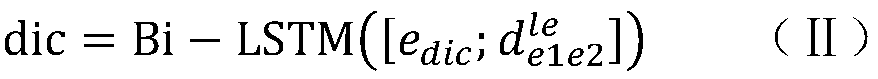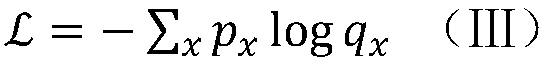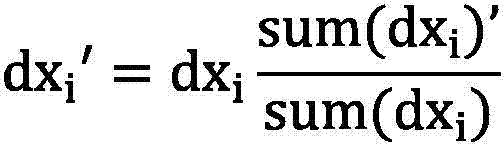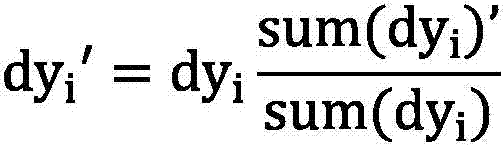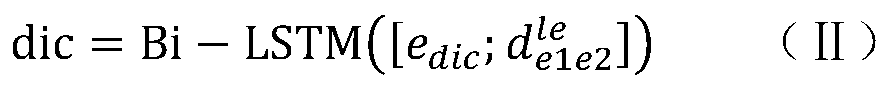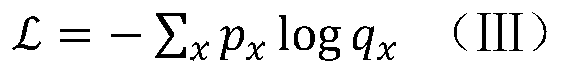Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
37results about How to "Confusing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Neural network relation classification method and an implementation system thereof, which fuse discrimination degree information
ActiveCN109344244ASolve the confusionWork lessSpecial data processing applicationsText database clustering/classificationFeature vectorRelation classification
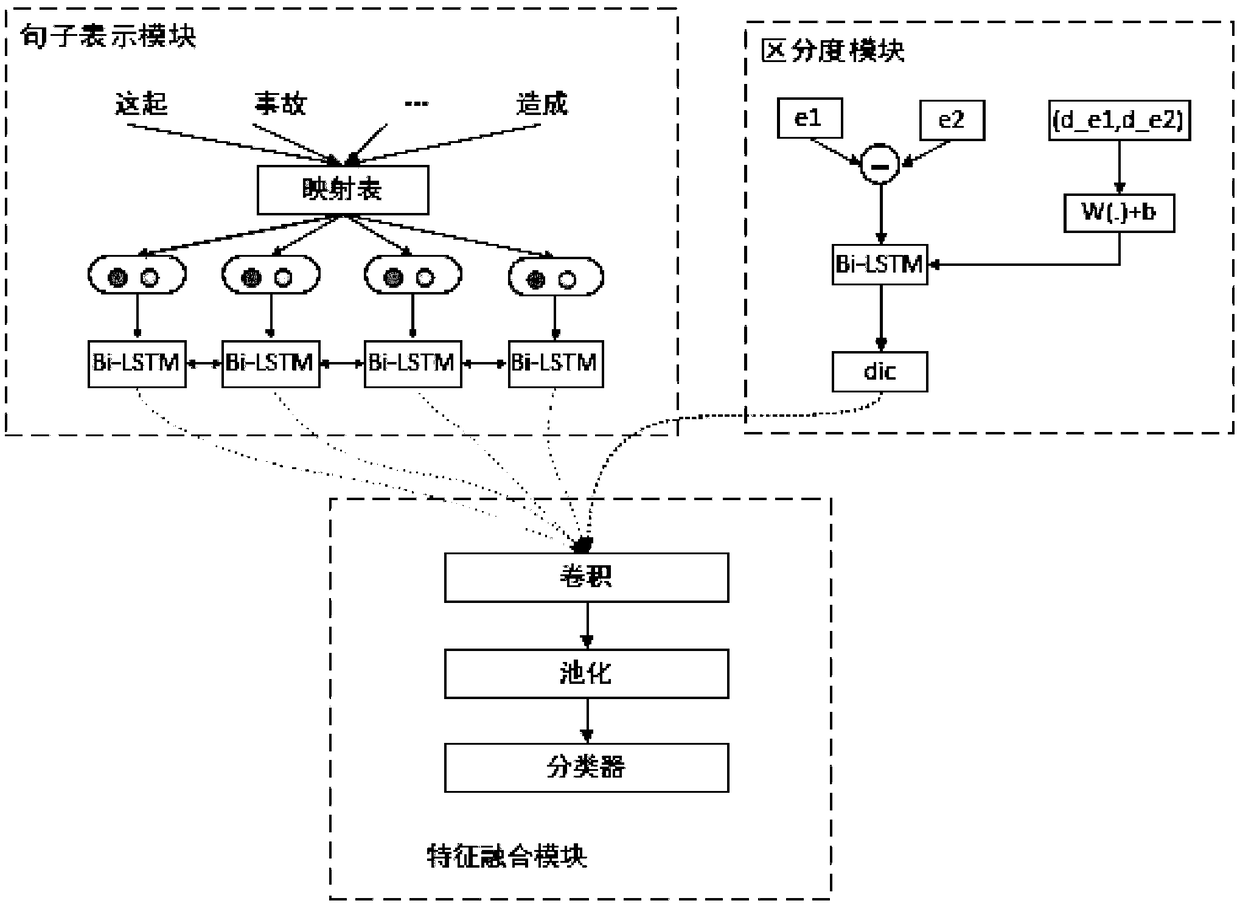
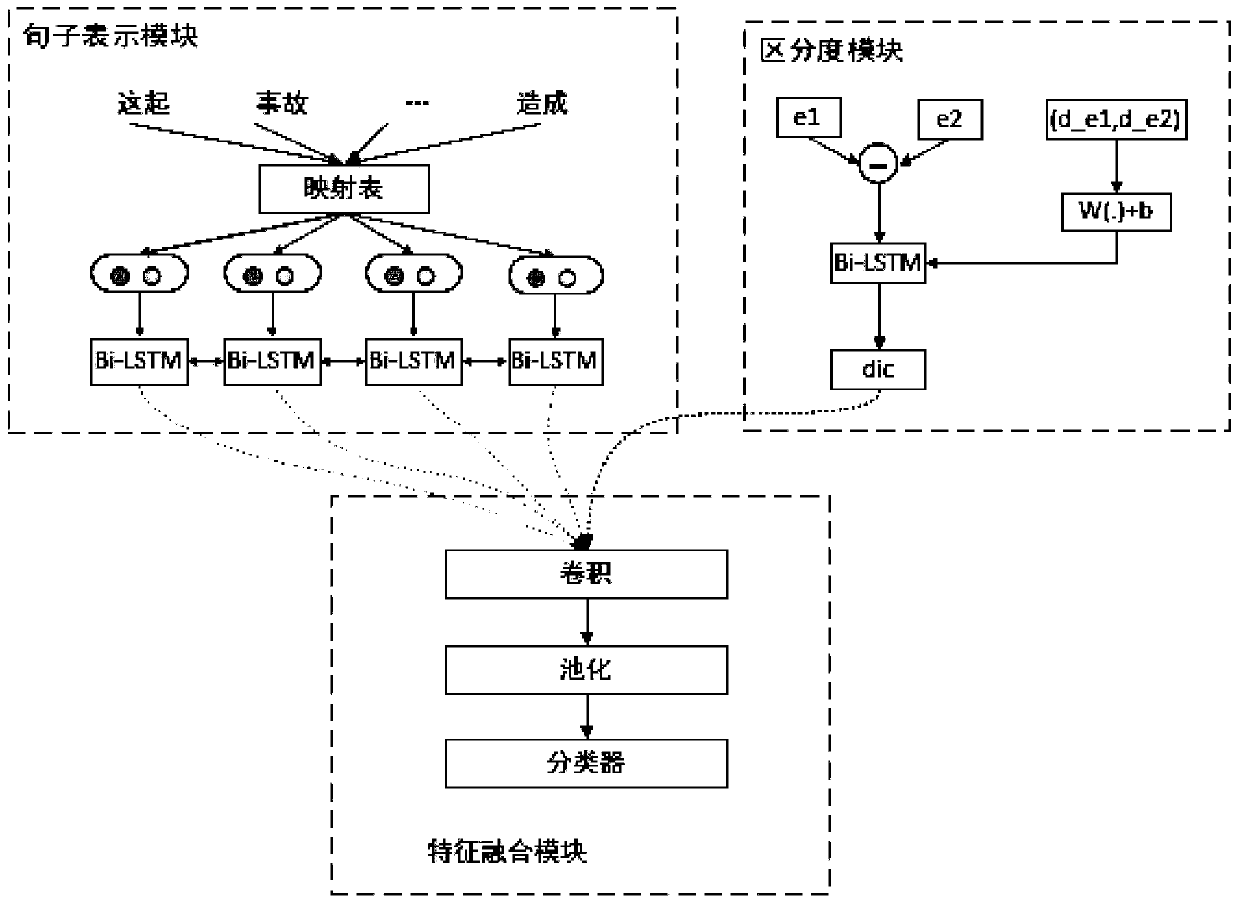
The invention relates to a neural network relation classification method and an implementation system thereof, which fuse discrimination degree information, comprising: (1) data preprocessing; (2) training word vector; (3) extracting position vector; Combining the word vector of each word with the high-dimensional position feature vector, the joint feature is obtained. (4) computing the semantic representation of sentences; The context information and semantic information of entities are encoded by bi-directional LSTM. (5) calculating a discrimination vector; After the two entity vectors are subtracted from each other and cascaded with a Bi-LSTM unit encode that input; (6) inputting the outputs of (4) and (5) to the CNN, outputting the feature vector fused with the discrimination information, and inputting the feature vector to the classifier for classification; (5) adopting a Loss function to train the model. The invention does not need to manually extract any features, and the jointmodel does not need to preprocess the data by means of other natural language processing tools, the algorithm is simple and clear, and the effect is best at present.
Owner:SHANDONG UNIV
Deep learning-based human action recognition method
InactiveCN107463879AImprove resolutionHigh similarityCharacter and pattern recognitionNeural architecturesPattern recognitionArtificial intelligence
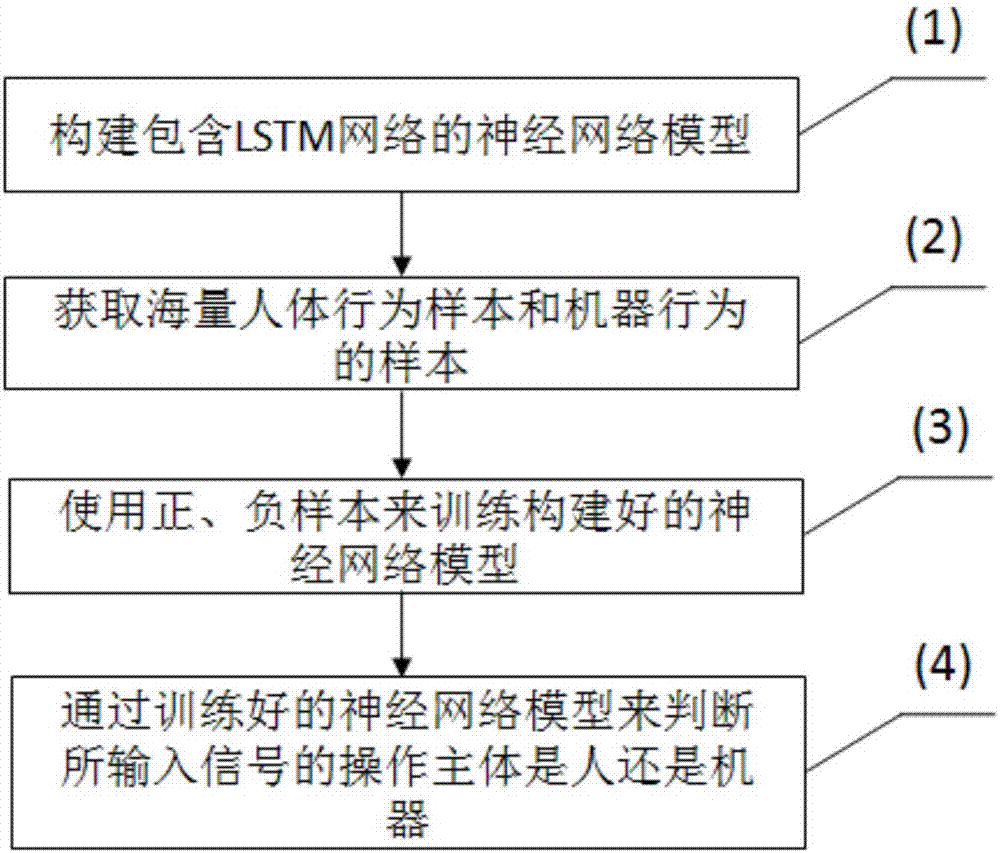
The invention relates to the field of captcha, in particular to a deep learning-based human action recognition method. According to the method, a neural network comprising an LSTM is adopted to realize the judgement of the current page operation main body; construction of machine action samples is based on human action samples; 4 generation manners which comprise random generation are adopted; positive sample tracks are randomly segmented into a plurality of sub-segments and the segmented sub-segments are randomly spliced; scaling and disturbance are carried out on track parameters on the basis of positive samples; and such a negative sample generation manner is based on the positive samples, so that the negative samples have higher similarity with the positive samples, the obfuscation is stronger, the neural network trained by training samples has higher distinguishing ability. According to the method, the recognition of the current page operation main body on the basis of an LSTM network is firstly realized; and the method is particularly suitable for the business scenes of realizing verification of operation main bodies during graph dragging and judging the operation main bodies.
Owner:成都数联铭品科技有限公司
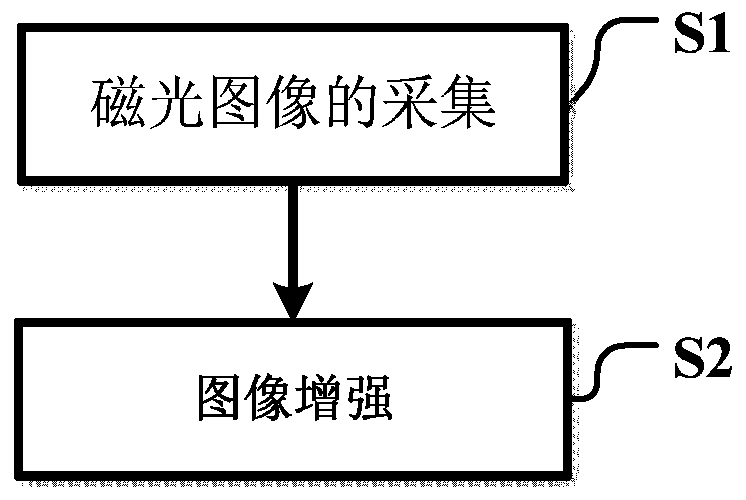
Magneto-optic image enhancement method based on optical flow algorithm
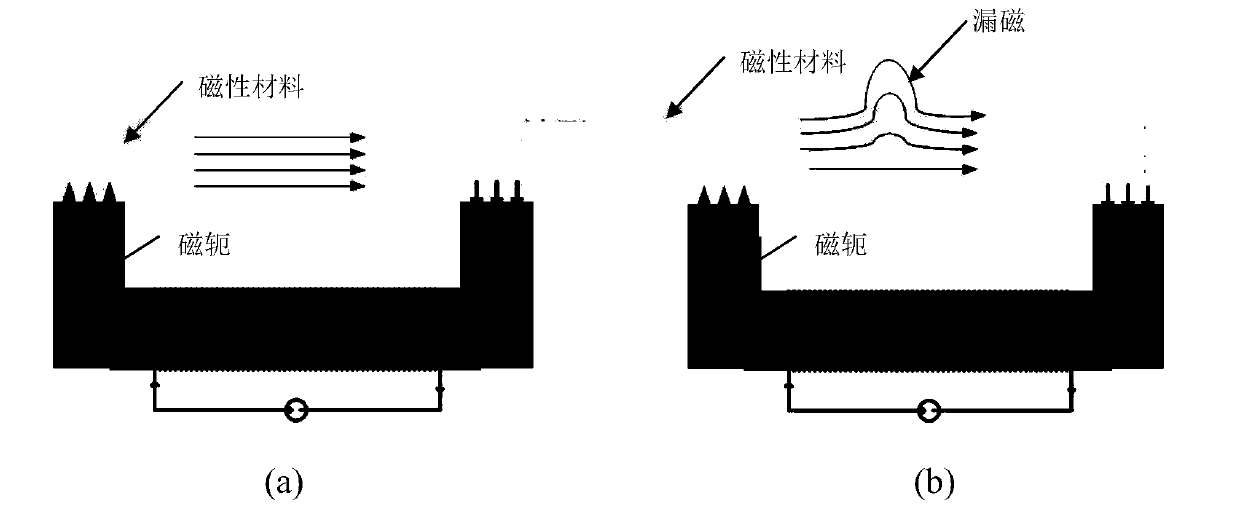
ActiveCN107180428ARich dataReduce skin effectImage enhancementImage analysisImage detectionSignal intensity
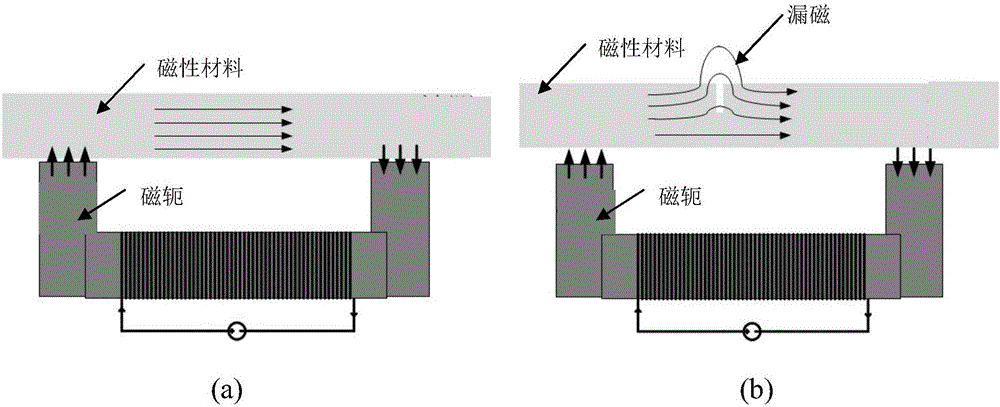
The invention discloses a magneto-optic image enhancement method based on an optical flow algorithm. Low-frequency AC excitation is used for excitation of a magnet yoke, an image set is obtained under different signal intensities through a periodic variable magnetic field, and a low-frequency signal enables magnetic force lines to pass through a deeper region of a detected object, thereby enabling a magneto-optic image to reflect the defect information of the deeper region, and reducing the impact from the skin effect. Meanwhile, the multi-point sampling and photographing (collection) can be carried out in one period, thereby increasing the data information of the magneto-optic image. However, the magneto-optic image obtained through the above method has the interference noise caused by magnetic domain movement under the action of a low-frequency AC signal, and is liable to be mixed with the defect information, thereby reducing the image detection information. Therefore, the method employs a pyramid optical flow algorithm for the iteration processing of the magneto-optic image, achieves the accumulation of feature points generating optical flow motion, and obtains an optical flow enhanced image. The enhanced image is more apparent in image gradient changes, greatly reduces the interference, and is more visual in defect information.
Owner:UNIV OF ELECTRONIC SCI & TECH OF CHINA
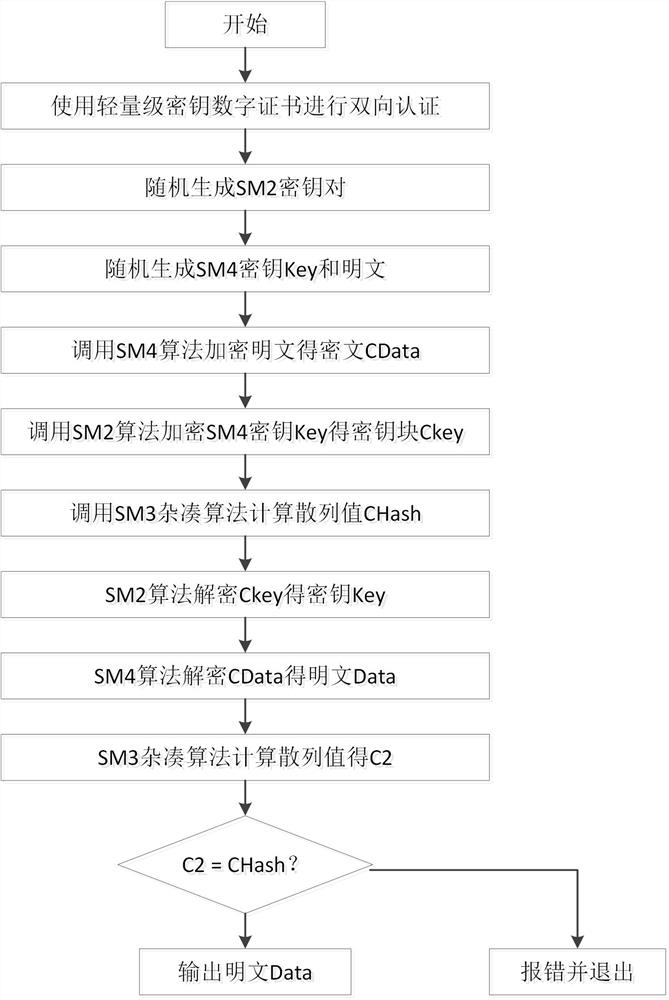
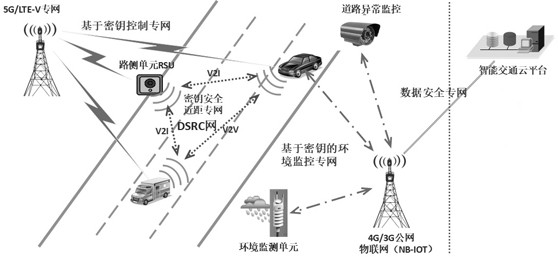
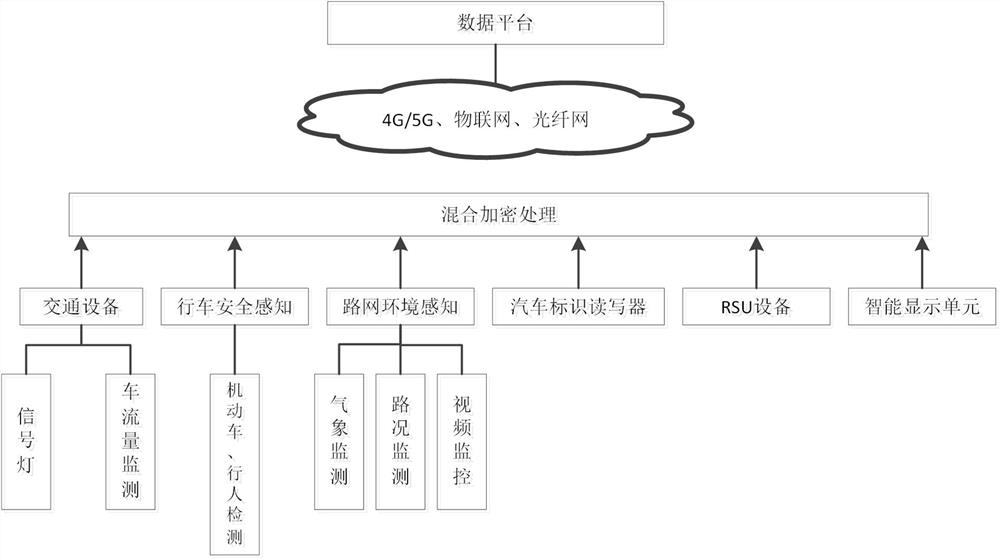
Traffic sensor network data transmission method and system based on hybrid encryption, and medium
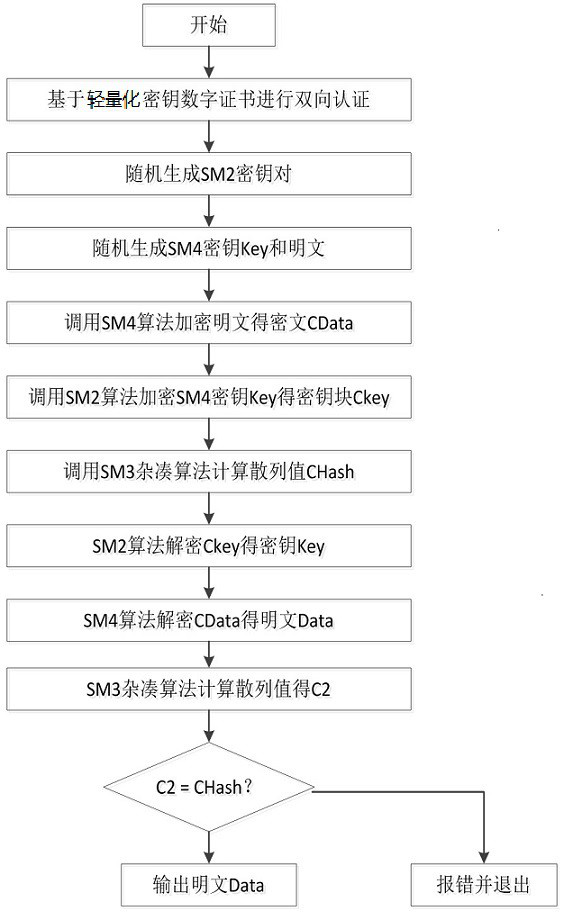
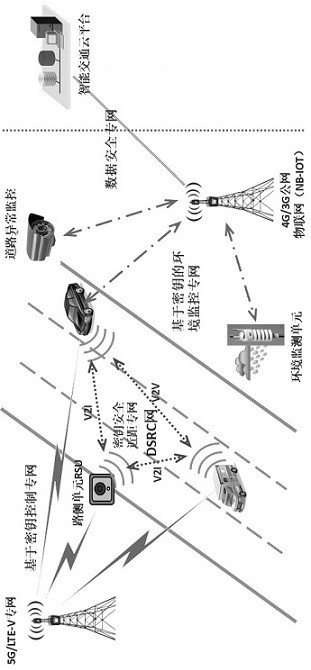
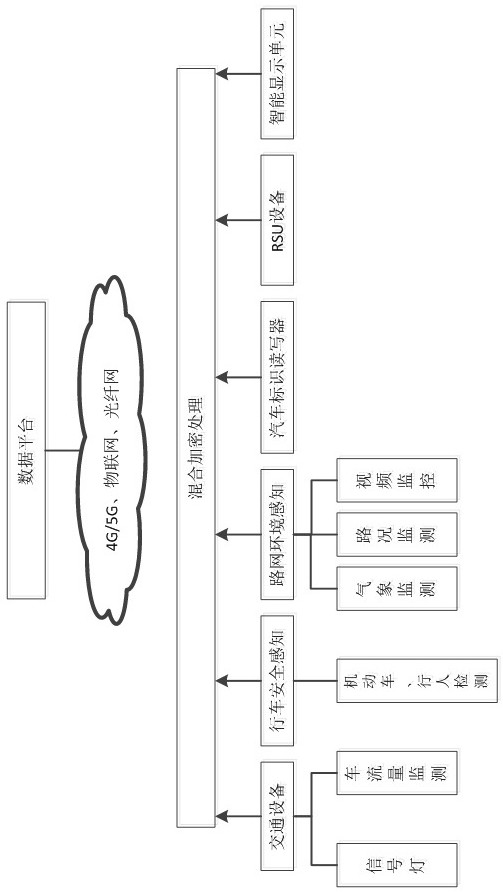
ActiveCN112469003ASimplify the data parsing processImprove authentication efficiencyParticular environment based servicesNetwork topologiesPlaintextSmart infrastructure
The invention discloses a traffic sensor network data transmission method and system based on hybrid encryption, and the method comprises the steps: carrying out the end-to-end data transmission between an intelligent vehicle-mounted terminal and intelligent infrastructure side equipment and a cloud computing center, and carrying out the bidirectional authentication through an intelligent trafficlight-weight secret key digital certificate borne by a server; and in the data transmission process, using a hybrid encryption transmission method for carrying out dual encryption on data, and meanwhile, adding a random key and a random plaintext to calculate a hash value for comparison and verification. According to the method, the advantages of high encryption and decryption speed of the SM4 symmetric encryption algorithm and low management difficulty and high security of the encryption key of the SM2 asymmetric encryption algorithm are combined, so that the method can be applied to the communication process of an intelligent terminal, intelligent basic side equipment and a computing center, and the security and the transmission efficiency of data transmission of the traffic sensor network can be effectively improved.
Owner:NANJING UNIV OF SCI & TECH
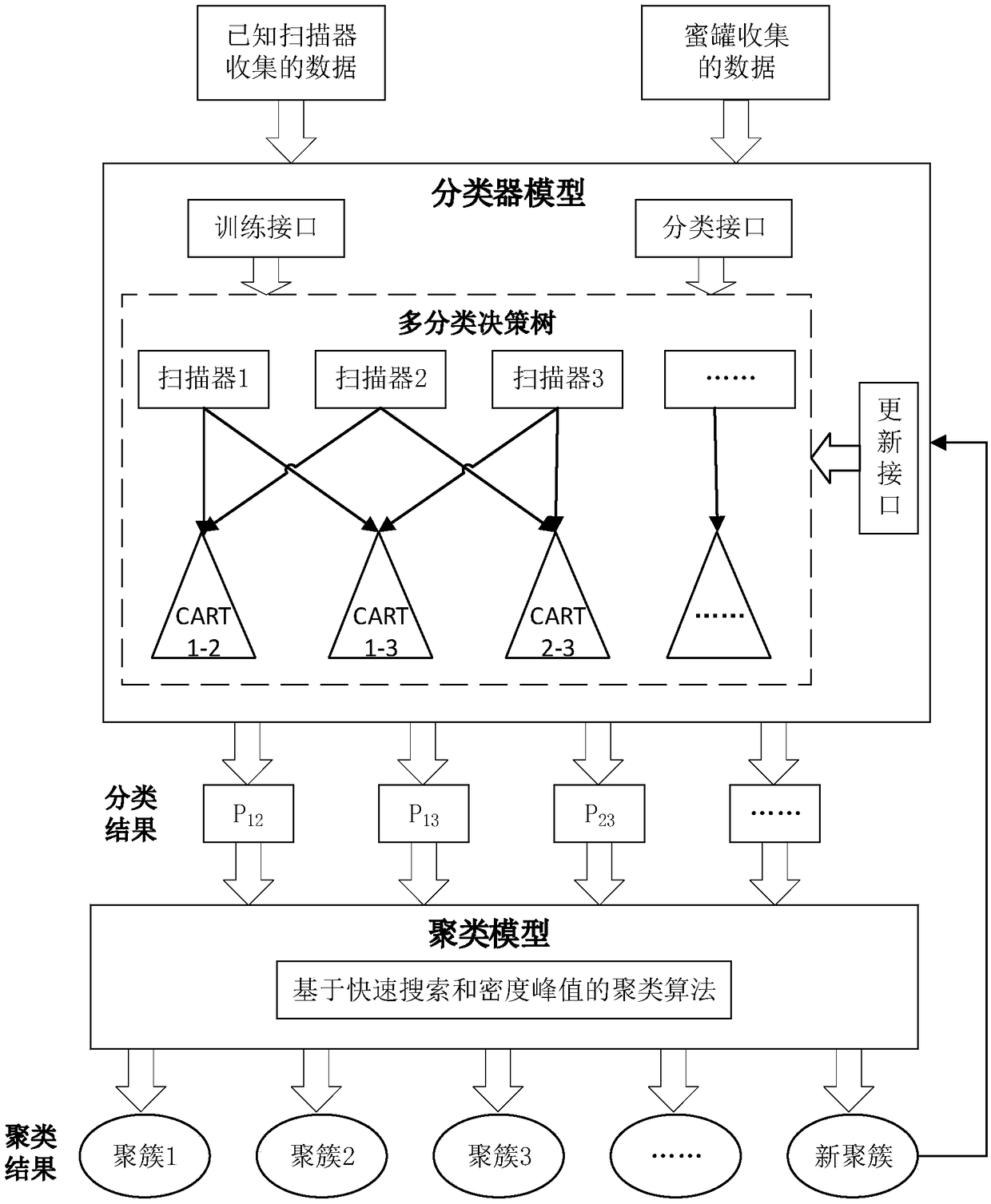
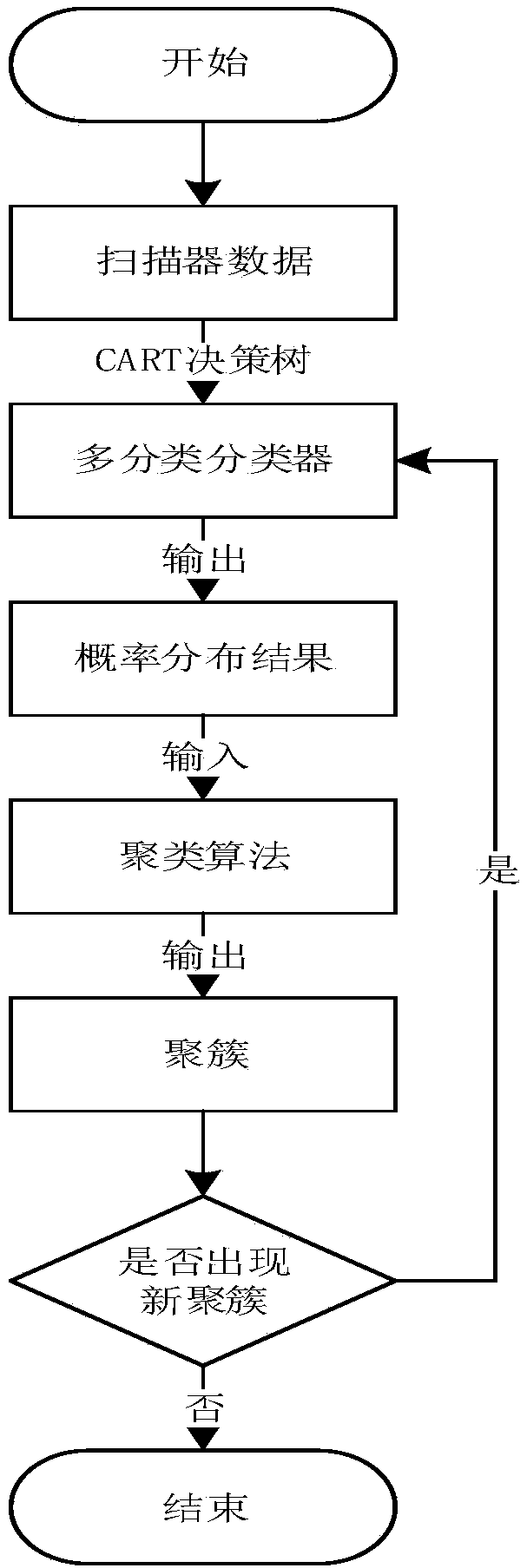
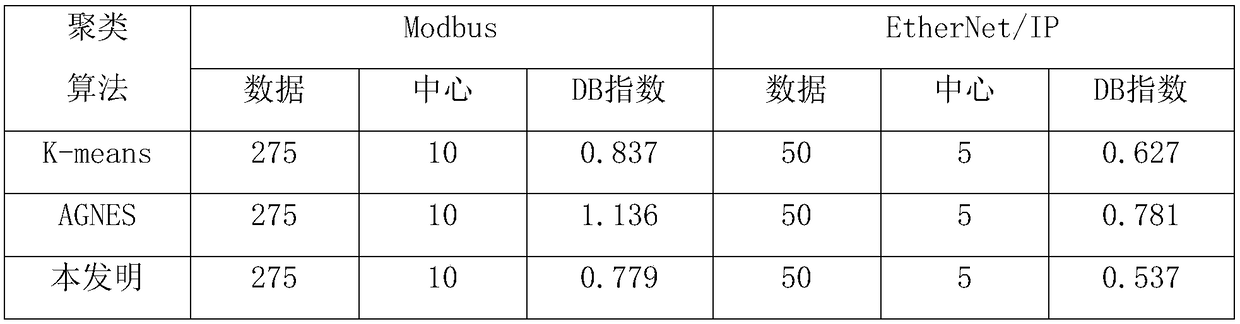
A fingerprint identification method of industrial control scanner based on honeynet data
ActiveCN109067778AHigh-precision identificationAccurate replyArtificial lifeTransmissionCluster algorithmComputer science
The invention provides a fingerprint identification method of an industrial control scanner based on honeynet data, comprising the following steps: scanning data captured through a honeypot network system in an industrial control network and an existing industrial control scanner are analyzed to obtain fingerprint information and a multi-classifier model of scanning data based on a CART decision tree is constructed. The multi-classification classifier model can effectively identify the specific scanning tools that initiate the scanning traffic and output the judgment probability of various scanner tags. After that, the output of the multi-classification classifier model will be used as the input data of the clustering algorithm. The clustering algorithm can discover the deeper relationshipbetween different scanning entities and form clustering. At the same time, the clustering algorithm can effectively extract scanning features of different clusters, form new scanner tags, and updatethem to the previous multi-classification decision tree, thereby improving the judgment ability of the invention for the novel scanner data.
Owner:NORTHEASTERN UNIV
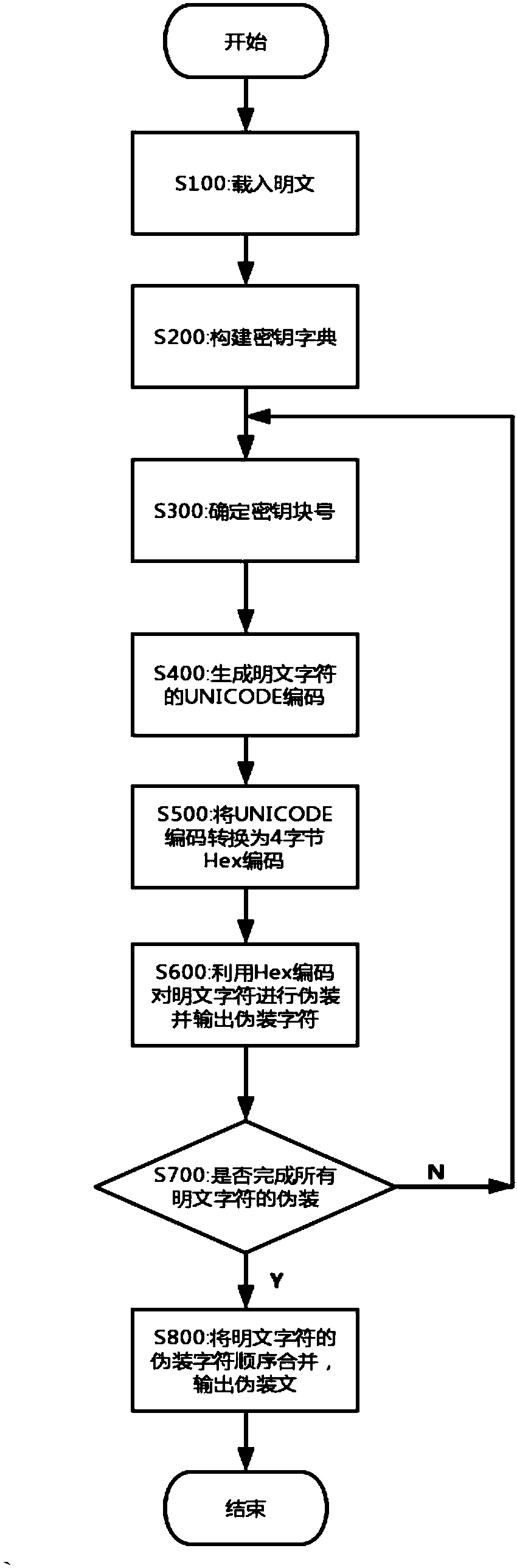
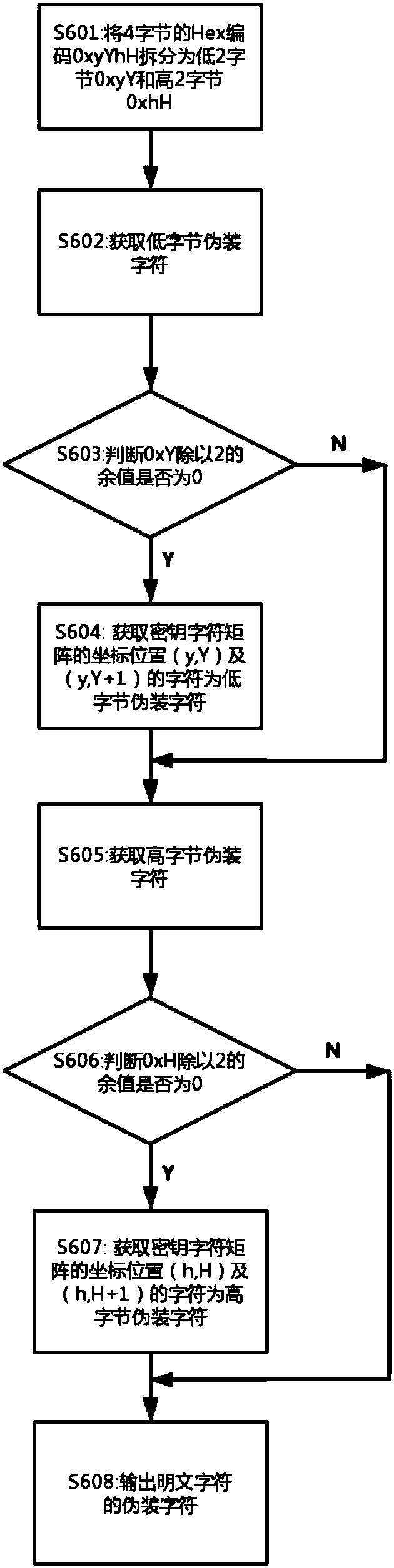
Method for performing camouflage and camouflage removal on characters based on unrepeated keys
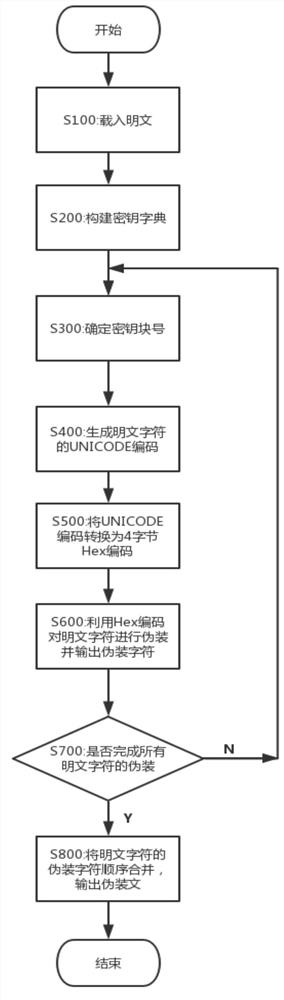
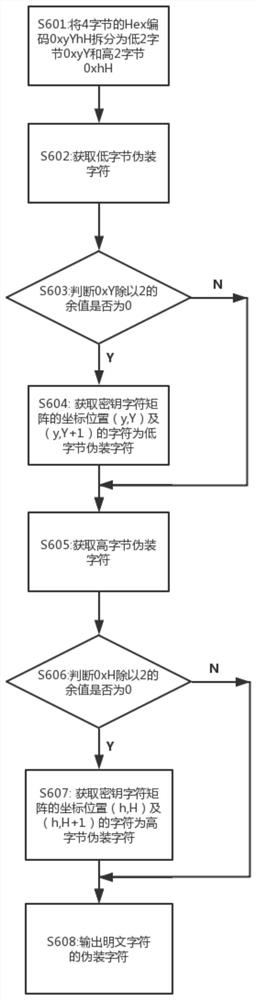
ActiveCN107659399AConfusingSolve the problem of the technical solution that does not camouflage the plaintextEncryption apparatus with shift registers/memoriesPlaintextByte
The invention discloses a method for performing camouflage and camouflage removal on characters based on unrepeated keys. The method is characterized by comprising the following steps: S100: loading plaintext; S200: constructing a key dictionary; S300: determining a key block number; S400: generating UNICODE codes of plaintext characters; S500: converting the UNICODE codes into 4 bytes of Hex codes 0xyYhH, wherein when the Hex codes are less than 4 bytes, filling the bytes via 0; S600: performing camouflage on the plaintext characters by using the Hex codes, and outputting camouflage characters; S700: judging whether the camouflage of the plaintext characters is completed, if so, executing step S800, and otherwise, executing step S300; and S800: merging the camouflage characters of the plaintext characters in sequence, and outputting a camouflage text. The camouflage removal can be performed on the camouflage text by a reverse method, and the plaintext is output.
Owner:SICHUAN QIAODUOTIANGONG PRECISION EQUIP CO LTD
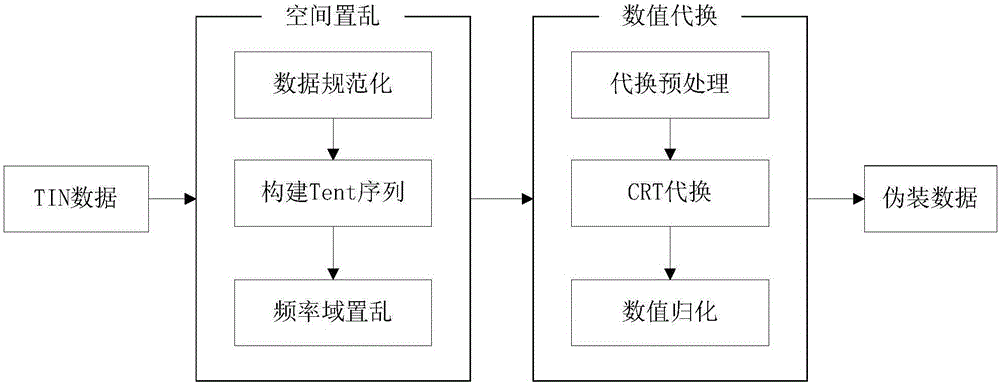
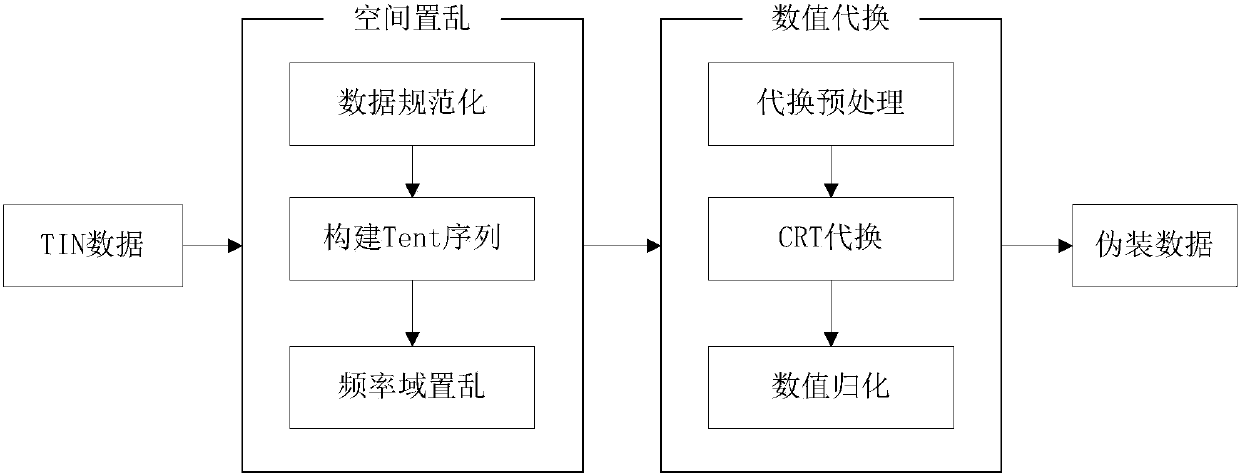
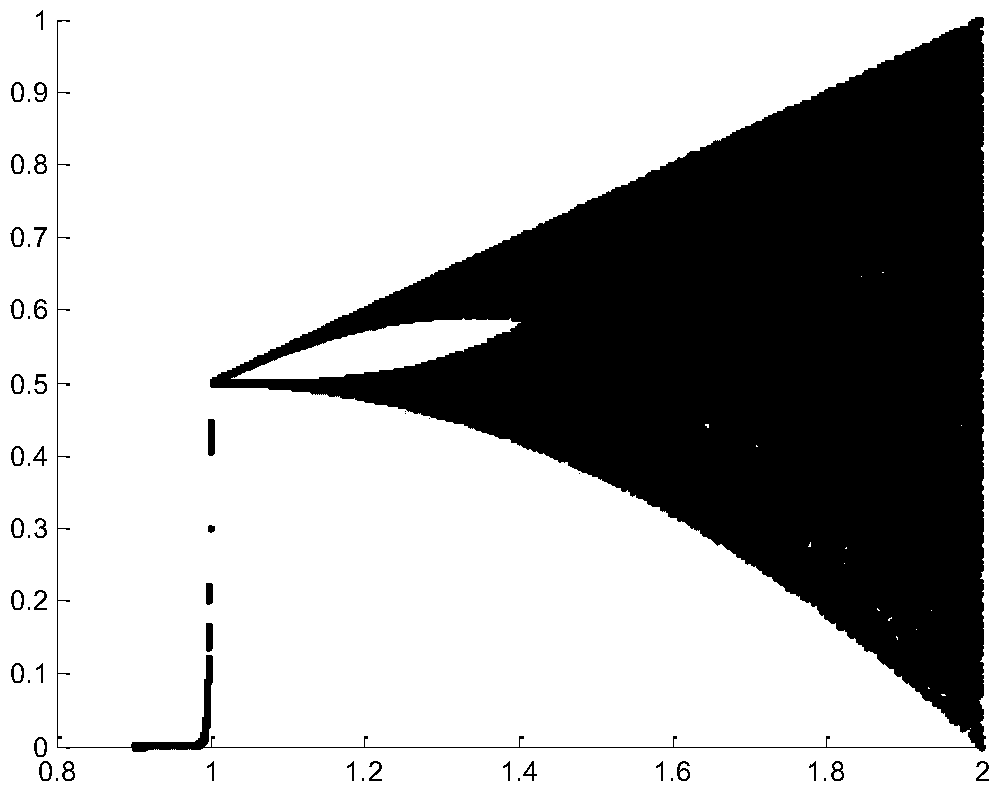
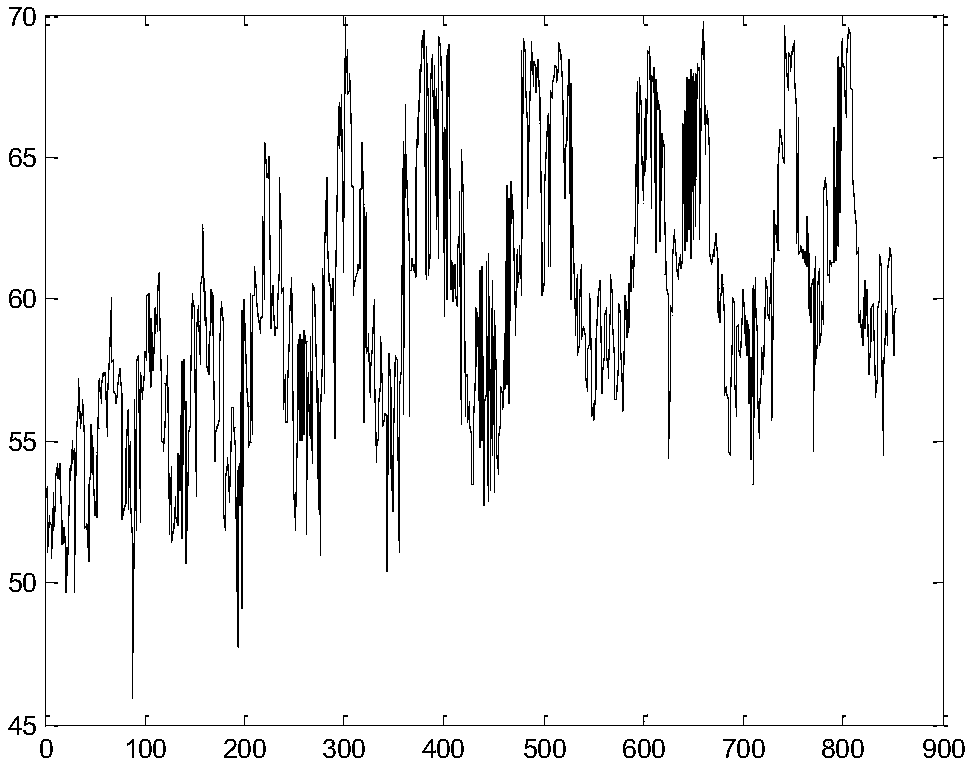
Information disguising and reducing methods suitable for triangulated irregular netting digital elevation model
ActiveCN105005961ASafe storageGuaranteed normal transmissionImage data processing detailsProgram/content distribution protectionChinese remainder theoremConfusion
The invention relates to information disguising and reducing methods suitable for a triangulated irregular netting digital elevation model, and belongs to the technical field of digital elevation data processing. The information disguising method mainly comprises space scrambling and numerical value substitution, wherein the space scrambling is implemented through a Tent chaotic mapping way; and the numerical value substitution is carried out through a Chinese remainder theorem. Compared with a conventional information protection method, the information disguising and reducing method has the advantages that information protection is carried out through the information disguising way, so that the advantages of high confusion and high security performance are realized; security protection can be provided for important elevation information in the triangulated irregular netting digital elevation model; and the storage and transmission of data in the triangulated irregular netting digital elevation model can be effectively ensured.
Owner:THE PLA INFORMATION ENG UNIV
Mechanical combination lock capable of eliminating three technical unlocking hidden troubles for safety box
InactiveCN102155118AThe means of committing the crime are easy to succeedImprove concealmentPuzzle locksPermutation locksDynamic balanceEngineering
The invention relates to a mechanical combination lock capable of eliminating three technical unlocking hidden troubles for a safety box, relating to a combination lock for a safety box; the mechanical combination lock uses an inner board in parallel and fixedly connected with the door plank of the safety box, a turn-knob shaft sleeve fixed into the inner board and the door plank interlayer of the safety box and extending outwards, a combination wheel assembly rotating on the extending part of the turn-knob shaft sleeve, an unlocking limit wheel matched with a compression spring and in clutch type match with a driving combination wheel, a retractable turn-knob and a lock executing mechanism; the mechanical combination lock eliminates the three hidden troubles of friction type technical unlocking, percussive technical unlocking and measuring dynamic balancing technical unlocking, and has 6.8 million times of dense variables; therefore, the mechanical combination lock becomes the mechanical combination lock with the strongest security at all times and in all lands, and is a novel product in the field. The mechanical combination lock is simple in structure, saves material, has reliable performance and long service life, and can be applied to safety boxes and document boxes in family.
Owner:石淳民
Specificity method for detecting candida albicans in clinical specimen
ActiveCN103196906AImprove the detection rateShorten the timeMaterial analysis by observing effect on chemical indicatorAntiserumBlood serum
Owner:众爱生河北生物科技有限公司
Process for preparing large super-thick nodular cast iron container sample
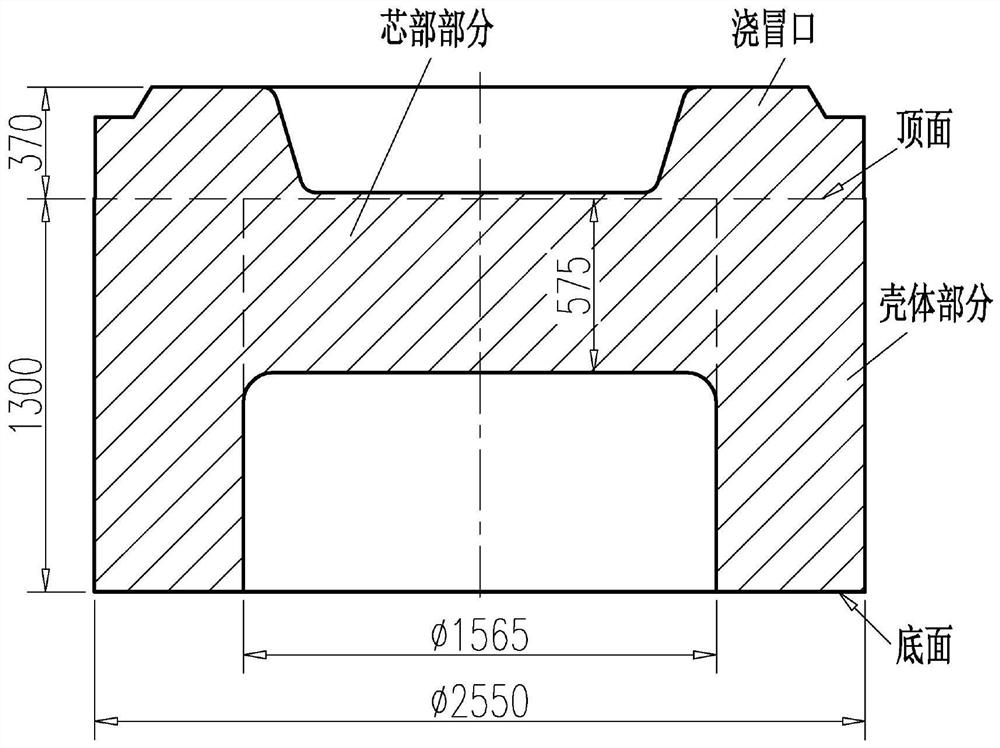
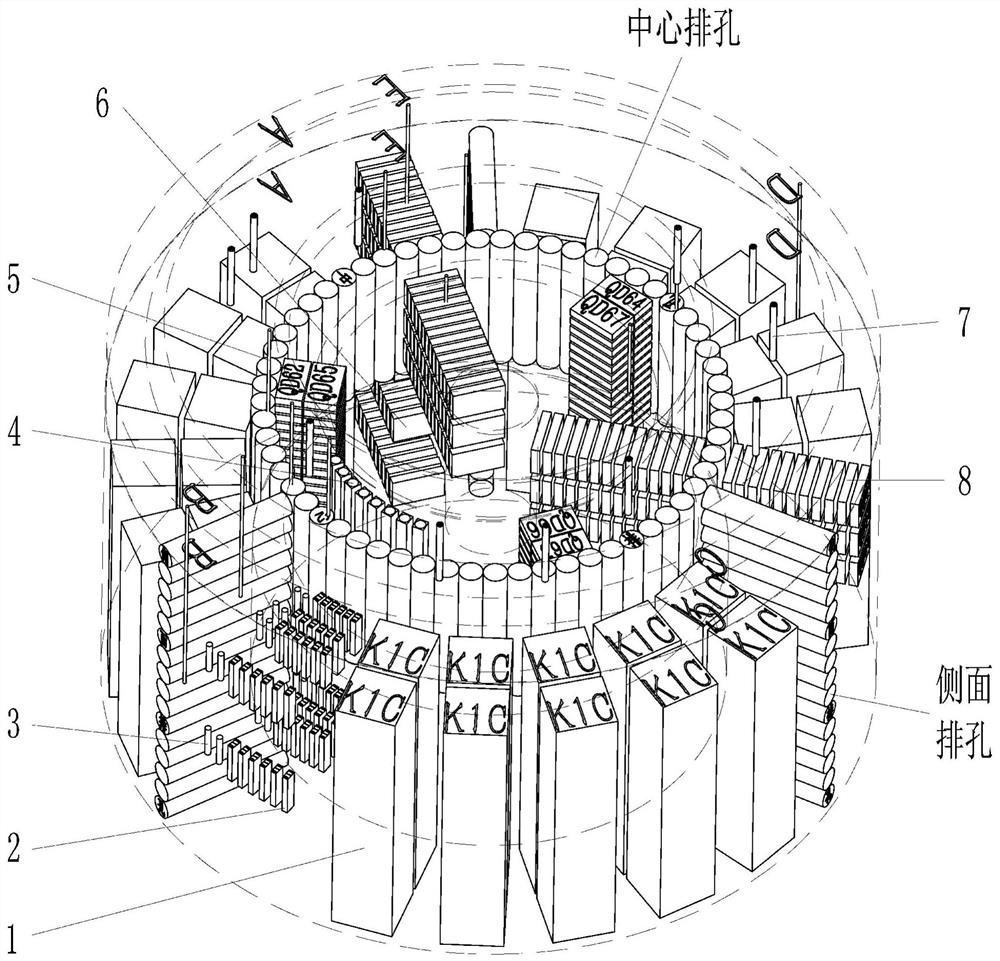
ActiveCN110907242APerformance is not affectedReduce processing costsPreparing sample for investigationEngineeringDuctile iron
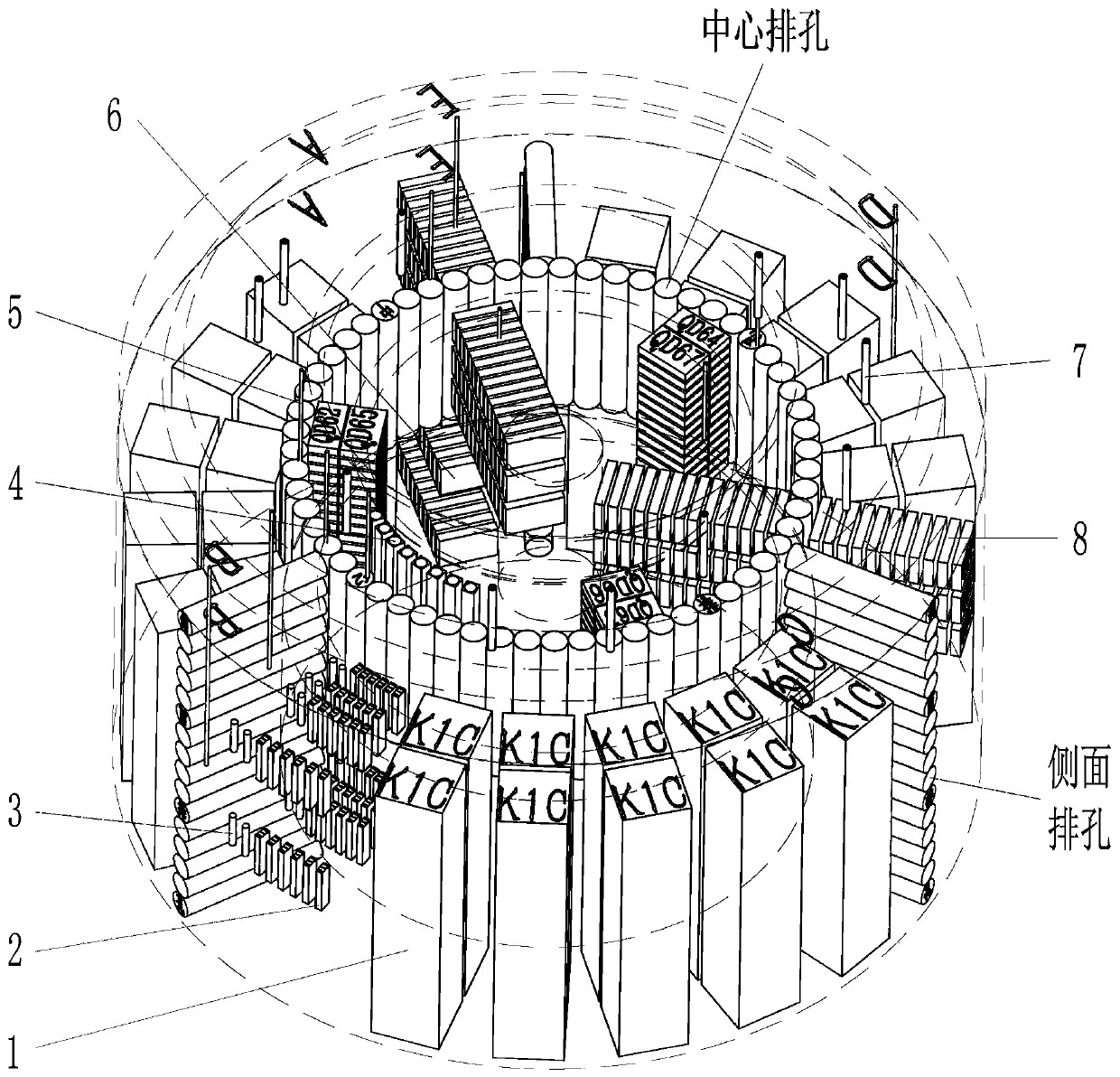
The invention relates to a process for preparing a large super-thick nodular cast iron container sample, which comprises: taking out a TM sample by using a trepanning drill blind hole sample preparation process, removing excess materials by turning or milling, and sequentially preparing a casting body by using the following processes: preparing a TD sample by using a trepanning drill; drilling a circle of central row holes at the diameter distribution position of the TD sample, wherein every two central row holes are intersected; longitudinally drilling three rows of through holes in the positions of the side face row holes and are evenly distributed in the circumferential direction by 120 degrees, and evenly dividing the positions of three sets of H1000 samples of the nodular cast iron container shell into three fan-shaped parts; sawing the 120-degree fan-shaped part into a 90-degree part and a 30-degree part respectively; longitudinally sowing off the 90-degree part in a five-equal-part mode according to 17 degrees, longitudinally sowing the 90-degree part into two equal parts respectively from the middle, namely an H1000 sample, and then milling the H1000 sample according to the size to meet the requirement; sawing the core part from the middle, and equally dividing the core part into two semicircles; and marking position lines from the top surfaces of the segmented parts according to respective regions, and further segmenting by using a conventional small sawing machine.
Owner:JIANGSU JIXIN WIND ENERGY TECH
Intelligent mosquito repelling and capturing device
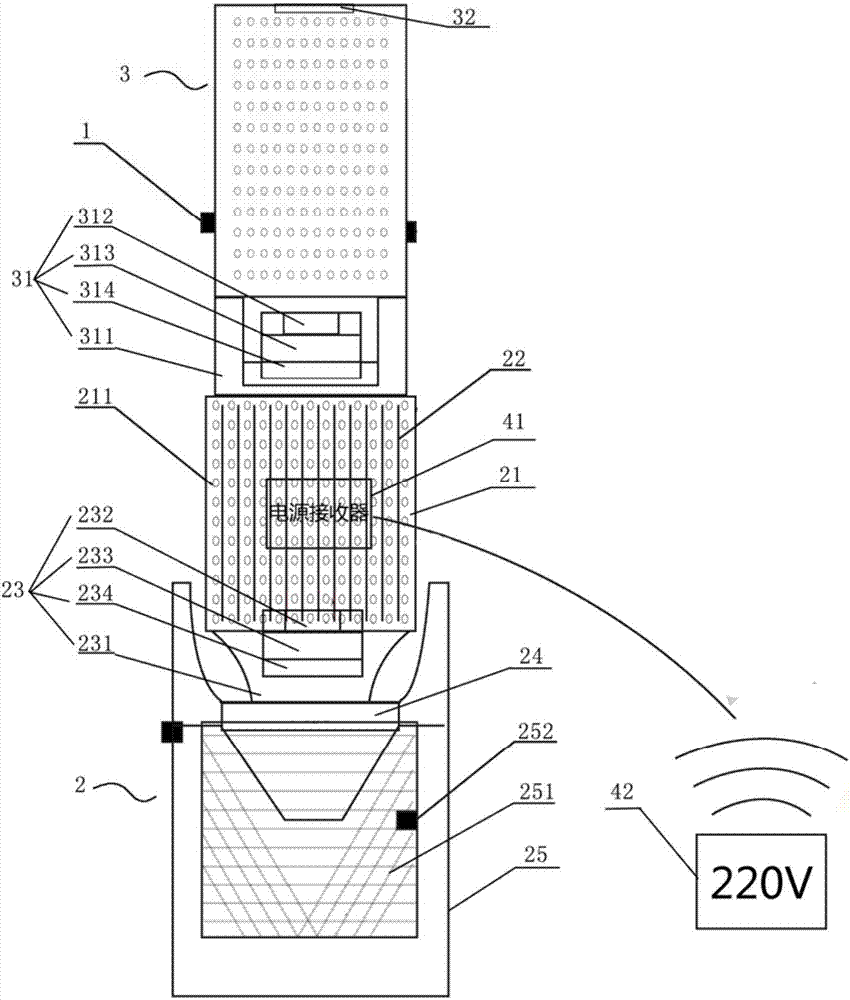
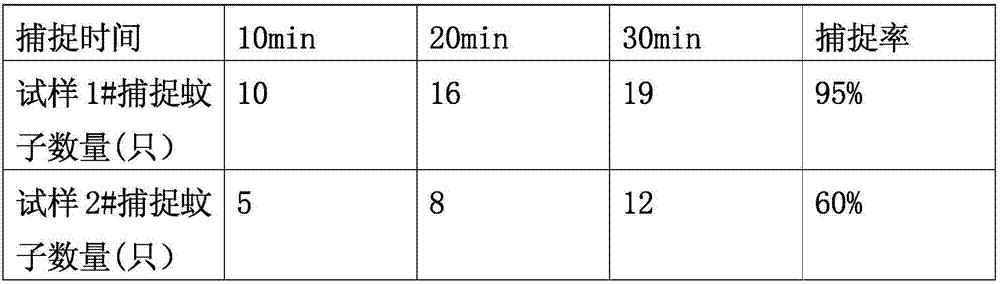
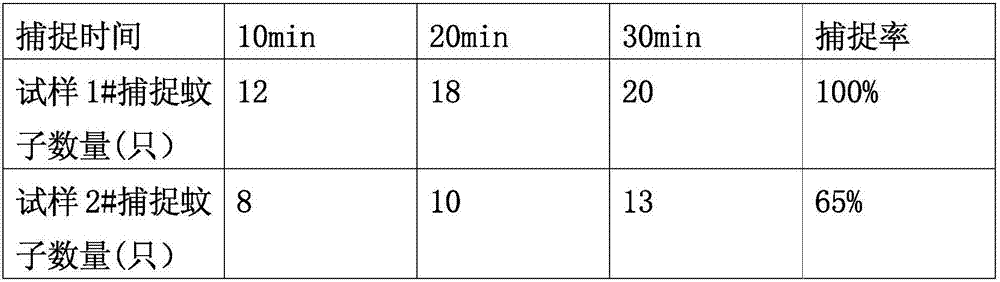
The invention discloses an intelligent mosquito repelling and capturing device. The device comprises a mosquito detection module, a mosquito capturing module, a mosquito repelling module and a power supply module, wherein the mosquito capturing module comprises bionic human body silica gel, carbon fiber heating sheets, a mosquito trapping diffuser, an exhaust fan and a mosquito storage chamber; the surface of the upper portion of the mosquito trapping diffuser is wrapped with a layer of bionic human body silica gel; the carbon fiber heating sheets are uniformly distributed between the mosquitotrapping diffuser and the bionic human body silica gel; the lower portion of the mosquito trapping diffuser is sleeved with the mosquito storage chamber, and the exhaust fan is arranged between the mosquito trapping diffuser and the mosquito storage chamber so as to suck in mosquitoes on the surface of the bionic human body silica gel; the mosquito repelling module comprises a mosquito repellingdiffuser and an orange light source, the mosquito repelling diffuser is arranged on the mosquito capturing diffuser, and the orange light source is arranged on the surface of the mosquito repelling diffuser. By the adoption of the intelligent mosquito repellent device, mosquito repelling and mosquito capturing modes can be automatically switched, the bionic degree is improved, and the intelligentmosquito repelling and capturing device has the advantages of being good in mosquito repelling and capturing effect, low in using cost and wide in application range.
Owner:佛山市顺德区欧凯电器科技有限公司
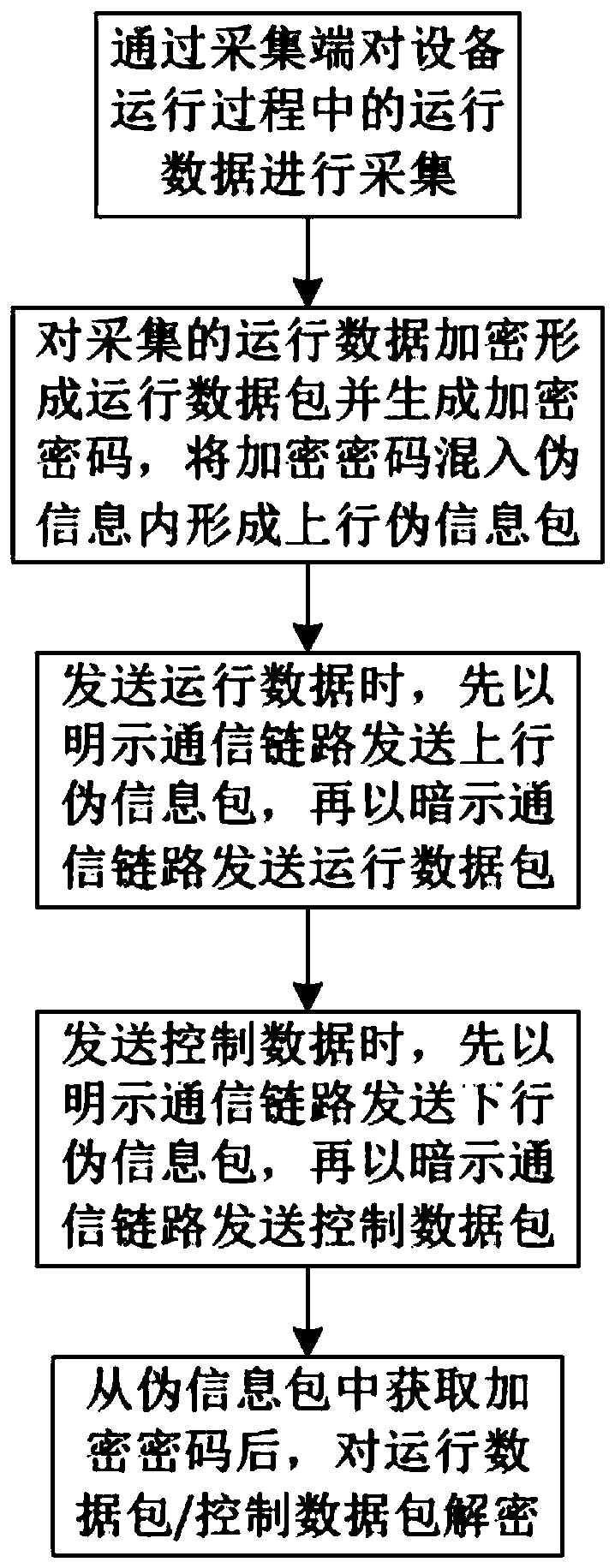
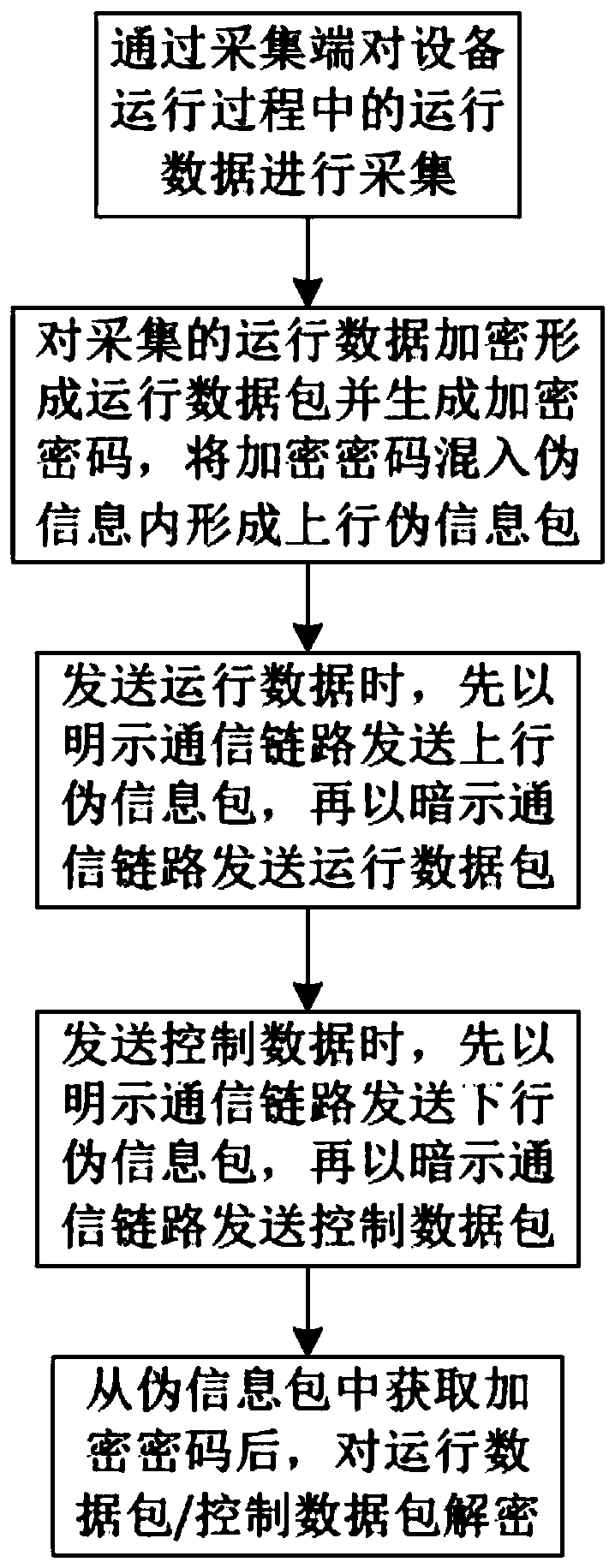
Remote operation and maintenance and data exchange method for equipment industrial control security
The invention relates to the technical field of information security, particularly relates to a remote operation and maintenance and data exchange method for equipment industrial control security. Themethod includes the following steps: s100, acquiring operation data in the operation process of the equipment through an acquisition terminal; and S200, encrypting the collected operation data to form an operation data packet and generate an encryption password, mixing the encryption password into the pseudo information to form an uplink pseudo information packet, and S300, when sending operationdata, sending the uplink pseudo information packet first and then sending the operation data packet. According to the method, the probability that the operation data packet is intercepted is reducedby counterfeiting normal operation data, the safety of sending the operation data is improved, and meanwhile, the encryption password is sent firstly, so that subsequent decoding is facilitated.
Owner:贵州航天云网科技有限公司
Method and an apparatus for realizing network traceless honeypot
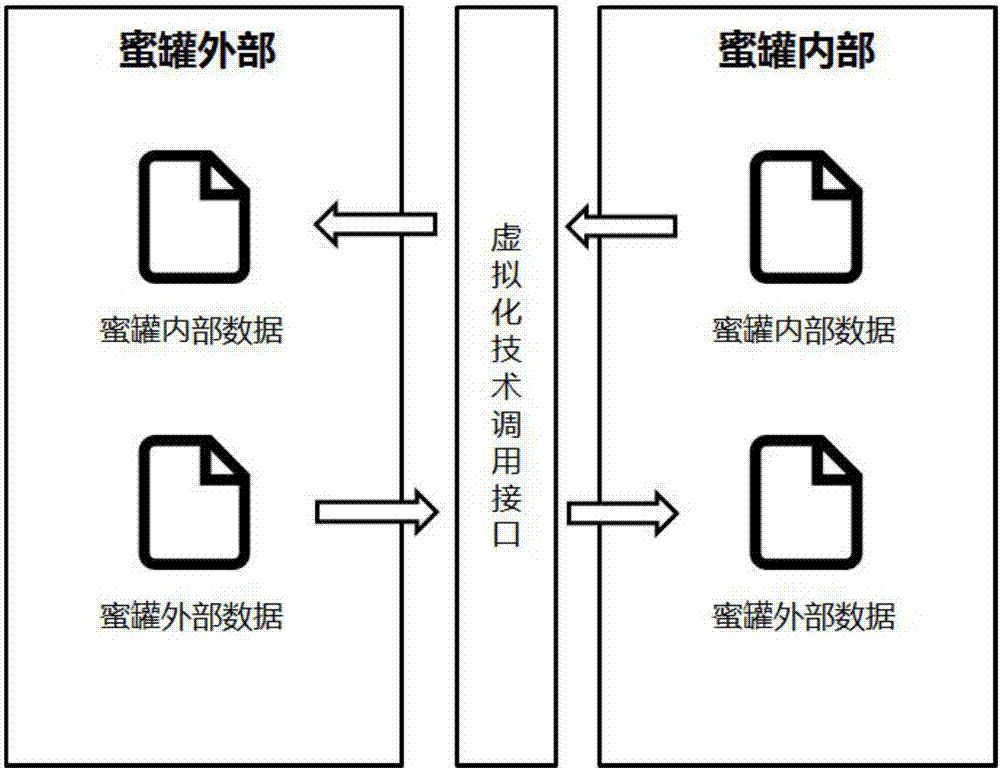
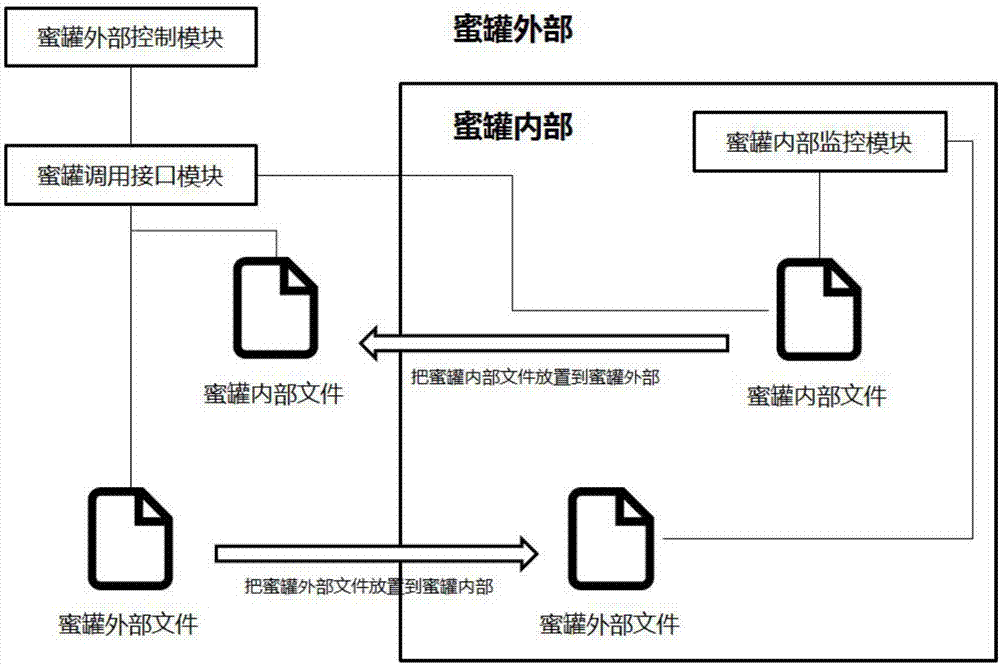
InactiveCN107465663AGuaranteed concealmentImplement two-way transmissionTransmissionComputer hardwareVirtualization
The invention provides a method and apparatus for realizing a network traceless honeypot. The method comprises the following steps: a honeypot environment is set up by use of a virtualization technology, through a control mode provided by the virtualization technology, a honeypot external control module actively initiates data transmission with a honeypot internal monitoring module, such a mode does not generate network flows in the honeypot environment, and the network location of a honeypot external control program cannot be obtained at all in a honeypot. The invention also brings forward a corresponding apparatus. Through the network traceless honeypot, network behavior of uploading data in the honeypot can be hidden completely, an attacker is quite confused, and thus the purpose of more effectively luring the attacker is realized.
Owner:广州锦行网络科技有限公司
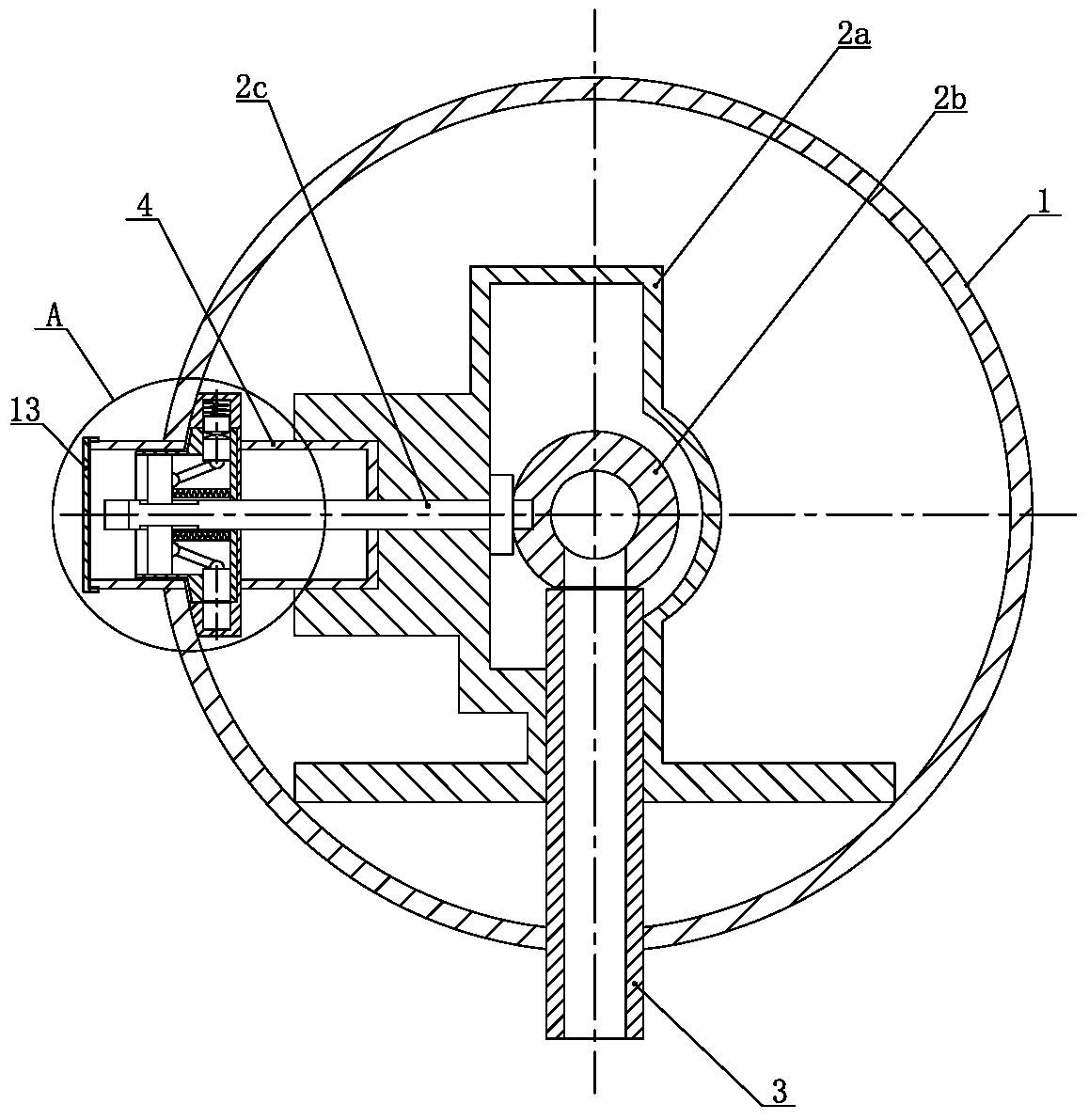
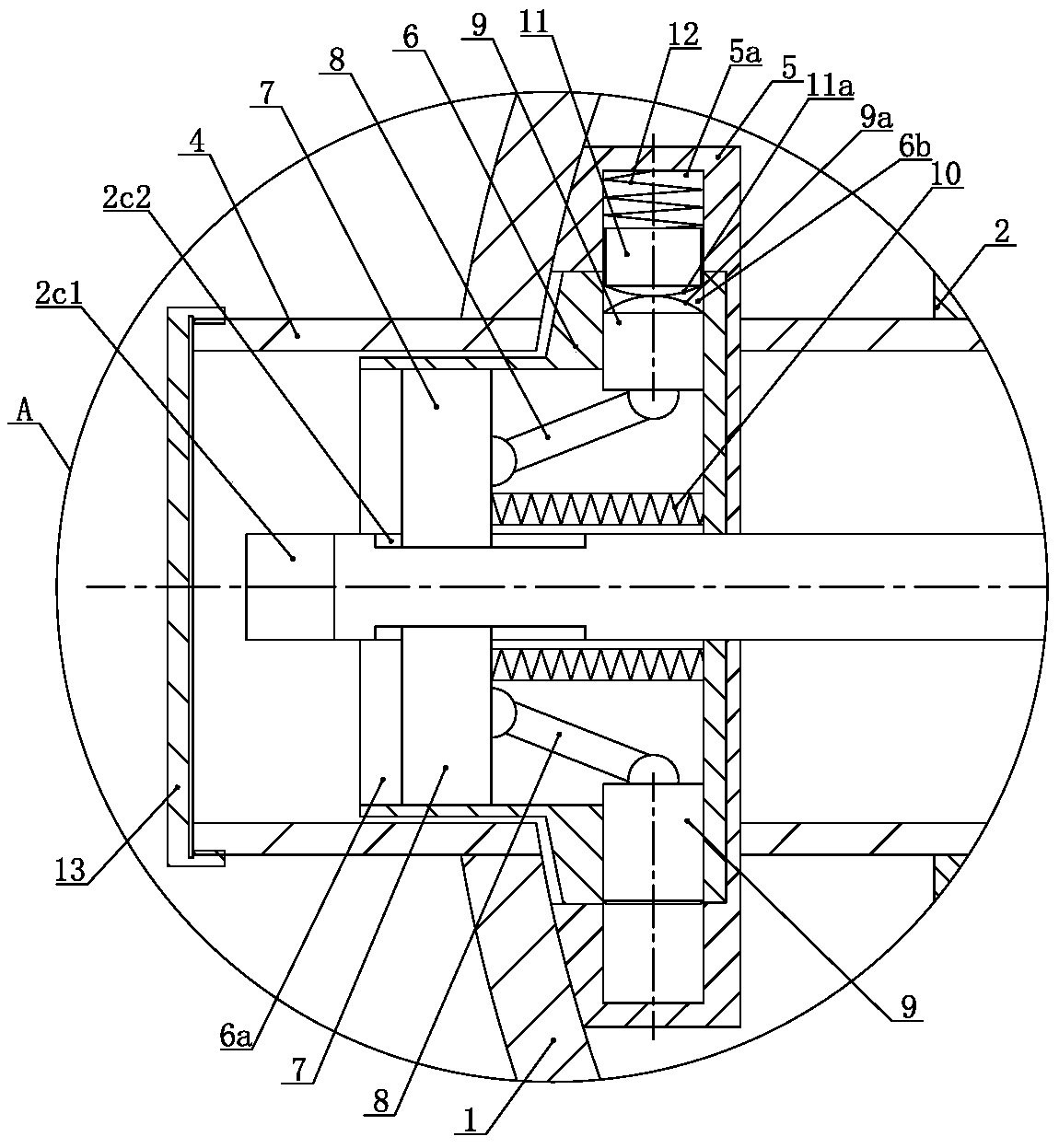
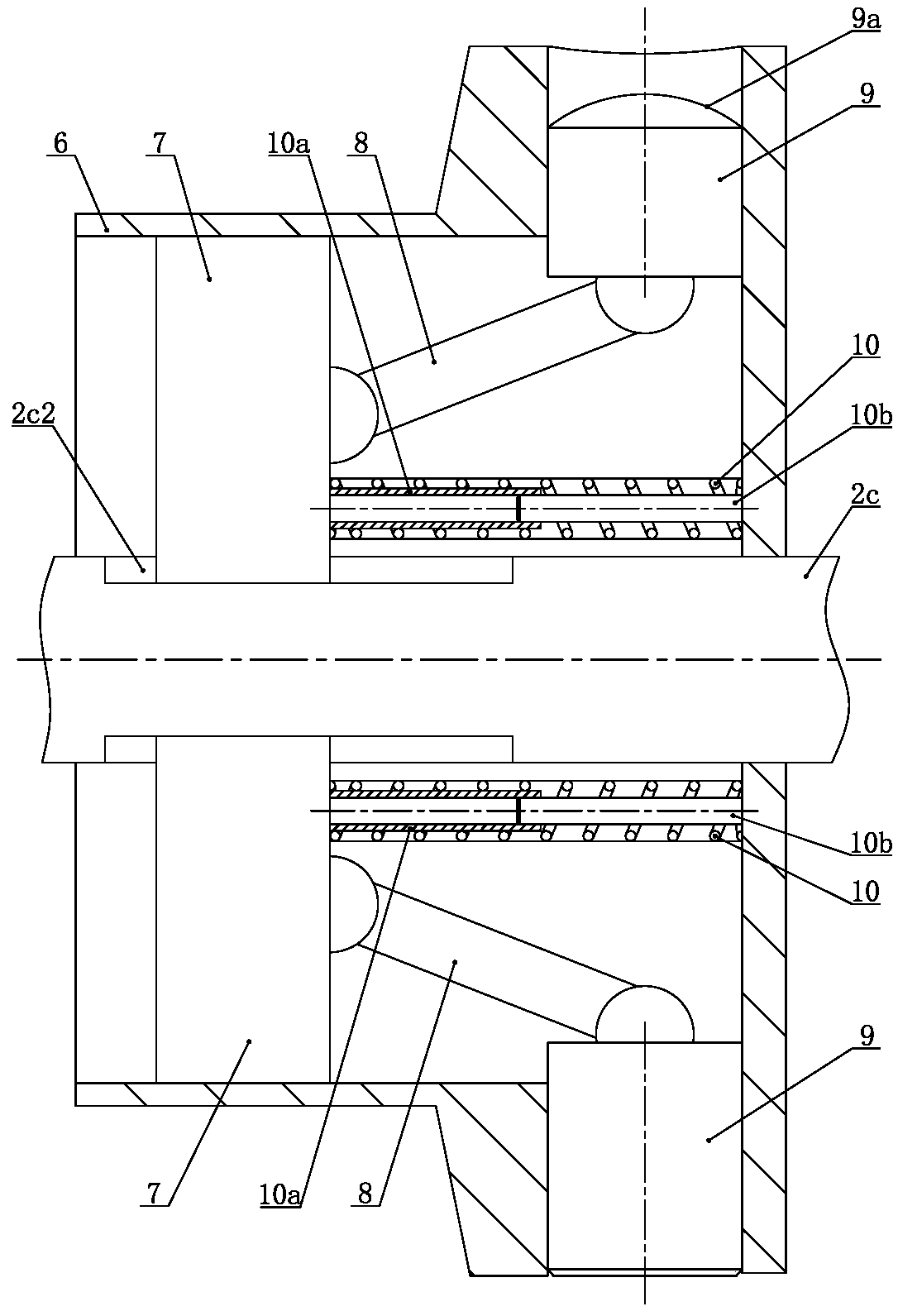
Wellhead anti-theft sampling device
ActiveCN110306949APrevent freezingImprove anti-theftConstructionsSpannersLocking mechanismEngineering
The invention relates to a wellhead anti-theft sampling device. The wellhead anti-theft sampling device comprises a sampling pipe, wherein a three-way cock valve is fixed in the sampling pipe; the three-way cock valve comprises a valve body, a spherical valve element and a valve rod for controlling the spherical valve element; a protective jacket is arranged on the periphery of the valve rod, theinner end of the protective jacket is connected with the valve body in a sealed mode, the outer end of the protective jacket stretches out of the sampling pipe and over the outer end of the valve rod,a valve rod square tenon is arranged at the outer end of the valve rod, the middle section of the protective jacket is provided with a fixing sleeve, the fixing sleeve and the protective jacket are coaxial, the valve rod penetrates out of the center of the bottom wall of the fixing sleeve, and a valve rod control mechanism is arranged in an inner cavity of the fixing sleeve; and the valve rod control mechanism comprises a lock cylinder which is coaxial with the fixing sleeve, the lock cylinder is in a T-shaped cross section, the large end of the lock cylinder is rotationally embedded in the inner cavity of the fixing sleeve, the small end of the lock cylinder is rotationally embedded in the inner cavity of the protective jacket, the center of the lock cylinder is fixedly connected with the valve rod, a plurality of lock cavities are formed in the lock cylinder, and locking mechanisms capable of locking or unlocking the lock cylinder and the fixing sleeve is arranged in the lock cavities. The wellhead anti-theft sampling device is convenient to operate and good in anti-theft performance.
Owner:CHINA PETROLEUM & CHEM CORP +1
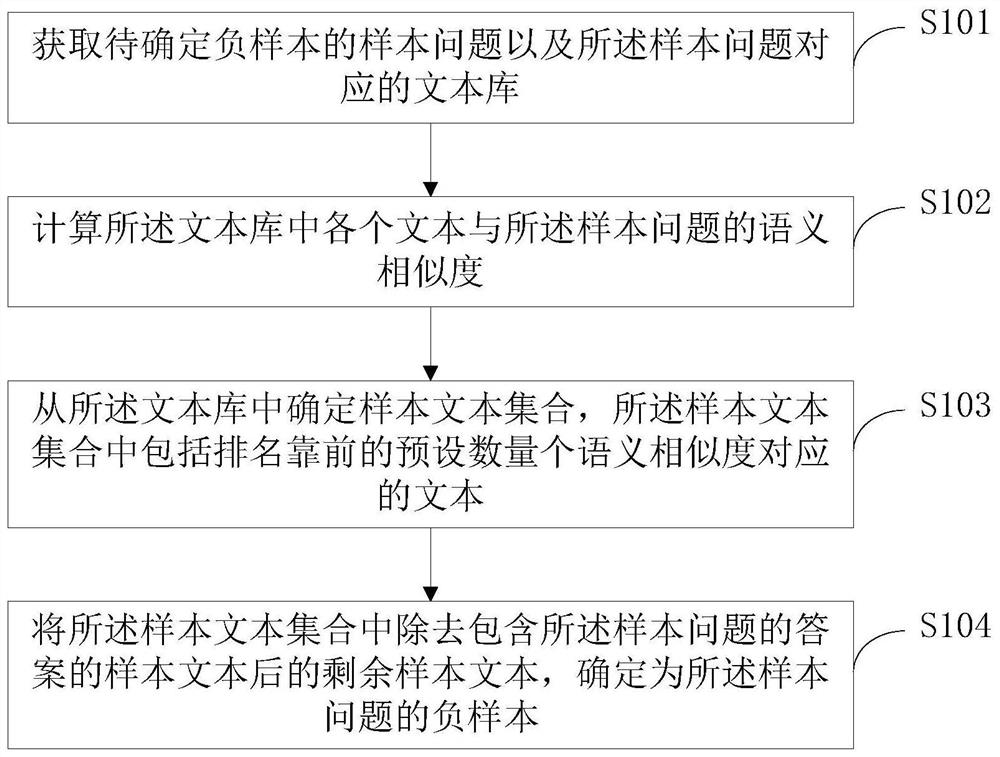
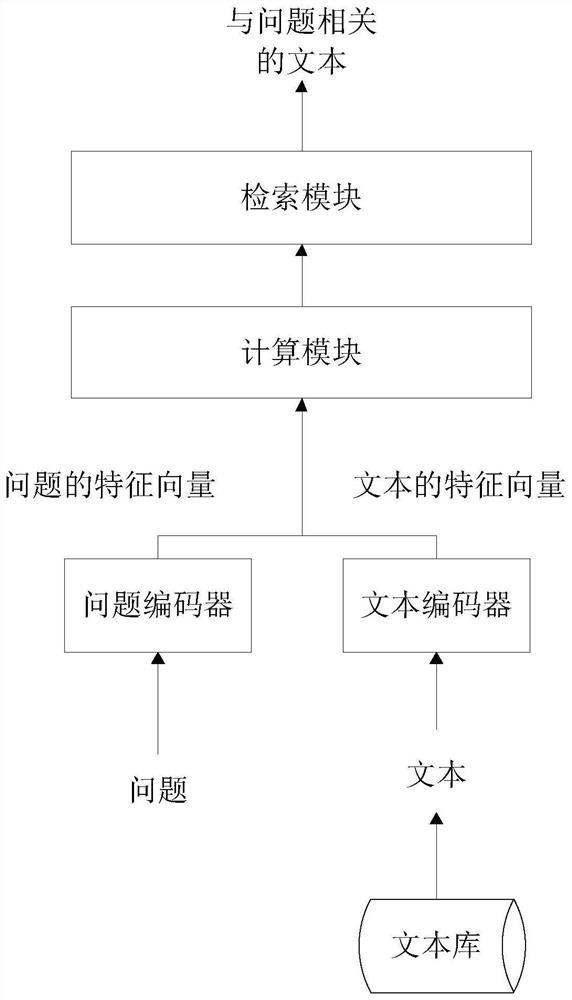
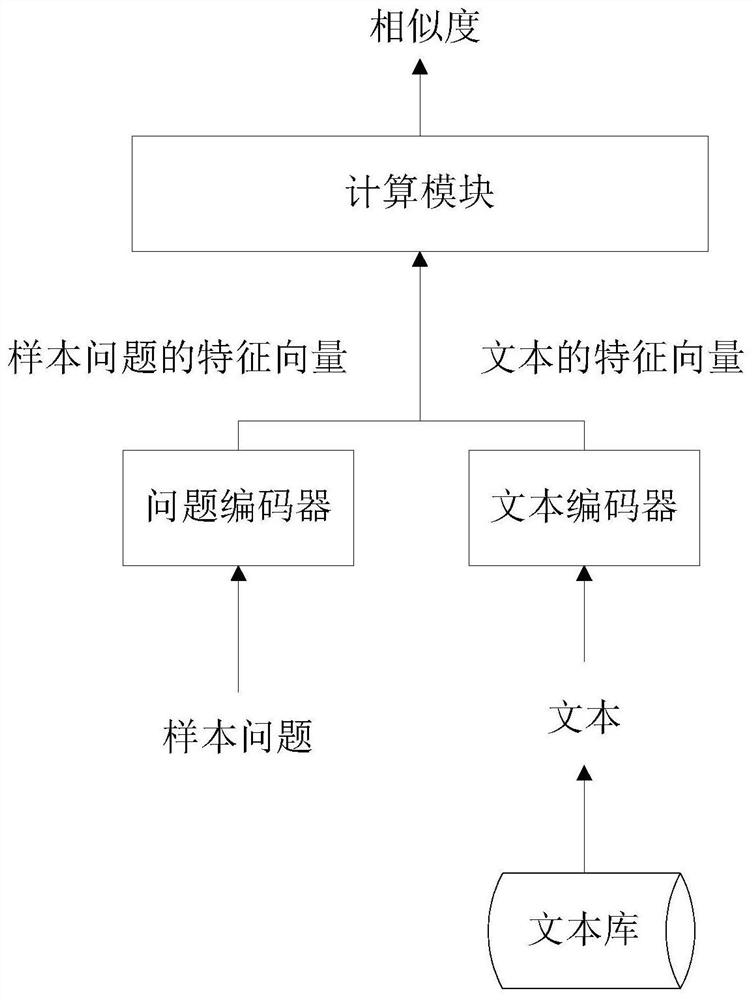
Negative sample determination method, related equipment and readable storage medium
PendingCN113849603AConfusingHigh semantic similarityCharacter and pattern recognitionText database queryingQuestions and answersDegree of similarity
The invention discloses a negative sample determination method, related equipment and a readable storage medium, and can determine a text which has high semantic similarity with a sample question but does not contain an answer to the sample question from a text library as a negative sample of the sample question based on the semantic similarity between each text in the text library and the sample question. The negative samples determined based on the method have high semantic similarity with the sample questions, but do not contain answers to the sample questions, so that the confusability on the sample questions is strong. Furthermore, the negative sample determined based on the method is used for training a retrieval model and a question and answer model in the intelligent question and answer system, and the training effect can be improved. Moreover, when the negative sample determined based on the method is used for testing the robustness of the retrieval model and the question-answering model in the intelligent question-answering system, the effect is better compared with the confrontation sample determined by adopting the prior art.
Owner:科大讯飞(北京)有限公司 +2
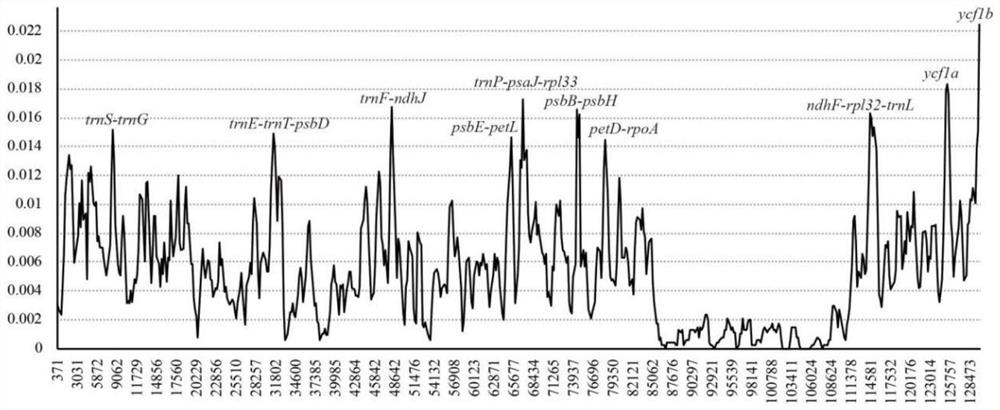
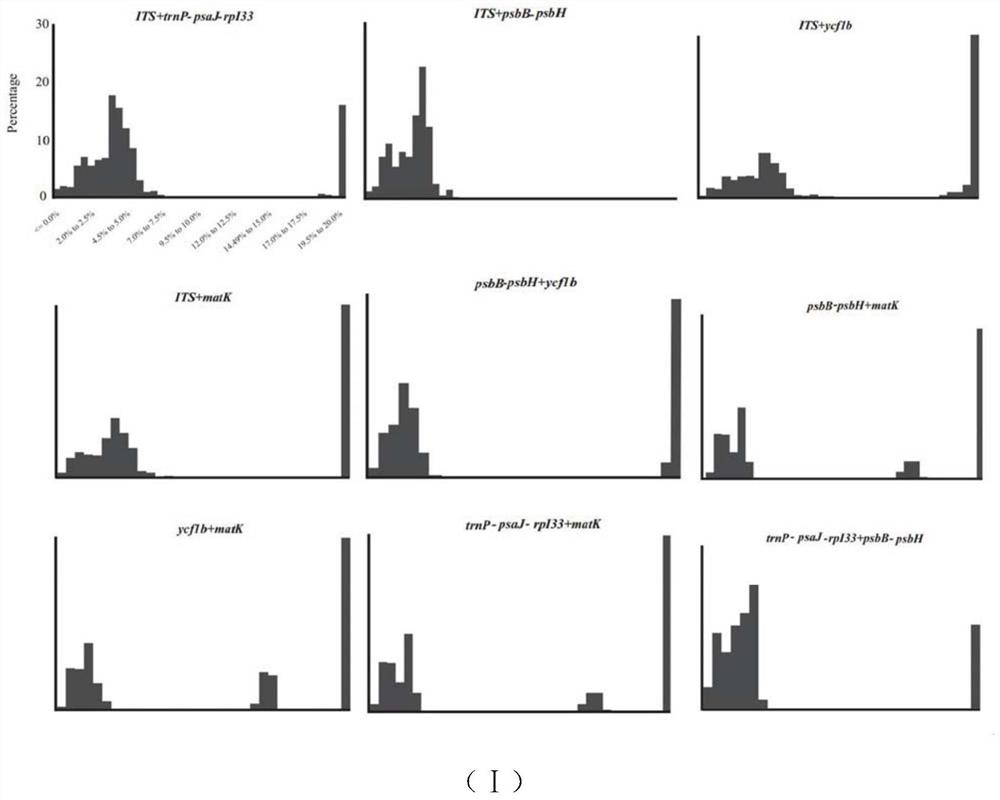
DNA bar code for identifying lilium plants and application thereof
InactiveCN112322634AObvious beneficial effectRapid identificationMicrobiological testing/measurementFermentationBiotechnologyWild species
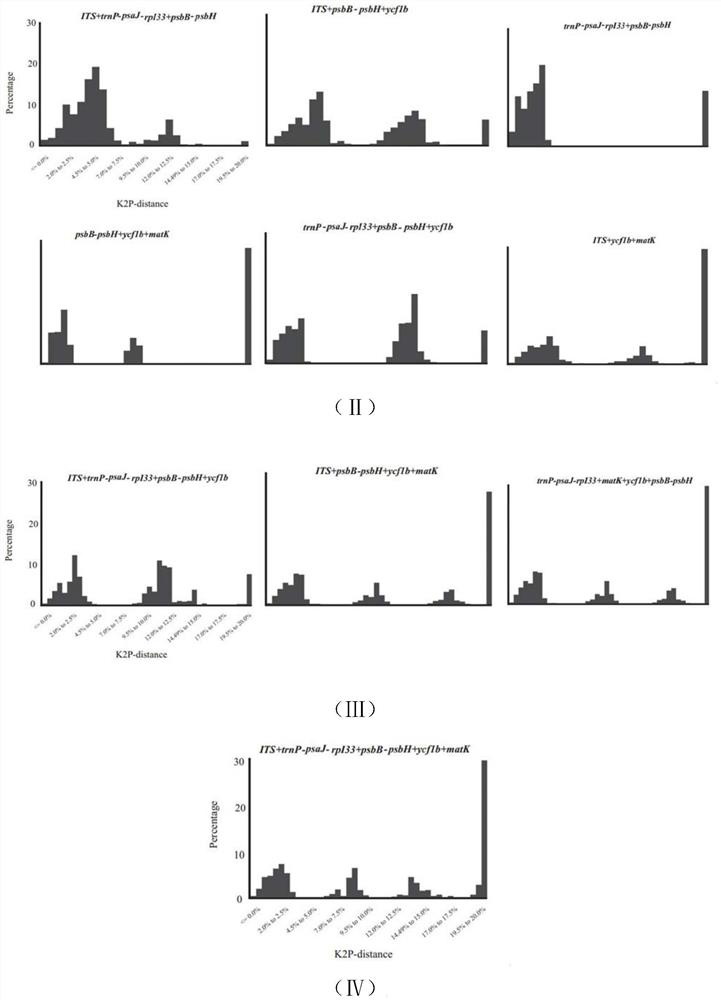
The invention discloses a DNA bar code for identifying lilium plants. The DNA bar code is formed by splicing three gene segments, namely trnP-psaJ-rpI33, psbB-psbH and ITS. Nucleotide sequences of a primer pair for amplifying trnP-psaJ-rpI33 are shown as SEQ ID NO: 1 and SEQ ID NO: 2 in SEQUENCE LISTING, nucleotide sequences of a primer pair for amplifying psbB-psbH are shown as SEQ ID NO: 3 and SEQ ID NO: 4, and nucleotide sequences of a primer pair for amplifying ITS are shown as SEQ ID NO: 5 and SEQ ID NO: 6. The DNA bar code can identify and distinguish lilium resources quickly and easily,and solve and improve classification of wild species of lilium plants.
Owner:BEIJING AGRO BIOTECH RES CENT
Picture processing method and terminal device capable of preventing fingerprint information leakage
InactiveCN110827431AEasy to removeSolve the problem of personal information securityRegistering/indicating time of eventsCharacter and pattern recognitionTerminal equipmentElectronic chip
The invention discloses a picture processing method and terminal device capable of preventing fingerprint information leakage and belongs to the fingerprint processing technological field. The terminal device comprises a working shell and an antiskid plate; the surface of the working shell is fixedly connected with one side of an antiskid plate; a placement groove is formed in the working shell; afingerprint collection board is fixedly connected to the bottom of the inner wall of the placement groove; an electronic chip working board is fixedly connected to the bottom of the fingerprint collection board; and sliding grooves are fixedly connected to two sides of the inner wall of the placement groove. According to the picture processing method and terminal device capable of preventing fingerprint information leakage of the invention, a sponge scrubbing block moves on the surface of the fingerprint collection board, so that fingerprints on the surface of the fingerprint collection boardcan be conveniently and quickly removed, so that a thief is prevented from collecting residual fingerprints on the surface of the fingerprint collection board through equipment such as a plastic paper sheet, and therefore, the problem that the personal information safety of a user is seriously influenced due to the fact that fingerprints on the surface of fingerprint collection glass can be easily copied is solved.
Owner:合肥触点传媒有限公司
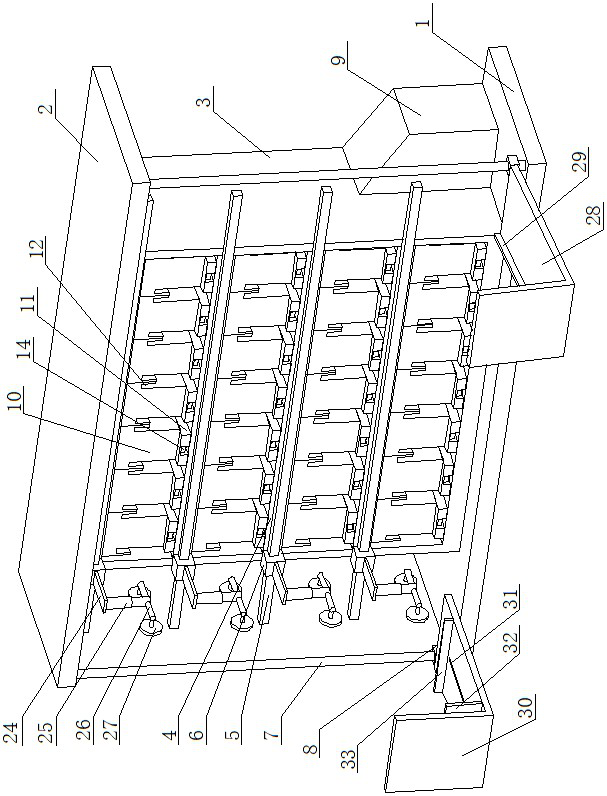
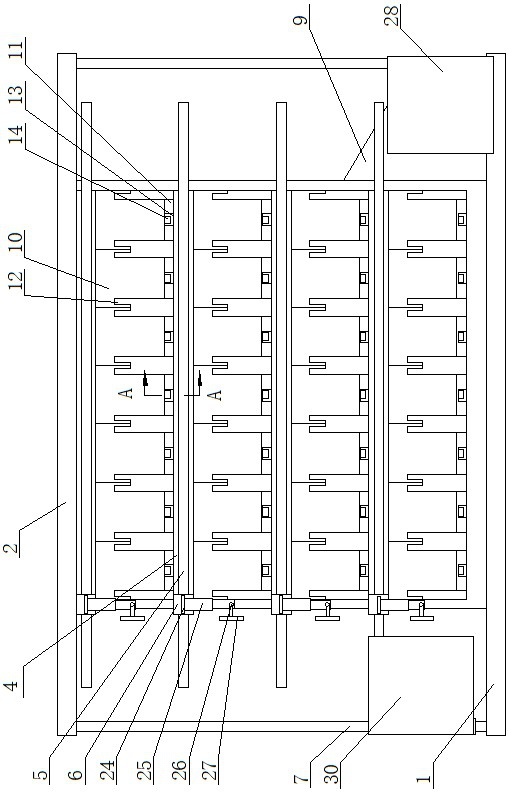
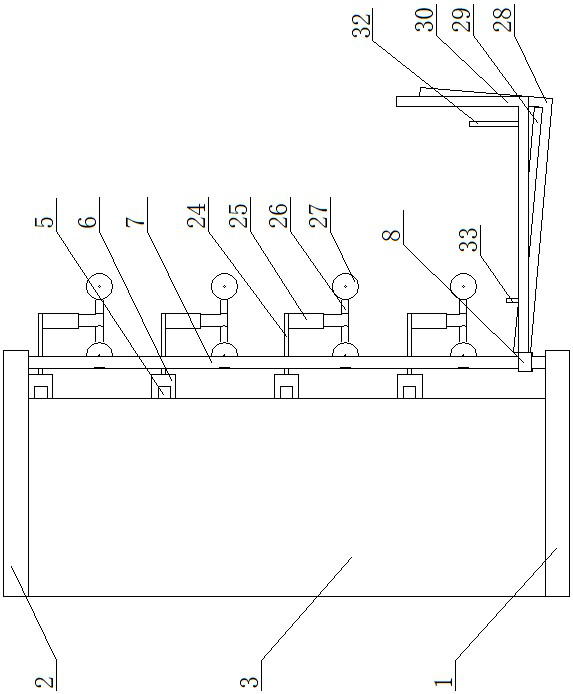
File management equipment facilitating accurately and quickly storing and taking large quantity of accounting documents
ActiveCN113800169AEasy and fast accessEasy accessEnergy efficient computingStorage devicesManagement processEngineering
File management equipment facilitating accurately and quickly storing and taking a large quantity of accounting documents comprises a base and a top plate, a supporting frame is arranged between the base and the top plate and comprises a plurality of partition plates, first electric guide rails are arranged on the front end faces of the partition plates, first electric sliding blocks are arranged on the first electric guide rails, and a conveying device is arranged on the first electric sliding blocks. A plurality of file storage devices are arranged on the partition plates, second electric guide rails are arranged on the two sides of the supporting frame, second electric sliding blocks are arranged on the second electric guide rails, a returning device is arranged on the second electric sliding block on one side, a taking device is arranged on the second electric sliding block on the other side, and an operation table is arranged on one side of the supporting frame. The console can control the conveying device, a file management device, the returning device and the taking device to operate. According to the equipment, files can be quickly taken and stored by controlling the operation table, and the design separately carries out file returning and file taking so that the files can be prevented from being easily mixed in the returning and taking processes, the file management process is standardized, and the working efficiency is improved.
Owner:李易
A remote operation and maintenance and data exchange method for equipment industrial control security
The invention relates to the technical field of information security, particularly relates to a remote operation and maintenance and data exchange method for equipment industrial control security. Themethod includes the following steps: s100, acquiring operation data in the operation process of the equipment through an acquisition terminal; and S200, encrypting the collected operation data to form an operation data packet and generate an encryption password, mixing the encryption password into the pseudo information to form an uplink pseudo information packet, and S300, when sending operationdata, sending the uplink pseudo information packet first and then sending the operation data packet. According to the method, the probability that the operation data packet is intercepted is reducedby counterfeiting normal operation data, the safety of sending the operation data is improved, and meanwhile, the encryption password is sent firstly, so that subsequent decoding is facilitated.
Owner:贵州航天云网科技有限公司
Information Disguise and Restoration Applicable to Irregular Triangulation Digital Elevation Model
ActiveCN105005961BSafe storageGuaranteed normal transmissionImage data processing detailsProgram/content distribution protectionChinese remainder theoremData treatment
Owner:THE PLA INFORMATION ENG UNIV
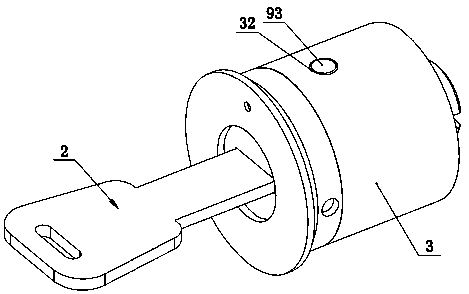
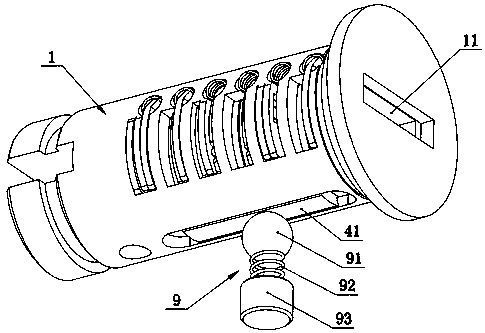
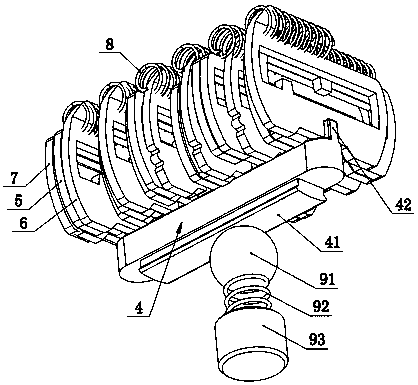
Lock
PendingCN107842250ARealize unlock operationImprove anti-theft performanceKeysCylinder locksEngineeringStructural engineering
The invention discloses a lock. The lock comprises a lock cylinder, a key and a fixing sleeve, wherein the lock cylinder is rotationally arranged in the fixing sleeve; a key channel for allowing the key to be inserted in the axial direction is formed in the lock cylinder; a plurality of blade insertion grooves are formed in the lock cylinder in a linear arrangement manner in the insertion direction of the key; each blade inserting groove is internally provided with a starting blade, a front time delay blade and a rear time delay blade in an inserted mode; each starting blade is clamped betweenthe corresponding front time delay blade and the corresponding rear time delay blade; a first core block which extends into the key channel is correspondingly arranged on each starting blade; a second core block which extends into the key channel is correspondingly arranged on each front time delay blade; a third core block which extends into the key channel is correspondingly arranged on each rear time delay blade; the first core blocks are correspondingly arranged on one side of the key channel; the second core blocks and the third core blocks are correspondingly arranged on the other sideof the key channel; and each first core block and the corresponding second core block and the corresponding third core block are arranged in a delta-shaped manner. The structure is adopted, and the lock is better in anti-theft performance.
Owner:ZHEJIANG HONGTAI ELECTRONICS EQUIP
A Neural Network Relation Classification Method and Its Realization System Fused with Distinguishing Degree Information
ActiveCN109344244BWork lessAvoid interferenceSpecial data processing applicationsText database clustering/classificationRelation classificationFeature vector
The invention relates to a neural network relation classification method and an implementation system thereof, which fuse discrimination degree information, comprising: (1) data preprocessing; (2) training word vector; (3) extracting position vector; Combining the word vector of each word with the high-dimensional position feature vector, the joint feature is obtained. (4) computing the semantic representation of sentences; The context information and semantic information of entities are encoded by bi-directional LSTM. (5) calculating a discrimination vector; After the two entity vectors are subtracted from each other and cascaded with a Bi-LSTM unit encode that input; (6) inputting the outputs of (4) and (5) to the CNN, outputting the feature vector fused with the discrimination information, and inputting the feature vector to the classifier for classification; (5) adopting a Loss function to train the model. The invention does not need to manually extract any features, and the jointmodel does not need to preprocess the data by means of other natural language processing tools, the algorithm is simple and clear, and the effect is best at present.
Owner:SHANDONG UNIV
Encryption method and authentication method based on magnetic resistance sensor, and mobile terminal and server
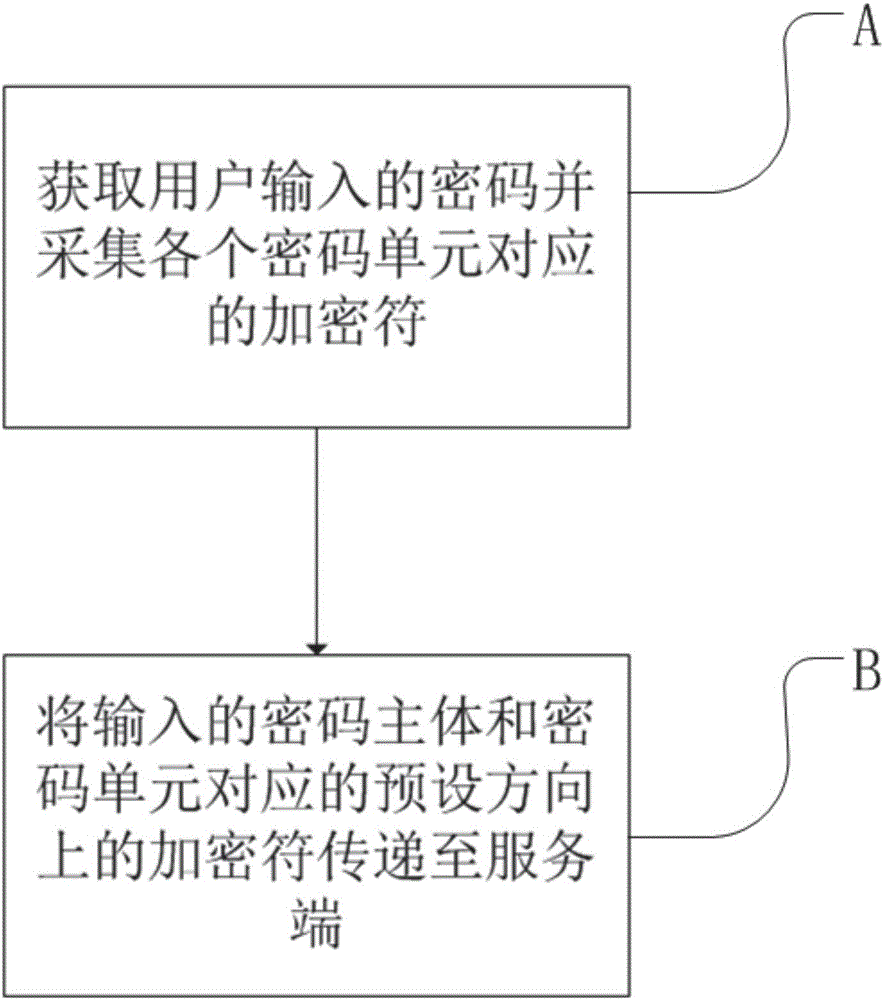
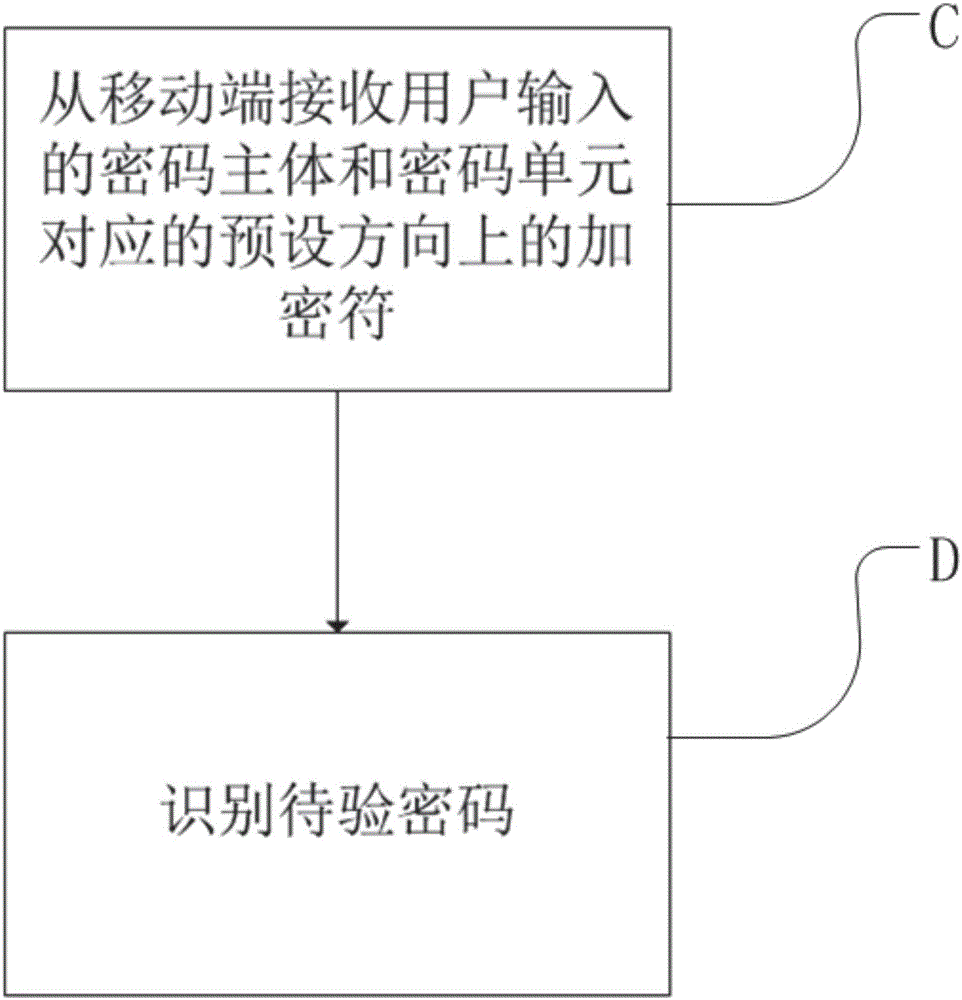
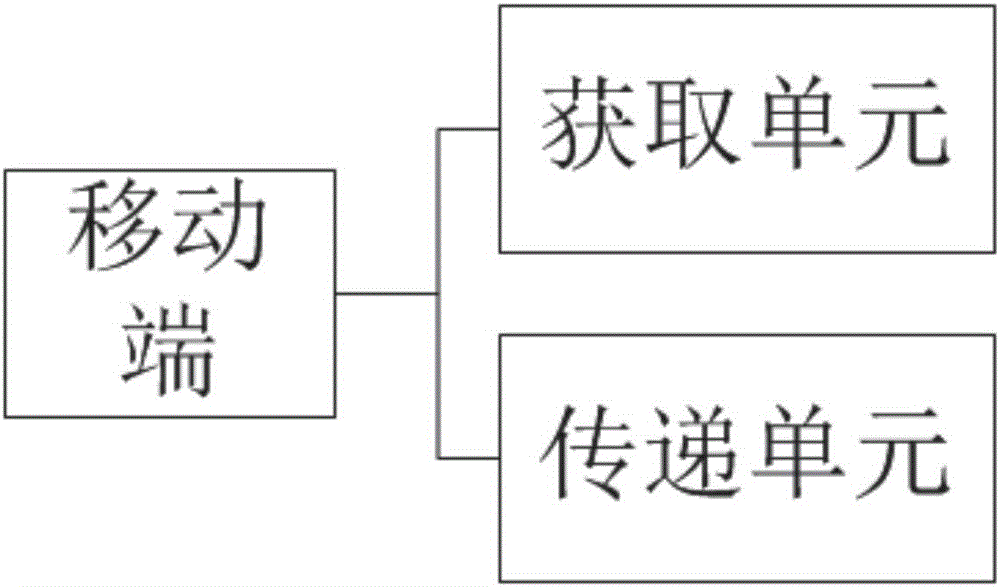
InactiveCN106341235ADownplay the importanceVerify accuracyKey distribution for secure communicationUser identity/authority verificationValidation methodsUser input
The invention discloses an encryption method and an authentication method based on a magnetic resistance sensor, and a mobile terminal and a server. The encryption method comprises the following steps: A, acquiring a password input by a user and collecting encryption characters corresponding to password units; and B, transmitting the password body and the encryption characters in preset directions corresponding to the password units to a server. Sensing information acquired by a magnetic resistance sensor is provided as encryption characters of the password units of a traditional password. When a traditional text password is used, even if a user chooses to keep the password, the accuracy of user identity can be verified conveniently and safely for key operations. Action memorization is easier and more confusing than character memorization. By combining actions and characters, the importance of text passwords can be weakened, the influence of shortcomings can be reduced, and the security can be strengthened.
Owner:深圳市启明星控股集团有限公司
Preparation process of a large ultra-thick ductile iron container sample
ActiveCN110907242BPerformance is not affectedReduce processing costsPreparing sample for investigationDuctile ironDrill
Owner:JIANGSU JIXIN WIND ENERGY TECH
Grain storage device
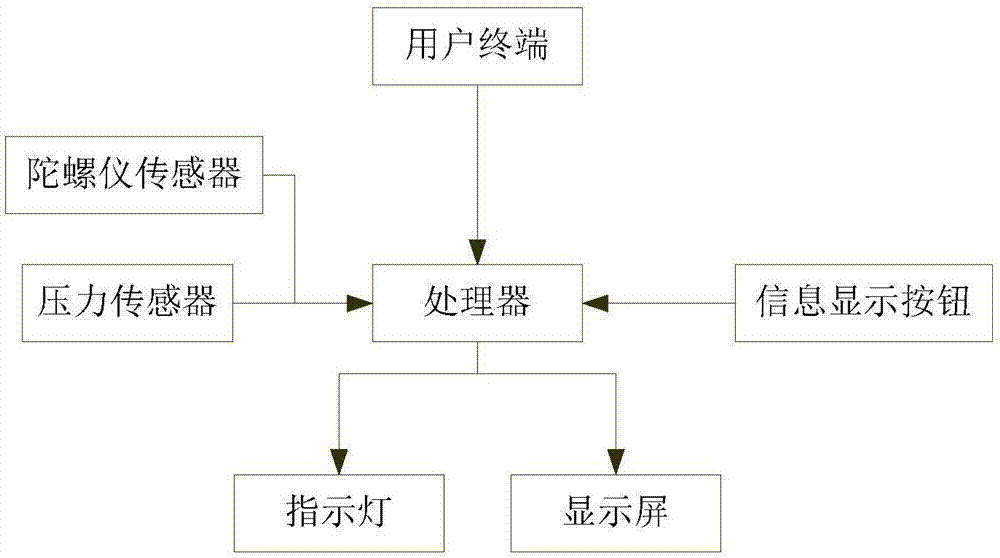
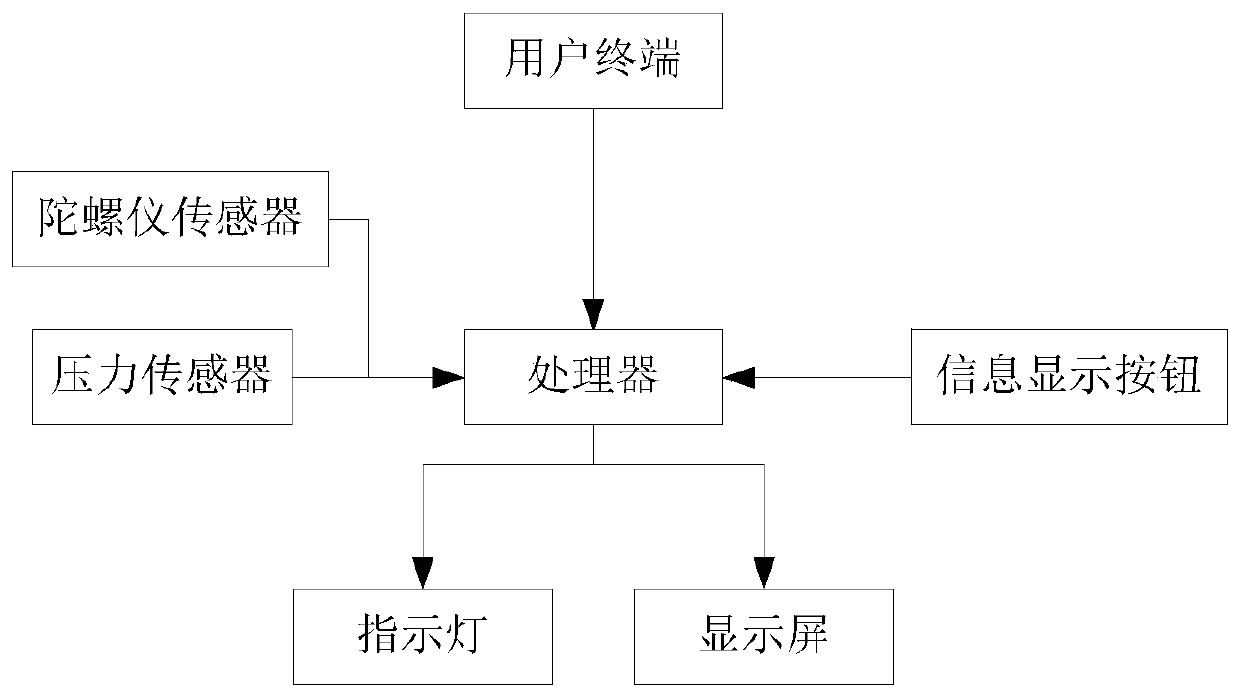
ActiveCN107493845AWill not affect normal workDoes not affect accuracyAgriculture tools and machinesClimate change adaptationGrain storageEngineering
The invention discloses a grain storage device. The device comprises a shell, one end of the shell is opened, and a grain storage barrel is placed into the shell; the grain storage barrel comprises a closed end and an opened end which are opposite, a cover which is detachably connected with the grain storage barrel is arranged on the opened end, and when the grain storage barrel is placed into the shell, the opened end is placed inward, and the closed end is placed outward; an indicator light and a display screen are arranged on the outer surface of the closed end, the device further comprises a processor and a user terminal, the input end of the process is in signal connection with the user terminal, and the output end of the processor is connected with the indicator light and the display screen. The invention aims at providing the grain storage device. The problem is solved that downstream users store grain inconveniently in the prior art, and the aim of long-term and efficient grain storage is achieved.
Owner:CHONGQING JIEBANG ELECTRIC CO LTD
Traffic sensor network data transmission method, system and medium based on hybrid encryption
ActiveCN112469003BSimplify the data parsing processImprove authentication efficiencyParticular environment based servicesNetwork topologiesPlaintextIn vehicle
The invention discloses a traffic sensor network data transmission method and system based on hybrid encryption, which performs end-to-end data transmission between intelligent vehicle terminals, intelligent road test equipment, and cloud platforms, and uses the intelligent traffic lightweight key carried by the server Digital certificates are used for two-way authentication; during data transmission, the data is double-encrypted using a hybrid encrypted transmission method, and at the same time, a random key and a random plaintext calculation hash value are added for comparison and verification. The present invention combines the advantages of fast encryption and decryption speed of the SM4 symmetric encryption algorithm and low encryption key management difficulty and high security of the SM2 asymmetric encryption algorithm to ensure that the method can be applied to the communication process of intelligent vehicle terminals, intelligent road test equipment and cloud platforms Among them, it can effectively improve the security and transmission efficiency of traffic sensor network data transmission.
Owner:NANJING UNIV OF SCI & TECH
Medical field data processing system and method based on blockchain architecture technology
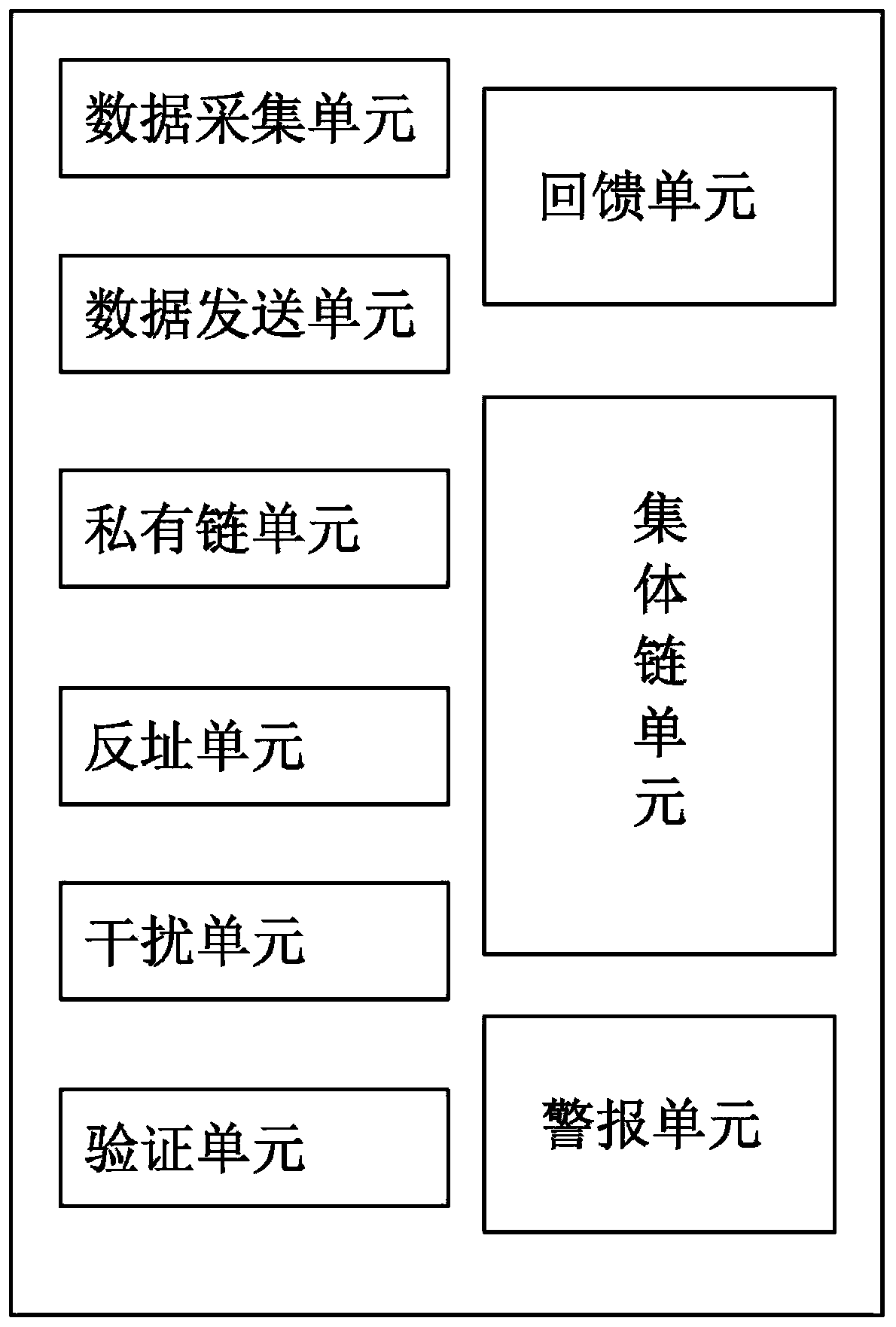
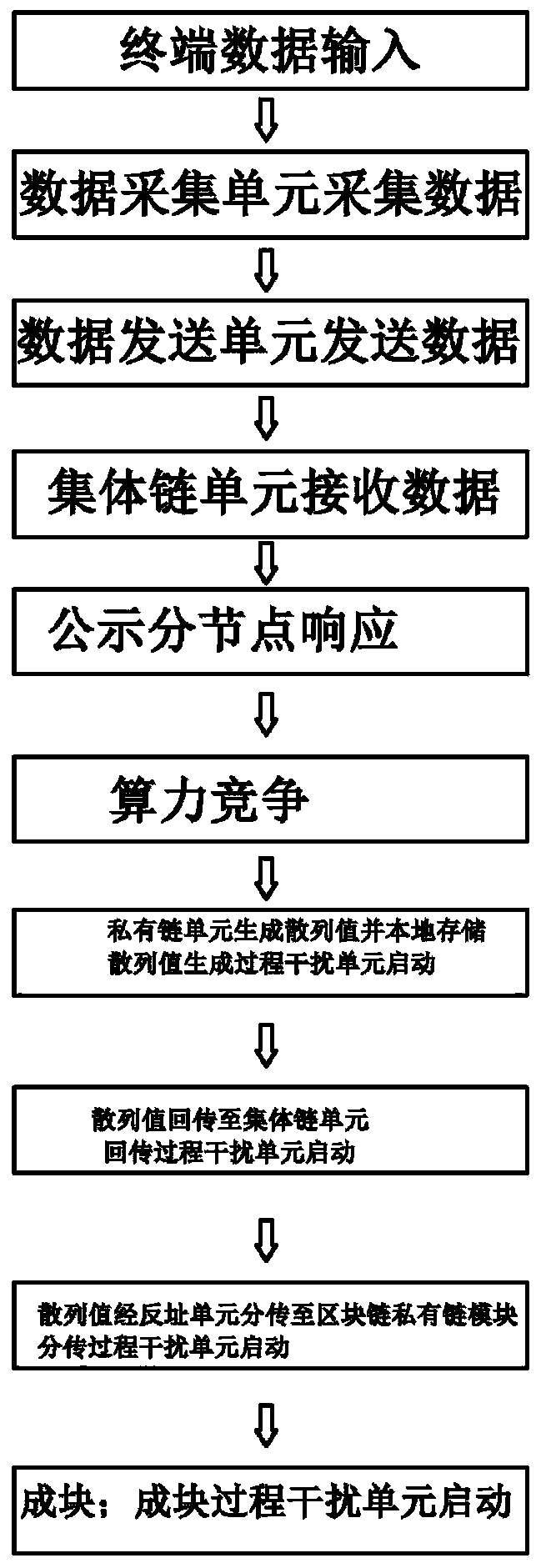
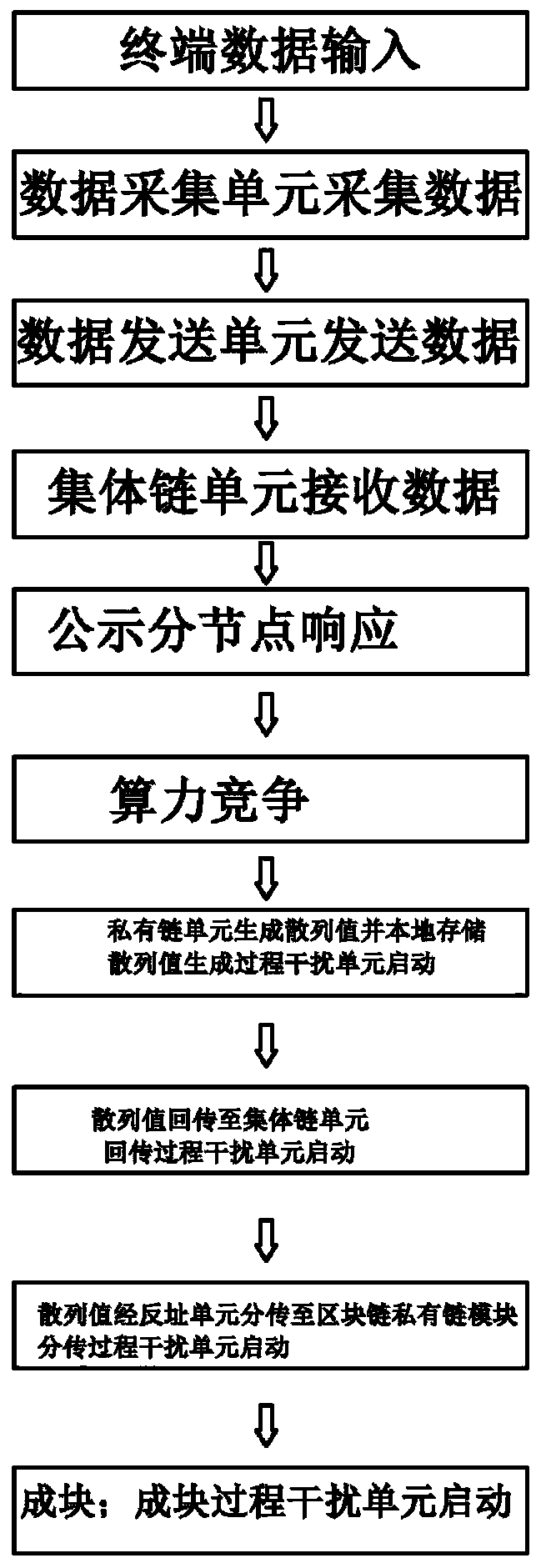
PendingCN111125755AImprove securitySame addressDatabase distribution/replicationDigital data protectionData processing systemEngineering
The invention provides a medical field data processing system based on a blockchain architecture technology, and belongs to the technical field of blockchains. The system comprises a data acquisitionunit which acquires data after an input node responds; a data transmission unit that responds to a relationship between units; a collective chain unit which is used for publicly distributing the hashvalues of the acquired data; a private chain unit which is used for storing hash values of the acquired data; a reverse address unit which is used for distributing and transmitting the return hash value in the collective chain unit to the block chain private chain module; and an interference unit which is used for forming a plurality of virtual private chain nodes with random addresses, wherein hash values in the private chain nodes are randomly generated, names of the virtual private chain nodes are blocked, the addresses are the same as block chain addresses, and the interference unit at least responds to a private chain hash value generation stage, a hash value return stage, a sub-transmission stage and a blocking stage. The system is high in safety performance.
Owner:陕西医链区块链集团有限公司
A Magneto-Optical Image Enhancement Method Based on Optical Flow Algorithm
ActiveCN107180428BRich dataReduce skin effectImage enhancementImage analysisData informationImage detection
The invention discloses a magneto-optical image enhancement method based on the optical flow algorithm. A low-frequency AC excitation amplifier is used to excite the yoke, and a periodically changing magnetic field is used to obtain image sets under different signal intensities, and the low-frequency signal enables the magnetic lines of force to pass through the yoke. Through the deep area of the measured object, the magneto-optical image can reflect the deepest defect information, which reduces the influence of the skin effect. However, the magneto-optical image obtained in this way has interference noise generated by magnetic domain motion under the action of low-frequency AC signals, which is easily confused with defect information and reduces image detection accuracy. Iterative processing is performed to accumulate the feature points that generate optical flow motion to obtain an enhanced optical flow image. In the enhanced image, the image gradient changes are more obvious, the interference is also greatly reduced, and the defect information is more intuitive.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
a grain storage device
ActiveCN107493845BWill not affect normal workDoes not affect accuracyAgriculture tools and machinesClimate change adaptationGrain storageEngineering
The invention discloses a grain storage device. The device comprises a shell, one end of the shell is opened, and a grain storage barrel is placed into the shell; the grain storage barrel comprises a closed end and an opened end which are opposite, a cover which is detachably connected with the grain storage barrel is arranged on the opened end, and when the grain storage barrel is placed into the shell, the opened end is placed inward, and the closed end is placed outward; an indicator light and a display screen are arranged on the outer surface of the closed end, the device further comprises a processor and a user terminal, the input end of the process is in signal connection with the user terminal, and the output end of the processor is connected with the indicator light and the display screen. The invention aims at providing the grain storage device. The problem is solved that downstream users store grain inconveniently in the prior art, and the aim of long-term and efficient grain storage is achieved.
Owner:CHONGQING JIEBANG ELECTRIC CO LTD
A method of masquerading and de-masquerading characters based on non-repeating keys
The invention discloses a method for disguising and uncamouflaging characters based on non-repetitive keys, which is characterized in that it comprises the following steps: S100: loading plaintext; S200: constructing a key dictionary; S300: determining the key block number ; S400: generate the UNICODE encoding of plaintext characters; S500: convert the UNICODE encoding into 4 bytes of Hex encoding 0xyYhH, wherein, when the Hex encoding is less than 4 bytes, fill the low byte with 0; S600: use the Hex encoding camouflages the plaintext characters and outputs the camouflage characters; S700: judge whether to complete the camouflage of all plaintext characters, if yes, perform step S800, otherwise, perform step S300; S800: merge the camouflaged character sequence of the plaintext characters , to output the camouflage text; the camouflage text can be de-camouflaged and output plain text by the reverse method.
Owner:SICHUAN QIAODUOTIANGONG PRECISION EQUIP CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com