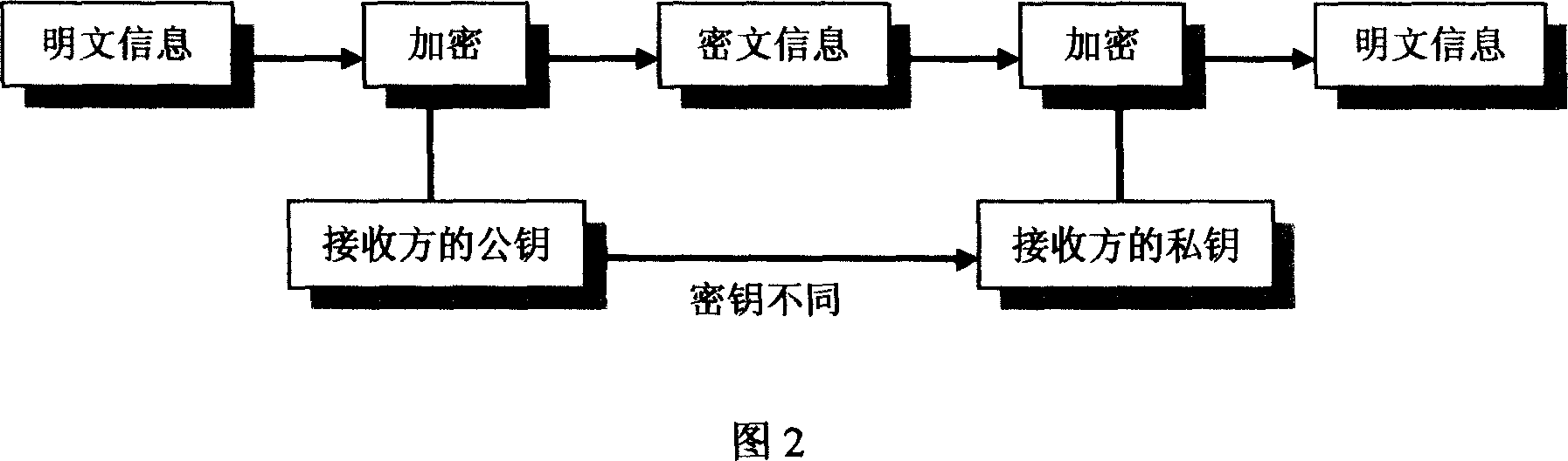
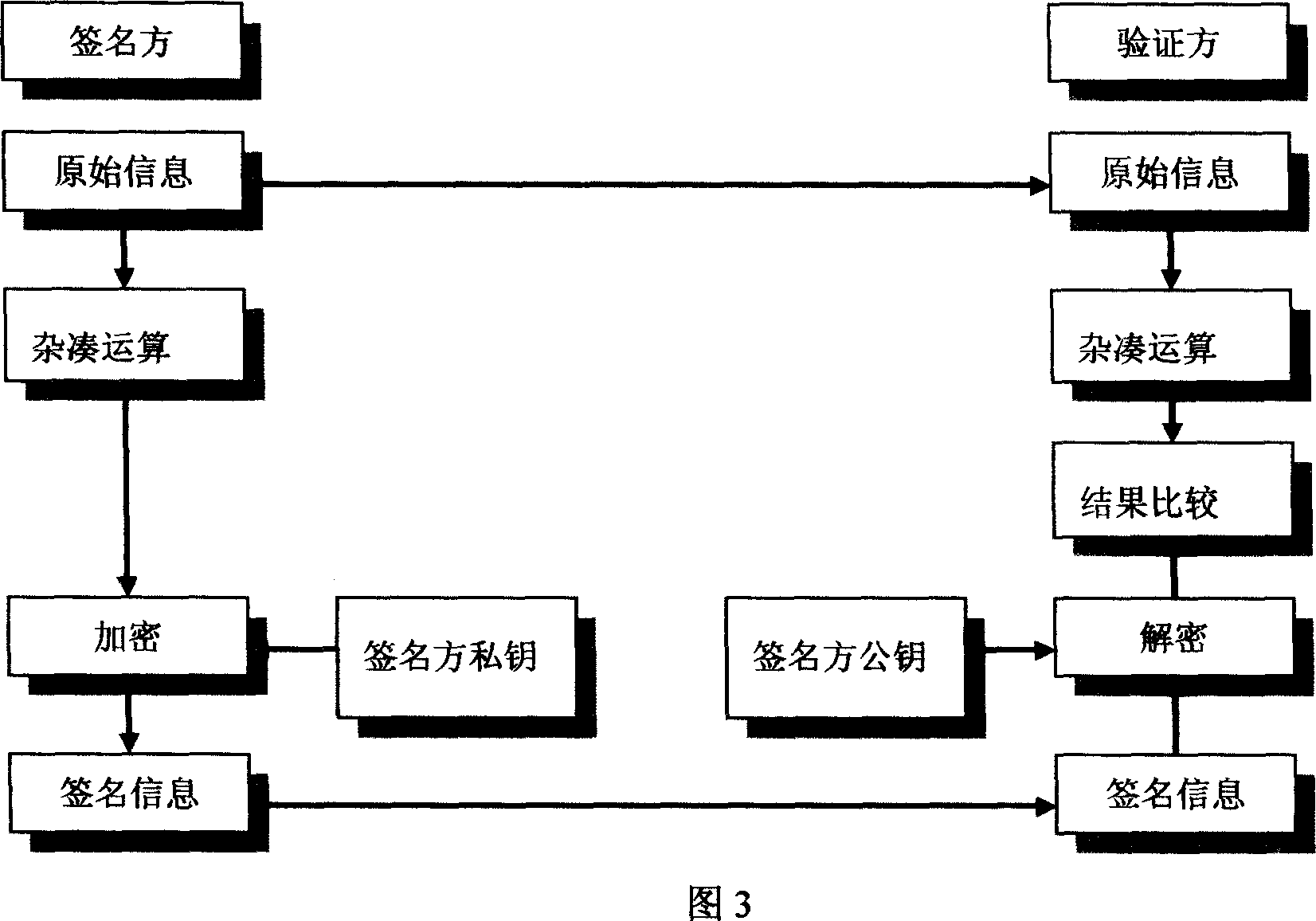
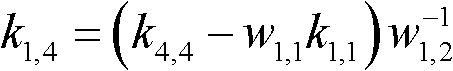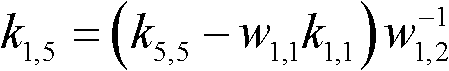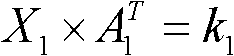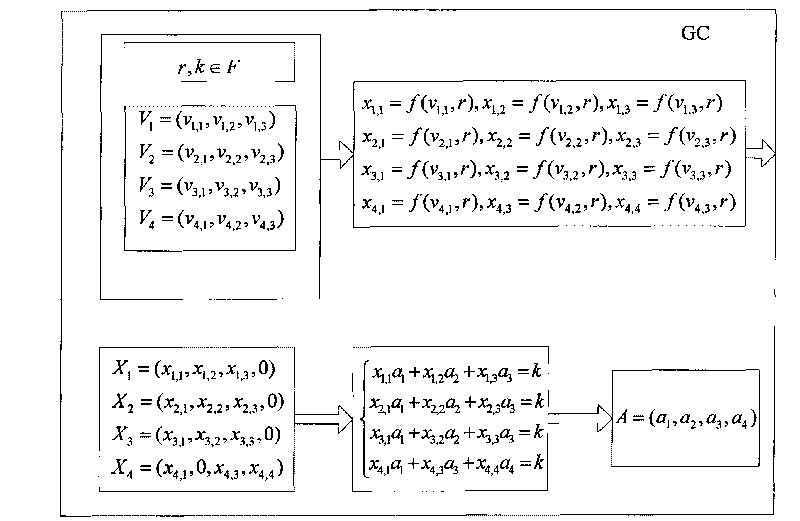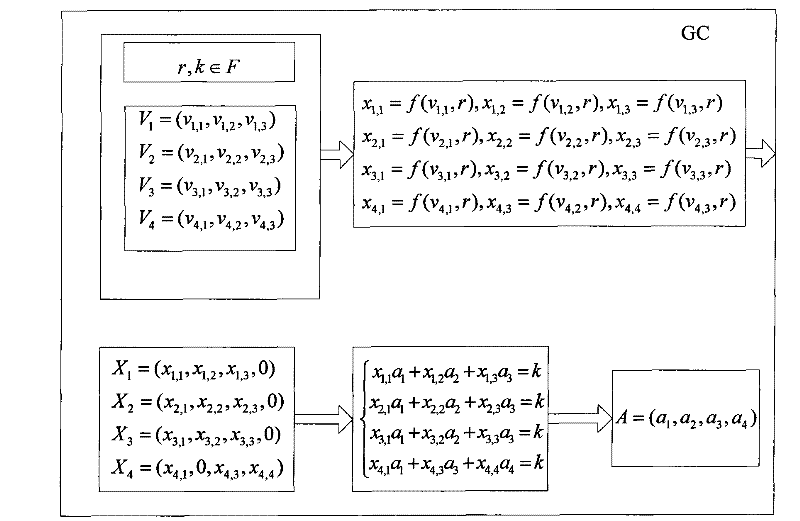Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
82results about How to "Reduce the likelihood of an attack" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
NFC (Near Field Communication) transmission method based on biometric feature recognition
InactiveCN104038256AImprove controllabilityReduce the likelihood of an attackNear-field transmissionCo-operative working arrangementsPaymentComputer hardware
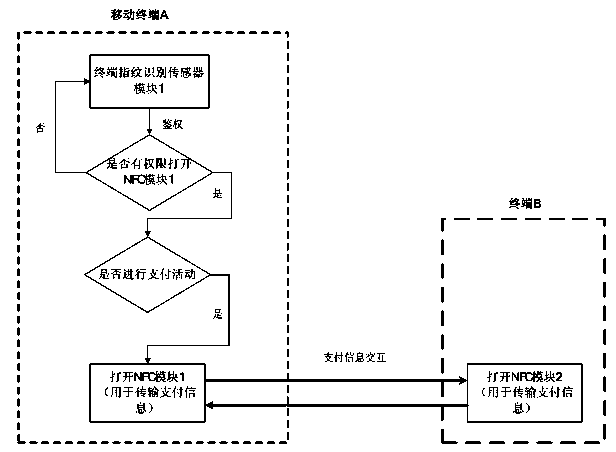
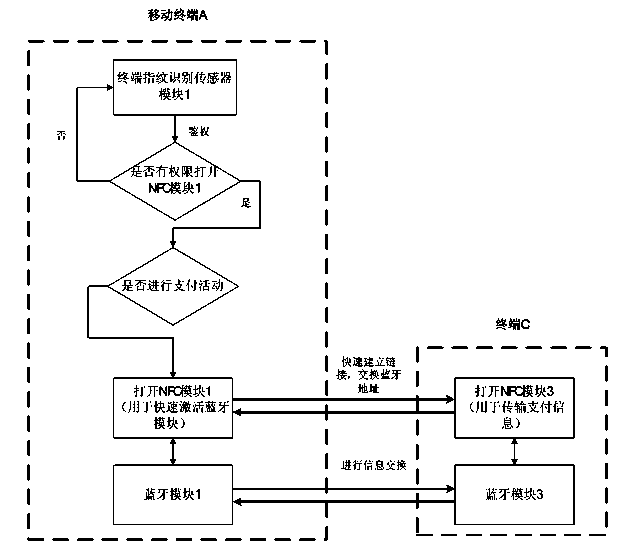
The invention relates to an NFC (Near Field Communication) transmission method based on biometric feature recognition. A fingerprint recognition sensor is integrated into a mobile terminal, and is functionally combined with an NFC module and a Bluetooth module. The method comprises the following steps: acquiring the fingerprint information of a user by using the fingerprint recognition sensor; deciding whether the NFC module is permitted to be started or not according to the authentication result of the fingerprint recognition sensor; if an NFC function is permitted to be started according to authentication, further judging a system task; if an NFC payment activity is performed, fully handing over a task for exchanging payment information to the NFC module for finishing by a system; if the system performs data exchange activities such as tag reading / writing, starting the NFC module, rapidly activating a Bluetooth module by using the NFC module, establishing a Bluetooth transmission link, and handing over a data transmission task to the Bluetooth module for processing. By adopting the NFC transmission method, the security of payment activities and data exchange is ensured, meanwhile links are established among terminals, and the data transmission speed is increased.
Owner:NANJING UNIV OF POSTS & TELECOMM
Method and system for connecting incoming call to Bluetooth headset
InactiveCN102752030AReduce the likelihood of an attackImprove securityNear-field transmissionUser inputBluetooth
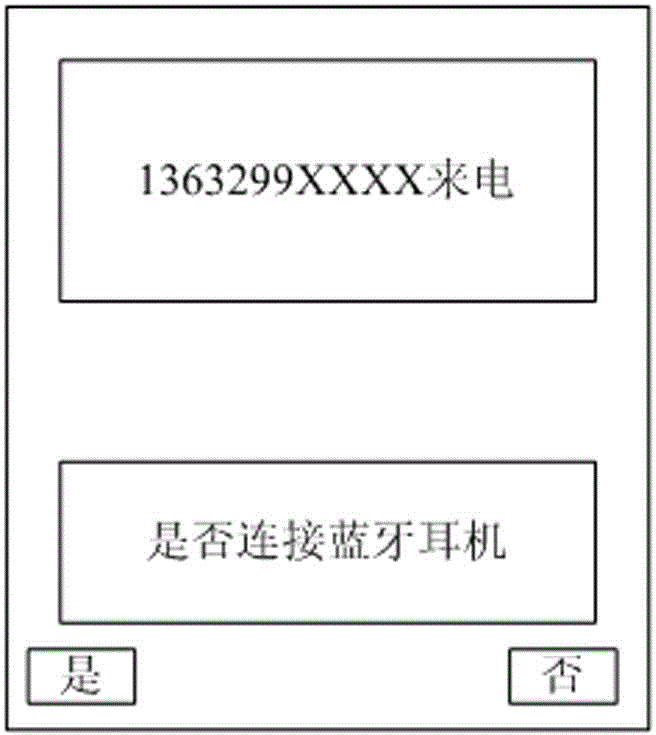
The invention provides a method for connecting an incoming call to a Bluetooth headset, which comprises the following steps: S1, when a calling request from a calling mobile phone is received, a prompt message of whether the Bluetooth headset needs to be connected is output; S2, a receiving user inputs the connection order of connecting to the Bluetooth headset according to the prompt message, and starts a Bluetooth module according to the connection order to search the matched Bluetooth headset and display a matching result; and S3, the target Bluetooth headset selected from the matching result by the user is acquired, communication connection between the incoming call and the target Bluetooth headset is established, and after the connection is succeeded, communication with the calling mobile phone is carried out through the target Bluetooth headset. The invention also provides a system for connecting the incoming call to the Bluetooth headset. According to the method for connecting the incoming call to the Bluetooth headset, a user does not need to hang up the incoming call when answering the incoming call and directly communicates with the calling mobile phone through the searched target Bluetooth headset, the user experience is greatly improved, and the operation is very convenient.
Owner:BYD CO LTD
Method for switching encryption safety data among peer-to-peer user nodes in P2P network
InactiveCN102111411AReduce the possibility of man-in-the-middle attacksReduce the likelihood of an attackPublic key for secure communicationUser identity/authority verificationPlaintextSecure communication
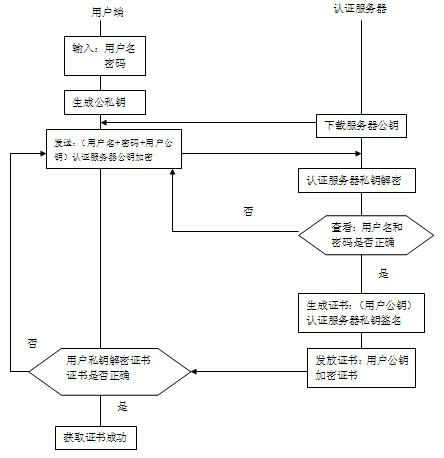
The invention provides a method for switching encryption safety data among peer-to-peer user nodes in a P2P (peer-to-peer) network. Two arbitrary peer-to-peer user nodes in the network, namely, a user node A and a user node B, log in the network to obtain a public key certificate through an authentication server; the user node A has a self-provided random number NA and a random number NB sent from the user node B; the user node B has a self-provided random number NB and a random number NA sent from the user node A; and the encryption algorithm is applied to enable the user node A and the user node B to form an encryption channel for data encryption transmission. In the invention, safety communication can be set simply, the interaction frequency is low, and except the first-time certificate transmitting of explicit message, other information interaction is achieved under the condition of encrypted message, so that a better security is ensured.
Owner:NANJING UNIV OF INFORMATION SCI & TECH
Method for improving safety of Web service
InactiveCN101640682AImprove securityReduce the possibility of leaksPublic key for secure communicationPlaintextWeb service
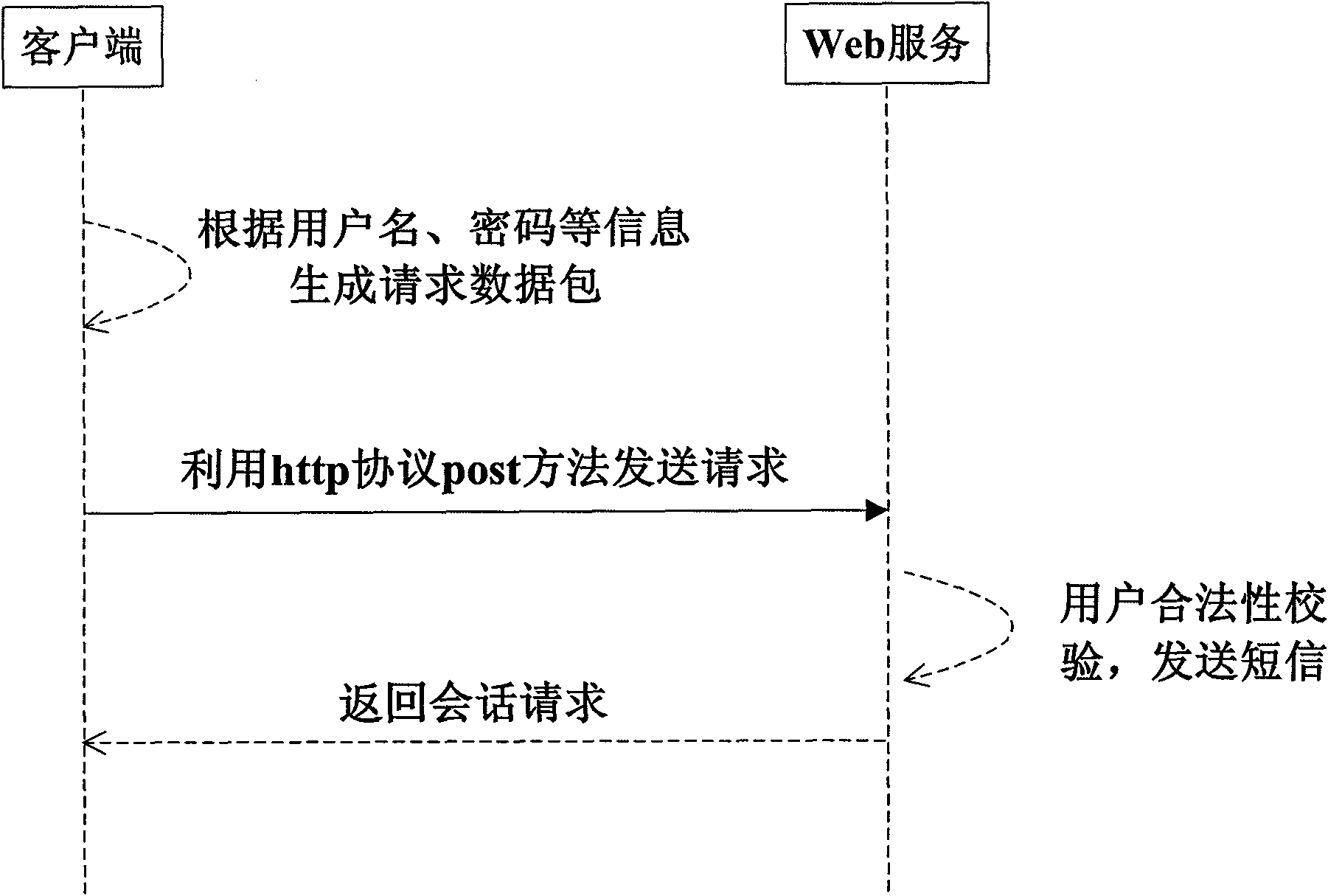
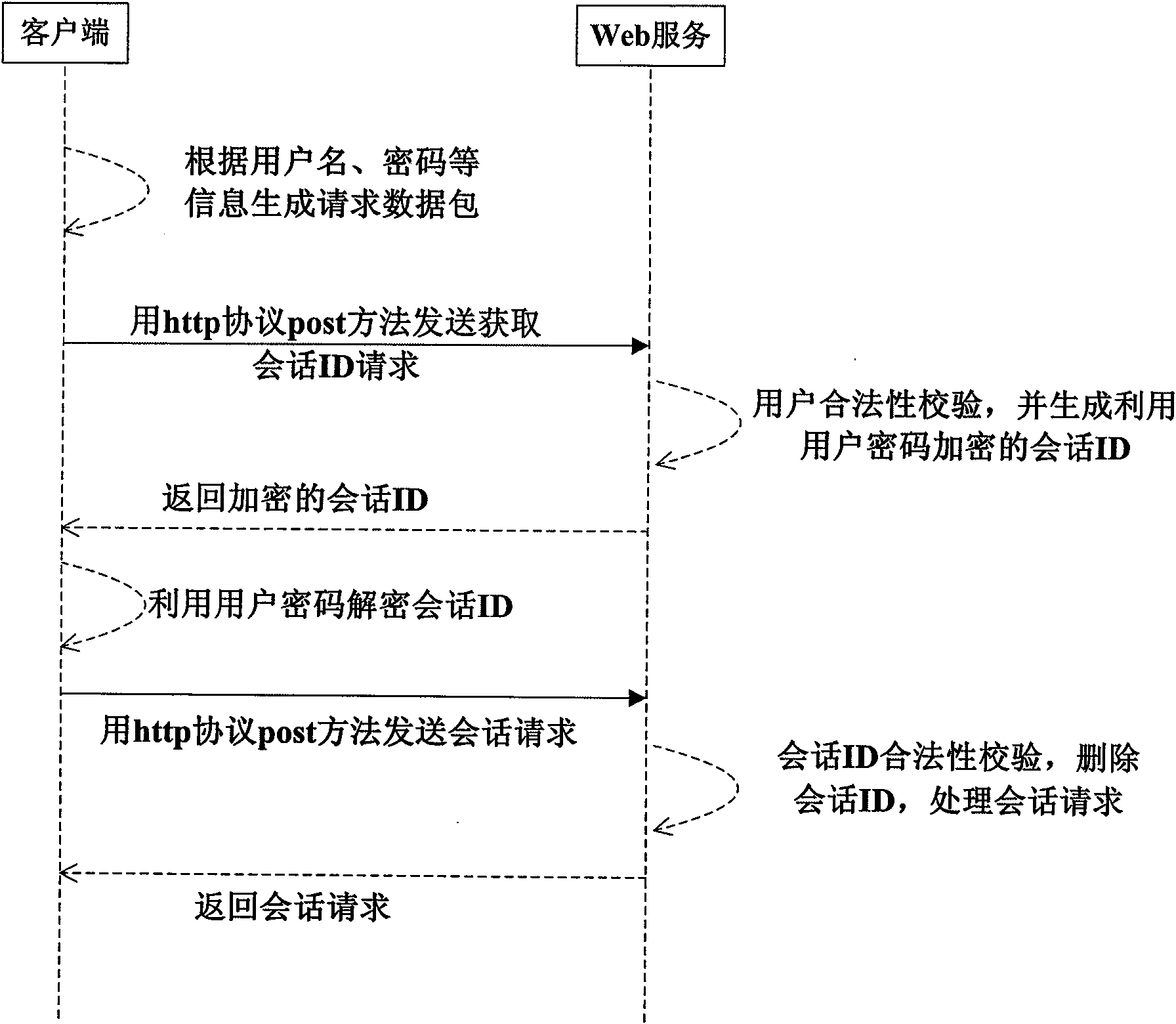
The invention discloses a method for improving the safety of Web service, which comprises the following steps: generating a request data packet comprising a first message digest generated by encrypting a user password by using a hash algorithm at a client side, and sending the data packet into a server side; using the hash algorithm to encrypt the stored user password by the service side, and generating a second message digest; comparing the first message digest with the second message digest by the server side, generating and storing a session identifier if the first message digest and the second message digest are same, using a symmetric encryption algorithm to encrypt the session identifier by taking the stored user password as a secret key, and sending the session identifier to the client side; using the symmetric encryption algorithm to decrypt the session identifier by taking the user password as the secret key by the client side to obtain a plaintext of the session identifier, and using the plaintext of the session identifier to send a session request to the server side; firstly judging whether the session identifier which is same as the session identifier in the session request exists or not in a memory by the service side, processing the session request and eliminating the session identifier if so, and returning a processing result.
Owner:深圳市励拓软件有限公司
Network reading system for resident identity card
InactiveCN1866824AReduced security requirementsLow running costUser identity/authority verificationResourcesComputer terminalElectronic information
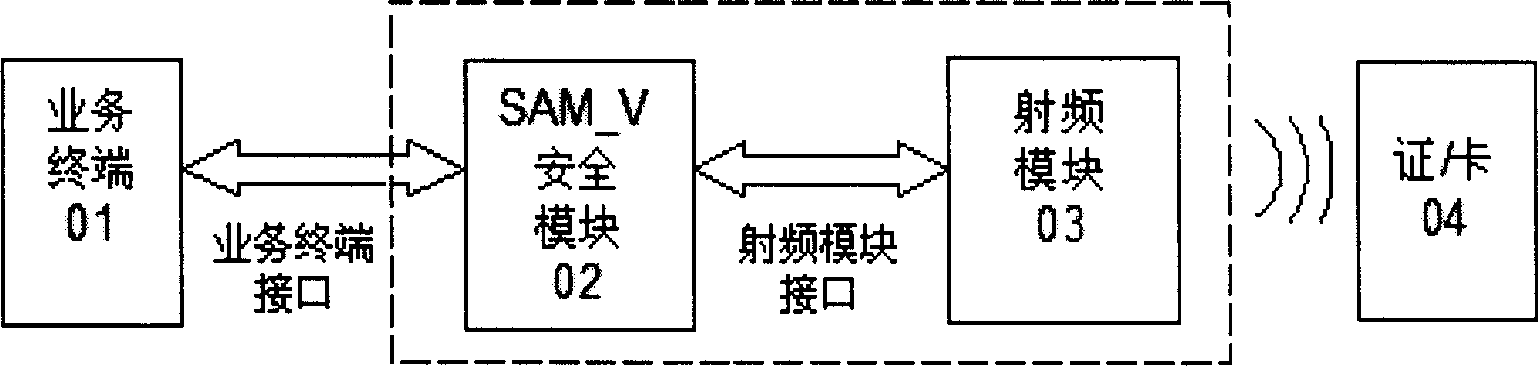
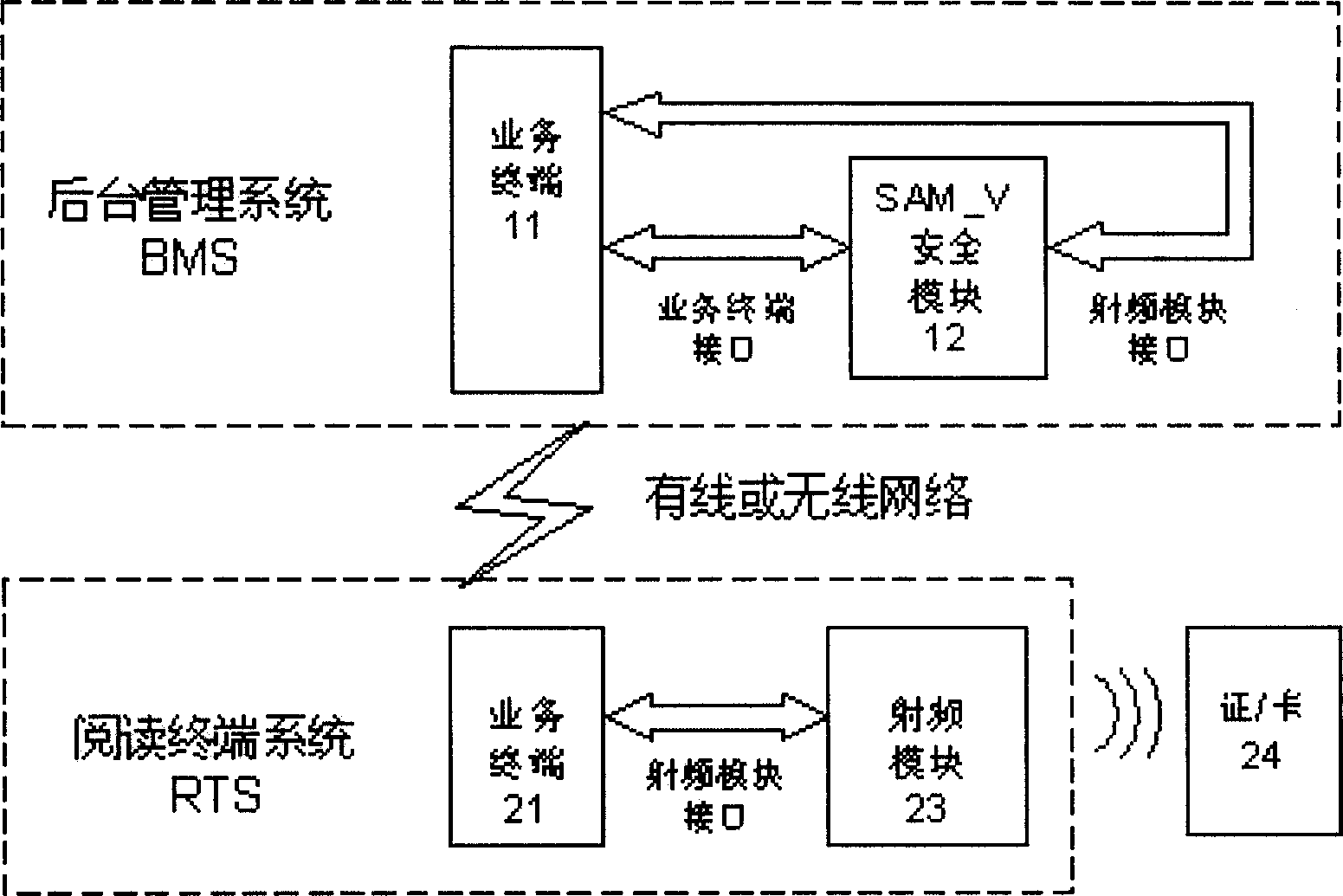
The invention discloses a resident identification card network reading system, which consists of background management system (BMS) and reading terminal system (RTS), wherein the BMS installs SAM_V safety modular for resident identification card electronic information operation processing or other hardware safety control equipment with the same code arithmetic function; the RTS installs radio frequency reading without SAM_V safety modular; the BMS and RTS communicate through private or common local (LAN) or wide area (WAN) network; the RTS sends the electronic information which is stored in the resident identification card chip to BMS to carry out code arithmetic function; after BMS code arithmetic function, the information is sent to RTS; TRS realizes reading, displaying, checking, storing and outputting resident identification card information.
Owner:王耀 +1
Safety detection method and device for Web application system
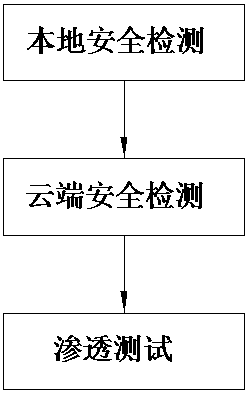
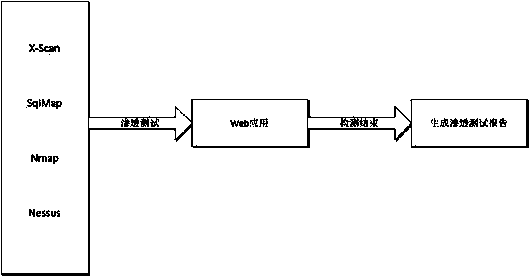
The invention discloses a safety detection method and device for a Web application system, aims at providing the safety detection method and device which can conduct dual detection including the local detection and the cloud end detection and are high in safety performance for the Web application system, and belongs to the technical field of network safety. Safety detection on the Web application system is achieved through the detection method including the steps of local safety detection, cloud end safety detection and permeation tests. The method and the system are used for safety detection of the Web application system.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
DHCP (Dynamic Host Configuration Protocol) anti-attacking method and device
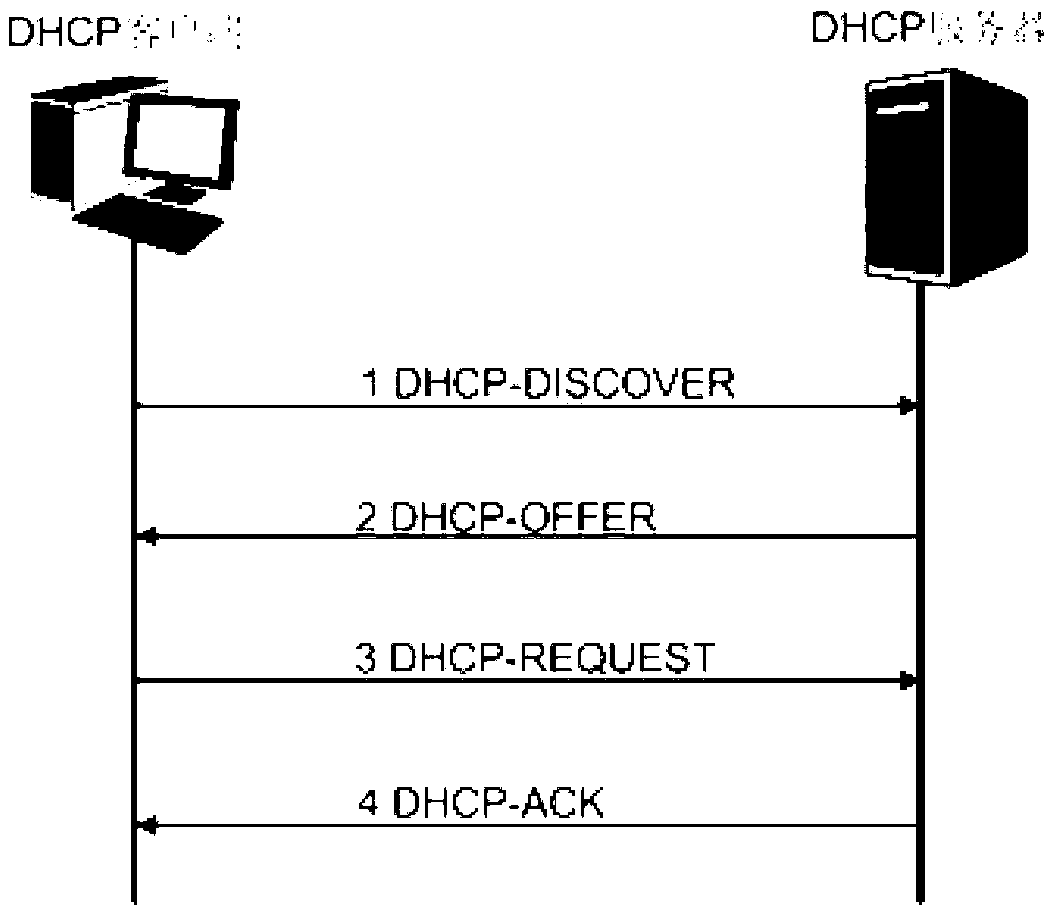
The invention provides a DHCP (Dynamic Host Configuration Protocol) anti-attacking method which is applied to being used as network equipment of a DHCP client. The method comprises the following steps of: A, storing a DHCP Offer message received by the DHCP client and / or information carried by a DHCP ACK (Acknowledgement Character) message, wherein the information at least comprises a source IP (Internet Protocol) address of the message and a server identification; and B, comparing whether the source IP address of the same message is the same as the server identification or not; if not, determining that the message is sent by an attacker. The DHCP anti-attacking method disclosed by the invention can be used for sufficiently utilizing the characteristics of a DHCP interaction process to prevent DHCP attacks and greatly reducing the possibility that the DHCP client is attacked by various means.
Owner:HANGZHOU DPTECH TECH
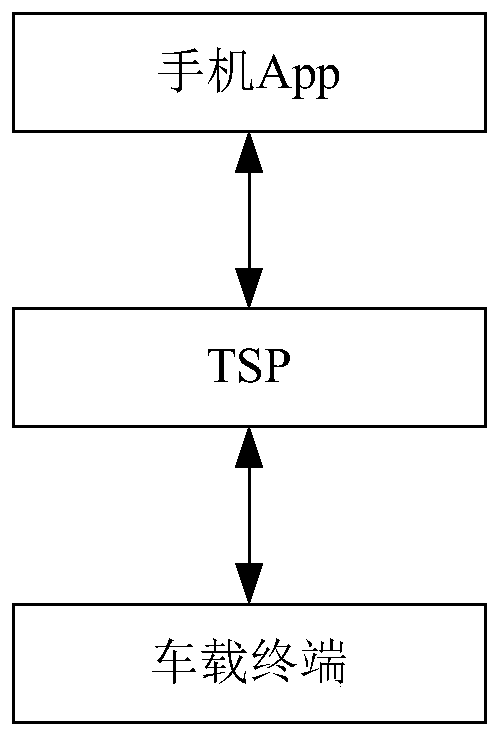
Vehicle unlocking method based on Bluetooth communication protocol
InactiveCN109720297AImprove securityImprove reliabilityAnti-theft devicesComputer terminalProtocol for Carrying Authentication for Network Access
The invention discloses a method for unlocking and locking a vehicle door on the basis of a Bluetooth communication protocol and belongs to the technical field of shared automobiles. Use scenes of a rent car and a private car are both taken into consideration so that the vehicle management safety is also taken into consideration while convenience is brought to a driver / borrower. The method for unlocking and locking the vehicle door on the basis of the Bluetooth communication protocol comprises the steps of S1, establishing binding of a vehicle-mounted terminal, a vehicle and a Phone APP; S2, logging in the Phone APP to transmit a car booking request, and enabling a TSP to receive reserve information to generate a digital key and transmit the digital key to the Phone APP and the vehicle-mounted terminal; S3, finding a car, performing communication connection through a Bluetooth, executing an unlocking instruction, unlocking the vehicle door after authentication, and otherwise, failing to unlock the vehicle door; and S4, performing secondary authentication through a PIN code; after successful authentication, activating a vehicle physical key and starting a vehicle; and otherwise, enabling the vehicle to be unable to start.
Owner:恒大新能源汽车(天津)有限公司
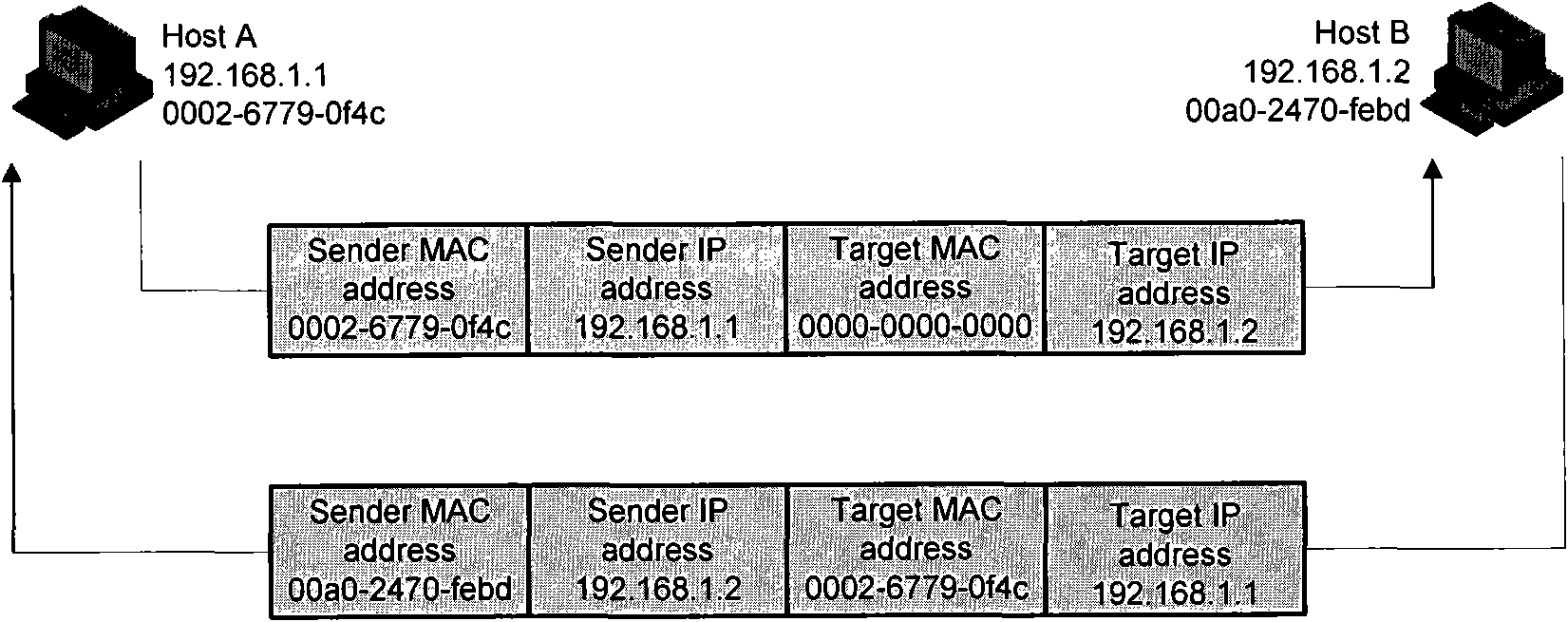
Method and device for detecting ARP message validity
InactiveCN101610266AReduce the likelihood of an attackData switching networksLayer interfaceIp address
The invention discloses a method and a device for detecting ARP message validity, which is applied in a system including a gateway device. The method comprises the following steps: the gateway device receives the ARP message and judges whether an inlet interface of the ARP message is a three-layer interface or not; if so, then the gateway device extracts a transmitting terminal internet protocol IP address in the ARP message and implements route searching by taking the transmitting terminal IP address in the ARP message as a target address to obtain the information of a corresponding outlet interface; when the obtained information of the outlet interface is consistent with the information of the inlet interface of the received ARP message, the ARP message is a valid ARP message; when the obtained information of the outlet interface is inconsistent with the received information of the inlet interface of the ARP message, the ARP message is an attack message. The method and the device for detecting ARP message validity realize the detection on invalid ARP messages.
Owner:NEW H3C TECH CO LTD
A method for preventing short-term bifurcation and double-spend attack on a block chain network
ActiveCN109033832AMinor changesEasy to implementPublic key for secure communicationPayment protocolsChain networkBlockchain
The invention discloses a method for preventing short-term bifurcation and double-spend attack on a block chain network. The method comprises the following steps: adding a CA certificate issuing and updating center to the block chain network; transforming the block data structure, adding signature and public key fields based on CA certificate; adding certificate validity verification of signatureand public key to the consensus algorithm of block chain network nodes; improving consensus algorithm; in the improved consensus algorithm, adding short bifurcation malicious double-spend attack riskidentification. The method has small modification to the original chain, is easy to realize, only increases the CA center and modifies and adds the necessary consensus algorithm, can effectively reduce the possibility of short-term bifurcation double-spend attack, and provides effective real-name system evidence for the judicial investigation after the event through the real-name system CA certificate.
Owner:WEALEDGER NETWORK TECH CO LTD
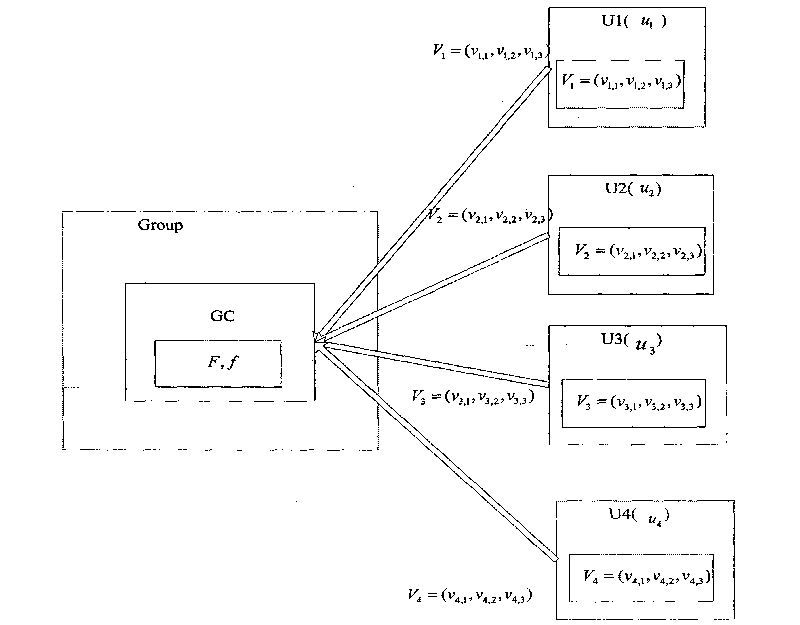
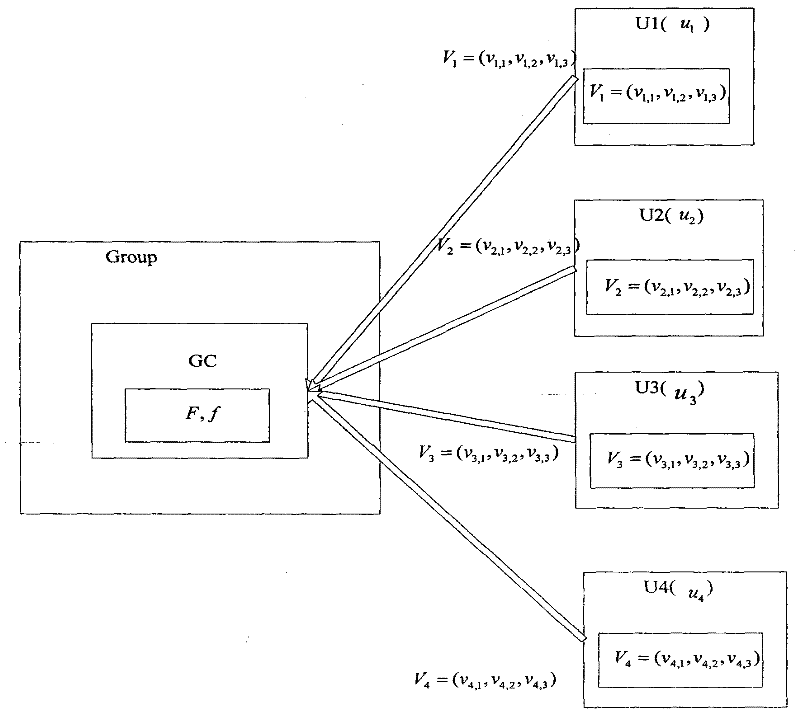
Graded group key management method based on line geometry
InactiveCN101848082AAvoid security impactReduce the likelihood of an attackKey distribution for secure communicationGroup controllerPrivate network
The present invention discloses a graded group key management method based on line geometry, which comprises the following steps: step 1. a central controller selects a finite field F, a mapping F and a constant for the use of groups and a N-dimension private vector for each sub-group; step 2. the central controller selects a mapping parameter r and maps the private vectors into a group of new vectors in a vector space; step 3. the central controller selects a sub-group key for each sub-group, constructs n linear equations and solves the linear equations, wherein the solutions of the linear equations are public vectors and n groups of public vectors form a public matrix; and the central controller further sends the public matrix and the mapping parameter r to all sub-group controllers via a public channel broadcast or multicast; and step 4. the sub-group controllers calculate confidential vector thereof and carry out a linear conversion on the confidential vector and the public matrix to obtain a group of key vectors. The graded group key management method is simple and flexible and is capable of avoiding violent attacks.
Owner:SOUTH CHINA UNIV OF TECH
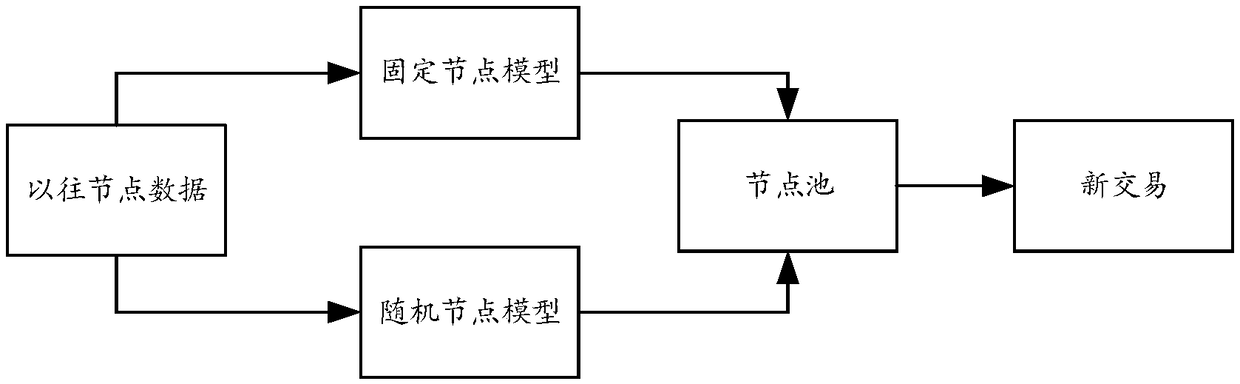
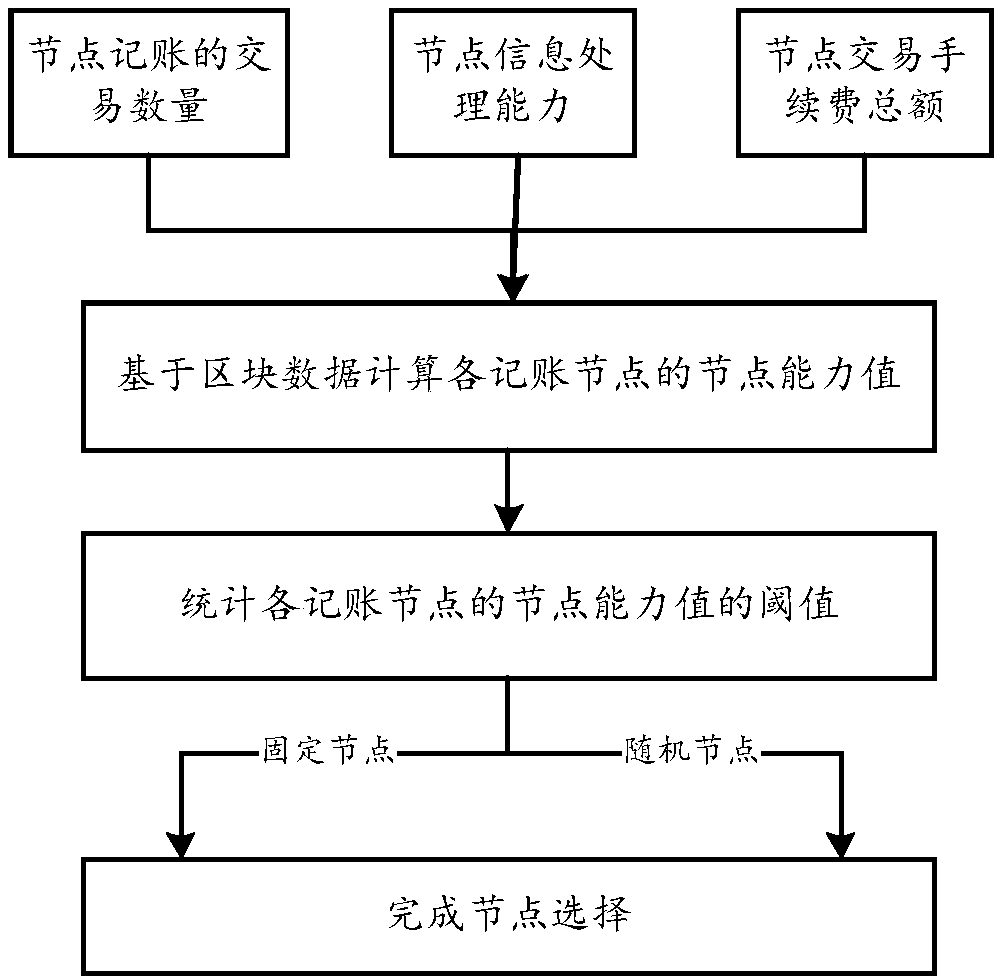
Intelligent selecting method of account keeping nodes
InactiveCN108665274AImprove securityReduce consumptionCryptography processingDigital data protectionCapacity valueRandom assignment
The invention discloses an intelligent selecting method of account keeping nodes, and relates to the field of block chains, virtual currency and artificial intelligence. The method comprises the stepsthat step one, node capacity value of each account keeping node is calculated based on block data; step two, threshold values of the node capacity value of each node are counted; step three, part ofaccount keeping nodes are selected randomly after a current account keeping node is determined according to the threshold values to complete node selection. The method aims at solving the problems ofaccount conflict, low account keeping efficiency and energy wasting caused by mining computing conducted by a large number of miners, and preventing the problems of unequal and non-decentralization caused by selecting account keeping nodes by adopting man-made voting; intelligent account keep right or mining right distribution mechanism are adopted based on block data and each dimensional data ofthe miners, hacker attack is prevented by adopting the account keeping right or mining right random distribution, and the problems of energy wasting and low account keeping efficiency caused by miningconflict are solved under the premises of equality, decentralization and safety of the block chains.
Owner:BEIJING EASY AI TECHNOLOGY CO LTD
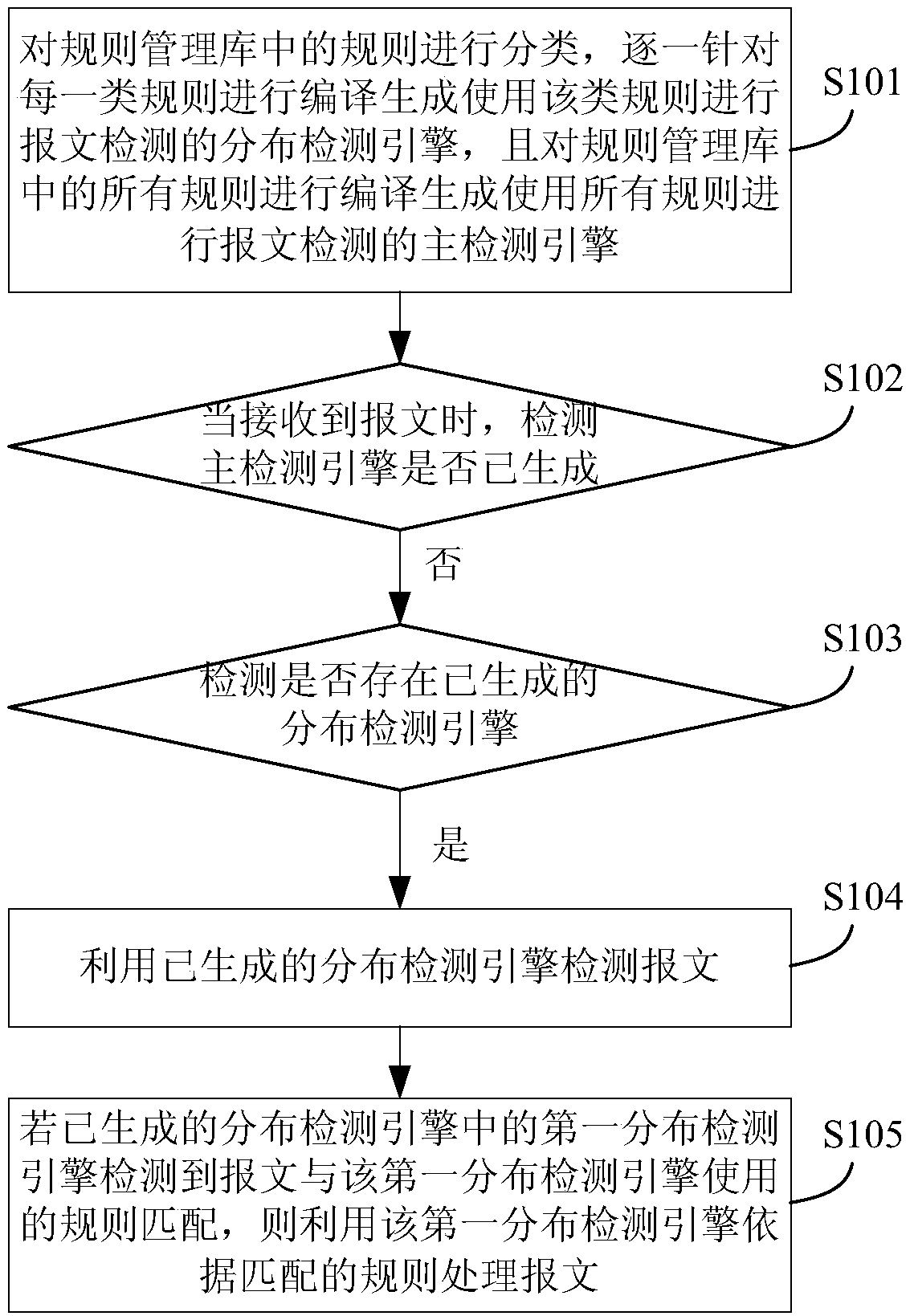
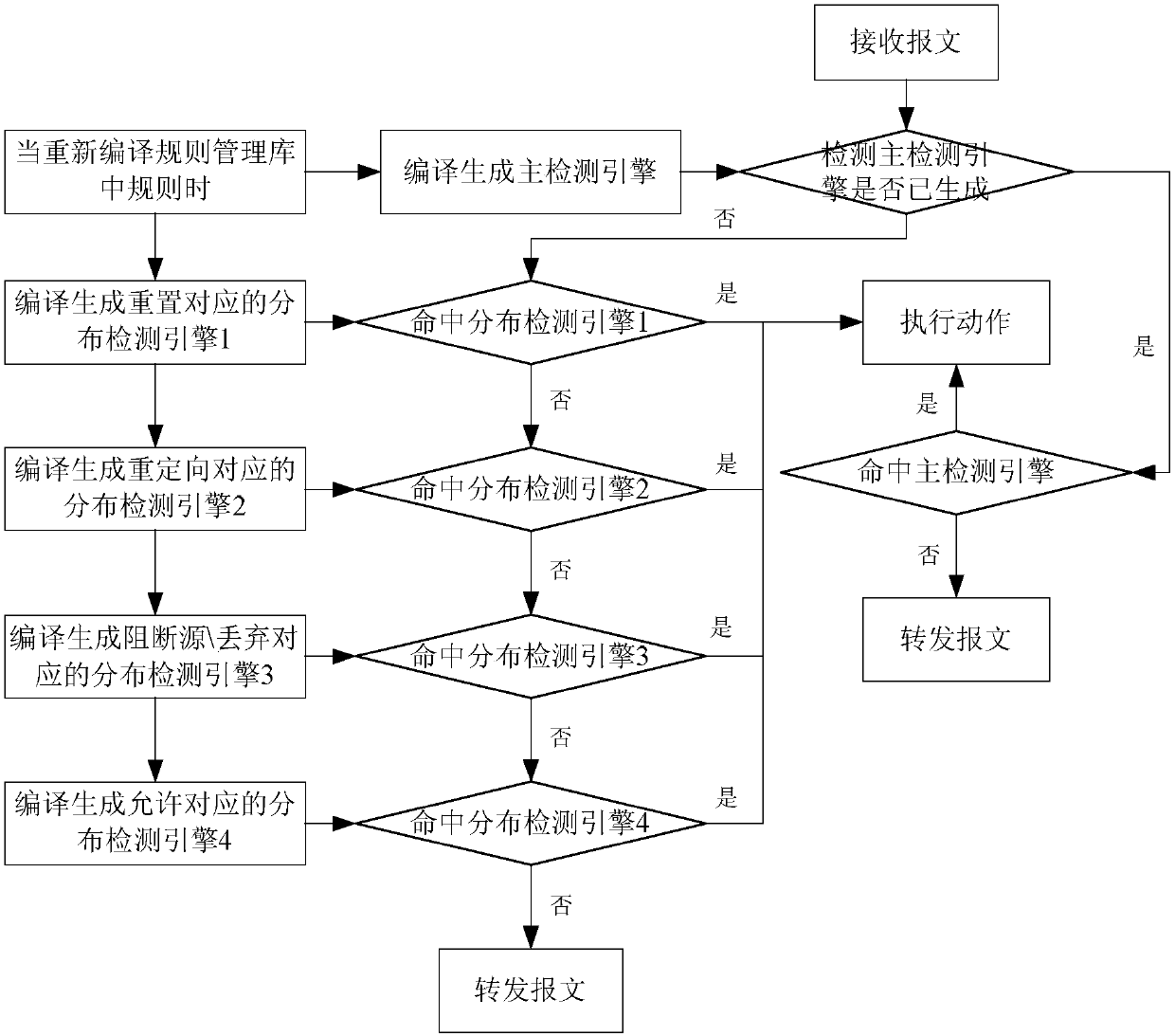
Message detection method and device
ActiveCN107645502AReduce downtimeReduce the likelihood of an attackTransmissionMatch ruleDistributed computing
The embodiment of the invention provides a message detection method and device, and is applied to security equipment. The method comprises the steps that the rules in a rule management library are classified, each type of rules are compiled one by one so as to generate distributed detection engines performing message detection by using the type of rules, and all the rules in the rule management library are compiled so as to generate a master detection engine performing message detection by using all the rules; when a message is received, whether the master detection engine is generated is detected; if the master detection engine is not generated, existence of the generated distributed detection engines is detected; if the generated distributed detection engines exist, the generated distributed detection engines are utilized to detect the message; and if the first distributed detection engine of the generated distributed detection engines detects that the message is matched with the rule used by the first distributed detection engine, the message is processed by using the first distributed detection engine according to the matched rule. With application of the message detection method and device, the possibility of attack to the network protected by the security equipment can be reduced.
Owner:NEW H3C SECURITY TECH CO LTD
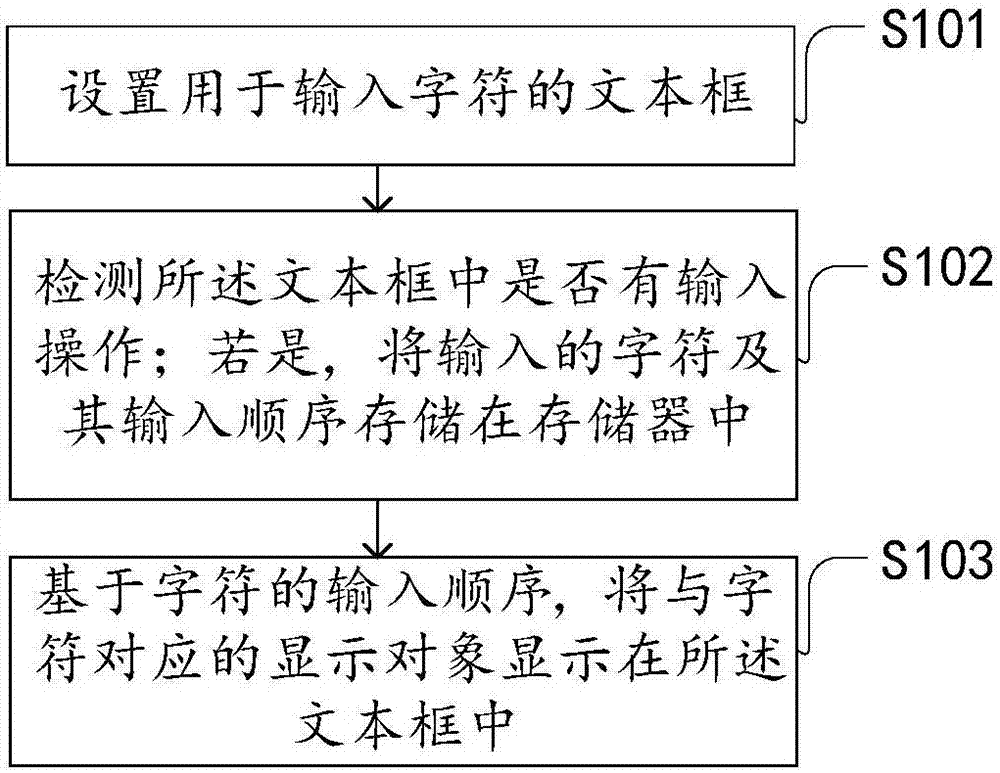
Input method, input device and electronic device
InactiveCN107292205AEnsure safetyEasy to rememberInternal/peripheral component protectionDigital data authenticationProgramming languageObject based
The invention provides an input method, an input device and an electronic device. Corresponding setting for a textbox and characters input to the textbox is carried out to enable a common textbox to have the characteristic of a password box. Therefore, when the input method is adopted, the input is the input supporting a multi-language character password; furthermore, a preset password display object rather than the input characters is displayed to guarantee the security of the input password. A user can set familiar languages or characters as the password, for example, the user can set Chinese characters as the password. Therefore, according to the method, as the input is the input supporting the multi-language character password, convenience is brought to memorization by using a local language character password, and the possibility of being attacked by a hacker is reduced indirectly. In addition, the method also can set the pattern of a password display object based on a need to form different password covering characters, so that the covering characters can fully guarantee the security of password input.
Owner:CAINIAO SMART LOGISTICS HLDG LTD
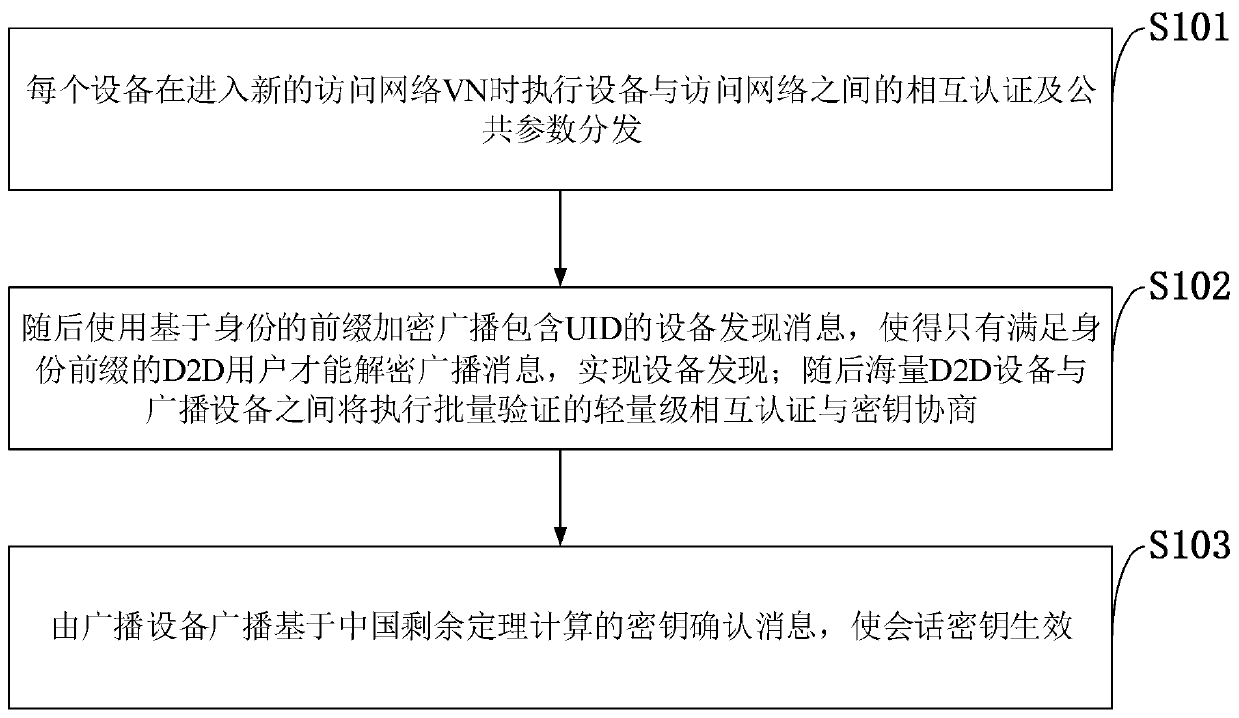
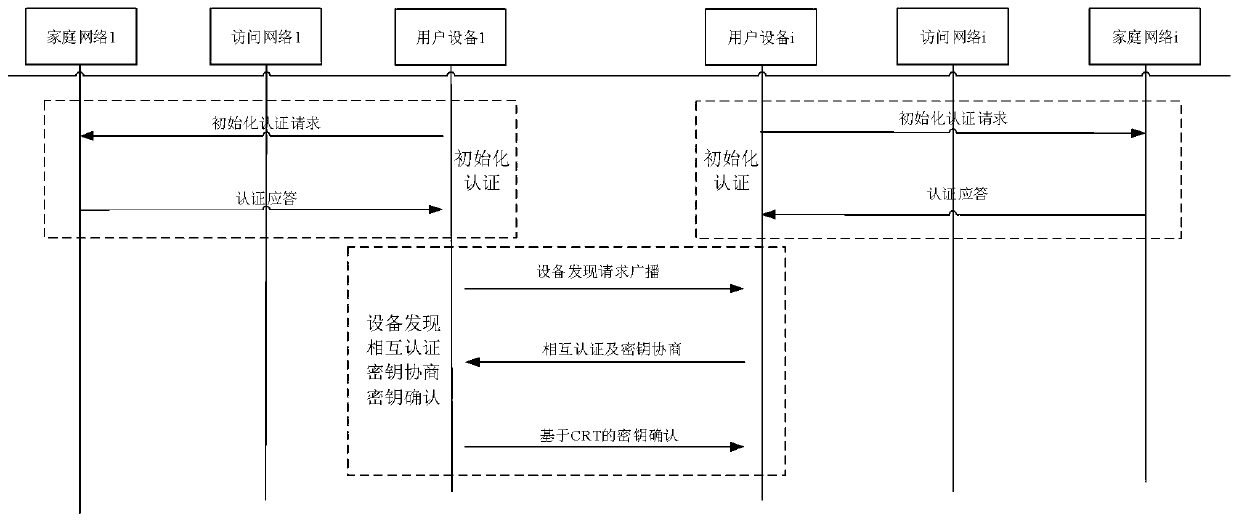
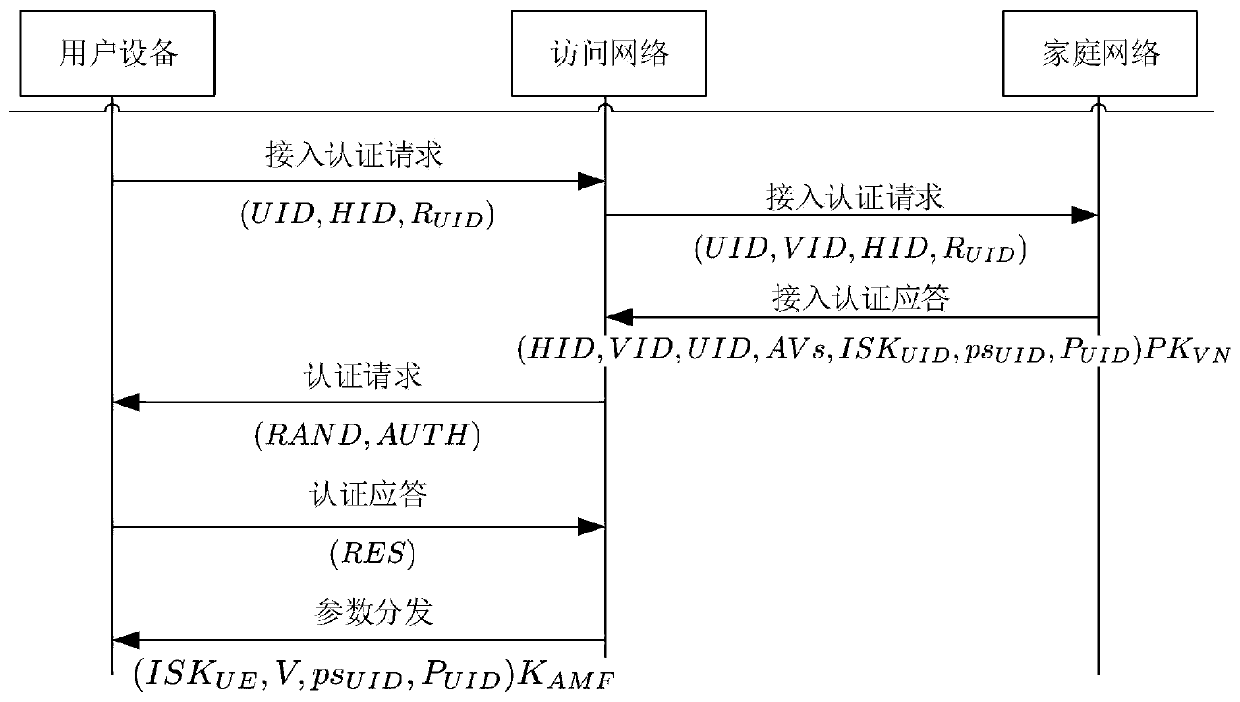
Mass D2D anonymous discovery authentication and key negotiation method
ActiveCN109768861AReduce communication overheadReduce computational overheadKey distribution for secure communicationSecurity arrangementCRTSIdentity privacy
The invention belongs to the technical field of communication network security, and discloses a mass D2D anonymous discovery authentication and key negotiation method. The method includes an initialization authentication stage; an anonymous device discovery stage based on prefix encryption; a mutual authentication and key negotiation stage based on batch verification; and a key confirmation stage.According to the scheme design carried out according to the 3GPP standard, communication equipment in the standard does not need to be changed, and the method can be applied to networks of all LTE-A / 5G mobile scenes; the general structure of the equipment discovery and authentication mechanism provided by the invention can realize discovery, mutual authentication, key negotiation and identity privacy protection of adjacent equipment; according to the rapid key confirmation method based on the CRT mechanism provided by the invention, the signaling number is effectively reduced; the signaling overhead, the communication overhead and the transmission overhead are reduced; direct mutual authentication between a large number of D2D devices can be directly realized, and all known attacks at present can be resisted.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
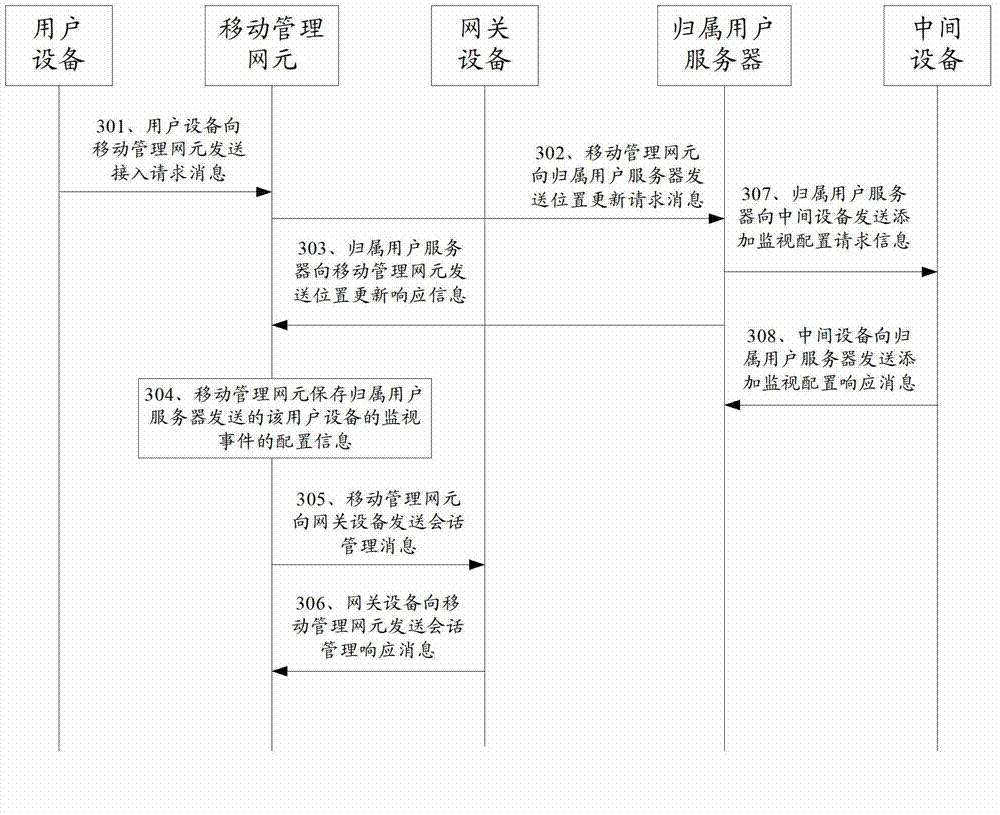
User-equipment information monitoring method, device and system
ActiveCN103716833AReduce the likelihood of an attackImprove network securityWireless communicationInformation monitoringUser equipment
The embodiment of the invention discloses a user-equipment (UE) information monitoring method, device and system, wherein the method includes: the monitoring device generates a monitoring event report of the UE when detecting a monitoring event of the UE which needs to be monitored; according to an internal identification of the UE, an intermediate device which forwards the monitoring event report of the UE is determined; and the internal identification of the UE and the monitoring event report of the UE are sent to the intermediate device so that the intermediate device acquires an external identification of the UE and the address of a corresponding monitoring server according to the internal identification of the UE and sends the external identification of the UE and the monitoring event report of the UE to the monitoring server according to the acquired address of the monitoring server. The UE information monitoring method, device and system are capable of improving monitoring-event report sending accuracy of the UE.
Owner:HUAWEI TECH CO LTD
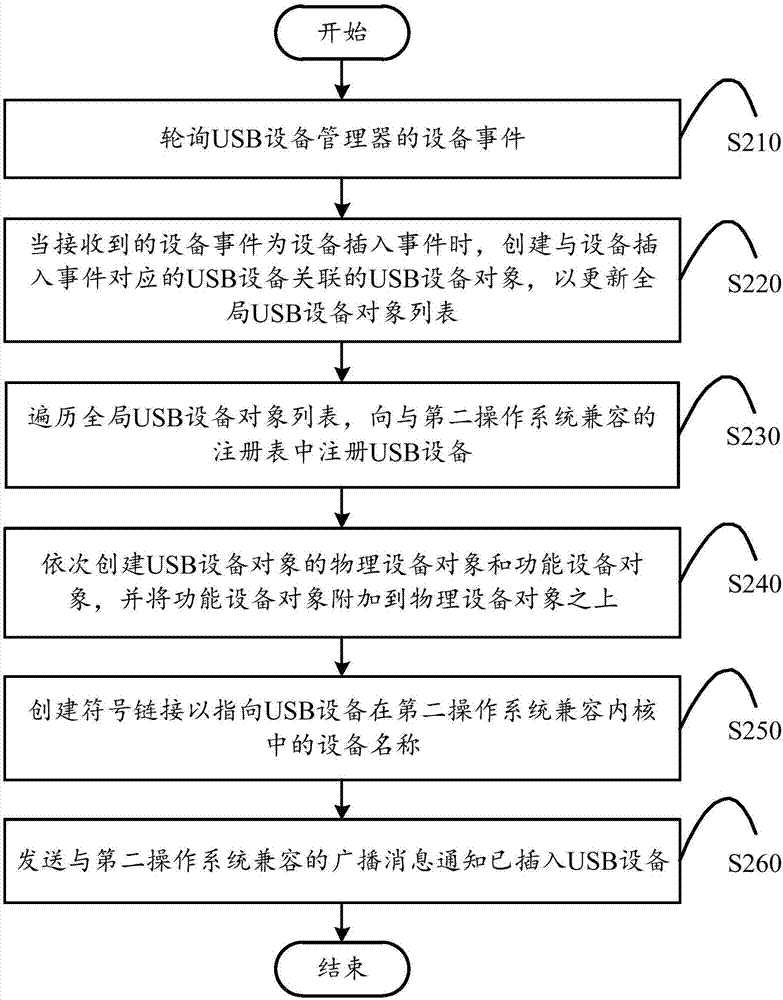
USB equipment control method and device and computing equipment
ActiveCN107329916AEasy to controlImprove compatibilityDigital data authenticationProtocol authorisationOperational systemComputer module
The invention discloses a USB equipment control method and device and computing equipment. A first operating system runs on the computing equipment, and a conversion module using the USB equipment control method is arranged on the computing equipment, so that a USB application designed for a second operating system can run in the first operating system. The method comprises the steps that equipment events of a USB equipment manager are polled; when an equipment insertion event is received, a USB equipment object associated with USB equipment corresponding to the event is created, and a global USB equipment object list is updated; the list is traversed, and the USB equipment is registered in a registry compatible with the second operating system; a physical equipment object and a functional equipment object of the USB equipment object are sequentially created, and the functional equipment object is attached to the physical equipment object; a symbol link is created to point to an equipment name of the USB equipment in a compatible kernel of the second operating system; a broadcast message compatible with the second operating system is sent to notify the inserted USB equipment.
Owner:北京统信软件技术有限公司
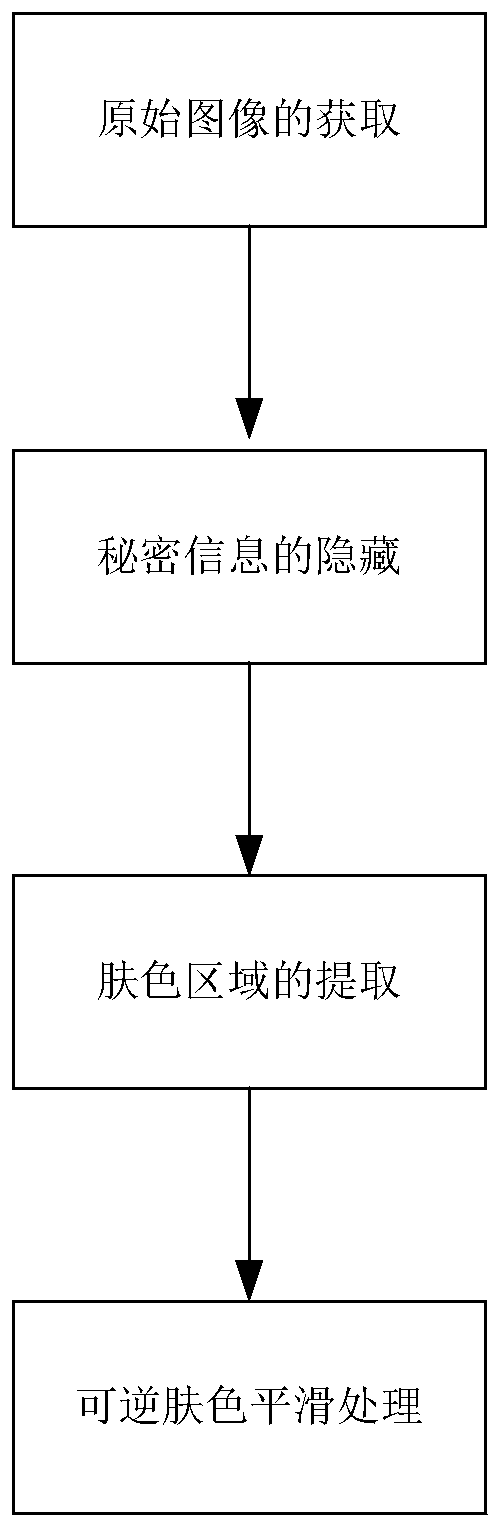
Reversible skin color smoothing method with a reversible information hiding function and an original image recovery method thereof
ActiveCN109840895ARestore losslessLess attentionImage enhancementDigital data protectionPattern recognitionState of art
The invention relates to a reversible skin color smoothing method with a reversible information hiding function and an original image recovery method thereof. Compared with the prior art, the reversible skin color smoothing method solves the defects that hidden information is easy to find and skin color smoothing processing is irreversible. The method comprises the following steps: obtaining an original image; hiding the secret information; extracting a skin color region; performing reversible skin color smoothing. According to the invention, a behavior hiding effect of skin color smoothness is realized; Namely, the original content is hidden by the face beautification image with the high visual quality characteristic, and the hidden information and the skin color are smooth and reversible, so that the attention and doubt of an attacker on the secret-carrying image are reduced, the possibility that the secret-carrying image is attacked is reduced, and the security of the image is further improved.
Owner:ANHUI UNIVERSITY
Payment method and system for mobile terminal
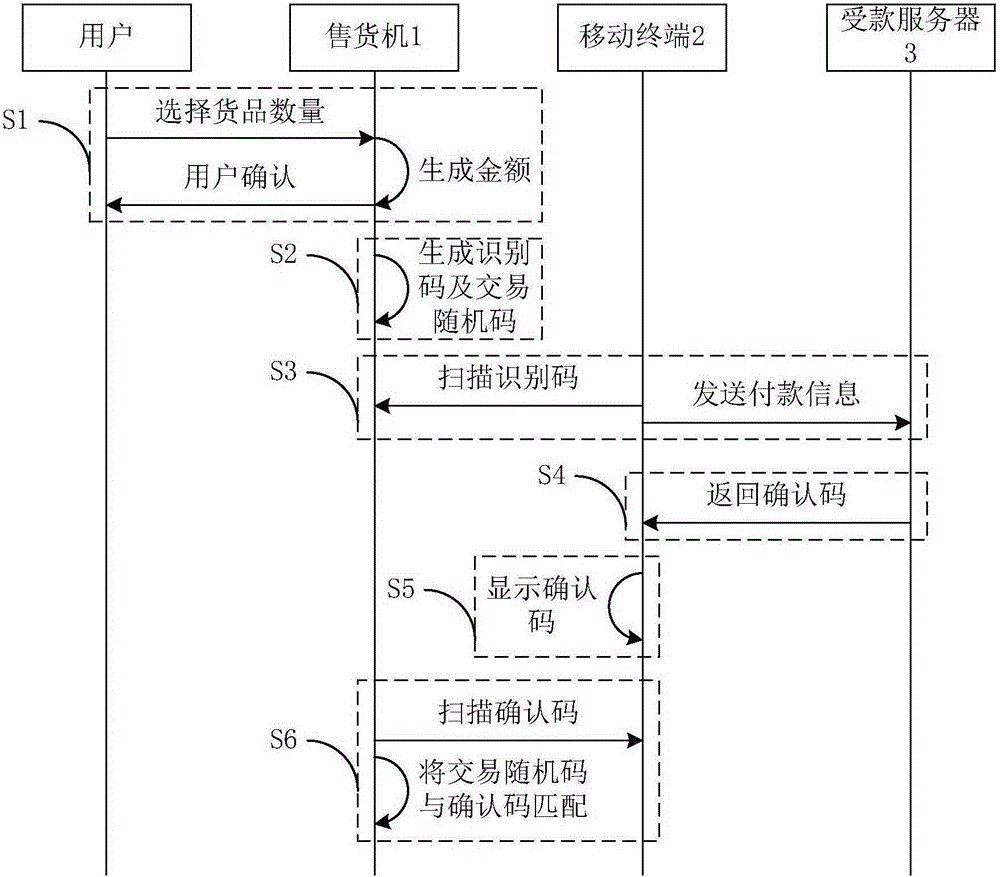
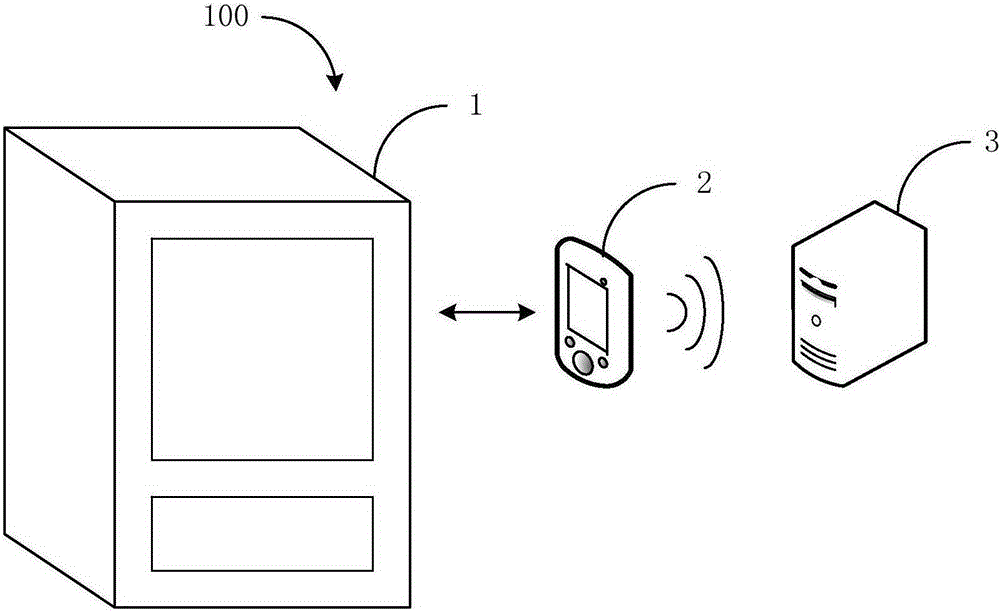
InactiveCN105184560AImprove experienceSave Internet costsCoin-freed apparatus detailsPayment architecturePaymentComputer terminal
The invention discloses a payment method and system for a mobile terminal, and the method comprises the steps: selecting the number of articles in a vending machine, and generating the amount of money through the vending machine according to the number of articles; generating an identification code comprising the information of money, and a transaction random code through the vending machine; enabling the mobile terminal to scan the identification code, so as to transmit payment information to a money-receiving server; returning a confirmation code to the mobile terminal after the money-receiving server receives the payment information; and enabling the mobile terminal to receive the confirmation code and display the conformation code. The vending machine scans the displayed confirmation code, and enables the transaction random code to be matched with the confirmation code. If the matching is successful, the article is sold. The beneficial effects of the invention are that the vending machine does not need to be connected with an Ethernet, thereby saving the networking cost, reducing the possibility of being attacked by network hackers, and improving the safety and reliability; the method and system achieves payment through a wireless network of the mobile terminal, thereby effectively saving the payment cost of the vending machine and management and maintenance cost of the vending machine, facilitating the payment, and optimizing the user experience.
Owner:SHANXI LANGZHONG INFORMATION TECH CO LTD
Classified net-cage fish cultivating method
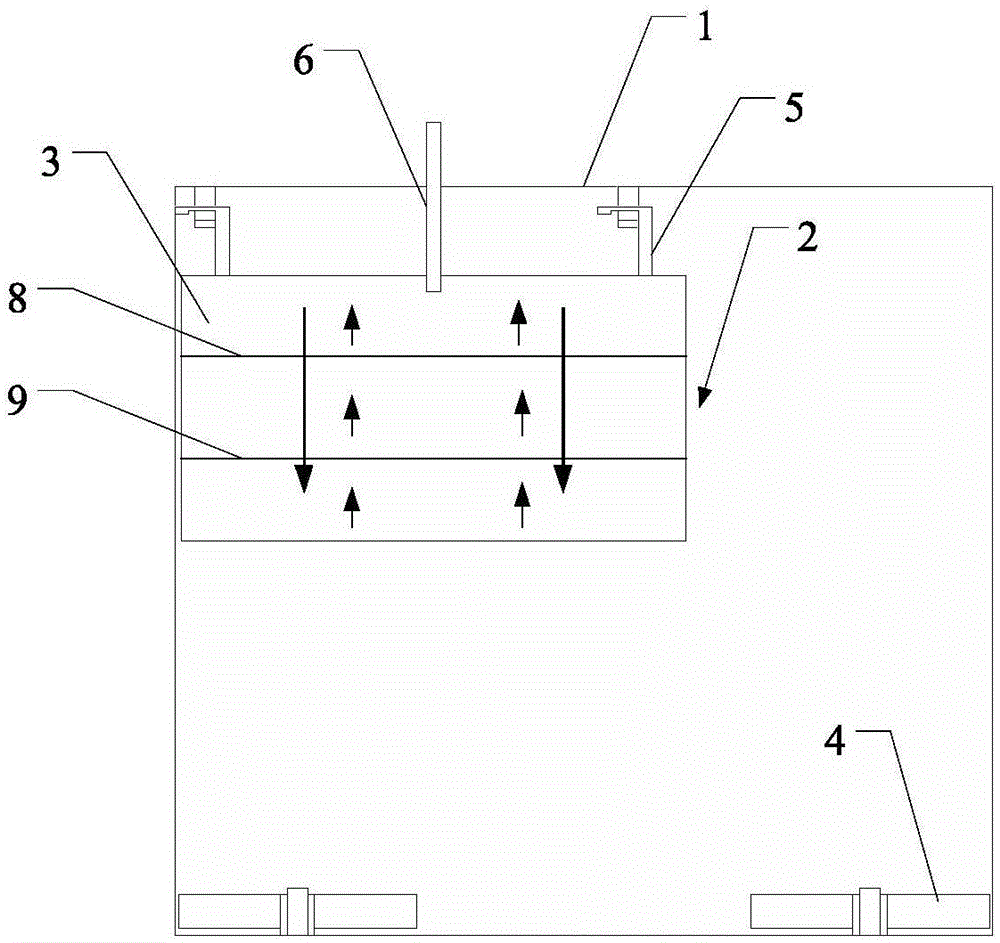
ActiveCN105028268AReduce the likelihood of an attackReduce exposureClimate change adaptationPisciculture and aquariaChest circumferenceBody type
The invention discloses a classified net-cage fish cultivating method. The method comprises the following steps: 1, providing an inner net cage and an outer net cage, wherein the inner net cage is positioned at one corner of the outer net cage, the mesh diameters of a top wall and a bottom wall of the inner net cage are 3 to 7cm, four side walls are watertight, the inner net cage is partitioned into three layers of box bodies through two interlayer plates, the mesh diameter of the first interlayer plate from top to bottom is 0.2 to 0.3cm, and the mesh diameter of the second interlayer plate is 1 to 2cm; 2, stocking fish fries in the outer net cage; 3, when the chest circumference of each fish fry does not reach the mesh diameter of the inner net cage, adding fish feeds into the inner net cage, when the chest circumference of a certain fish fry exceeds the mesh diameter of the inner net cage, adding the feeds into the outer net cage for 20 to 30min firstly, then adding the feeds into the inner net cage for 2 to 3min, and pumping water by using a water pump every day, so that water flow which flows from top to bottom is formed in the inner net cage. According to the classified net-cage fish cultivating method, fishes of different body types can be effectively separated, and the possibility that smaller fishes are attacked is reduced.
Owner:谢元莲
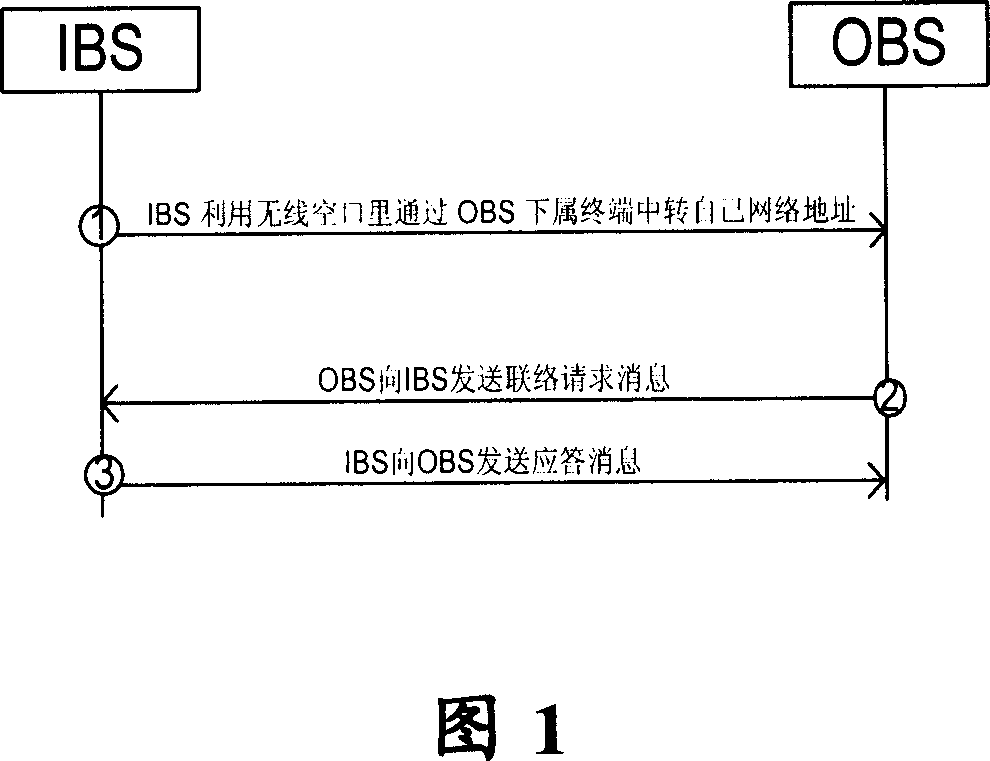
Safety telecommunication method
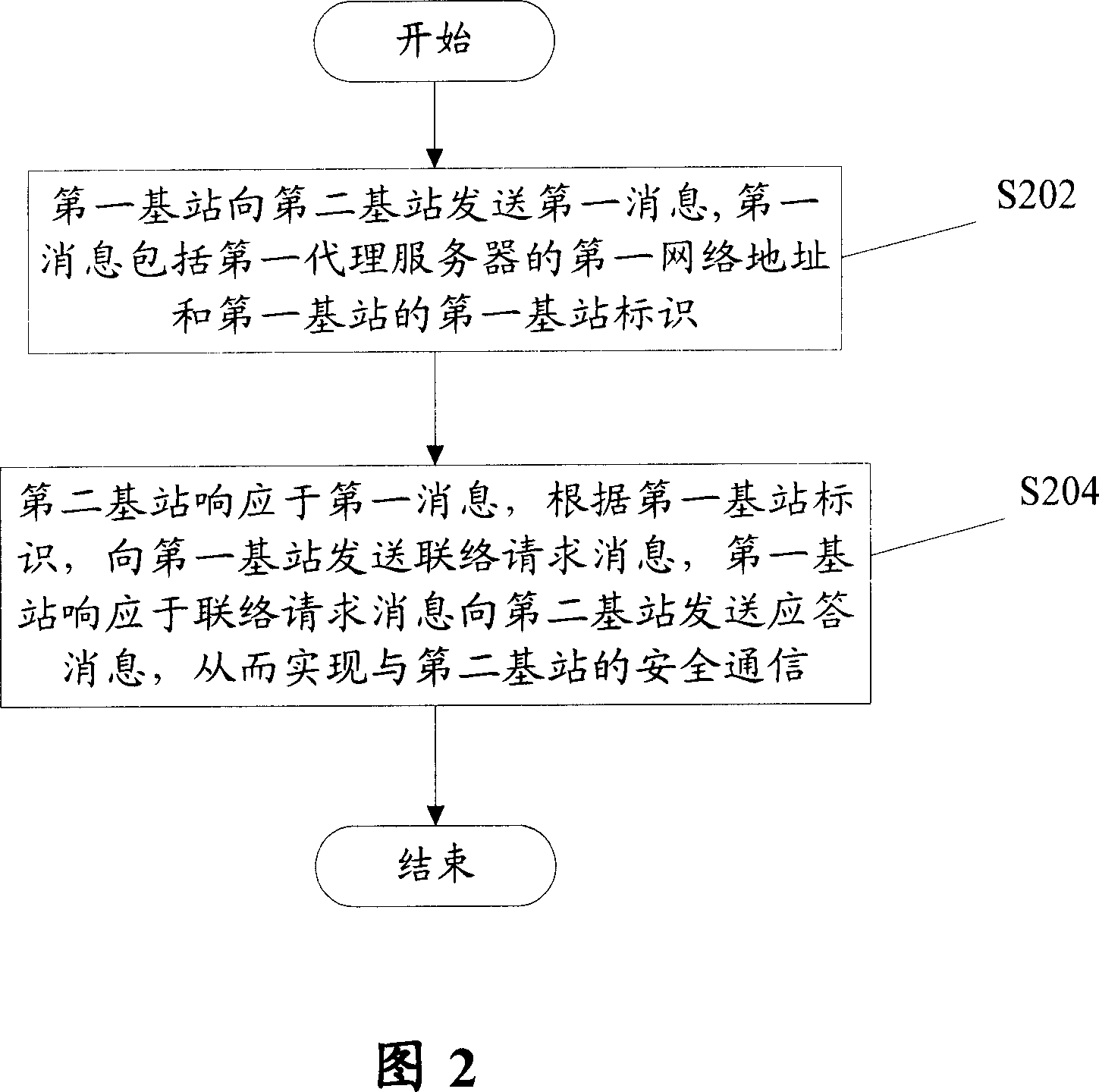
InactiveCN101031141ASimple functionLow costWireless network protocolsRadio/inductive link selection arrangementsSecure communicationNetwork address
The method is used for realizing a security communication between the first base station and second base station. The first base station comprises: at least one first proxy server. It comprises: 202) the first base station sends a first message to the second base station; the first message comprises a first network address of first proxy server and a first ID of the first base station; 204) the second base station responds to the first message, and according to the ID of the first base station, sends a connection request message to the first base station; the first base station responds to the connection request message, and sends a confirmation message to the second base station. By the invention the address of base station is not opened on the public network so as to reduce the possibility of getting a network attack.
Owner:北京智讯伙伴科技有限公司
Flow control mechanism suitable for online identity authentication
The invention relates to the technical field of information security, and discloses a flow control mechanism suitable for online identity authentication. The mechanism provides a strict flow management and control method for online identity authentication, namely after a marking client browser is locked, strict read-write management and control are carried out on a Session object in a communication session, and strict verification management and control are carried out on Cookies contents, therefore even if the Session ID or Coolies contents and other information are leaked, the hackers can also be prevented from posing the identities of legal users by using these resources to prevent the further leakage of the user information, thereby greatly reducing the possibility of information leakage and hacker attacks, and ensuring the security of the online identity authentication process.
Owner:上海金融云服务集团安全技术有限公司
Method for implementing electronic digital sealing system
InactiveCN101079086AAvoid attackVulnerable to attackDigital data protectionInternal/peripheral component protectionDigital signatureMalware
The invention provides a method of achieving the electronic digital signature system in the information system safety special technique field. The method with the association of the software and the hardware achieves the electronic digital signature system, wherein the calculation of all the digital signatures and all the signature checks is made in the hardware printing circuit board and the application-specific integrated circuit. The method enhances the safety of the electronic digital system.
Owner:DALIAN HAISHENGDA TECH
Gateway attack prevention method and device
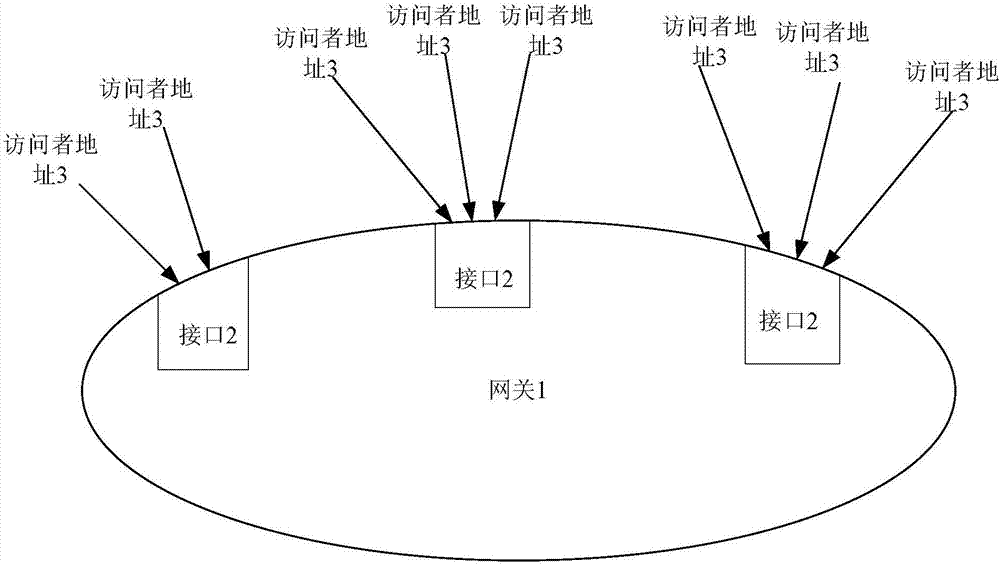
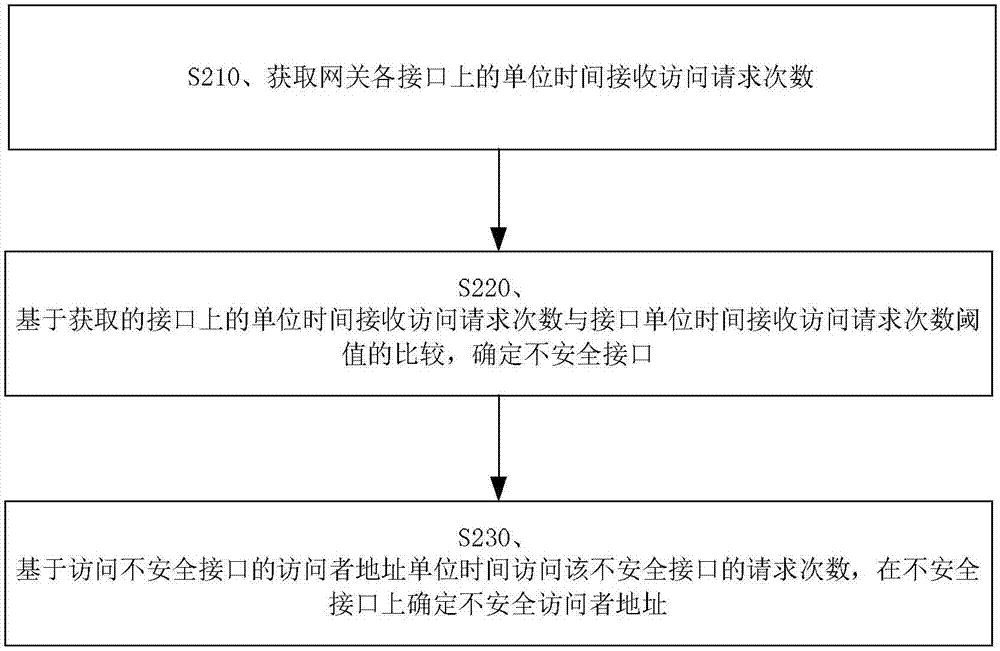
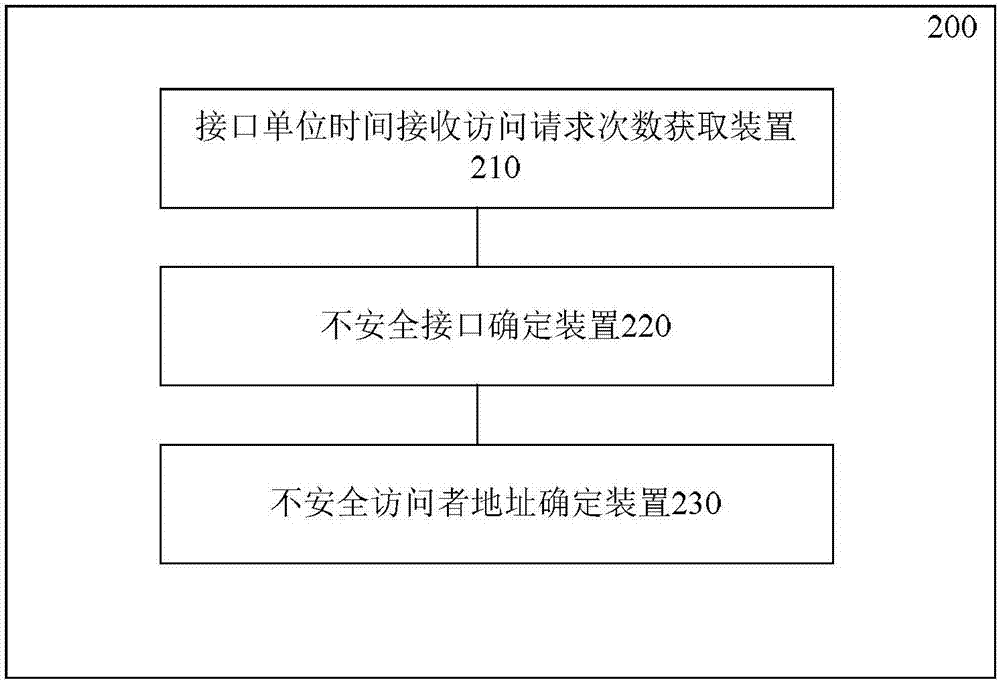
ActiveCN106878282AAvoid visitingReduce frequent visitsNetwork connectionsBand countsAttack prevention
The invention provides a gateway attack prevention method and device. The method comprises the steps: obtaining the number of access requests received by each interface of a gateway in a unit time; determining an unsafe interface based on the comparison of the obtained number of access requests received by the interface of the gateway in a unit time with the threshold value of the number of access requests received by the interface in a unit time, wherein the threshold value is determined in advance based on the maximum number of load access requests of the interface in a unit time and the proportion of the counted mean load saturation degree of the interface to the sum of the mean load saturation degrees of all interfaces of the gateway; and determining the address of an unsafe visitor at the unsafe interface based on the number of requests of the visitor, visiting the unsafe interface, for access to the unsafe interface in the unit time. The method reduces the possibility of taking the frequent visit of a normal user as the attack while recognizing the address of the unsafe visitor more accurately.
Owner:BEIJING BAIDU NETCOM SCI & TECH CO LTD
A secure communication method based on smart card and a system thereof
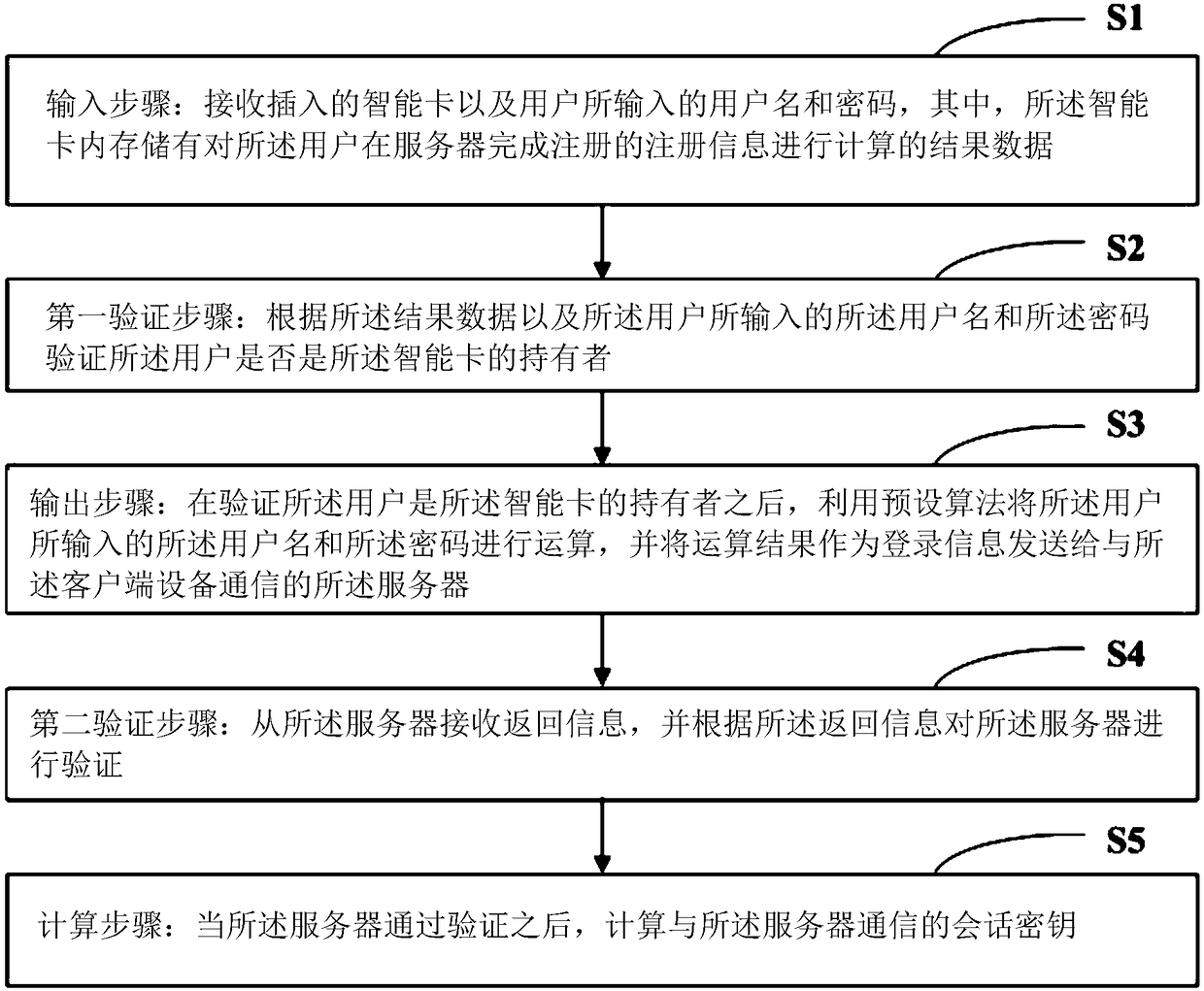
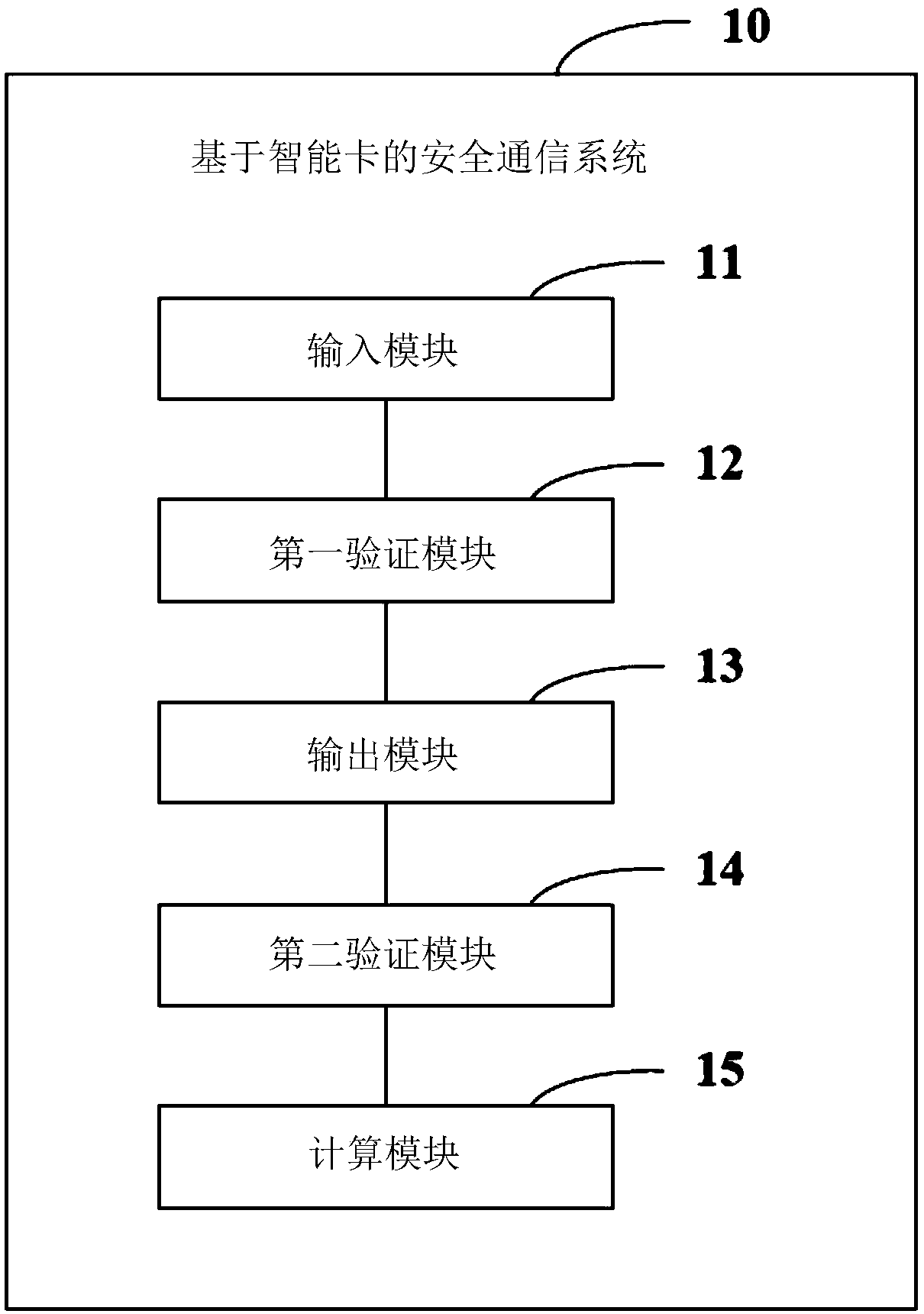
InactiveCN109088888AImprove securityRelieve pressureUser identity/authority verificationPasswordSmart card
The invention provides a secure communication method based on a smart card, wherein, the method comprises the following steps of: receiving an inserted smart card and a user name and password input bya user; wherein, the smart card stores the result data for calculating the registration information of the user completed registration in a server; and the method comprises the steps of: receiving the inserted smart card and the user name and password input by the user. Verifying whether the user is the holder of the smart card according to the result data, the user name and the password input bythe user; Output step: after verifying that the user is the holder of the smart card, calculating the user name and the password input by the user by using a preset algorithm, and sending the calculation result to the server as login information. The invention also provides a secure communication system based on a smart card. The technical proposal provided by the invention can effectively improve the safety of data.
Owner:SHANDONG UNIV OF SCI & TECH
Group key management method based on linear geometry
InactiveCN101753295AReduce storageSmall amount of calculationSpecial service provision for substationKey distribution for secure communicationGroup controllerAlgorithm
The invention discloses a group key management method based on linear geometry, comprising the following steps: step 1, a group controller selects finite field F and mapping f used by group; a group member selects a secret vector on the finite field F, and transmits to the group controller by a secure channel; step 2, the group controller selects a mapping parameter and maps the secret vector of all group members into a group of new vectors using the mapping f; step 3, the group controller selects a random number k as a group key and constructs a linear equation set using the new vector group and group key; and the group controller solves the central vector and transmits the central vector and the mapping parameter to the group member; step 4, the group member maps the secret vector thereof to a new vector in a vector space according to the mapping parameter and then calculates the product of the new vector and the central vector to obtain the group key. The method has the advantages of few storage content, small calculated amount and high security, and can effectively avoid brute force attack.
Owner:SOUTH CHINA UNIV OF TECH
Group key management method based on linear geometry
InactiveCN101753295BReduce storageSmall amount of calculationSpecial service provision for substationKey distribution for secure communicationGroup controllerAlgorithm
The invention discloses a group key management method based on linear geometry, comprising the following steps: step 1, a group controller selects finite field F and mapping f used by group; a group member selects a secret vector on the finite field F, and transmits to the group controller by a secure channel; step 2, the group controller selects a mapping parameter and maps the secret vector of all group members into a group of new vectors using the mapping f; step 3, the group controller selects a random number k as a group key and constructs a linear equation set using the new vector groupand group key; and the group controller solves the central vector and transmits the central vector and the mapping parameter to the group member; step 4, the group member maps the secret vector thereof to a new vector in a vector space according to the mapping parameter and then calculates the product of the new vector and the central vector to obtain the group key. The method has the advantages of few storage content, small calculated amount and high security, and can effectively avoid brute force attack.
Owner:SOUTH CHINA UNIV OF TECH
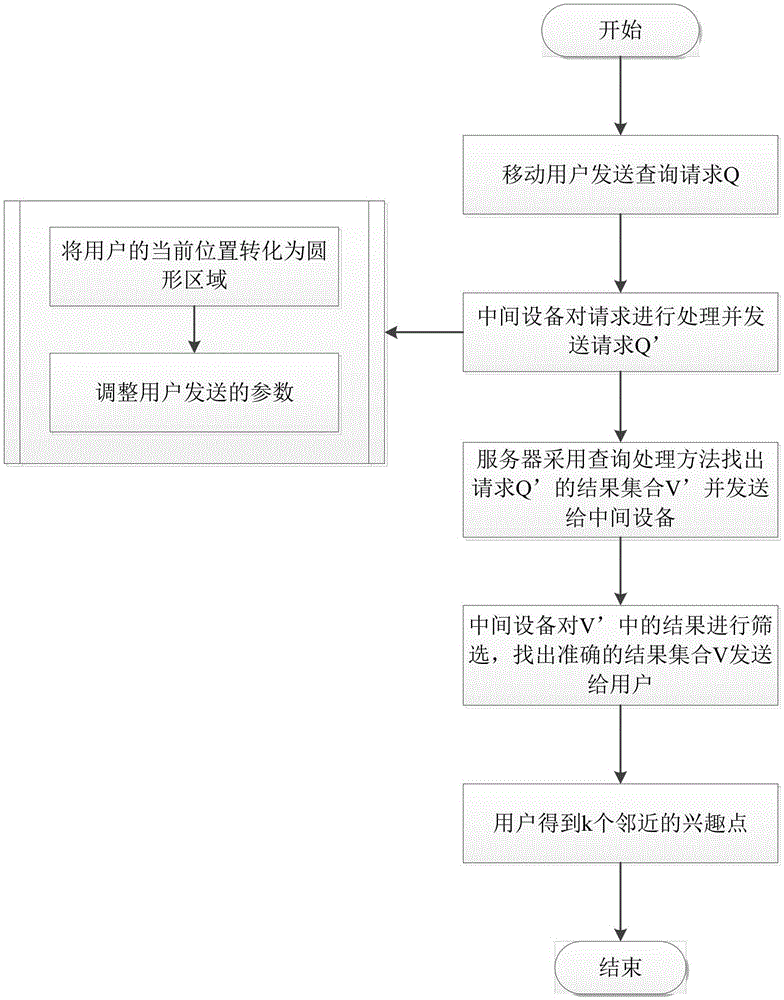
Mobile user position privacy protection method for avoiding attacks performed through circular region overlapping parts
InactiveCN105554743AProtect location privacyReduce the likelihood of an attackLocation information based serviceSecurity arrangementAttackPrivacy protection
The invention provides a mobile user position privacy protection method for avoiding attacks performed through circular region overlapping parts, and relates to the field of position privacy protection. The method comprises the following steps that: firstly, a user sends a request Q (a current position of the user, the number of query results and the like) to intermediate proxy equipment; the intermediate equipment converts a real position of the user into a circular region, specifies a value which is greater than a confidence level needed by the user and the number of query results, and sends a request Q' to an LBS (Location Based Service) server provider; an LBS finds points of interest satisfying a condition with a query processing method, puts the points of interest satisfying the condition into a set V', and returns the V' to the intermediate equipment; and the intermediate equipment screens the V', and returns a screening result to the user. Through adoption of the method, the attacks performed through the circular region overlapping parts are effectively avoided when the user queries a server, and the position privacy of the user can be protected more accurately. The mobile user position privacy protection method is suitable for protecting privacy of the user position when the user queries surrounding points of interest.
Owner:NANJING UNIV OF INFORMATION SCI & TECH
Key management method, key use method, key management device, key use device and key use equipment
ActiveCN112636907ANot easy to losePrevent leakageKey distribution for secure communicationFinanceComputer securityEngineering
The embodiment of the invention provides a secret key management method, a secret key use method, a secret key use device and equipment. The method comprises the steps: receiving a registration request sent by a user side, and enabling the registration request to comprise an identity identification of a user; generating a user key corresponding to the identity identifier; splitting the user key into a plurality of key slices; and combining the key slices according to a preset rule and then sending the key slices to each key node for storage, wherein each key node comprises a trusted mechanism node and a client node. According to the embodiment of the invention, the user key is split into the key slices, one part is stored in the credible institution node, and the other part is stored in the client node, so that the user key is not easy to lose; meanwhile, the user secret keys are dispersed in different secret key nodes, the possibility that all the nodes are attacked by the network is extremely low, the user secret keys are not prone to leakage, and the safety of the user secret keys is guaranteed.
Owner:WEBANK (CHINA)
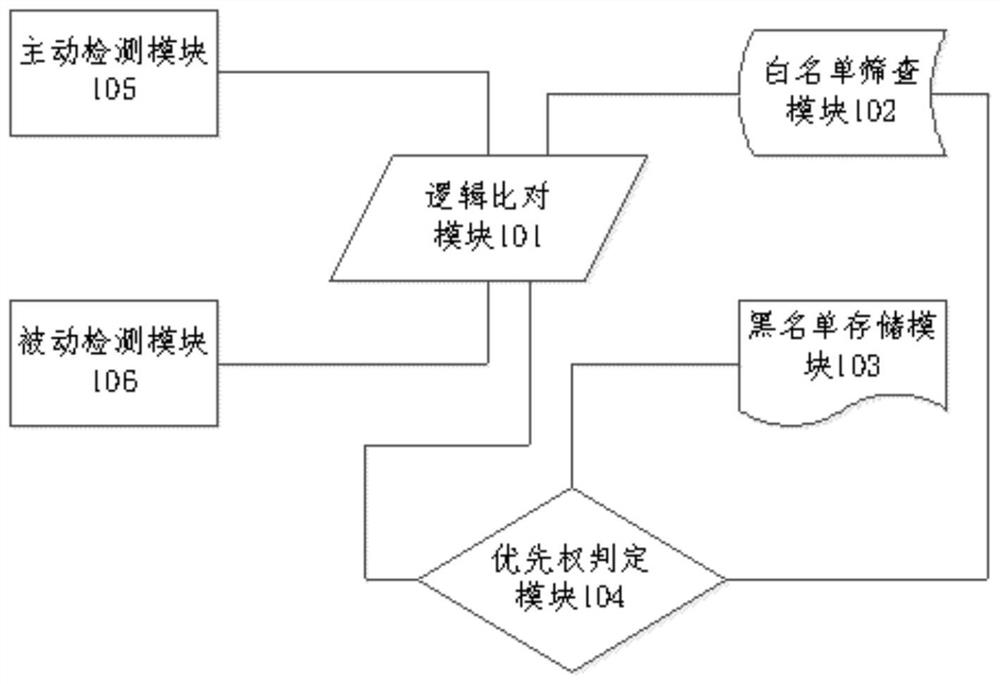
Enterprise safety protection system and method based on white list mechanism
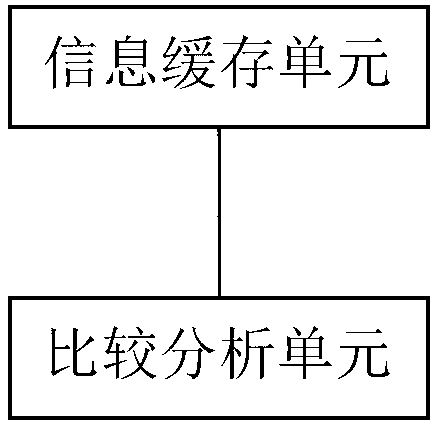
The invention discloses an enterprise safety protection system based on a white list mechanism. The enterprise safety protection system comprises a fingerprint information detection module, a logic comparison module, a white list screening module, a black list storage module and a priority judgment module, aiming at the defects that an existing terminal white list protection system is low in recognition precision and is easily attacked, an active and passive dual detection technology is adopted and is matched with an active filtering logic design of a priority judgment module, so that the attack possibility is greatly reduced, the blocking and priority processing effects of a white list are improved, and the time delay condition of terminal login is reduced to a certain extent; the dual-detection data is identified under the synchronous clock through the terminal type dictionary, thereby achieving high-precision terminal identification protection; and through scientific lag time function design, the identification range and the identification precision of the method are greatly increased, and more realizable technical means are added for safe white list architecture design.
Owner:北京哈工信息产业股份有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com