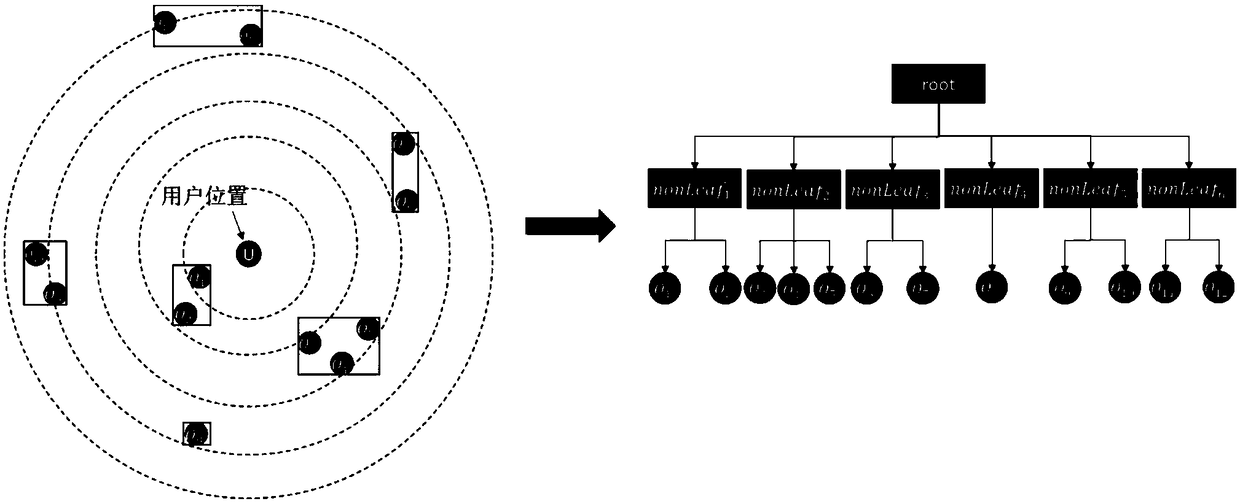
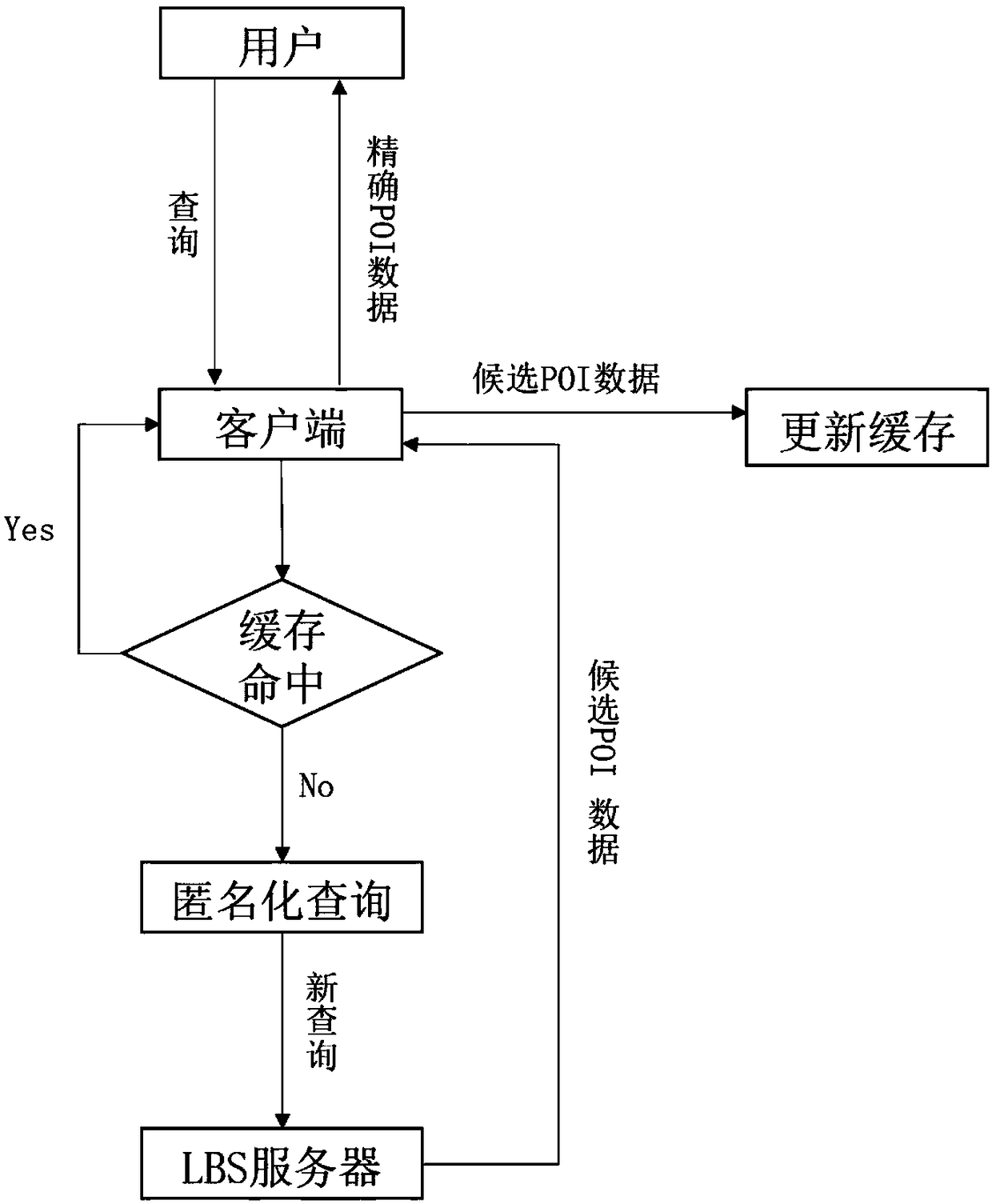
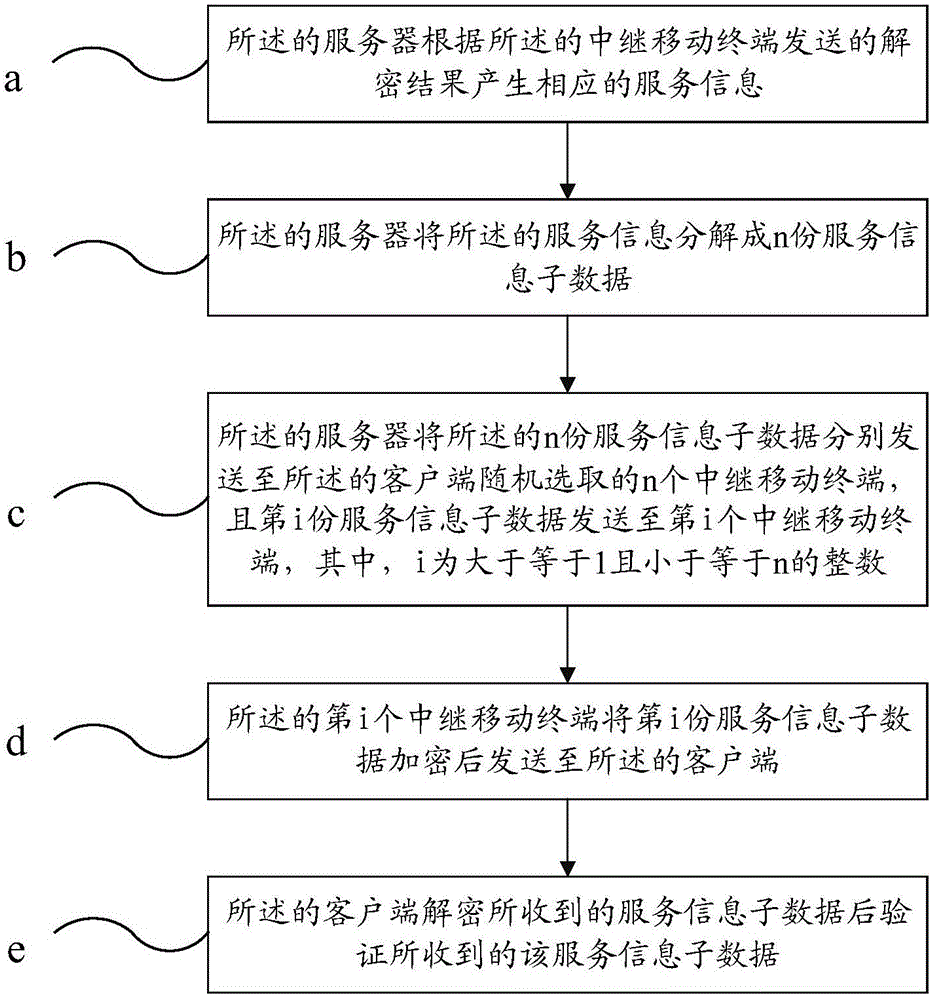
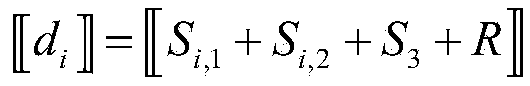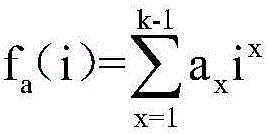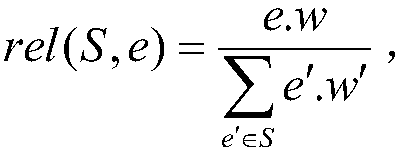Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
85results about How to "Protect location privacy" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
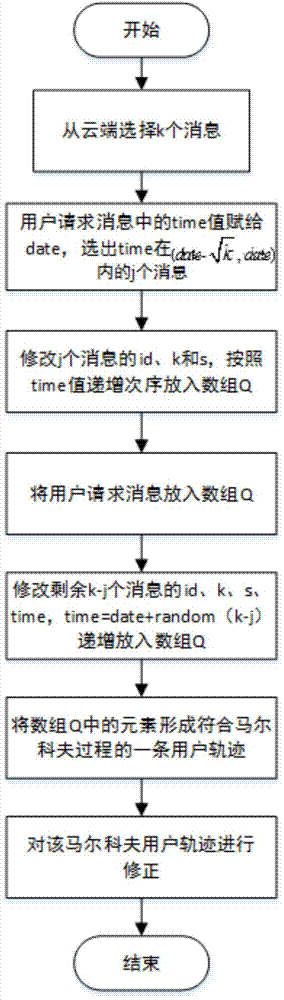
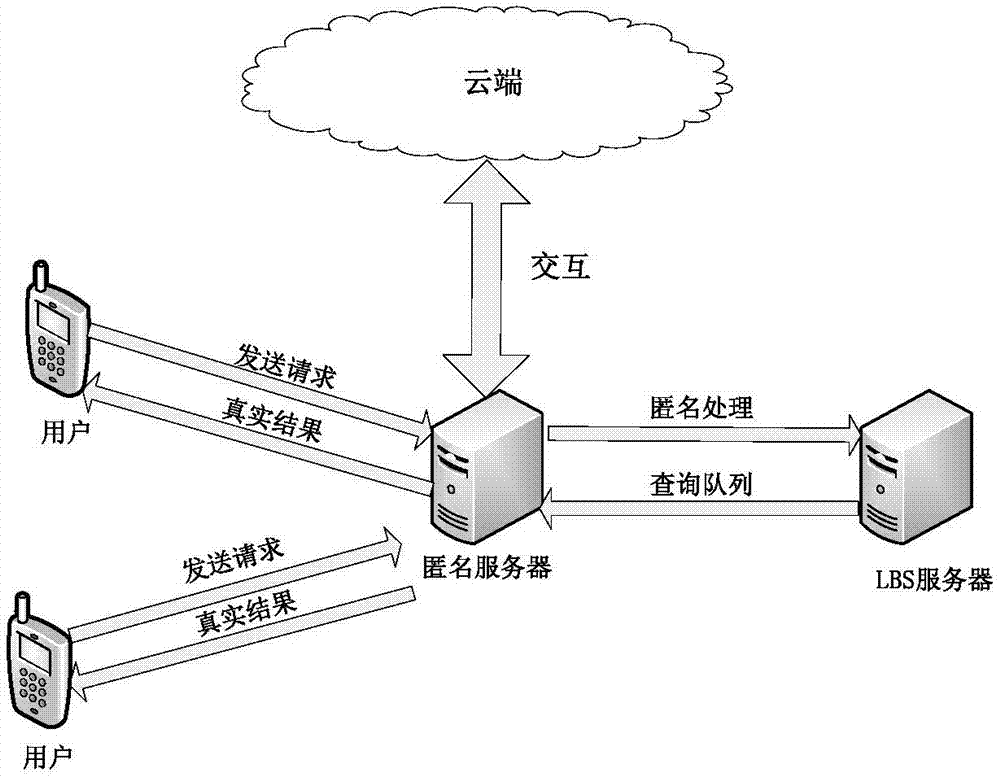
Continuous query oriented location anonymizing method applicable to location service system
InactiveCN102892073AFix the leakSufficiently diverseLocation information based serviceTransmissionPersonalizationPrivacy protection
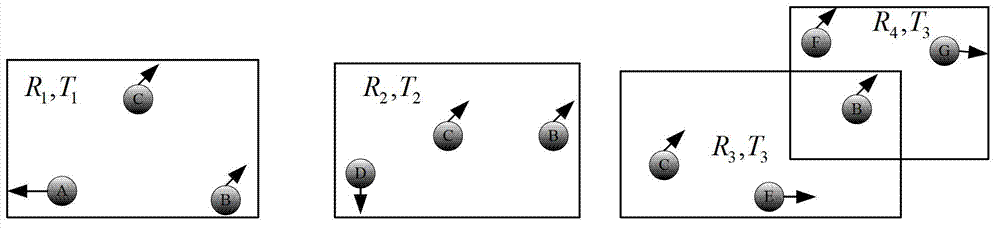
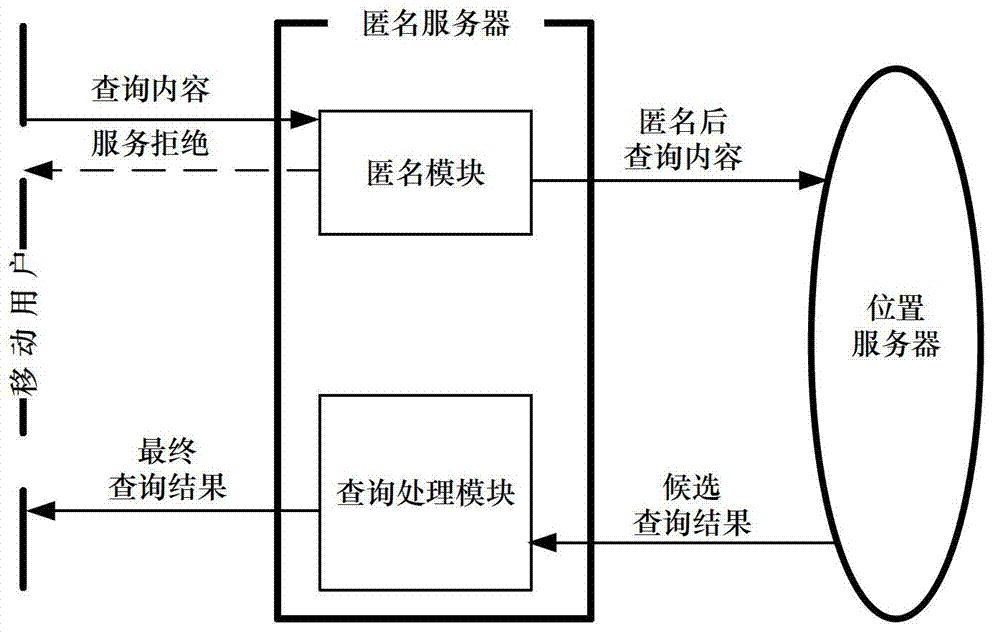
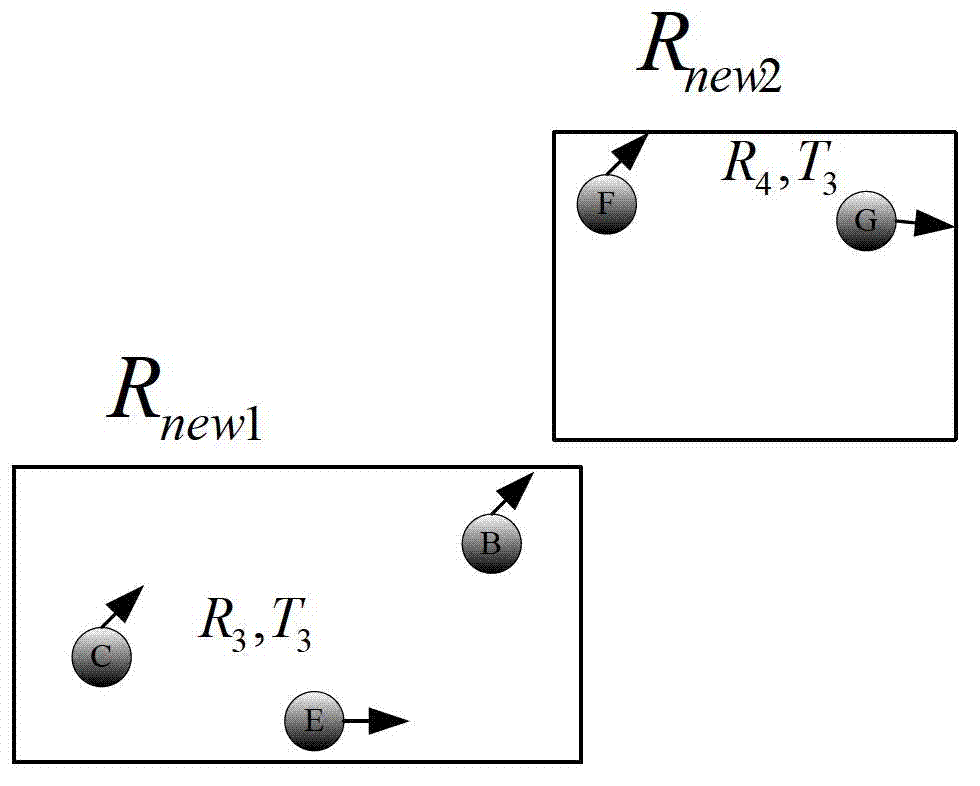
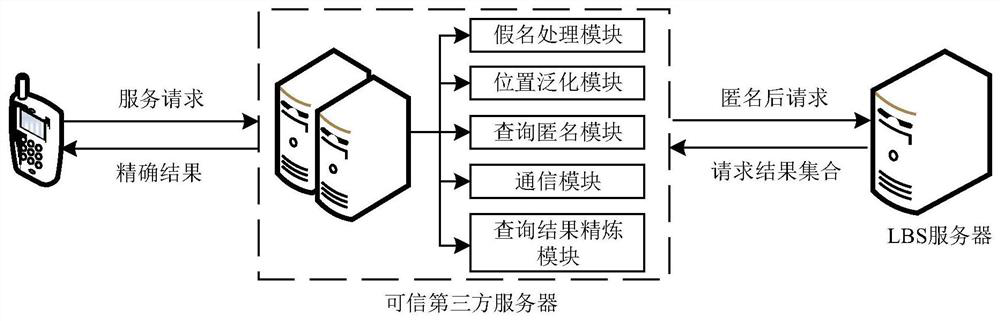
The invention discloses a continuous query oriented location anonymizing method applicable to a location service system, belonging to the technical field of privacy protection of location service, which comprises the steps of: proposing an anonymizing request by a mobile user; anonymizing the request by an anonymizing module in an anonymizing server, and sending the anonymized request to a location server; processing the request by the location server, integrating query results and sending to the anonymizing server; integrating and filtering received candidate results by a query processing module of the anonymizing server, and sending a precise result to the corresponding mobile user. According to the anonymizing method, personalized customization of privacy protection parameters of the user is permitted. The anonymizing module operates in the anonymizing server, and is used for calculating by the anonymizing method provided by the invention depending on the privacy protection parameters of the mobile user, to guarantee that all anonymizing regions of the mobile user include an identical number of queries in a query valid period and the anonymizing space is shared by the mobile users in the space; and the query privacy of the mobile user who proposes a continuous query in the location service is effectively protected.
Owner:BEIHANG UNIV
Network position privacy protection method of wireless sensor
InactiveCN102843673AProtect location privacyScattered location distributionNetwork topologiesSecurity arrangementWireless sensor networkingPrivacy protection
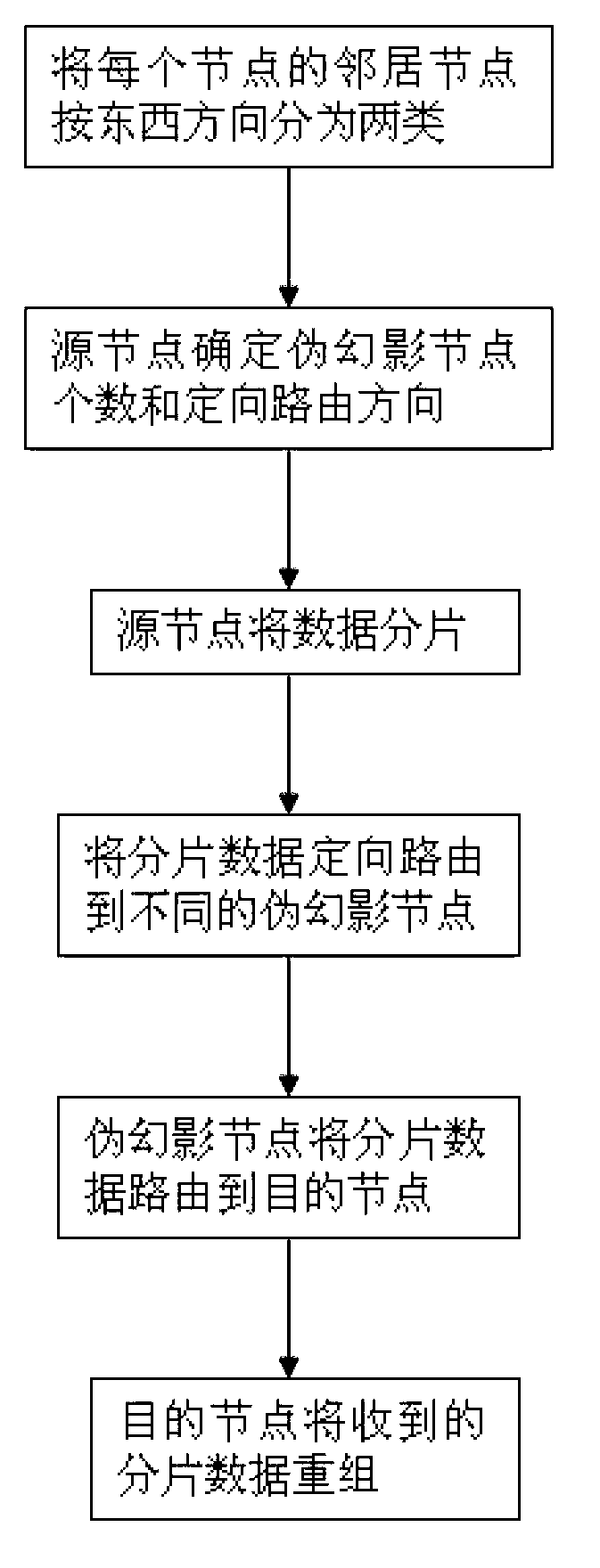
The invention discloses a network position privacy protection method of a wireless sensor. The method comprises the following steps: dividing the data to be sent into m fragment data by a source node; routing the m fragment data to n different pseudo phantom nodes which are selected at random though a directional routing method; routing the received fragment data to a target node through the n pseudo phantom nodes; reconstituting the fragment data through the target node after receiving all fragment data. Compared with the prior art, the method of multi-phantom pseudo source node is adopted, then the difficulty of an attacker to track a real source node can be increased, so that the privacy of the position of the source node can be effectively protected; and moreover, the method is suitable for middle and large scaled sensor networks.
Owner:JIANGSU UNIV OF SCI & TECH +1
Homomorphic encryption-based position privacy querying method
ActiveCN107749865AGuaranteed privacyFast encryptionKey distribution for secure communicationCommunication with homomorphic encryptionPlaintextCiphertext
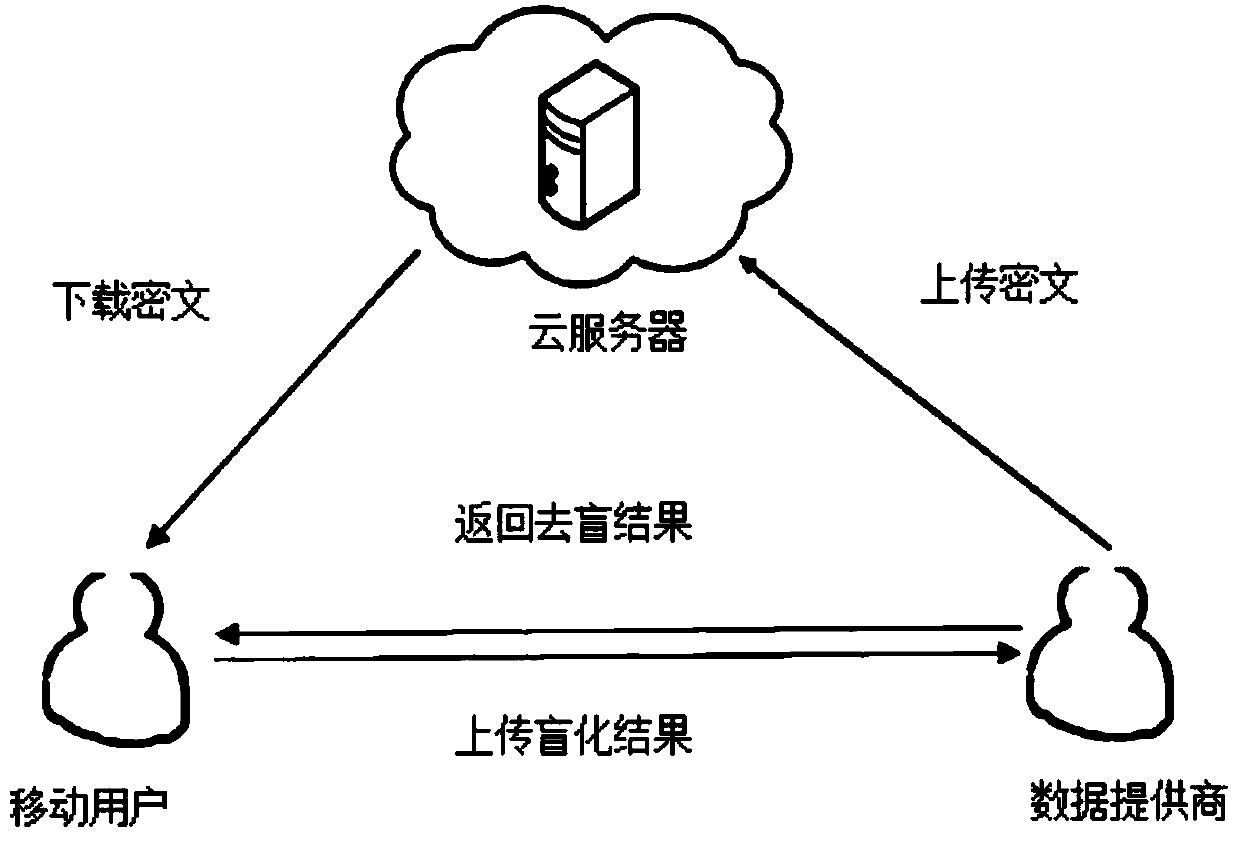
A homomorphic encryption-based position privacy querying method disclosed by the present invention comprises a cloud server, a data service provider and a plurality of mobile users. The data service provider SP partitions the areas in a map according to the intensity of the querying objects, then encrypts the querying objects in the partitions via a symmetric encryption algorithm, and encrypts thesymmetric secret keys via a homomorphic encryption algorithm, and finally stores all ciphertexts in the cloud server, thereby secretly saving the private keys of the homomorphic encryption. Users download the ciphertexts of the querying objects and the corresponding symmetric secret key ciphertexts from the cloud server according to the own positions, and further carry out the blind processing onthe symmetric secret key ciphertexts and transmit to the data service provider, and the data service provider transmits the decrypted blind plaintexts to the users, and finally, users decrypt the corresponding querying objects to obtain the final query results. According to the present invention, the position information of the users is not leaked during the whole process, thereby protecting theposition privacy.
Owner:安徽迪科数金科技有限公司
Block chain-based distributed anonymous area cooperative construction method capable of achieving privacy keeping
ActiveCN108173805AGenerate efficientlyProtect location privacyUser identity/authority verificationDigital data protectionK-anonymityBlockchain
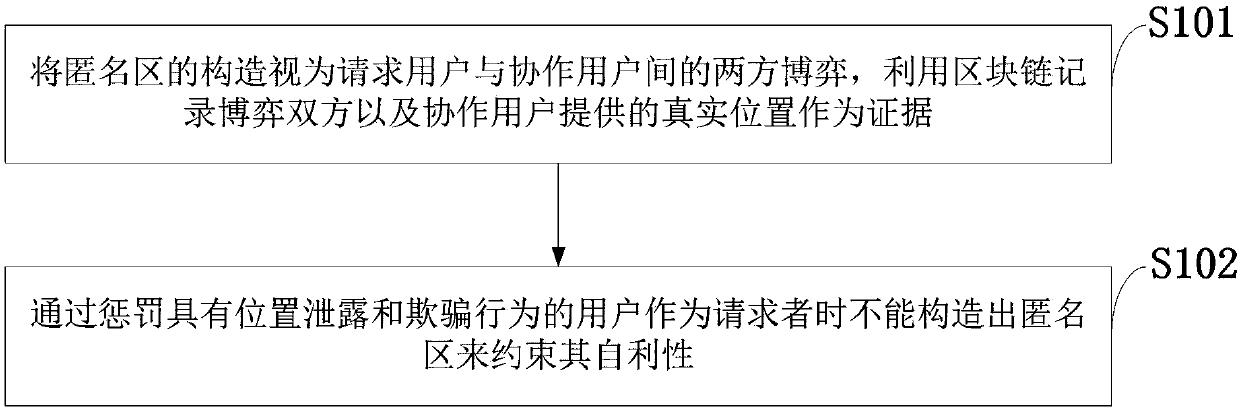
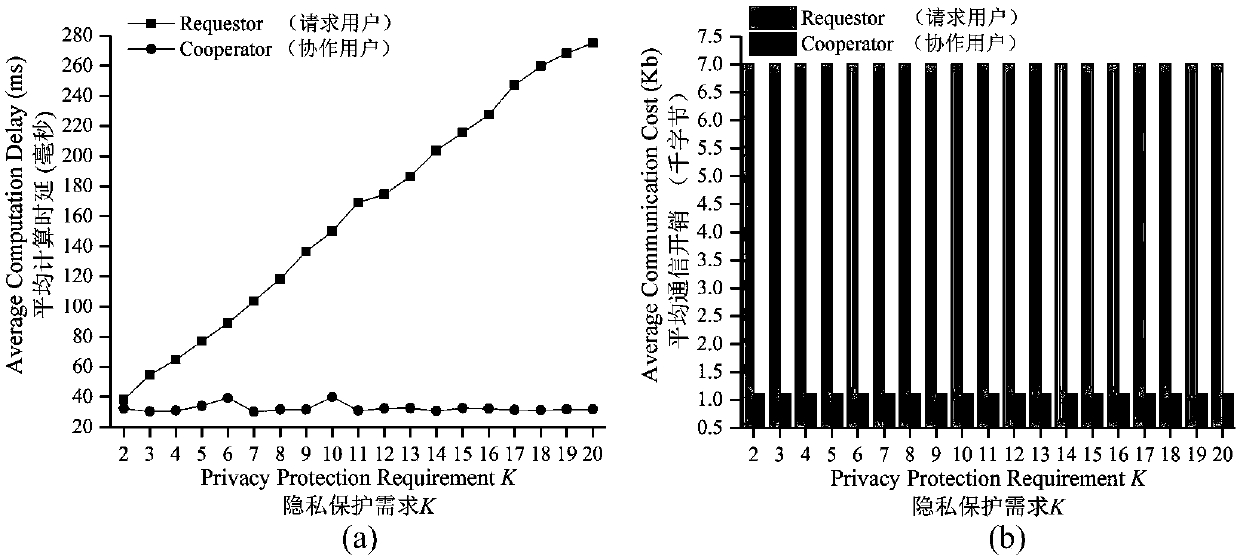
The invention belongs to the technical field of privacy protection, and discloses a block chain-based distributed anonymous area cooperative construction method capable of achieving privacy keeping. Construction of an anonymous area is regarded as a two-party game between a request user and cooperative users, the two game parties and locations provided by the cooperation users are recorded by a block chain to serve as evidences, the user having location leakage and cheating behaviors is punished to be not capable of constructing the anonymous area when serving as the requester to restrain theself-interest of the user, and then the block chain-based distributed anonymous area cooperative construction method capable of achieving privacy keeping is proposed. According to the method, the condition that the request user leaks location information of the cooperation users can be prevented, the anonymous area can be efficiently generated while the cooperation users are motivated to provide real locations to participate in anonymous area construction, and the location privacy of the users in distributed K anonymity-based LBS querying is effectively protected.
Owner:XIDIAN UNIV
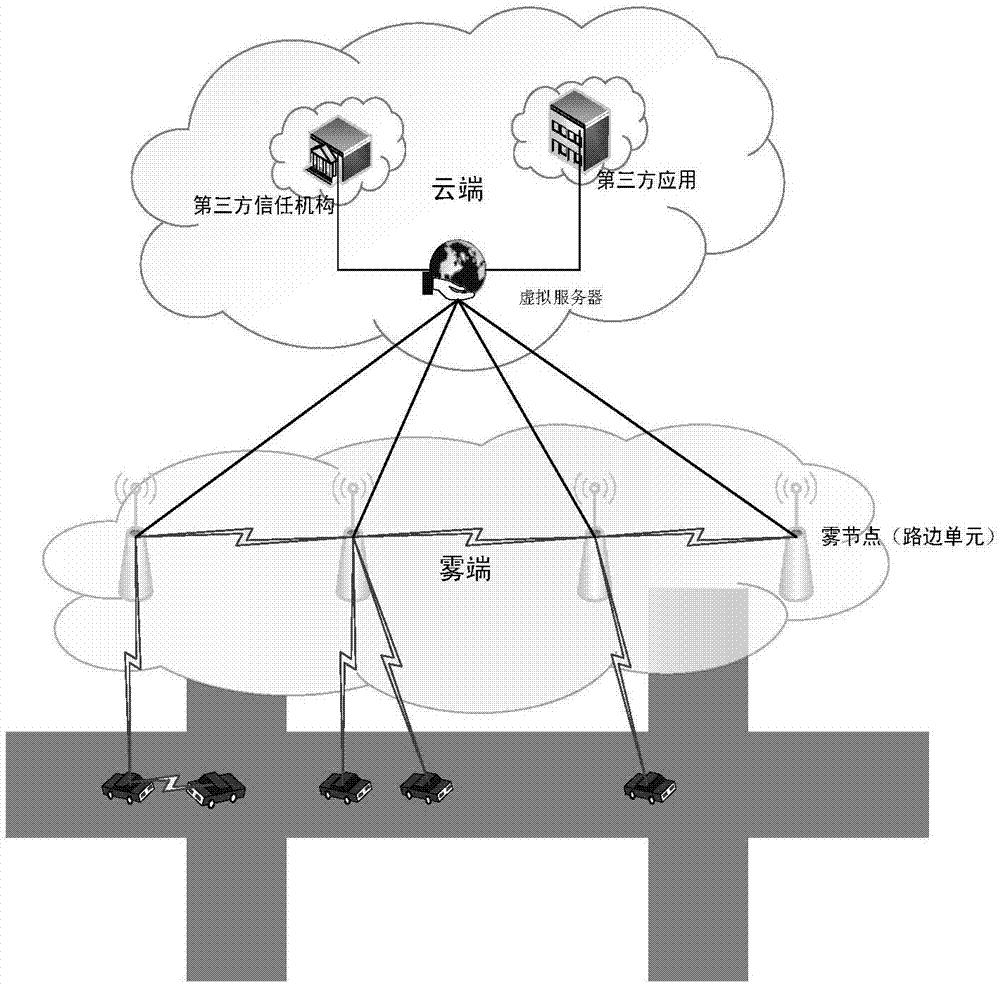
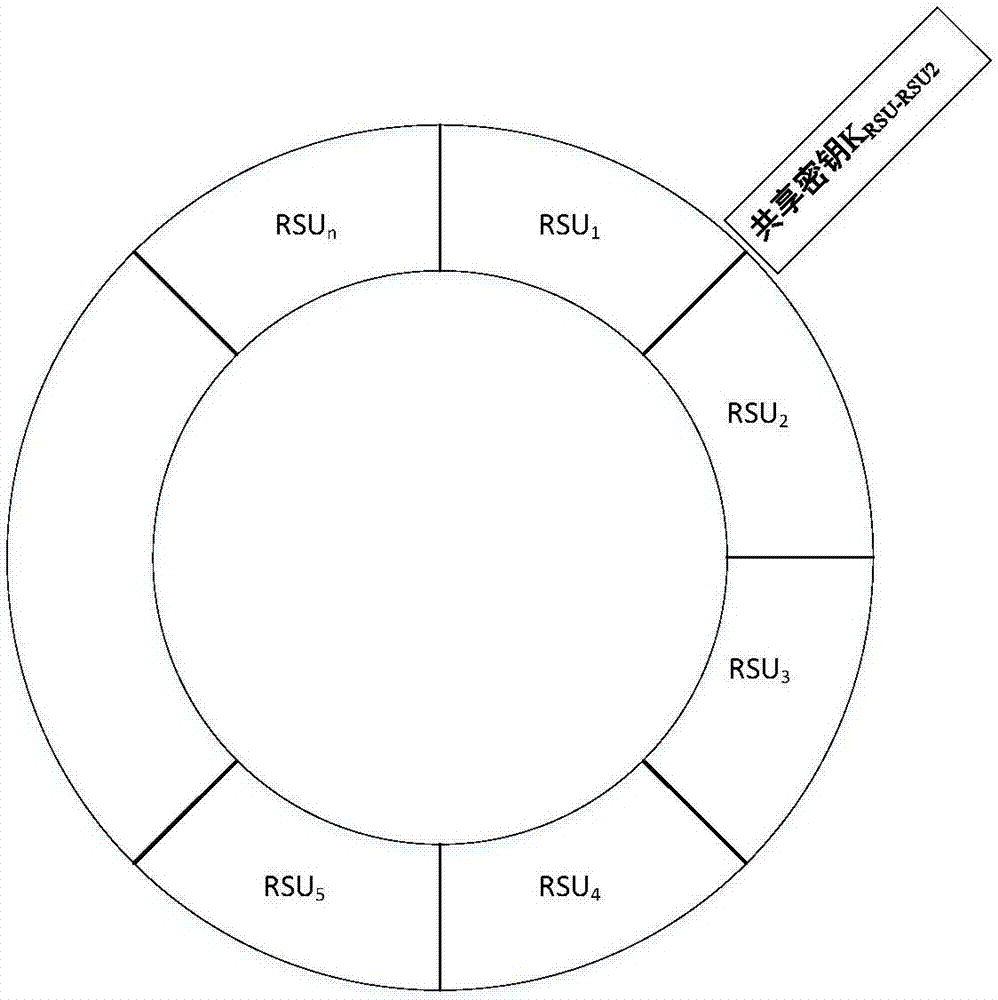
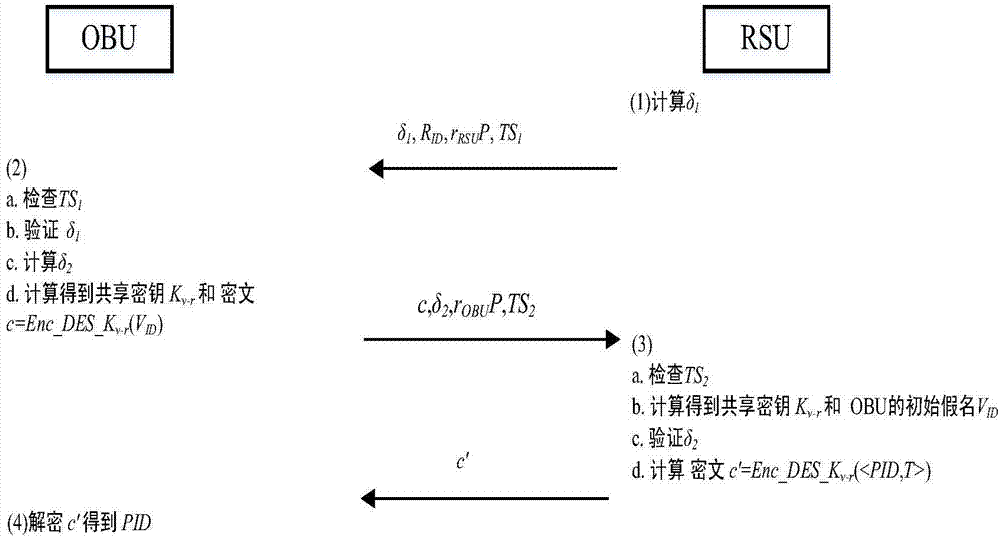
VANETs position privacy protection query method under fog computing architecture
ActiveCN108012232AReduce waiting time for responseProtect location privacyParticular environment based servicesTransmissionProtocol for Carrying Authentication for Network AccessSelf-organizing network
The invention provides a VANETs position privacy protection query method under a fog computing architecture, which comprises the following steps: both a roadside unit RSU and a vehicular unit OBU areregistered to a third-party trust mechanism TA; a ring is formed between the adjacent roadside units RSU; the roadside unit RSU in the ring serves as a fog node in the ring and is provided with a pioneer node and a successor node, and a shared secret key is arranged between the adjacent roadside units RSU in the ring; when the vehicular unit OBU is connected to the vehicular self-organizing network VANETs for the first time, bidirectional access authentication is carried out between the vehicular unit OBU and the roadside unit RSU, and a temporary query code PID is issued to the OBU by the roadside unit RSU; and a query based on a position service is completed between the vehicular unit OBU and the roadside unit RSU by adopting an anonymous forwarding chain generated based on the ring formed by the roadside unit RSU. According to the method in the invention, the anonymous forwarding chain technology is applied to the process of a vehicle node of the VANETs protocol to carry out serviceinquiry; the anonymous forwarding chain technology is used, so that the position privacy of the vehicle node is effectively protected.
Owner:NORTHEASTERN UNIV
User privacy protection method, equipment and system for location business
InactiveCN102457805AImprove securityAvoid leakage of user privacyLocation information based serviceTransmissionUser privacyPrivacy protection
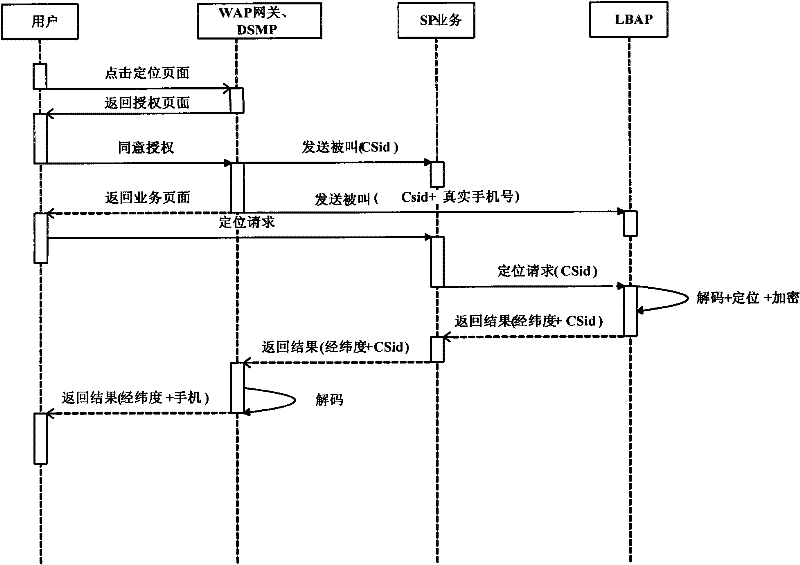
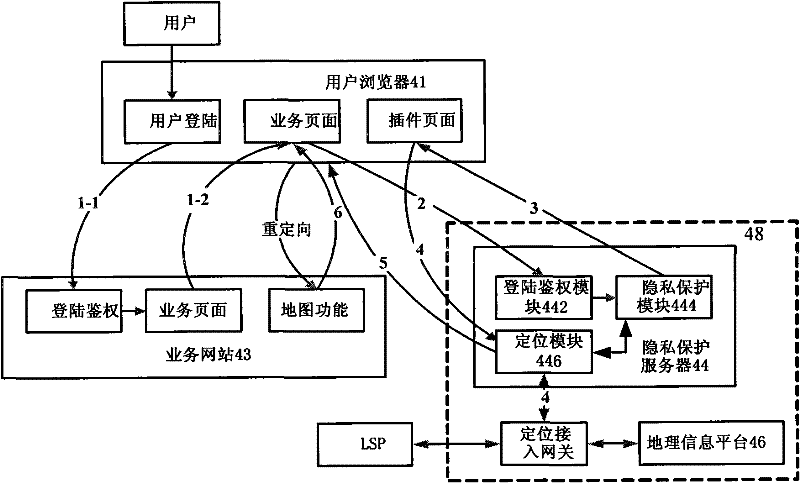
The invention discloses a user privacy protection method, equipment and a system for a location business, wherein the method comprises the following steps of: receiving a started location positioning request by a user browser end when an internet user visits a business website, and directly sending the location positioning request to privacy protection equipment of a wireless communication network side by the user browser end; verifying the location positioning request by the privacy protection equipment, after the location positioning request is passed, and returning a positioning result corresponding to the location positioning request to the user browser end; and returning positioning result location information requested by the internet user to the business website by the user browser end. In the invention, user privacy protection can be achieved when the internet user uses the location business, safety for user location privacy can be improved, and defects that the user location privacy is leaked and privacy protection for the internet user can not be achieved in the prior art can be solved.
Owner:LIAONING MOBILE COMM
Indoor and outdoor positioning method and indoor and outdoor positioning system
InactiveCN105891867AWide coverageAchieve seamless integrationSatellite radio beaconingPositioning systemReal-time computing
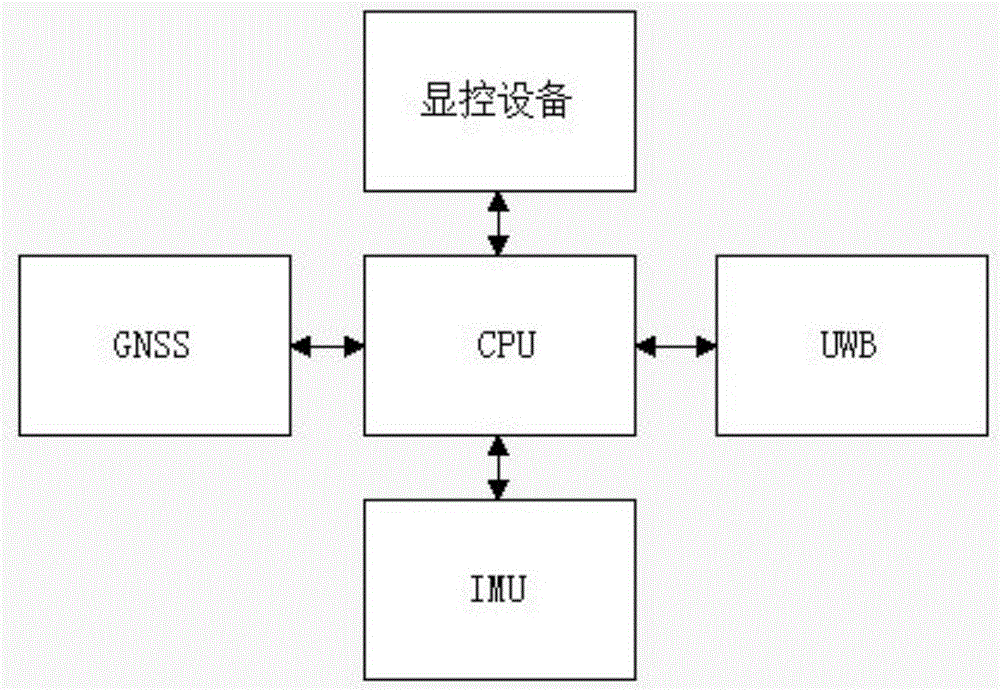
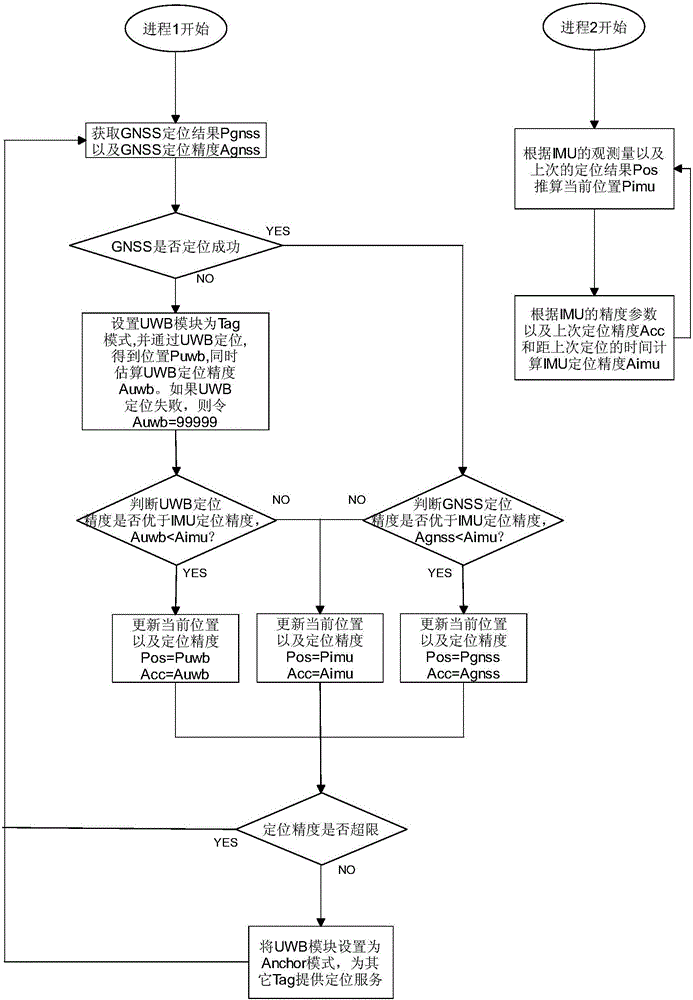
An indoor and outdoor positioning method and an indoor and outdoor positioning system are provided. The indoor and outdoor positioning method is characterized in that a plurality of nodes are set, and each node includes a CPU, a GNSS receiver, an IMU, and a UWB positioning module; for each node, the attribute is set as Tag before the node gets the position thereof, and the attribute is set as Anchor after the node gets the position thereof, which provides a reference position for the positioning of the other nodes; information transmitted between an Anchor node and a Tag node includes ranging information and the position information of the Anchor node; and the nodes of which the attribute is set as Tag are compared in GNSS, UWB and IMU positioning results and positioning accuracy according to a preset Anchor node, the node of highest positioning accuracy is selected, whether the positioning accuracy is over-limit is judged, and if the positioning accuracy is not over-limit, the Tag is converted into Anchor to provide positioning service for other Tags. The scope of positioning is expanded, the system cost is reduced, the reliability and the system scalability are improved, and the privacy of positioning users is protected.
Owner:WUHAN UNIV
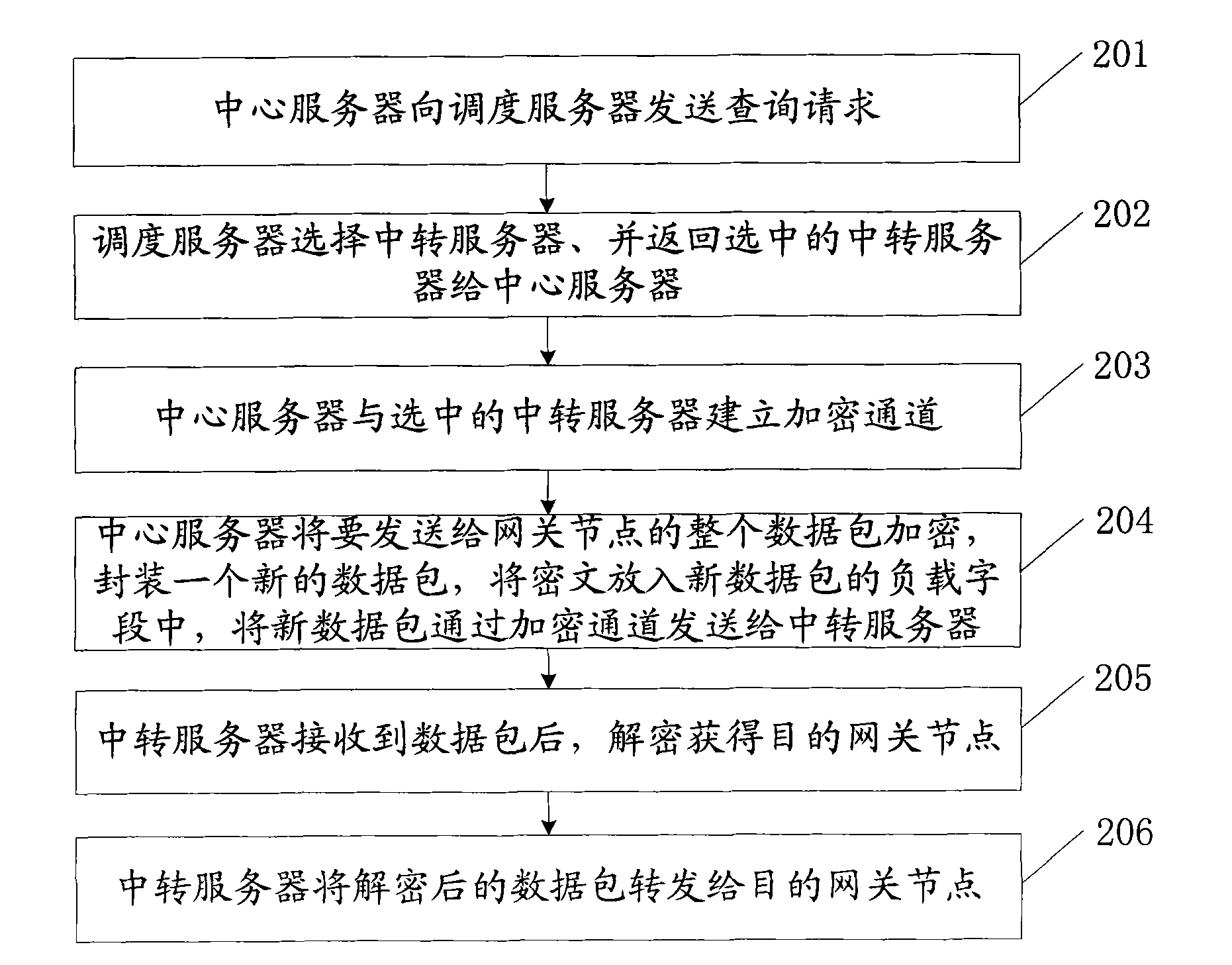
Efficient query processing method for protecting location privacy and query privacy
ActiveCN111083631AProtect data privacyReduce time complexityDigital data information retrievalDigital data protectionQuality of serviceMobile device
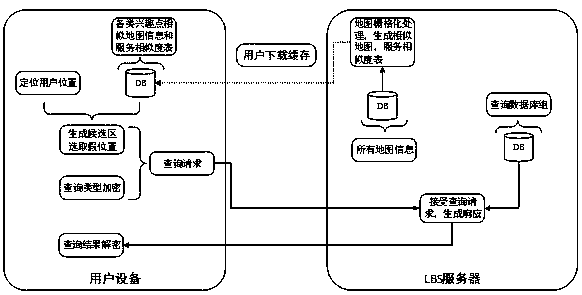
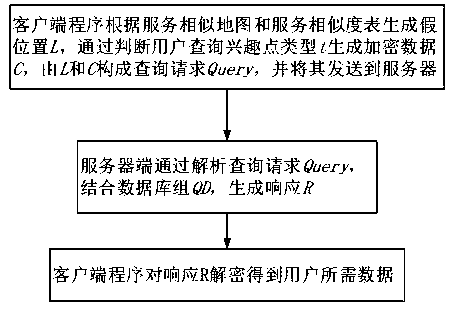
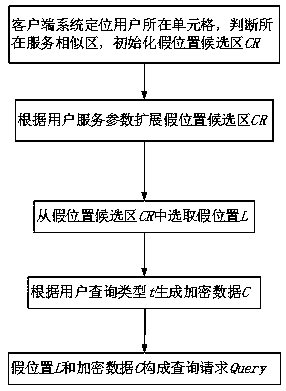
An efficient query processing method for protecting location privacy and query privacy specifically comprises the following steps: (1) a user selecting a false location through a cached service similarity map and a service similarity table by using mobile equipment at a client; generating encrypted data according to the interest point types to be queried by the user and the total number of the interest point types; forming a query request by the false position and the encrypted data, and sending the query request to an LBS (Location Based Service) server; (2) according to the received query request, generating a response by using a stored database by the server, and returning the response to the client; and (3) the client decrypting the data in the response returned by the server to obtainthe data required by the user. According to the method, the false position is selected by utilizing the existing service similarity, so that certain service quality is ensured while the position privacy is protected. The type inquired by the user is encrypted by utilizing homomorphic encryption, so that the server can return data required by the user under the condition that the inquiry type of the user is not exposed.
Owner:LANZHOU JIAOTONG UNIV
Position privacy protection method combining k-anonymity and cloud end
ActiveCN104717292AQuality improvementWithout compromising accuracyTransmissionLocation information based serviceK-anonymity
The invention discloses a position privacy protection method combining k-anonymity and the cloud end. The method is based on position k-anonymity, the cloud end technology is adopted, and by means of a large number of data of the cloud end, it is guaranteed that the situation that anonymity of an anonymous server fails due to the fact that the k value is not reaches is avoided. The method is simple and easy to achieve, distribution position information precision does not need to be reduced while mobile user position privacy is protected, and a user obtains satisfying position service. Even if the anonymous server is attacked by an attacker, the attacker only obtains useless or false information stored at the cloud end and can not obtain real information of the user, and position privacy of the user is further protected.
Owner:NANJING UNIV OF POSTS & TELECOMM
Position privacy protection method, device and system
ActiveCN104754560AAvoid exposureAvoid trackingTransmissionLocation information based servicePrivacy protectionReal-time computing
Provided are a location privacy protection method, device and system, the method comprising: generating an identifier update notification message transmitted to at least one access point (AP), the identifier update notification message comprising the first identifier and the second identifier information of a wireless terminal, the first identifier indicating that the identifier update notification message is transmitted by the wireless terminal; transmitting the identifier update notification message, such that the AP acquires a second identifier according to the second identifier information, and uses the second identifier as the identifier of the wireless terminal; and transmitting to the AP a subsequent message comprising the second identifier to indicate that the subsequent message is transmitted by the wireless terminal. The wireless terminal can periodically or aperiodically transmit the identifier update notification message for updating the identifier thereof, such that the identifier field value of the wireless terminal in the subsequent message is not fixed, thus avoiding the problem of disclosing and tracking the wireless terminal location due to the fixed identifier field value of a transmitting device in the message, and effectively protecting the location privacy of a user using the wireless terminal.
Owner:HUAWEI DEVICE CO LTD
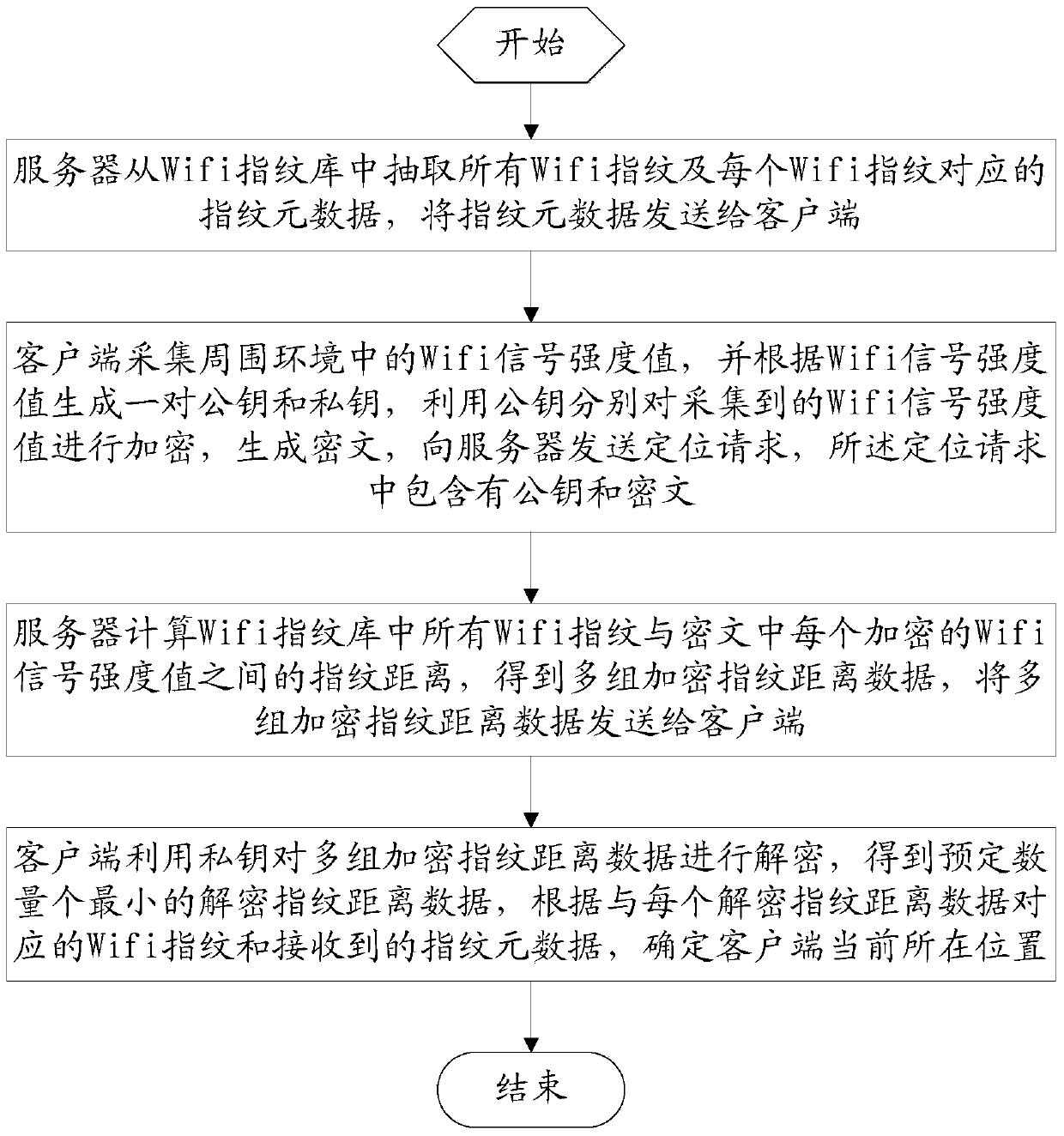
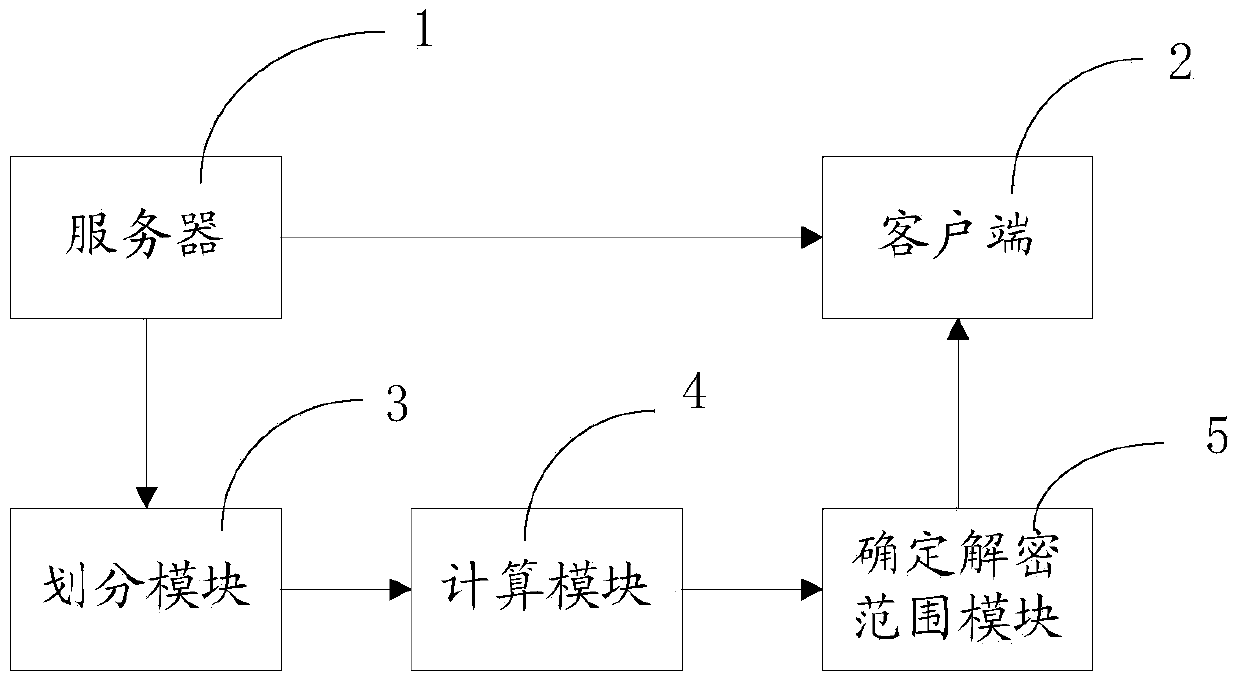
Privacy protection method and device for Wifi fingerprint positioning
InactiveCN103442335AAvoid privacyGuaranteed positionWireless commuication servicesSecurity arrangementPrivacy protectionEngineering
The invention relates to a privacy protection method and device for Wifi fingerprint positioning. The privacy protection method for Wifi fingerprint positioning comprises the following steps that a server extracts all the Wifi fingerprints and fingerprint metadata; a client terminal collects Wifi signal intensity values in the peripheral environment and generates a public key and a private key according to the asymmetrical encryption algorithm, encryption is respectively conducted on the collected Wifi signal intensity values by the public key and a positioning request is sent to the server; the server calculates the fingerprint distance between all the Wifi fingerprints and each encrypted Wifi signal intensity value and transmits multiple sets of encrypted fingerprint distance data to the client terminal; the client terminal uses the private key to decrypt the multiple sets of the encrypted fingerprint distance data, and determines the current location of the client terminal according to the Wifi fingerprint corresponding to each decrypted fingerprint distance datum and the received fingerprint metadata. The privacy protection method and device for Wifi fingerprint positioning solves the privacy problem in an existing WiFi fingerprint positioning technology, and can protect the location privacy of a user and the data privacy of a service provider.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
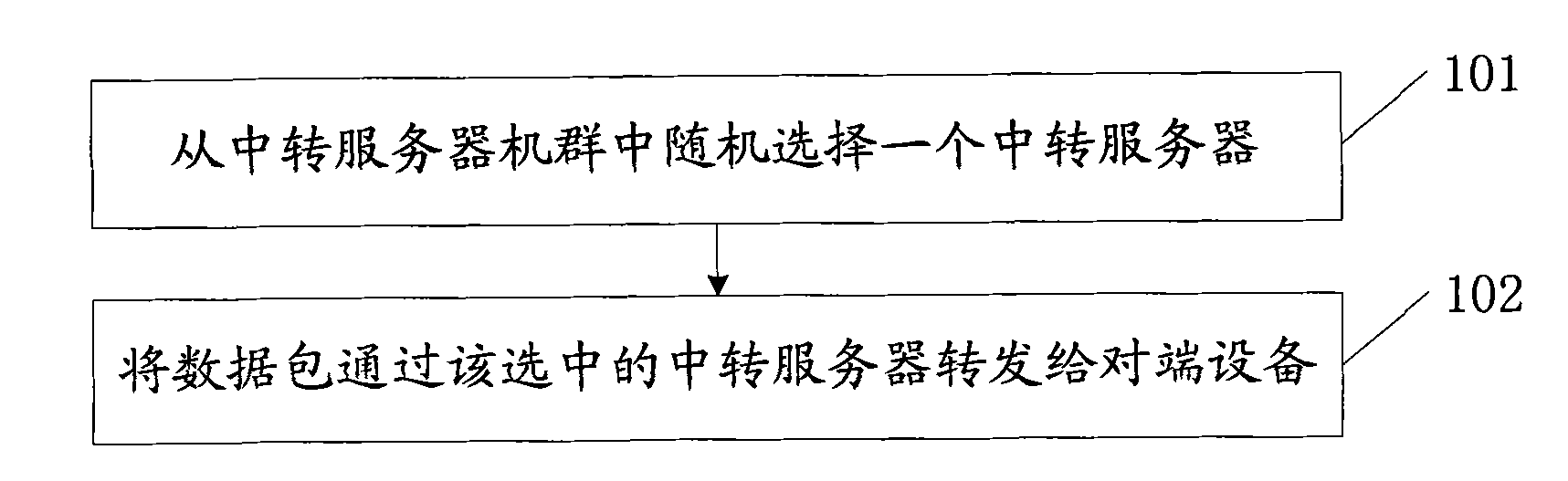
Method, device and system for anonymizing gateway node
The invention discloses a method a device and a system for anonymizing a gateway node, belonging to the field of internet of things. The method comprises the following steps of: randomly selecting a transfer server from a transfer server cluster, and transferring a data packet to an opposite-end device through the selected transfer server. The central server comprises a first selecting module anda first transferring module. The gateway node comprises a second selecting module and a second transferring module. The system comprises the central server, the transfer server cluster and the gateway node. One original fixed link is stretched into a plurality of irregular temporary links through the radon data transferring method to ensure that an attacker can not know where data goes, the position of the target gateway node is hidden in the internet, and the position privacy of objects behind the target gateway node is further protected.
Owner:北京哈工创新计算机网络与信息安全技术研究中心 +2
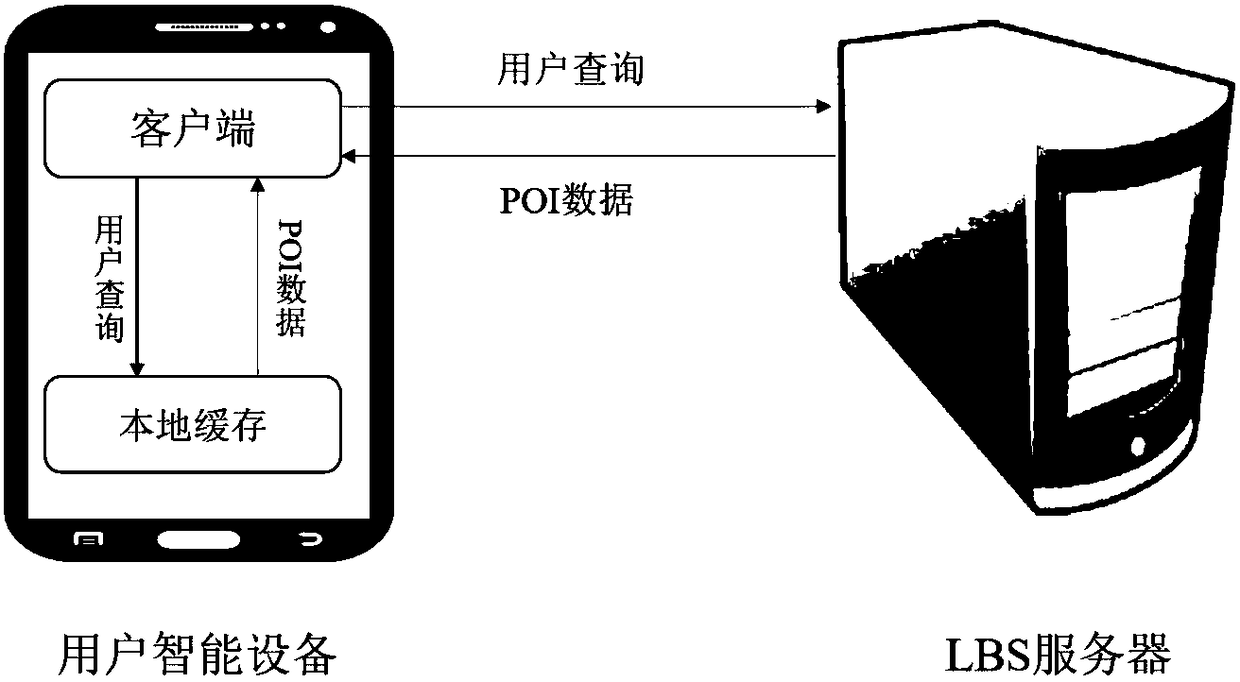
Method for protecting position privacy based on cache
InactiveCN108280162AEnsure location privacy and securityIncrease speedSpecial data processing applicationsUser privacyClient-side
The invention provides a method for protecting position privacy based on a cache. According to the current position of a mobile user, information point data quite high in using possibility in future is cached, a client side first retrieves the local cache to solve user inquiry, the cache misses the hit, then the inquiry is sent to an LBS server, the processing rate of inquiry is increased, meanwhile, the communication frequency between the client side and the server is reduced, and user privacy protection is enhanced. The invention further provides a distance hierarchical tree index structureand a maximum distance replacement algorithm suitable for the cache. The rate can be effectively increased when the cache is retrieved, and the cache hit ratio is increased. The method is simple in realization process and easy to operate.
Owner:CENT SOUTH UNIV
Client and server communication method capable of protecting geographic position privacy
ActiveCN105681362AProtect location privacyEasy to operateLocation information based serviceTransmissionGeolocationClient-side
The invention relates to a client and server communication method capable of protecting geographic position privacy. The client communication method comprises the following steps: a client generates service request information according to user operation; the client decomposes the service request information into n service request information subdata; the client encrypts the n service request information subdata and sends the encrypted subdata to n relay mobile terminals selected randomly by the client respectively, wherein the ith encrypted service request information subdata is sent to the ith relay mobile terminal, and the i is an integer equal to or larger than 1 and smaller than or equal to n; and after decrypting the received service request information subdata, the relay mobile terminal sends the decryption result to a server. According to the client and server communication method capable of protecting geographic position privacy, the geographic position privacy of any user can be protected when the user, based on geographic position information service, utilizes the client to use the service; and the method is simple to operate and wide in application range.
Owner:THE THIRD RES INST OF MIN OF PUBLIC SECURITY
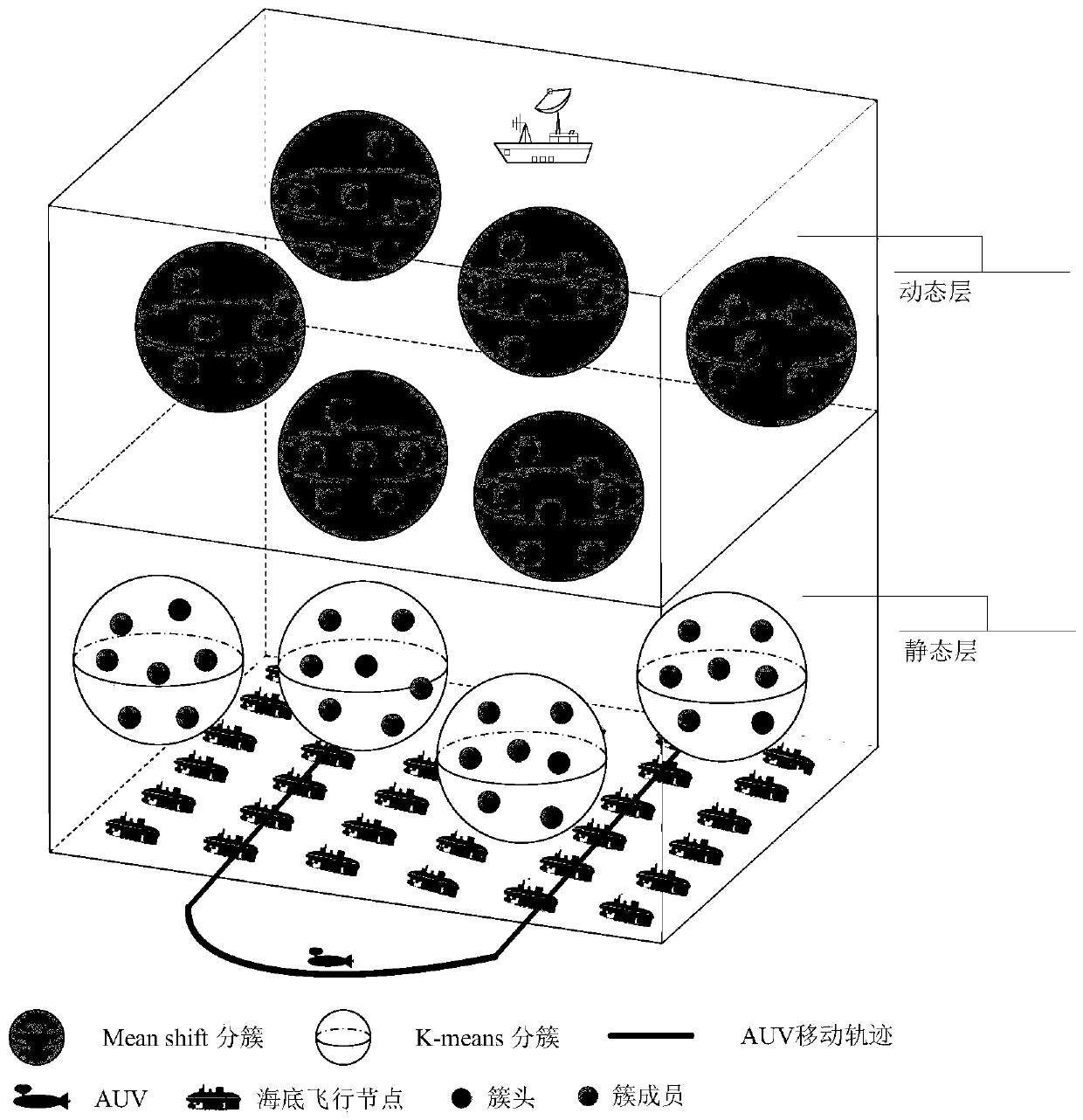
Source node privacy protection method based on position pushing in underwater acoustic sensor network
PendingCN111343631AEnhanced location awarenessProtect location privacySonic/ultrasonic/infrasonic transmissionNetwork topologiesData transmissionSource data
The invention relates to a multi-channel interference source node position privacy protection method in an underwater acoustic sensor network, which comprises the following steps of: firstly, respectively selecting a node clustering mode and a region division mode according to the characteristics of a static layer and a dynamic layer in combination with an Euckmann drifting model; secondly, in order to cope with monitoring attacks of attackers, combining source-pseudo data hybrid transmission and MAC layer multi-channel interference, covering a source data channel with multi-pseudo data channel interference, and protecting the position privacy of a source node; after multi-channel interference data transmission is utilized, enabling an underwater node to use a principal component analysistechnology to reduce the dimension of a sensing signal, enhancing the AUV movement sensing of the node, then predicting the AUV movement direction by using an equal SNR curve, and adjusting the working state of the node in time; and finally, enabling the AUV in each region to plan a data collection route through an ant colony algorithm, and transmitting data to the mobile base station after data collection. According to the method, the success rate of attack monitoring of an attacker can be hindered, the collection efficiency of underwater data is improved, the default known precondition of the node position is abandoned, and the protection of the source node position privacy in the underwater environment is enhanced.
Owner:HOHAI UNIV CHANGZHOU
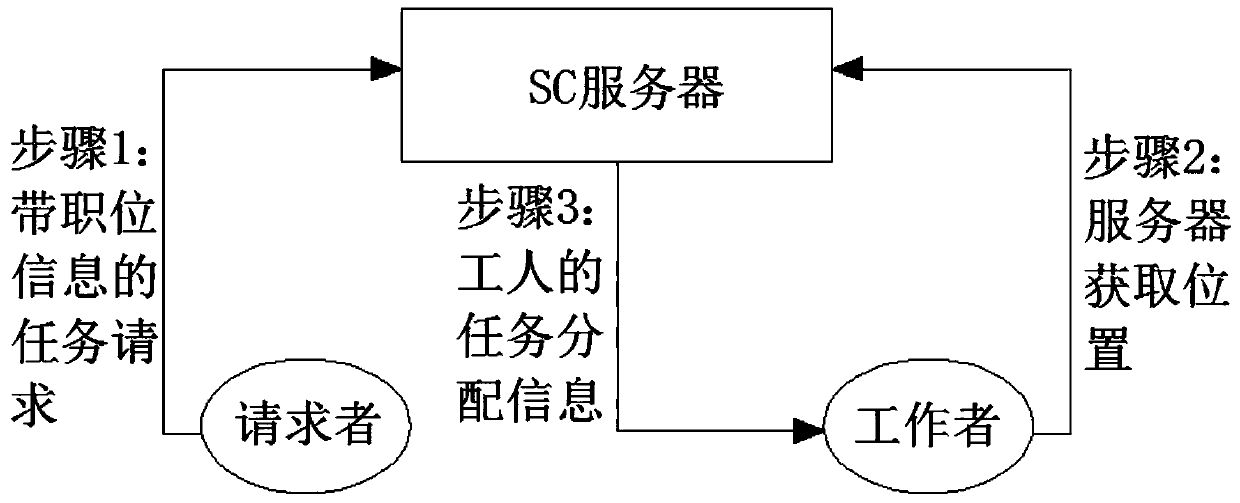
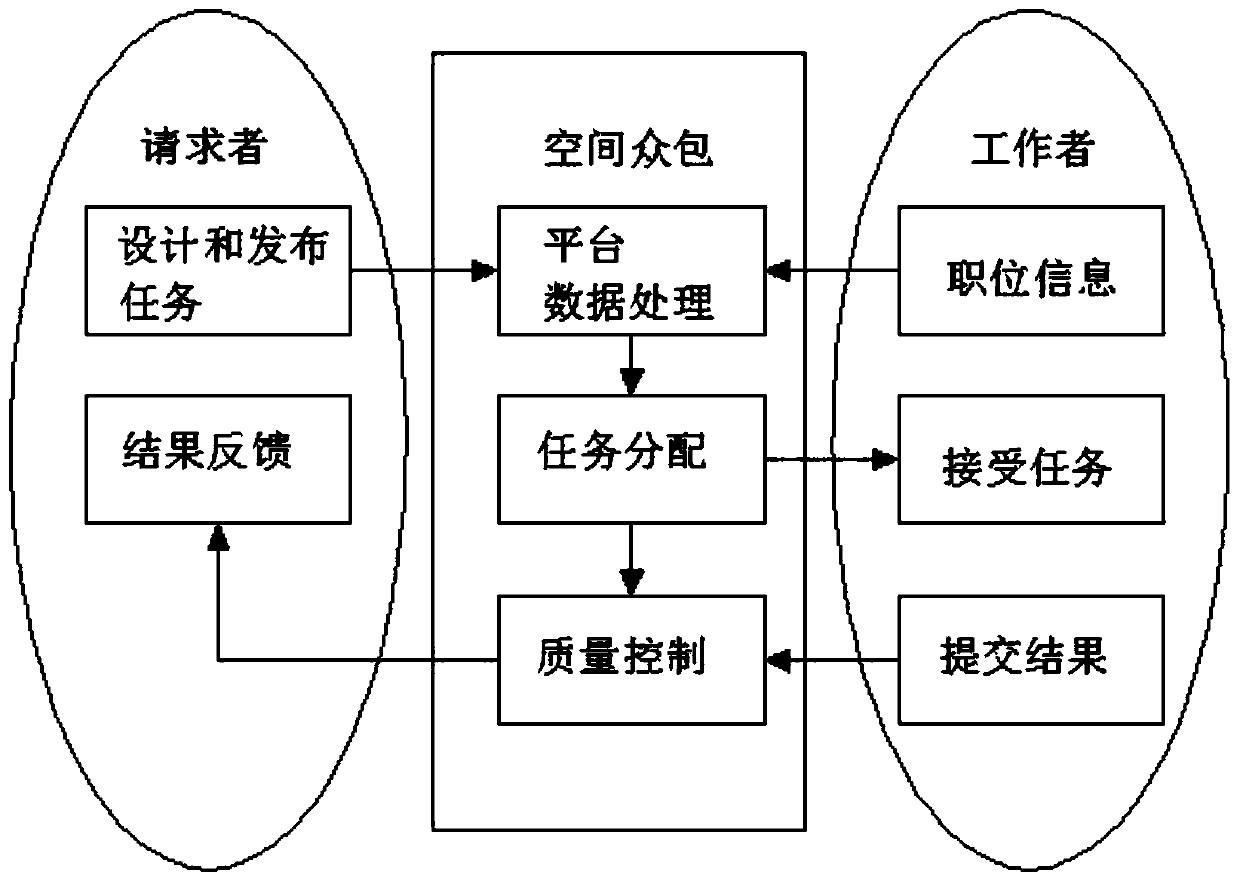
A spatial crowdsourcing quality control model is based on location privacy protection and decessor detection
PendingCN110110545AProtect location privacyQuality assuranceDigital data protectionOffice automationThird partyQuality control
The invention provides a spatial crowdsourcing quality control model based on position privacy protection and decessor detection. The method specifically comprises the following steps: taking a crowdsourcing platform as a credible third party, firstly formulating a position privacy protection strategy of a worker according to a task issued by a requester, then carrying out k anonymity fuzzy on position privacy submitted by the worker, and transmitting protected position information to the requester; using the trained ELM to carry out common worker and spammer classification detection on the test data; and estimating an error rate by using an EM algorithm, and estimating the error rate by using an expected maximum algorithm. In one aspect, a space k is employed And the anonymous algorithmis used for protecting the location privacy of general space outsourcing personnel. In another aspect, a spoofer is detected using an ELM algorithm, and an error rate is estimated using an EM algorithm. The efficiency of the model is simulated by selecting different parameters, and the result shows that the space crowdsourcing model provided by the invention can ensure the quality of crowdsourcingprojects on the premise of protecting the privacy of employees.
Owner:湖州学院
Big data based position privacy protection system with homomorphic encryption mechanism
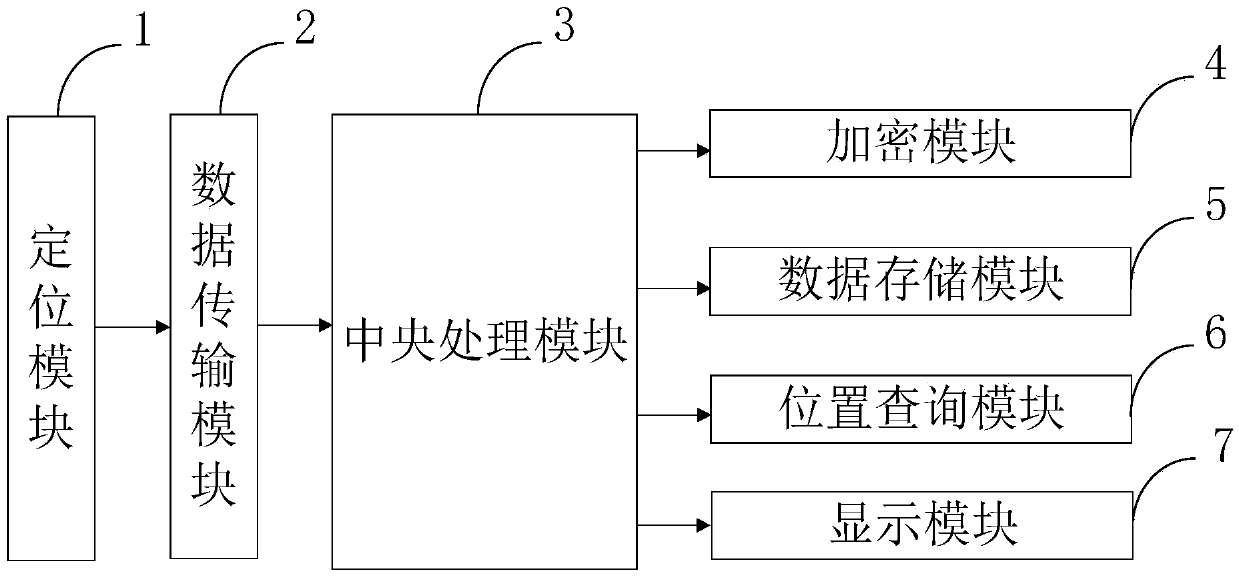
InactiveCN108650675AReduce computational overheadProtect location privacyLocation information based serviceSpecial data processing applicationsPrivacy protectionComputer module
The invention belongs to the technical field of privacy protection, and discloses a big data based position privacy protection system with a homomorphic encryption mechanism. The big data based position privacy protection system with the homomorphic encryption mechanism comprises a positioning module, a data transmission module, a central processing module, an encryption module, a data storage module, a position inquiry module and a display module. According to the invention, by the encryption module, in the same environment configuration, compared to the bootstrap process in an original scheme, the bootstrap process is reduced by 47%; safety of the scheme can be specified to the LWE problem, and can reach safety of 128 bits; and meanwhile, according to the invention, a cloud server and ahomomorphic encryption algorithm are introduced by the position inquiry module, a user can obtain a corresponding inquiry result only by implementing homomorphic encryption for once, homomorphic multiplication for once and subtraction operation for once, so that calculation cost of the user is reduced.
Owner:XUCHANG UNIV
Position privacy protection method in Internet-of-Things authentication
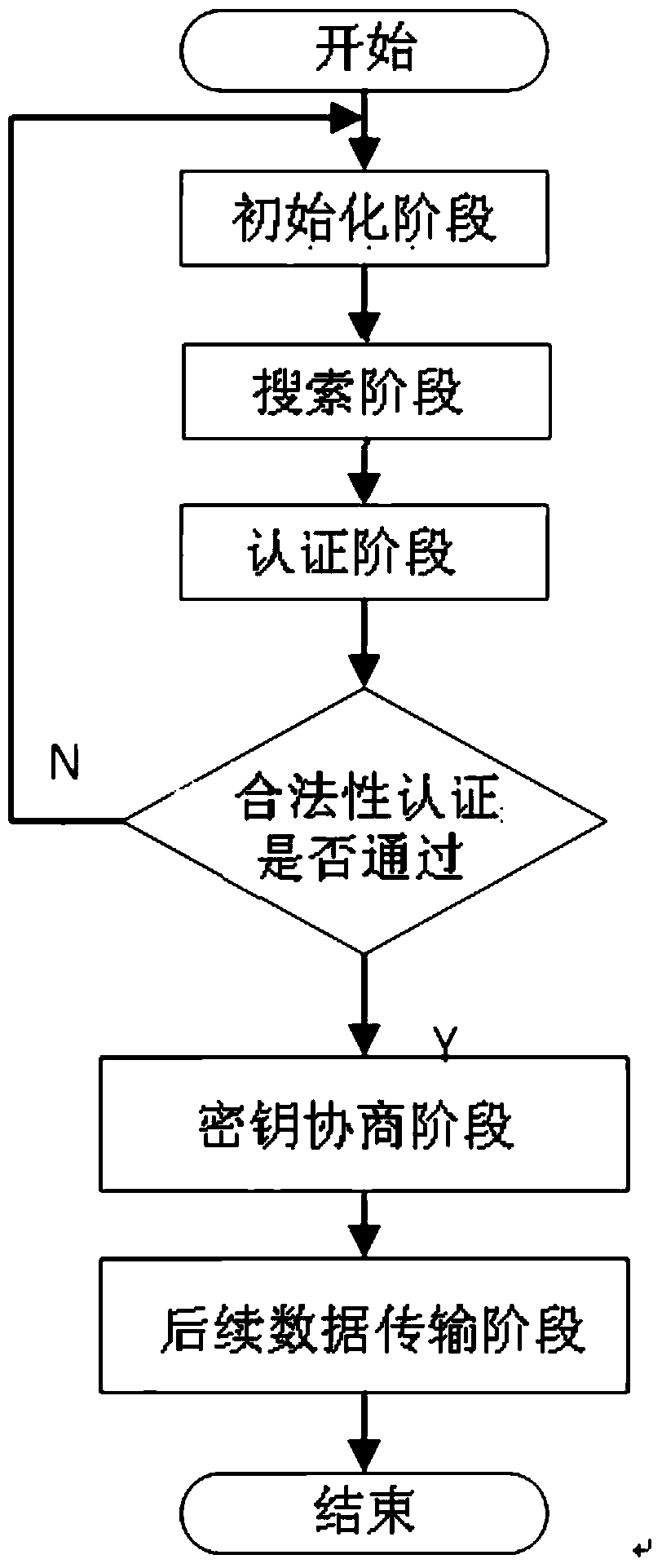
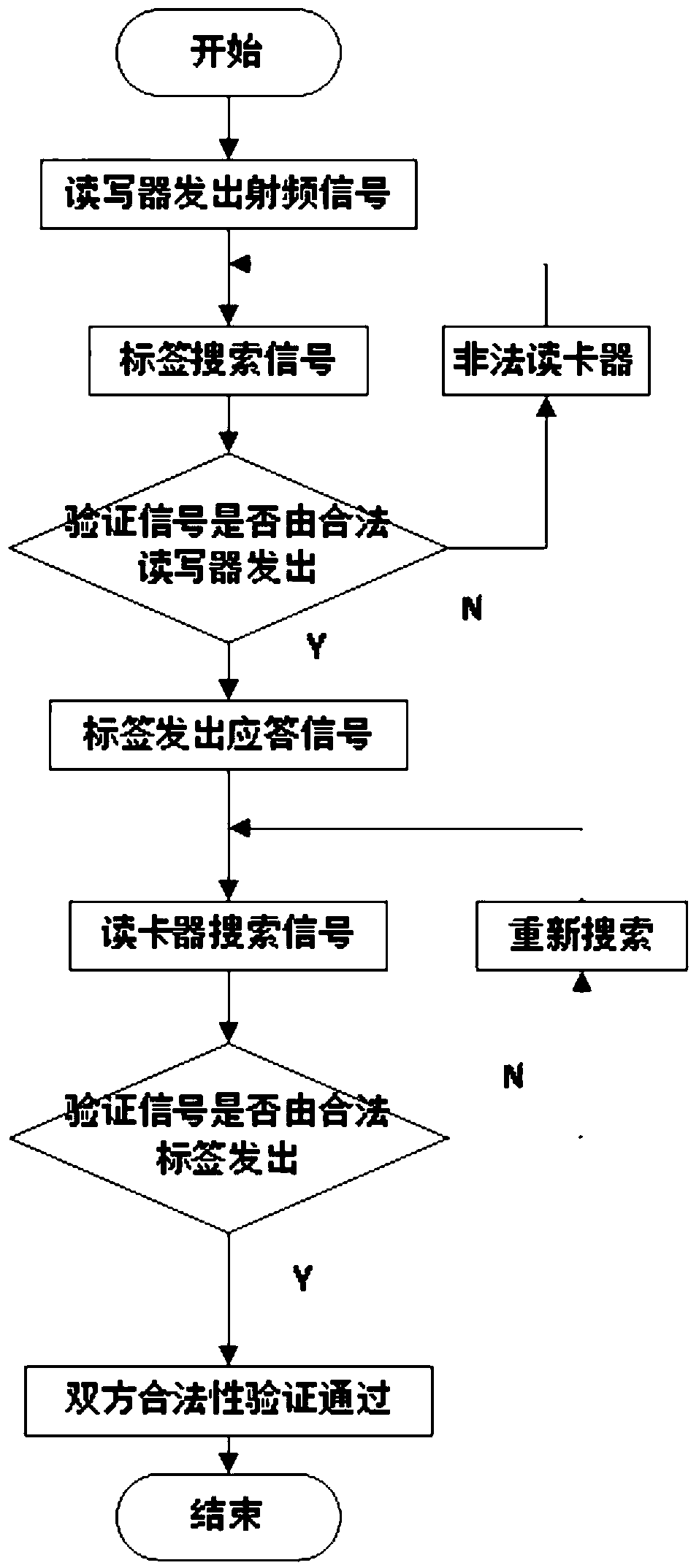
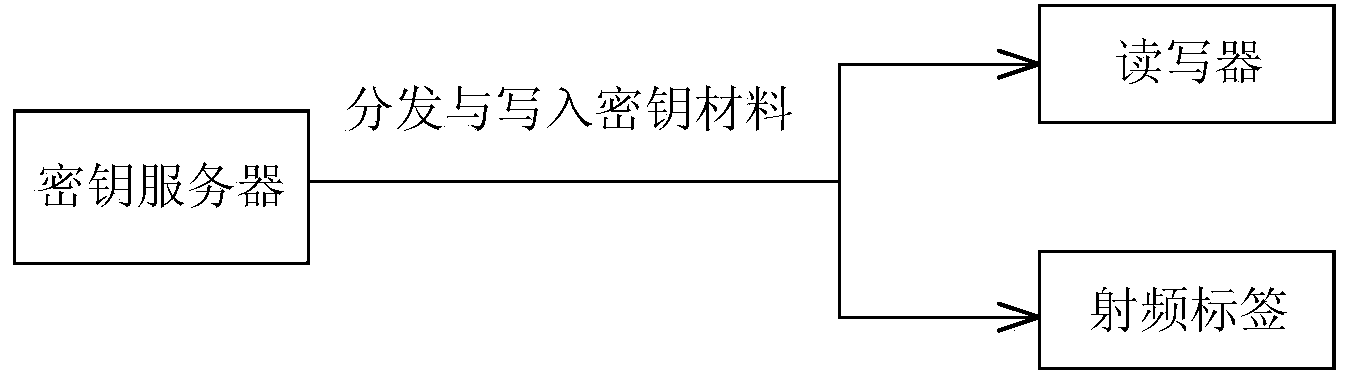
ActiveCN103763106AProtect location privacy and securityTake computing power into considerationKey distribution for secure communicationUser identity/authority verificationPrivacy protectionThe Internet
The invention discloses a position privacy protection method in Internet-of-Things authentication, and belongs to the technical field of Internet-of-Things safety. The position privacy protection method includes the following steps: (1) secret key distribution is carried out: secret key contents are distributed from a secret key server to a radio frequency tag and a read-writer; (2) searching and authentication are carried out: identity encryption is carried out through a designed square root algorithm, and then the reader-writer is in data communication with the radio frequency tag to complete identity authentication; (3) a shared secret key is generated: the reader-writer and the radio frequency tag respectively calculate to obtain the shared secret key, and communication information such as the ID of the radio frequency tag is transmitted through the secret key. According to the position privacy protection method, the position privacy safety of communication of a perception layer of the Internet of Things is guaranteed, namely, only the legal reader-writer can find and know the position of the radio frequency tag, and therefore the position of the radio frequency tag is hidden.
Owner:SOUTHEAST UNIV
Position privacy protection method based on game theory and block chain fusion
ActiveCN110505217AProtect location privacyProtect location privacy securityTransmissionInformation repositoryPrivacy protection
The invention discloses a position privacy protection method based on game theory and blockchain fusion, and the method comprises the following steps: 1, constructing a position manager which has a position information base, and setting an access threshold according to the tolerance degree of the leakage of the position information base; only when the probability of the user integrity is greater than the access threshold, the location manager cooperates with the user integrity; 2, establishing a reputation mechanism which comprises a user reputation value, a reputation level and earnings underdifferent reputation values, defining a strategy set of users and position managers and earnings obtained by the users and the position managers under different strategies based on the game theory, and performing Nash equilibrium derivation according to a game matrix of the users and the position managers to obtain the probability of user integrity; and 3, recording the whole game process by using the block chain, designing a punishment period, carrying out revenue reduction or blacklist pull-in punishment on the users in the punishment period, and constraining the self-profit behaviors of the users. According to the invention, the location privacy of the user can be effectively protected, and the cooperation between the user and the location manager is promoted.
Owner:HEBEI UNIVERSITY OF SCIENCE AND TECHNOLOGY
Auxiliary positioning method, device and equipment based on reference point position
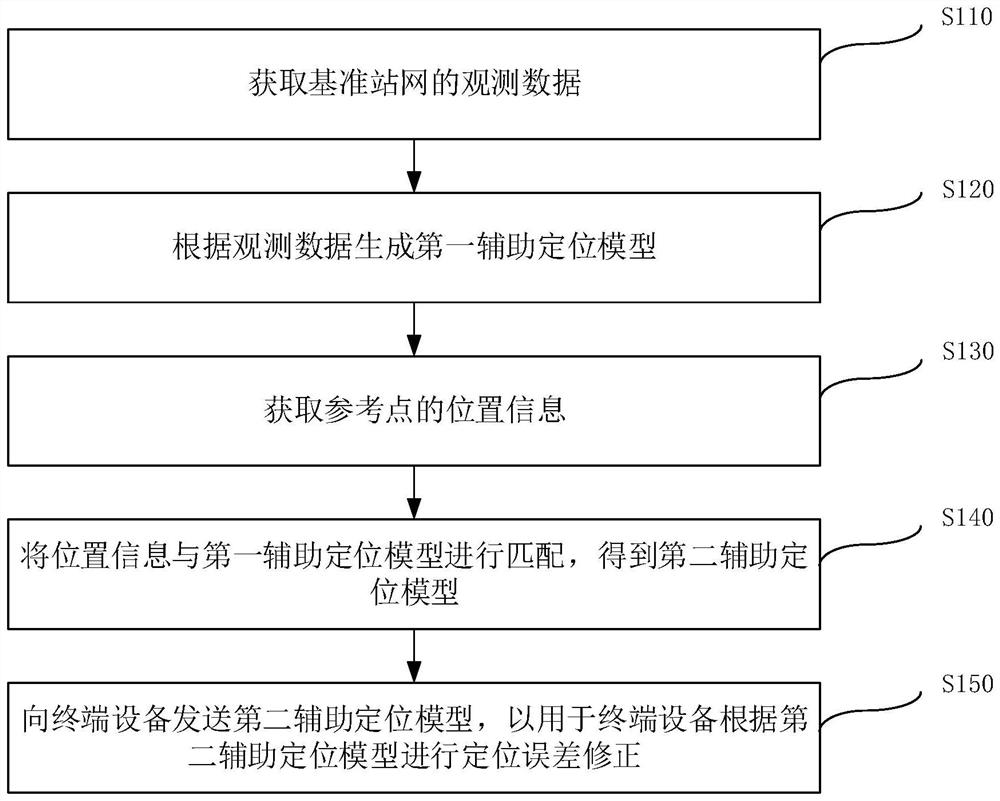
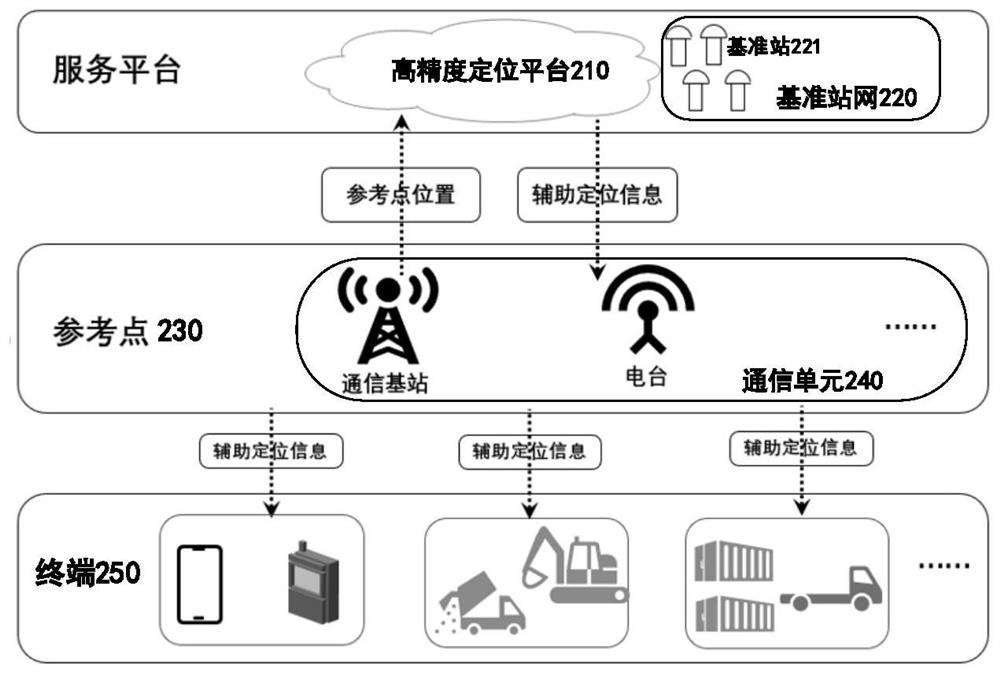
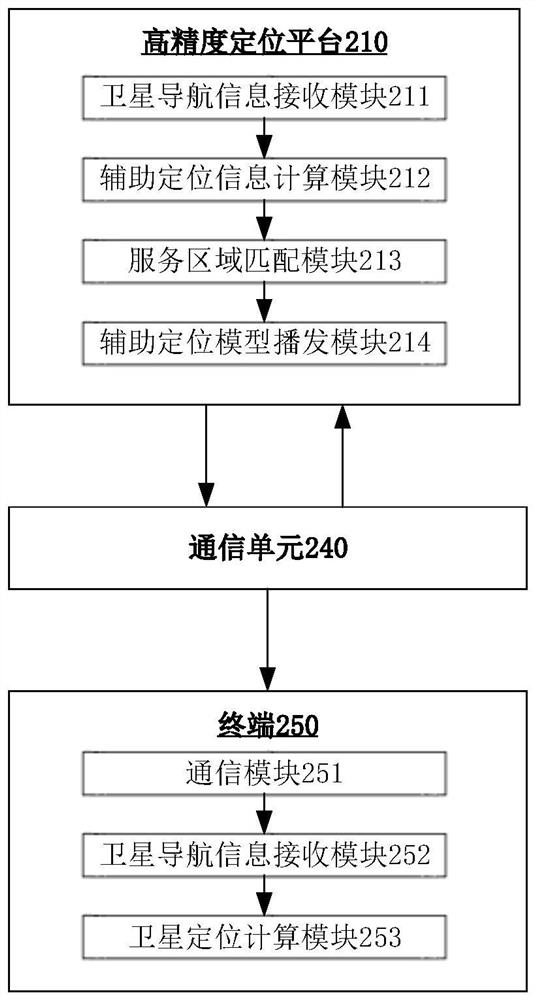
ActiveCN113075714AGuaranteed validityGuaranteed accuracySatellite radio beaconingCommunication unitObservation data
The embodiment of the invention provides an auxiliary positioning method, device and equipment based on the position of a reference point, and the method comprises the steps: obtaining the observation data of a reference station network, generating a first auxiliary positioning model according to the observation data, obtaining the position information of the reference point, and matching the position information of the reference point with the first auxiliary positioning model to obtain a secondauxiliary positioning model, and sending the second auxiliary positioning model to the terminal equipment, so that the terminal equipment can carry out positioning error correction according to the second auxiliary positioning model. According to the embodiment of the invention, the user does not need to upload own position information, so that the position privacy of the user is protected while the effectiveness of the auxiliary positioning model of the user position is ensured, a communication unit and a satellite signal transceiving unit do not need to be deployed at a reference point at the same time, electromagnetic interference between a communication signal and a satellite signal is avoided, and the accuracy of the obtained auxiliary positioning model is ensured, so that the positioning accuracy of the terminal equipment is improved.
Owner:CHINA MOBILE SHANGHAI ICT CO LTD +2
Path sharing method and system for privacy protection
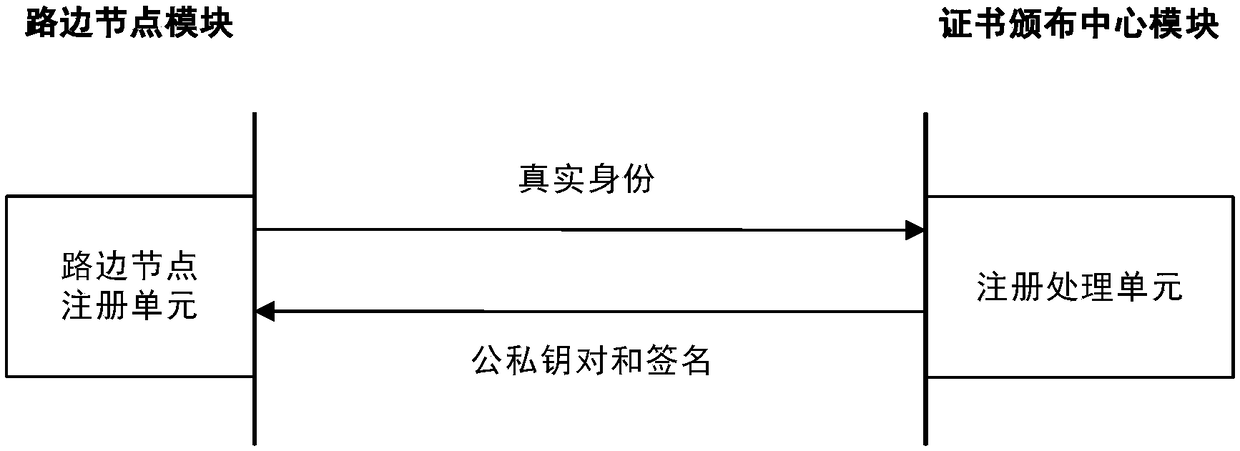
ActiveCN109309681AProtection securityGuaranteed confidentialityEncryption apparatus with shift registers/memoriesUser identity/authority verificationLocation sharingTeam communication
The invention discloses a path sharing method and system for privacy protection, and belongs to the technical field of anonymous authentication and privacy protection. The method comprises the following steps that a user registers with a certificate issuing center, and a queue leader user sends a team request to a roadside node and sends a team name, a team communication key and a destination to members of the team; a team member user sends a team adding request to the roadside node; and the roadside node anonymously authenticates the identity of the user, verifies the request, matches the queue leader user and the team member user, uploads team information after team formation to a cloud service provider, acquires path information, and returns the path information and team information tothe user, and the users in the team share avatars, positions and tracks in real time. The method and the system have the beneficial effects that user privacy, including identity, location and track isprotected, and team member camouflage attacks, team peek attacks and multiple group attacks of opponents are resisted. Compared with an existing location sharing method, the path sharing method has the advantage that the computing overhead and communication overhead are reduced. Compared with an existing path sharing system, the path sharing method has the advantage that security and privacy protection is provided.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
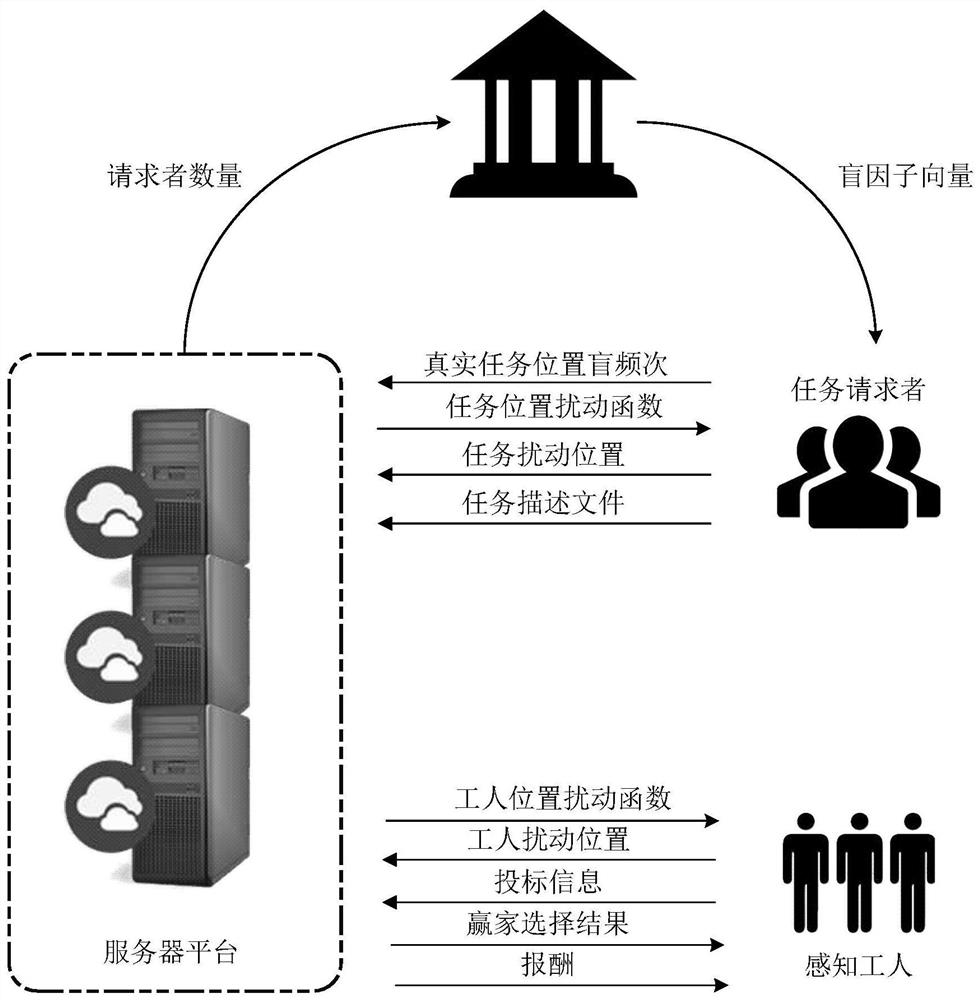
Mobile crowd sensing excitation method, device and system and storage medium
ActiveCN112967118AMeeting Privacy NeedsSatisfy mission quality requirementsDiscounts/incentivesDigital data protectionSimulationServer
The invention discloses a mobile crowd sensing excitation method, device and system and a storage medium. The system comprises a trusted center, a task requester, a sensing worker and a server platform. The trusted center is used for generating a blind factor key and helping the server platform to obtain probability distribution of a real position of a task; the task requester is used for generating a task blind frequency vector, generating a task disturbance position and sending a result and a task description file to the server; the sensing worker is used for disturbing the position of the sensing worker and sending the disturbed position and bidding information to the server; and the server platform is used for counting the real position distribution of the task, issuing a position disturbance function, receiving a disturbance position to estimate the position of the task and generate a bidding task set of the workers, and selecting a winner from the bidding workers and deciding a reward. According to the method, the ideal property of auction and the privacy of bilateral positions are met, and approximate minimization of social cost under an untrusted platform is realized.
Owner:SOUTH CHINA UNIV OF TECH
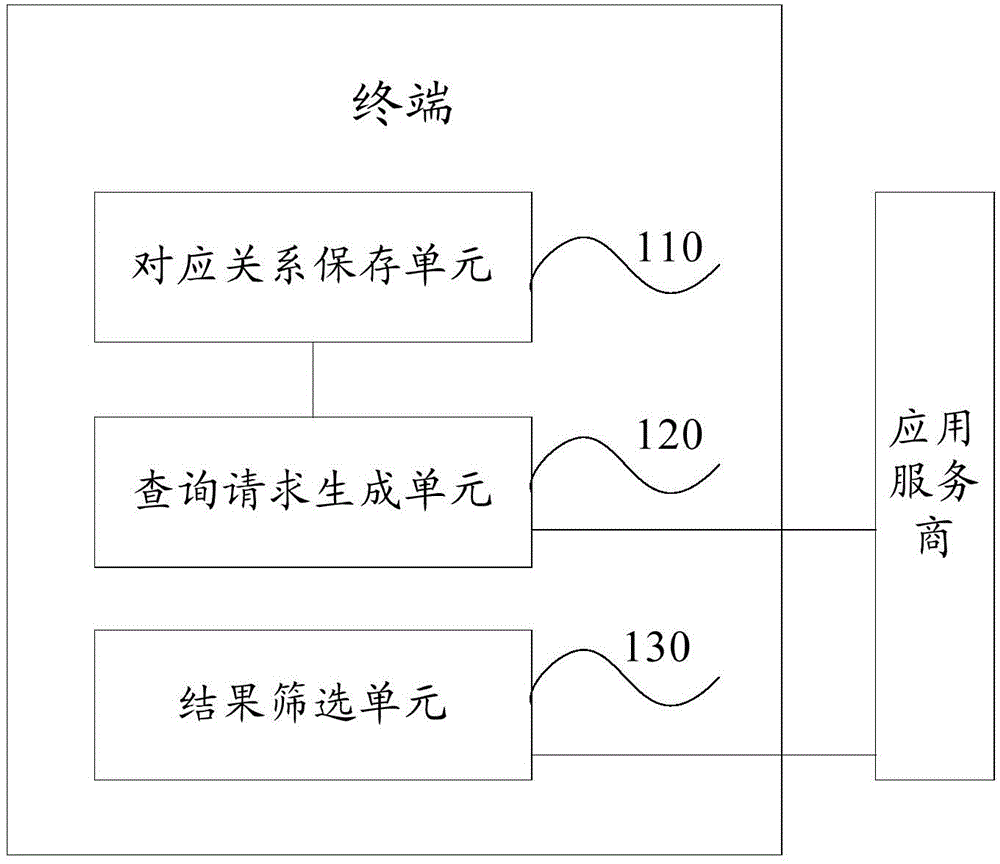
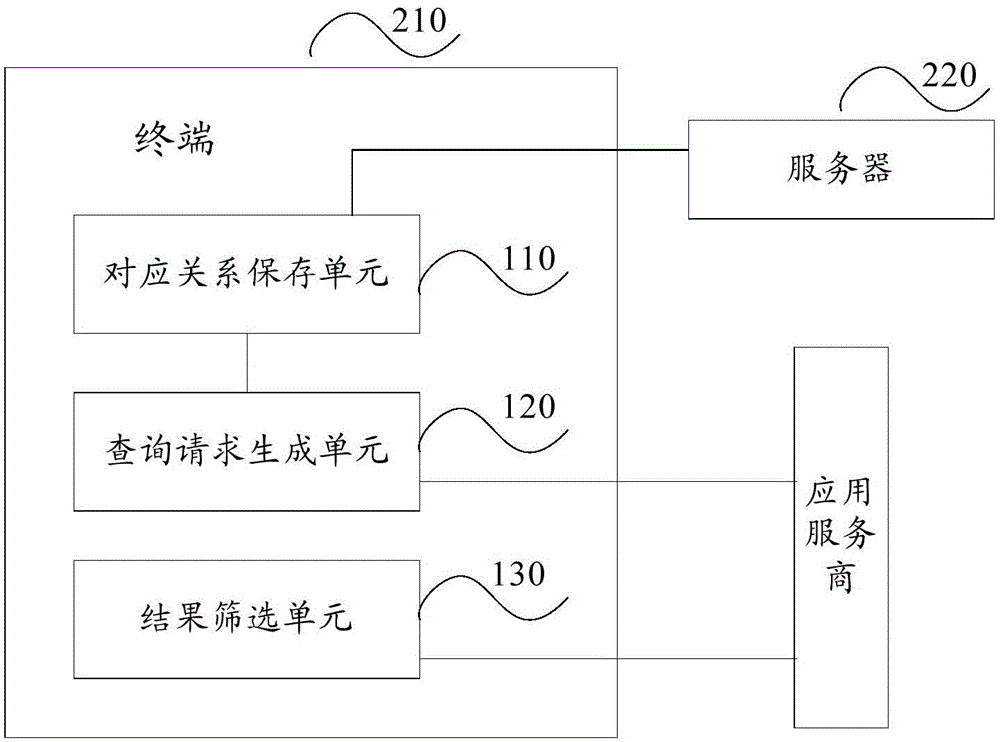
Method, terminal and system for protecting user position privacy
ActiveCN105472547APrecise location serviceProtect location privacyLocation information based serviceAmbiguityApplication service provider
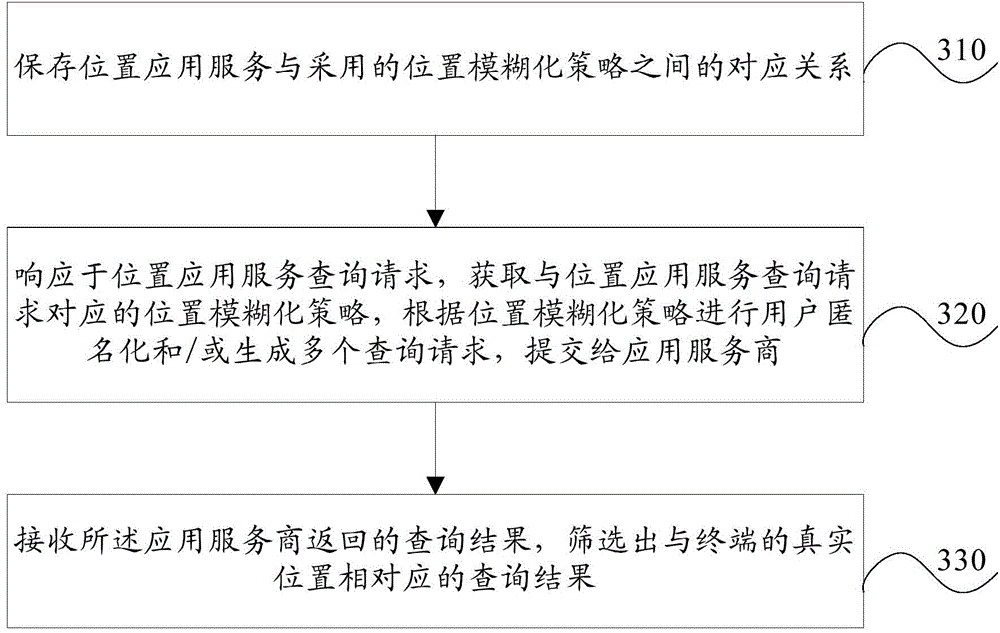
The invention discloses a method, a terminal and a system for protecting a user position privacy. The method comprises the steps of storing a correspondence between a position application service and an adopted position ambiguity strategy; in response to a position application service query request, acquiring a position ambiguity strategy which corresponds with the position application service query request, performing user anonymization and / or generation of a plurality of query requests according to the position ambiguity strategy, wherein the plurality of query requests comprise position information which is related with the true position of the terminal, and transmitting the plurality of query requests to an application service provider; receiving a query result which returns from the application service provider, and screening out a query result which corresponds with the true position of the terminal. The method, the terminal and the system supplies an accurate position service for a user and furthermore protects the user position privacy.
Owner:CHINA TELECOM CORP LTD
Crowd-sourcing sensing position privacy protection payment method based on license chain
The invention provides a crowd-sourcing sensing position privacy protection payment method based on a license chain. A crowd-sourcing sensing platform encrypts core privacy information of participantsby using asymmetric encryption; a public key and a private key are matched to cross the crowd-sourcing platform to transmit data, and the crowd-sourcing platform cannot obtain core privacy information of participants; the crowd-sourcing sensing platform sends the account transfer request to an anonymous payment network CrowdChain for account transfer; the anonymous payment network CrowdChain useszero knowledge proof to ensure complete privacy and anonymity of the transfer transaction, wherein a license chain is used as a carrier of the account transfer system. During data transmission, onlydata necessary for a task is transmitted, and user identity information is not bound. A message transmission mechanism for sending the key message to the third party across the platform is realized. Adigital asset which can be claimed only by using a hash digest of a participant wallet address is generated. According to the payment method, the position privacy of the user is effectively protected.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
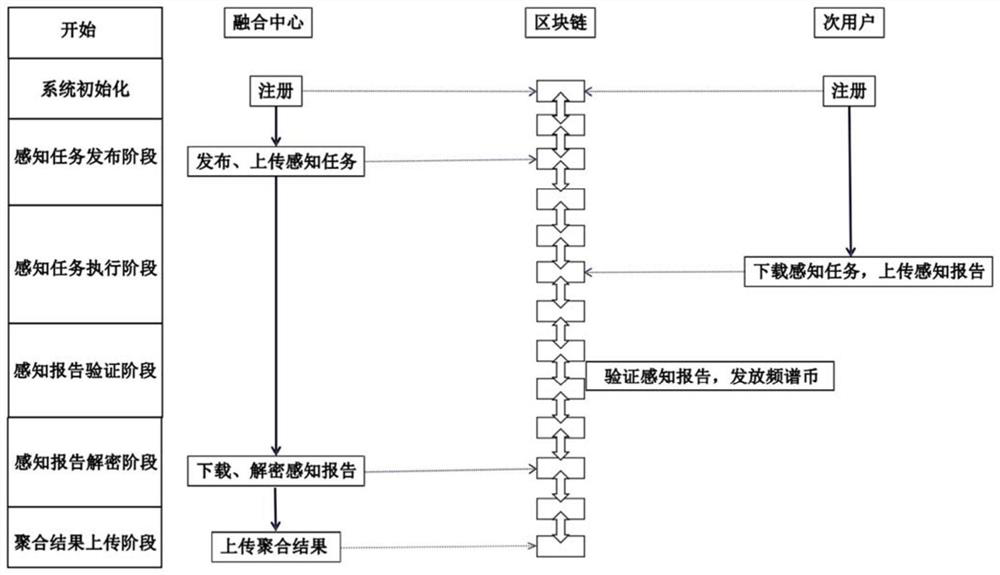
Cooperative spectrum sensing location privacy protection method based on blockchain
ActiveCN113079140AProtection securityPrevent theftKey distribution for secure communicationPublic key for secure communicationFusion centerTimestamp
The invention discloses a cooperative spectrum sensing location privacy protection method based on a blockchain, which utilizes the anonymity of the blockchain to enable a secondary user to anonymously upload a sensing report to the blockchain, avoids the relevance between the sensing report and the secondary user, prevents a fusion center from associating the sensing report with the secondary user during decryption, and protects the security of the sensing report in the fusion process. The secondary user encrypts and signs the sensing report by using the elliptic curve cryptography technology, so that the sensing report is prevented from being stolen and tampered in the transmission process, and the confidentiality and integrity of the sensing report in the transmission process are ensured. According to the method, the sensing report is prevented from being replayed in the transmission process by using the timestamp, and the timeliness of the sensing report in the transmission process is ensured. According to the method, the automatic verification characteristic of a smart contract is utilized, and the smart contract, instead of the fusion center, automatically verifies the digital signature of the sensing report, so that the calculation overhead of the fusion center is reduced.
Owner:FUJIAN NORMAL UNIV
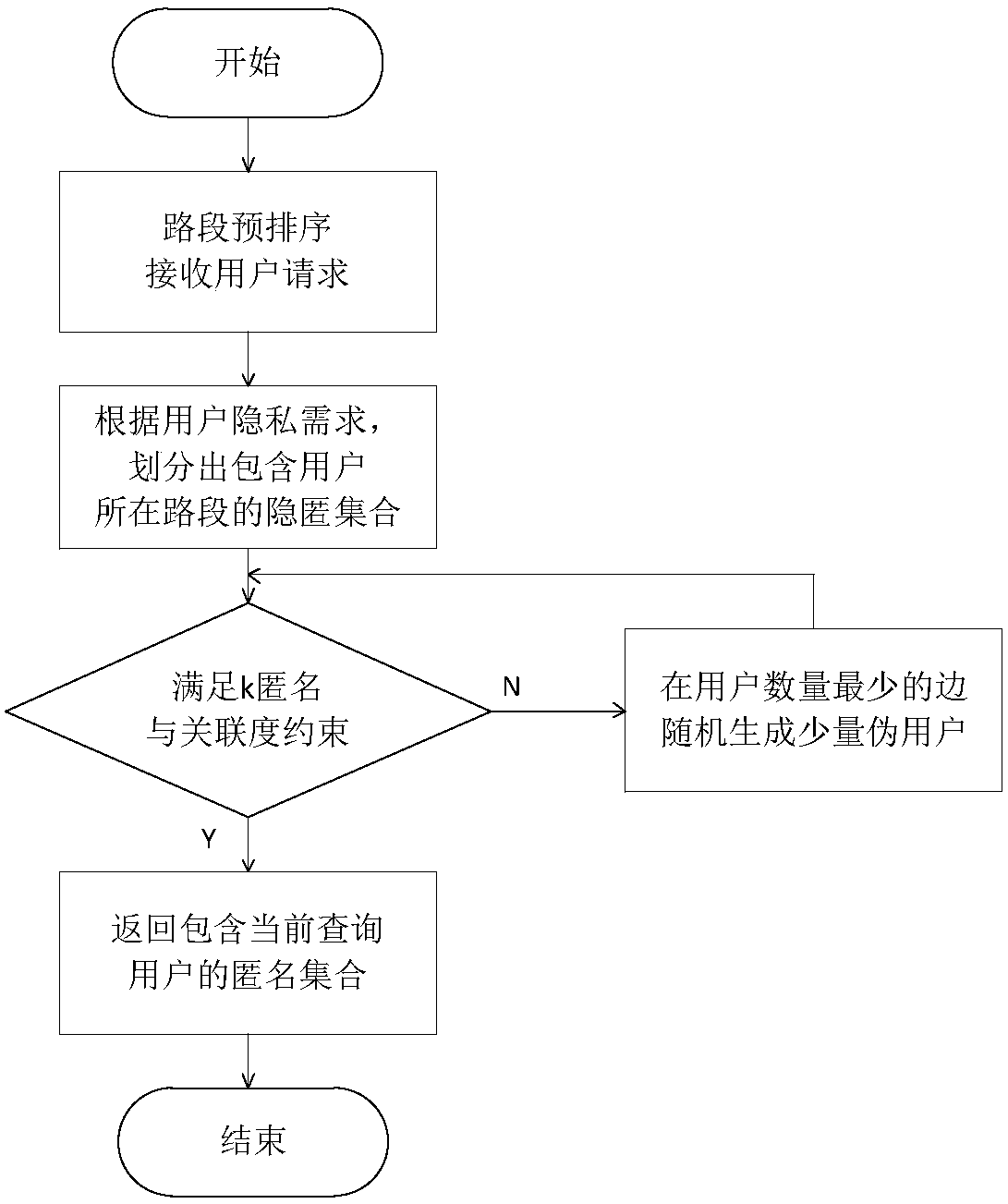
Location anonymous method for resisting replay attack in road network environment
ActiveCN108040321AReduce query costQuick service responseLocation information based serviceSecurity arrangementInference attackRoad networks
The invention discloses a location anonymous method for resisting a replay attack in a road network environment. The location anonymous method for resisting the replay attack in the road network environment comprises the steps that: (1), road sections are pre-processed; the road sections are pre-sorted for one time by adoption of breadth-first sorting; and the location query cost is reduced; and (2), an anonymous set is constructed; an equivalent partition is obtained from the sorted road sections; an anonymous and equivalent road section concealment set is obtained; various road sections in the concealment set are equalized by adoption of a pseudo-user adding mechanism, so that the edge weight association degree satisfies a pre-set threshold value; and thus, a privacy threat due to an edge weight inference attack also can be prevented while the replay attack is resisted. By means of the location anonymous method for resisting the replay attack in the road network environment disclosedby the invention, the common replay attack and edge weight inference attack in the road network environment can be resisted while the concealment set can be effectively generated; and furthermore, the method is low in query cost and quick in service response.
Owner:HOHAI UNIV
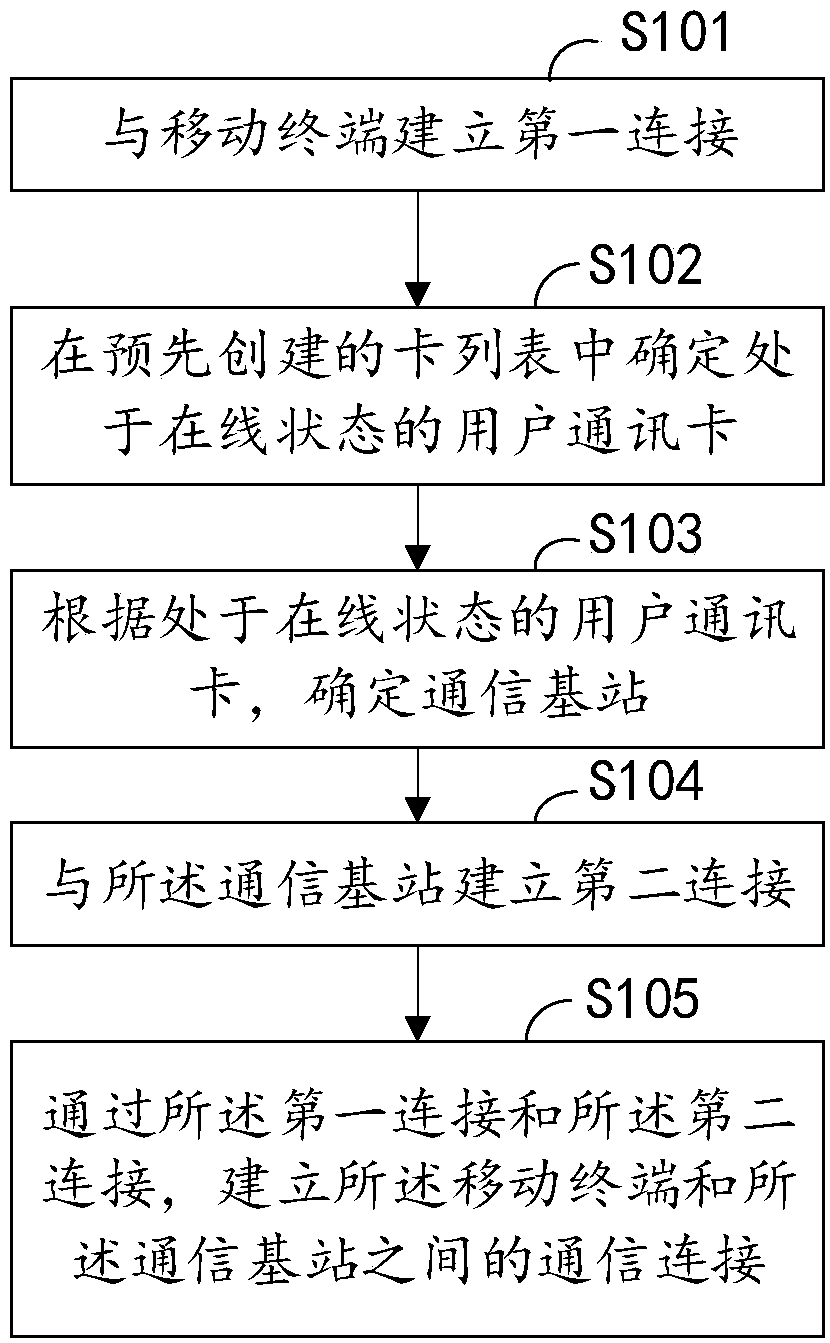
Mobile user location privacy protection method and mobile gateway
ActiveCN108307380AAvoid real-time location trackingProtect location privacyConnection managementLocation information based servicePrivacy protectionNetwork communication
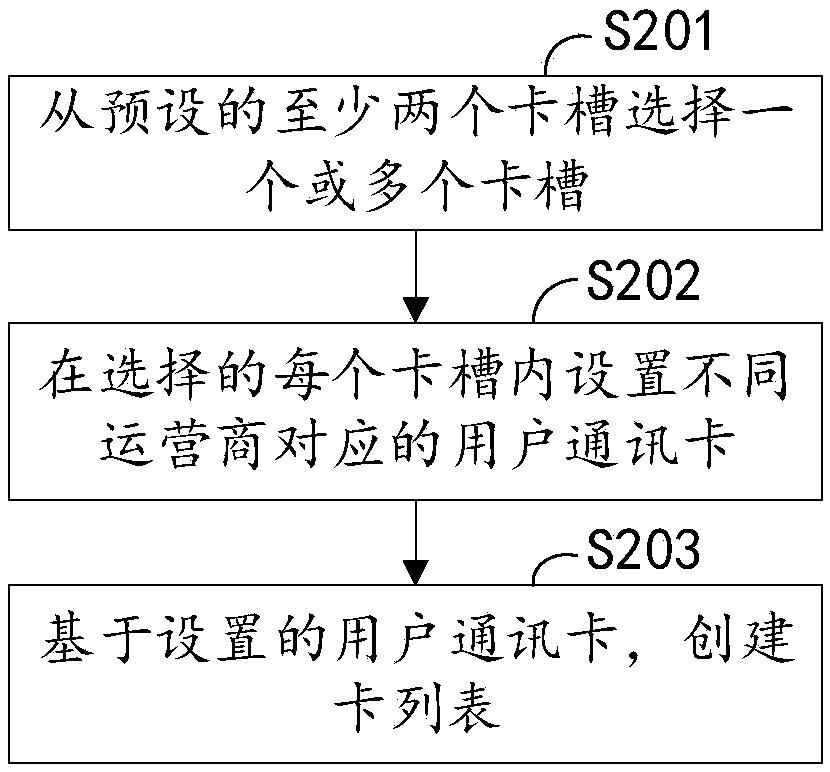
The invention discloses a mobile user location privacy protection method and a mobile gateway. The method comprises the following steps: establishing first connection with a mobile terminal; determining a user communication card in online state in a pre-created card list; determining a communication base station according to the user communication card in the online state; establishing the secondconnection with the communication base station; and establishing the communication connection between the mobile terminal and the communication base station through the first connection and the secondconnection. The mobile gateway comprises a wireless module, at least two card slots, at least one communication module, a memorizer and a processor. The different operator network is selected in eachcommunication based on the mobile gateway with the multi-card multi-mode multi-operator, so that the malicious attacker for single operator cannot acquire the complete mobile user location track information, the hop multi-operator network communication is realized, the mobile user cannot be positioned and tracked in real time, and the location privacy of the user is protected.
Owner:CHINA ACADEMY OF ELECTRONICS & INFORMATION TECH OF CETC
LBS service privacy protection method based on differential privacy
ActiveCN111797433AProtect location privacyAvoid questions that are not entirely believableDigital data protectionGeographical information databasesComputer networkData set
The invention discloses an LBS service privacy protection method based on differential privacy. A query k-anonymity set conforming to differential privacy is constructed according to background knowledge of a cluster where a user is located and an area where the user is located obtained in a DP-(k1, l)-means algorithm, and the anonymity set is sent to an LSP, so that leakage of a real query request of a user is avoided, the query privacy of the user is protected, and reasoning attacks and space-time correlation attacks of attackers are avoided. In a DP-k2-anonymy algorithm, according to the time characteristics, query requests sent in the same time period t are selected to construct a query k-anonymity set, and the data set is processed by using an index mechanism, so that the reasonability of the query requests in time is ensured, and the privacy of users is protected from being leaked.
Owner:LIAONING UNIVERSITY OF TECHNOLOGY
Mobile user position privacy protection method for avoiding attacks performed through circular region overlapping parts
InactiveCN105554743AProtect location privacyReduce the likelihood of an attackLocation information based serviceSecurity arrangementAttackPrivacy protection
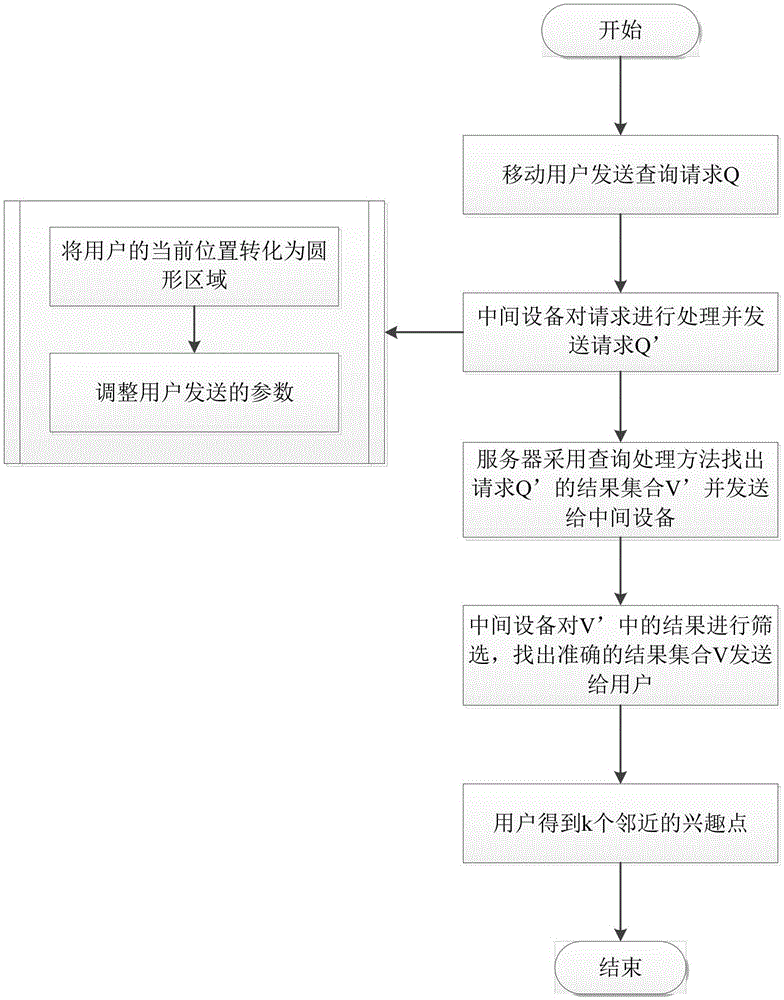
The invention provides a mobile user position privacy protection method for avoiding attacks performed through circular region overlapping parts, and relates to the field of position privacy protection. The method comprises the following steps that: firstly, a user sends a request Q (a current position of the user, the number of query results and the like) to intermediate proxy equipment; the intermediate equipment converts a real position of the user into a circular region, specifies a value which is greater than a confidence level needed by the user and the number of query results, and sends a request Q' to an LBS (Location Based Service) server provider; an LBS finds points of interest satisfying a condition with a query processing method, puts the points of interest satisfying the condition into a set V', and returns the V' to the intermediate equipment; and the intermediate equipment screens the V', and returns a screening result to the user. Through adoption of the method, the attacks performed through the circular region overlapping parts are effectively avoided when the user queries a server, and the position privacy of the user can be protected more accurately. The mobile user position privacy protection method is suitable for protecting privacy of the user position when the user queries surrounding points of interest.
Owner:NANJING UNIV OF INFORMATION SCI & TECH
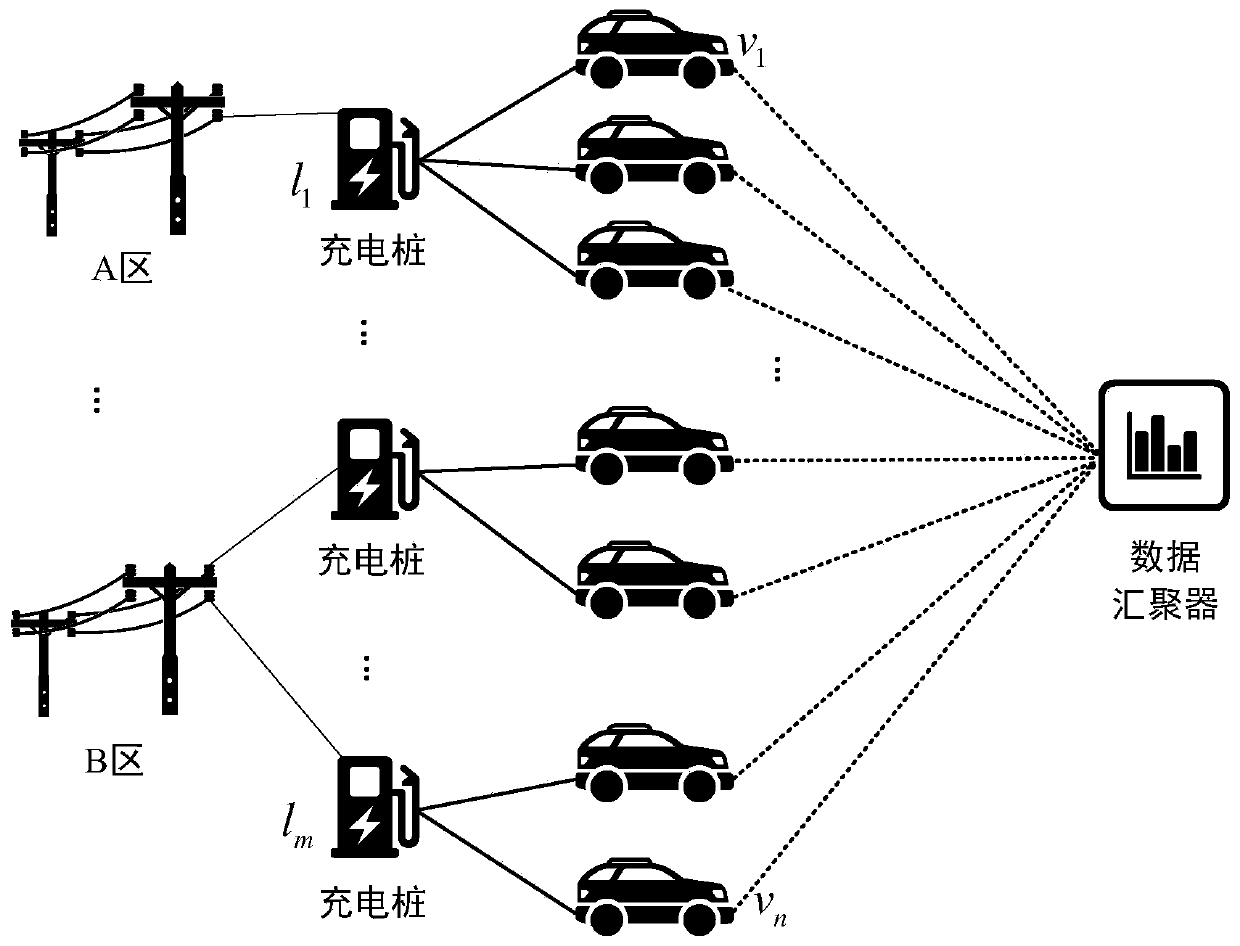
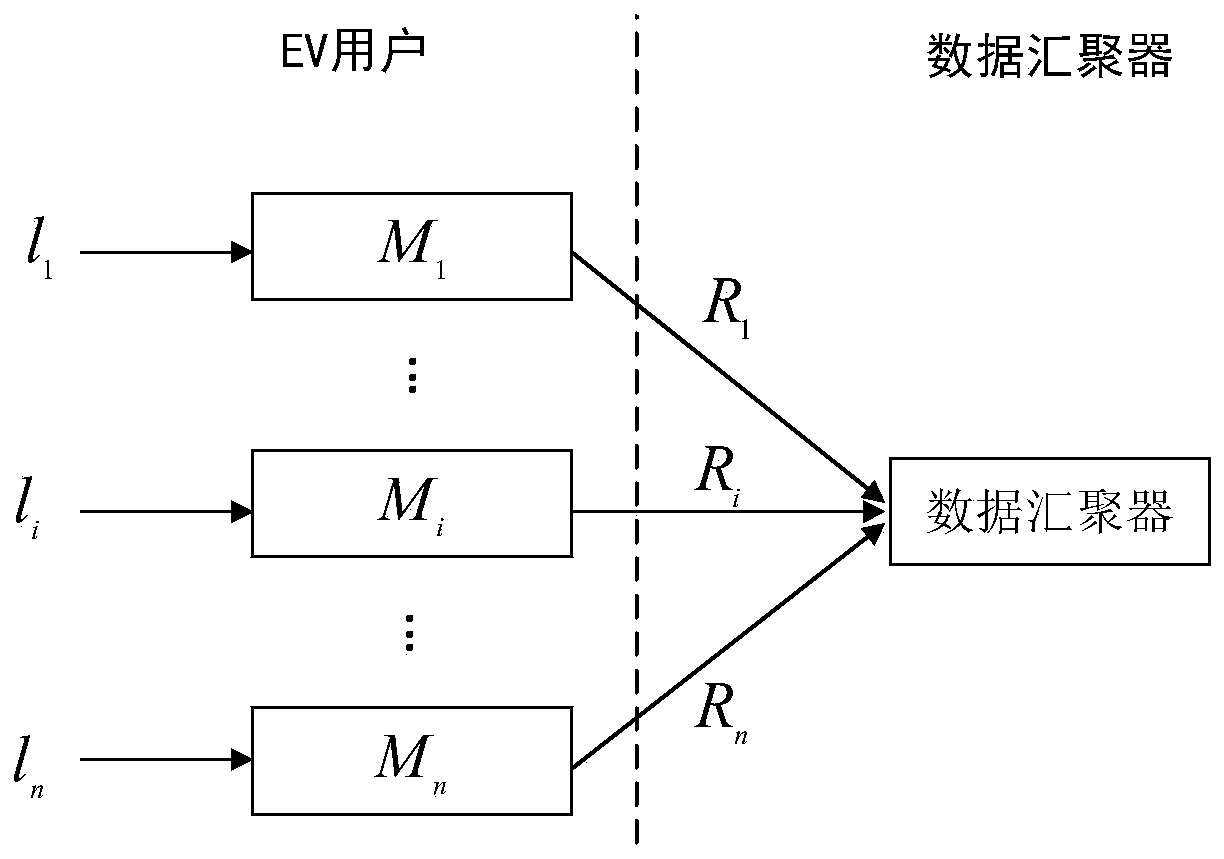
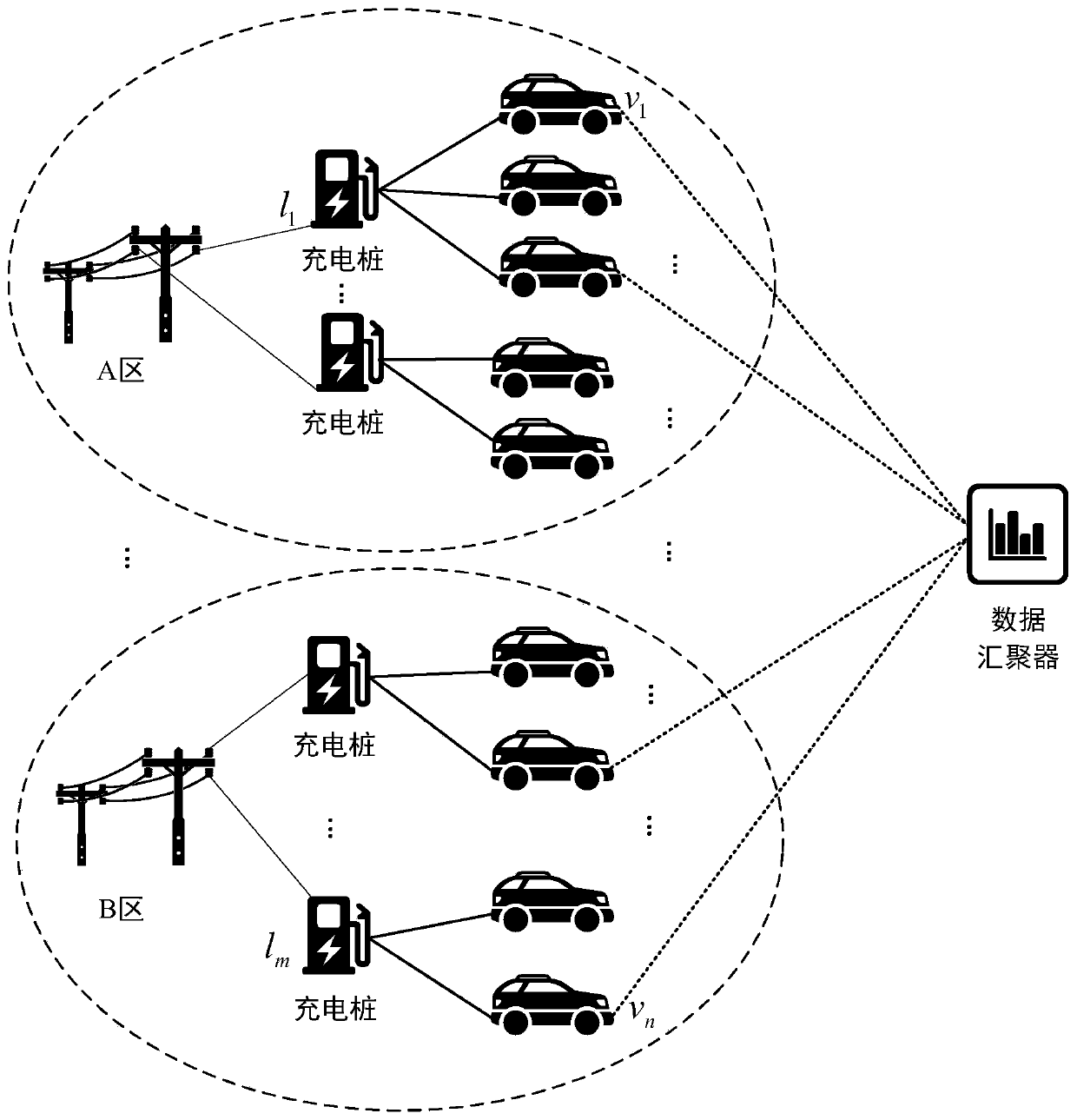
An electric vehicle charging position data privacy gathering method based on local differential privacy
ActiveCN109886042AImprove usabilityIncrease sample sizeDigital data protectionDifferential privacyData aggregator
The invention relates to an electric vehicle charging position data privacy convergence method based on local differential privacy. According to the method, on the basis of analysis of application scenarios and charging position data characteristics, a novel Bayesian multi-pseudo local differential privacy method and a method based on power supply line partitioning are combined, and the electric vehicle charging position data privacy convergence method is designed. According to the method, the disturbance output sample size is increased through a Bayesian multi-pseudo method, and meanwhile, the availability of an electric vehicle charging position data aggregation result is effectively improved in a manner of reducing a privacy position domain by partition.
Owner:WUHAN UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com