Enterprise safety protection system and method based on white list mechanism
A security protection and whitelist technology, applied in the transmission system, electrical components, etc., can solve problems such as theft and destruction that are difficult to prevent hackers from infiltrating, low filtering standards, and whitelist login delays
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
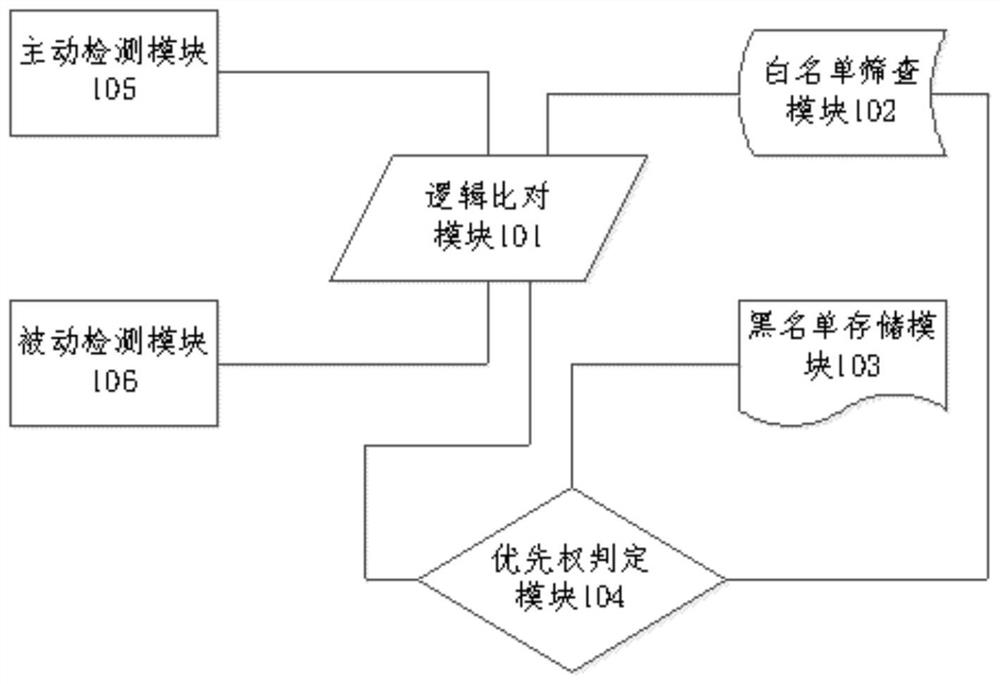
[0073] Below, reference figure 1 As shown, a corporate security protection system and method based on whitelist mechanism, where:
[0074] A enterprise security system based on whitelist mechanism, including: fingerprint information detection module, logic alignment module 101, white list screening module 102, blacklist storage module 103, and priority determination module 104;
[0075] Further, the fingerprint information detecting module includes: the active detecting module 105 and the passive detection module 106, a proactive detection and passive detection for fingerprint information; the fingerprint information refers to the IP address of the terminal and MAC information, vendor information, and hardware. Host information such as serial number information;
[0076] One end of the active detecting module 105 is electrically connected to one end of the logic ratio module 101; one end of the passive detection module 106 is electrically connected to the other end of the logic al...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com