Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
3595results about How to "Increase consumption" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
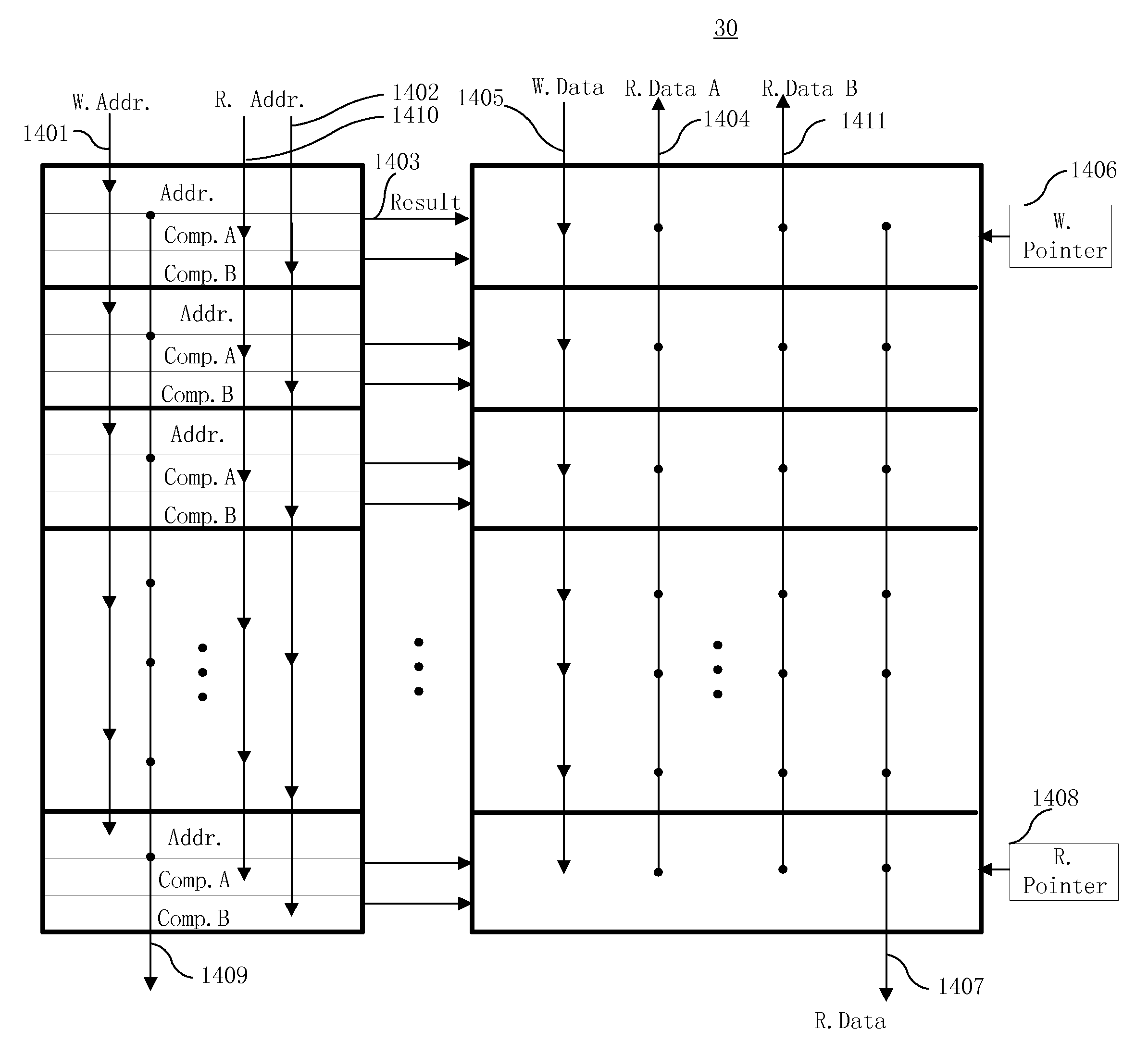
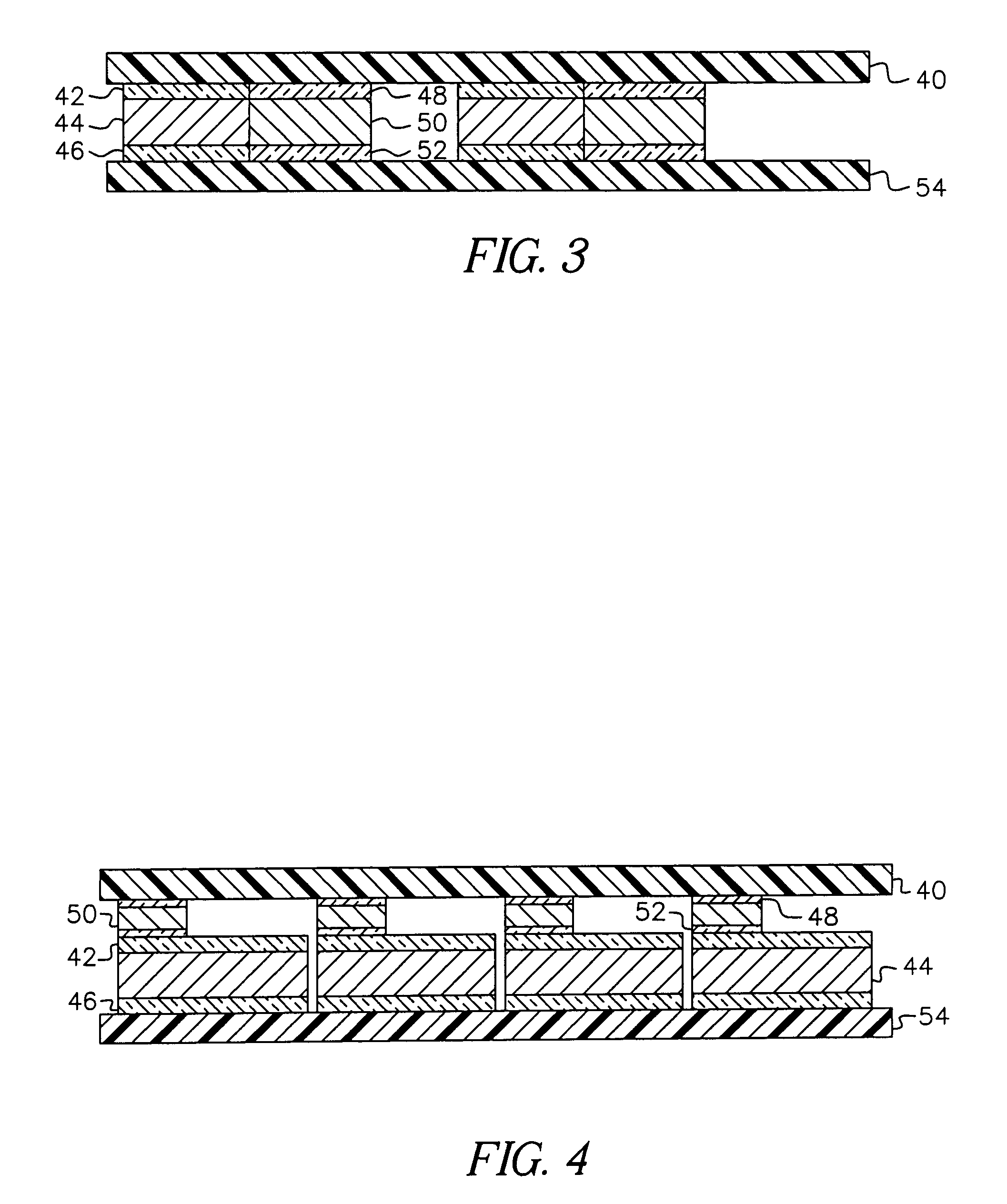
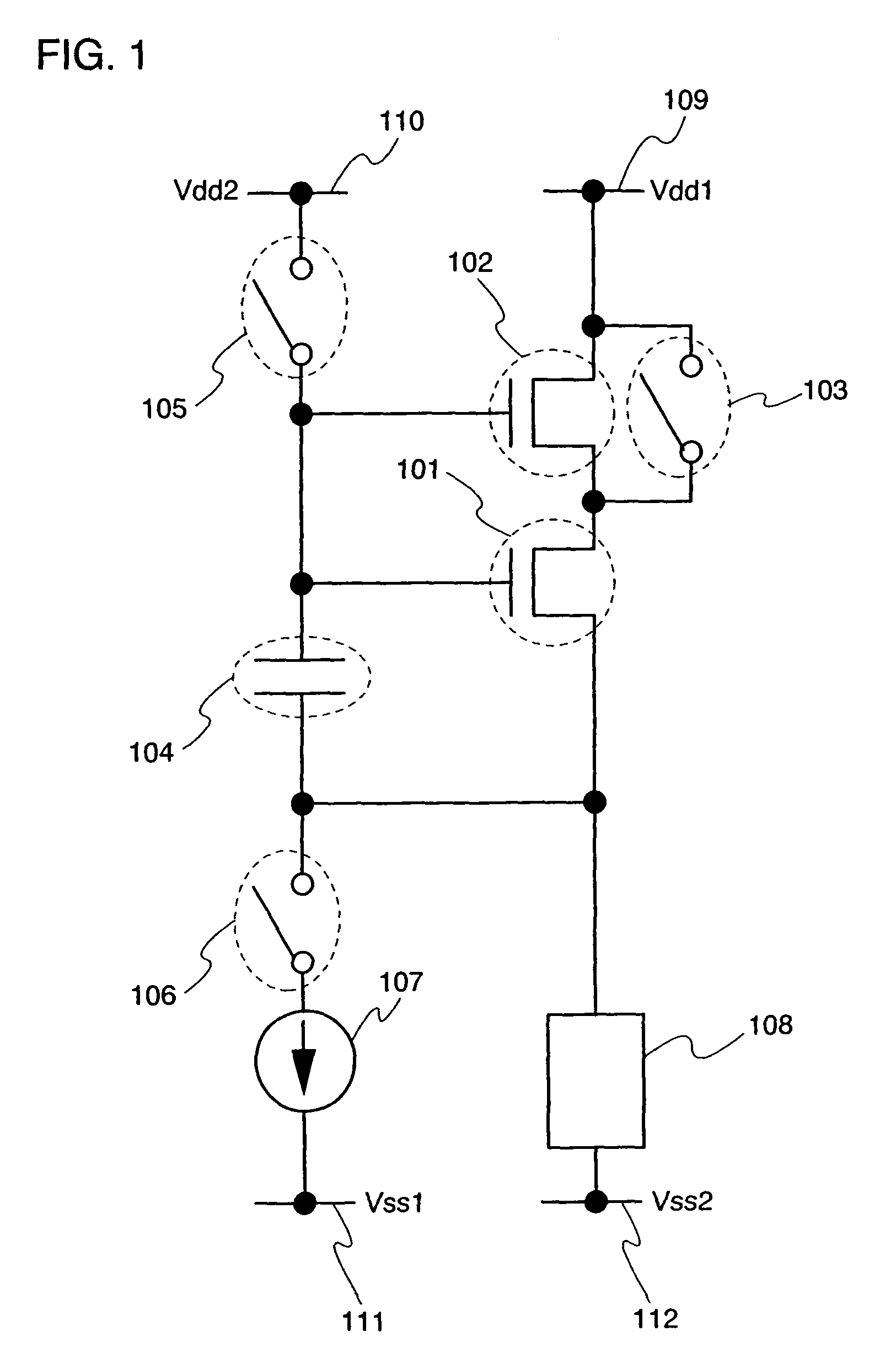
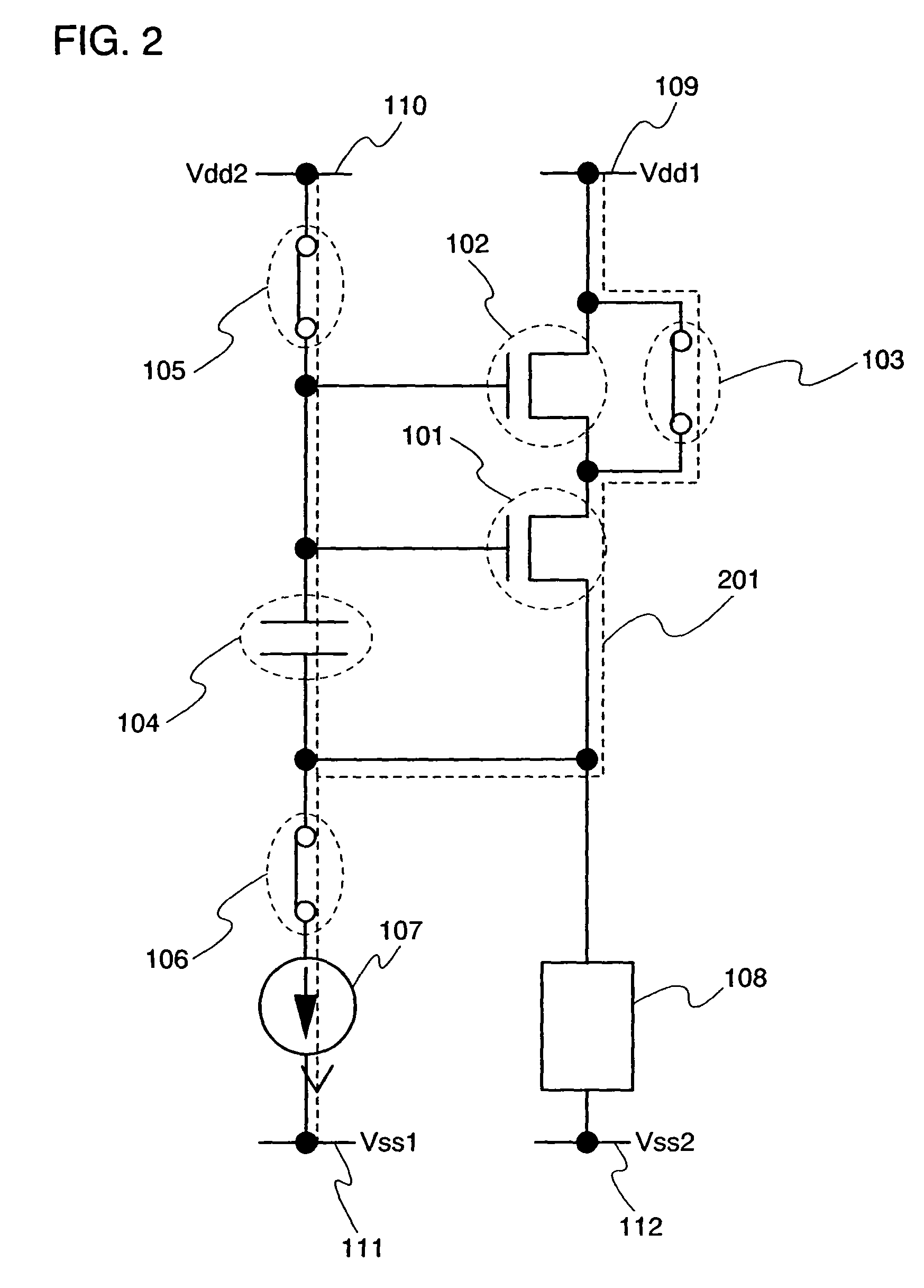
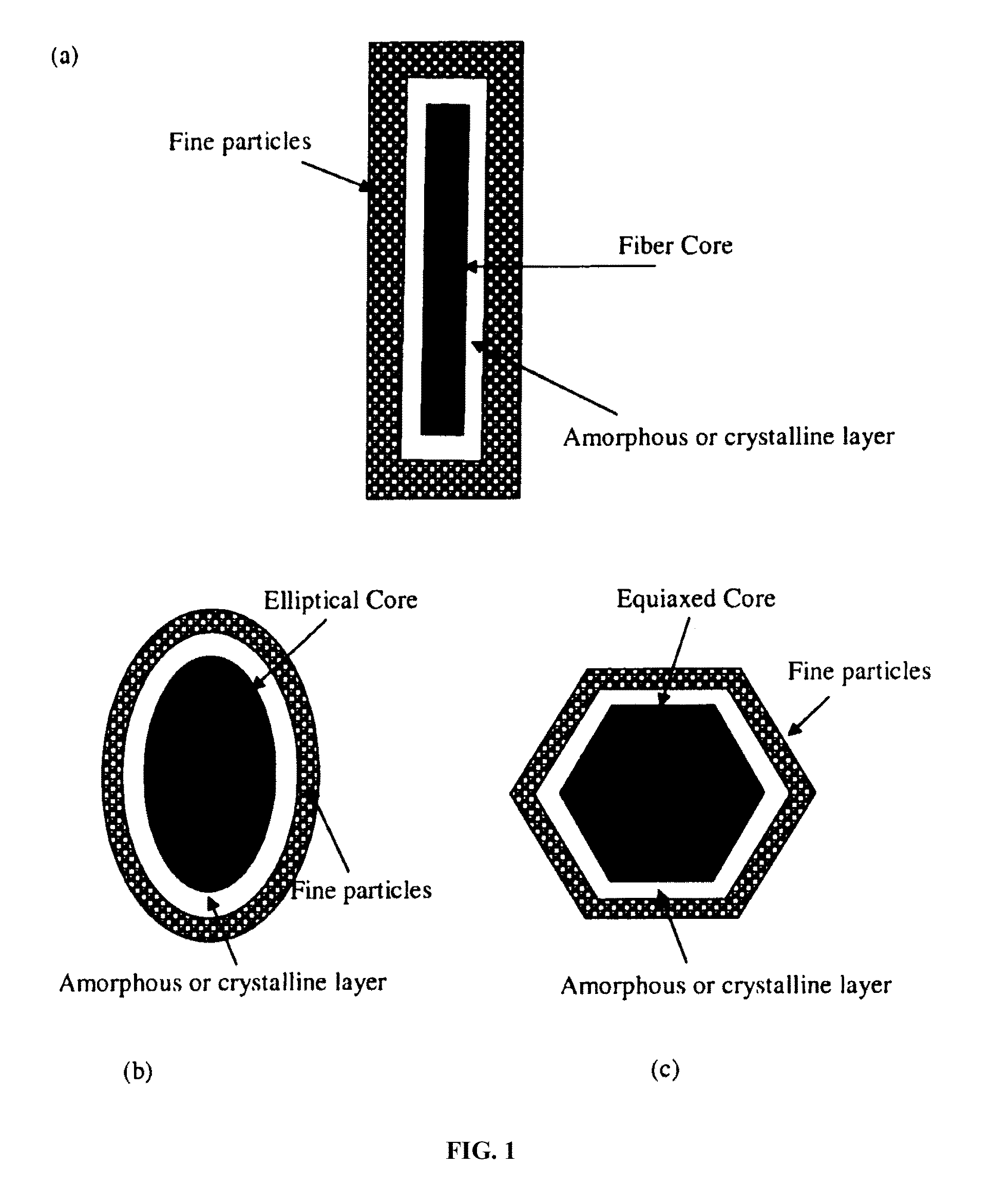
Processor-cache system and method
ActiveUS9047193B2Shorten the counting processEfficient and uniform structureEnergy efficient ICTRegister arrangementsAddress generation unitProcessor register
A digital system is provided. The digital system includes an execution unit, a level-zero (L0) memory, and an address generation unit. The execution unit is coupled to a data memory containing data to be used in operations of the execution unit. The L0 memory is coupled between the execution unit and the data memory and configured to receive a part of the data in the data memory. The address generation unit is configured to generate address information for addressing the L0 memory. Further, the L0 memory provides at least two operands of a single instruction from the part of the data to the execution unit directly, without loading the at least two operands into one or more registers, using the address information from the address generation unit.
Owner:SHANGHAI XINHAO MICROELECTRONICS
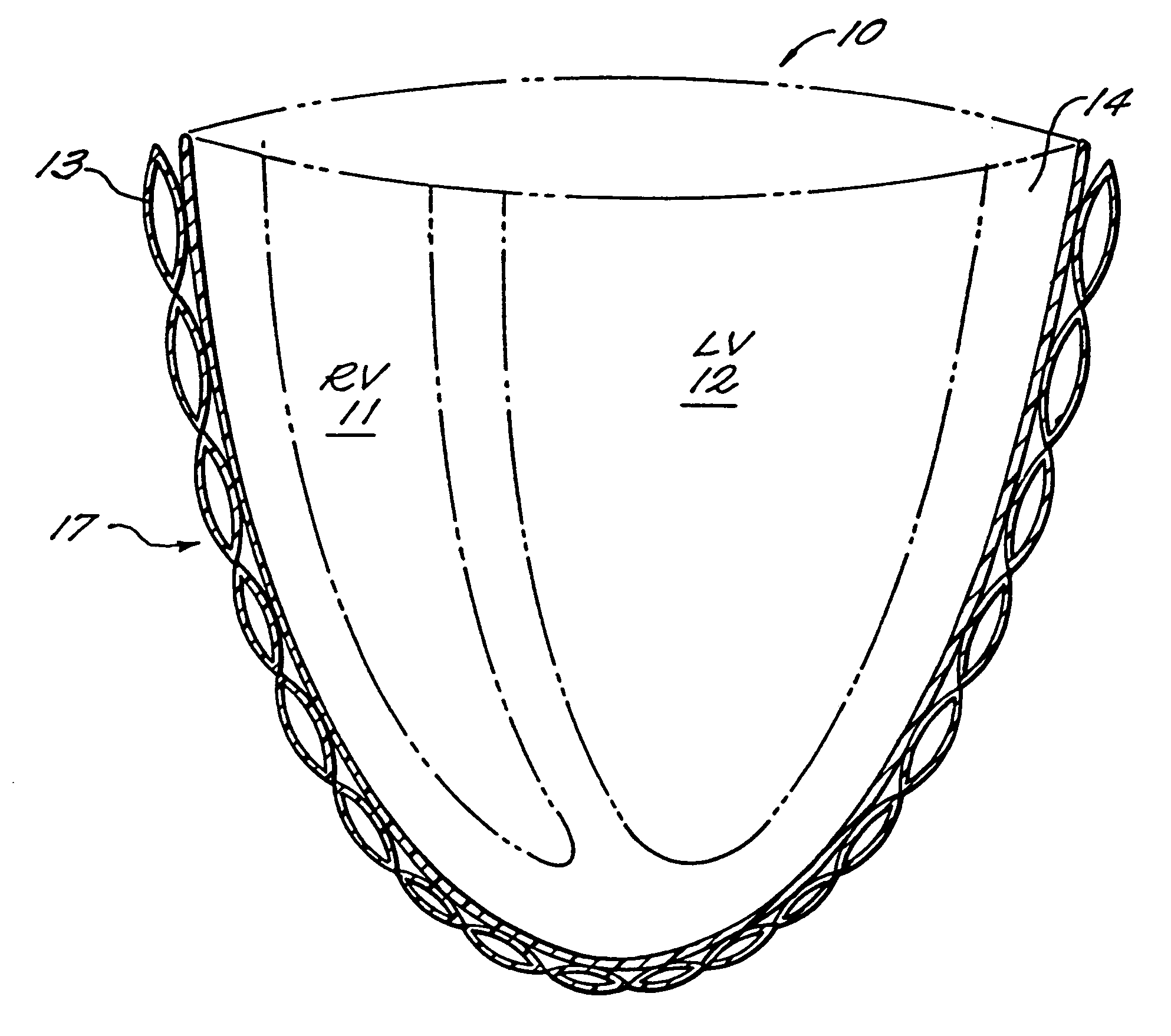
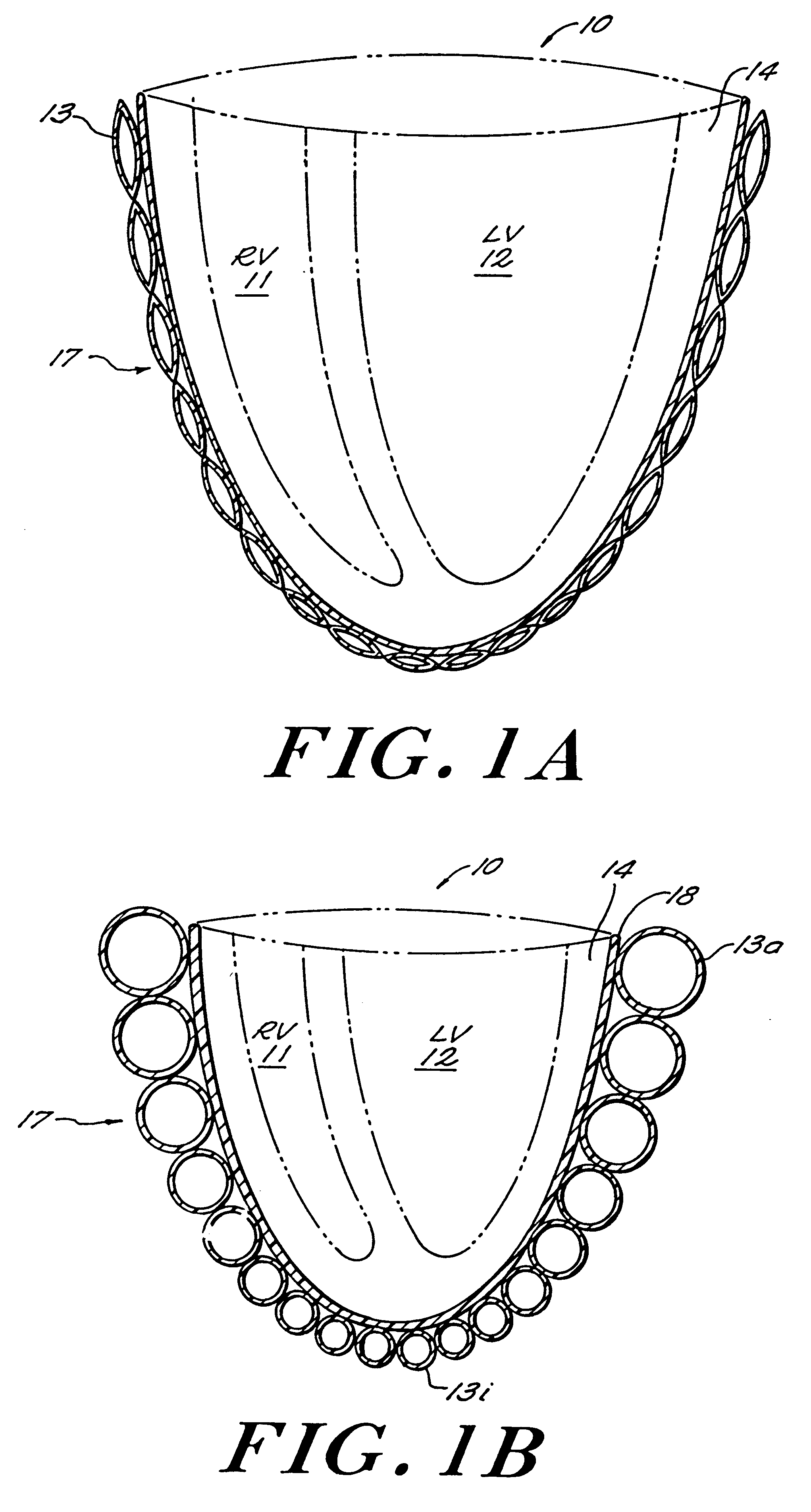
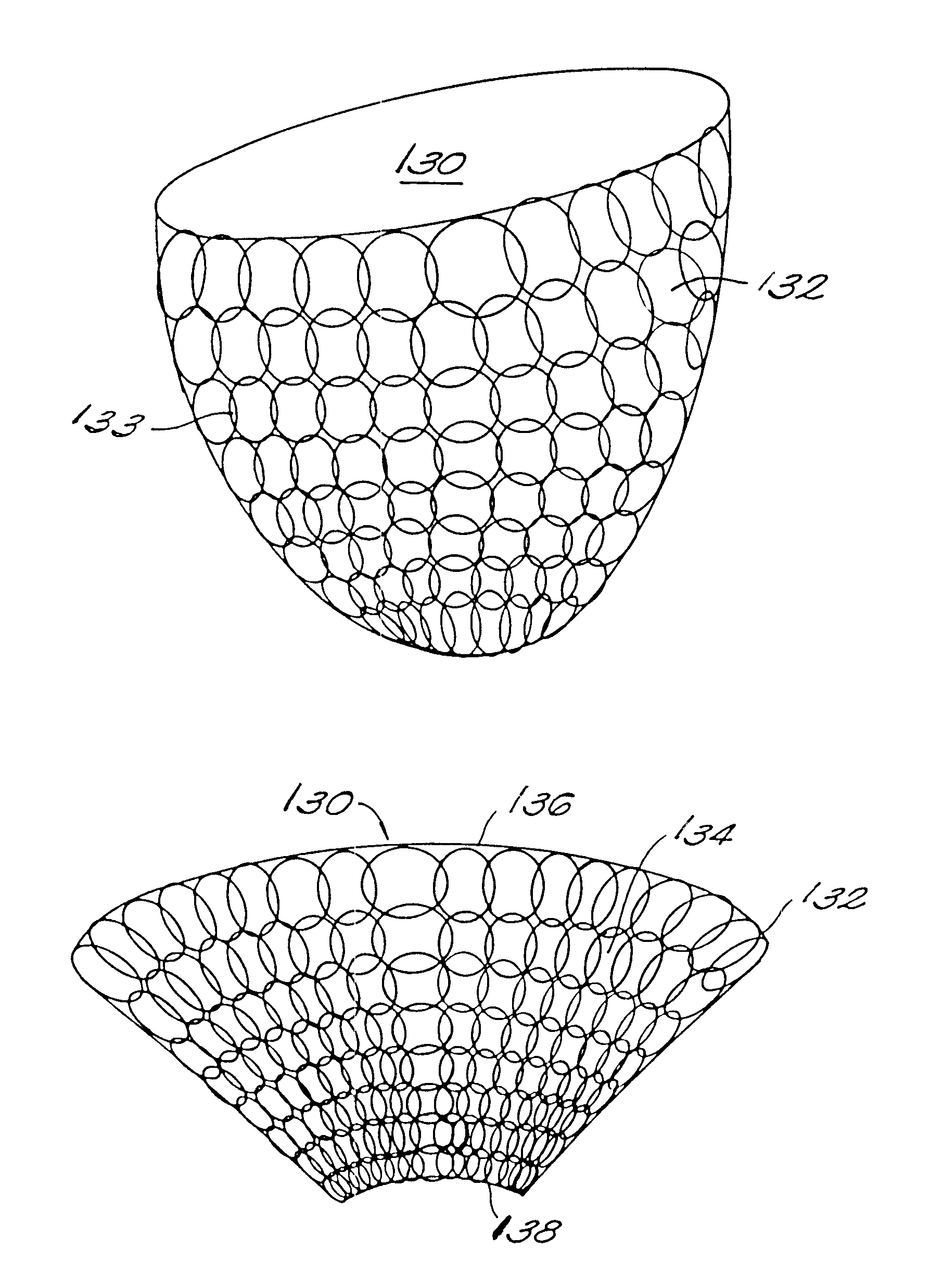
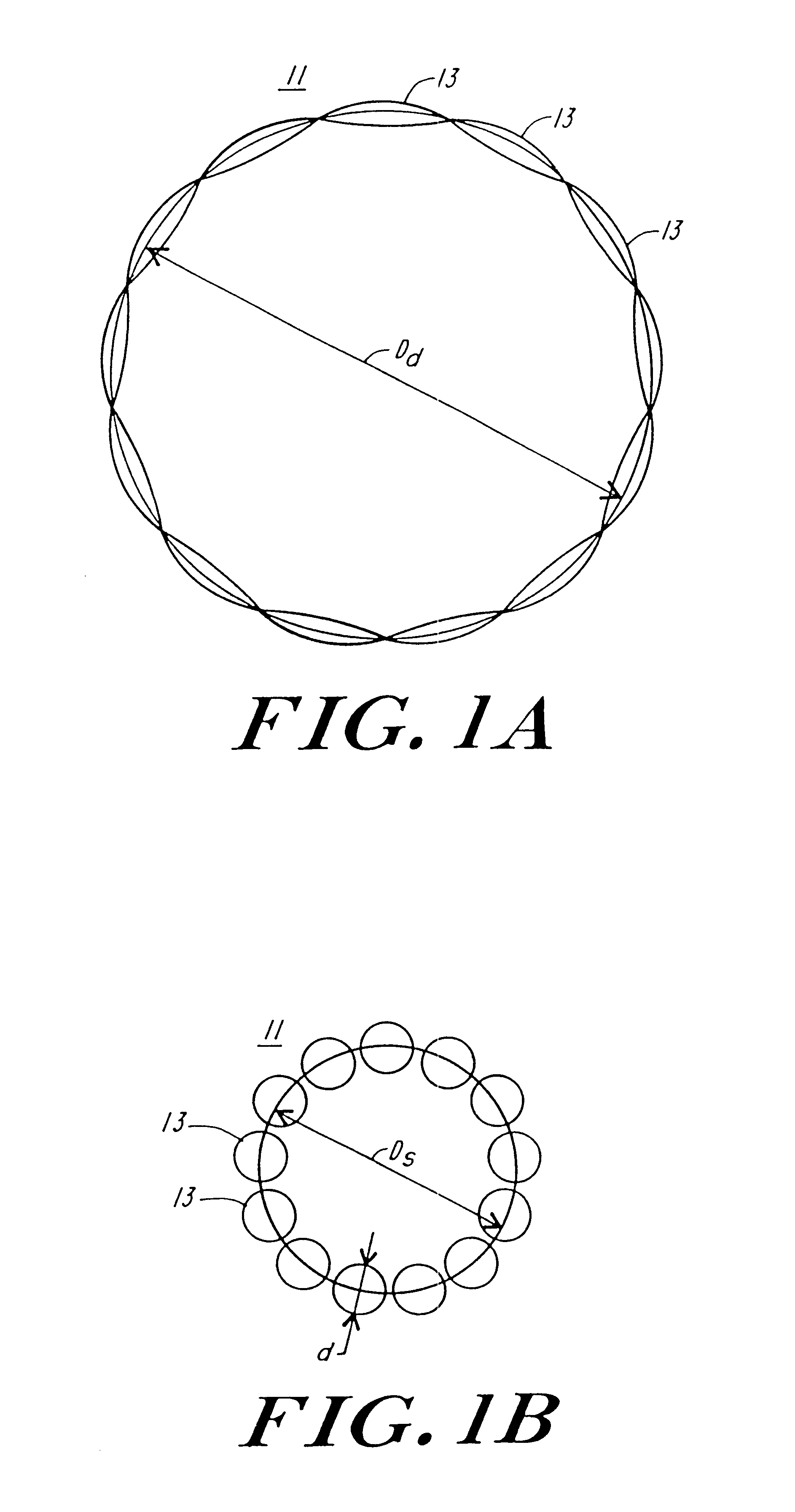
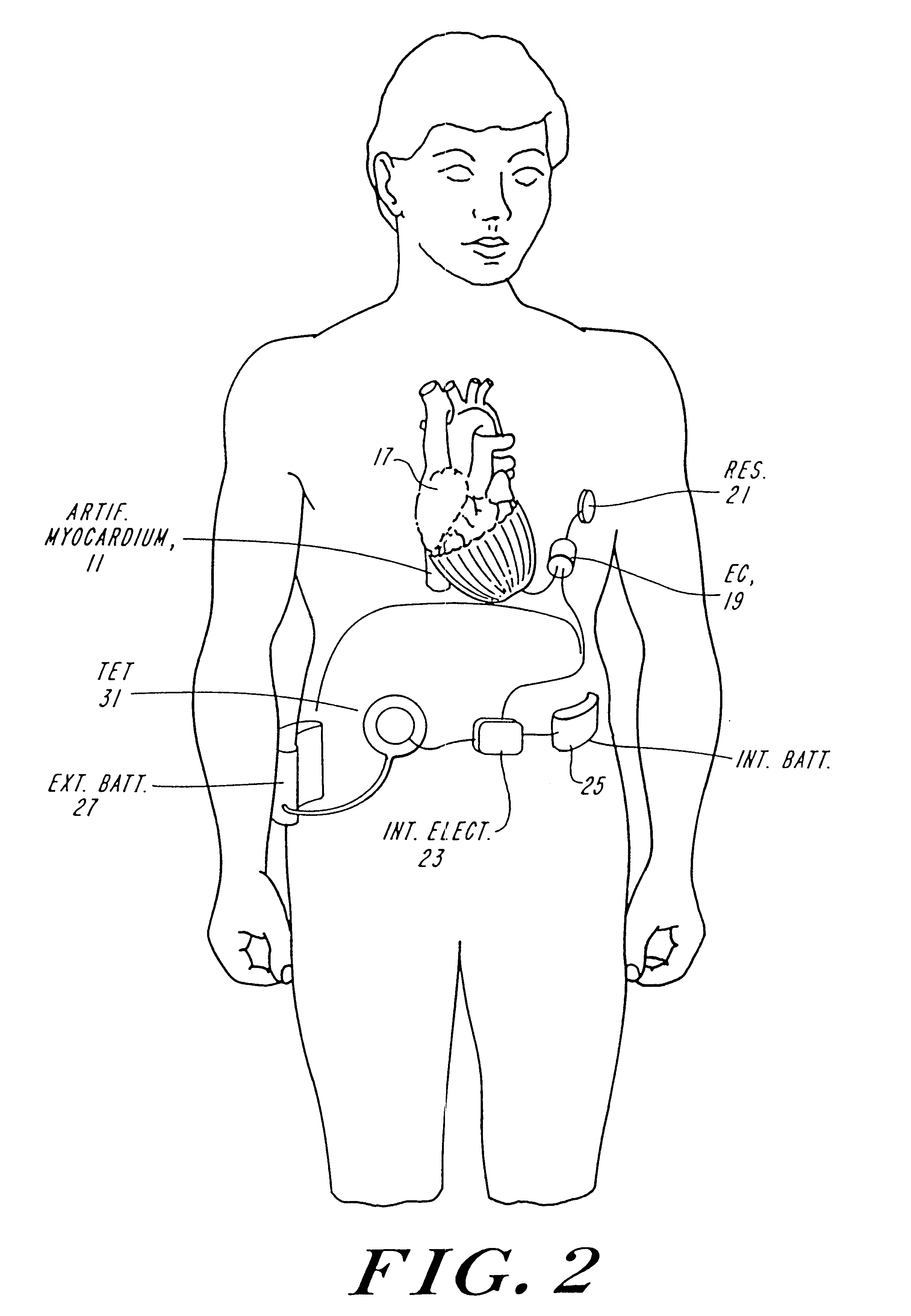
Passive girdle for heart ventricle for therapeutic aid to patients having ventricular dilatation
InactiveUS6224540B1Increased oxygen consumptionLarge increases in the tension-time integralHeart valvesControl devicesVentricular dilatationCardiac muscle
A passive girdle is wrapped around a heart muscle which has dilatation of a ventricle to conform to the size and shape of the heart and to constrain the dilatation during diastole. The girdle is formed of a material and structure that does not expand away from the heart but may, over an extended period of time be decreased in size as dilatation decreases.
Owner:ABIOMED
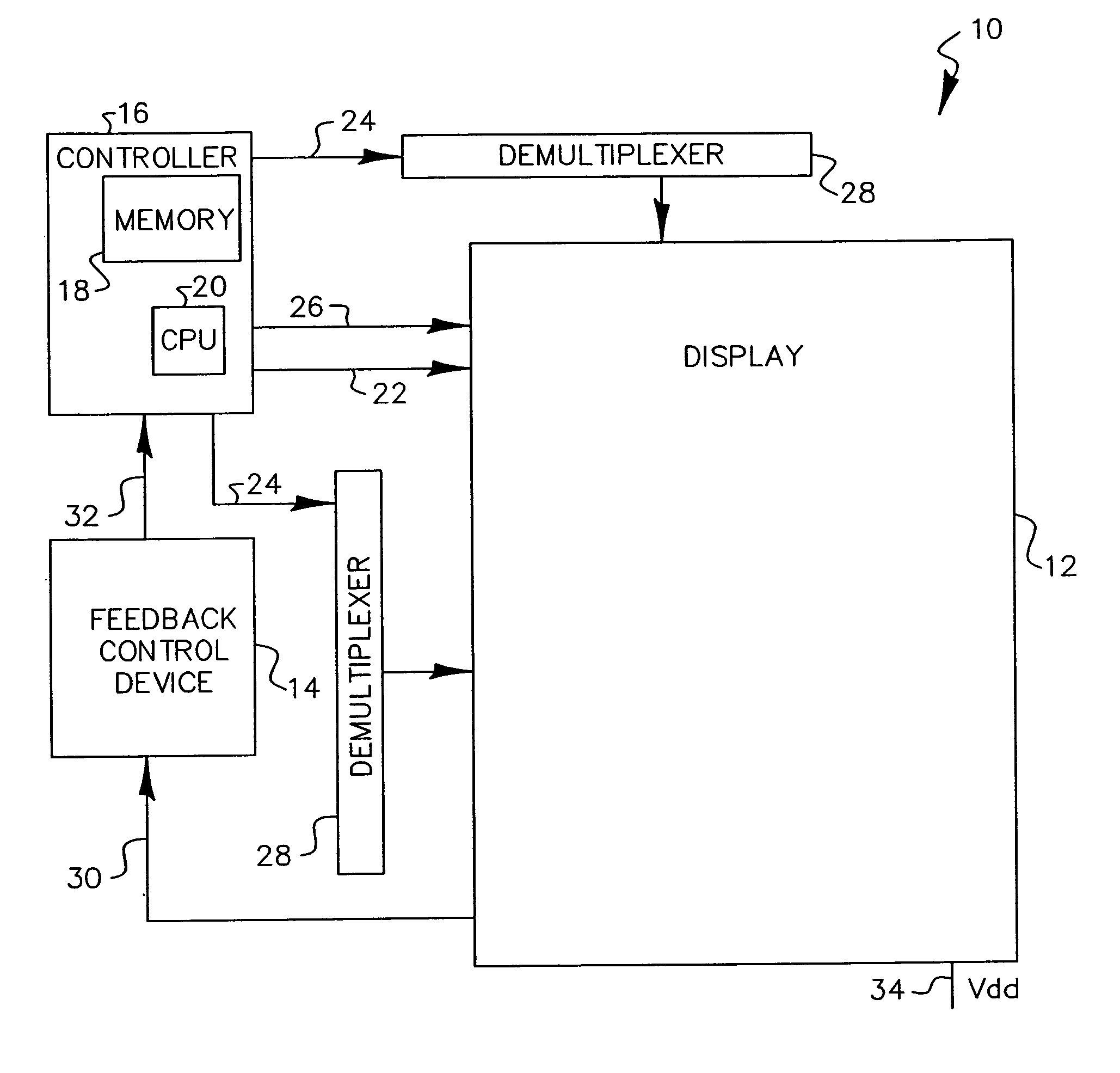
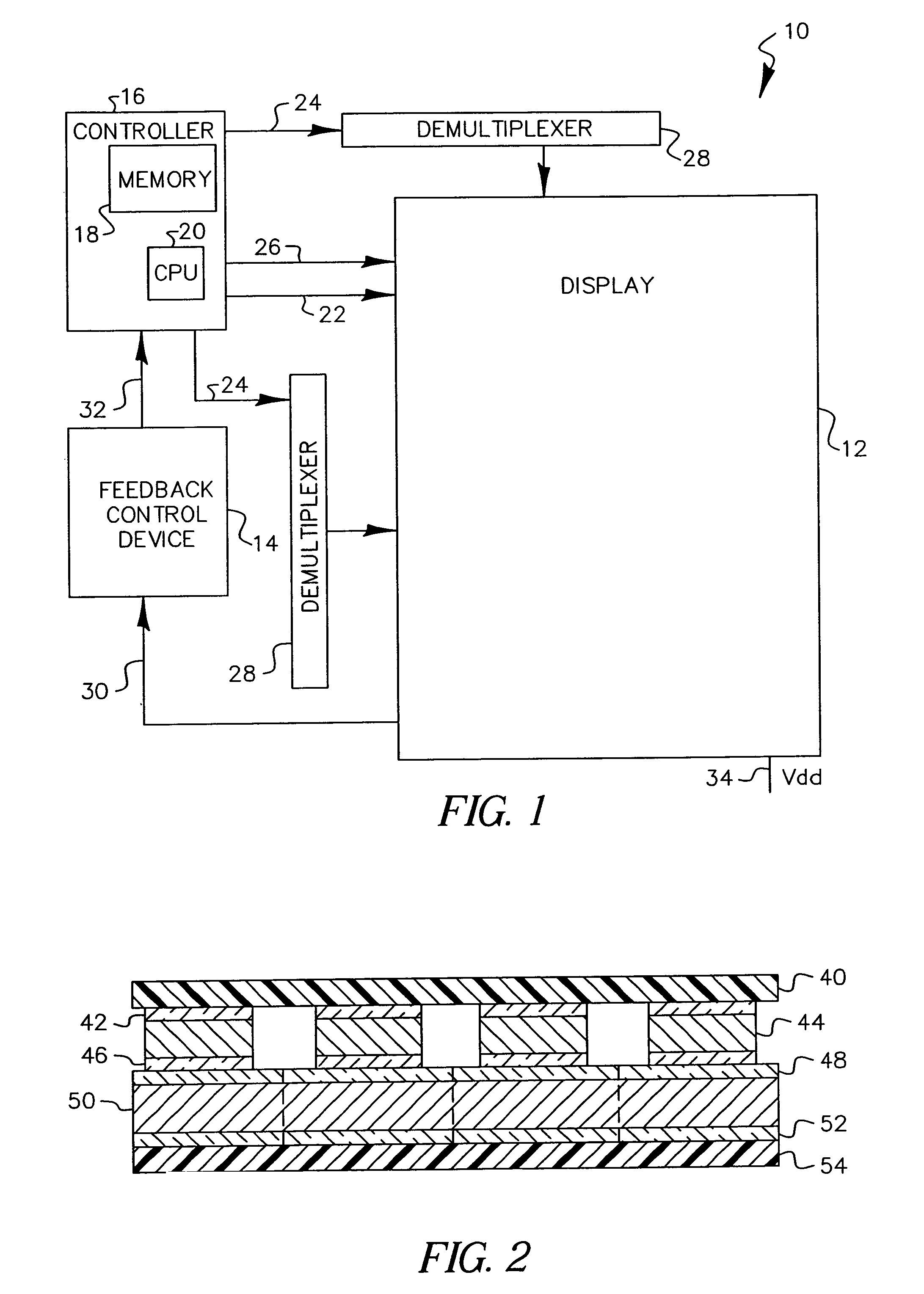
Flat-panel display with luminance feedback
InactiveUS7064733B2Improve performanceIncrease brightnessTelevision system detailsElectroluminescent light sourcesDisplay deviceOpto electronic
An image display, includes a substrate; a light emitter formed on the substrate; and a photo-sensor formed on the substrate and optically coupled directly to the light emitter.
Owner:GLOBAL OLED TECH
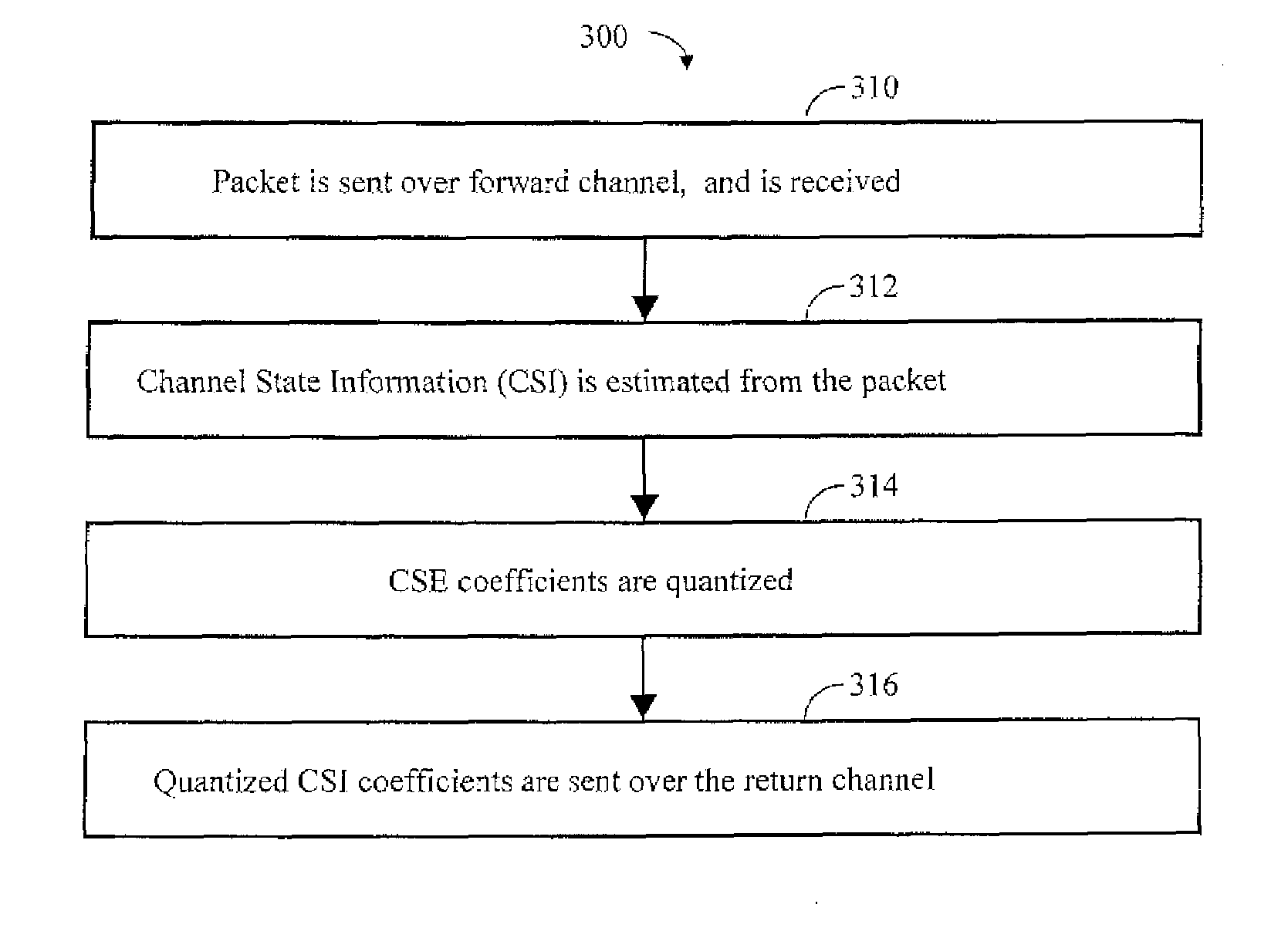
Varying size coefficients in a wireless local area network return channel
InactiveUS20070153731A1Quality improvementIncrease consumptionReceivers monitoringRadio/inductive link selection arrangementsChannel state informationTelecommunications
Sending channel related parameters known as channel state information (CSI) over a WLAN return channel. The size of these coefficients is not fixed. Rather, the coefficients are quantized in a certain resolution, which is determined adaptively according to a measure of the channel quality. This allows minimizing the component of the bandwidth of the wireless connection that is not used for payload transfer.
Owner:METALINK LTD
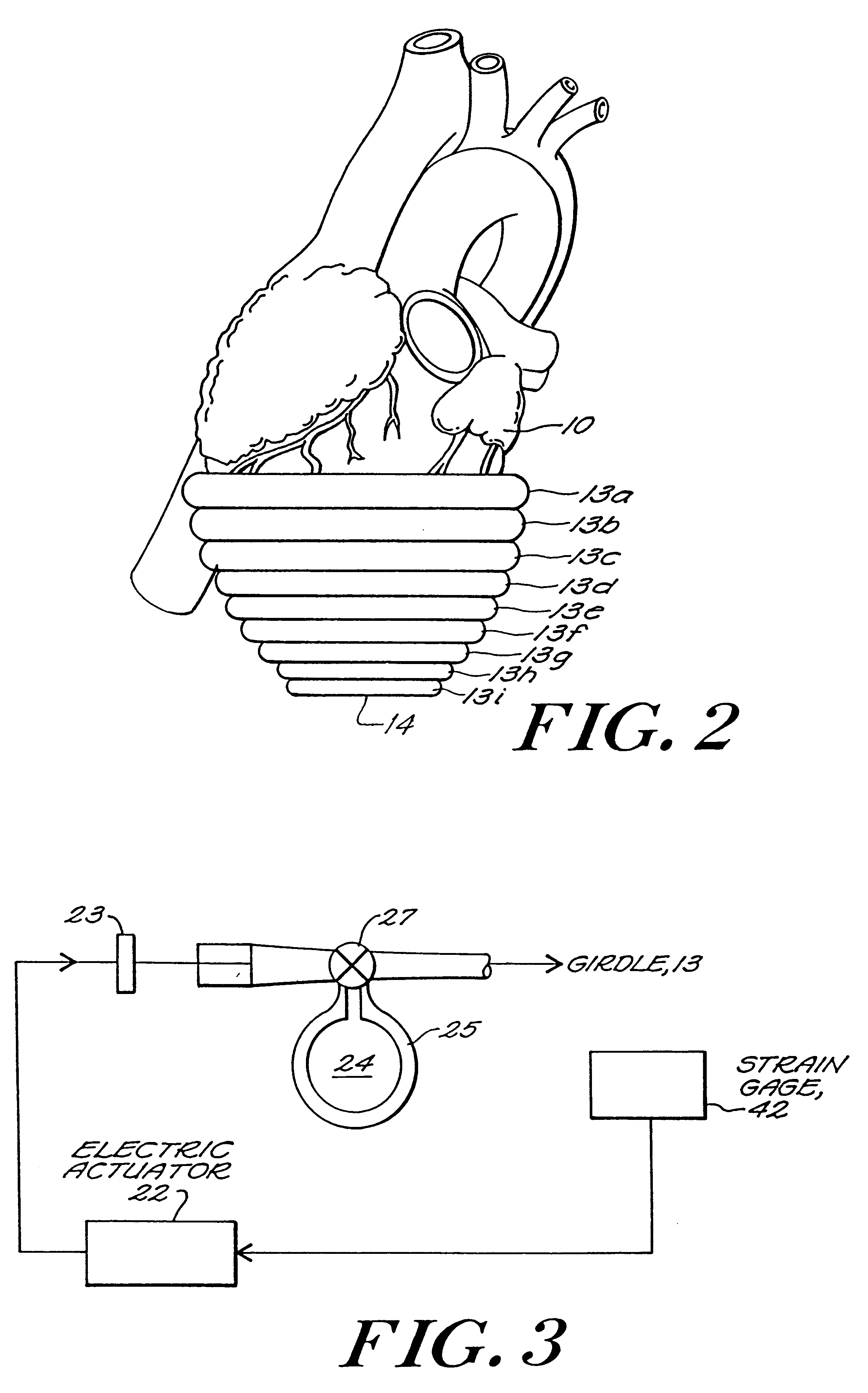
Passive cardiac assistance device
InactiveUS6508756B1Large increases in the tension-time integralIncrease consumptionHeart valvesControl devicesLong axisCardiac muscle
Artificial implantable active and passive girdles include a heart assist system with an artificial myocardium employing a number of flexible, non-distensible tubes with the walls along their long axes connected in series to form a cuff and a passive girdle is wrapped around a heart muscle which has dilatation of a ventricle to conform to the size and shape of the heart and to constrain the dilatation during diastole. The passive girdle is formed of a material and structure that does not expand away from the heart but may, over an extended period of time be decreased in size as dilatation decreases.
Owner:ABIOMED
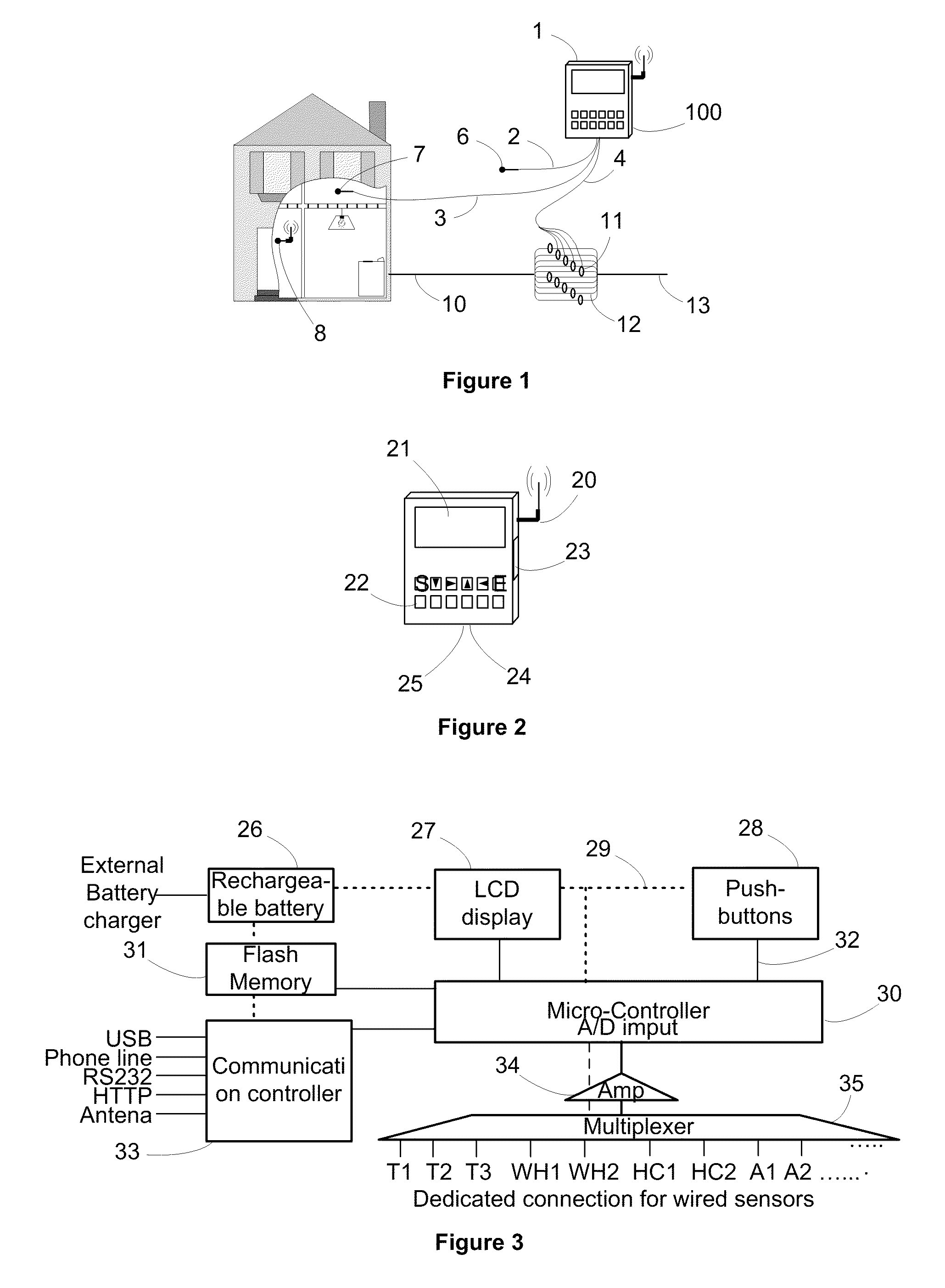
Method and apparatus for comprehensive energy measurement and analysis of a building
InactiveUS20100211222A1Low costReduce heat lossLevel controlSpace heating and ventilationEnergy transferElectricity
An energy monitoring and analysis system for a building includes a logging unit, a processing unit, temperature sensors that read the temperatures inside and outside the building, electric current sensors that read electric currents in all independent electric connections at the main connection panel of the building, and other types of sensors such as those related to natural gas flow. The logging unit periodically collects the data from all the sensors and transmits the data to the processing unit. The processing unit analyzes the data using highly sophisticated algorithms, extracts various parameters, profiles the electric energy usage, identifies potential problems with energy transfer and use, and lists recommendations for corrective actions. The processing unit analyzes data of the building, an HVAC system associated with the building, and consuming devices associated with the building.
Owner:GHOSN MICHEL
Discontinuous reception operation with additional wake-up opportunities
ActiveUS20150003311A1Short response timeMinimal impactPower managementTransmission systemsLongest cycleShort length
The invention relates to methods for improving the DRX operation of a UE by introducing an additional DRX wake-up cycle, which runs in parallel to the short and / or long DRX cycle. The DRX wake-up cycle defines time intervals after which the UE starts monitoring the PDCCH for a wake-up duration of time; the UE does not perform any other operation during the wake-up duration apart from monitoring the PDCCH. The time intervals of the wake-up cycle between the wake-up durations are preferably shorter than the one of the DRX long cycle, and may have the same or a shorter length than the ones of the DRX short cycle. The wake-up duration may be as long as the on-duration of the DRX short / long cycle, or may be preferably much shorter, such as only one or a few subframes.
Owner:APPLE INC
Method for synthesizing Beta molecular sieve by organic-free template
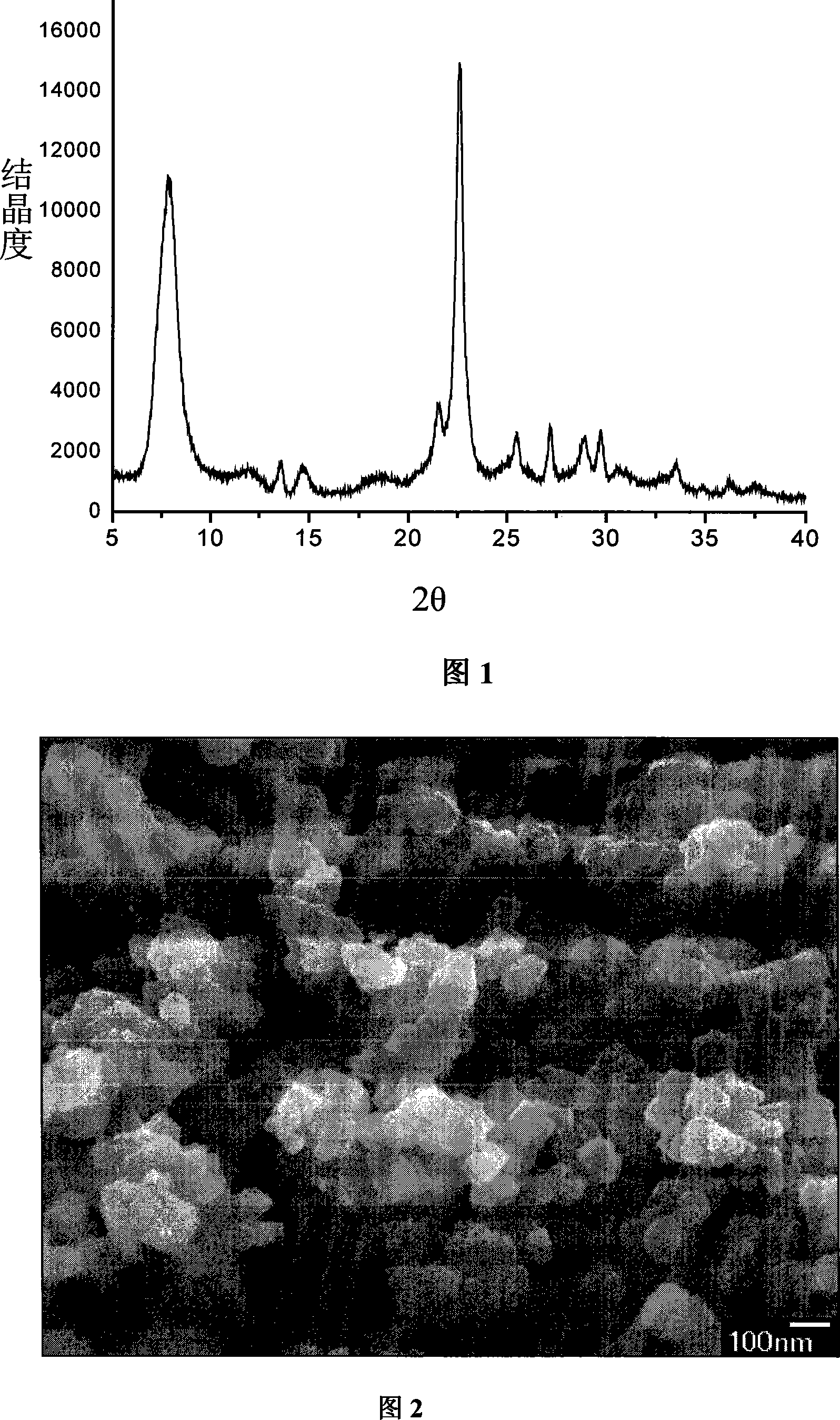
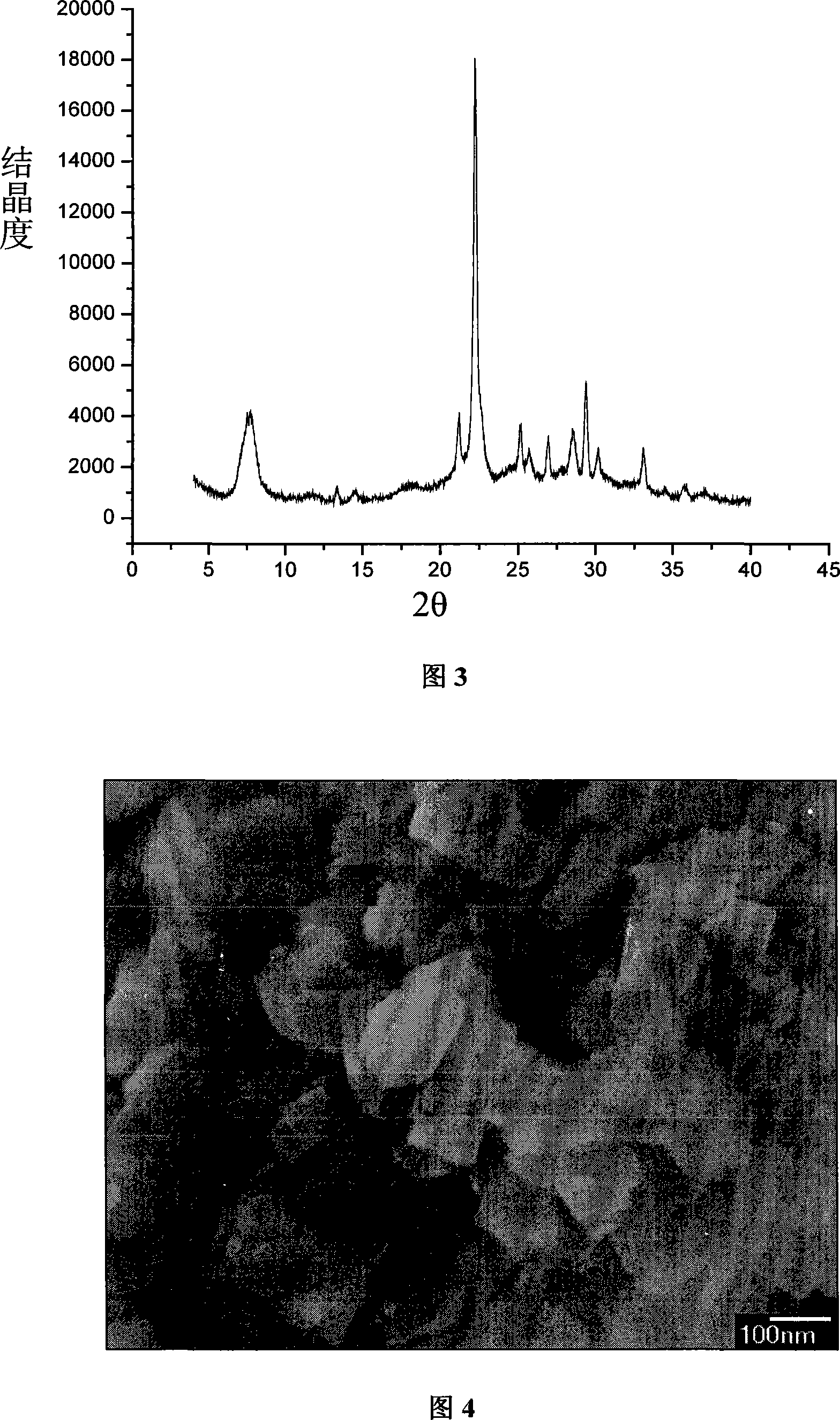
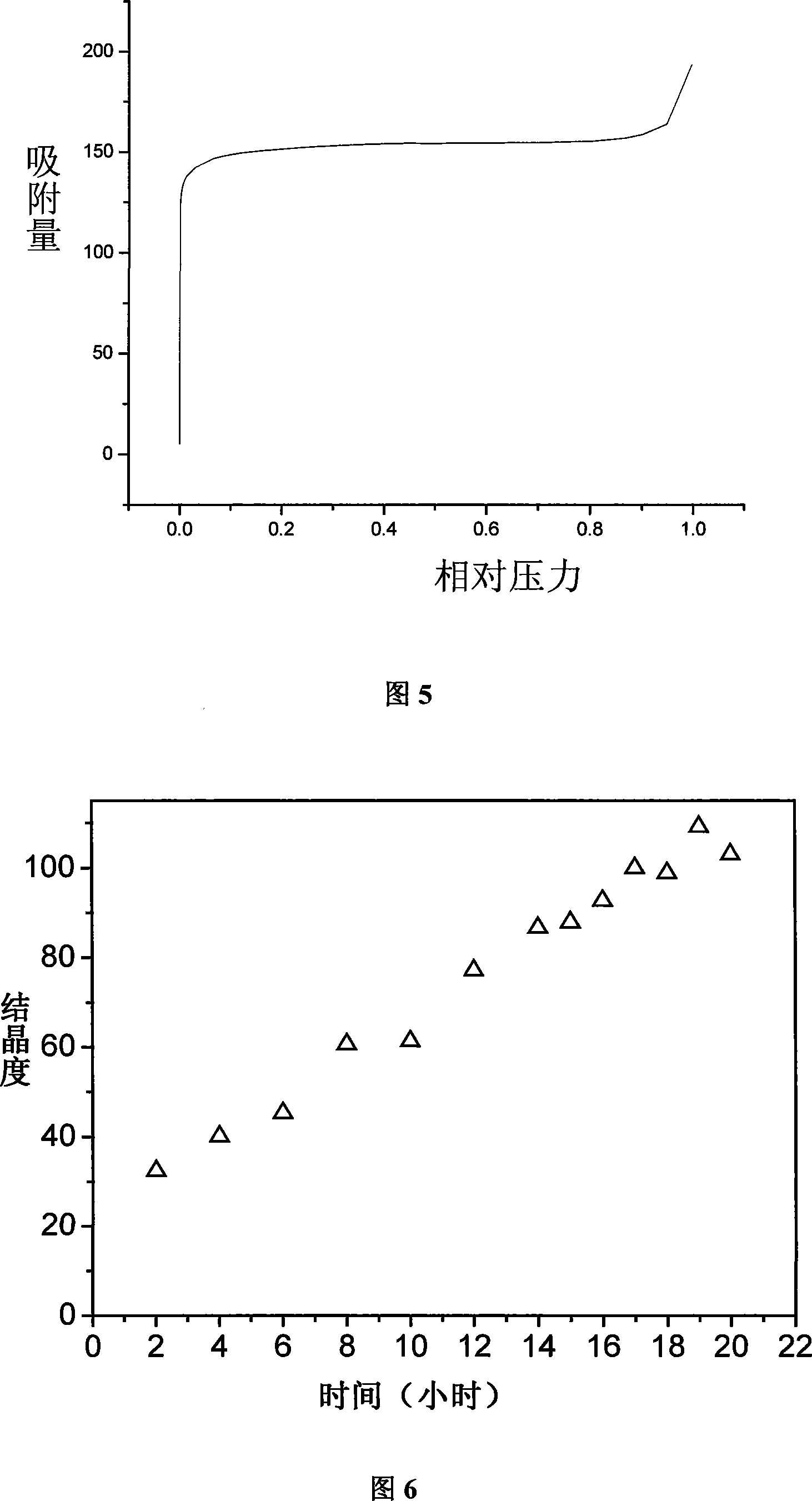
InactiveCN101249968AFast crystallization rateSynthesis fastCrystalline aluminosilicate zeolitesMolecular sieveAlumina gel
The invention relates to a method of synthesizing Beta molecular sieve without organic templates, which belongs to the technical field of catalytic chemistry. The steps of the invention comprise mixing alkali oxide sources, alumina sources, silica sources and water, stirring and synthesizing initial silica-alumina gel, then adding with Beta zeolite crystal seed, crystallizing 12-24 hours under the temperature of 100-180 DEG C and hydro-thermally synthesizing the Beta molecular sieve, SiO2 / Al2O3 of the Beta zeolite crystal seed equals 22-25, and the quality of addition quantity is 5%-20% of the silica sources. The method of the invention suits requirements of applying zeolite molecular sieve in industry, not only can directly synthesize high crystallinity crystal of the Beta molecular, but also can increase crystallizing speed of the molecular and reduce manufacturing cost. Because the synthesis process doesn't use any organic templates without roasting, thereby a pore path is unimpeded, and environmental pollution and relatively consumption are avoided.
Owner:JILIN UNIV
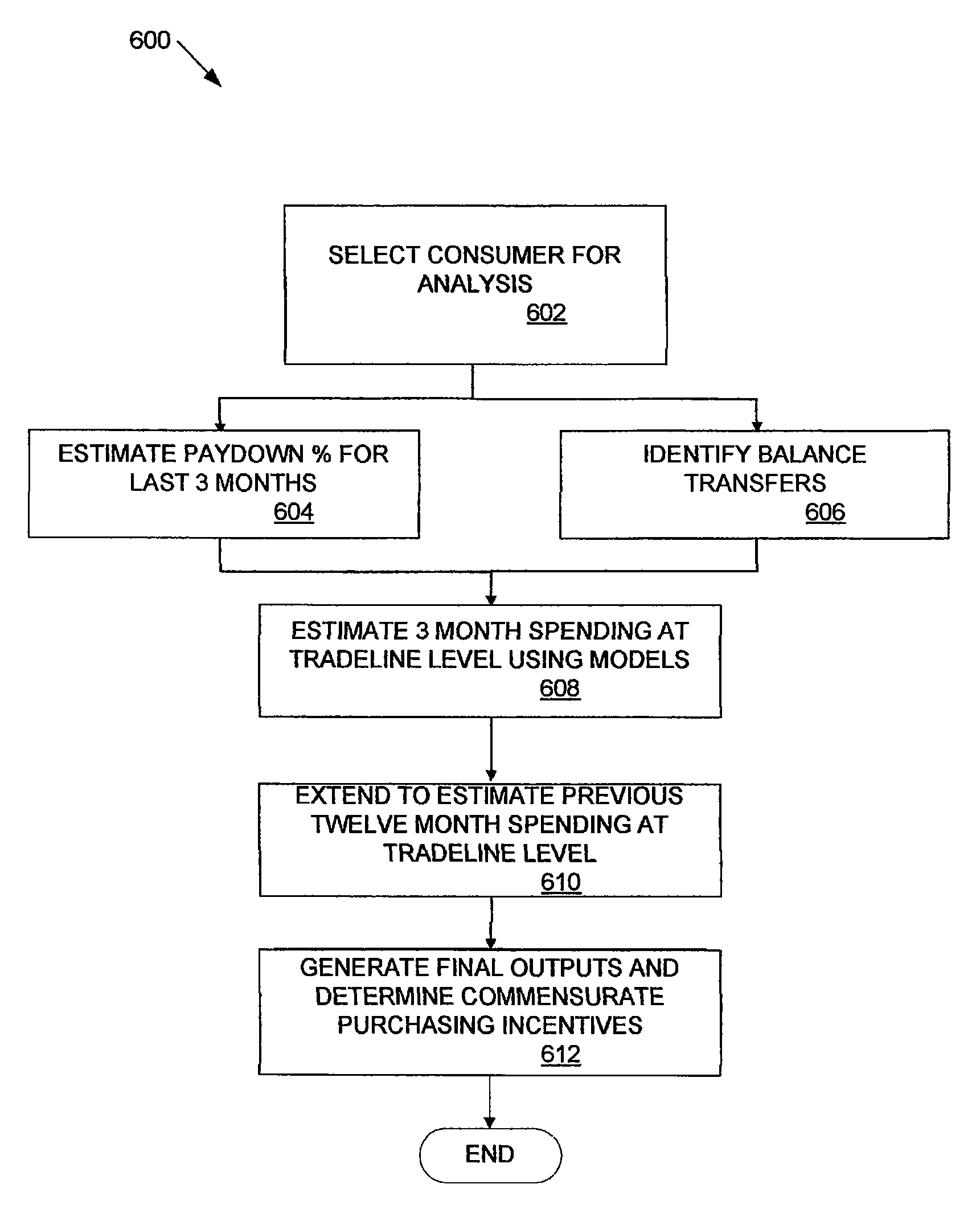
Estimating the spend capacity of consumer households
ActiveUS8204774B2Efficient managementIncrease profitabilityMarket predictionsFinanceComputer science
The spend capacity of a consumer typically increases as the number of consumers in the household increases, since the consumer can draw on the spending power of other consumers in the household. The size of wallet of the household is thus a better indicator of the consumer's spend capacity than an individual size of wallet. All consumers in a given household can be aggregated based on, for example, their address of record. Duplicate tradelines within each household are removed from consideration in a size of wallet estimate. A spend capacity is then estimated for each tradeline using calculations derived from a consumer behavior model. The spend capacities for all tradelines in the household are combined to determine a household size of wallet. Each consumer in the household is then tagged with the household size of wallet, rather than their individual size of wallet.
Owner:AMERICAN EXPRESS TRAVEL RELATED SERVICES CO INC
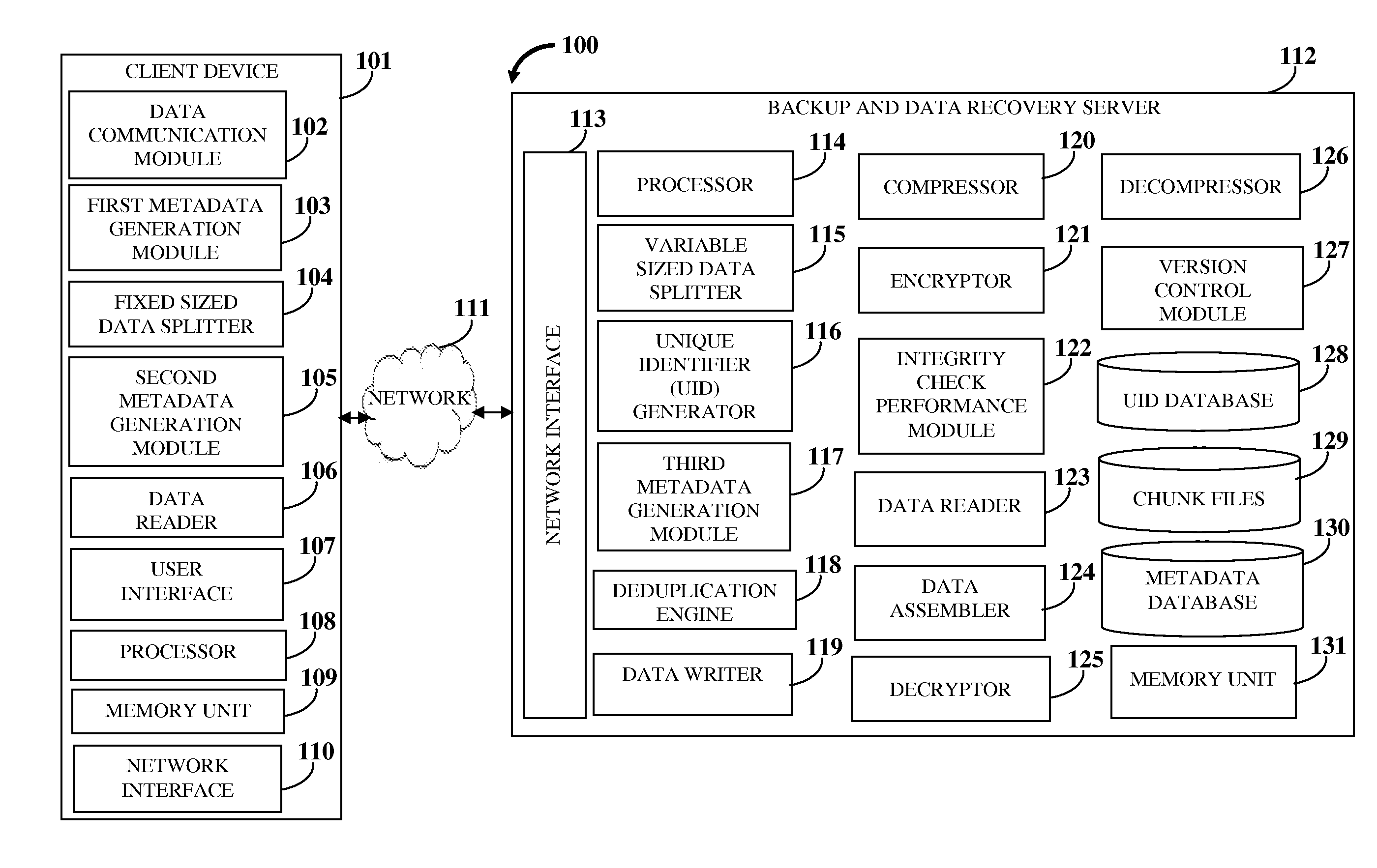
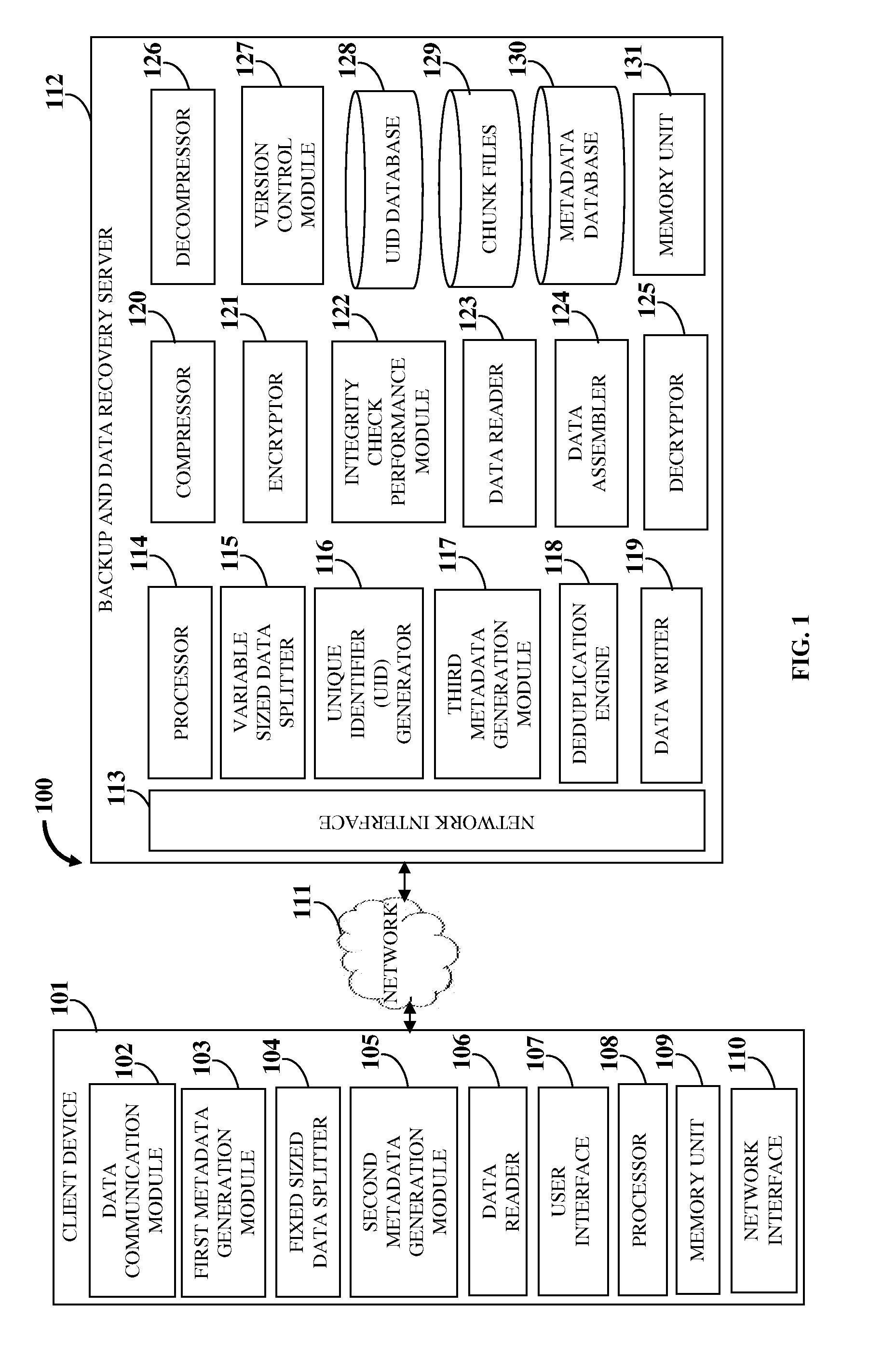
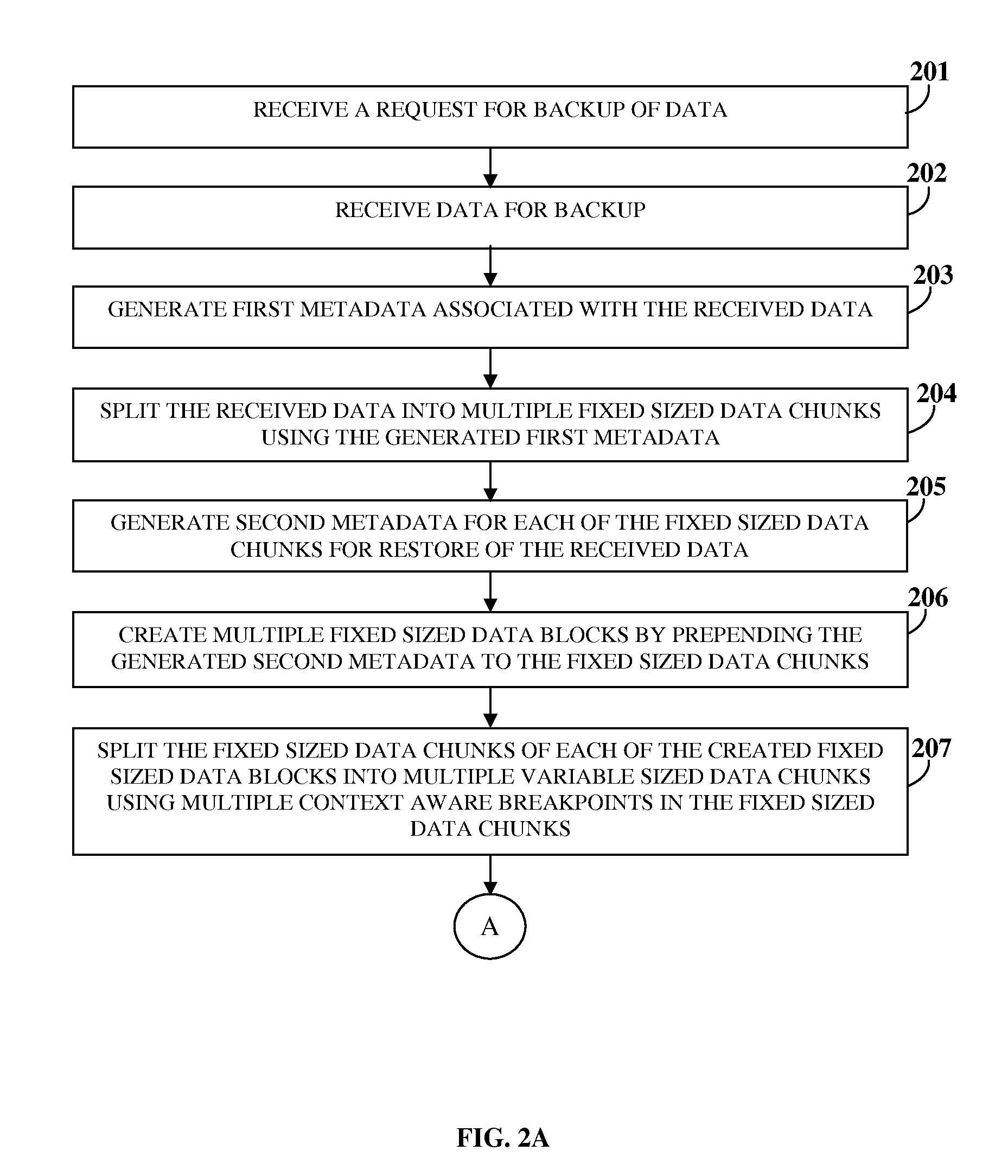
Secure Relational File System With Version Control, Deduplication, And Error Correction
ActiveUS20150293817A1Reduce storage spaceMaximum flexibilityDigital data information retrievalDigital data processing detailsRevision controlUnique identifier
A computer implemented method and a secure relational file system (SRFS) for storing and managing data for backup and restore are provided. The SRFS receives data, generates first metadata including file-to-sector mapping information, splits the data into fixed sized data chunks (FSDCs), generates second metadata including logical boundaries used for splitting, creates fixed sized data blocks by prepending the second metadata to the FSDCs, splits each FSDC into variable sized data chunks (VSDCs), generates third metadata including unique identifiers (UIDs) for the VSDCs, creates variable sized data blocks (VSDBs) by prepending the third metadata and the second metadata to each VSDC, identifies unique variable sized data chunks (UVSDCs) of the VSDBs using the UIDs, stores the UVSDCs in chunk files, and stores the first metadata, the second metadata extracted from the VSDBs, and storage locations of the UVSDCs with the third metadata of the UVSDCs and duplicate VSDCs in databases.
Owner:VEMBU TECH
Integrated circuits having post-silicon adjustment control
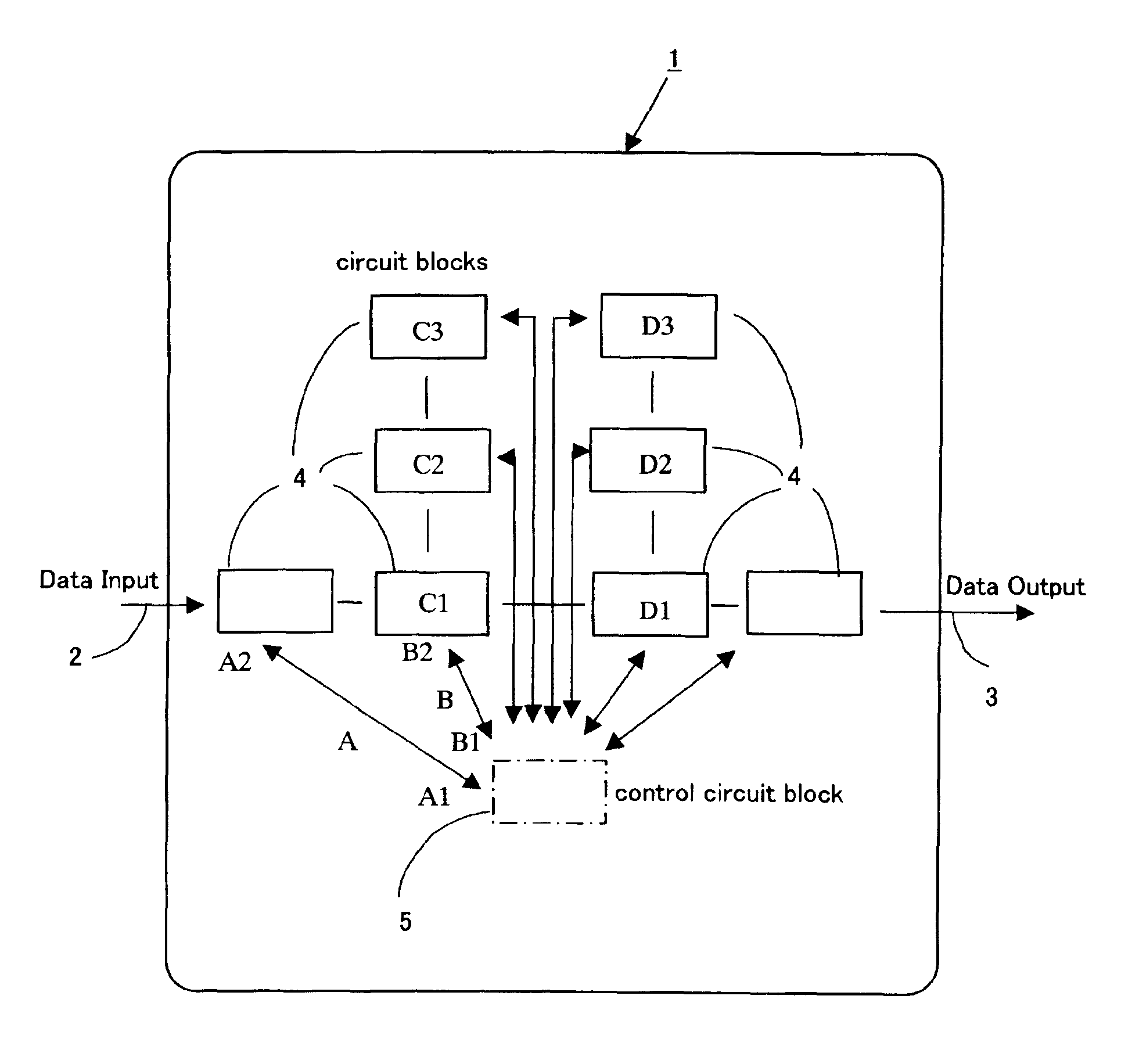
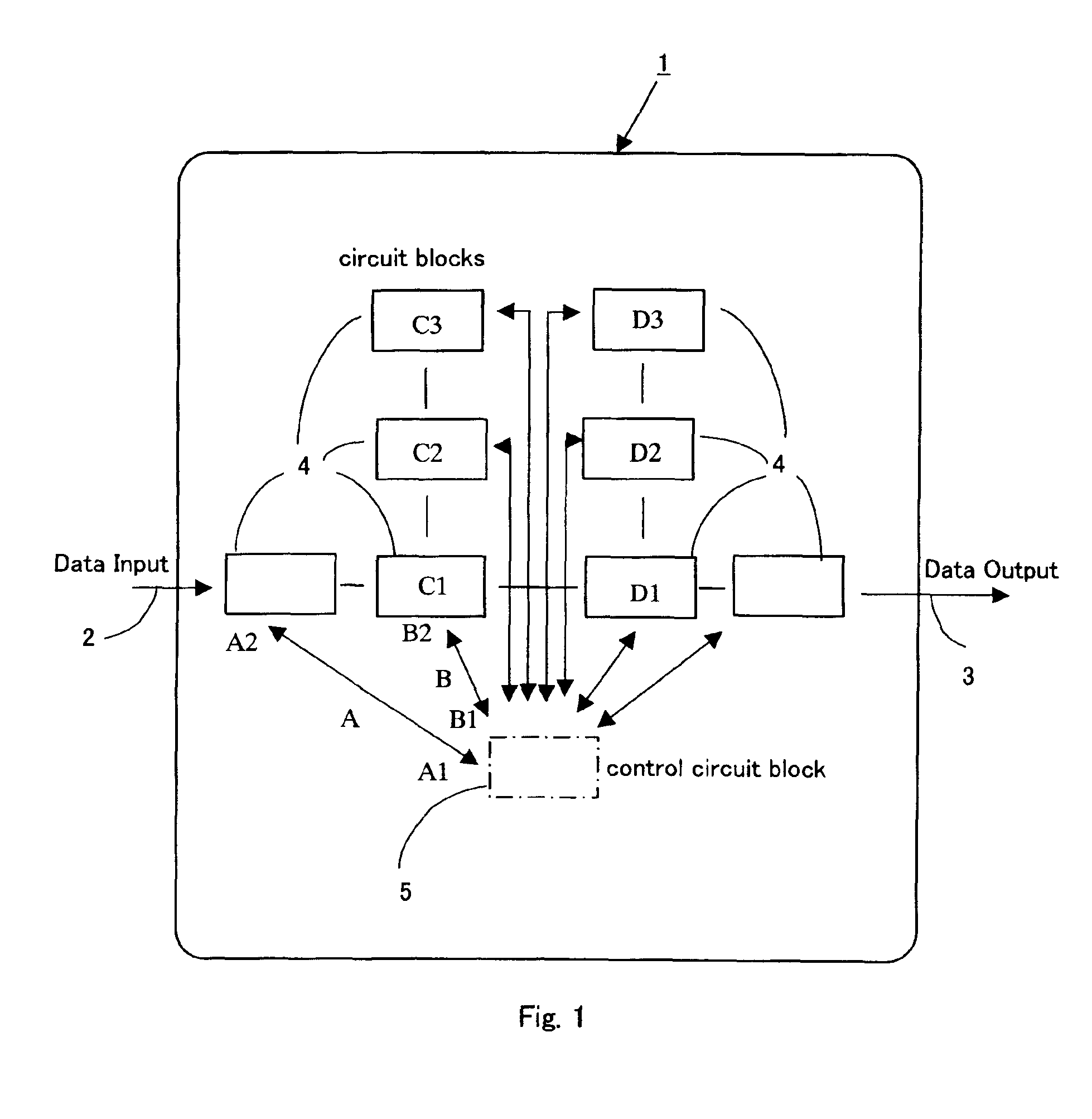
InactiveUS6957163B2Double program execution timeReduce power consumptionThermometer detailsDigital circuit testingControl systemIntegrated circuit layout
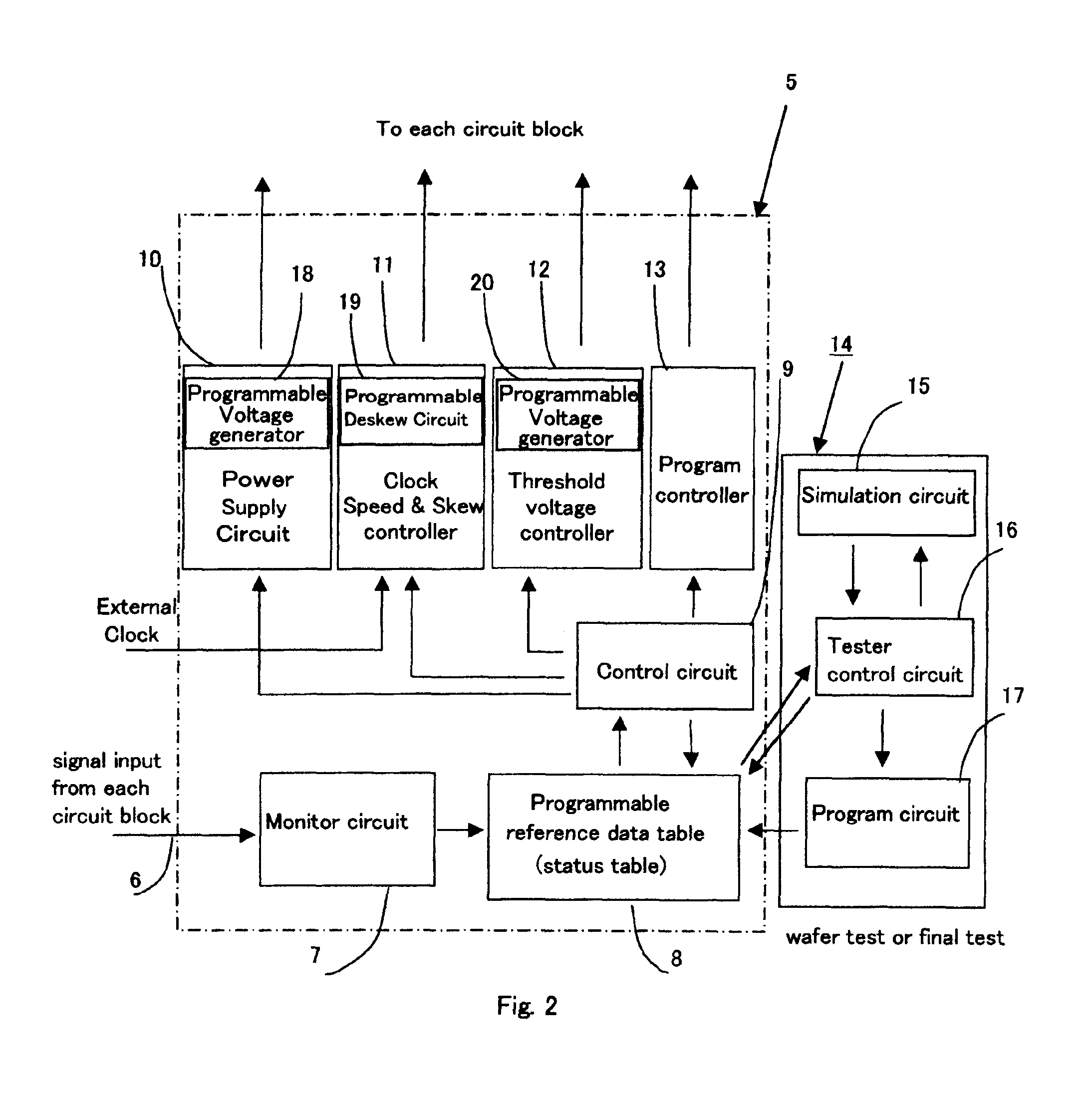
An integrated circuit system has a reference data table for holding information that is used to control at least one circuit block in the system and also has a power supply circuit, a body bias control circuit, a clock delivery circuit, a temperature monitor circuit, and / or a configuration control circuit. The performance of the system is improved by obtaining system performance data by testing the system at different supply voltages, different body-bias voltages, different clock speeds, and / or different temperatures. Values based on the data are entered into the reference data table. The power supply circuit, the body bias control circuit, the clock delivery circuit, and / or the temperature monitor circuit data is adjusted using the entered values.
Owner:RPX CORP
Advertisement of multiple security profiles in wireless local area networks
InactiveUS20100020746A1Meet compatibilityLow costWireless commuication servicesTransmissionRadio channelMAC address
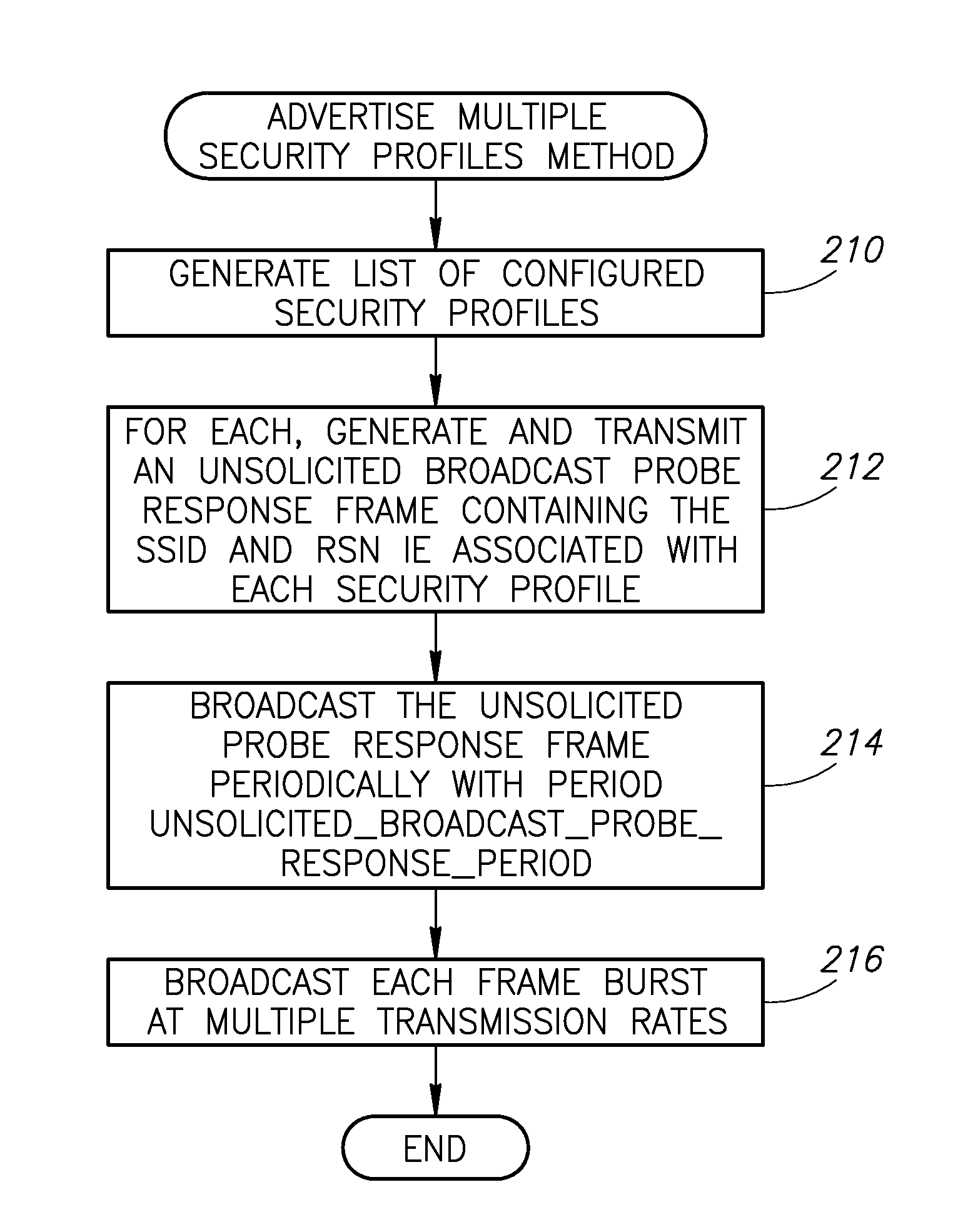
A novel and useful apparatus for and method of advertising multiple security profiles in wireless local area networks (WLANs). The security profile advertisement mechanism of the present invention advertises all configured security profiles by sending unsolicited 802.11 management probe response frames to the broadcast MAC address for available security profile. The access points sends these unsolicited probe response frames periodically, such as with the Beacon period. The conventional management application in the stations receives unsolicited advertisements of multiple SSIDs and perform a passive scanning process to obtain a list of BSSs available on the radio channel. The station can then display a list of all detected SSID advertisements to the user. The user of the station thus obtains information on all security profiles available on the access point without requiring any prior knowledge of specific SSIDs.
Owner:TEXAS INSTR INC
Digital currency mining circuitry having shared processing logic
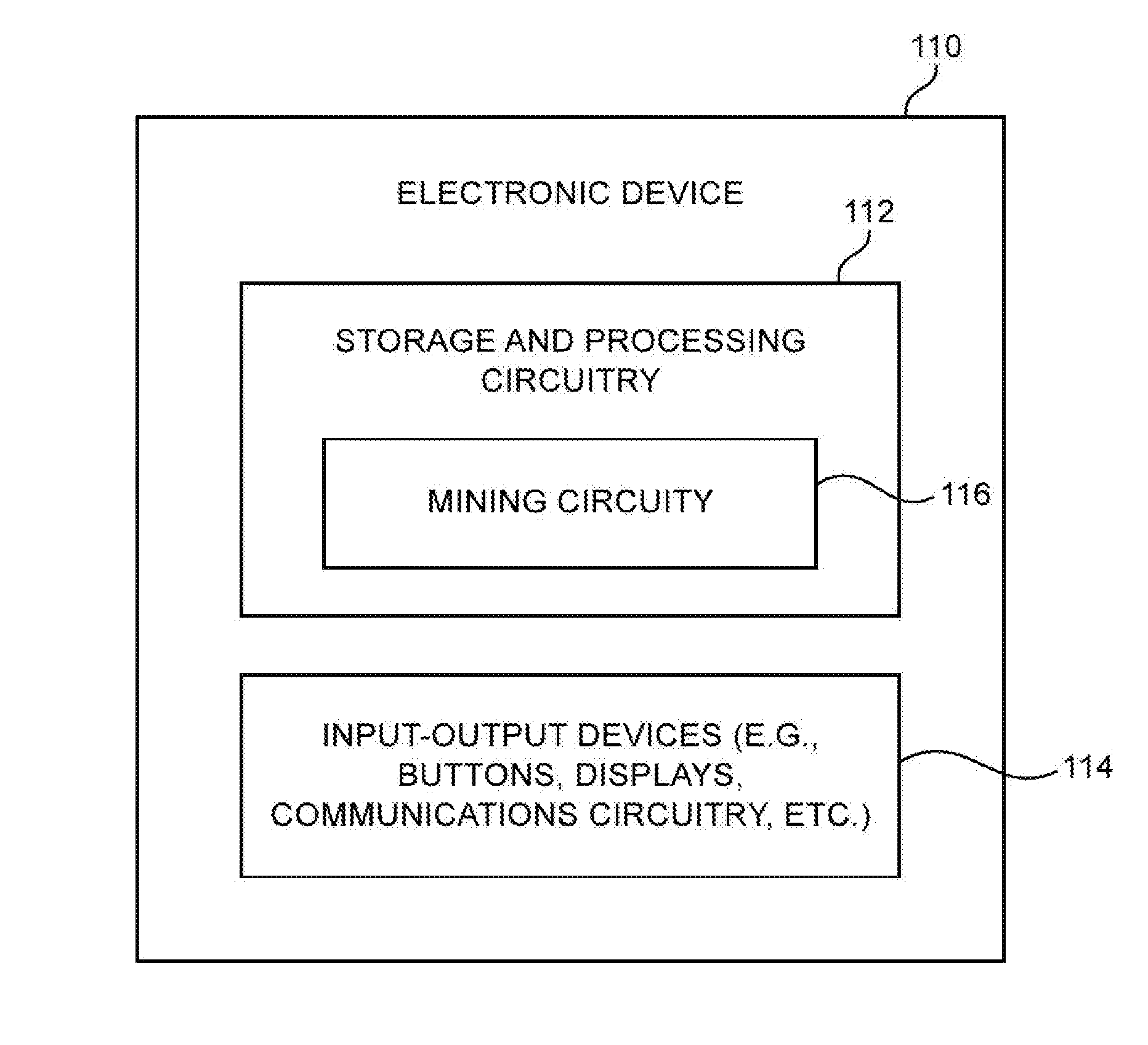
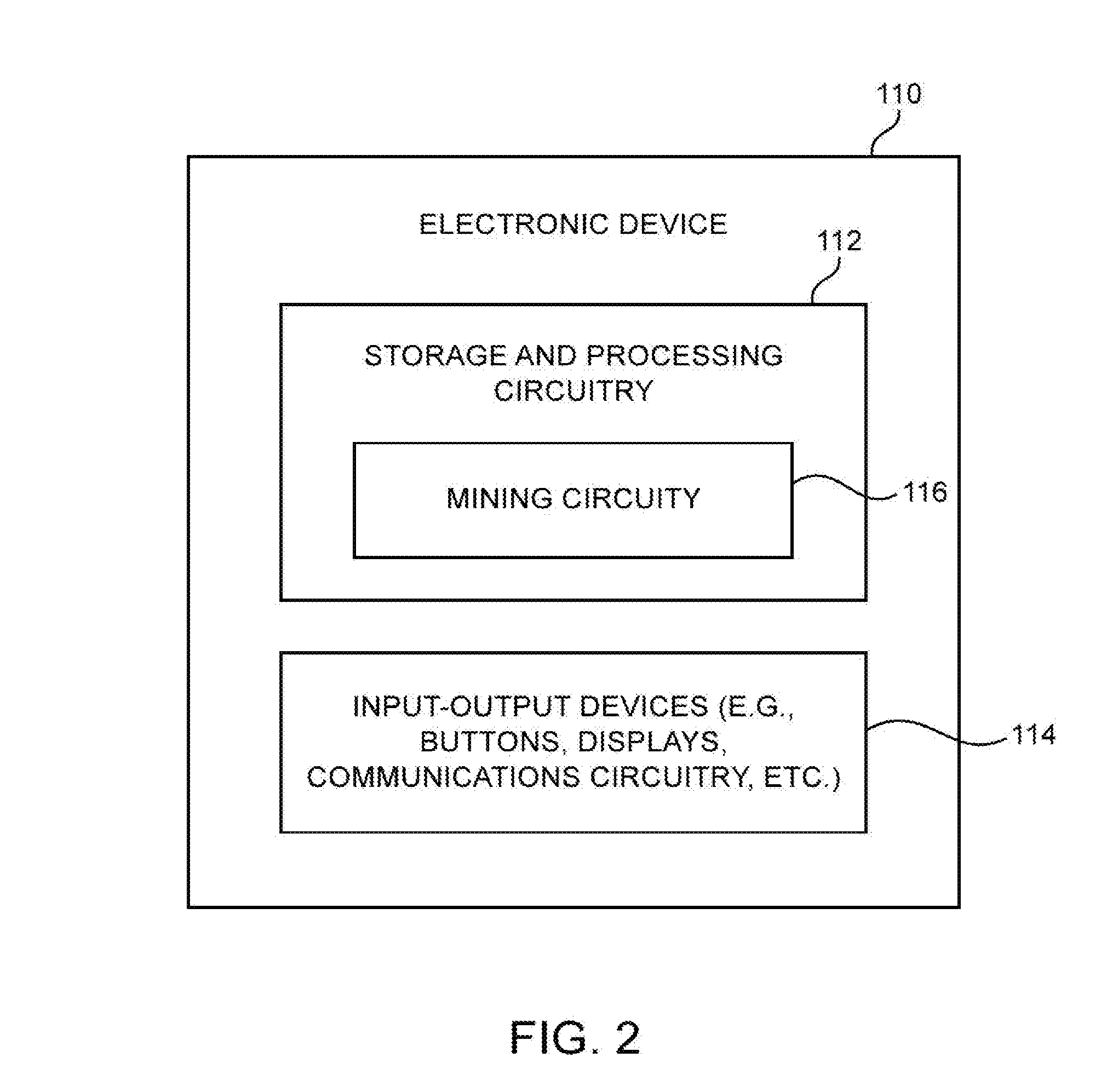
ActiveUS20160125040A1Increase consumptionIncrease powerFinanceWeb data indexingDigital currencyProcessing core
An integrated circuit may be provided with cryptocurrency mining capabilities. The integrated circuit may include control circuitry and a number of processing cores that complete a Secure Hash Algorithm 256 (SHA-256) function in parallel. Logic circuitry may be shared between multiple processing cores. Each processing core may perform sequential rounds of cryptographic hashing operations based on a hash input and message word inputs. The control circuitry may control the processing cores to complete the SHA-256 function over different search spaces. The shared logic circuitry may perform a subset of the sequential rounds for multiple processing cores. If desired, the shared logic circuitry may generate message word inputs for some of the sequential rounds across multiple processing cores. By sharing logic circuitry across cores, chip area consumption and power efficiency may be improved relative to scenarios where the cores are formed using only dedicated logic.
Owner:COINBASE
Semiconductor device, display device and electronic device equipped with the semiconductor device
InactiveUS20070035340A1Reduce power consumptionAvoid flowImpedence convertorsElectroluminescent light sourcesCapacitanceElectrical resistance and conductance
The present invention provides a semiconductor device which can prevent a current from flowing into a display element at a signal writing operation, without increasing power consumption and without changing a potential of a power supply for supplying a current to a load in each row. When a predetermined current is supplied to a transistor to set a gate-source voltage of the transistor, a potential of a gate terminal of the transistor is adjusted so as to prevent a current from flowing into a load which is connected to a source terminal of the transistor. Thus, a potential of a wire connected to the gate terminal of the transistor is made different from that of a wire connected to a drain terminal of the transistor. At that time, an operation of a transistor is shifted so as to allow a large amount of current to flow, and influences by intersection capacitance parasitic to a wire or the like or wire resistance are hardly caused, and a set operation is conducted quickly.
Owner:SEMICON ENERGY LAB CO LTD
Organic EL device
InactiveUS6280861B1Reduce displayEasy to produceDischarge tube luminescnet screensElectroluminescent light sourcesThin metalMono layer
An amorphous electrically conductive oxide such as In-Zn-O-containing amorphous oxide or amorphous ITO is used alone, or a laminate having a two- or three-layer structure constituted of the amorphous electrically conductive oxide and at least a thin metal layer is used, to form a transparent electrode whose side surface has a tapered form and whose top layer is formed of a layer of the above amorphous electrically conductive oxide, an organic single-layer portion or an organic multi-layer portion containing at least an organic light-emitting material is formed on the above transparent electrode, and further, an opposing electrode is formed on the above organic single-layer portion or the above organic multi-layer portion, whereby an organic EL device is obtained. A flattening layer is optionally provided so as to abut on the side surface of the transparent electrode for moderating a height-level difference between the above transparent electrode and the surface of the above substrate. Further, the above organic EL device is used to form an organic EL display panel.
Owner:IDEMITSU KOSAN CO LTD
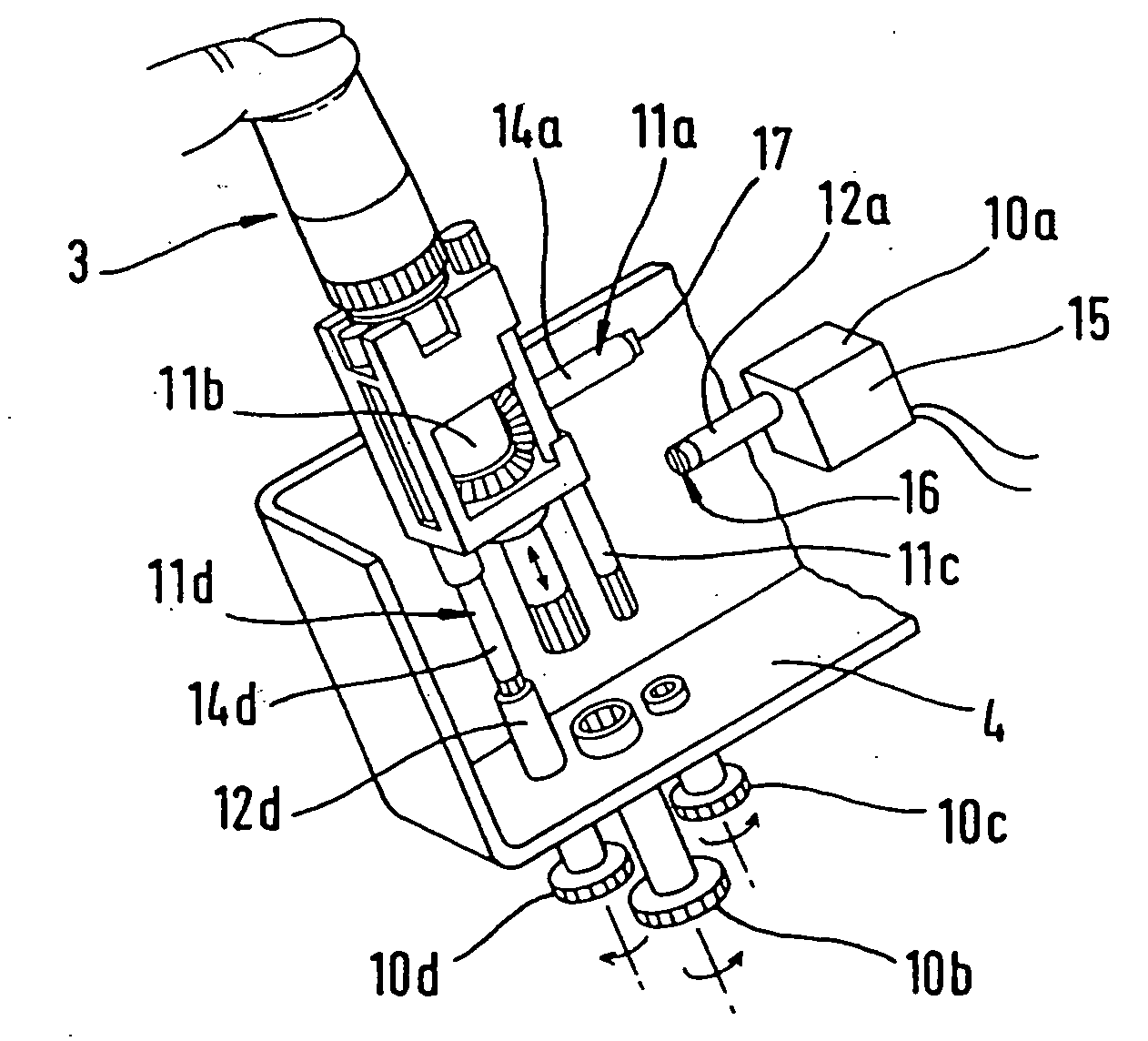
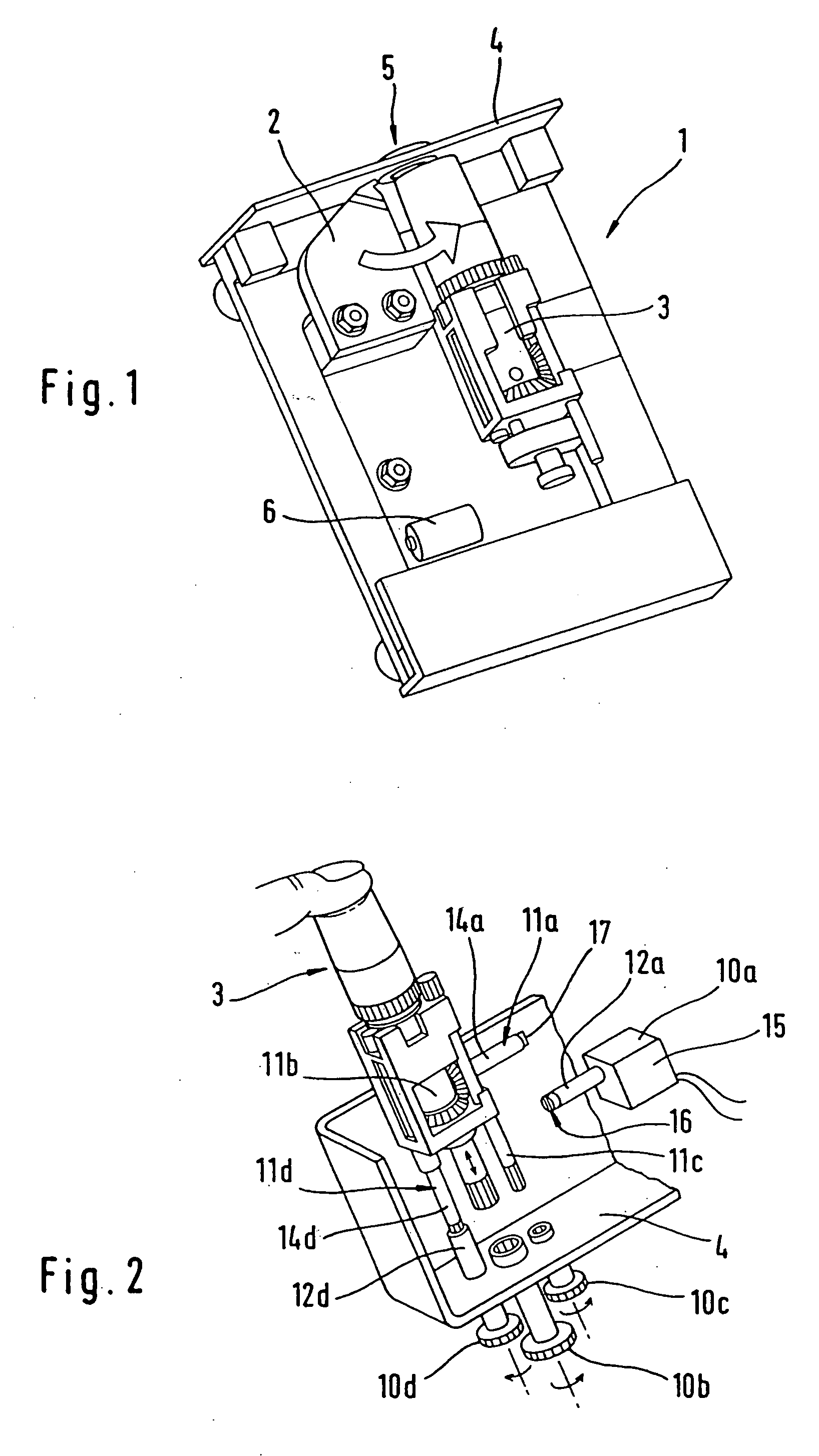
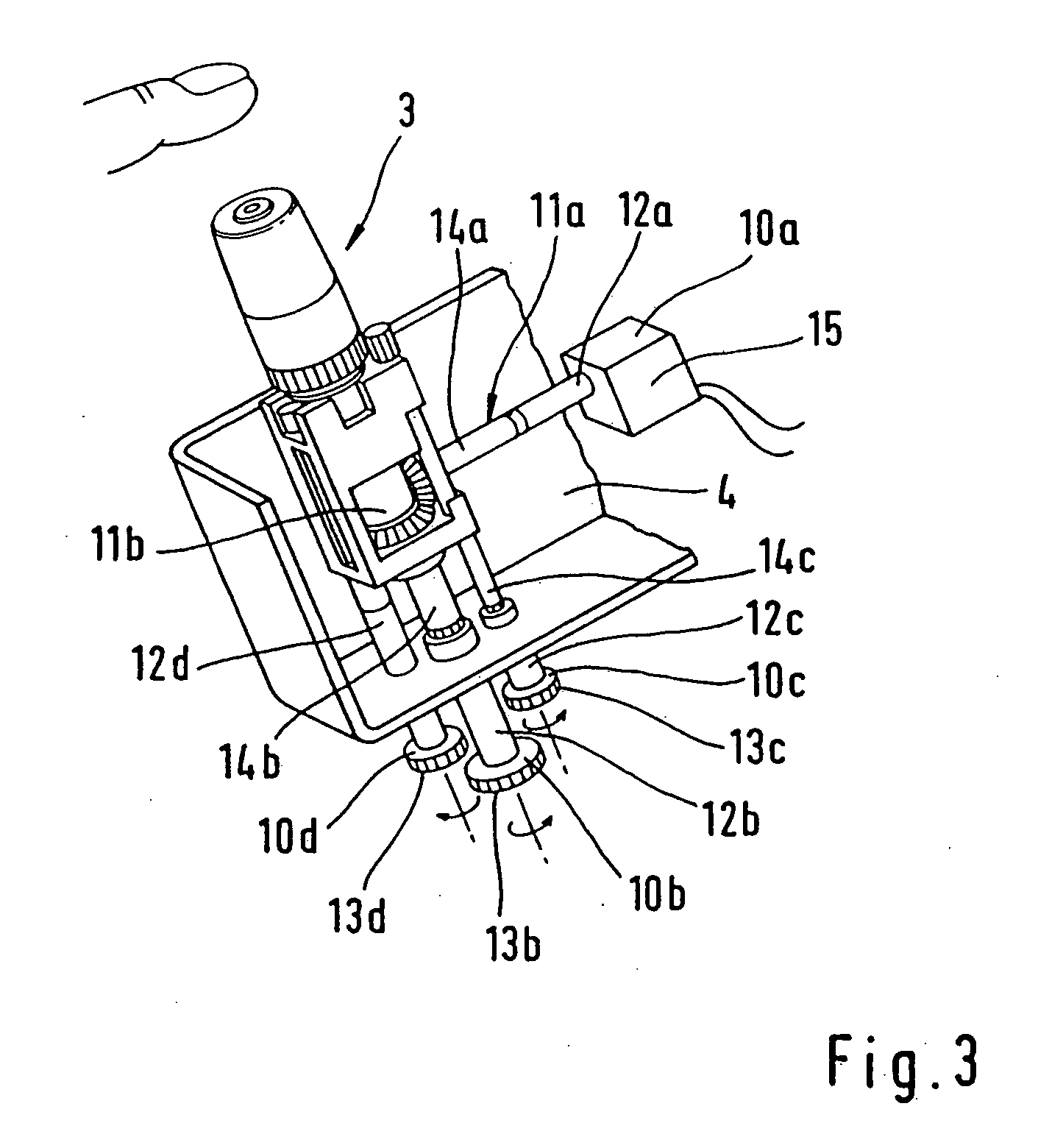
Hand-held instrument for the analysis of body fluids
ActiveUS20070004990A1Compact manufacturingIncrease consumptionCatheterDiagnostic recording/measuringPuncture WoundRest position
The present invention provides a hand-held analysis instrument for analyzing a body fluid. The instrument comprises a housing with a housing opening to which a body part, in particular, a finger, can be applied to generate a puncture wound, an analysis unit for analyzing a sample of a body fluid obtained at the puncture wound, and a piercing unit including a lancet and lancet drive for generating a puncture movement of the lancet. The piercing unit, including the lancet drive, is movable between an operating position and a rest position, the piercing unit being located at the housing opening in the operating position in such a manner that by means of the lancet a puncture wound can be generated in a body part pressed against the housing opening, and the piercing unit being remote from the housing opening in the rest position in such a manner that the space in front of the housing opening is free for the analysis unit, so that it can be moved into a position for receiving blood. An operating device is used for actuating a functional mechanism of the piercing unit. The piercing unit is decoupled from the operating device in one of its two positions and is coupled to the operating device in the other position.
Owner:ROCHE DIABETES CARE INC
Beamforming and distributed opportunistic scheduling in wireless networks
InactiveUS20060221920A1Improve performanceIncrease consumptionError preventionTransmission systemsSignal strengthWireless network
A system and method that addresses the issue of inducing and exploiting multi-user diversity in, e.g., a WLAN system in a fully distributed and opportunistic manner. In some embodiments, the system includes: an access point having a variable beamformer configured to fluctuate signal strength as perceived by stations within a range of the access point; and a plurality of stations having modified distributed-MAC protocol such as to be channel-aware and opportunistic.
Owner:TELCORDIA TECHNOLOGIES INC +1
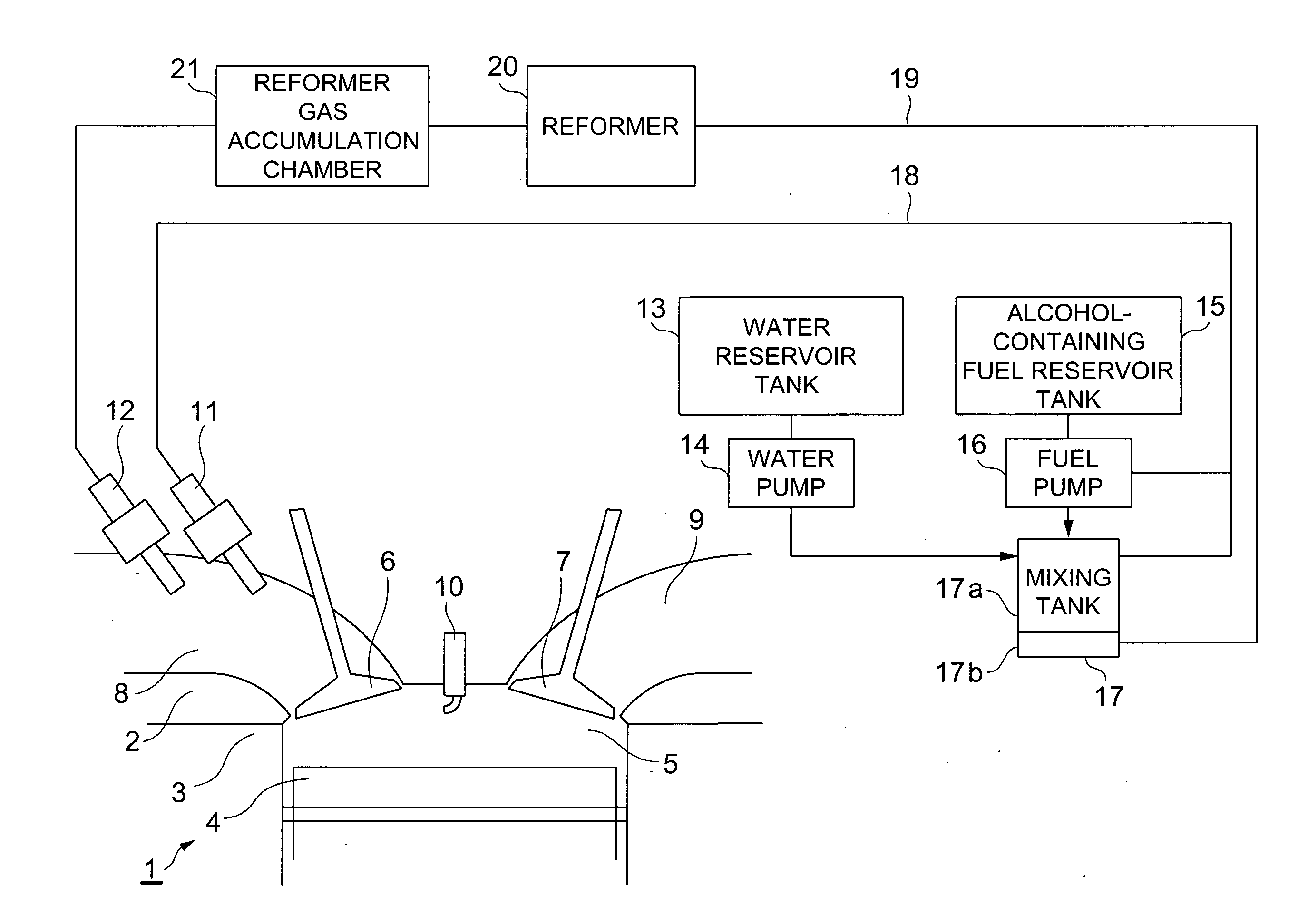
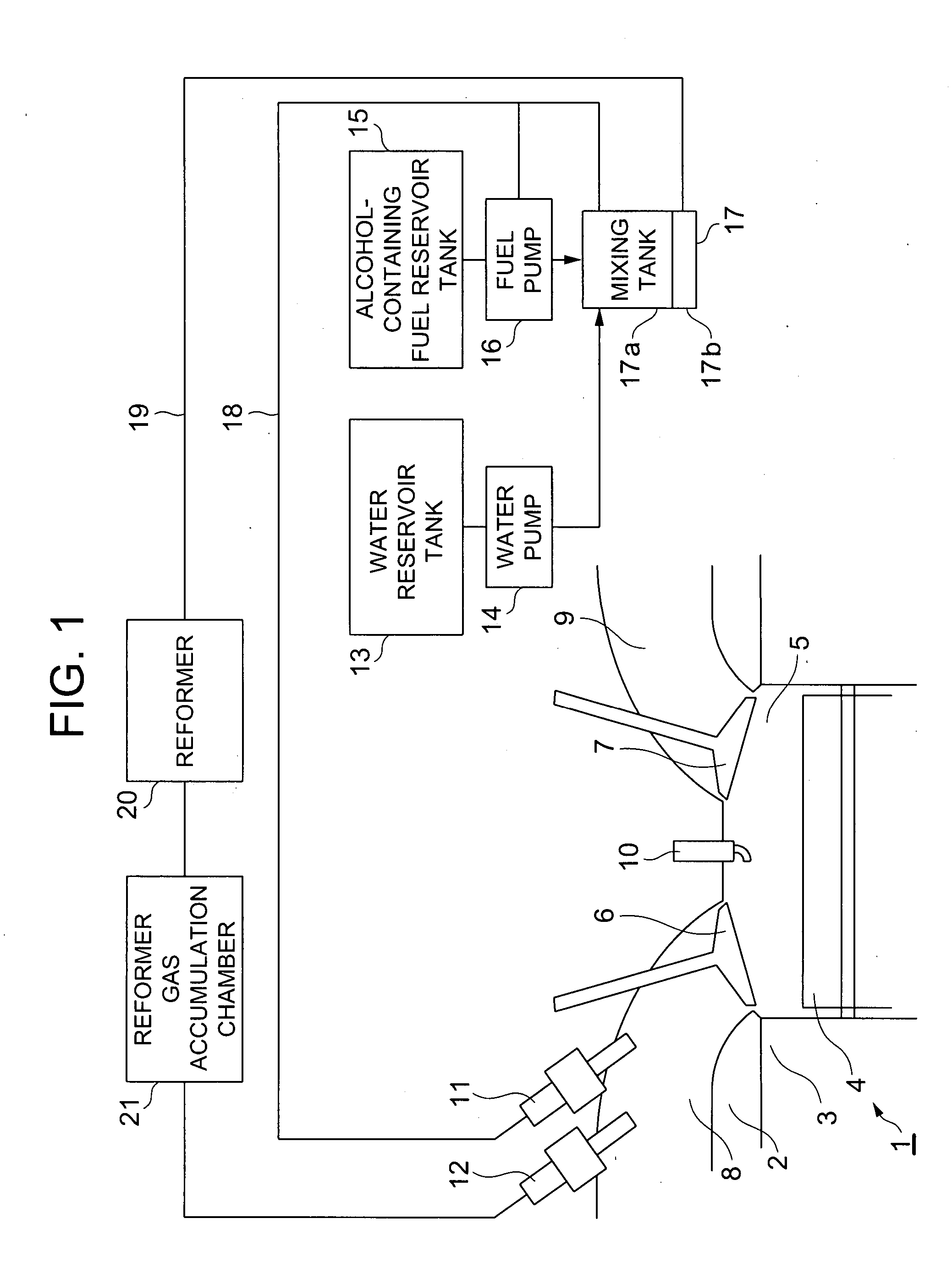
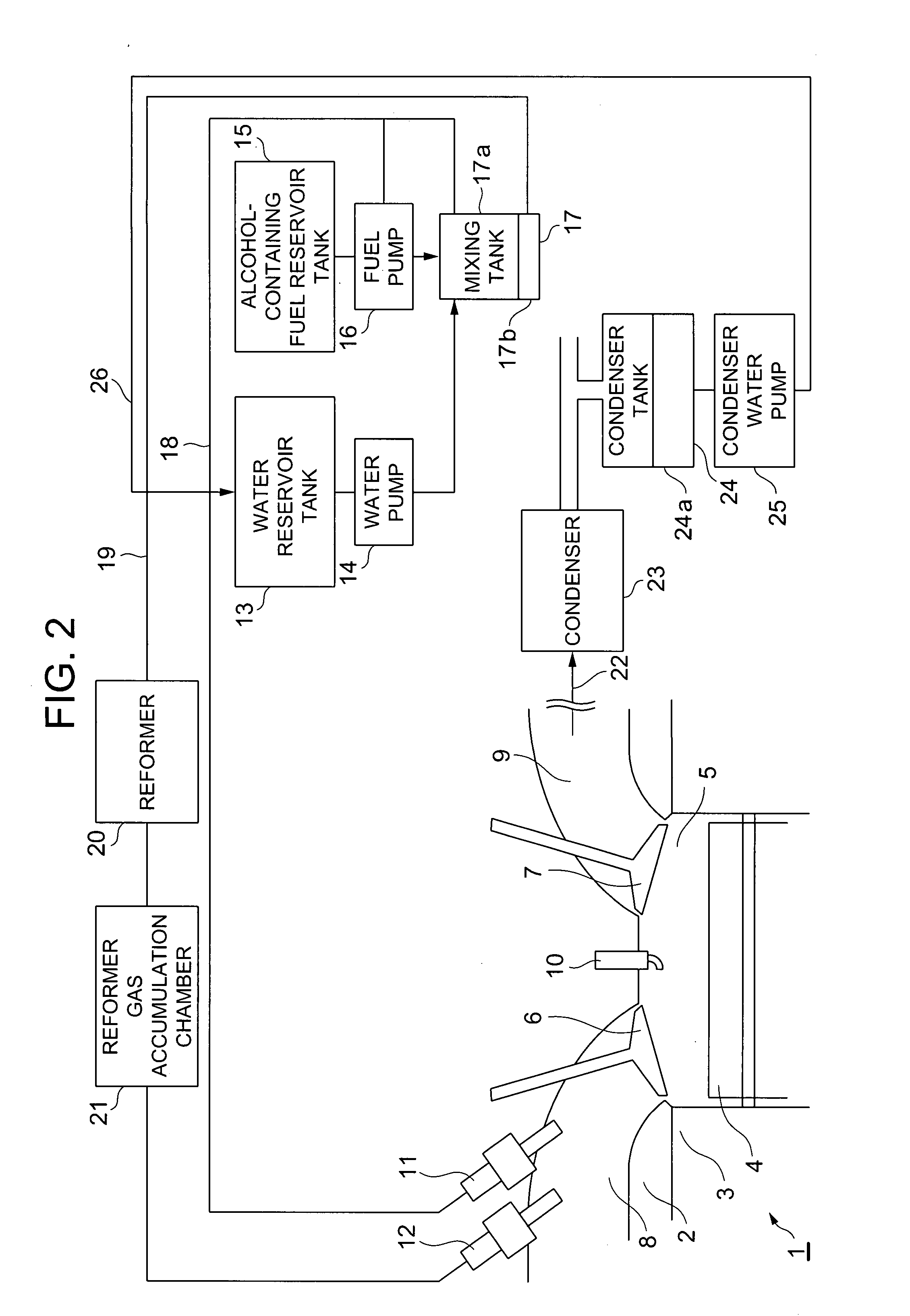
Reforming apparatus, internal combustion engine with reforming apparatus, and fuel cell system with reforming apparatus
InactiveUS20070204813A1Improve fuel consumption rateSimple and compactInternal combustion piston enginesNon-fuel substance addition to fuelElectricityFuel cells
A heat engine system includes a fuel reforming system for supplying a reformed gas to be combusted in an internal combustion engine or used to generate electricity in a fuel cell. An alcohol-containing fuel and water are mixed in a tank and separated into a hydrocarbon based fuel and the fluid mixture of alcohol and water. A reformer uses an endothermic reaction, such as a water vapor reforming process, to obtain the reformed gas from the fluid mixture.
Owner:NISSAN MOTOR CO LTD
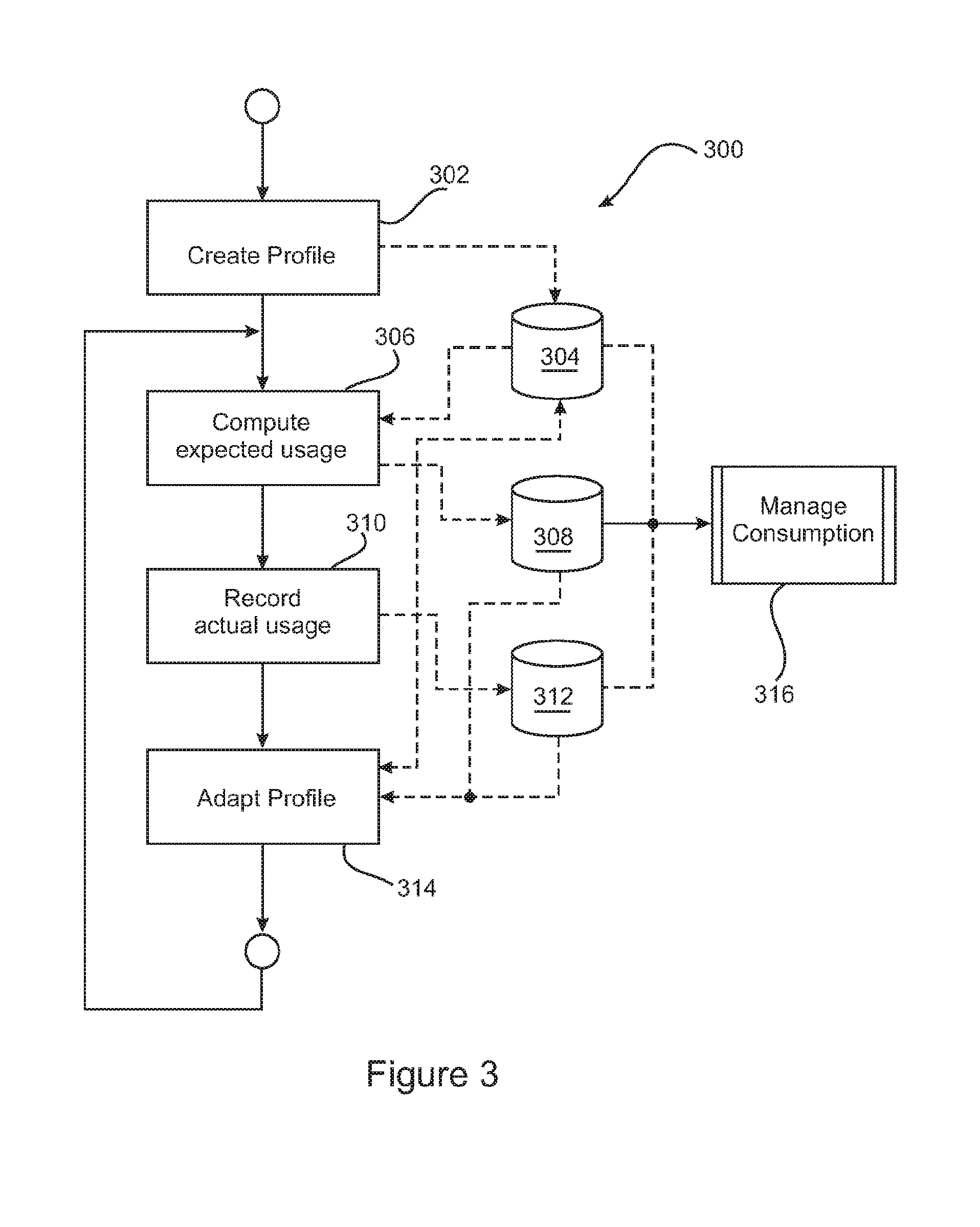
Method and system for energy management
ActiveUS20120215369A1Facilitates customised managementAccurate calculationMechanical power/torque controlLevel controlProcess engineeringEnergy expenditure
A method (300) of managing energy consumption associated with premises includes firstly generating (302) and storing an initial energy profile (304) of the premises. The profile (304) includes information characterising the premises, such as occupancy patterns, function of the premises, geographical location, installed appliances (108), and so forth. An expected energy usage (308) associated with the premises is computed over a predetermined time period based upon the information in the initial energy profile (304). Actual energy usage (312) associated with the premises is then recorded over the predetermined time period and the energy profile (304) is adaptively updated based upon the recorded energy usage (312). The energy profile (304) and the actual energy usage (312) are used to manage energy consumption associated with the premises. An installable system (100) and apparatus (102) for implementing the method at premises are also provided.
Owner:LA TROBE UNIVERSITY
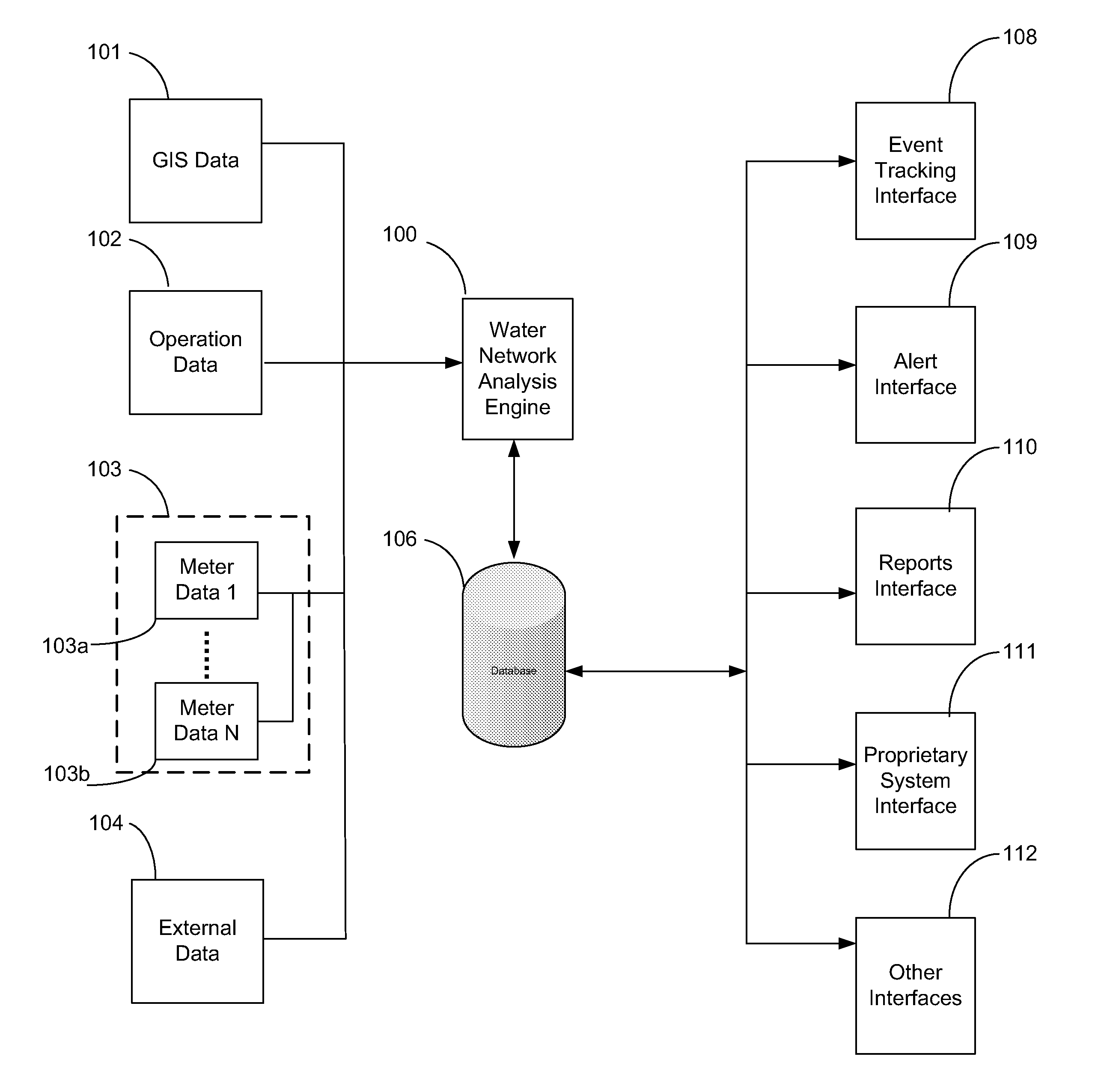
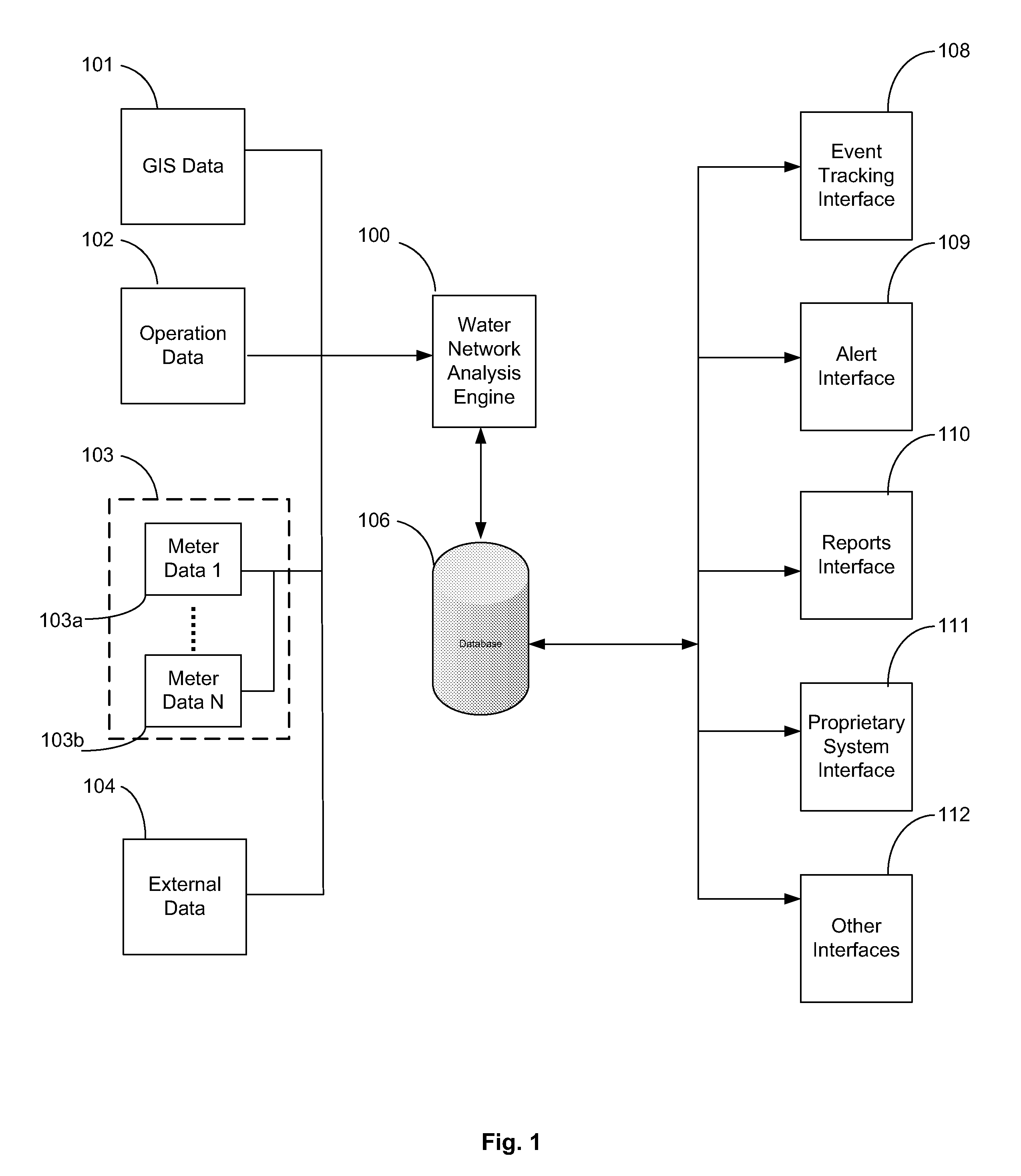
System and method for monitoring resources in a water utility network
ActiveUS20110215945A1The result is accurateReduce or eliminate false alarmsElectric signal transmission systemsMeasurement of fluid loss/gain rateWater utilityTurbidity
A computerized method for monitoring a water utility network, the water utility network comprising a network of pipes for delivering water to consumers and a plurality of meters positioned within the pipes across the water distribution network. The method includes receiving meter data representing parameters measured by the meters, such as flow, pressure, chlorine level, pH and turbidity of the water being distributed through the pipes. The method also includes receiving secondary data from sources external to the meters and representing conditions affecting consumption of water in a region serviced by the water utility network such as weather and holidays. The meter and secondary data is analyzed using statistical techniques to identify water network events including leakage events and other events regarding quantity and quality of water flowing through the pipes and operation of the water network. The events are reported to users via a user interface.
Owner:TAKADU
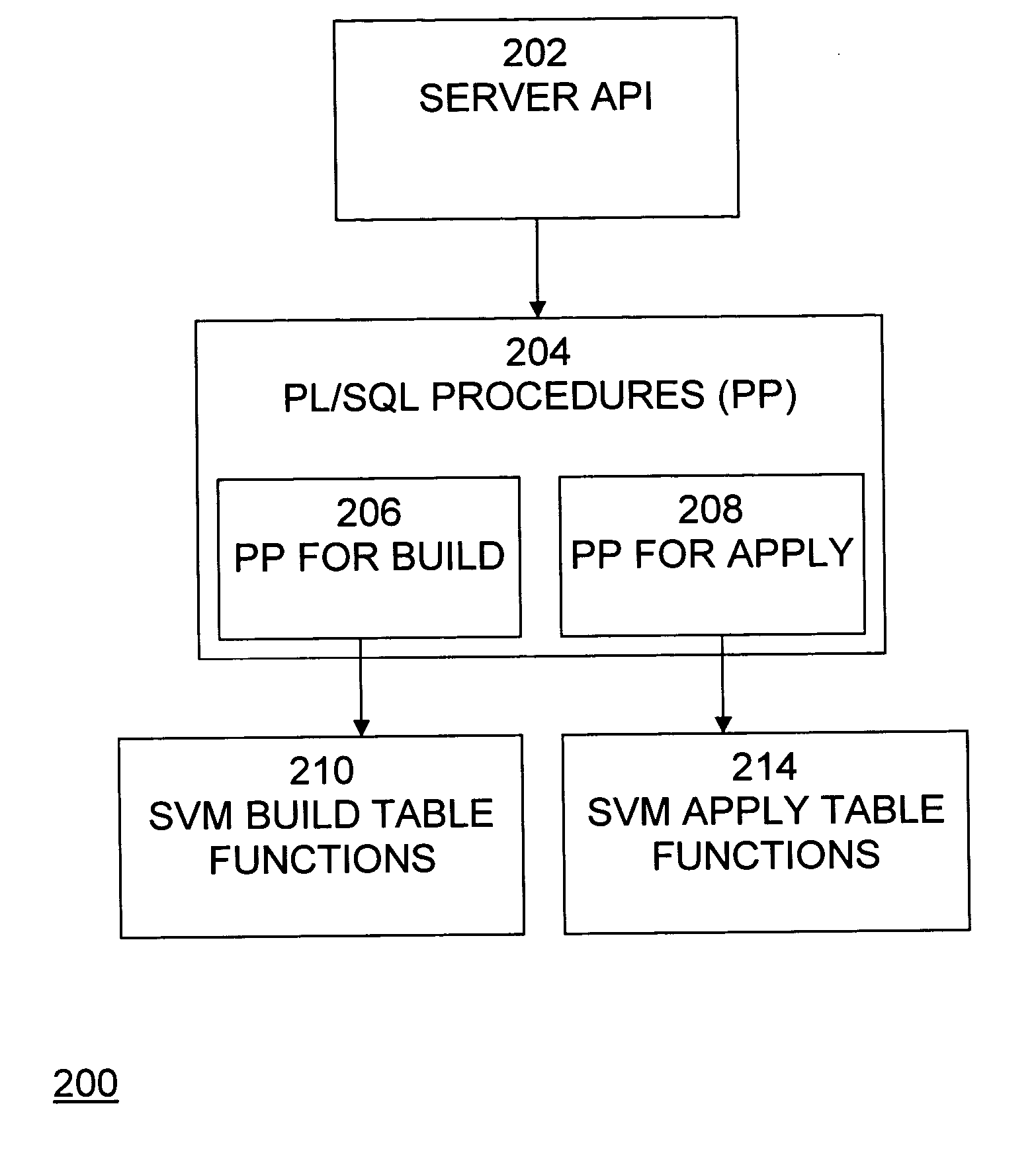
Support vector machines processing system
ActiveUS20050049990A1Reduce computational costReduce data movementDigital data processing detailsDigital computer detailsClient-sideData security
An implementation of SVM functionality improves efficiency, time consumption, and data security, reduces the parameter tuning challenges presented to the inexperienced user, and reduces the computational costs of building SVM models. A system for support vector machine processing comprises data stored in the system, a client application programming interface operable to provide an interface to client software, a build unit operable to build a support vector machine model on at least a portion of the data stored in the system, based on a plurality of model-building parameters, a parameter estimation unit operable to estimate values for at least some of the model-building parameters, and an apply unit operable to apply the support vector machine model using the data stored in the system.
Owner:ORACLE INT CORP
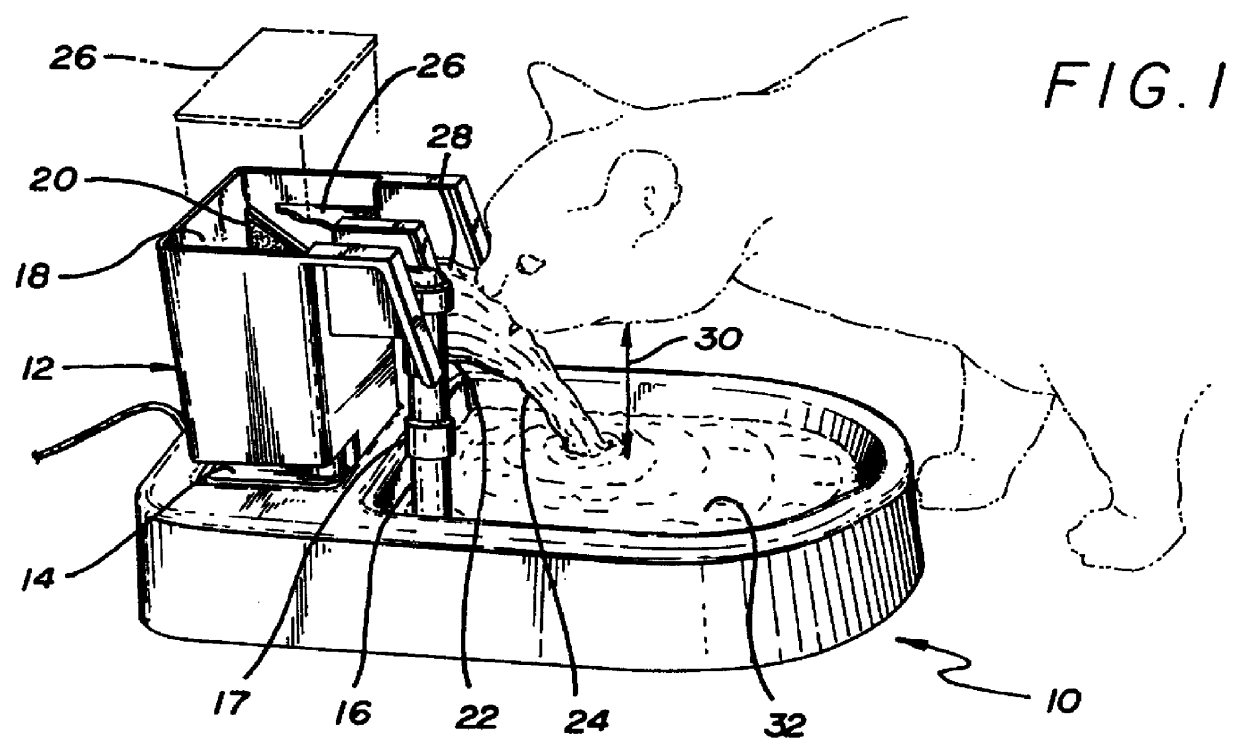
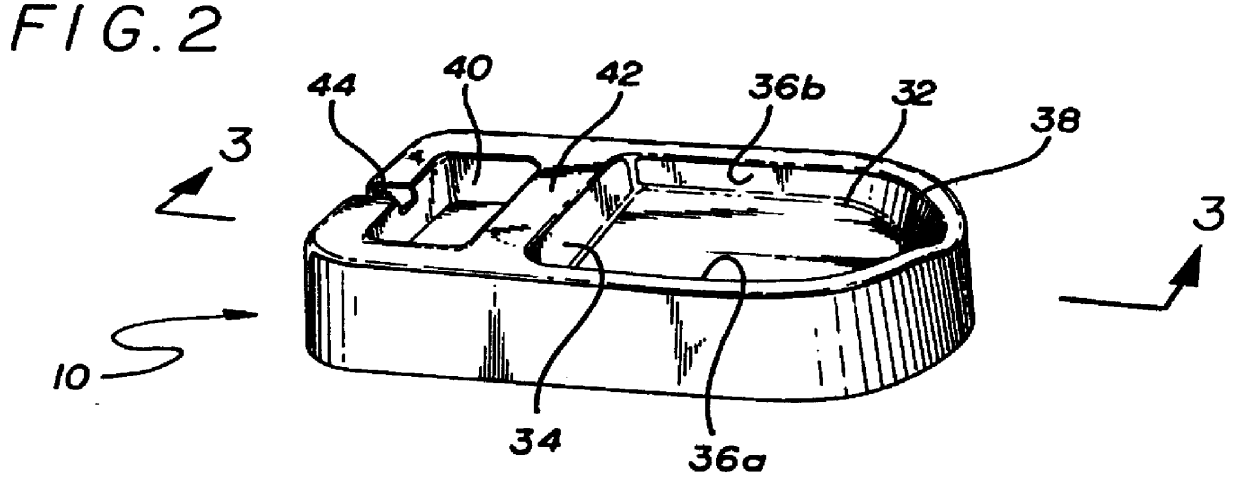
Animal waterer
InactiveUS6055934AEnhancing its appealDecreases unwanted behaviorAnimal watering devicesTransportation and packagingFree fallingFiltration
A device is disclosed which comprises a drinking fountain for animals in the configuration of a free falling stream of water, or continuous waterfall. A pump moves water from a reservoir upward to a discharge ramp, or ramps, where water spills over into a receptacle. The reservoir and receptacle may consist of the same part. The cascade of water takes advantage of a preference demonstrated by animals for moving drinking water. The waterfall action also aerates the water and increases freshness, by breaking the surface tension of the standing water and drawing in oxygen from the atmosphere. Filtration of the circulating water in this self-contained system is easily accomplished.
Owner:RADIO SYST CORP
Air conditioner for vehicle
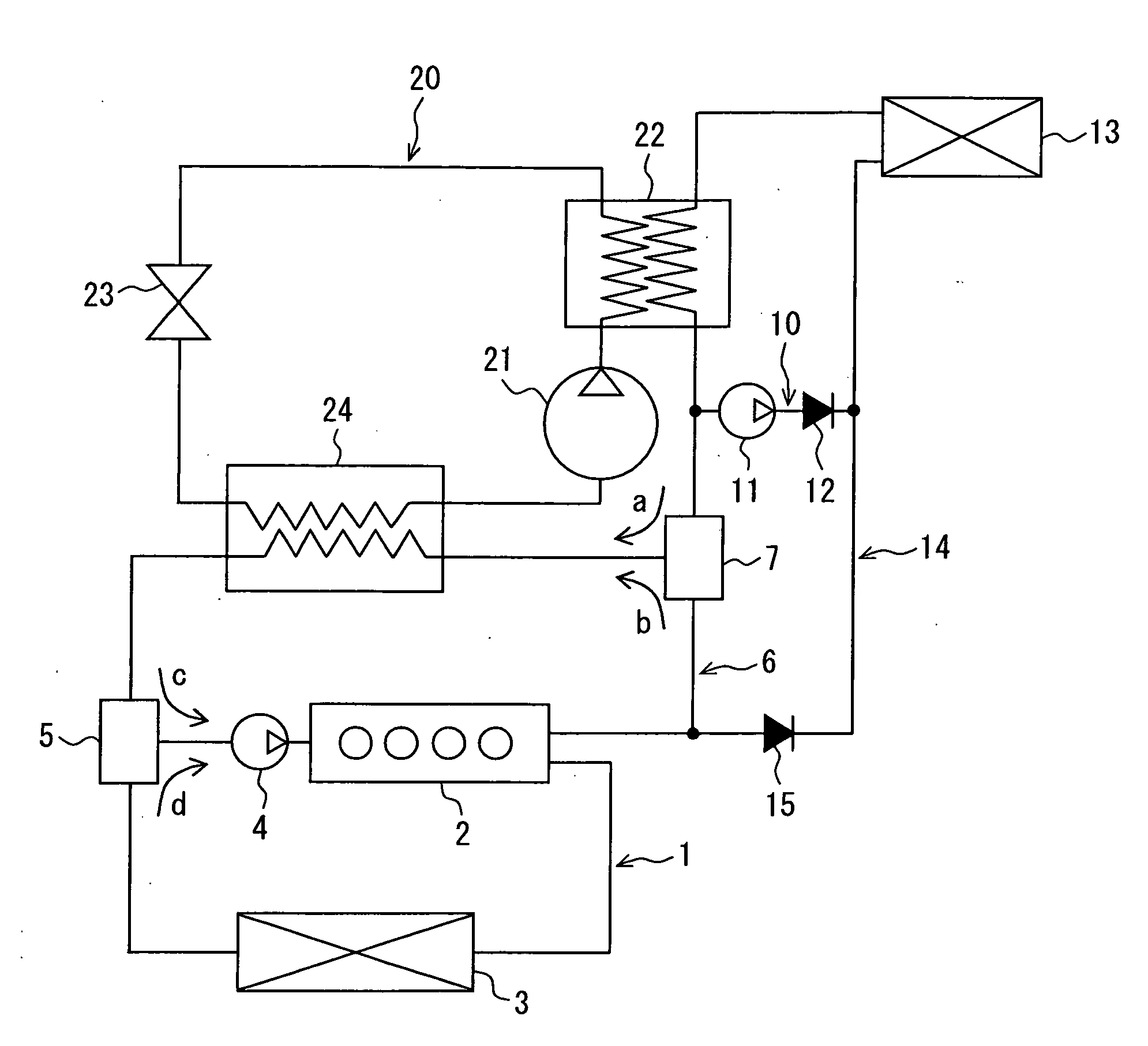
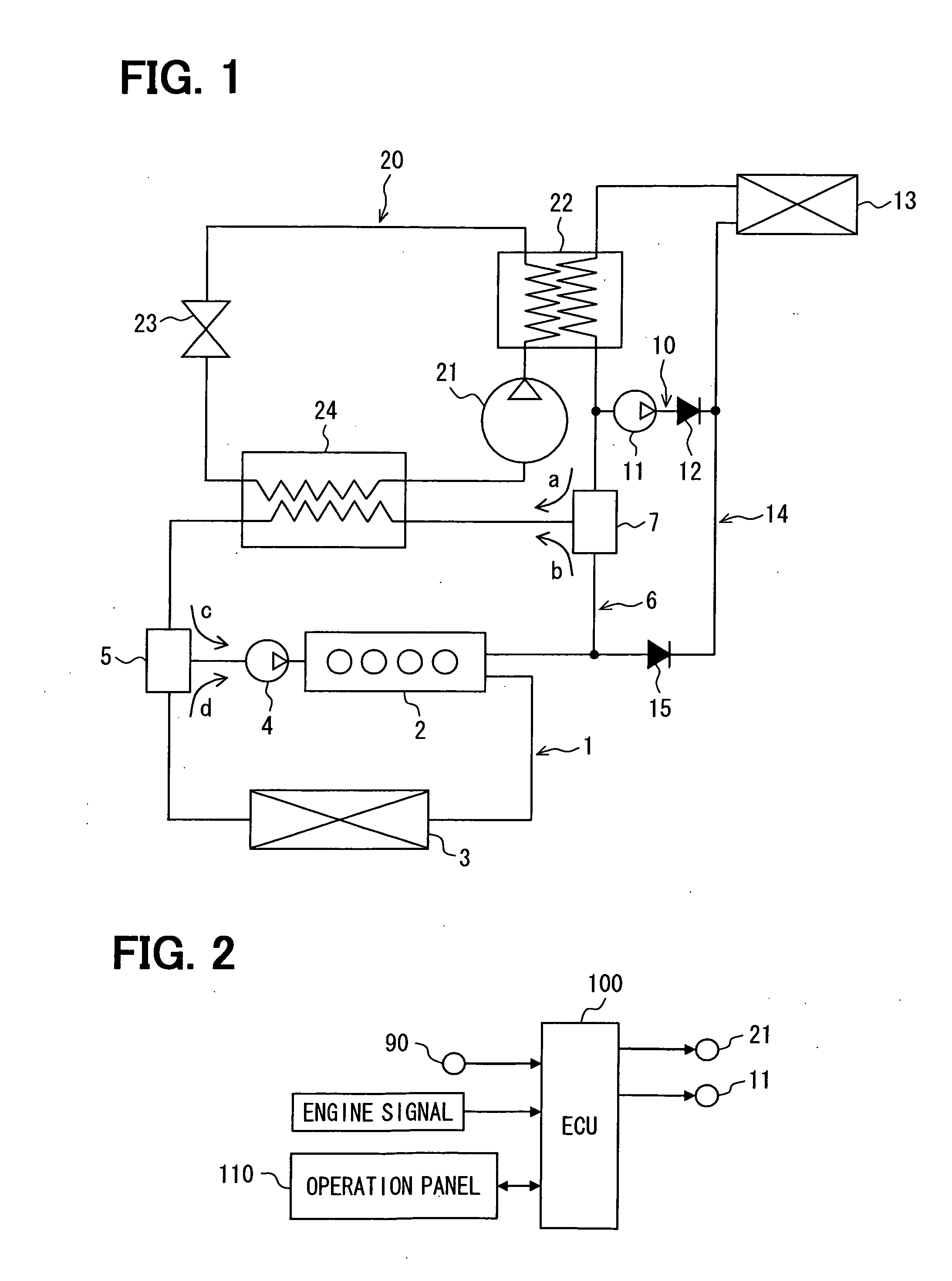
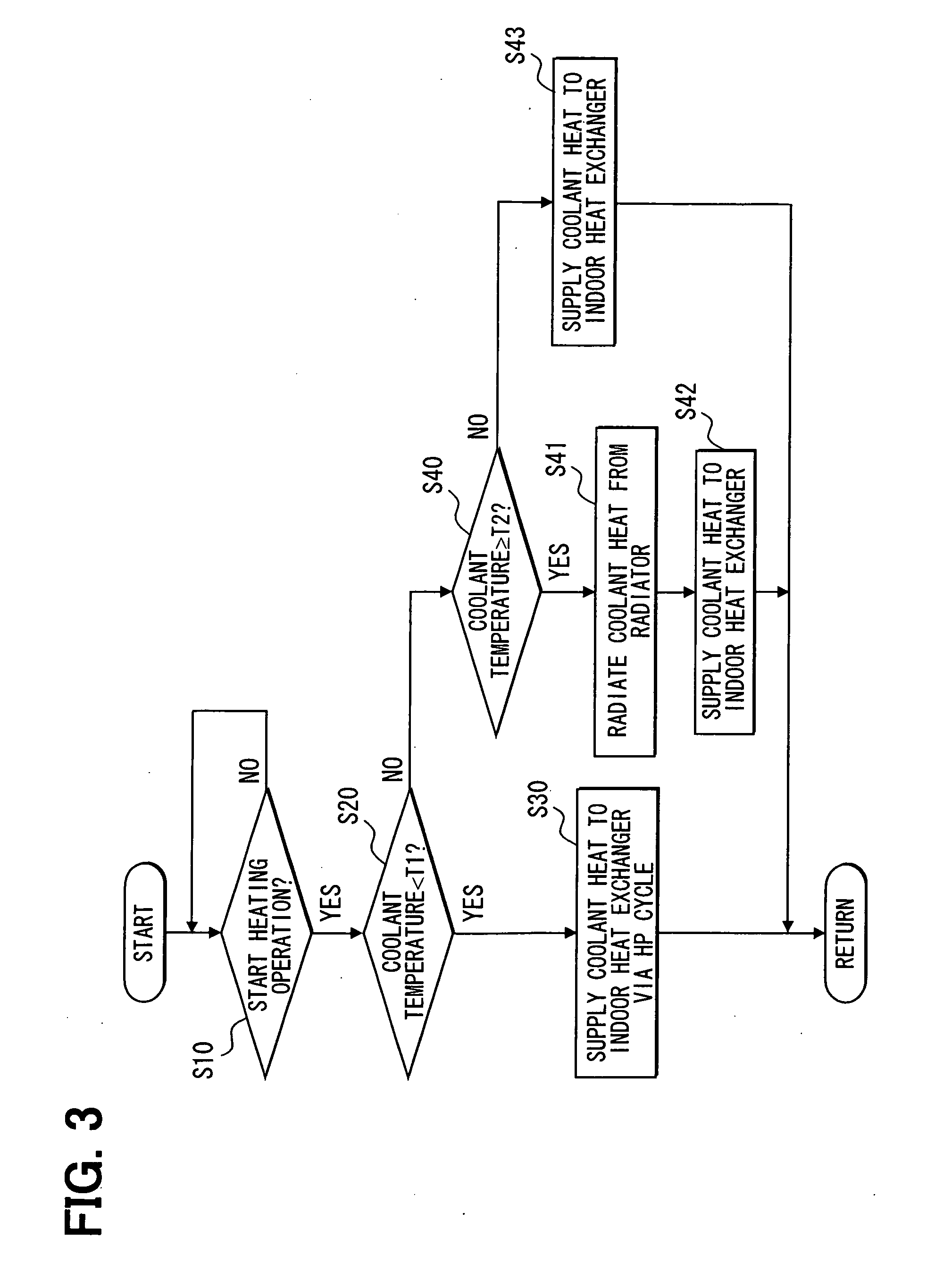
InactiveUS20100281901A1Solve insufficient heating capacityReduce energy lossAir-treating devicesRailway heating/coolingCoolant flowEngineering
In an air conditioner for a vehicle, in a heating operation for heating a vehicle compartment, when heating capacity is obtained by flowing a coolant through an inside of an indoor heat exchanger, the coolant flows directly in the inside of the indoor heat exchanger to heat air to be supplied to the vehicle compartment. In contrast, when the heating capacity is not obtained by flowing the coolant through the inside of the indoor heat exchanger, the coolant flows through a first water-refrigerant heat exchanger and a refrigerant in a heat pump cycle circulates so that heat of the coolant is absorbed by the refrigerant in the first water-refrigerant heat exchanger, and the air is heated in the indoor heat exchanger by using heat of the refrigerant that has absorbed the heat of the coolant.
Owner:DENSO CORP +1
Marble-like composite materials and methods of preparation thereof
InactiveUS20140127450A1Low costIncrease consumptionLayered productsCoatingsCalcium silicateFlexural strength
The invention provides novel marble-like composite materials and methods for preparation thereof. The marble-like composite materials can be readily produced from widely available, low cost raw materials by a process suitable for large-scale production. The precursor materials include calcium silicate and calcium carbonate rich materials, for example, wollastonite and limestone. Various additives can be used to fine-tune the physical appearance and mechanical properties of the composite material, such as pigments (e.g., black iron oxide, cobalt oxide and chromium oxide) and minerals (e.g., quartz, mica and feldspar). These marble-like composite materials exhibit veins, swirls and / or waves unique to marble as well as display compressive strength, flexural strength and water absorption similar to that of marble.
Owner:RIMAN RICHARD E +1
Decorative base paper with an ink-jet receiving layer
InactiveUS6706372B2Increase consumptionImage definition is often inadequateDecorative surface effectsSpecial ornamental structuresPulp and paper industry
Owner:TECHNOCELL DEKOR GMBH & CO KG
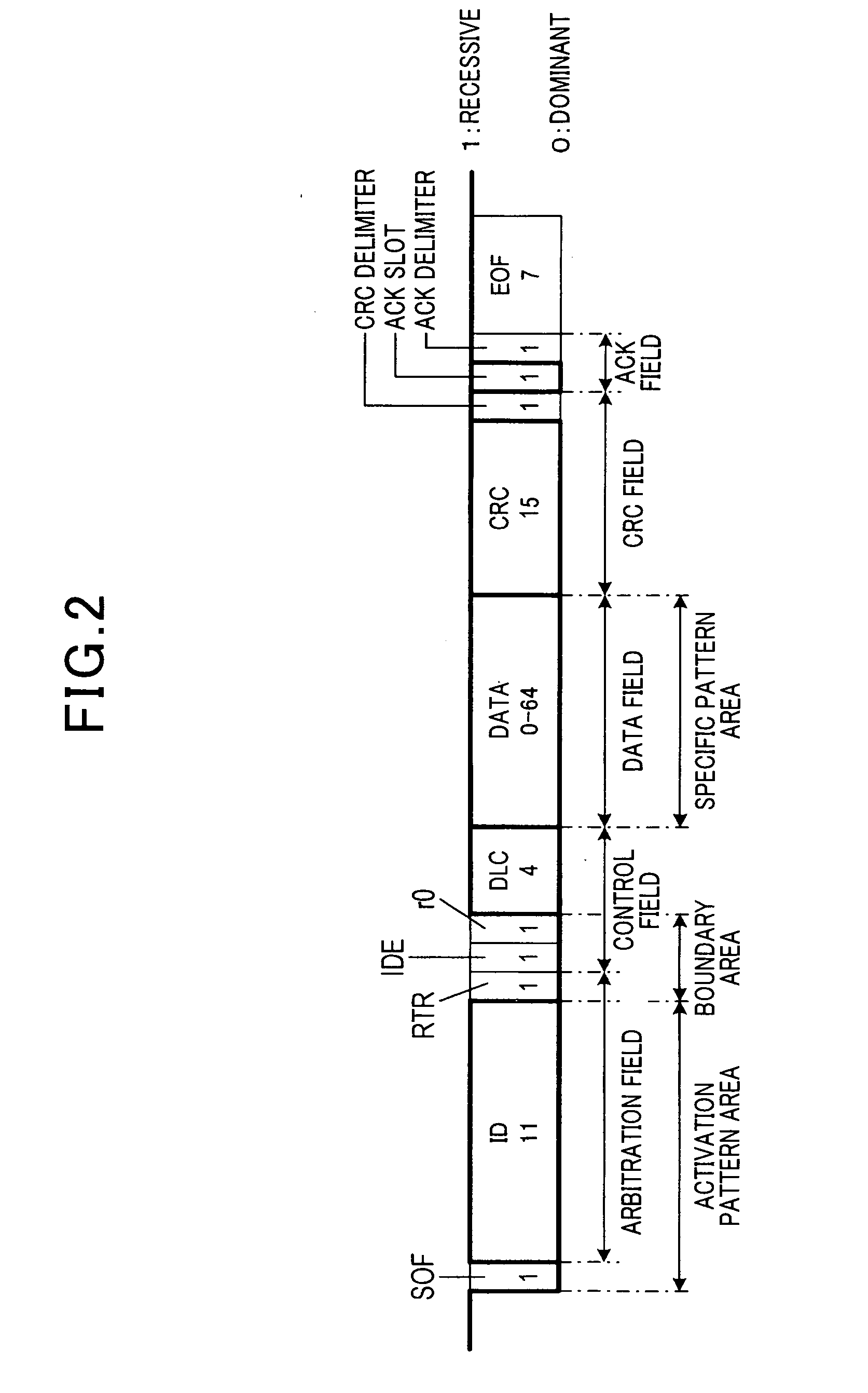
Communication system with a plurality of nodes communicably connected for communication based on NRZ (non return to zero) code
InactiveUS20120051241A1Increase power consumptionAverage power consumptionEnergy efficient ICTError preventionCommunications systemSignal on
In a communication system, plural nodes are communicably connected to a communication line and mutually communicate based on an NRZ (Non Return to Zero) code. Each node detects, as a data frame head, a dominant level when a signal on the line changes to a dominant level during a stand-by state of the line. An activation frame is transmitted during a sleep mode. The activation frame has an activation pattern area storing therein a bit pattern showing that the frame is the activation frame, a specific pattern area storing therein a bit pattern showing a node to be activated, a boundary position satisfying a predetermined boundary condition and being a boundary between the activation and specific pattern areas. Each node performs a switchover from the sleep mode to a normal mode based on the bit patterns in the activation and specific pattern areas and information given by the boundary position.
Owner:NIPPON SOKEN +1
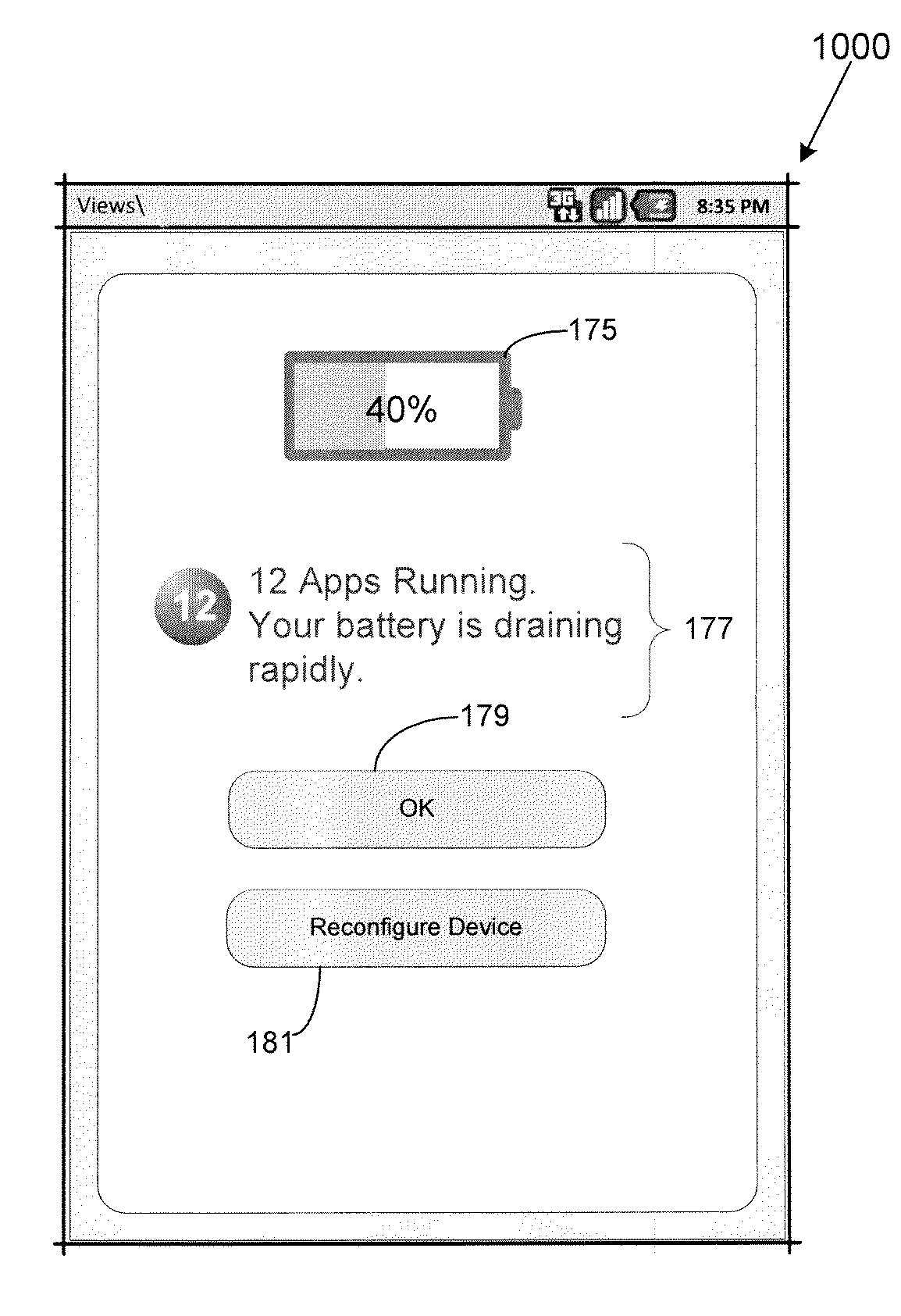
Dynamic battery saver for a mobile device
ActiveUS8958854B1Improve abilityImprove abilitiesPower managementTransmission systemsEmbedded systemManagement functions
A user can manage battery consumption of a mobile device using a mobile device battery management program which provides improved battery management functions, such as a dynamic battery use estimator, a battery threshold manager, and a profile based battery manager. Using the dynamic battery use estimator, the user can input different configuration settings of the mobile device and get estimates of the projected remaining battery life for the inputted configuration settings before applying any change to the operational configuration setting. The battery threshold manager allows the user to select a trigger and set its associated condition for turning off at least one application, service, or component of the mobile device when the condition is reached. Using the profile based battery manager, the user can select one of multiple profiles and set the mobile device to operate in an operational configuration setting corresponding to the selected profile.
Owner:CELLO PARTNERSHIP DBA VERIZON WIRELESS
Cluster system and failover method for cluster system
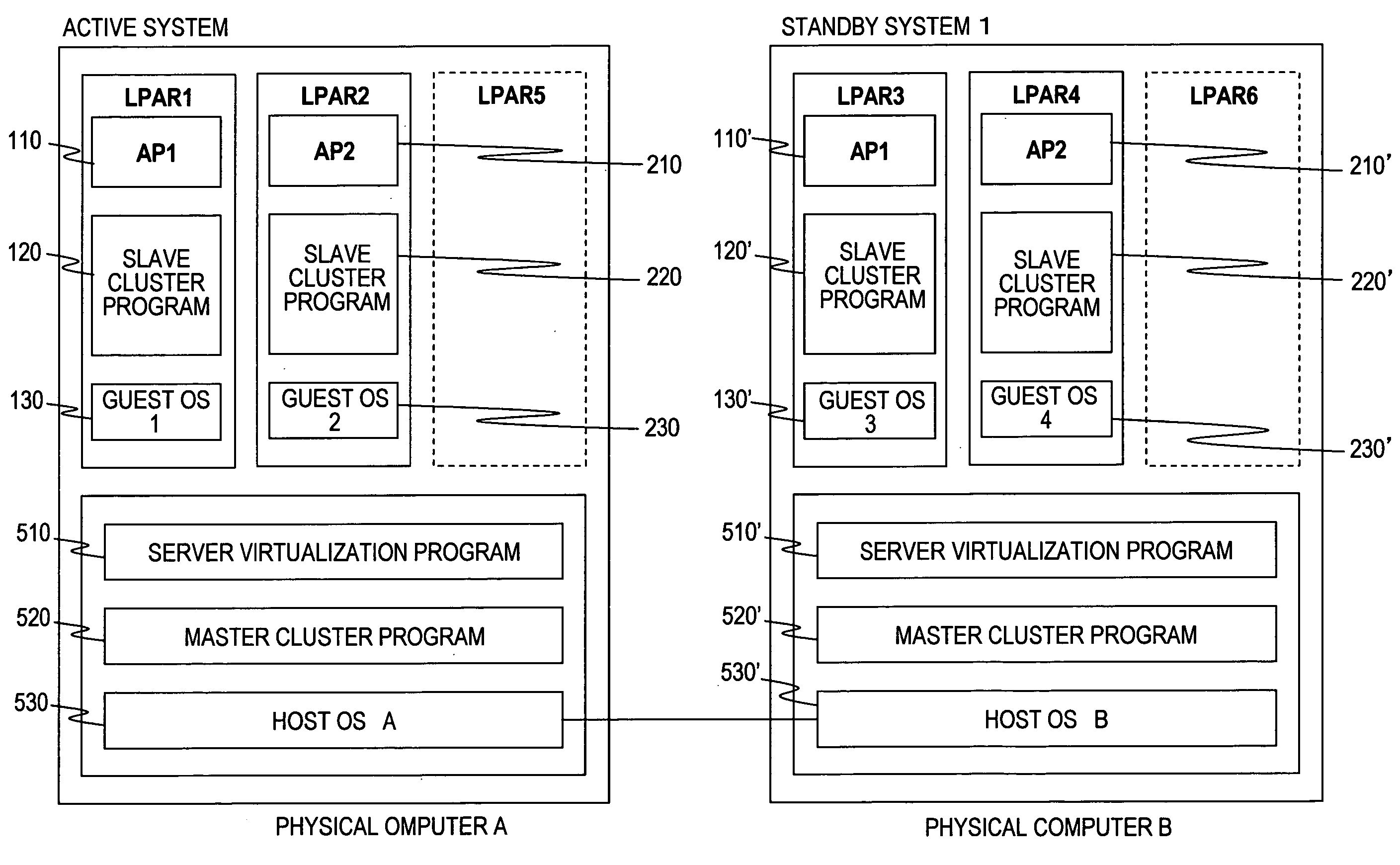
InactiveUS20080162983A1Lower performance requirementsIncrease consumptionFault responseComputer resourcesFailover
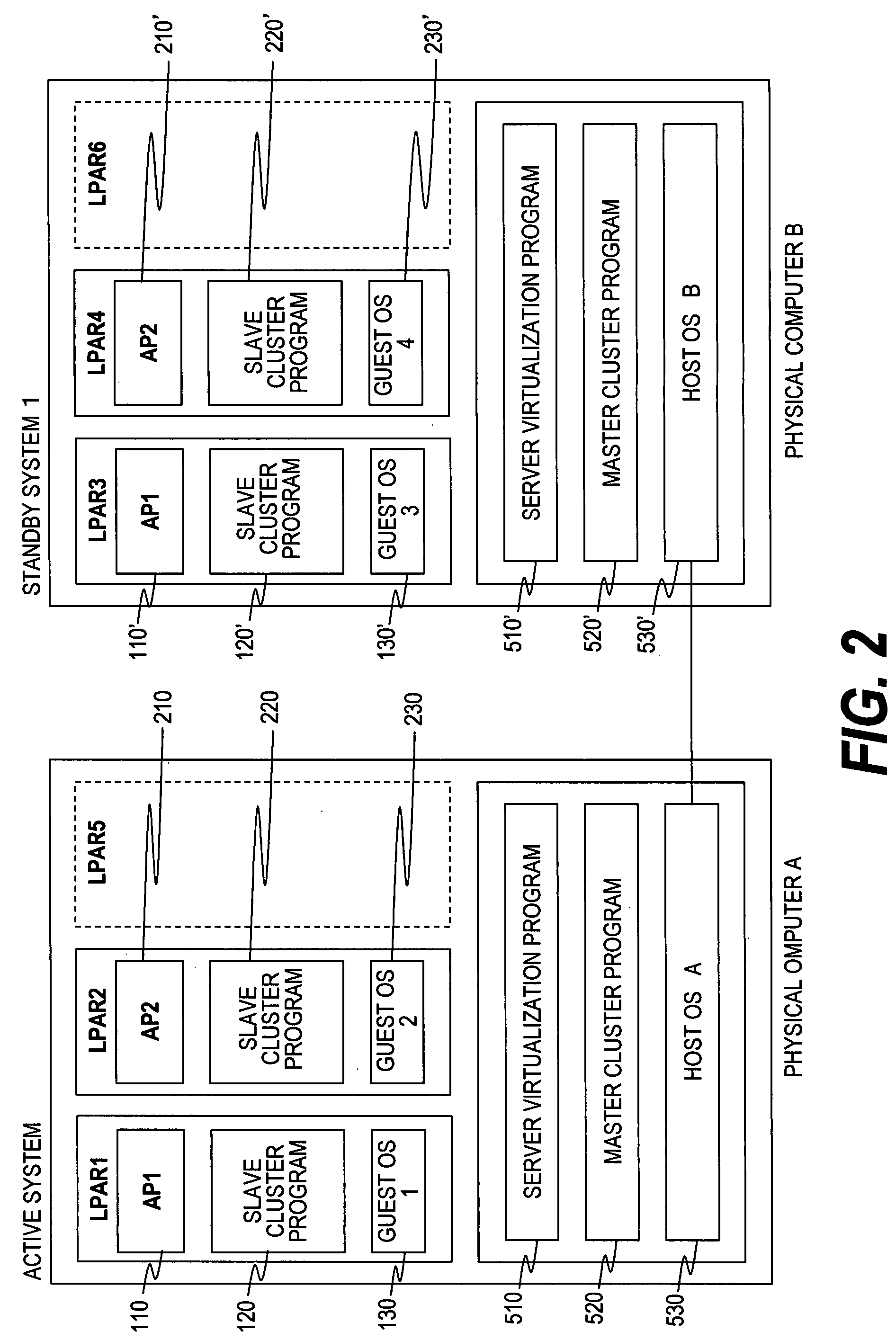
Provided is a failover method for a cluster system for realizing smooth failover of the guest OS's, even when there are many guest OS's, while reducing consumption of computer resources of a server. Smooth failover is realized by preventing competition during failover even when the number of guest OS's is increased. In a cluster configuration in which a slave / master cluster program is operated in a guest OS / host OS, the master cluster program (510) collects and transmits heartbeats of the slave cluster program, thereby realizing failure monitoring through the certain amount of heartbeats without depending on the number of guest OS's. Further, when the master cluster program monitors failures of the slave cluster program of its own computer to find a normal operation of the guest OS, the amount of communication through heartbeats is reduced by eliminating the necessity of communication to a standby system slave cluster program.
Owner:HITACHI LTD
Electrical device utilizing charge recycling within a cell
InactiveUS7567372B2Increase power consumptionGood optical performanceStatic indicating devicesSemiconductor/solid-state device manufacturingElectricityElectrical battery
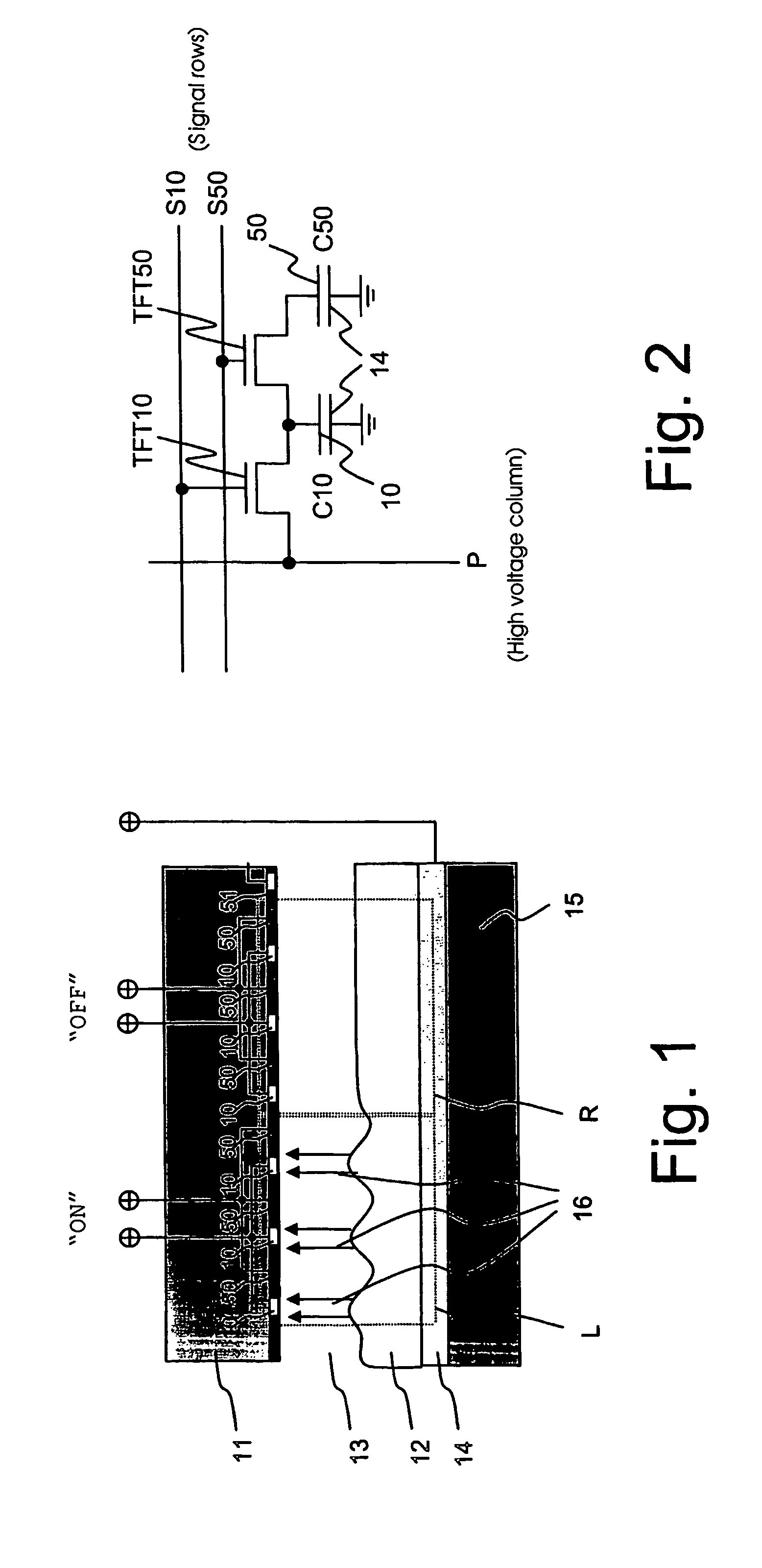
The invention relates to an electrically controlled device, which device comprises at least one electrically and individually controllable cell (L,R) with at least two separate electrode structures (10,50) arranged within the cell, each of the electrode structures capable of storing electric charges (C10,C50). The device further comprises a charge transfer mechanism (P,S10,S20,TFT10,TFT50) to transfer electric charges in a temporally controlled manner between the at least two separate electrode structures (10,50), and that for at least one of the electrode structures within the cell, the charge transfer mechanism comprises substantially the only means for providing electrical power and / or electrical driving. The invention reduces the power consumption of the electrode structures by use of a new type of in-cell type charge recycling. The invention is especially suitable to be used in light modulator components based on the use of electrically deformable viscoelastic materials.
Owner:NOKIA CORP
Attenuated computer virus vaccine
InactiveUS20050204150A1Increase in bandwidth consumptionReduce rateUser identity/authority verificationUnauthorized memory use protectionIp addressSelection algorithm
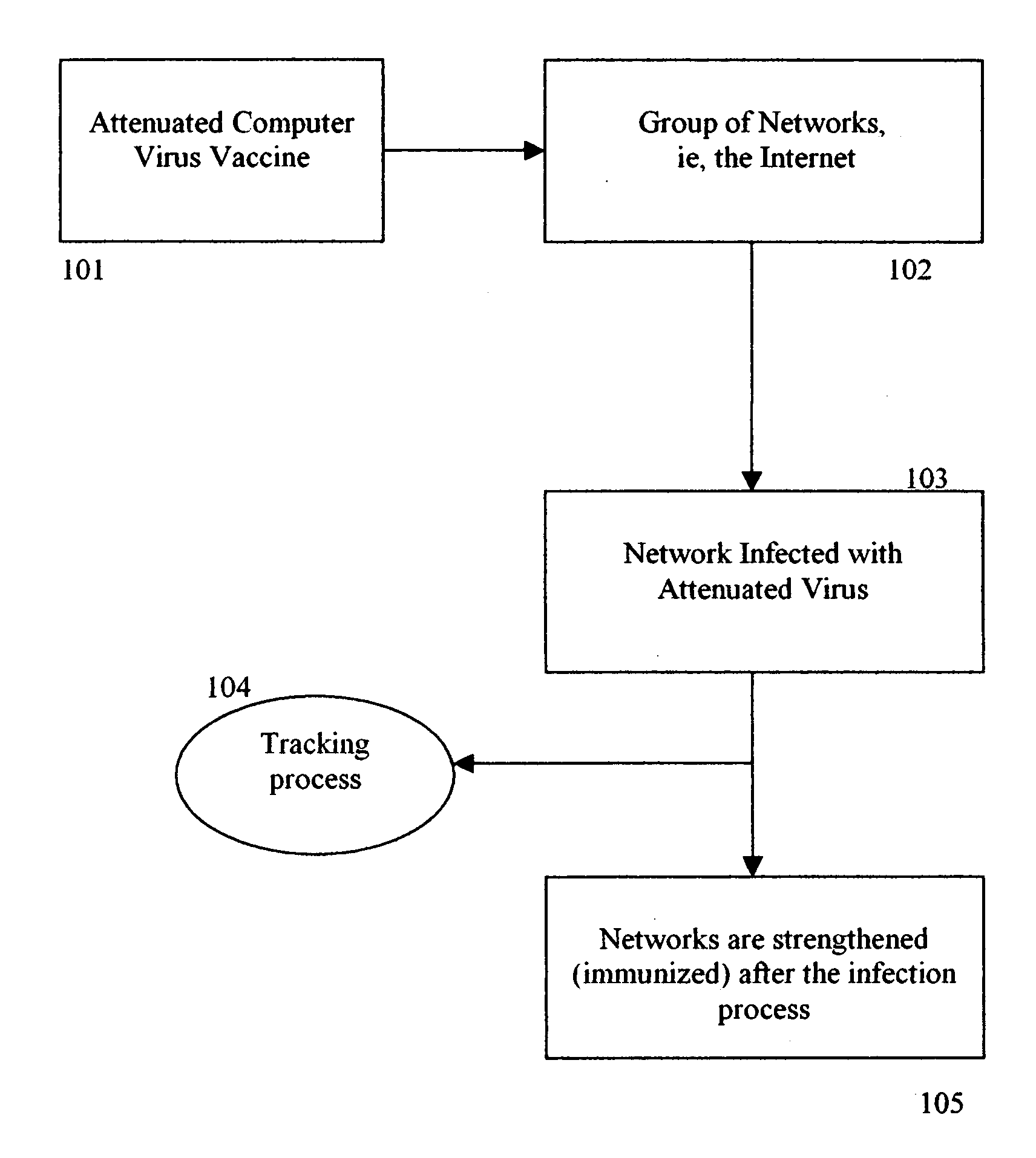
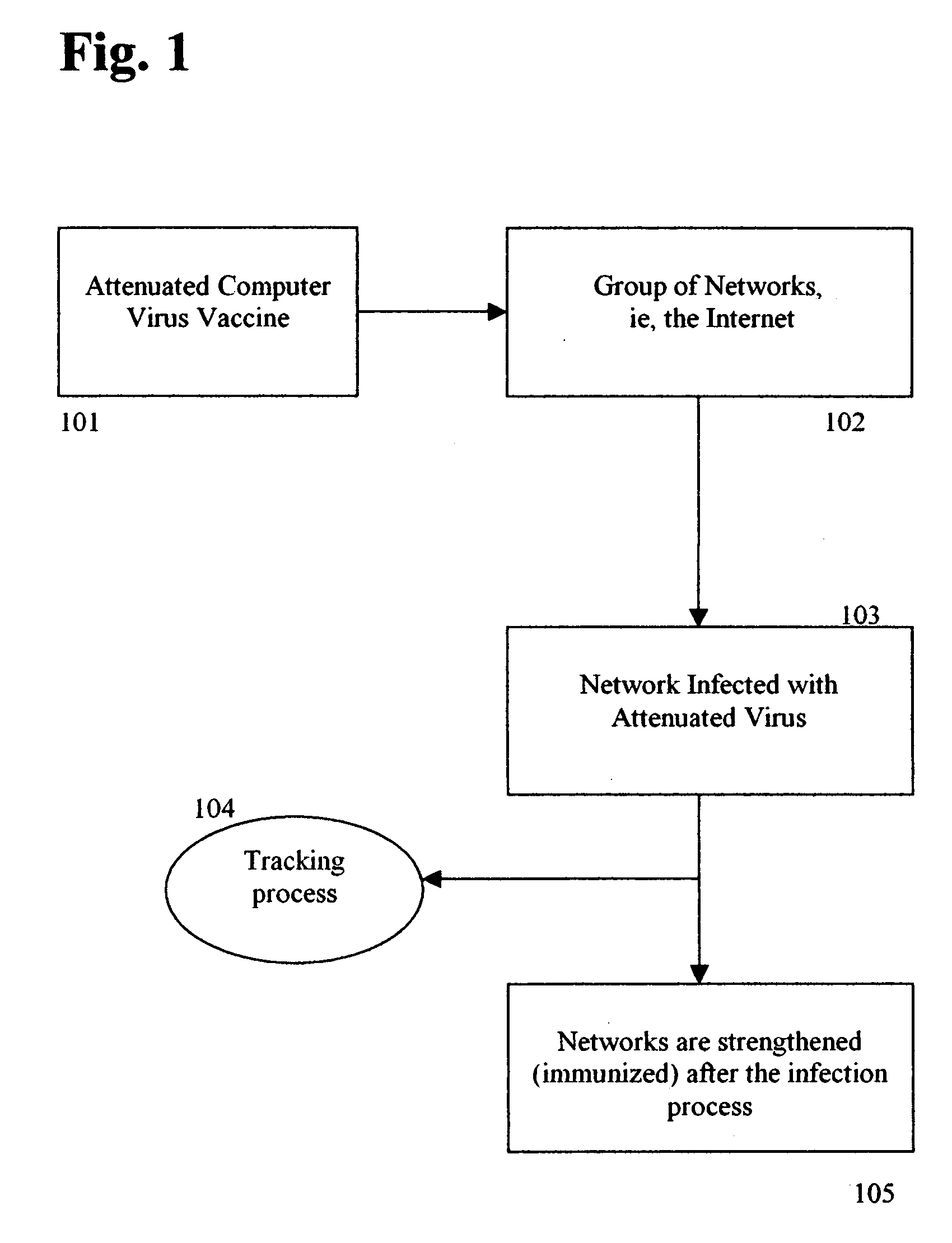
A method and apparatus optimizes the protection of computing networks. This protection utilizes attenuated (weakened) strains of live, replicating, malicious code such as viruses and worms, analogous to the development of live, attenuated, human vaccines in the medical field. In a preferred embodiment, this is achieved by (1) attenuating a malicious program, e.g. a virus or worm, or software vulnerability by limiting its virulence, i.e., limiting its damage and resource usage, (2) modifying the virus to confer immunity on the network that it infects, e.g., automatically patching a vulnerability, or marking the infected host as immune to further infection, (3) releasing the newly attenuated virus into the network, (4) tracking the attenuated virus and its success rate (e.g., rate and ratio of successfully patched to un-patched vulnerable hosts), and (5) limiting the spread of the virus vaccine, e.g., emergency termination, timeout to die, “white-list” of hosts not to touch, network IP address limitation, restricted IP ranges, variable address selection algorithm.
Owner:PEIKARI CYRUS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com