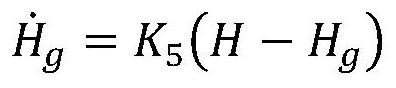Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
43results about How to "Guaranteed absolute security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
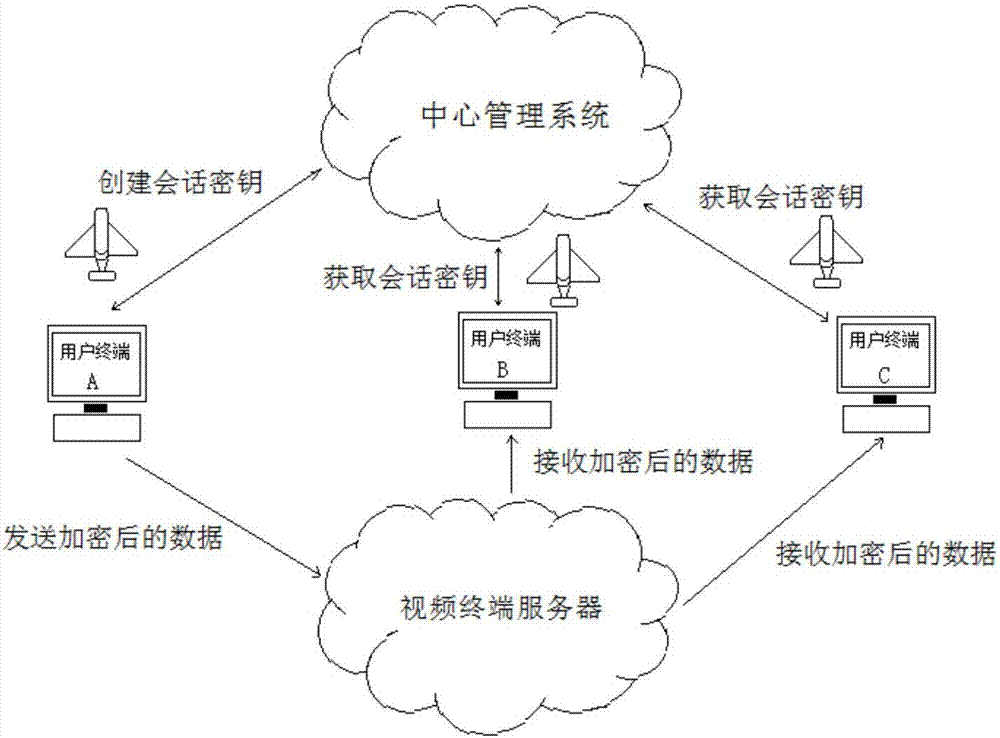
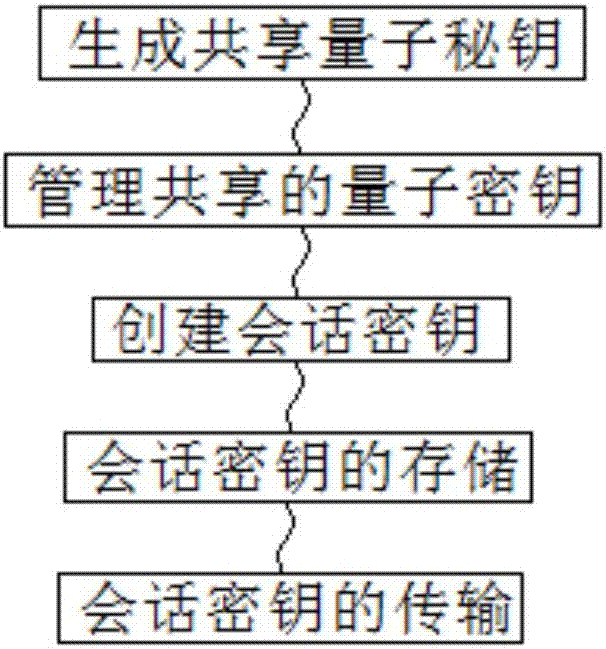
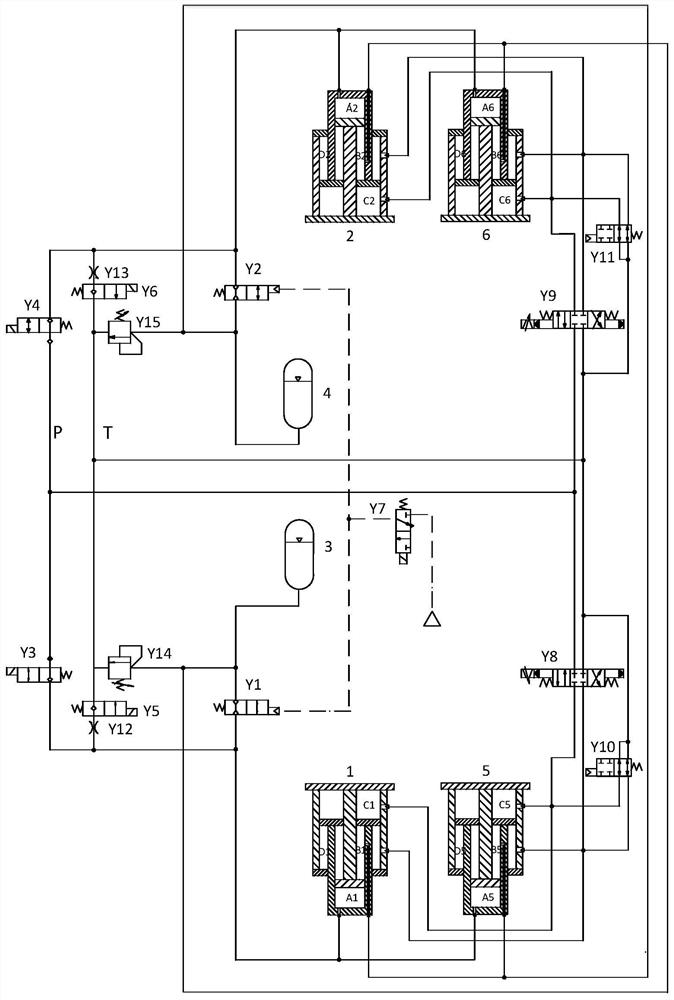
Key distribution system and key distribution method based on multiuser remote communication
PendingCN107040378AGuaranteed absolute securityAvoid high standardsKey distribution for secure communicationSynchronising transmission/receiving encryption devicesQuantum channelKey distribution
The invention discloses a key distribution system and a key distribution method based on multiuser remote communication. Quantum key synchronization between each user terminal and a central management system is realized in a manner of carrying a key relay server by an aerial vehicle. Then the central management system distributes a session key to a user terminal which requires participation into communication in a quantum key encrypted session key manner. A data packet only requires session key encryption, thereby realizing a purpose of multi-user-terminal communication. The key distribution system and the key distribution method ensure absolute safety in multiple-party communication and prevent a high-standard requirement for a QKD system in a one-packet and one-key manner so that quantum encrypted communication is suitable for a large-scale multiple-party communication occasion. Furthermore, establishing of a quantum channel between each user terminal and the central management system is not required. Not only is a problem of quantum information attenuation in remote channel transmission settled, but also a problem of difficult quantum channel disposition is alleviated.
Owner:ZHEJIANG QUANTUM TECH CO LTD
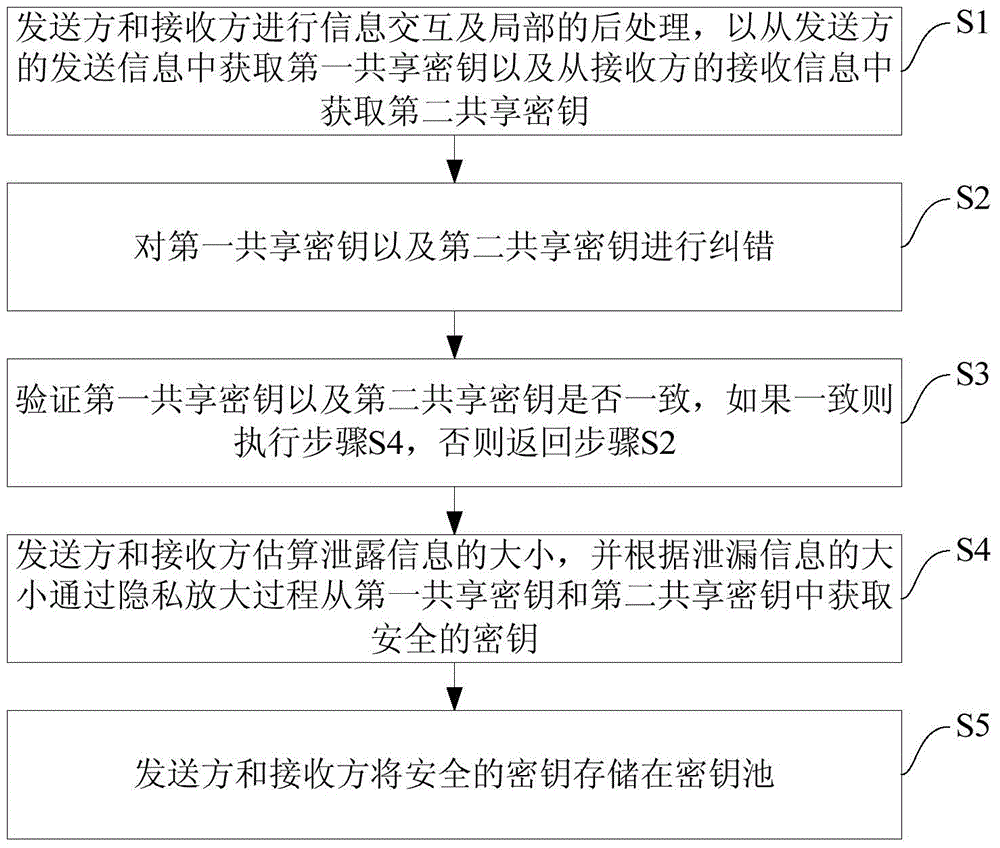
Postprocessing method for quantum key distribution
ActiveCN105071929AImprove accuracyImprove securityKey distribution for secure communicationComputer hardwareKey distribution
The invention provides a postprocessing method for quantum key distribution. The postprocessing method comprises the following steps of S1, performing information interaction and local postprocessing by a transmitting party and a receiving party, thereby acquiring a first shared key from transmitting information of the transmitting party and acquiring a second shared key from receiving information of the receiving party; S2, performing error correction on the first shared key and the second shared key; S3, verifying whether the first shared key and the second shared key are same, if yes, performing a step S4, and otherwise returning to the step S2; S4, evaluating the size of the leakage information by the transmitting party and the receiving party, and acquiring a safe key from the first shared key and the second shared key according to the size of the leakage information through a privacy amplification process; and S5, storing the safe key in a key pool by the transmitting party and the receiving party. The postprocessing method can improve correctness and safety in quantum key distribution.
Owner:TSINGHUA UNIV
Effervescence preparation composition used for sanitary towel and preparation method and application thereof
ActiveCN101518658AStable efficacyNo negative effectsAbsorbent padsBaby linensSodium bicarbonateTriclosan
The invention relates to an effervescence preparation composition used for a sanitary towel and a preparation method and application thereof. The effervescence preparation composition is made from thefollowing raw material by weight proportion: 7 to 10 percent of malic acid, 3 to 5 percent of boletic acid, 10 to 15 percent of sodium bicarbonate, 1 to 4 percent of medical PVP, 35 to 70 percent oftragantine, 0.05 to 0.3 percent of triclosan and 0 to 30 percent of additive agent which contains at least one kind of sodium dodecyl sulfate, beta-cyclodextrin, glycerin, lanoline, propolis and jasmine essence. The effervescence preparation composition adopts the raw materials in the food grade and is safe without toxicity. The preparation adopts the powder technology. After the preparation encounters water, acid and alkali in the preparation are subjected to neutralization reaction to produce gas. The repulsive interaction of the gas accelerates the dissolution rate of the preparation in thewater, makes efficacy ingredients rapidly dissolve, solves the problem of unobvious drug effect of a solid preparation, improves the utility ratio of the content of effective ingredients of a liquidpreparation and can be used for preparing sanitary towels, sanitary protecting mats or panty-shape diapers.
Owner:韩海星
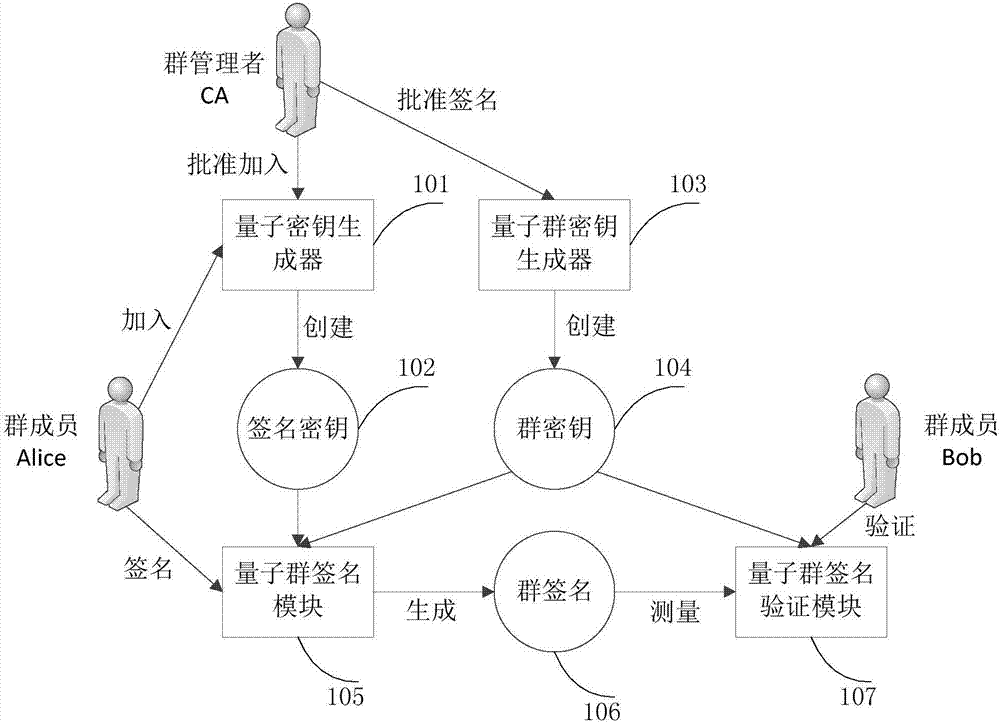
Group signature system based on quantum keys
ActiveCN107395367AGuaranteed absolute securityImprove securityKey distribution for secure communicationUser identity/authority verificationKey generatorLaser source
The invention discloses a group signature system based on quantum keys. The group signature system comprises a quantum key generator, a signature key, a quantum group key generator, a group key, a quantum group signature module, a group signature and a quantum group signature verification, wherein the quantum key generator is a quantum sequence device generated by a laser source, and is used for forming a shared key of a newly-added group member and a group administrator; the quantum group key is issued to group members by the group administrator and used for encryption in signing according to a quantum state sequence generated by means of the quantum group key generator, and different sequences are generated according to different business transactions; and the quantum group signature module is used for performing quantum encryption on messages and signatures by the group members. The group signature system based on the quantum keys has the significant advantages that: identities are determined through distribution and measurement of the quantum keys, the efficiency is higher while the security is improved, and group members can be added and deleted quickly; and the group signature system is more suitable for a complex group signature environment, has the features of unlinkability and coalition attack resistance, and can realize coalition signature of a plurality of the group members.
Owner:CHINA THREE GORGES UNIV
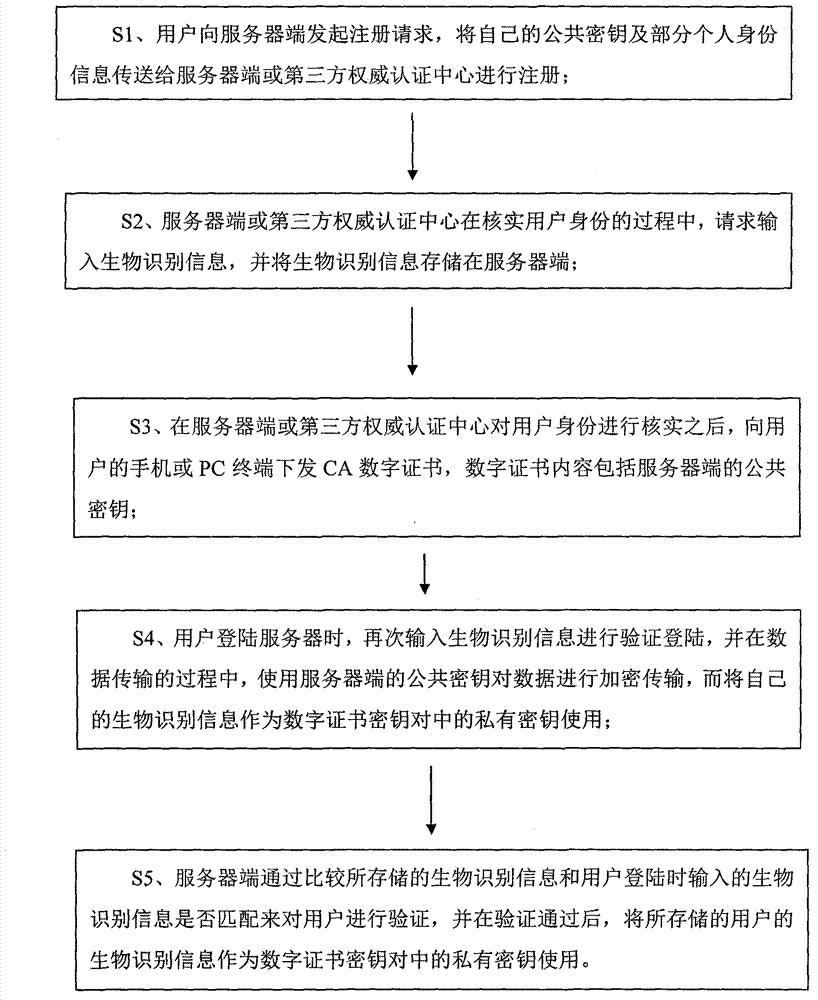
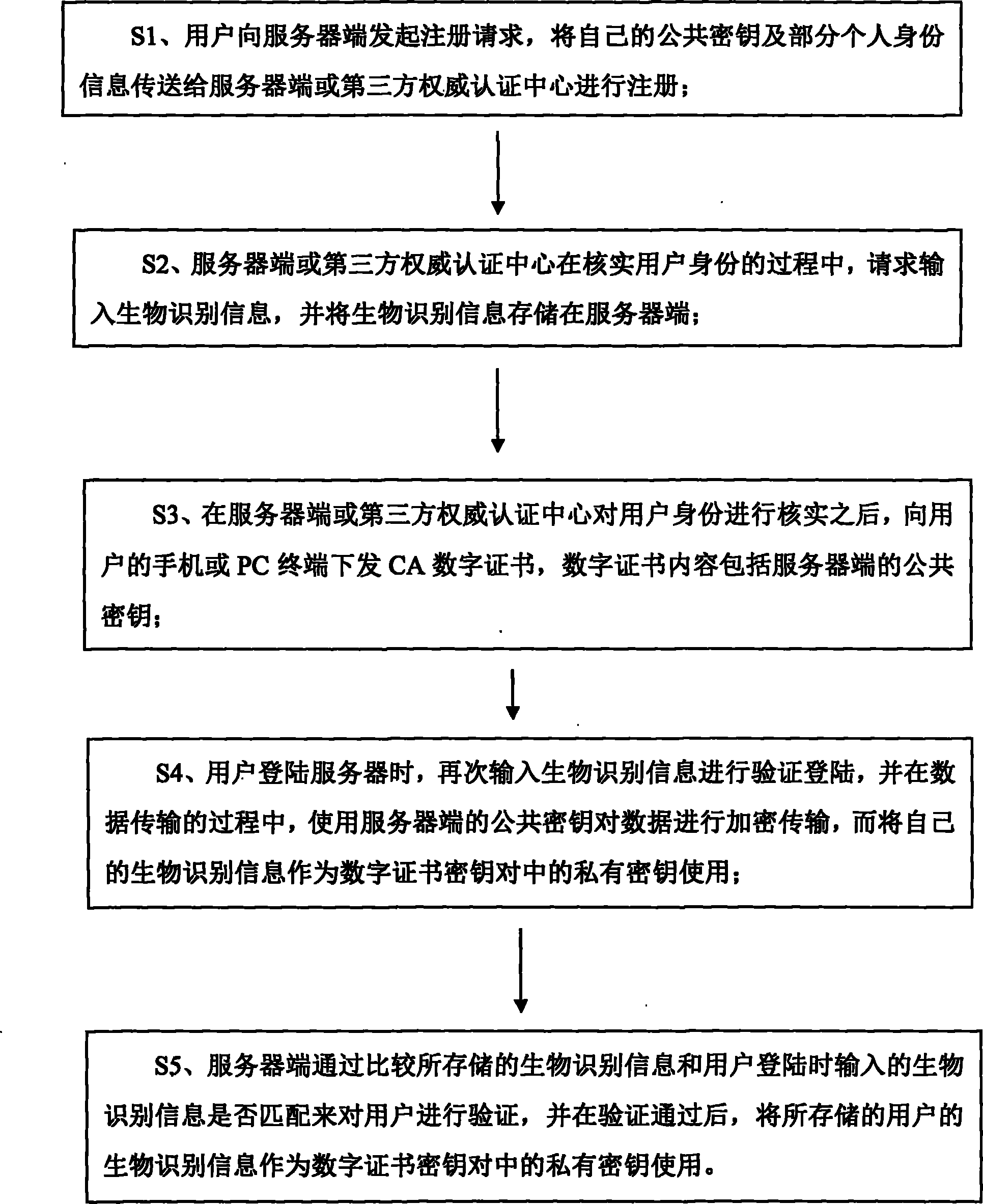
Two-factor authentication method based on digital certificate and biological identification information
ActiveCN102769623AEnsure safetyGuaranteed absolute securityUser identity/authority verificationThird partyPersonal computer
The invention discloses a two-factor authentication method based on a digital certificate and biological identification information. The main idea of the method is that a certificate authority (CA) digital certificate is transmitted to a mobile phone or a personal computer (PC) terminal of a user which is a normal user or a financial approval leader in a server such as a server of an accounting document management system, the digital certificate can pass the authentication of a third-party authority electronic authentication center, validity of the user is verified by the digital certificate, and the biological identification information is used as a respective private key in a digital certificate key pair which is used by the server and a client in the authentication process of the digital certificate to further ensure the security of authentication; and the biological information such as iris information and fingerprint information is identity inherent information and cannot be copied or stolen, so that the absolute security of authentication can be ensured.
Owner:BEIJING HUACAI REASONABLE ACCOUNT CONSULTANTS
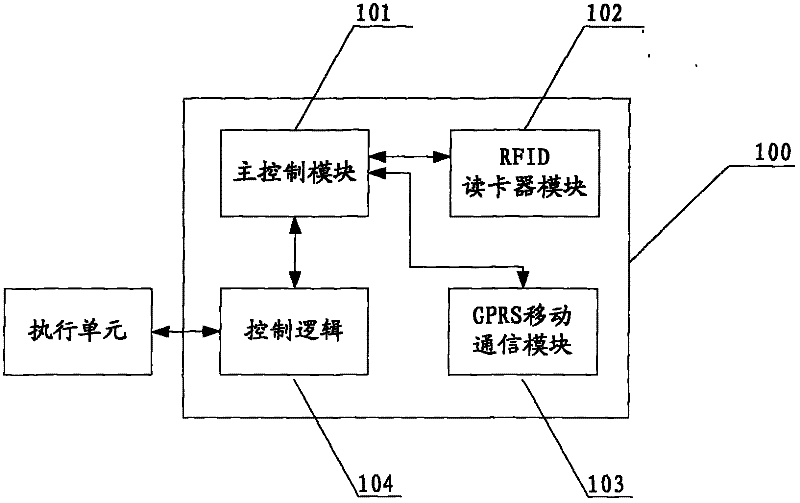
Security electronic control system and method based on 2.4G radio frequency identification (RFID) smart card system
ActiveCN102547691AAvoid safety hazardsGuaranteed absolute securitySensing record carriersSecurity arrangementGeneral Packet Radio ServiceSmart card
The invention discloses a security electronic control system and a security electronic control method based on a 2.4G radio frequency identification (RFID) smart card system, and relates to the fields of wireless radio frequency communication and electronic tags, in particular to a 2.4G RFID-subscriber identity module (SIM) card. The security electronic control system consists of two parts, namely a 2.4G RFID security electronic control unit and a 2.4G RFID security electronic key, wherein the 2.4G RFID security electronic control unit consists of a 2.4G RFID card reader module, a general packet radio service (GPRS) mobile communication module, a master control module and a control logic part; and the 2.4 G RFID security electronic key consists of a 2.4G RFID smart card and a mobile communication terminal. Double identity authentication between the control unit and the key is performed by adopting a security authentication protocol and a user password, so that potential safety hazards caused by an anti-counterfeited key and key loss can be prevented, convenience for use is provided, and the absolute security of electronic control operation is ensured at the same time.
Owner:NATIONZ TECH INC
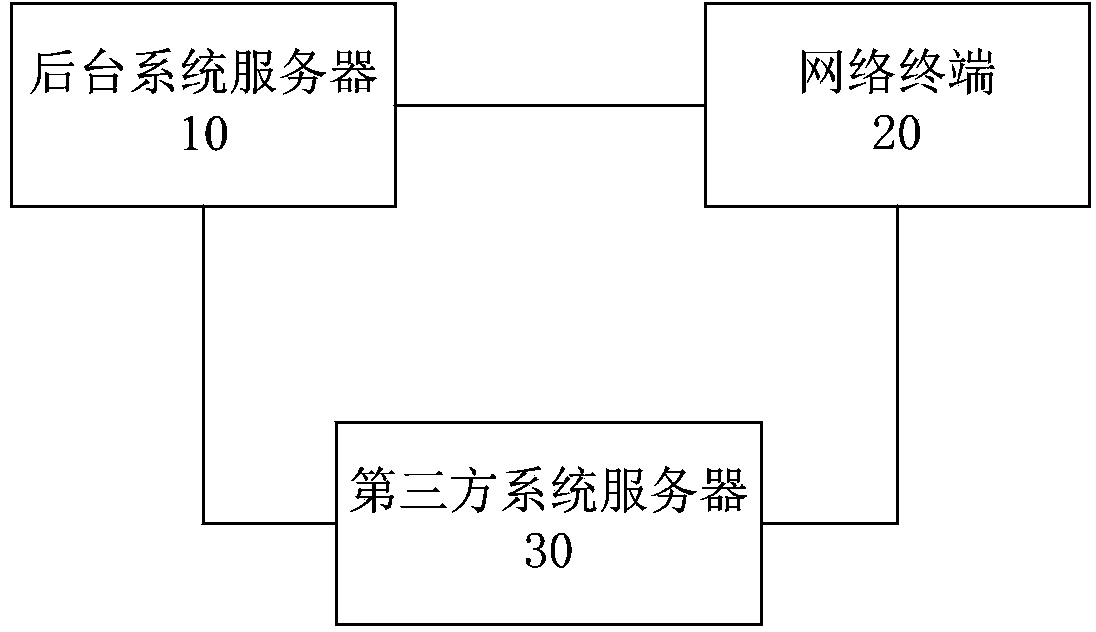
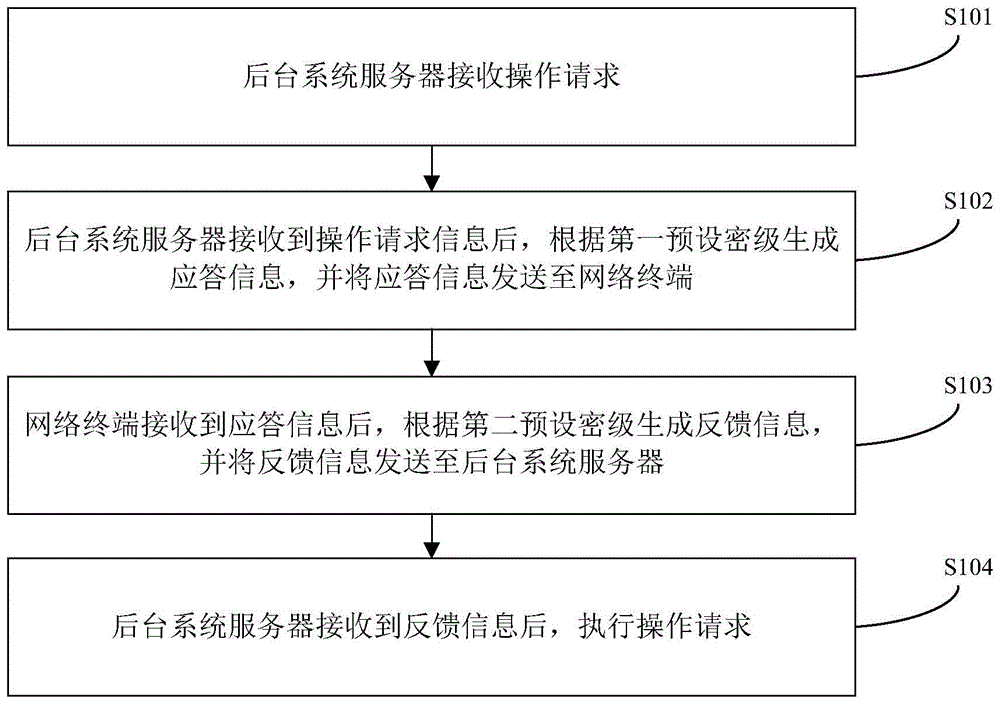
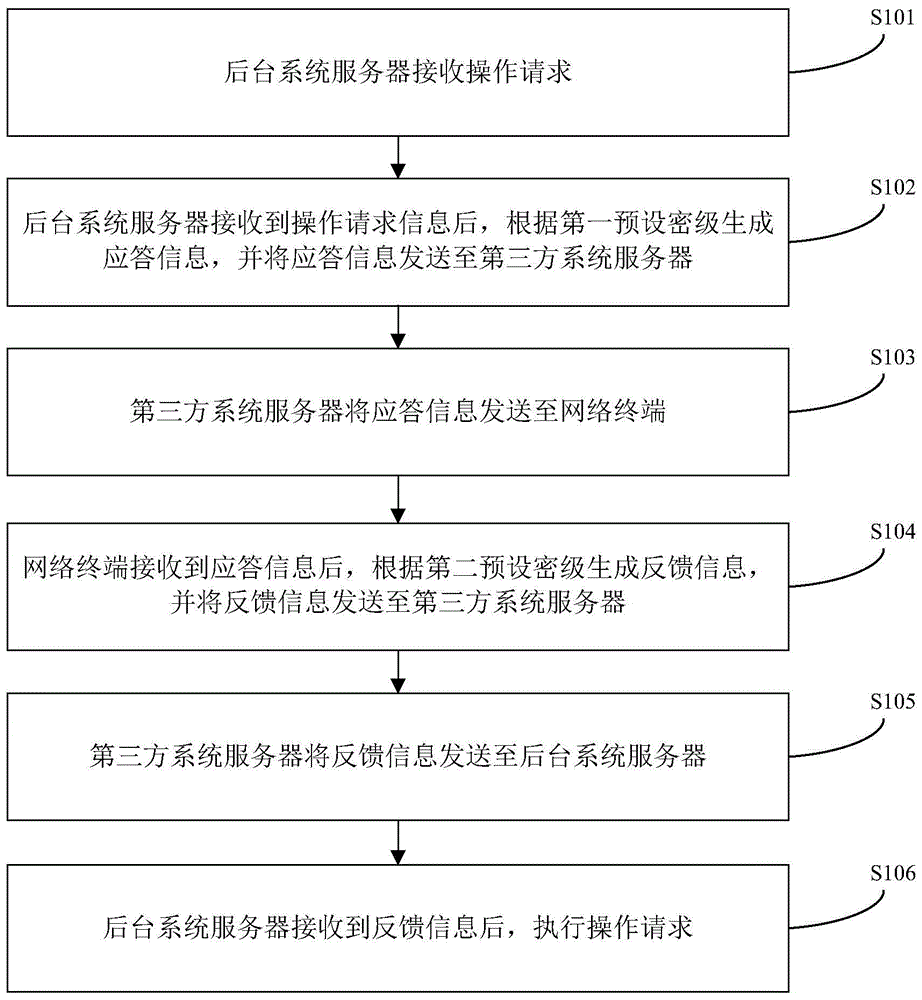
Operation request processing method and system
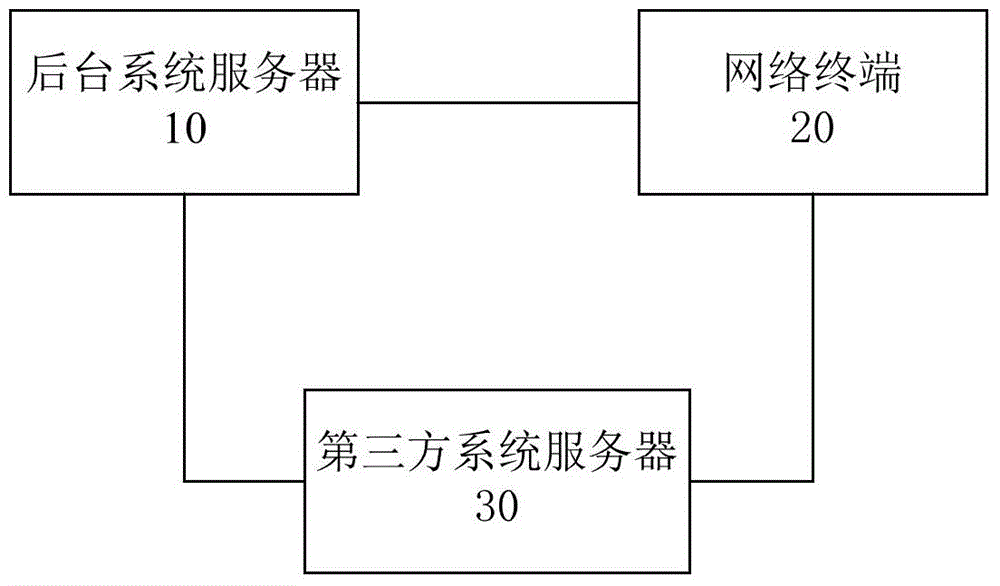
ActiveCN103716327AGuaranteed absolute securityIntegrity guaranteedTransmissionPlaintextNetwork termination
The invention provides an operation request processing method and system. The operation request processing method comprises the steps that after receiving an operation request message, a background system server generates a response message according to a first preset security class and sends the response message to a network terminal through a third-party system server; after receiving the response message, the network terminal generates a feedback message according to a second preset security class and sends the feedback message to the background system server through the third-party system server; after receiving the feedback message, the background system server executes an operation request. By conducting security classification on data to be transmitted, semi-transparency of communication data is realized, a part of the communication data are transmitted in the form of plaintexts, and the integrity and the safety of the data to be transmitted with a higher security class can also be guaranteed on the premises that the absolute security of the data to be transmitted with the highest security class is guaranteed and the plaintexts of the data to be transmitted with the higher security class and the plaintexts of the data to be transmitted with a lower security class are visible.
Owner:TENDYRON CORP
Control method and system for internal and external network security access
InactiveCN110430179AAchieve data security goalsImprove authentication securityTransmissionControl systemTerminal equipment
The invention discloses a control system for internal and external network security access. The system comprises a terminal security access subsystem and a gateway security access subsystem. The terminal security access subsystem solves the security problem encountered when the terminal accesses the intranet; access establishment process, providing unique recognition, communication process, data generated in the communication process is encrypted and stored in a partitioned manner; communication end process, securing in-time cleaning of caches, the gateway security access subsystem mainly realizes authentication auditing work for terminal access, can accurately authenticate terminal identity representation in the authentication process, and adopts different communication measures for the terminal according to an authentication result to ensure absolute security of the data. The invention further provides a corresponding control method which can be applied to an institution organizationwhich has high requirements for intranet data security and requires the terminal equipment to have a certain degree of flexibility.
Owner:XI AN JIAOTONG UNIV
Quantum encryption transmission device and transmission method for internet of things data
InactiveCN109104428AGuaranteed absolute securityKey distribution for secure communicationClient-side encryptionInternet of Things
The invention discloses an Internet of Things data quantum encryption transmission device and a transmission method. The quantum encryption transmission device for Internet of Things data comprises aquantum encryption device and a quantum key distribution device. The quantum encryption device comprises a control platform end encryption device and a client end encryption device. The Internet of Things cloud platform is interconnected with the public network through the control platform end encryption device, and the Internet of Things terminal network is interconnected with the public networkthrough the client end encryption device. The quantum key distribution device comprises a quantum gateway, a control platform end encryption device and a client end encryption device are arranged beside the quantum gateway, and the control platform end encryption device and the client end encryption device obtain the quantum key from the quantum gateway in real time. The invention also provides atransmission method of a quantum encryption transmission device for Internet of Things data.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
Post-processing system and method for phase polarization joint modulation QKD
PendingCN111200493AIncrease transfer rateImprove bit error rateKey distribution for secure communicationPhotonic quantum communicationTransceiverChannel parameter
The invention discloses a post-processing system for phase polarization joint modulation QKD. The system comprises a sender and a receiver. Each of the sender and the receiver comprises an informationinteraction unit, a parameter estimation unit, an error correction unit and a confidentiality amplification unit which are connected in sequence. The information interaction unit, the parameter estimation unit, the error correction unit and the confidentiality amplification unit of the sender are respectively connected with the information interaction unit, the parameter estimation unit, the error correction unit and the confidentiality amplification unit of the receiver in a one-to-one correspondence manner through channels. According to the invention, aiming at the characteristics of a phase polarization joint modulation QKD system and a double-speed protocol used by the phase polarization joint modulation QKD system, a traditional transceiver base vector comparison step is not needed in the information interaction unit, so that the information interaction amount is reduced, and the post-processing efficiency is improved; and the parameter estimation unit estimates the bit error rate of the key by using a packet parity check method, and selects a reasonable error correction method and a secrecy amplification method after estimating channel parameters, so that the correctness andthe safety of quantum key distribution are improved by the steps.
Owner:GUANGDONG INCUBATOR TECH DEV CO LTD
Data acquisition method and system based on block chain
ActiveCN109376172AGuaranteed absolute securityImprove utilization efficiencyDigital data information retrievalFinanceData informationData acquisition
The present application provides a data acquisition method and system based on block chain, the method comprises the following steps: a terminal sends a data acquisition request to at least one node in a block chain, wherein the data acquisition request includes a user identification and a data attribute identification, so that each node in the at least one node determines data information corresponding to the user identification and the data attribute identification; the terminal receives data information sent by each of the at least one nodes, wherein the data information includes a data attribute identification; the terminal decrypts each data information in at least one data information to obtain each decrypted data information. The terminal determines the final data information according to each decrypted data information. Because the data information is encrypted in pieces and placed on different nodes, the incompleteness of pieces of data can ensure the absolute security of thedata, and the data information will not be sold and disclosed.
Owner:恩亿科(北京)数据科技有限公司
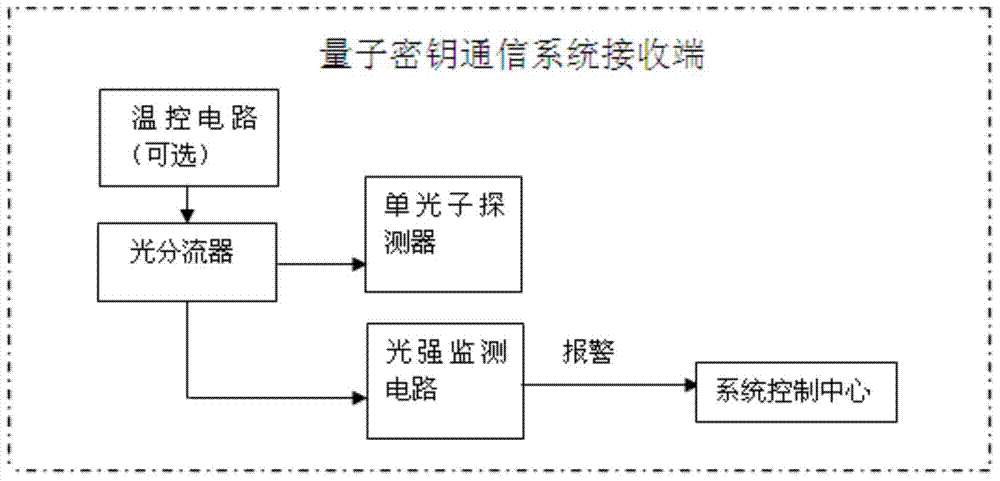
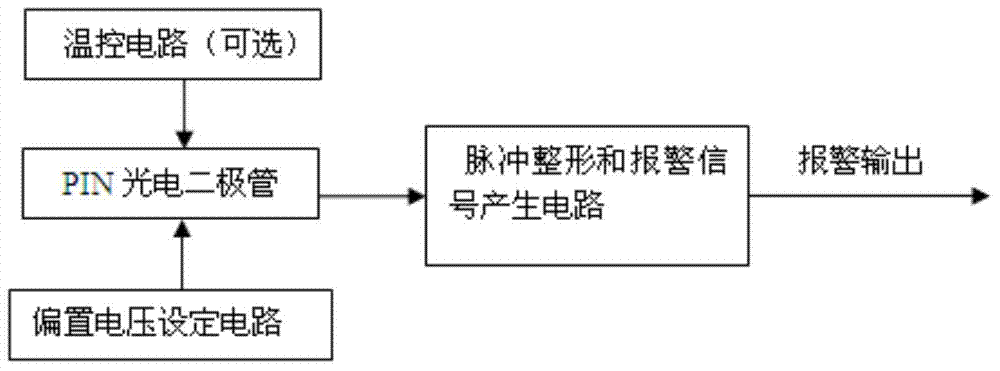
Hard light induced blindness monitoring device and method of single-photon detector
InactiveCN104215328AGuaranteed absolute securityLow costKey distribution for secure communicationPhotometry using electric radiation detectorsHemt circuitsEngineering
The invention discloses a hard light induced blindness monitoring device of a single-photon detector. The hard light induced blindness monitoring device comprises a temperature control circuit module, a PIN photoelectric diode, a bias voltage setting module and a pulse shaping and alarm signal generating module, wherein the PIN photoelectric diode is used for converting hard light narrow-pulse signals transmitted by an attacker into narrow-pulse current and outputting narrow-pulse voltage in proportion to the narrow-pulse current, the pulse shaping and alarm signal generating module is used for converting the narrow-pulse voltage outputted by the PIN photoelectric diode into a standard level which can be identified by follow-up master control chips, and the bias voltage setting module is used for setting reverse bias voltage added on the PIN photoelectric diode. The invention further discloses a hard light induced blindness monitoring method. The hard light induced blindness monitoring device is simple in circuit and low in cost, when showing up in quantum channels, hard light attack signals can be immediately monitored, and alarm signals can be transmitted to an upper computer, accordingly, absolute safety of a quantum key communication system is ensured.
Owner:ANHUI QASKY QUANTUM SCI & TECH CO LTD
Control system suitable for secure access of intranet data
ActiveCN111901360ACannot be modifiedImprove securityDigital data protectionTransmissionControl systemTerminal equipment
A control system suitable for secure access of intranet data comprises a system starting security authentication subsystem and an intranet connection security authentication subsystem. The system starting safety authentication subsystem solves the safety problem encountered in the starting stage of terminal equipment, self-loop encryption is conducted through a bootstrap program to prevent data from being tampered with, hard disk read-write permission is set for isolated storage of intranet data, and when the terminal equipment fails to be started multiple times, a data safety control chip executes local sensitive data erasure. The intranet connection security authentication subsystem solves the security problem encountered when the terminal equipment is connected with the intranet, an encrypted data channel is established by using a fixed key of the terminal equipment, an intranet access white list is synchronized to audit the behavior of the terminal equipment, and when audit does not succeed for multiple times, an intranet gateway sends a remote sensitive data erasure instruction. The invention provides a specific logic process and a practical strategy of the system, and the system can be applied to an organization which has high requirements on intranet data security and requires terminal equipment to have certain data protection capability.
Owner:XI AN JIAOTONG UNIV
Operation request processing method and system
ActiveCN103716328AGuaranteed absolute securityIntegrity guaranteedUser identity/authority verificationPlaintextNetwork termination
The invention provides an operation request processing method and system. The operation request processing method comprises the steps that after receiving an operation request message, a background system server generates a response message according to a first preset security class and sends the response message to a network terminal; after receiving the response message, the network terminal generates a feedback message according to a second preset security class and sends the feedback message to the background system server; after receiving the feedback message, the background system server executes an operation request. By conducting security classification on data to be transmitted, semi-transparency of communication data is realized, a part of the communication data are transmitted in the form of plaintexts, and the integrity and the safety of the data to be transmitted with a higher security class can also be guaranteed on the premises that the absolute security of the data to be transmitted with the highest security class is guaranteed and the plaintexts of the data to be transmitted with the higher security class and the plaintexts of the data to be transmitted with a lower security class are visible.
Owner:TENDYRON CORP
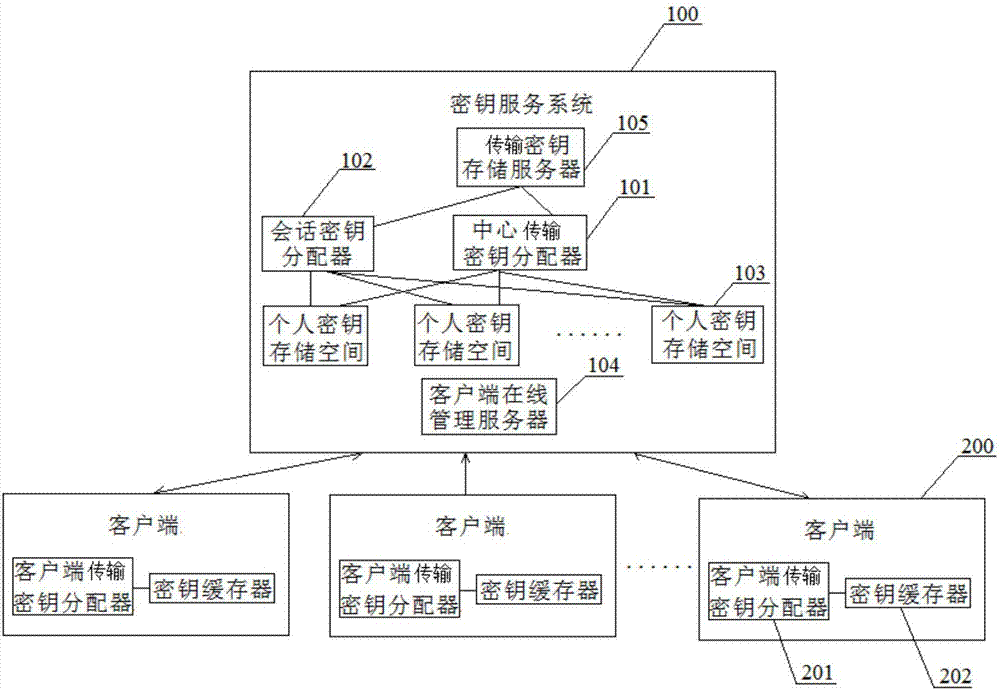
Key service-oriented architecture based on multi-terminal communication and distribution method
InactiveCN107147491AImprove securityImprove efficiencyKey distribution for secure communicationDistribution methodKey storage
The invention relates to key service-oriented architecture based on multi-terminal communication and a distribution method. The key service-oriented architecture comprises a key service system, a plurality of personal key storage spaces are formed in the key service system; each client can access the corresponding personal key storage space, and cannot access the personal key storage space of other clients; the key service system is further provided with a client online management server, wherein the client online management server is used for monitoring whether each client is in the online connection state, and pushing a session key to each client in online state. Compared with the prior art, the aim of security communication in multi-party clients can be realized by only adopting the data packet session key encryption way, and the one-packet key high-standard requirement to the QKD system is avoided at the same time, the quantum encryption communication can be well suitable for the large-scale multi-party communication occasion; the key service-oriented architecture guarantees that the participants can rapidly and accurately receive the session keys, and the security and the efficiency of the communication are improved.
Owner:ZHEJIANG QUANTUM TECH CO LTD
Anti-toppling mechanical device and method for internal suspension stay wire holding pole
ActiveCN113530347AGuaranteed absolute securityNot destroyedTowersWind energy generationTowerControl theory
The invention discloses an anti-toppling mechanical device and method for an internal suspension stay wire holding pole. The anti-toppling mechanical device mainly comprises a triggering mechanism and an anti-toppling mechanism, the triggering mechanism comprises a triggering box, the triggering box is installed on the holding pole, a channel is formed in the triggering box, the middle of the channel is low, the outer side of the channel is high, a triggering ball is installed at the low position of the channel, a groove is formed in the high end of the channel, a pressure sensor is arranged in the groove, the anti-toppling mechanism comprises a plurality of supports, the upper portion of each support is hinged to a longitudinal beam of the holding pole, a first electromagnet and a second electromagnet are installed on the lower portion of each support, When each first electromagnet is powered on and the corresponding second electromagnet is powered off, the first electromagnet and the holding pole are attracted and fixed, and when each first electromagnet is powered off and the corresponding second electromagnet is powered on, strong springs unfold the supports to abut against an iron tower. According to the anti-toppling mechanical device and method for the internal suspension stay wire holding pole, the internal suspension stay wire holding pole is prevented from toppling, it is guaranteed that a tower body is not damaged, and constructors are not injured.
Owner:SANMENXIA ELECTRIC POWER DESIGN
Integrated control design method of ship-borne unmanned aerial vehicle arresting landing and escape re-flight
ActiveCN112148027AEnsure safetyGuaranteed absolute securityPosition/course control in three dimensionsAerospace engineeringSystems engineering
Owner:CHENGDU AIRCRAFT INDUSTRY GROUP
Two-factor authentication method based on digital certificate and biological identification information
ActiveCN102769623BEnsure safetyGuaranteed absolute securityUser identity/authority verificationThird partyPersonal computer
Owner:BEIJING HUACAI REASONABLE ACCOUNT CONSULTANTS
Small intelligent super-flat bearing robot for loading VRU target object
The invention provides a small intelligent super-flat bearing robot for loading a VRU target object. The bearing robot comprises a bearing machine body, a driving mechanism, a power supply system and a control system, wherein the bearing machine body comprises a machine body frame main body and a machine body cover plate, and is used for bearing the VRU target object and providing installation of parts of the driving mechanism, the power supply system and the control system; the driving mechanism comprises a steering driving module, a power driving module, a braking module and an air cylinder supporting module; the power supply system provides a power source and energy for the driving mechanism and the control system of the small intelligent super-flat bearing robot; and the control system is used for completing operation of the small intelligent super-flat bearing robot and control over the experiment process. By means of the design of the added air cylinder mechanism, it is guaranteed that tires can be recycled immediately when a tested vehicle is pressed upwards, adjustment of the ground clearance of the small intelligent super-flat bearing robot is achieved, road condition adaptability is high, testing cost is low, and then the testing requirement for the actual road condition of Chinese roads is met.
Owner:湖南立中科技股份有限公司
Functional form herb high-calcium native
InactiveCN101341983APromote absorptionAchieve a complementary effectFood preparationBiotechnologyVitamin C
The invention discloses a functional materia medica high-calcium element, in particular to a functional materia medica high-calcium element which has the nutrition health functions of strengthening stomach and promoting digestion, supplementing calcium and discharging lead, promoting growth and intelligence, replenishing qi and blood and is specially used for children and youths as well as a preparation method. The invention belongs to the field of nutrition and health food and is manufactured by taking lotus root powder, chrysanthemum powder, calcium powder, iron powder, zinc powder, vitamin C, taurine and casein phosphopeptide as the main materials. The manufacture technique is simple and convenient; the operability is high. The safety and the taste of the product are good; besides, the product has no bitter and iron fishy smell, does not stimulate gastrointestinal tracts, is easily eaten, is easily absorbed by a human body, has a plurality of nutrition health functions and provides the most effective nutrition help for the health growing of children and youths.
Owner:呼伦贝尔友谊乳业(集团)有限责任公司
Production process for mineral beer
The invention discloses a production process for mineral beer, which comprises: activating naphtha, and adding the activated naphtha into beer to soak the naphtha for at least 7 days before the beer is filled; taking the soaked naphtha out from beer liquid, and filtering under a sterile condition; and after sterile filling, sterilizing by radiation with cobalt-60 as a radioactive source. In the process, the naphtha is used to mineralize common beer, so that the beer contains various trace elements such as magnesium, selenium, lithium, manganese, boron, strontium, germanium and the like; lucid ganoderma also can be added to increase the germanium content in the beer; the radiation sterilization mode is adopted for complete sterilization, so the quality guarantee period of the beer is prolonged and the drawback of reduction in nutrients of the conventional sterilization is overcome; and thus, the beer which contains various trace elements, is benefit for health of human bodies and has a long quality guarantee period is produced.
The switching control loop between the hydro-pneumatic suspension and the active suspension
ActiveCN109050192BSimple structureGuarantee a smooth rideResilient suspensionsEngineeringControl valves
A oil-air suspension and active suspension switching control circuit and a suspension oil cylinder, first of all: the structure of the suspension oil cylinder is improved, that is, the outer cylinder wall of the suspension oil cylinder is provided with oil ports at the upper and lower sides, and the inner cylinder is built in the center through hole of the upper end cover. , the wall of the inner cylinder is provided with two oil ports respectively connected to the inner rodless cavity and the inner rod cavity, the end of the inner cylinder located in the outer cylinder is connected to the outer piston located in the outer cylinder, and the inner One end of the cylinder rod located in the inner cylinder is connected with the inner piston, and one end located in the outer cylinder is fixedly connected with the lower end cover. The present invention adds an active suspension control circuit to the existing interconnected oil-air suspension switching control circuit, which is based on the improved suspension oil cylinder, and adopts left and right servo valves and left and right oil-gas recovery control valves to cooperate with it. Through the active suspension control loop, three control modes of oil-air control, active control and rigidity control of the suspension system can be realized, and the three control modes can be switched mutually without affecting each other.
Owner:YANSHAN UNIV
Functional herbal calciferin
InactiveCN101341983BRegulatory functionPromotes nutrient absorptionFood preparationBiotechnologyVitamin C
The invention discloses a functional materia medica high-calcium element, in particular to a functional materia medica high-calcium element which has the nutrition health functions of strengthening stomach and promoting digestion, supplementing calcium and discharging lead, promoting growth and intelligence, replenishing qi and blood and is specially used for children and youths as well as a preparation method. The invention belongs to the field of nutrition and health food and is manufactured by taking lotus root powder, chrysanthemum powder, calcium powder, iron powder, zinc powder, vitamin C, taurine and casein phosphopeptide as the main materials. The manufacture technique is simple and convenient; the operability is high. The safety and the taste of the product are good; besides, the product has no bitter and iron fishy smell, does not stimulate gastrointestinal tracts, is easily eaten, is easily absorbed by a human body, has a plurality of nutrition health functions and provides the most effective nutrition help for the health growing of children and youths.
Owner:呼伦贝尔友谊乳业(集团)有限责任公司
An operation request processing method and system
ActiveCN103716328BGuaranteed absolute securityIntegrity guaranteedUser identity/authority verificationPlaintextNetwork termination
Owner:TENDYRON CORP
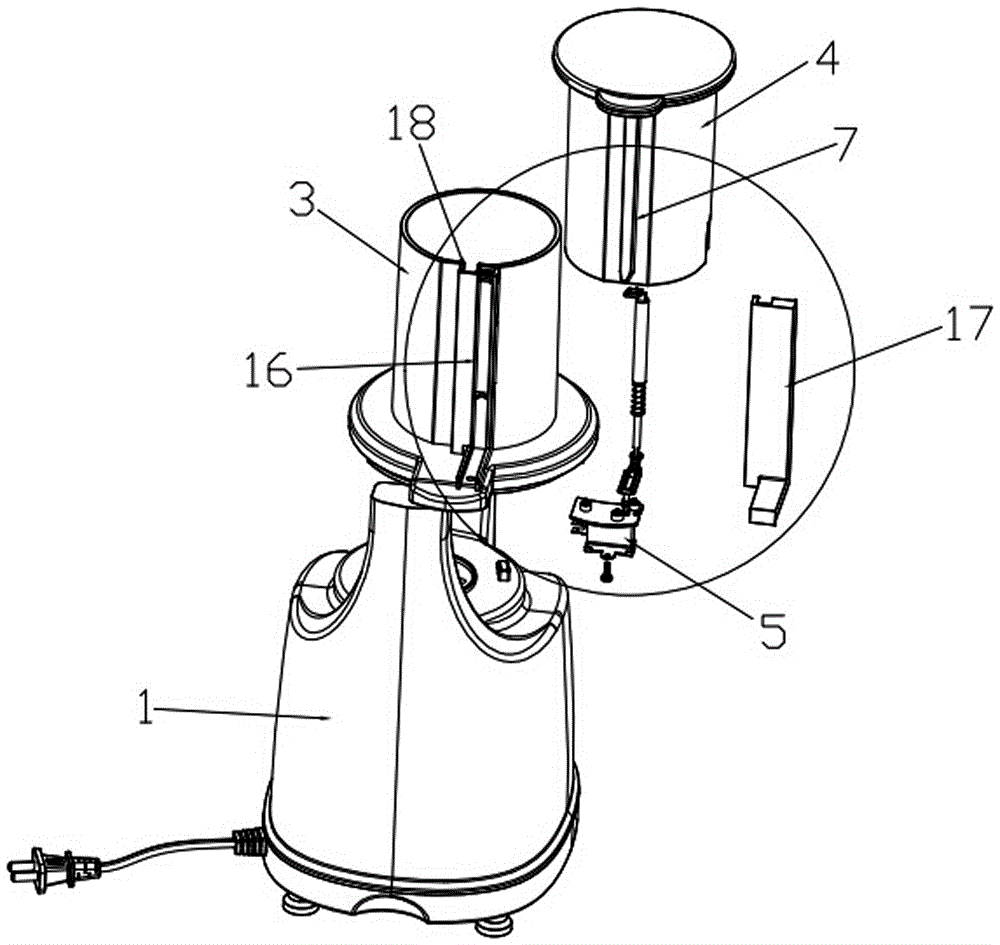
High security large caliber fruit juice machine
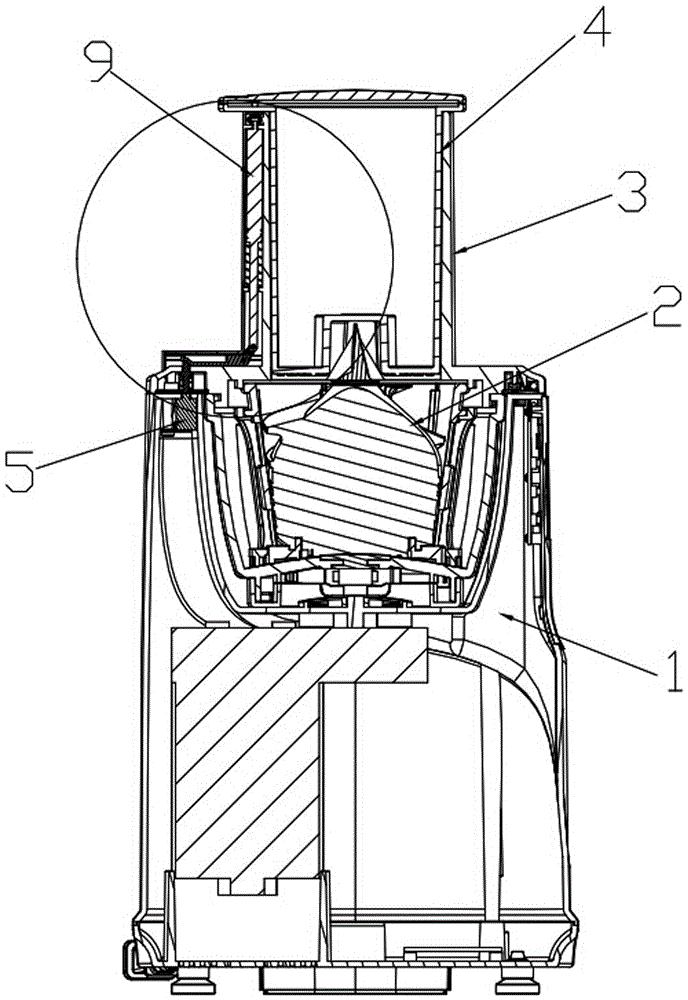
ActiveCN104367156BGuaranteed absolute securityAvoid the dangers caused by the actionStrainersEngineeringFood processing
The invention discloses a high-safety large-diameter juice machine, and belongs to the field of food processing equipment. The high-safety large-diameter juice machine comprises a machine base and a stirring chamber located at the top of the machine base. A large-diameter feeding opening is internally provided with a pressure head rod for downwards pressing fruits and capable of being inserted into and taken out of the feeding opening. The machine base is internally provided with a tact switch for enabling the machine to normally operate. The outer surface of an upper cover is provided with a sliding rod assembly for touching the tact switch in a moving mode so as to make the touch switch be turned off and turned on. The sliding rod assembly is further provided with an elastic assembly enabling the sliding rod assembly to reset. After the sliding rod assembly resets, the touch switch resets and is turned off at the same time. According to the high-safety large-diameter juice machine, the tact switch is additionally arranged to achieve safe starting, in combination of inserting of the pressure head rod, the sliding rod assembly is touched to close the tact switch, and the machine is safely started; when the pressure head rod is taken out, the machine stops operating, the danger generated due to the fact that a hand stretches into the large-diameter juice machine before the pressure head rod is inserted into the machine is avoided, and absolute safety in using the large-diameter juice machine is structurally guaranteed.
Owner:DONGGUAN FUSHIDUO ELECTRIC CO LTD
An operation request processing method and system
ActiveCN103716327BGuaranteed absolute securityIntegrity guaranteedTransmissionThird partyNetwork termination
The present invention provides a method and system for processing an operation request, wherein the method includes: after the background system server receives the operation request information, generates response information according to the first preset security level, and sends the response information to the network through the third-party system server The terminal; the network terminal generates feedback information according to the second preset security level after receiving the response information, and sends the feedback information to the background system server through the third-party system server; the background system server executes the operation request after receiving the feedback information. By classifying the confidentiality level of the data to be transmitted, the communication data can be made translucent, and part of the communication data can be transmitted in plain text. Under the premise of ensuring the absolute security of the data to be transmitted with the highest confidentiality level, it can also be transmitted at a lower and higher confidentiality level. Under the premise that the plaintext of the high-level data to be transmitted is visible, the integrity and security of the high-level confidentiality-level data to be transmitted is guaranteed.
Owner:TENDYRON CORP
Implementation method of public component based on configurable financial transaction SMS verification code
ActiveCN113191762BSolve the problem of functional redundancyImprove acceleration performanceProtocol authorisationSoftware engineeringEngineering
The invention discloses an implementation method based on a configuration type financial transaction short message verification code public component. The method includes determining and storing the binding relationship between specific services and SMS verification code template configuration; the back-end exposes HTTP interface services such as SMS verification code sending and verification to form a back-end component, and the back-end component exposes SMS verification code sending and verification services For front-end components to call; publish front-end components to the resource library through npm to form front-end components, other projects are installed directly through npm, and the front-end components can be used in the page after being introduced and activated. The invention solves the function redundancy problem of the system, improves the expansibility and isolation of the system, and is easy to maintain and upgrade; the short message verification code component can be used at the front end through simple configuration, and it can also be distinguished according to different incoming parameters. The difference of SMS verification codes for different business activities is eliminated; the absolute security of business activities is guaranteed.
Owner:江苏苏宁银行股份有限公司
An integrated control design method for shipborne unmanned aerial vehicles to arrest the ship and escape and go around
ActiveCN112148027BEnsure safetyGuaranteed absolute securityPosition/course control in three dimensionsDesign controlUncrewed vehicle
Owner:CHENGDU AIRCRAFT INDUSTRY GROUP
A method and a system device based on a remote connection operation strategy
InactiveCN109933512AGuaranteed absolute securityDoes not involve compilationSoftware testing/debuggingTransmissionUser codeOperating system
The invention discloses a method and a system device based on a remote connection operation strategy. The method comprises the following steps: a web end creates a strategy; The local strategy end obtains the operation code and the execution code of the strategy and operates the strategy; The local strategy end sends the operation result to the strategy service; The strategy service sends the operation result to a web end; And the web end receives the operation result and presents the operation result to a user. Compared with some quantification platforms in the market, codes of the platform are local to the user instead of on the web side, and absolute safety of the user codes is guaranteed.
Owner:武汉优品楚鼎科技有限公司
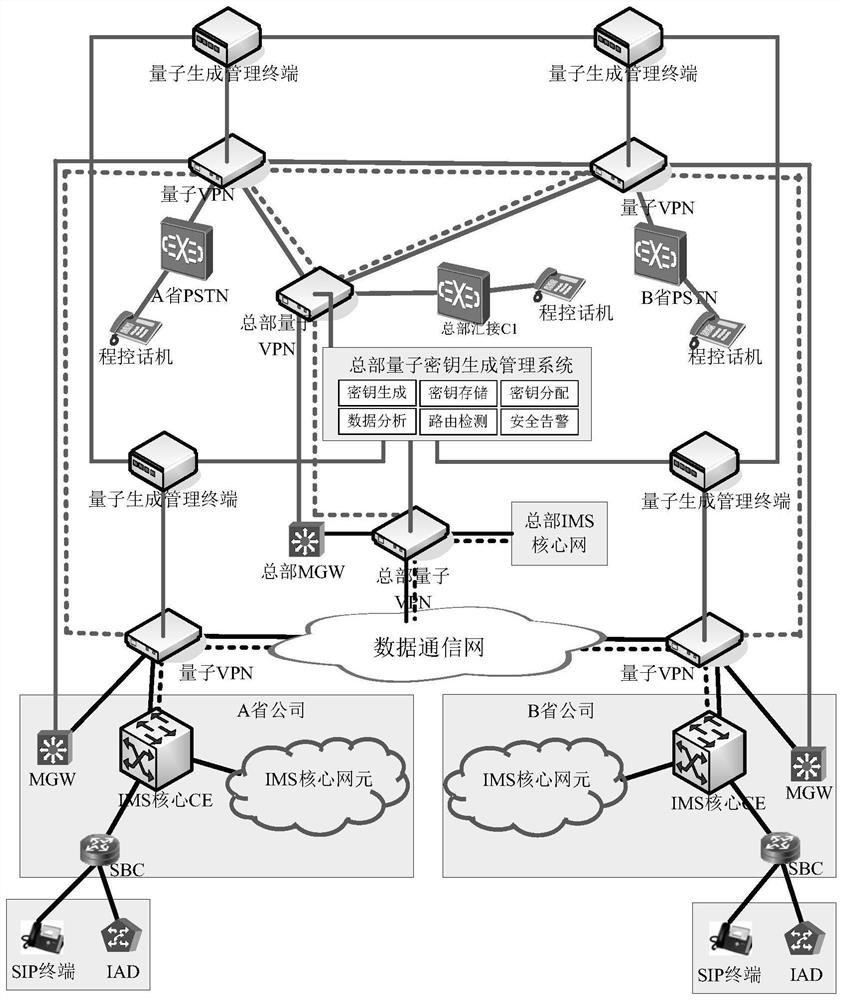
Quantum Encryption System and Encrypted Communication Method for Telephone Switching Network
ActiveCN109150527BGuaranteed absolute securityGuaranteed reliabilityKey distribution for secure communicationNetworks interconnectionEngineeringSwitched mesh
The invention discloses a quantum encryption system and encrypted communication method for a telephone exchange network. The encryption system includes a total quantum generation management system, a total PSTN domain and a total IMS domain quantum VPN, and PSTN domains and IMS domain quantum generation in multiple regions The management terminal, and the PSTN domain and IMS domain quantum VPN in the multiple areas, based on this system, through the quantum encryption of data packets, can realize the state grid company IMS domain phone, PSTN domain phone, IMS domain Communication between the phone and the PSTN domain phone is encrypted.
Owner:STATE GRID CORP OF CHINA +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com