Method for switching encryption safety data among peer-to-peer user nodes in P2P network
A P2P network and peer-to-peer user technology, which is applied in the direction of public keys for secure communication, user identity/authority verification, electrical components, etc., can solve the problem of identity being easily eavesdropped, without considering the security of data transmission, SSL/TLS and IKE security Defects and other problems, to achieve the effect of simple establishment process, less interaction times, and good security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] Below in conjunction with accompanying drawing, the present invention will be further described.
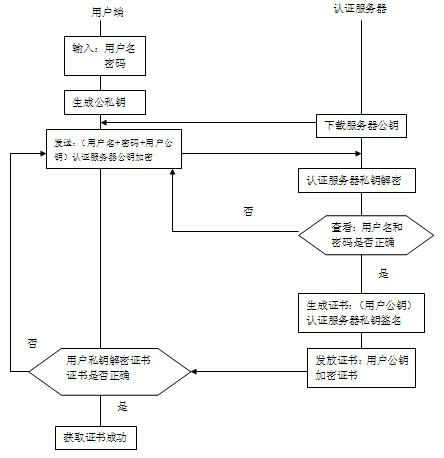
[0031] For the convenience of understanding, a simple P2P network is taken as an example to illustrate the implementation method of the present invention. Such as figure 1 As shown, in this P2P network, there are two user nodes, user node A and user node B respectively, and an authentication server connected through the network. User nodes in the network will get their own certificates during the login process. Using this certificate, the public key algorithm can be used to realize the exchange of random numbers in an encrypted environment and establish encrypted and secure communication. refer to figure 2 , firstly, the process of obtaining the user node certificate is described.
[0032] A user node, assuming user node A, first downloads the public key of the authentication server from the authentication server, and then enters the user name and password to log in to...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com