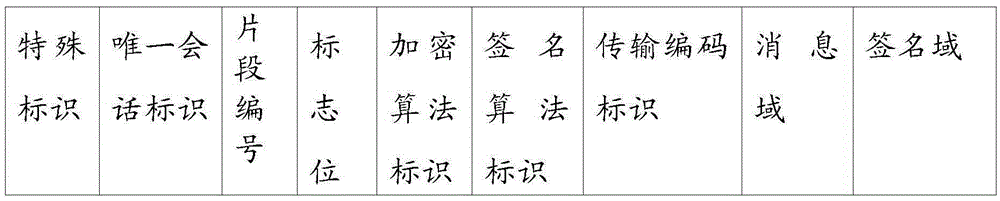
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
32results about How to "Won't attack" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
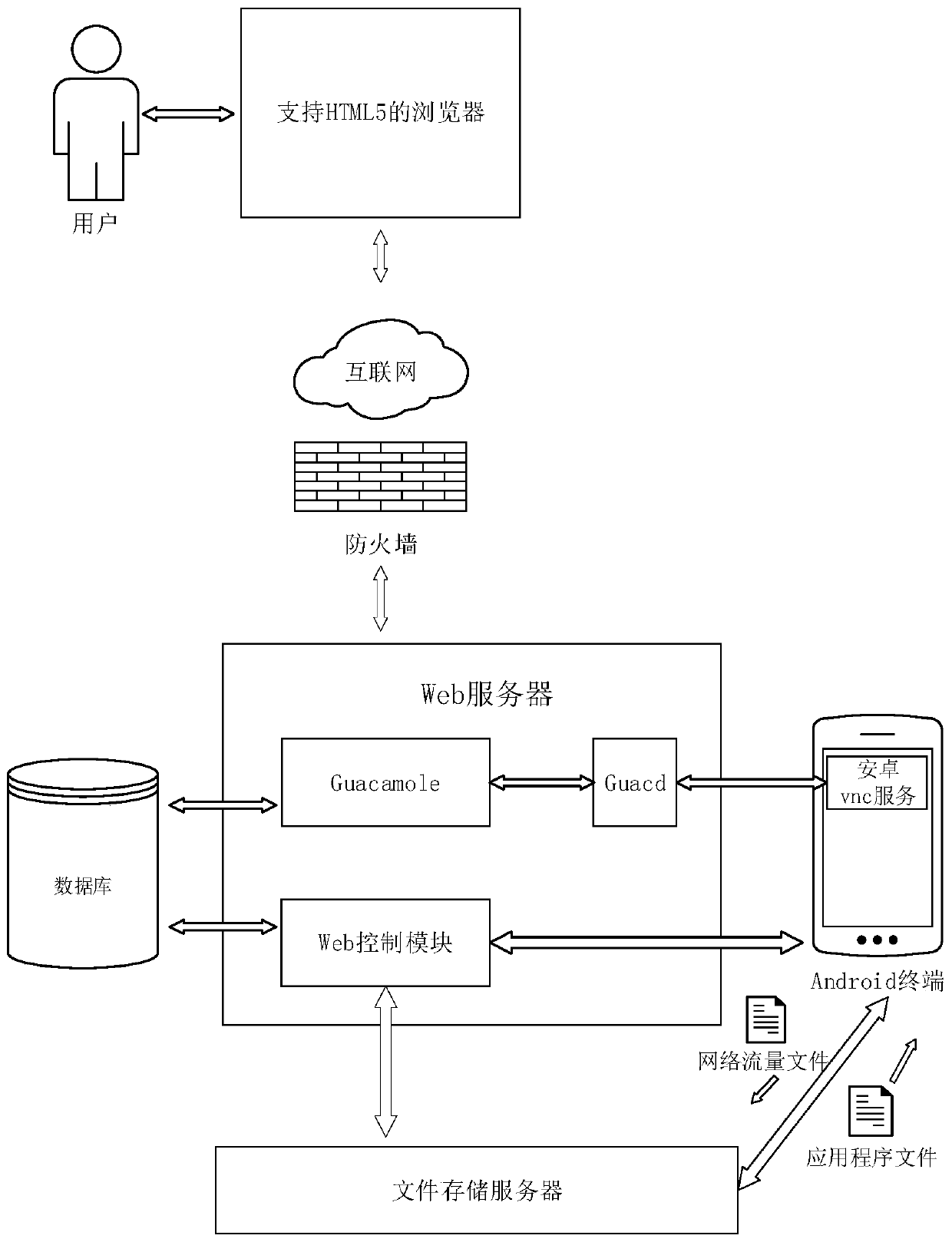
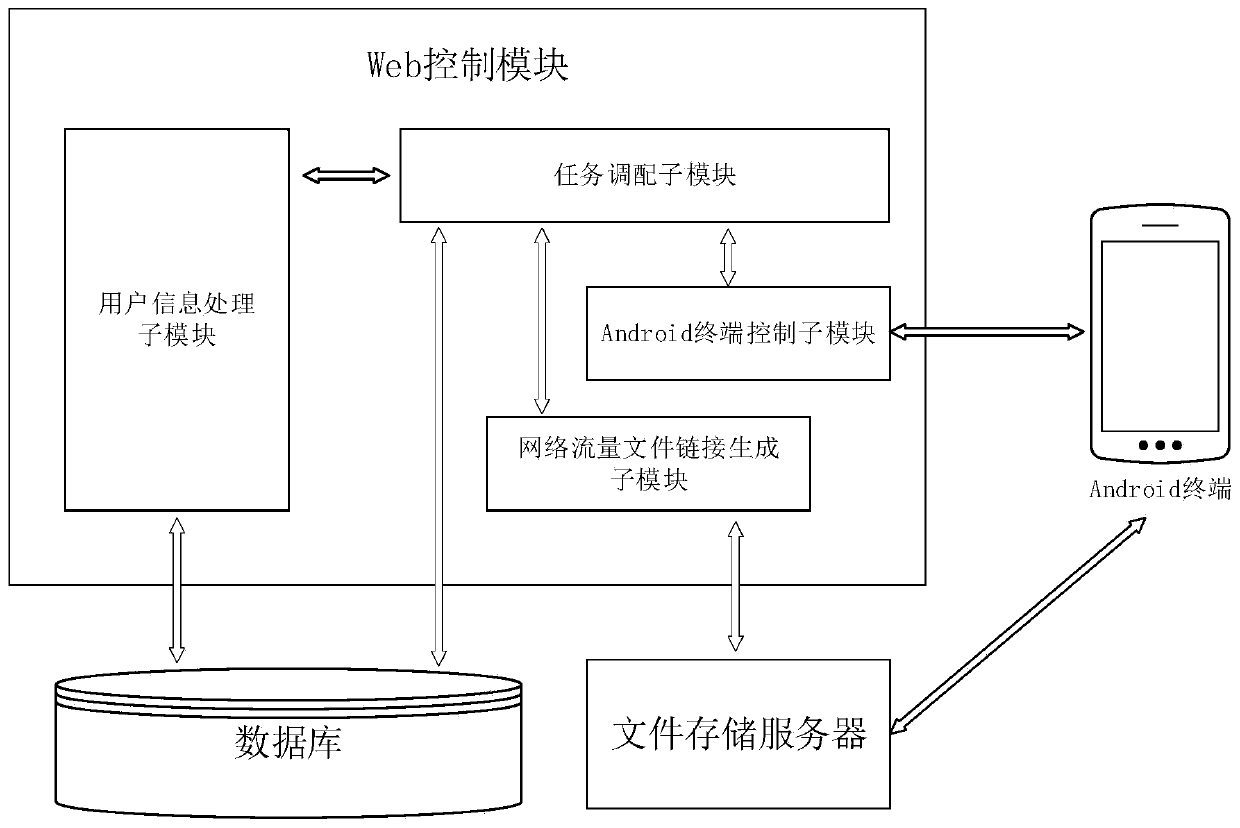
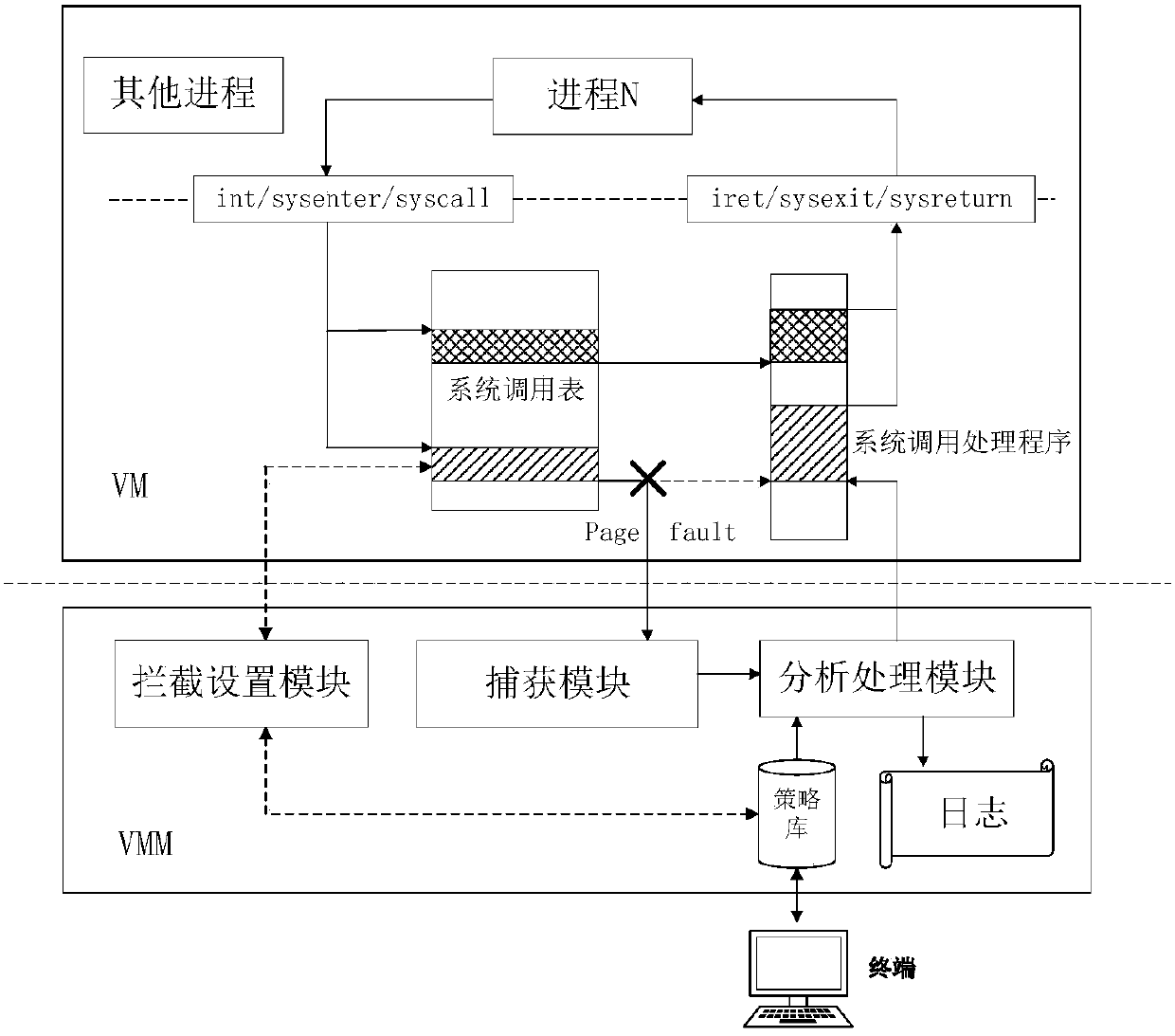
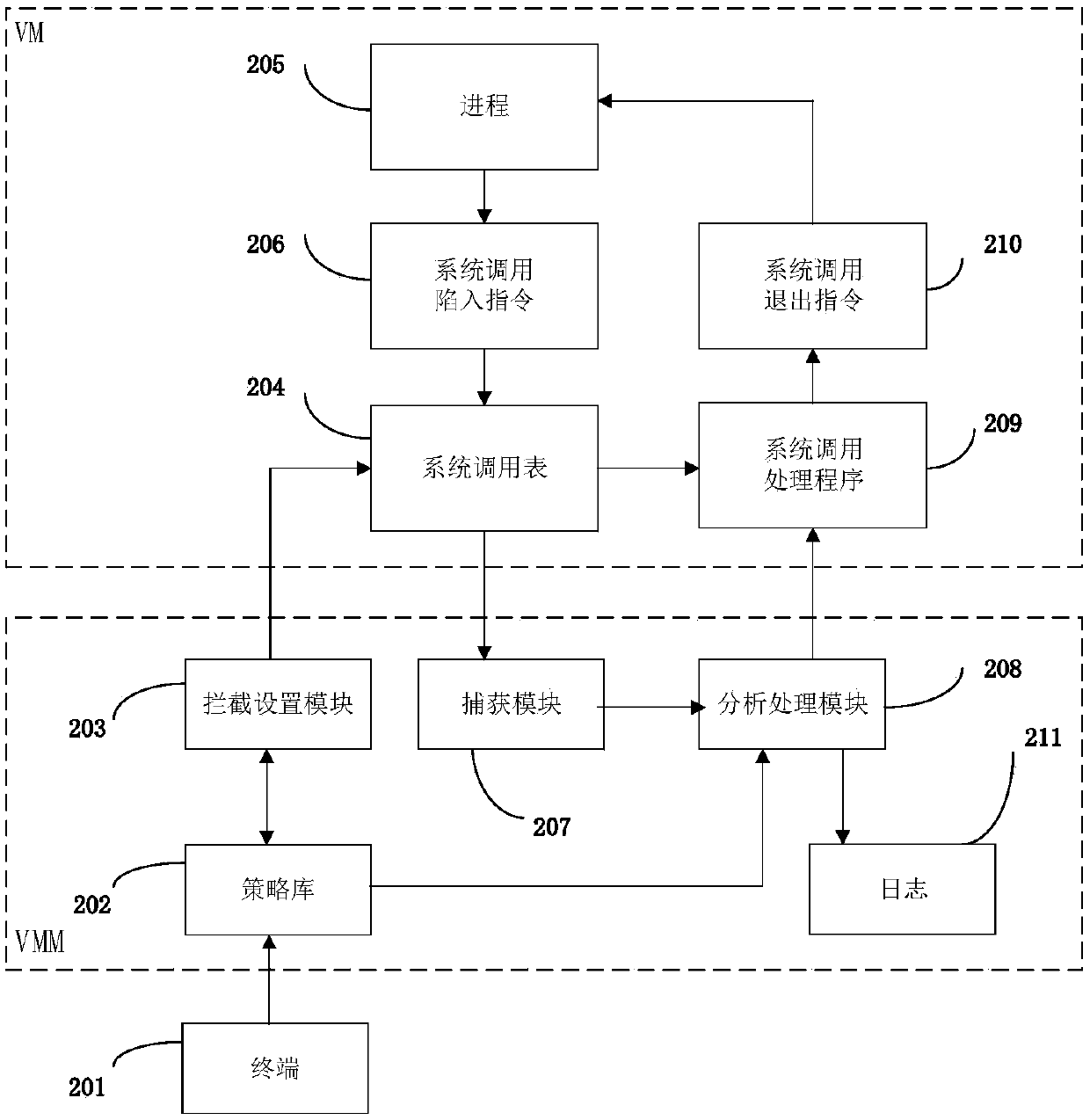
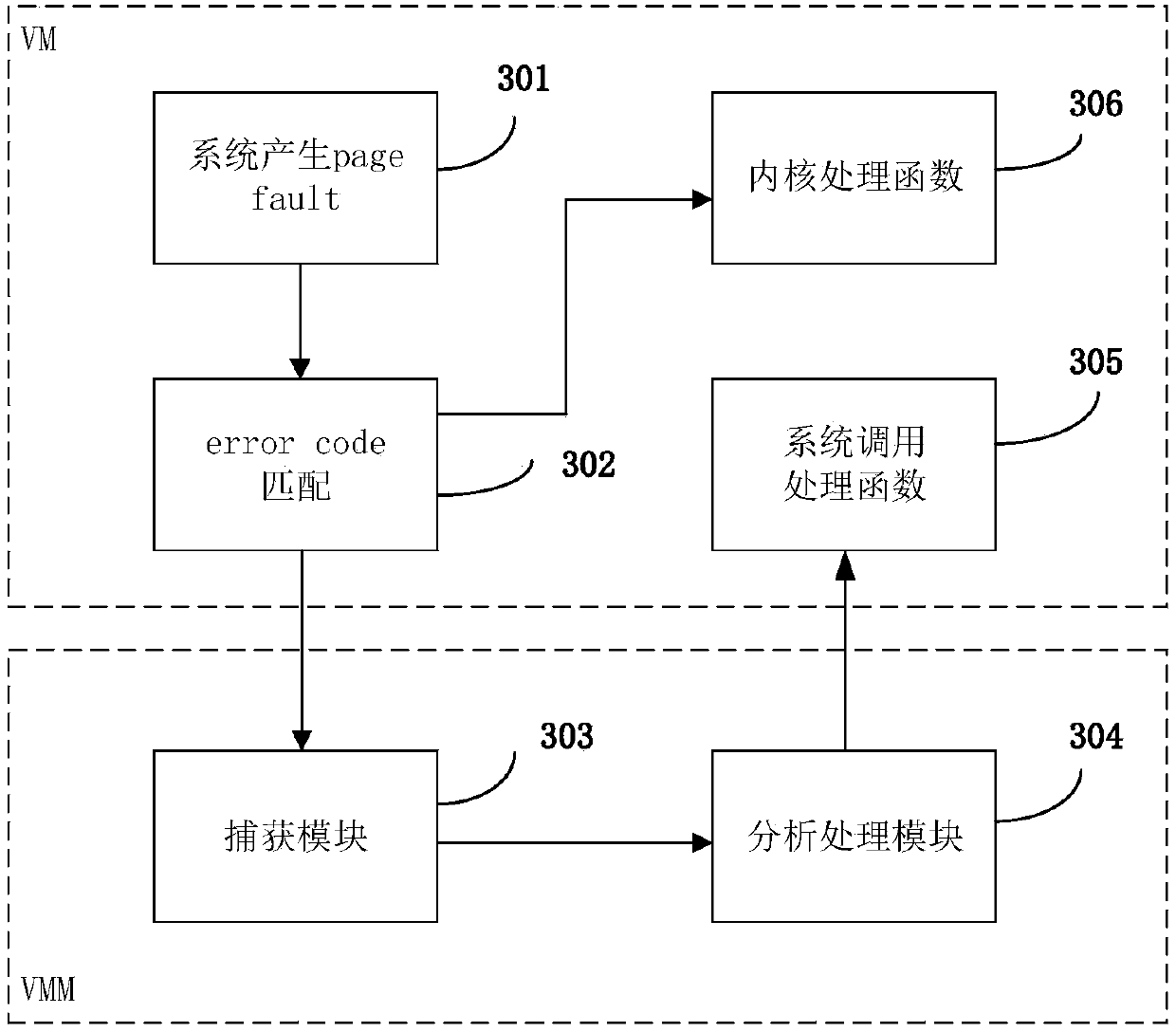
System and method for monitoring virtual machine process, and method for filtering page fault anomaly
ActiveCN106055385AIncrease flexibilityNo performance lossSoftware simulation/interpretation/emulationProcess systemsComputer module
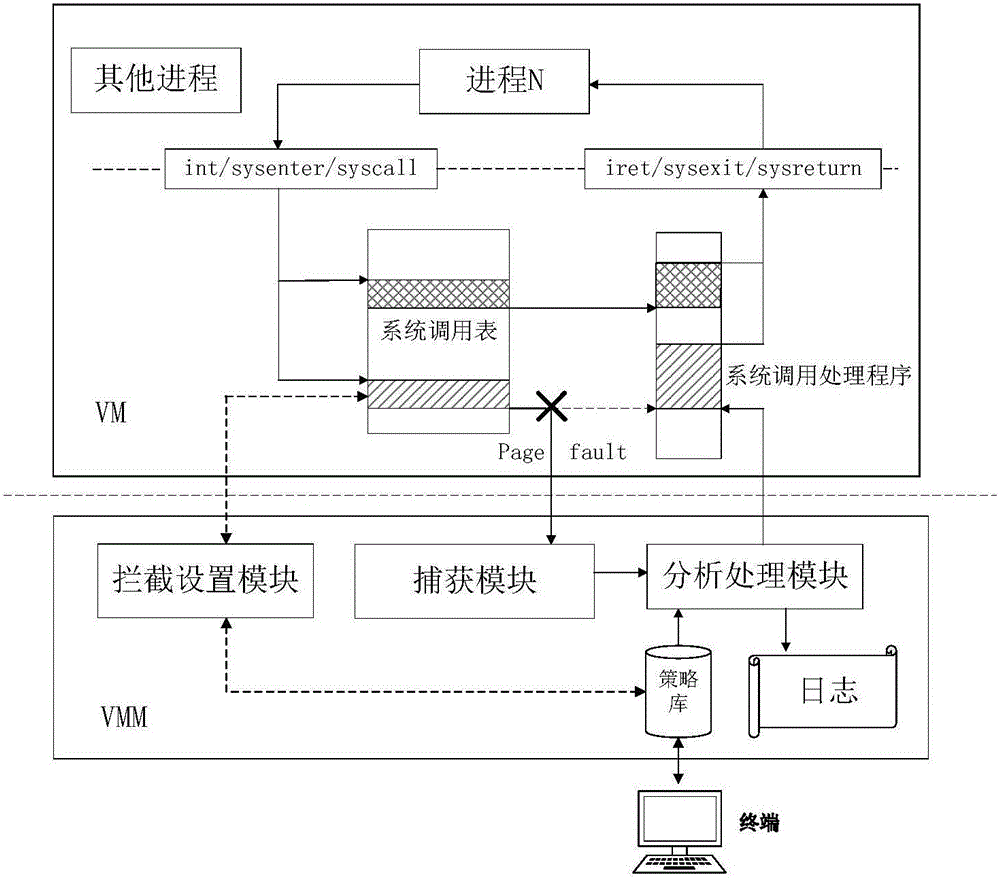
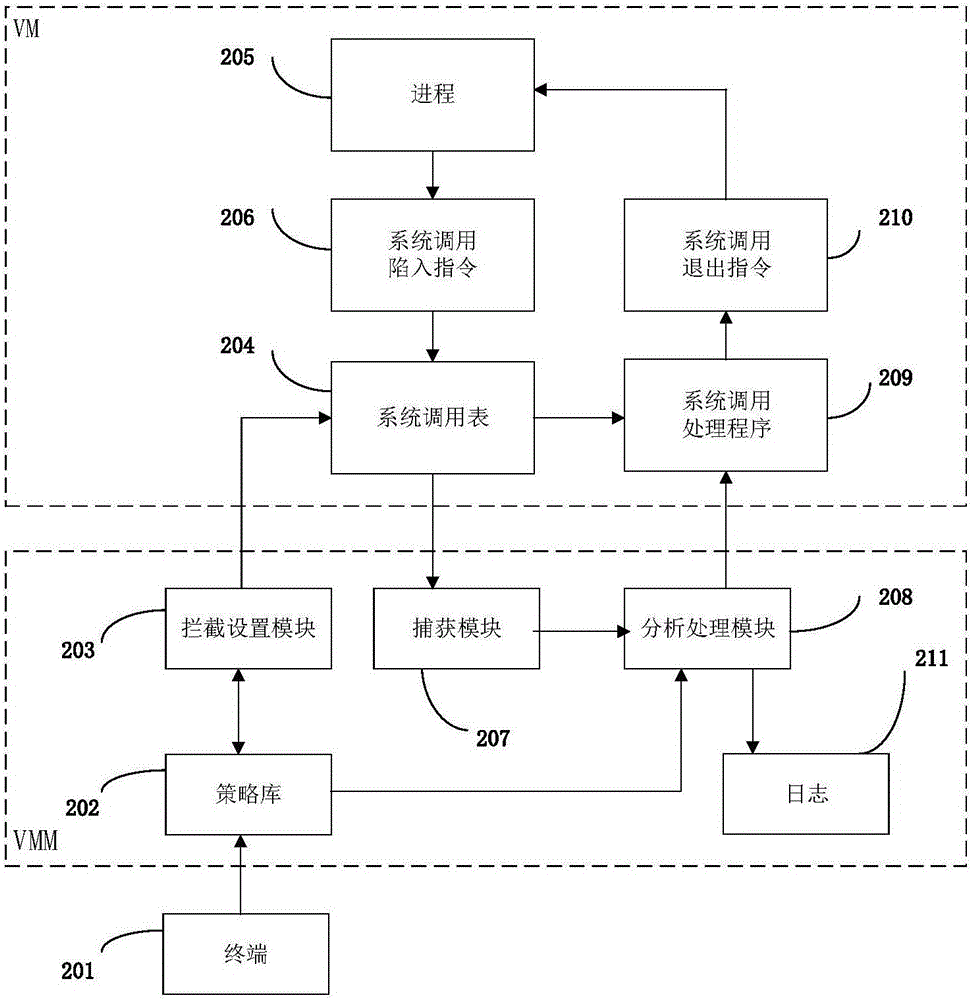
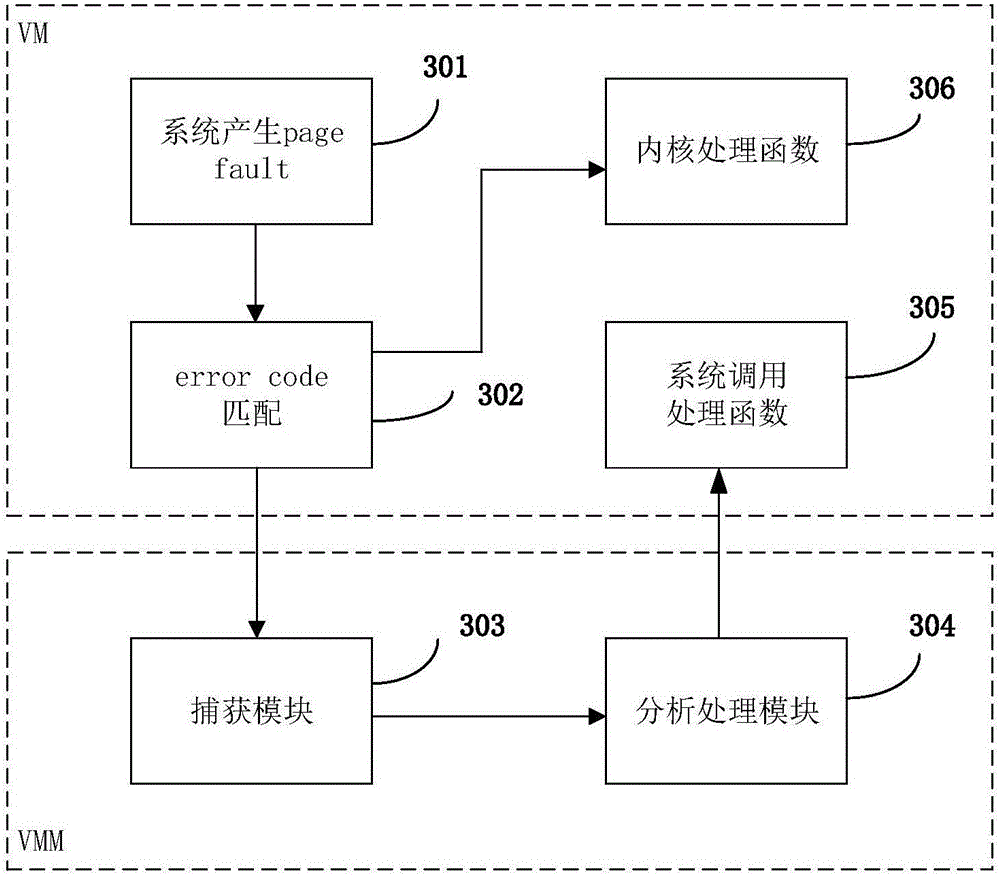
The invention discloses a system and method for monitoring a virtual machine process, and a method for filtering page fault anomalies. The monitoring system comprises an interception setting module which modifies a virtual machine system call table dynamically in real time and intercepting virtual machine system call; a capturing module which captures anomalies generated when the virtual machine process is called by a monitoring system; an analysis processing module which analyzes a virtual machine process system call behavior is abnormal or not; a strategy library which stores virtual machine system call monitoring strategies, wherein abnormal system call behavior data in the virtual machine is stored in logs; and a terminal which updates the strategy library dynamically in real time. According to the system and methods, according to functions needing to be monitored, the monitoring strategies are configured dynamically in real time; the monitoring strategies can take effect instantly without rebooting the virtual machine or a cloud platform; extra performance consumption resulting from the fact that the virtual machine process is unnecessarily called by the monitoring system can be avoided; and the system and methods are compatible with system call processes initiated by all x86 instructions.
Owner:SICHUAN UNIV
Method and device for realizing the extended authentication protocol in the wireless network
InactiveCN101009910AImprove securityComprehensive treatmentRadio/inductive link selection arrangementsTransmissionComputer scienceSession key
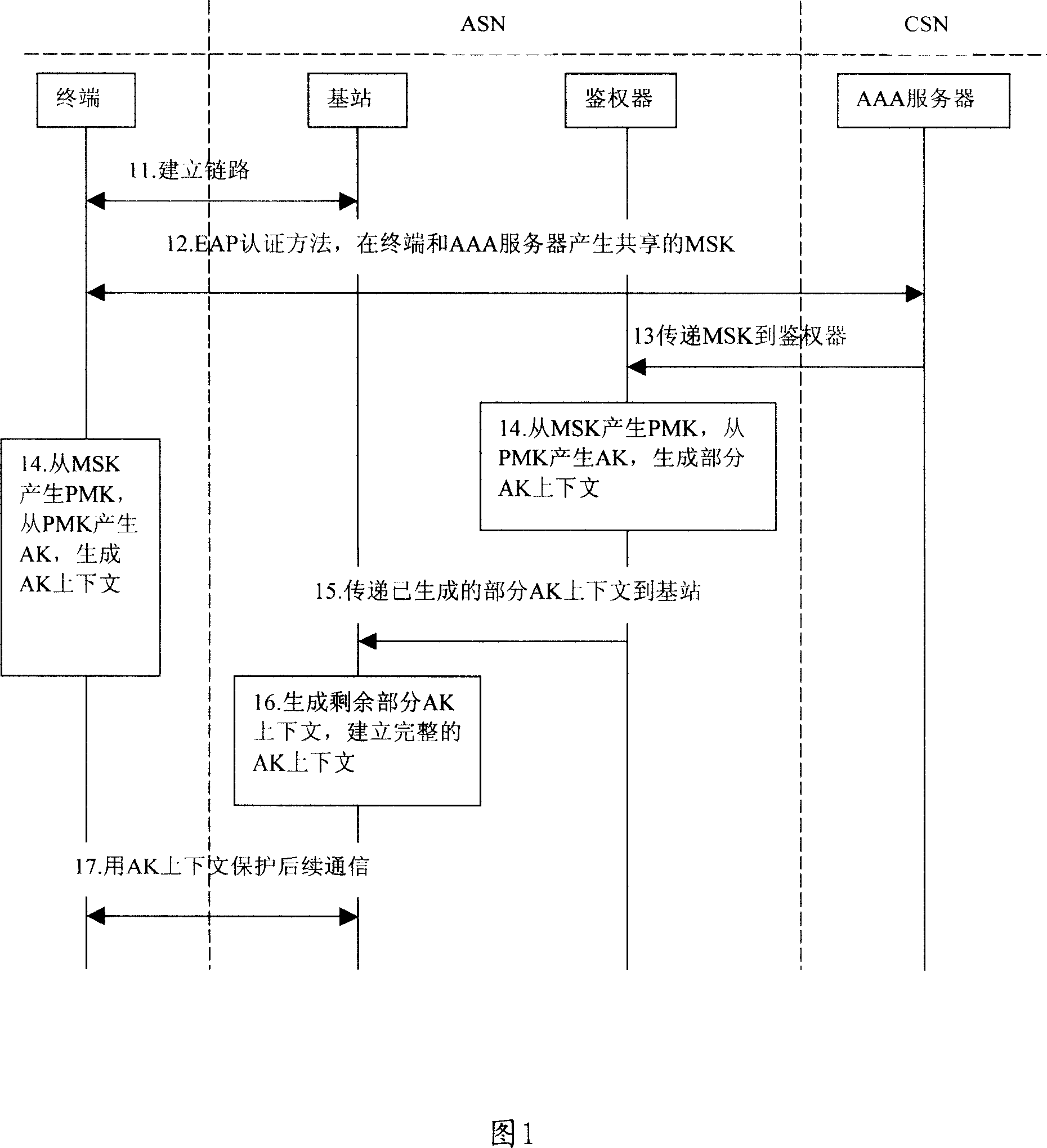
The related method for realizing EAP certification in wireless network comprises: on authentication device, generating corresponding EIK according to obtained MSK in EAP process; then, sending EIK message to BS to generate complete EIK text. This invention improves security for wireless communication network business, both on preventing illegal attack to provider, and providing reliable business for user.
Owner:HUAWEI TECH CO LTD
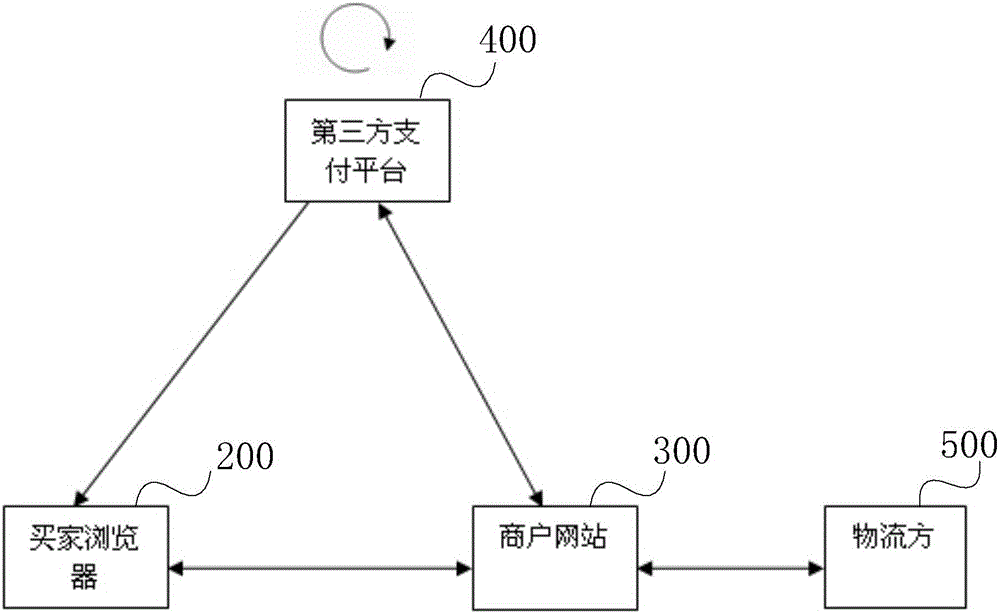
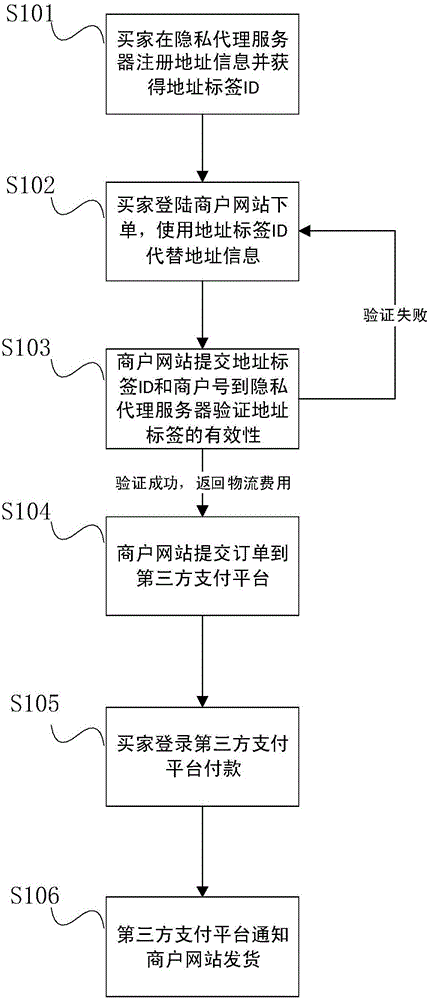
User privacy protection method and system based on third party payment platform
InactiveCN105812467AStrengthen supervisionGuaranteed isolationPayment architectureBuying/selling/leasing transactionsUser privacyInternet privacy
The invention discloses a user privacy protection method and system based on a third party payment platform. The method comprises the steps that: an agent server storing user privacy data is established, a buyer only needs to register personal address information on the agent server, the agent server will generate an address label ID, and only logistic distribution platforms authenticated by the privacy agent server can obtain address information through the address label; when the buyer places an order on a merchant website, the buyer needs to provide the address label instead of related address information, the merchant website obtains a temporary encrypted code from the agent server according to the address label ID and the order number in a delivering process, and the logistic distribution platform decrypts the encrypted code to obtain the related address information; and after the buyer receives the goods, the buyer informs the agent server through the third party payment platform to invalidate the encrypted code. According to the invention, the personal privacy of the buyer in the shopping online process is protected to the maximum extent, and the personal information of the buyer is prevented from being leaked.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
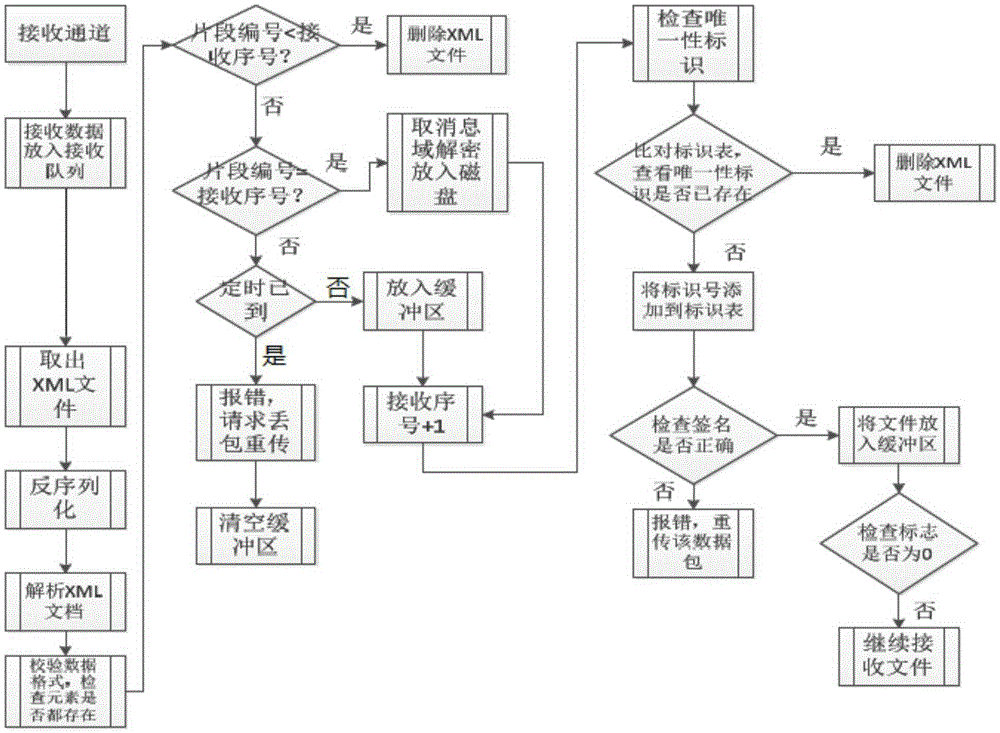
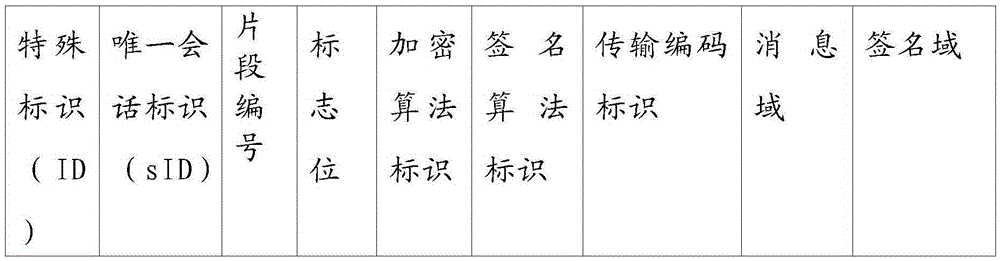
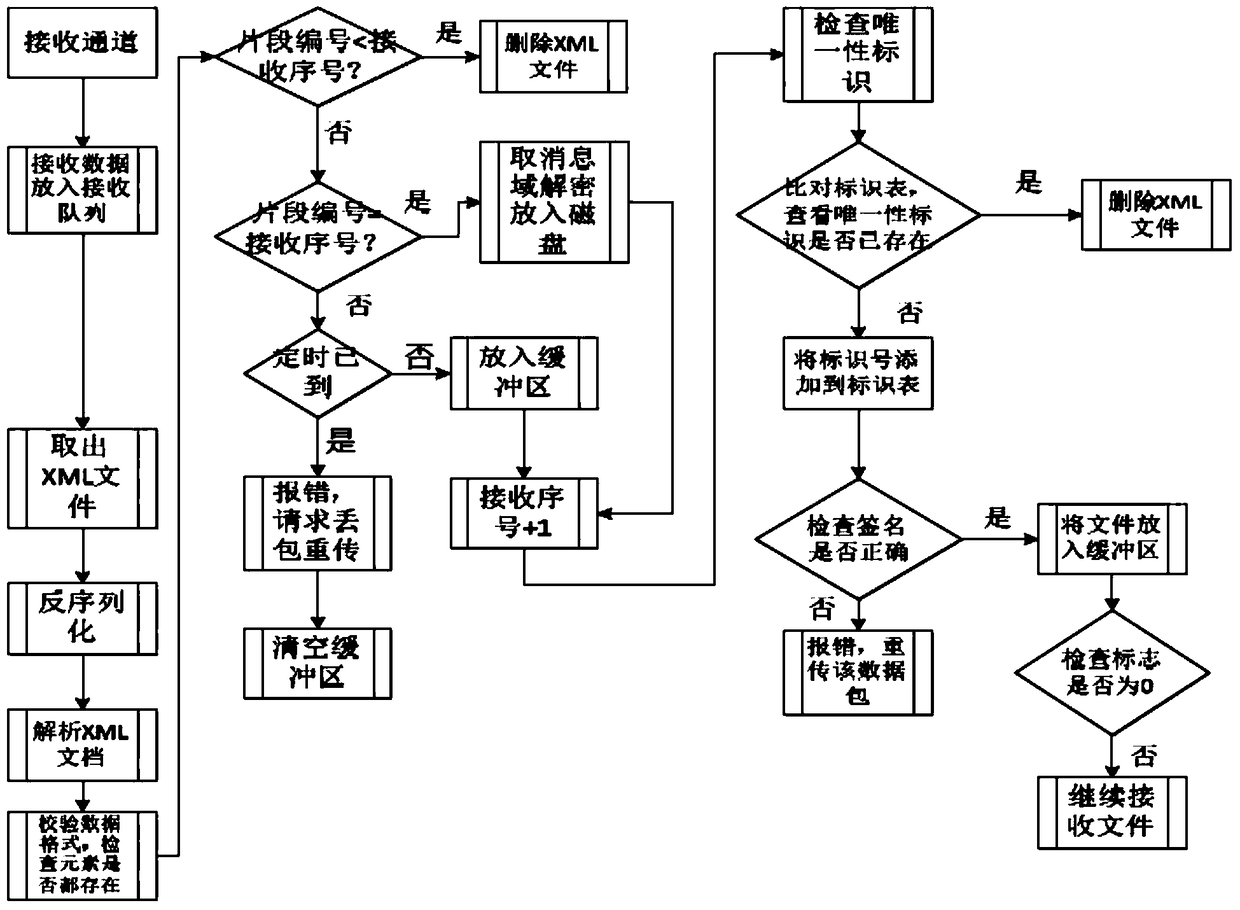
Method for resisting DDOS attacks based on channel hopping mode
ActiveCN105262737AImprove securityImprove reliabilityTransmissionComputer hardwareCommunications security
The invention relates to a method for resisting DDOS attacks based on a channel hopping mode. According to the method, communication parties negotiate about different communication channels temporarily, attackers cannot determine an attack target, and as long as one channel of the multiple channels can normally transmit data at any time, the communication parties can maintain a safe data channel; temporary keys are mapped to port numbers, the port numbers are generated in a random manner, the attackers are difficult to attack, a data packet is defined in the XML format, after the data packet is received, a flag bit is checked, duplicate removal is facilitated, packet loss is prevented, communication security and reliability are improved, and the DDOS attacks can be effectively resisted.
Owner:XIDIAN UNIV
Farm crop fungus resistant polypeptides and method for making same
InactiveCN101200727ADelay drug resistanceLow chance of developing drug resistanceFungicidesFermentationSide effectMonilinia laxa
The present invention discloses a novel anti-crop-epiphyte polypeptide and a preparation method thereof. A recombined anti-crop-epiphyte polypeptide is formed by linking gene which codes white candida pheromone and the gene which codes colicin. Compared with the prior anti-crop-epiphyte medicine, the novel anti-crop-epiphyte polypeptide of the present invention has the advantages that the novel anti-crop-epiphyte polypeptide directly forms ionic passage at epiphytic cell membrane to kill the epiphyte, so the killing efficiency is thousands times stronger than the prior anti-crop-epiphyte medicine; the epiphyte can hardly amend the geometrical damage at the cell membrane caused by the polypeptide by the mutation-expression form, so the polypeptide can not induce the epiphyte producing the traditional drug resistance; the polypeptide is a biological preparation and has target killing towards the epiphyte, so the novel anti-crop-epiphyte polypeptide does not have the toxic and side effects of the prior anti-crop-epiphyte medicine.
Owner:畿晋庆堂国际生物技术有限公司
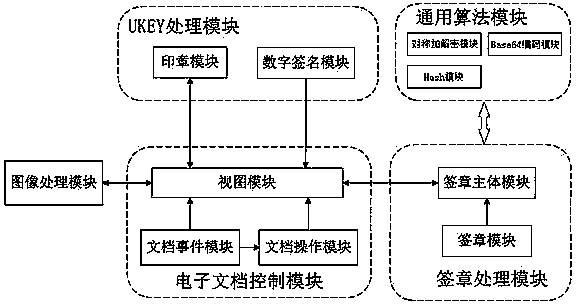
Electronic signature method based on electronic document image object
ActiveCN110532808AImprove integrityIncrease authenticityDigital data protectionDigital data authenticationElectronic documentImaging processing
The invention discloses an electronic signature method based on an electronic document image object, a signature procedure and signature verification process. The invention comprise a UKEY processingmodule, an image processing module, a signature processing module, a universal algorithm module and an electronic document control module, and a view module is connected with the image processing module, the signature main body module, the seal module and the digital signature module; and the signature processing module is in signal connection with a general algorithm module. The electronic signature is intercommunicated with a mobile terminal at a PC personal computer end to verify the integrity and authenticity of documents. A seal is stored in an electronic document in a simple image objectmode, and a computer cannot be attacked. The invention can be suitable for electronic document office software, and is beneficial to improving the compatibility, stability and maintainability of software products.
Owner:江西金格科技有限公司
Control system for intelligent prepayment teletransmission water meter
InactiveCN103035071AConvenient fee managementEasy to manageApparatus for hiring articlesControl systemEconomic benefits
The invention discloses a control system for an intelligent prepayment teletransmission water meter, which relates to the technical field of water supply systems. The control system comprises a prepayment water meter, a collector, a concentrator and a server, wherein the output end of the prepayment water meter is in one-way connection with the input end of the collector; the collector and the concentrator are in double-way connection by a wireless network; and the concentrator and the server are in double-way connection. The control system provided by the invention has the benefits that intelligent control over the water meter is truly realized by a water supply company through the system, various worries of the water supply company about the intelligent water meter are solved, and the purposes of truely intelligent water supply and water resource saving are achieved. A teletranmission function is increased on the basis of the existing intelligent prepayment water meter so that the difficult charging and messy water management problems of the water supply company are thoroughly solved. On the basis of the realization of the intelligent prepayment control, the system can also avoid stealing and leakage, timely discover failed water meters and ensure the economic benefit of the water supply company.
Owner:泊头市普惠仪表有限公司
An environment-friendly organic dry film stripping liquid
InactiveCN109116689AFall off completelyWon't attackPrinted circuit liquid treatmentPhotosensitive material processingFine lineOrganic base
The invention discloses an environment-friendly organic dry film stripping liquid, which comprises the following raw materials in parts by volume: 5-30 parts of organic base, 5-20 parts of an organicsolvent, 5-15 parts of an inhibitor, 0.1-5 parts of a corrosion inhibitor and 30-85 parts of deionized water. The circuit board of the invention is used for treating fine lines: 1. the dry film fallsoff completely, and there is no residual ''pinching film'' phenomenon; 2. the invention doe not attack a tin plating layer; 3. the dry film is broken into small diaphragms so as not to cause blockageto a pipeline; and 4. toxicity is low and wastewater is relatively easy to treat.
Owner:珠海特普力高精细化工有限公司
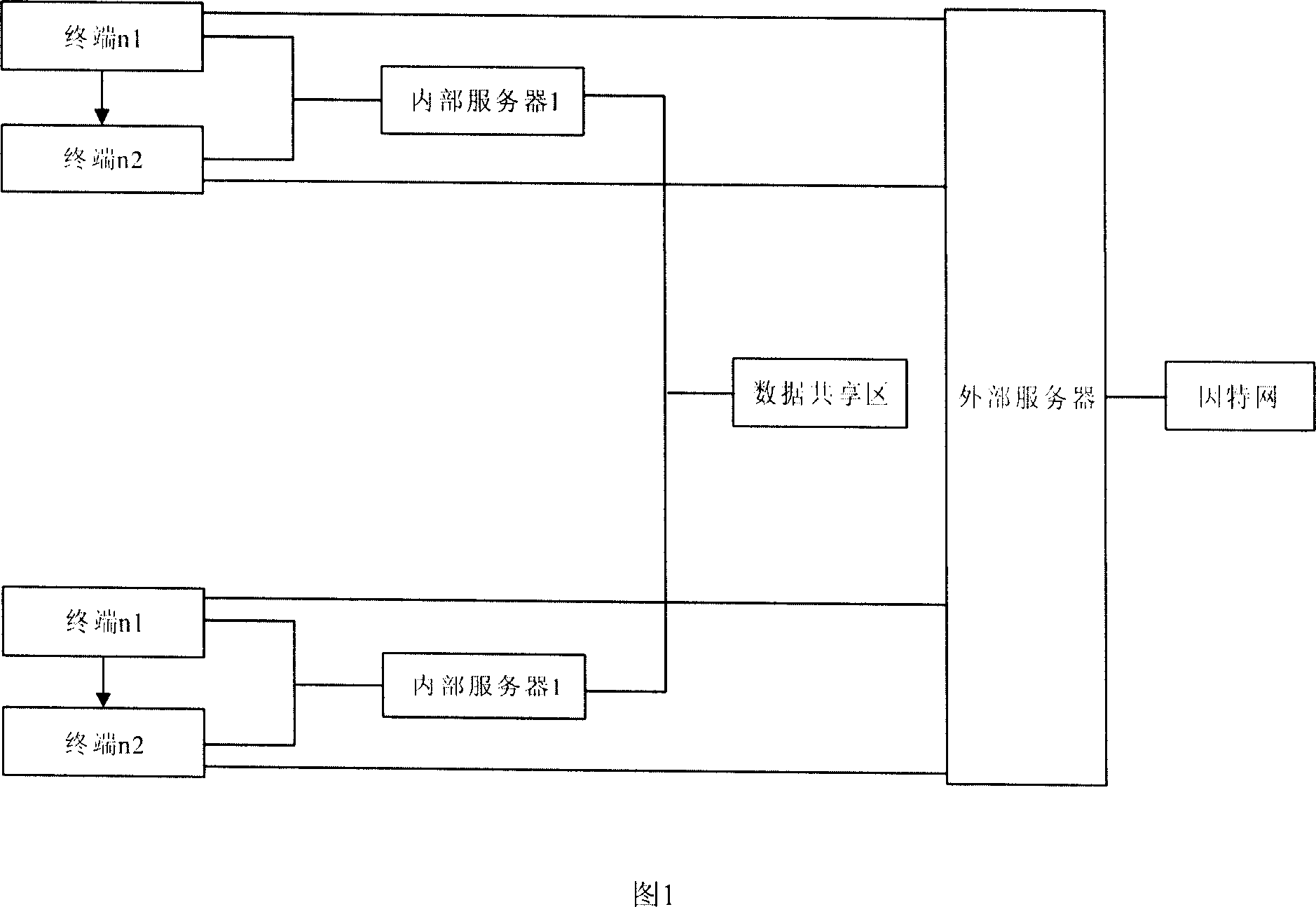
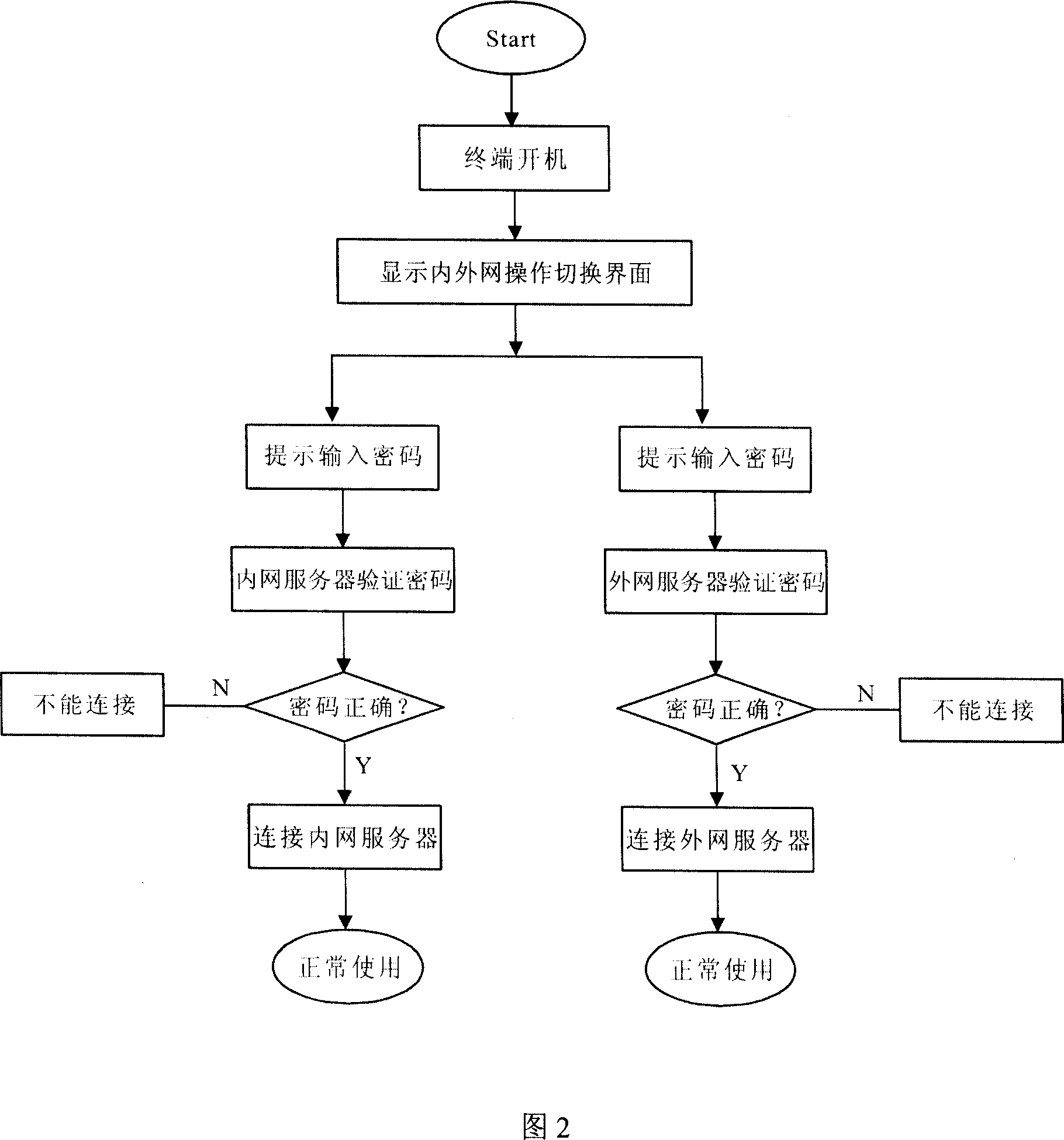
Intelligent terminal system and its operating method
The invention relates to an intelligent terminal system and relative operation, wherein said system comprises server, terminal connected to server via data communication; the server comprises internal data manage server and external manage server; each terminal comprise host without memory device, display, and input device; the host has two network ports selectively to connect internal data manage server and external manage server; the host is embedded with start module. The invention has two servers while only one can be connected to network at one time, and the terminal has no data memory. Therefore, operator can only network in network, but not span network. The data of internal network will not be transmitted outside; and the internal network will not be attacked via external virus.
Owner:YITUO SCI & TECH CO LTD SHENZHEN
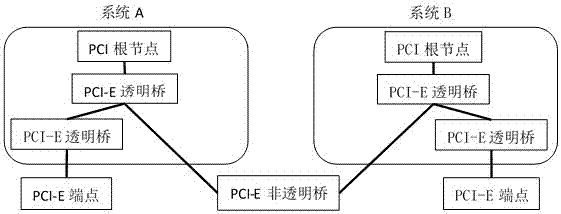
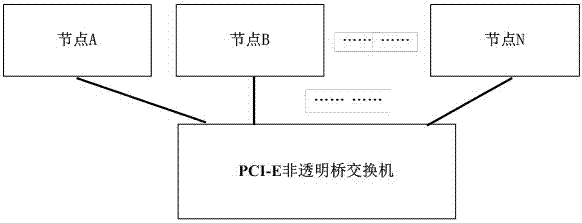
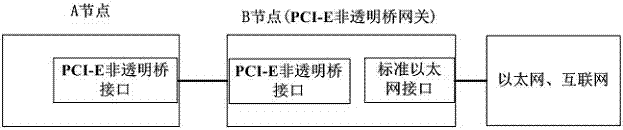
Gateway structure for communicating heterogeneous interconnection media and configuration method
InactiveCN107360088AEasy to useEnsure data securityNetwork connectionsHigh level techniquesData securityCluster Node
The invention relates to a gateway structure for communicating heterogeneous interconnection media and a configuration method. The Gateway structure for communicating heterogeneous interconnection media comprises at least one PCI-E (Peripheral Component Interconnect Express) cluster node and a PCI-E non-transparent bridge gateway; the PCI-E non-transparent bridge gateway includes a standard Ethernet interface and a PCI-E network interface; the PCI-E cluster nodes are connected with the PCI-E non-transparent bridge gateway through the PCI-E network interface; and the PCI-E non-transparent bridge gateway is connected with the Ethernet and / or Internet through the standard Ethernet interface. With the gateway structure for communicating heterogeneous interconnection media and the configuration method of the invention adopted, communication between a PCI-E network cluster and the Ethernet or the Internet can be realized; any node in the PCI-E network cluster can freely access the resources of the Internet, while the Internet does not see the PCI-E network cluster node, and therefore, the use of the PCI-E network cluster can be more convenient, the data security of the PCI-E network cluster can be ensured and will not be attacked by external Internets.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
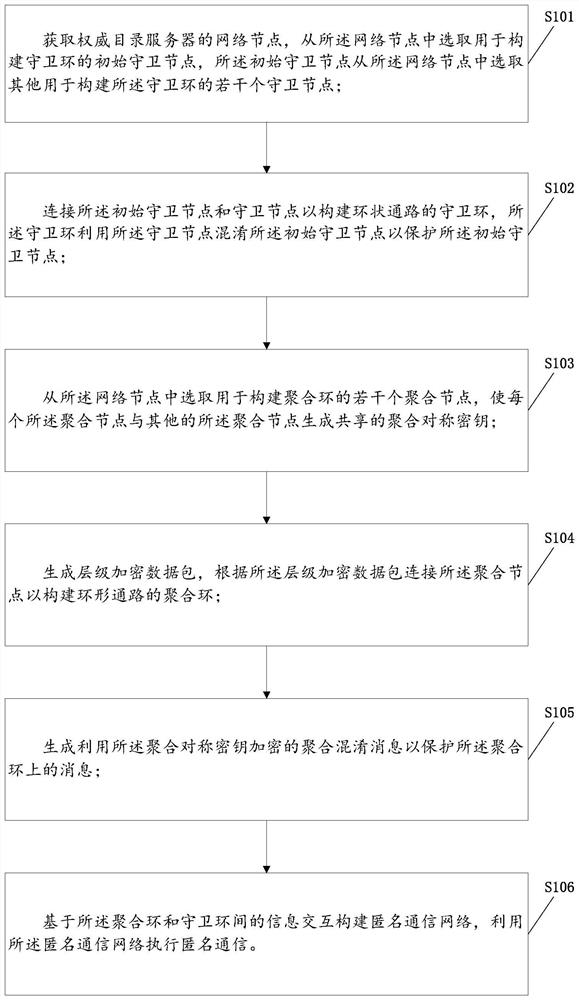
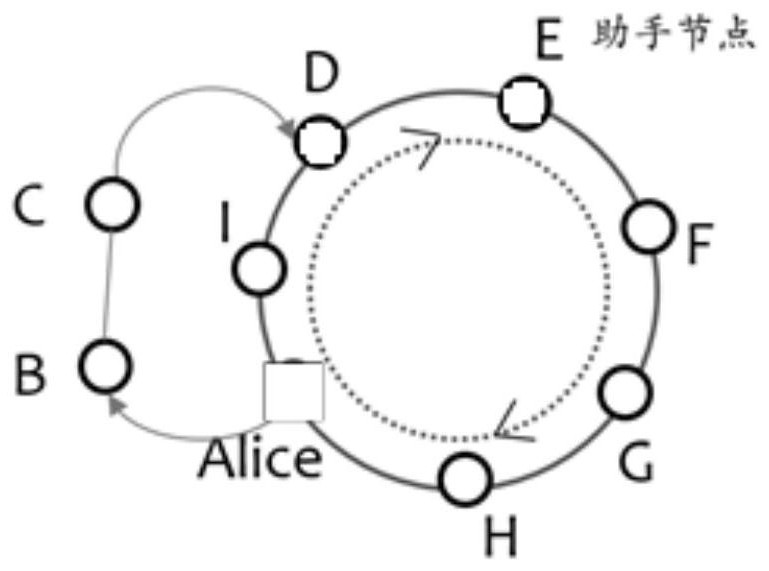
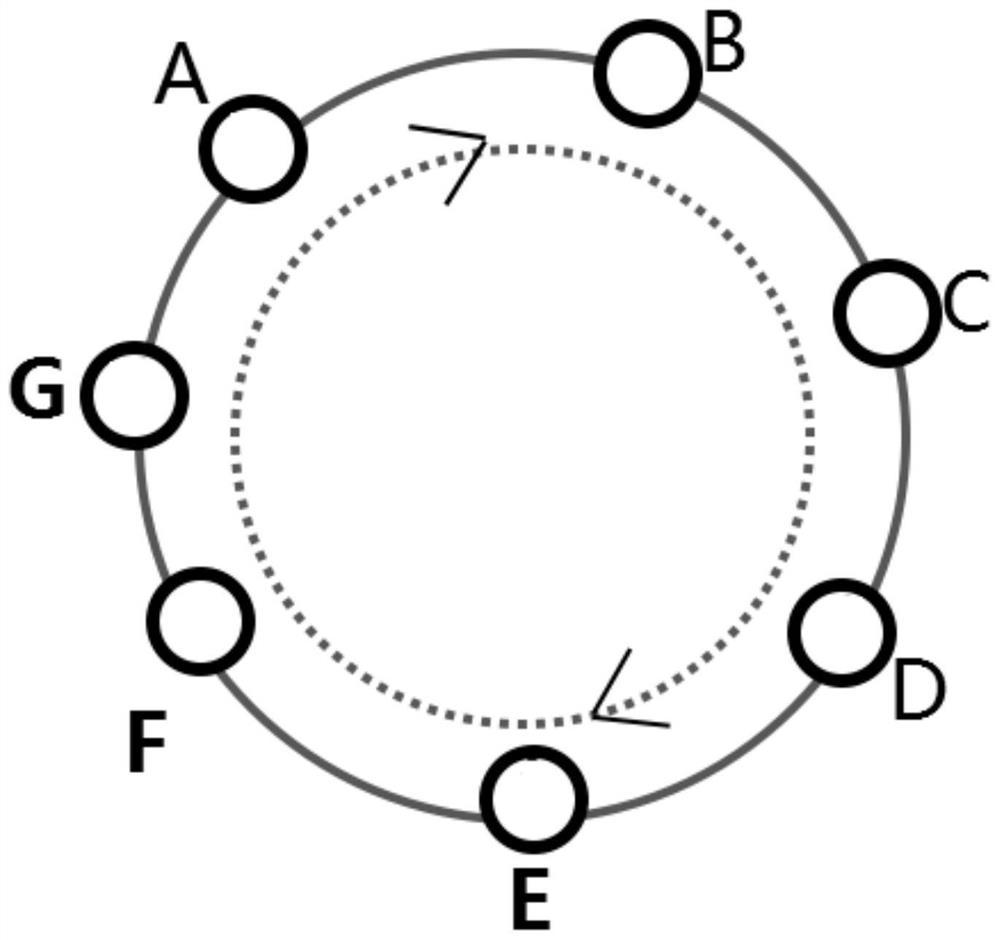
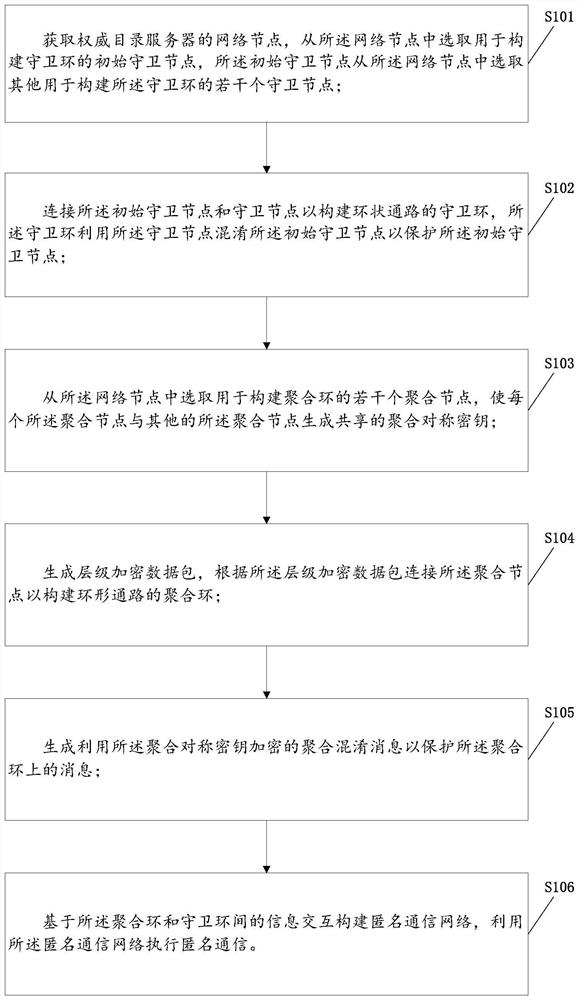
Heterogeneous layered anonymous communication network construction method and device
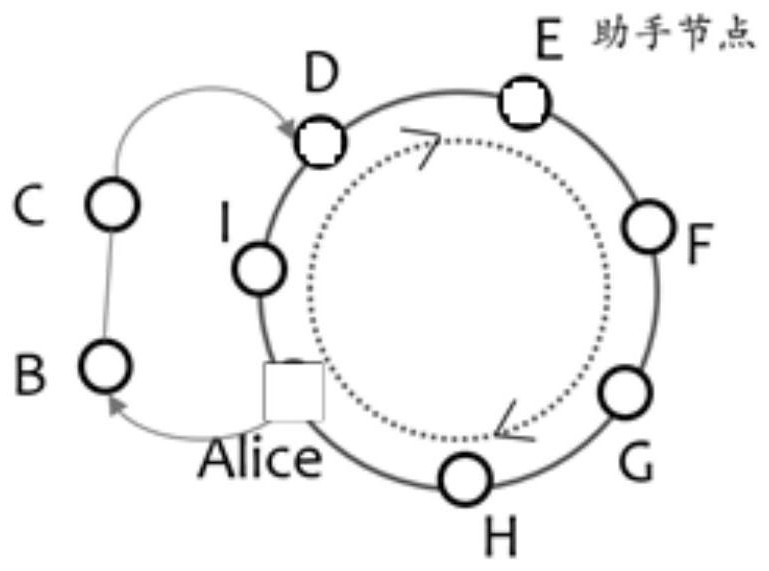
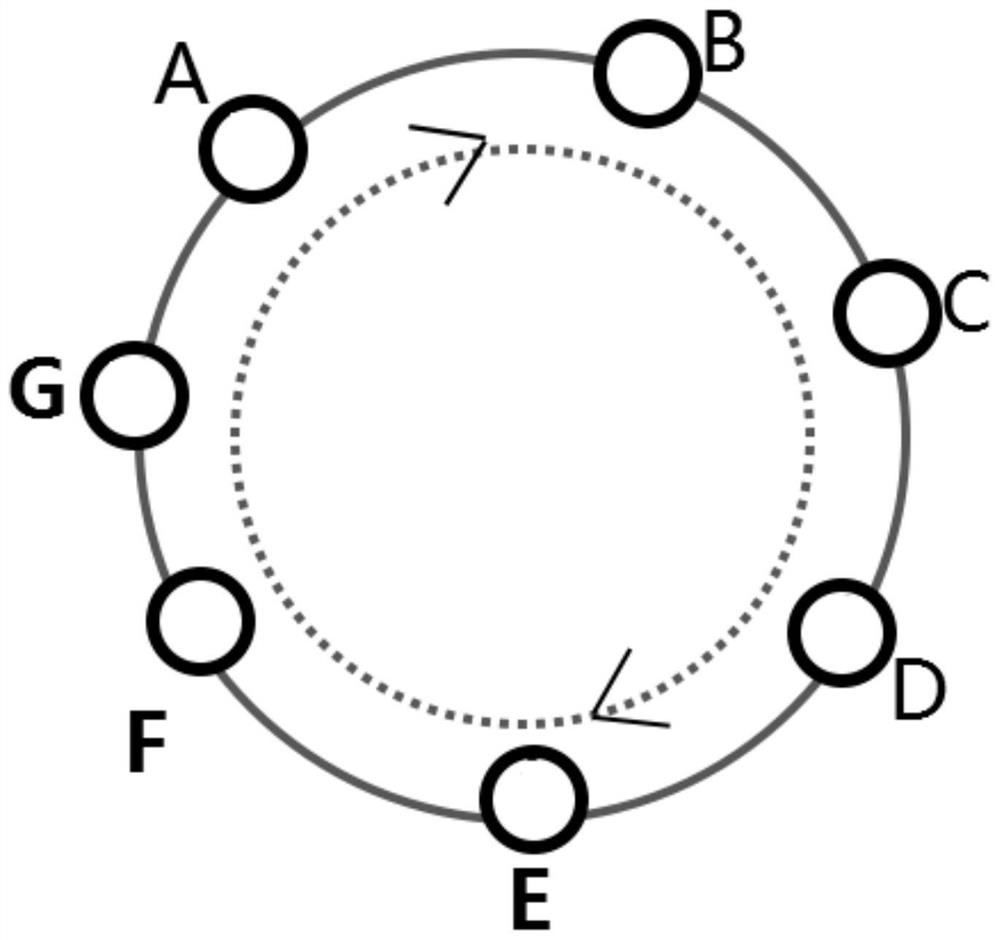
One or more embodiments of the invention provide a heterogeneous layered anonymous communication network construction method and device. The heterogeneous layered anonymous communication network construction method comprises the following steps of: acquiring an initial guard node and a plurality of guard nodes; constructing a guarding ring of an annular path; selecting a plurality of aggregation nodes of an aggregation ring to be constructed, and enabling each aggregation node and other aggregation nodes to generate a shared aggregation symmetric key; generating a hierarchical encryption datapacket, and connecting the aggregation nodes according to the hierarchical encryption data packet to construct an aggregation ring of an annular path; generating an aggregation confusion message encrypted by using the aggregated symmetric key to protect the message on the aggregation ring; and constructing an anonymous communication network based on information interaction between the aggregationring and the guarding ring, and executing anonymous communication by utilizing the anonymous communication network. According to the heterogeneous layered anonymous communication network constructionmethod and the device, properties of different nodes can be exerted, the guarding ring is used for protecting a sender and a receiver of the message, the aggregation ring is used for preventing message leakage, and the anonymity of the whole network is improved.
Owner:BEIJING UNIV OF POSTS & TELECOMM
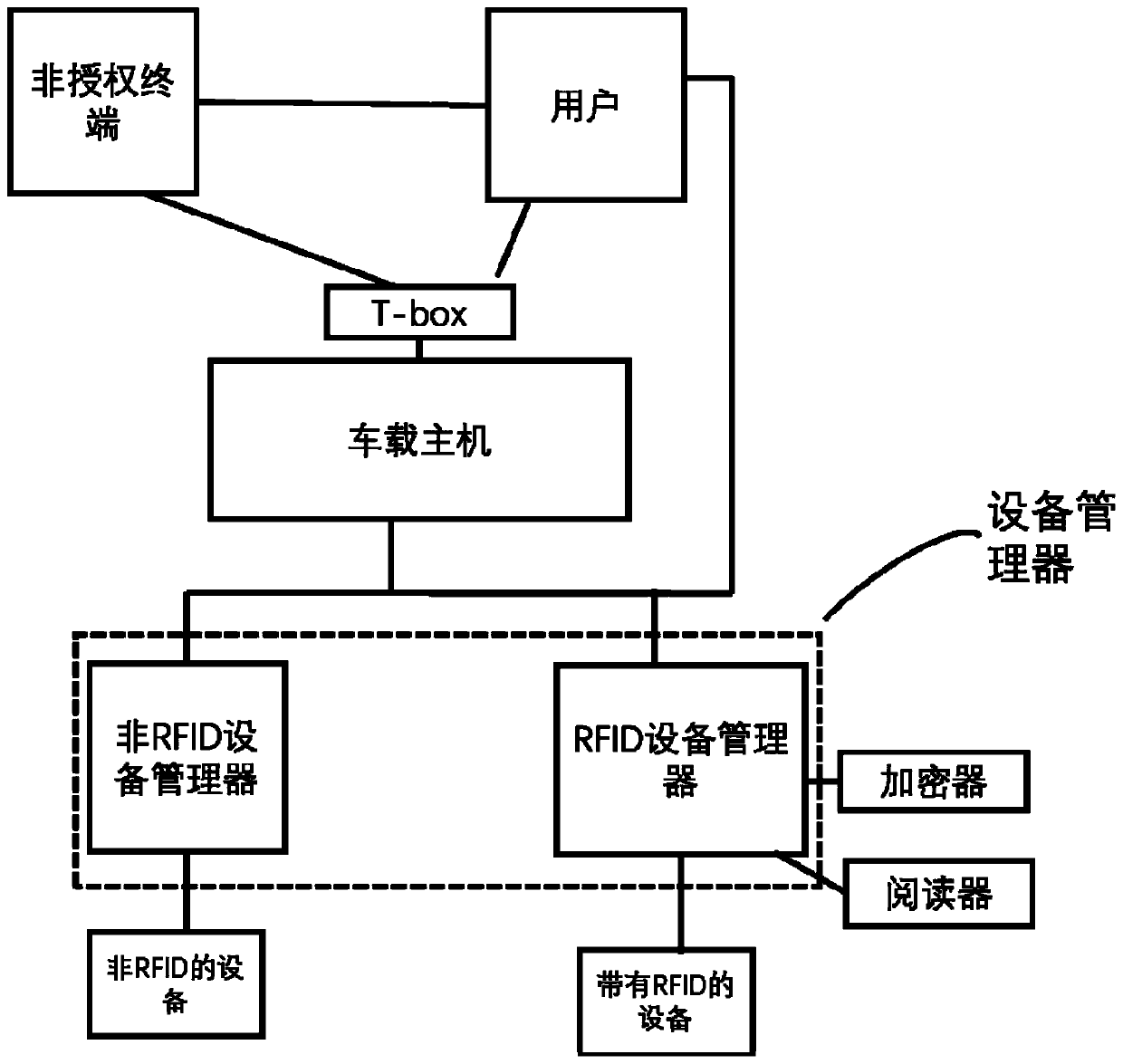
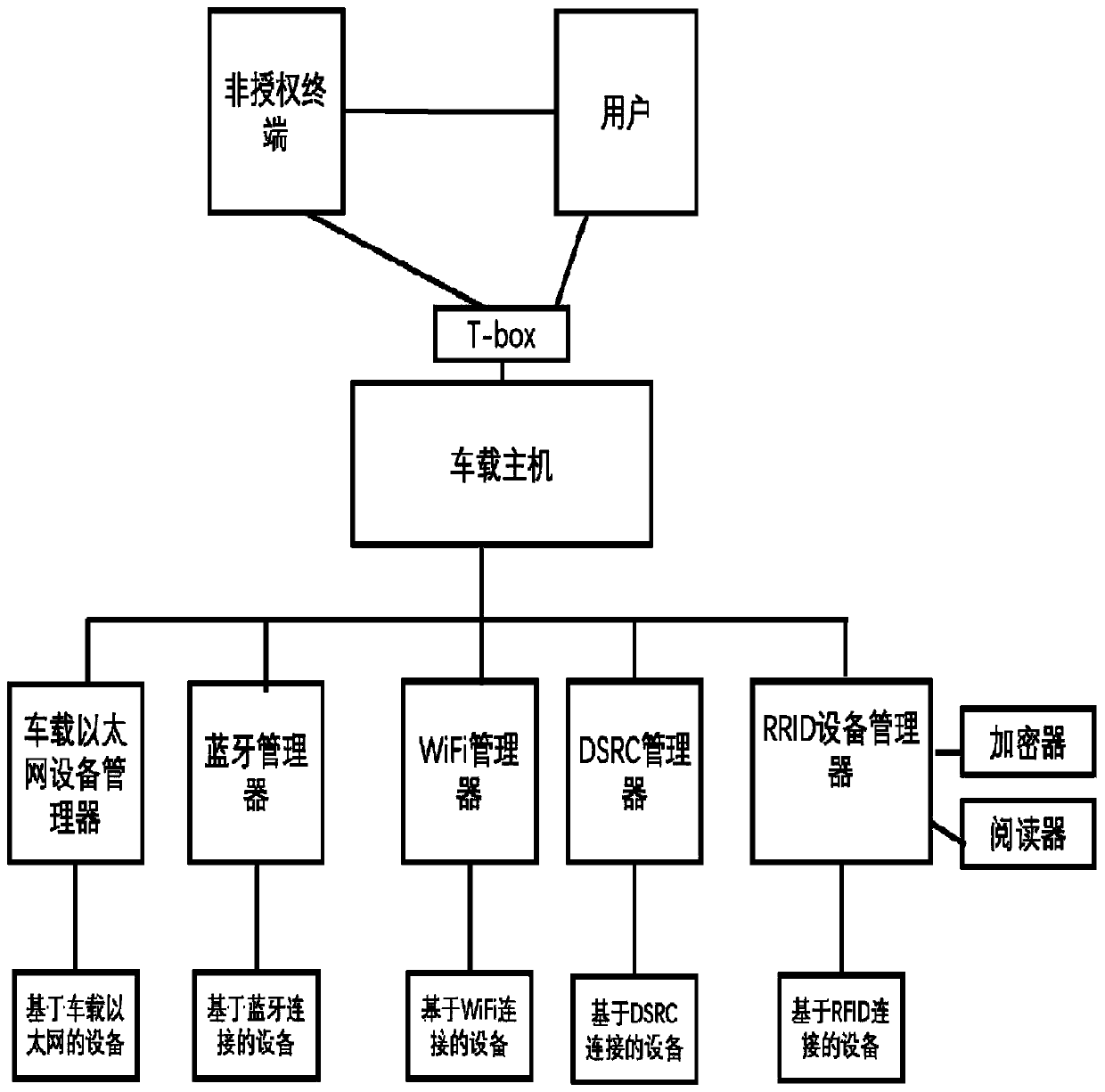
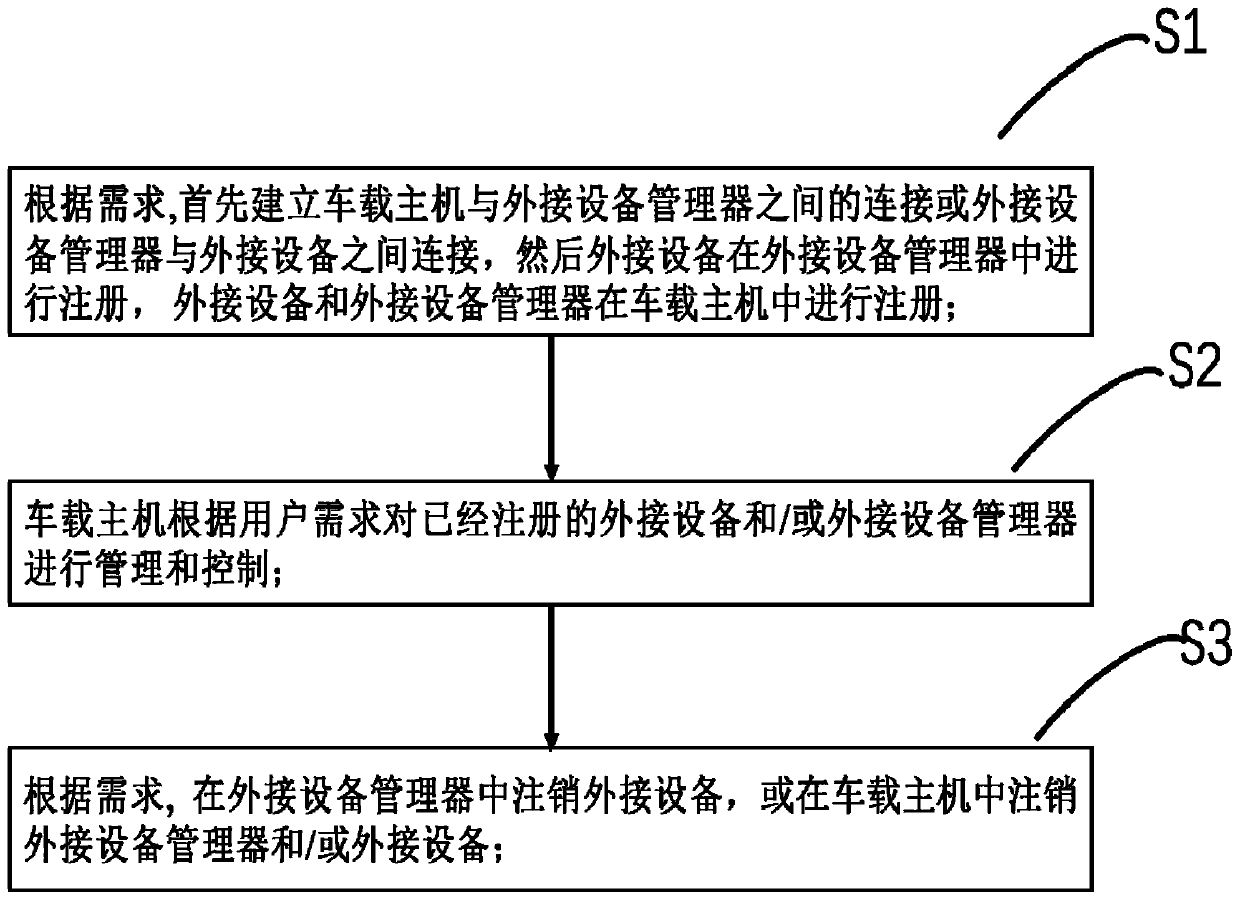
Vehicle-mounted management system and method applied to addable equipment
ActiveCN110708192ARealize managementFlexible managementCo-operative working arrangementsTotal factory controlIn vehicleAutomotive engineering
The invention discloses a vehicle-mounted management method and a vehicle-mounted management system applied to addible equipment. The vehicle-mounted management method comprises the following steps: firstly, establishing connection between a vehicle-mounted host and an external equipment manager or connection between the external equipment manager and external equipment according to requirements,then registering the external equipment in the external equipment manager, and registering the external equipment and the external equipment manager in the vehicle-mounted host; and the vehicle-mounted host manages and controls the registered external equipment and / or the external equipment manager according to user requirements. The vehicle-mounted management system specifically comprises a vehicle-mounted host and an external equipment manager, wherein the external equipment manager comprises an RFID-based equipment manager and a non-RFID equipment manager. By adopting the equipment managerprovided with various different communication interfaces, equipment and parts such as sensors and controllers for vehicles can be quickly and conveniently added into an automobile system, so that theexternal equipment can be managed. The equipment manager can be compatible with vehicle-mounted host platforms of different manufacturers.
Owner:SHANGHAI HEQIAN ELECTRONICS TECH CO LTD
Processing method for medicinal raw material of artificially bred cobra
PendingCN112138027AAdvantages of processing methodNot easy to attackUnknown materialsBiotechnologyVenom gland
The invention discloses a processing method for a medicinal raw material of an artificially bred cobra. The processing method comprises the following steps of (1) collecting the cold-chain transportedcobra by using a thickened nylon mesh bag; (2) performing weighing in a factory, and randomly sampling and measuring medicine residues; (3) putting the cobra into a retention chamber for low-temperature retention until the cobra enters a hibernation state; (4) pouring the cobra into a normal-temperature pool, and performing immersion cleaning for 20-30 seconds; (5) putting the cobra into a cold water pool, and performing rinsing for 1-2 minutes; (6) fixing the head of the cobra without extruding the poison gland, fixing the tail of the cobra to prevent curling and struggling, obliquely putting a funnel into the mouth to receive venom, and performing electrode discharge to promote venoming; (7) after venoming is finished, cutting the head to collect the head of the cobra, and carrying outbloodletting to collect blood; (8) feeding the cobra body into a hot water pool for soaking, removing scales, and spray-washing the surface of the cobra body; (9) cutting open the abdomen of the cobrabody to strip the internal organs, and cleaning the cobra body; and (10) centrifugally spin-drying water on the surface of the cobra body, and performing disinfection, weighing and packaging in vacuum to obtain the finished fresh cobra body. The method can be suitable for processing cobras into medicinal raw materials on a large scale, and can reduce or avoid accidents that people are bitten by the cobras.
Owner:黄恒
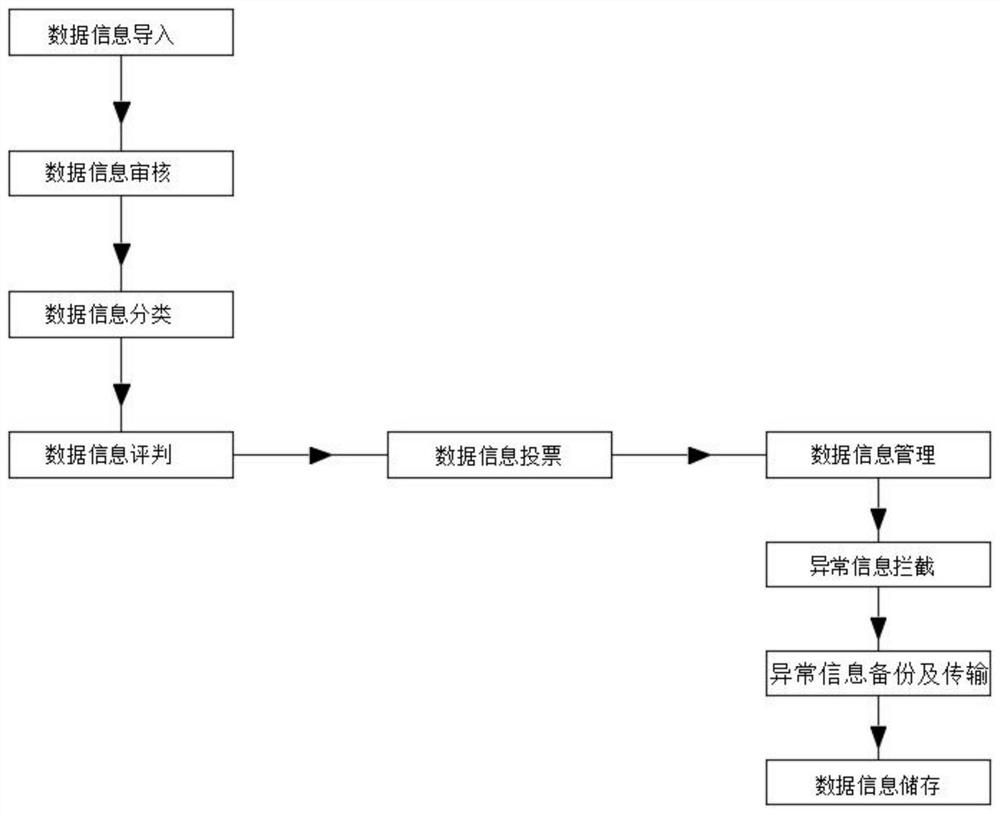
Data processing method of block chain
PendingCN114003968ATimely classificationGuarantee authenticityDigital data protectionData informationAttack
The invention relates to the technical field of block chains, and discloses a data processing method of a block chain. The method comprises the following steps: step 1, importing data information: transmitting or importing the data information into a system; step 2, checking the data information: checking the transmitted information, checking the information according to the information entering path and the authenticity of the information, and directly intercepting the data information, subjected to risk control and shielded under the condition that the access path or authenticity of the data information is not confirmed; and step 3, classifying data information: classifying the types of the data; and respectively dividing into text documents. According to the system, the data can be classified in time, and meanwhile, the data can be audited; the authenticity of internal information can be ensured; illegal information intrusion is avoided; the information security can be guaranteed; and attack and tampering are avoided, so that the use safety and legality of the information are guaranteed.
Owner:北京八分量信息科技有限公司 +1
Farm crop fungus resistant polypeptides and method for making same
InactiveCN101200727BDelay drug resistanceLow chance of developing drug resistanceFungicidesFermentationSide effectMonilinia laxa
Owner:畿晋庆堂国际生物技术有限公司
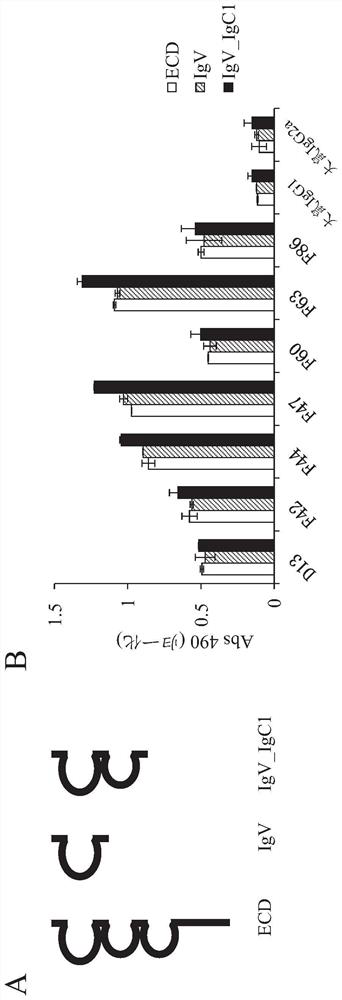
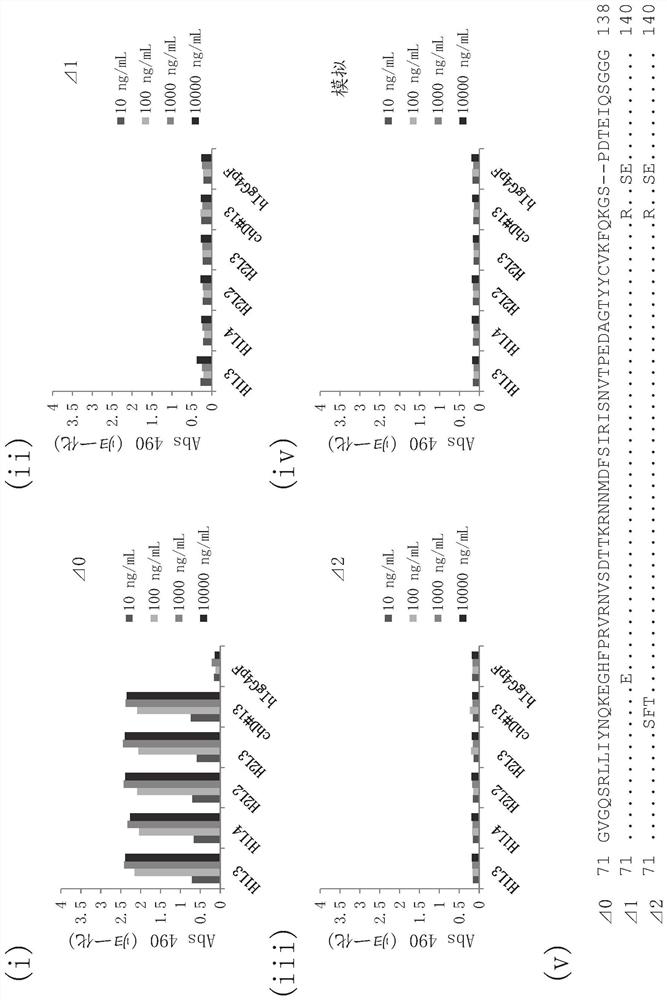
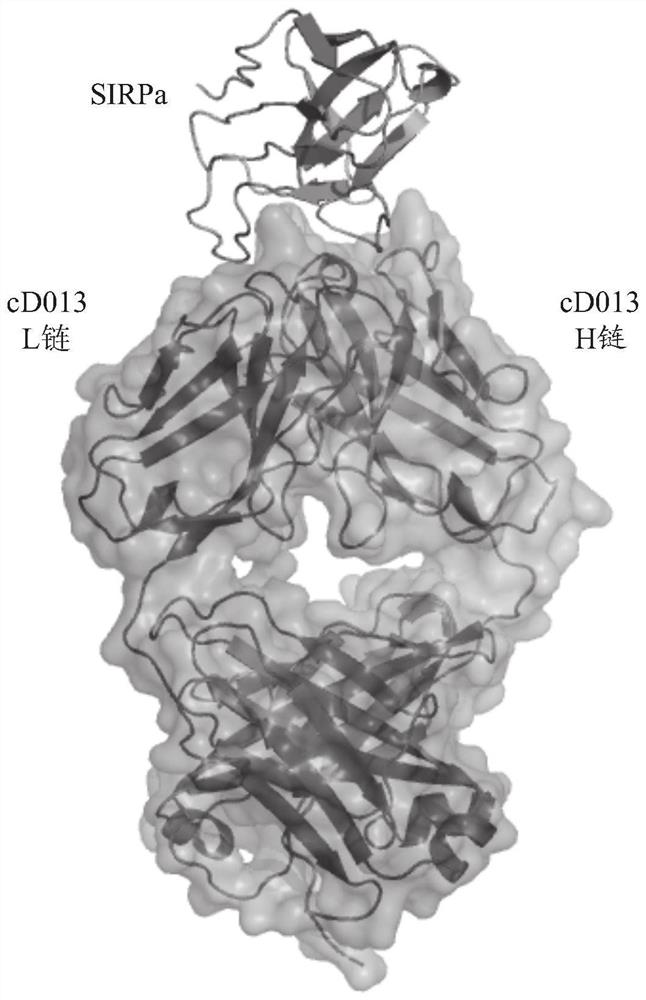
ANTI-SIRPalpha ANTIBODY
ActiveCN112673023AWon't attackImprove anti-tumor effectFungiBacteriaAntiendomysial antibodiesBULK ACTIVE INGREDIENT
The present invention addresses the problem of providing: an anti-SIRPalpha antibody which can be used as a tumor agent; and an anti-tumor agent containing the antibody as an active ingredient. The present invention is an antibody capable of binding specifically to human SIRPalpha to inhibit the binding between human SIRPalpha and CD47, the antibody containing (a) a light-chain CDRL1 comprising the amino acid sequence represented by SEQ ID NO: 1, (b) a light-chain CDRL2 comprising the amino acid sequence represented by SEQ ID NO: 2, (c) a light-chain CDRL3 comprising the amino acid sequence represented by SEQ ID NO: 3, (d) a heavy-chain CDRH1 comprising the amino acid sequence represented by SEQ ID NO: 4, (e) a heavy-chain CDRH2 comprising the amino acid sequence represented by SEQ ID NO: 5 and (f) a heavy-chain CDRH3 comprising the amino acid sequence represented by SEQ ID NO: 6, wherein a heavy-chain constant region is a heavy-chain constant region of human IgG4, and an phenylalanine residue at position-234, a leucine residue at position-235 and a serine residue at position-228, as numbered according to the EU index as in Kabat et. al., are substituted by an alanine residue, an alanine residue and a proline residue, respectively.
Owner:KOBE UNIV +1
A heterogeneous layered anonymous communication network construction method and device
One or more embodiments in this application provide a method and device for constructing a heterogeneous and hierarchical anonymous communication network, including: obtaining the initial guard node and several guard nodes; constructing a guard ring of a ring path; selecting the aggregation to be constructed Several aggregation nodes of the ring, so that each aggregation node and other aggregation nodes generate a shared aggregation symmetric key; generate hierarchical encrypted data packets, connect the aggregation nodes according to the hierarchical encrypted data packets to build an aggregation ring of ring paths; generate aggregation rings using aggregation Aggregation and obfuscation messages encrypted with symmetric keys to protect messages on the aggregation ring; an anonymous communication network is constructed based on the information interaction between the aggregation ring and the guard ring, and the anonymous communication network is used to perform anonymous communication. This application can take advantage of the characteristics of different nodes, use the guard ring to protect the sender and receiver of the message, use the aggregation ring to prevent message leakage, and improve the anonymity of the overall network.
Owner:BEIJING UNIV OF POSTS & TELECOMM
A special gold-plated pad manufacturing method
ActiveCN108235598BThere will be no problem of damaging electro-gold graphicsWon't attackConductive pattern reinforcementPrinted element electric connection formationSurface patternCopper
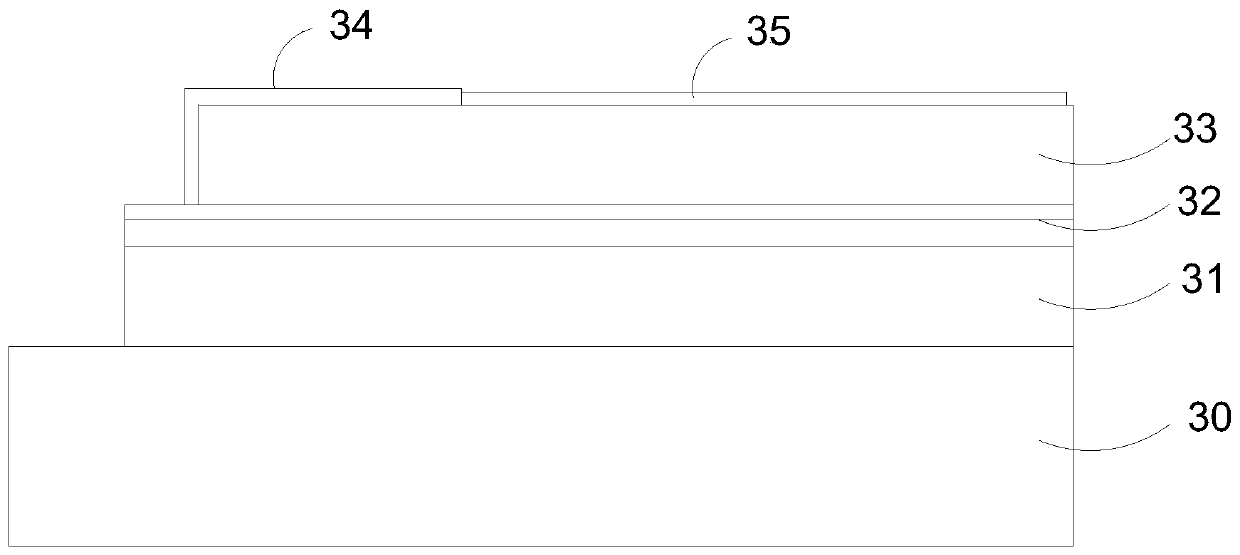
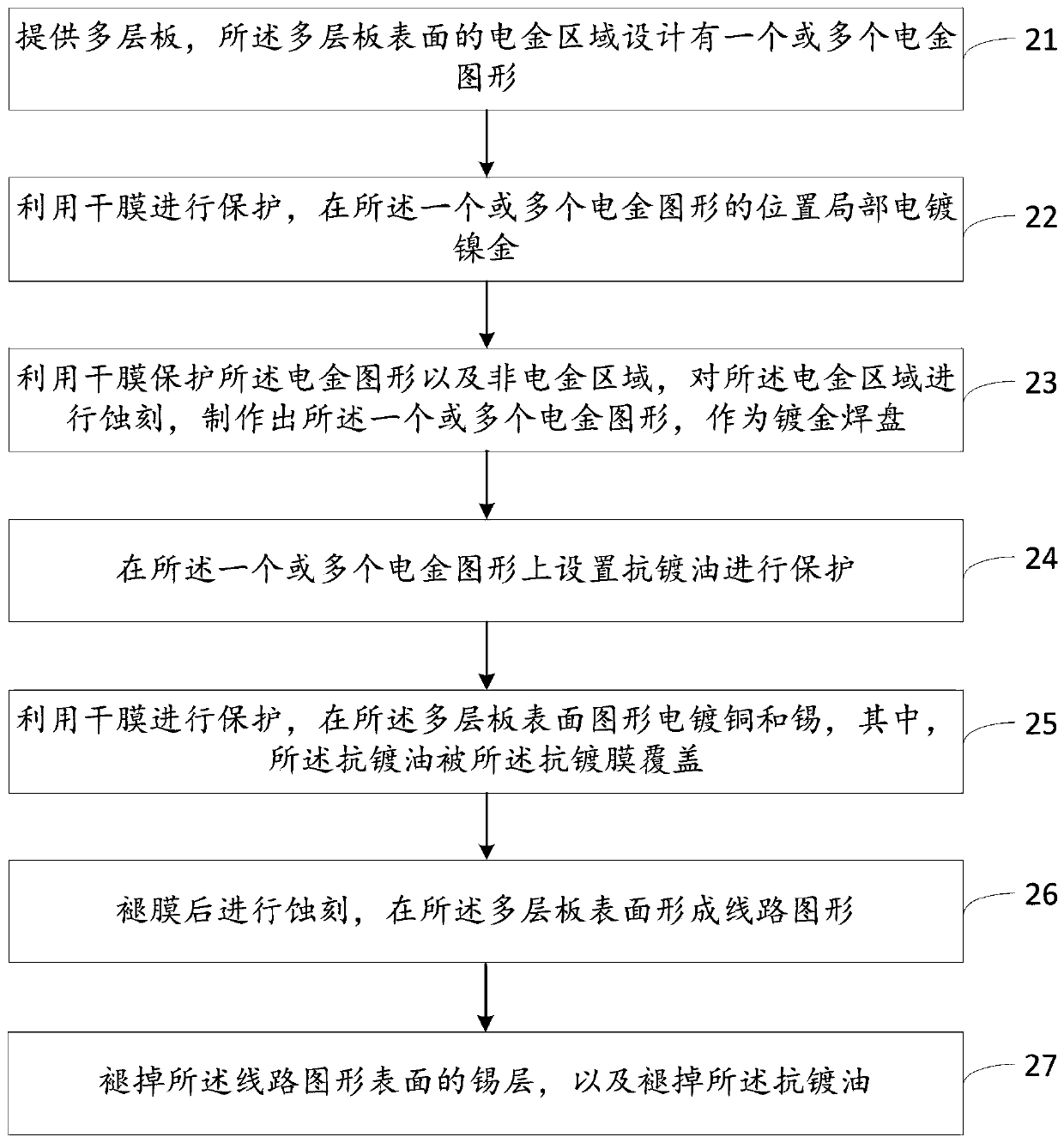
The invention discloses a special manufacturing method for a gold-plated bonding pad. The method comprises the following steps: supplying a multi-layer plate, wherein one or a plurality of gold plating patterns are designed in a gold plating area on the surface of the multi-layer plate; protecting by utilizing a dry film, and locally electroplating one or more gold plating patterns with nickel gold; protecting the one or more gold plating patterns and a non-gold-plating area by utilizing films; etching the gold plating area to obtain one or more gold plating patterns as the gold-plated bondingpad; arranging anti-plating oil on the one or more gold plating patterns for protection, wherein the anti-plating oil is covered with an anti-plating film; protecting by utilizing the dry film; electroplating the surface patterns of the multi-layer plate with copper and tin; etching after removing the films to form a circuit pattern on the surface of the multi-layer plate; removing a tin layer onthe surface of the circuit pattern; and removing the anti-plating oil. According to the method, the gold plating patterns are etched in advance and are protected by the anti-plating oil, so that problems in the prior art can be solved or reduced.
Owner:SHENNAN CIRCUITS
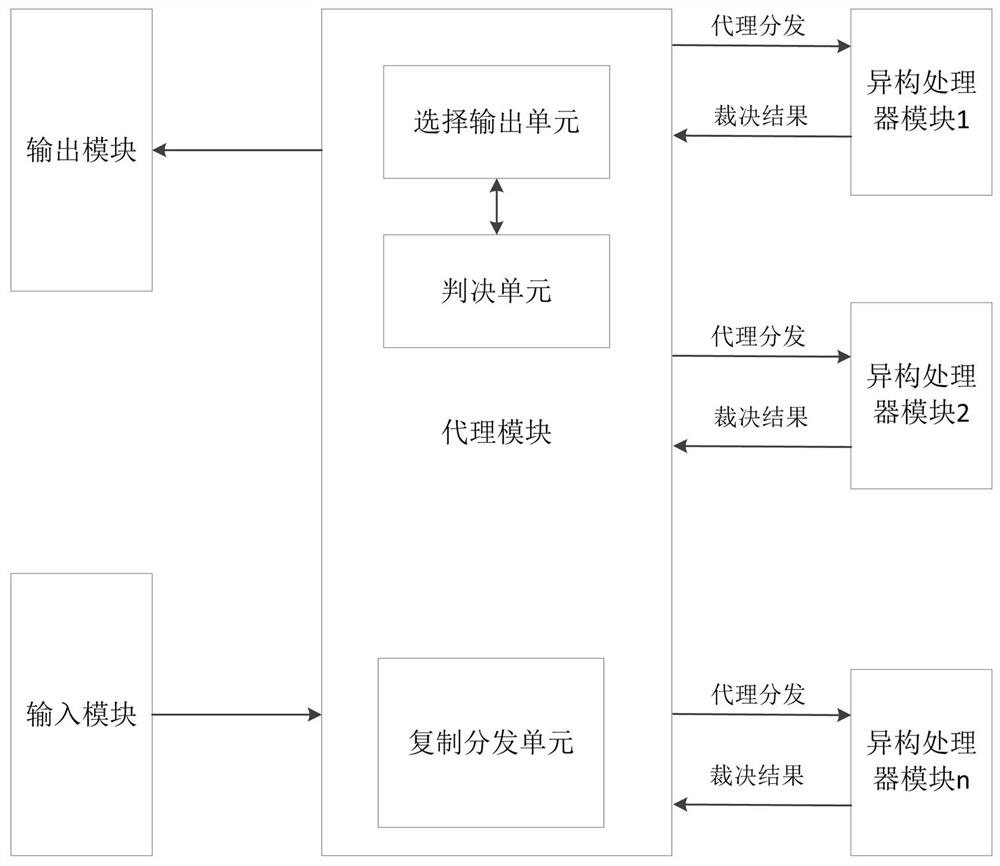
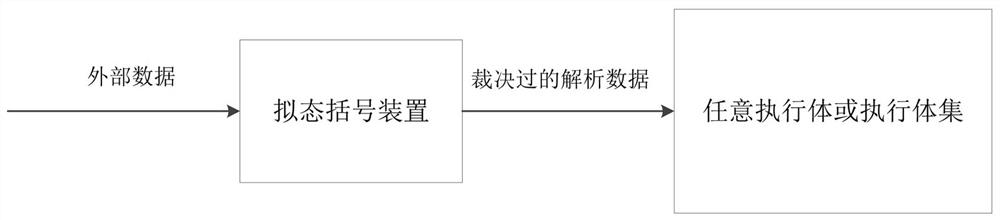
A mimetic defense device, mimetic defense method and mimetic defense architecture
ActiveCN111783079BHighlight substantiveSignificant progressPlatform integrity maintainanceExternal dataArbiter
The present invention provides a mimic defense device, a mimic defense method, and a mimic defense architecture, wherein the mimic defense device includes an input module, an output module, an agent module and a plurality of heterogeneous processor modules, and the agent module includes a copy distribution unit, a judgment unit and select output unit; copy distribution unit, receive external data sent by input module and copy and distribute to multiple heterogeneous processor modules; each heterogeneous processor module includes an arbiter and multiple heterogeneous virtual machines. The arbiter is used to process external data, and the arbiter is used to adjudicate the processing results of multiple heterogeneous virtual machines; select the output unit, and select a heterogeneous processor module according to the judgment result and the preset selection strategy. The result is output through the output module; the judgment unit is configured to judge the judgment results output by the multiple heterogeneous processor modules.
Owner:河南信大网御科技有限公司 +1
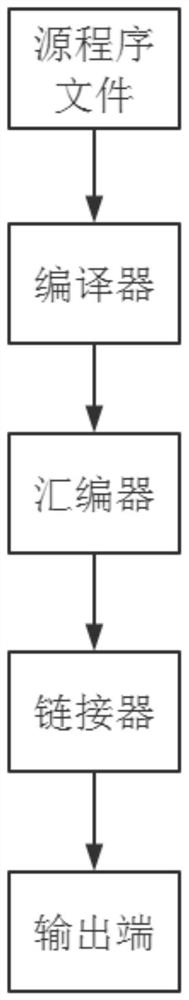
Device for detecting user interface for compiling software development kit and server
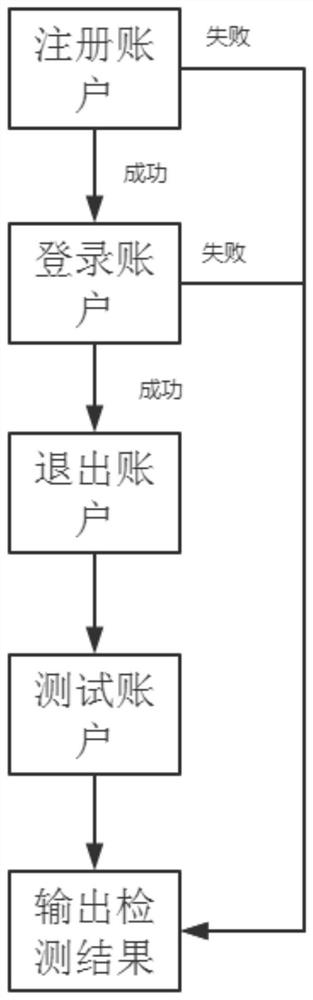
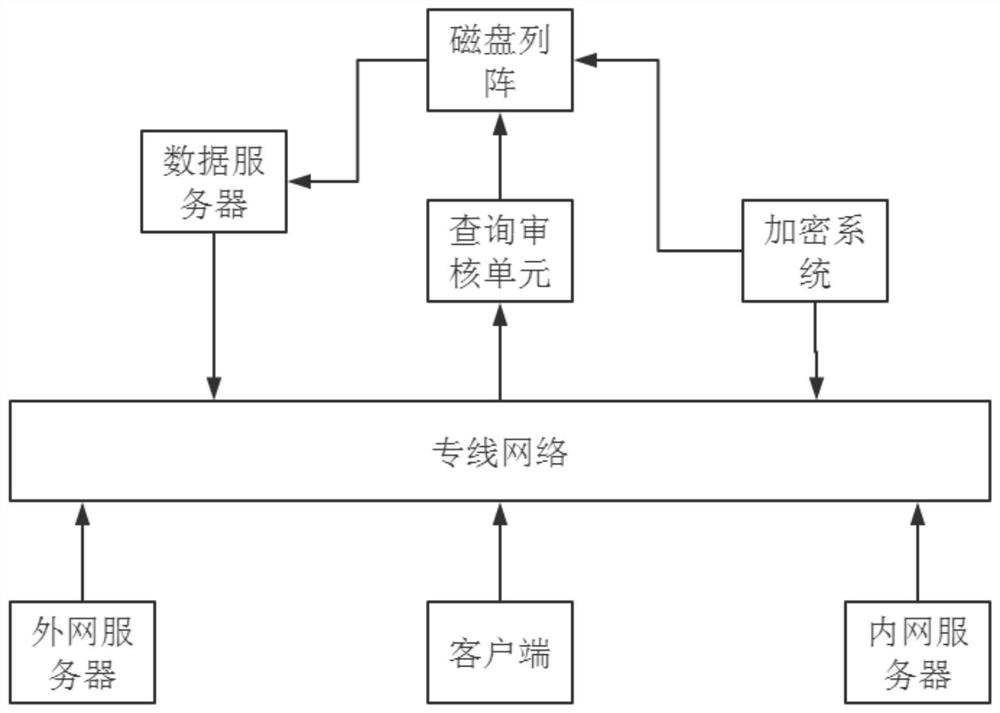
InactiveCN112765024AAvoid mistakesEasy to detectDigital data protectionSoftware testing/debuggingSoftware engineeringSoftware development
The invention discloses a device for detecting a user interface for compiling a software development kit and a server, and relates to the technical field of user interface detection. The problem that dynamic detection in user interface detection is complicated and changeable is solved. The device for detecting the user interface for compiling the software development kit comprises a source program file, a compiler, an assembler, a linker and an output end, and a server of the device for detecting the user interface of the compilation of the software development kit comprises a client, an extranet server, an intranet server, a private line network and an encryption system. The user interface in the server is detected through the source program file, the compiler, the assembler and the linker generation output end, on one hand, the compiler, the assembler and the linker translate an assembly language into an unexecutable machine language, detection of the user interface is facilitated, on the other hand, success rate of compiling increases. Program errors are avoided, and the stability and safety of the device are improved.
Owner:青岛懿雅新程传媒有限公司
Nickel removing liquid agent for electronickelling anti-corrosion layer, preparation method and chemical nickel removing process
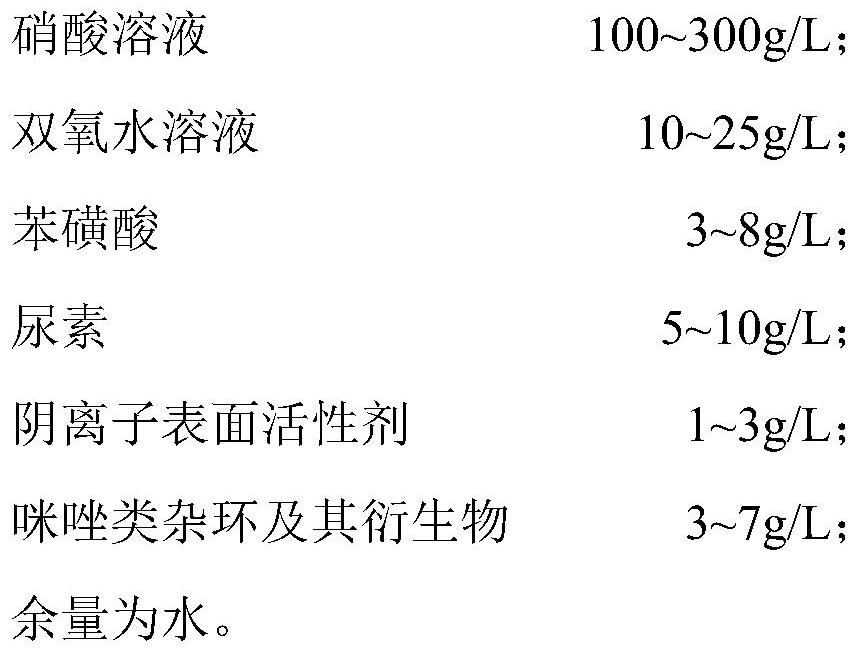
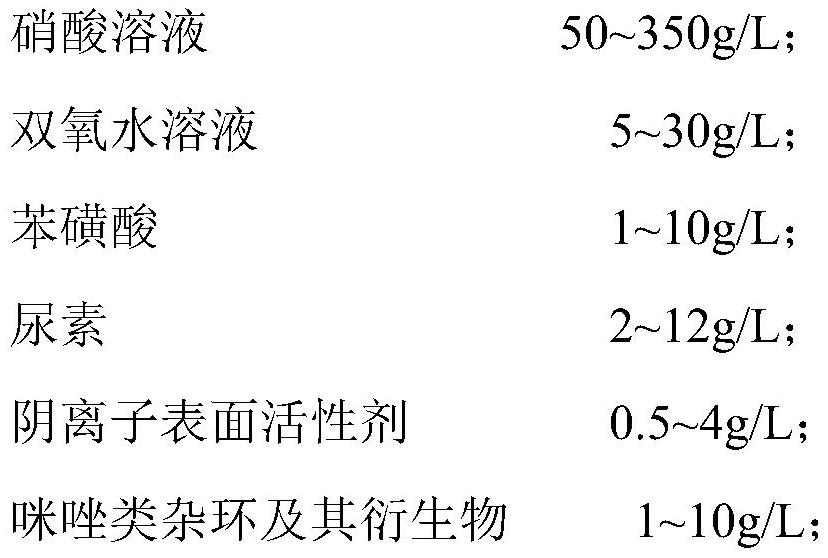
The invention relates to the technical field of a chemical nickel removing liquid agent, in particular to a nickel removing liquid agent for an electronickelling anti-corrosion layer, a preparation method and a chemical nickel removing process. The nickel removing liquid agent contains 50-350 g / L of a nitric acid solution, 5-30 g / L of a hydrogen peroxide solution, 1-10 g / L of benzenesulfonic acid, 2-12 g / L of urea, 0.5-4 g / L of an anionic surfactant, 1-10 g / L of an imidazole heterocyclic ring and derivative thereof, and the balance of water. The problems that in the prior art, a traditional chemical nickel removing liquid agent system is high in use temperature, low in speed and complex in removing technology are solved. When the nickel removing liquid agent is used for treating a circuit board containing the electronickelling anti-corrosion layer, an electronickelling layer on the surface of copper metal can be rapidly and effectively removed by controlling the temperature of the nickel removing liquid agent within the range of 20-40 DEG C, a bright and imprint-free metal copper circuit layer is exposed, and the requirements of a subsequent automatic optical inspection (AOI) procedure for the appearance and brightness of a copper surface are met.
Owner:江苏悦锌达新材料有限公司
Antineoplastic dibasic polypeptide and application and preparation method thereof
ActiveCN101139613BAchieve the purpose of killing tumor cellsSpecific targetingPeptide/protein ingredientsHybrid peptidesDouble strandBacilli
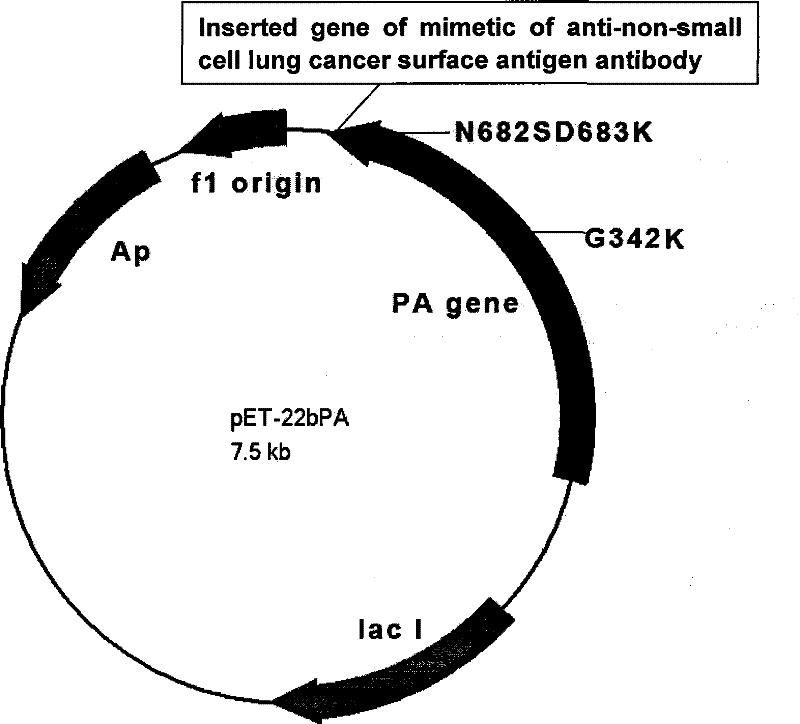
The invention provides a gene, recombinant plasmid and polypeptide for an anti-tumor binary polypeptide. The gene of the recombinant anti-tumor binary polypeptide is obtained by connecting in an operable way the gene of a coding antibody simulator with a recombinant bacillus anthraci protein antigen gene. The recombinant plasmid of the invention is formed by inserting the gene of the coding antibody simulator by double-chain oligomeric nucleotide directed mutagenesis method into the recombinant bacillus anthraci protein antigen gene. The obtained recombinant plasmid is infected into engineering bacillus coli BL-21 to get engineering bacillus coli cell of anti-tumor binary polypeptide; the anti-tumor binary polypeptide can be obtained by expanding the bacillus coli, settling in centrifugalway the bacillus coli body, crushing in altrasonic way, settling and crushing bacillus coli body by hi-speed centrifuging and treating the upper clean solution. The anti-tumor binary polypeptide is of special targeting characteristic, higher efficiency in killing special physical tumor than prior anti-tumor medicine, and will not attack normal cells, and has much lower toxicity and poor-reactionthan prior anti-tumor medicine.
Owner:姜荣锡
A kind of cell transplantation synergistic protection device and preparation method thereof
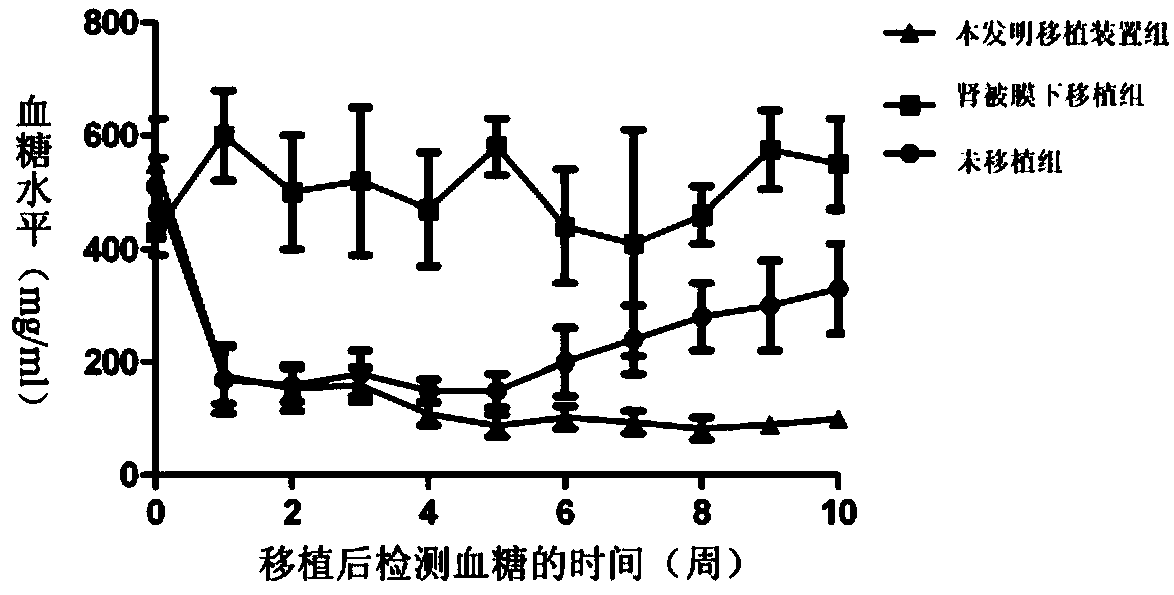
The invention belongs to the technical field of medical transplantation devices and preparation of the medical transplantation devices, and in particular relates to a cell transplantation synergistic device and a preparation method thereof. The cell transplantation synergistic protective device comprises transplant blocks made of highly biocompatible GMP-grade materials, namely poly(DL-lactide-caprolactone), and cell storage pipelines, as well as angiogenesis related factors. The cell transplantation device can carry any treatment human cells to be transplanted to subcutaneous, muscle and abdominal parts, renal cysts and specific treatment parts. In addition, the transplantation device can promote the formation of blood vessels around storage tubes of grafts, so that the grafts can play a role in transplantation parts, and secreted therapeutic substances further can reach the whole body through peripheral blood vessels to play related curative effects. The transplantation device can increase or remove the grafts in the process of transplantation properly; therefore, the dose of the grafts can be easily, fast, safely and effectively regulated. The cell transplantation synergistic protective device disclosed by the invention is simple in structure, easy to manufacture and capable of realizing large-scale production, and plays a role of treating related diseases.
Owner:HUNAN XENO LIFE SCI
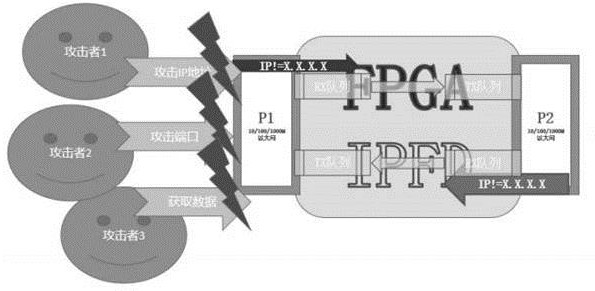
Method for improving security of server by adopting IP strategy packet
The invention discloses a method for improving the security of a server by adopting an IP strategy packet, which comprises the following steps of: S010, allocating a number to a client, and respectively registering an ID (Identity) and a secret key in the client and a trusted authorization system; S020, mutually recognizing the client and the trusted authorization system based on a protocol; S030,enabling the client to perform authentication, and if the authentication is passed, enabling the trusted authorization system to take the IP address of the client as a parameter, filling an IP strategy packet and sending the IP strategy packet to a corresponding server; S040, analyzing and processing the IP strategy packet by a preposed IP filter of the server, and recording the IP address of thelegal client; and S050, if the authentication of the client and the trusted authorization system is normal, enabling the IP packet from the client to communicate with the server. According to the method, remote unauthorized access and unauthorized internet surfing of the server are shielded to the maximum extent, and the problems of random connection of an internal Trojan horse program to an external network, remote malicious attacks, connection and the like are reduced.
Owner:深圳深度探测科技有限公司
Wall-mounted d-shaped frameless bee hive
A wall-hung D-shaped frameless Apis cerana hive is characterized in that a D-shaped base ring is placed on a D-shaped metal bracket, a concave base plate is mounted below the D-shaped metal bracket, 4-6 D-shaped supers are stacked on the D-shaped base ring, a D-shaped cover covers the supers, and gaps between the D-shaped supers and gaps between the D-shaped supers and the cover are sealed by bee wax. The wall-hung D-shaped frameless Apis cerana hive has the advantages that Apis cerana is allowed to form spherical clusters, viewing, swarming and honey taking are convenient, and honey is prevented from secondary pollution; the Apis cerana hive which accords to natural living habits of Apis cerana is suitable for Apis cerana beekeeping in permanent apiary in scattered families in villages and modern villas, the Apis cerana hive combines advantages of novel Apis cerana hives and traditional Apis cerana hives and overcomes defects of the novel Apis cerana hives and the traditional Apis cerana hives, the Apis cerana hive is free of usual management and feeding, and the honey produced is purely natural, original, and various in kinds; the wall-hung D-shaped frameless Apis cerana hive is simple to mount, convenient to assemble, firm and durable, and long in service life.
Owner:CHEGNGDU CHENG KE TROTHER APICULTURE COMPANY
An intelligent logistics method and system for online shopping based on third-party payment
ActiveCN104766196BPrevent the situation of first shipmentEnsure safetyBuying/selling/leasing transactionsLogisticsThird partyLogistics management
The invention discloses an intelligent logistics method and system based on third-party payment online shopping. The method includes setting a logistics proxy server, adding an interface to the third-party payment platform to the logistics proxy server, and passing the interface , The third-party payment platform transmits information with the logistics agent server; the third-party payment platform submits an order request to the logistics agent server, and the logistics agent server according to the shipping information in the order request With the delivery information, select the logistics party closest to the delivery address to receive the goods; the logistics agency server sends the order request to the logistics scanning device of the logistics party, when the goods are delivered, the logistics scan The device scans the order number identifier provided by the buyer and uploads the order number identifier to the logistics agency server for verification, and at the same time feeds back the verification result. After the verification is passed, the third-party payment platform updates the order information.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
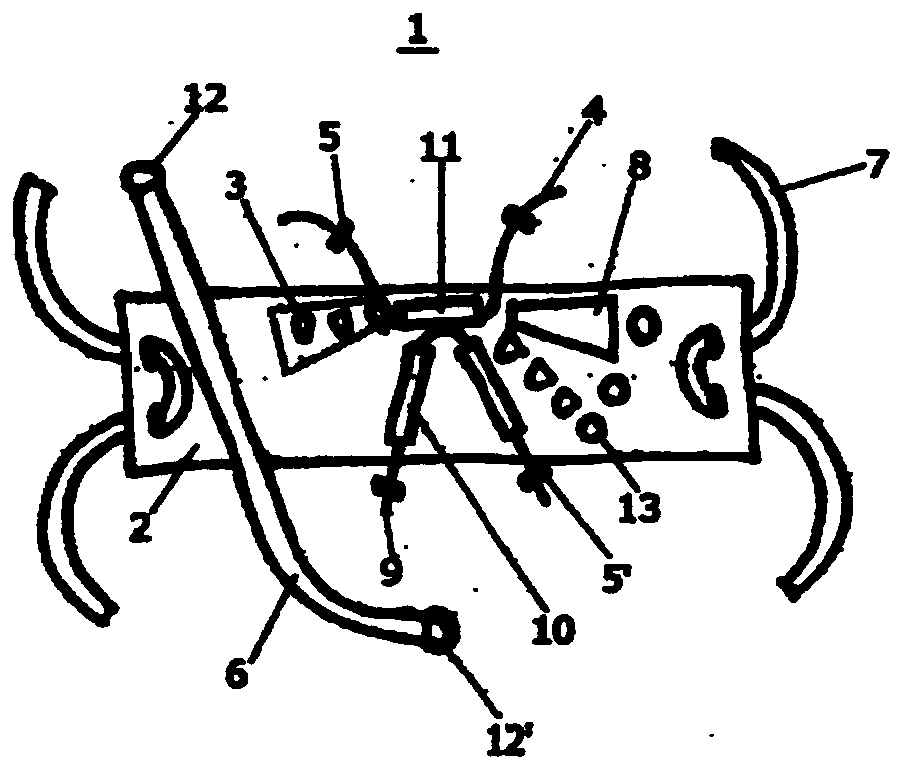
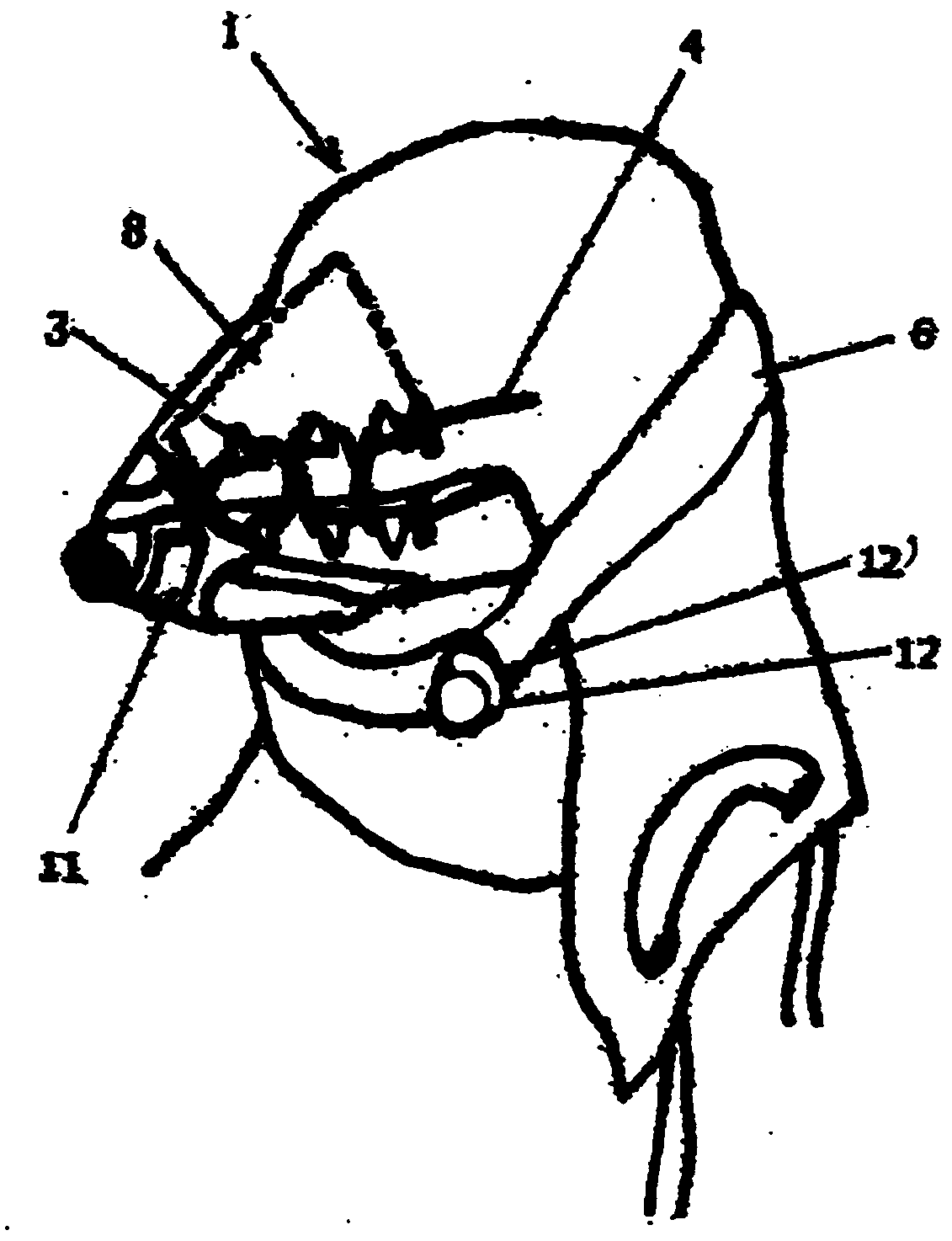
Bite prevention towel
ActiveCN110267530ALess risk of being bittenSwift ban on movementTaming and training devicesSurgeryCompanion animal
The present invention provides a bite prevention implement with which, when trimming a dog's hair at a pet grooming parlor or providing medical treatment to a dog at a veterinary hospital, it is possible to safely restrain the dog in place with less stress for both human and dog without placing a burden on the dog. The bite prevention implement according to the present invention is a towel-like fabric that is wide enough to cover the entire lower jaw of a dog and long enough to cover the entire head except for the nose. The dog's jaw is placed in the center of said towel-like fabric, and then the fabric is wrapped around the back of the head so as to restrain the jaw joint in place. The width of the towel-like fabric is adjusted by a pair of covers and a string. Both ends of the towel-like fabric have an extension belt attached thereto so as to have the belt connected on both sides for holding a region from the back of the head to the neck. Further, the center of the towel-like fabric has attached thereto a hook-and-loop fastener, a string, and a hook, all of which function to restrain the jaw in position. The towel-like fabric has a pad added to the top end thereof, and is configured in such a manner as to allow the nose to be exposed out of the fabric.
Owner:金子美树
System and method for monitoring virtual machine process, method for filtering page fault exception
ActiveCN106055385BIncrease flexibilityNo performance lossSoftware simulation/interpretation/emulationProcess systemsMonitoring system
Owner:SICHUAN UNIV
A method of defending against ddos attacks based on channel hopping mode
ActiveCN105262737BImprove reliabilityWon't attackTransmissionCommunications securityComputer hardware
The invention relates to a method for resisting DDOS attacks based on a channel hopping mode. According to the method, communication parties negotiate about different communication channels temporarily, attackers cannot determine an attack target, and as long as one channel of the multiple channels can normally transmit data at any time, the communication parties can maintain a safe data channel; temporary keys are mapped to port numbers, the port numbers are generated in a random manner, the attackers are difficult to attack, a data packet is defined in the XML format, after the data packet is received, a flag bit is checked, duplicate removal is facilitated, packet loss is prevented, communication security and reliability are improved, and the DDOS attacks can be effectively resisted.
Owner:XIDIAN UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com