DHCP (Dynamic Host Configuration Protocol) anti-attacking method and device
A technology to prevent attacks and attackers, applied in the field of network security, can solve problems such as leaks, equipment cannot access the network normally, and wrong configuration information, etc., to achieve the effect of reducing the possibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
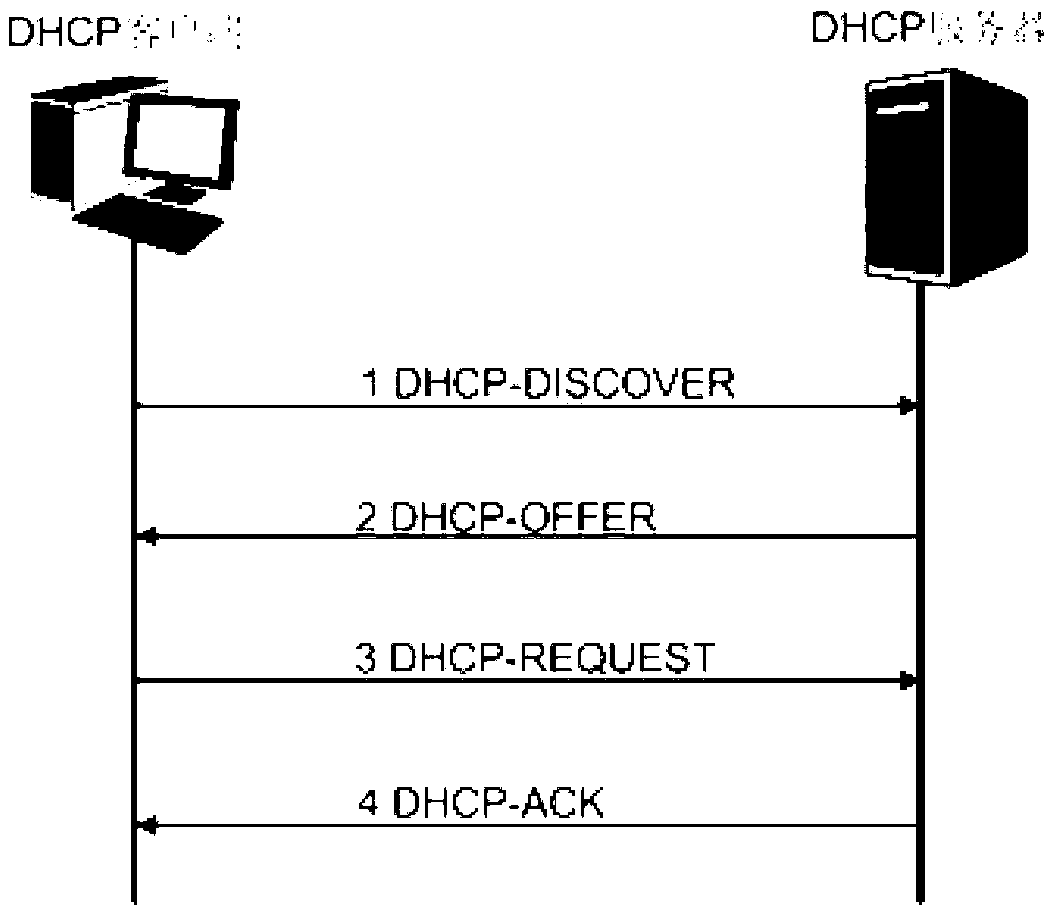
[0013] Please refer to figure 1 , generally, the network device that needs to be configured can realize its own configuration by exchanging packets with the DHCP server twice. The network equipment mentioned in the present invention is not narrow switches and routers, but covers all nodes in all networks that need to obtain IP addresses and related network configurations. In the process of interacting with the DHCP server, first, the network device as the DHCP client sends a broadcast DHCP Discover message to the network, carrying a list of configuration information that the DHCP client cares about. The DHCP Offer message is filled with the IP address resources managed by itself and other configuration information, and sent back to the DHCP client in the form of broadcast (in most cases) or unicast (in a few cases).
[0014] Since there may be multiple DHCP servers on the network, the DHCP client may receive multiple DHCP Offer messages. The DHCP client can select a DHCP ser...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com