Method and system for secure communication between radio frequency identification tags and reading devices
A reading device and secure communication technology, applied in the field of RFID tags and corresponding reading devices, can solve the problems of slow verification process and achieve the effect of saving processing time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
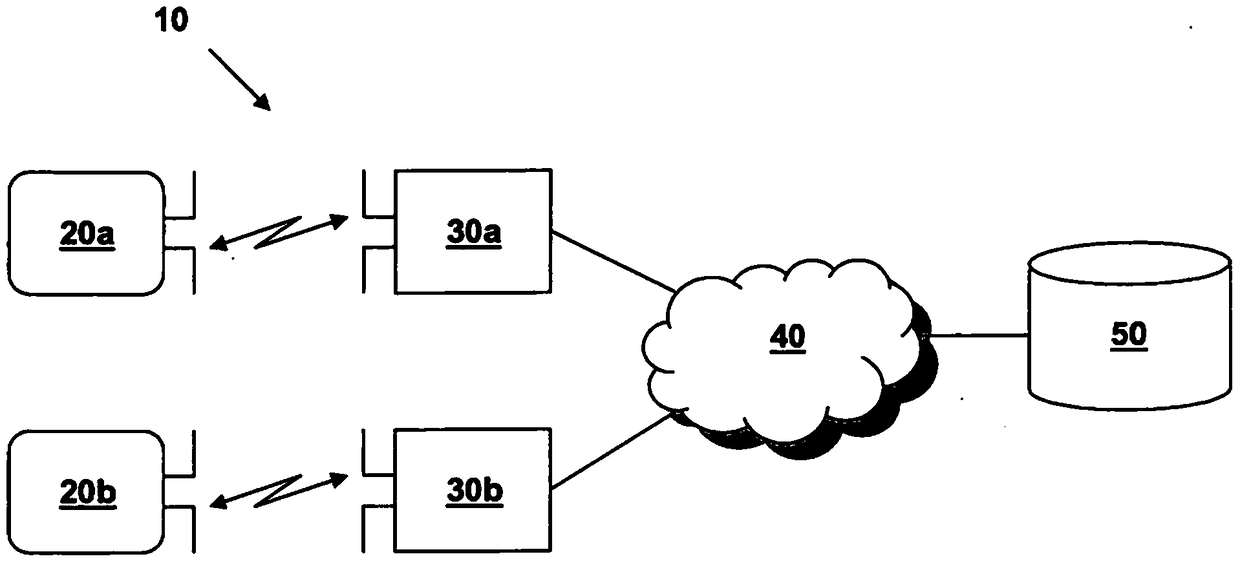
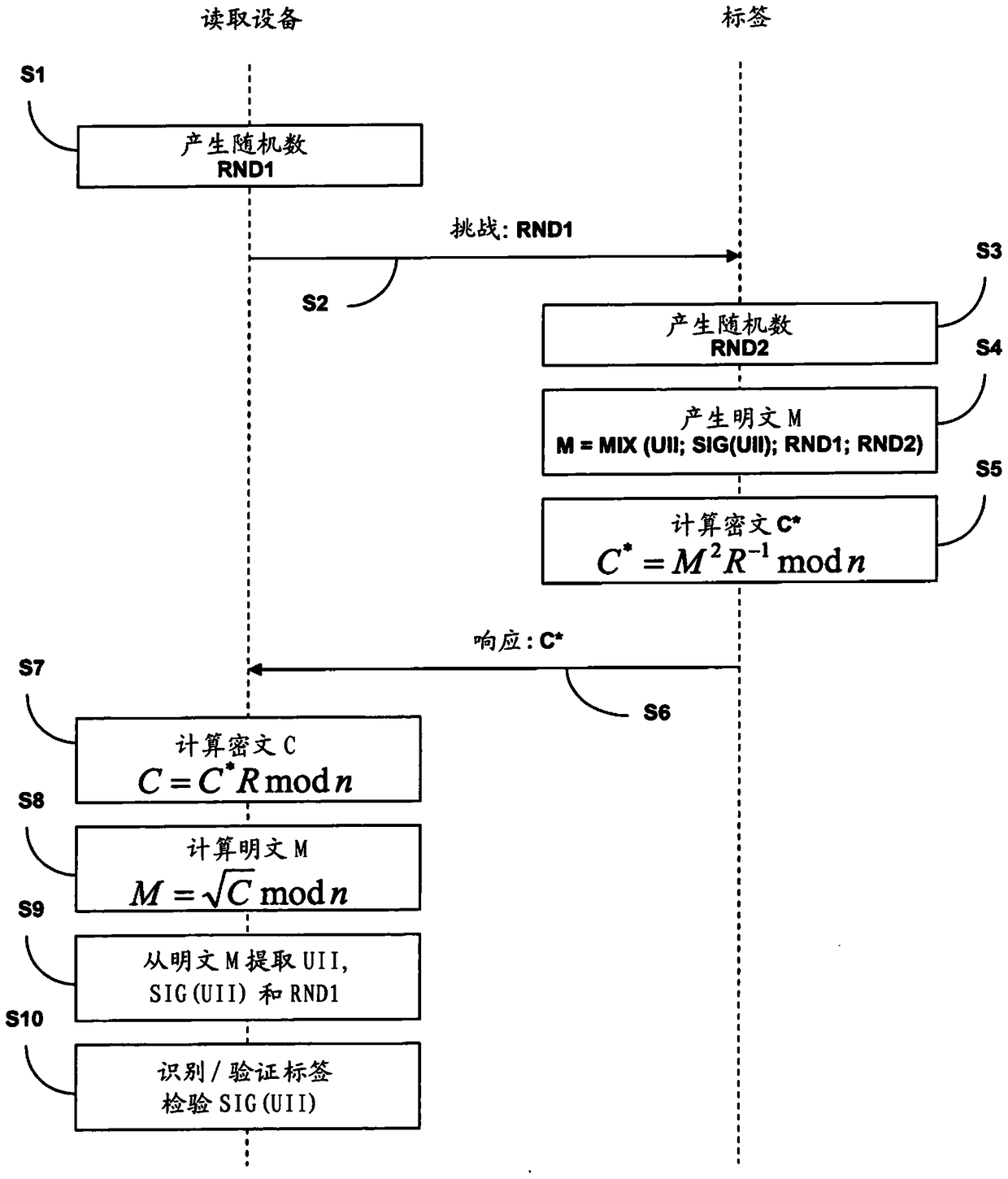
[0039] figure 1 A schematic diagram of a system 10 for secure communication between RFID tags and reading devices according to a preferred embodiment of the present invention is shown. System 10 may be, for example, an electronic ticketing system in which the RFID tag is an electronic ticket carried by a person.
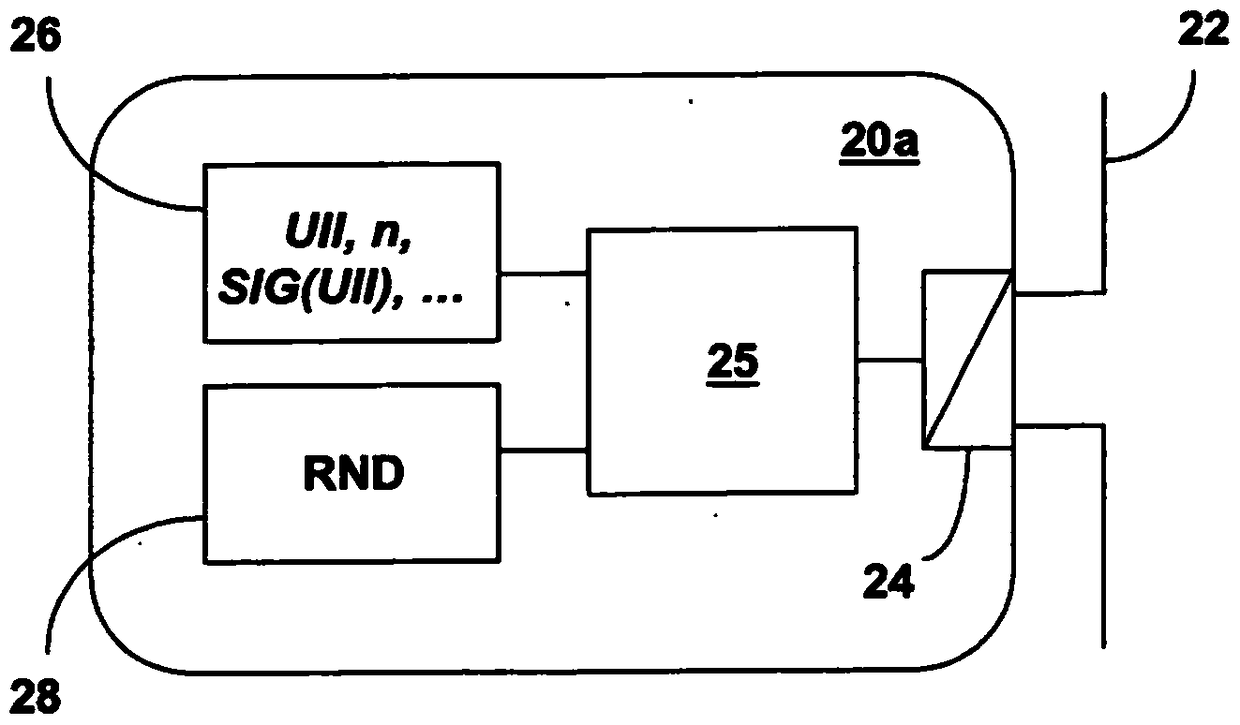
[0040] For example, the system 10 includes two RFID tags, namely, RFID tag 20a and RFID tag 20b, which can communicate with the reading device 30a and the reading device 30b through the air interface respectively, and the respective RFID tags 20a, 20b are located in their communication range or reading range. Take the range. Preferably, the RFID tags 20a, 20b are RFID tags according to standard ISO / IEC 18000-63 or EPC Class-1 Generation-2, also referred to herein as EPC tags.
[0041] The reading devices 30a, 30b are connected via a suitable communication network 40 to a background or backend system 50 in which data associated with the RFID tags 20a, 20b are stored...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com