Key management method, key use method, key management device, key use device and key use equipment
A key management and key technology, which is applied in the data encryption field of financial technology, can solve problems such as the inability to guarantee the security of user keys, network attacks, and inability to retrieve them
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
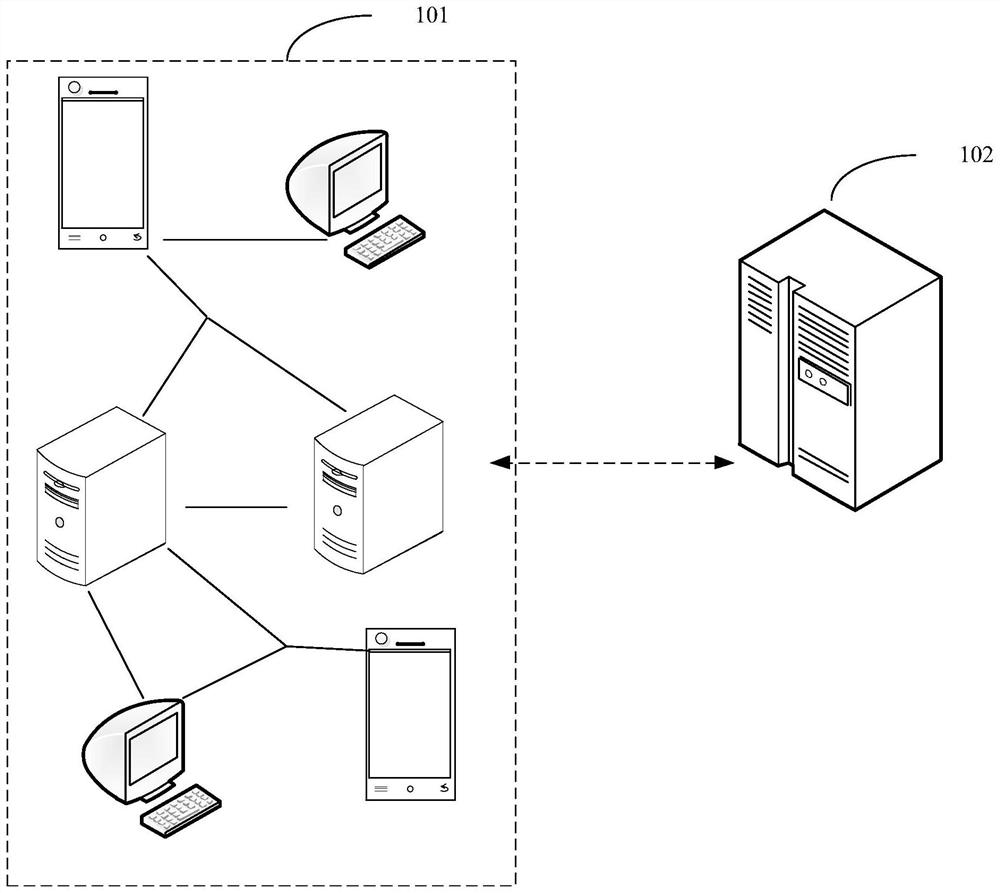
Image
Examples
example 1
[0189] Example 1. It is assumed that there are m=2 trusted institution nodes, key slice n=10, and the number of key slices stored by each key node is i=4.
[0190]Then, 2*4<10 satisfies the necessary conditions, and the number of client nodes needs to satisfy 16≤x≤208, then the complete user key can be obtained after obtaining the combination of key slices returned by at most 16 client nodes , key slices can be stored on 210 nodes (including two trusted institutions) in a non-repeating arrangement and combination.
[0191] Assuming that the probability of each key node losing the key segment is 50%, then at least 194 nodes and above will lose the key segment and the user key cannot be retrieved. The probability is about 50% to the 194th power, so basically It is impossible to lose the user key.
[0192] It can be seen from the above description that the number x of client nodes needs to meet the preset constraint range by setting, so as to ensure that the user key will not be...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com