Safety detection method and device for Web application system
A security detection and web application technology, applied in the field of network security, can solve the problems of inability to locate the source code of vulnerabilities, high false positive rate, and low security of web application systems, so as to improve code security awareness, strengthen security, and enhance The effect of code security awareness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
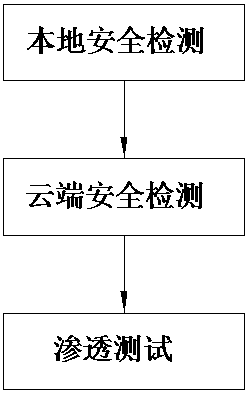
[0033] A security detection method for a web application system, the steps comprising:
[0034] Step 1. Local security detection
[0035] Local security detection mainly analyzes the code of the web application system, uses crawler technology to simulate the use of the web application system, and marks the detected web application system code vulnerabilities as warning marks;
[0036] The process of code analysis is to firstly detect the dangerous function of the code of the Web application system, and then perform parameter filtering and identity verification on the code of the Web application system.
[0037] The source code analysis technique is adopted in the code analysis, and the source code analysis technique mainly includes the following three steps:
[0038] Step 3-1, first perform lexical analysis and syntax analysis on the code of the Web application system (for example, perform mathematical modeling on the logical structure of the code of the Web application syste...
Embodiment 2
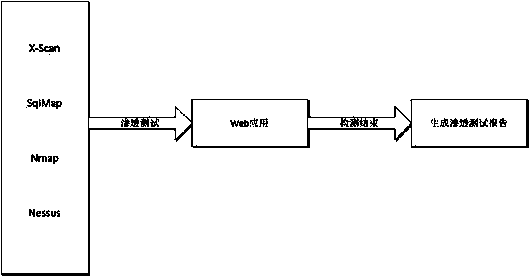
[0058] A security detection device for a web application system includes a local security detection module, a cloud security detection module and a penetration testing module.
[0059] The local security detection module is used to analyze the code of the Web application system by using the source code analysis technology, simulate the use of the Web application system by using the crawler technology, and mark the detected code loopholes of the Web application system as warnings. The local security detection module adopts the local security detection method in the first embodiment above.
[0060] The cloud security detection module is used for uploading the sample of the Web application system code to the cloud server, and comparing each basic block of the sample of the Web application system code with the defective basic block pre-stored on the cloud server, and comparing the generated Web Application system code vulnerabilities are marked with warnings. The cloud security d...
Embodiment 3
[0064] On the basis of the second embodiment, an update module is also provided. The update module is used to update the defective basic blocks, security modules and penetration testing tools pre-stored on the cloud server.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com