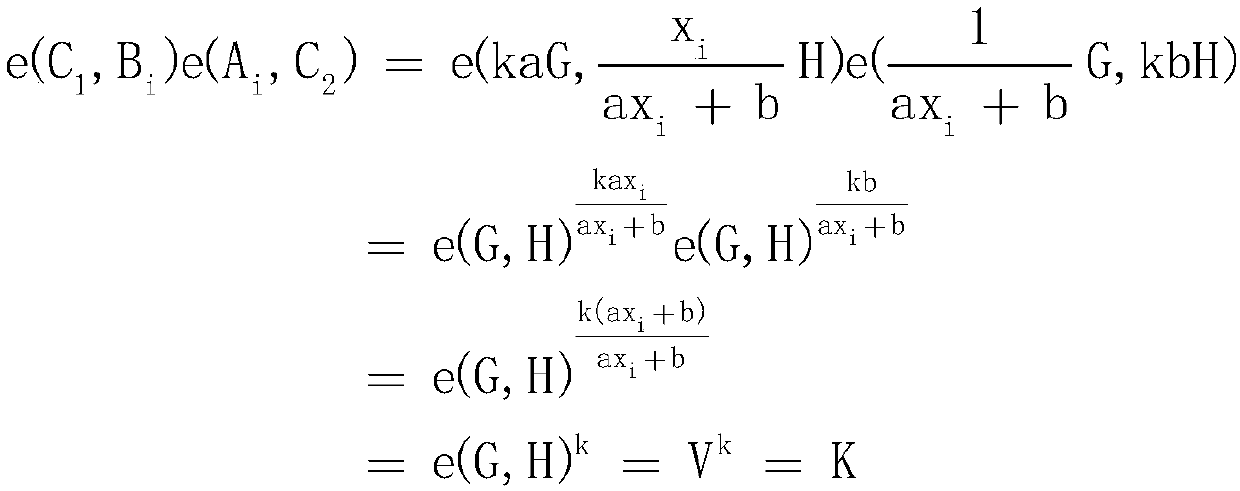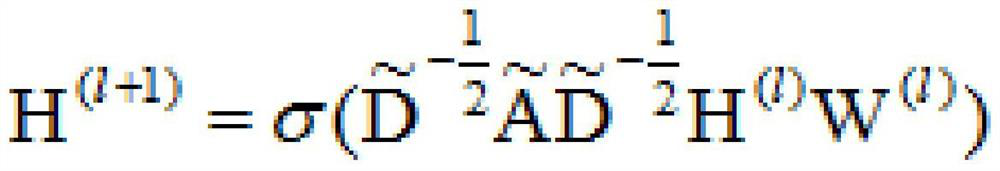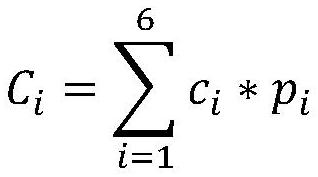Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
62results about How to "Satisfy Integrity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
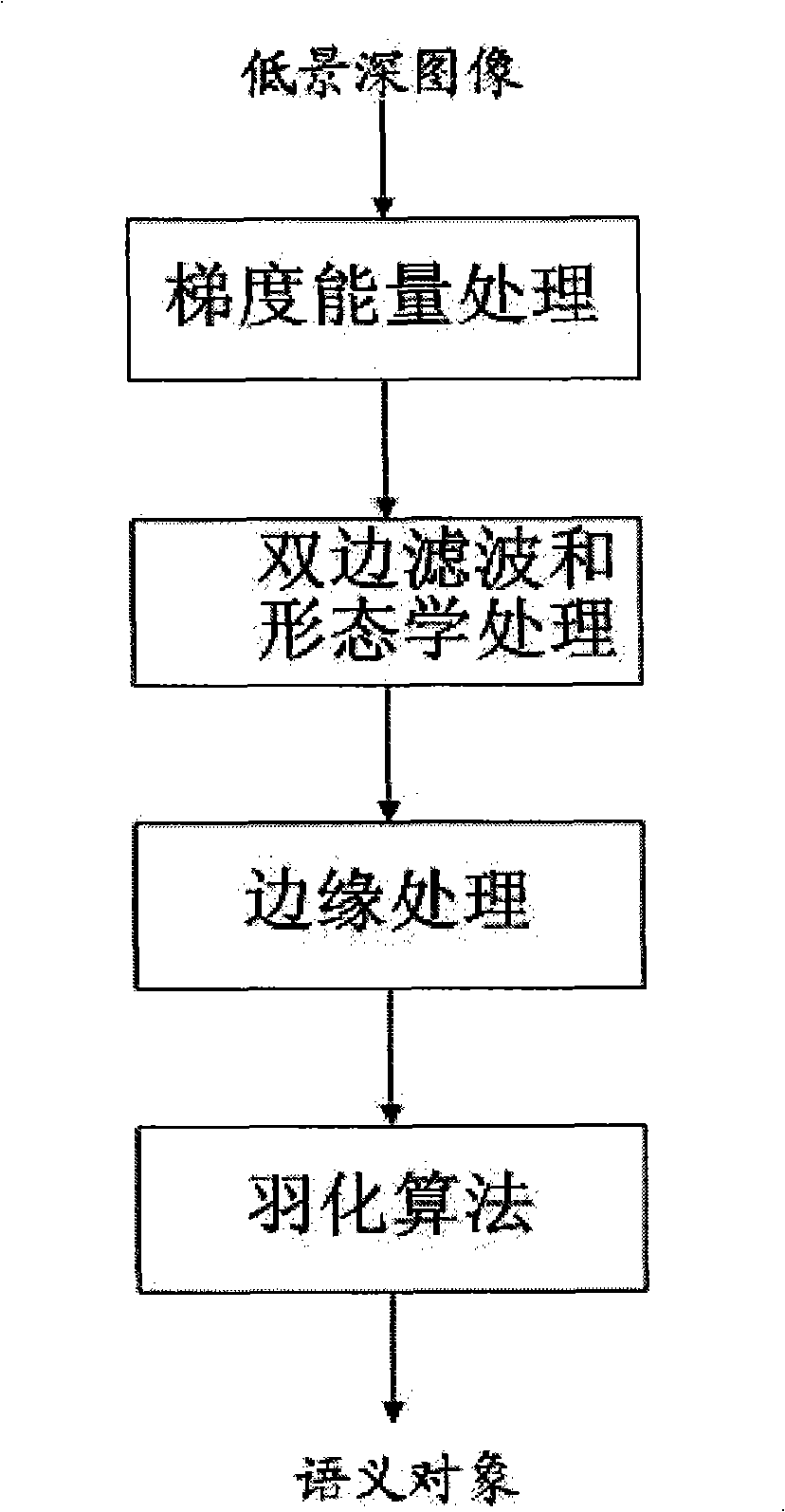
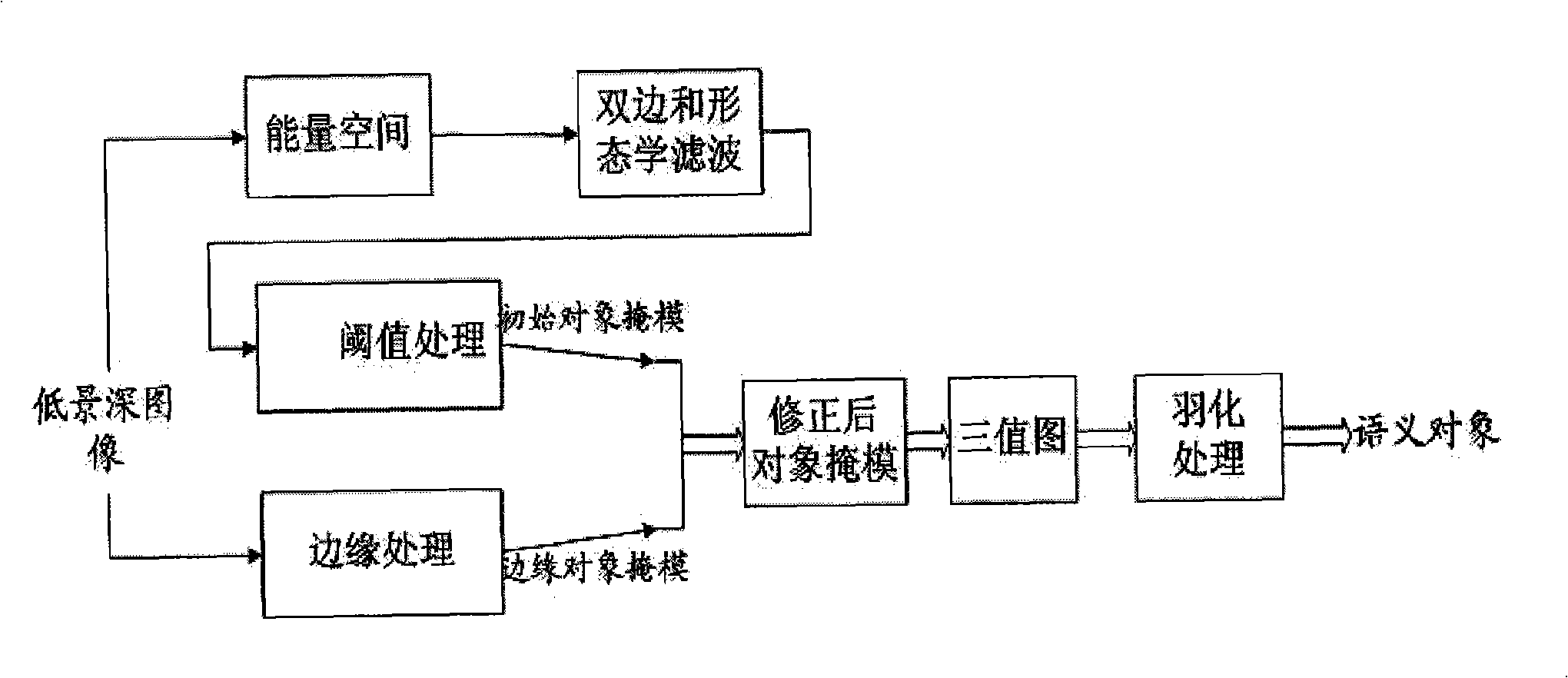
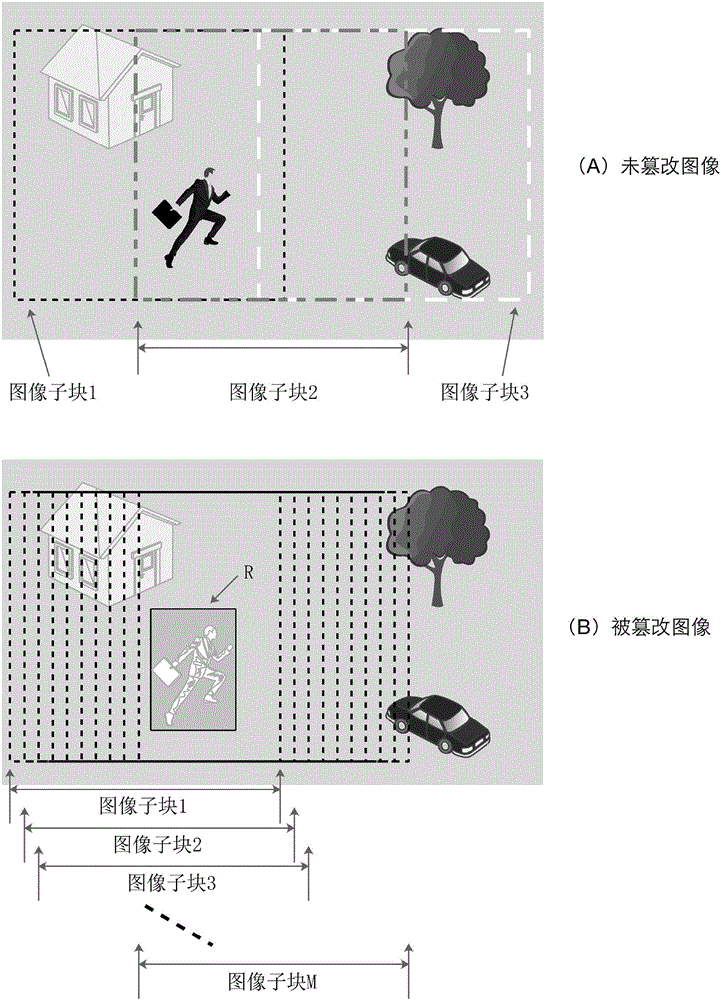
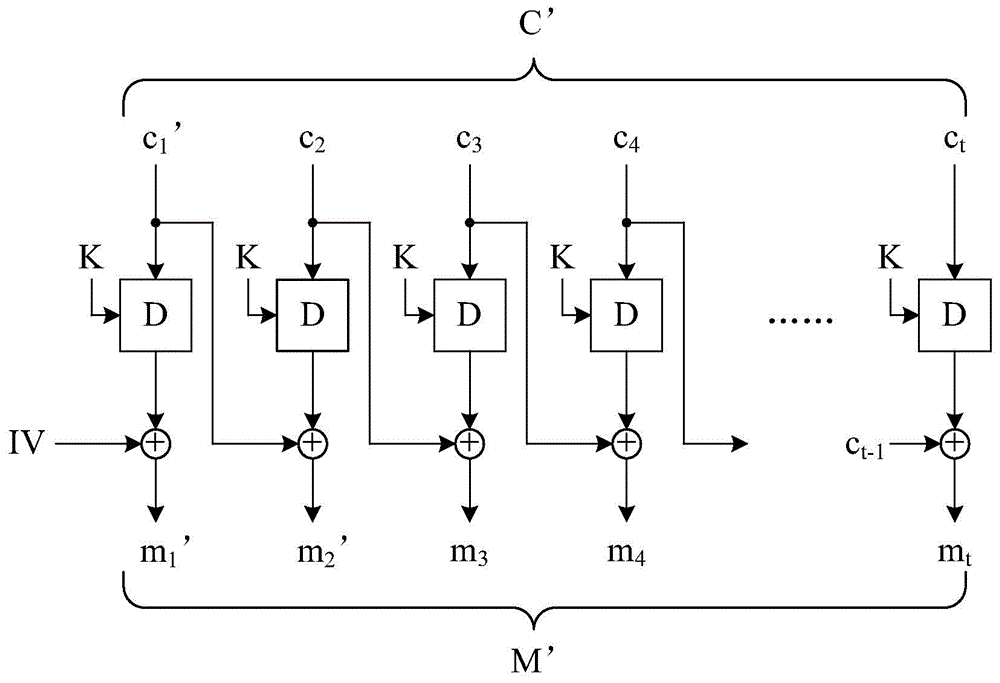
Semantic object dividing method suitable for low depth image
InactiveCN101299268ASatisfy IntegrityMaintain object detailImage enhancementImage analysisDepth of fieldVideo sequence
The present invention relates to a semantic object segmentation method suitable for low field depth image, which includes: firstly introducing gradient histogram to figure out the distribution of image in the energy space, obtaining an energy focusing significance map in combination with the character of the low field depth map; using the two-sided filter and morphology instrument to rehandle the energy focusing significance map; and then setting self-adapting threshold value and processing to obtain an initial object mask map, combining with the edge information obtained by canny operator to obtain the corrected object mask, in order to raise the segmentation accuracy of the interesting object; finally using the Bayesian eclosion algorithm to obtain the ideal semantic object segmentation result, in order to delicately process the complicated image boundary, such as hairs. Accurate segmentation to the interesting object in the field depth scope in the image video sequence.
Owner:SHANGHAI UNIV
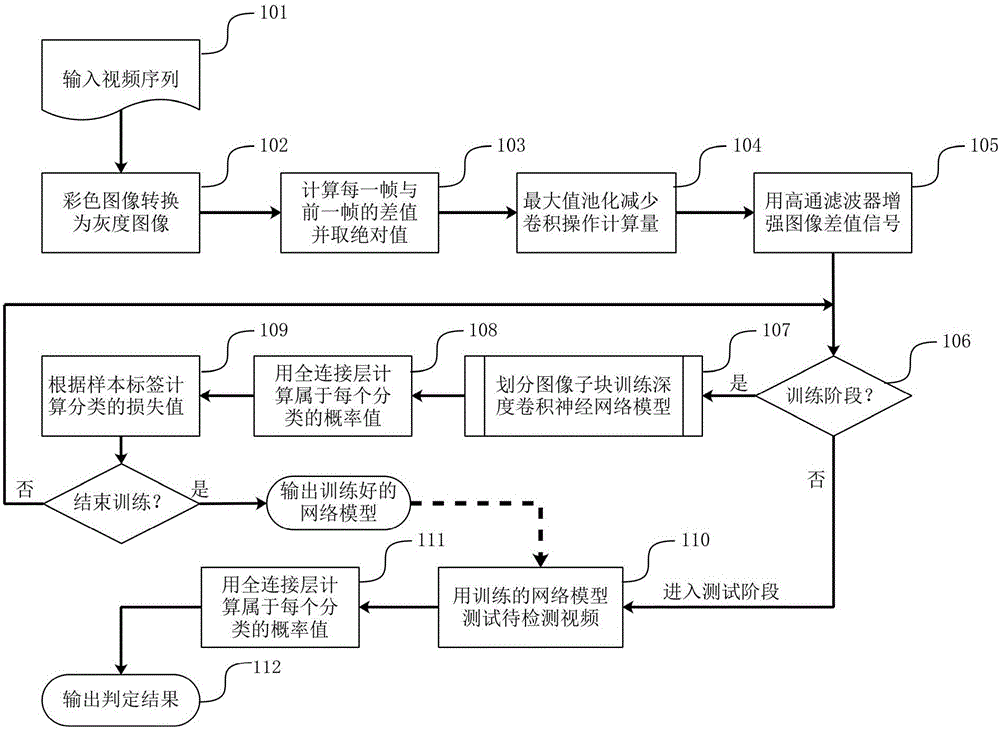
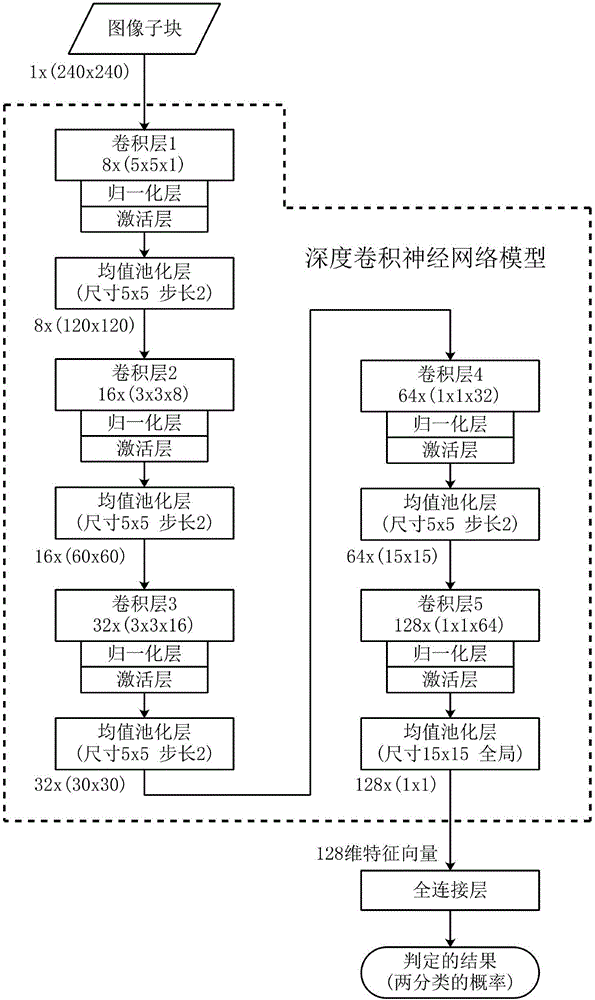
Video object removal tampering detection method based on deep learning
ActiveCN107527337ASatisfy IntegrityGood effectImage enhancementImage analysisPositive sampleNetwork model
The invention provides a video object removal tampering detection method based on deep learning. The method comprises steps of: performing pretreatment in order to convert a video sequence into a grayscale difference image; reducing the calculation amount of convolution by maximum pooling; enhancing the difference signal of the image through high-pass filter; obtaining positive samples and negative samples with similar quantities by using an asymmetric image sub-block partitioning strategy; finally training a neural network model based on a deep learning theory; by using the trained network model, testing each video image frame of the video sequence to be tested to obtain a result of determining whether video object removal tampering occurs in each frame of the video sequence to be tested. The method can achieve video object removal tampering detection in the video sequence, determines whether video object removal tampering occurs in each frame of the video sequence, can meet the verification requirement of video integrity and authenticity, is a solution of passive video evidence acquisition and has broad application prospect.
Owner:HANGZHOU HUICUI INTELLIGENT TECH CO LTD
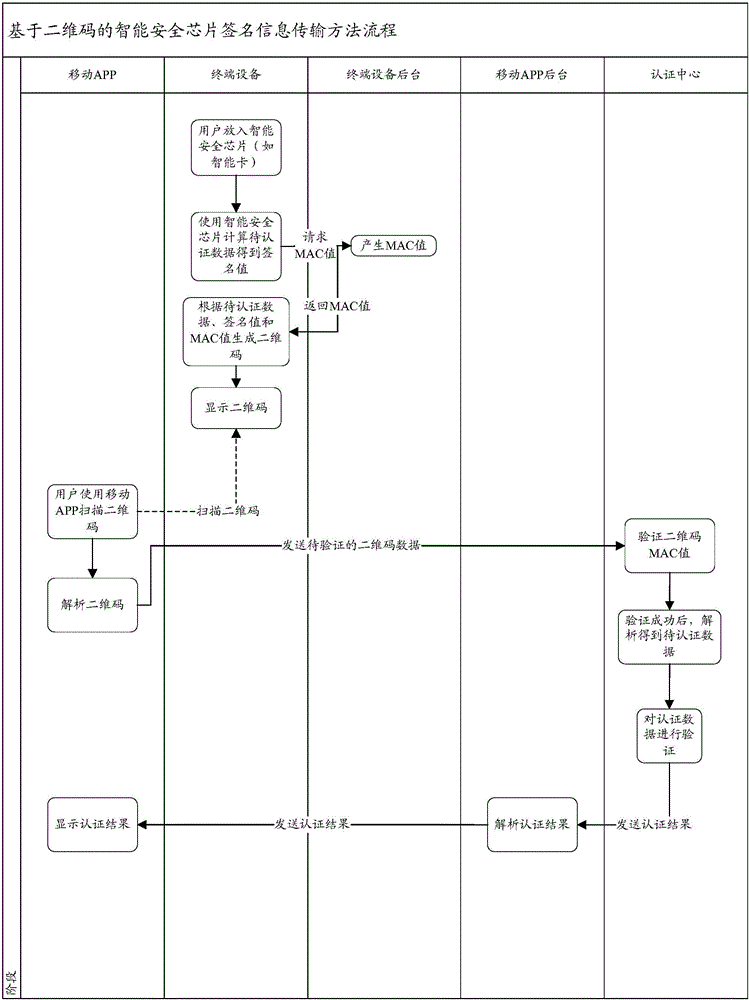
Intelligent security chip signature information transmission method and system based on 2-dimensional bar code
ActiveCN106100850AImprove securitySatisfy confidentialityEncryption apparatus with shift registers/memoriesUser identity/authority verificationInformation transmissionOriginal data
The invention relates to an intelligent security chip signature information transmission method and system based on a 2-dimensional bar code. The 2-dimensional bar code is generated by the following steps: an intelligent security chip is inserted into a terminal device; the intelligent security chip is used to put a signature on the original data and thus signature value information is obtained; and the terminal device assemblies the original data, the signature value information and a message verification code to generate a 2-dimensional bar code, and displays the 2-dimensional bar code. Scanning authentication of the 2-dimensional bar code comprises the following steps: an application scans the 2-dimensional bar code, parses the data of the 2-dimensional bar code so as to obtain the to-be-authenticated data, and then sends the to-be-authenticated data to an application background; an authentication center verifies the to-be-authenticated data, and sends a verification result back to the application through the application background. With application of the intelligence security chip signature information transmission method and system based on a 2-dimensional bar code, in an intelligent card identity authentication application system, the problem of poor data communication between an intelligent card and a background system due to unavailable card reading devices is solved, so that comparative transmission of the signature information of the intelligent card is fulfilled without using a particular intelligent card reading device.
Owner:THE THIRD RES INST OF MIN OF PUBLIC SECURITY
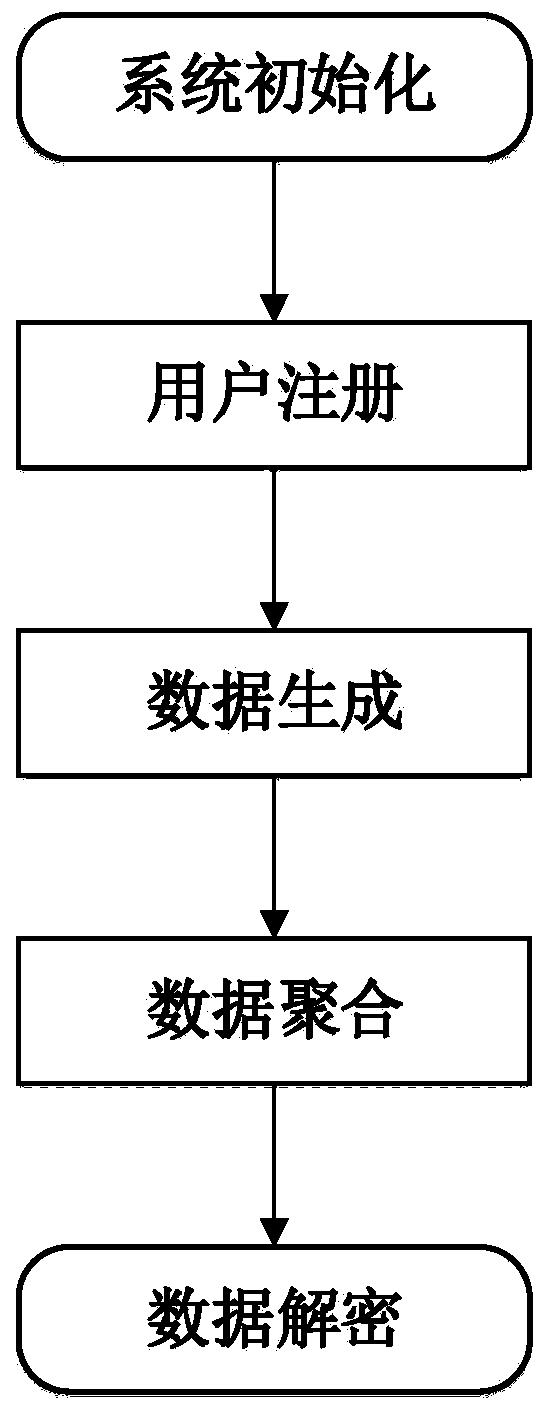
Privacy protection data aggregation method and system for smart power grid
ActiveCN111131148AImprove reliabilitySatisfy confidentialityKey distribution for secure communicationPublic key for secure communicationThird partyConfidentiality
The invention requests to protect a privacy protection data aggregation method and system for a smart power grid. The method and system can protect the data privacy of a single user from being leakedand aggregates the sum of data in a certain area, and only a control center can read an aggregation result. The method comprises a system initialization step, a user registration step, an encrypted data generation step, a data aggregation step and a data decryption step. According to the invention, an intelligent electric meter and an aggregator negotiate a session key, and a BGN encryption algorithm based on an elliptic curve is used to encrypt the data. The method does not depend on a trusted third party, the system can still operate normally when the intelligent electric meter is missing, so that better reliability is achieved, the identity of the user is anonymous, and an attacker cannot obtain the real identity of the user. According to the method, the calculation efficiency is improved, the corresponding security requirements of confidentiality, integrity, certification and the like are met, and the security can be proved.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
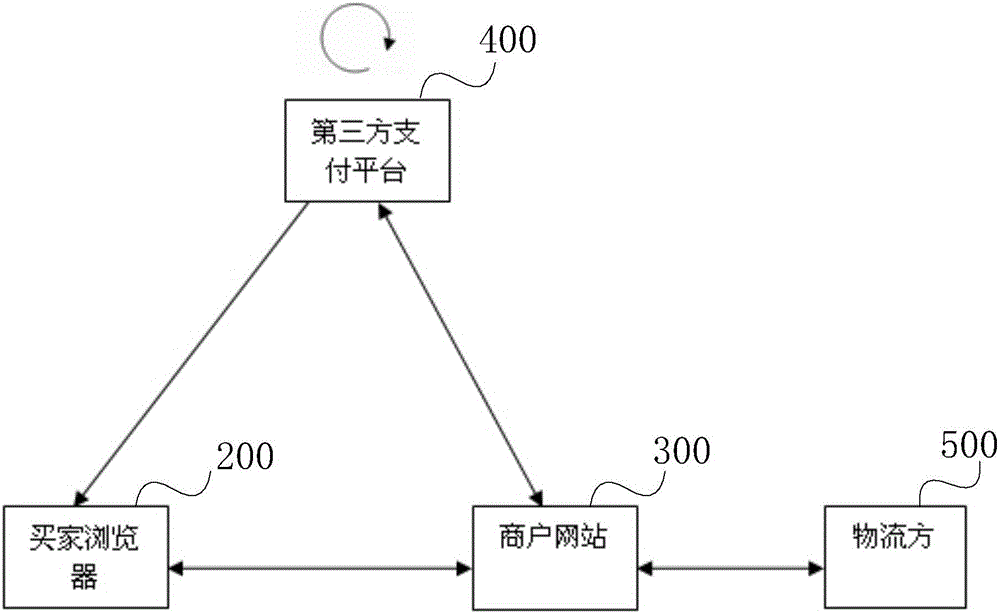
User privacy protection method and system based on third party payment platform
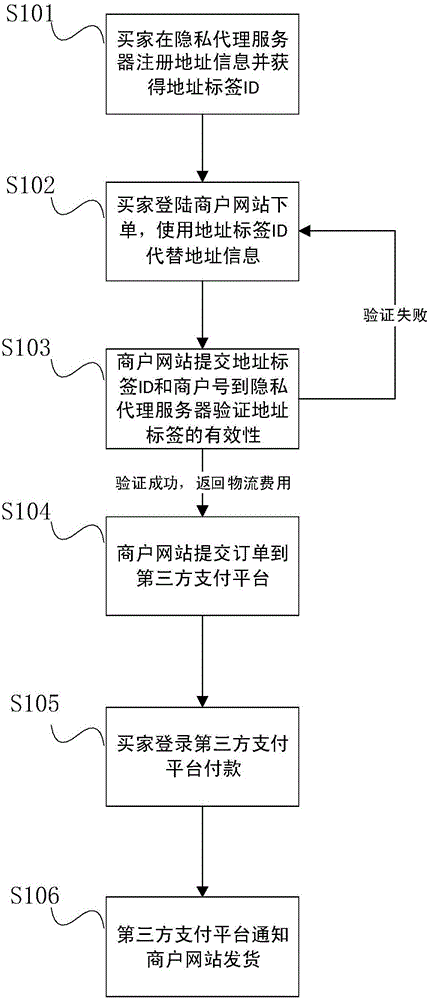
InactiveCN105812467AStrengthen supervisionGuaranteed isolationPayment architectureBuying/selling/leasing transactionsUser privacyInternet privacy
The invention discloses a user privacy protection method and system based on a third party payment platform. The method comprises the steps that: an agent server storing user privacy data is established, a buyer only needs to register personal address information on the agent server, the agent server will generate an address label ID, and only logistic distribution platforms authenticated by the privacy agent server can obtain address information through the address label; when the buyer places an order on a merchant website, the buyer needs to provide the address label instead of related address information, the merchant website obtains a temporary encrypted code from the agent server according to the address label ID and the order number in a delivering process, and the logistic distribution platform decrypts the encrypted code to obtain the related address information; and after the buyer receives the goods, the buyer informs the agent server through the third party payment platform to invalidate the encrypted code. According to the invention, the personal privacy of the buyer in the shopping online process is protected to the maximum extent, and the personal information of the buyer is prevented from being leaked.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
Parameter self-adaption method, device and equipment of high-speed signal and readable storage medium
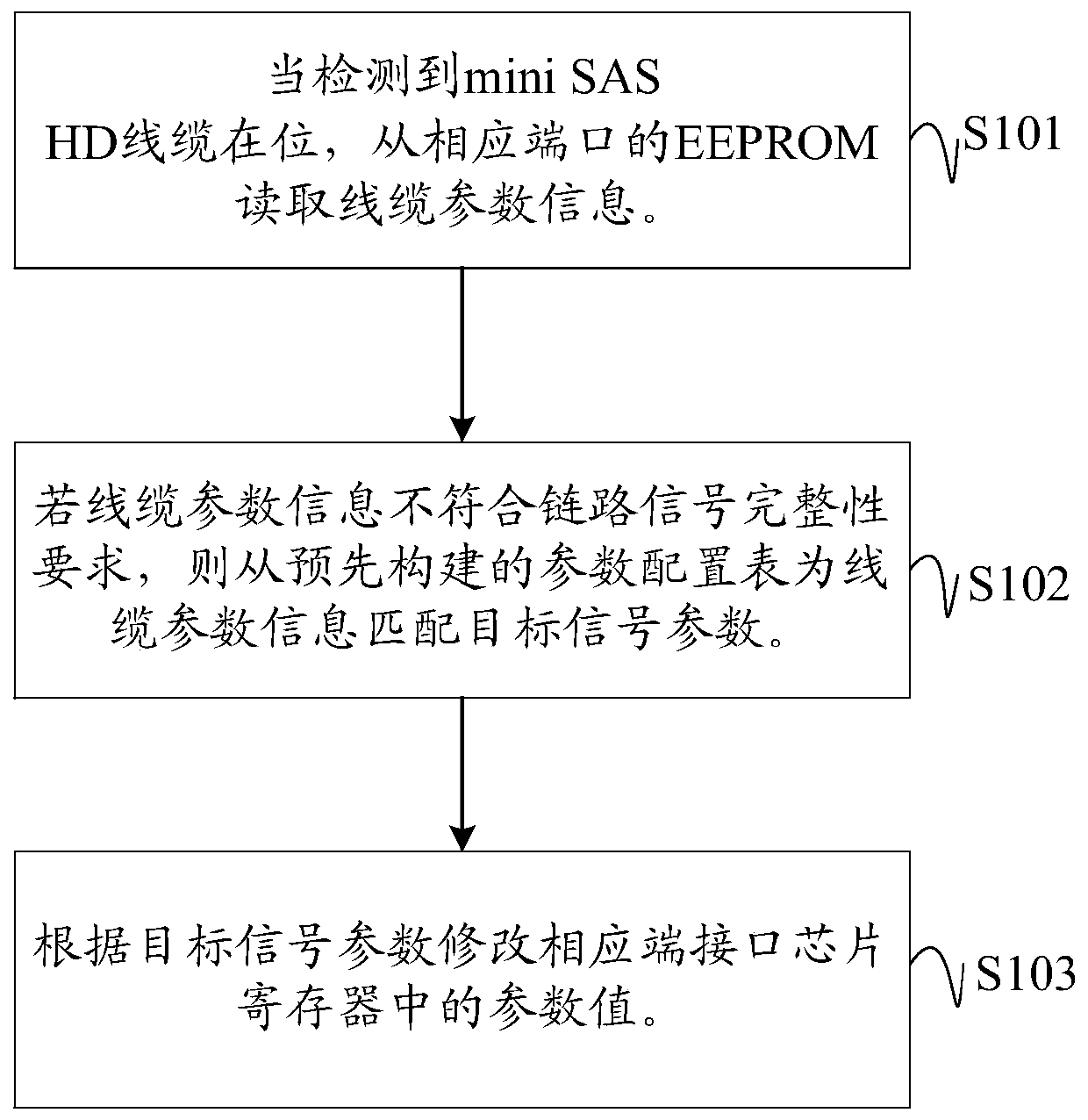
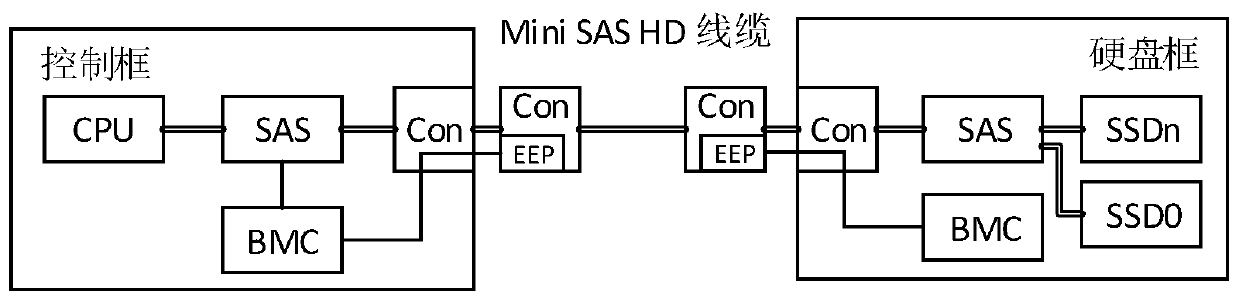
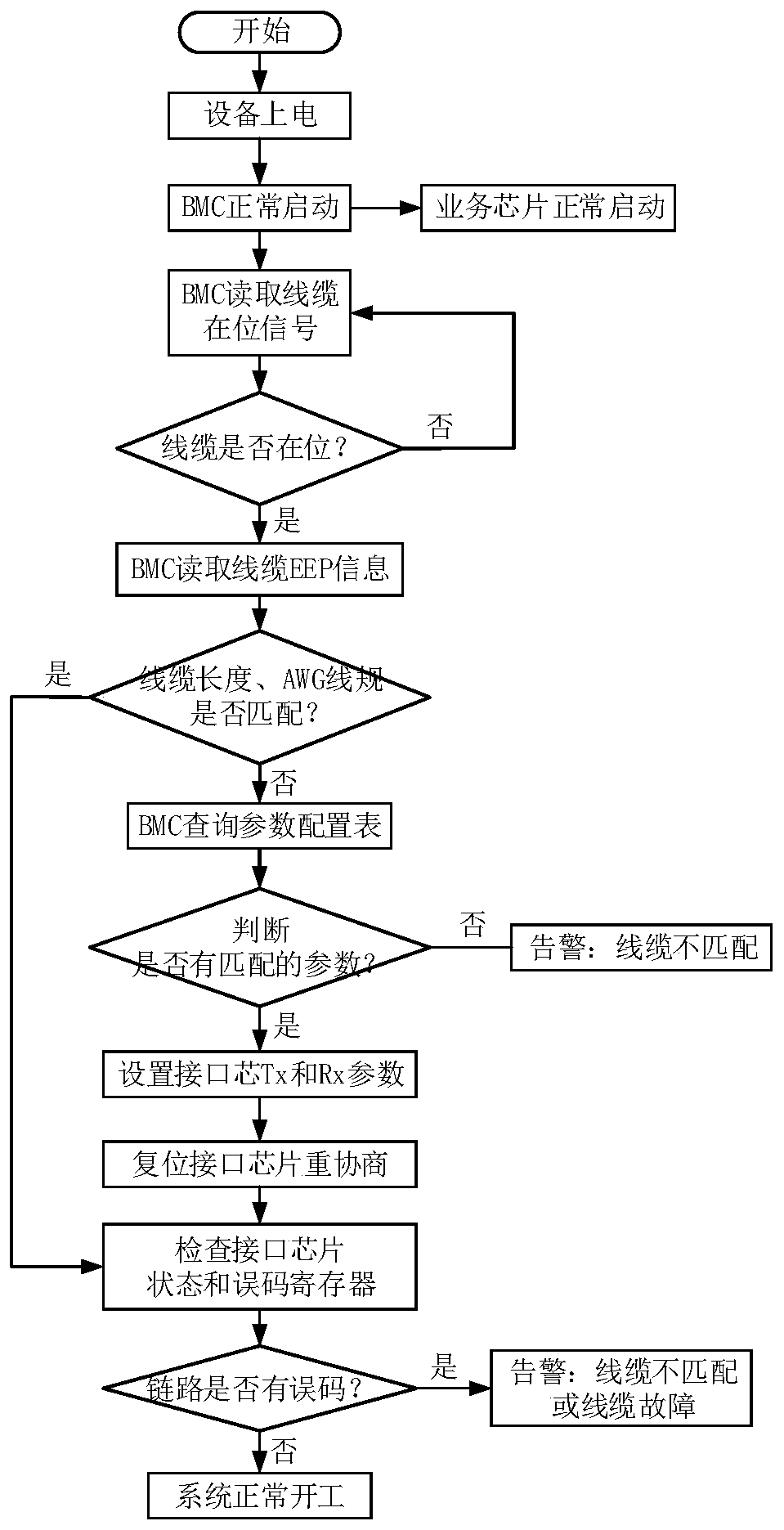
ActiveCN111030778ASatisfy IntegrityImprove driving abilityReceiver specific arrangementsTransmitter specific arrangementsTarget signalSelf adaptive
The invention discloses a parameter self-adaption method, device and equipment of a high-speed signal and a computer readable storage medium. A baseboard management controller is suitable for controlling a sending end and a receiving end for signal transmission based on a mini SAS HD cable. When it is detected that the mini SAS HD cable is in place, cable parameter information is read from an EEPROM of a corresponding port. If the cable parameter information does not meet the link signal integrity requirement, the target signal parameters of the sending end and the receiving end are matched for the cable parameter information from a parameter configuration table, and the parameter configuration table is used for recording and storing the optimal matching relation between the cable parameters and the interface chip parameters. A parameter value in a register of the interface chip at the corresponding end is modified according to the target signal parameter, so that self-adaptive adjustment of parameters of the signal sending end and the signal receiving end of the mini SAS HD cable is achieved, and the driving capability of the sending end and the signal receiving capability of thereceiving end are enhanced. The requirement for link signal integrity is met. A customized high-cost cable is replaced with a low-cost common cable, and the application cost of the system is reduced.
Owner:INSPUR SUZHOU INTELLIGENT TECH CO LTD
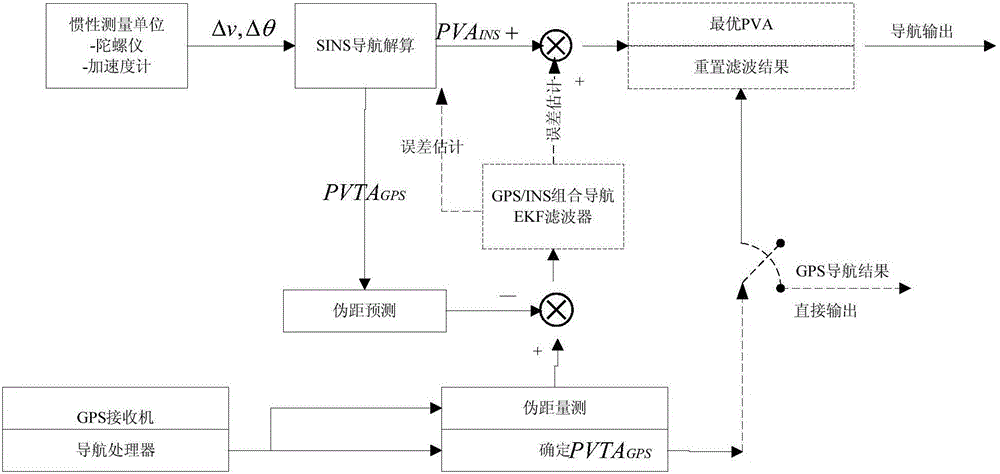
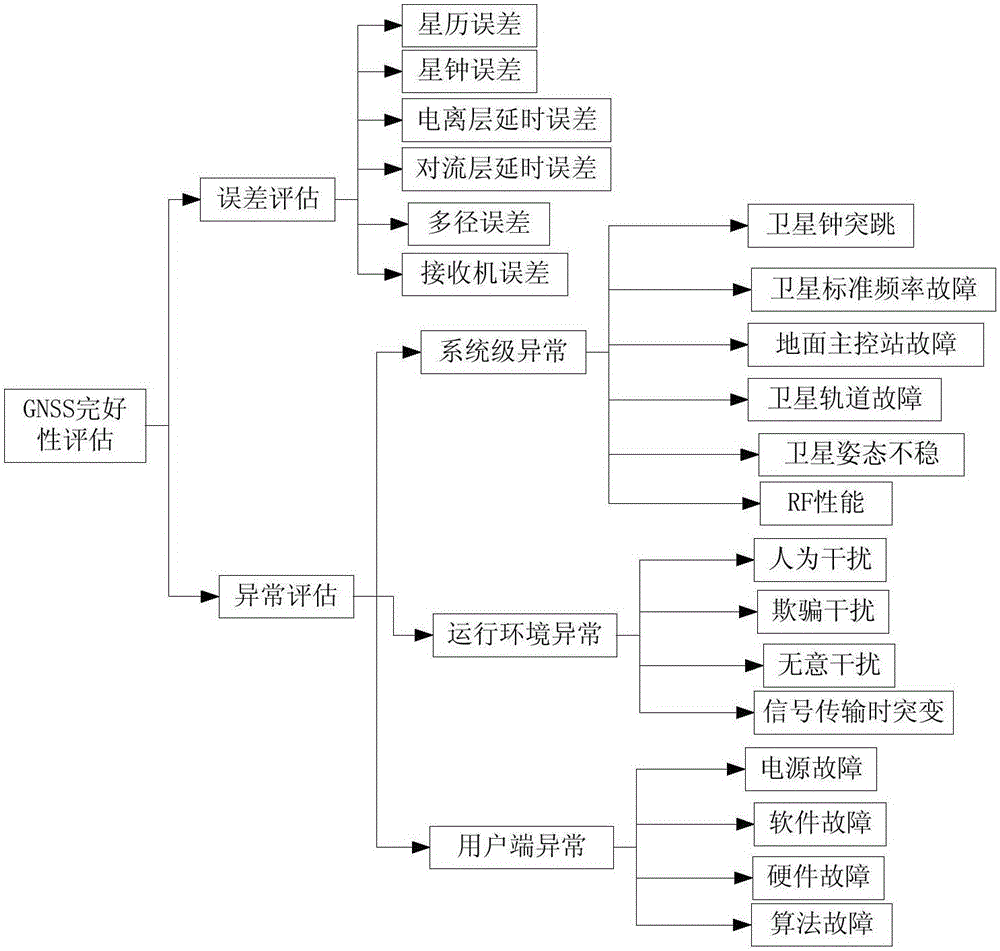
GNSS system integrity evaluation method and device
ActiveCN105911567ASatisfy IntegrityEffective assessmentSatellite radio beaconingObservation dataSystem integrity
The invention provides a GNSS system integrity evaluation method and a GNSS system integrity evaluation device. The GNSS system integrity evaluation method comprises the steps of: acquiring observation data of a navigation receiver; performing gross error detection on the observation data, and generating a correction number; evaluating an abnormity when a gross error detection result indicates a residual error abnormity; carrying out error evaluation according to the correction number when the abnormity threatens the integrity; and calculating and outputting a hazard misleading information probability HMI, and sending out an alarm. The GNSS system integrity evaluation method provided by the invention can be used for evaluating integrity of GNSS comprehensively and accurately, acquiring the operation state of the GNSS system in time, carrying out fault isolation and repair in time, and improving the accuracy and stability of the GNSS system.
Owner:SICHUAN BEIDOU SATELLITE OF CHINA TECH CO LTD
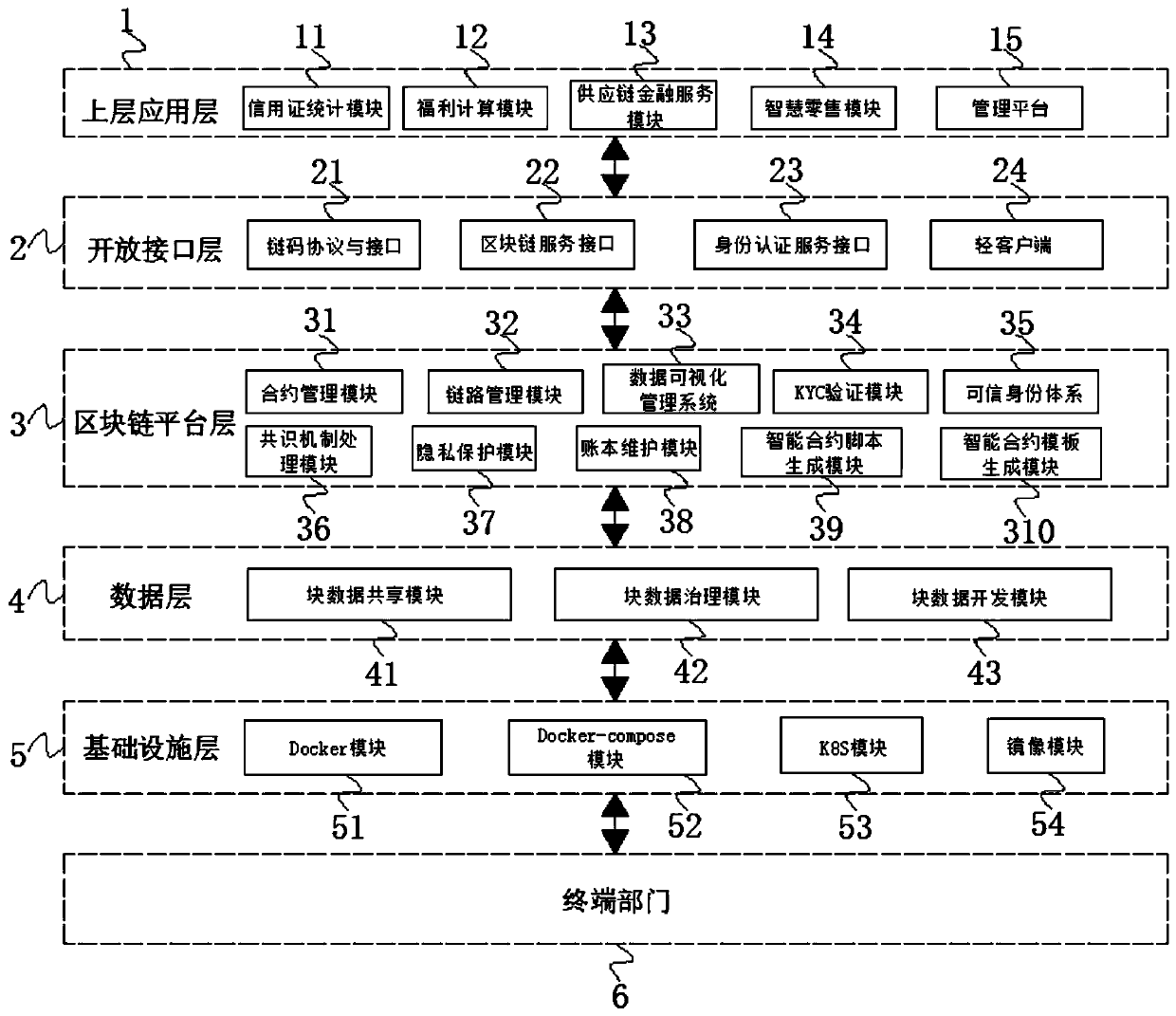
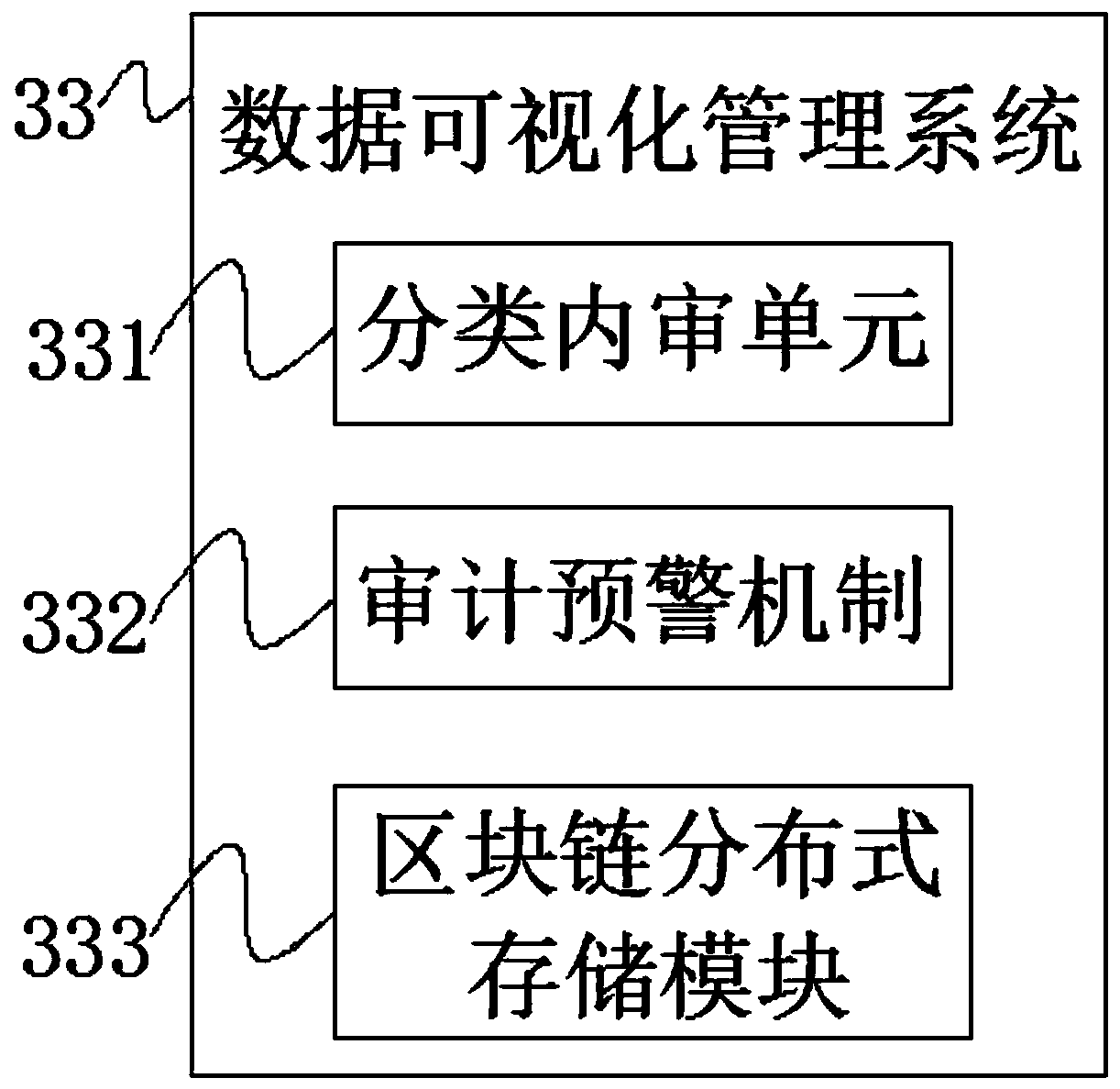
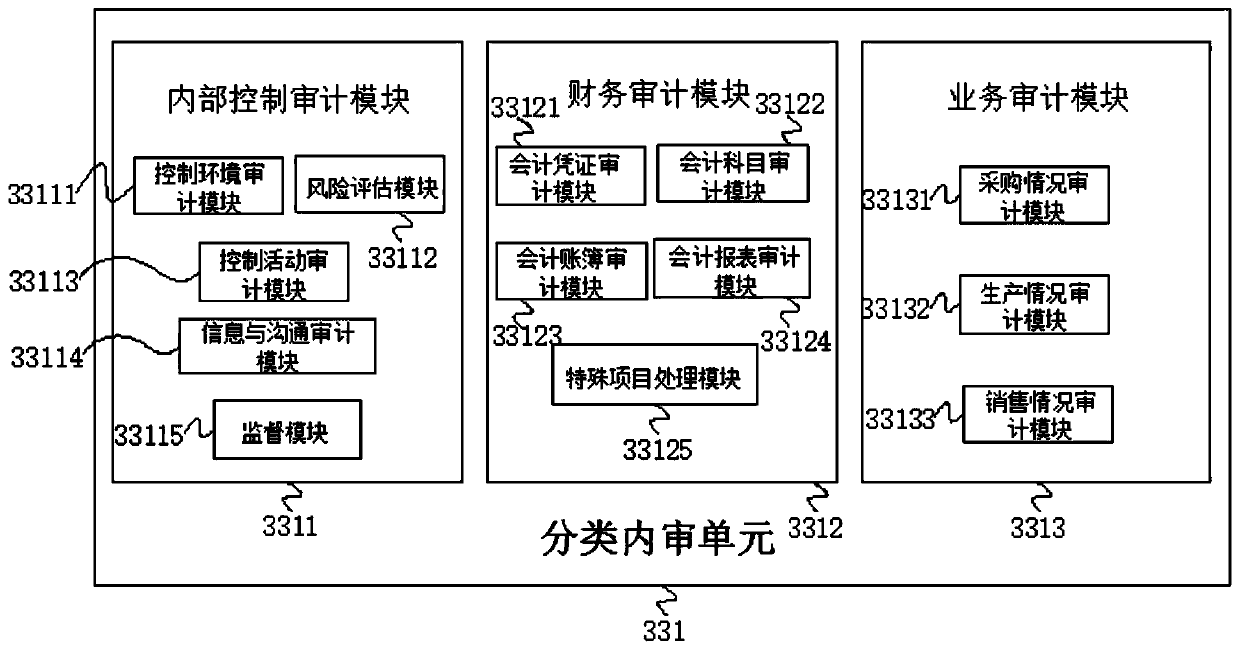
Enterprise internal auditing system based on block chain technology
The invention discloses an enterprise internal auditing system based on a block chain technology. The enterprise information processing system comprises an upper application layer, a development interface layer, a block chain platform layer, a data layer, an infrastructure layer and a terminal department, the upper application layer and the development interface layer are in bidirectional connection, and the open interface layer and the block chain platform layer are in bidirectional connection. The invention discloses an enterprise internal auditing system based on a block chain technology. Aplurality of auditing modes can be set. The actual requirements of enterprise departments are met. Actual services of different enterprises can be met. The standardization and the unification of audit services in an enterprise can also be completed. According to the method, the original data information can be obtained accurately, the efficiency and quality of obtaining audit evidences by internal audit of enterprises are improved, and the reliability of obtaining the evidences by the internal audit is effectively guaranteed, so that the efficiency and effect of executing audit work in the enterprises are improved, and the storage mode of the networked internal audit data is improved.
Owner:威海华智数字经济研究院有限公司
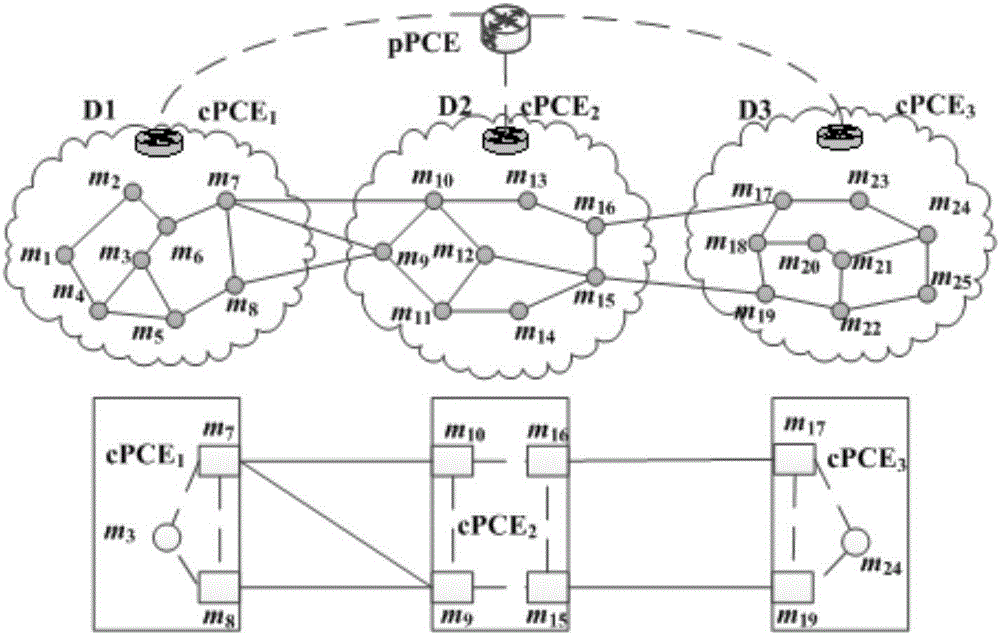
Layered PCE based multi-domain optical network secure light path establishment protocol
ActiveCN106851441AShort setup delaySatisfy confidentialityMultiplex system selection arrangementsUser identity/authority verificationConfidentialityPrivacy protection
The invention discloses a layered PCE based multi-domain optical network secure light path establishment protocol. Aiming at the problems of security problem and comprehensive efficiency existing in a multi-domain optical network light path establishment process, a new GO-PCE (Global Optimizing secure light-path protocol based PCE in multi-domain optical network) is designed by combining with a trust model and a key management scheme, adopting a globally optimized multi-domain trusted path selection, usable wavelength calculation and wavelength distribution strategy, and utilizing a TLS based bidirectional identity authentication, TCP-AO based source authentication, identity cryptography based encryption and digital signature technology and a Path-Key based privacy protection mechanism. The secure service requirements such as confidentiality, completeness, authenticity, non-repudiation, freshness and privacy can be met; compared with an SD-PCE and pH-PCE light path establishment protocols, the layered PCE based multi-domain optical network secure light path establishment protocol has relatively low blocking rate and relatively short light path establishment time delay.
Owner:ENG UNIV OF THE CHINESE PEOPLES ARMED POLICE FORCE
Contour machining method of OGS (One Glass Solution) glass
ActiveCN102999240AIntegrity guaranteedSatisfy IntegrityInput/output processes for data processingNumerical controlCyanide
The invention discloses a contour machining method of OGS (One Glass Solution) glass. The method comprises the following steps: printing acid-proof protective films on both surfaces of a big piece of glass, wherein the contour of each acid-proof protective film is similar to that of the OGS glass; equivalently etching non-protective areas by using cyanide fluorhydric acid, thereby forming a base plate; tempering the base plate, thereby forming a uniform tempered layer on the surface of the base plate, wherein the tempered base plate is called as a parent plate; carrying out a plurality of film coating and yellow light machining treatments on the parent plate, thereby forming an ink layer and a TTO (Indium Tin Oxide) line layer on the non-etching area of one surface of the parent plate, wherein the parent plate with the ink layer and the TTO layer is called as a functional slice; removing waste materials from a groove in the parent plate in a cutting manner, thereby forming a monolithic OGS glass semi-finished product; and finally, grinding a cutting surface by using CNC (Computerized Numerical Control Machine), thereby forming an OGS glass finished product. According to the invention, the integrity of the tempered layer of the surface of the OGS glass is guaranteed essentially, so that the functions of the stress layer of the surface of the OGS glass are guaranteed. Therefore, the overall strength and bulk strength of OGS capacitive touch screens are guaranteed.
Owner:抚州联创电子有限公司
Test piece preparation mould special for shearing test and preparation method thereof
InactiveCN101871863AEasy to disassembleSatisfy IntegrityPreparing sample for investigationStrength propertiesEngineeringSurface layer
The invention discloses a test piece preparation mould special for a shearing test and a preparation method thereof, and relates to the technical field of road inter-layer binding performance tests. The invention solves the problems that no special forming mould for preparing a test piece is available and in the conventional method, the uniformity of the structures at the middle base and the surface layer is poor, the strength of the cut base layer of the test piece is reduced and the accuracy of the test result is affected. Two parallel side plates in the mould are connected with the two ends of a supporting bottom plate; two pairs of slots are oppositely formed in the inner walls of the two side plates; split bearing baffles are symmetrically inserted between two bearing baffles through the slots; the method comprises the following steps of: 1, uniformly stirring broken stones, water and cement and pouring the mixture into a mould provided with a second split bearing baffle; 2, controlling the speed of a pressure head so that the distance between the pressure head and the upper end of the second split bearing baffle is 40 mm; 3, coating priming oil on the test piece and then standing for 24 hours; 4, after the priming oil penetrates, arranging a first split bearing baffle, sealing with the broken stone and placing the sealed first split bearing baffle on the test piece for 4 hours; 5, pressing and forming; and 6, demoulding and preserving. The test piece preparation mould is used for a shearing test for measuring the road interlayer binding performance.
Owner:HARBIN INST OF TECH
Encrypted access control method under CCN
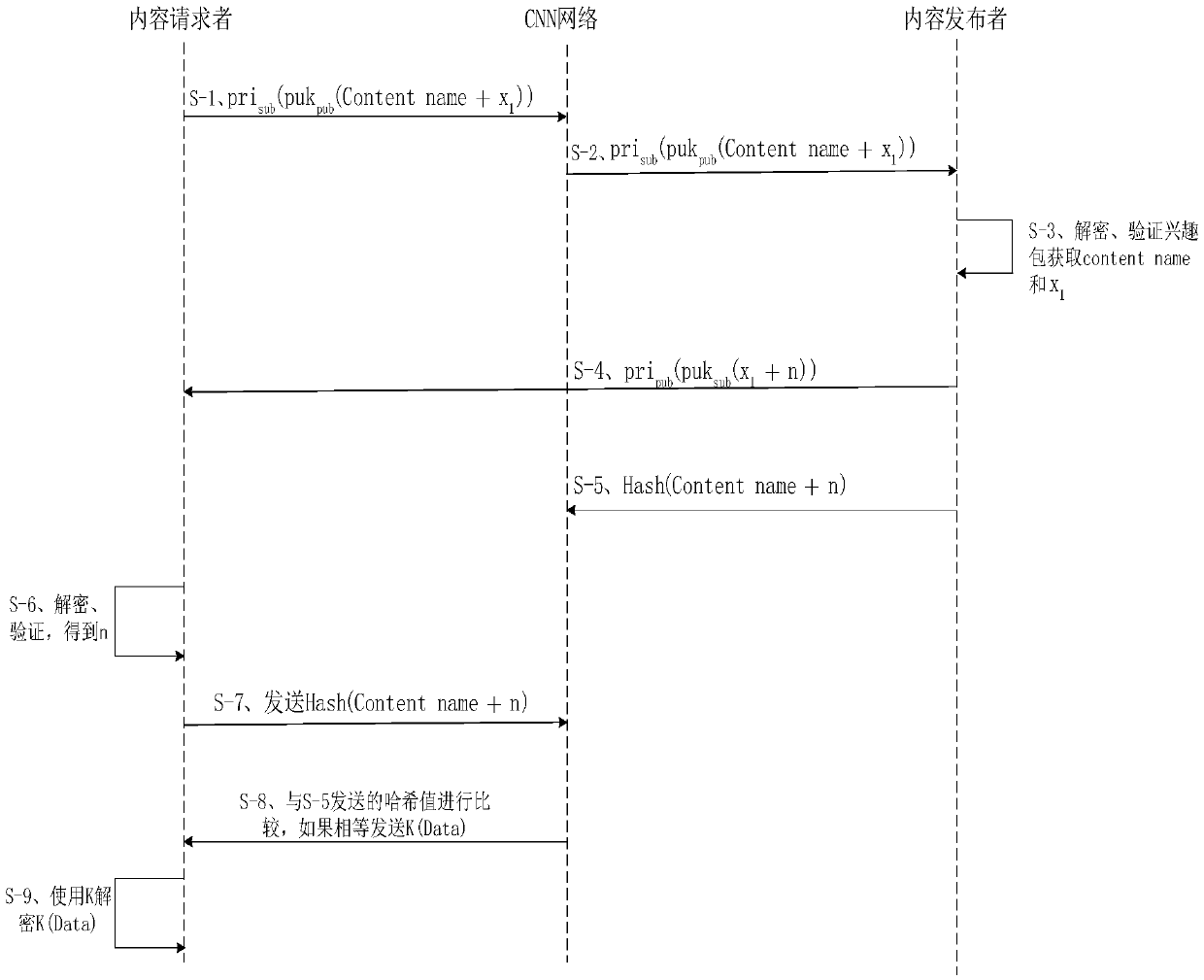
InactiveCN108833339ASatisfy IntegrityAvoid Privacy LeakageUser identity/authority verificationContent centric networkingAuthorization
The invention relates to an encrypted access control method under CCN (Content Centric Networking). Broadcast encryption is adopted for encrypting data packets, so that a condition that different requesters can decrypt the same authorized content can be ensured. Data encryption effectively protects privacy of a content publisher. At the same time, the encrypted data sent by the content publisher is firstly stored in a router. A requester acquires a content mark number after authorization verification by the content publisher and then the requester performs Hash operation on a requested contentname and the content mark number. Only when an obtained Hash value is identical to that sent by the content publisher in the router, the router sends the encrypted data to the requester. The authorized requester can obtain the data packets after acquiring the request content mark number and performing Hash value calculation and after the router confirms the matching success. A requester authorized to access a part of the content cannot acquire content buffering other unknown content mark numbers.
Owner:GUANGDONG UNIV OF TECH
Wireless sensor network security routing method based on IPv6 addressing
ActiveCN104811934AWith data collectionWith wireless communication moduleTransmissionSecurity arrangementTimestampRouting table
The invention discloses a wireless sensor network security routing method based on IPv6 addressing. Network IP addressing and network joining and leaving rules of nodes based on a tree topological structure are provided by aiming at the practical requirement that data require security transmission in a wireless sensor network so that storage space of IP addresses and routing tables is greatly saved, and time and space utilization efficiency is enhanced. Meanwhile, a message security routing transmission strategy based on unicast and multicast is designed, and the network is enabled to resist attack means like replaying and capturing by the characteristic of combination of encryption and decryption, hash algorithm and timestamps.
Owner:张北数据港信息科技有限公司
Estate information analysis system based on databank
ActiveCN104299114ASatisfy IntegritySatisfy the orderlinessResourcesSpecial data processing applicationsData displayInformation analysis
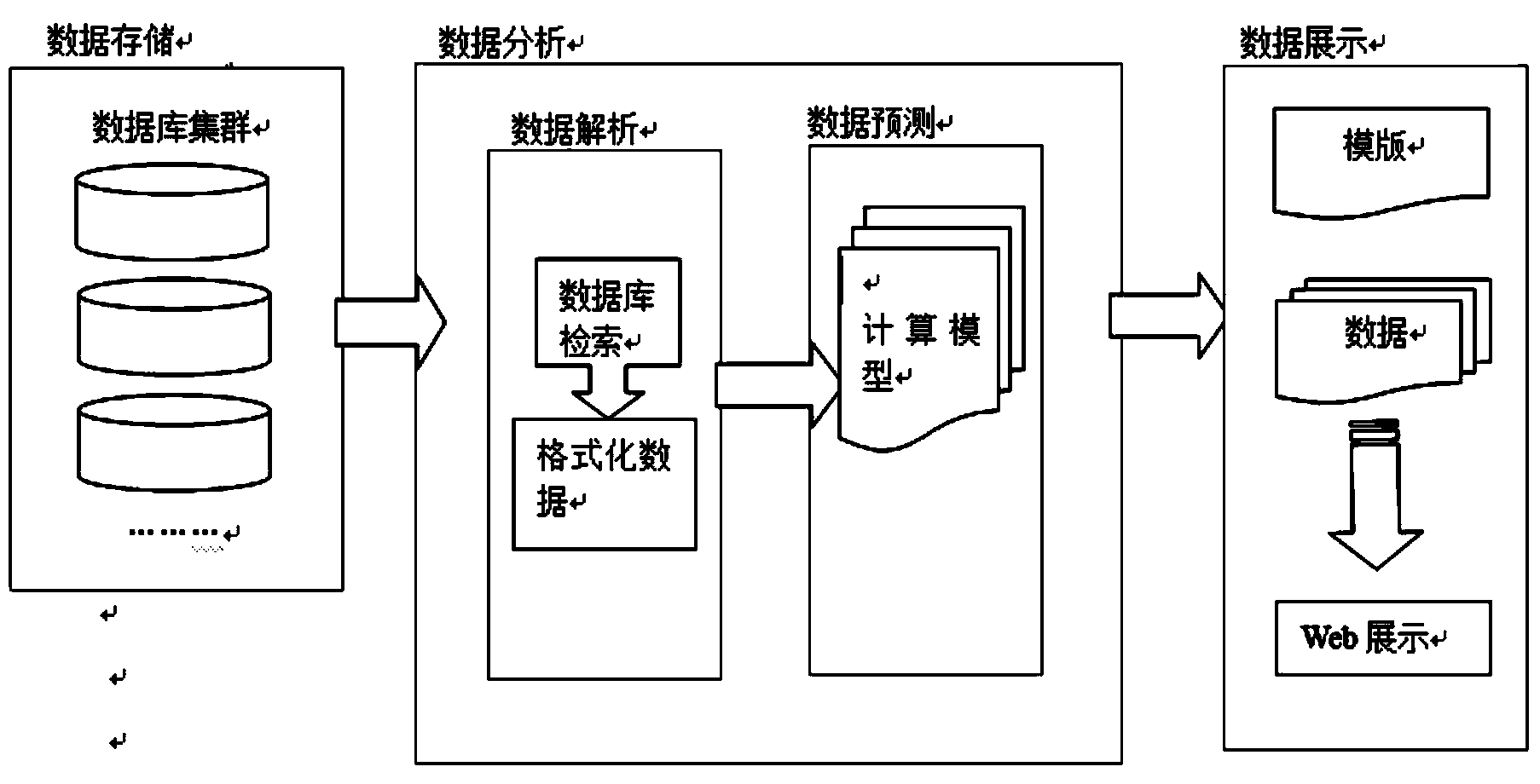
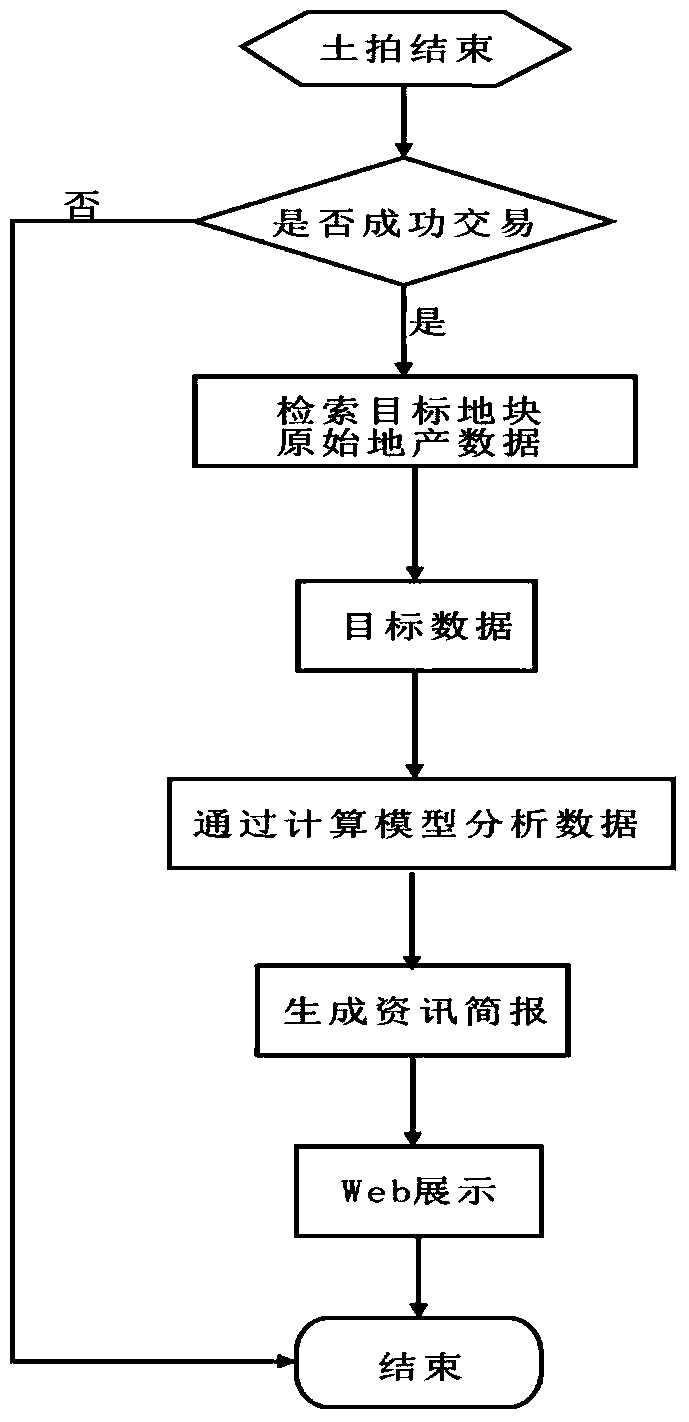
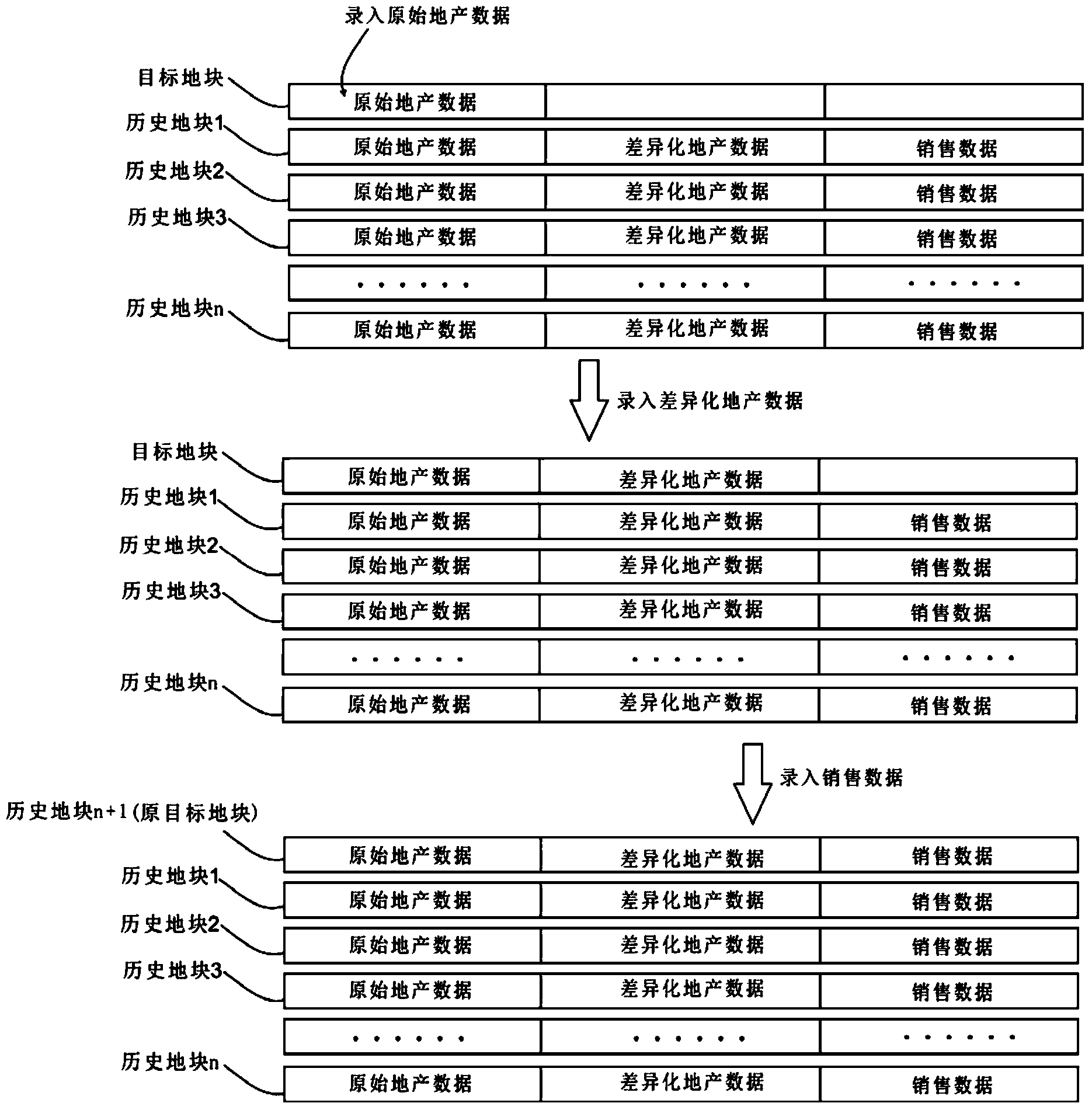
The invention discloses an estate information analysis system based on a databank. The estate information analysis system comprises a data storage module, a data analysis module and a data display module, wherein the data storage module comprises at least one databank for storing the original estate data, the differential estate data and the sale data of lands; the data analysis module comprises a data analysis module and a data prediction module; the data analysis module is used for searching the original estate data of a target land from the databank so as to obtain target data; the data prediction module is used for analyzing target data through a calculation module so as to obtain middle data; the data display module is used for receiving middle data and used for treating the middle data so as to generate information brief reports and display the information brief reports in a Web mode. By effectively integrating estate information, the requirements on completeness, ordering, sharing and real-time property of estate information are met, and meanwhile by establishing a calculation model, the future possible sale data of the target land can be predicted according to the sale data of a similar land, and data support is provided for development decision of the target land.
Owner:CHENGDU REALLYINFOR TECH
Seedling taking device for preventing bowl lumps from scattering for seedling transplantation
InactiveCN112616394APrevent fallingGuaranteed survival rateTransplantingApparatus for force/torque/work measurementEngineeringMechanical engineering
The seedling taking device comprises a soft mechanical claw and an ejection mechanism, the soft mechanical claw adopts flexible air bag clamping fingers, pot seedlings can be grabbed without damage, the integrity of a soil matrix is kept, the distance between the two clamping fingers is adjustable, proper clamping force can be guaranteed, and the seedling taking device can adapt to the pot seedlings of different sizes; The ejection mechanism is used for ejecting the bowl seedlings out of a seedling tray, grabbing of the mechanical claw is facilitated, compared with the prior art, the bowl seedling soil matrix can be well protected, and the application range is wide.
Owner:HENAN UNIV OF SCI & TECH
Single-shutter type steel composite thermal-insulation fire-resistance rolling shutter door
InactiveCN103670226ASatisfy the thermal insulationSatisfy IntegrityShutters/ movable grillesFireproof doorsThermal insulationWater resources
The invention discloses a single-shutter type steel composite thermal-insulation fire-resistance rolling shutter door. The rolling shutter door comprises transmission mechanisms, a case, a slide, a guide rail and roller shutters. The transmission mechanisms comprise a main transmission mechanism and an auxiliary transmission mechanism which are mounted in the case respectively. The slide is fixed between the main transmission mechanism and the auxiliary transmission mechanism, the guide rail is perpendicularly mounted below main and auxiliary supporting plates, a lifting mechanism is arranged in the guide rails, and the roller shutters are hinged to the lifting mechanism which is connected with the main transmission mechanism and the auxiliary transmission mechanism. According to the rolling shutter door, an independent water supply system is not needed, so that a large number of water resources are saved, the rolling shutter door is convenient to design and mount, and detection can be performed according to a GB / T7633 fire resistance test method without the water curtain protection, so that 2-to-3-hour heat insulation property (the unexposed surface average temperature is lower than 140 DEG C, and the peak temperature is lower than 180 DEG C) and completeness of the rolling shutter door can be met. Shutter plates are made of non-poisonous environment friendly materials and are harmless to human.
Owner:刘永贵
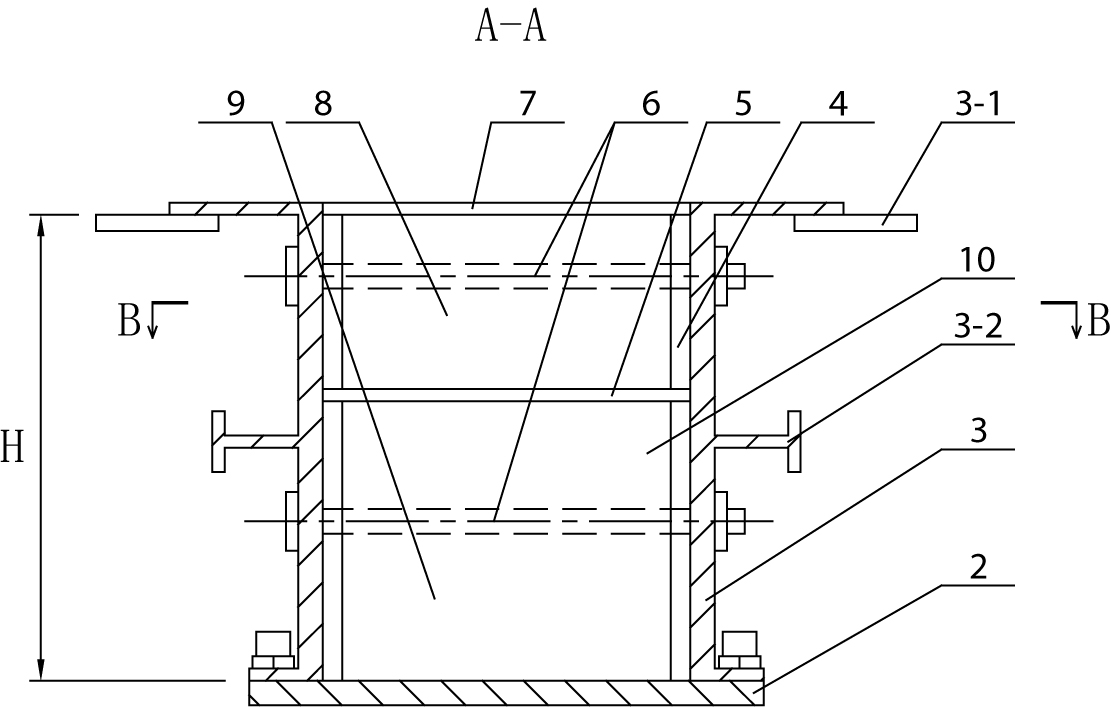
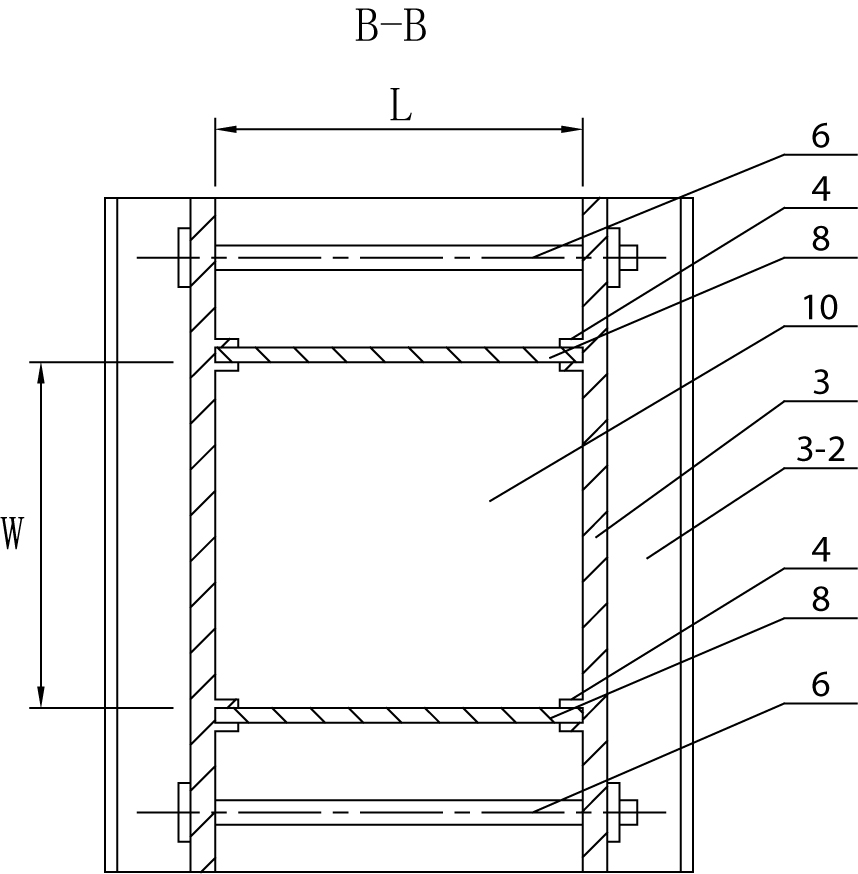
Heavy water reactor spent fuel basket testing inspection device
ActiveCN106705810ASatisfy IntegrityIntegrity guaranteedNuclear energy generationMechanical counters/curvatures measurementsNuclear powerDry storage
The invention belongs to the technical field of nuclear power station spent fuel dry storage, and particularly relates to a heavy water reactor spent fuel basket testing inspection device. The invention aims to develop a spent fuel basket testing inspection device, that is, a manufactured spent fuel basket is transferred to the testing inspection device, a dial indicator is erected after the inspection device is in place, the circularity, the coaxiality and the flatness of the fuel basket can be tested by rotating the fuel basket, and a cover of the fuel basket is opened to check whether the internal structure is completed or not. The characteristics lie in that the heavy water reactor spent fuel basket testing inspection device comprises a supporting and hanging bracket, a hand-cranking winding device, a supporting and hanging bracket supporting and locking device, a basket cover gripping apparatus, a rotating inspection platform, a base and a measuring and inspecting dial indicator device. The spent fuel basket testing inspection device disclosed by the invention is accurate in measured data, safe, reliable, convenient to operate and improved in work efficiency, can ensure subsequent relevant operations to be conducted normally before the fuel basket is loaded with spent fuel rod bundles, and ensures the integrity of fuel rod bundles and welding of upper and lower welding seams of the fuel basket to meet requirements of a welding technology.
Owner:CNNC NUCLEAR POWER OPERATION MANAGEMENT +1
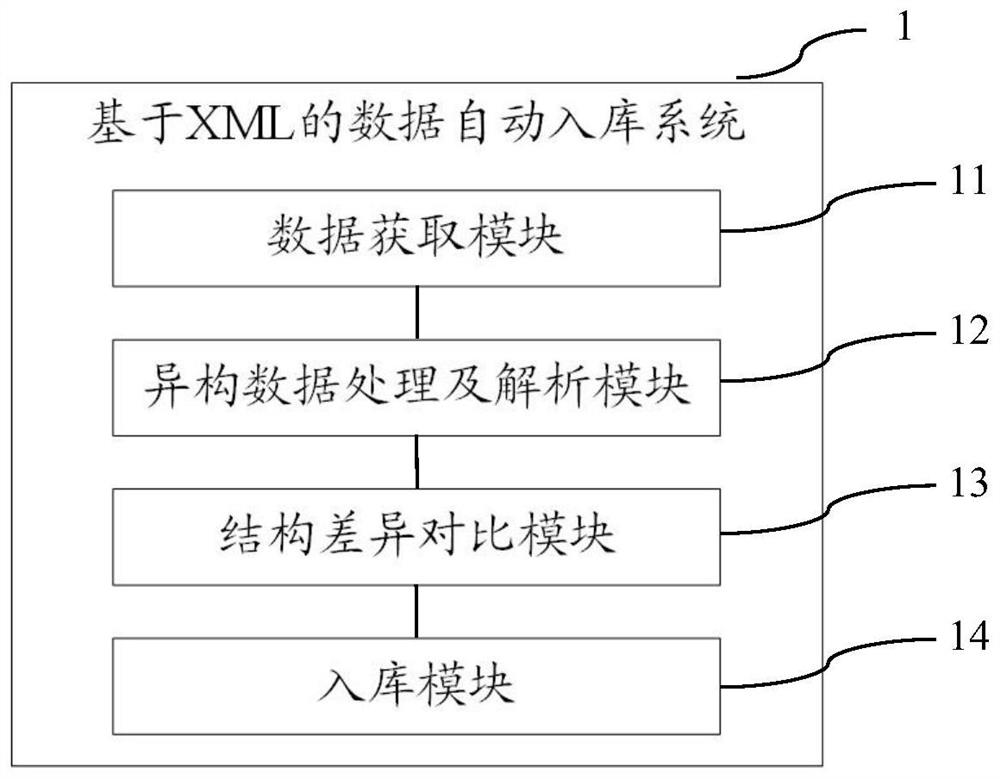
Automatic data storage method, system and device based on XML, and storage medium
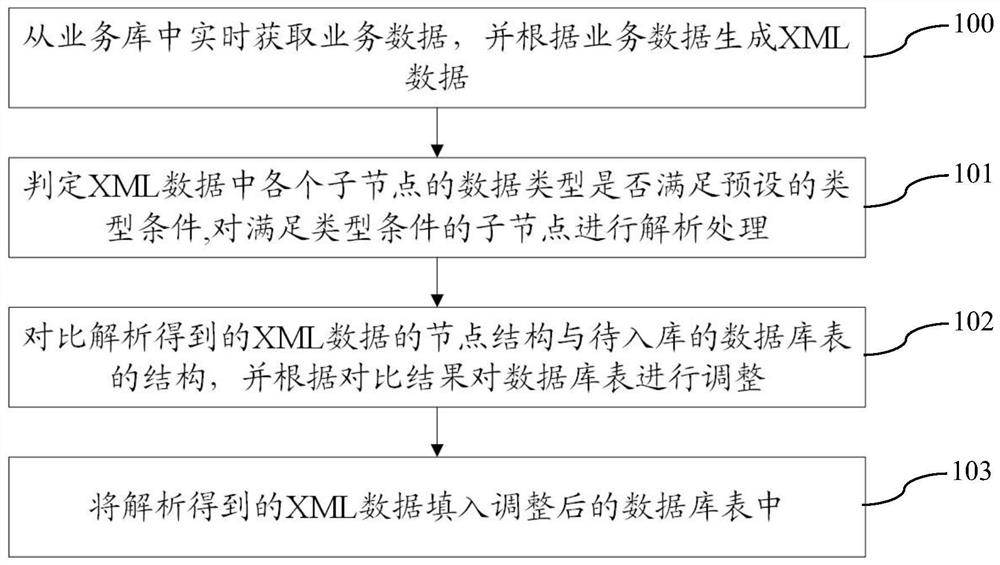
PendingCN111984826ASatisfy the effectivenessMeet the accuracySemi-structured data indexingSemi-structured data mapping/conversionStructure of Management InformationBusiness data
The invention provides an automatic data storage method, system and device based on XML, and a storage medium. The method comprises the following steps: obtaining business data from a business libraryin real time, and generating XML data according to the business data; judging whether the data type of each child node in the XML data meets a preset type condition or not, and analyzing the child nodes meeting the type condition; comparing the node structure of the XML data obtained by analysis with the structure of a database table to be stored, and adjusting the database table according to thecomparison result to ensure the correctness and integrity of the data of each sub-node of the XML in the database table structure; and filling the XML data obtained by analysis into the adjusted database table. The automatic data storage method provided by the invention meets the requirements of effectiveness, accuracy, integrity and convenience of model training, index calculation or statisticsand the like in the current real-time business for data.
Owner:河北幸福消费金融股份有限公司
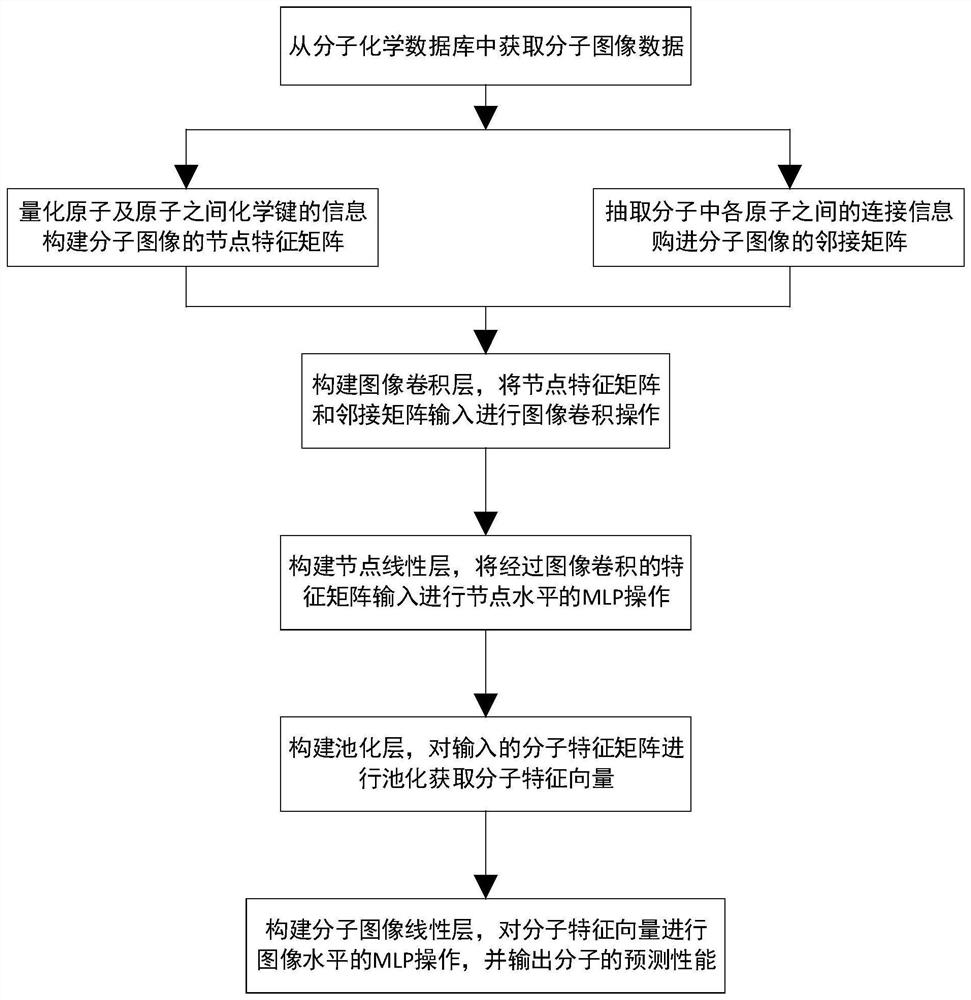
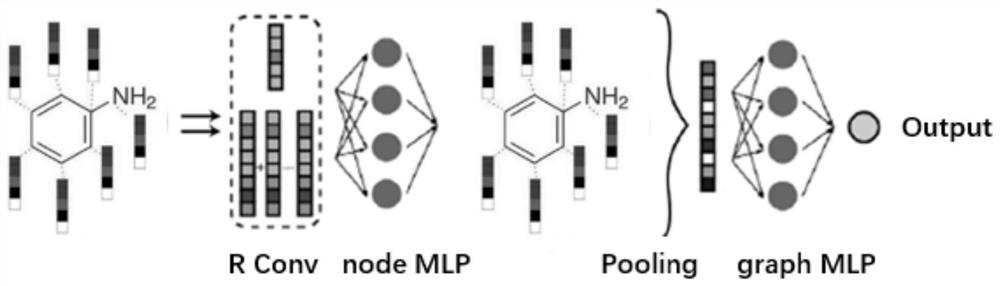
Molecular feature extraction and performance prediction method based on image convolution
ActiveCN113409893ASatisfy IntegrityEfficient crawlingMolecular designNeural architecturesAlgorithmNetwork model
The invention provides a molecular feature extraction and performance prediction method based on image convolution, and the method comprises the steps: carrying out the quantification of the information of atoms and chemical bonds between the atoms, forming a node feature matrix of a molecular image, extracting the connection information between the atoms in a molecule, and forming an adjacent matrix of the image, and fusing the feature matrix and the adjacent matrix into a network model based on image convolution to obtain a molecular feature matrix containing relatively complete atomic information, chemical bond information and molecular structure information, and then performing model training to obtain a final network model. According to the method, the molecular information is effectively captured, and the prediction precision of the model molecular performance is improved.
Owner:CHENGDU POLYTECHNIC
Block encryption device, block encryption method, block decryption device and block decryption method considering integrity verification
ActiveCN104683093ASatisfy IntegritySatisfy confidentialityEncryption apparatus with shift registers/memoriesUser identity/authority verificationComputer hardwareCiphertext
An encryption method and decryption method are provided. The encryption method divides an electronic file into a plurality of message blocks, wherein the message blocks have a sequence. The encryption method sets a checking vector as the last message block. The encryption method performs the following steps on each message block according to the sequence: generating an input block, deriving an output block by encrypting the input block by an encryption key, and deriving an encrypted block by applying XOR operation to the output block and the previous message block, wherein the input block is equivalent to applying XOR operation to the message block, the output block corresponding to the previous message block, and the message block before the previous one. The encryption method generates an electronic encrypted file by concatenating the encrypted blocks. The decryption method performs a series of operations corresponding to the above operations.
Owner:INSTITUTE FOR INFORMATION INDUSTRY
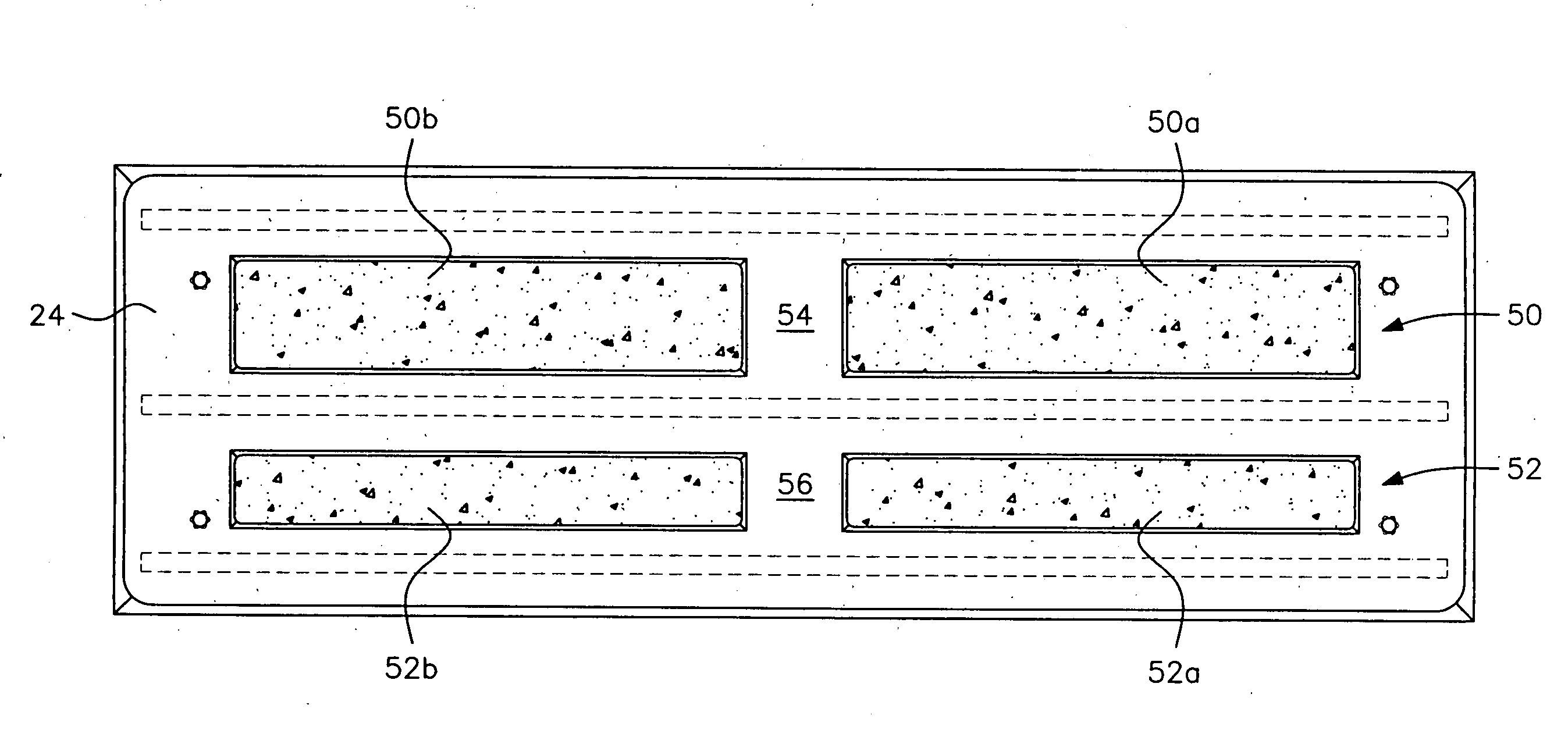
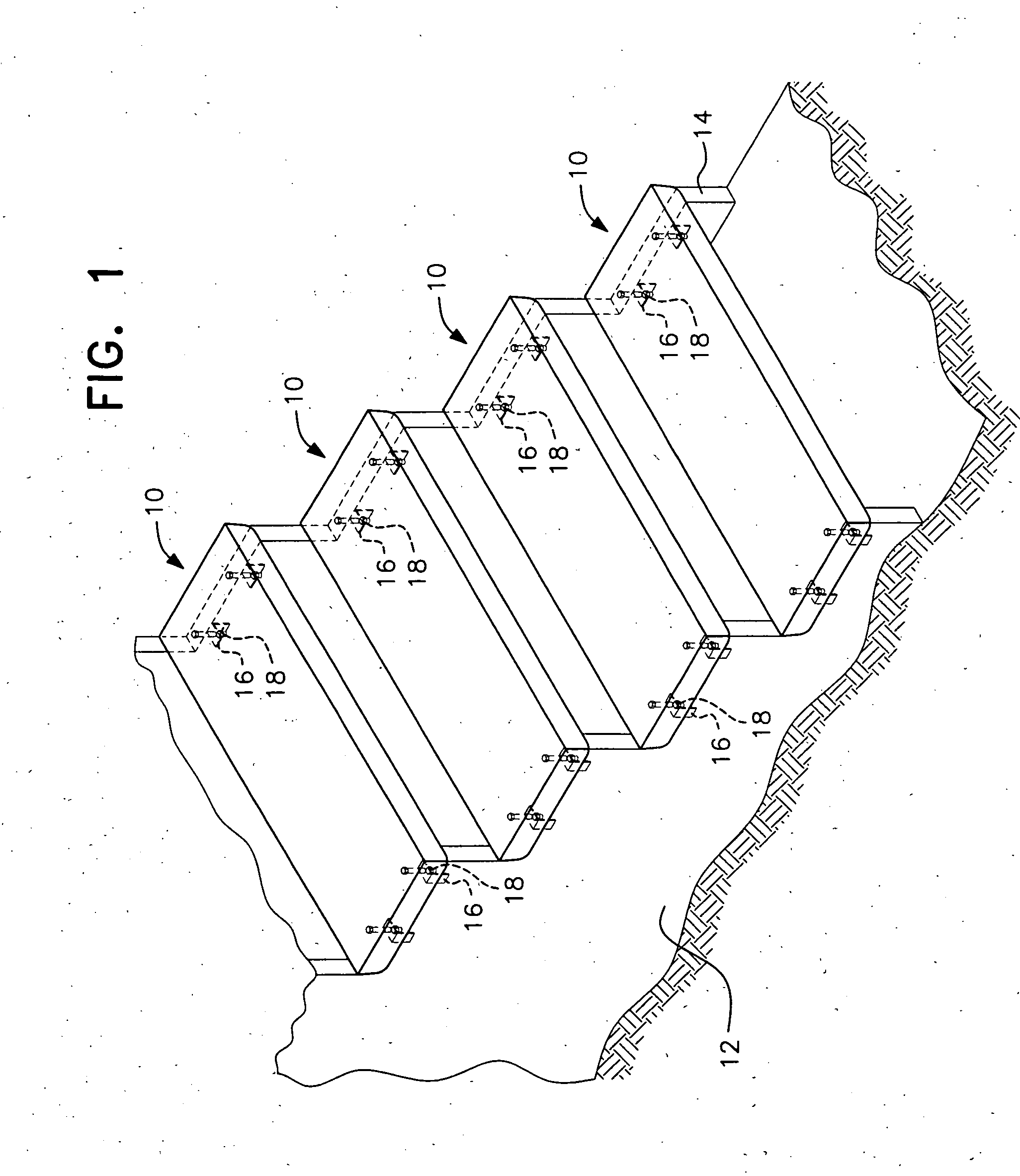
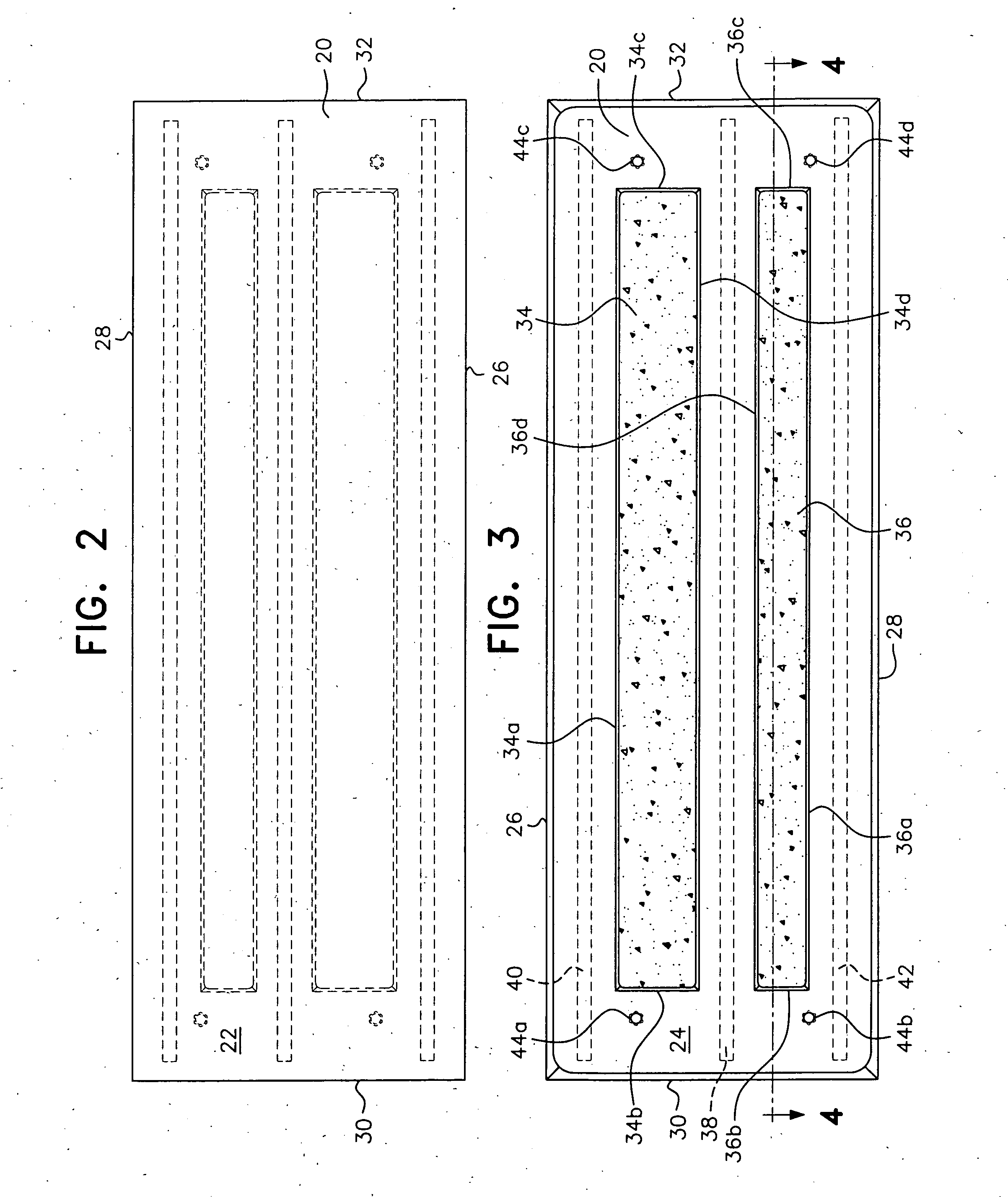
Precast stair tread with bolts
A stair tread having a width of 10, 11 or 12 inches. The tread length varies from 32 inches up to 60 inches in length. The thickness of the tread will usually be 2¼ or 3 inches thick, with a draft of ¼ inch and exposed edges having a ⅜ inch radius. A significant reduction in weight is obtained by forming two rows of recesses in a bottom surface of the stair tread. On a tread having a thickness of 2¼ inches, the depth of the recesses is 1¼ inches deep. On a tread having a thickness of 3 inches, the recesses have a depth of 2 inches. Therefore, the depth of the recesses will be at least 50% of the thickness of the tread.
Owner:MUNSON BOARDMAN
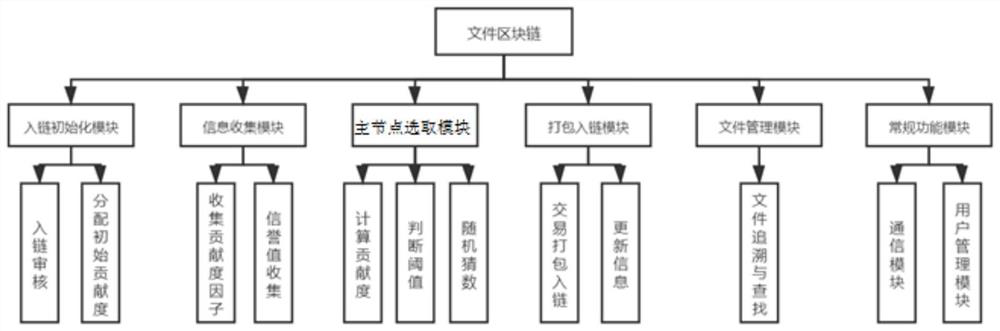
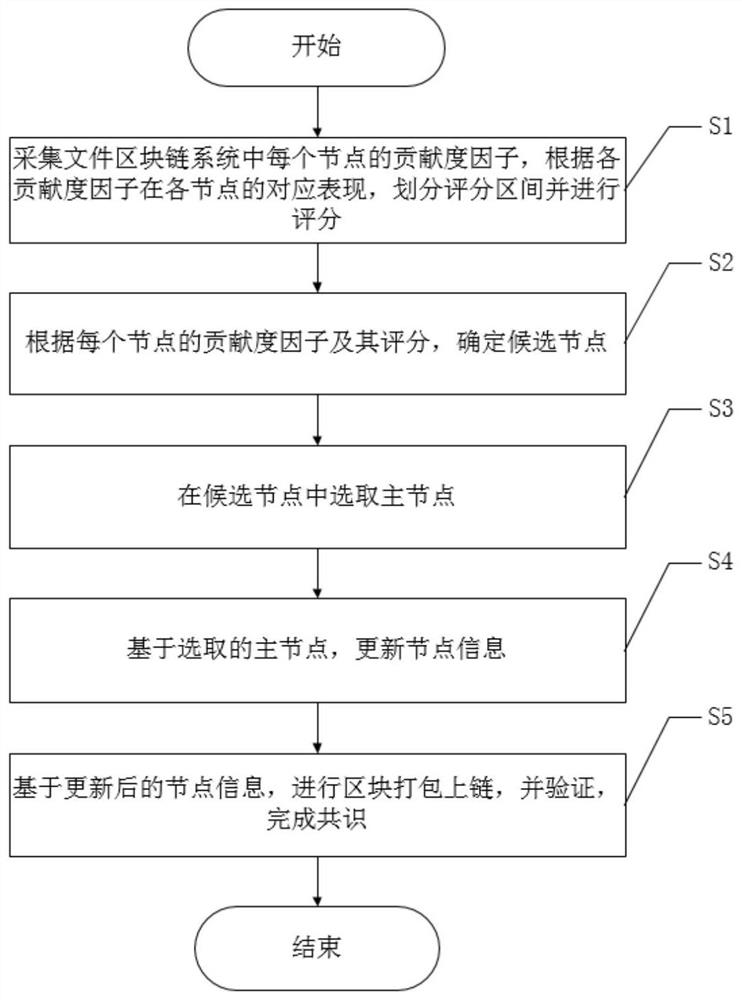
Consensus device and method for file block chain based on contribution value proof
PendingCN114741721AGuaranteed uplink efficiencyIntegrity guaranteedDigital data information retrievalDigital data protectionInformation HarvestingCommunication bandwidth
The invention discloses a consensus device and a consensus method for a file block chain based on contribution value proof. The consensus device comprises an in-chain initialization module, an information collection module, a main node selection module, a packaging in-chain module and a file management module. The consensus device is used for realizing the consensus method, ensuring the file chaining efficiency when the block chain technology is used in the file management field, and ensuring the integrity and the security of the file block at the same time. When an existing virtual currency consensus mechanism is transplanted to the field of file management, a contribution value proof-based method is designed, and the size of a block, the transmission pressure of nodes, the communication bandwidth, the storage amount, the performance, the historical performance and the like serve as calculation factors for calculating contribution values; when the main bookkeeping node is selected, the main bookkeeping node meeting the requirements of all the factors is fully considered and elected, so that the file uplink efficiency in the file management field is met, and meanwhile, the completeness and safety of file blocks are ensured.
Owner:国网四川省电力公司天府新区供电公司
A kind of wooden heat insulation fire door
The invention discloses a wood thermal insulating fireproof door, comprising a door opener, hinges, a door sheet, a door frame, a fireproof glass, a door lock, a handle, an inner frame, a fire protection layer, an angle iron, a wood block, a wall, a pulling rivet, a thermal-protective coating, a decorative surface, and a silica gel acid-Al web. The fireproof door is a movable fireproof separator. The door has functions of a common door, and in a certain time, the door can satisfy fire stability and integrality with the frame, and has special functions of fire protection, smoke insulation, and high-temperature resistance. In case of fire, the door has functions of automatic closure and signal feedback. The fireproof door can freely open at the angle of 180 DEG, and smoothly close, and defects that a door closer of a normally-closed fireproof door can open at the angle of 90 DEG at most and use is not convenient. Once the fireproof door is to close, under a condition that the releaser of the fireproof door is not reset, the releaser overcomes a problem that the normally-closed fireproof door has to be closed manually or cannot close after the normally-closed fireproof door is pushed to a certain limit.
Owner:NINGBO TIANYI FIRE EQUIP CO LTD
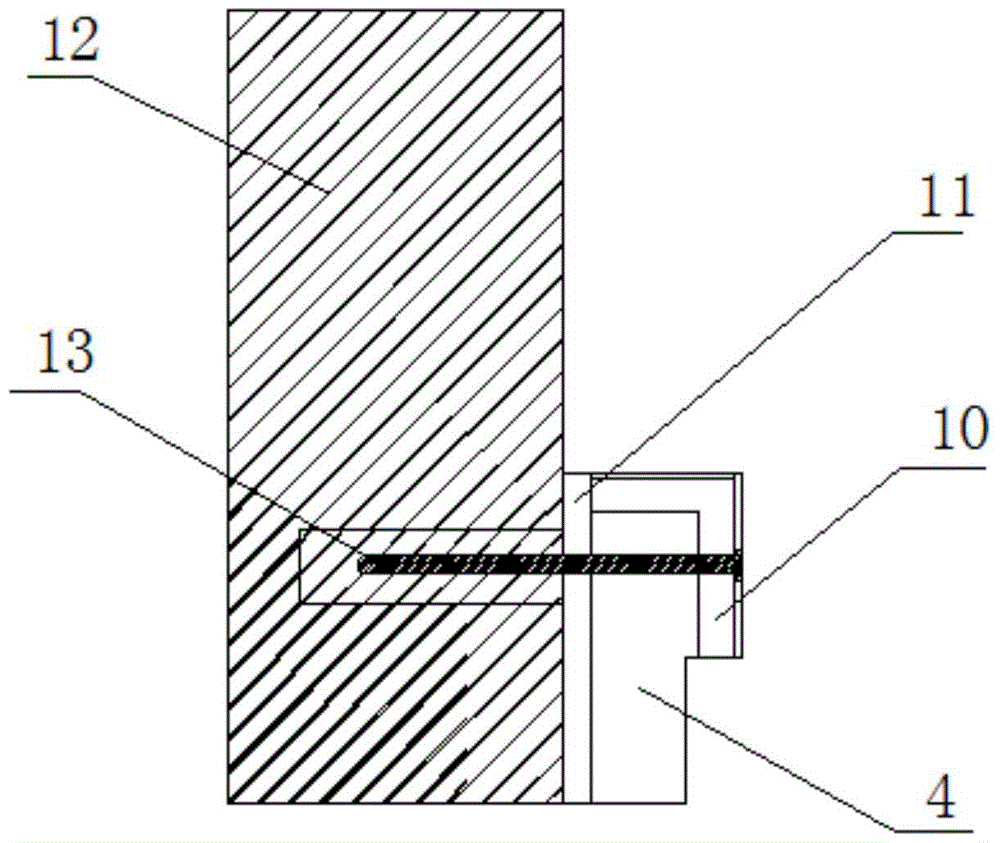
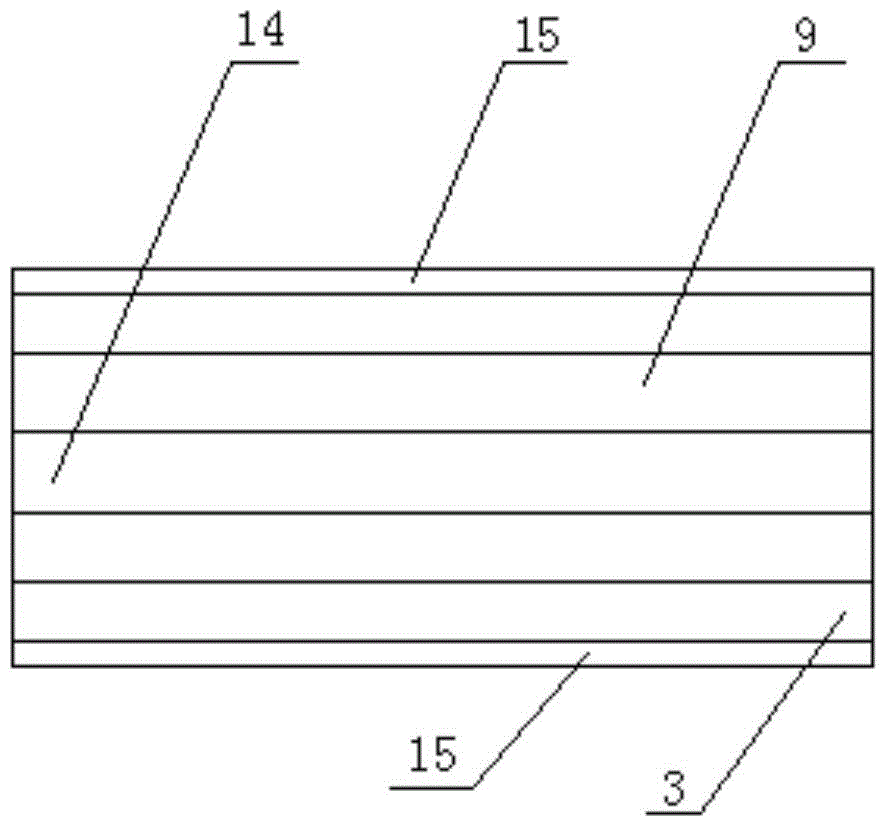
Enterprise signature device, system and method
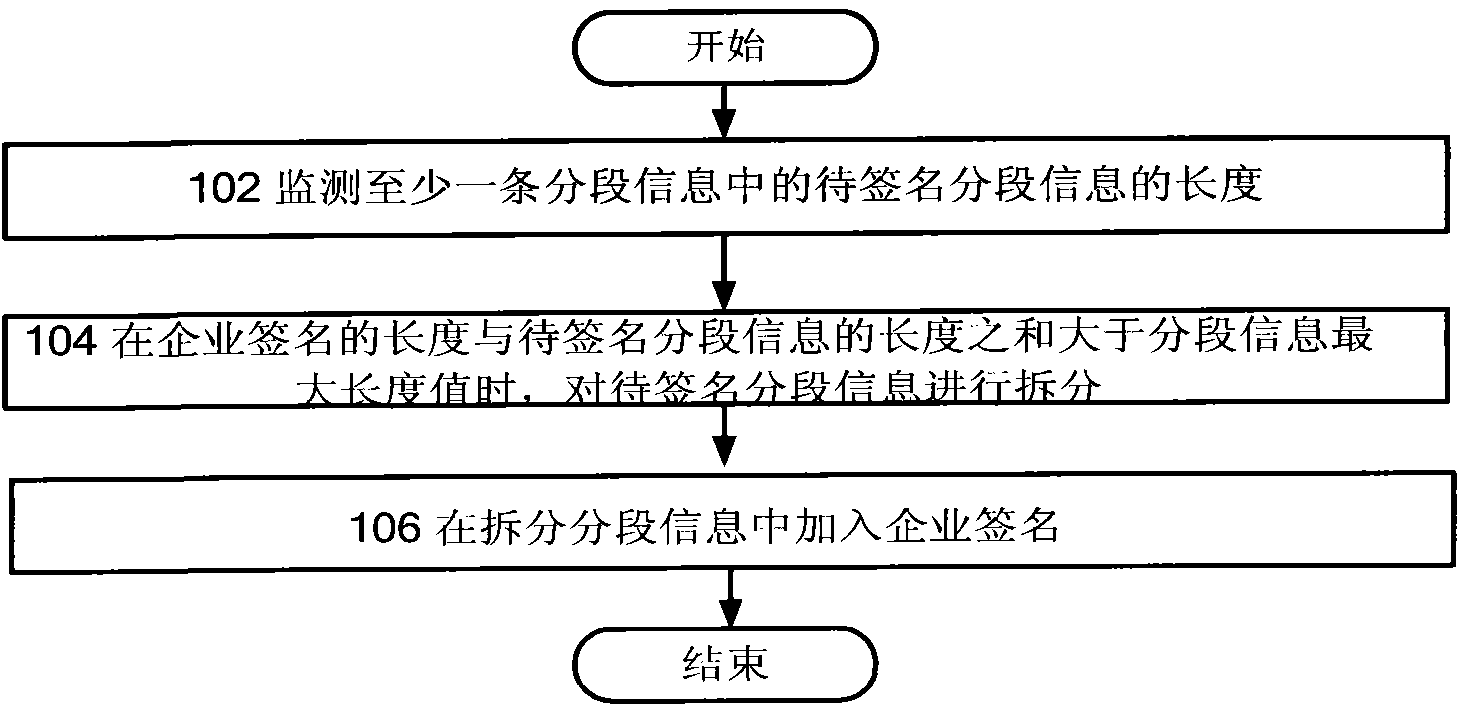
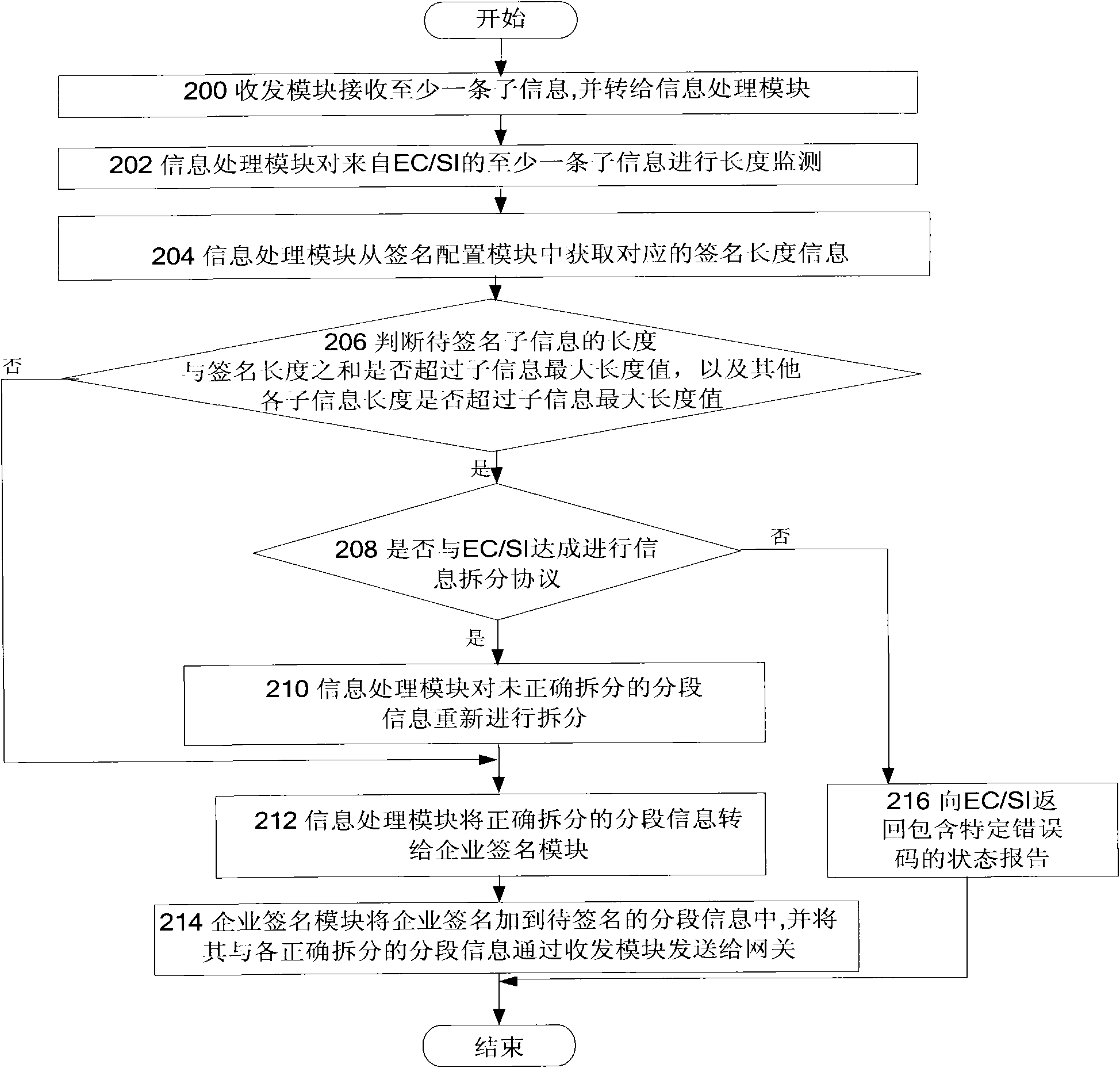
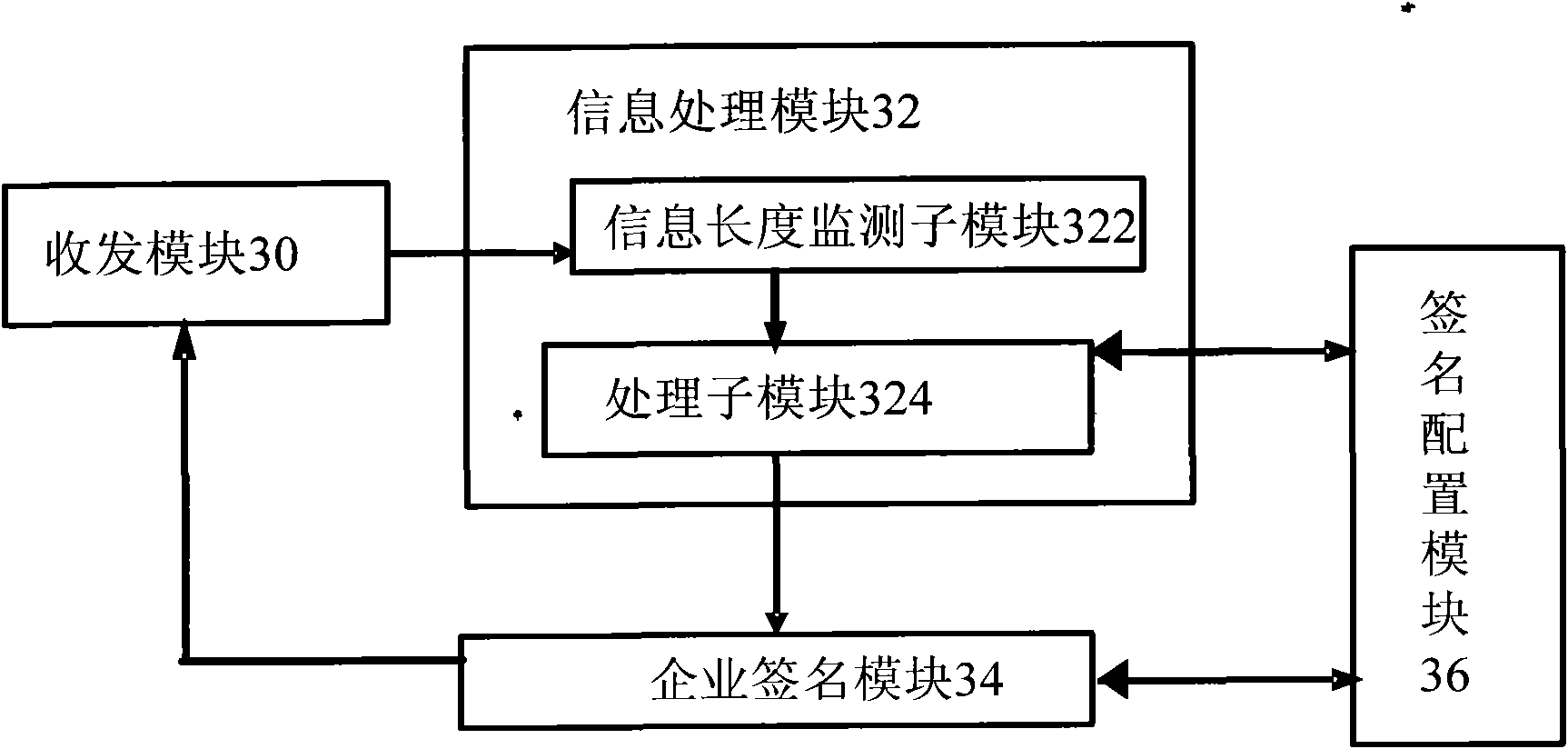
ActiveCN102572748ASatisfy IntegrityMessaging/mailboxes/announcementsSecurity arrangementInformation processingData mining
The invention provides an enterprise signature device, system and method, wherein the device comprises an information processing module and an enterprise signature module; the information processing module is used for monitoring the length of to-be-signed section information in at least one piece of section information belonging to one same total information, and dividing the to-be-signed section information to obtain at least two pieces of section information when judging that the sum of the length of a preset enterprise signature and the length of the to-be-signed section information is larger than the maximum length value of the preset section information; and the enterprise signature module is used for adding the enterprise signature into the divided section information, and sending other section information except for the divided section information in the at least two section information, the signed divided section information, and other section information expect for the to-be-signed section information in the at least one section information. According to the invention, the completeness of information and enterprise signature content can be realized at the same time.
Owner:CHINA MOBILE COMM GRP CO LTD
Strong privacy protection method suitable for medical scene and based on certificateless signature
PendingCN114884665AProtect identity privacyReduce risk of leakageKey distribution for secure communicationPublic key for secure communicationHash functionSecure transmission
The invention relates to a certificateless signature-based strong privacy protection method suitable for a medical scene, which comprises the following steps: step 1), system initialization generation: a key generation center is responsible for generating a system master key and a master public key, constructing a secure hash function and finally disclosing system parameters; step 2), secret value generation: the medical sensor node generates a false identity of the medical sensor node and a part of public key through the randomly selected secret value; the method comprises the following steps of (1) carrying out secret key generation, (2) carrying out secret key generation, (3) carrying out temporary partial private key generation, (4) carrying out initial secret key generation, (5) carrying out updated secret key generation, (6) carrying out signature generation, and (7) carrying out signature verifier.According to the method, a certificateless signature technology is adopted to guarantee safe transmission of medical data, and the method can meet the safety requirements of integrity, authentication, anonymity, traceability and the like of messages.
Owner:YANGZHOU UNIV
Wooden energy dissipation and shock absorption device and wooden structure system with same
ActiveCN108915081AReduce the level of disturbanceImprove seismic performanceProtective buildings/sheltersShock proofingEngineeringStructure system
The invention discloses a wooden energy dissipation and shock absorption device and a wooden structure system with the same. The wooden energy dissipation and shock absorption device comprises two connecting sections, wherein the two connecting sections are connected through an energy dissipation section. The energy dissipation section comprises two sections of wooden connecting pieces, wherein the two sections of the wooden connecting pieces are connected through soft steel shear dampers, dovetail-shaped tenons are separately arranged at the outer ends of the two wooden connecting pieces, dovetail-shaped grooves are separately formed in the two connecting sections, and the tenons of the two wooden connecting pieces are separately inserted into the grooves of the two connecting sections. The connecting sections are wooden columns or wooden panel walls. When the connecting sections are the wooden columns, friction plates are separately arranged at the outer ends of the two wooden connecting pieces. A main structure of the wooden structure system is rigidly connected with the wooden energy dissipation and shock absorption device. According to the wooden energy dissipation and shock absorption device, earthquake energy can be dissipated, the damage to wooden structure buildings under an earthquake is reduced, and energy dissipation components after the earthquake are convenient toreplace. The wooden energy dissipation and shock absorption device and the wooden structure system with the same can be used for improving the seismic performance of existing wooden structure buildings and building new wooden structure buildings.
Owner:BEIJING UNIV OF CIVIL ENG & ARCHITECTURE
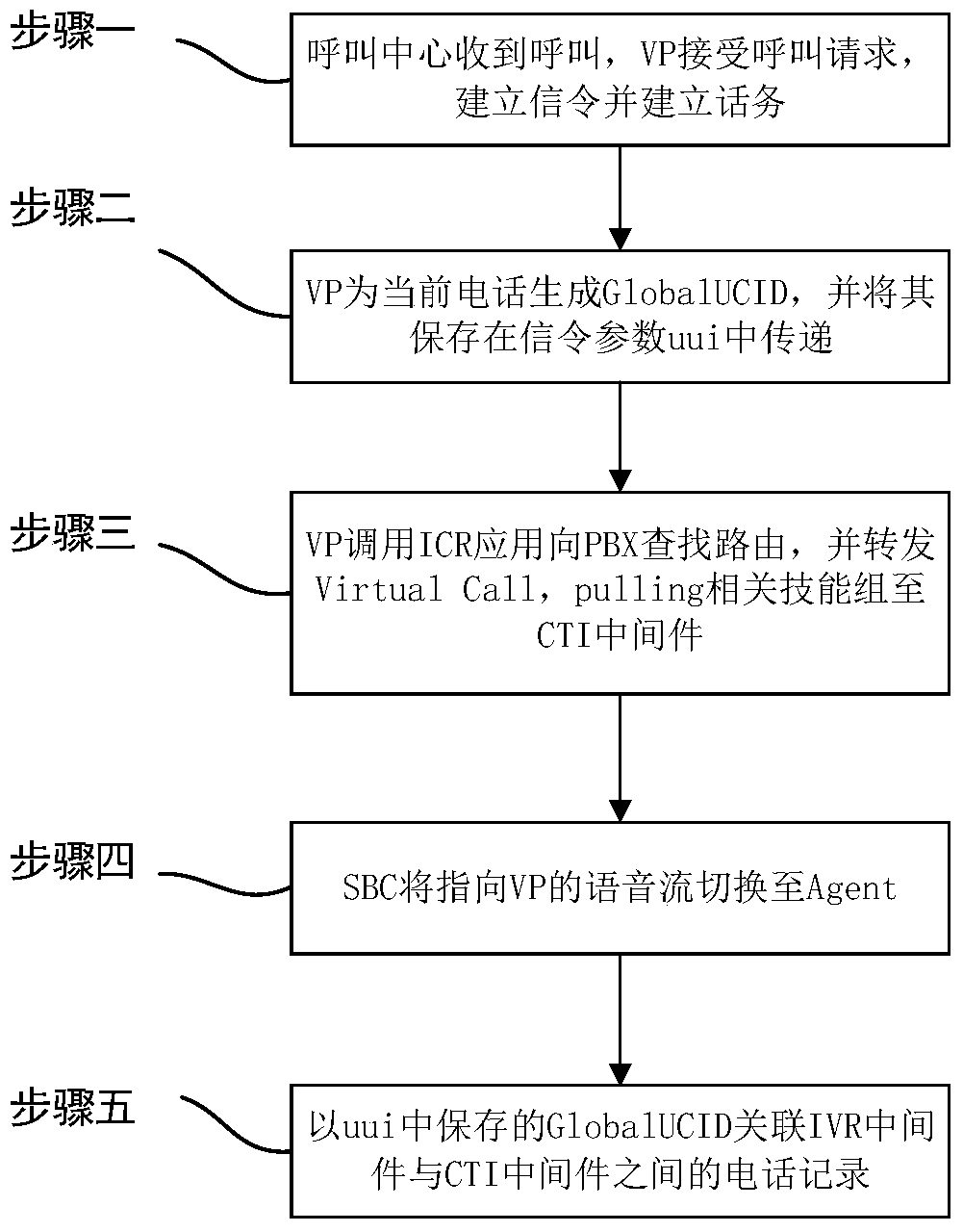
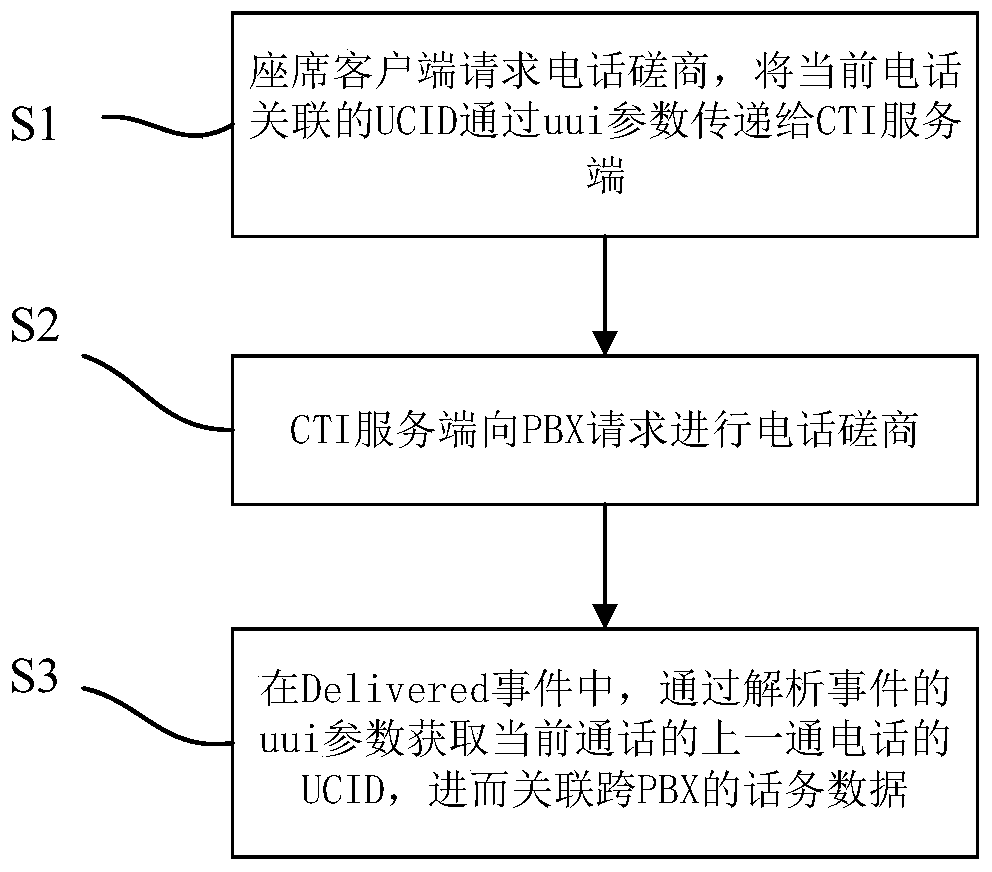
Traffic data association method of call center
ActiveCN105592236BRealize associationSatisfy IntegritySpecial service for subscribersSecure telephoneSpeech sound
The invention discloses a telephone traffic data association method of a call center. The telephone traffic data association method includes following steps: the call center receives a call, a VP receives a call request, and a signaling and telephone traffic are established; the VP generates a global UCID for the current telephone, and the global UCID is saved in a signaling parameter uui for transmission; the VP calls an ICR application, searches routing to a PBX, and forwards Virtual call and pulling related skill groups to a CTI middleware; an SBC switches a speech stream pointing to the VP to Agent; and the global UCID saved in uui is associated with telephone records between an IVR middleware and the CTI middleware. According to the method, the integrity of telephone traffic data of a call center telephone system can be realized, complete track of the telephone between the PBXs is recorded, and the accuracy and the efficiency of data analysis, mining, statistics, and telephone charging etc. can be improved.
Owner:携程旅游信息技术(上海)有限公司
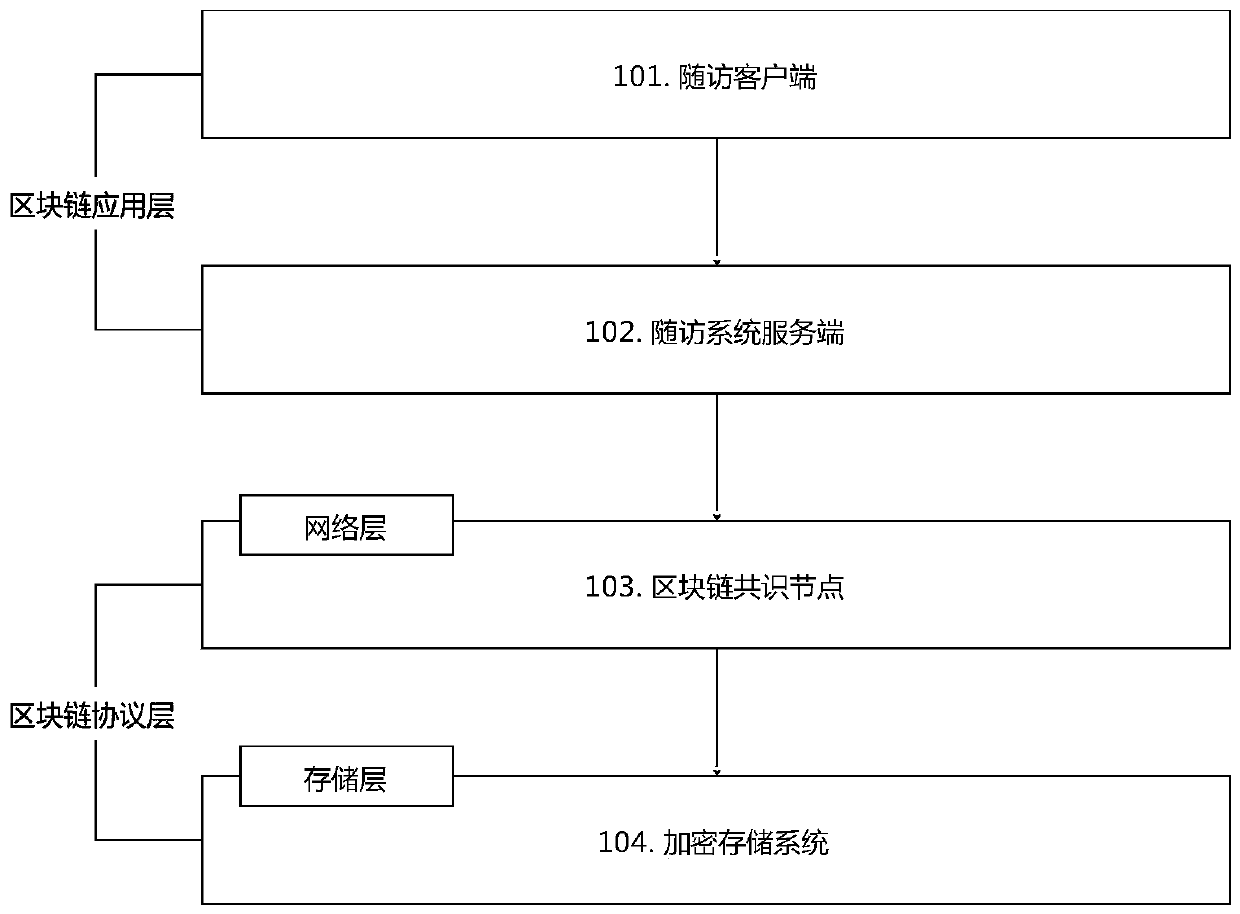
Distributed follow-up visit system based on block chain and ciphertext retrieval technology
PendingCN111414433AImprove usabilityFulfil requirementsDatabase distribution/replicationSpecial data processing applicationsCiphertextOriginal data
The invention relates to the technical field of medical follow-up visits and block chains, in particular to a distributed follow-up visit system based on a block chain and ciphertext retrieval technology. The block chain protocol layer comprises a plurality of block chain consensus nodes used for forming a block chain network and realizing data consensus, and all the block chain consensus nodes equally participate in the consensus process and can generate blocks and store block chains. According to the distributed follow-up visit system based on the block chain and the ciphertext retrieval technology, the system comprises a block chain application layer and a block chain protocol layer, by implementing a block chain technical means and by virtue of the characteristics of decentralization,trust removal and collective maintenance of a block chain, the heterogeneous storage of follow-up visit data can be realized, so that the reliability of the data is ensured, and the data is ensured not to be lost, tampered and non-repudiated through a consensus algorithm; and by implementing database encryption and ciphertext retrieval technical means, original data cannot be identified in a database and can be retrieved without decryption.
Owner:北京阳光辰鑫科技有限责任公司
High-gloss non-tinning coating of black bus bar and preparation method of black bus bar
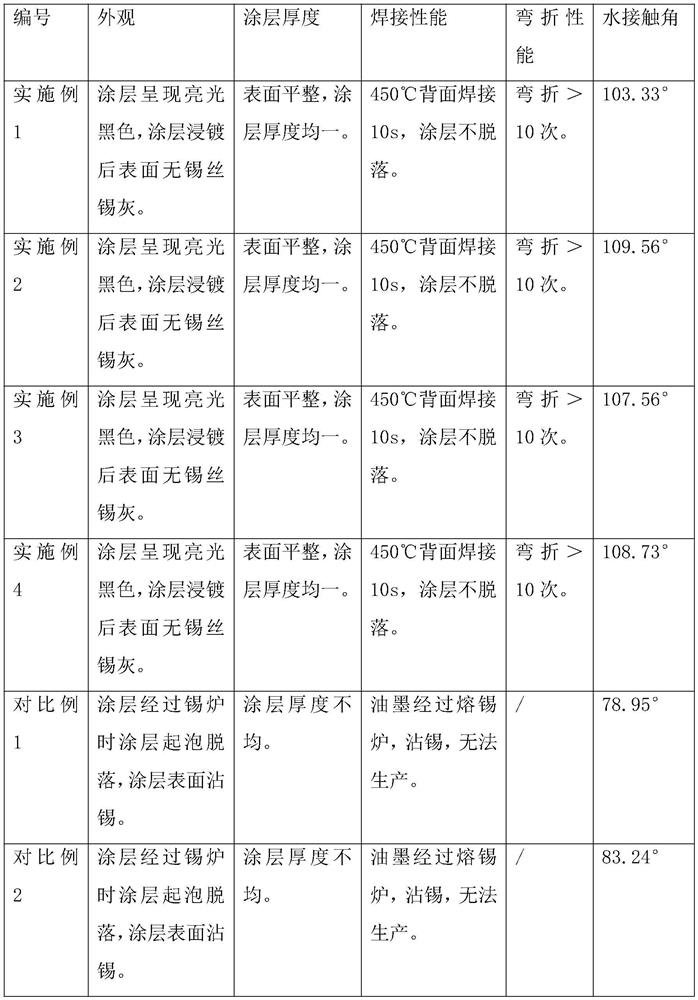
ActiveCN114292551AGuaranteed cleanlinessImprove temperature resistanceInksPhotovoltaic energy generationDiethylene glycol monobutyl etherEthyleneglycol monobutyl ether
The invention discloses a black bus bar highlight non-wetting coating and a black bus bar preparation method, and the black bus bar highlight non-wetting coating comprises the following components by weight: 25-30 parts of a water-based polyhydroxy acrylic emulsion, 3-10 parts of a fluorine modified acrylic emulsion, 5-6 parts of carbon black, 5-10 parts of nano titanium dioxide, 15-25 parts of isobutanol, 10-15 parts of diethylene glycol monobutyl ether, and 5-8 parts of water. By using the formula, an unprinted area is uniformly plated with a tin-lead alloy during tin plating, and the tin-lead alloy can only be slightly attached to a printed area due to low surface energy and can be scraped off by an air knife when the printed area is taken out of a tin furnace, so that the cleanness of the surface of a coating is ensured; and meanwhile, the high-gloss non-tinning ink has better temperature resistance than other inks, and the copper base body has higher melting point, so that the phenomenon that the copper base serving as a printing stock is melted due to overhigh welding temperature when the ink is printed on the copper base is avoided, the displacement phenomenon of the ink layer is avoided, and the high-gloss non-tinning ink is more convenient for customers to use.
Owner:SUZHOU TONYSHARE ELECTRONICS MATERIALS TECH
Desulfurized gypsum calcination apparatus
The invention discloses a desulfurized gypsum calcination apparatus which comprises a hot gas source device, a gypsum conveying device, a calcination device and a tail gas absorption device, wherein the hot gas source device is connected with the inlet end of the calcination device through a first pipeline; the outlet end of the calcination device is connected with the tail gas absorption device through a second pipeline; the bottom of the calcination device is connected with a third pipeline; the inlet end of the third pipeline is connected with the gypsum conveying device; and the outlet end of the third pipeline is connected with the calcination device. By using the above manner, the desulfurized gypsum calcination apparatus has a simple structure, can ensure sufficient gypsum supply to the inside of the calcination device, ensures the continuity of the calcination process, ensures the full integrality of the calcination process and improves the calcination efficiency.
Owner:CHANGZHOU VOCATIONAL INST OF ENG +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com