Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
114results about How to "Prevent discovery" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
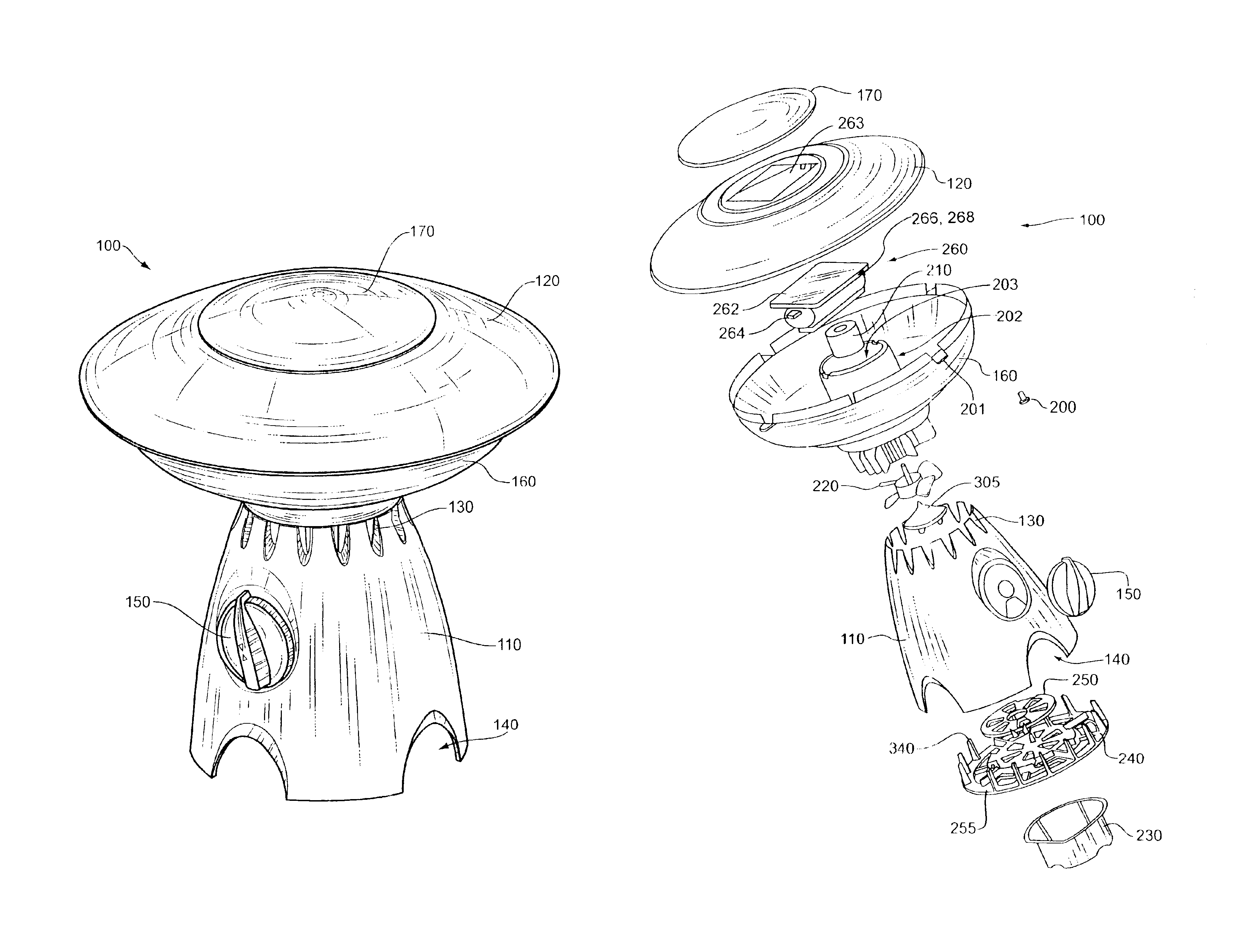
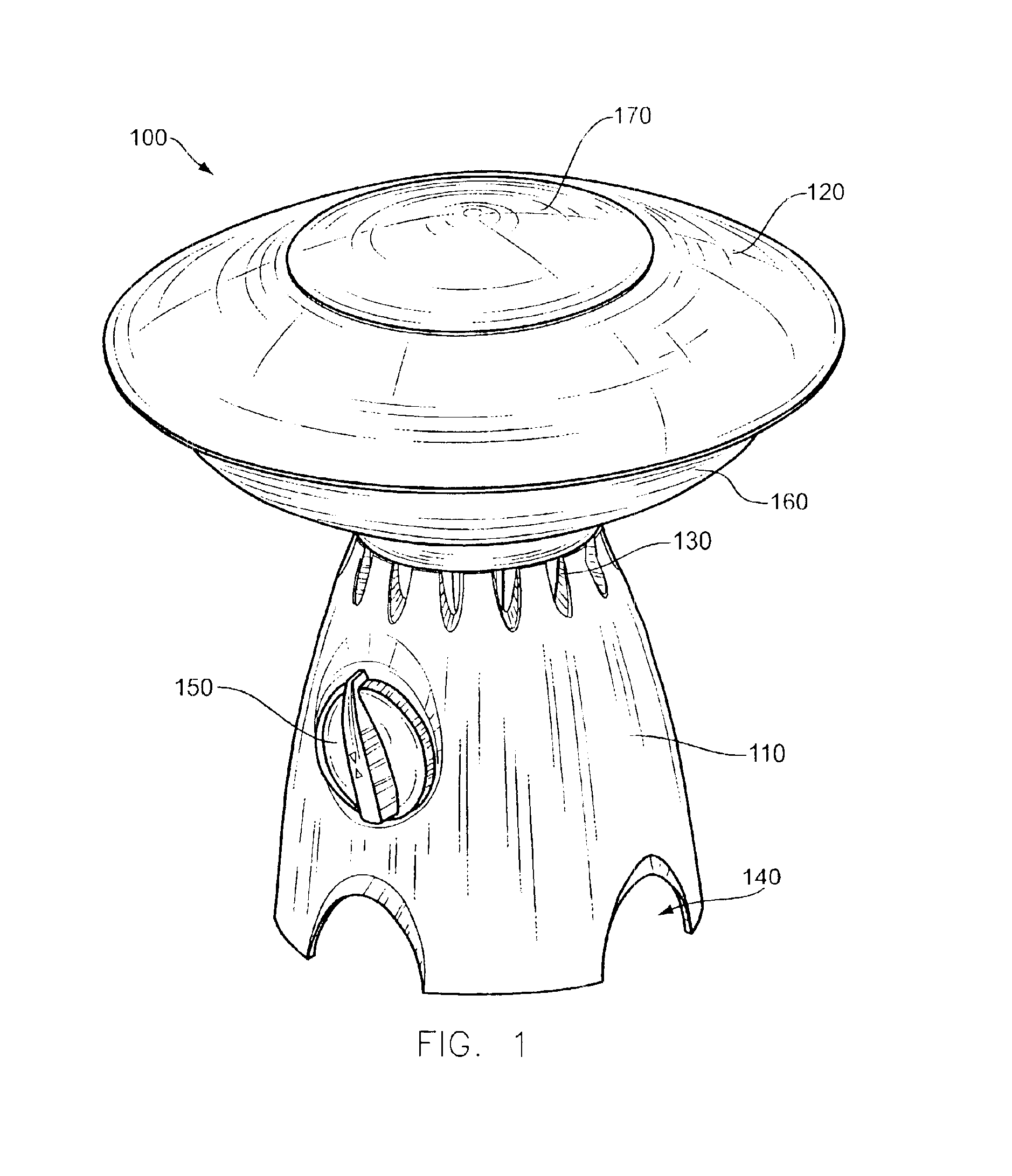
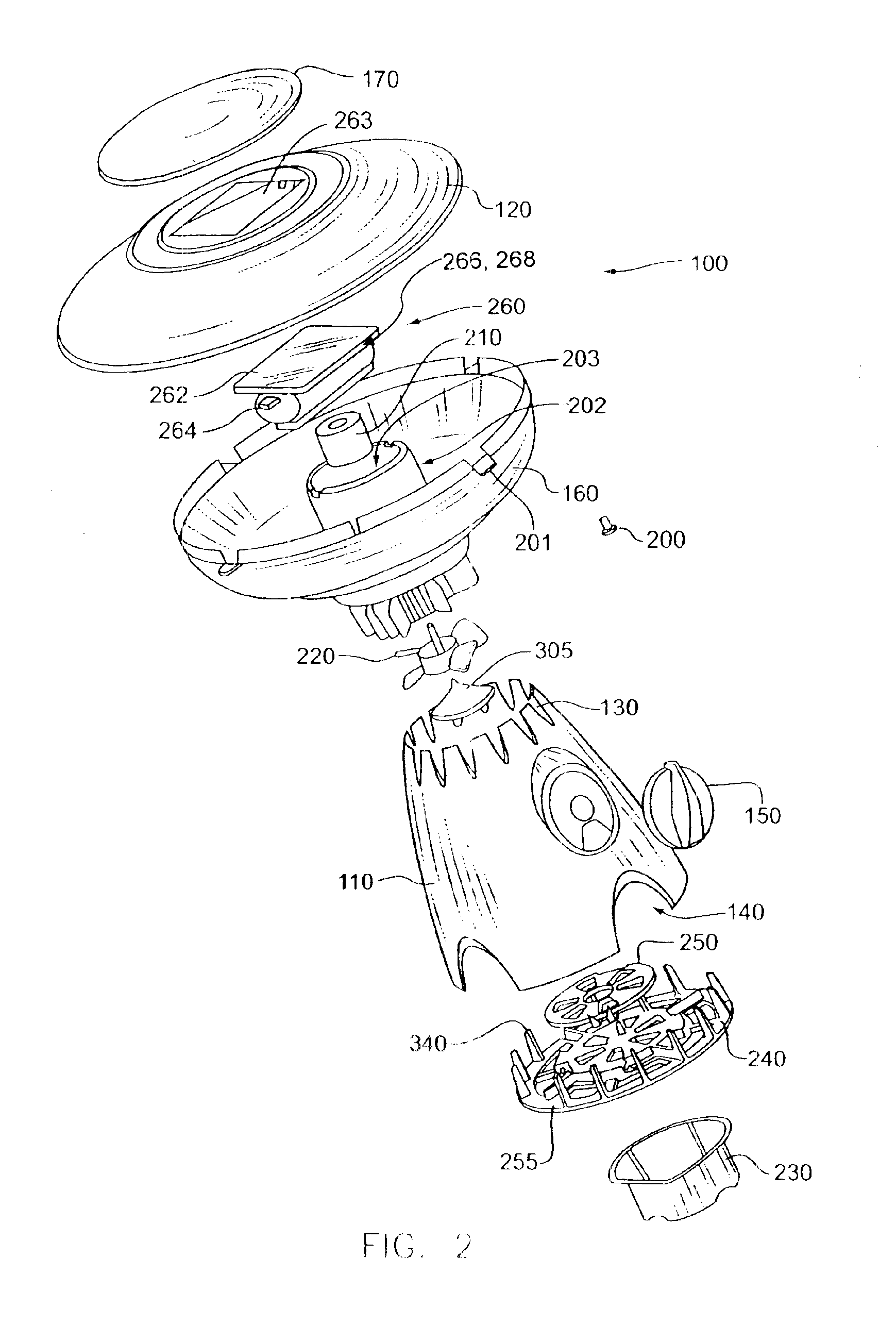
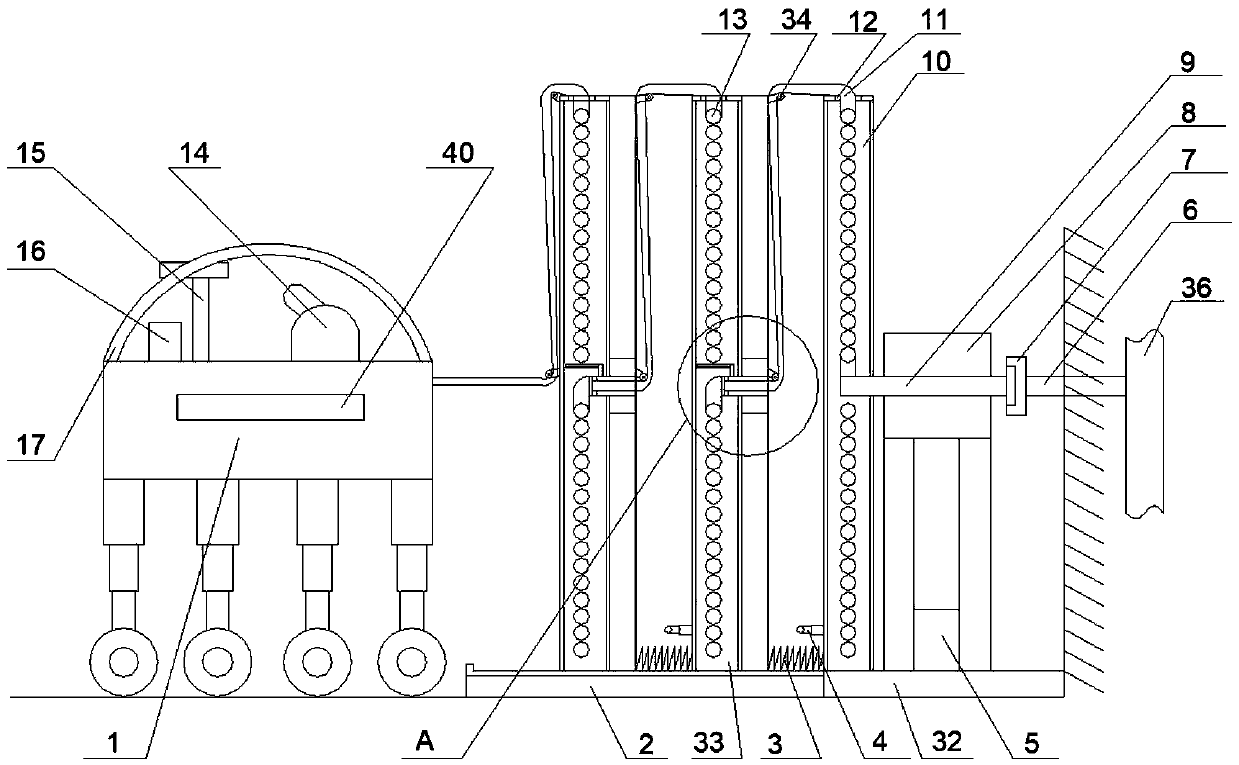
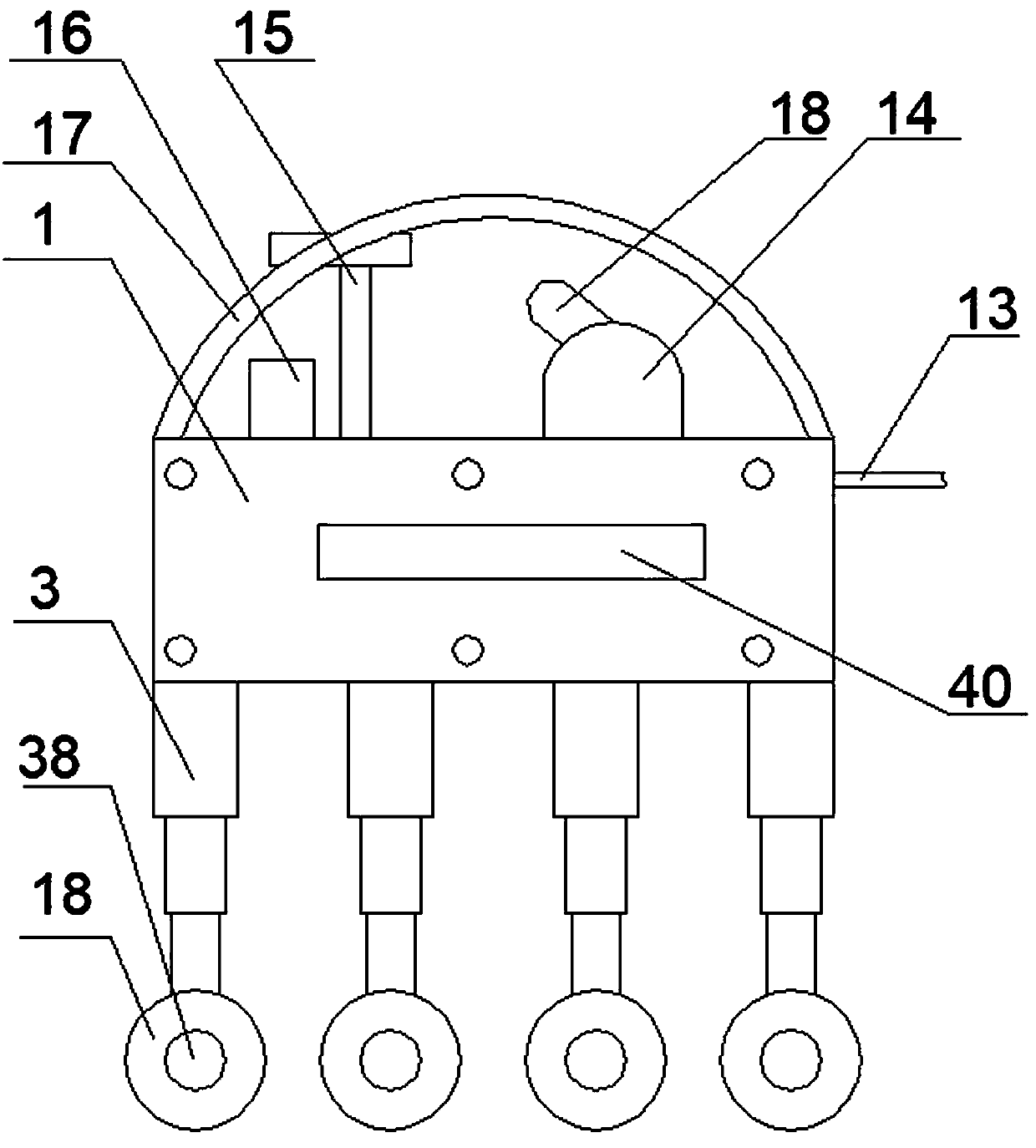
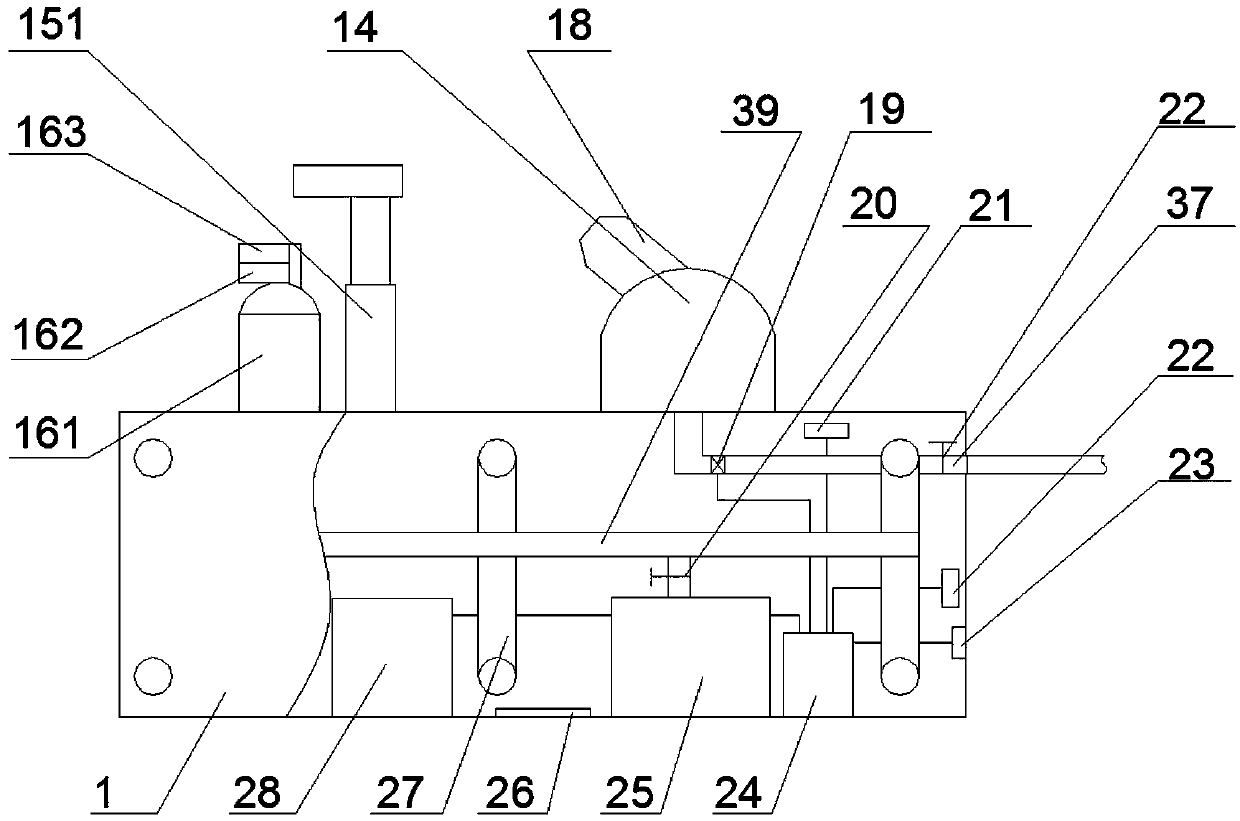
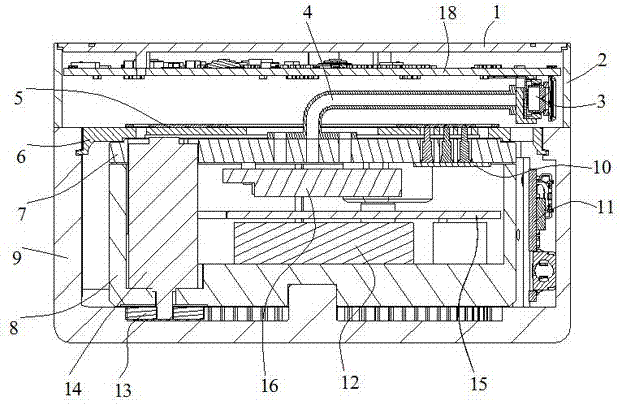
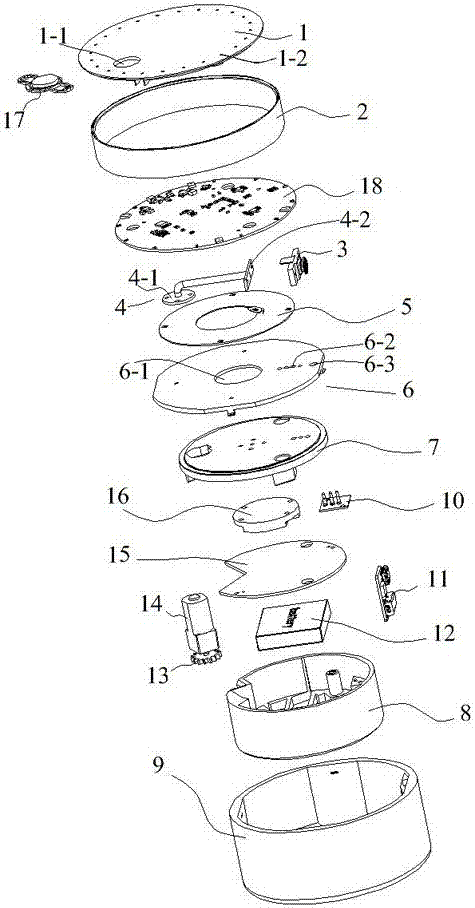
Light fixture and chemical distribution device
InactiveUS6854208B1Prevent discoveryLighting and heating apparatusMixing methodsChemical distributionEngineering
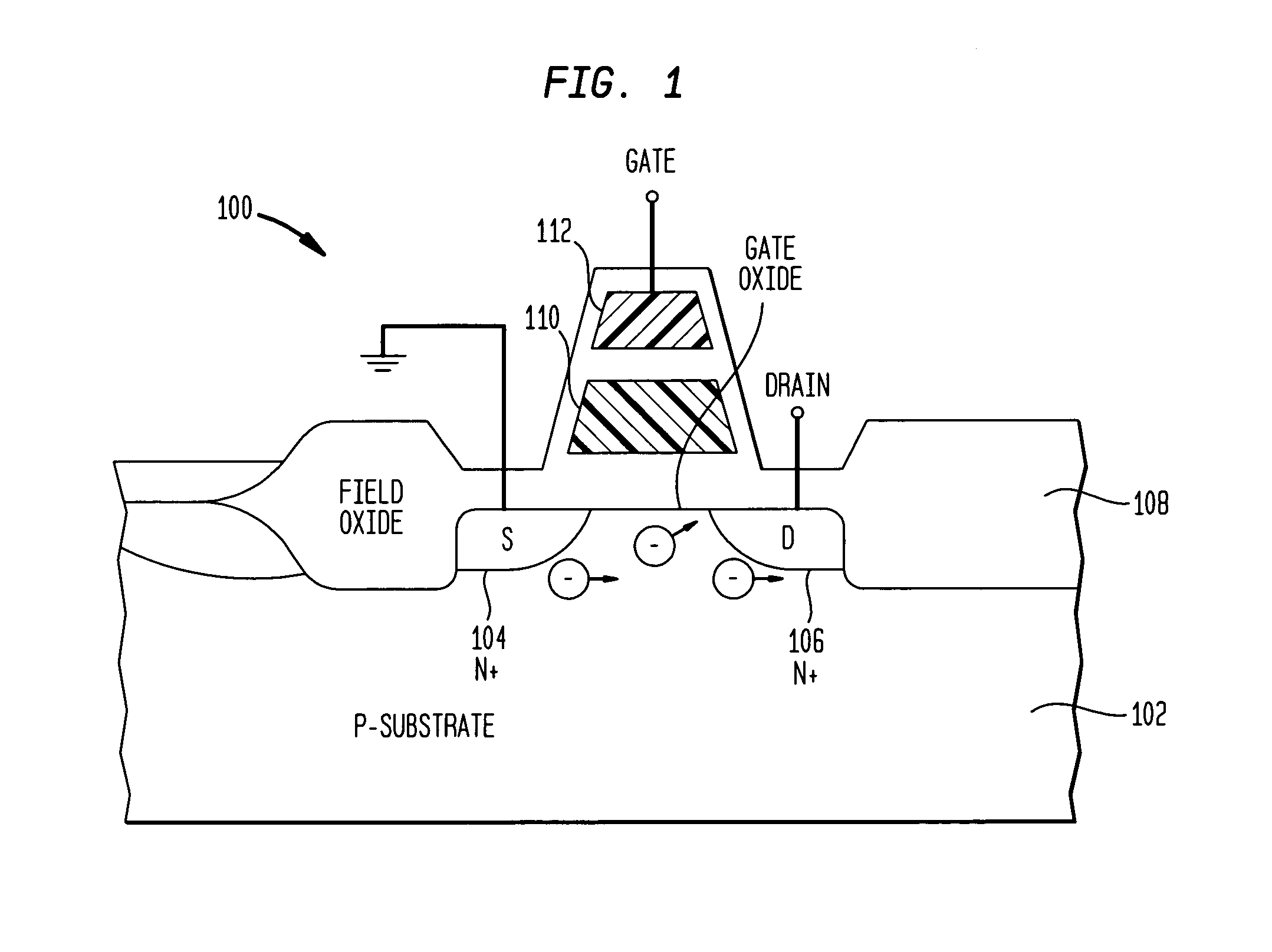
A device is disclosed for distributing chemicals, such as mosquito inhibitor chemicals. The device includes a housing and a light source. The light source is positioned within the housing such that the light source can be used to illuminate objects located near the device. The housing also includes a chemical disperser capable of distributing the chemicals. A solar panel provides power to the device.
Owner:J BAXTER BRINKMANN INT
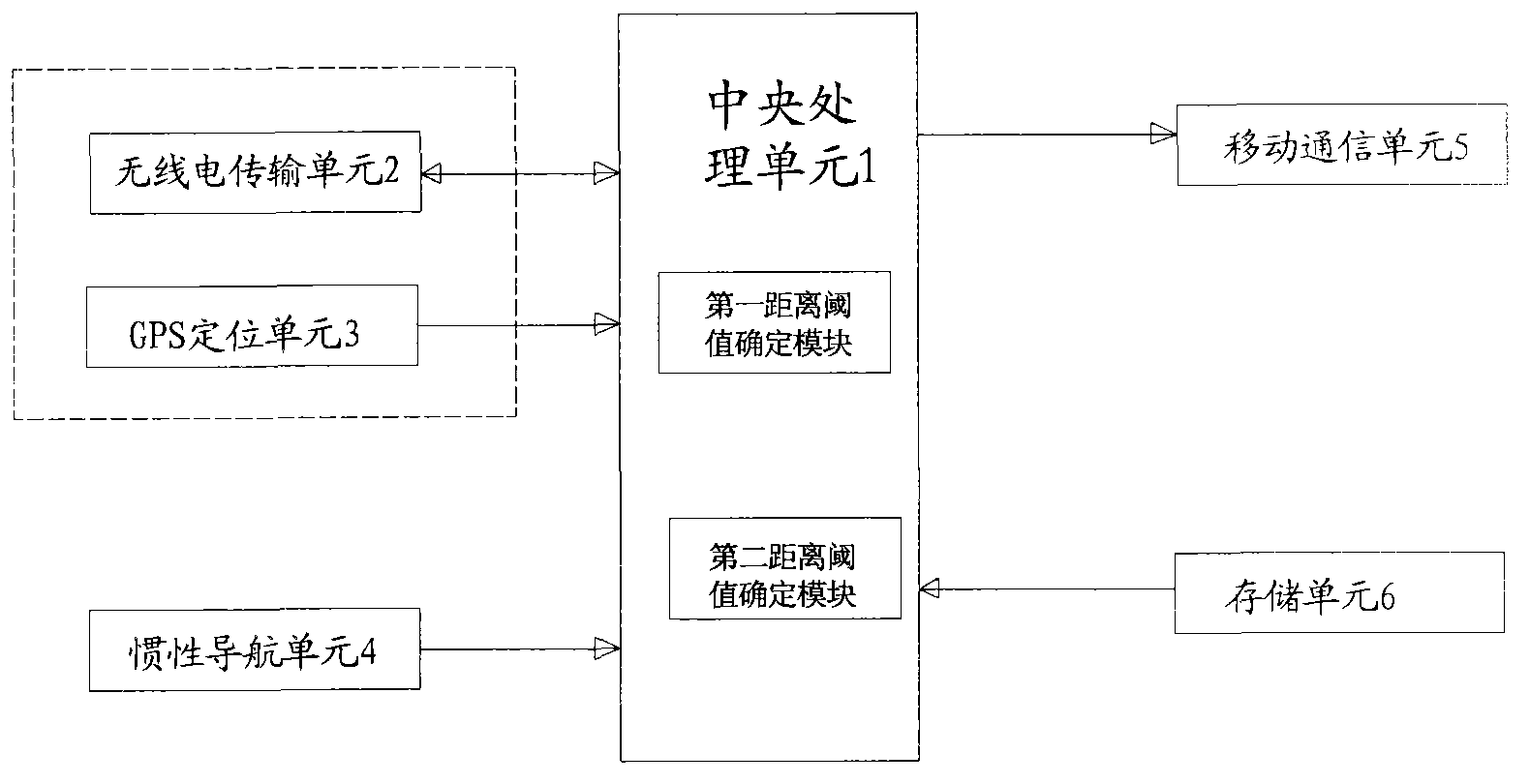
Locator-based locating method
ActiveCN103237292ASolve power consumptionSolve the problem of indoor positioning trackingEnergy efficient ICTNear-field systems using receiversGyroscopeAccelerometer
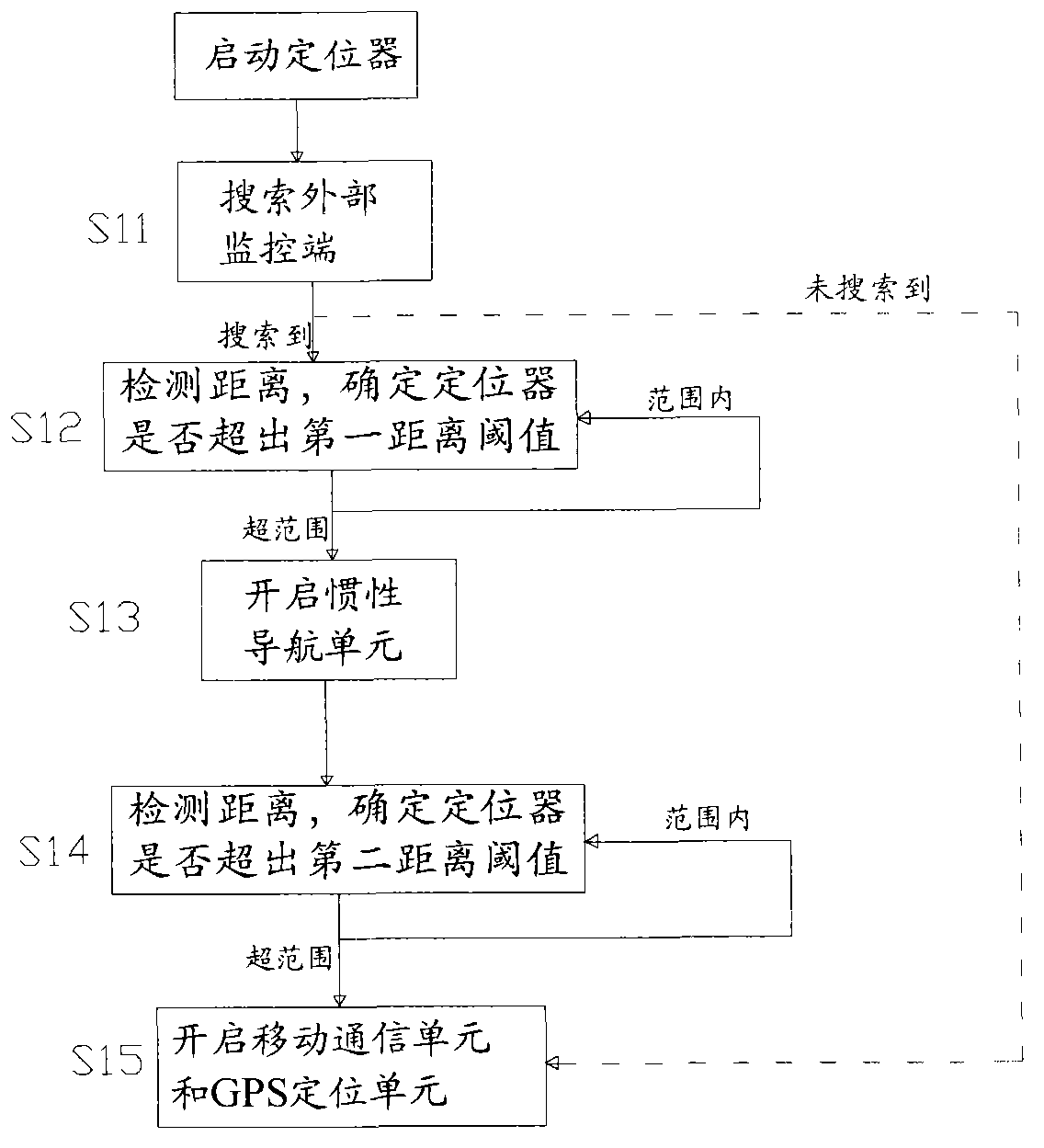
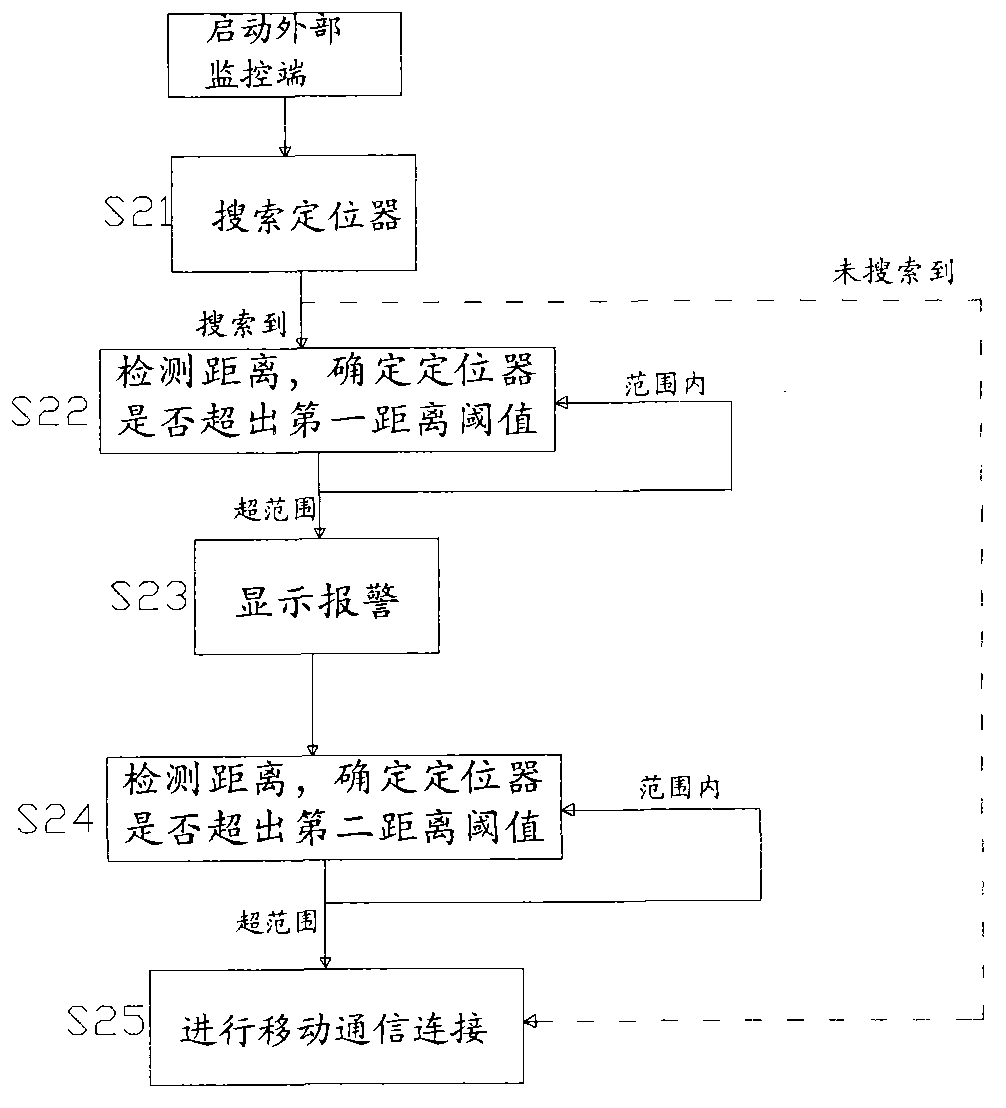
The invention provides a locator-based locating method. A locator comprises a central processing unit, a wireless unit, a global positioning system (GPS) locating unit, an inertial navigation unit, a mobile communication unit and a storage unit. The method comprises the following steps that a corresponding external monitoring end is searched based on a wireless detection signal; whether the current distance between the locator and the external monitoring end exceeds a first distance threshold value is determined based on the current wireless signal intensity and a mapping table stored in the storage unit; the inertial navigation unit is started when the current distance exceeds the first distance threshold value; whether the current distance exceeds a second distance threshold value is determined by detecting whether wireless connection can be established between the locator and the external monitoring end; and the mobile communication unit and the GPS locating unit are started when the current distance exceeds the second distance threshold value. By combining low power consumption Bluetooth, wireless fidelity (WIFI), a gyroscope and an accelerometer, the problem of power consumption due to the sustained use of a mobile network and GPS locating is solved.
Owner:钟国峰
Methods and apparatus for mediametric data cryptoprocessing
InactiveUS6993130B1Good security against compromisePrevent discoveryTransistorUser identity/authority verificationComputer scienceMemory array
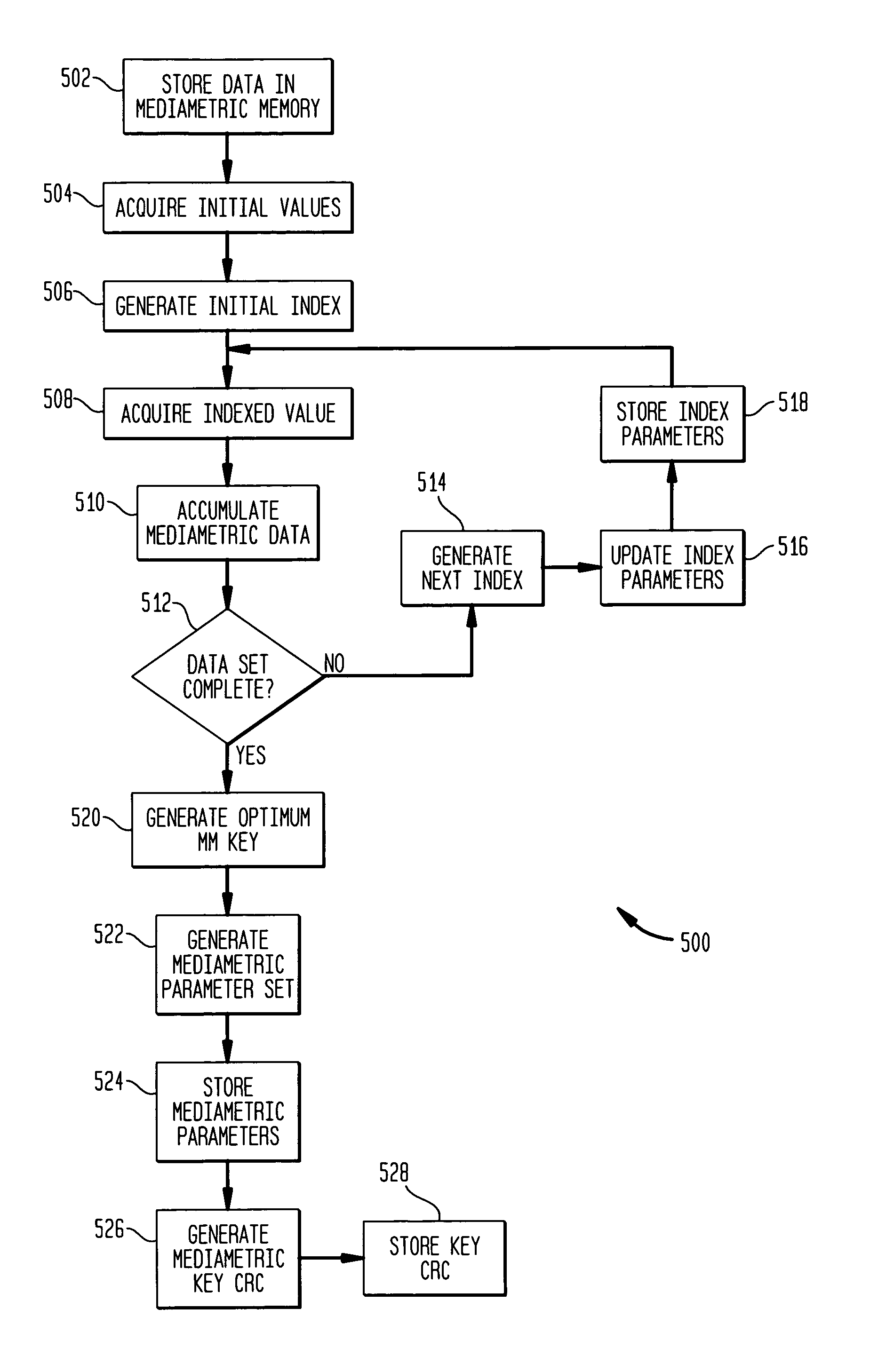
A data storage device having mediametric properties used as a source of data for cryptoprocessing keys. A memory array is formed by a plurality of memory cells, each cell containing a level of trapped charges that are difficult or impossible to set to a specific value, but which may be read relatively precisely. The levels of trapped charges are read from selected cells. Data relating to the level of the trapped charges is used to produce the cryptoprocessing keys. In addition, data relating to the charge levels in a memory array is used in generation of random numbers. When a random number is desired, data is written to selected cells of the memory array in order to establish random charge levels in the cells. The data is then read from the selected cells and processed to yield a random number.
Owner:XTEC INC
Method for preventing network gam from being external
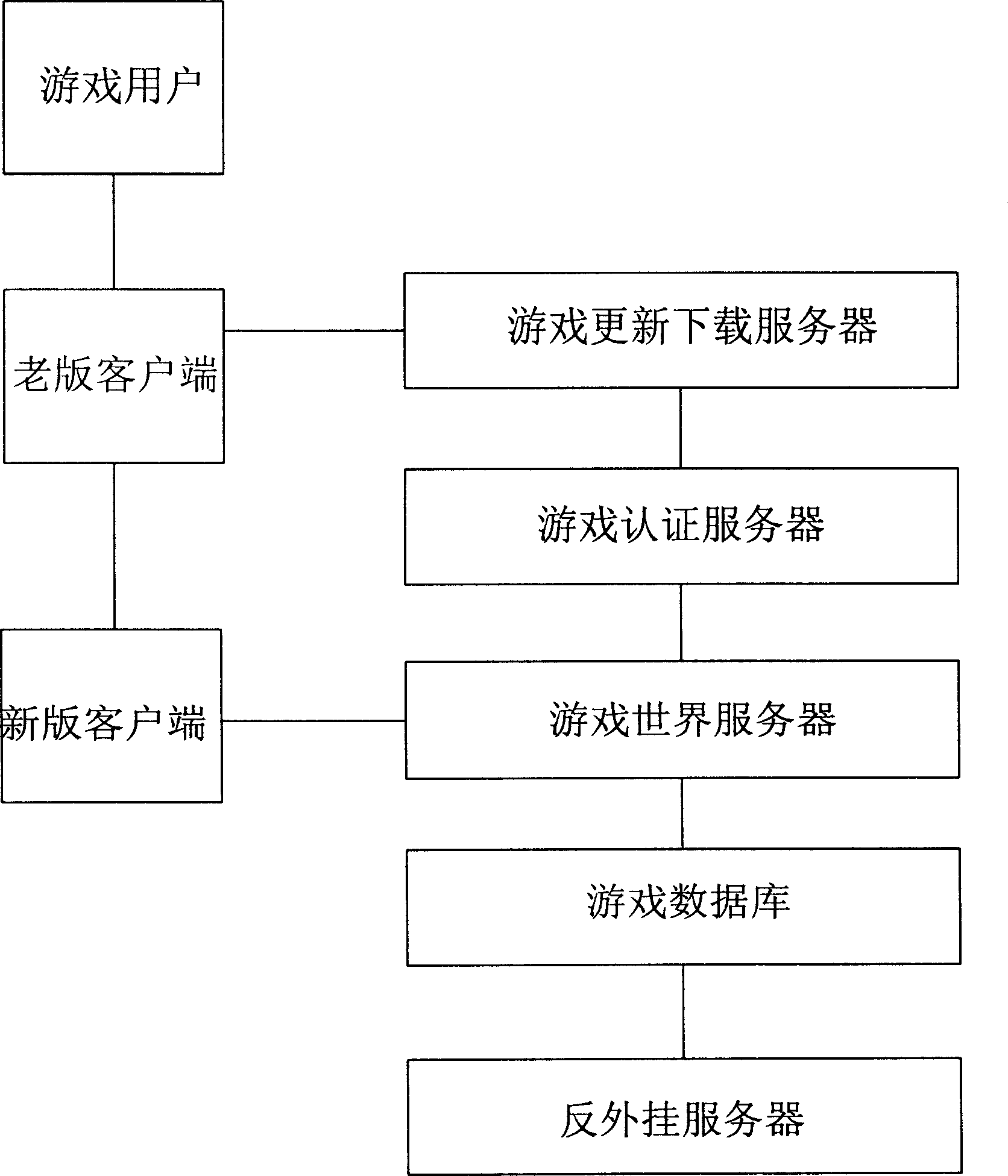
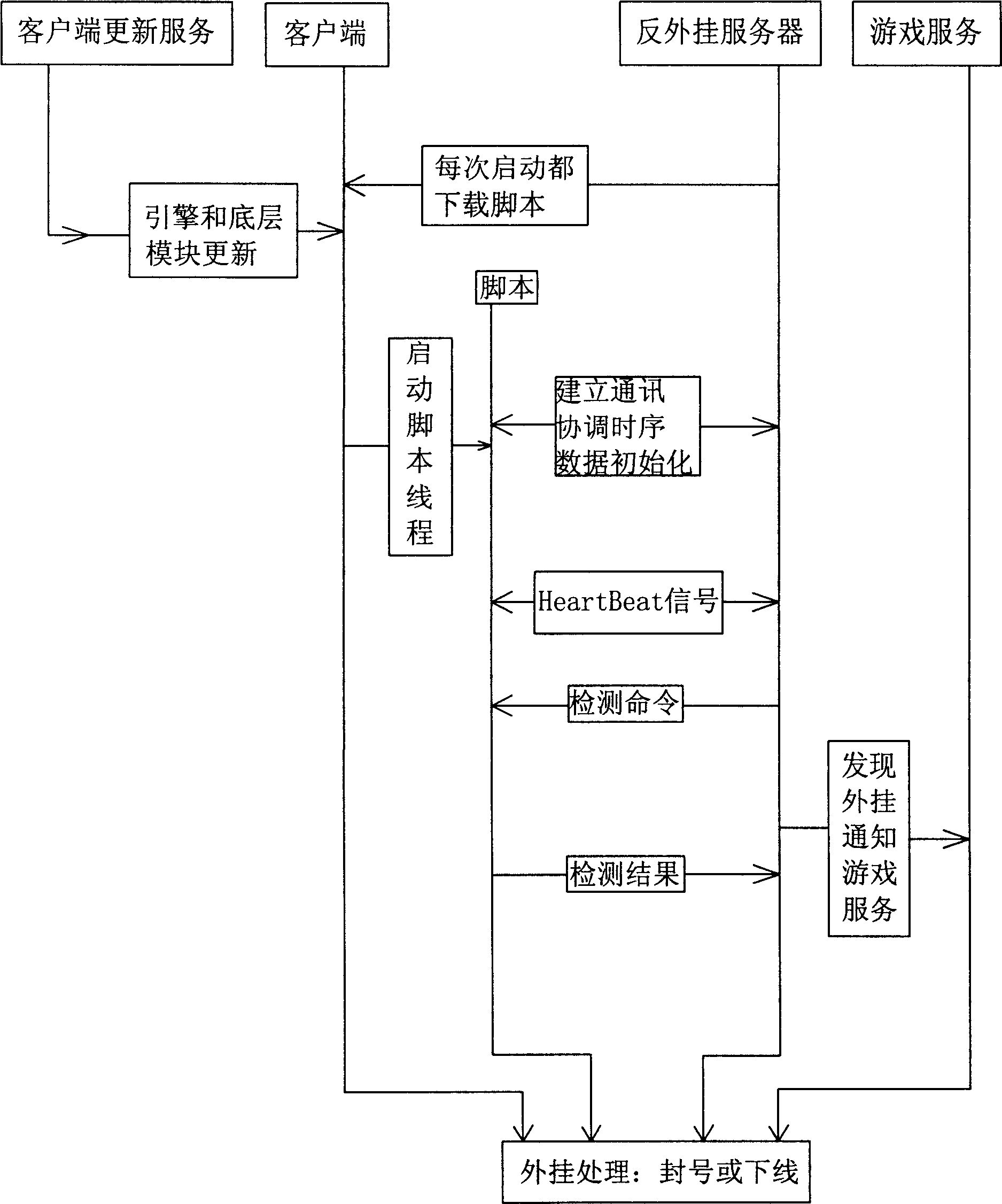
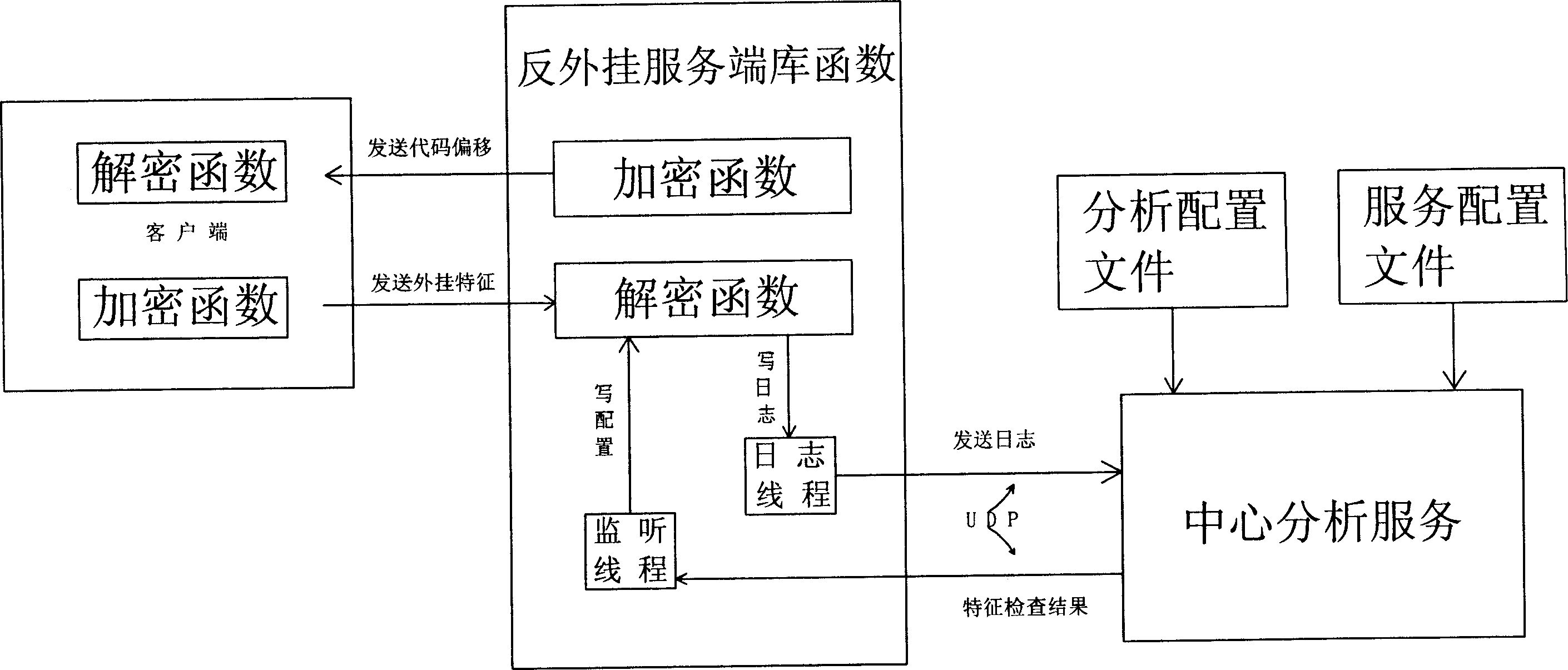
InactiveCN1744525AIncrease update frequencyPrevent discoveryData switching networksSpecial data processing applicationsNetwork packetClient-side
The method includes steps: adding script engine at client end, and down loading detection script and associated data compiled in bytecode from independent script server; next, adding additional field for holding external plug in attributive information in transferred data packet; then, server end sends down one data to add to the timing signal; finally, decryption function at server end examines operating environment at client end to obtain result whether external plug in is used or not. Advantages are: keeping watch of external plug in strictly and flexible updating.
Owner:北京一起玩网络科技有限公司
Preparation method of high-temperature-resistant and corrosion-resistant infrared invisible coating
InactiveCN102086311AImprove distributionPrevent discoveryLiquid surface applicatorsAlkali metal silicate coatingsIonCorrosion resistant
The invention relates to a preparation method of a high-temperature-resistant and corrosion-resistant infrared invisible coating, which mainly comprises the following steps of: A. taking 30-60 parts of high-melting point infrared absorbers, 15-25 parts of high-melting point oxides and 10-20 parts of vitrified matter titanium dioxide, adding all the components subjected to dry modification to 5-20 parts of bonding agents by using 3-7 parts of modifiers, then adding to 10-50 parts of deionized water as a dispersion medium, and carrying out ball-milling mixing for 1-12 hours to obtain an infrared invisible coating material; and B. carrying out blast sanding on a nickel base alloy plate, spraying a bonding layer containing NiCrAlY on the alloy plate with a linear spraying method, wherein the thickness of the bonding layer is 0.2-0.3mm; spraying the infrared invisible coating obtained in the step A on the bonding layer, and then airing wherein the thickness of the infrared invisible coating is 0.08-0.13mm; and annealing for 1-2 hours (a temperature rise speed is 10 DEG C / min) at the temperature of 650-850 DEG C to obtain the infrared invisible coating with the roughness of 1100-1800 microfeet.
Owner:LIAONING SILICATE RES INST
Application starting method and device
InactiveCN106293478APrevent discoveryProtect personal privacyDigital data authenticationProgram loading/initiatingThe InternetComputer engineering
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
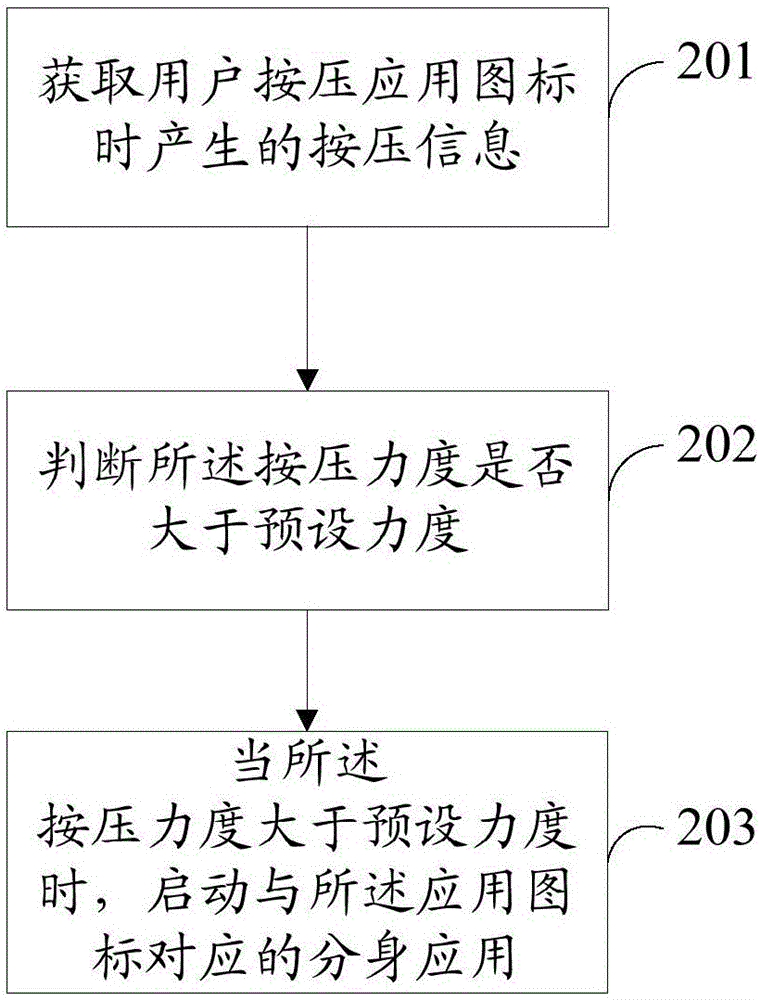
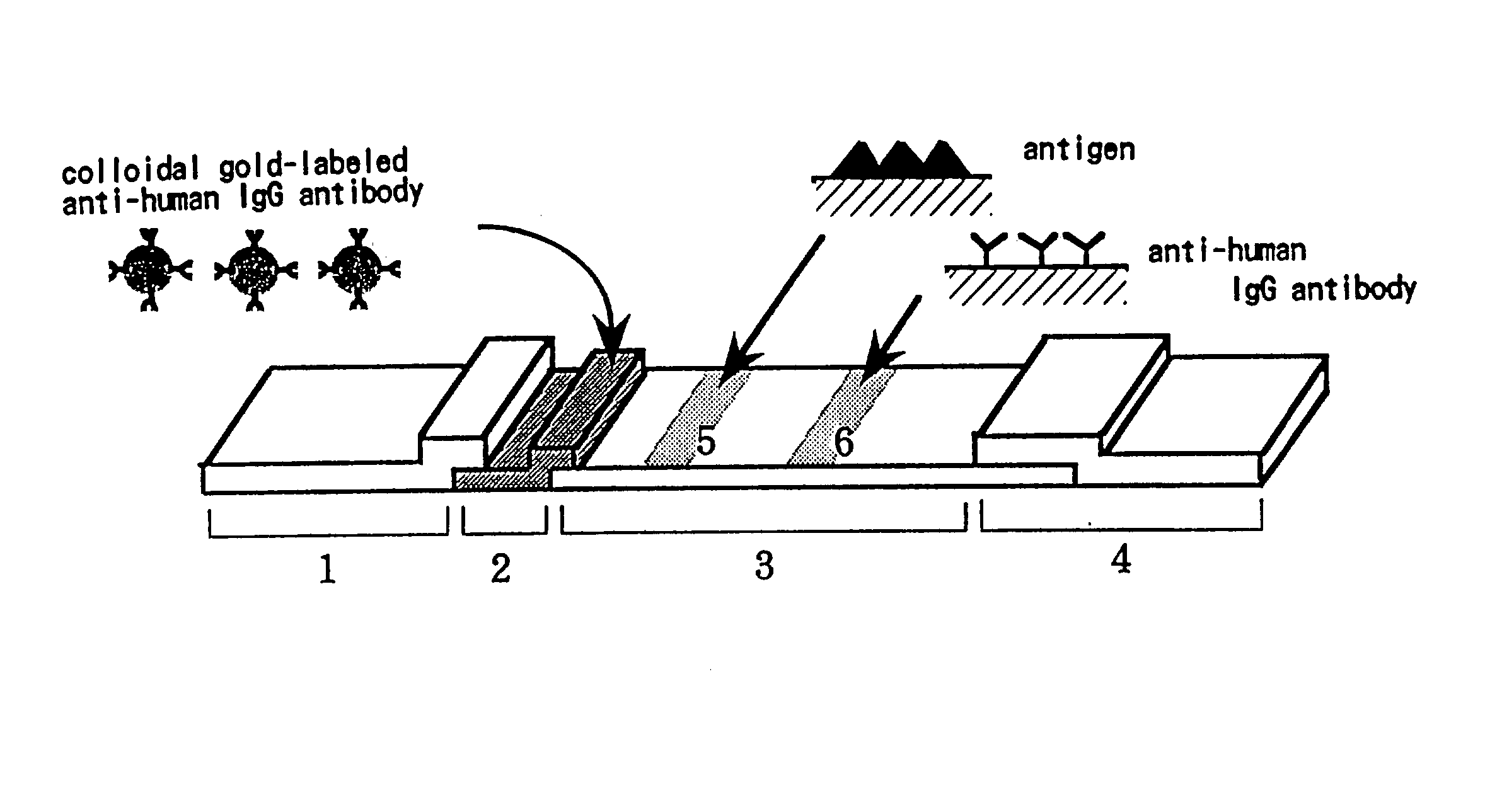
Method for assay of antibodies and antibody assay device
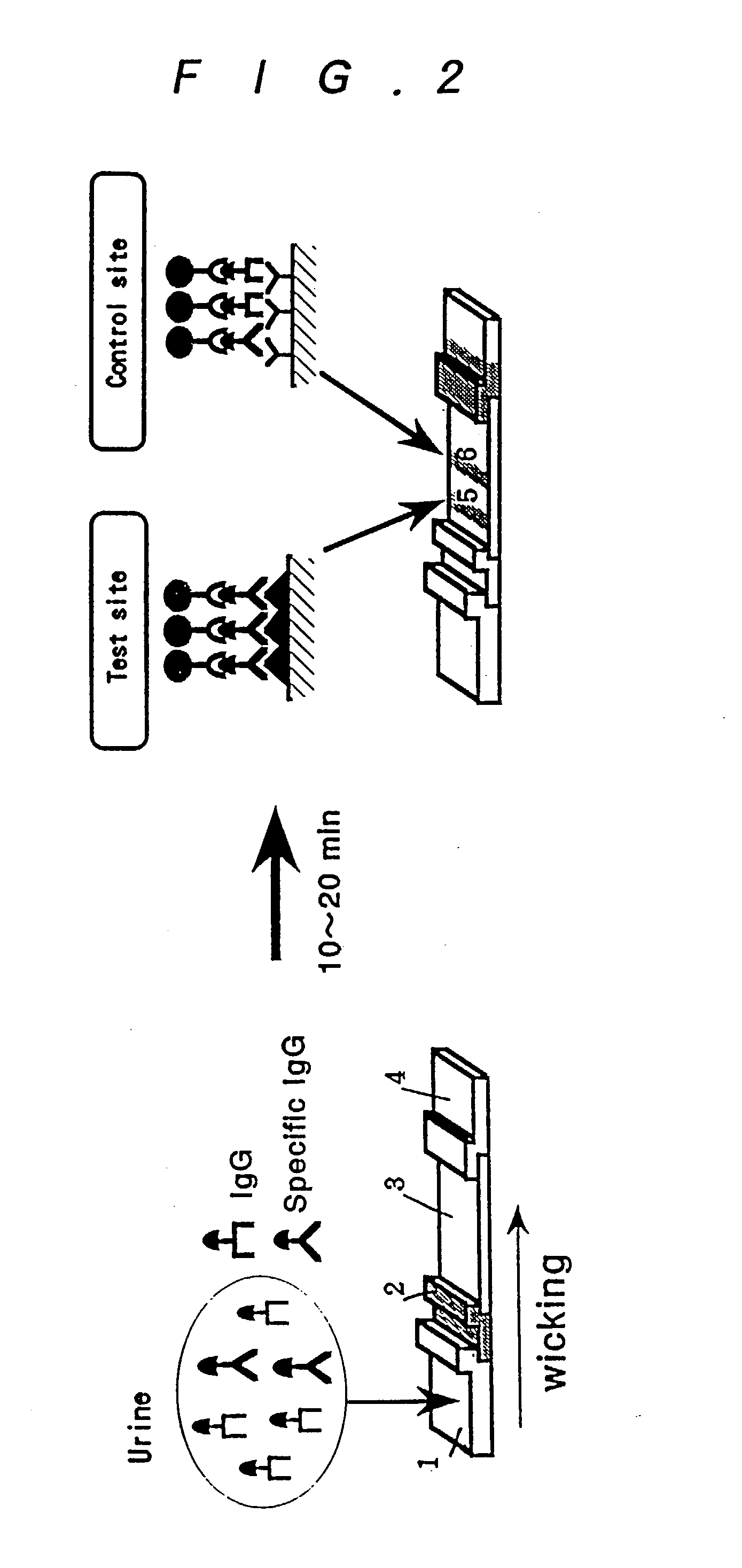
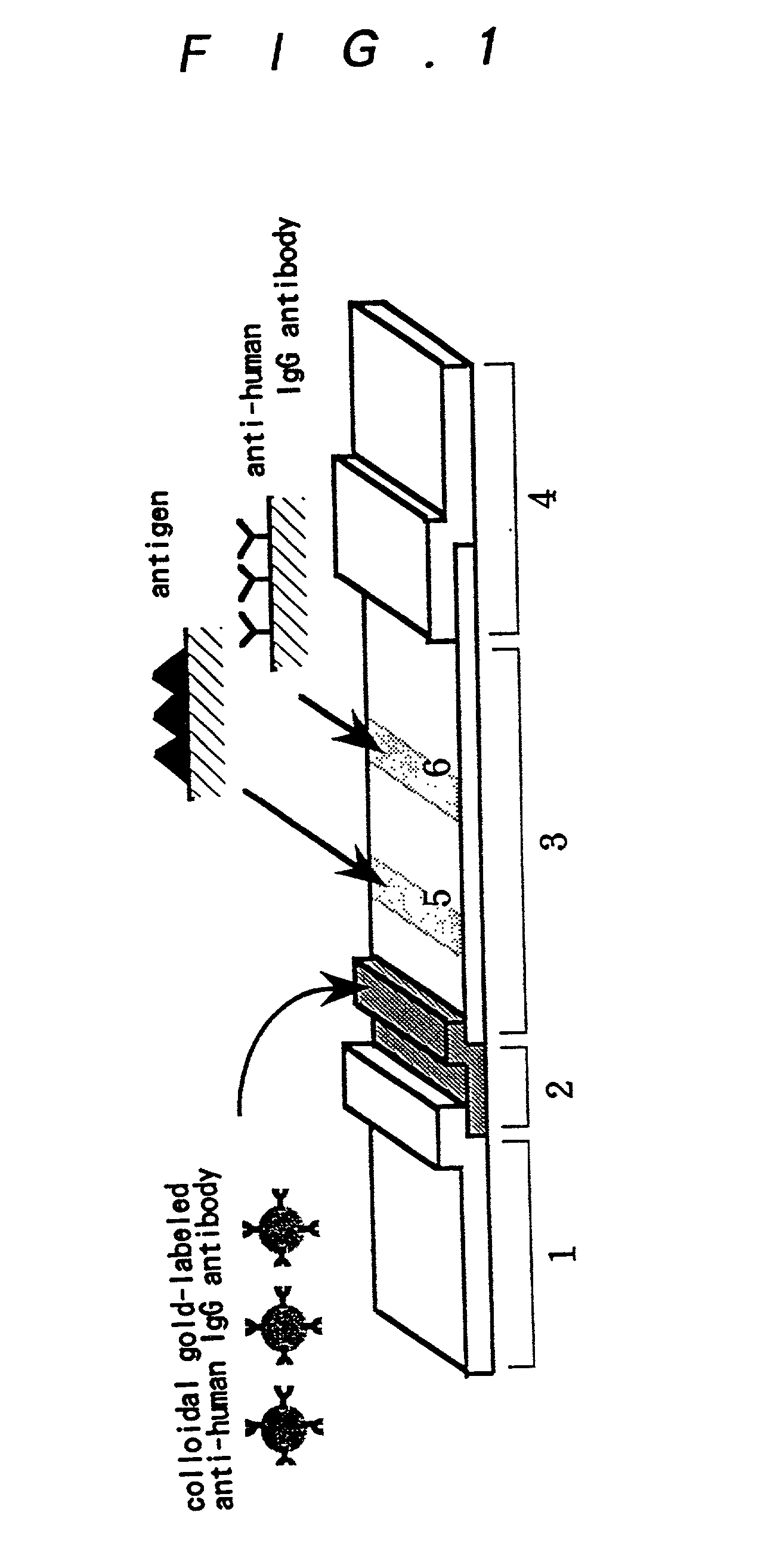
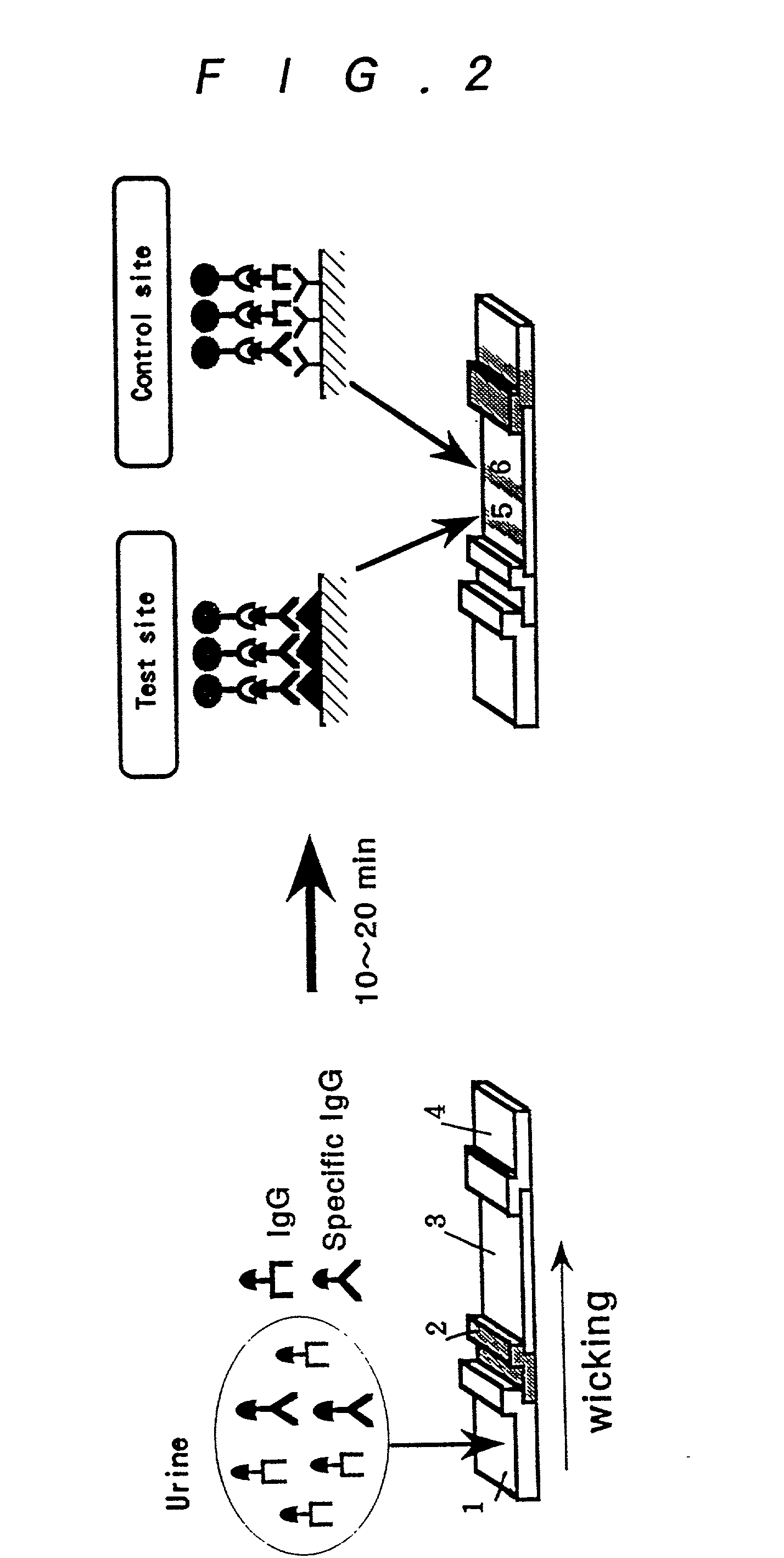
InactiveUS20030175699A1Enough timePrevent discoveryBioreactor/fermenter combinationsBiological substance pretreatmentsAssayAntigen-antibody reactions
The invention relates to a technology by which antibodies directed to sources of infection in body fluids can be assayed with high accuracy, expediency and specificity. More particularly, the invention provides an antibody immunoassay method in which the antigen-antibody reaction between a target antibody in a sample and an assay antigen is conducted in the presence of an E. coli component and an antibody assay method which comprises using a reagent having a specific affinity for the Fc region of an antibody IgG as the antibody assay reagent. The invention further provides an antibody assay device comprising a solid-phase support having at least (a) a first region to which a sample is applied and (b) a second region where the antibody in the sample is reacted as disposed in such an arrangement that the sample is wicked from the first region to the second region and a labeling means for detection of the result of the reaction in the second region, characterized in that the (b) second region is provided with (i) a test site in which a ligand for capturing the target antibody to be assayed is immobilized and (ii) a control site in which a ligand for capturing an arbitrary antibody occurring in the sample is immobilized.
Owner:OTSUKA PHARM FAB INC
Moving target tracking unmanned aerial vehicle for police
ActiveCN107284661APrevent discoveryEasy to trackImage enhancementImage analysisComputer visionGps positioning
The invention relates to vehicle pre-warning equipment and particularly relates to a moving target tracking unmanned aerial vehicle for police. A camera acquires target characteristics to extract target video information in real time; a target designation module is used for performing positioning tracking; a target track pre-judging module is used for establishing target moving track and pre-judging track; track simulating tracking module is used for setting the optimal tracking path. The unmanned aerial vehicle can use the camera to acquire video information to firstly acquire target characteristics such as facial features of people, license plates and color, characteristics are established for locking a target, so that tracking is convenient. The method is used for establishing the pre-judging track to make a tracking plan in advance; GPS positioning is combined to determine pre-judging tracking track according to the pre-judging track, so that accurate reference is provided; the optimal tracking angle can be set, so that a tracked object is prevented from being found; the optimal tracking flight gesture is regulated, so that tracking efficiency and tacitness are improved.
Owner:CHENGDU UNIVERSITY OF TECHNOLOGY
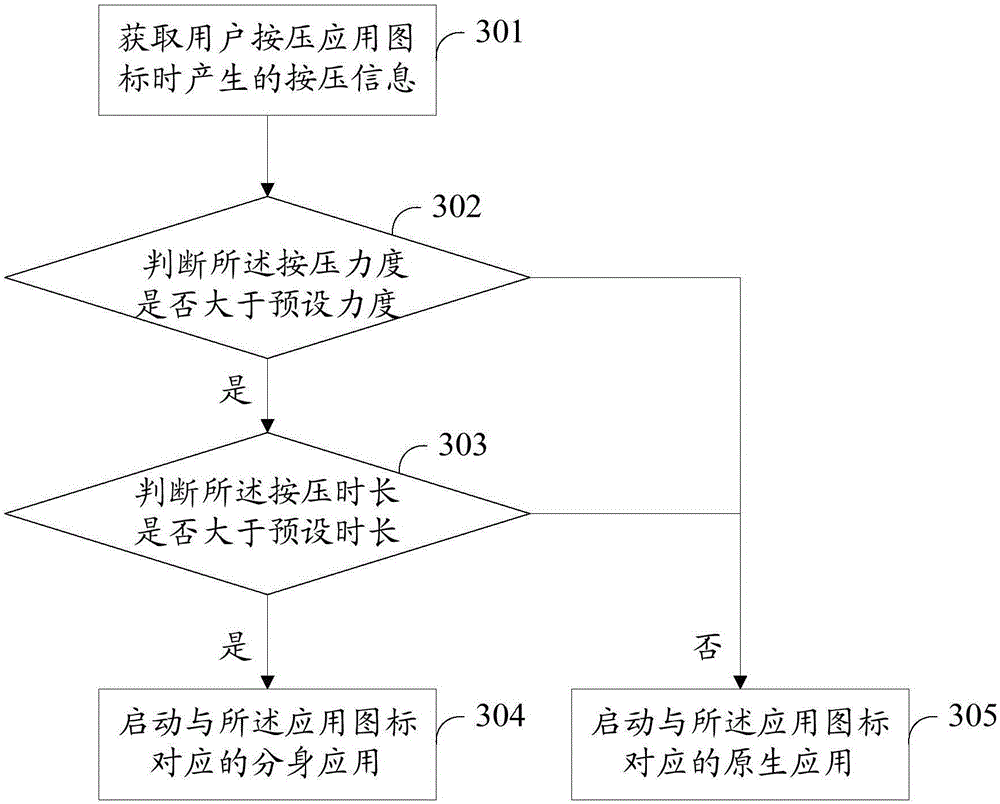
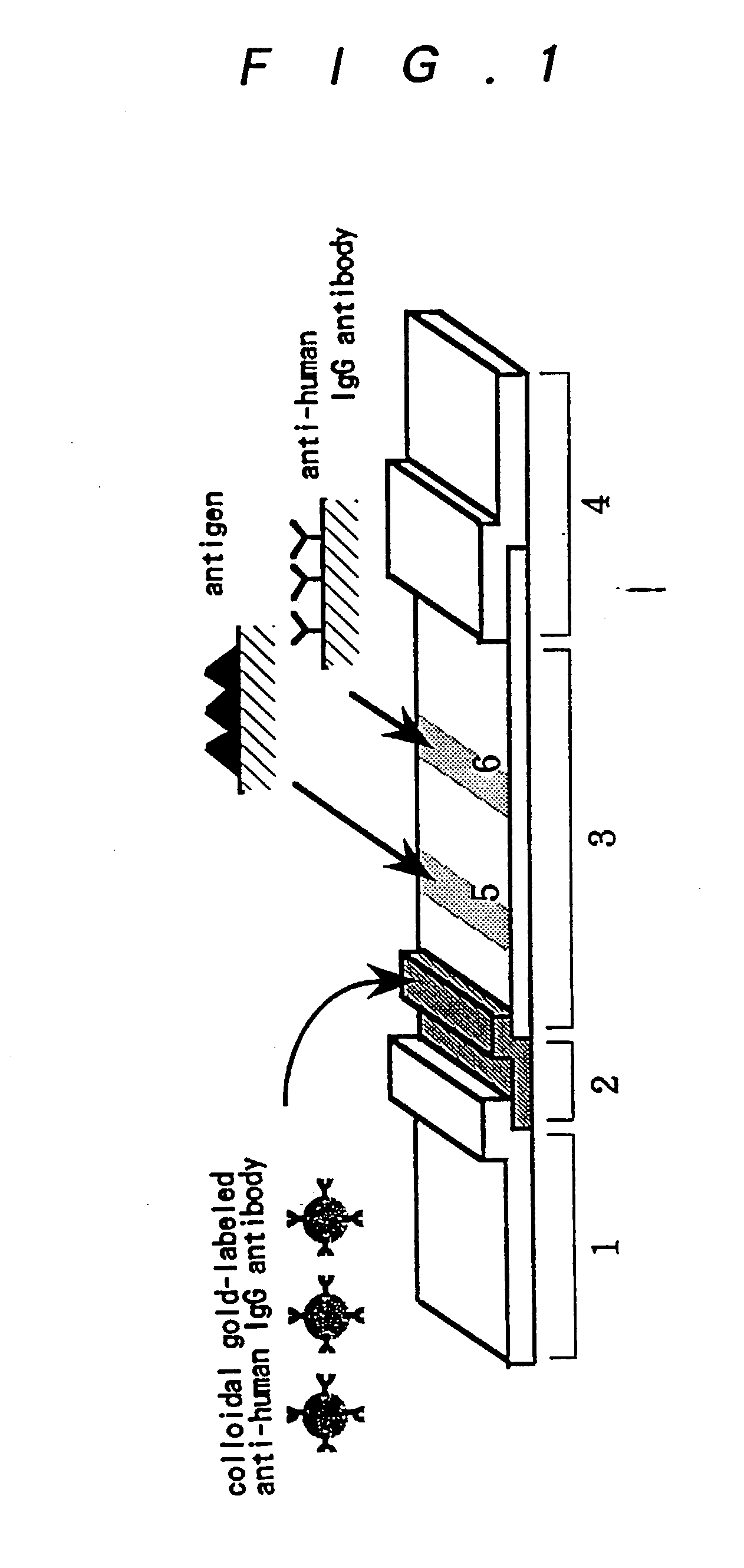
Method for assay of antibodies and antibody assay device
InactiveUS20020187510A1Enough timePrevent discoveryBioreactor/fermenter combinationsBiological substance pretreatmentsEscherichia coliAntigen-antibody reactions
The invention relates to a technology by which antibodies directed to sources of infection in body fluids can be assayed with high accuracy, expediency and specificity. More particularly, the invention provides an antibody immunoassay method in which the antigen-antibody reaction between a target antibody in a sample and an assay antigen is conducted in the presence of an E. coli component and an antibody assay method which comprises using a reagent having a specific affinity for the Fc region of an antibody IgG as the antibody assay reagent. The invention further provides an antibody assay device comprising a solid-phase support having at least (a) a first region to which a sample is applied and (b) a second region where the antibody in the sample is reacted as disposed in such an arrangement that the sample is wicked from the first region to the second region and a labeling means for detection of the result of the reaction in the second region, characterized in that the (b) second region is provided with (i) a test site in which a ligand for capturing the target antibody to be assayed is immobilized and (ii) a control site in which a ligand for capturing an arbitrary antibody occurring in the sample is immobilized.
Owner:OTSUKA PHARM CO LTD
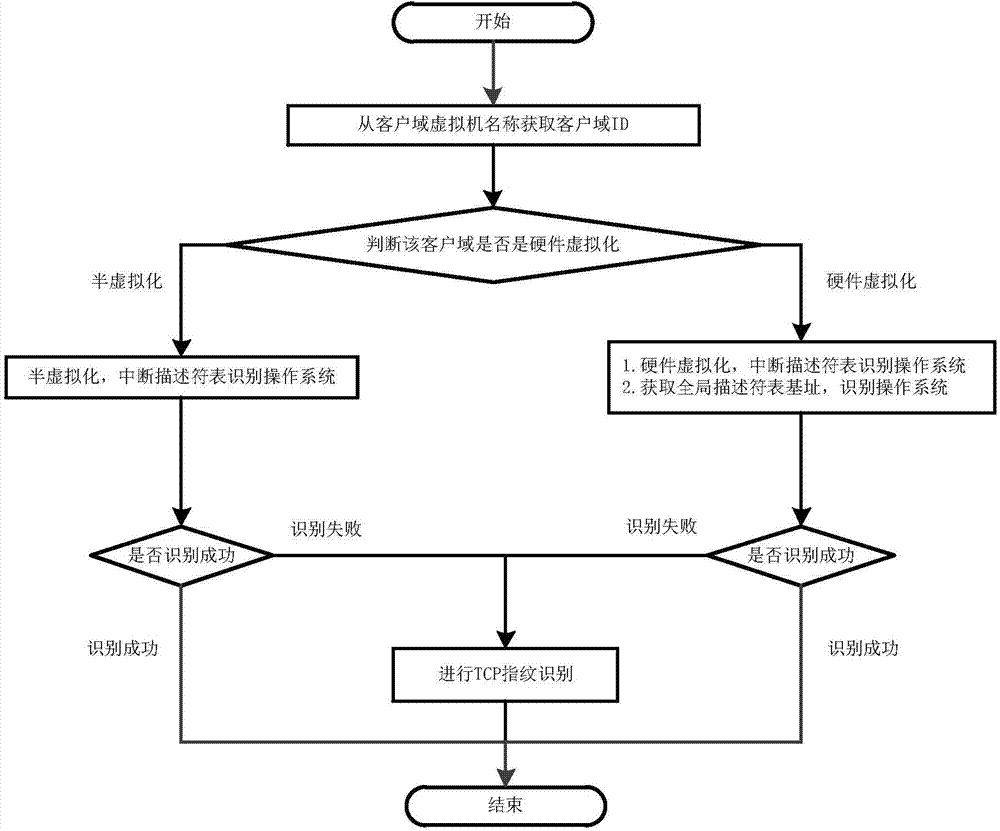
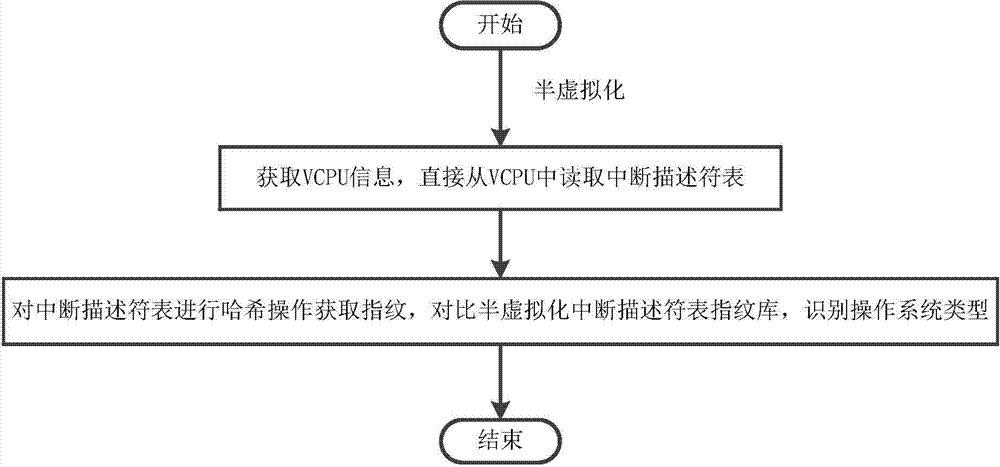
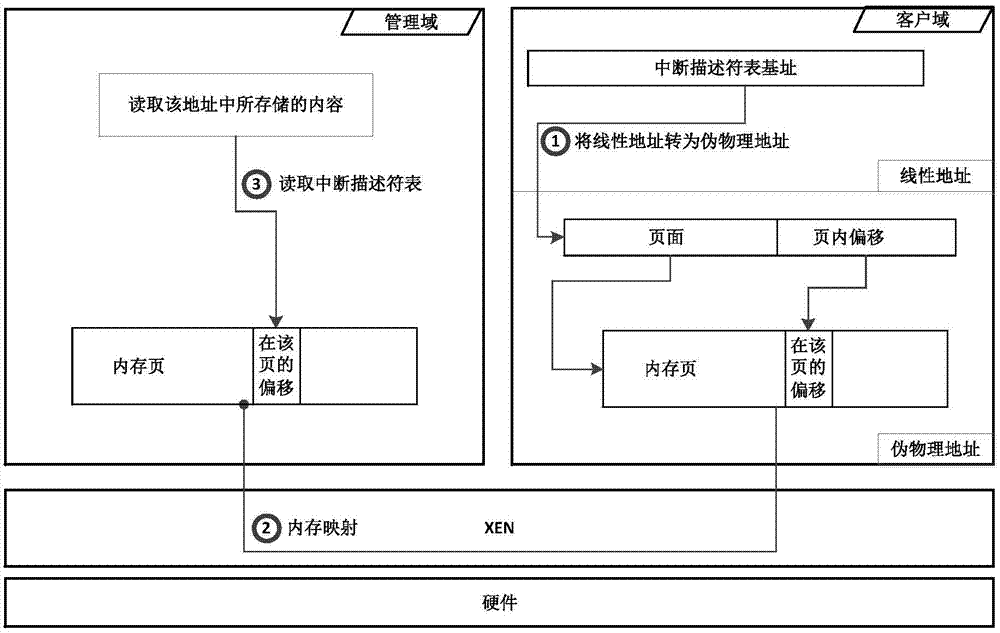
Xen-based operating system identification method
InactiveCN103544089AAvoid misidentificationNot strong stickinessHardware monitoringPlatform integrity maintainanceVirtualizationOperational system
The invention discloses a Xen-based operating system identification method, and belongs to the technical field of computer virtualization technology. The method is applied in identification of operating system type in virtualization environment. The method includes combination of accurate identification of fine grain and flexible identification of coarse grain, the operating system type is identified overfull, and the accurate identification of the fine grain is performed in two identification methods of interrupt descriptor tables and global descriptor table bases. By means of the accurate identification of the fine grain, the operating system type in a client domain from a management domain can be identified accurately, if the accurate identification of the fine grain is failed to identify the operating system, the operating system type in the client domain can be identified by utilizing TCP fingerprinting coarse grain, and accordingly the operating system type in the client domain from the management domain can be identified. According to the method, the client operating system is not modified during identification, information is acquired from the management domain, client operating system is not required to participate, the method is protected from being found by the client operating system and guarantees own safety.
Owner:XIDIAN UNIV
Automobile oil tank anti-theft device
InactiveCN109795314AEasy to insertPrevent discoveryAnti-theft devicesUnderstructuresFuel tankPetroleum engineering
The invention discloses an automobile oil tank anti-theft device, and belongs to the field of automobile accessories. The automobile oil tank anti-theft device comprises an automobile oil tank, an anti-theft fixing base, a sealing cover and an anti-theft oil sieve. The top of one end of the automobile oil tank is provided with an oil filling pipe. A center of the interior of the oil filling pipe is connected with the anti-theft fixing base. A center of the top of the anti-theft fixing base is provided with the sealing cover, and a bottom end of the interior of the anti-theft fixing base is inscrew connection with the anti-theft oil sieve. The automobile oil tank anti-theft device is capable of, through installing an annular locking strip, a sliding block, a fixing rod, an iron sheet, a telescopic cavity, an electromagnetic sheet and a first spring, after a thief damages a device for power supply, enabling the electromagnetic sheet to be power-off, enabling the sliding block to be slidin the interior of the telescopic cavity under the action of a resilience force of the first spring, driving the annular locking strip to be stretched out, enabling the annular locking strip to be effectively locked in the interior of the automobile oil tank while the thief draws and pulls the anti-theft fixing base, deadlocking the oil filling pipe, and avoiding the thief from stealing through detaching the anti-theft fixing base.
Owner:ANHUI UNIVERSITY OF TECHNOLOGY AND SCIENCE
Method for setting highway amphibian passage system
InactiveCN103790116AChoose scientifically and reasonablyAct as a "stepping stone"Ground-workWater diversionEngineering
The invention relates to a method for setting a highway amphibian passage system. The method includes determining position of the highway amphibian passage system, setting amphibian migration inducing habitat like a micro pool group and a migration corridor, setting amphibian migration corridor protection facilities like C-shaped structures, structures easy for amphibians to go in an out and warning signs, and evaluating effect of the amphibian passage system. By the highway amphibian passage system, comprehensive functions of realizing water diversion and allowing the amphibians to go through can be realized at the same time and do not interfere each other, and needs for passing through of part of reptiles and small-medium-sized mammals can be met. The method can be used for optimizing the highway amphibian passage system of reconstructed and extended highways and can be used for guiding setting of the highway amphibian passage system of new highways.
Owner:CHINA ACAD OF TRANSPORTATION SCI
Digital signal controller secure memory partitioning
InactiveCN1954302AAvoid changePrevent discoveryUnauthorized memory use protectionCode segmentOperant conditioning
A controller offers various security modes for protecting program code and data stored in memory and ensuring that the protection is effective during all normal operating conditions of the controller. The controller includes configuration settings that segment program memory into a boot segment, a secure segment and a general segment, each with a particular level of security including no enhanced protection. The boot code segment (BS) is the most secure and may be used to store a secure boot loader. The secure code segment (SS) is useful for storing proprietary algorithms from third parties, such as algorithms for separating ambient noise from speech in speech recognition applications. The general code segment (GS) has the least security. The controller is configured to prevent program flow changes that would result in program code stored in high security segments from being accessed by program code stored in lower security segments. In addition, the processor may be configured to have associated secure data portions of both program memory, such as flash memory, and random access memory (RAM) corresponding to the BS, SS and GS. Attempts 15 to read data from or write data to the program memory or RAM associated with a higher security level from a lower security level are prevented from occurring.
Owner:MICROCHIP TECH INC
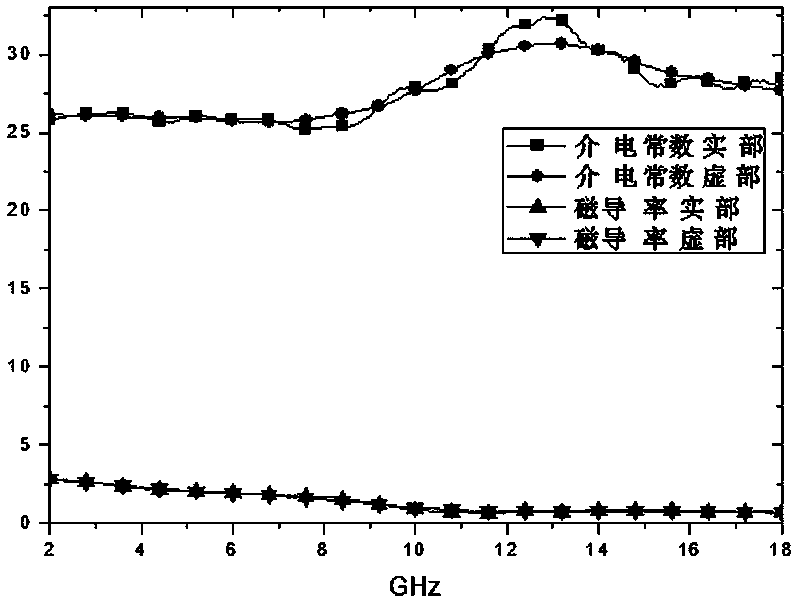
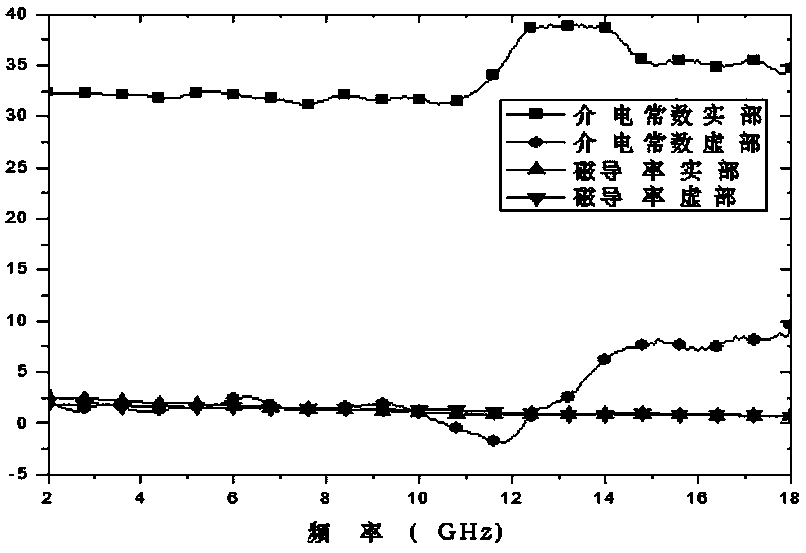
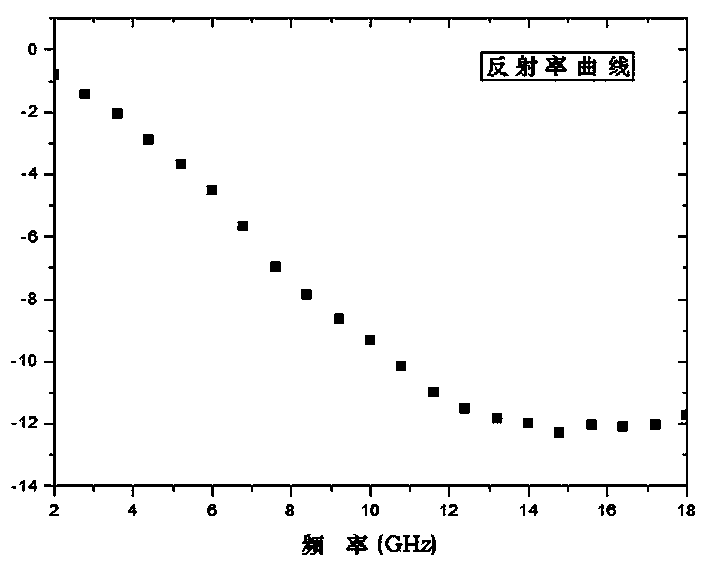
Graphene containing infrared radar compatible stealth coating and preparation method thereof
InactiveCN110054942AImprove reflective absorption performanceImprove conductivityRadiation-absorbing paintsElectrically-conductive paintsSlurrySolvent
The invention discloses a graphene containing infrared radar compatible stealth coating and a preparation method thereof. The graphene containing infrared radar compatible stealth coating comprises aresin system formed by mixing of resin, a solvent and an assistant, aluminum powder with conductivity and a radar wave reflection absorbent are dispersed in the resin system, and the radar wave reflection absorbent is composed of graphene with high dielectric constant and a magnetic absorbent. The dielectric properties of graphene are combined with electromagnetic properties of the magnetic absorbent to improve the reflection and absorption properties of the coating from two aspects of dielectric loss and electromagnetic loss, so as to achieve the effect of radar stealth' in addition, the graphene for radar absorption is dispersed among aluminum slurry particles in the resin system, the aluminum slurry particles are connected by the lamellar structure of the resin system to improve the conductivity of the coating, and low infrared emissivity is achieved; the coating can be used in high temperature radiation and radar bright spots of ships and warships, and can also be extended to ground equipment with high temperature position and radar stealth demand.
Owner:725TH RES INST OF CHINA SHIPBUILDING INDAL CORP
Transformer station secondary cable laying and cleaning protective device
ActiveCN104882829ASimple structureLow costCleaning using toolsApparatus for laying cablesTransformerEngineering
The invention provides a transformer station secondary cable laying and cleaning protective device including a mount, a clamping cleaner, and a combination connecting piece, the mount includes a body, a connecting piece, a connecting bolt, a clamping screw rod, and a clamping block, the connecting piece is connected with the body through the connecting bolt, the clamping screw rod is arranged on the connecting piece, the clamping block is connected with one end of the clamping bolt, the clamping cleaner includes a frame, a first screw rod, a second screw rod, a first extension spring, a second extension spring, a first roller brush, and a second roller brush, the first roller brush and the second roller brush are arranged on the frame through the first screw rod and the second screw rod respectively, and the first extension spring and the second extension spring connect the first screw rod and the second screw rod. When the protective device is used, the clamping cleaner is fixedly connected with the mount through the combination connecting piece. The protective device provided is simple in structure, low in cost, and convenient to carry and install; and moreover, when the protective device is used, the protective device can effectively protect civil engineering and electric equipment of a new building transformer station; and meanwhile, the protective device can further protect and clean a secondary cable itself.
Owner:CHANGZHOU POWER SUPPLY OF JIANGSU ELECTRIC POWER +2
Ethernet multipath branching unit and realization method thereof
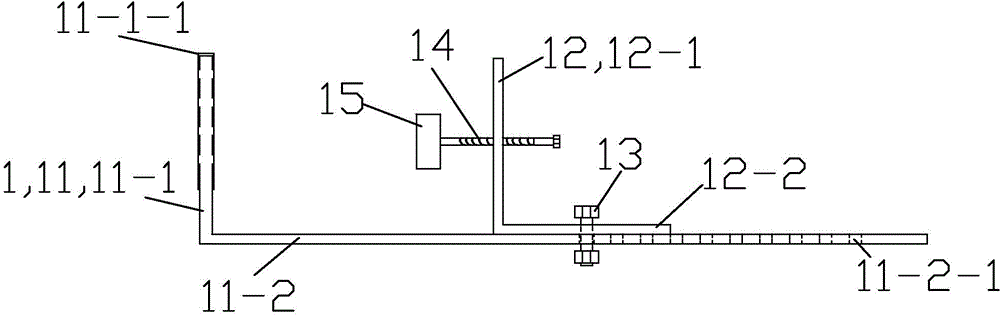
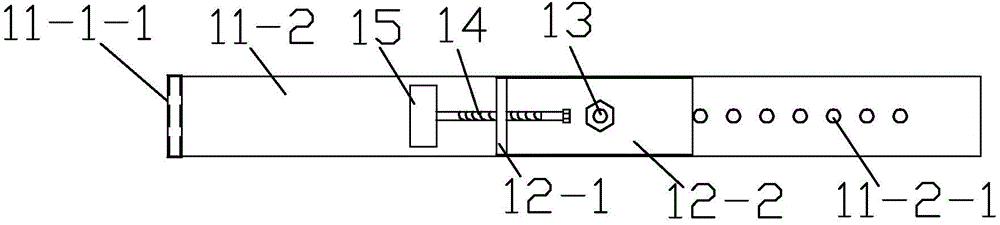
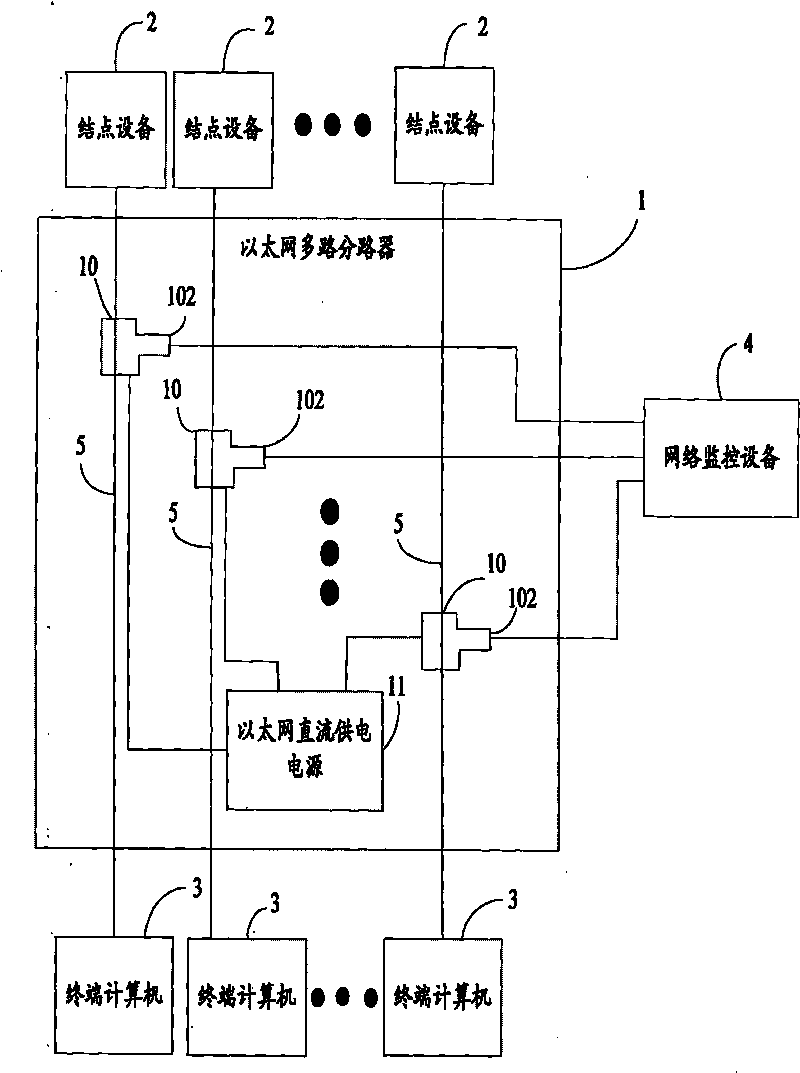
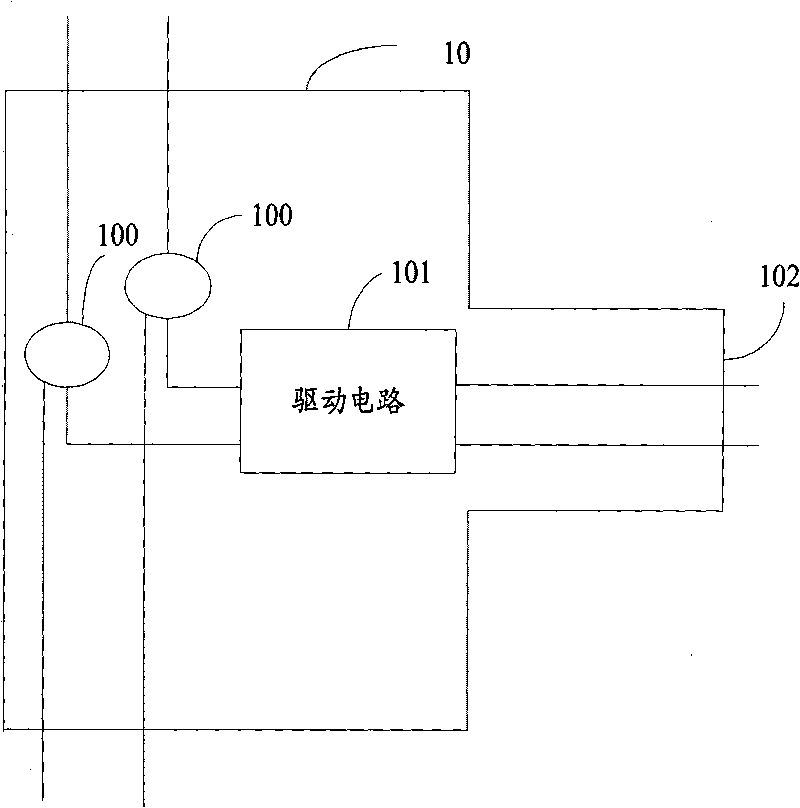
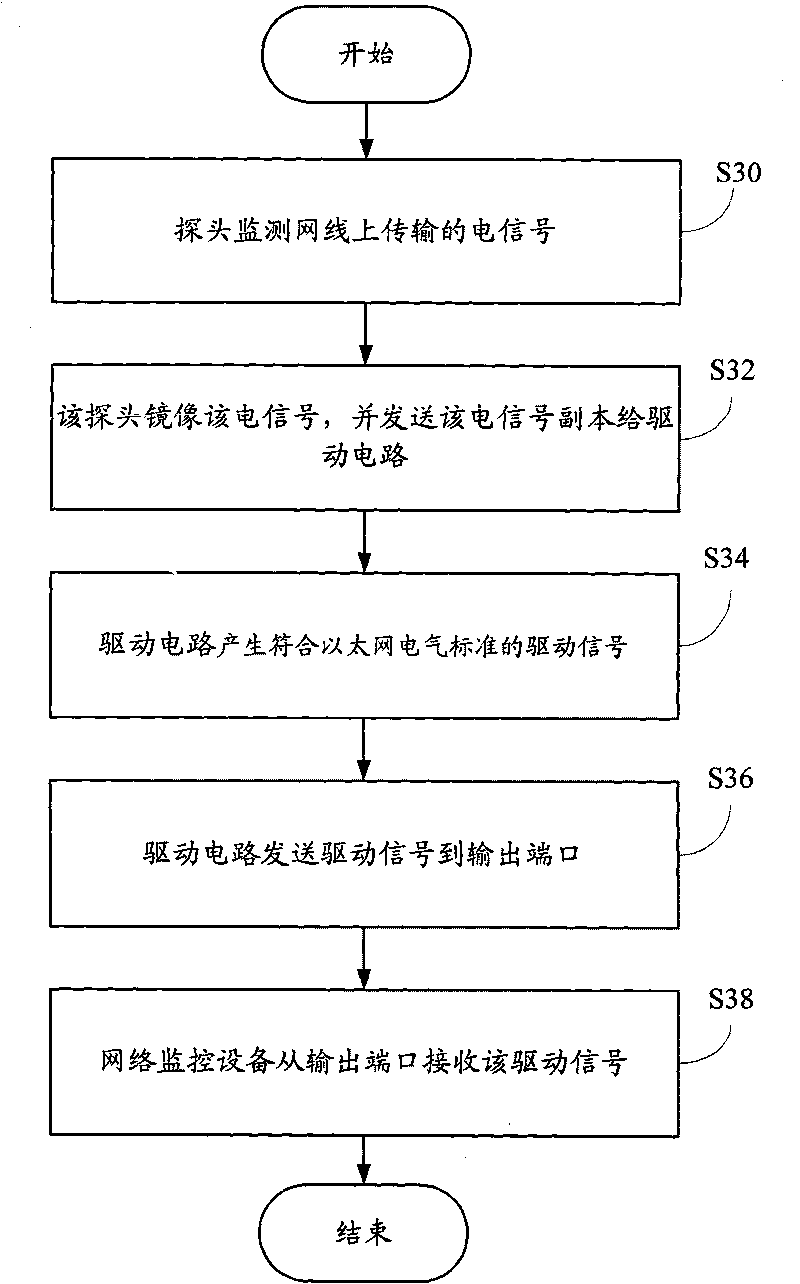
InactiveCN101741571APrevent discoveryAvoid controlData switching detailsData switching by path configurationEngineeringEthernet
The invention provides an Ethernet multipath branching method, comprising the following steps: electrical signals transmitted on a network cable are monitored by a pair of probes of each monitoring circuit; the monitored electrical signals are mirrored by the probe, the copy of the electrical signals are sent to the driving circuit connected with the probe; after being received by the driving circuit, the copy of electrical signals is followed and amplified to generate driving signals conforming to Ethernet electric standard, and the processed signal copy is sent to the output port of the monitoring circuit. The invention also provides an Ethernet multipath branching unit. The adoption of bypass switching-in and respective detection of each path can not only prevent hacker discovery and control, but also increase no fault point, thus ensuring safety of network, and solving the technical problem of network fault point increment and easy detection due to the fact that the current Ethernet multipath branching unit and the branching method are necessarily accessed through a network bridge.
Owner:PEKING UNIV SHENZHEN GRADUATE SCHOOL +1
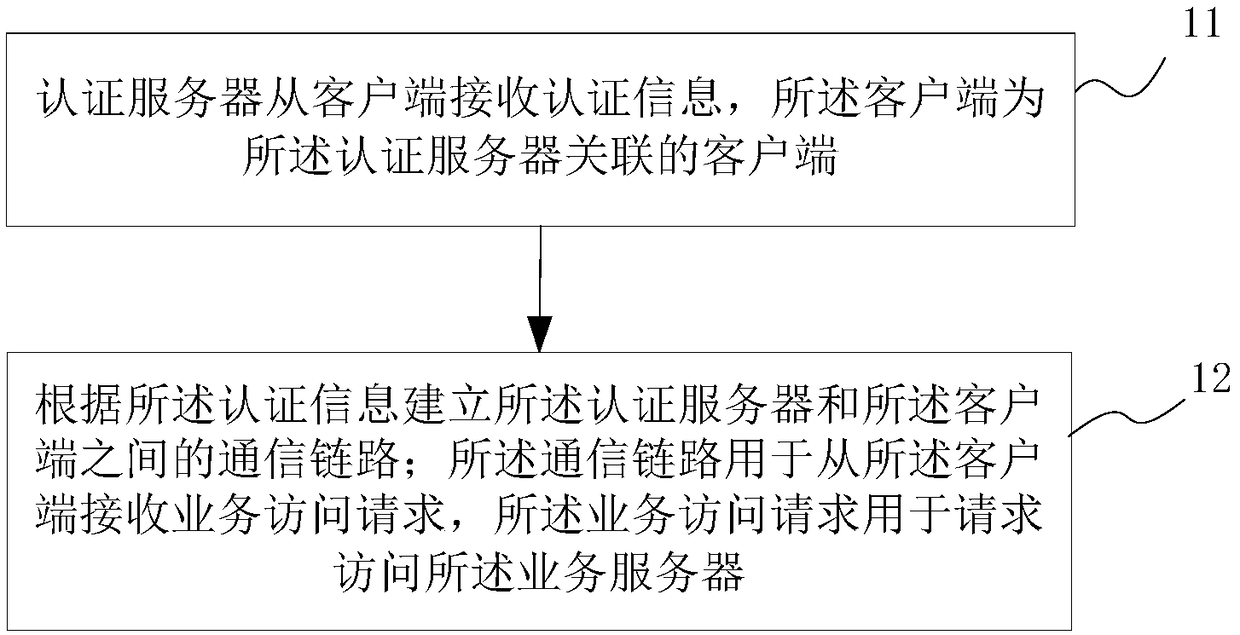
Service access method and apparatus, terminal, server and storage medium
InactiveCN109309684AAvoid detection or attackAccess does not affectTransmissionService systemClient-side
The embodiment of the invention discloses a service access method and apparatus, a terminal, a server and a storage medium. The service access method comprises the following steps: receiving, by an authentication server, authentication information from a client, wherein the client is a client associated with the authentication server; and establishing a communication link between the authentication server and the client according to the authentication information, wherein the communication link is used for receiving a service access request from the client, and the service access request is used for requesting to access the service server. The service access method and apparatus disclosed by the embodiment of the invention has the following advantages: a service system is hidden behind theauthentication server, the service system can always remain invisible, and the hidden service system becomes an invisible boundary; and a user can access the service system through the communicationlink between the client and the authentication server, thereby preventing the service system from being discovered or attacked without affecting the access to the service system by the server.
Owner:MEITONGYUNDONG BEIJING TECH CO LTD
Method and device for automatically auditing business receipts of ERP financial system
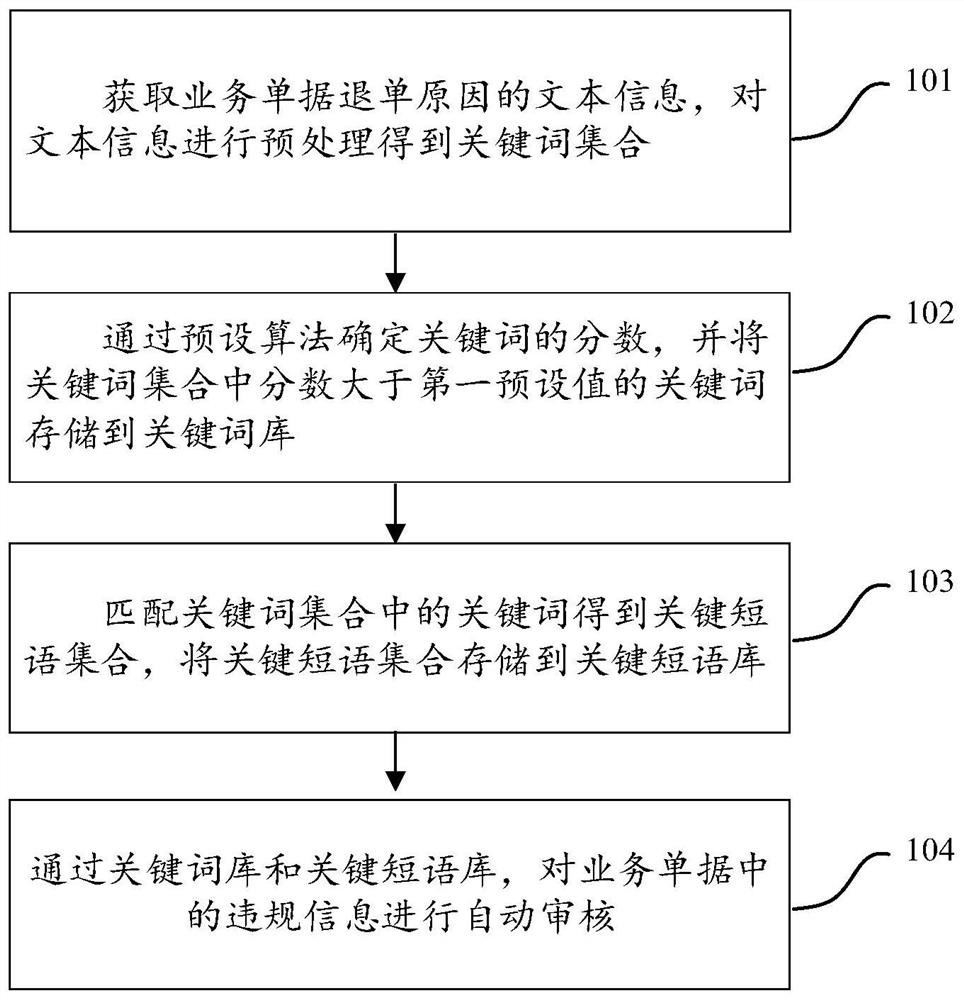
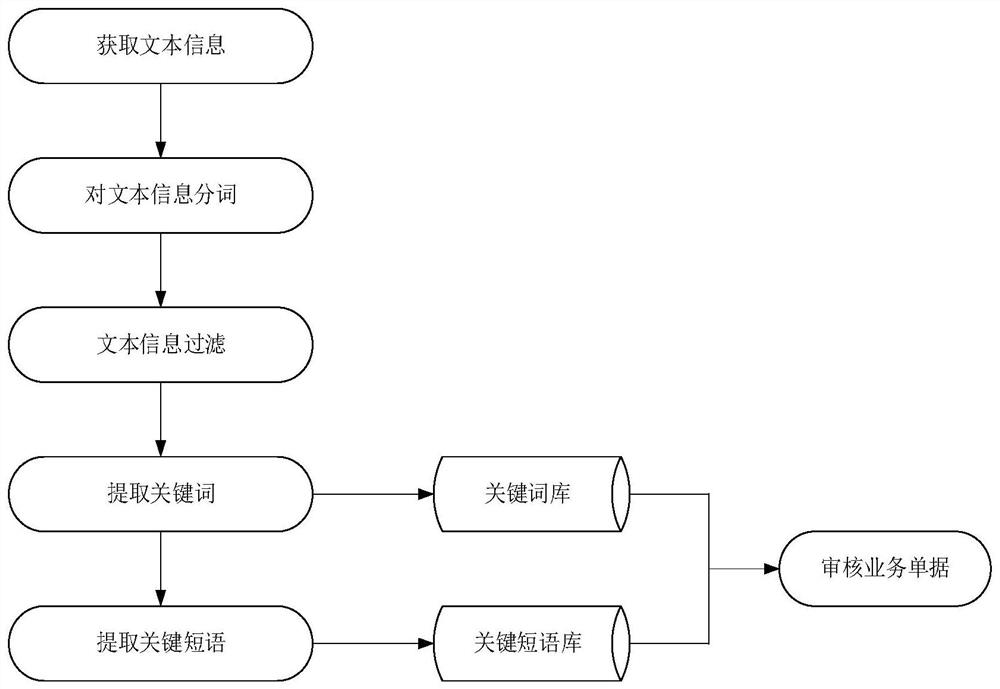
PendingCN112364645APrevent discoveryShorten the timeFinanceNatural language data processingData miningOperations research
The invention discloses a method and device for automatically auditing business receipts of an ERP financial system, and aims to solve the problem that efficiency and accuracy of a business processingprocess are seriously affected due to the fact that auditing personnel spend a large amount of time in checking the business receipts in a manual recognition mode and some wrong receipts are discovered during financial settlement. The method comprises the following steps: obtaining text information of a business receipt returning reason, and preprocessing the text information to obtain a keywordset; determining scores of the keywords through a preset algorithm, and storing the keywords of which the scores are greater than a first preset value in the keyword set into a keyword library; matching keywords in the keyword set to obtain a key phrase set, and storing the key phrase set into a key phrase library; and automatically auditing violation information in the business document through the keyword library and the key phrase library. Error receipts caused by manual auditing of auditors are reduced, and auditing efficiency and accuracy of the auditors are greatly improved.
Owner:INSPUR COMMON SOFTWARE
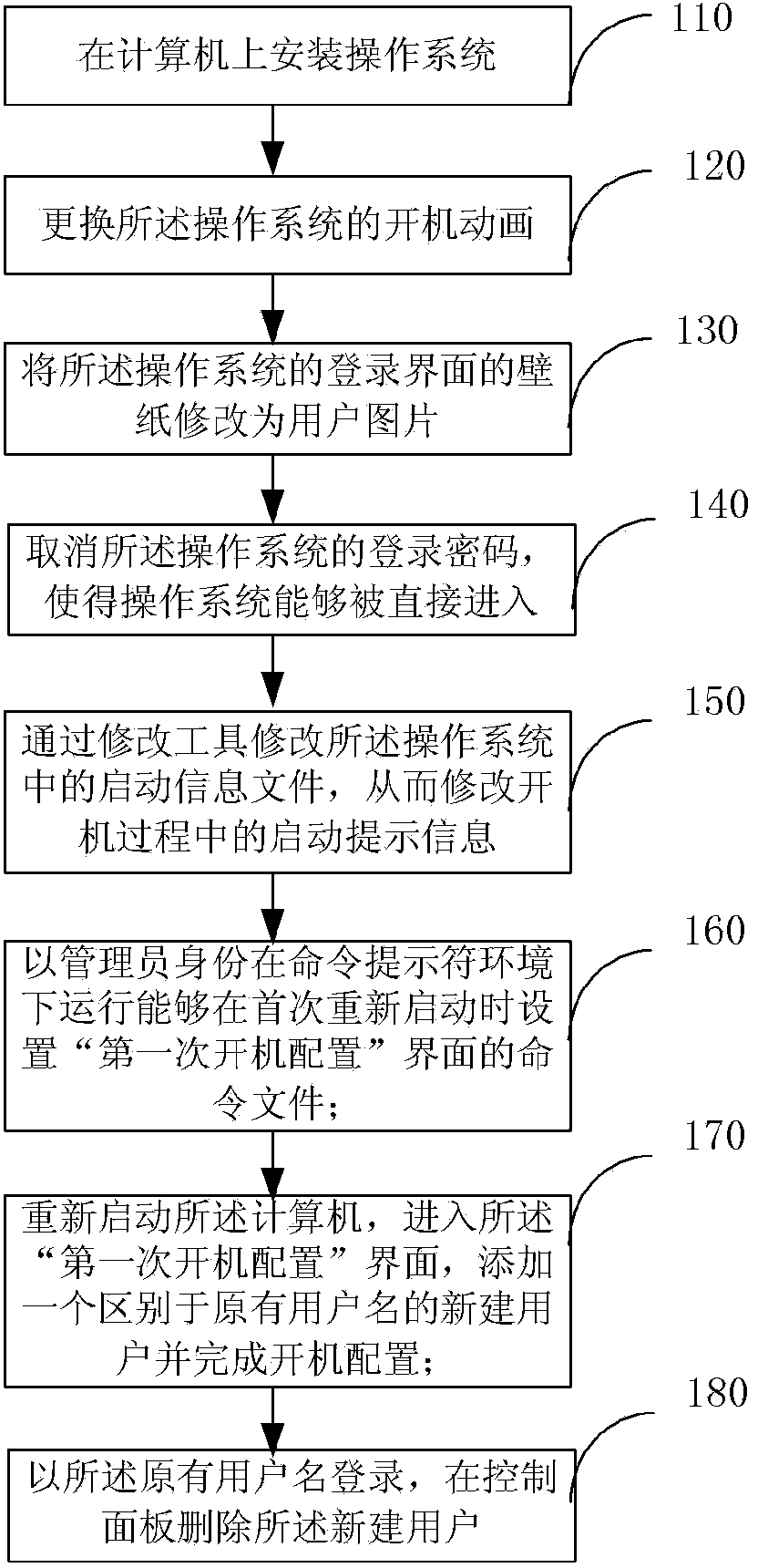
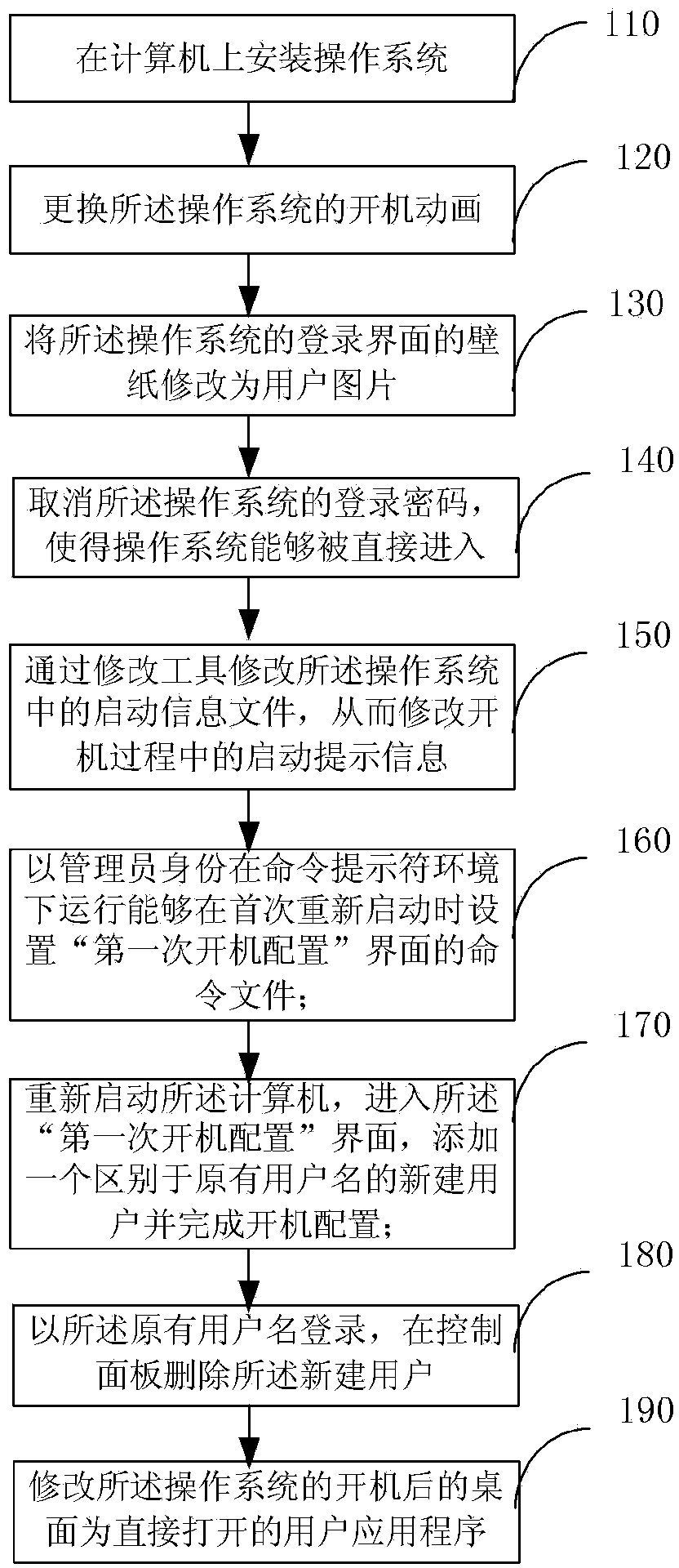
Customization method for computer starting process and computer
InactiveCN103559050AMaintain information securityUnify and enhance the imageDigital data protectionProgram loading/initiatingPersonalizationOperational system
The invention provides a customization method for a computer starting process and a computer. The method includes A. installing an operation system on the computer; B. replacing starting animation of the operation system; C. changing wall paper of a login interface of the operation system into a user picture; D; canceling a login password; E. modifying a starting information file in the operation system to modify starting prompt information; F. operating a command file capable of setting a first-time starting configuration interface during first-time restarting under the command prompt environment in the identity of an administrator; G. restarting the computer, entering the first-time starting configuration interface, adding a newly-built user different from an original user name and finishing starting configuration; H. logging in the system through the original user name and deleting the newly-built user in a control panel. By means of the method, users can hide the operation system information of themselves, system safety and confidentiality are improved, a personalized starting process can be provided, and a user image is improved.
Owner:TVMINING BEIJING MEDIA TECH
Community discovery method based on local optimization
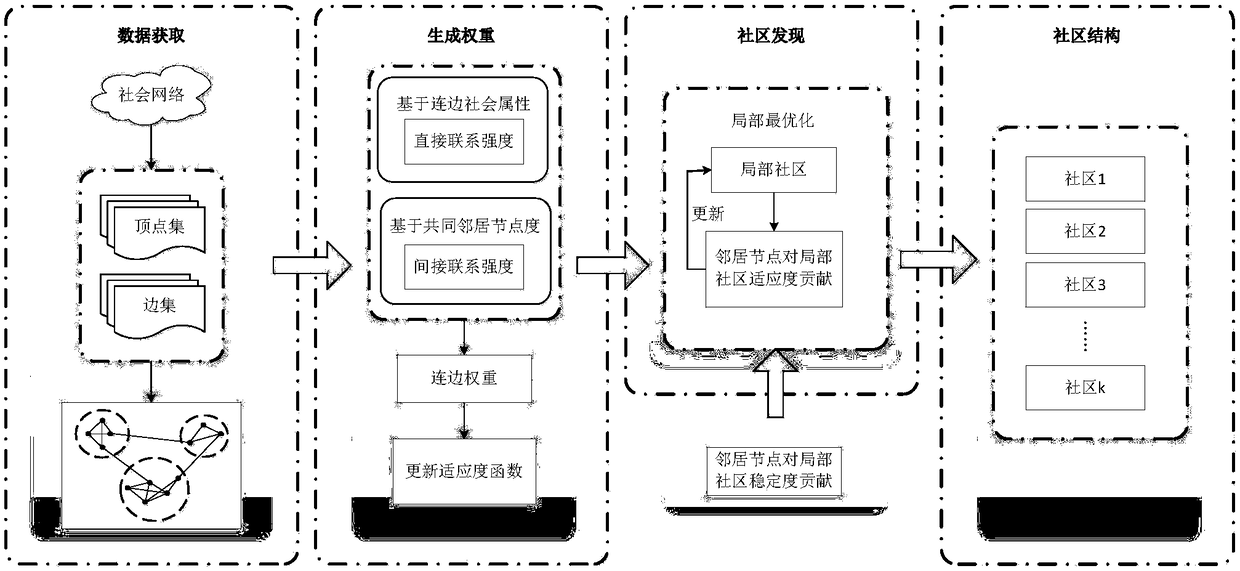
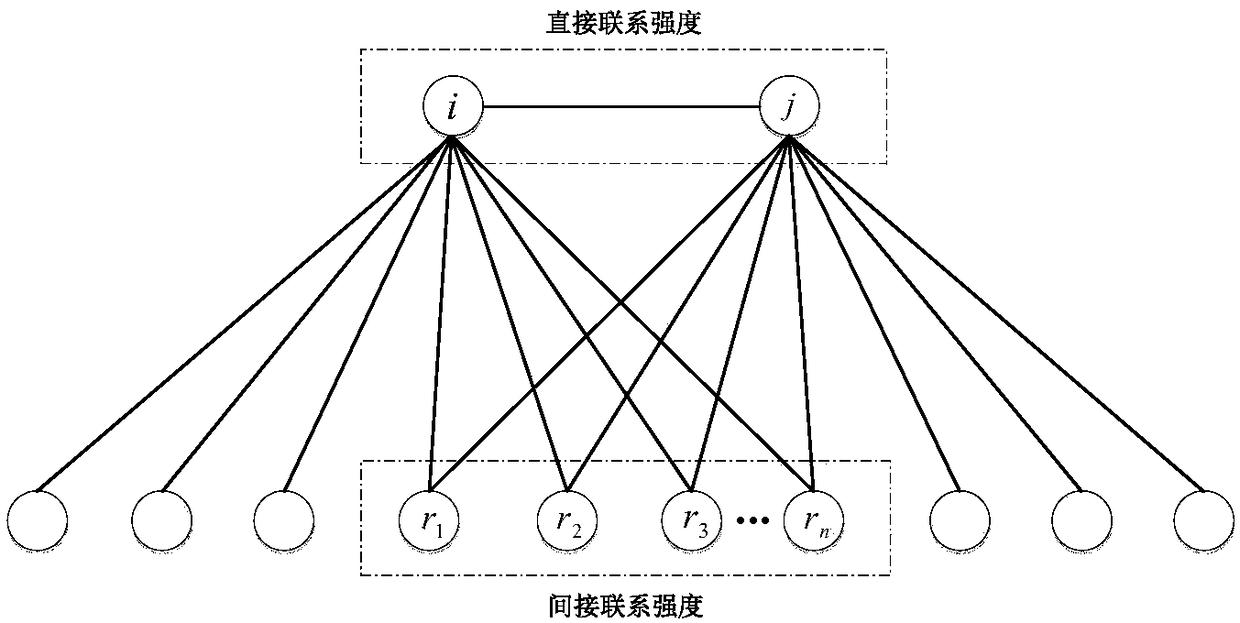
InactiveCN108400889ASlow down the expansion rateStabilize community structureData processing applicationsData switching networksLocal optimumSocial network
The invention relates to the community discovery field in a complex network, and specifically discloses a community discovery method based on local optimization. On the basis of an LFM (Local FitnessMaximum) algorithm, on the one hand, a weighting method for integrating internodal boundary social attribute with common neighbor node degree in the network is proposed, and a fitness function in theLFM algorithm is updated by using the formed boundary weight; on the other hand, the concept about the local community stability is imported into the local optimization process of the LFM algorithm, the contribution degree on the community stability by the node is judged by computing the community stability before and after the node adds in the local community, and the contribution degree is usedas the criterion whether the node is added in the community. Through the method disclosed by the invention, the appearance of the over-sized community is avoided, the more significant groupuscule structure in the network can be easily discovered, and the method is suitable for the real social network.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Super high-rise building fire extinguishing device
The invention provides a super high-rise building fire extinguishing device, the super high-rise building fire extinguishing device comprises fire-fighting pipes arranged in a high-rise building, fire-fighting outlet pipes disposed at the fire-fighting pipes of floors, pipeline storage mechanisms disposed at the fire-fighting outlet pipes, walking mechanisms disposed at the front ends of the pipeline storage mechanisms, water spray mechanisms which are arranged on the walking mechanisms and communicated with the pipeline storage mechanisms, identification modules provided on the walking mechanisms, obstacle breaking mechanisms for breaking obstacles which are arranged on the walking mechanisms, righting mechanisms for righting which are arranged on the walking mechanisms, and control mechanisms disposed on the walking mechanisms; the super high-rise building fire extinguishing device is capable of waiting online all the time, and capable of crossing the obstacles or breaking the obstacles, and directly extinguishes a fire aiming at the point of fire, when dumped, the super high-rise building fire extinguishing device resets and keeps on moving, can extinguish the fire in the earlystage of the fire, avoids greater economic and personnel losses, and avoids the potential danger of firefighters entering the fire.
Owner:张桂华
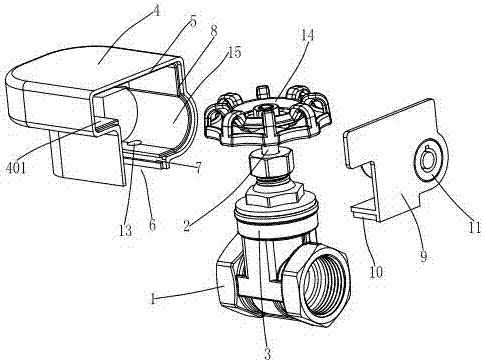
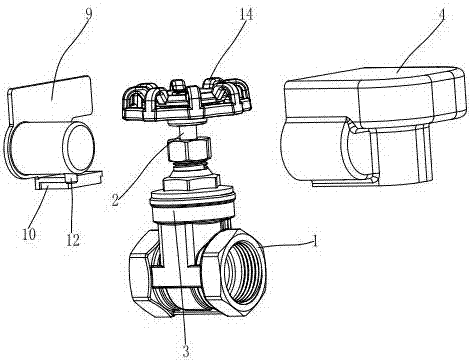
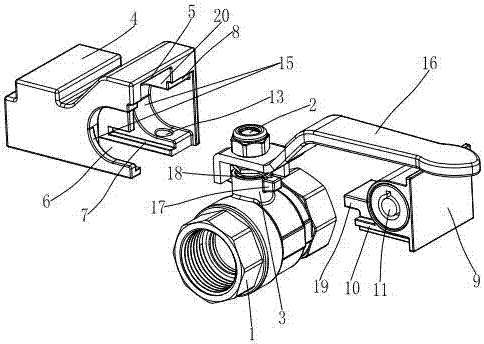
Locking valve
ActiveCN107131337AAvoid accidentsPrevent discoveryOperating means/releasing devices for valvesValve housingsValve stemVALVE PORT
A locking valve comprises a valve body, an opening and closing member arranged in the valve body and a valve stem connected with the opening and closing member. A middle hole is formed in the valve body, one end of the valve stem penetrates out of the middle hole and is connected with a valve switch, the valve body is covered with a protective cover, an opening is formed in one side of the protective cover, and the valve switch, the middle hole and the valve stem penetrating out of the middle hole are all located in the protective cover. A U-shaped opening is formed in the bottom of the protective cover. Symmetrical sliding ways are arranged on the two sides of the U-shaped opening. A mounting step is arranged on the opening. The mounting step is covered with a cover plate. The opening is covered and closed with the cover plate. A sliding seat matched with the sliding ways is arranged at the bottom of the cover plate. By the adoption of the locking valve, when the valve switch is locked, a lock cylinder and a lock hole can be hidden, damage to the lock cylinder and the lock hole by strangers is avoided, extrusion and damage to the valve switch is avoided in the valve switch locking process, and the service life of the valve is guaranteed.
Owner:名盾有限公司
Sound box
PendingCN107302728AEasy to hideEasy to useTelevision system detailsColor television detailsEngineeringCamera module
The invention discloses a sound box. The sound box comprises a casing and a master control board; the casing comprises an upper cover, a transparent light ring and a bottom casing; the transparent light ring is fixed to the upper part of the bottom casing; the upper cover covers the transparent light ring; a camera module is arranged in the casing; the master control board controls the rotation of the camera module; the position of the camera module corresponds to the position of the transparent light ring. According to the sound box disclosed by the invention, the camera module is hidden in the casing so as to be prevented from being discovered or damaged; moreover, the position of the camera module corresponds to the position of the transparent light ring, so that image signals outside the casing can be acquired through the transparent light ring, and normal use of the camera module is ensured; the master control board controls the rotation of the camera module, signals around the outside of the casing are acquired through the transparent light ring; the sound box disclosed by the invention facilitates hiding of the camera module, and also ensures the camera module functions of normally shooting images and videos.
Owner:GEER TECH CO LTD
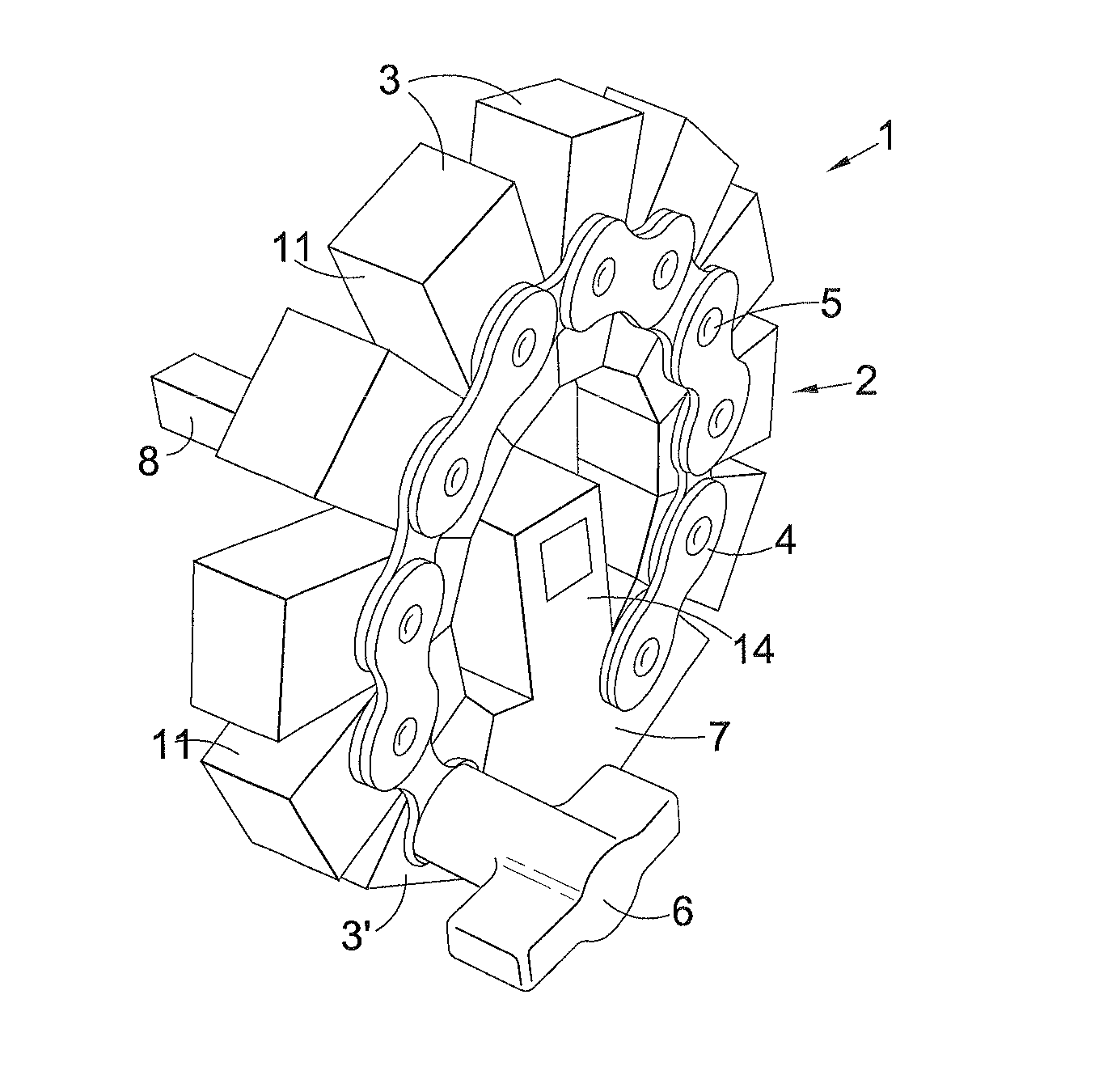
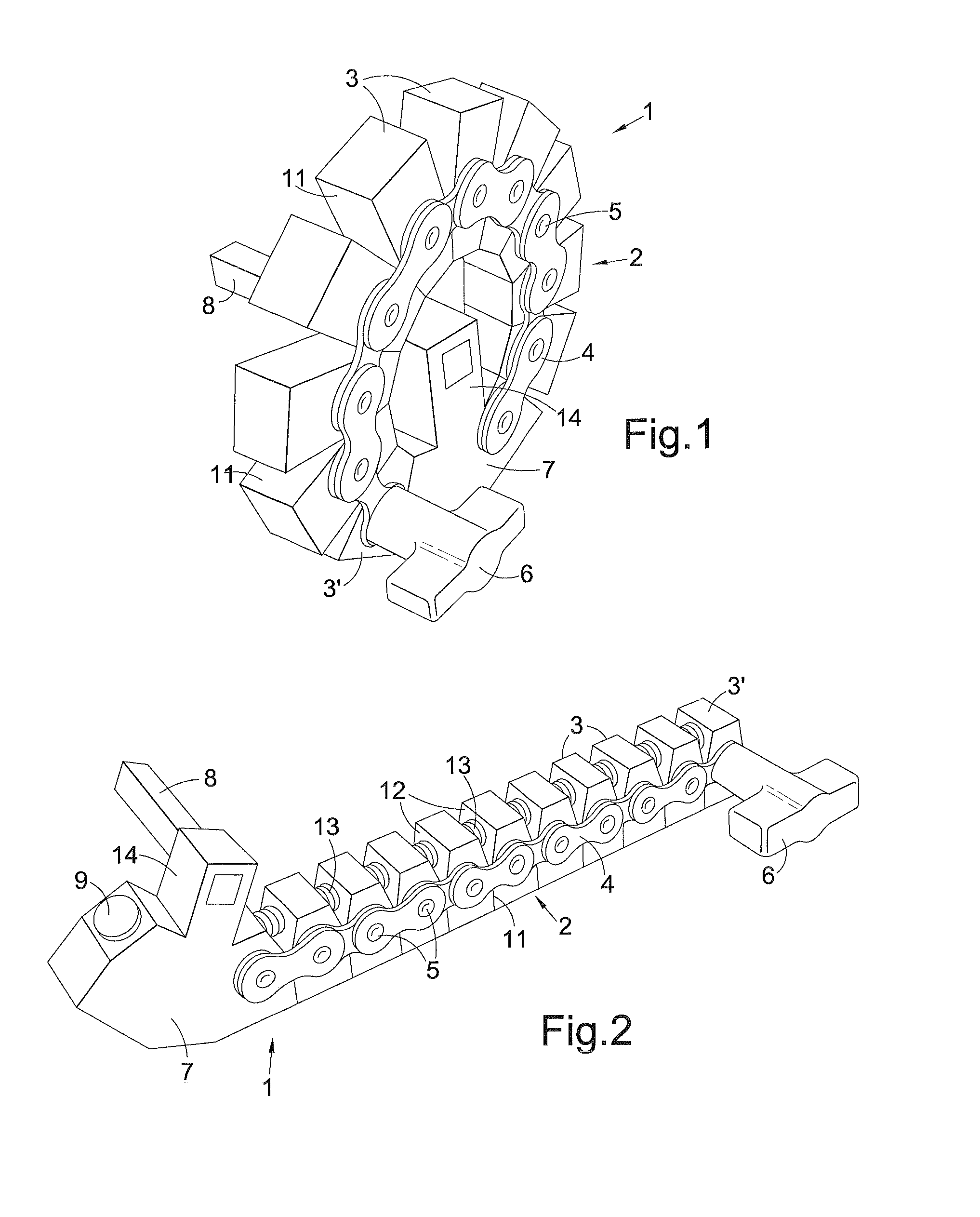
Variable radius lever arm assembly
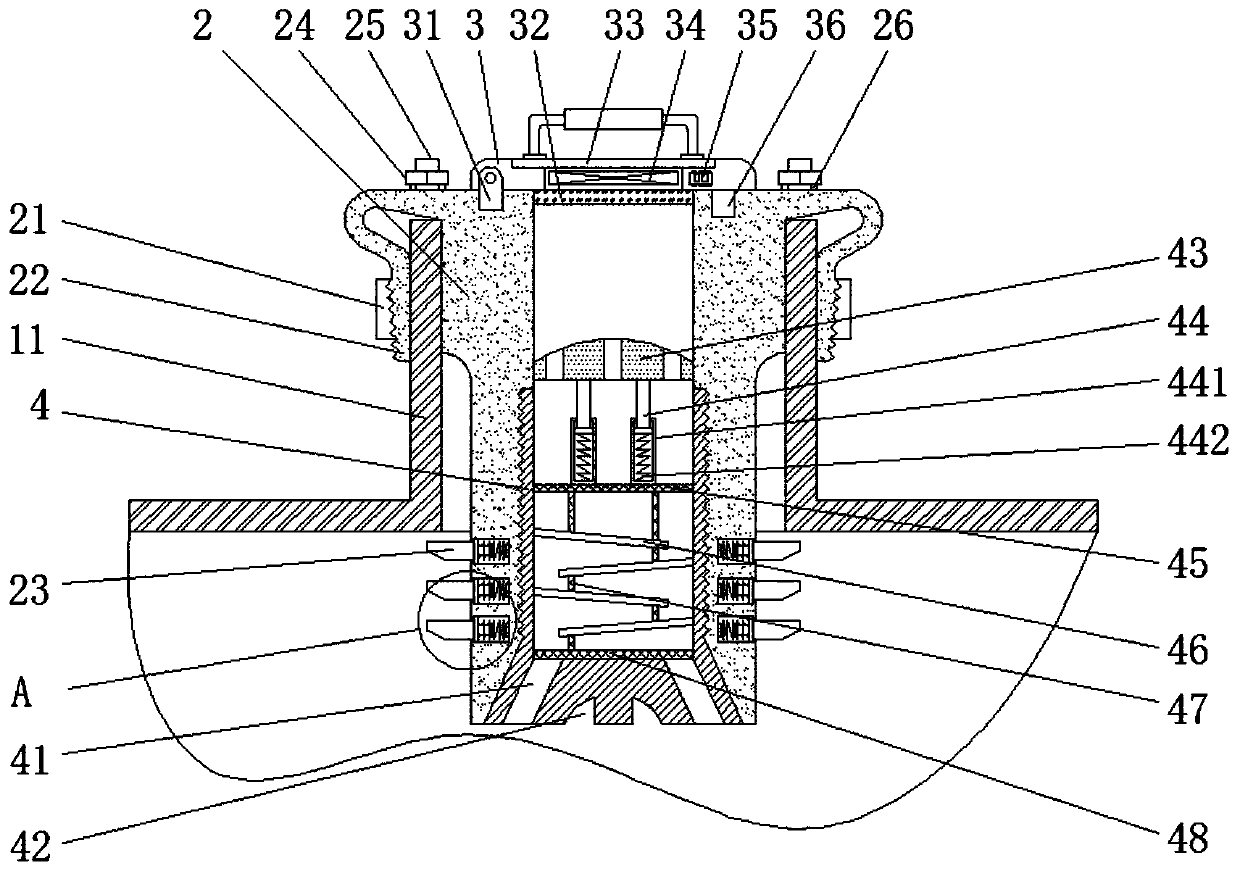
InactiveUS20140216199A1Increase static frictionPrevent discoveryControlling membersLeversJackscrewEffective length
A curled variable radius lever comprises a lever arm of variable effective length that curls and uncurls about a drive axis. In a preferred arrangement the lever assembly has a plurality of rigid blocks linked together by a chain or spring steel strip. Each block has a pair of walls 11 that face and abut each other in an uncurled, straightened state of the lever arm. The abutment of the walls of the lever arm rigidifies the arm and prevents the arm from bending further in the direction of uncurling when a driving force is applied by users to a handle. The lever may be used with socket sets, yacht winch, fishing rod reel, a bicycle crank or a jack assembly.
Owner:MALTBY MALORY
Speed measurement snapshot mechanism with hiding function based on road traffic man-made damage prevention
InactiveCN112435483APlay a concealed effectPrevent discoveryDetection of traffic movementTraffic signalsCar drivingDriver/operator
The invention provides a speed measurement snapshot mechanism with a hiding function based on road traffic man-made damage prevention, and relates to the technical field of speed measurement snapshot.The problems that an existing mobile traffic radar speed measurement snapshot instrument is placed on one side of a road excessively obviously, the speed measurement snapshot effect is poor, and an automobile driver can clearly observe the position of the traffic radar speed measurement snapshot instrument at a distance are solved. The speed measurement snapshot mechanism with the hiding functionbased on road traffic artificial damage prevention comprises a square cone, a square buckle cover is slidably connected to the bottom end face of the square cone, and a warning shell matched with thesquare buckle cover in an inserted mode is embedded in the bottom end face of the square cone. The speed measurement snapshot mechanism is small in size and convenient to move and has a hiding function, a vehicle driver cannot observe the speed measurement snapshot mechanism remotely, and therefore the speed measurement snapshot mechanism can effectively measure the speed and snapshot illegal vehicles which do not normally run according to traffic rules.
Owner:孙正梅
Portable folding oil tank oil level detection control system and method for transformer
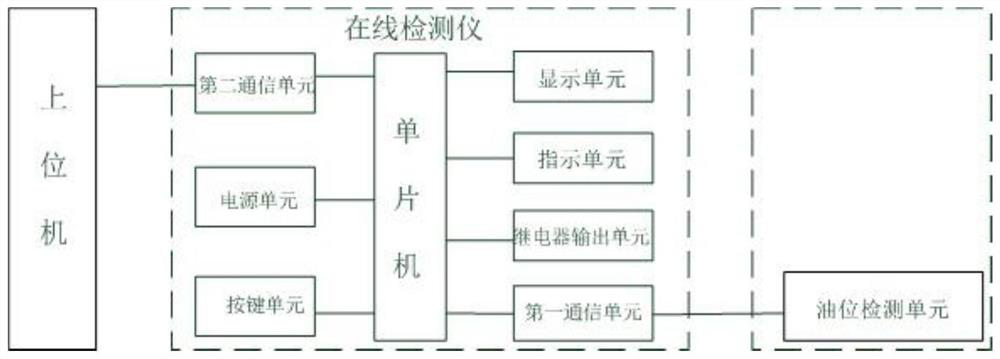
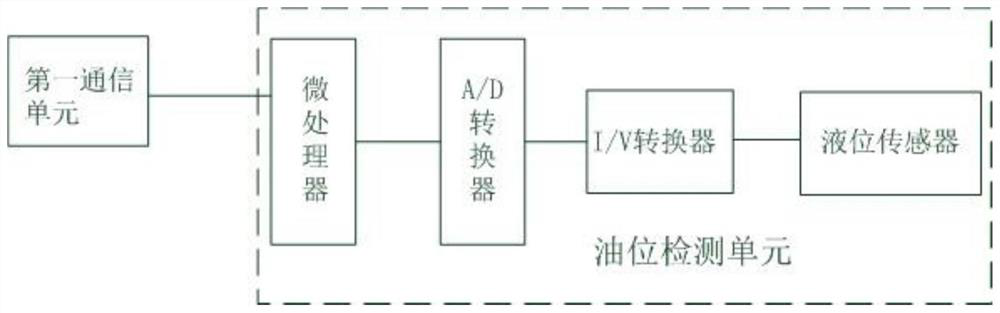
PendingCN112099416AConditions affecting normal useReal-time control of liquid level statusProgramme controlComputer controlControl systemData information
The invention discloses a portable folding oil tank oil level detection control system and method for a transformer, and the system comprises: an oil level monitoring unit which is used for monitoringthe liquid level data information of insulating oil in an oil storage tank in real time; an on-line detector which is connected with the oil storage tanks and used for receiving and displaying the liquid level data information of the oil storage tanks, processing and analyzing the liquid level data information and controlling the oil storage tanks to be opened or closed according to the control instruction; and an upper computer which is connected with the online detector and is used for receiving and storing the liquid level data information and sending a first control instruction to the online detector. According to the portable folding oil tank oil level detection control system and method for the transformer, the oil level in the oil storage tank for each transformer can be automatically monitored in real time, use is convenient, real-time and labor-saving is achieved, the management and efficiency and the use efficiency of the oil storage tank for each station transformer are improved, great convenience is brought to a user, and good popularization and application values are achieved.
Owner:STATE GRID HUBEI ELECTRIC POWER CO XIAOGAN POWER SUPPLY CO
A robot-based skin detection system and method
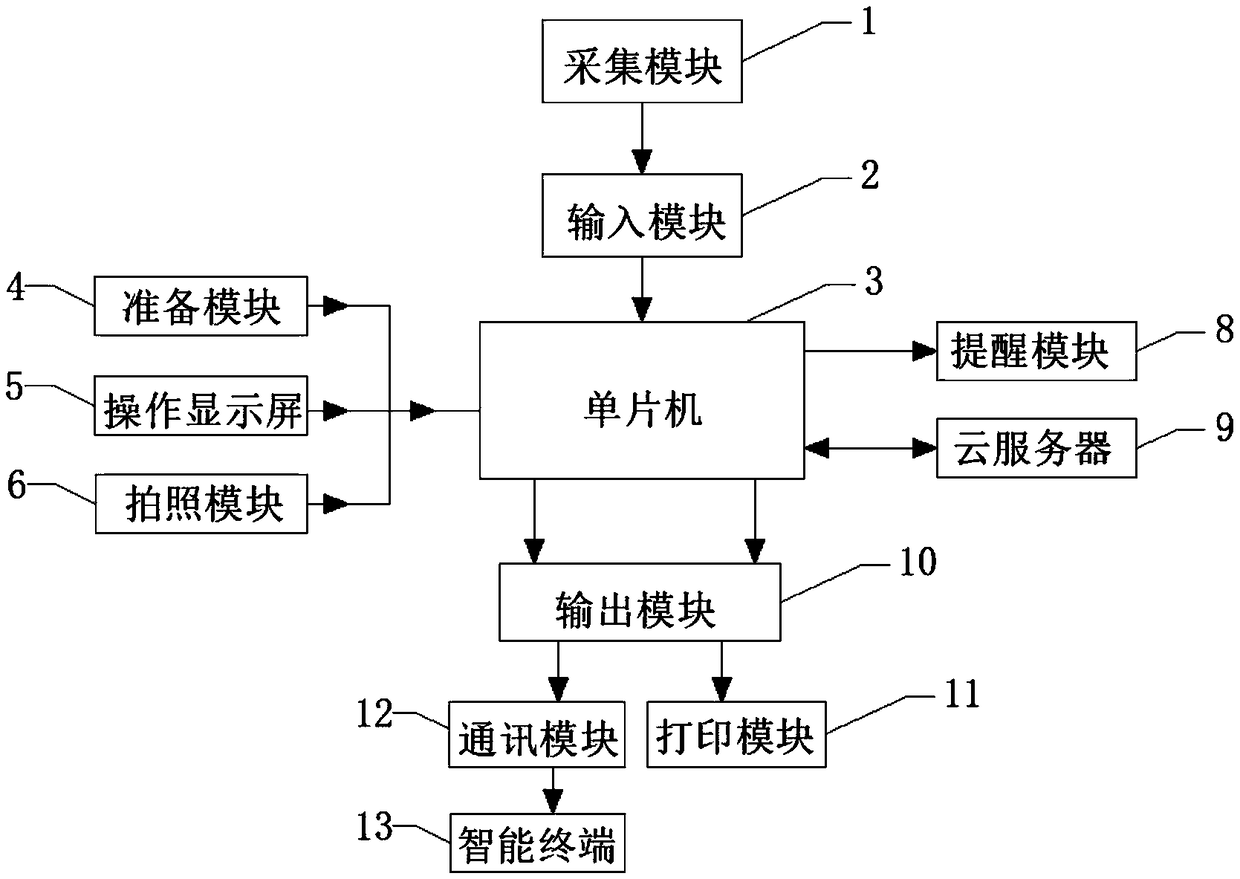
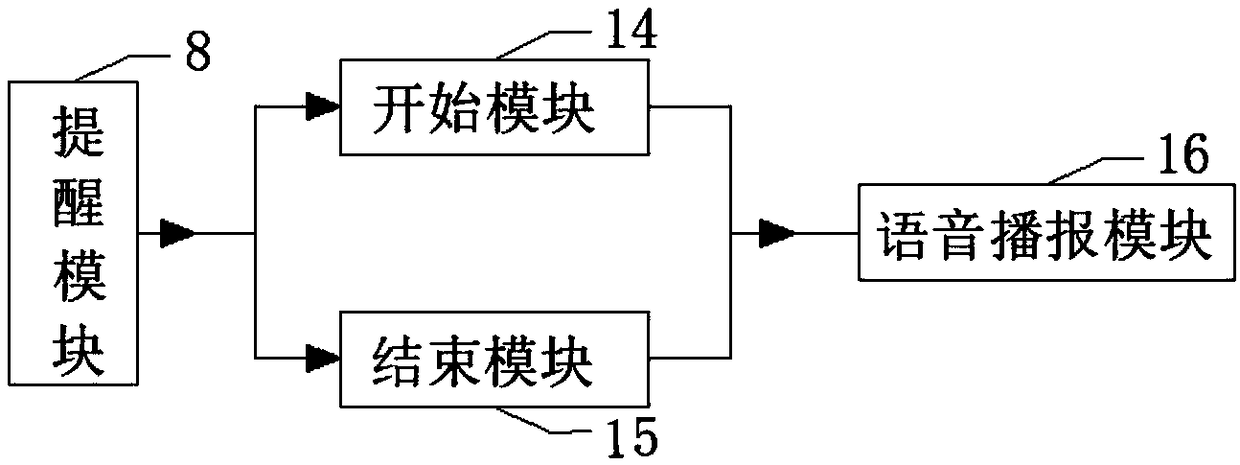
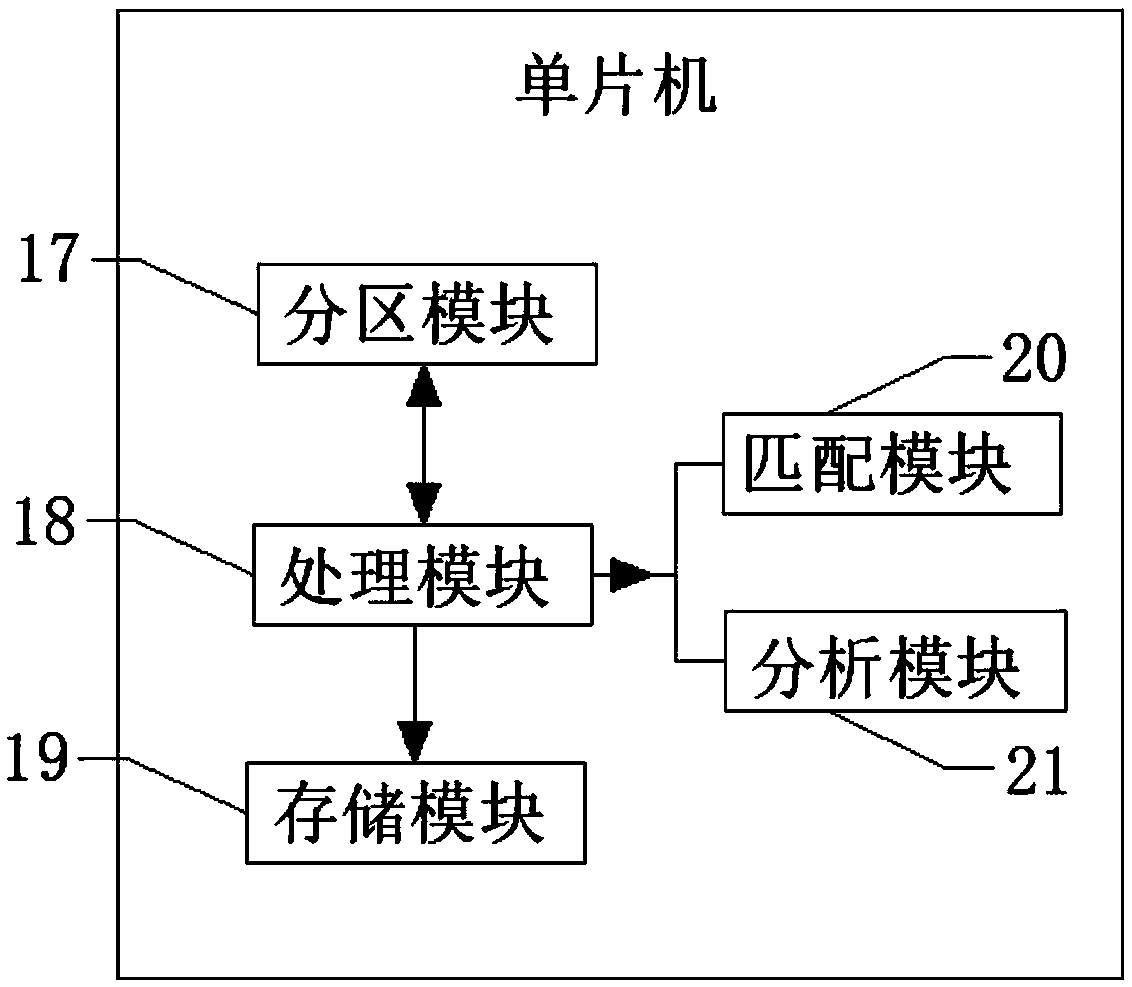
InactiveCN109124587AImprove efficiencyPrevent the discovery of duplicate namesHealth-index calculationDiagnostic recording/measuringMicrocomputerCloud server
The invention discloses a robot-based skin detection system, including an acquisition module, a MCU, a reminder module, a preparation module, a printing module, an operating display and an intelligentterminal. The single chip microcomputer is arranged in the interior of the robot, the SCM is connected with input module, the output module, the preparation module, the operating display, an imagingmodule, the reminder module and the cloud server respectively. The single-chip microcomputer is connected with an acquisition module through an input module, a communication module and a printing module through an output module, and an intelligent terminal is connected with the communication module. The single-chip microcomputer and the cloud server are connected with each other through a wirelessnetwork. The single-chip microcomputer is also provided with a zoning module, a processing module, a storage module, a matching module and an analysis module inside the single-chip microcomputer. Theskin detection system and method based on the robot are convenient for the user to use and view, improve the detection efficiency of the user, and at the same time, the skin condition of each position of the user can be instructed and suggested pertinently.
Owner:SHANGHAI CHANGREN INFORMATION TECH CO LTD
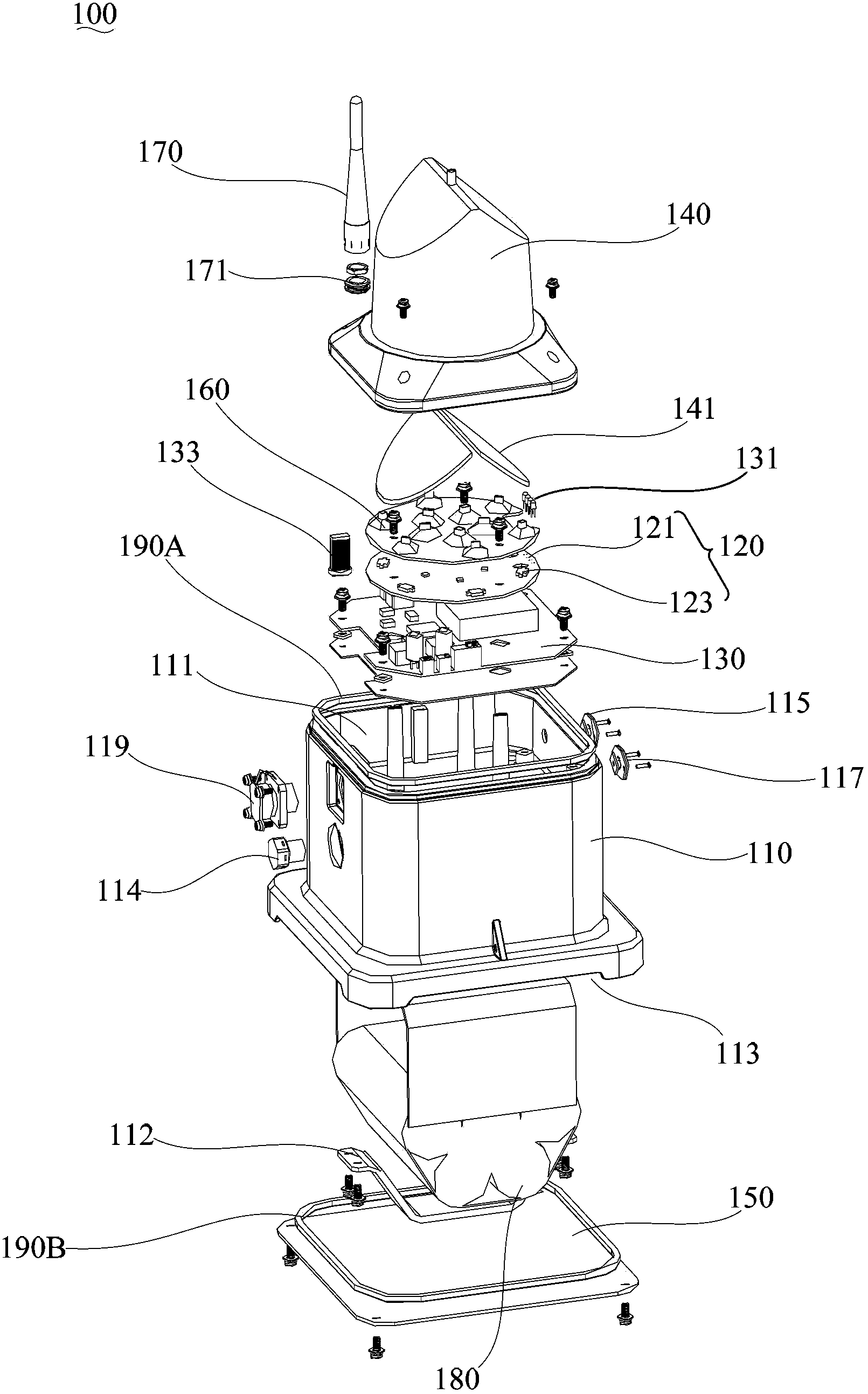
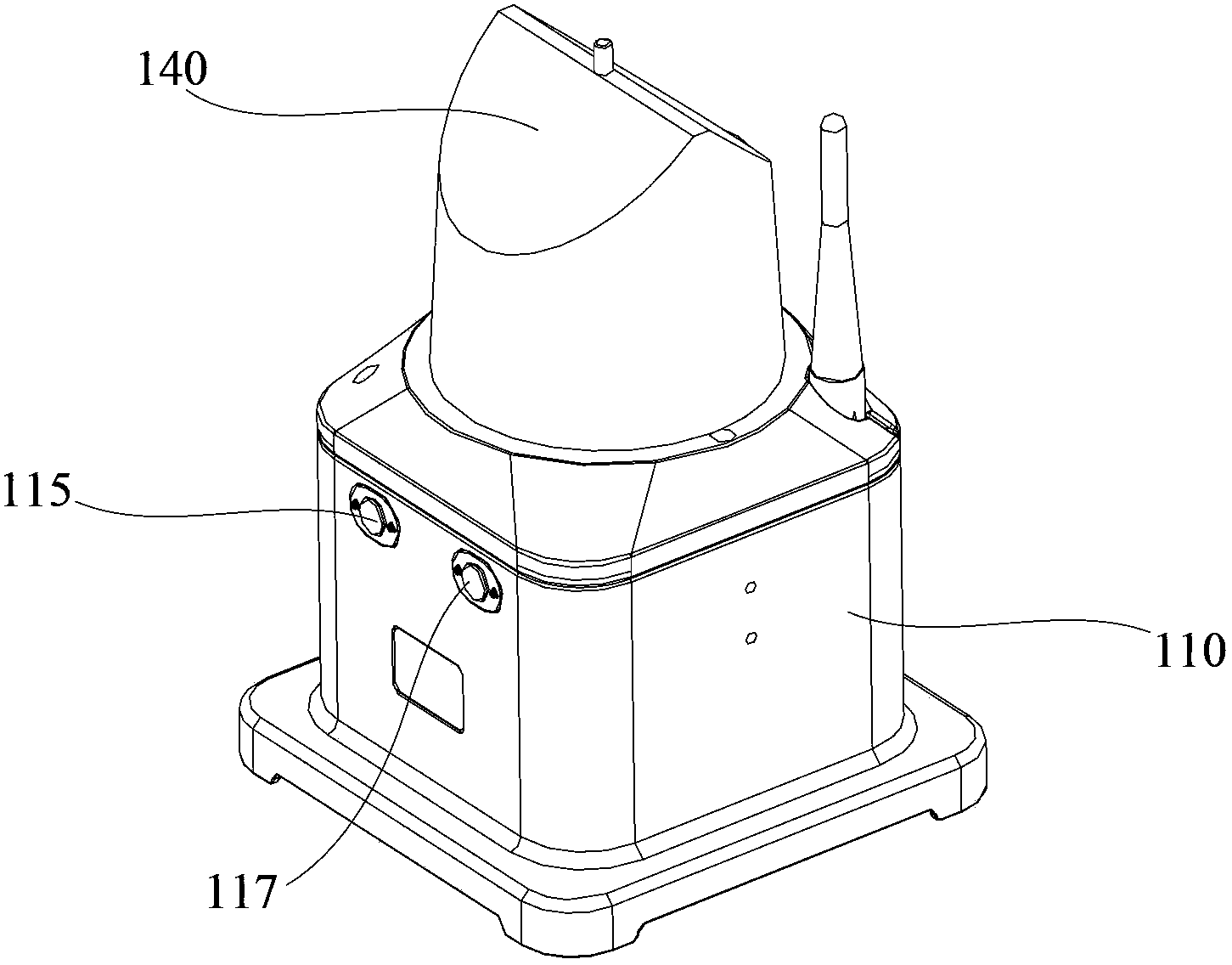
Field landing indicator lamp for helicopter
InactiveCN104071344ACompact structureReduce volumeEnergy efficient board measuresAircraft landing aidsEffect lightEngineering
The invention relates to a field landing indicator lamp for a helicopter. The indicator lamp comprises a casing, a light emitting assembly, a control circuit board and an upper transparent cover. After a battery is mounted, the light emitting assembly can emit light under the control of the control circuit board, wherein light emitted by a visible light emitter is used for lighting, and infrared light emitted by an infrared emitter is used for indicating a position. After specific equipment is arranged, the infrared light can be observed, so that the field landing indicator lamp for the helicopter can be prevented from being found by others. In addition, the light emitting assembly and the control circuit board are housed in a housing cavity formed by assembling the casing and the upper transparent cover, so that the field landing indicator lamp for the helicopter is compact in structure, less in volume, and is not easy to find in the field. Therefore, the field landing indicator lamp for the helicopter effectively improves the invisibility.
Owner:SHENZHEN OCEANS KING LIGHTING ENG CO LTD +1
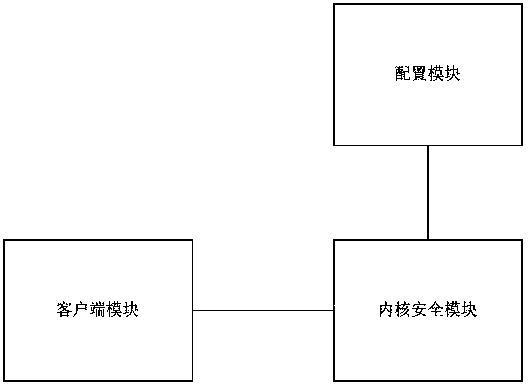
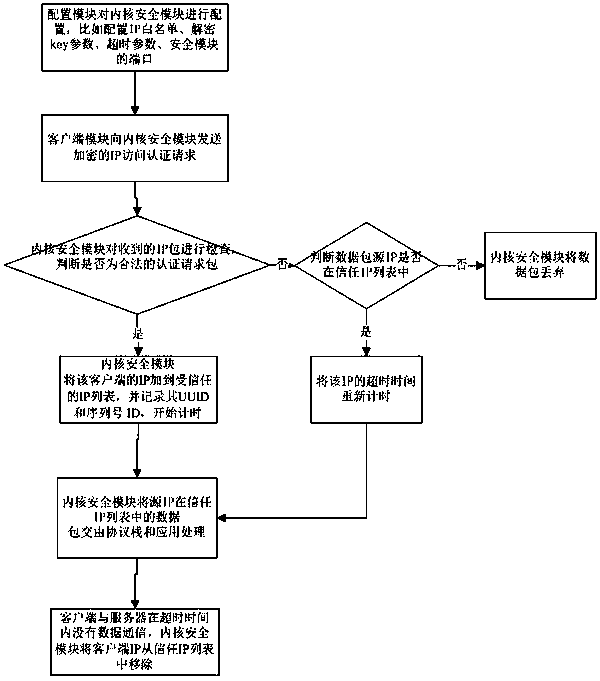
System and method for hiding host in network
The invention belongs to the field of information technology processing, and specifically relates to a system and method for hiding a host in a network. The system comprises a client module used for sending an encrypted IP access authentication request to a kernel security module; the kernel security module used for performing security authentication on a request content of the client module; a configuration module used for configuring the kernel security module; and the kernel security module and the configuration module are deployed on a server, the client module is deployed on a client, andthe kernel security module is respectively in signal connection with the configuration module and the client module. The system for hiding the host in the network provided by the invention performs access control at an IP layer, and is applicable to protection of any application host; the server responds only to a TCP connection request initiated by a trusted IP, and does not respond to a TCP connection request initiated by a non-trusted IP; and the host cannot be discovered through a port scanning mode, and no extra authentication server needs to be added.
Owner:COLASOFT
Cryptographic countermeasure method by deriving a secret data
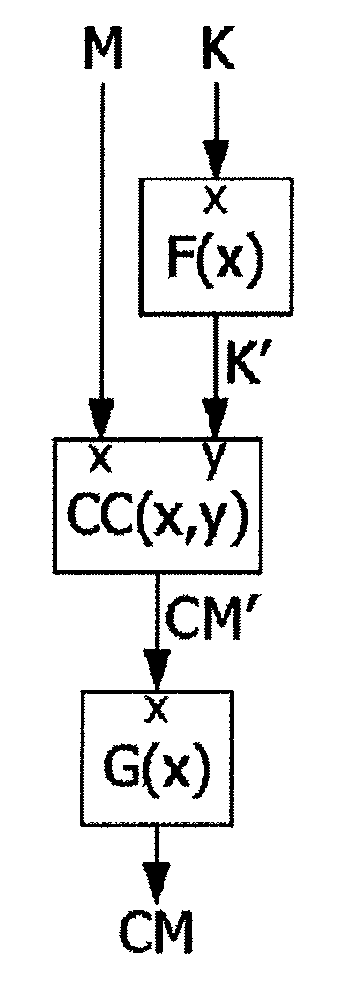
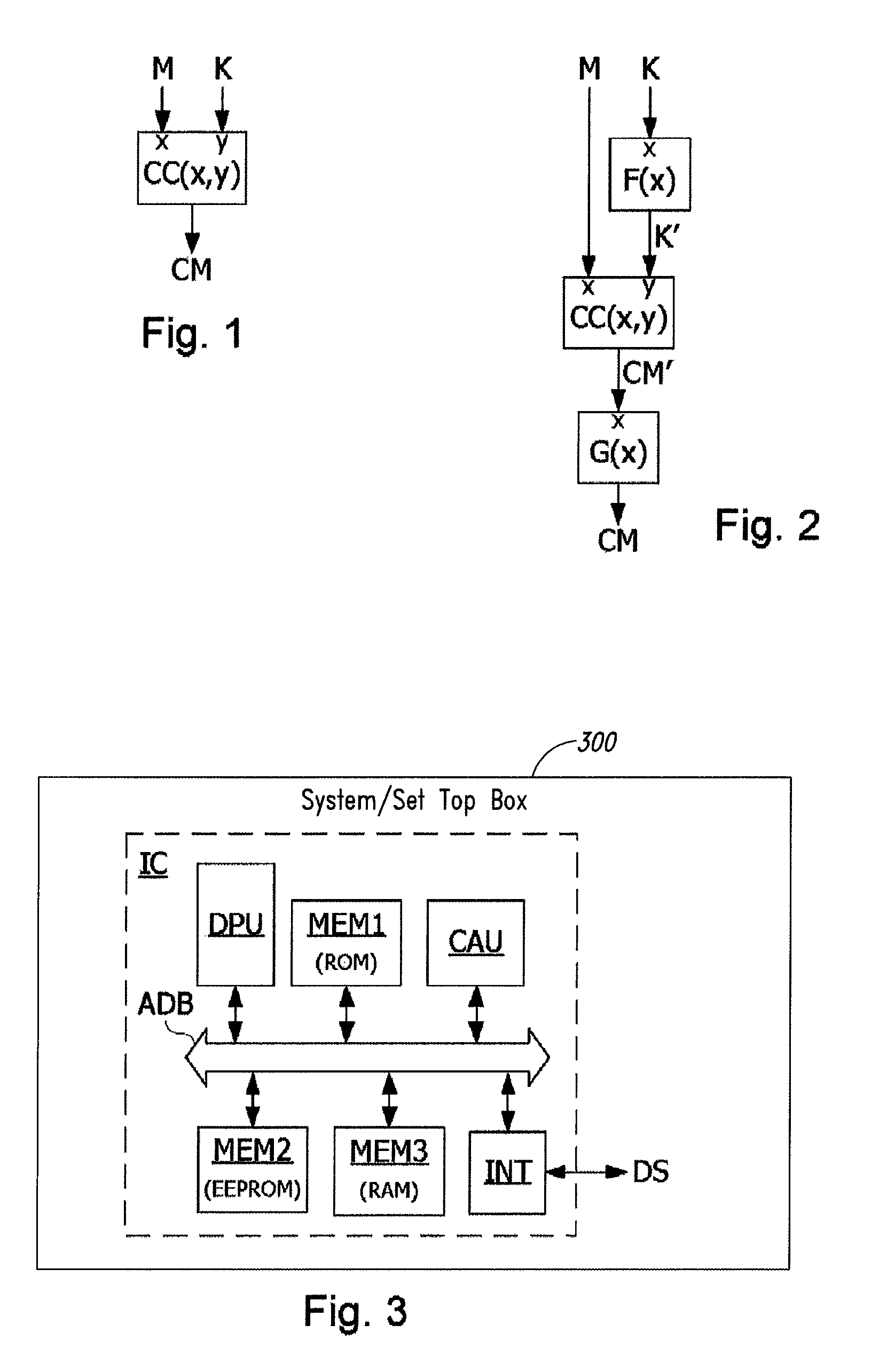
ActiveUS8666067B2Prevent discoveryData stream serial/continuous modificationPublic key for secure communicationComputer hardwareCountermeasure
A method of protecting a circuit from attacks aiming to discover secret data used during the execution of a cryptographic calculation by the circuit, by, executing a transformation calculation implementing a bijective transformation function, receiving as input a secret data, and supplying a transformed data, executing a cryptographic calculation receiving as input a data to process and the transformed data, and executing an inverse transformation calculation receiving as input the result of the cryptographic calculation, and supplying a result that the cryptographic calculation would have supplied if it had been applied to the data to process and directly to the secret data, the data to process belong to a stream of a multiplicity of data, the transformed data being supplied as input to the cryptographic calculation for all the data of the stream.
Owner:STMICROELECTRONICS (ROUSSET) SAS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com