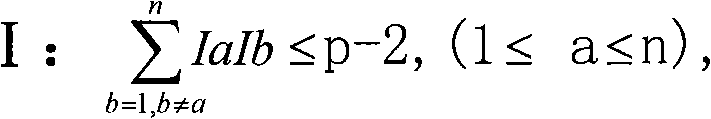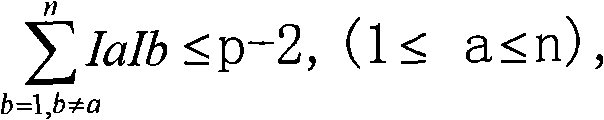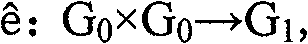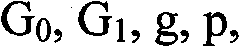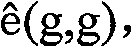Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
48results about How to "Security is not compromised" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Electric long-distance kicker
InactiveCN105258552ASecurity is not compromisedFast and Accurate CastingSpring gunsCast linesEngineeringBuoy
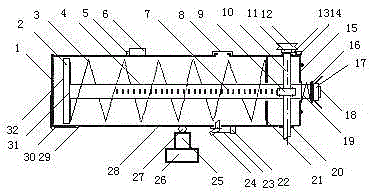
The invention relates to a kicker, in particular to an electric long-distance kicker. The electric long-distance kicker is characterized in that through intelligent operation, the kicker gathers elastic potential energy of a spring by means of a mechanism, then motivates the elastic potential energy into kinetic energy of a kicked object, conducts aiming by means of a periscope and an accent light and accurately kicks the kicked object in place. The kicker can be mounted on naval vessels and fishing boats and used for launching bombs and grenades and jetting stones or bricks to enemy vessels; the kicker can also be used as a water cannon or a gas gun to kick life floats or life buoys to trapped personnel and overboard personnel so that the trapped personnel and the overboard personnel can be saved quickly; the kicker can be mounted on an automobile and used for long-distance fire extinguishment so as to guarantee that firefighters are protected against injuries; during high-rise fire extinguishment, the kicker can be used for jetting heavy objects to break doors and windows open and jetting fire extinguishing bombs into a house rapidly and accurately; the kicker can also be used as the water cannon to jet thousands of jin of water into the house at a time; when a high-tension power line ices up, the kicker can conduct continuous deicing operation on the charged condition; during wartime, the kicker can be used for jetting shrapnels, bombs and grenades to an enemy position a few hundred meters away. The electric long-distance kicker is simple in structure, capable of being operated intelligently, high in jetting speed, accurate in jetting and long in jetting distance.
Owner:银世德
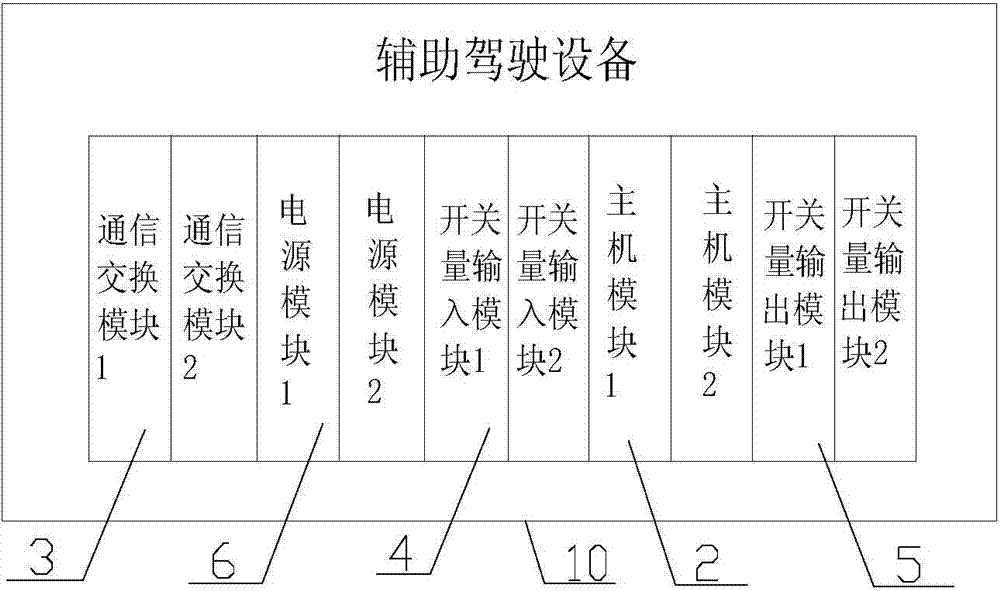
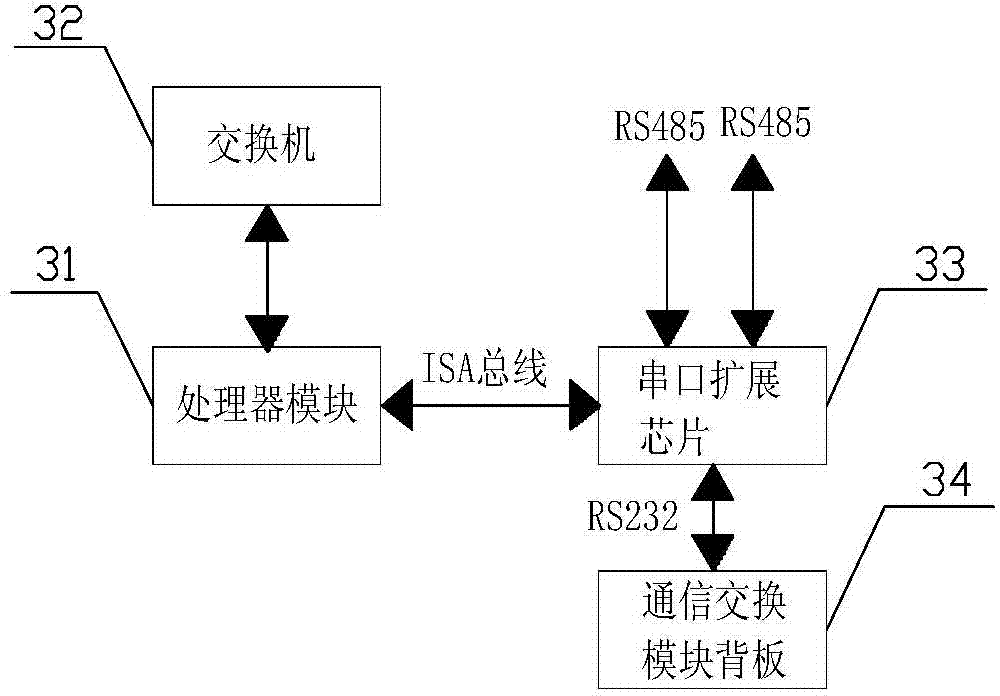
Auxiliary driving equipment
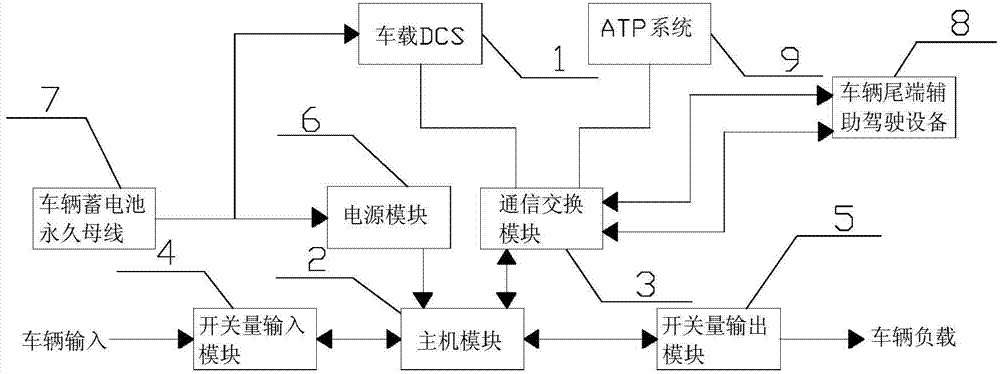
ActiveCN104494649AEnsure normal driving requirementsGuaranteed reliabilitySignalling indicators on vehicleLocomotivesSystem requirementsSerial port
The invention relates to auxiliary driving equipment. The auxiliary driving equipment fits a vehicle-mounted wireless communication module for use, and comprises a mainframe module and a communication exchange module, an on-off input module, an on-off output module and a power supply module connected with the mainframe module, wherein the communication exchange module comprises a processor module and an exchanger; the vehicle-mounted wireless communication module communicates with the exchanger; the exchanger is connected with the processor module; the processor module is connected with a serial port expansion chip, and communicates with the mainframe module through the serial port expansion chip; and the mainframe module acquires states of trains through the on-off input module, and gives a control command to an execution system of the trains through the on-off output module. The auxiliary driving equipment, provided by the invention, satisfies the system requirements of full-automatic unmanned circuits, can realize remote sleeping and awakening for the whole trains, and has reliability and usability.
Owner:TRAFFIC CONTROL TECH CO LTD
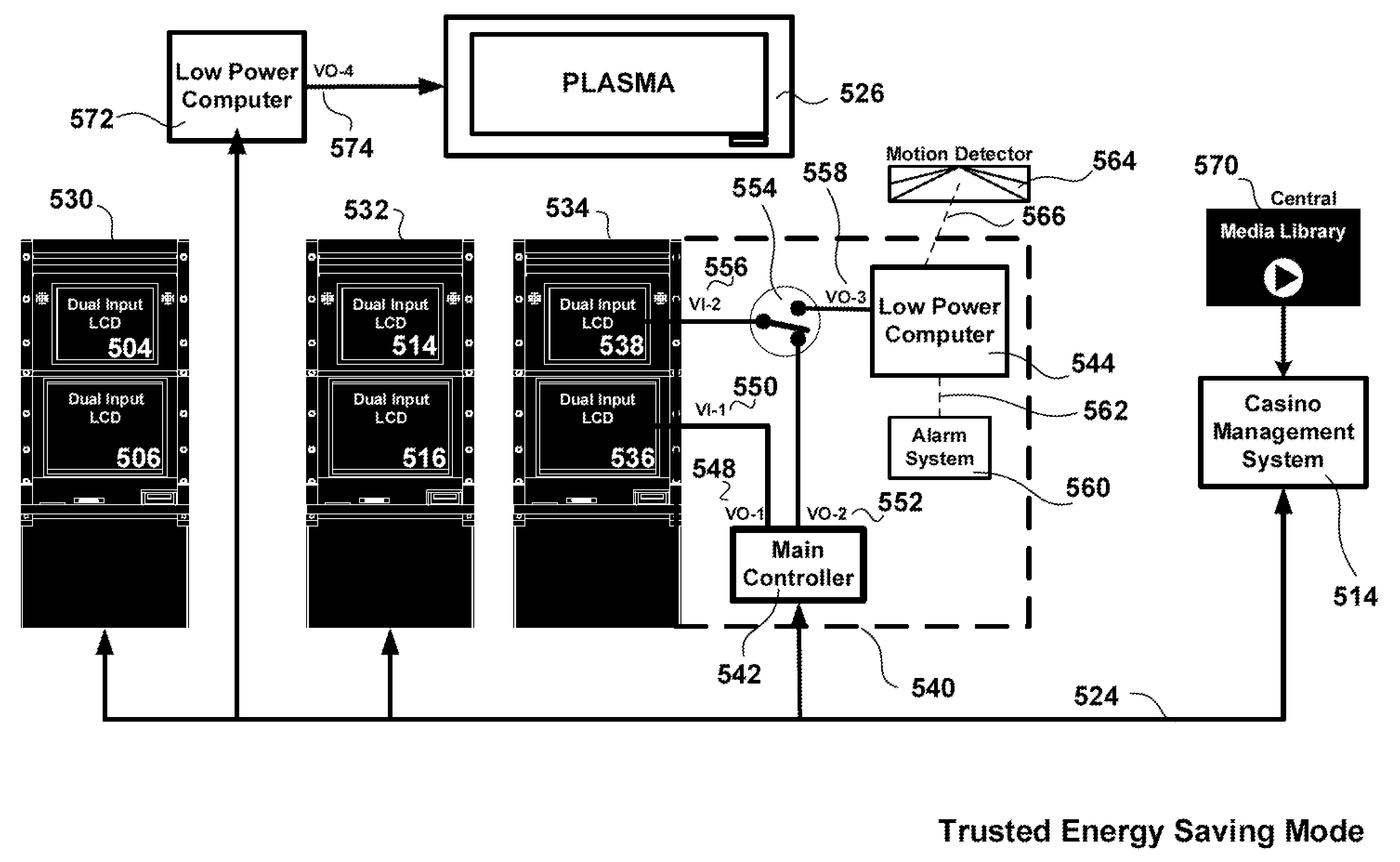
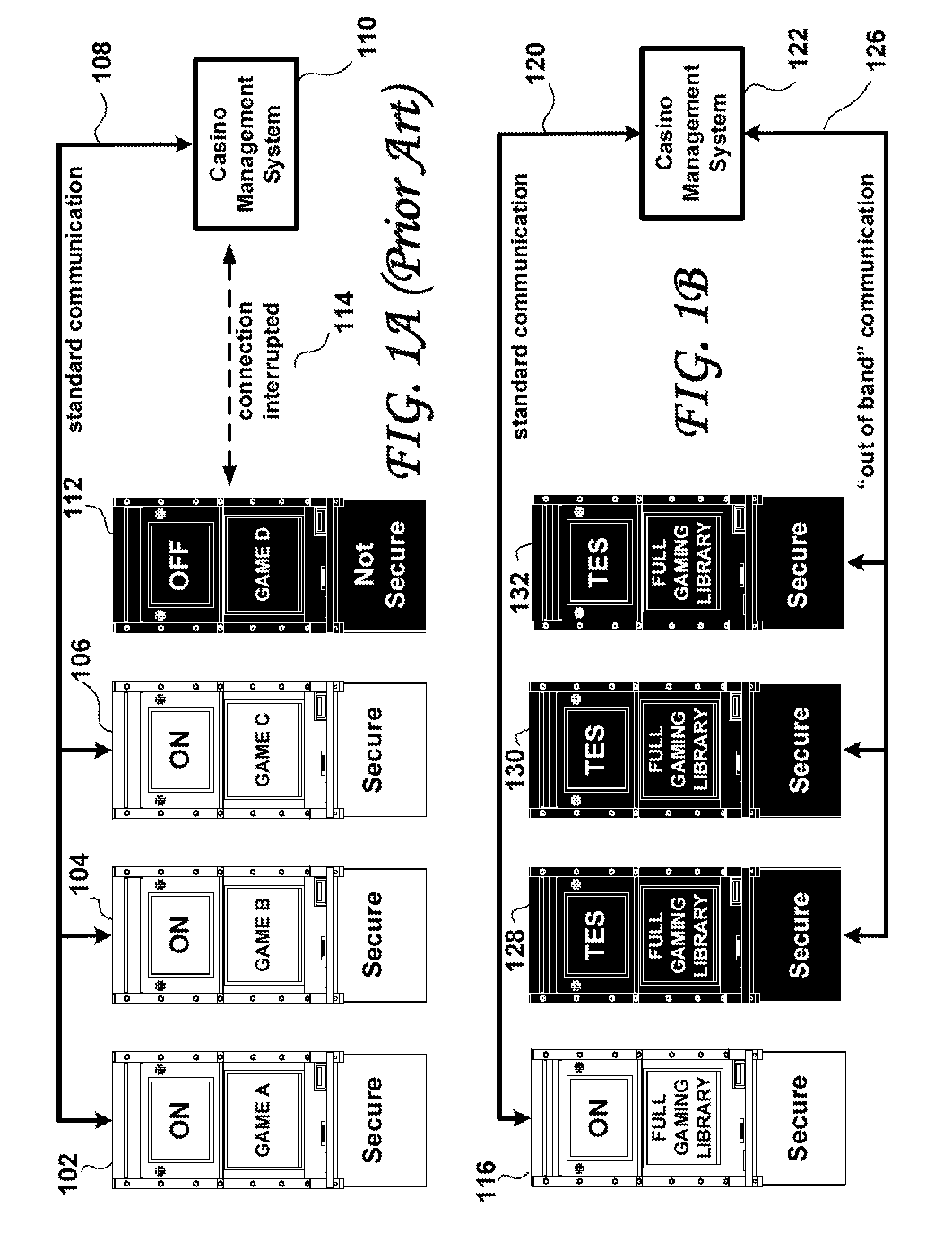
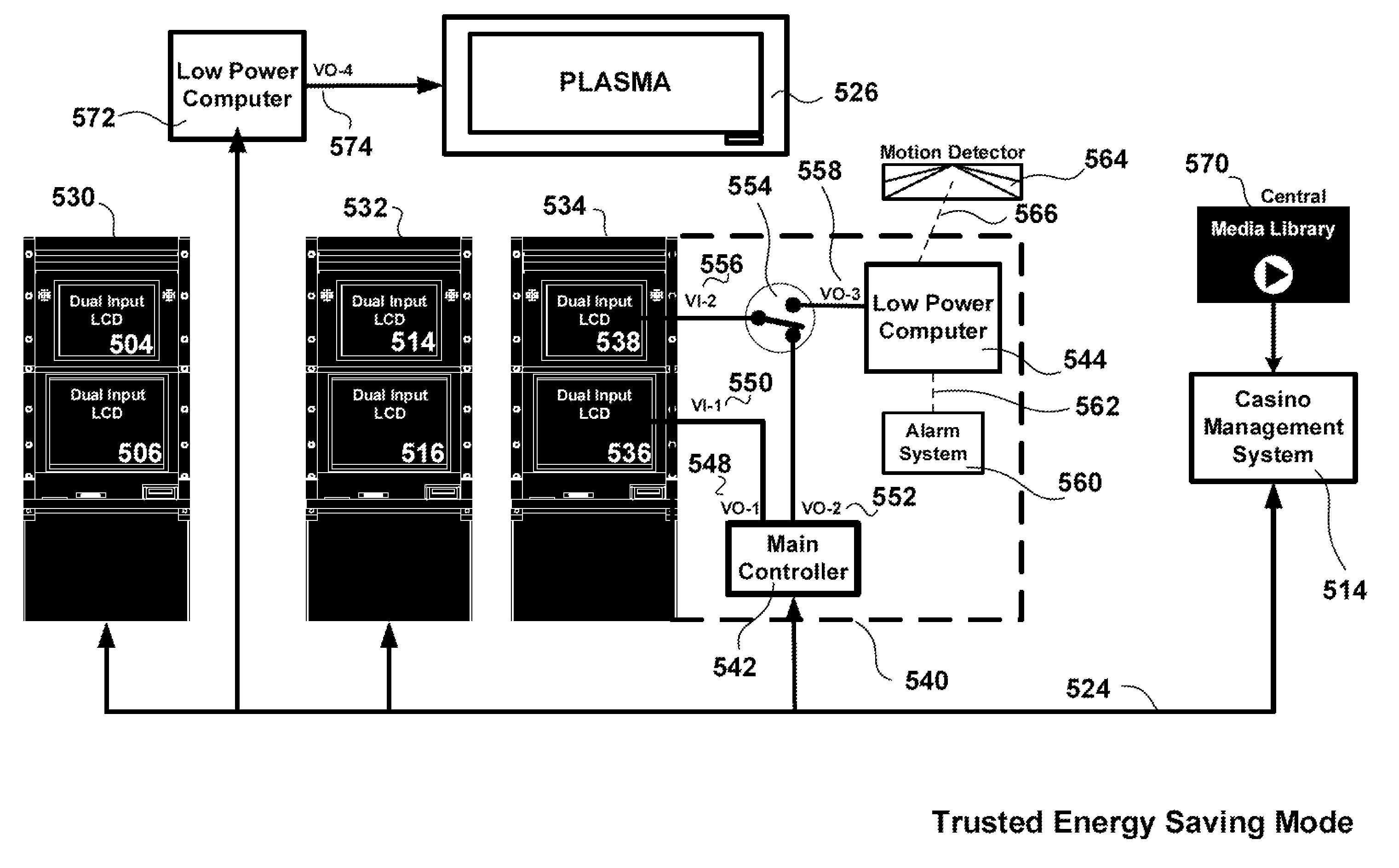
Regulated Gaming Trusted Energy Saving
ActiveUS20090221363A1Save moneyControl power consumptionMechanical apparatusVolume/mass flow measurementPower modeEngineering
Trusted Energy Saving (TES) methods applied to server based distributed downloadable gaming for allowing casino operators to significantly reduce their energy bills by placing the main controller of selected unused gaining machines into low-power mode while retaining total control and trust. Trusted Energy Saving is accomplished by: (1) establishing a secure “out-of-band” communication (or equivalent) between gaming machines and the casino's management system such that full network security is maintained while the main controller is in low power standby mode, (2) employing intelligent strategies to wake-up and turn-off the main controller of selected gaming machines by anticipating player use, (3) waiving the lengthy security verification required by regulation upon every gaming machine start-up and optionally (4) by displaying video promotional content on each turned-off gaming machine to continue to attract prospective players and to use the timing of each player approach to intelligently structure game menus based on the promotional content that has successfully attracted the player. The mapping of the TES gaming machines that are turned-on and in low-power mode may be periodically forwarded to the air-conditioning management system and / or to the lighting management system for energy optimization.
Owner:IGT
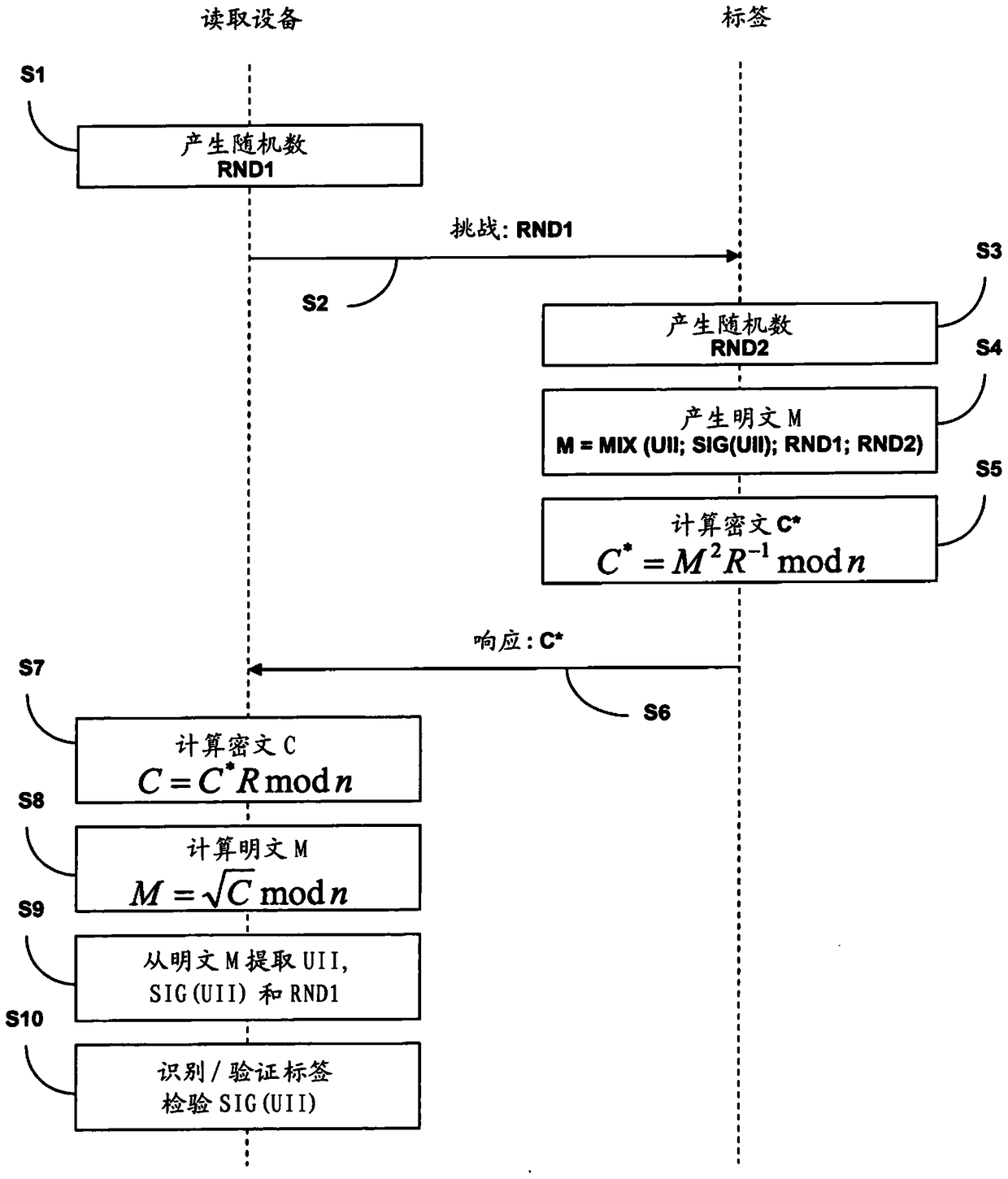
Methods and system for secure communication between an rfid tag and a reader
ActiveCN104488219AReduce processing timeSecurity is not compromisedPublic key for secure communicationUser identity/authority verificationPlaintextSecure communication
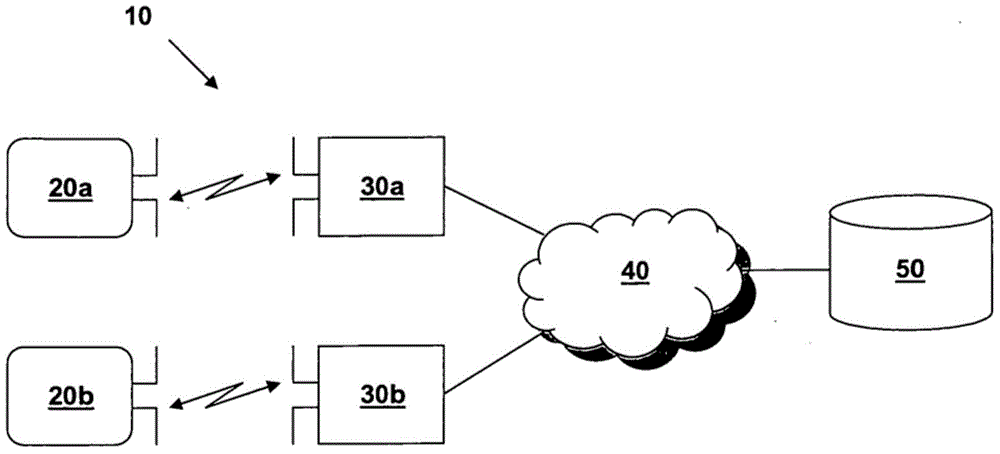
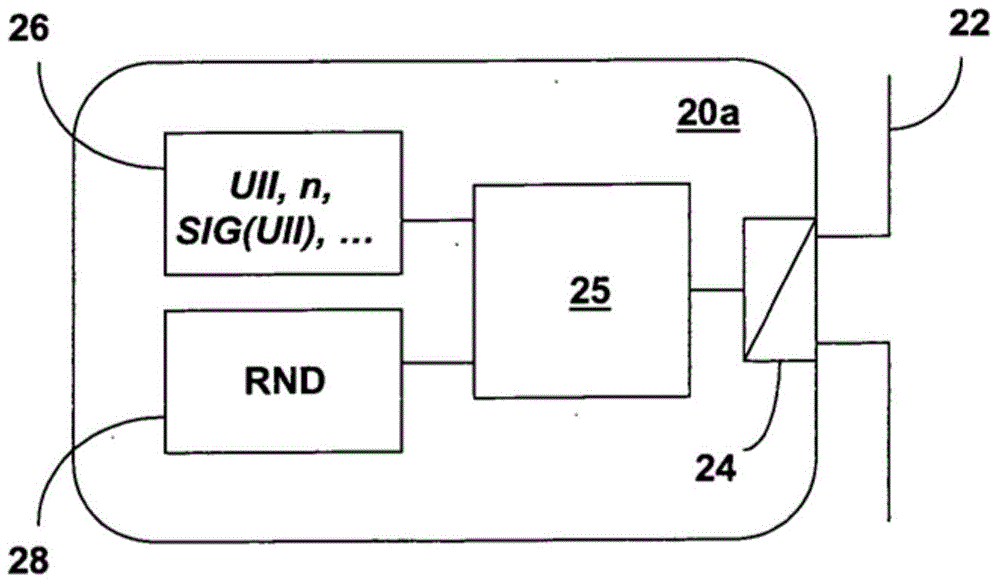
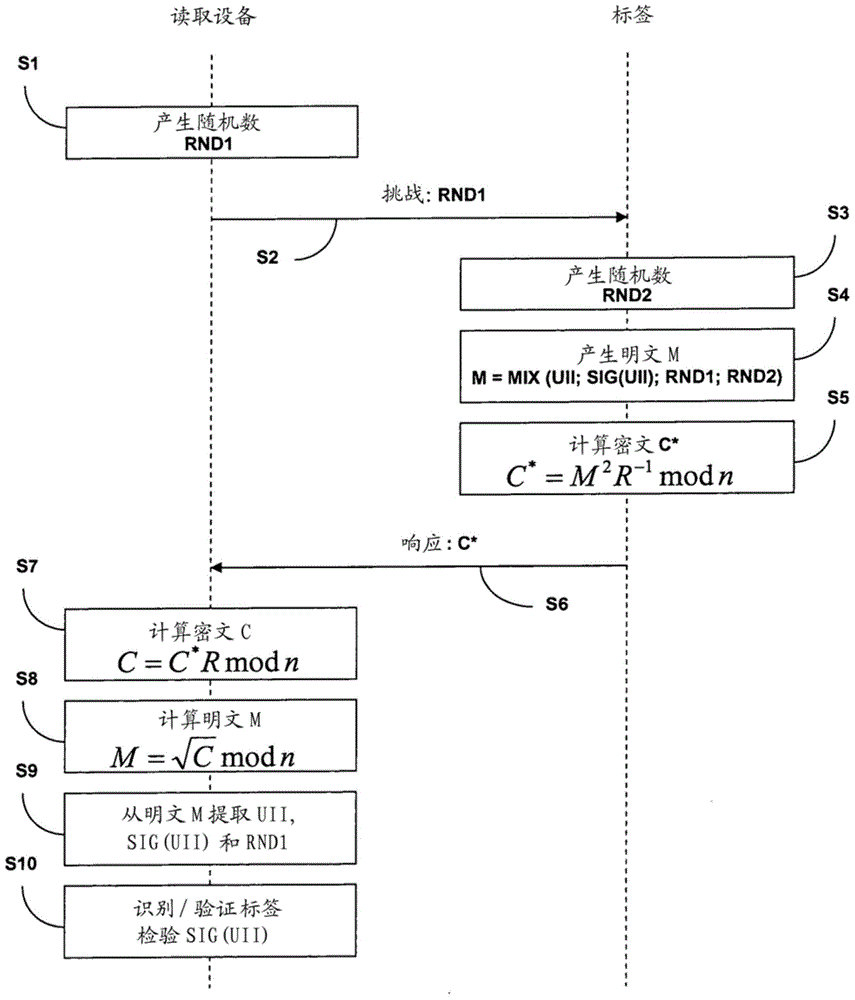
The invention relates to methods and a system for secure communication between an RFID tag and a reader via the air interface and to corresponding RFID tags and corresponding readers. The invention is based on the fundamental idea that, for the purpose of secure communication between an RFID tag and a reader, a modification of Rabin's method is used, in which, within the scope of encrypting plain text M, which includes an identification element of the RFID tag or of an object provided with the latter, the Montgomery residual ('Montgomery reduction') of the square of the plain text M modulo n with respect to a Montgomery base R, that is to say C* = Mu2 R-1mod n, is calculated from the RFID tag instead of the square of the plain text M modulo n, that is to say M2 mod n, and the resultant ciphertext C* is used to authenticate the RFID tag. In this case the modulus n = p.q is the public key of the reader, the prime numbers p, q are the private key of the reader and the Montgomery base R is an integer greater than the modulus n.
Owner:捷德移动安全有限责任公司
Diaphragm and battery comprising same
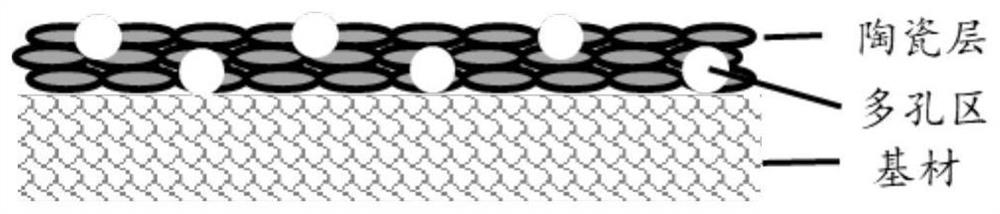
PendingCN112018312AHigh porosityHigh magnificationCell seperators/membranes/diaphragms/spacersLi-accumulatorsCeramic coatingPore diameter
The invention provides a diaphragm and a battery comprising the diaphragm. The diaphragm comprises a diaphragm base layer and a ceramic coating arranged on the first surface of the diaphragm base layer, wherein the ceramic coating comprises ceramic particles, micropores are formed in the surface and / or the interior of the ceramic coating, the porosity of the ceramic coating is 40-80%, and in the micropores, the volume of pores with the pore diameter being 0.1 micrometer or above accounts for 45-90% of the total pore volume, and the volume of pores with the pore diameter being 1.0 micrometer orabove accounts for 40-80% of the total pore volume. According to the invention, a large number of micropores are formed in the surface and / or the interior of a ceramic coating, so that the porosity of a diaphragm is improved so as to improve the battery rate, residual liquid amount, low-temperature discharge and long-cycle performance, and the needling strength, the self-discharge and the safetyperformance of the diaphragm are not influenced.
Owner:ZHUHAI COSMX BATTERY CO LTD
Method for checking electricity stealing based on remote calibration for grid line running error
ActiveCN107817395ASecurity is not compromisedImprove the level of measurement technologyElectrical testingTime integral measurementMeasurement deviceSingle phase
The invention relates to a method for checking electricity stealing based on remote calibration for a grid line running error. The method specifically comprises the steps of (1) dividing detection subareas, additionally arranging new electric energy measurement equipment in the subareas, and improving the digital resolution of all electric energy measurement data; (2) installing a detachable single-phase electric energy meter for each detection subarea to serve as an error standard for error detection; (3) acquiring all electric energy data of the detection subareas, and substituting the datainto an electric energy data error calculation model; (4) taking the 2-3 detachable single-phase electric energy meters installed in the detection subareas back to a laboratory, and checking the accuracy of the calculation result; and (5) calculating 10KV user electricity stealing conditions in a distribution network according to the calculation result. According to the method, the loss of a powersupply line can be accurately measured and monitored in real time, power interruption is not required, measurement for an error of all electric energy measurement devices within a 10kV distribution network is realized, loss detection and real-time monitoring for transmission lines of the distribution network can be achieved, and thus an electricity stealing line can be tracked and checked quicklyand accurately.
Owner:TIANJIN ELECTRIC POWER TECH DEV CO LTD
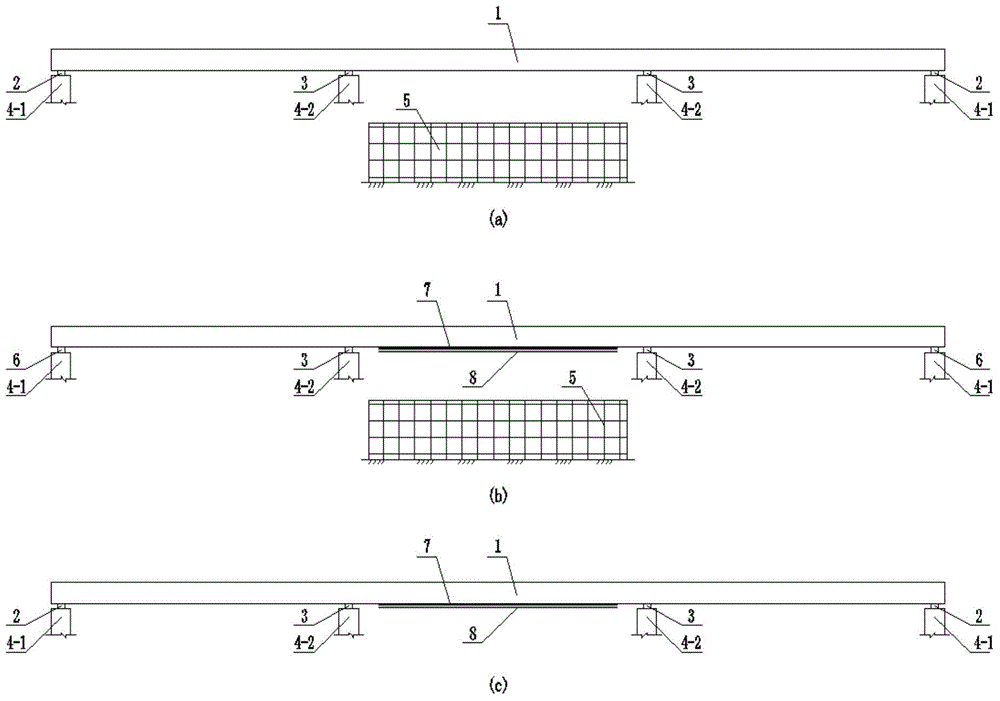
Method for reinforcing midspan of ordinary three-span steel continuous beam bridge
ActiveCN104652296AImprove the bending capacitySolve the problem of relative lag of stress and strainBridge erection/assemblyBridge strengtheningContinuous beamEngineering
The invention discloses a method for reinforcing a midspan of an ordinary three-span steel continuous beam bridge. The method comprises the following steps: building a construction operation platform; treating the surface of a midspan bottom plate; jacking up two side spans by virtue of a jack and then dismantling a side span support seat; lowering the jack to be lower than the side span support seat; calculating to obtain the lowered value of the jack relative to the side span support seat; unloading dead load bending moment of the midspan, and then pasting and fixing with a steel plate; jacking up the edge spans by virtue of the jack, and reinstalling the dismantled side span support seat at the original position; and lowering the jack, relocating the edge spans on the side span support seat, and then shifting out the jack. According to the method, by unloading the dead load bending moment of the midspan and then pasting and fixing with the steel plate, the steel plate can participate into the activities of bearing the load of a car and then adding dead load, can also participate into the activity of bearing the dismantled dead load bending moment; the bending bearing capacity of the main girder can be effectively improved; meanwhile, the material properties of reinforcing steel plate can be put into a relatively full play; and the bridge safety is not affected by lowering the jack in the construction process.
Owner:广州展亚土木工程技术有限公司
An internet data exchange system and its internet data switch
The invention relates to an inter-network data exchange system and an inter-network data exchange, including an inter-network data exchange terminal system, an inter-network optical disk transmission system, a special power supply and a physical platform. The inter-network data exchange terminal system includes: at least two network terminal controllers with CPU computing capability and programming capability, database, related software programs, network interface, and CD recorder. The inter-network disc transmission system includes: a horizontal or vertical track platform and a drive motor, a drive mechanism controller of a disc pick-and-place mechanical arm with CPU computing power and programming capabilities, a software program, a disc pick-and-place mechanical arm and corresponding Drive mechanism, signal detection unit composed of optical and magnetic detection components.
Owner:郝晓力
Safety switching method of high-speed train target base station based on relay station auxiliary
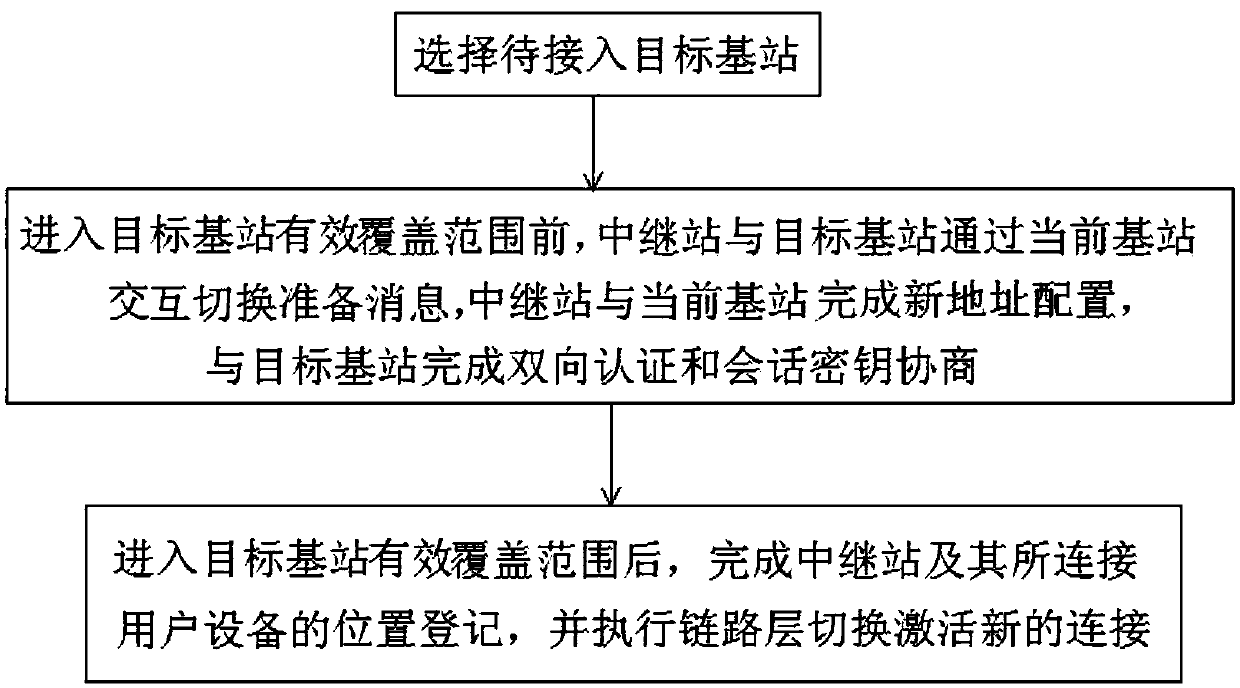
ActiveCN108495311APrevent Forgery AttacksSecurity is not compromisedTransmissionSecurity arrangementConfidentialityUser equipment
The invention discloses a safety switching method of a high-speed train target base station based on relay station auxiliary. The method comprises the following steps: (1) selecting a to-be-accessed target base station; (2) interacting switching preparation message by a relay station and the target base station through the current base station before entering the coverage range of the target basestation, accomplishing the new address configuration by the relay station and the current base station, thereby accomplishing the bidirectional authentication and the session key negotiation with thetarget base station; and (3) after entering the coverage range of the target base station, accomplishing the location registration of the relay station and the connected user equipment, and executingthe link layer switching to activate the new connection. Through the base station switching method disclosed by the invention, the forward security can be satisfied, the node forgery attack can be effectively prevented, the denial of service attack is prevented, the replaying attack is resisted, the computing efficiency is high, and the good safety protection is adopted for the confidentiality andthe integrity of the signaling message.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
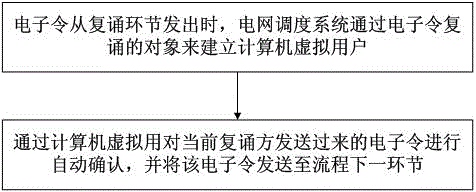
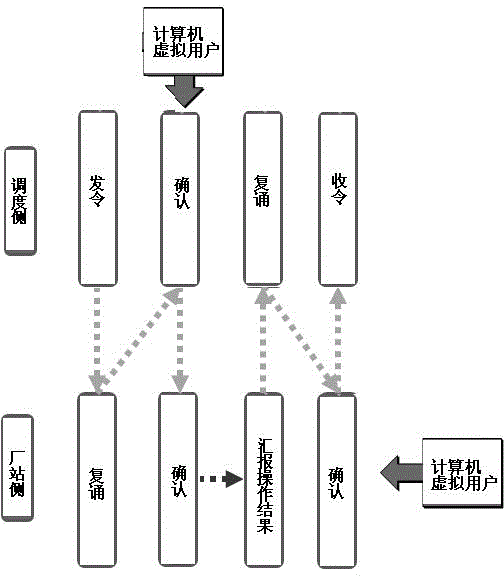
Automatic power grid dispatching electronic token confirming method based on network token issuing
The invention discloses an automatic power grid dispatching electronic token confirming method based on network token issuing. The automatic power grid dispatching electronic token confirming method based on network token issuing comprises the following steps of (1) establishing a computer virtual user by using a power grid dispatching system through an electronic token repeating object when an electronic token is issued from a repeating link; and (2) automatically confirming the electronic token transmitted from a current repeated side through the computer virtual user and transmitting the electronic token to a next link, which is a power station side confirming link or a dispatching side token collecting link, of a procedure. With the aid of an automatic verification function of network communication, integrity and correctness of data of the repeating link are guaranteed, so that the necessity of manual intervention of confirming operation after repeating is reduced. By the method of automatically confirming and transmitting the electronic token by the virtual user, the work efficiency of a dispatching operation command issuing procedure is improved under the condition that the safety of a system is not affected, and the application prospect is good.
Owner:GUANGXI POWER GRID CORP +1
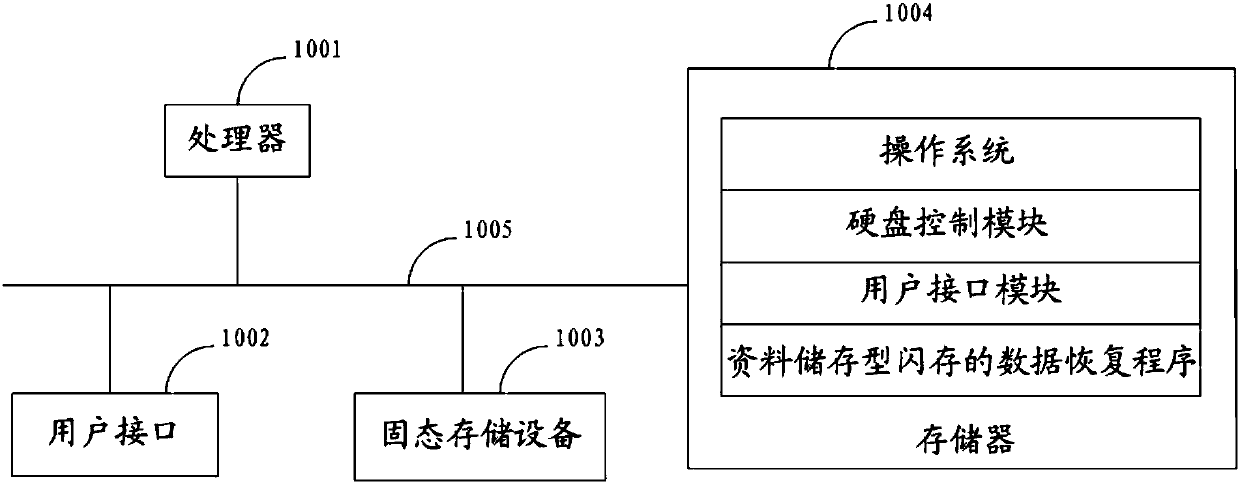
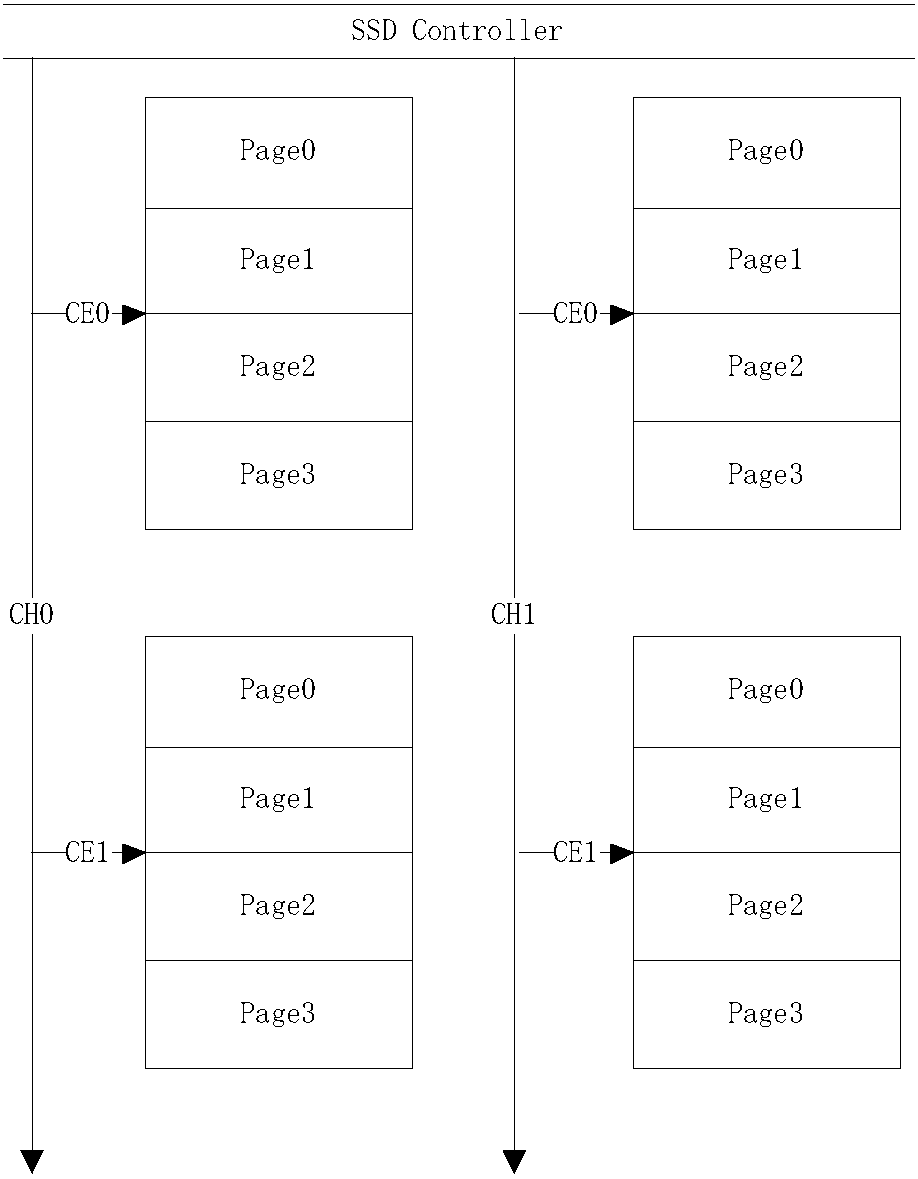
Data recovery method and device of flash memory of data storage type
ActiveCN107704338AReduce resource overheadStability is not affectedRedundant operation error correctionData bufferRecovery method
The invention discloses a data recovery method and device of a flash memory of a data storage type. According to the method, target physical-blocks in the flash memory of the data storage type are setto an abstract model with n abstract pages; a checking information page is selected from the n abstract pages, and a physical checking code is set for the checking information page; and data recoveryis carried out on a to-be-recovered abstract page, of which valid data are lost, according to the physical checking code of the checking information page when the to-be-recovered abstract page appears in the abstract model. According to the method, data which are invalid due to data destruction can be recovered for a case where the flash memory of the data storage type cooperates with a buffer with a lower resource overhead, and not impacting stability and security of work of the flash memory of the data storage type can be guaranteed while data recovery is carried out.
Owner:YEESTOR MICROELECTRONICS CO LTD +1
Digital signature scheme based on discrete logarithm problem
InactiveCN101635627AOvercoming inefficienciesTo overcome the inability to use the same value k for two different information x <sub>1<</sub> Key distribution for secure communicationUser identity/authority verificationDigital signatureDiscrete logarithm
The invention relates to a digital signature scheme based on a discrete logarithm problem. The technical scheme of the invention comprises the following steps: (1) user private key register and verification phase: a private key management centre publishes one primitive root g of a model p, wherein p is a large prime number, the value of the p determines the difficulty of decoding the private key, thus, the proper value of the p can be selected according to a safety requirement of a system to obtain the balance of safety and efficiency, a registered user registers a personal private key Ii to the private key management centre through a safe path, the private key simultaneously satisfies two conditions as above formula, the private key is stored well to avoid divulging after passing the verification of the private key management centre, and then the own public key g is published on a bulletin board system.
Owner:LANZHOU UNIVERSITY +1
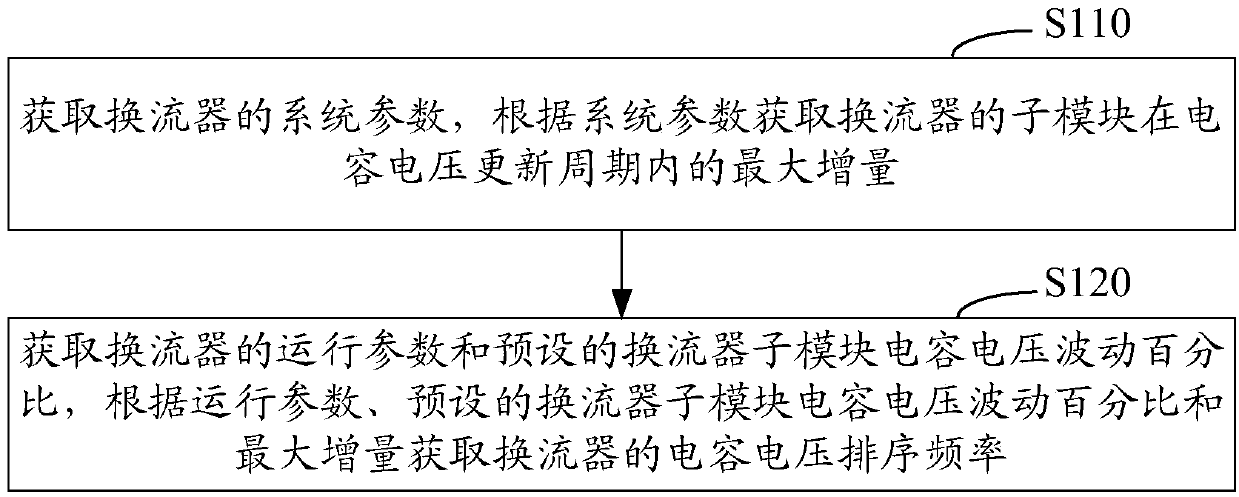
Capacitor voltage sorting frequency optimization control method and system of converter
ActiveCN107612290ASecurity is not compromisedUnaffected reliabilityPower conversion systemsCapacitanceSorting algorithm
The invention relates to a capacitor voltage sorting frequency optimization control method and system of a converter. The optimization control method comprises the steps of obtaining system parametersof the converter, operating parameters of the converter, and preset converter sub module capacitor voltage fluctuation percentage; obtaining the maximum increment of the sub module of the converter in a capacitor voltage updating period according to the system parameters; and obtaining the capacitor voltage sorting frequency of the converter according to the operating parameters, the preset converter sub module capacitor voltage fluctuation percentage and the maximum increment. In the scheme, the sorting frequency is obtained under the premise of satisfying the preset converter sub module capacitor voltage fluctuation percentage, so that it is ensured that the safety and reliability of the converter are not influenced; in addition, the minimum sorting frequency can be obtained under the maximum capacitor voltage increment; when the sorting frequency is applied to a capacitor voltage sorting algorithm, the switching frequency of a switching device can be lowered; and in addition, the implementation mode is simple, and the problem of overhigh resource consumption of the switching frequency of the converter can be solved.
Owner:ELECTRIC POWER RESEARCH INSTITUTE, CHINA SOUTHERN POWER GRID CO LTD
Flue gas waste heat recovery method for rotary kiln
InactiveCN102102944AGuaranteed qualityHigh return on investmentRotary drum furnacesEnergy industryRecovery methodEngineering
The invention discloses a flue gas waste heat recovery method for a rotary kiln, wherein the method can be used for realizing the efficient and reliable waste heat resource recovery of the rotary kiln. The method is characterized in that the flue gas of a rotary kiln 1 is introduced into waste heat recovery heat exchangers 2 and 3, the heat exchangers absorb the heat in the flue gas up to the hilt, and the waste heat is utilized after being transformed into the enthalpy values of liquid, gas and steam; a flue gas steady flow system 4 is connected at the flue gas outlet of the heat exchanger 3 in series, the flue gas steady flow system 4 can perform automatic regulation according to the thermal regulation of the rotary kiln 1, so that the change brought by additionally arranging the waste heat recovery heat exchangers 2 and 3 can be overcome, and the different temperature field and pressure field parameters of the rotary kiln 1 under different working conditions can be maintained; and the rotary kiln 1 is also provided with a radiation heating surface which can absorb high-temperature radiant heat so as to reduce the heat dissipation of the rotary kiln 1 and recover the waste heat in all directions, thereby most comprehensively recovering the waste heat up to the hilt, and simultaneously ensuring that the rotary kiln operates stably, parameters have no need to be changed and can not be changed, and the quality of produced products is not influenced at all.
Owner:厦门热工环保系统工程有限公司
Regulated gaming trusted energy saving
ActiveUS8235810B2Save moneyControl power consumptionMechanical apparatusVolume/mass flow measurementPower modeEngineering
Trusted Energy Saving (TES) methods applied to server based distributed downloadable gaming for allowing casino operators to significantly reduce their energy bills by placing the main controller of selected unused gaining machines into low-power mode while retaining total control and trust. Trusted Energy Saving is accomplished by: (1) establishing a secure “out-of-band” communication (or equivalent) between gaming machines and the casino's management system such that full network security is maintained while the main controller is in low power standby mode, (2) employing intelligent strategies to wake-up and turn-off the main controller of selected gaming machines by anticipating player use, (3) waiving the lengthy security verification required by regulation upon every gaming machine start-up and optionally (4) by displaying video promotional content on each turned-off gaming machine to continue to attract prospective players and to use the timing of each player approach to intelligently structure game menus based on the promotional content that has successfully attracted the player. The mapping of the TES gaming machines that are turned-on and in low-power mode may be periodically forwarded to the air-conditioning management system and / or to the lighting management system for energy optimization.
Owner:IGT
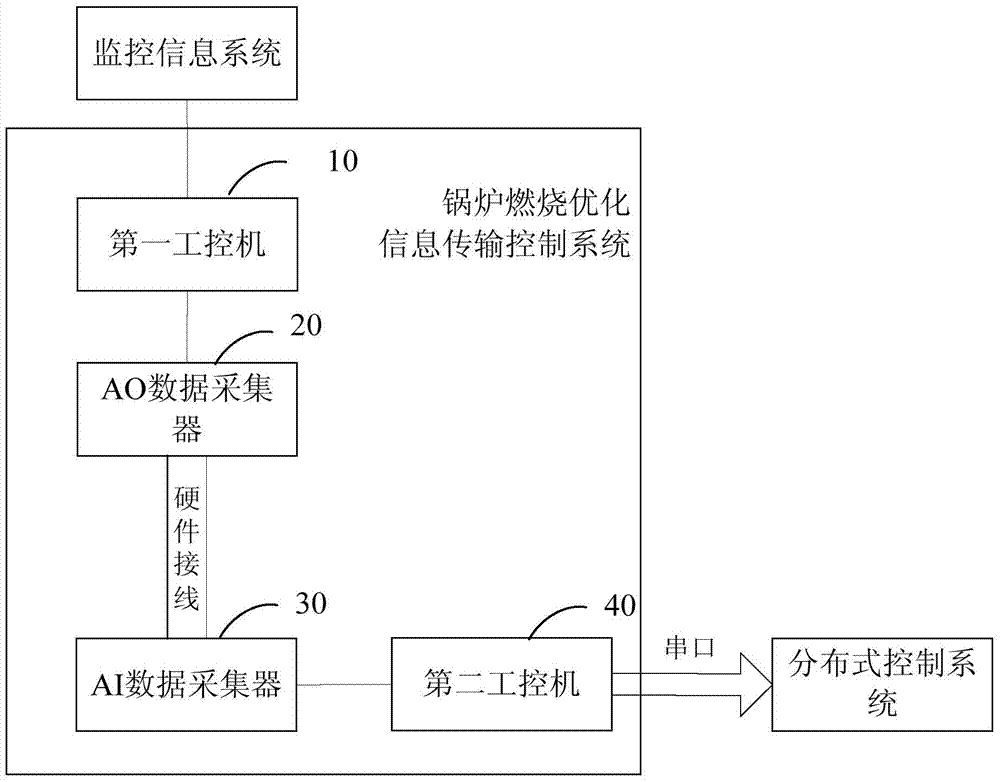
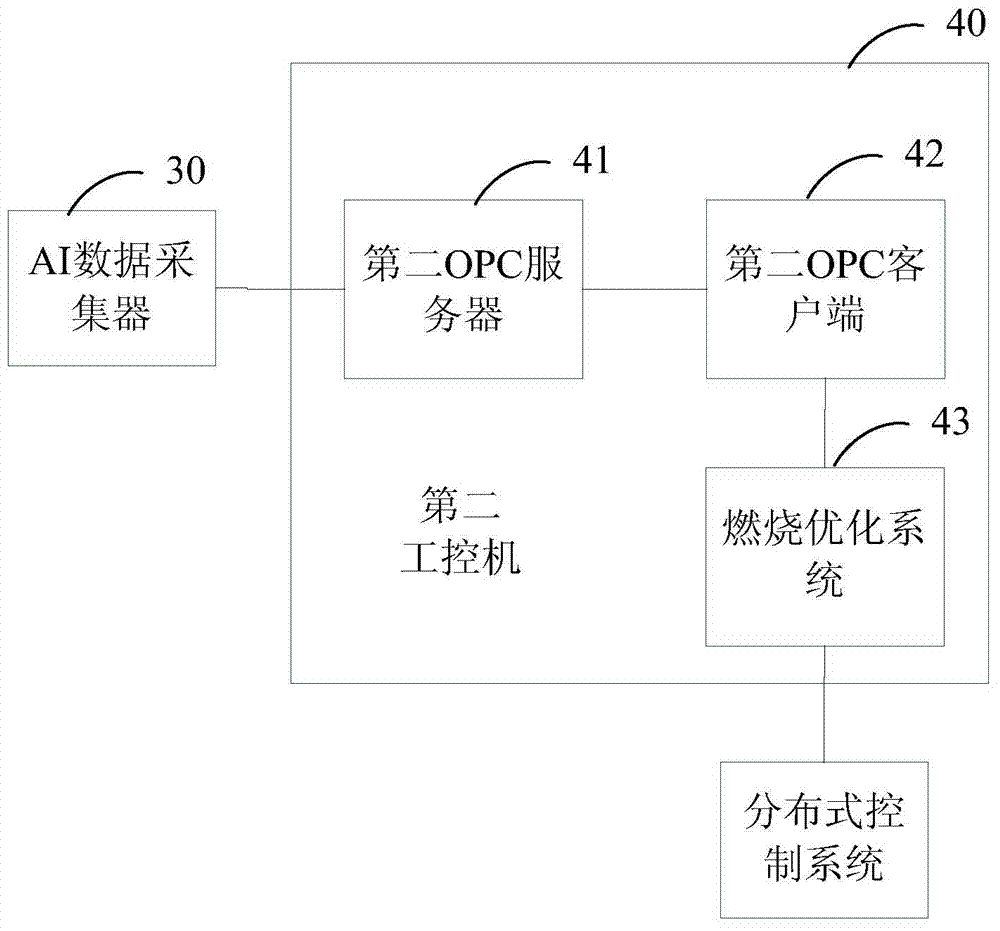
Boiler combustion optimization information transmission control system
ActiveCN103793338AEnsure safetySecurity is not compromisedElectric digital data processingInformation transmissionCombustion
The invention provides a boiler combustion optimization information transmission control system. Boiler combustion optimization information of an SIS is converted into physical signals through a first industrial personal computer, the physical signals can be recognized by an AO data acquisition device, the AO data acquisition device is communicated with an AI data acquisition device at the end of a DCS through hardware wiring, and therefore physical isolation between the SIS and the DCS is achieved. The boiler combustion optimization information is transmitted to a second industrial personal computer in the mode of the physical signals, calculation is performed on the boiler combustion optimization information through the second industrial personal computer to generate combustion optimization control instructions, and then the combustion optimization control instructions are transmitted to a distributed control system through a serial port for combustion control. Hardware wiring is a basic data transmission mode, is a pure physical signal, and can shield abnormal information and guarantee that the safety of the DSC is not influenced. A serial port communication mode has a complete verification mechanism, and therefore the safety of data communication is guaranteed further.
Owner:ELECTRIC POWER RES INST OF GUANGDONG POWER GRID +2
Method and system for secure communication between radio frequency identification tags and reading devices
ActiveCN104488219BReduce processing timeSecurity is not compromisedPublic key for secure communicationUser identity/authority verificationSecure communicationCiphertext
The invention relates to a method and a system for secure communication between an RFID tag and a reading device via an air interface, as well as a corresponding RFID tag and a corresponding reading device. The invention proceeds from the basic idea that, for secure communication between an RFID tag and a reading device, a modification of the Rabin method is used, in which the identification element of the plaintext M (of the RFID tag or of the object associated with it enters all In the scope of the plaintext) encryption, the RFID tag does not calculate the square modulo n of the plaintext M, that is, M2 mod n, but calculates the Montgomery reduction ("Montgomery reduction") of the square of the plaintext M with respect to the Montgomery base R modulo n, namely , C*=M2 R‑1 mod n, and the resulting ciphertext C* is used to verify the RFID tag. The modulus n=p·q is here the public key of the reader, wherein the prime numbers p, q are the private keys of the reader and the Montgomery base R is an integer greater than the modulus n.
Owner:捷德移动安全有限责任公司
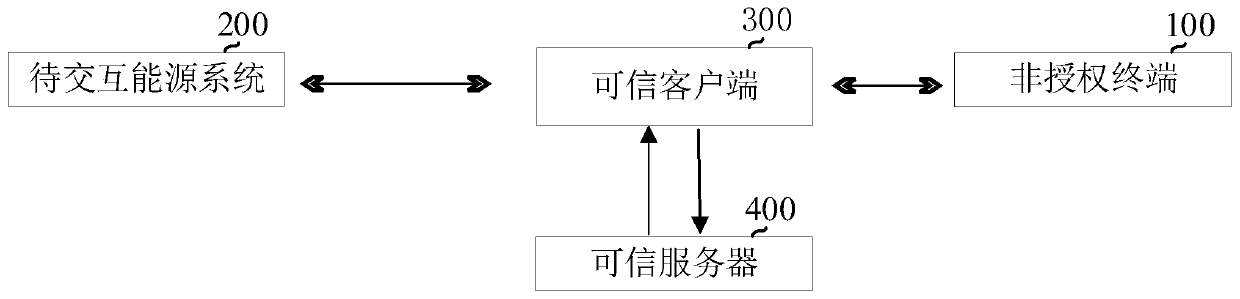
Trusted access method for energy internet, trusted client and server
ActiveCN110035076AAchieve securityRealize information interactionKey distribution for secure communicationAccess methodTrusted client
The invention provides a trusted access method for an energy internet, a trusted client and a server. A trusted authentication service system (comprising a trusted server and a trusted client) is added between an unauthorized terminal and a to-be-interacted energy system; the network access security of various energy internet unauthorized terminals is realized by using a credible access idea, theinformation interaction of a system-level energy system is realized, the interaction security between systems is ensured, and the problem of vulnerability attack caused by the difference between multiple systems is avoided.
Owner:NORTH CHINA ELECTRICAL POWER RES INST +1
Combined hierarchical cryptographic mechanism based on pairs
PendingCN111082944AImprove data storage modeReduce data transferKey distribution for secure communicationUser identity/authority verificationData transmissionInformation transfer
The invention provides a combined hierarchical cryptographic mechanism based on pairs. The mechanism comprises the following steps: S1, initializing a root PKG; S2, generating a private key; S3, performing signing; s4, performing signature verification. On the basis of an HIBC encryption mechanism, a combined public and private key idea is introduced, a data storage mode is improved, data transmission is reduced, and the robustness of the system is improved while the information transmission and signature verification efficiency is improved; a combined public key idea is introduced into generation and verification of public and private keys of the layer of the PKG, so under the condition that the PKG of a certain i layer is broken through, only the private keys of the nodes of the i + 1 layer can be forged under the PKG, the security of the nodes larger than the i + 1 layer is not affected, and the robustness of the system is greatly improved. A flat hierarchical identification password encryption and decryption and signature verification algorithm is designed, so the problem of overlong signature or ciphertext caused by interactive transmission of a plurality of PKG local layer public keys is avoided, and a support is provided for signature verification and ciphertext decryption offline optimization.
Owner:湖南安方信息技术有限公司
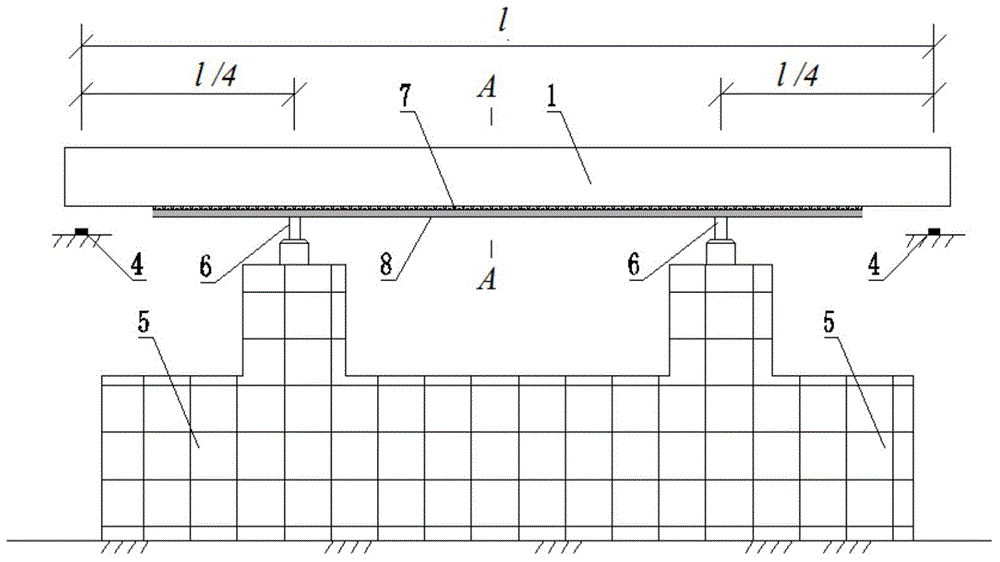
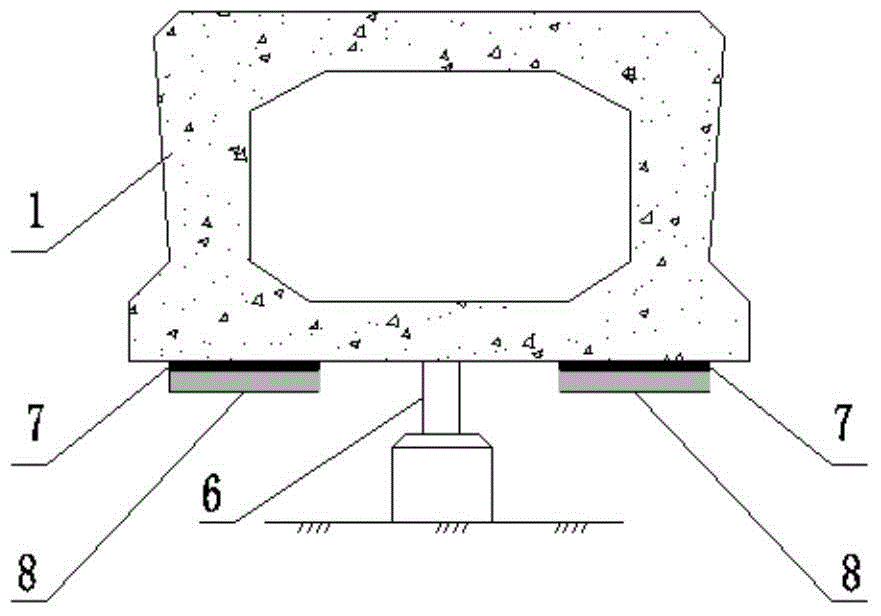
Simply supported hollow plate girder bending resistance reinforcement method
ActiveCN104818678AImprove the bending capacityIncrease profitBridge erection/assemblyBridge strengtheningRebarSteel plates
A simply supported hollow plate girder bending resistance reinforcement method has the construction steps of demounting ancillary facilities of a bridge deck, chiseling hinge joints between girders and a bridge deck cast-in-situ layer, and retaining the girders; setting up operation platforms used for construction to carry out surface treatment on the girders; jacking the girders through jacks under the precondition that safety of the girders is guaranteed; removing mid-span bending moments of dead load of the girders; sticking steel plates after the bending moments of dead load of the girders are removed; pouring concrete to the hinge joints and the bridge deck cast-in-situ layer; synchronously uninstalling the jacks after the curing time is reached, so that the girders are located on supports, and then removing the jacks; pouring concrete to the hinge joints and the bridge deck cast-in-situ layer; restoring the ancillary facilities of the bridge deck, and completing the bending resistance reinforcement of the girders. The simply supported hollow plate girder bending resistance reinforcement method has the beneficial effects that the steel plates are stuck after the mid-span bending moments of dead load of the girders are removed, thus the steel plates can not only participate in the bearing of the load of automobiles and later-imposed dead load, but also participate in the bearing of the removed bending moments of dead load, so that the bending resistance bearing capacity of the girders can be improved; the steel plates are stuck when the strain stress of rebars at mid-span tensile regions of the girders is decreased, so that the material performance of the reinforcing steel plates can be fully exerted better.
Owner:广州展亚土木工程技术有限公司
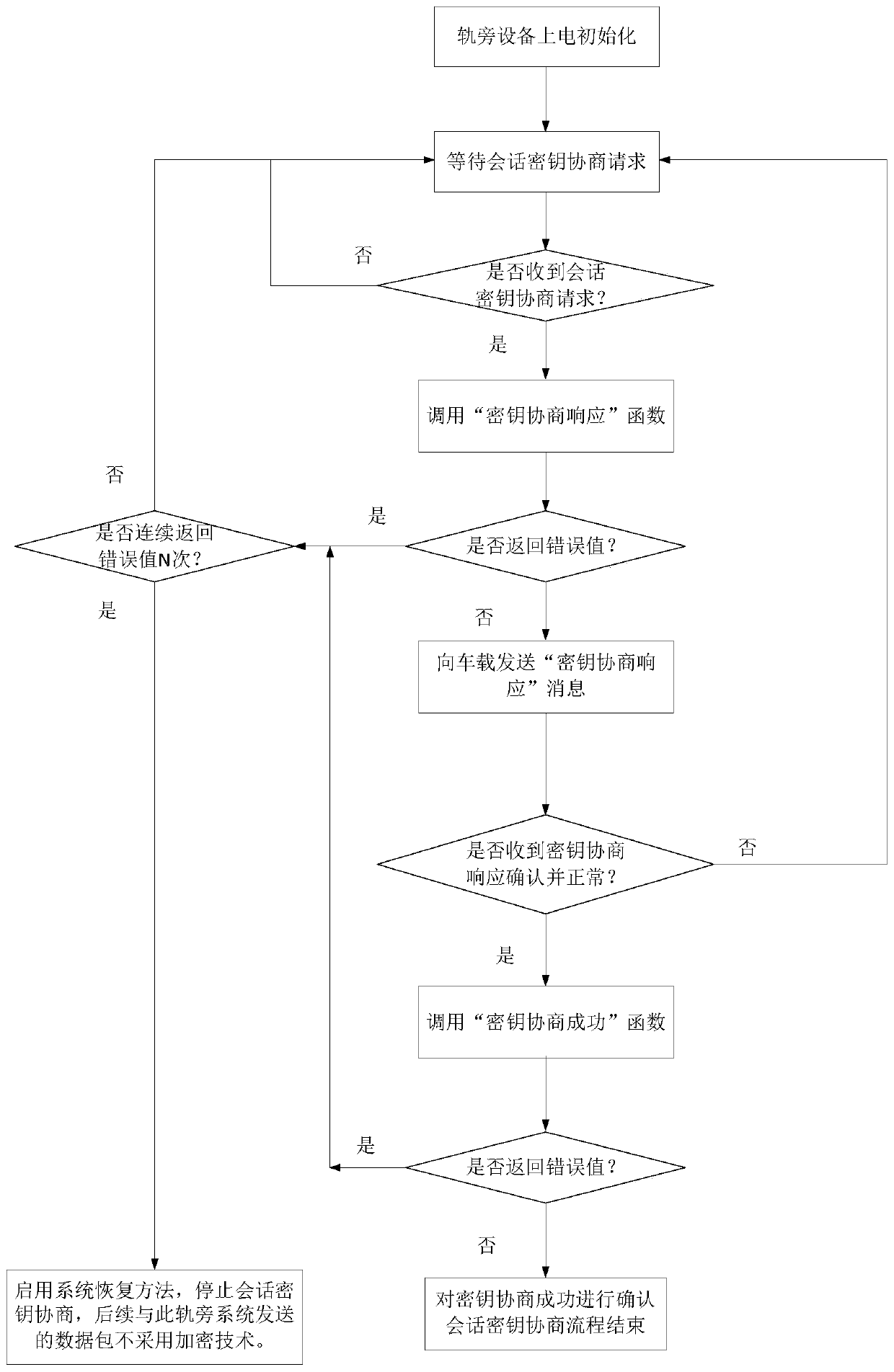
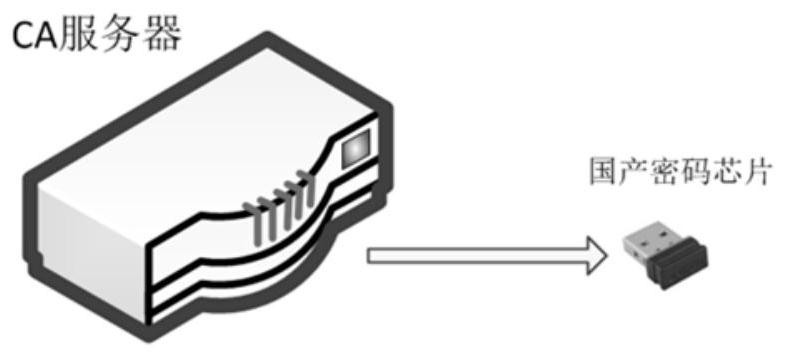
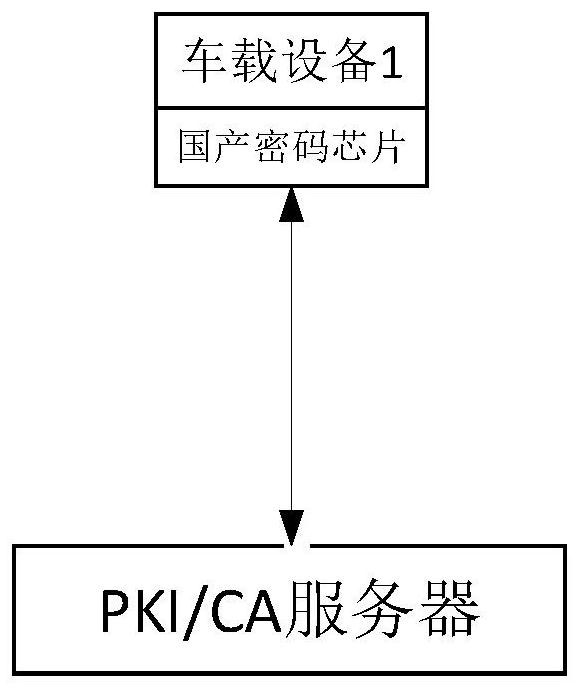
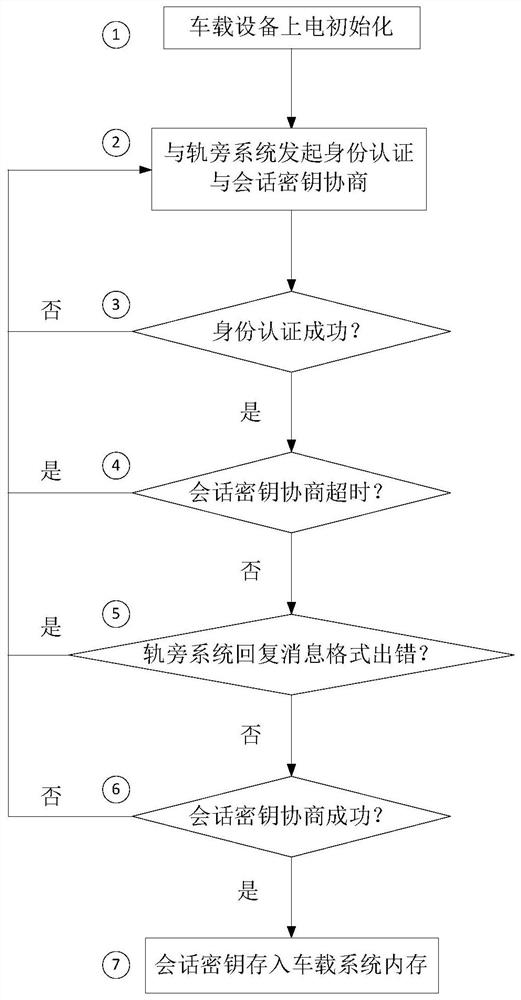
Operation and restoration method of rail transit signal system based on domestic encryption technology
ActiveCN110733535ADoes not affect normal operationSecurity is not compromisedRailway traffic control systemsSignaling systemEmbedded system
The invention relates to an operation and restoration method of a rail transit signal system based on domestic encryption technology. According to the method, it is judged that a domestic encryption security chip possibly fails through the signal system itself, if a fault occurs, the domestic encryption security chip is isolated, the signal system is enabled to restore to a state where the encryption technology is not adopted, and meanwhile, warning information is given to a maintenance terminal in the shortest time; and compared with the prior art, the method has the advantages that the normal operation of the signal system is still not affected even under the condition that the domestic encryption security chip fails, and the like.
Owner:CASCO SIGNAL
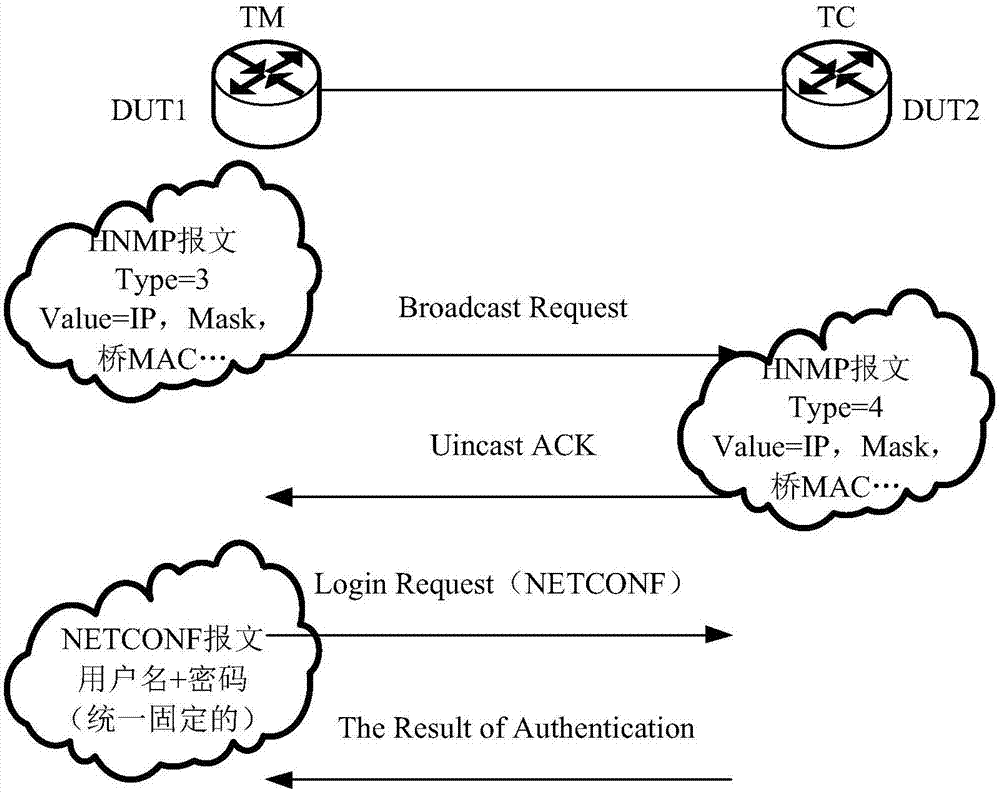
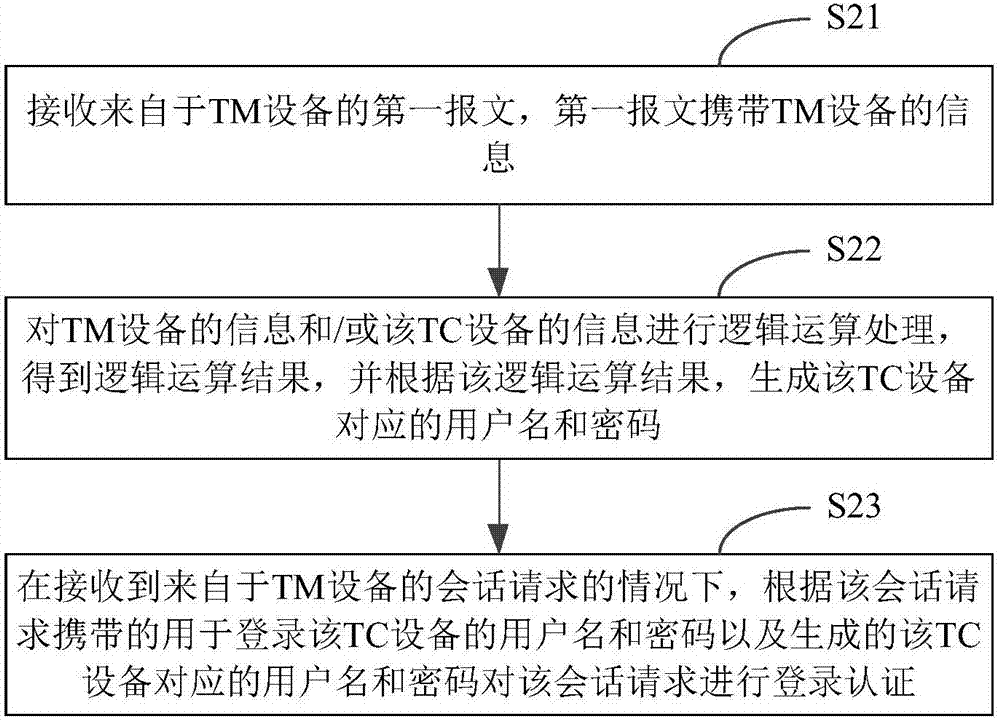
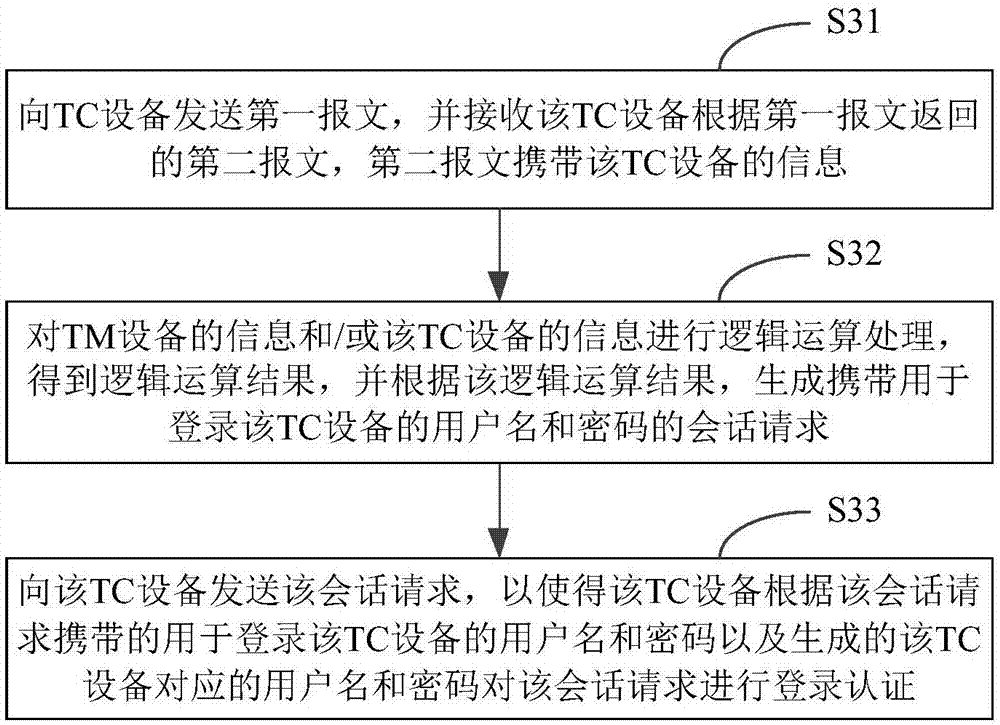
Login authentication method and device
ActiveCN107888383ASecurity is not compromisedImprove securityKey distribution for secure communicationUser identity/authority verificationPasswordLogical operations
The invention relates to a login authentication method and a login authentication device. The method comprises the steps of receiving a first message from TM equipment, wherein the first message carriers the information of the TM equipment; performing logical operation processing on the information of the TM equipment and / or the information of TC equipment to acquire a logical operation result, and generating a user name and a password corresponding to the TC equipment according to the logical operation result; and under the condition of receiving a session request from the TM equipment, performing login authentication on the session request according to the user name and the password used for logging in the TC equipment and carried by the session request and the generated user name and password corresponding to the TC equipment. According to the login authentication method and device provided by the invention, the user name and the password corresponding to each piece of TC equipmentare dynamically generated, and do not need to be statically configured by an administrator of the TC equipment. In addition, the user name and the password corresponding to each piece of TC equipmentare not accordant basically, and the security of the SmartMC network is wholly greatly improved.
Owner:NEW H3C TECH CO LTD
Load-bearing inverted abdominal muscle training device capable of stimulating muscles in multiple directions and using method thereof
InactiveCN111714838AContribute to developmentMeet the needs of training intensityMuscle exercising devicesPhysical medicine and rehabilitationTraining intensity
The invention belongs to the technical field of fitness equipment, and discloses a load-bearing inverted abdominal muscle training device capable of stimulating muscles in multiple directions and a using method thereof. The invention discloses the load-bearing inverted abdominal muscle training device capable of stimulating muscles in multiple directions. The device comprises a bottom plate, fourcorners of the upper surface of the bottom plate are fixedly connected with four corners of the lower surface of a top frame through four vertical rods respectively, an auxiliary handle is fixedly connected to the left side of the lower surface of the top frame, a weight adjusting frame is fixedly connected to the right end of the lower surface of the top frame, and a limiting plate is fixedly connected to the middle of the weight adjusting frame. The invention discloses the load-bearing inverted abdominal muscle training device capable of stimulating muscles in multiple directions, a load point position adjusting mechanism is arranged; the stress point of a trainee in the upside-down abdominal curl process can be adjusted, stronger stimulation can be provided for abdominal muscles, the stimulation on the abdominal muscles is more targeted by adjusting the stress point, the comprehensive development and sufficient training of the abdominal muscles are facilitated, and the requirement of weightlifting athletes for abdominal muscle training intensity can be fully met.
Owner:周志富
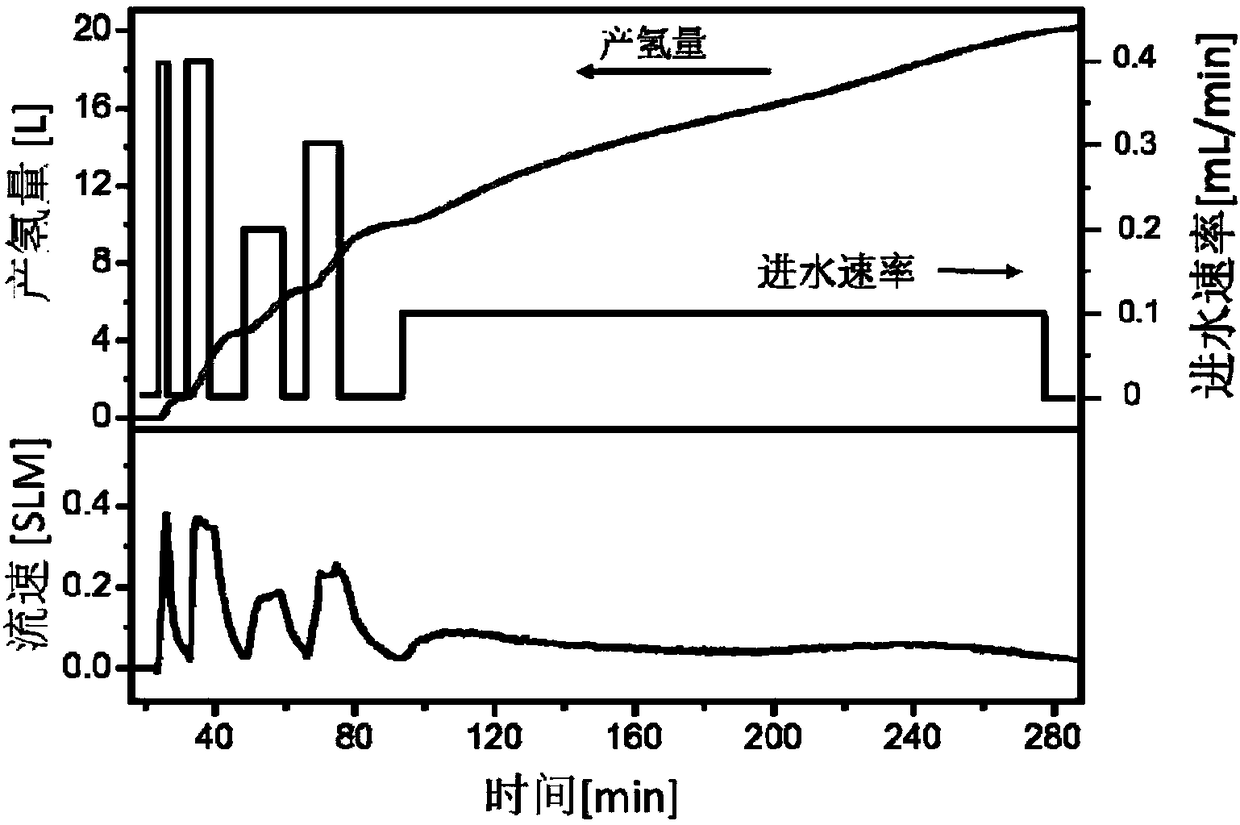
Atmospheric pressure hydrogen reaction device and hydrogen fuel cell power supply system
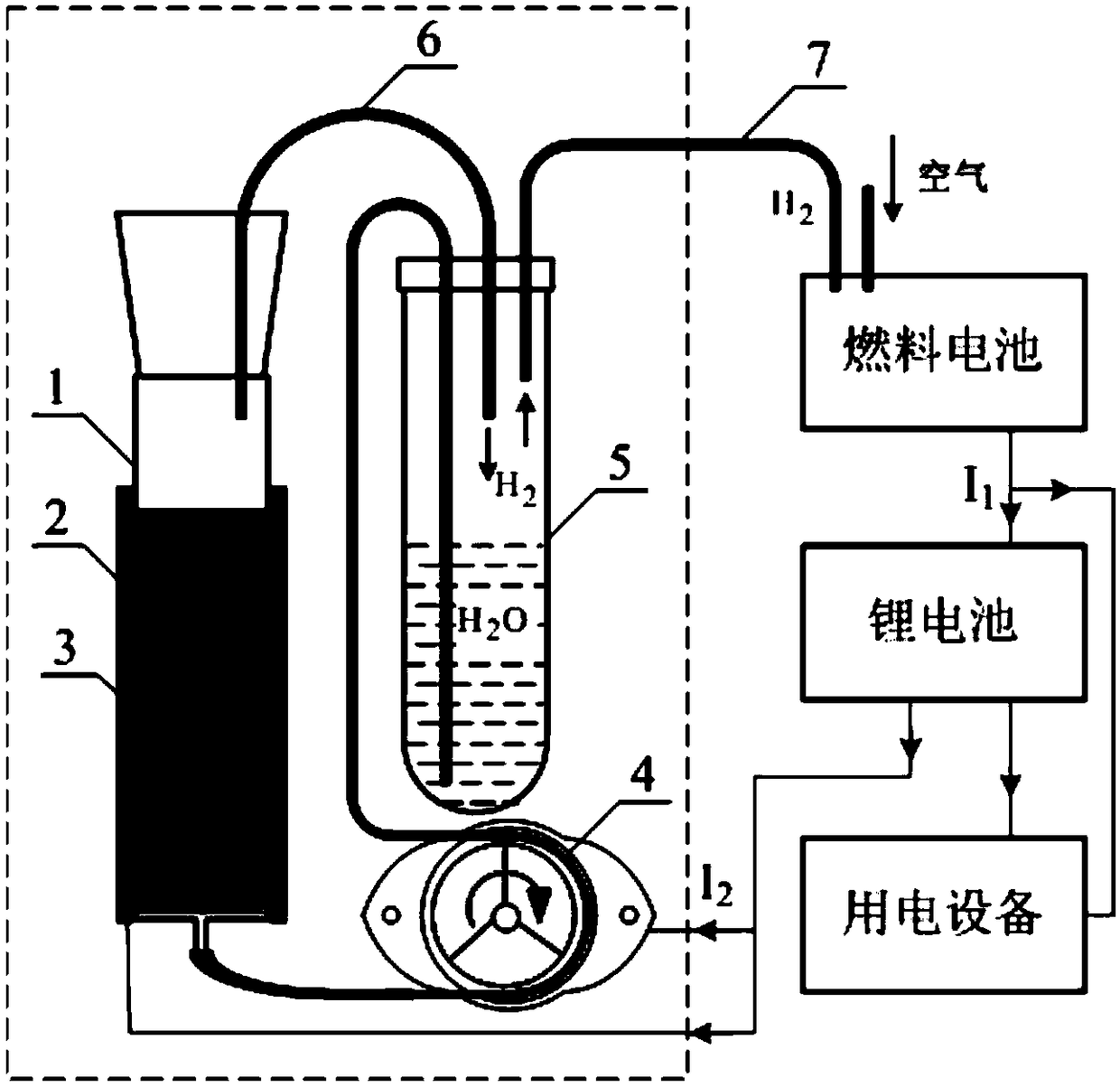
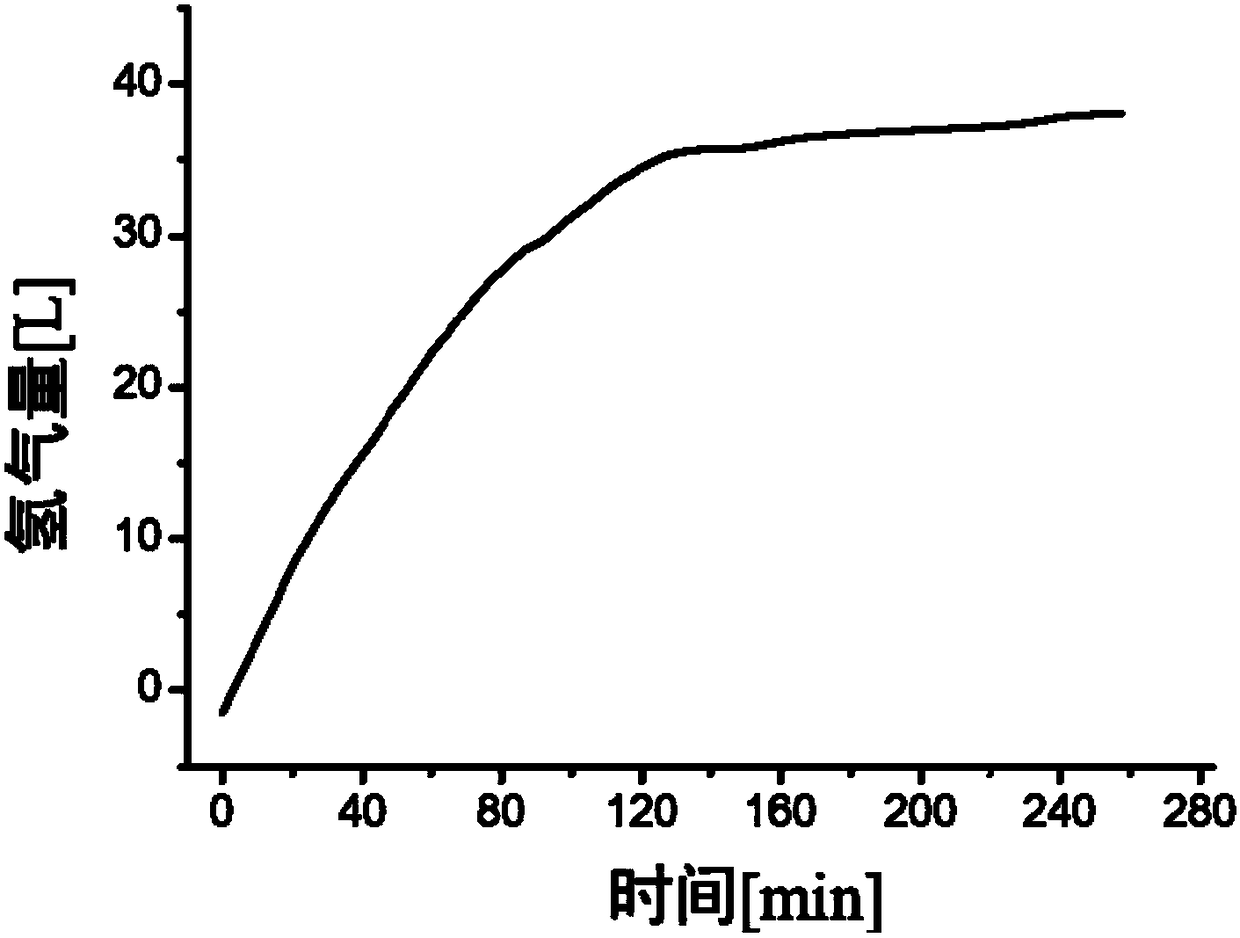
ActiveCN106276790BIncrease hydrogen production capacityConserve waterBatteries circuit arrangementsHydrogen productionLiquid waterLow load
The invention discloses a normal-pressure hydrogen production reaction device which comprises a reactor, a conveying pump and a heater, wherein the reactor is used for loading a hydrolysis hydrogen production material and provided with a water inlet and a first gas outlet; one end of the conveying pump is connected with a water source while the other end of the conveying pump is connected with the water inlet, and the conveying pump is used for performing control so as to convey water to the reactor; the heater is used for heating the water so that the water entering the reactor is in a gasified state. Preferably, the normal-pressure hydrogen production reaction device also comprises a water container for storing liquid water as a water source; the water container is provided with a water outlet which is connected with the conveying pump. According to the normal-pressure hydrogen production reaction device, the temperature of hydrolysis reaction is increased, the uniformity of contact between the water and the solid reactant is greatly improved, sufficient conversion of the solid reactant is facilitated, the reaction temperature can be kept at relatively high temperature through reaction heat release, and overall energy consumption of the system is very low. The device cooperates with a lithium battery and a hydrogen fuel to form a hydrogen fuel cell power supply system, sudden change of load power can be addressed very well, the output stability is improved, and the waste of hydrogen energy is avoided in the case of relatively low load.
Owner:苏州清德氢能源科技有限公司
Case body of electric fire case
InactiveCN103423810AChange the status quo of only roasting feetLow temperature requirementLighting and heating apparatusSpace heating and ventilation detailsEngineeringSecurity level
The invention discloses a case body of an electric fire case. The case body is characterized in that one or a pair of U-shaped grooves are formed in the upper edge of a frame of the case body, and holes which are capable of exposing the U-shaped grooves completely are formed in the skirt of a covering quilt. A user can extend feet into the case body through the holes, knees can span on the U-shaped grooves in a crossed or separated manner, so that calves and knees can get warmed with the feet simultaneously; gaps between the legs and the case body and the covering quilt are eliminated, and comfort and energy-efficient effect of the existing electric fire case are improved significantly; when the user stands up and leaves, the U-shaped grooves are cooling channels, so that possibility of a fire due to heat accumulating is eliminated completely, and security level of the existing electric fire case is raised significantly.
Owner:易礼
Methods and system for secure communication between RFID tag and reader
ActiveCN108833103AReduce processing timeSecurity is not compromisedPublic key for secure communicationUser identity/authority verificationPlaintextSecure communication
The invention relates to methods and a system for secure communication between an RFID tag and a reader via the air interface and to corresponding RFID tags and corresponding readers. The invention isbased on the fundamental idea that, for the purpose of secure communication between an RFID tag and a reader, a modification of Rabin's method is used, in which, within the scope of encrypting plaintext M, which includes an identification element of the RFID tag or of an object provided with the latter, the Montgomery residual ('Montgomery reduction') of the square of the plain text M modulo n with respect to a Montgomery base R, that is to say C* = M<2>R<-1>mod n, is calculated from the RFID tag instead of the square of the plain text M modulo n, that is to say M<2>mod n, and the resultantciphertext C* is used to authenticate the RFID tag. In this case, the modulus n (being equal to p.q) is the public key of the reader, the prime numbers p, q are the private key of the reader and the Montgomery base R is an integer greater than the modulus n.
Owner:JIEDE MOBILE SECURITY CO LTD
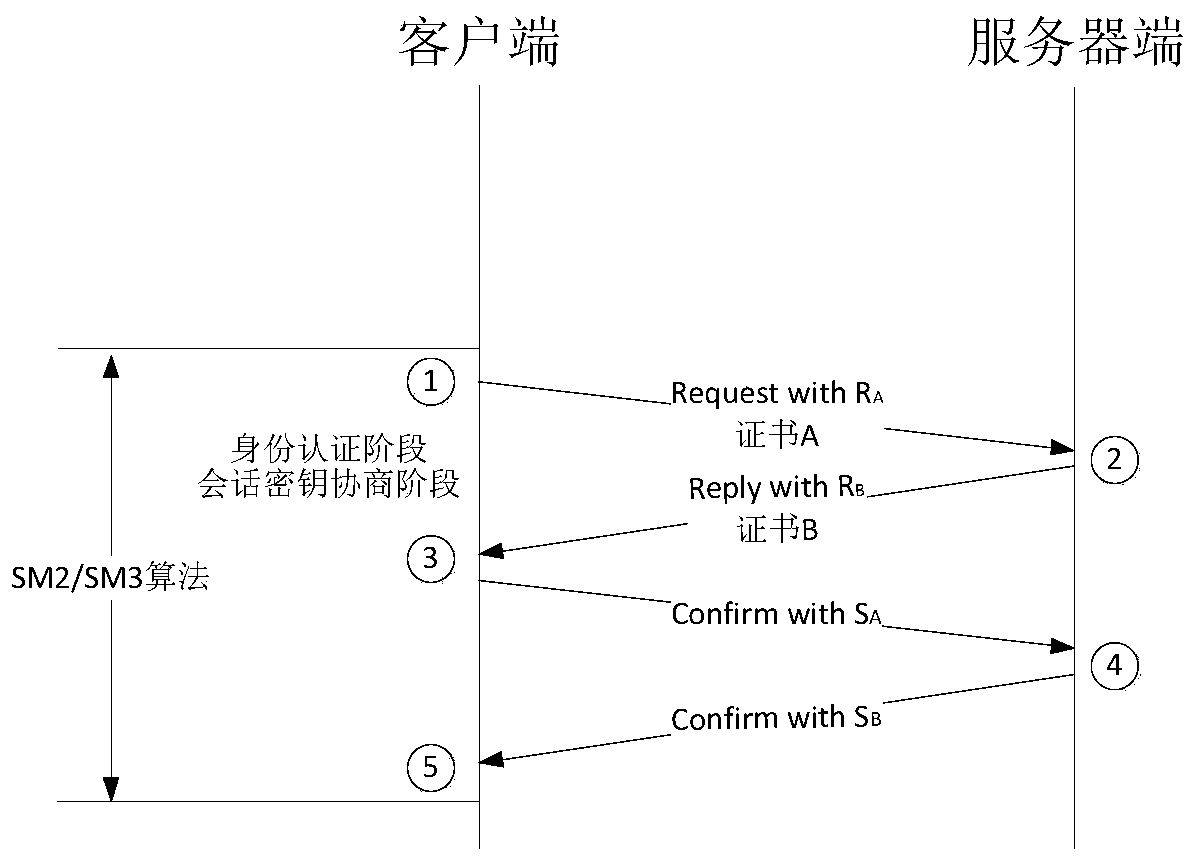
Information security and confidentiality method and device for rail transit on-board signal control system
ActiveCN109889484BImprove the level of information securityImprove securityKey distribution for secure communicationUser identity/authority verificationConfidentialityIn vehicle
The invention relates to a method and device for information security and confidentiality for a rail transit on-board signal control system. The method adds a domestic password protection technology to the on-board signal system part of a communication-based train control system, and the on-board signal system adds a domestic password protection technology. After that, the workflow of the security method includes a chip filling phase, a certificate revocation list update phase, an identity authentication and session key negotiation phase, and an application data communication phase. Compared with the prior art, the present invention applies the data encryption technology to the end-to-end application layer equipment of the vehicle-ground wireless communication of the signal system, thereby improving the information security level of the vehicle-ground wireless communication and the like.
Owner:CASCO SIGNAL
Regulated gaming trusted energy saving
InactiveUS20130005435A1Save moneyControl power consumptionMechanical apparatusApparatus for meter-controlled dispensingPower modeEngineering
Casino operators can reduce their energy bills by placing the main controller of selected unused gaming machines into low-power mode while retaining total control and trust. Trusted Energy Saving is accomplished by: (1) establishing a secure “out-of-band” communication (or equivalent) between gaming machines and the casino's management system such that full network security is maintained while the main controller is in low power standby mode, (2) employing intelligent strategies to wake-up and turn-off the main controller of selected gaming machines by anticipating player use, (3) waiving the lengthy security verification required by regulation upon every gaming machine start-up and optionally (4) by displaying video promotional content on each turned-off gaming machine to continue to attract prospective players and to use the timing of each player approach to intelligently structure game menus based on the promotional content that has successfully attracted the player.
Owner:IGT
Preservative method of haematococcus pluvialis pulp or mashed haematococcus pluvialis
InactiveCN107535799AWon't rotReduce breeding rateClimate change adaptationFood preservationPreservativeMicroscopic exam
The invention discloses a preservative method of haematococcus pluvialis pulp or mashed haematococcus pluvialis. The method specifically comprises the following steps that firstly, the pH value of thehaematococcus pluvialis pulp of which the concentration is 3g / L-10g / L is regulated with an acid and an alkali to be smaller than or equal to 6, then 0.05%-0.5% of a frequently-used preservative is added to the haematococcus pluvialis pulp, uniform mixing is performed, after 3 days, any colonies are not found to be formed, the haematococcus pluvialis pulp is not rotten or generates bad smell, andthrough microscopic examination, haematococcus pluvialis cells are found to be complete without rupture. According to the preservative method disclosed by the invention, the condition that haematococcus pluvialis liquid is rotten or generates bad smell in the process of concentration or before spray drying can be effectively avoided, the condition that the haematococcus pluvialis cells are damagedand ruptured is also avoided, the product quality cannot be influenced, and the preservative method is low in cost and simple in operation flows.
Owner:山东鸣惠生物科技股份有限公司
Network multicast information encryption method against conspiracy attack
InactiveCN101860796BSmall amount of calculationReduce energy consumptionBroadcast service distributionSecurity arrangementPretreatment methodHash function
The invention relates to a network multicast information encryption method against conspiracy attack, which keeps ciphertext length unchanged, shortens the cost for node encryption and decryption and has application prospect without changing the security. The security of an encryption scheme of the invention is based on the complicacy of calculating elliptic curve bilinear map in mathematics, andthe key to reduce the computational energy consumption of a system is to reduce the bilinear map operation number. The bilinear operation can be completed in advance through a pre-treatment method and released in the form of a public key, the encryption and decryption process only involves a small amount of bilinear operation. Assuming the bilinear map is that: e: G0 *G0 -> G1, wherein g is an element generated on a G0 group, the order of the group is q, the public key with the attribute of i is as follows: PKi=(PKil,PKi2), wherein PKil=gti, PKi2=e (g,g)q.ti,ti=H(i), and H(i) is the Hash function value to i. When in encryption and decryption, the scheme of the invention only needs to carry out simple multiply operation.
Owner:盐城市鹤业实业投资有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com