System and method for hiding host in network
A host, network technology, applied in the field of information technology processing, can solve problems such as IP access control of network ports
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
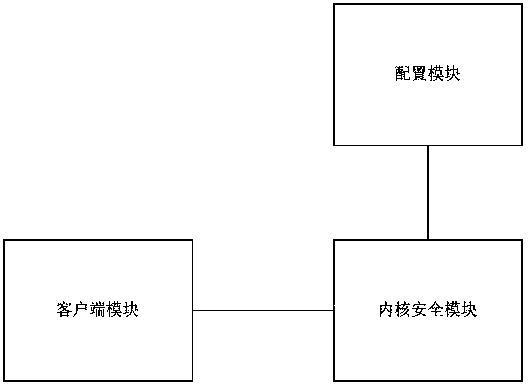
[0029] A system for realizing the hiding of hosts in the network, characterized in that: comprising
[0030] Client module: used to send an encrypted IP access authentication request to the kernel security module;
[0031] Kernel security module: used to perform security authentication on the request content of the client module;
[0032] Configuration module: used to configure the kernel security module;
[0033] The kernel security module and the configuration module are deployed on the server, the client module is deployed on the client, and the kernel security module is signally connected to the configuration module and the client module respectively.
Embodiment 2
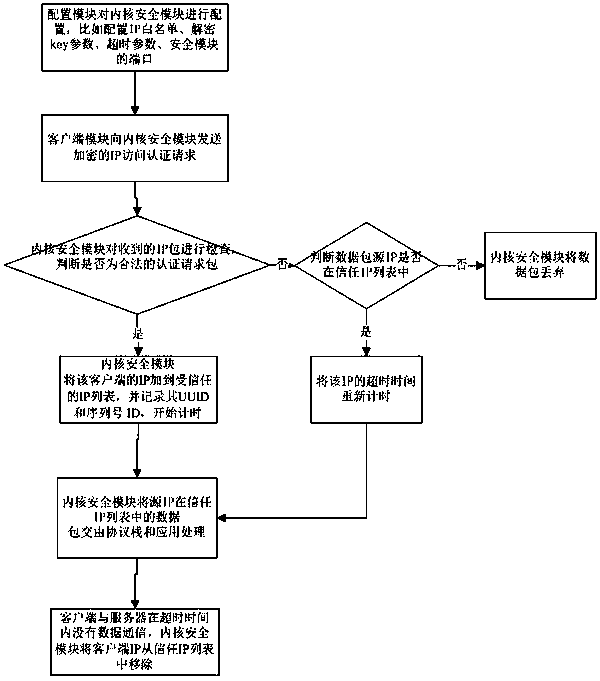
[0035] A method for realizing the hiding of hosts in the network is characterized in that it comprises the following steps:
[0036] (1) Configure the kernel security module through the configuration module, such as configuring the IP whitelist, decryption key parameters, timeout parameters, and ports of the security module. The kernel security module only allows the trusted IP to communicate with the server, and all other IP communication packets are discarded;
[0037] (2) The client module sends an encrypted IP access authentication request to the kernel security module;
[0038] (3) After the kernel security module receives the IP access authentication request, it decrypts the request message and extracts the information of the request. If the fields of the authentication request are all legal, the authentication passes, and the client's IP is added to the trusted IP list. And record its UUID and serial number ID, and start timing;
[0039] (4) The client module initiate...
Embodiment 3
[0047] The specific implementation process takes the Linux system as an example:
[0048] (1) When the kernel security module is initialized, read the authentication request decryption key, port number, white list, kernel security module password (optional) and other parameters, and register the NF_IP_PRE_ROUTING and NF_IP_LOCAL_OUT hook functions through netfilter.
[0049] (2) The configuration module communicates with the kernel security module for configuration delivery and status information acquisition through the Netlink socket. It is mainly to decrypt the key, port number, whitelist, password (optional) configuration update and obtain information such as trusted IP, whitelist, kernel security module status, etc.
[0050] (3) The client module sends a UDP authentication request packet to the port configured by the kernel security module. The authentication request packet contains the UUID string associated with the server IP, the serial number ID, and the password of th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com