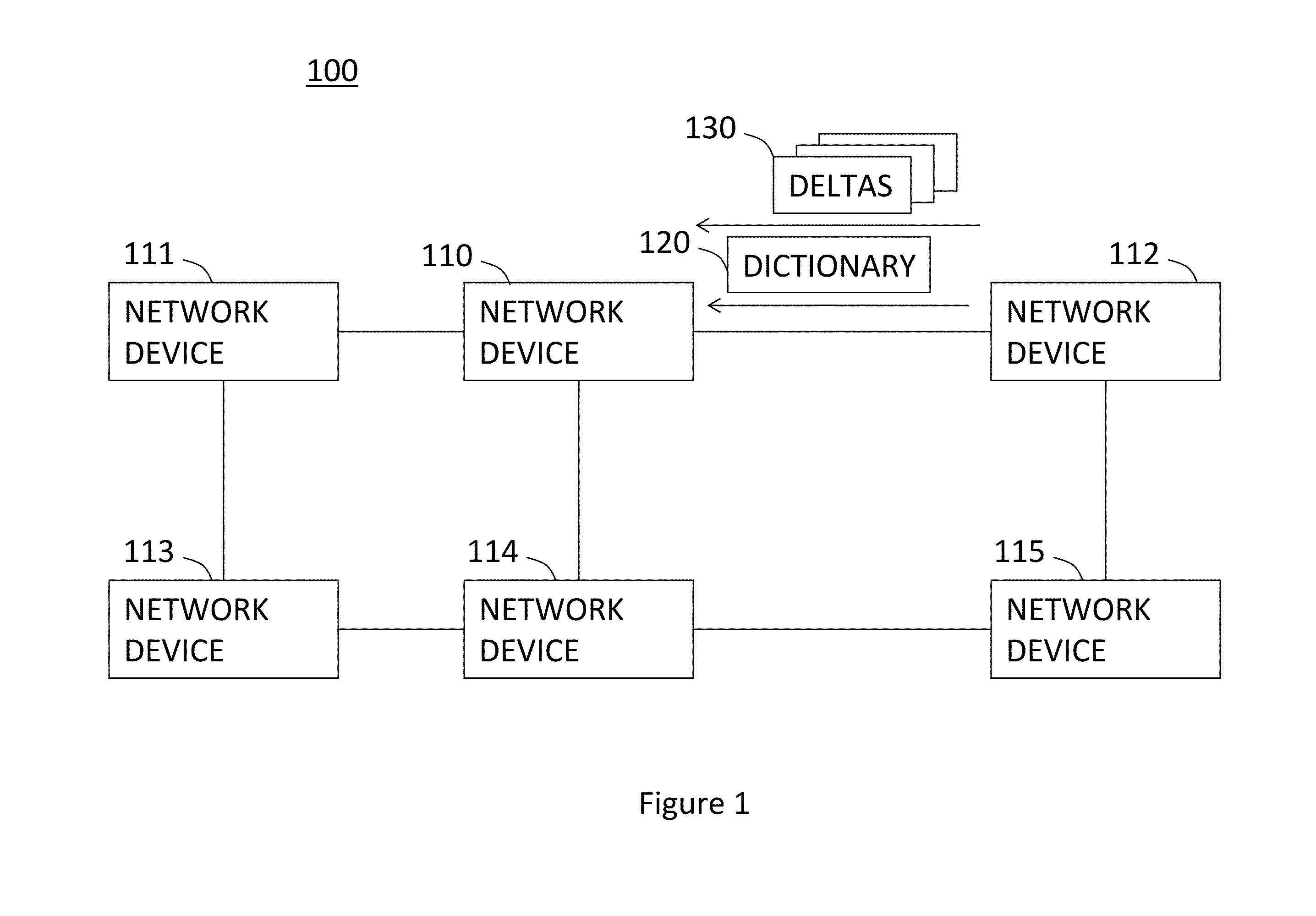
Method and system for decompression-free inspection of shared dictionary compressed traffic over HTTP
ActiveUS20130254197A1Facilitate scanningImprove performanceWeb data retrievalDigital data processing detailsTraffic volumeTraffic capacity
A system and a method for decompression-free inspection of compressed data are provided herein. The method includes the following stages: obtaining a dictionary file comprising a string of symbols, each associated with a respective index; obtaining at least one delta file associated with said dictionary file, wherein said delta file comprises a sequence of instructions that include at least one copy instruction pointing to an index within said dictionary and a length of a copy substring to be copied; scanning said dictionary using a pattern matching algorithm associated with a plurality of patterns and implemented as a Deterministic Finite Automaton (DFA), to yield DFA execution data; scanning said at least one delta file, using said pattern matching algorithm, wherein said DFA execution data is used to skip at least part of the scanning of the copy substrings for at least one of the copy instructions.
Owner:YISSUM RES DEV CO OF THE HEBREW UNIV OF JERUSALEM LTD +2
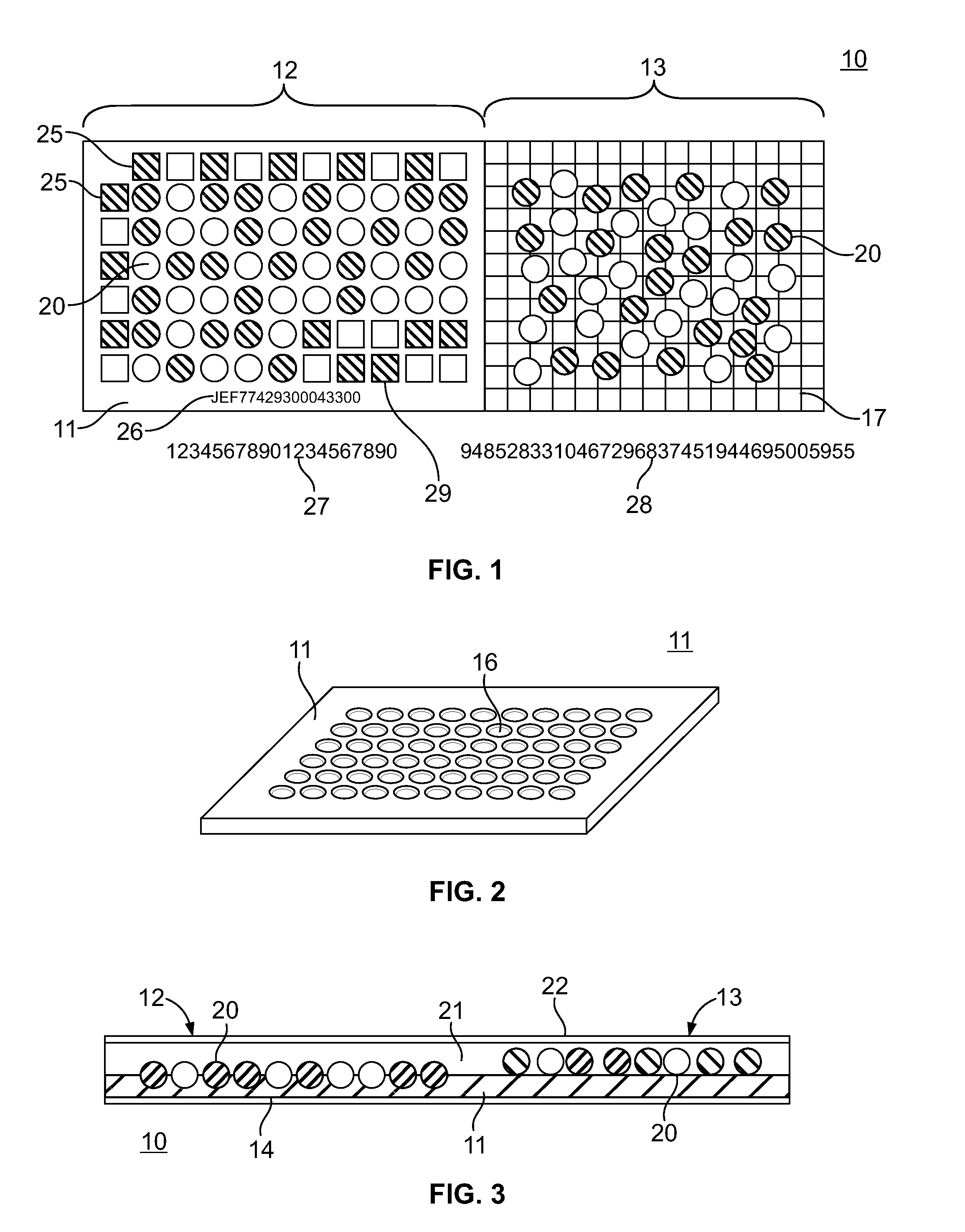
Optically Readable Identification Security Tag or Stamp
InactiveUS20130306737A1Low costSuitable for applicationLiquid surface applicatorsElectrography/magnetographyGlass ballArray data structure
The invention relates to a security tag made unique by randomly distributing a mixture of large numbers of multicolored small objects, such as two colored glass balls, into a regular geometric array or pattern onto a substrate and encapsulating those objects. The objects in the regular array on the substrate will create a unique, non-reproducible pattern. The data, saved to a secure database, can be processed and calculated quantities can be derived from the field of binary data, which can be affixed to the document or manufactured part that the stamp is affixed to. The regular array can be read out by scanner, quantities calculated, and compared to the values printed on the part or document. Additionally, the regular array can be read out by optical scanner and parts or all of the data compared to the data stored in the secure database.
Owner:FREEMAN JAMES
Laser power regulating method based on model features
InactiveCN107599382ASmall amount of calculationEasy to operateAdditive manufacturing apparatus3D object support structuresClassical mechanicsLaser additive manufacturing
The invention belongs to the technical field of laser material additive manufacturing, and particularly relates to a laser power regulating method based on model features. The laser power regulating method comprises the following steps that a special region with a complex structure in a model is obtained, slicing processing is conducted on the workpiece model, and preprocessing is conducted on thesplice contour of a special region in the contour data of each layer, the laser power of the point needed to be adjusted is calculated point-by-point; and the slice contour of a non-special region ineach layer contour data is filled in a conventional filling mode; and the process is repeated until layer processing of all slices of the workpiece model is finished, and finally the laser printing path data of the workpiece model is generated. According to the laser power regulating method based on the model features, the heat accumulation effect generated by excessively intensive scanning and printing of in the local region of the laser is utilized, and the laser power of the progressive contour ring filling path in the region is adjusted dynamically, so that adverse effects caused by the heat accumulation effect is avoided, and the fact that the temperature of a material molten pool is stable in the melting temperature range of powder materials all the time is guaranteed.
Owner:HUAZHONG UNIV OF SCI & TECH
Dental imager and method for recording photographic impressions
ActiveUS20170215997A1Improve image qualityReduce errorsMusculoskeletal system evaluationImpression capsEngineering3d printer
A dental imager includes an elongated handle with a rotatable head coupled to a distal end thereof and having a central platform with a plurality of arcuate scanning arms pivotally coupled thereto by a hinge. The arcuate scanning arms are of a shape and size for general deployment around a tooth and each include at least one scanner and a roller guide that comfortably rolls along the surface of the tooth or gums to bias the scanners a desired distance from the surface of the tooth, conducive for imaging thereof. In this respect, such a dental imager may be used in a process to scan and record the contours of an intraoral surface, the data of which may be used to create a digital three-dimensional surface impression printable by a 3D printer or the like.
Owner:MARTIN MARCO
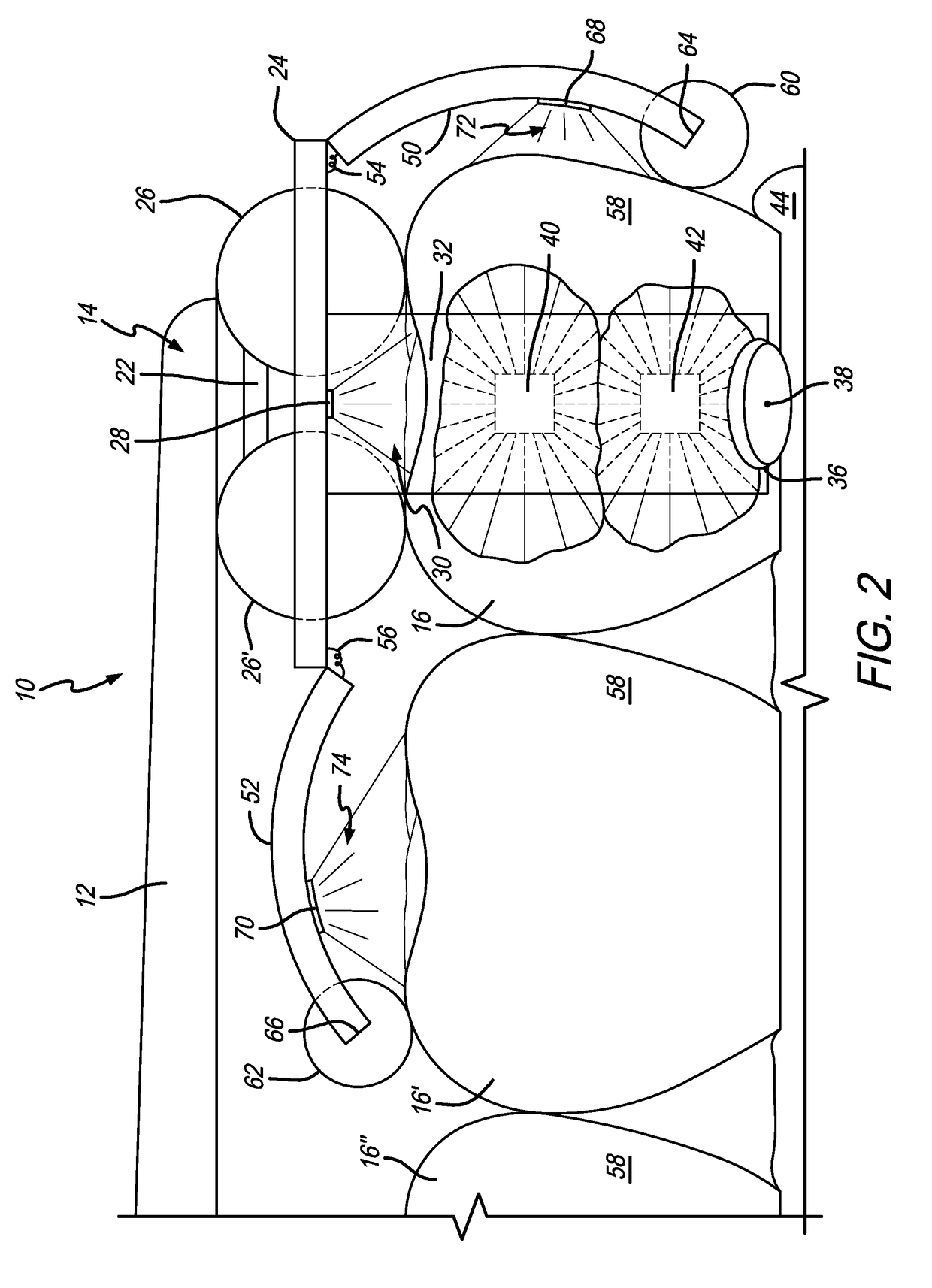
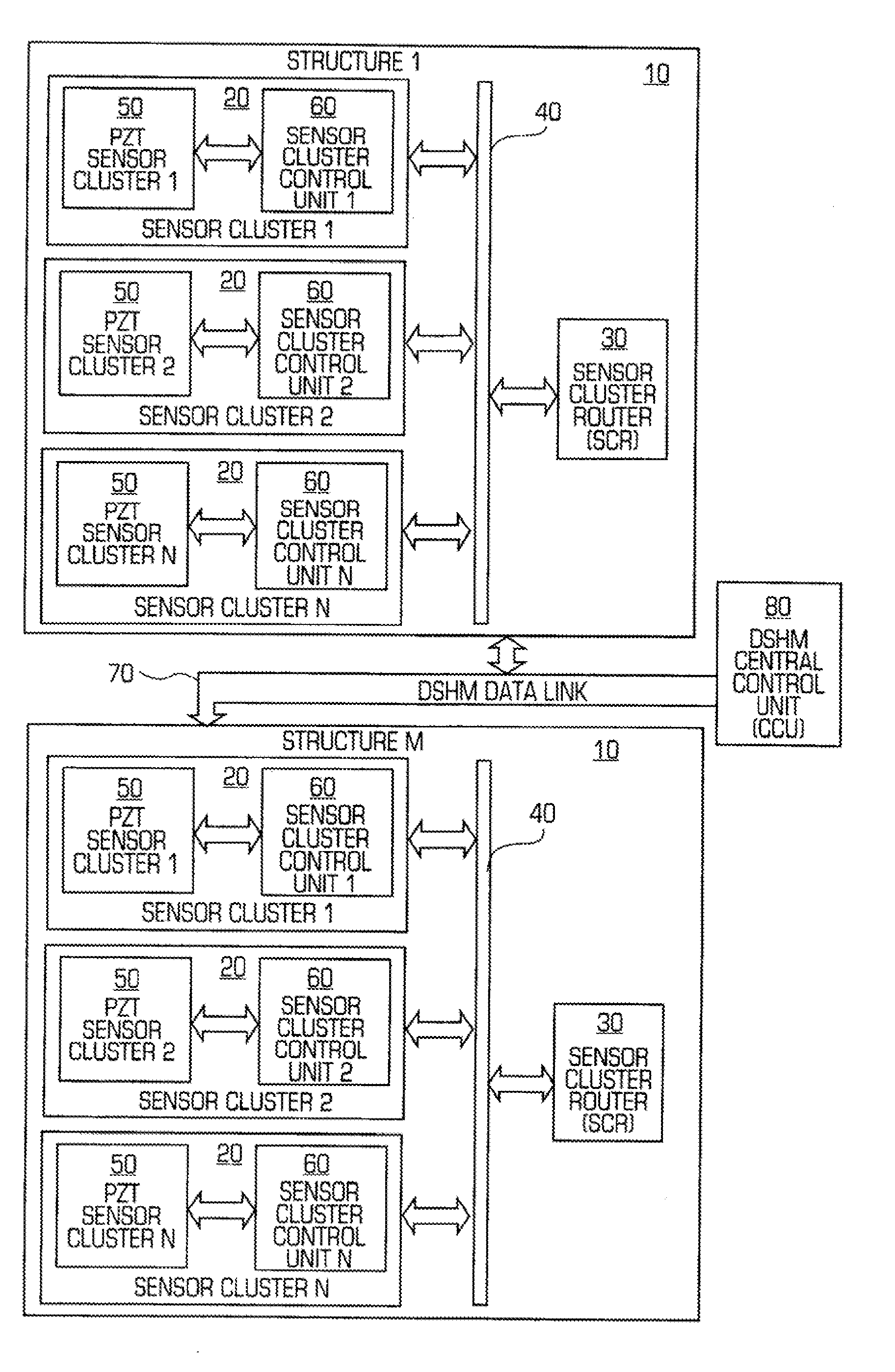
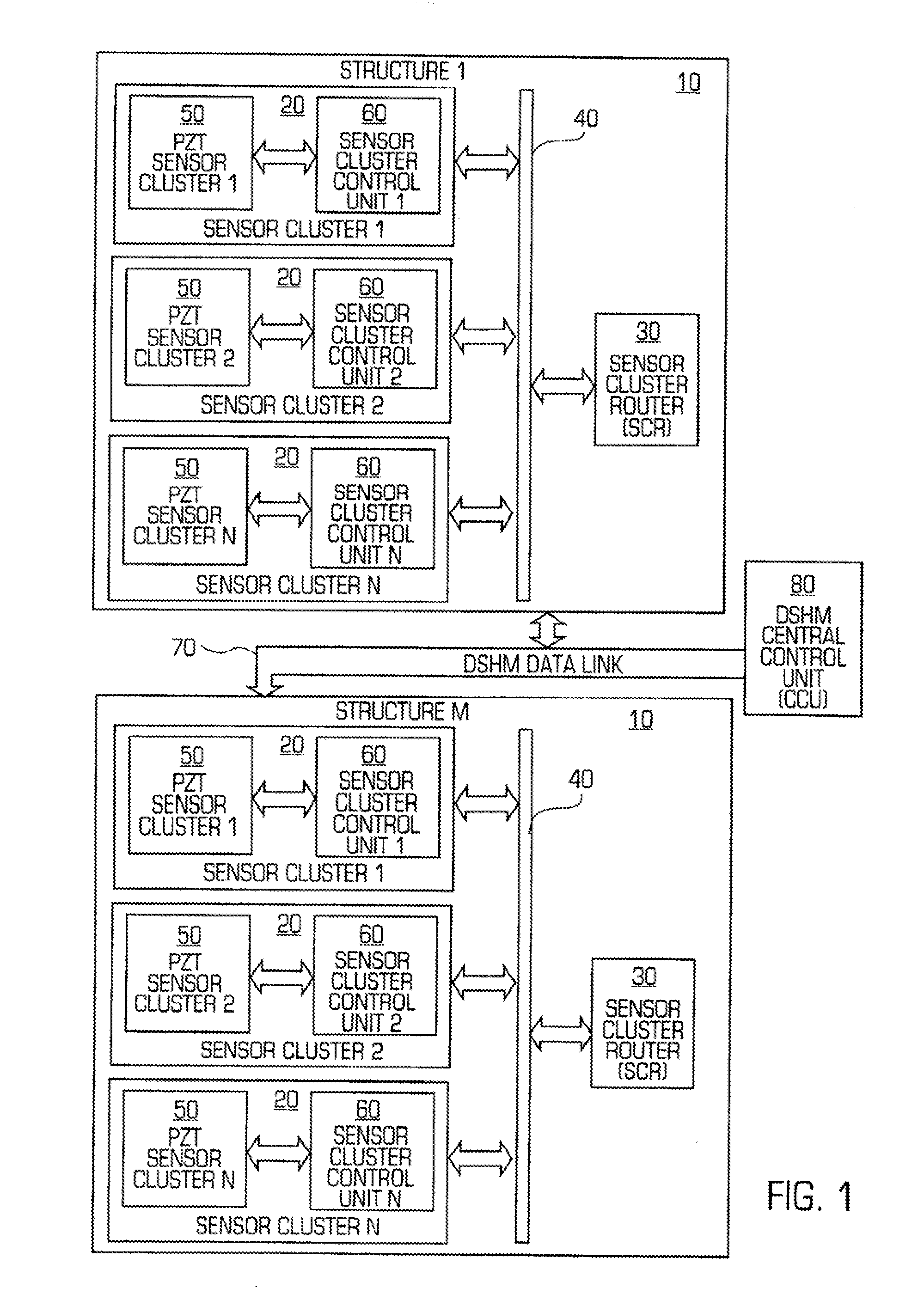
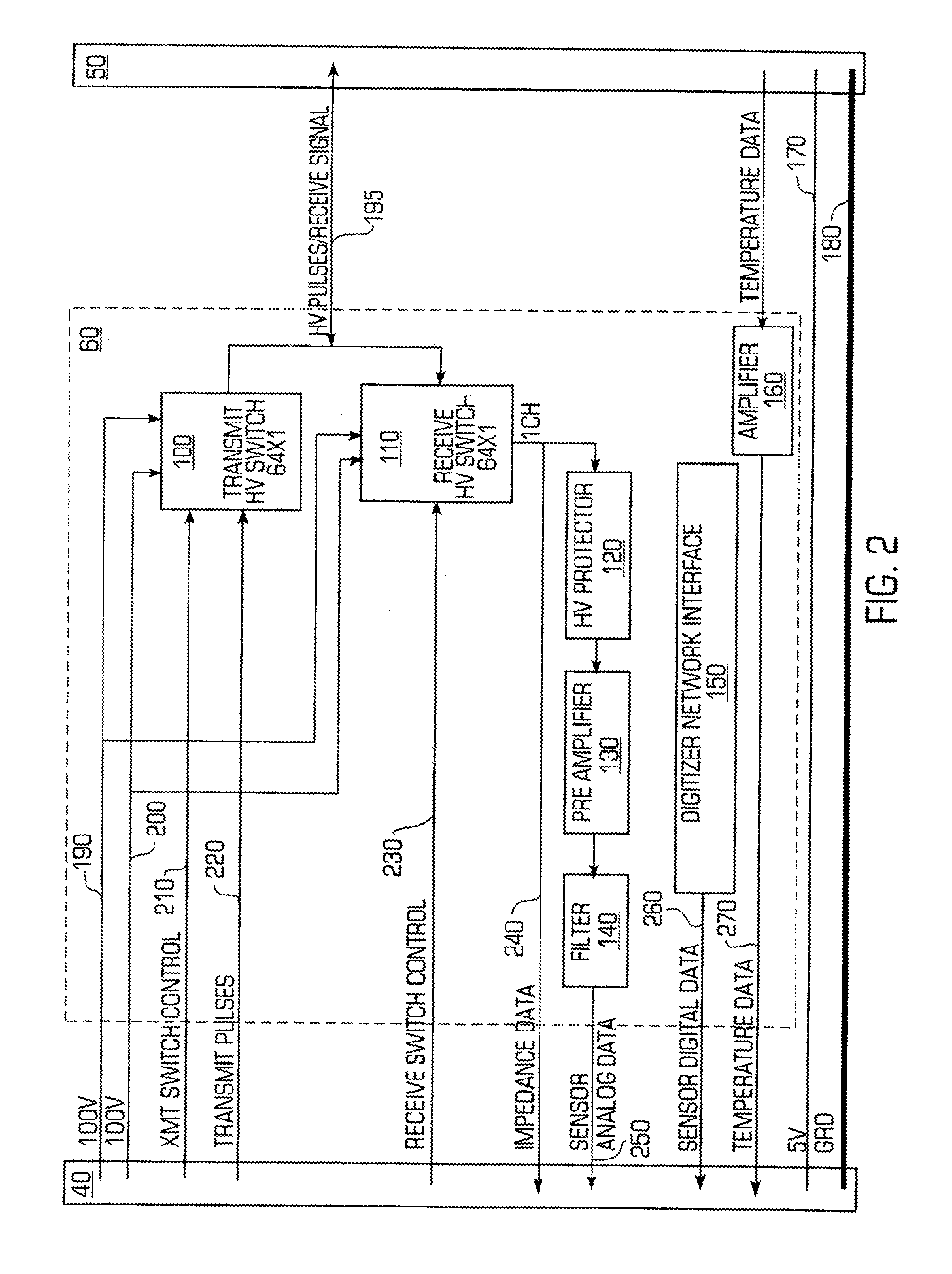
Structural health monitoring network
InactiveUS20100161283A1Easy to controlEasy to scanMaterial analysis using sonic/ultrasonic/infrasonic wavesError detection/correctionStructural health monitoringMultiple sensor
A networked configuration of structural health monitoring elements. Monitoring elements such as sensors and actuators are configured as a network, with groups of monitoring elements each controlled by a local controller, or cluster controller. A data bus interconnects each cluster controller with a router, forming a networked group of “monitoring clusters” connected to a router. In some embodiments, the router identifies particular clusters, and sends commands to the appropriate cluster controllers, instructing them to carry out the appropriate monitoring operations. In turn, the cluster controllers identify certain ones of their monitoring elements, and direct them to monitor the structure as necessary. Data returned from the monitoring elements is sent to the cluster controllers, which then pass the information to the router. Other embodiments employ multiple sensor groups directly connected to a central controller, perhaps with distributed local control elements. Methods of operation are also disclosed.
Owner:ACELLENT TECH
Community access control method and community access control system
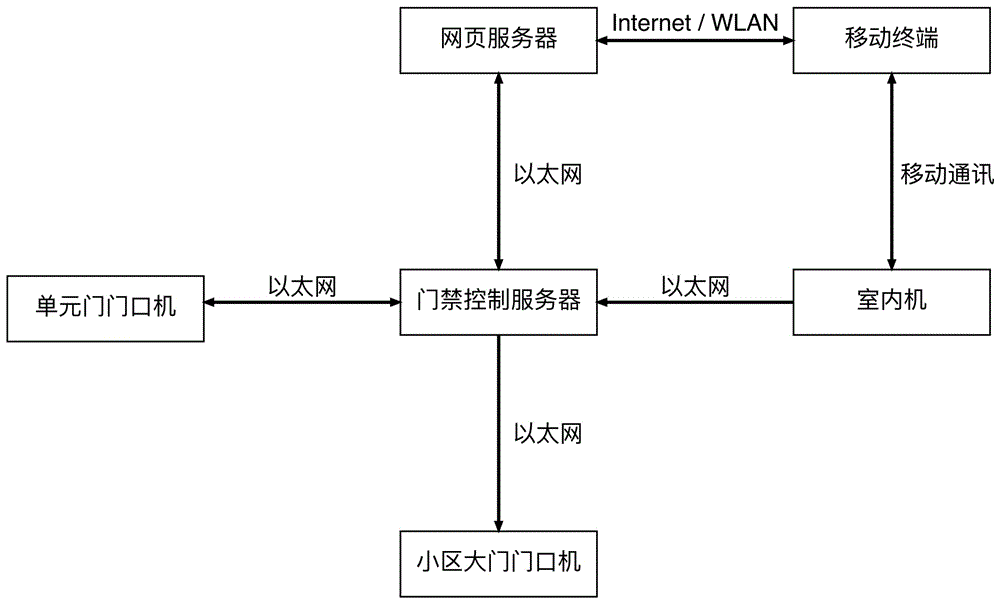
ActiveCN106340103AAvoid the trouble of downloading APPAvoid troubleIndividual entry/exit registersControl systemComputer terminal
The invention discloses a community access control method and a community access control system. The community access control method comprises the steps of scanning a two-dimensional code arranged at a community gate with a mobile terminal to open a webpage to fill resident address information and obtain a telephone number fed back from a webpage server, dialing the telephone number to connect to a resident indoor unit, allowing the indoor unit to inform an access control server to open a door, allowing the access control server to indicate to open the community gate, transmitting opening key information of a unit gate to the webpage server, allowing the webpage server to transmit the key information to a visitor, and allowing the visitor with the key to open the unit gate after checking by the access control server. The control system comprises the mobile terminal, the webpage server, the access control server, the indoor unit, a community gate entrance machine and a unit gate entrance machine. According to the method and the system, the visitor initiates a single request, and the resident is only required to confirm for one time to achieve opening of community gate access and unit access without downloading an APP (application).
Owner:XIAMEN DNAKE INTELLIGENT TECH CO LTD
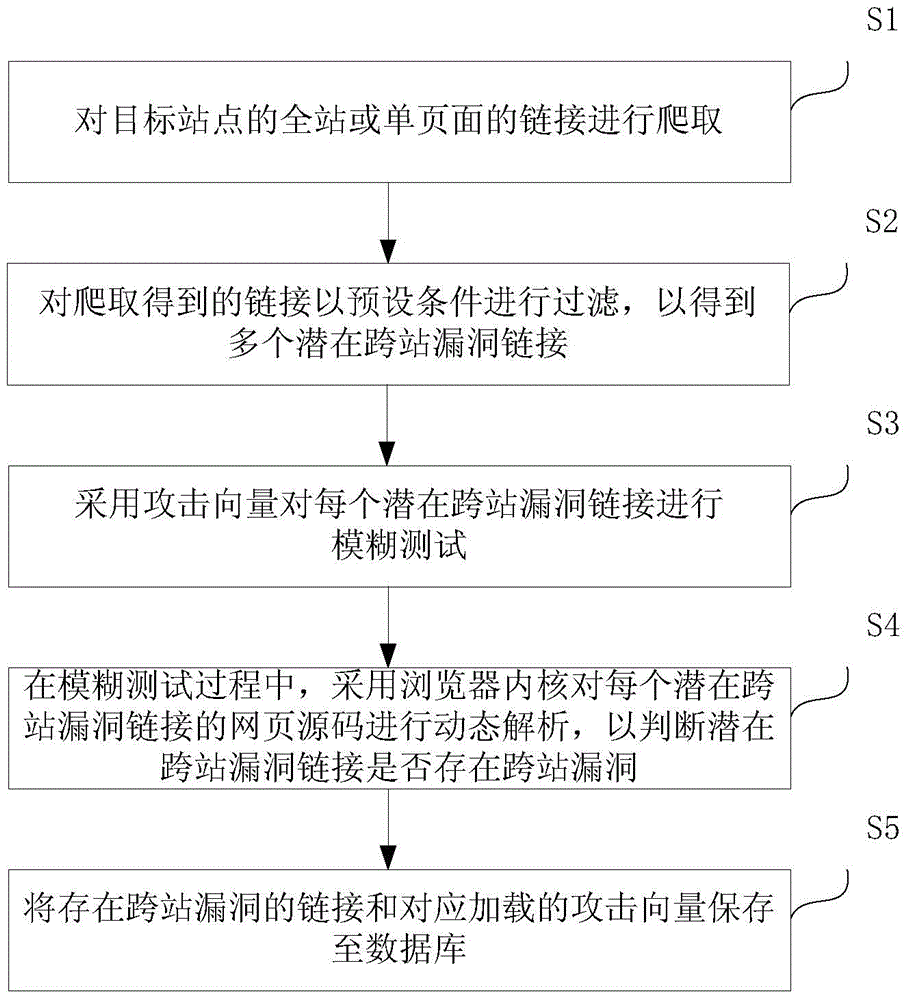
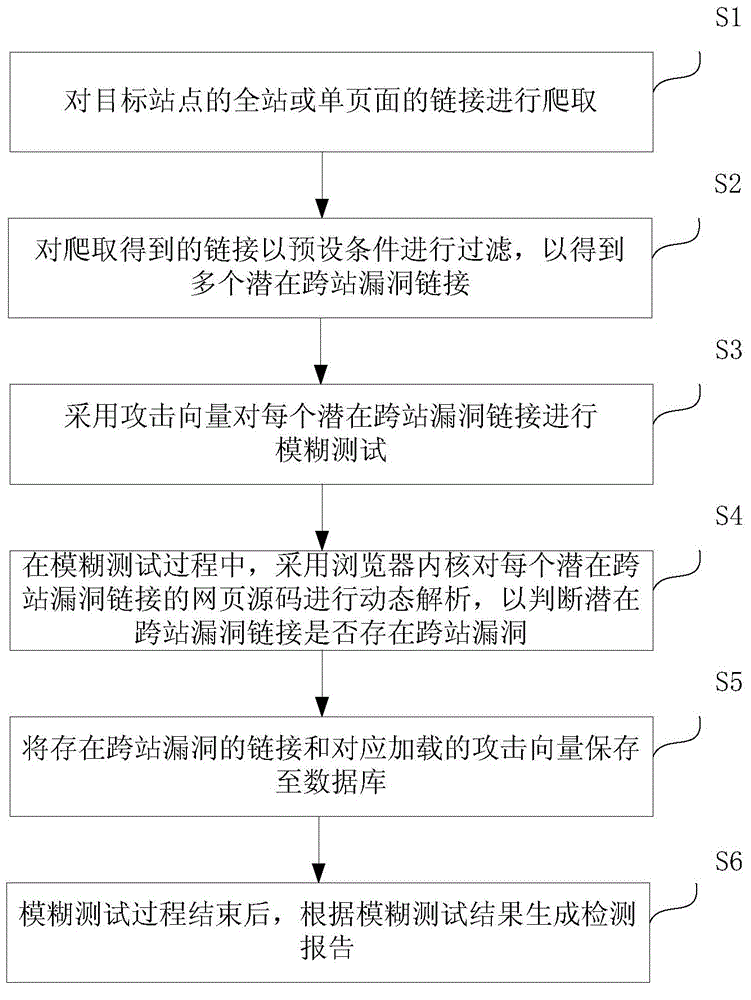
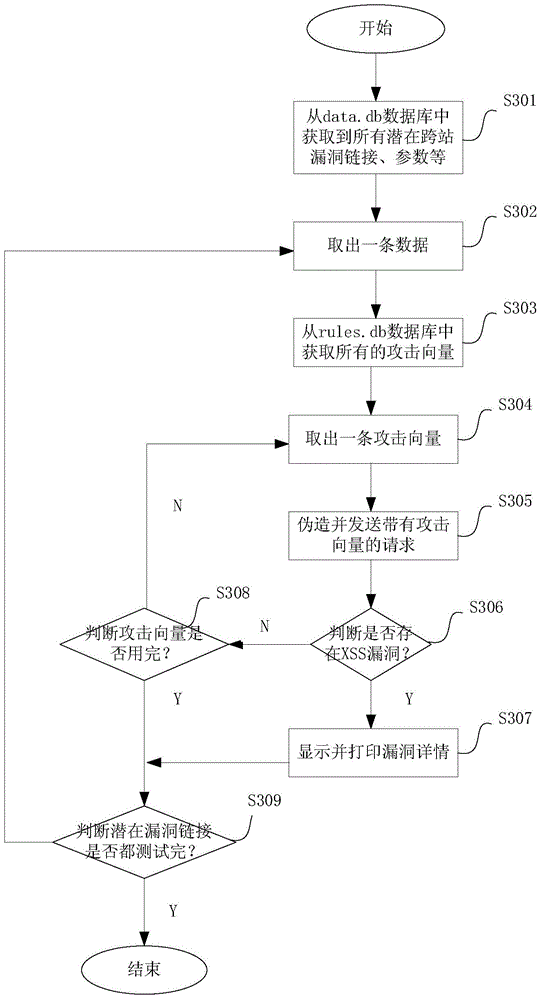
Method and system for scanning cross-site vulnerability
The invention provides a method and a system for scanning a cross-site vulnerability. The method comprises the following steps of crawling the links of the full site or the single page of a target site; filtering the links obtained by crawling according to a preset condition, so as to obtain a plurality of potential cross-site vulnerability links; carrying out a fuzzy test on each potential cross-site vulnerability link by adopting an attack vector; in the process of the fuzzy test, dynamically analyzing the webpage source code of each potential cross-site vulnerability link by adopting the inner core of a browser, so as to judge whether the potential cross-site vulnerability link has the cross-site vulnerability or not; storing the link having the cross-site vulnerability and the attack vector loaded correspondingly in a database. By using the method and the system for scanning the cross-site vulnerability, a method and a system, which are high in efficiency, low in false alarm rate and complete in scanning, for detecting the cross-site vulnerability can be provided.
Owner:XINGHUA YONGHENG BEIJING TECH CO LTD
Drink bottle label with two-dimension code
ActiveCN103268508AEasy to scanSmooth sweepstakesStampsUser identity/authority verificationBottleSales promotion
The invention discloses a drink bottle label with a two-dimension code. The right side of the drink bottle label with the two-dimension code is provided with a two-dimension code identification region composed of a background layer and a two-dimension code pattern layer. The background layer is transparent. After two ends of the label are connected to form a sealing sleeve, The back, located on the position opposite to the two-dimension code identification region, of the label is provided with a color piece coating which faces the two-dimension code identification region and is a contrast to the color of two-dimension code patterns. The area of the color piece coating is sufficient to ensure that the whole two-dimension code identification region is completely mapped on the color piece coating. The drink bottle label with the two-dimension code has the advantage that the two-dimension code can be scanned after a consumer has a drink, and therefore a role in sales promotion can be really played.
Owner:上海凌脉网络科技股份有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com