Homomorphic encryption-based position privacy querying method
A technology of homomorphic encryption and query method, which is applied in homomorphic encryption communication, secure communication device, and key distribution, which can solve the problems of mobile user privacy leakage, lower query accuracy, and user information leakage, so as to protect location privacy and reduce Computational overhead, the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] The technical solutions of the present invention will be described in detail below, but the protection scope of the present invention is not limited to the examples.
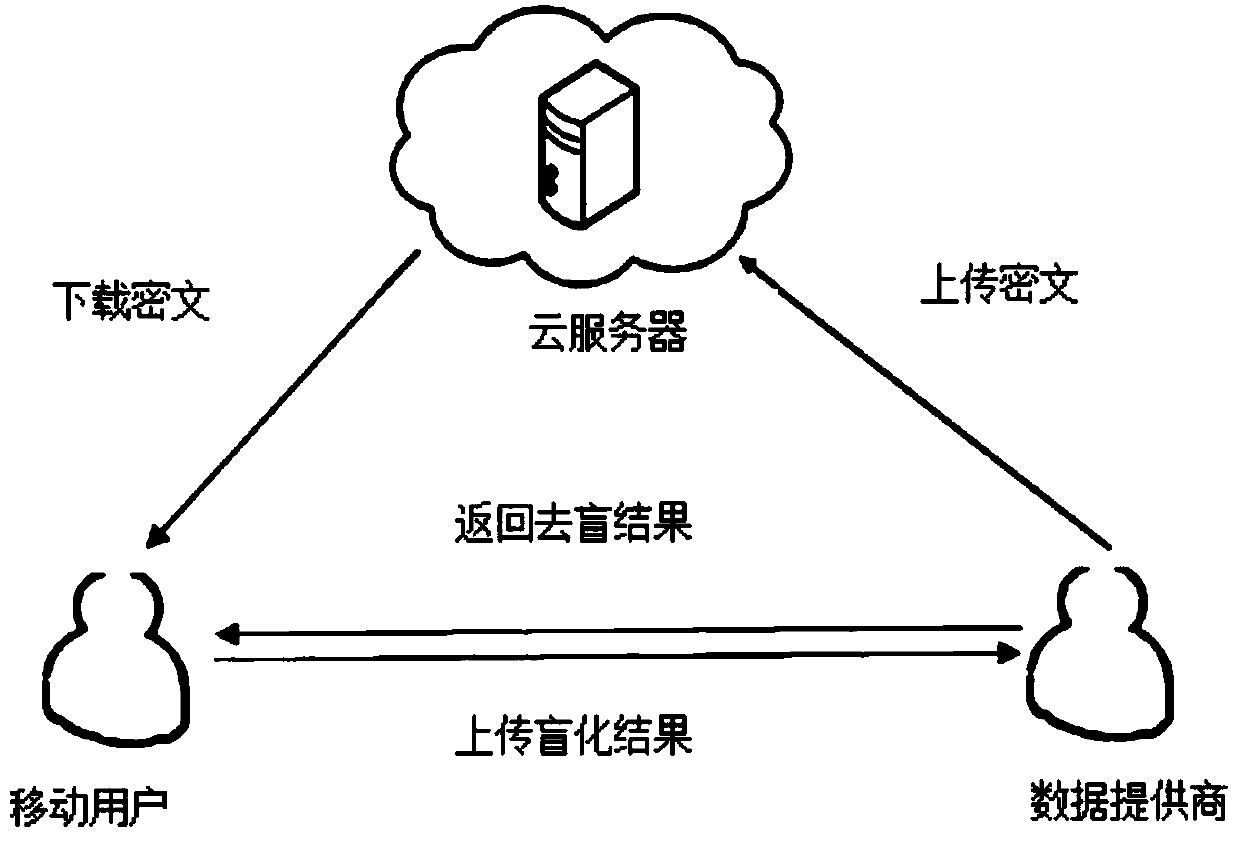
[0034] In this example, if figure 1 As shown, a location privacy query method based on homomorphic encryption is applied to a mobile Internet network environment composed of several mobile users, a data service provider and a cloud server. The specific entity model is as follows: figure 1 Shown: ① mobile user U. Make a service request to the data service provider according to your location; ②Data service provider SP. The data owner is responsible for receiving the service request of the mobile user U and responding accordingly, and the institution is semi-trusted. ③Cloud server CS. The data service provider SP can store the data on the CS by means of payment, and the ciphertext stored on the cloud server CS is completely public, and the institution is semi-trusted. The location privacy protection meth...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com