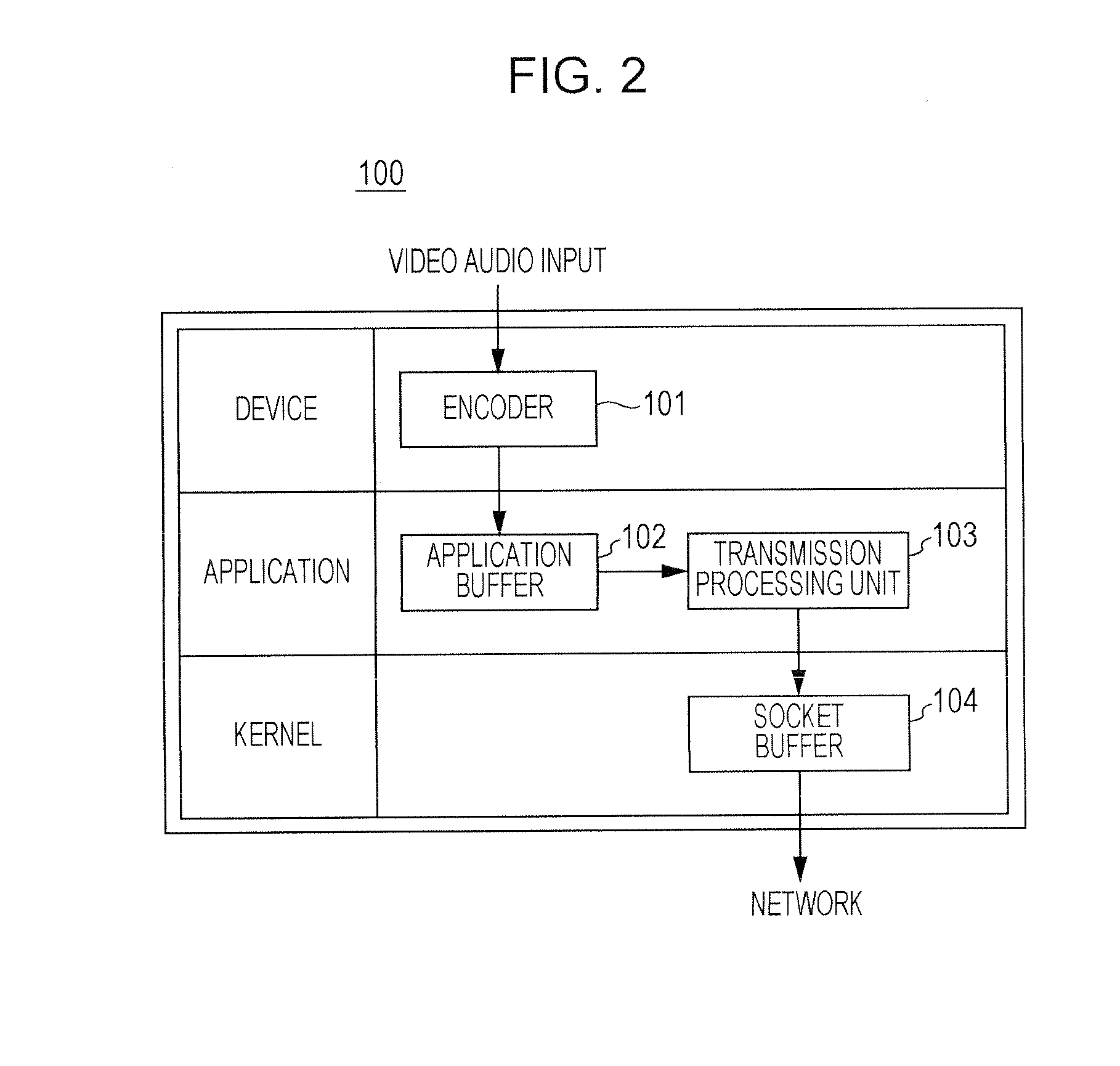
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
71 results about "Throughput degradation" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
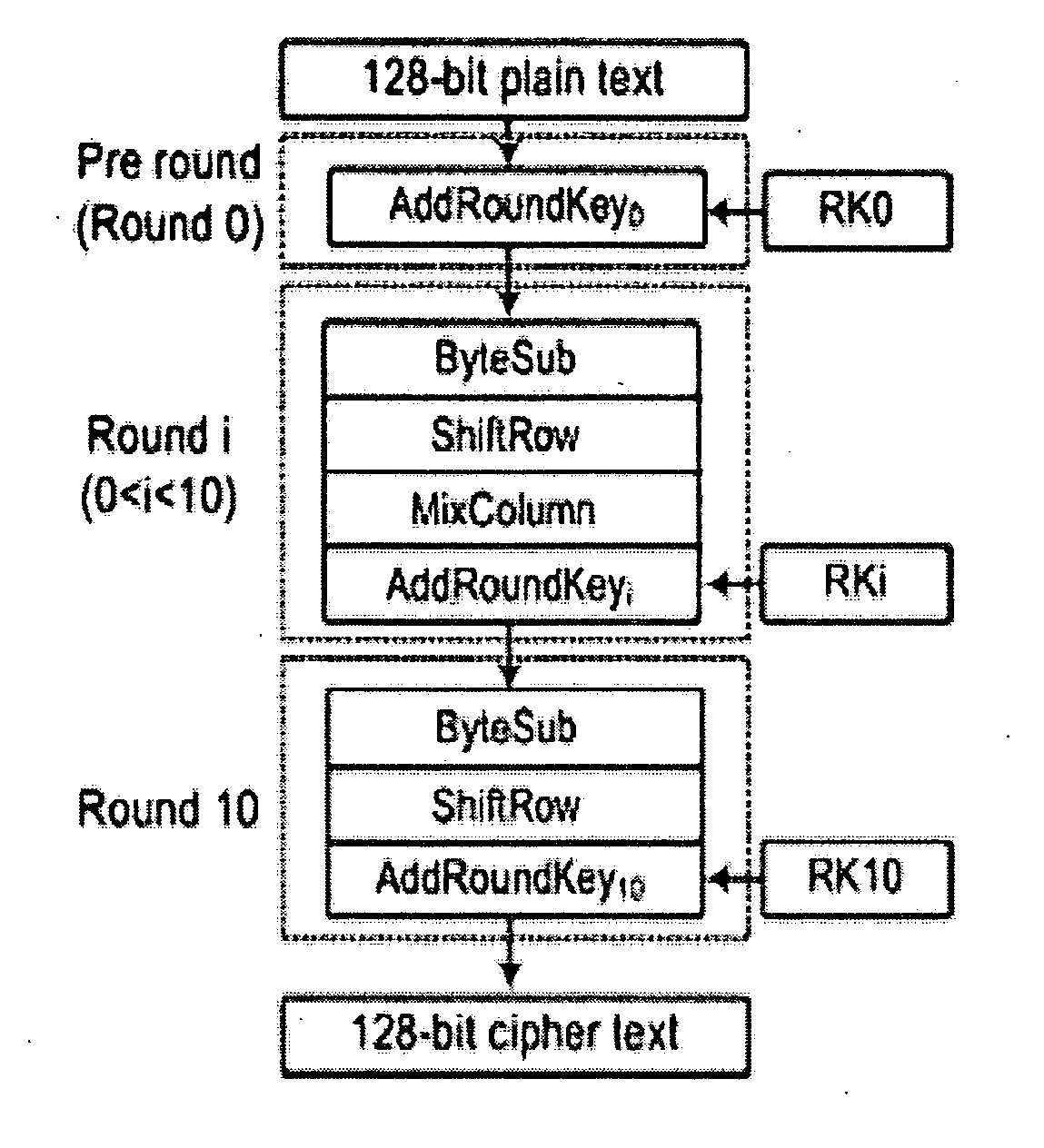
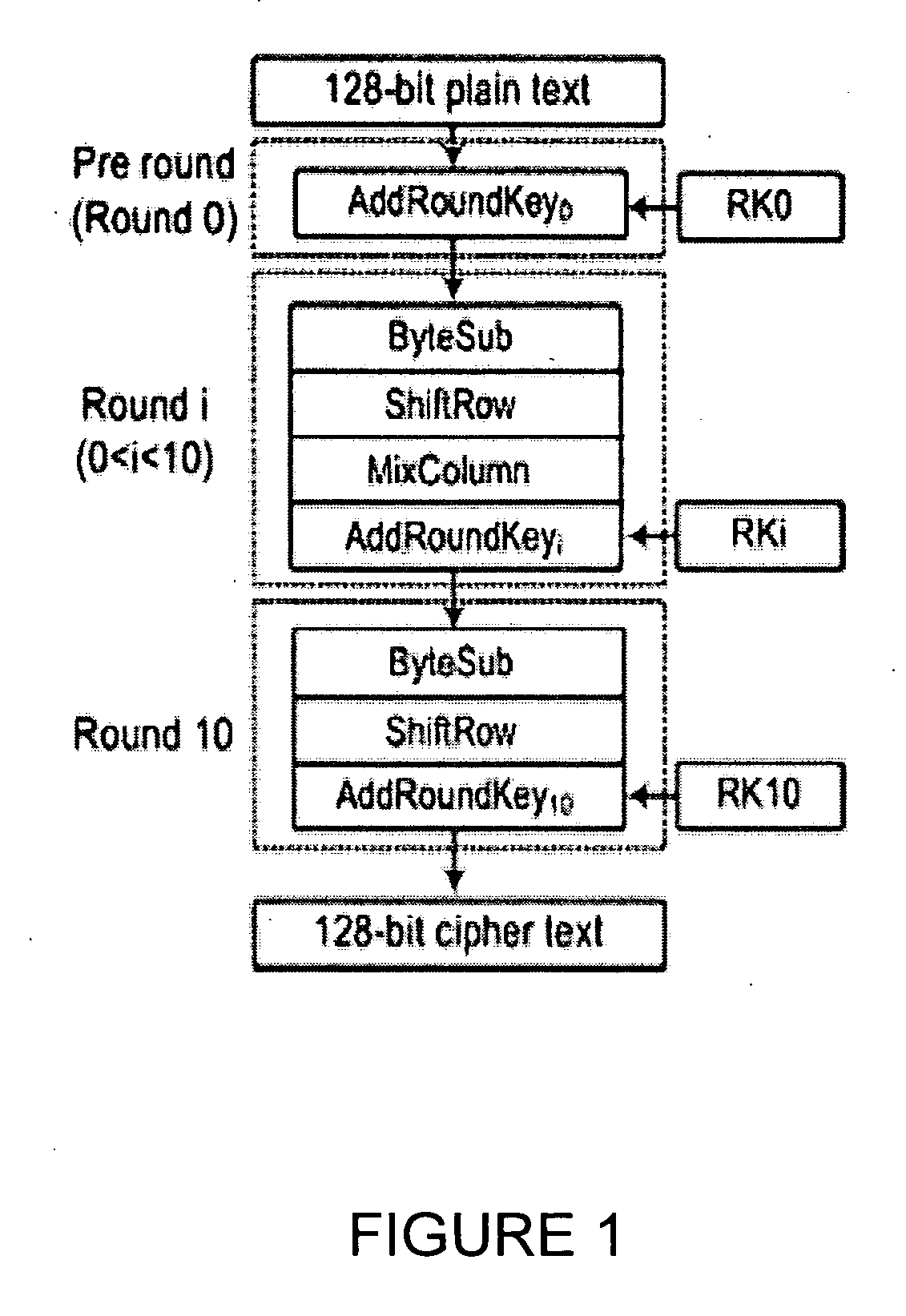
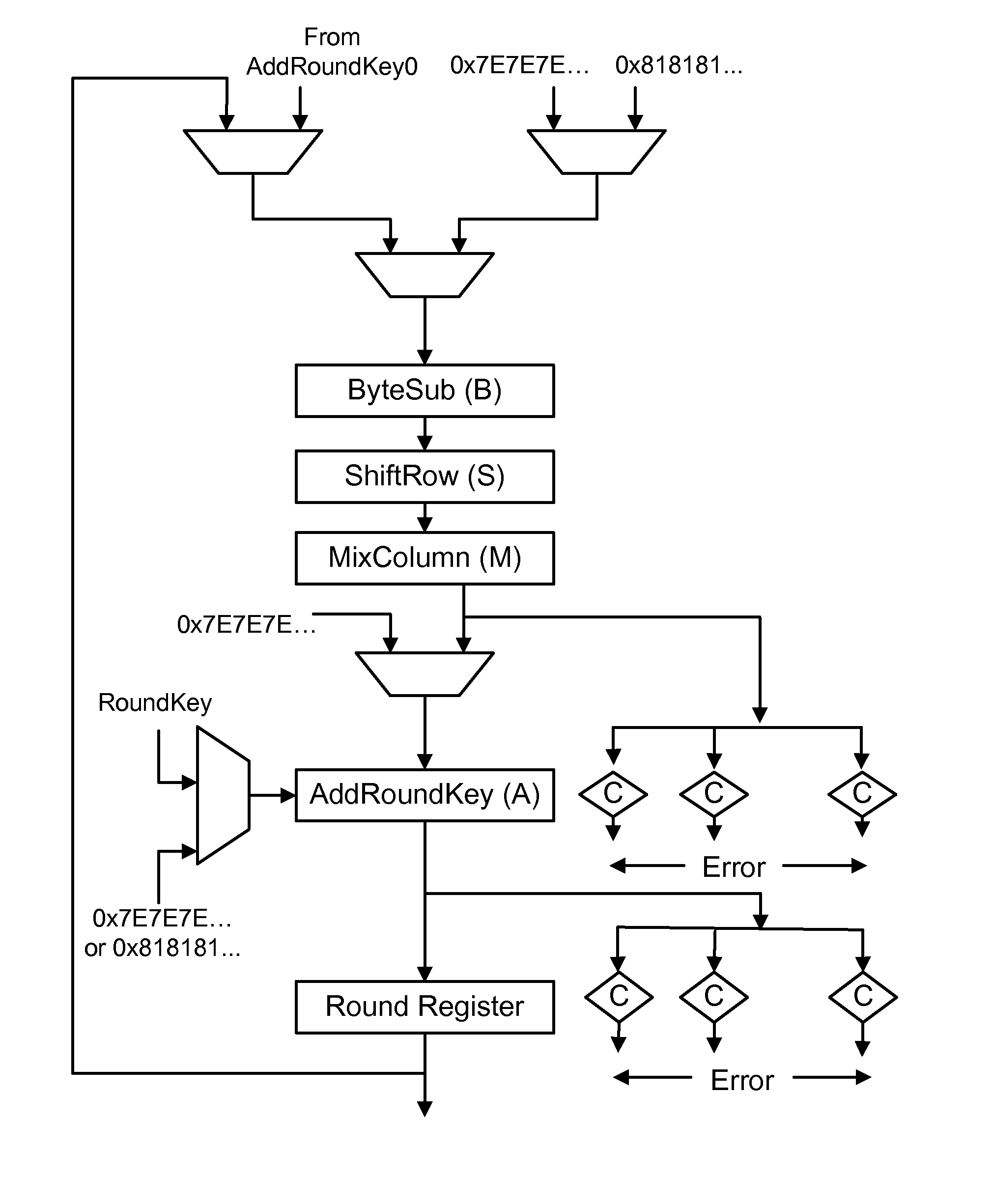
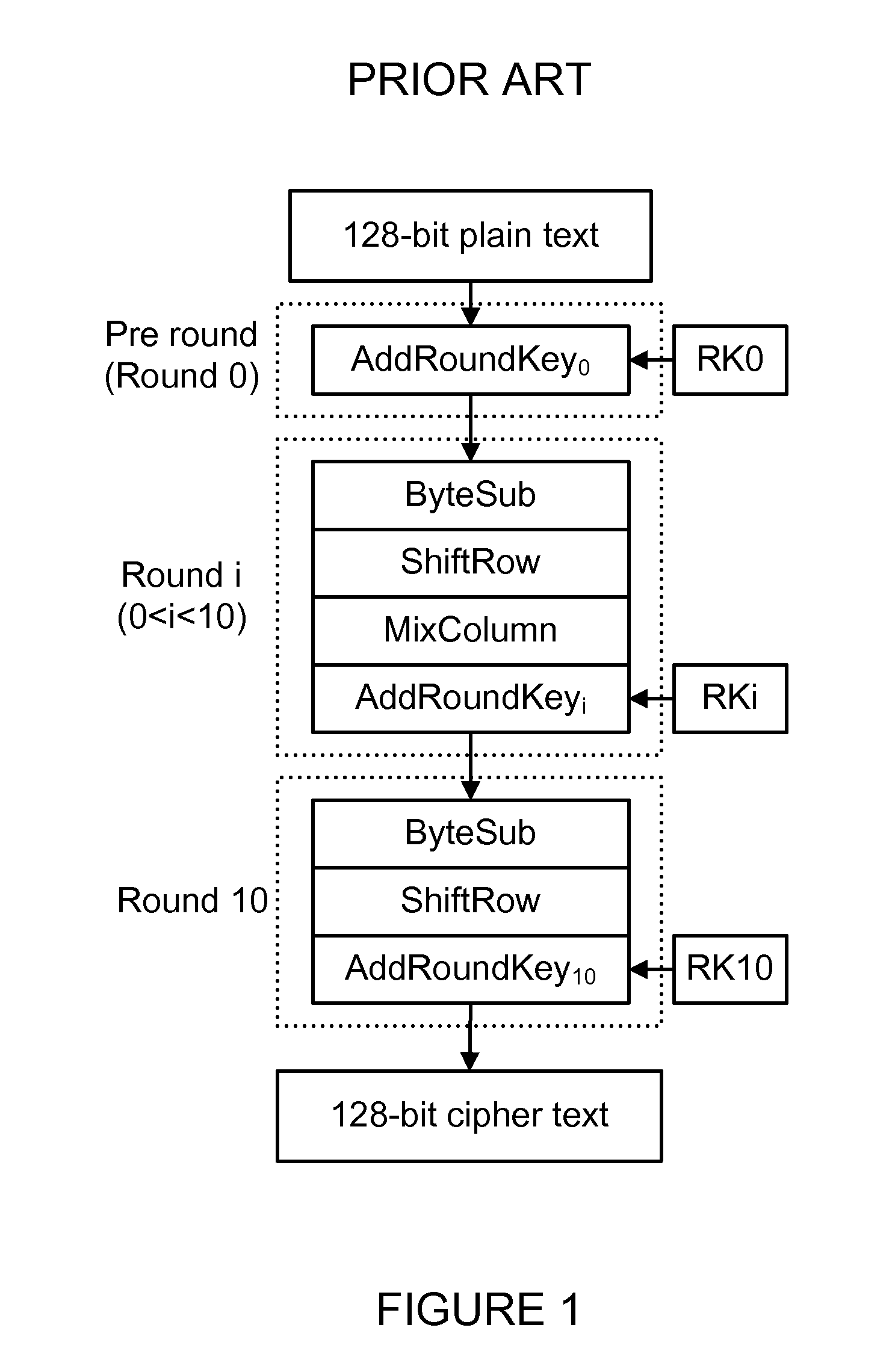
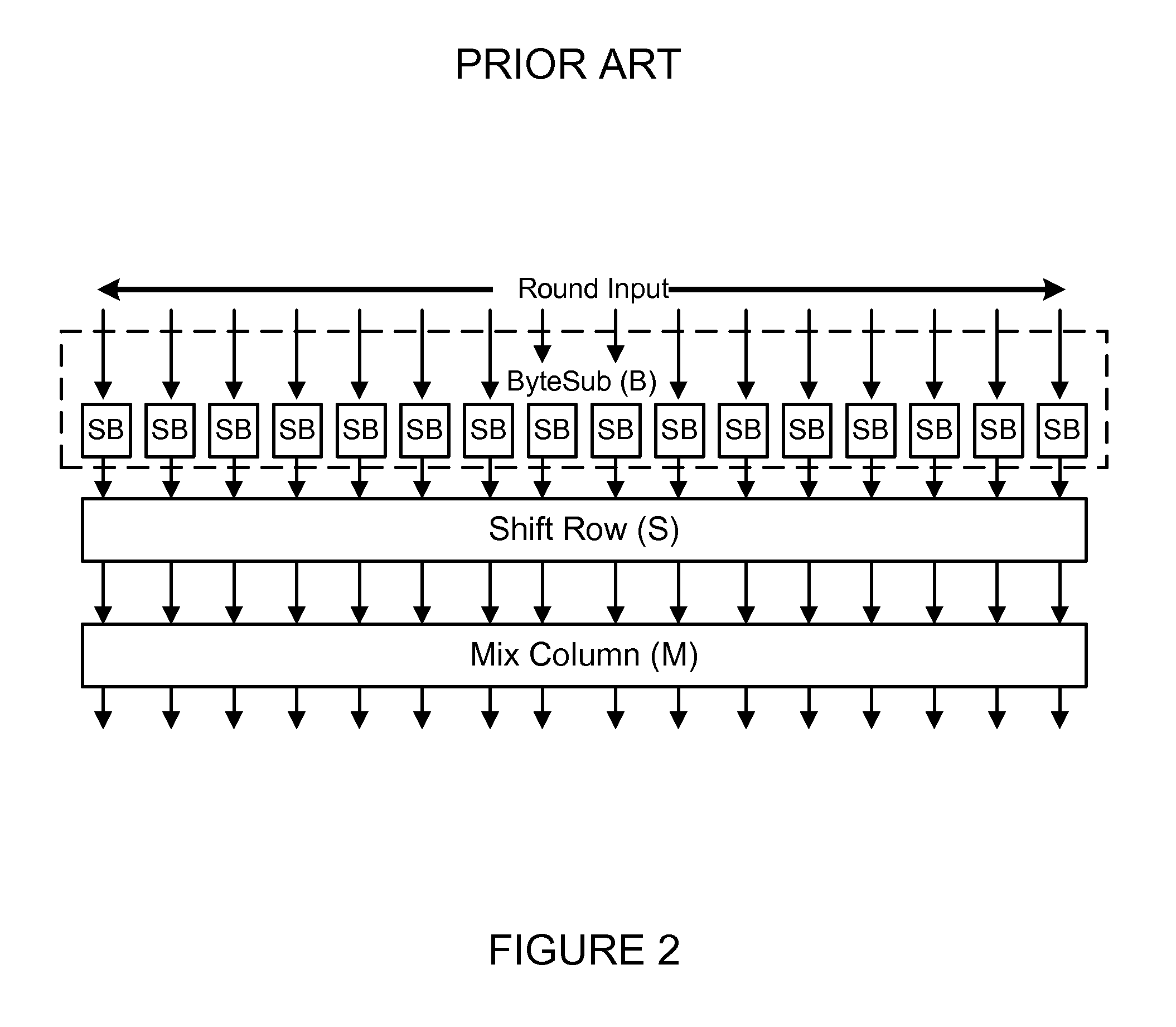
Invariance based concurrent error detection for the advanced encryption standard
ActiveUS20070014395A1Protection attackPublic key for secure communicationSecret communicationThroughput degradationAdvanced Encryption Standard
Advanced Encryption Standard (AES) is an encryption algorithm for securing sensitive unclassified material by U.S. Government agencies and, as a consequence the de facto encryption standard for commercial applications worldwide. Performing concurrent error detection (CED) for protection of such a widely deployed algorithm is an issue of paramount importance. We present a low-cost CED method for AES. In this method, we make use of invariance properties of AES to detect errors. For the first time, the invariance properties of the AES, which are for the most part used to attack the algorithm, are being used to protect it from fault attacks. Our preliminary ASIC synthesis of this architecture resulted in an area overhead of 13.8% and a throughput degradation of 16.67%.
Owner:POLYTECHNIC INST OF NEW YORK
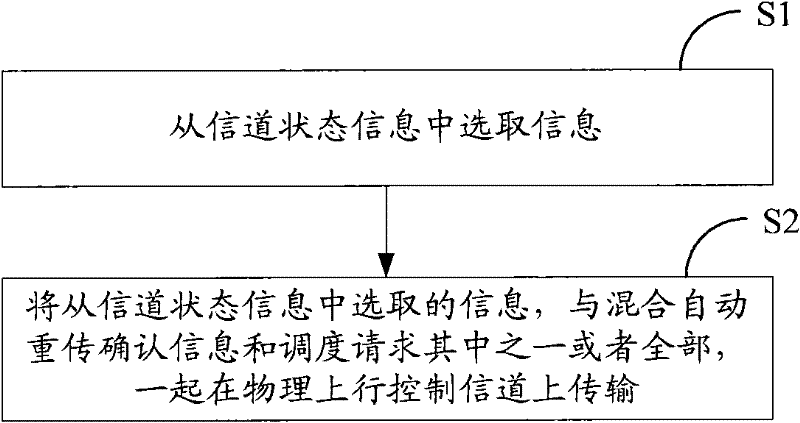
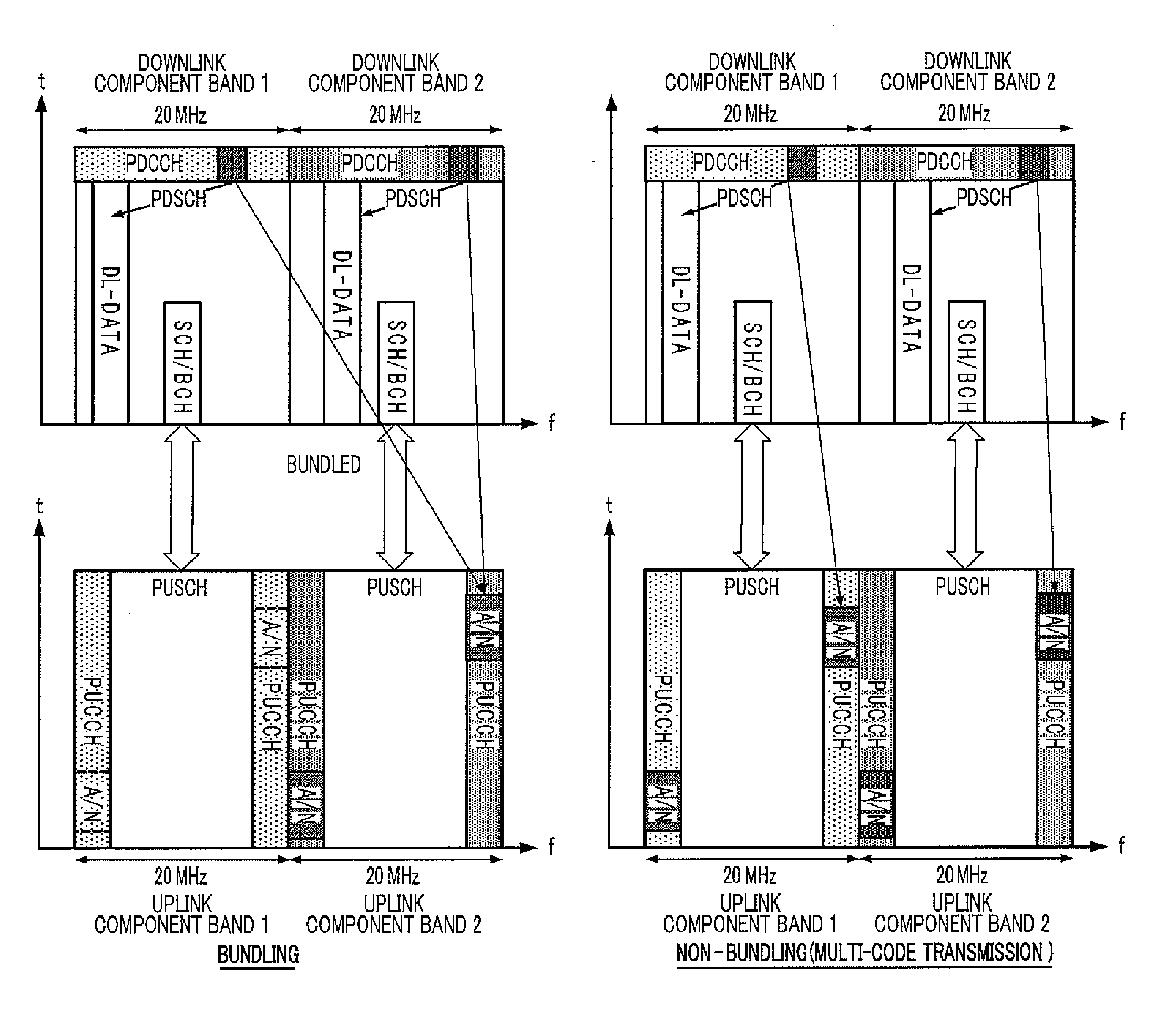
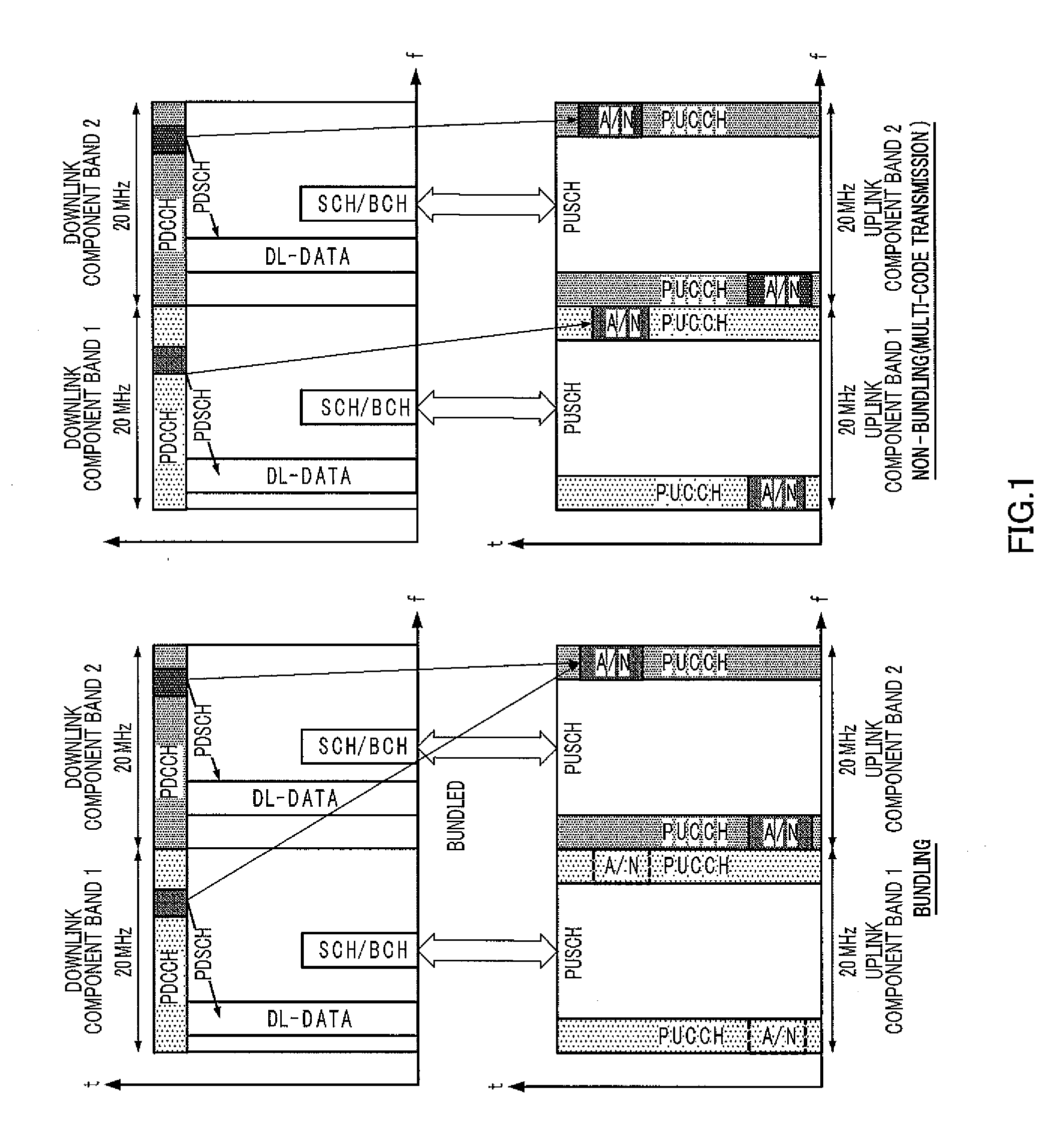
A method and device for transmitting information on a physical uplink control channel
ActiveCN102281133AGuaranteed performanceAvoid Throughput ImpactError prevention/detection by using return channelSpatial transmit diversityChannel state informationTelecommunications
The present invention discloses a method and a device for transmitting information on a physical uplink control channel (PUCCH). The method includes the following steps: a user equipment (UE) selects information from channel state information (CSI) to transmit (S1); the information selected from the CSI is transmitted on the PUCCH with one or both of hybrid automatic retransmission acknowledgment information and a scheduling request (S2), which enables a base station to obtain not only the information in the CSI but also one or both of the hybrid automatic retransmission acknowledgement information and the scheduling request from the PUCCH. The present invention avoids the problem of system downlink throughput degradation caused by dropping all CSI by the UE in the prior art, and avoids the problem that system downlink throughput is influenced by unnecessary data retransmission on a downlink carrier caused by ACK / NACK bundling among carriers.
Owner:NOKIA TECHNOLOGLES OY
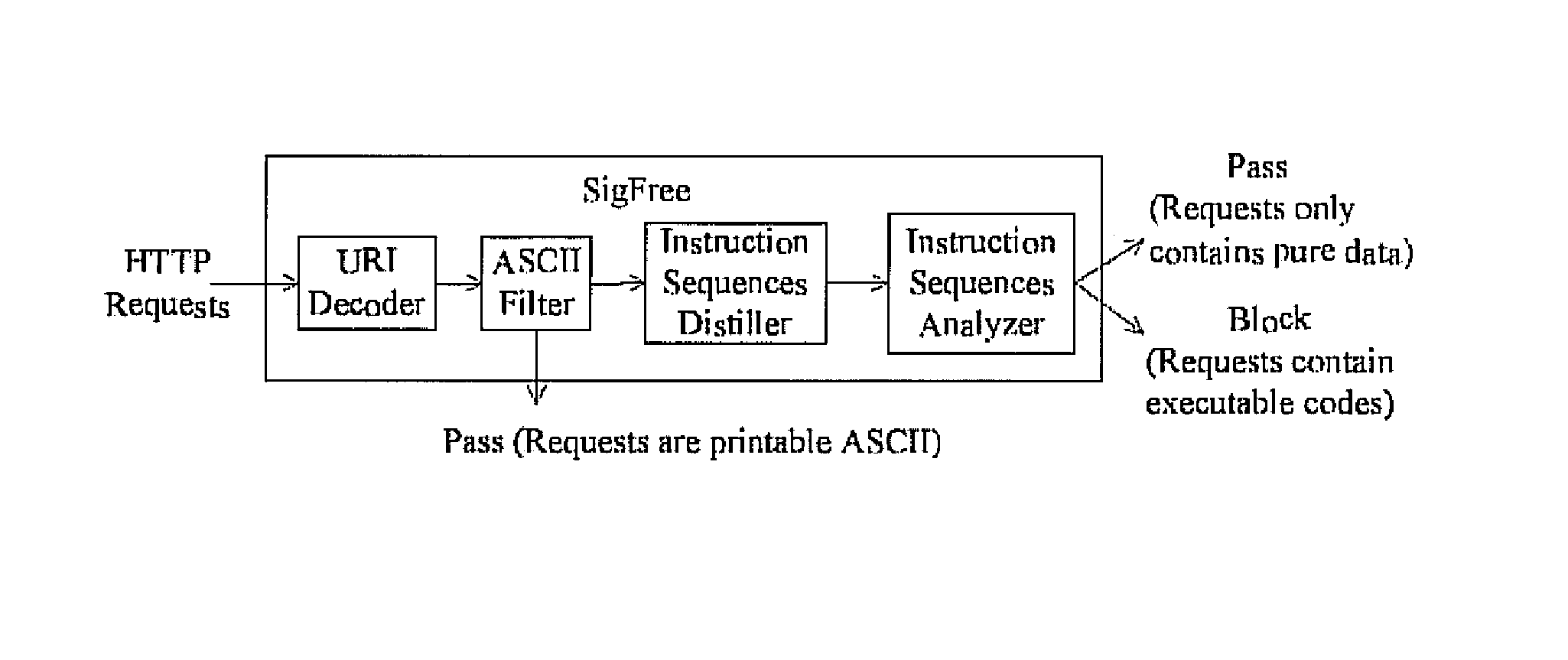
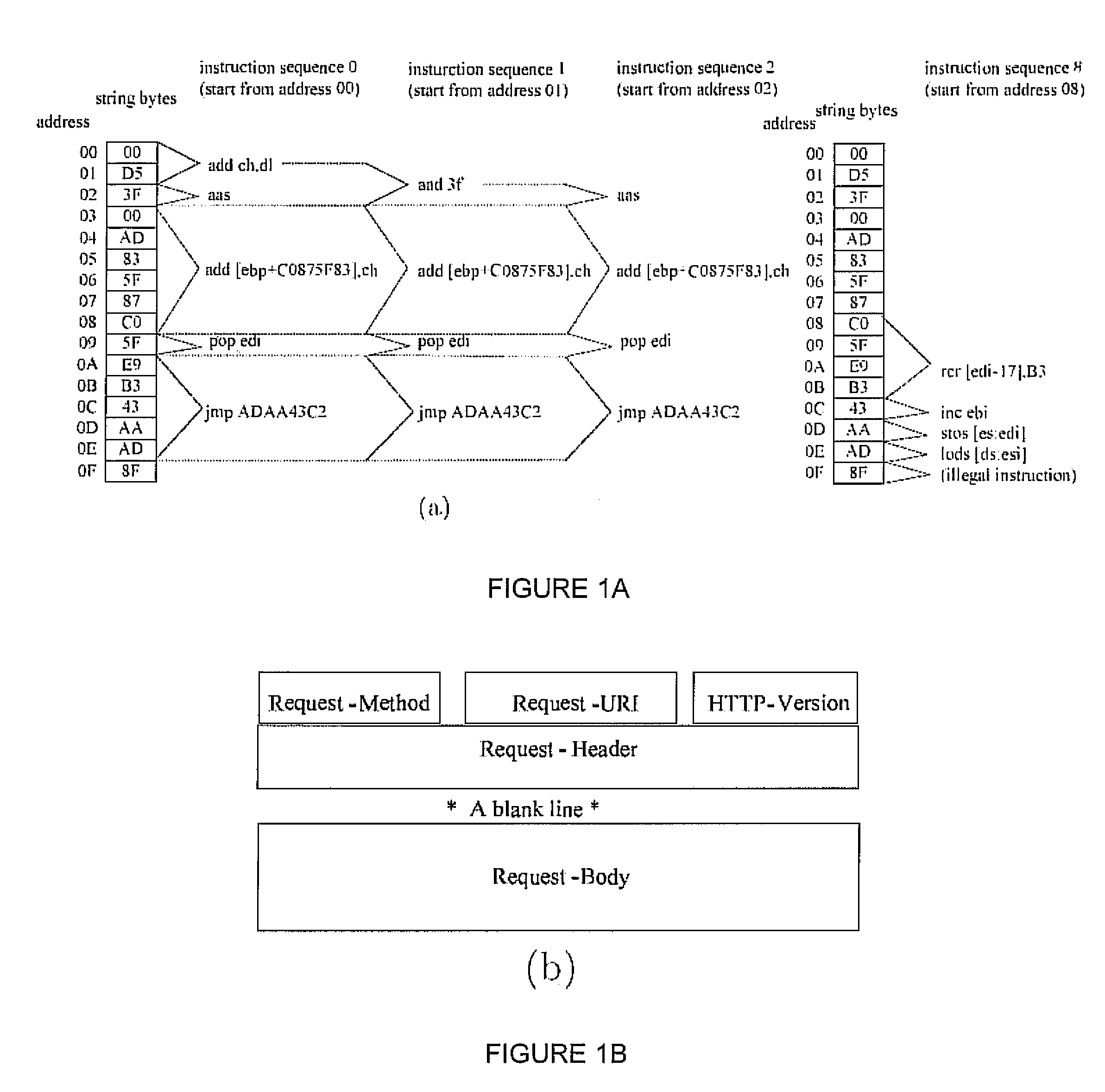
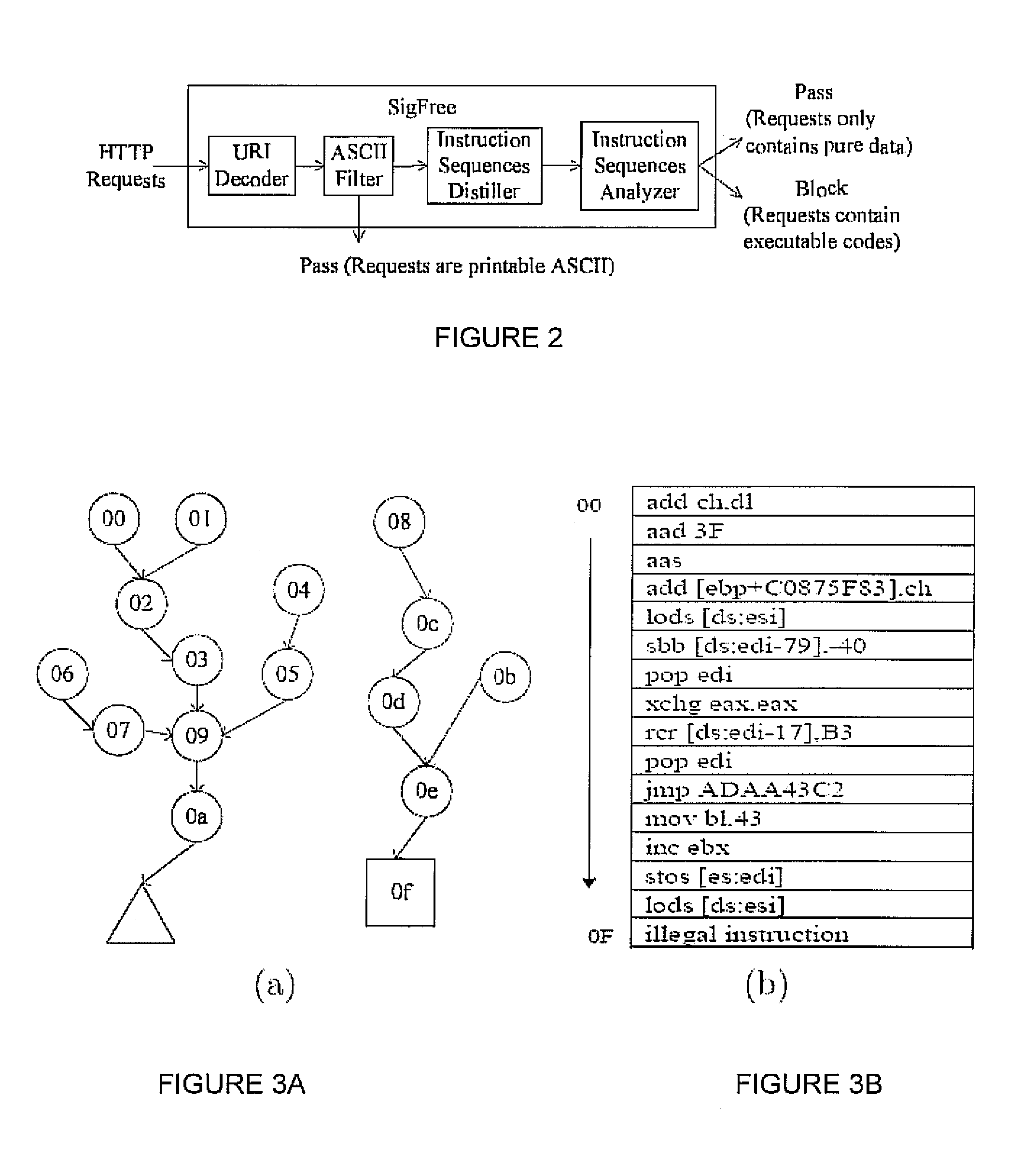
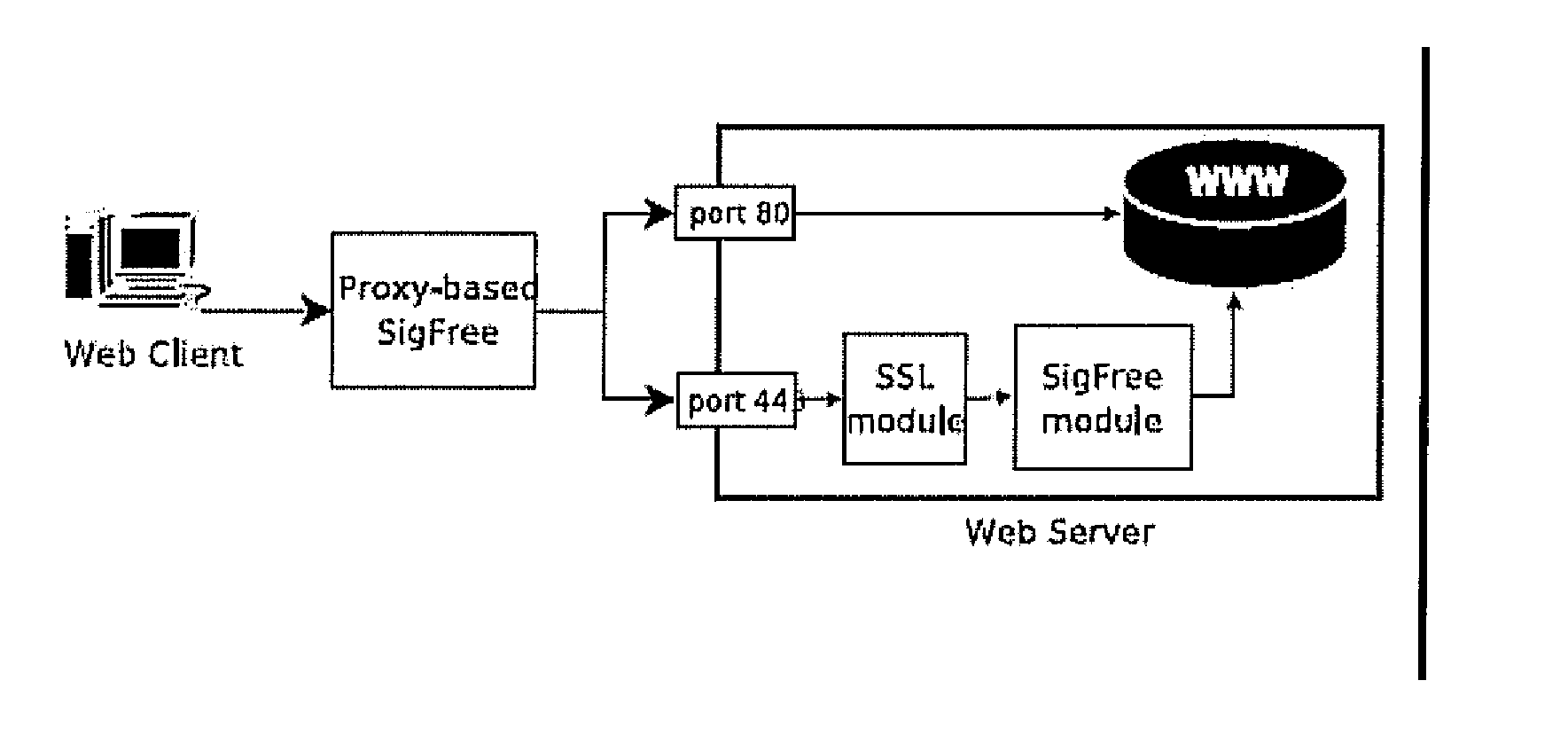
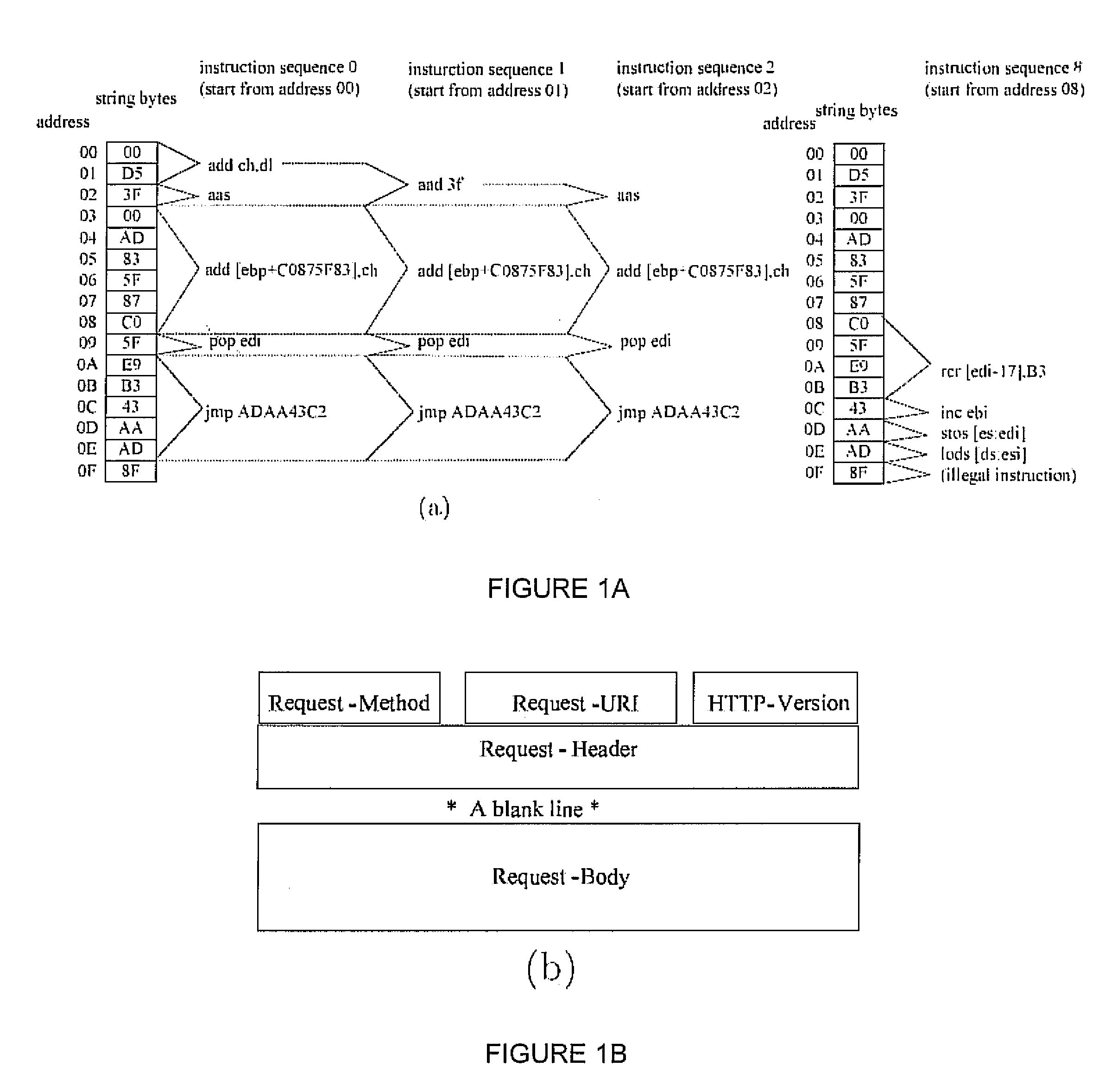
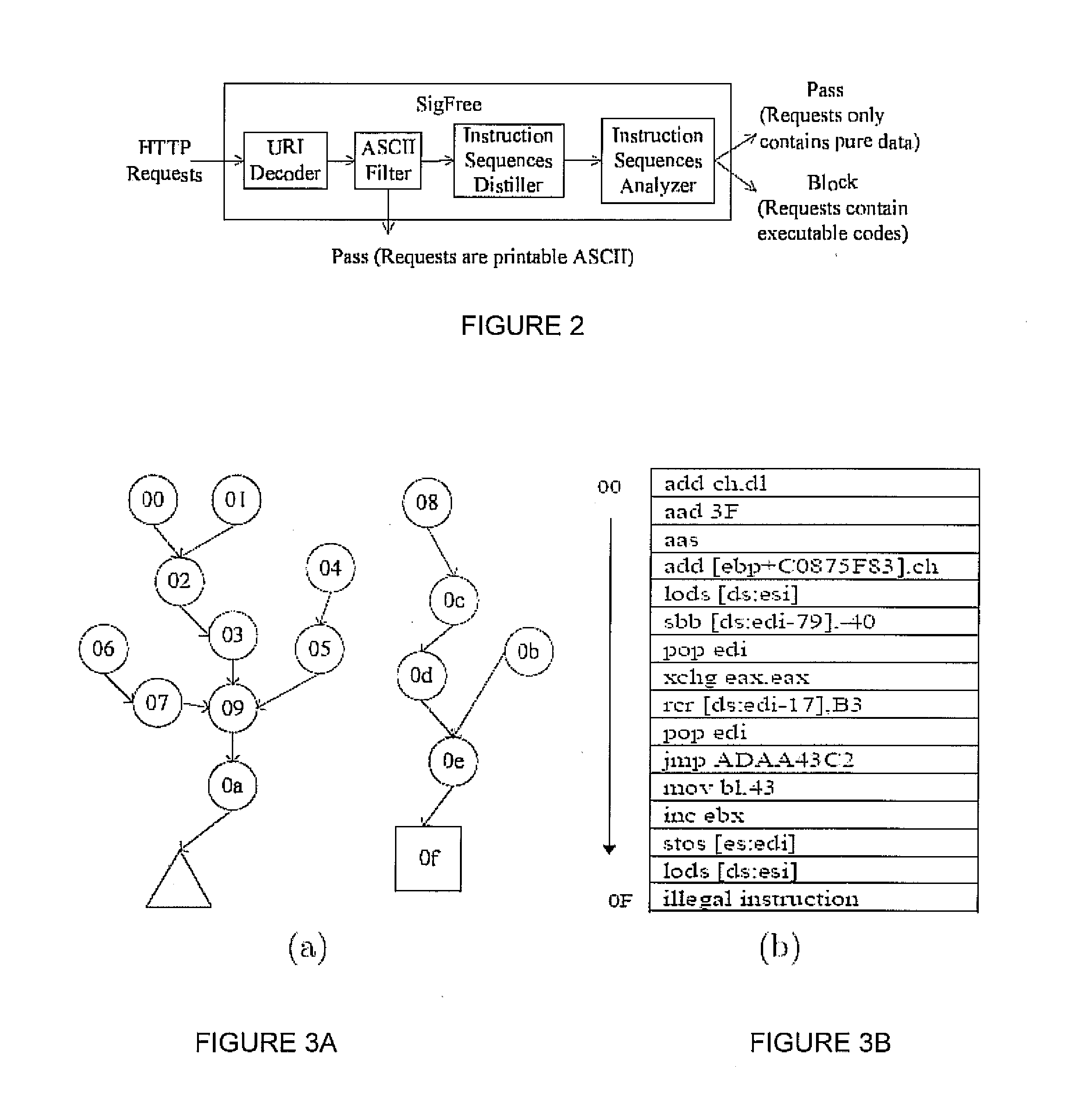
Signature-free buffer overflow attack blocker
ActiveUS8443442B2Transparent to serverLow deploymentMemory loss protectionError detection/correctionObfuscationWeb service
A real-time, signature-free, blocker prevents buffer overflow attacks. The system and method, called SigFree, can filter out code injection buffer overflow attack packets targeting at various Internet services such as web services. Motivated by the observation that buffer overflow attacks typically contain executables whereas legitimate client requests never contain executables in most Internet services, SigFree blocks attacks by checking, without any preknowledge of the real attacks, if “executable” instruction sequences can be blindly disassembled and extracted from a packet. Being signature-free, the invention can block new and unknown buffer overflow attacks. It is immunized from almost every attack-side code obfuscation method, and transparent to the servers being protected. The approach is therefore suited to economical Internet-wide deployment with very low deployment and maintenance costs. SigFree can also handle encrypted SSL packets. An experimental study shows that SigFree can block all types of code-injection attack packets without yielding any false positives or false negatives. Moreover, SigFree causes negligible throughput degradation to normal client requests.
Owner:PENN STATE RES FOUND
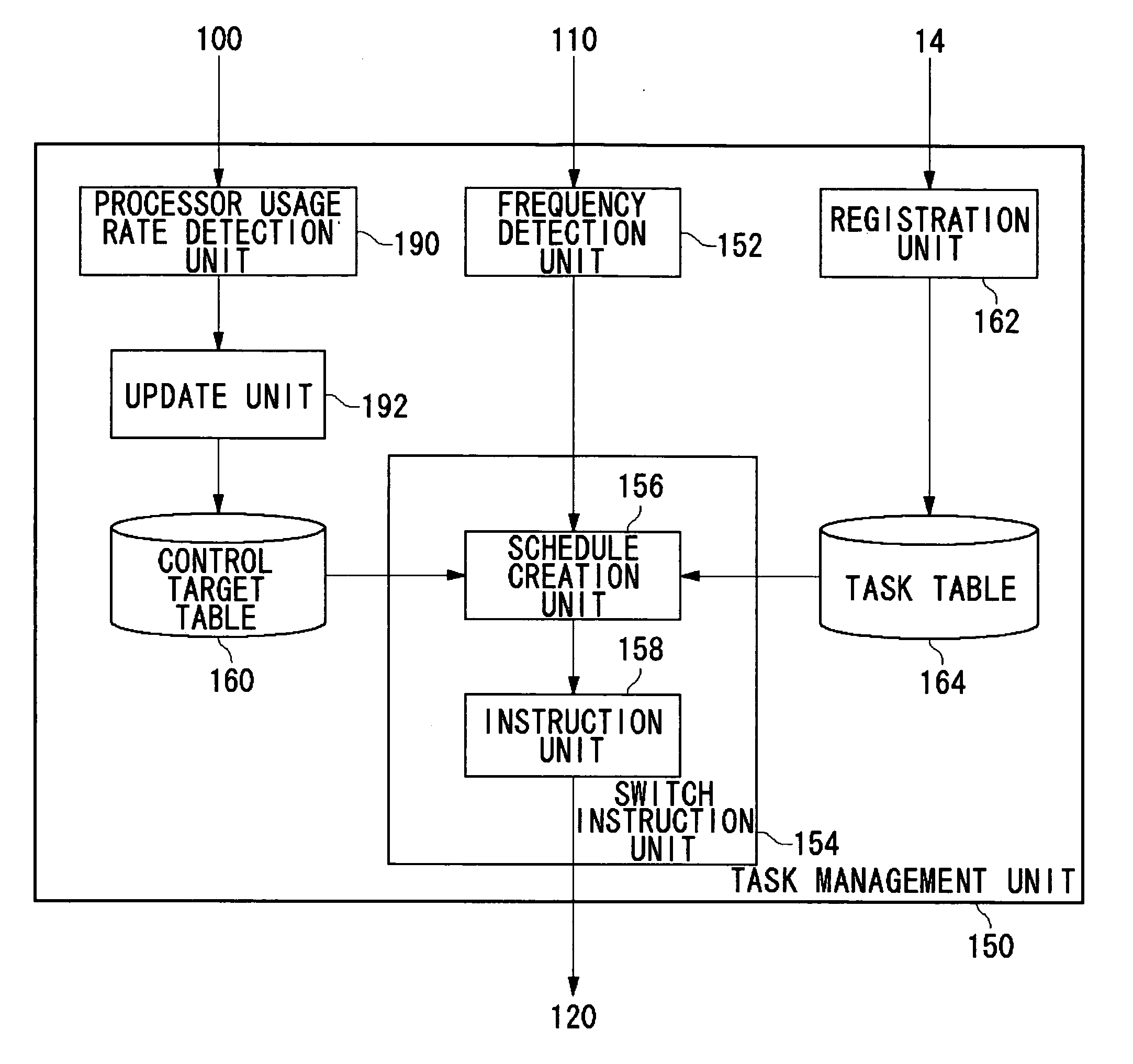
Task management method, task management device, semiconductor integrated circuit, electronic apparatus, and task management system
ActiveUS20070074216A1Increase probabilityEnergy efficient ICTProgram initiation/switchingThroughput degradationComputer science
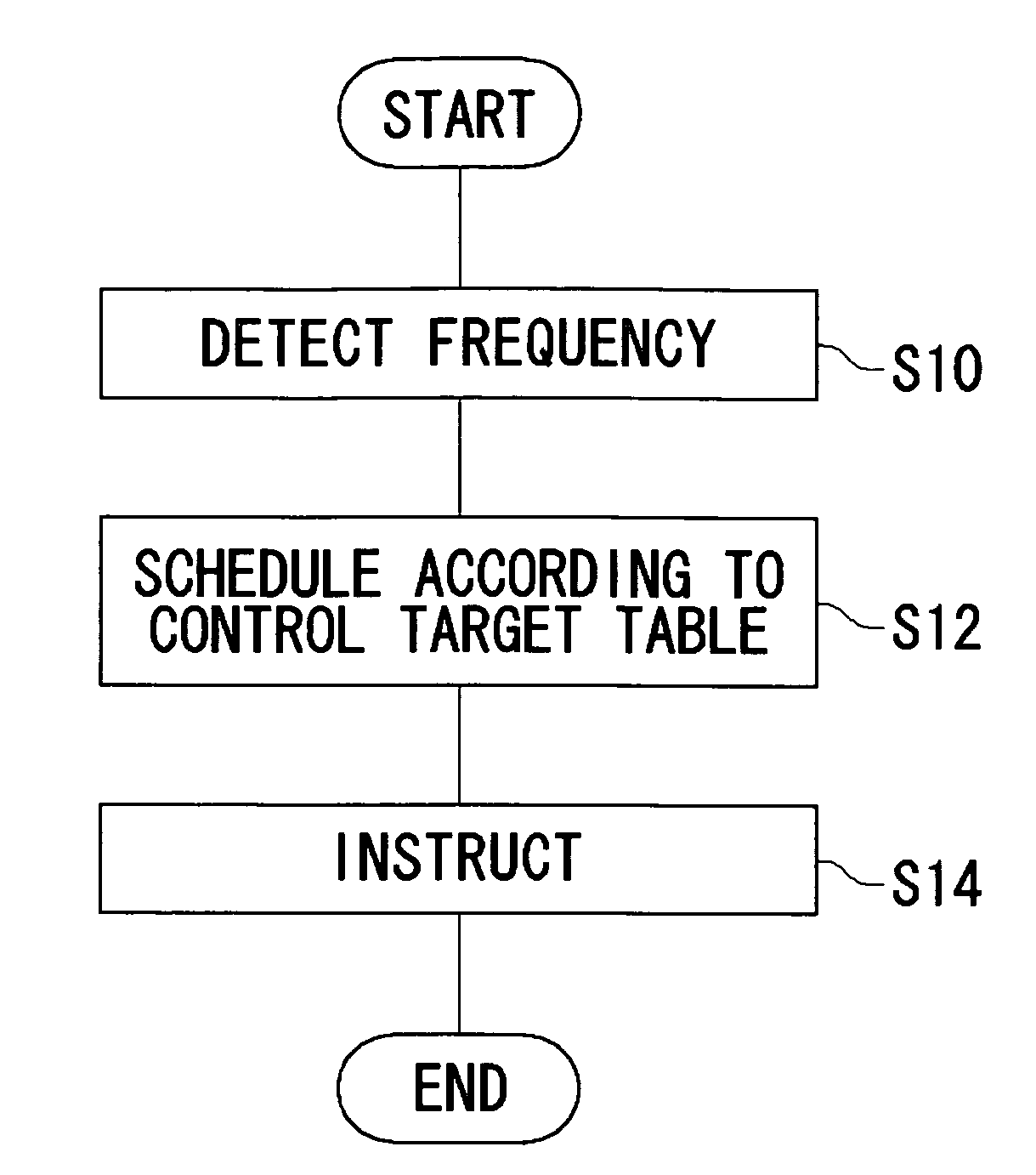
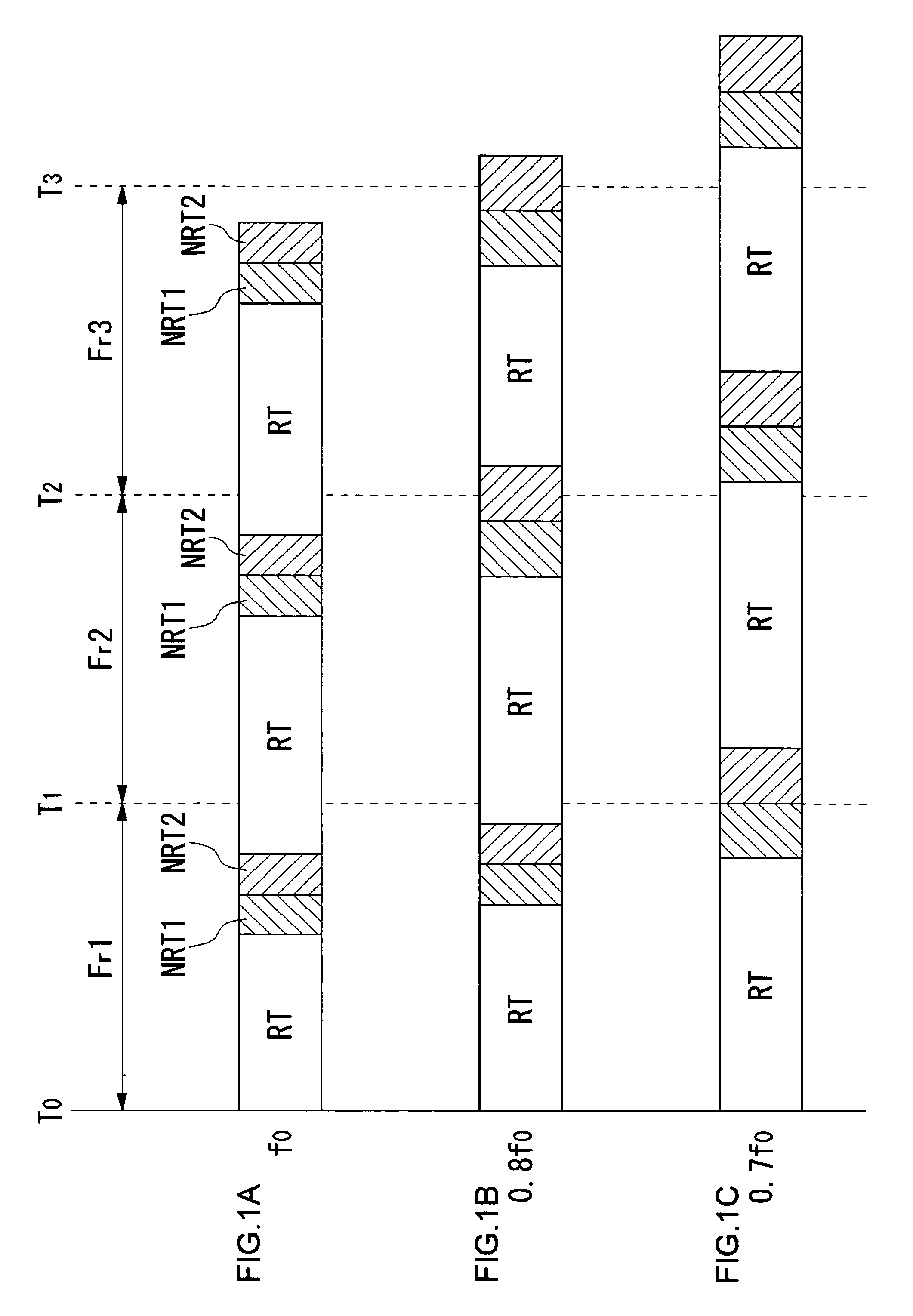
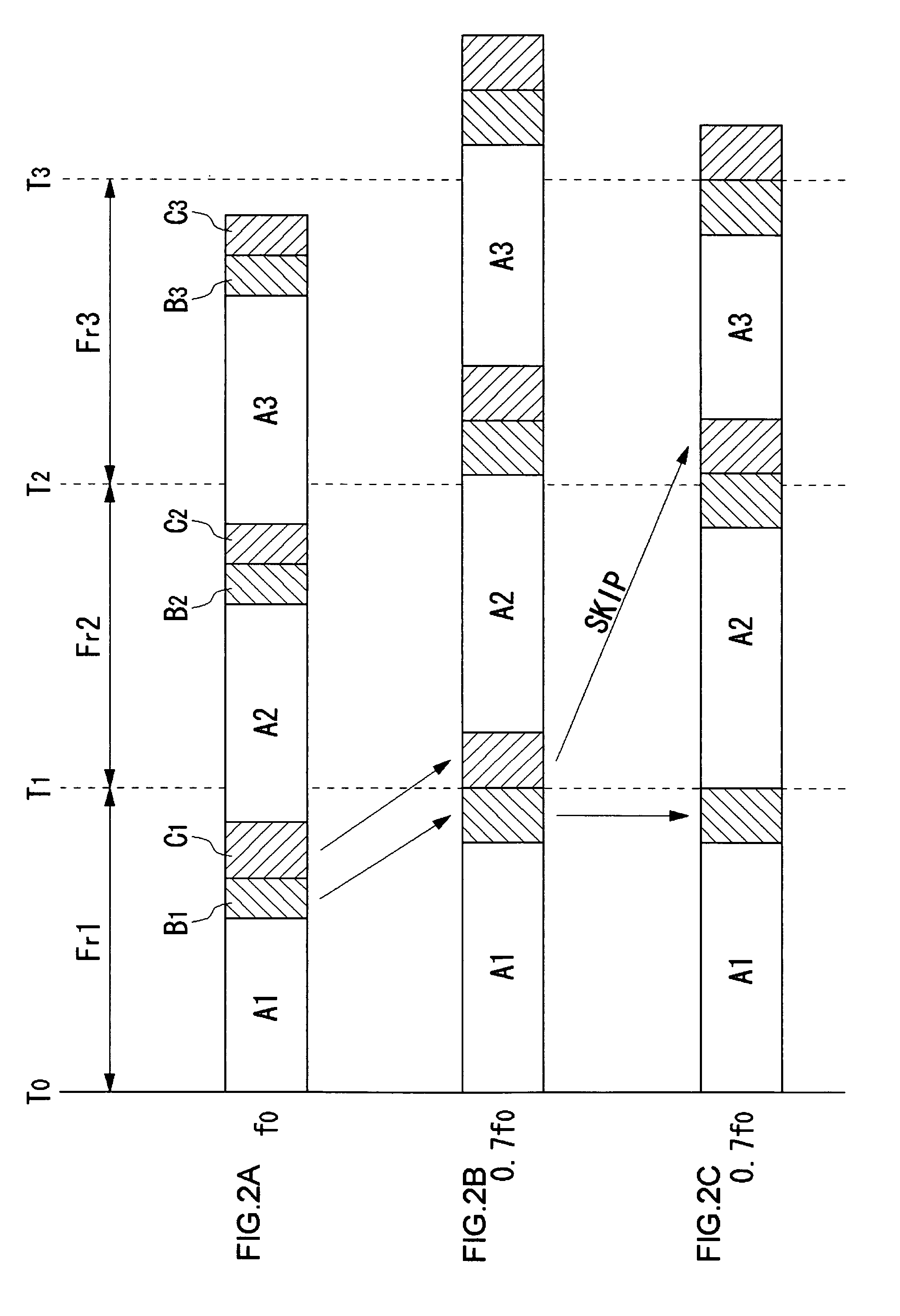
This task management method includes dividing a unit time of processing into a reserved band for guaranteeing real-timeness and a non-reserved band not for guaranteeing real-timeness, and skipping a task to be executed in the non-reserved band as appropriate when processor throughput falls. That is, when the operating frequency of the processor is lowered in order to suppress heat generation, the real-timeness of tasks to be executed in the reserved band is guaranteed at the expense of processing the task to be executed in the non-reserved band in a best-efforts fashion.
Owner:SONY COMPUTER ENTERTAINMENT INC
Signature-free buffer overflow attack blocker
ActiveUS20080022405A1Negligible throughput degradationTransparent to serverMemory loss protectionError detection/correctionData packExperimental research
A real-time, signature-free, blocker prevents buffer overflow attacks. The system and method, called SigFree, can filter out code injection buffer overflow attack packets targeting at various Internet services such as web services. Motivated by the observation that buffer overflow attacks typically contain executables whereas legitimate client requests never contain executables in most Internet services, SigFree blocks attacks by checking, without any preknowledge of the real attacks, if “executable” instruction sequences can be blindly disassembled and extracted from a packet. Being signature-free, the invention can block new and unknown buffer overflow attacks. It is immunized from almost every attack-side code obfuscation method, and transparent to the servers being protected. The approach is therefore suited to economical Internet-wide deployment with very low deployment and maintenance costs. SigFree can also handle encrypted SSL packets. An experimental study shows that SigFree can block all types of code-injection attack packets without yielding any false positives or false negatives. Moreover, SigFree causes negligible throughput degradation to normal client requests.
Owner:PENN STATE RES FOUND
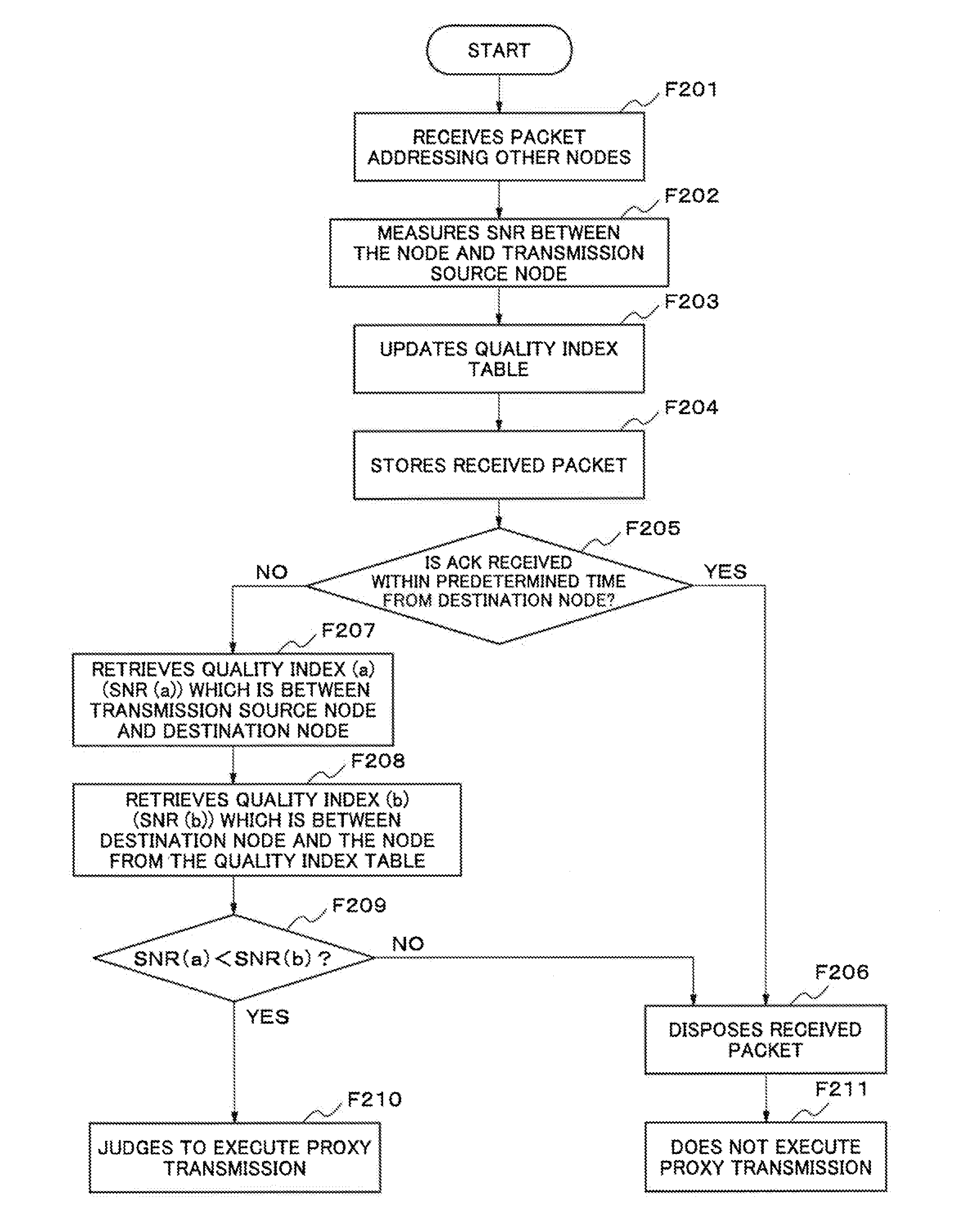
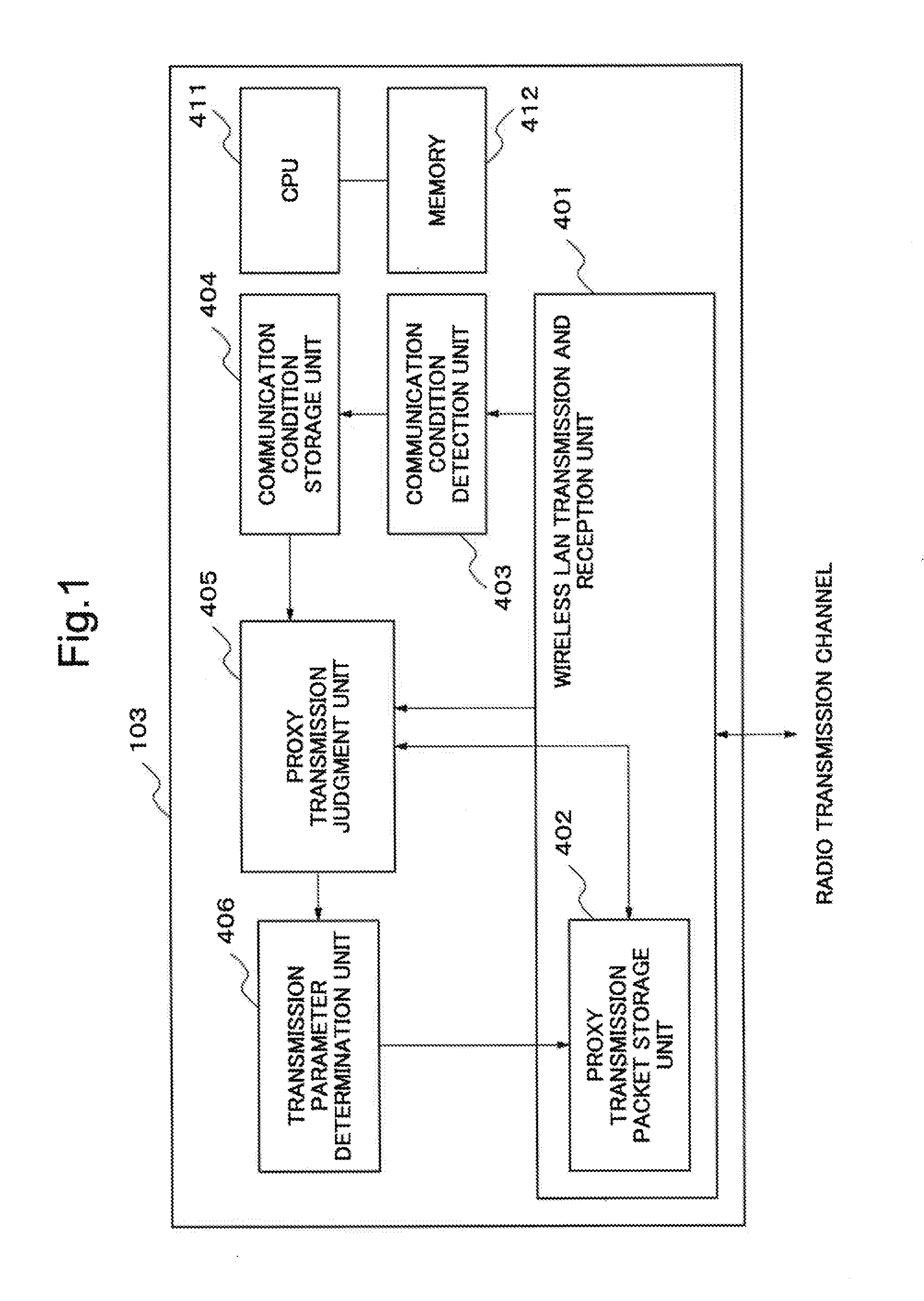
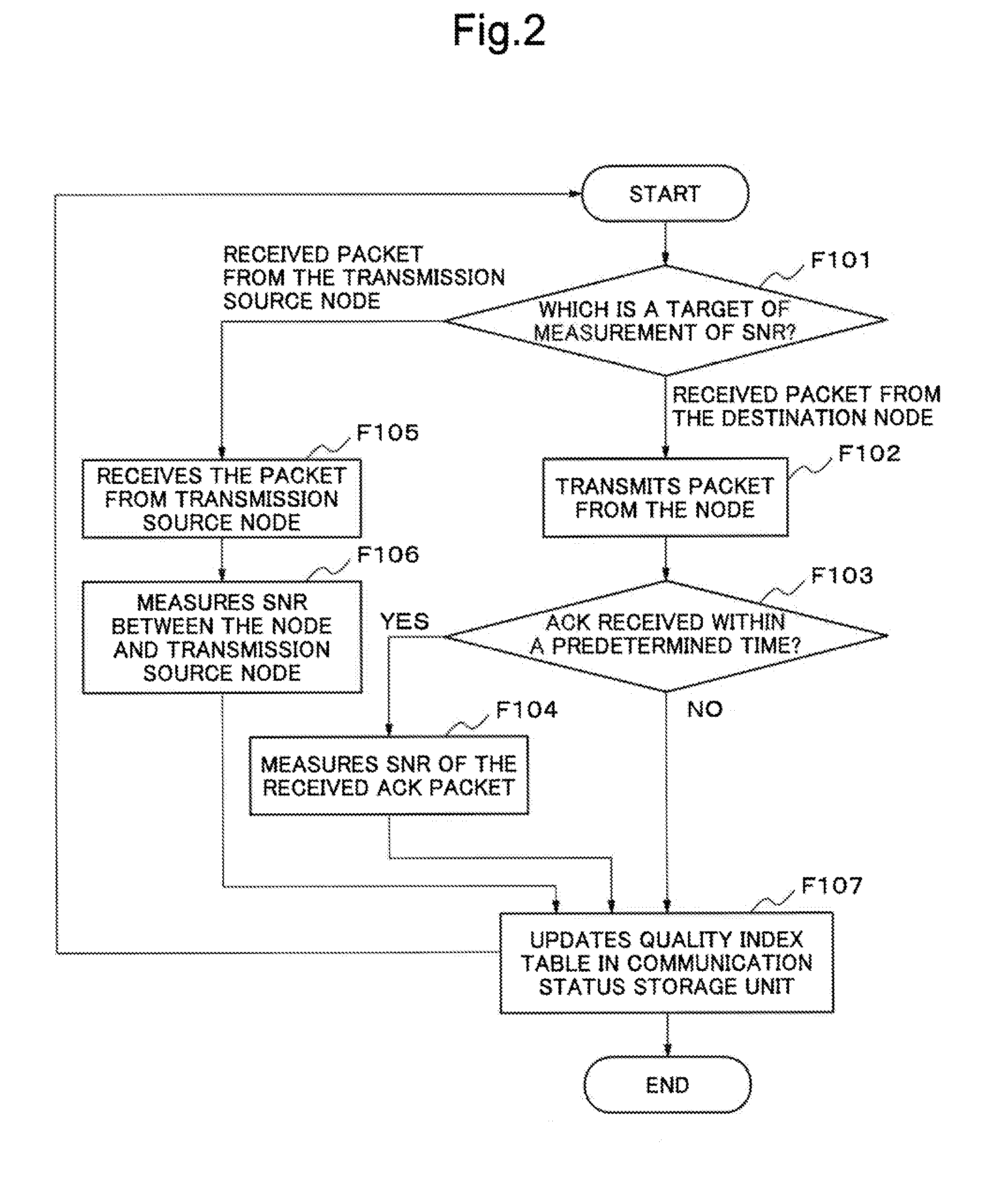
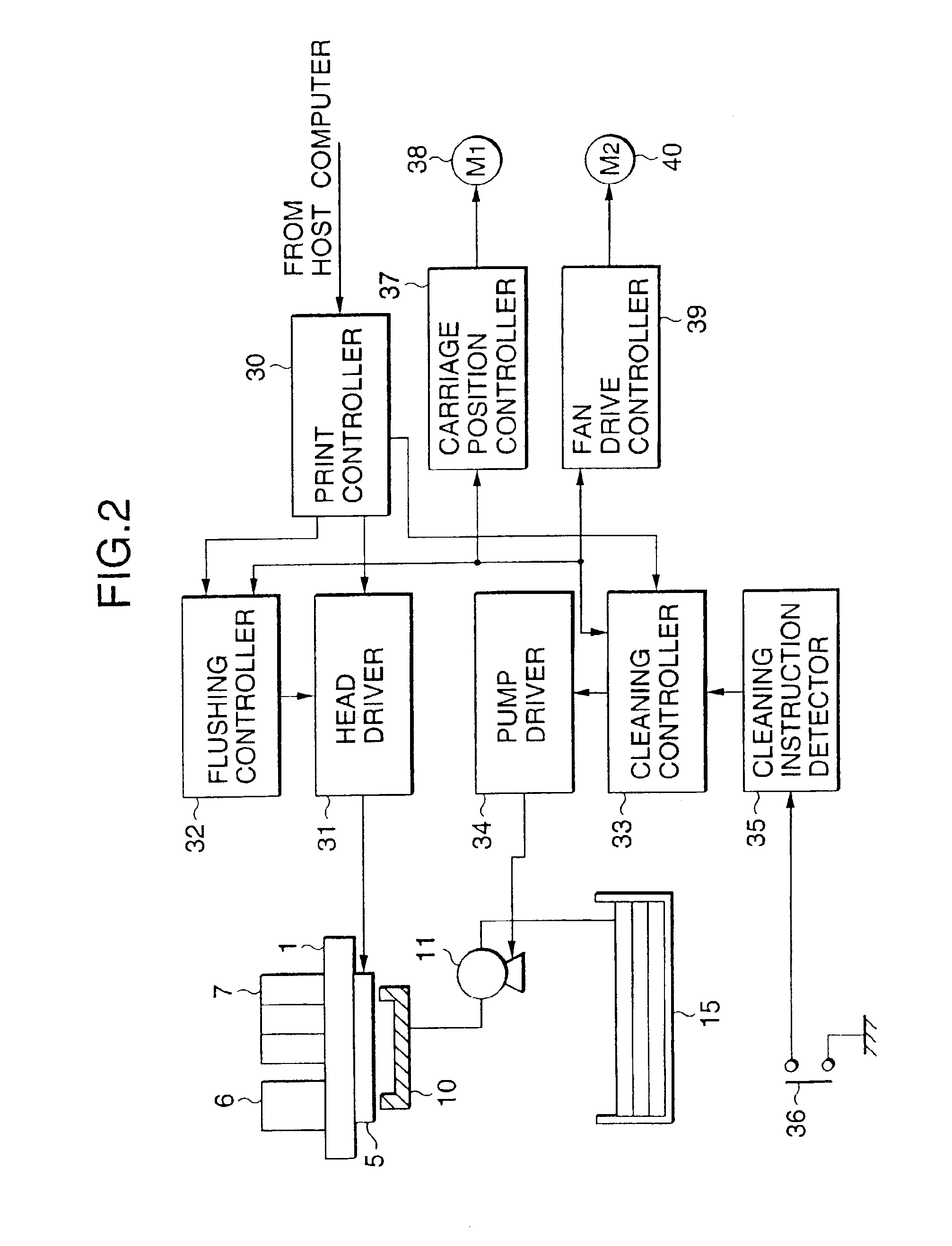
Communication device, recording medium for control program of communication device, communication system and communication method
ActiveUS20120003940A1Prevent degradationNetwork topologiesTransmission monitoringComputer hardwareCommunications system
In order to settle a problem of suppressing degradation of a throughput of a communication system, a communication device is provided with a reception means which receives and accumulates a first datum which a first device transmits addressing a second device and a second datum which the second device transmits, a transmission means which transmits the first datum to the second device, a quality index acquisition means which acquires a first index which is a quality of communication between the first device and the second device and a second index which is a quality of communication between the communication device and the second device, and a judgment means which forces to transmit the accumulated first datum to the second device using the transmission means in the case of judging that the second index is better than the first index and a reception condition of the second datum shows that the second device does not receive normally the first datum.
Owner:NEC CORP
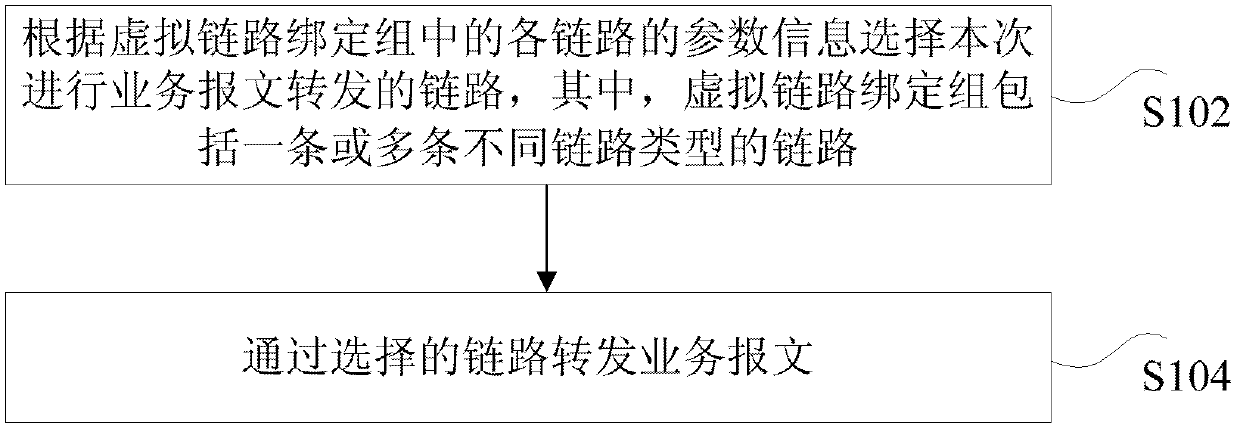
Service message forwarding method and device
ActiveCN103312613ASolve the delay problemSolve the problem of business throughput declineData switching networksTime delaysThroughput degradation
The invention discloses a service message forwarding method and a service message forwarding device. The method comprises the following steps of selecting a link for current service message forwarding according to the parameter information of each link in a virtual link binding group, wherein the virtual link binding group comprises one or more links of different link types; and forwarding a service message by using the selected link. According to the method and the device, the problems of long service forwarding time delay and service throughput reduction, which are caused by a mode of forwarding the service message in turns by using the links, in the prior art are solved, and the technical effects of effectively utilizing link resources, improving the service throughput, increasing a link bandwidth and improving the networking flexibility are achieved.
Owner:ZTE CORP
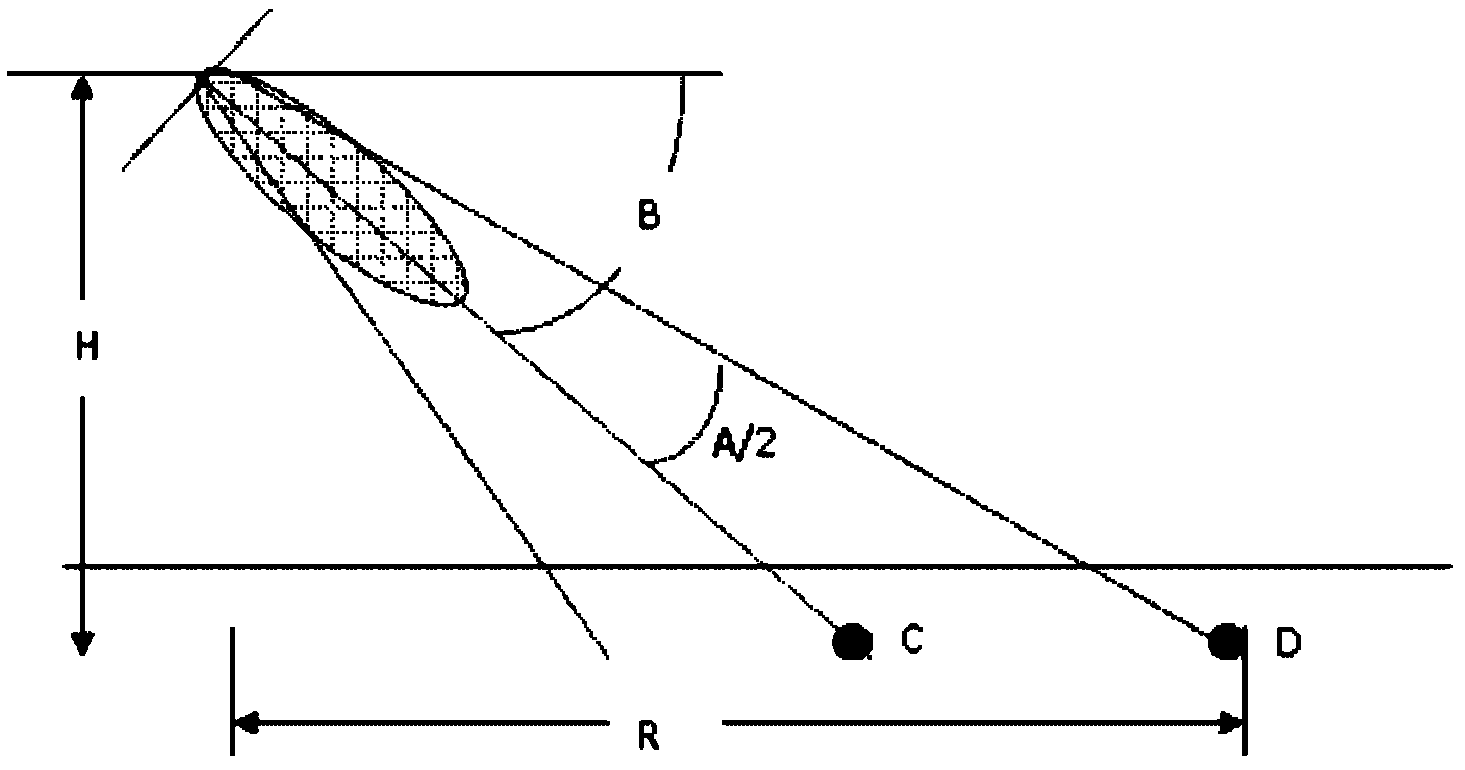
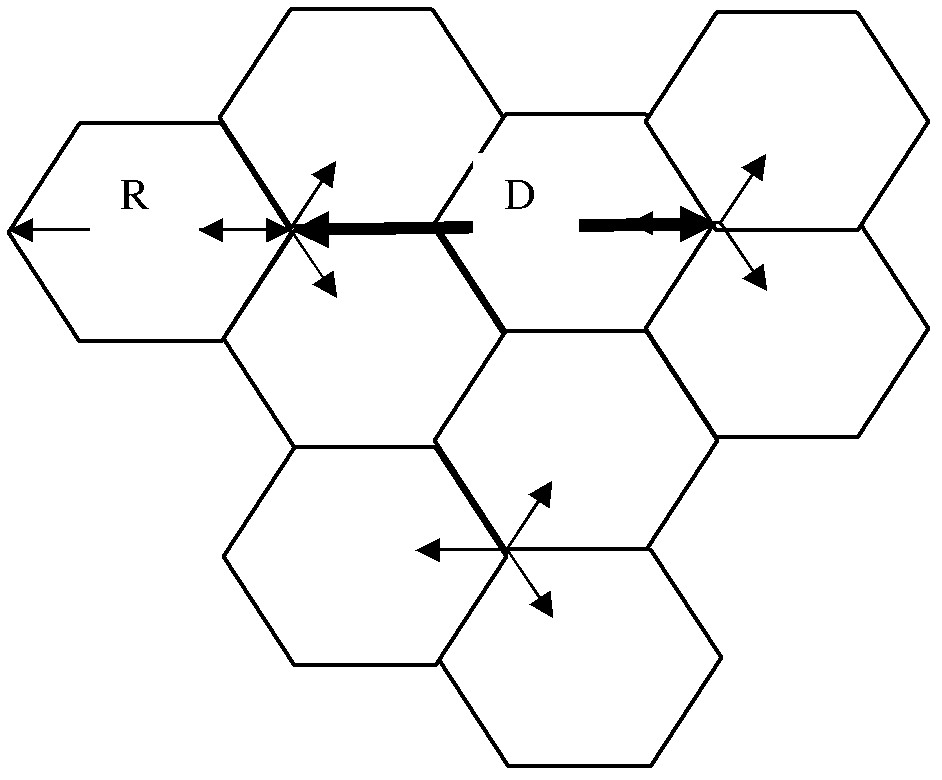
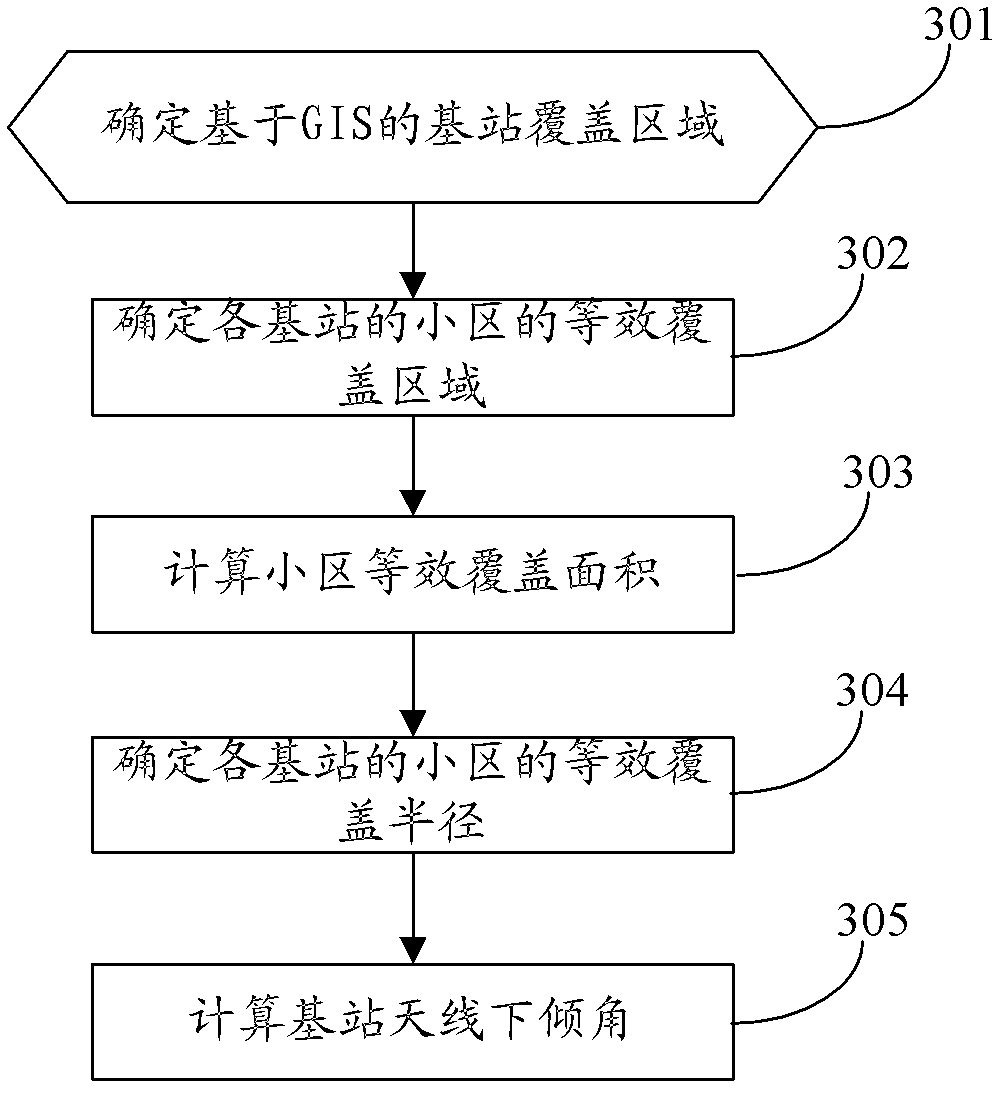
Antenna downward inclination angle determination method and device based on geographic information system (GIS)
ActiveCN103188693AAvoid overlapping coverageAvoid throughput drop issuesNetwork planningAdjacent-channel interferenceTime-Division Long-Term Evolution
The invention discloses an antenna downward inclination angle determination method and device based on a geographic information system (GIS). The method comprises the following steps: determining an equivalent coverage radius of a cell of each base station according to base station location information in the GIS and the Thiessen polygon principle and determining a maximum coverage radius of the cell of each base station according to an application scene which the cell of each base station is located in; when the equivalent coverage radius is ascertained to be smaller than or equal to the maximum coverage radius, determining the antenna downward inclination angle of the base station which the cell belongs to based on the equivalent coverage radius; and when the equivalent coverage radius is ascertained to be larger than the maximum coverage radius, determining the antenna downward inclination angle of the base station which the cell belongs to based on the maximum coverage radius. According to the technical scheme of the antenna downward inclination angle determination method and device based on the GIS, the problems, that handling capacity in a border cell is reduced and a resource usage ratio is low, caused by unreasonable arrangement of the antenna downward inclination angle of the base station in same-frequency networking in a time division-long term evolution (TD-LTE) system can be avoided, same and adjacent channel interference among cells can be reduced effectively and network service quality and user experience effects are improved.
Owner:CHINA MOBILE GROUP JIANGSU
Pattern inspection method and inspection apparatus
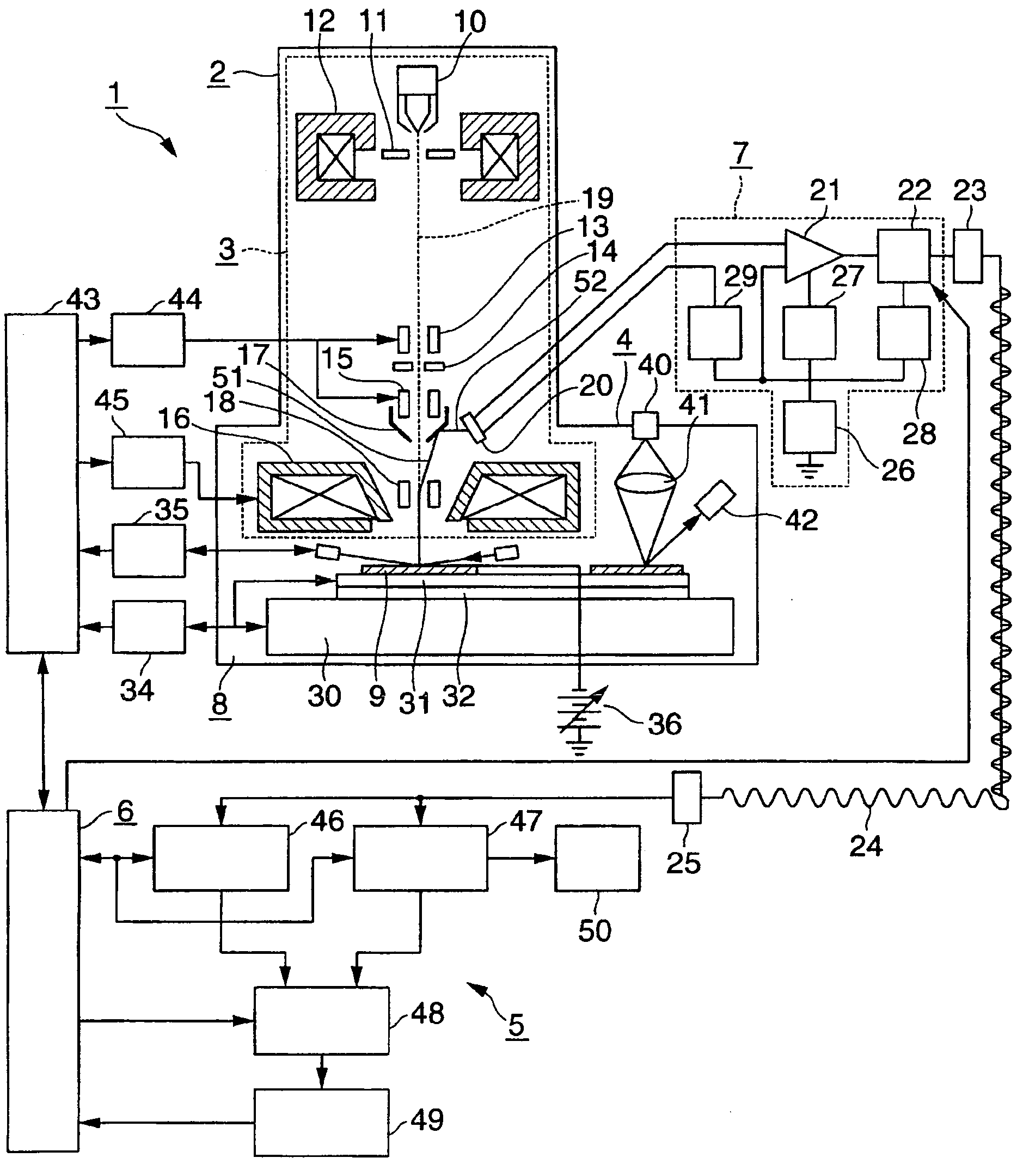
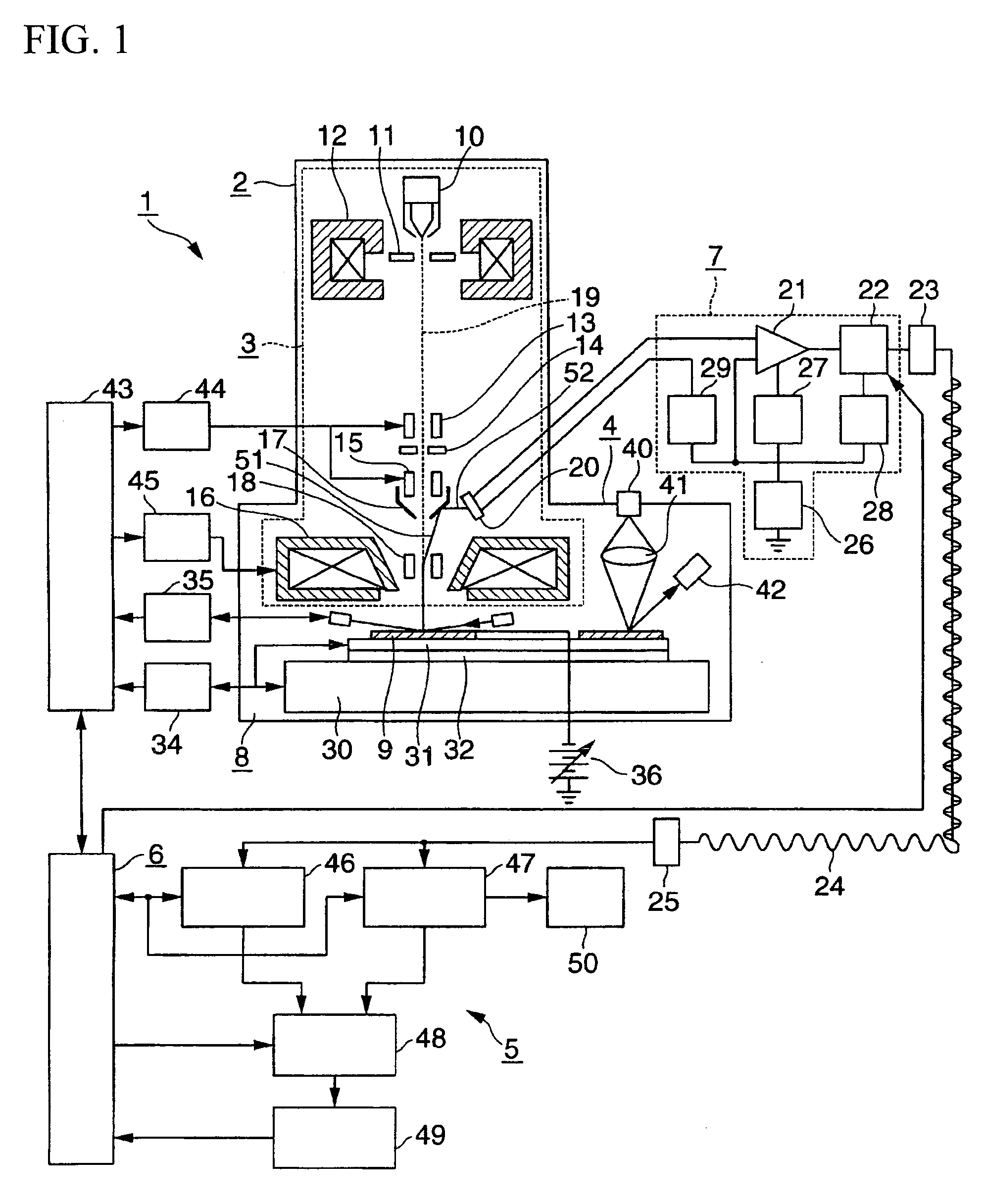
InactiveUS20090206257A1Prevent throughput degradationImprove accuracyMaterial analysis using wave/particle radiationElectric discharge tubesSecondary electronsThroughput degradation
An object of the present invention is to provide an inspection apparatus and an inspection method excellent in that high-sensitivity defect detection performance is achieved without causing throughput degradation even if an adequate contrast of a defective region cannot be obtained due to characteristics of an inspected sample. To achieve the object, according to the present invention, an SEM pattern inspection apparatus for determining defective portions from an image generated based on secondary electrons or reflected electrons generated from the sample after causing an electron beam to repeatedly scan the inspected sample reciprocatingly on a line has a function to use a retrace of the electron beam for image acquisition, precharging, or discharging.
Owner:HITACHI HIGH-TECH CORP
Skipping non-time-critical task according to control table when operating frequency falls
ActiveUS7954101B2Increase probabilityEnergy efficient ICTProgram initiation/switchingTime criticalThroughput degradation
This task management method includes dividing a unit time of processing into a reserved band for guaranteeing real-timeness and a non-reserved band not for guaranteeing real-timeness, and skipping a task to be executed in the non-reserved band as appropriate when processor throughput falls. That is, when the operating frequency of the processor is lowered in order to suppress heat generation, the real-timeness of tasks to be executed in the reserved band is guaranteed at the expense of processing the task to be executed in the non-reserved band in a best-efforts fashion.
Owner:SONY COMPUTER ENTERTAINMENT INC
Data storage method of block chain system, nodes and block chain system
ActiveCN109495249AKey distribution for secure communicationFinanceThroughput degradationChain system
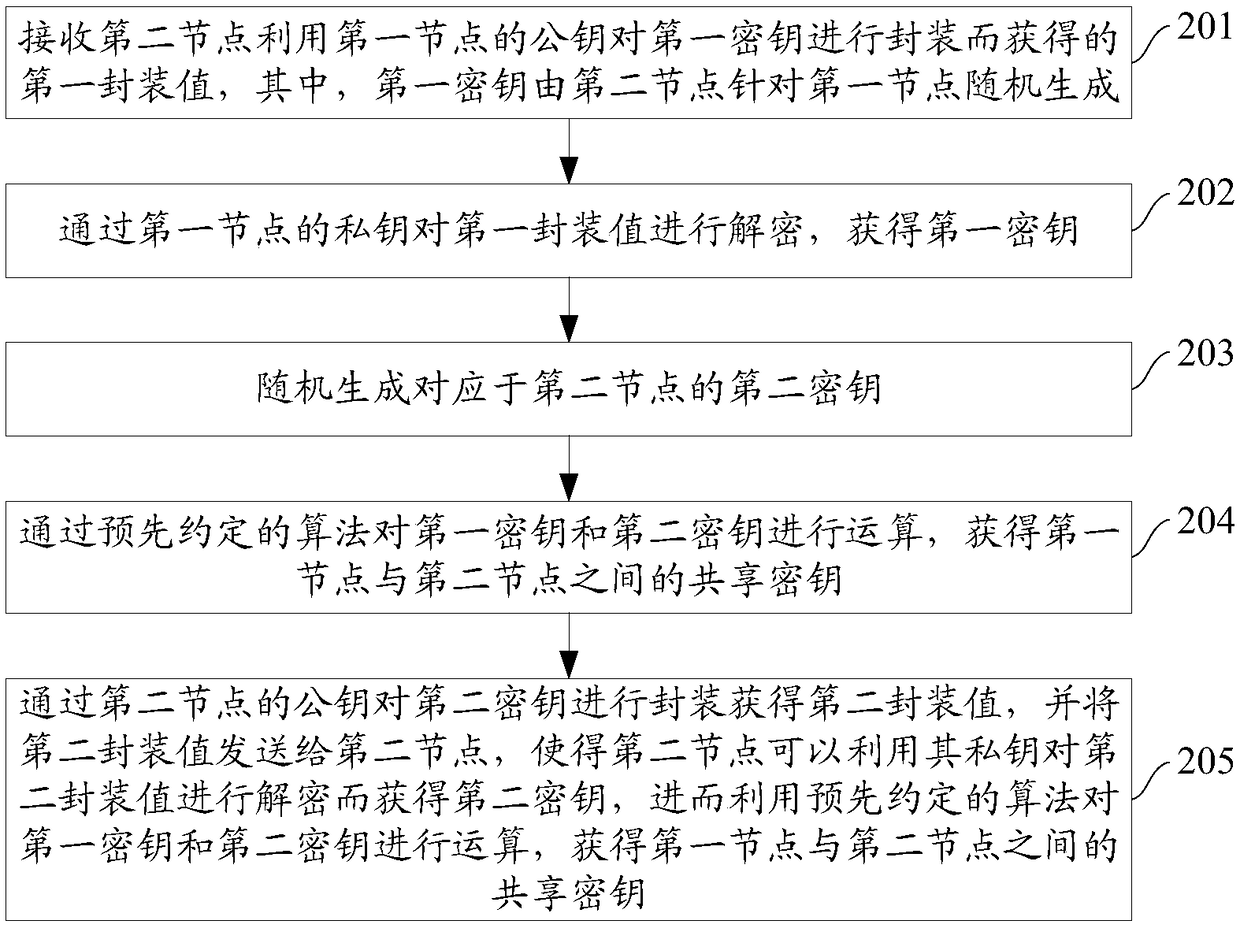
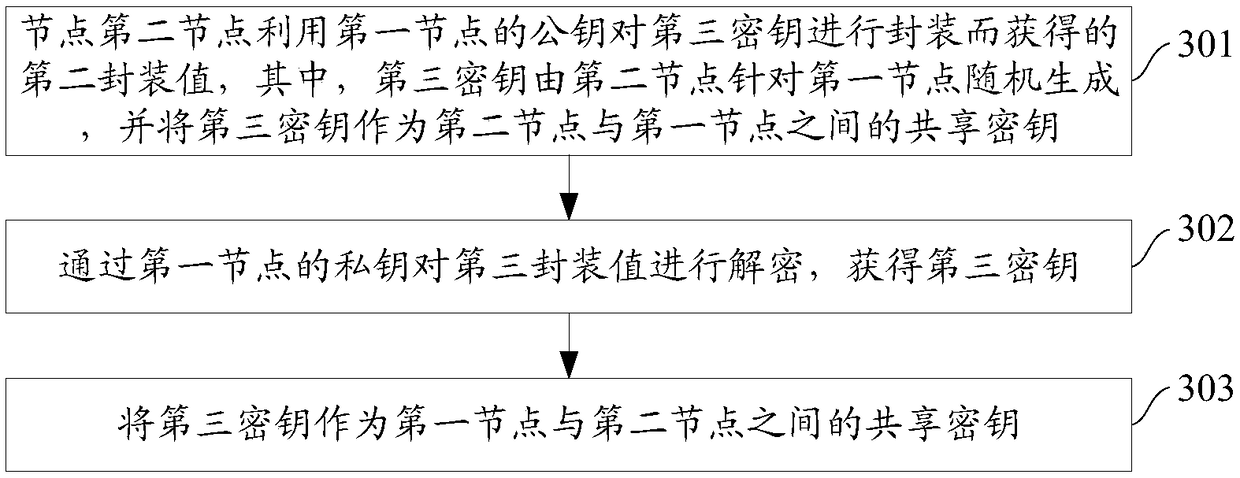
The invention provides a data storage method for a block chain system, nodes and a block chain system. The data storage method comprises the following steps of: for the any first node in the block chain system, respectively acquiring a shared secret key between the first node and the other second nodes in the block chain system; acquiring the transaction information of the transaction initiated bythe first node; processing the transaction information through each shared secret key and a preset keyed hash algorithm to obtain a hash tag; broadcasting the transaction information and the hash tagto each second node; determining an honest node from nodes comprised in the block chain system according to the verification message broadcasted by each second node; and if the honest node determinesthat the transaction is a real transaction, the honest node storing the transaction information in a newly generated block for a main chain. The verification message comprises a result of the secondnodes verifying the authenticity of the transaction. According to the data storage method, the block chain system can resist quantum attacks, and the throughput falling of the block chain system is avoided.
Owner:全链通有限公司
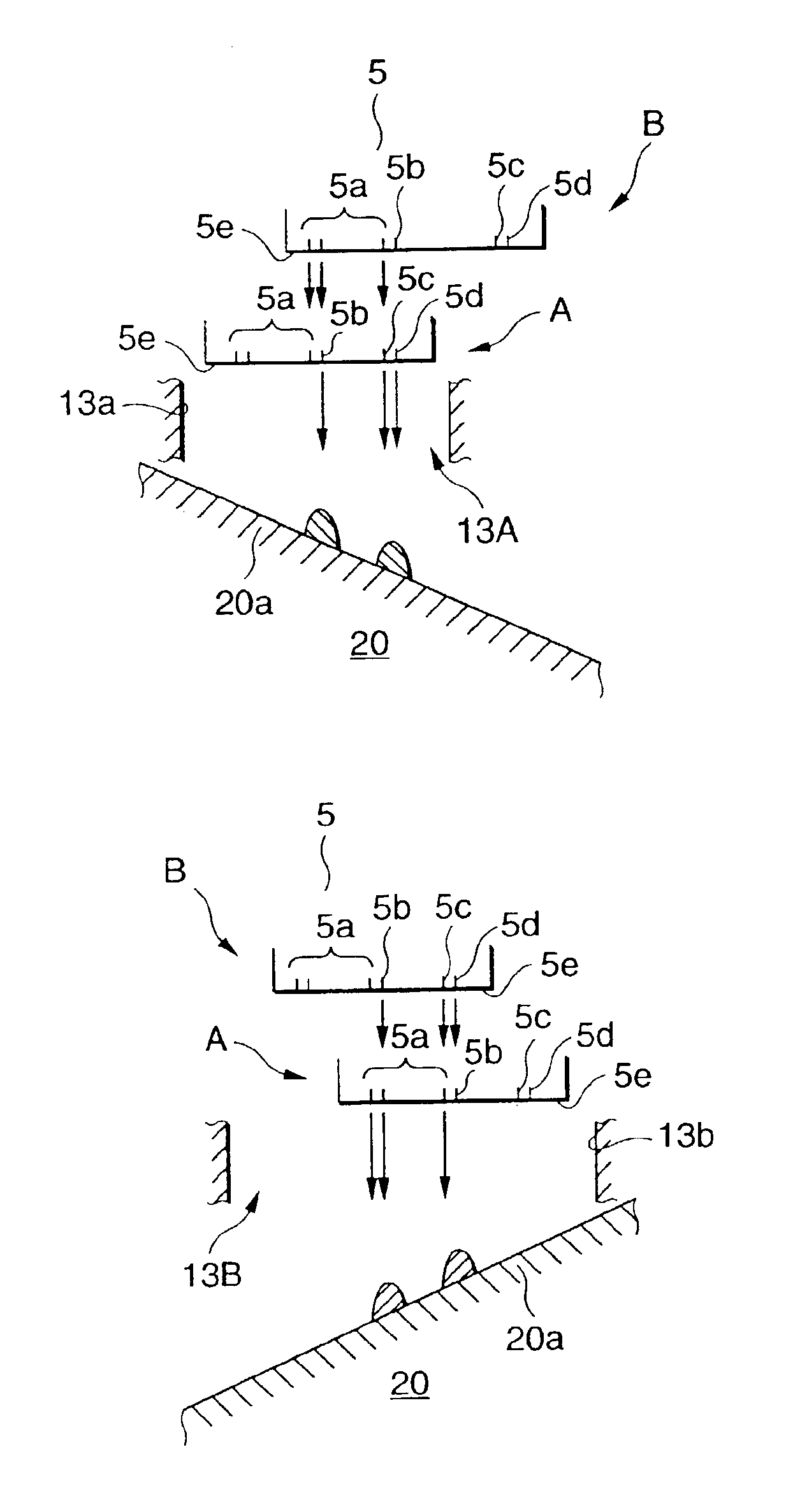
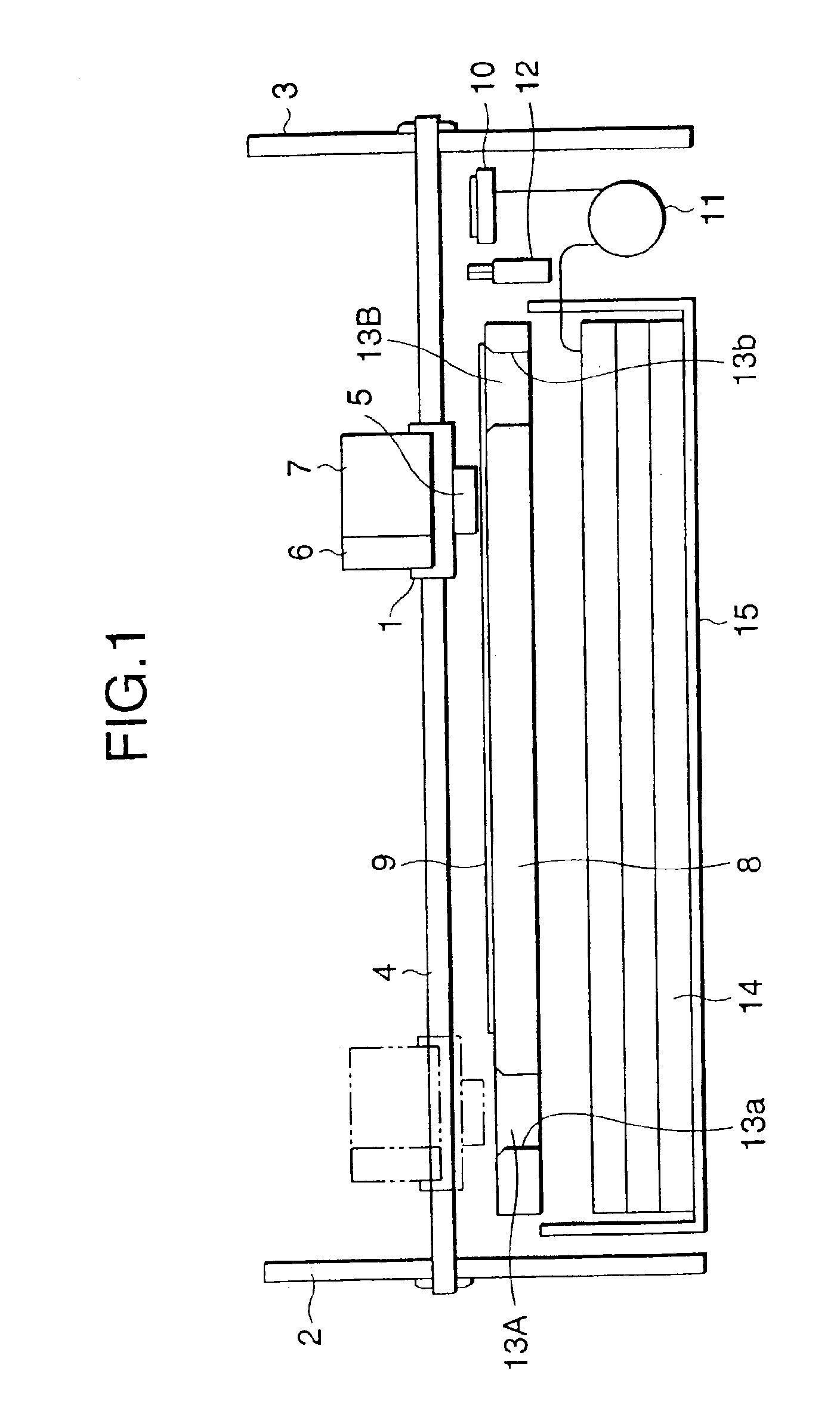
Flushing position controller incorporated in ink-jet recording apparatus and flushing method used for the same
Flushing regions for receiving ink droplets to be ejected when flushing signal is supplied to a recording head are provided in both of non-print regions situated at both sides of print region in order to prevent throughput during the flushing operation from deteriorating. A guide member having a slant surface is disposed between the recording head and an ink absorbing member to which the ink landed on the slant surface flows in order to reduce in size of the ink absorbing member. A porous sheet member closely faced to nozzle orifices of the recording head for receiving the ink droplets ejected therefrom is provided in order to prevent undesired mist of fine ink droplets from generating. A plurality of plate members closely faced to the nozzle orifices are provided at a predetermined angle with respect to the flight direction of the ink droplets in order to prevent the undesired mist from generating. The flushing operation is performed so as to prevent solidification of the ejected ink.
Owner:SEIKO EPSON CORP
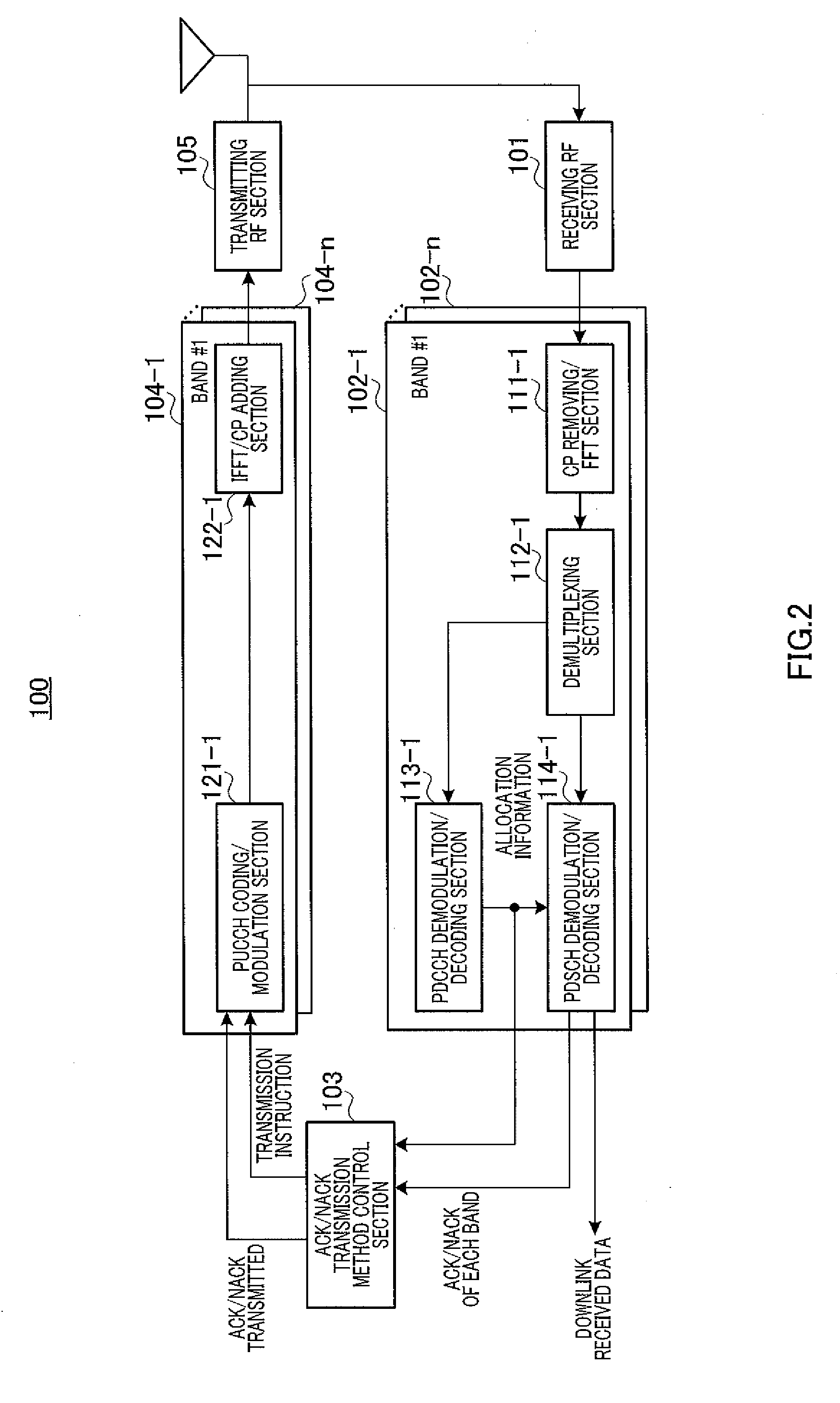
Terminal, base station, response method, and retransmission control method
ActiveUS20120294256A1Reduce in quantityPrevent throughput degradationError prevention/detection by using return channelNetwork traffic/resource managementThroughput degradationReal-time computing
Disclosed are a terminal, a base station, a response method, and a retransmission control method, which are capable of switching the response signal transmission method while preventing throughput degradation and without increasing the number of signaling bits. A bundling determination unit (132) of a terminal (100) determines parameters that denote the allocated resource quantities that are allocated thereto from a base station (200), or in other words, a downstream band that is included in a bundling group and a downstream band that is not included in the bundling group, from among a plurality of downstream bands on the basis of base station transmission parameters. Specifically, a degree of resource share (Xn) that is allocated from each respective downstream band to the terminal (100) is employed in the base station transmission parameters.
Owner:PANASONIC INTELLECTUAL PROPERTY CORP OF AMERICA
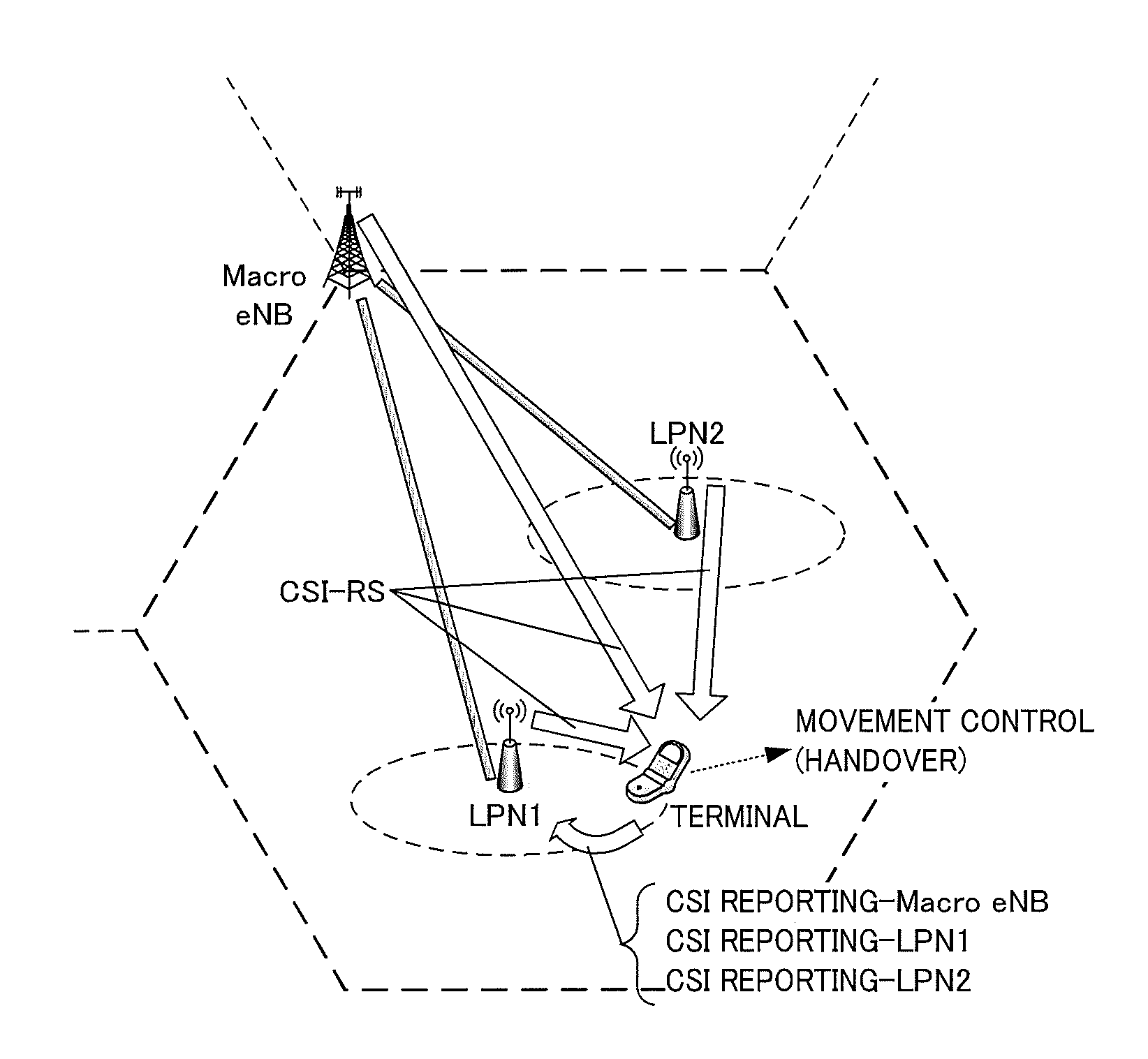
Terminal, base station, transmission method, and reception method
ActiveUS20150009922A1Guaranteed accuracyPrevent deterioration of throughputTransmission path divisionSignal allocationEngineeringSignal generator
Provided is a terminal whereby the accuracy of CSI measurement results in the terminal can be assured, and declines in throughput prevented. In this terminal, a reception processor (203) receives reference signals respectively transmitted from a plurality of transmission points. A CSI generator (206) identifies a second subframe on the basis of a first subframe respectively established for each of the plurality of transmission points, and using the reference signals from the plurality of transmission points, generates channel information in a subframe other than the second subframe, without generating channel information in the second subframe. A transmission signal former (208) transmits the generated channel information.
Owner:PANASONIC INTELLECTUAL PROPERTY CORP OF AMERICA
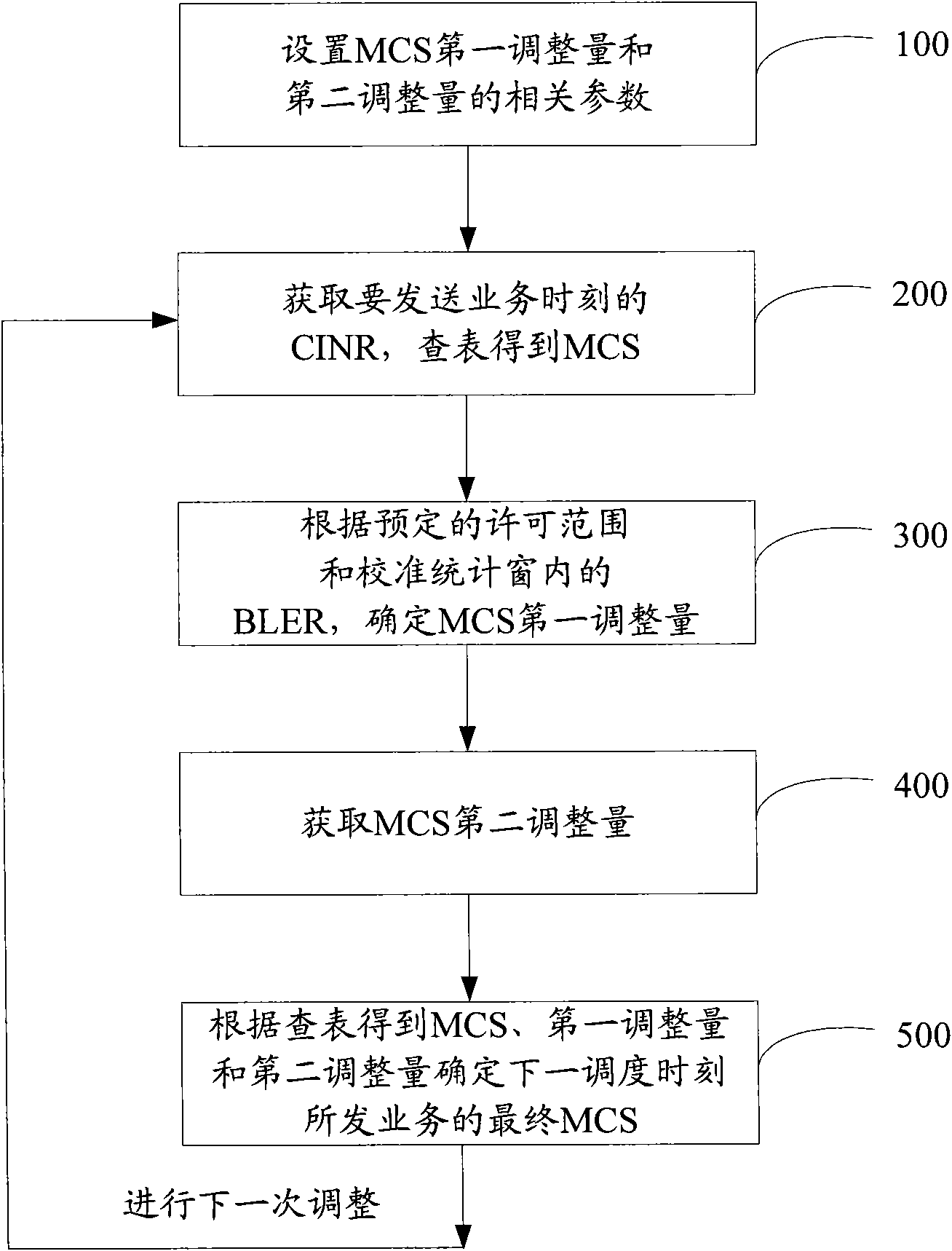
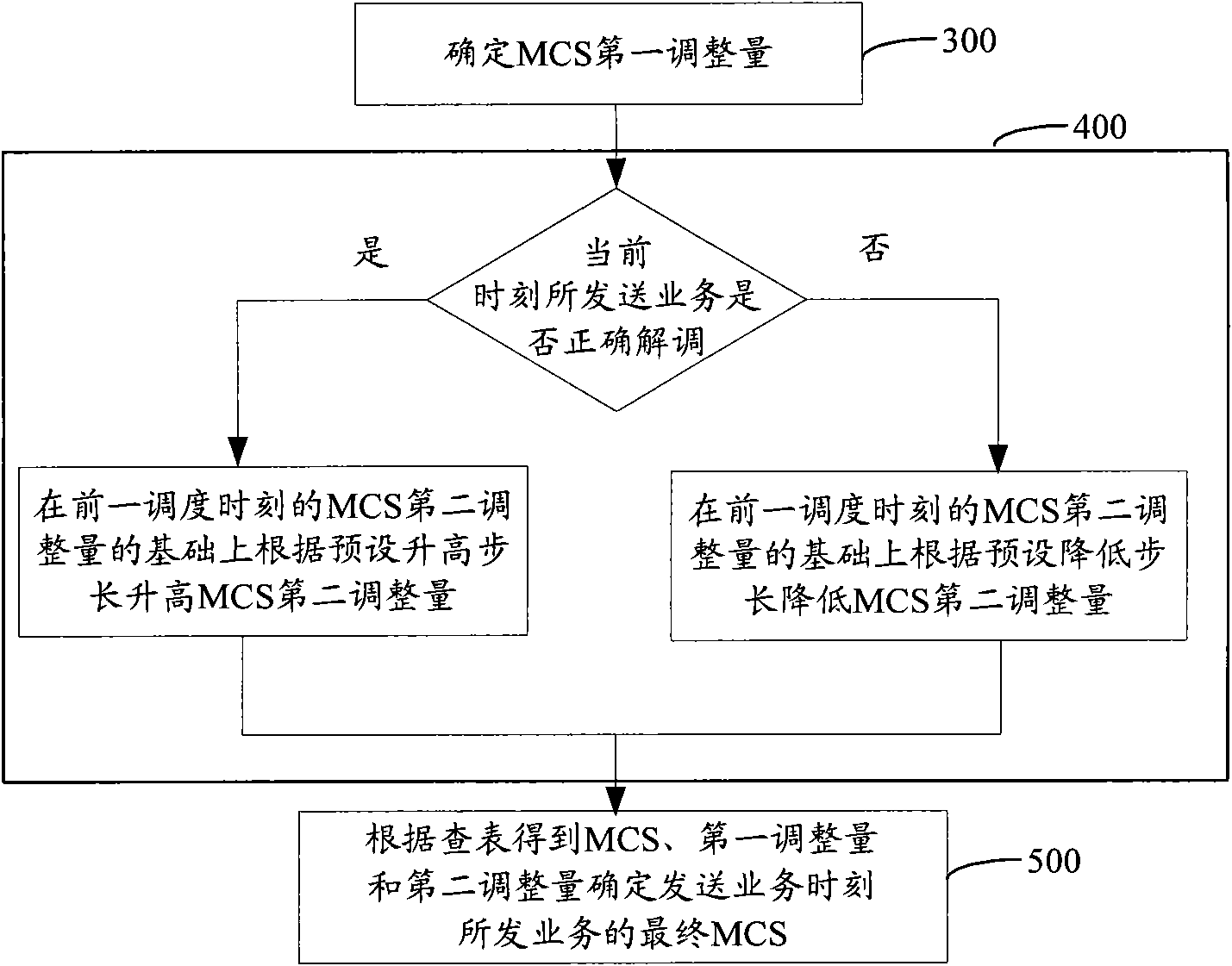
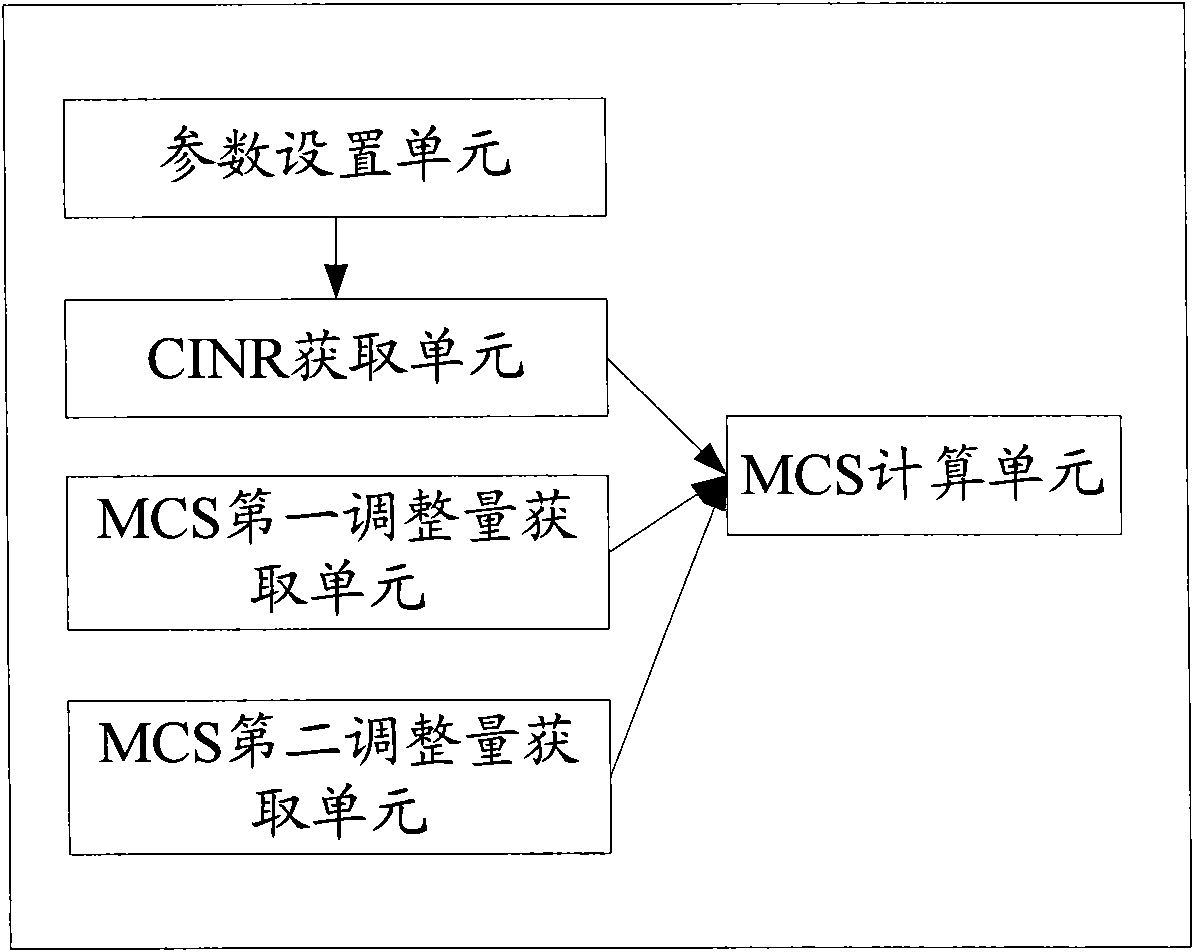
Adaptive modulation and coding method and device
InactiveCN102377513ASolve problems that cannot meet user QoS requirementsSolve power problemsNetwork traffic/resource managementAdaptation strategy characterisationQuality of serviceThroughput degradation
The invention provides an adaptive modulation and coding method and an adaptive modulation and coding device. The method comprises the following steps of: acquiring a carrier interference and noise ratio (CINR) at a moment when a service is to be sent and acquiring a modulation and coding scheme (MCS) by looking up a table; acquiring a second adjusting quantity of the MCS during determination of a first adjusting quantity of the MCS; and determining a final MCS of the service sent at the next scheduling moment by acquiring the MCS as well as the first adjusting quantity and the second adjusting quantity of the MCS by looking up the table. By the method and the device, the problems of a waste of power and reduction of throughput caused by oversmall BLER and the problem that a requirement of a user on the quality of service (QoS) cannot be met caused by overlarge BLER within a BLER calibration statistical interval in the prior art can be solved.
Owner:ZTE CORP
Invariance based concurrent error detection for the advanced encryption standard
ActiveUS8005209B2Public key for secure communicationSecret communicationTechnical standardThroughput degradation
Advanced Encryption Standard (AES) is an encryption algorithm for securing sensitive unclassified material by U.S. Government agencies and, as a consequence the de facto encryption standard for commercial applications worldwide. Performing concurrent error detection (CED) for protection of such a widely deployed algorithm is an issue of paramount importance. We present a low-cost CED method for AES. In this method, we make use of invariance properties of AES to detect errors. For the first time, the invariance properties of the AES, which are for the most part used to attack the algorithm, are being used to protect it from fault attacks. Our preliminary ASIC synthesis of this architecture resulted in an area overhead of 13.8% and a throughput degradation of 16.67%.
Owner:POLYTECHNIC INST OF NEW YORK
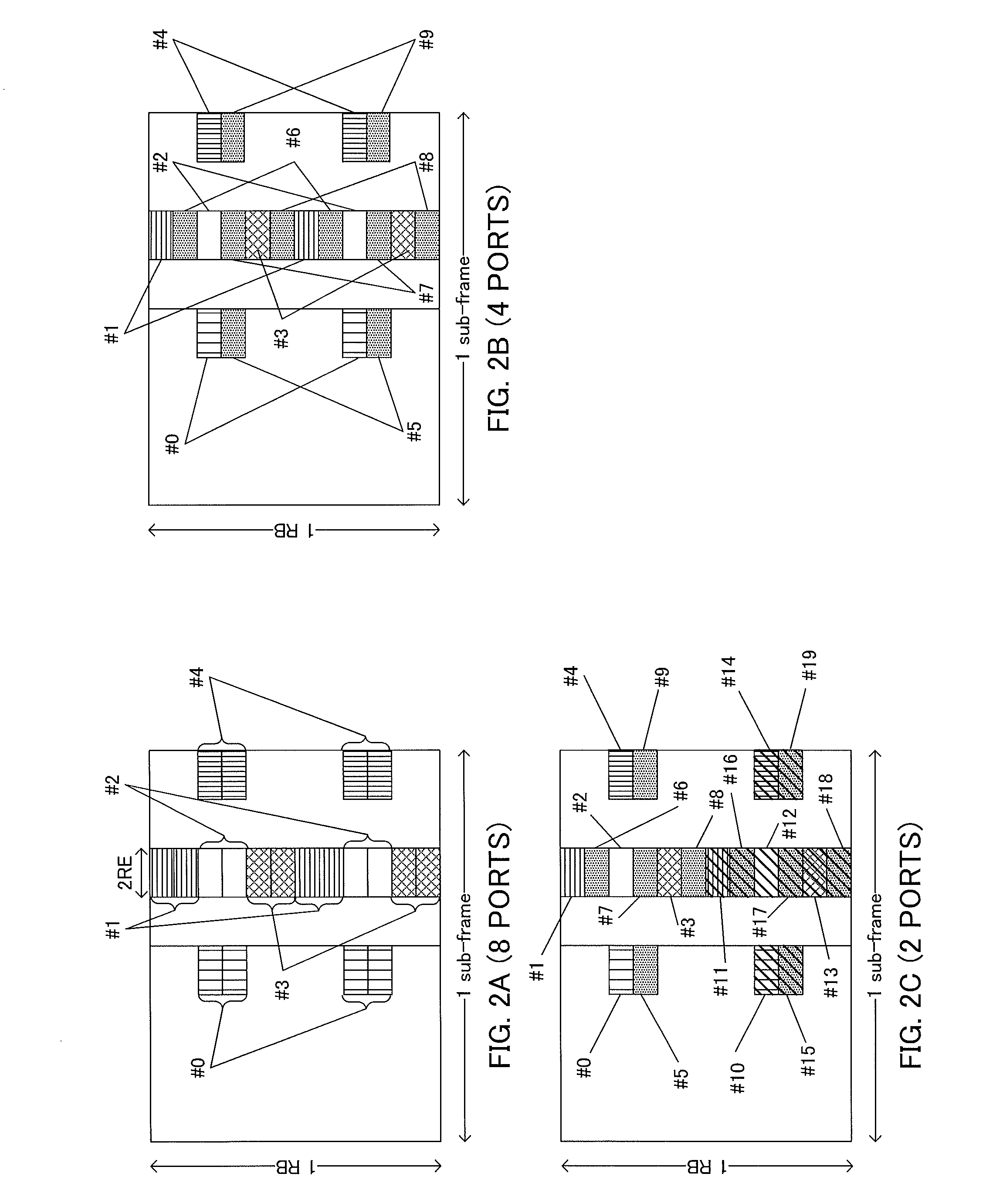
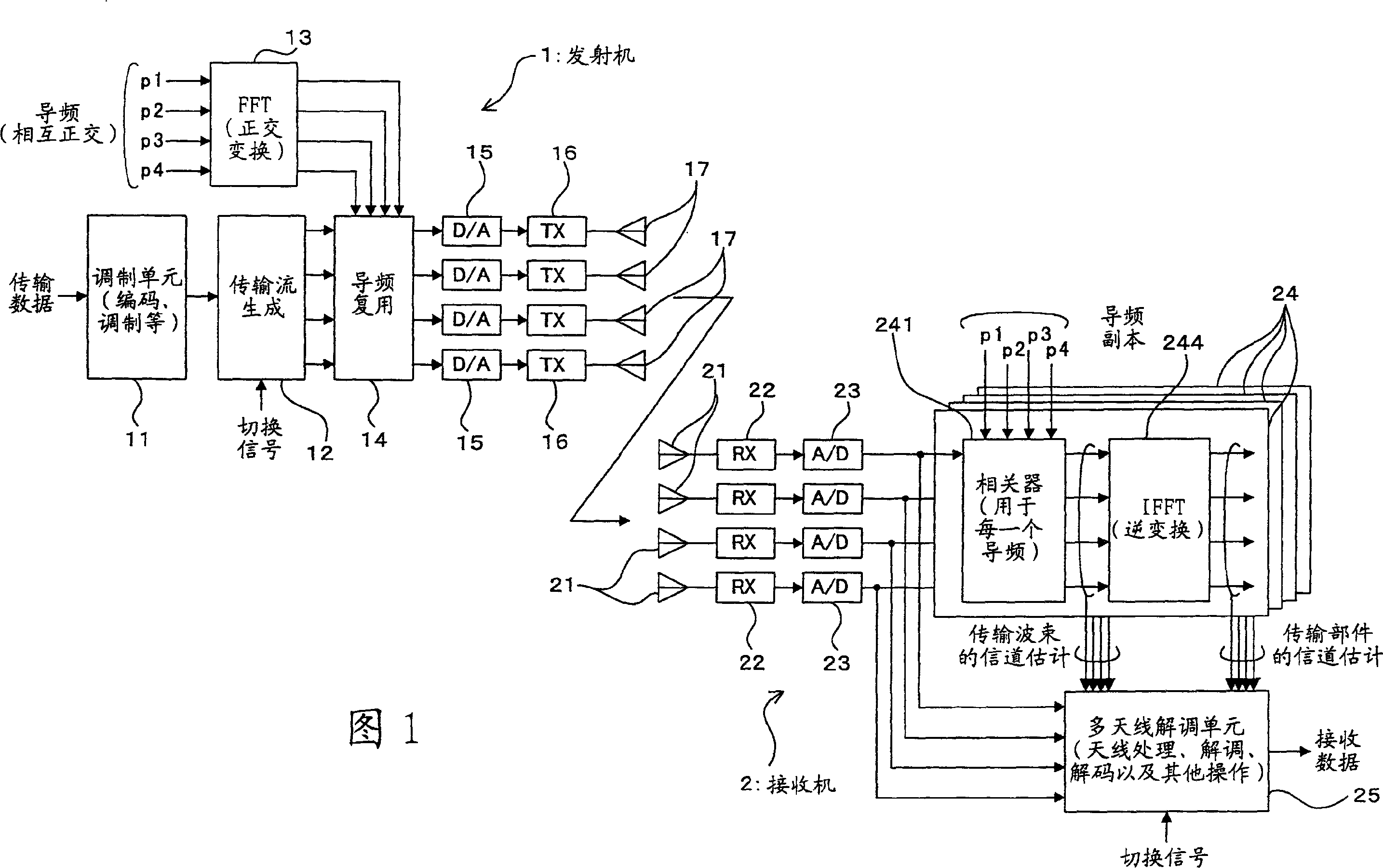
Radio communication system, radio communication method, radio transmitter and radio receiver using plurality of antennas
InactiveCN1893309AAvoid complicationsReduce transmission efficiencySpatial transmit diversityMultiplex communicationRadio receiver designMultiplexing
Owner:FUJITSU LTD
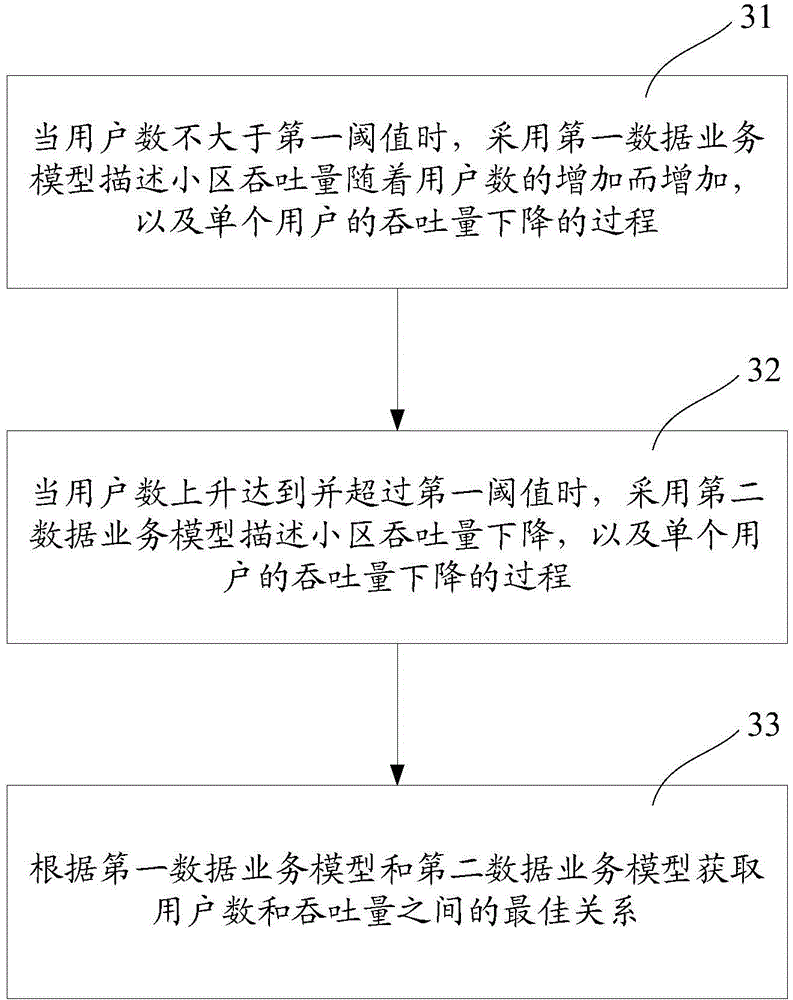
Method and device for establishing data service model
The embodiment of the invention provides a method and a device for establishing a data service model. The method comprises: when the number of users is not greater than a first threshold value, adopting a first data service model to describe the increase of cell throughput along with the increase of the number of the users, and to describe a process in which an individual user throughput decreases; when the number of the users increases and exceeds the first threshold value, adopting a second data service model to describe decrease of the cell throughput, and to describe the process in which the individual user throughput decreases; and acquiring the best relation between the number of the users and the throughput according to the first data service model and the second data service model. The data service model is established in a statistical manner, the Markov process is not used as the basis, and the model is proposed based on actual test results; meanwhile, parameters alpha and beta of the model can be corrected according to a scene, so that the model has a broader application range; and based on the data service model, the relation between the number of the users and the throughput is described and the maximum cell throughput is predicted.
Owner:CHINA MOBILE GROUP DESIGN INST
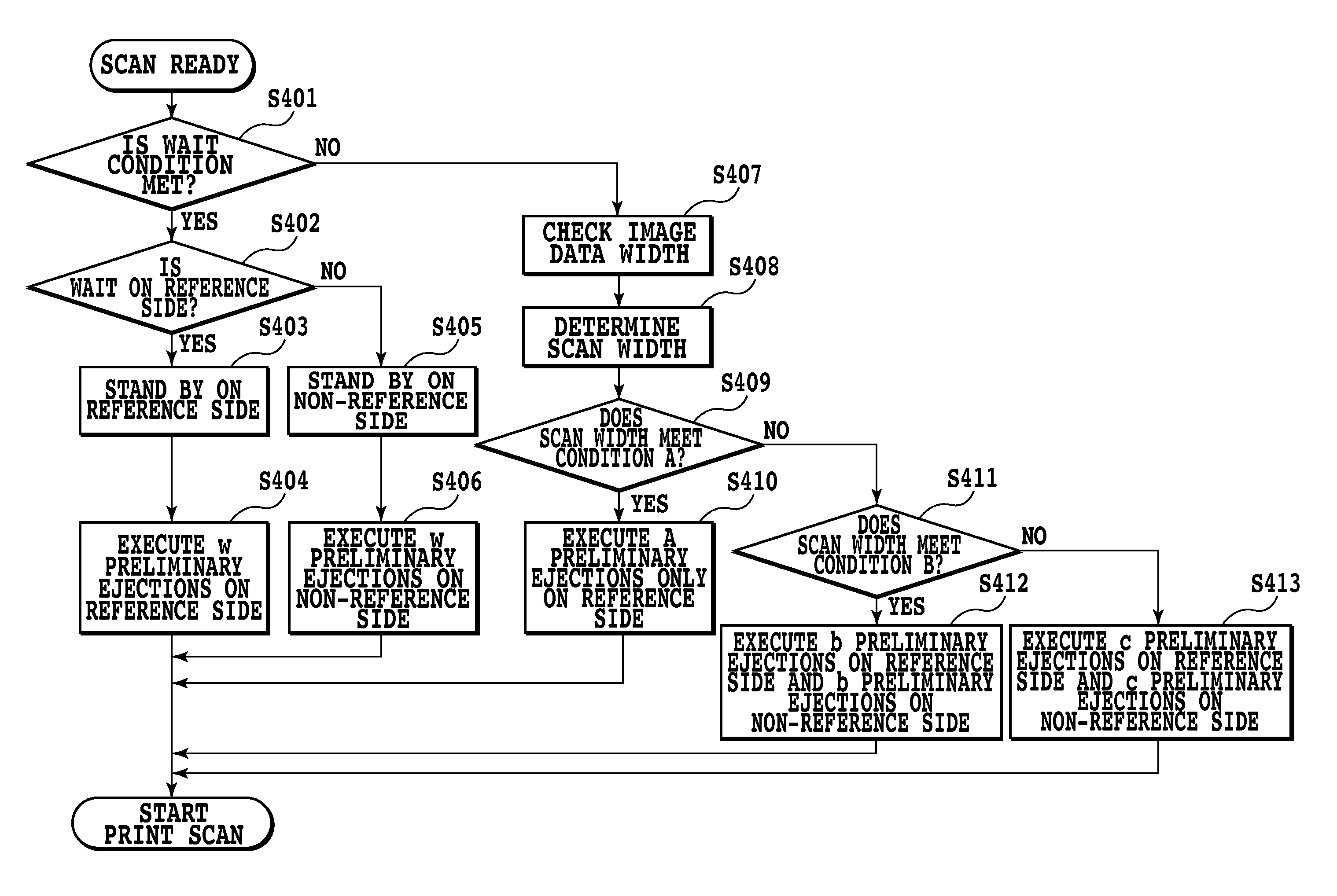
Inkjet printing apparatus and inkjet printing method
ActiveUS20100238222A1Minimizing throughput degradationThroughput degradation as smallPower drive mechanismsOther printing apparatusEngineeringThroughput degradation
An inkjet printing apparatus and an inkjet printing method are realized which can improve a print quality while minimizing the volume of waste ink, running cost and throughput degradations. For this purpose, the scan width is set according to the size and position of the print medium and then, based on that scan width, a location where the preliminary ejections are to be executed and the number of times that the preliminary ejection is to be executed in a single preliminary ejection session are determined.
Owner:CANON KK
Processing device, control method for a processing device, program, processing system and control method for a processing system
InactiveUS7866666B2Detection moreReduce loadDigital data processing detailsSensing record carriersThroughput degradationComputer science
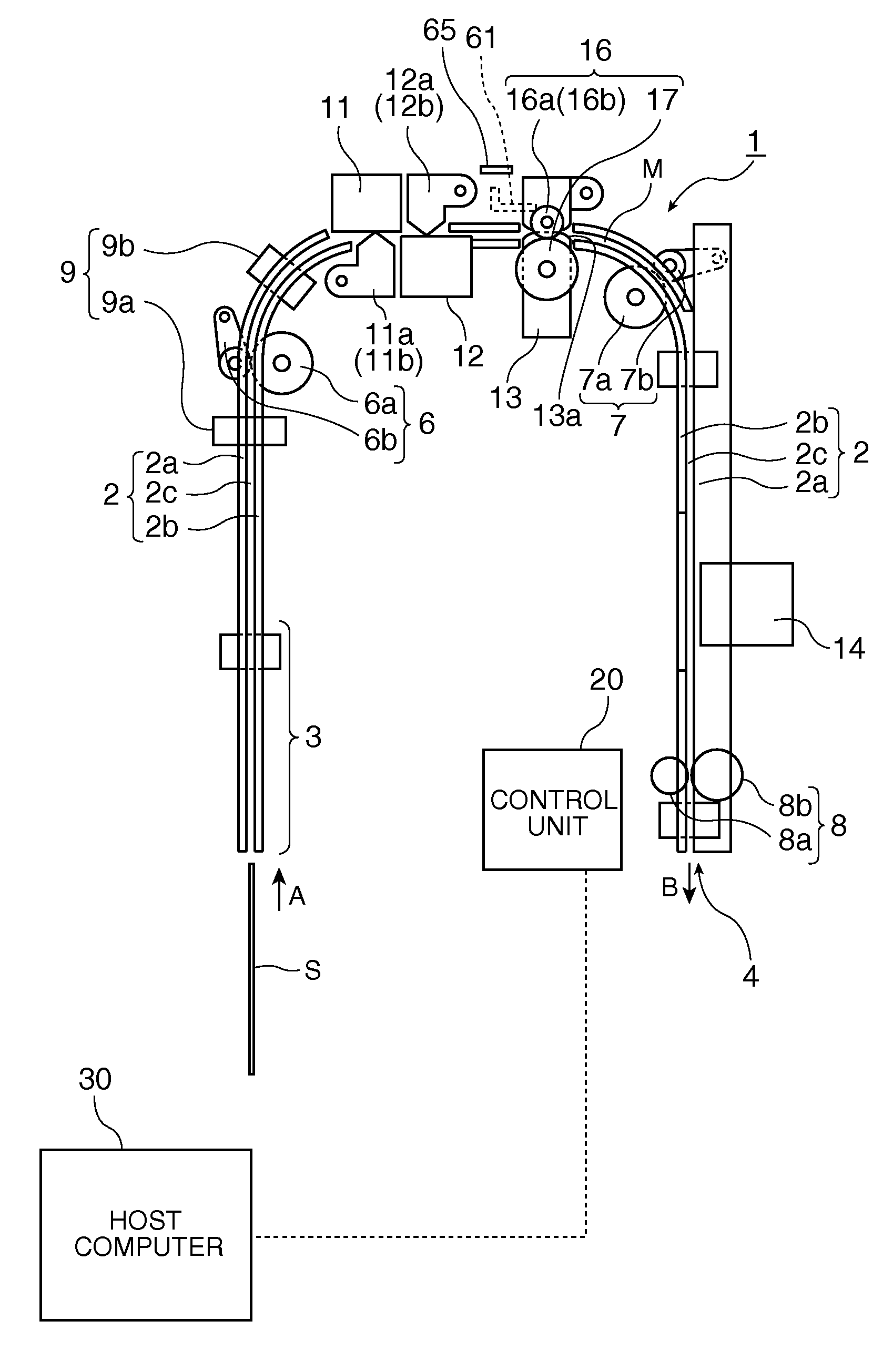
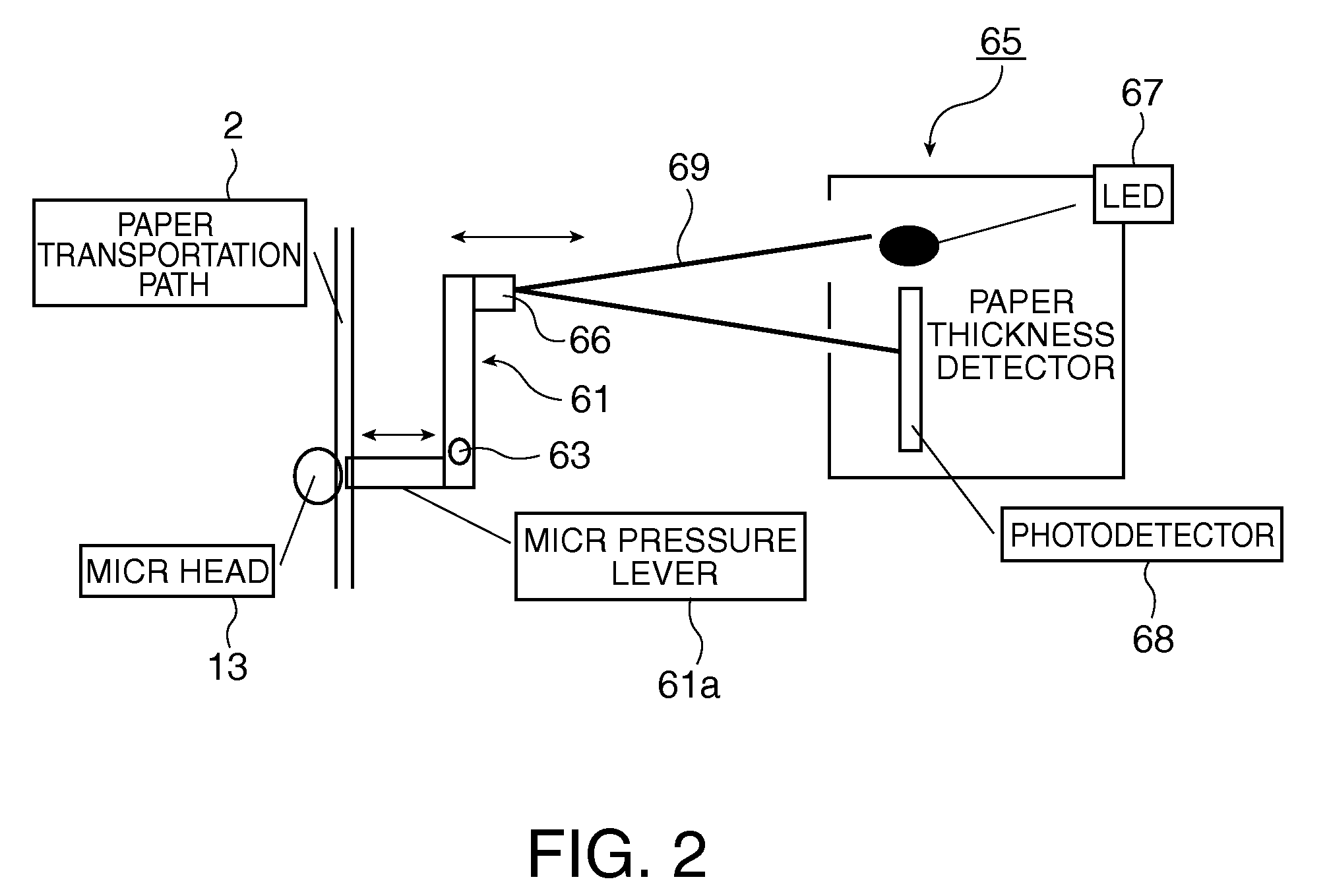
A hybrid processing system improves the reliability of multifeed detection even when plural different types of media are processed together without increasing the cost or size of the hybrid processing device due to increased performance, and without incurring a drop in throughput. In addition to image data captured from the processed media by an internal image reader, the hybrid processing device 1 also sends data for confirming multifeeding to the host computer 30. This multifeed confirmation data includes the result from a first multifeed detection process, the result from a second multifeed detection process, the paper length data detected by a paper length detection means 9, and the paper thickness data detected by a paper thickness detection means 65. The host computer 30 uses the image data and the multifeed confirmation data received from the hybrid processing device 1 to independently detect multifeeding, and thereby enables more reliable multifeed detection.
Owner:SEIKO EPSON CORP
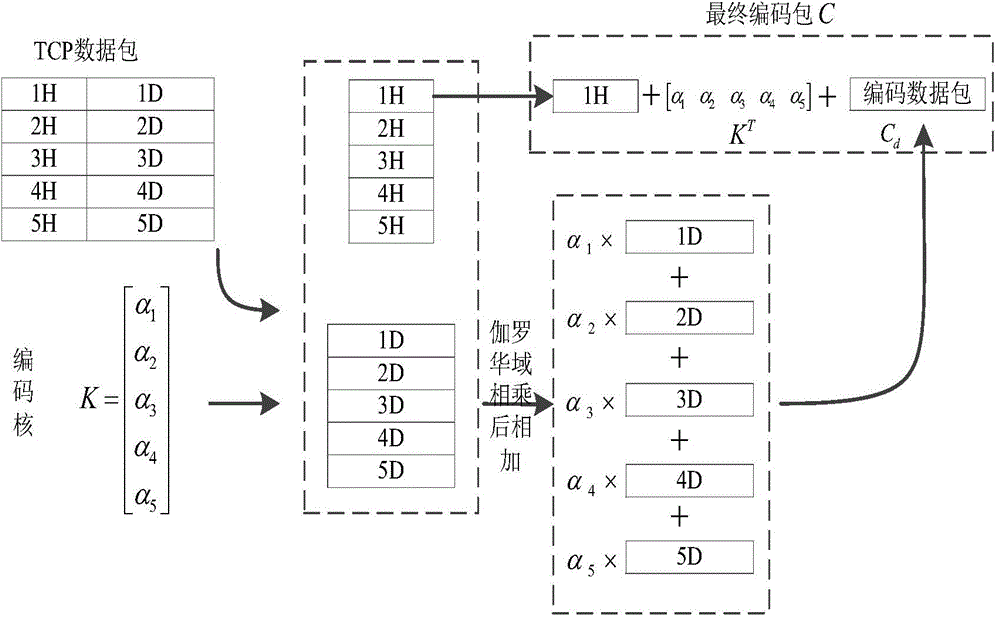
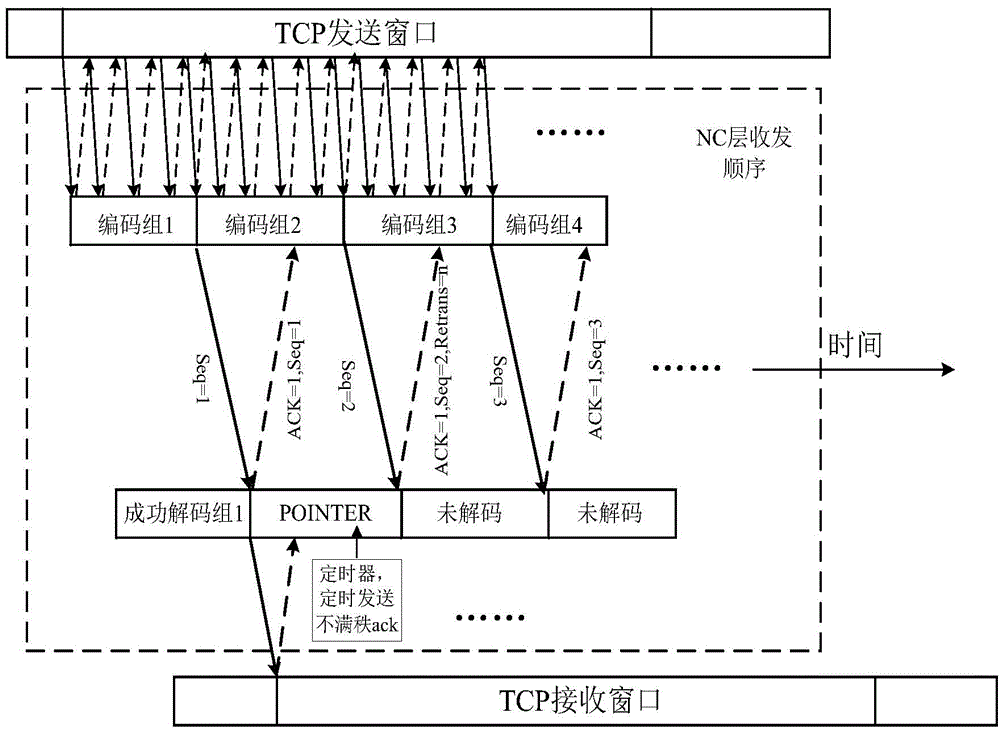
Transmission control method based on random linear network coding
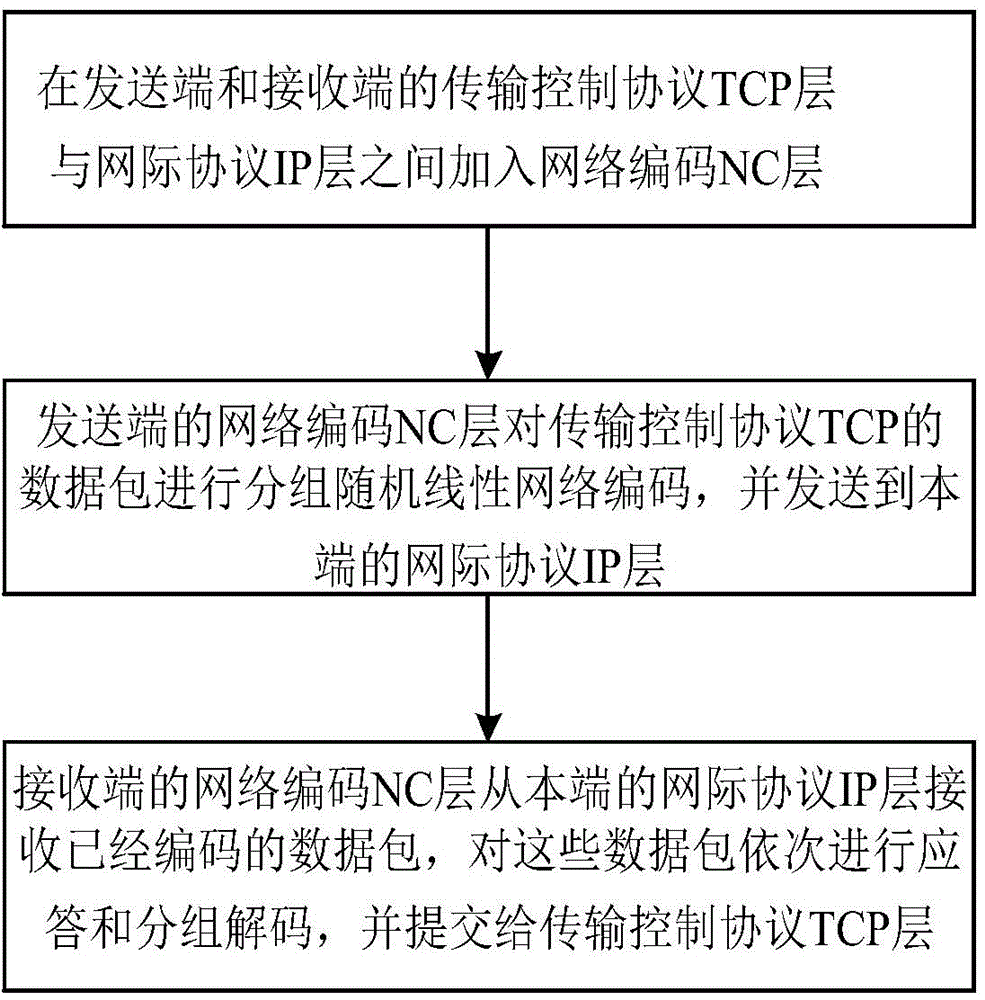
InactiveCN104683070AReduce complexityFast encodingError preventionInternet protocol suiteNetwork code
The invention discloses a transmission control method based on random linear network coding and mainly solves the problems of large time delay of a transmission control protocol (TCP) under a high-bit error rate link and decrease of throughput. The transmission control method comprises the following realization steps: (1) adding network coding (NC) layers between a transmission control protocol layer and an internet protocol (IP) layer which are respectively at the transmitting end and the receiving end; (2) performing grouping random linear network coding on data packets of the transmission control protocol through the network coding layer at the transmitting end and transmitting to the internet protocol layer at the local end; (3) receiving the coded data packets from the internet protocol layer at the local end through the network coding layer at the receiving end, wherein the data packets are subjected to response and grouping decoding in sequence and are submitted to the transmission control protocol layer. According to the transmission control method, the network throughout capacity under the high-bit error rate link is effectively improved, and the effect of round-trip delay of the link on the transmission control protocol performance is reduced.
Owner:XIDIAN UNIV
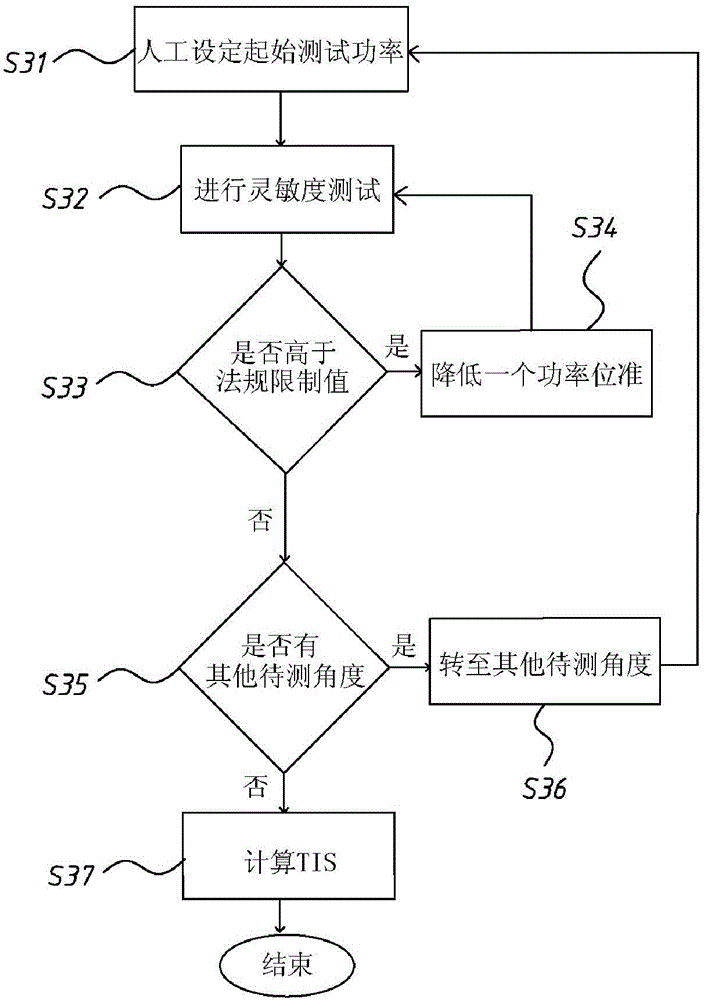
Method for accelerating measurement of mobile terminal total isotropic sensitivity
InactiveCN104158612ASimple test methodOmnidirectional sensitivityTransmission monitoringMoving averageTest power
The invention provides a method for accelerating the measurement of mobile terminal total isotropic sensitivity, and aims to shorten the conventional long and time-consuming tests. The method provided by the invention mainly comprises two stages. In the first stage, test power is estimated by an exponential moving average method, i.e. an in nite impulse response lter, which weights sensitivities measured by other points according to the distances of test points, and estimates the initial test power of each test point transmission terminal. In the second stage, a quick search method is used to search effective isotropic sensitivity in a quick degradation manner, thereby accelerating the search of the sensitivity of the point; and the maximum degradation interval is set to prevent connection breakage so as to prevent reconnection. If the throughput capacity drops too much, backtracking correction is carried out, so that the sensitivity of the point is obtained, and thereby the mobile terminal total isotropic sensitivity is calculated. The method provided by the invention can accelerate the measurement of the mobile terminal total isotropic sensitivity.
Owner:SPRING FOUND OF NCTU
Image forming device and controlling method thereof
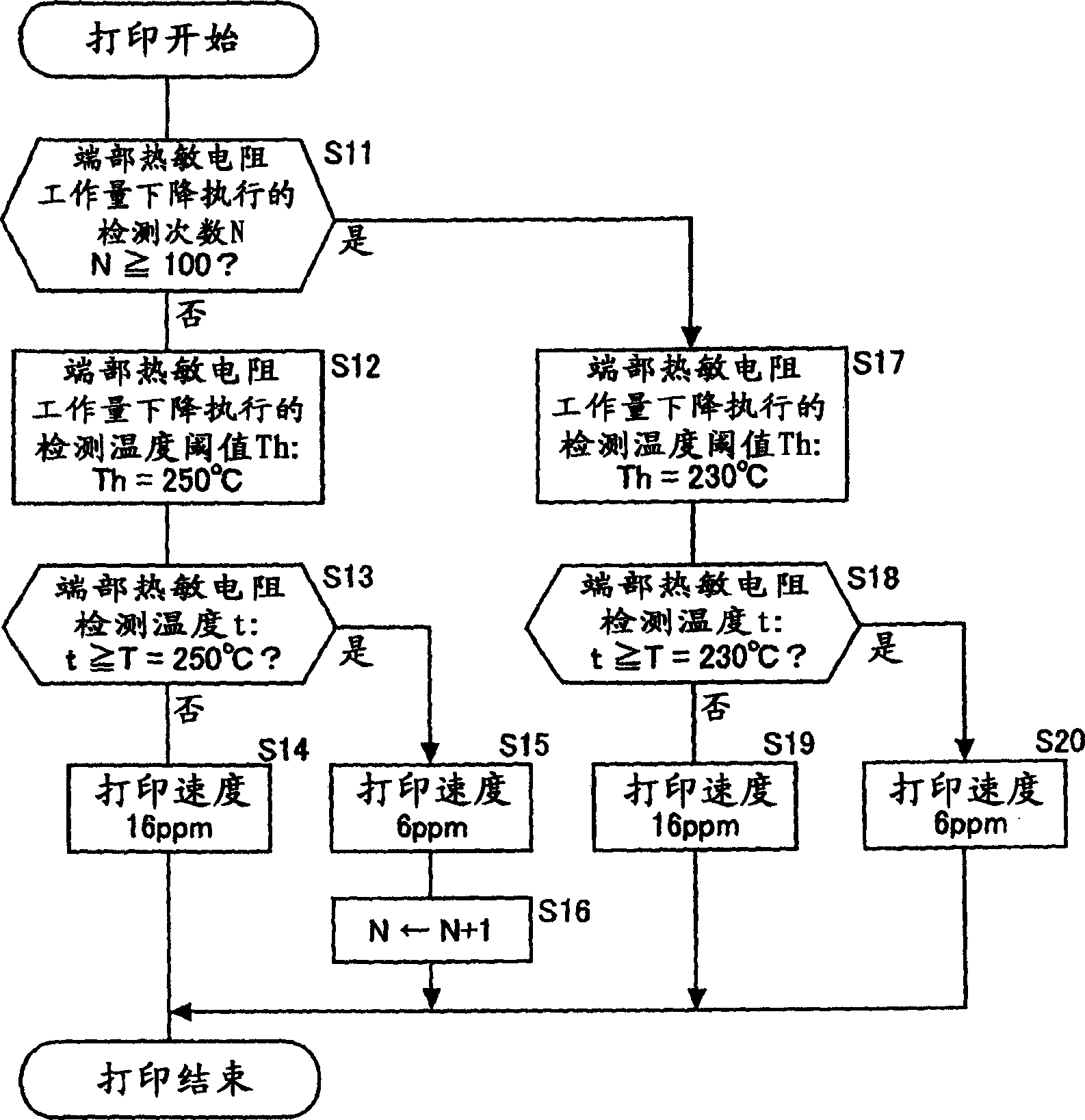
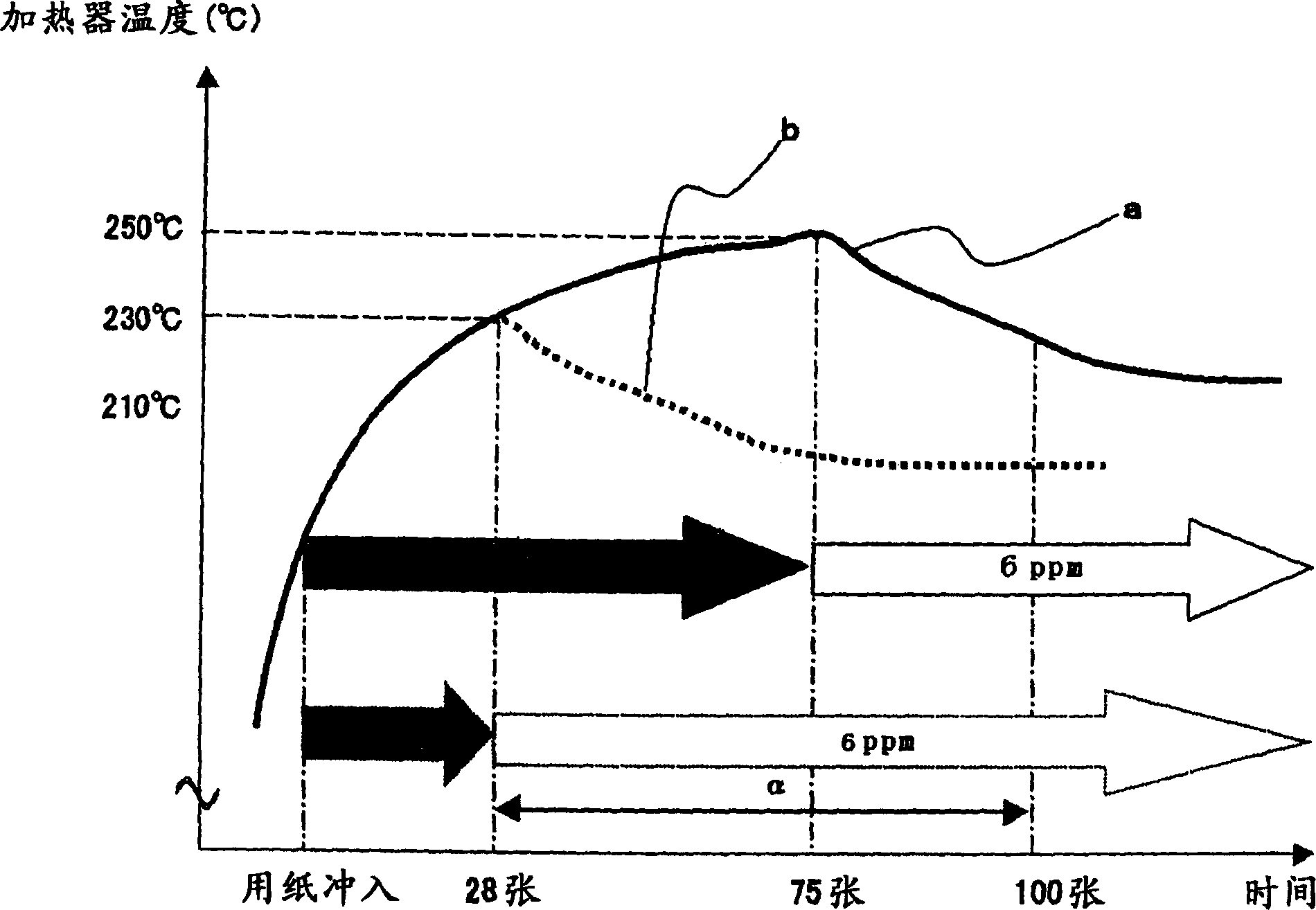
InactiveCN1770039APrevent overflowIncreased durabilityElectrographic process apparatusImage formationThroughput degradation
The detected temperature t at the end in the longitudinal direction of the heating body is compared with the threshold value Th, and the printing speed (throughput) is controlled based on the comparison result. The threshold Th is switched according to a predetermined condition. For example, it is used as the above-mentioned predetermined condition that the number of throughput reduction executions for which the printing speed reduction switching has been performed reaches a predetermined value. Alternatively, whether or not the small-size passing paper ratio is greater than a predetermined value is used as the above-mentioned predetermined condition. This prevents the lubricant from overflowing, prevents the sliding properties of the fixing film and the heating body from deteriorating, prevents the paper from being unable to be conveyed, generates sliding noise, and causes poor fixing, thereby improving the durability of the fixing device.
Owner:COPYER
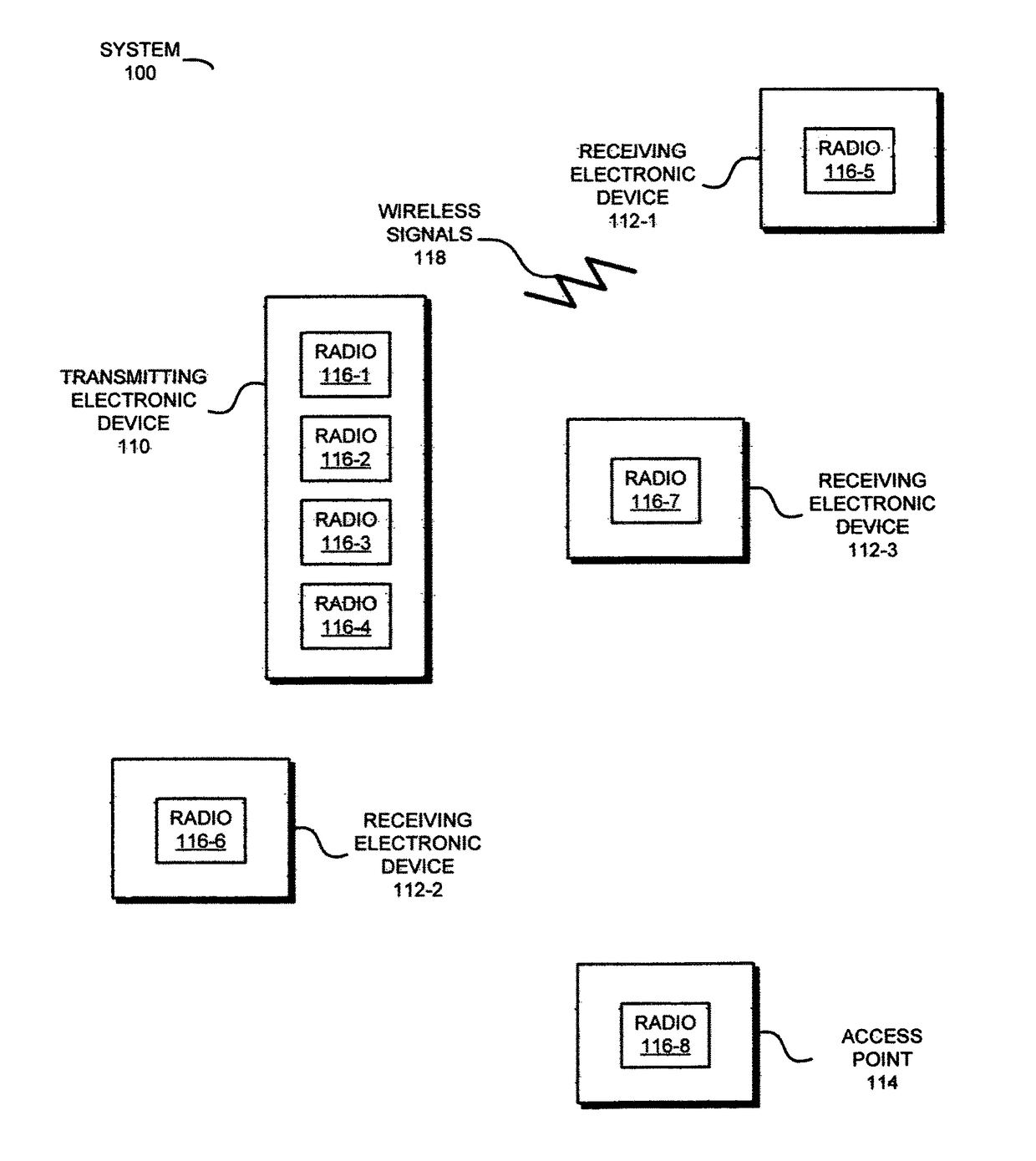
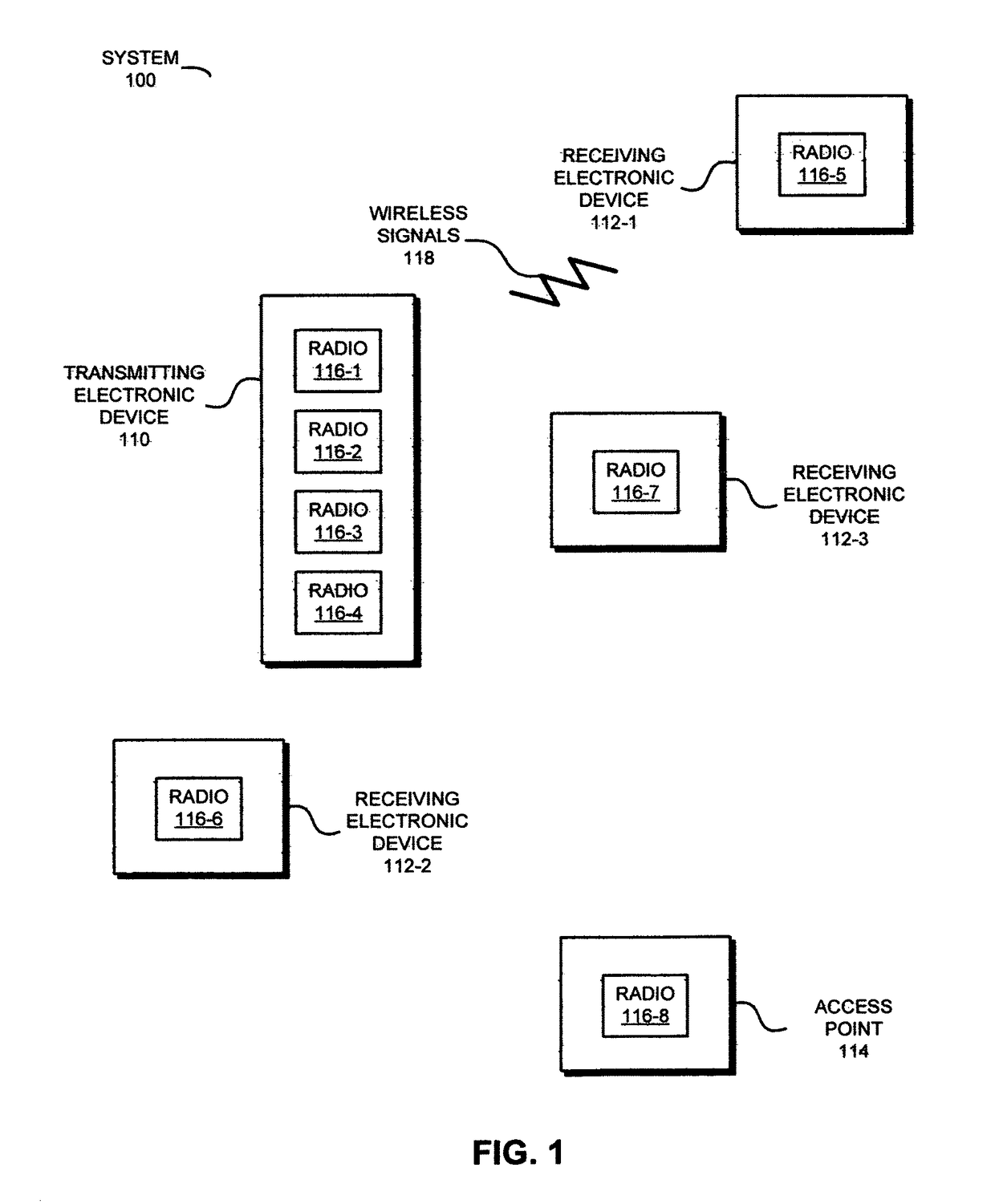
Redundant links for reliable communication
In order to maintain performance during wireless communication, a transmitting electronic device may concurrently and independently communicate redundant information to a receiving electronic device. In particular, information associated with a data stream may be communicated to the receiving electronic device using one or more channels by two radios using one or more wireless local area network communication protocols. The packets transmitted by the radios may preferentially include the same information. Moreover, the transmitting electronic device may attempt to maintain the redundant communication if a performance metric associated with the one or more channels degrades. For example, the transmitting electronic device may transfer communication to a different channel or may compress the information in the packets in the one or more channels if the throughput drops below a threshold value. Furthermore, the concurrent communication may allow the transmitting electronic device determine link quality without disrupting the communication of the information.
Owner:B & W GRP LTD
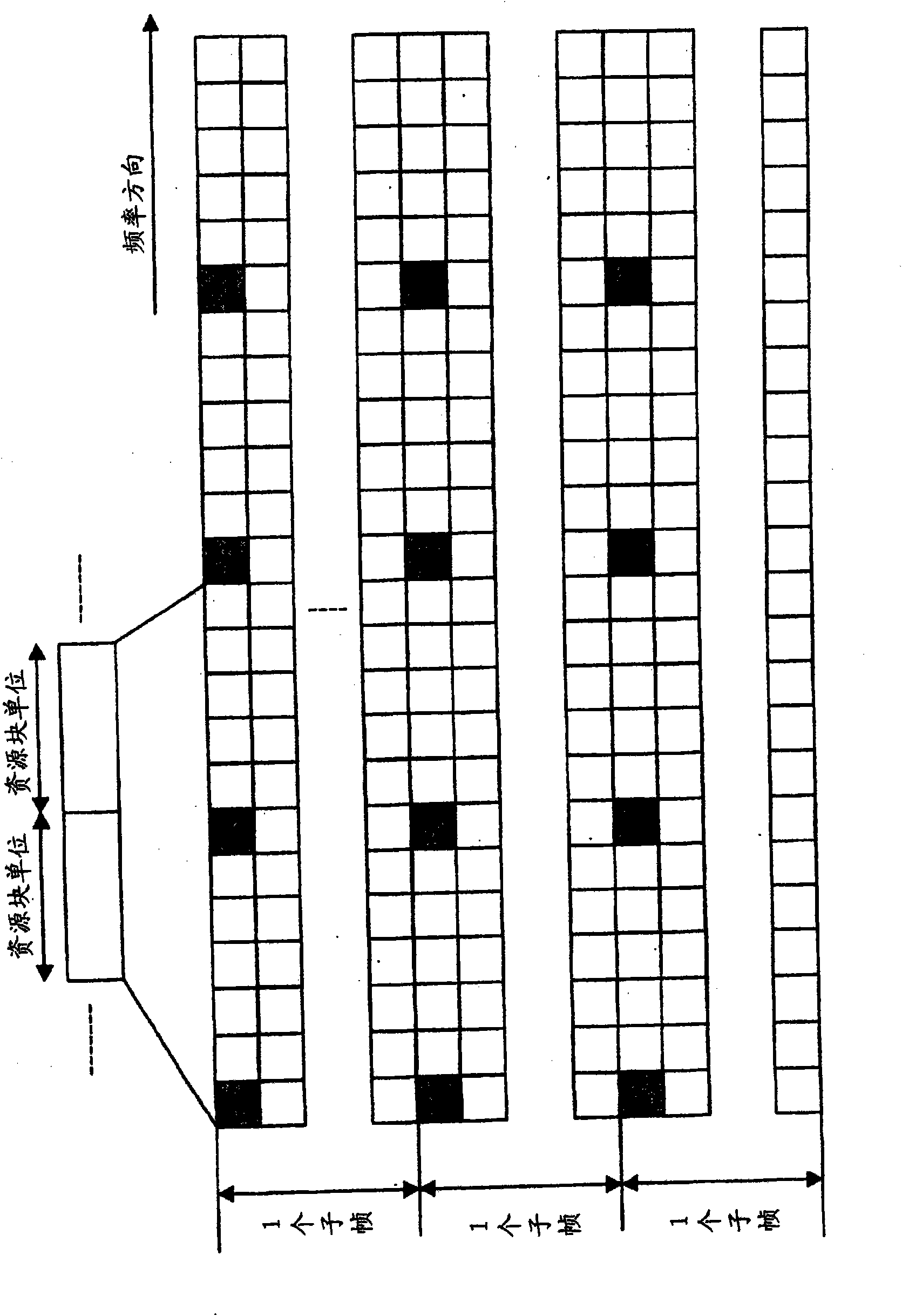
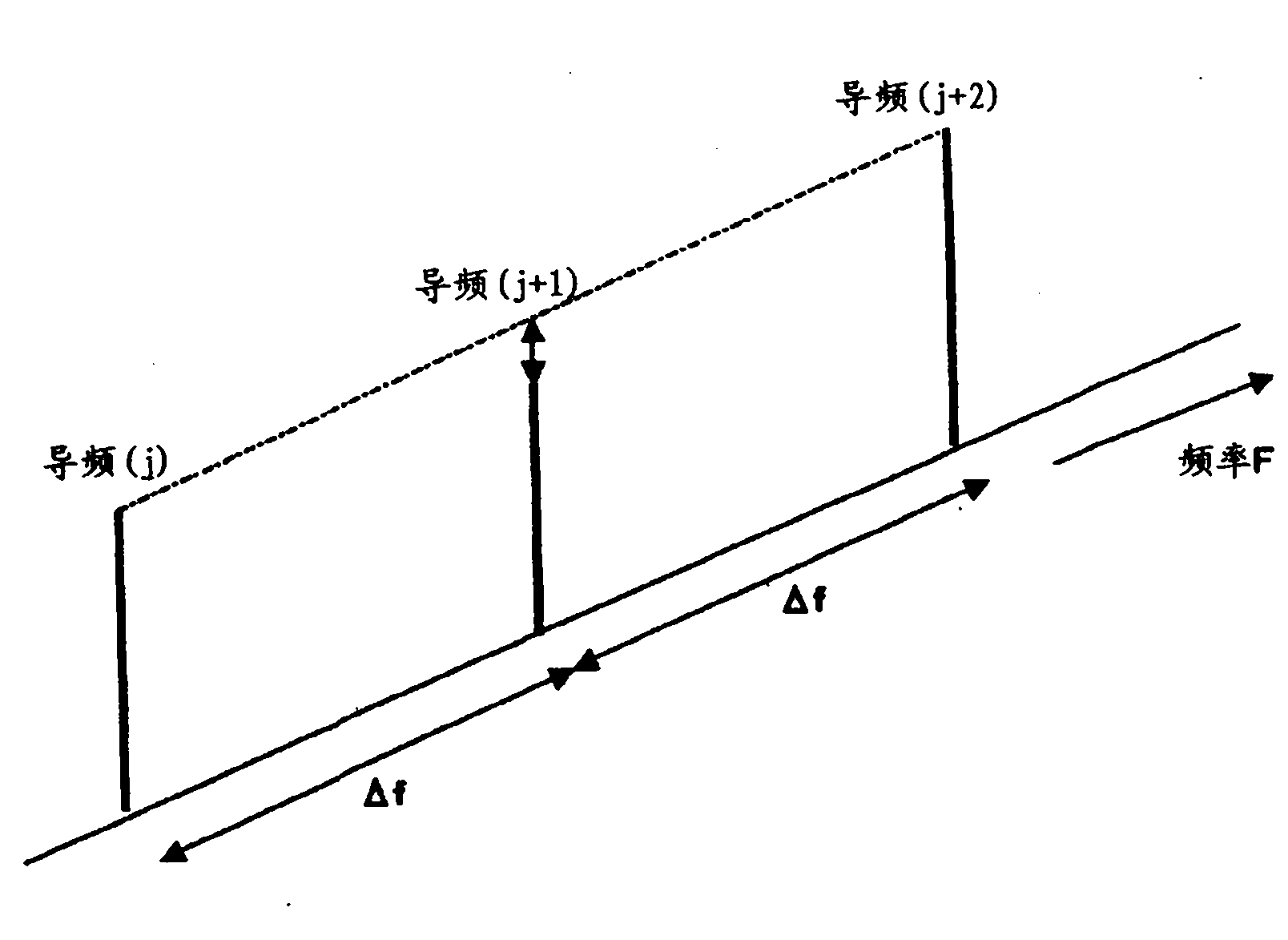
Pilot arrangement method in a mobile radio communication system and transmitter receiver set applied in the method
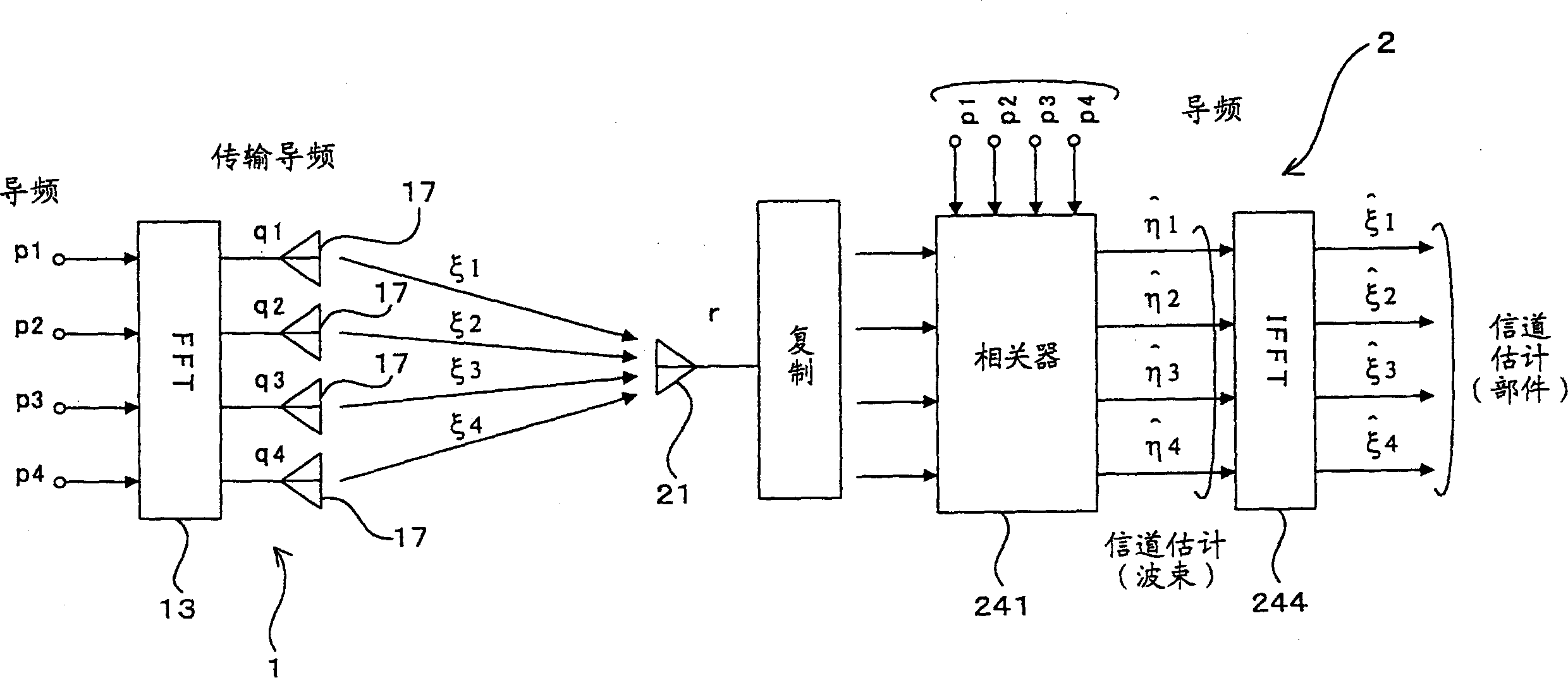
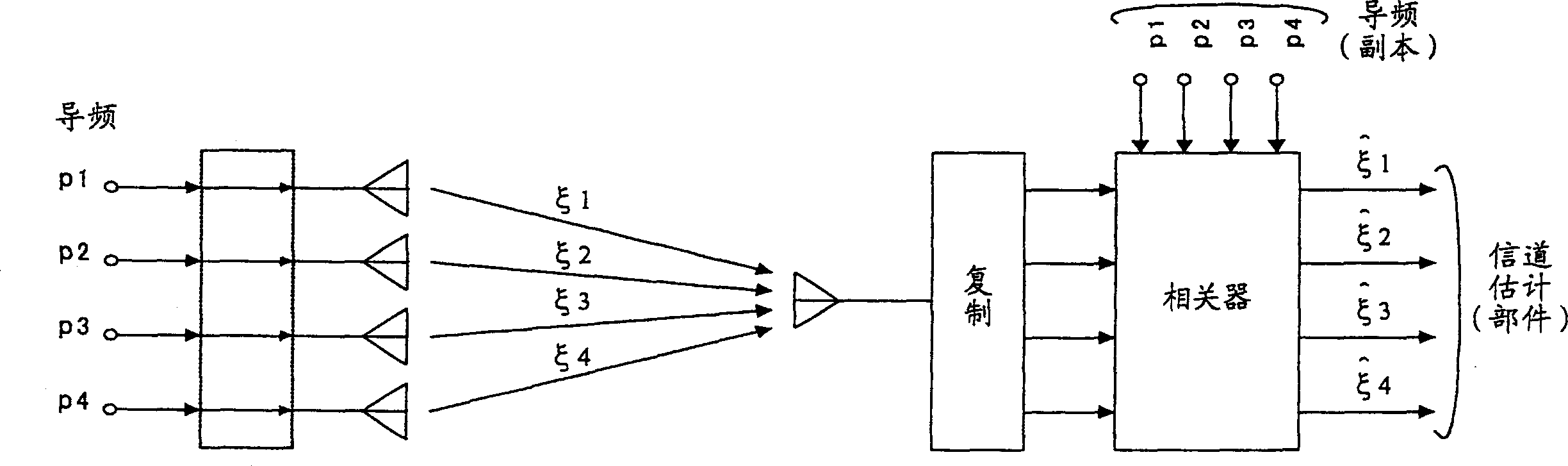
ActiveCN101772913AImprove estimation accuracyReduce throughputTransmission path divisionTime-division multiplexCommunications systemReference intervals
Owner:FUJITSU LTD
Transmission terminal and transmission method
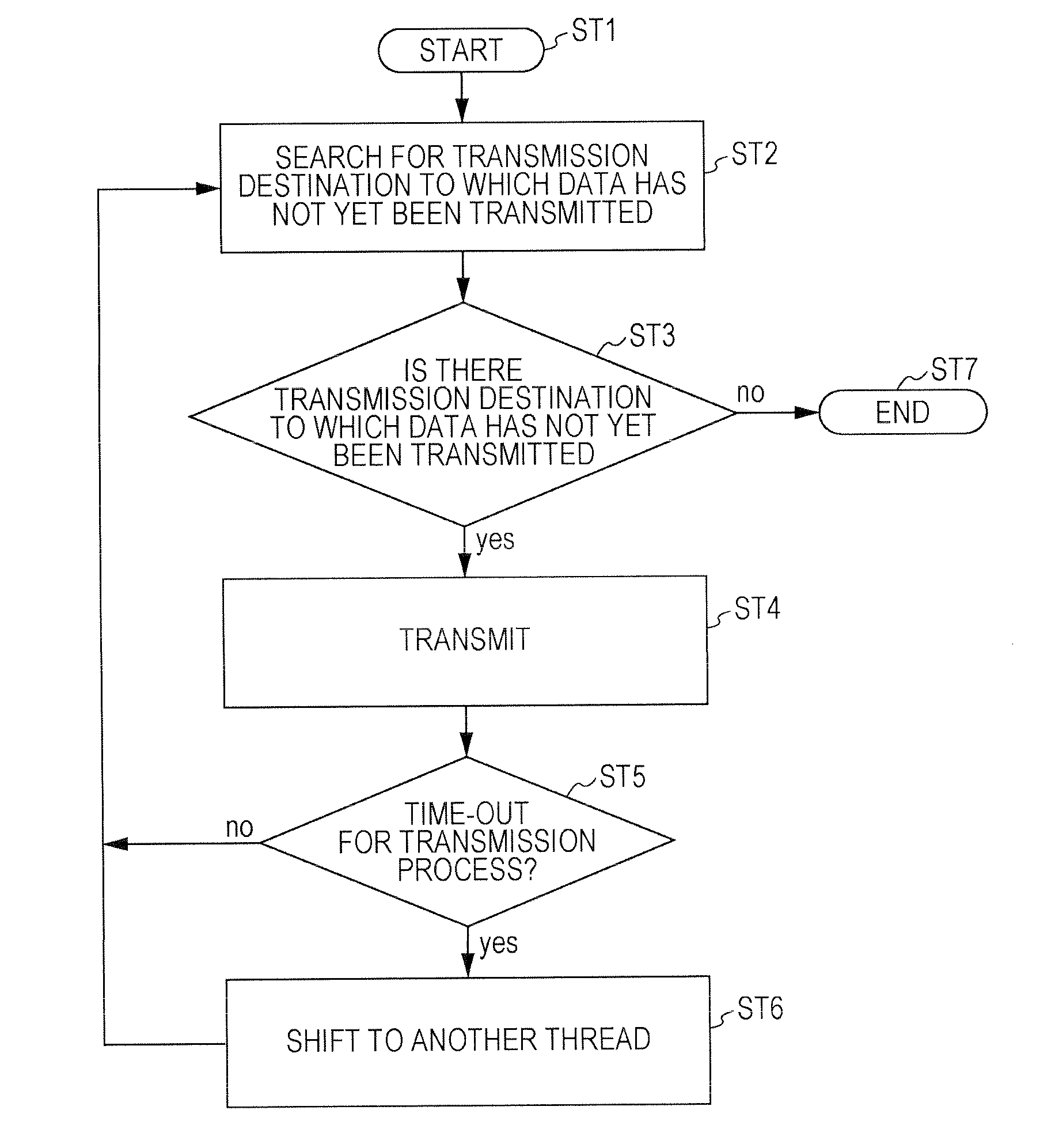
InactiveUS20130028078A1Improve carrying capacityError preventionTransmission systemsDistribution systemMultiple point
To realize a state in which a decrease in throughput at one place does not affect other transmission destinations while preventing CPU load from becoming high.The present technology can be applied to a multiple point distribution system that transmits a video stream to a plurality of transmission destinations by using a transport protocol having a congestion control mechanism, such as TCP. A transmission terminal transmits the video stream in the same thread (first thread) with respect to receiving terminals A and C in which throughput is sufficient, and transmits the video stream in another thread (second thread) with respect to a receiving terminal B in which throughput has decreased. As a result of adopting such a transmission method, a decrease in throughput for the receiving terminal B does not affect transmission to the receiving terminals A and C. Furthermore, transmission is not performed to the receiving terminals A, B, and C in mutually different threads, and an increase in the number of threads, thus, an increase in CPU load, can be suppressed.
Owner:SONY CORP
Transmitting apparatus and transmitting method
InactiveCN1860754APrevention of deterioration of error rate characteristicsPrevent throughput degradationError prevention/detection by using return channelPhase-modulated carrier systemsThroughput degradationData mining
A transmitting apparatus capable of preventing the error rate characteristic from degrading and of preventing the throughput from degrading due to repetition of retransmittals. In the apparatus, a mapping decision part (103) decides to perform a normal constellation mapping at a first transmission and decides to change the constellation mapping positions or change bit mapping of symbols in accordance with the number of times of retransmittal at a retransmittal. A data interchanging part (105) interchanges the transmitted data for each bit on a symbol-by-symbol basis such that the data are arranged in the bit mapping decided by the mapping decision part (103). A mapper part (106) maps the transmitted data, which are inputted from the data interchanging part (105), onto each symbol such that the data are arranged in the constellation mapping position decided by the mapping decision part (103).
Owner:OPTIS WIRELESS TECH LLC
Ad hoc network cooperative relay method based on distributed space-time coding
InactiveCN101951641AReduce latencyImprove connectivityNetwork traffic/resource managementNetwork topologiesPhysical layerThroughput degradation
The invention discloses an Ad hoc network cooperative relay method based on distributed space-time coding, which mainly solves the problems that in the prior art, when the network is relatively sparse or has larger loads, the delay is increased and the throughput is lowered. The method comprises the following steps of: (1) for an physical layer of an Ad hoc network, restraining the length of a control packet to acquire a communication range specially used for sending the control packet; (2) in the communication range of the control packet, computing the even-hop shortest path and the odd-hop shortest path between every two nodes by a routing layer according to adjacent nodes searched by each node; and (3) according to the even-hop shortest path and the odd-hop shortest path, selecting the next hop to a destination node as a relay node by an MAC layer, sending the control packet to invite the relay node to participate in three-point cooperation, selecting the next hop to the destination node as a receiving node by the relay node, and finishing the data transmission in a distributed space-time coding manner. The invention can improve the network throughput and reduce the delay, and can be applied to the field of cooperative communication.
Owner:XIDIAN UNIV
Radio interrogator system and radio communication method therefor
InactiveUS20070057770A1Reduce throughputMemory record carrier reading problemsSubscribers indirect connectionTelecommunicationsOperation mode
There is provided a radio interrogator system which reduces the interference with a radio transponder and avoids the decrease in throughput of the entire system in a case in which a plurality of radio interrogators are disposed at positions brought relatively close to each other and are simultaneously placed into operation. The plurality of radio interrogators are classified into two groups and each of the radio interrogators has an operation mode setting unit capable of exclusively setting, for each of the classified groups, a transmission mode for transmitting a radio transmission signal to a radio transponder or a reception mode for receiving a radio response signal transmitted from the radio transponder as a response to a radio transmission signal from the radio interrogator.
Owner:FUJITSU LTD
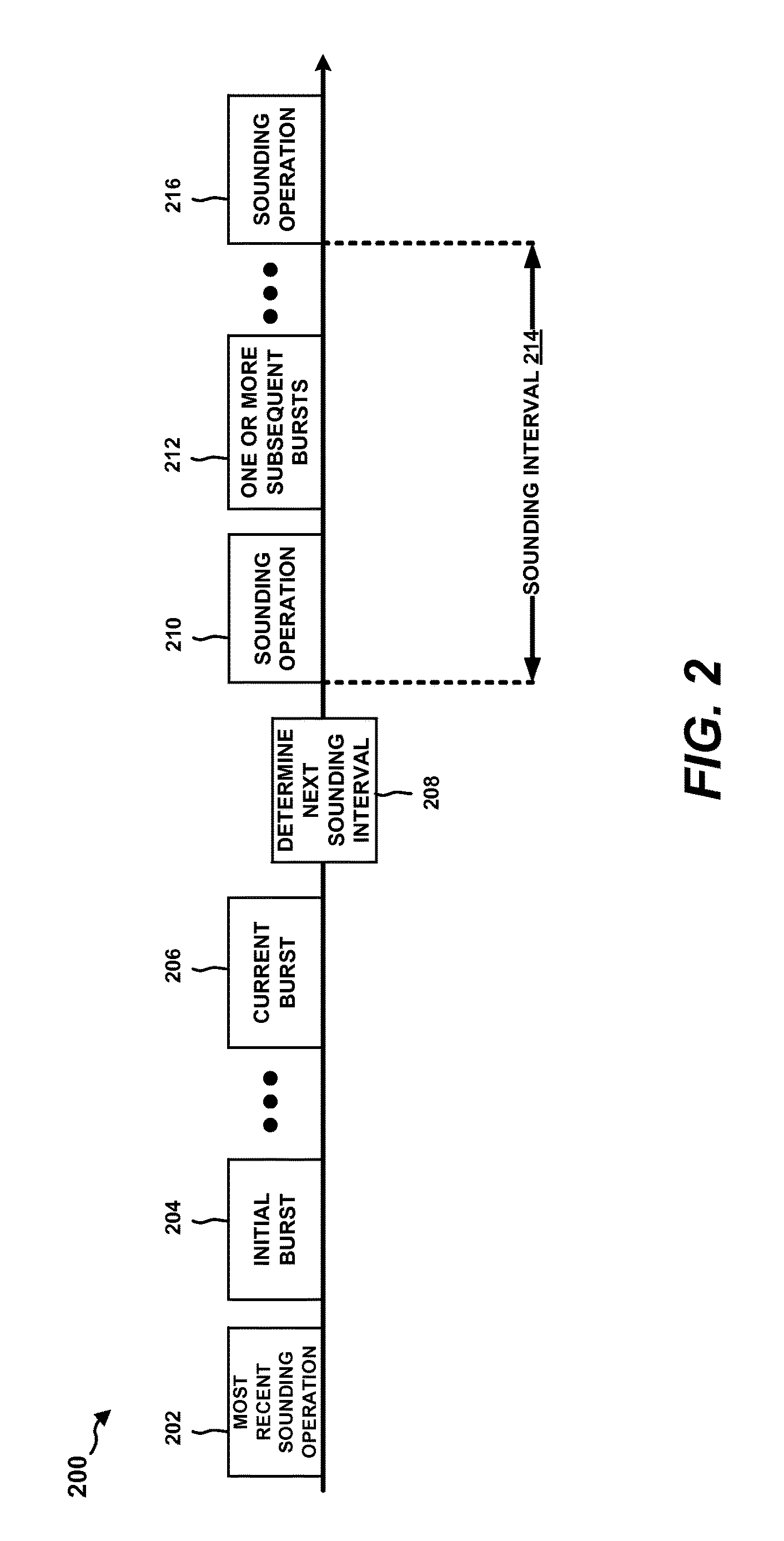
Techniques for managing sounding intervals of a wireless communications device
InactiveUS20170033950A1Improved sounding interval selectionBaseband system detailsSignalling characterisationTelecommunicationsThroughput degradation
Various aspects are provided for managing a sounding interval of a wireless communications device, which may include setting a timing of one or more channel sounding operations performed by the communications device. For instance, a method is provided for channel sounding management. This example method may include obtaining information regarding a modulation and coding scheme (MCS) or a throughput degradation gradient associated with one or more transmissions. In addition, the example method may include determining a timing of one or more sounding operations based on the information regarding the MCS or the throughput degradation gradient. Additionally, apparatuses and computer-readable media are provided for channel sounding management in a communications device, which are configured to perform, or store computer-executable code to perform, the disclosed example methods.
Owner:QUALCOMM INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com