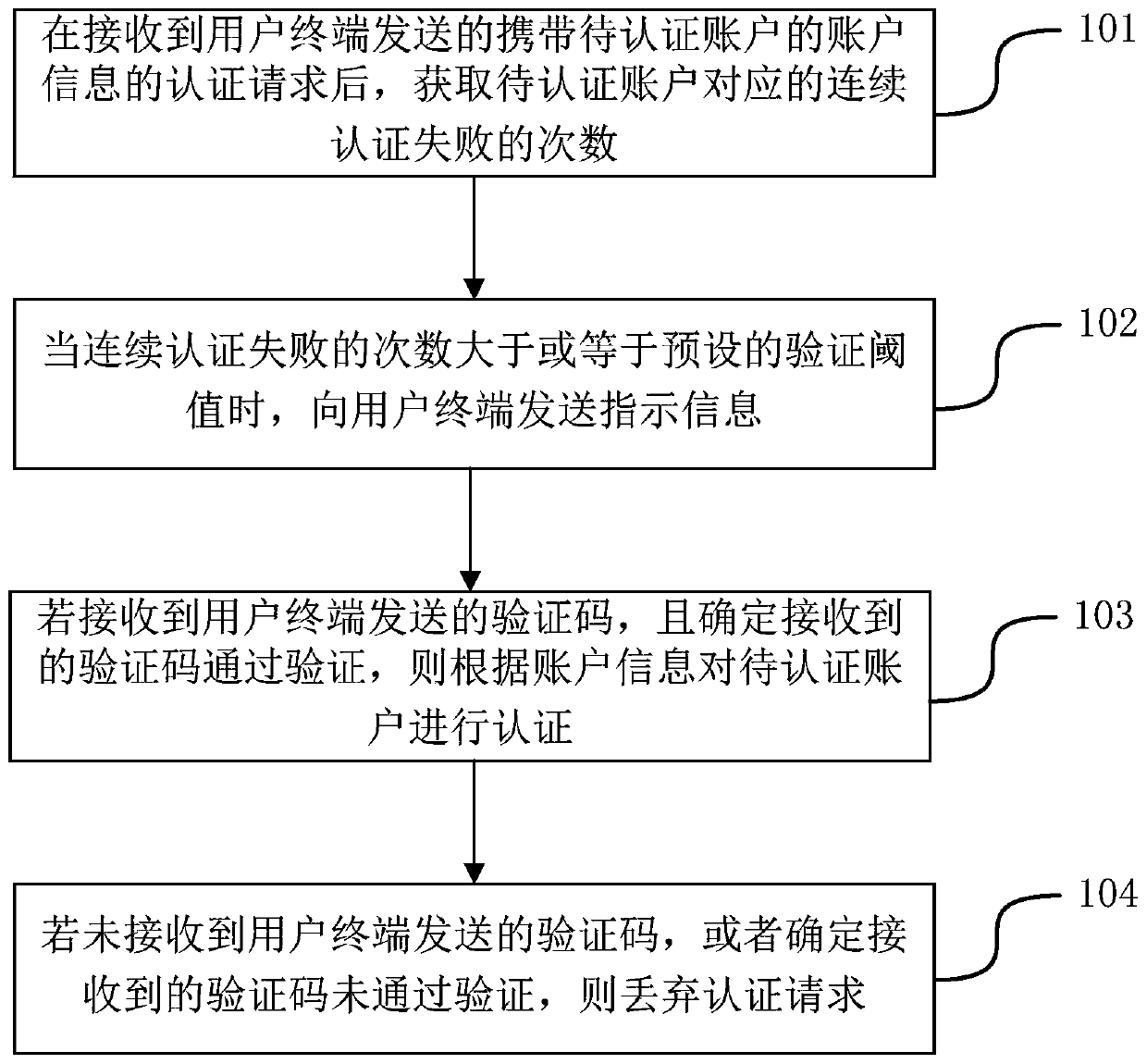
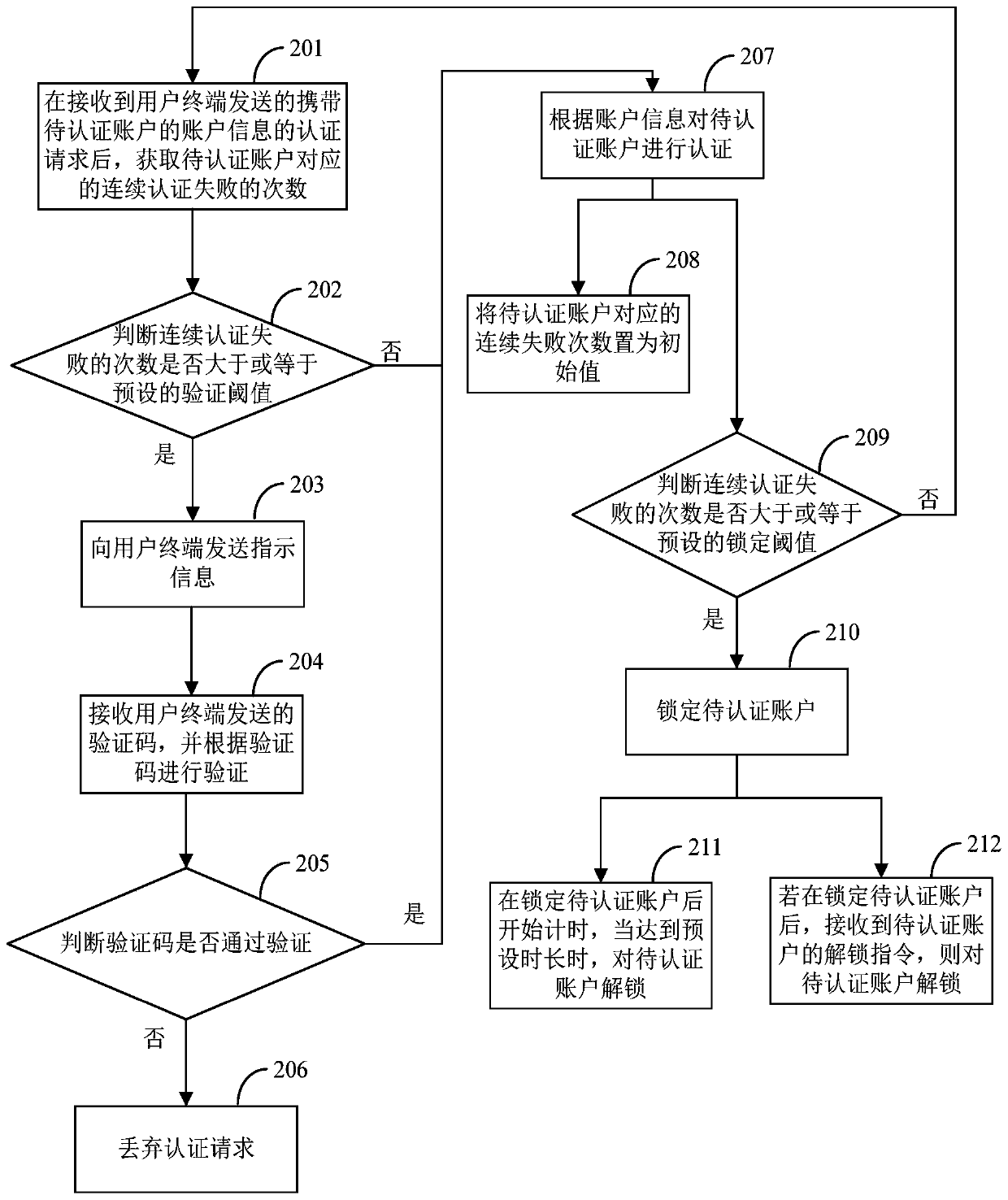
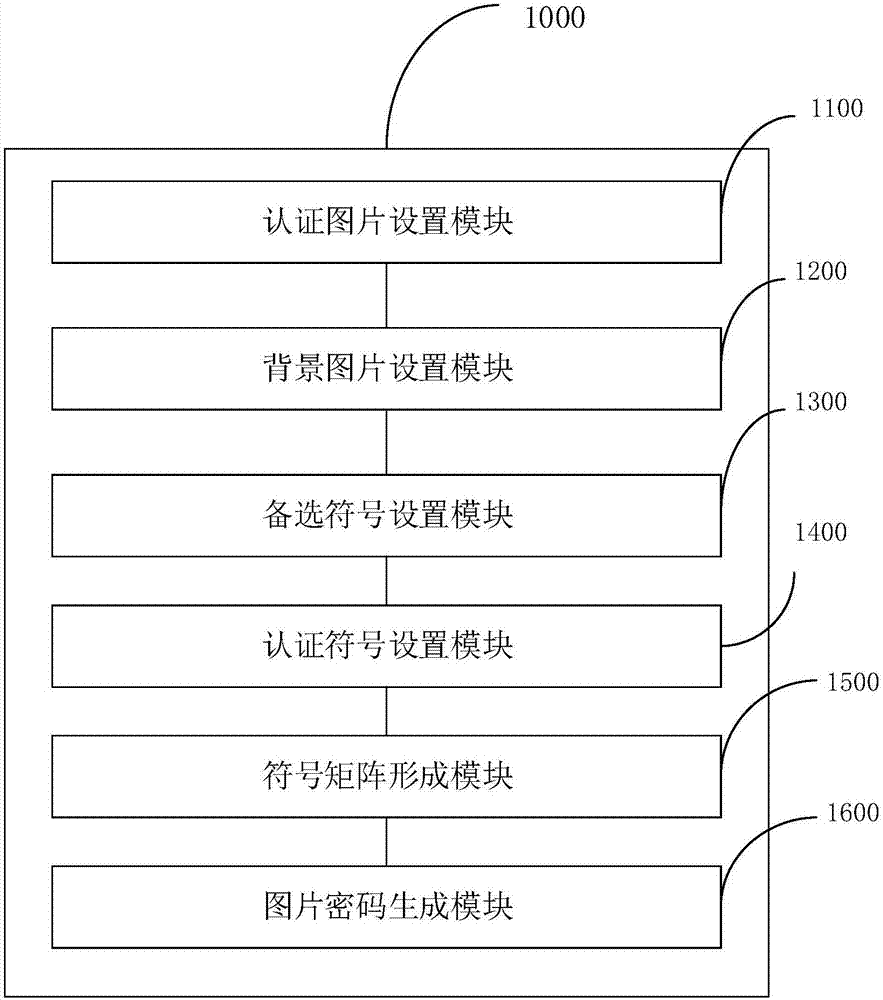
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
88results about How to "Prevent brute force cracking" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
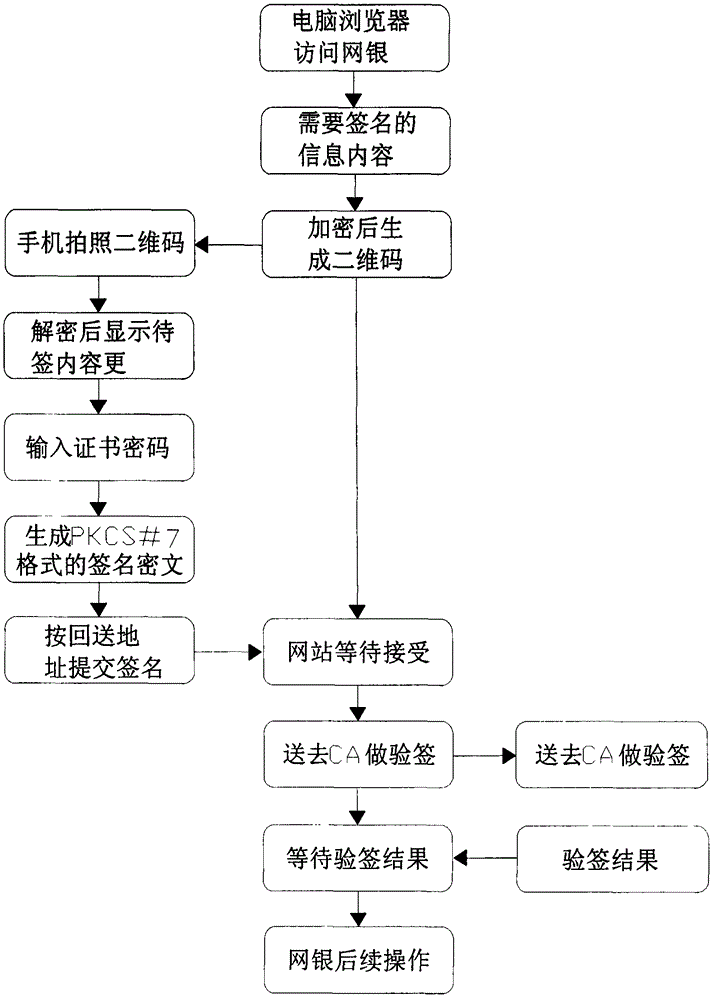
Mobile terminal digital certificate electronic signature method
ActiveCN105323062AIngenious ideaReasonable ideaUser identity/authority verificationIssuing bankInternet privacy
The invention relates to a mobile terminal digital certificate electronic signature method. According to the method, based on the characteristics of public keys and private keys and on the premise of not violating the rules prescribed by the electronic signature law, for example, a private key should be generated in a user terminal and should not leave the user terminal, a private key should not be transmitted via the network, and the like, a private key is discarded and locally and discretely stored after encryption, and the cloud uses strategies such as storing the public key and certificate to ensure that the private key is not locally cracked. In the transport layer, strategies such as double key and one-time pad are adopted to ensure that important information is not intercepted and decoded in network transmission. The identity of a certificate applicant is verified through the interface of an issuing bank, the user identity verification result of the bank counter is inherited, and therefore, remote online certificate issuing is realized in the system. The method not only can ensure that all the links of certificate applying, certificate issuing, certificate storing and certificate using are safe, but also can prevent hackers and Trojans from stealing certificate files, prevent network package-capture parsing, prevent password intercepting through screen capture and prevent an algorithm from being known through software decompiling.
Owner:BANKEYS TECH
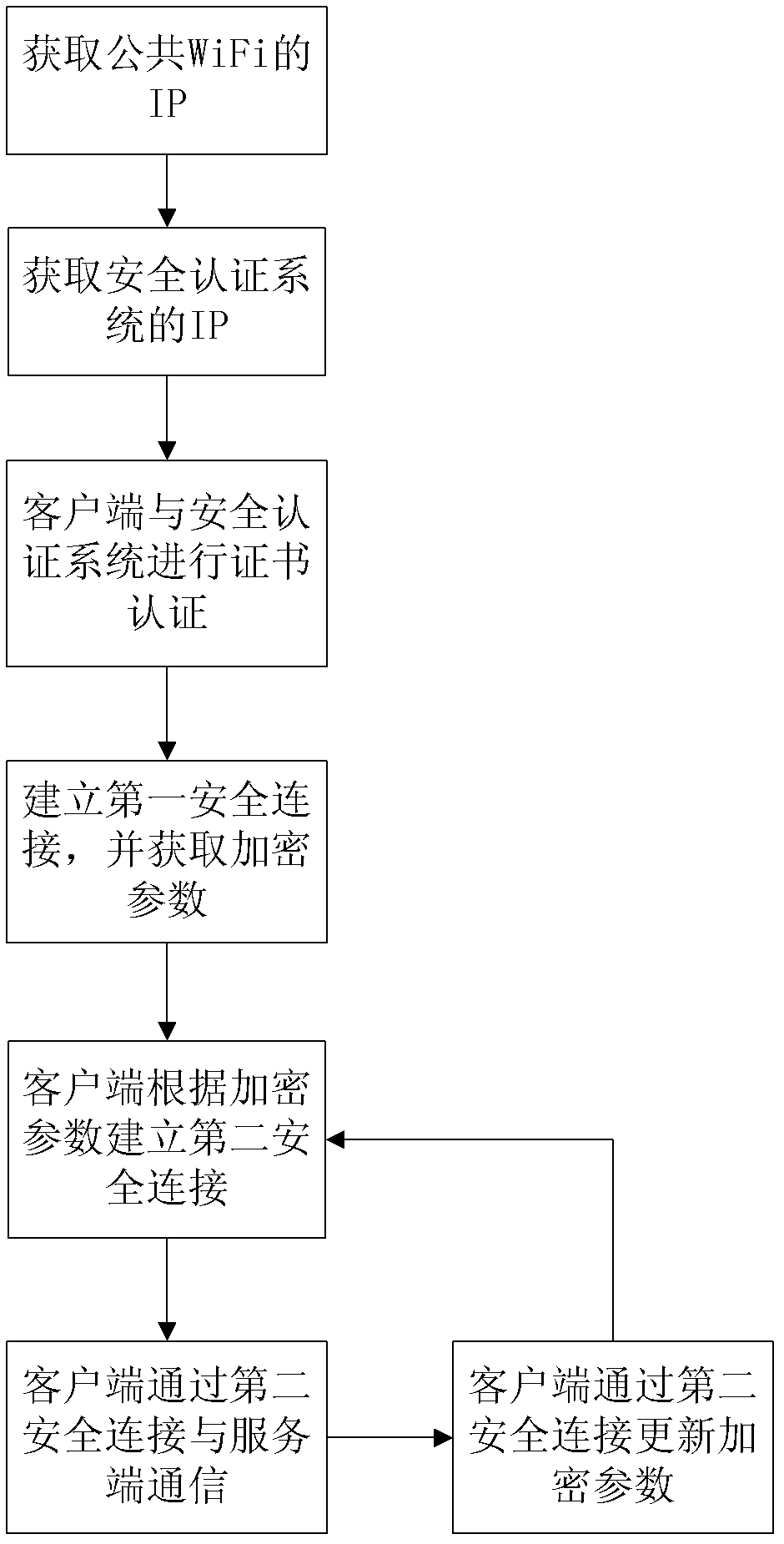
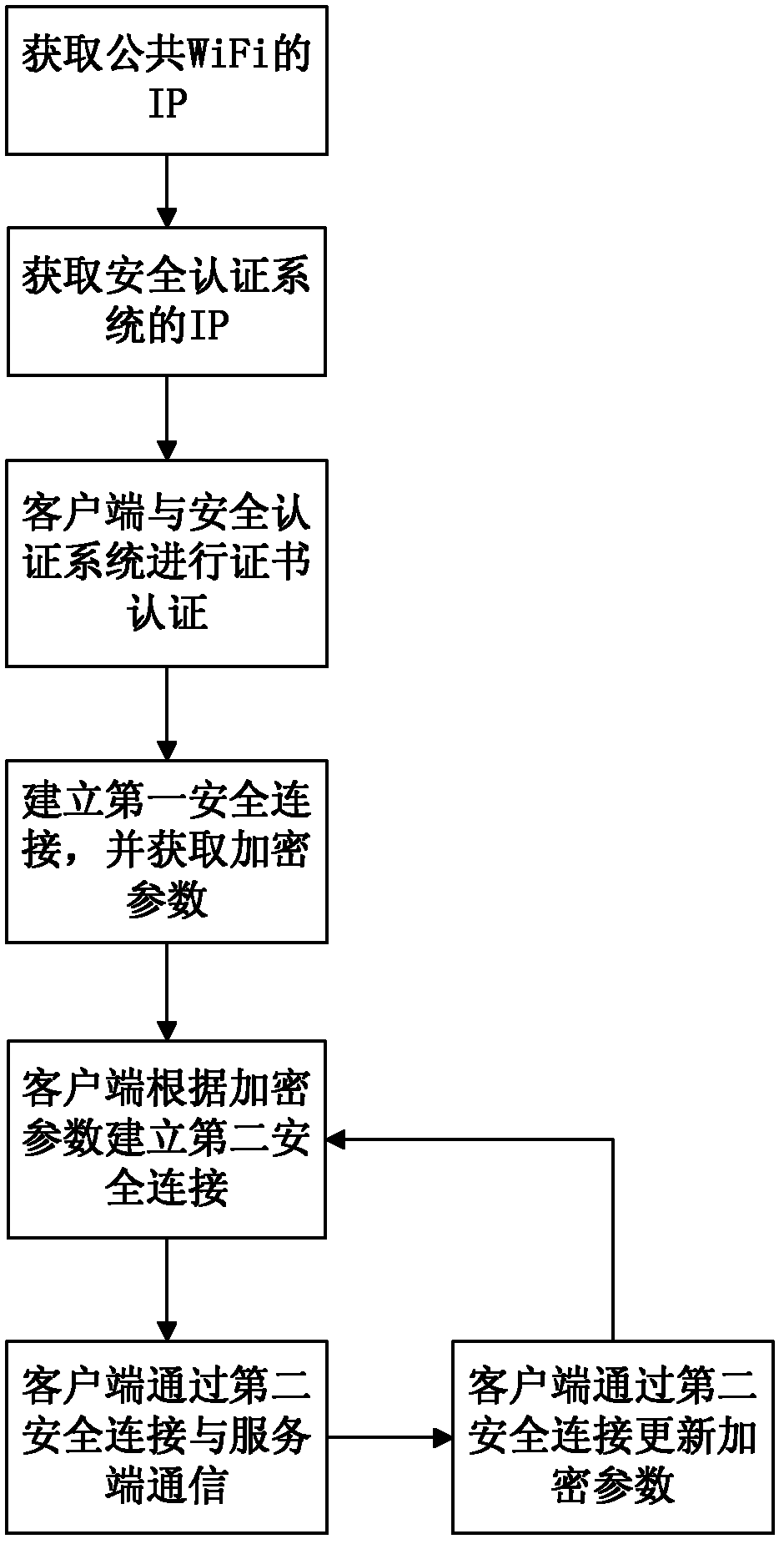
Security authentication method for wireless network
ActiveCN102547695AImplement Live BindingAvoid the possibility of leakageConnection managementSecurity arrangementBrute forceIp address
The invention relates to a security authentication method for a wireless network. A wireless fidelity (WiFi) server and a client are involved, and the security authentication method comprises the following steps that: a, an authentication service program is deployed in the client, and the client is connected to a public open system of the WiFi server to acquire a corresponding internet protocol (IP) address; b, according to the IP address, the client acquires and accesses an IP address of a security authentication system of the WiFi server; c, the WiFi server authenticates a client certificate; d, the client which passes the authentication establishes first security connection with the WiFi server and acquires encryption parameters; e, the client establishes a second security connection with the security authentication system of the WiFi server according to the encryption parameters; and f, the client and the WiFi server communicate and are updated through the second security connection. By the security authentication method, the client and the WiFi server can be connected easily and quickly by using a complex key and a complex encryption way; and meanwhile, the security during connecting can be guaranteed by using a method of updating the key regularly to ensure that brute force-based cracking and possibility of key leakage are avoided.
Owner:成都飞鱼星科技股份有限公司
Open knowledge bases method and equipment for user authentication
InactiveCN101938466APrevent brute force crackingReduce cost pressureTransmissionSpecial data processing applicationsUser deviceService provision
The invention aims to provide open knowledge bases method and equipment for user authentication. The method comprises the following steps of: selecting a problem from the open knowledge base by the network equipment; sending the problem and an answer input frame thereof to the UE (User Equipment) of a user; acquiring a user response to the problem, wherein the user response is input in the answer input frame by the user; and matching and comparing the user response with the answer to the problem so as to acquire a matching result; and feeding back information related to the matching result to the UE. Compared with the prior art, by selecting the user authentication problem from the open knowledge base, the invention effectively avoids brutal computer cracking and relieves the cost pressure of an authentication service provider for maintaining a great amount of data so as to realize a user authentication technology with high security and high reliability in an effective cost mode.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
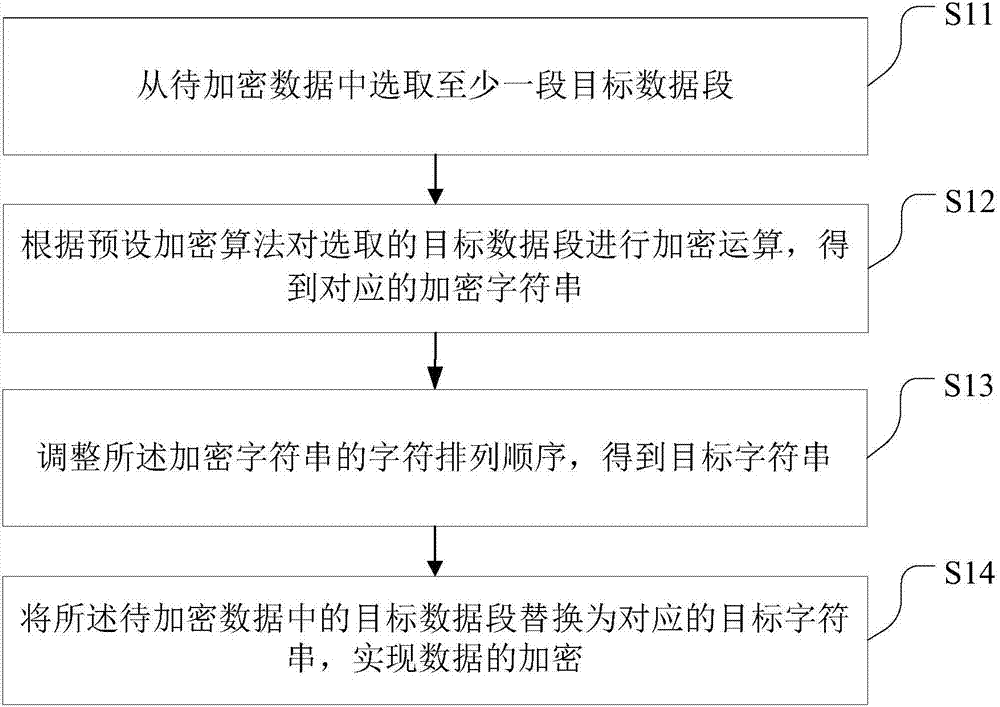
Data encryption method and device
ActiveCN107147616AImplement cryptographic operationsImprove securityTransmissionBrute forceData segment
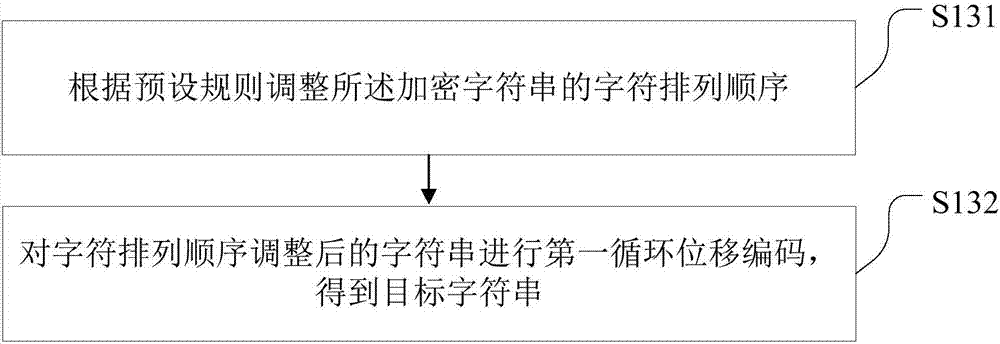
The embodiment of the invention provides a data encryption method and device. The method comprises the following steps: selecting at least one target data segment from data to be encrypted; performing encryption operation for the selected target data segment according to a preset encryption algorithm to obtain a corresponding encrypted character string; adjusting the character arrangement order of the encrypted character string to obtain a target character string; replacing the target data segment in the data to be encrypted to the corresponding target character string to achieve data encryption. According to the data encryption method and device provided by the embodiment of the invention, the encryption operation of the data can be rapidly achieved, the brute force cracking of malicious programs to the encrypted data can be effectively prevented, and the security of the data can be improved.
Owner:江西创佳工程技术有限公司 +1
Data encryption method, device, equipment and system and data decryption method, device, equipment and system
ActiveCN104601325ASolve the problem of low securityImprove securityUser identity/authority verificationDigital data protectionXML EncryptionData decryption
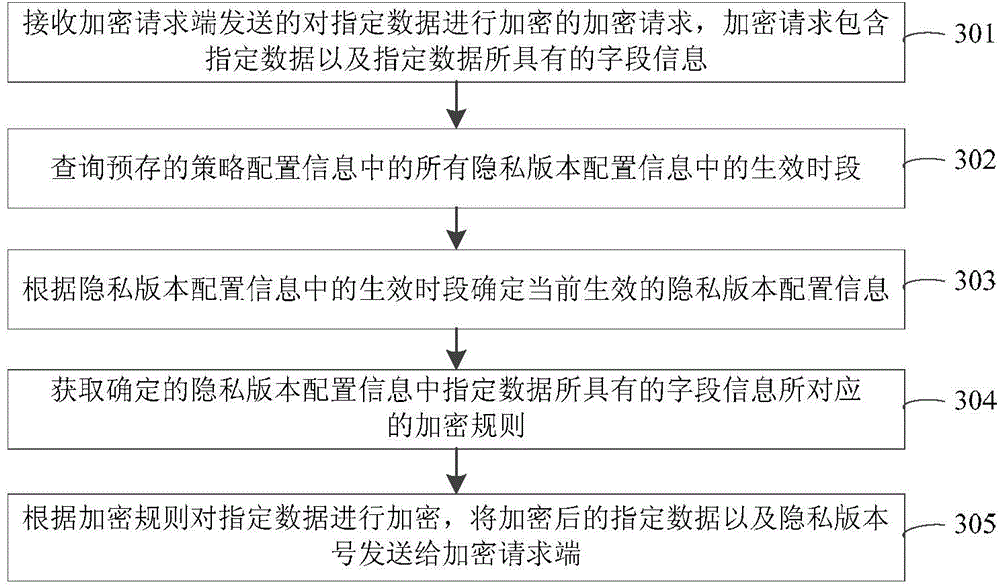
The embodiment of the invention provides a data encryption method, device, equipment and system and a data decryption method, device, equipment and system, and relates to the field of data security. The data encryption method comprises the following steps: receiving an encryption request for encrypting specified data; acquiring an encryption rule corresponding to field information in pre-stored currently-effective privacy version configuration information; and encrypting the specified data according to the searched encryption rule. The specified data is encrypted through the preconfigured currently-effective privacy version configuration information. The problem of low security of encryption and decryption methods provided in the prior art is solved. The effective privacy version configuration information is updated automatically along with time, so that the probability of forced cracking of encrypted data can be lowered to a great extent, and the security during data encryption or decryption can be enhanced greatly.
Owner:HUAWEI TECH CO LTD
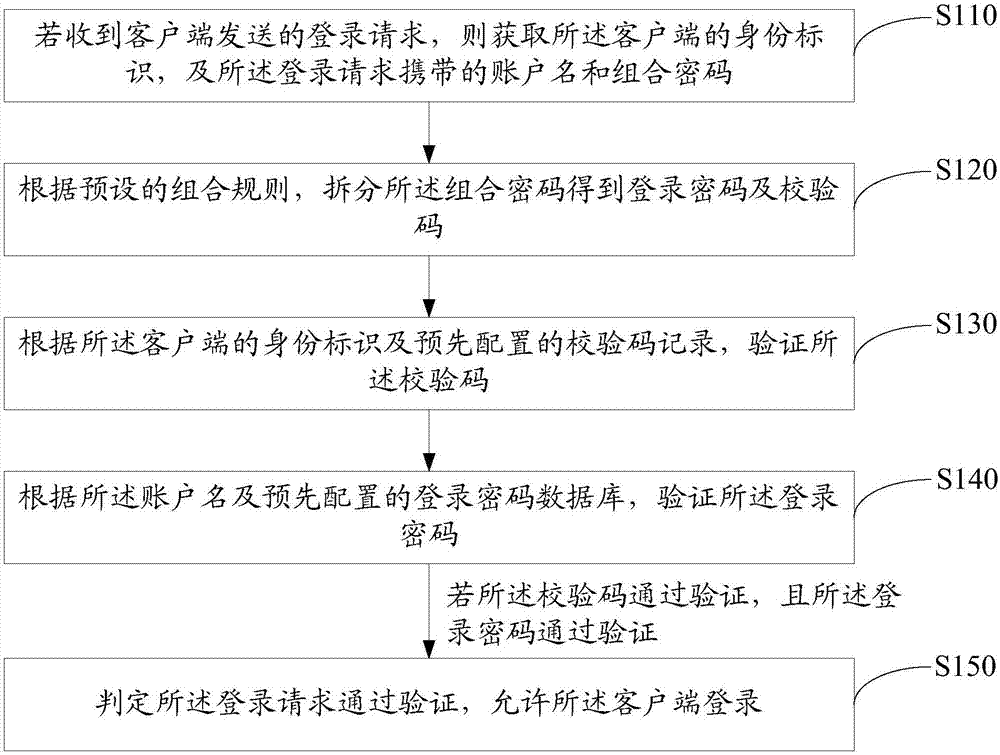
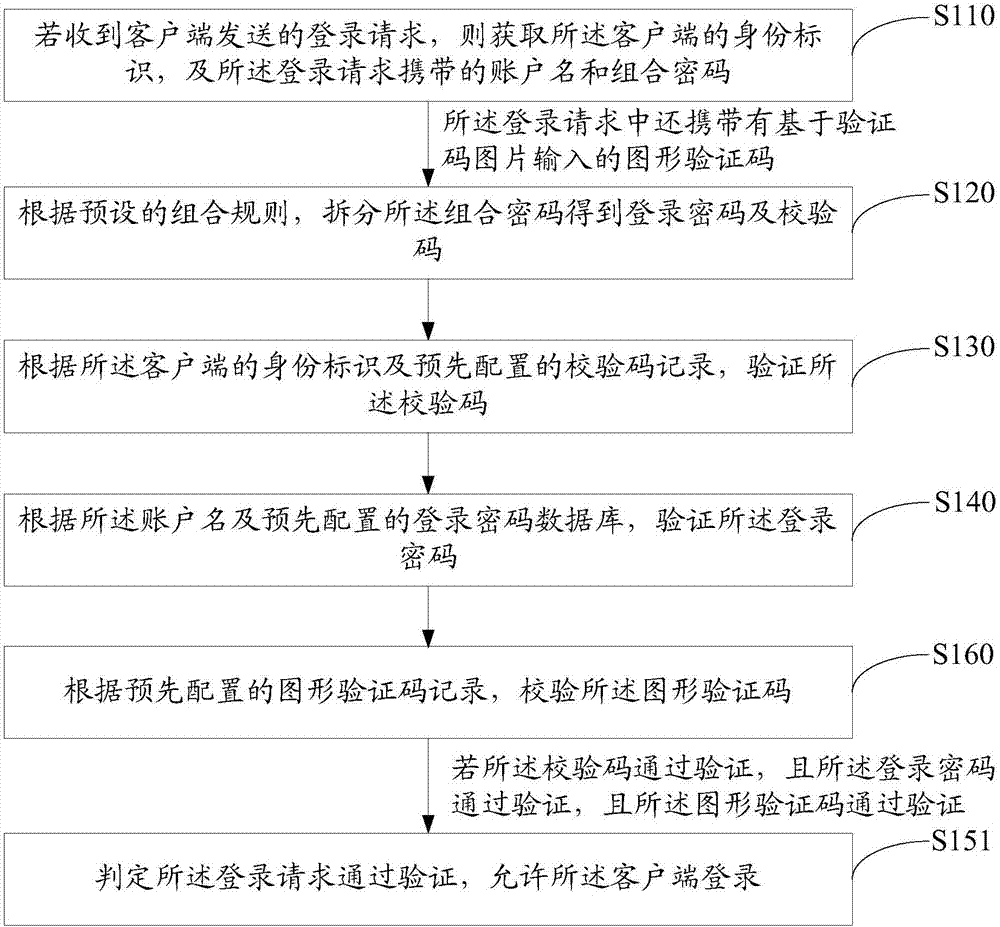
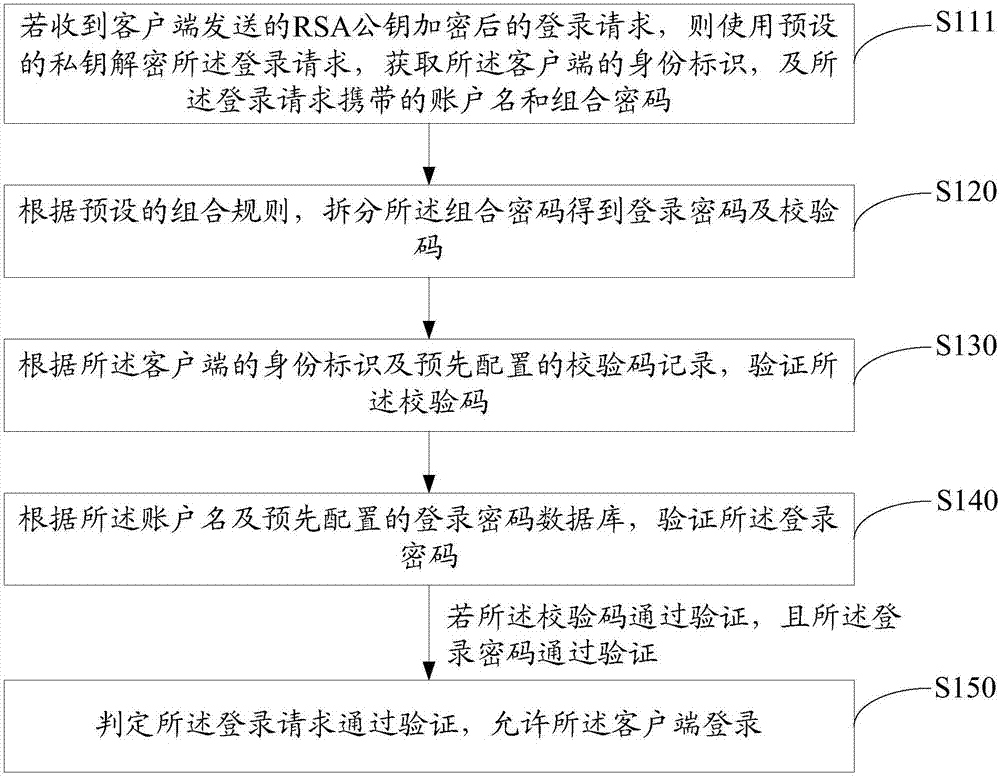
Login verification method, login request method and secure login system
ActiveCN107317791AEnhance the difficulty of blastingPrevent brute force crackingDigital data authenticationTransmissionClient-sideValidation methods
The invention discloses a login verification method. The method comprises the following steps: if a login request sent by a client is received, obtaining an identity identifier of the client and an account name and a combined password carried in the login request; splitting the combined password to obtain a login password and a check code according to a preset combination rule; verifying the check code according to the identity identifier of the client and a preset check code record; verifying the login password according to the account number and a preset login password database; and if the check code is verified, the login password is verified, determining that the login request is verified, and allowing the client to log in. The invention further discloses a login request method and a secure login system. By adoption of the login verification method, the security of the login mode is greatly improved.
Owner:PING AN TECH (SHENZHEN) CO LTD
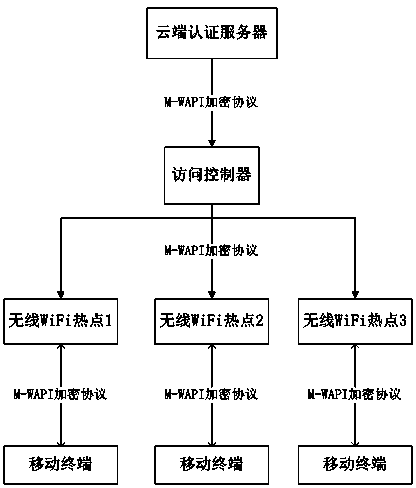
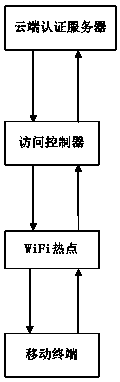
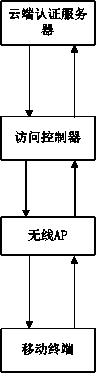
WiFi Internet surfing connecting authentication method and system based on asymmetric full-process encryption
ActiveCN104270250AAvoid PhishingFirmly connectedUser identity/authority verificationAuthentication systemWifi network
The invention relates to a WiFi Internet surfing connecting authentication method based on asymmetric full-process encryption. The WiFi Internet surfing connecting authentication method includes the steps that a cloud authentication server defines an encryption access strategy for an access controller; the cloud authentication server issues the encryption access strategy to the assigned access controller based on the M-WAPI protocol; the access controller issues the encryption access strategy based on the M-WAPI protocol to a mobile terminal accessing the WiFi for the first time; the mobile terminal sends an encrypted authentication request to the cloud authentication server for authentication through the encryption access strategy, and if authentication is successful, the mobile terminal can access the Internet. The invention further discloses a WiFi Internet surfing connecting authentication system based on the asymmetric full-process encryption. By means of the asymmetric full-process encryption method and system, the mobile terminal can be rapidly connected to legal WiFi hot points, phishing, AP cheating, network hijacking, brute force attacking and the like can be effectively avoided, and it is guaranteed that users can safely use WiFi network resources without worries to protect sensitive information of the users from leakage and stealing.
Owner:HEFEI CITY COULD DATA CENT
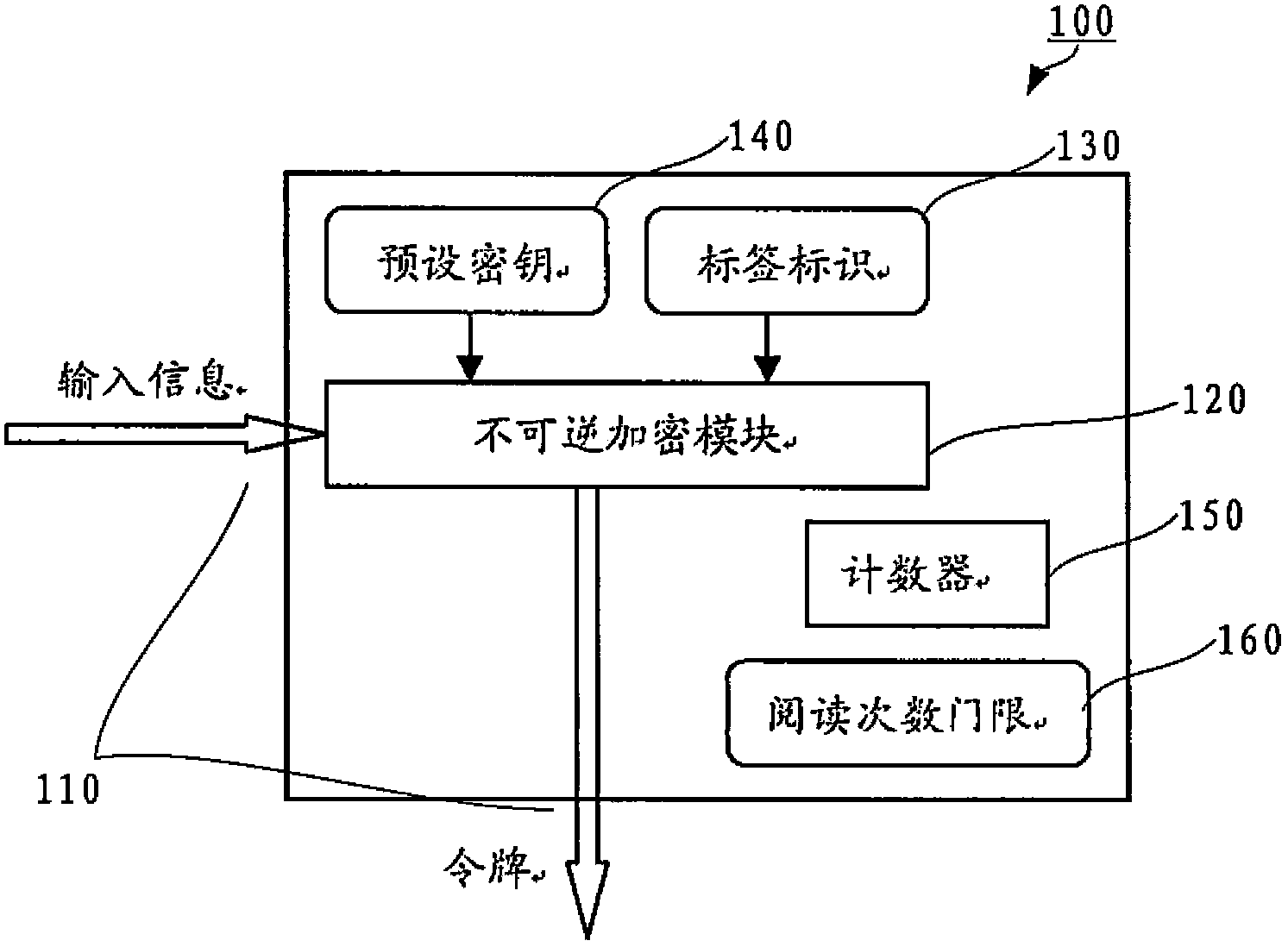
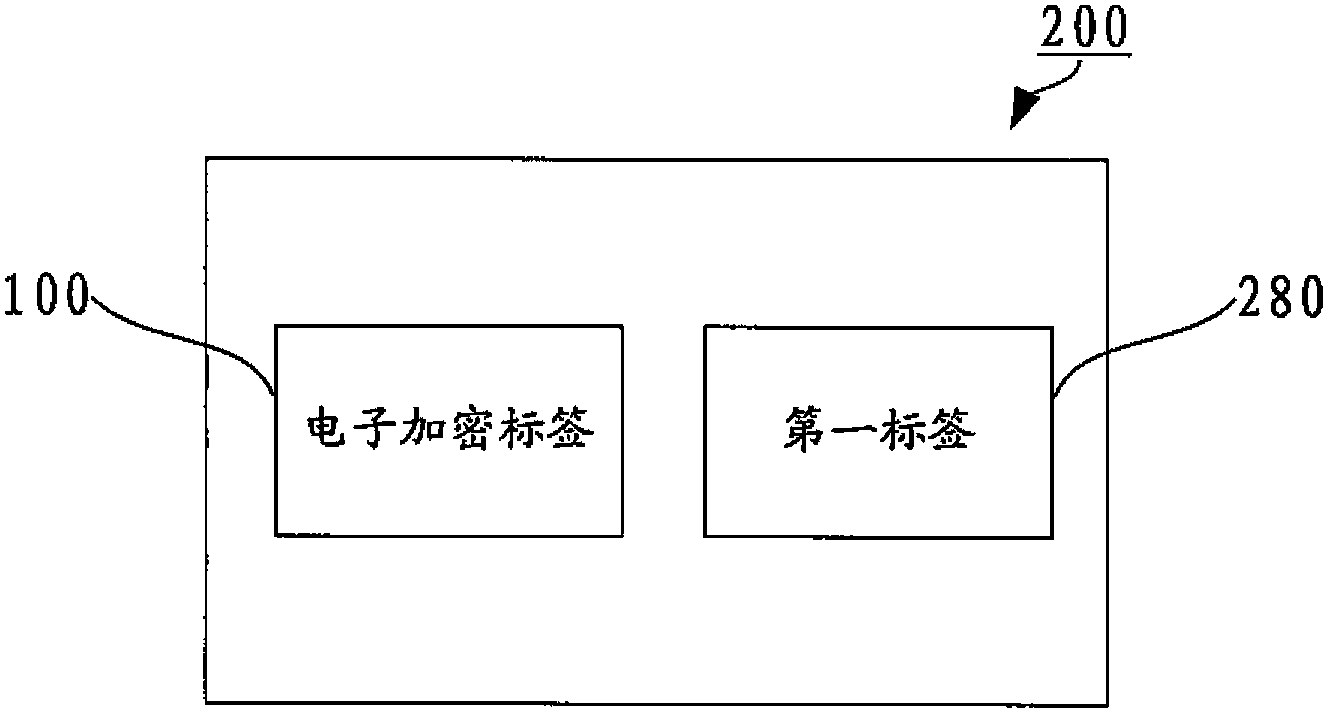
Electronic encryption label, false proof label system, and article false proof system and method
InactiveCN103985043APrevent brute force crackingImprove securitySensing record carriersCommerceInput/outputComputer hardware
The invention relates to an electronic encryption label, a false proof label system, and an article false proof system and method. The electronic encryption label comprises an input output interface and an irreversible encryption module, the input output interface is constructed to receive first information, and the irreversible encryption module is constructed to generate an identification token according to the first information and output the token through the input output interface. A specific encryption algorithm on the basis of the electronic encryption label can be one of many known encryption algorithms, the encryption process is irreversible, i.e., information such as an encryption key used in en encryption process cannot be reversely deduced through reverse engineering by means of the identification token. By using such a mode, violent declassification by criminals can be prevented, thus the security of the electronic encryption label can be further improved, the circulation and sale of counterfeit or inferior commodities can be effectively cracked down, and the legitimate interests of consumers and commodity manufacturers can be effectively protected.
Owner:JIANGSU DONGREN NETWORK TECH
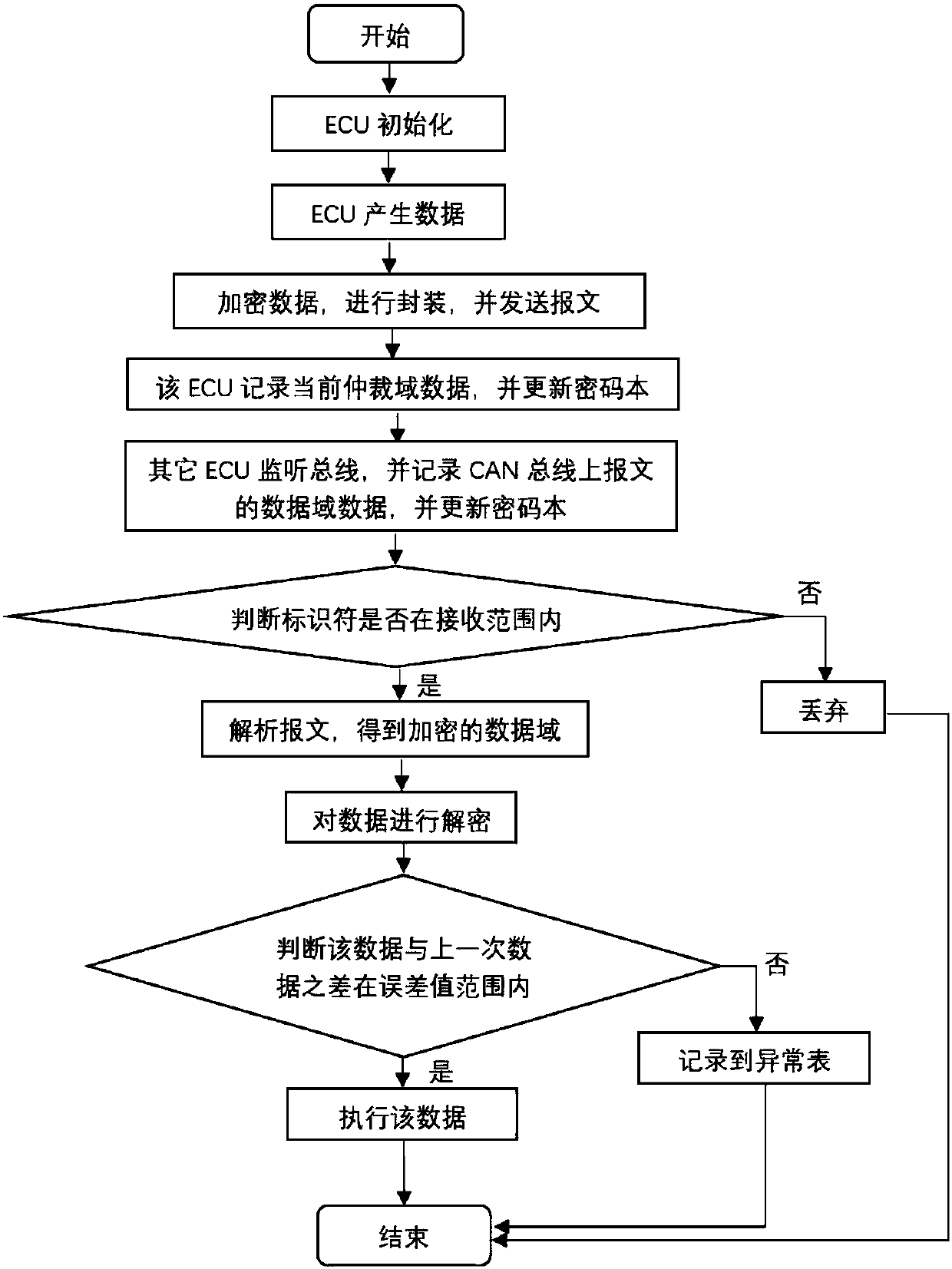
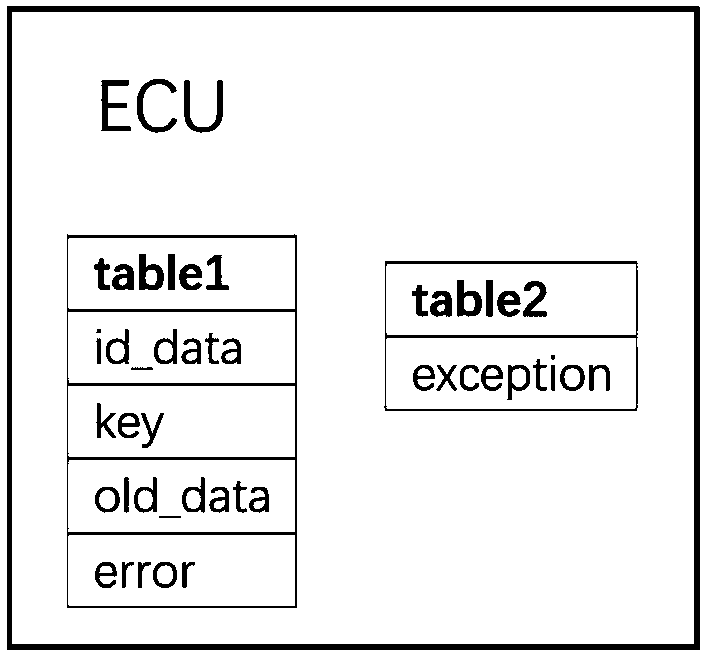
Anti-attack method and system of CAN bus message based on block chain technology
ActiveCN107749845AImprove securitySolving Difficult Management ProblemsBus networksAttack modelCode book
The invention belongs to the technical field of anti-attack of messages, and discloses an anti-attack method and system of a CAN bus message based on the block chain technology. The method comprises the following steps: improving an account book generated in a block chain, generating a password with a fixed length and updating the password in real time; performing, by each ECU, encryption processing on arbitration domain data monitored every time and a code book to obtain a new code book; before a message is sent, encrypting the data domain information via the latest code book to obtain an encrypted data domain, and finally sending the data domain; filtering, by the ECU, an identifier in the arbitration domain to obtain the necessary message, analyzing the message to obtain the encrypted data domain, and decrypting the encrypted data domain by using own code book; then judging the validity of the data obtained by decryption; and if the data are valid, executing the data, and otherwise,discarding the data. By adoption of the anti-attack method and system, the counterfeit, replay and other attacks can be defended, and the security of the vehicle is enhanced.
Owner:CHENGDU UNIV OF INFORMATION TECH
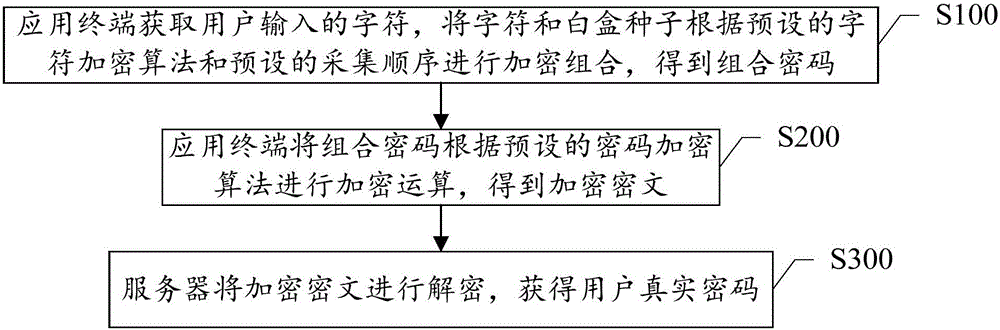
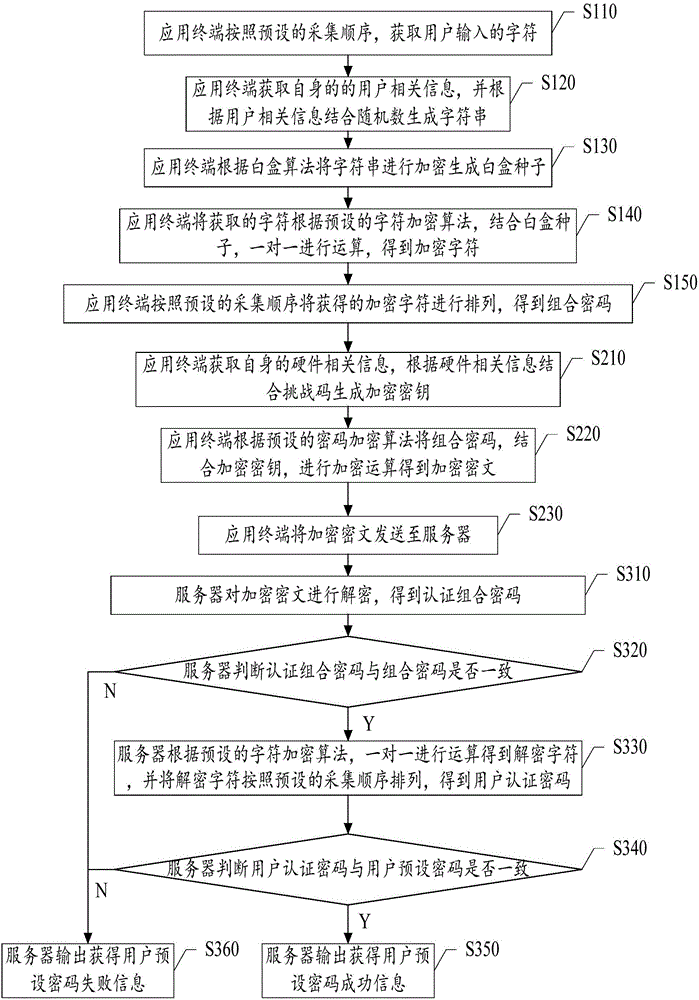
Encryption method and system based on white box
ActiveCN106506158AProtection securityProtect privacy and securityKey distribution for secure communicationBrute forceUser input
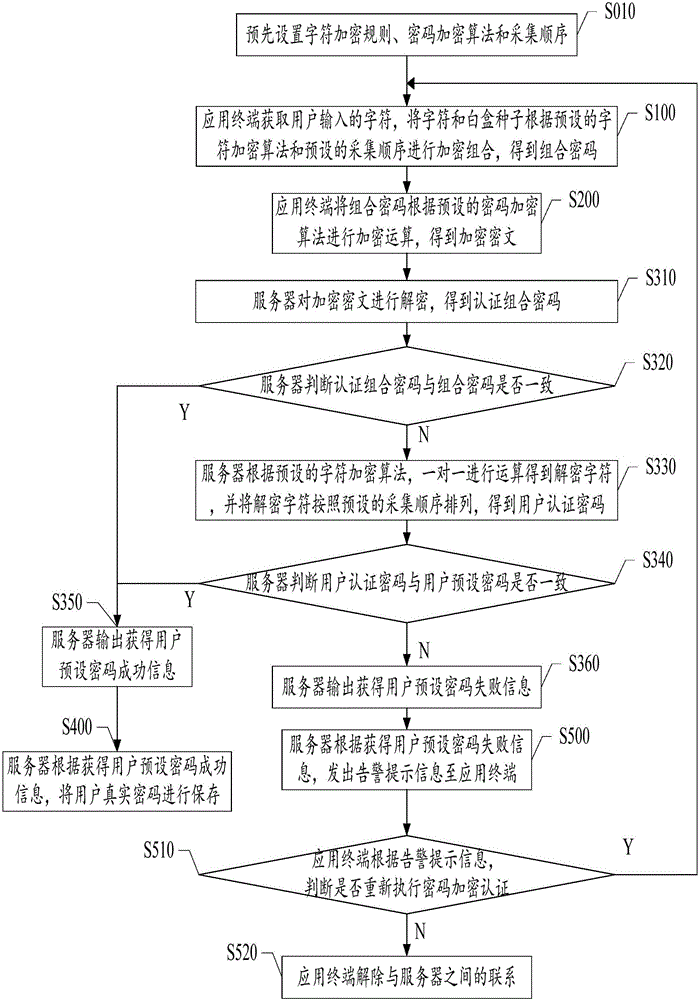
The invention discloses an encryption method and system based on a white box. The method comprises the following steps: S100, an application terminal acquires characters input by a user, and implements encryption combination on the characters and white box seeds in accordance with a preset character encryption algorithm and a preset acquisition sequence to obtain a combined password; S200, the application terminal implements encryption operation on the combined password according to a preset password encryption algorithm to obtain an encrypted ciphertext; and S300, a server decrypts the encrypted ciphertext to obtain a user default password. According to the encryption method and system disclosed by the invention, the characters input by the user can be obtained by clicking or touching a software simulation keyboard through a mouse, a white box cryptography is applied to a password keyboard of the application terminal to enable that the characters input by the user are firstly separately encrypted and then integrally encrypted, so that the way of obtaining the password through brute force can be better prevented.
Owner:SHANGHAI PEOPLENET SECURITY TECH
A method and system for binding of software and hardware
InactiveCN102663325APrevent brute force crackingImprove securityProgram/content distribution protectionClient-sideSoftware
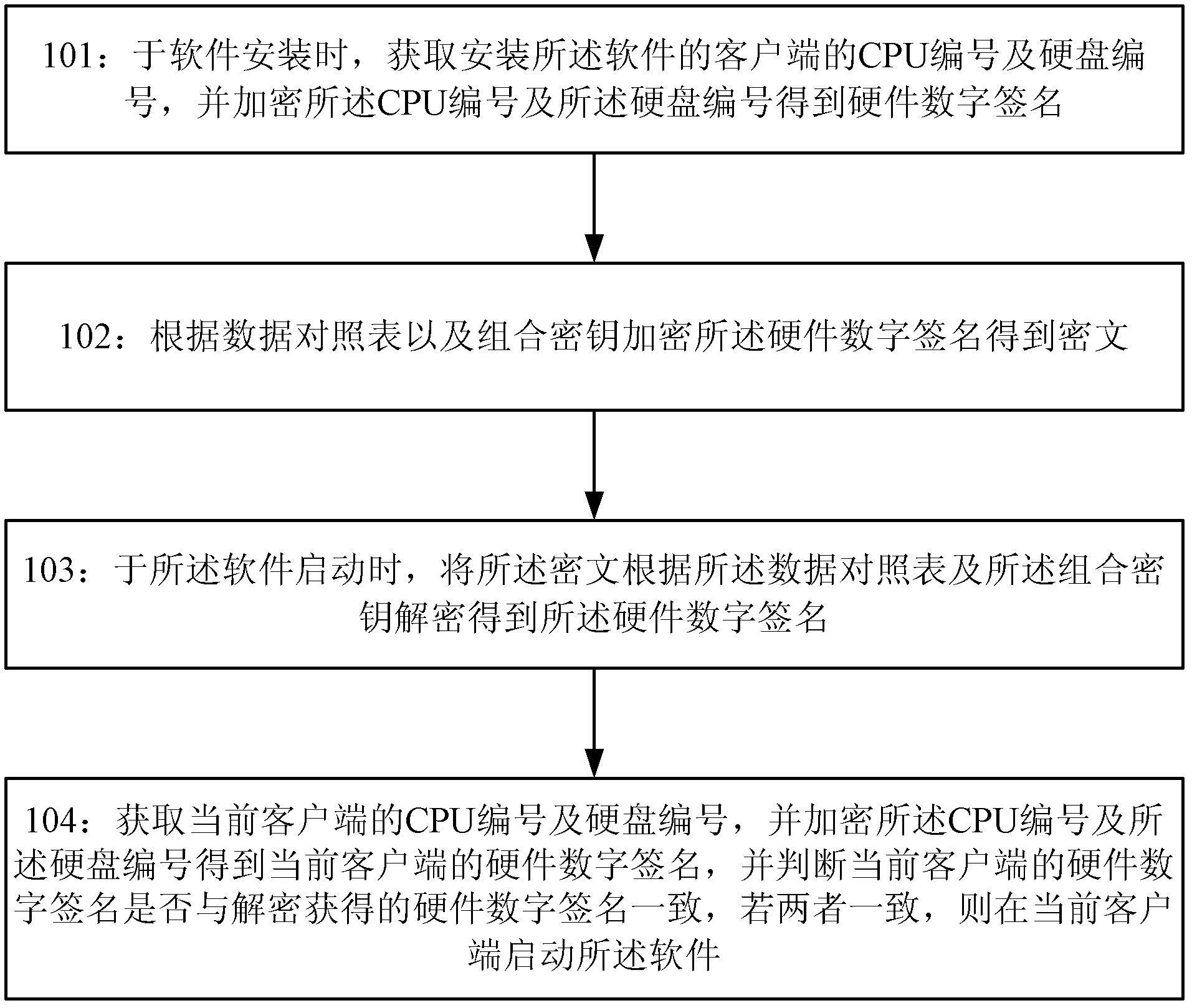
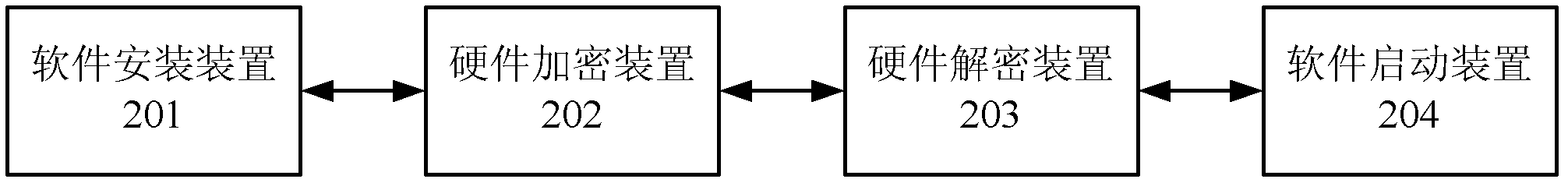
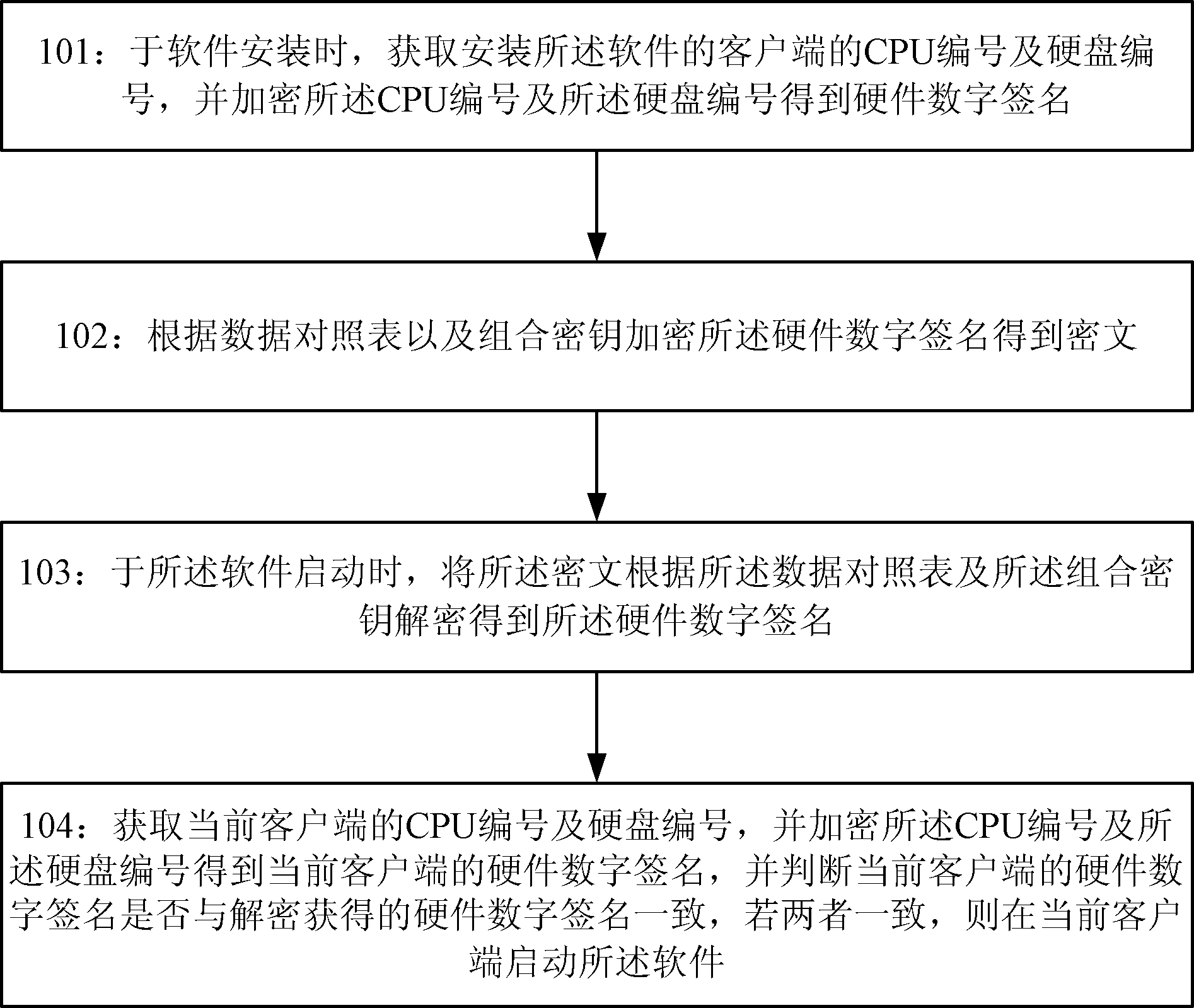
The invention provides a method and system for binding of software and hardware. The method comprises the steps of: obtaining a CPU number and a hard disk number of a client-side of installing the software during installation of the software and encrypting the CPU number and hard disk number to obtain a hardware digital signature; obtaining cryptograph through encrypting the hardware digital signature according to the data parallel table and a combination key; decrypting the cryptograph based on the data parallel table and combination key to obtain the hardware digital signature when the software starts; obtaining the CPU number and hard disk number of the present client-side, encrypting the CPU number and hard disk number to obtain the hardware digital signature of the present client-side, and determining whether the hardware digital signature of the present client-side is consistent with the hardware digital signature obtained through decryption, if yes, then starting the software on the present client-side.
Owner:SUZHOU CODYY NETWORK SCI & TECH
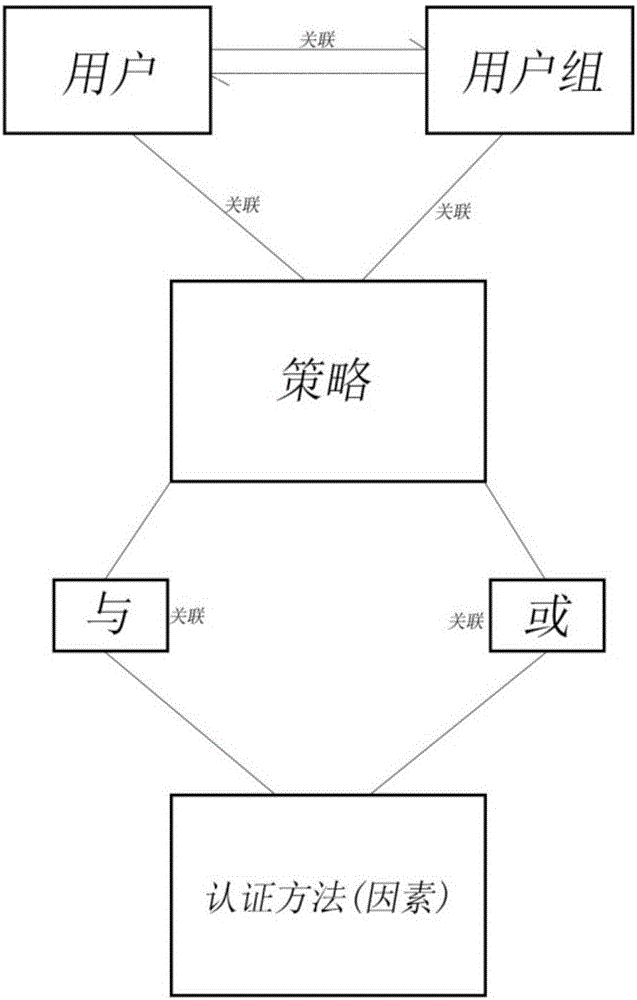
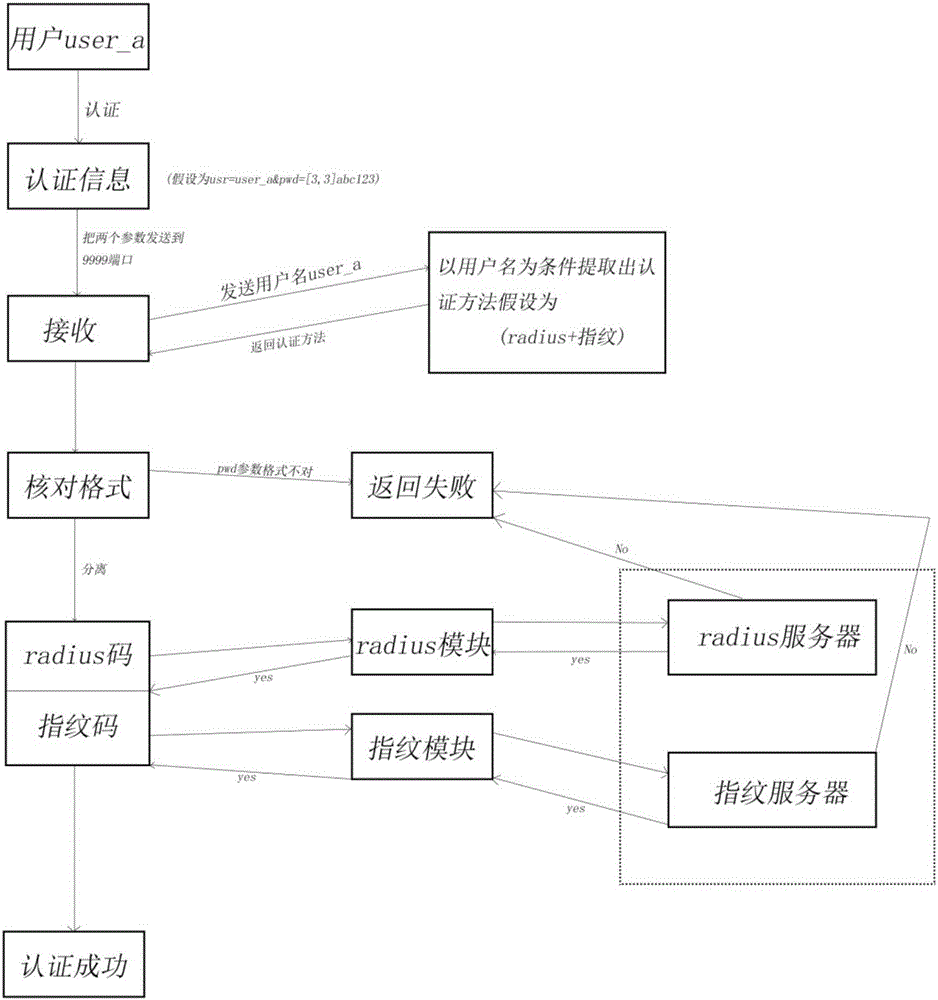
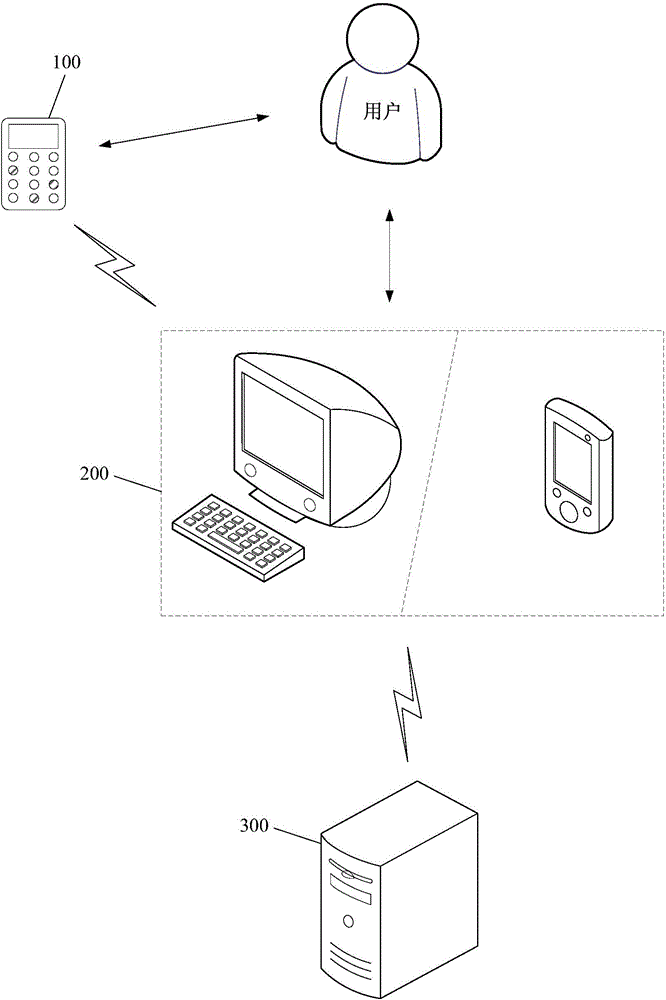
Multi-factor user authentication method capable of flexible configuration
InactiveCN106230845APrevent brute force crackingImprove scalabilityTransmissionComputer moduleModularity
The invention discloses a multi-factor user authentication method capable of flexible configuration. According to the method, multi-factor authentication (MFA) is employed, authentication systems of two or more authentication methods are performed to verify the legitimacy of a current user, and it is more difficult to try to access target information by unauthorized people through establishment of multi-layer defense. Besides, in order to better prevent violent cracking by the user, the method is additionally provided with an authentication policy at the very beginning of user authentication. Different users have their own policies, the policy records a plurality of authentication methods in the authentication system of the current user, and a protection effect is additionally provided for user security. According to the method, the design concept is based on modularization, each authentication method has independent modules, and later development is facilitated.
Owner:PALADI NETWORK TECH HANGZHOU
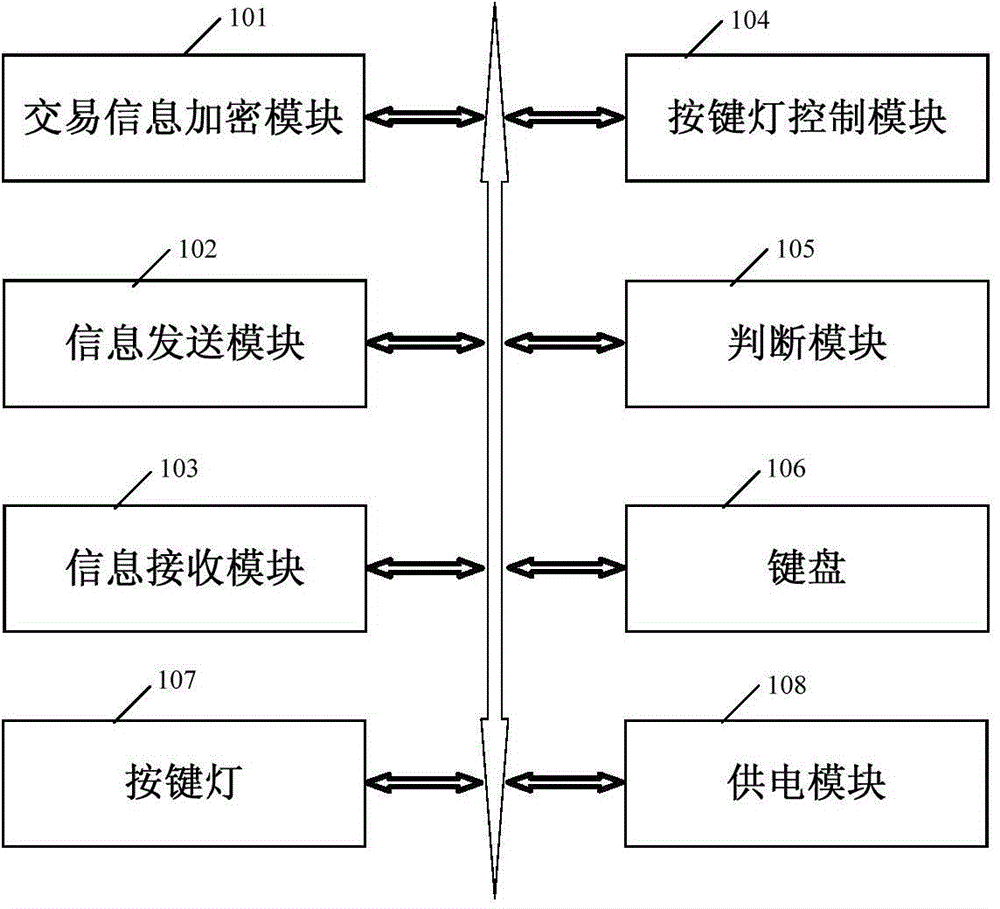
Transaction information verification method and device
ActiveCN104680376AImprove experiencePrevent brute force crackingDigital data authenticationProtocol authorisationDigital signatureValidation methods
The invention provides a transaction information verification method and a transaction information verification device. The transaction information verification method comprises the following steps: receiving transaction information submitted by a user, and performing digital signature and encryption processing; transmitting encryption transaction information with a digital signature to an electronic bank server, verifying the digital signature and judging the legality of the transaction information through the electronic bank server, and after judging that the digital signature is qualified and the transaction information is legal, generating a transaction verification code according to the transaction information; receiving a transaction verification code and a server electronic signature fed back from the electronic bank server, and verifying the server electronic signature; after the verification is approved, prompting the user to input the verification code in a mode that button lamps are lightened or tuned off or the colors of the button lamps are changed through corresponding buttons according to the transaction verification code; judging whether the verification code input by the user through operation buttons is correct or not; after the verification code is correctly input, generating verification approval information, transmitting to the electronic bank server, and processing the transaction information through the electronic bank server according to the verification approval information, and completing the transaction.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
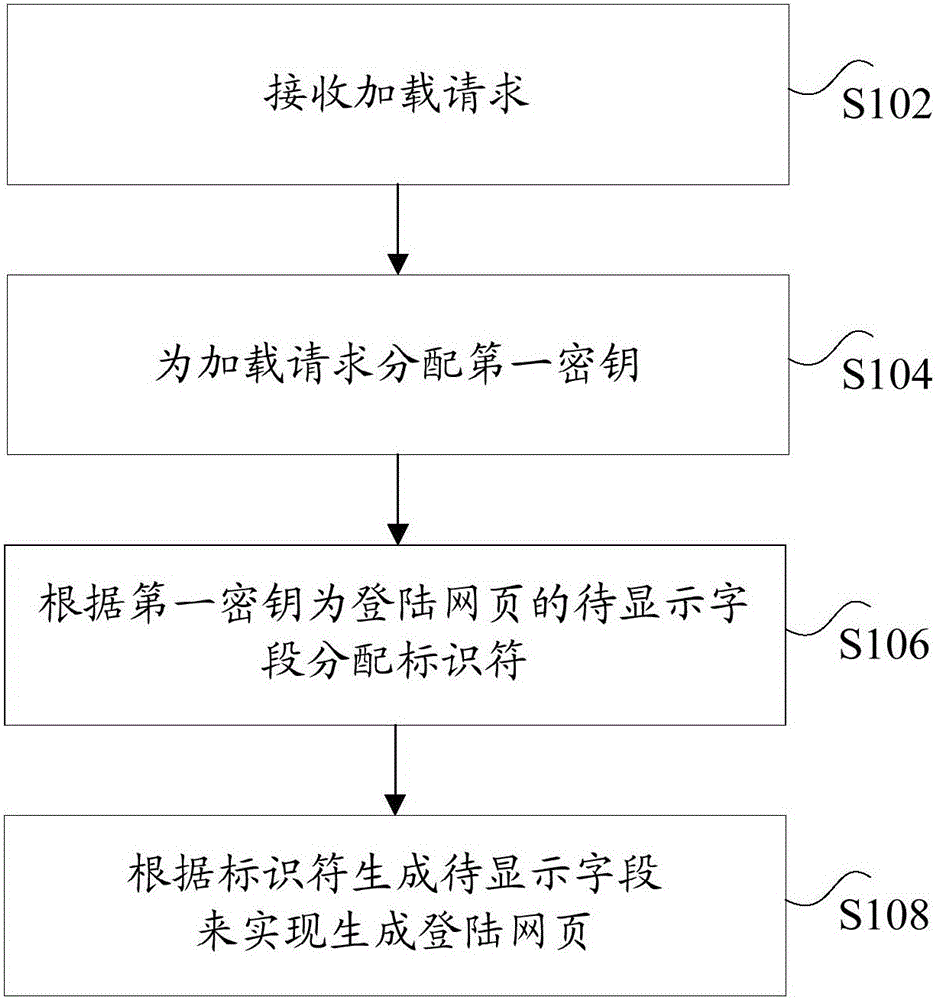
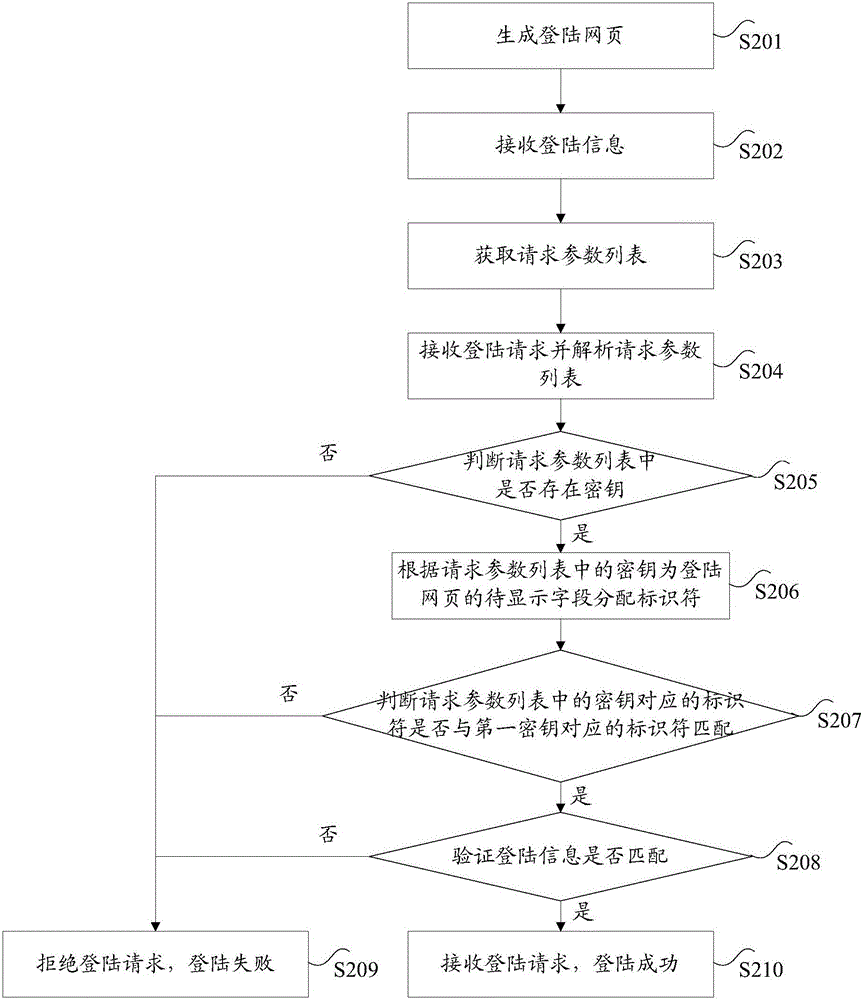
Method and device for generating login webpage
ActiveCN106302317APrevent brute force crackingSolve technical problems that are vulnerable to brute force crackingDigital data protectionTransmissionPasswordWeb page
The invention discloses a method and a device for generating a login webpage. The method comprises the steps of receiving a loading request, wherein the loading request is a request for loading a login webpage; allocating a first key to the loading request; allocating an identifier for a field to be displayed of the login webpage according to the first key, wherein a corresponding relation exits between the identifier and the first key; and generating the field to be displayed according to the identifiers so as to realize generation of the login webpage. The method and the device disclosed by the invention solve a technical problem that a password of the login webpage is easy to be forcibly broken in the prior art.
Owner:BEIJING GRIDSUM TECH CO LTD
Account authentication method and device
InactiveCN109981626AImprove experiencePrevent brute force crackingDigital data authenticationTransmissionComputer terminalInformation security
The embodiment of the invention provides an account authentication method and device, and relates to the technical field of information security. The method comprises the steps that after an authentication request which is sent by a user terminal and carries account information of an account to be authenticated is received, the number of times of continuous authentication failure corresponding tothe account to be authenticated is obtained; when the number of times of continuous authentication failures is larger than or equal to a preset verification threshold value, indication information issent to the user terminal, and the indication information is used for indicating input of a verification code; if the verification code sent by the user terminal is received and it is determined thatthe received verification code passes the verification, the to-be-authenticated account IS authenticated according to the account information; and if the verification code sent by the user terminal isnot received or it is determined that the received verification code does not pass the verification, the authentication request is discharded. By adopting the method, the user experience can be improved.
Owner:NEW H3C SECURITY TECH CO LTD
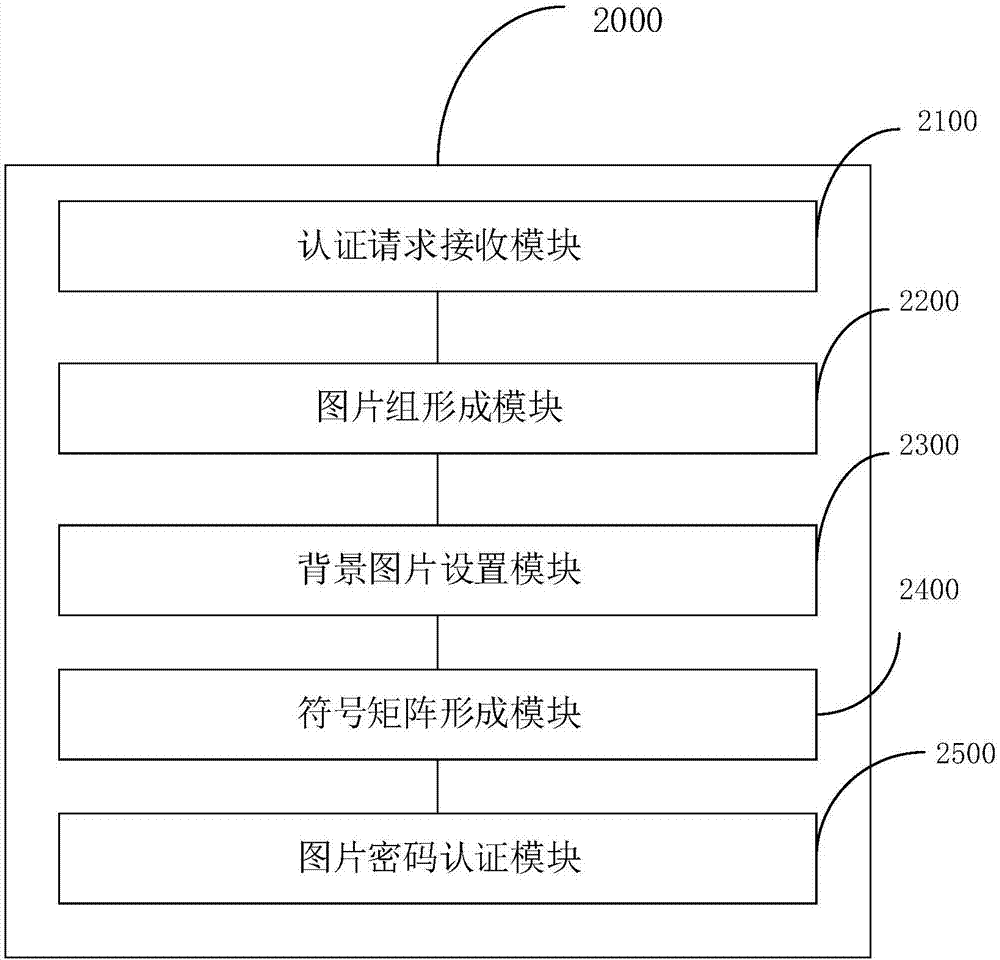
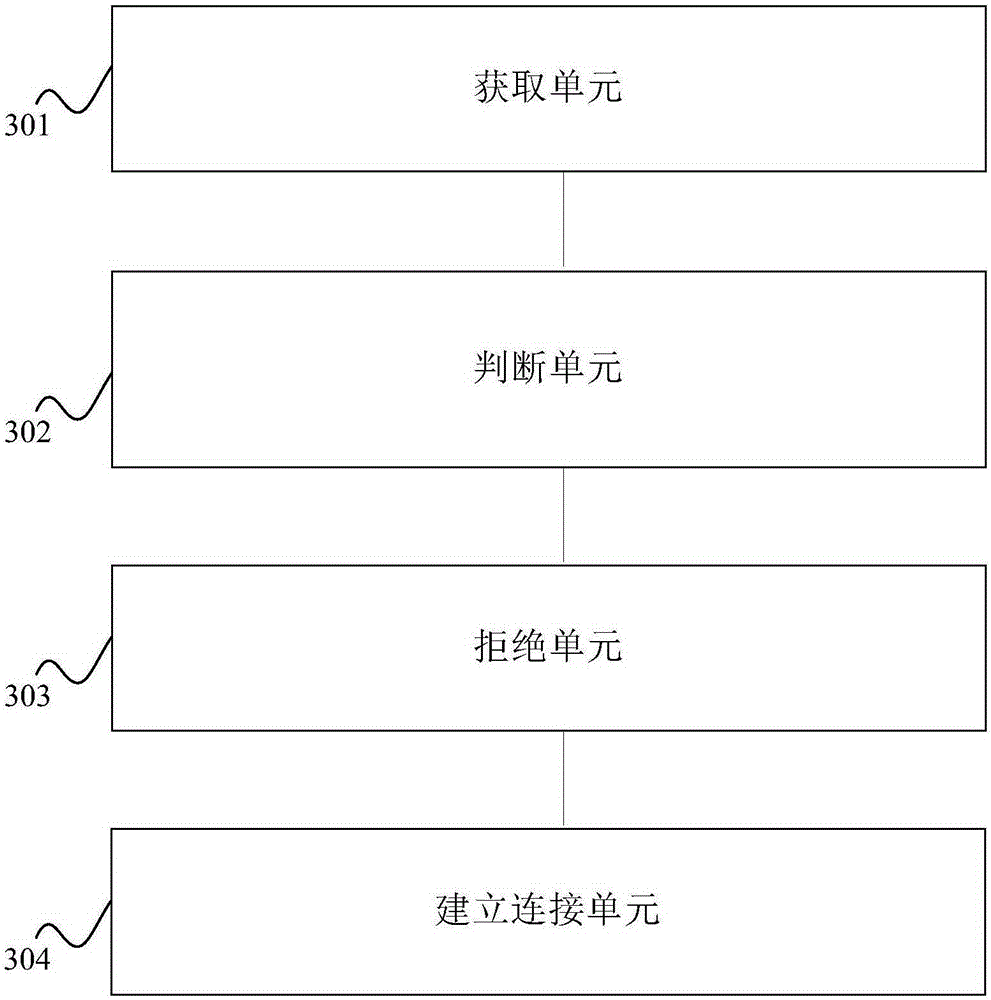
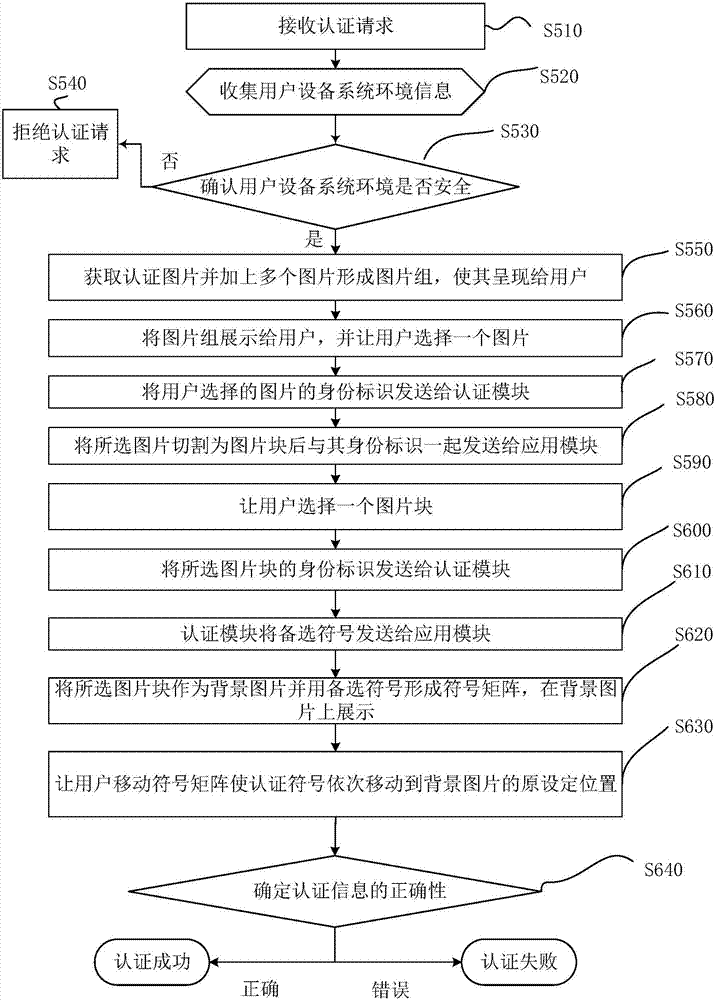
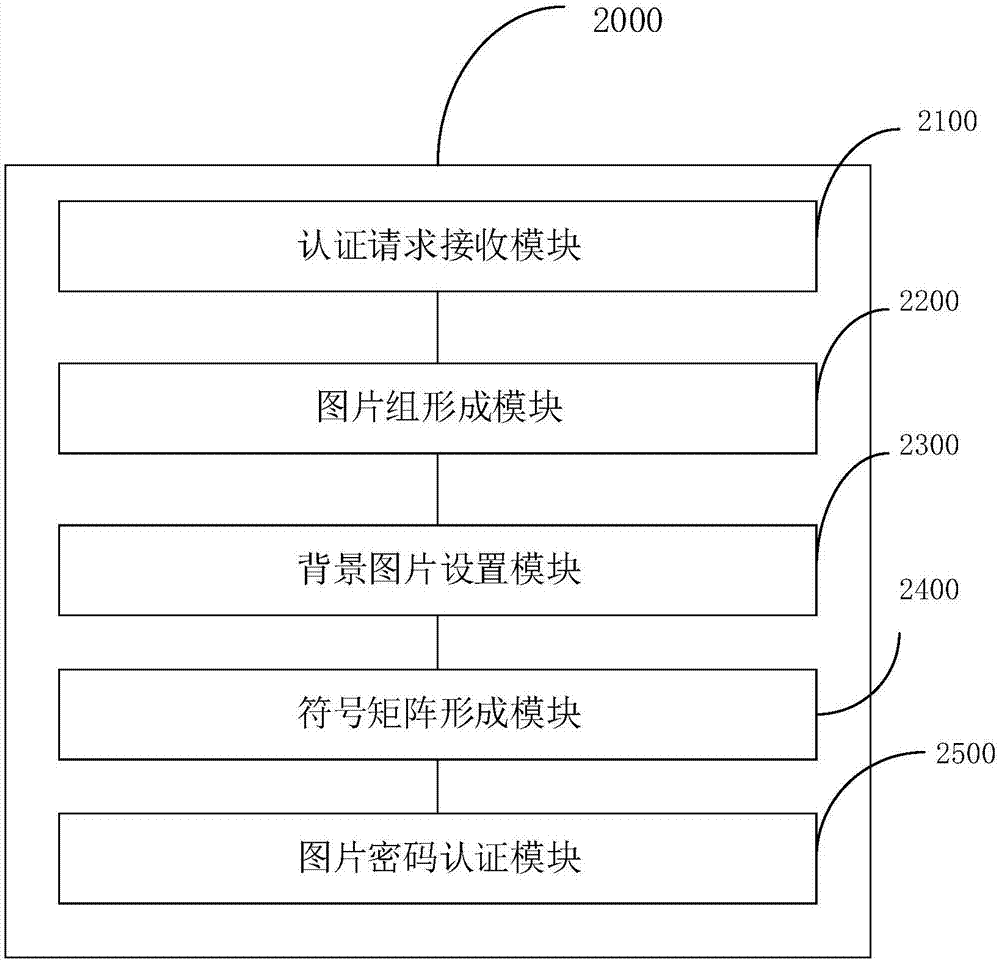
Picture password authentication method and picture password authentication device
InactiveCN106997432ATo prevent theftNo chance of being stolenDigital data authenticationTransmissionPasswordUser authentication
The invention discloses a picture password authentication method and a picture password authentication device. The picture password authentication method comprises the following steps that: initiating an authentication request, wherein the authentication request comprises unique identification related to a user; according to the unique identification, obtaining an authentication picture, and adding a plurality of pictures to form a picture group; requesting the user to select one picture; taking one picture selected by the user as a background picture, and in addition, forming a symbol matrix by alternative symbols during the generation of a picture password; enabling the user to move the symbol matrix in the background picture to move an authentication symbol to a position during the generation of the picture password; and determining whether the user selects a correct background picture or not, determining whether the authentication symbol is moved to the same position during the generation of the picture password or not, if the background pictures are correct, proving that user authentication is successful, and otherwise, proving that authentication fails. The authentication method and the authentication device of the invention are high in reliability, and are unlikely to generate the problems that the password is stolen and leaked and the like.
Owner:SECBOOT INFORMATION TECH CO LTD
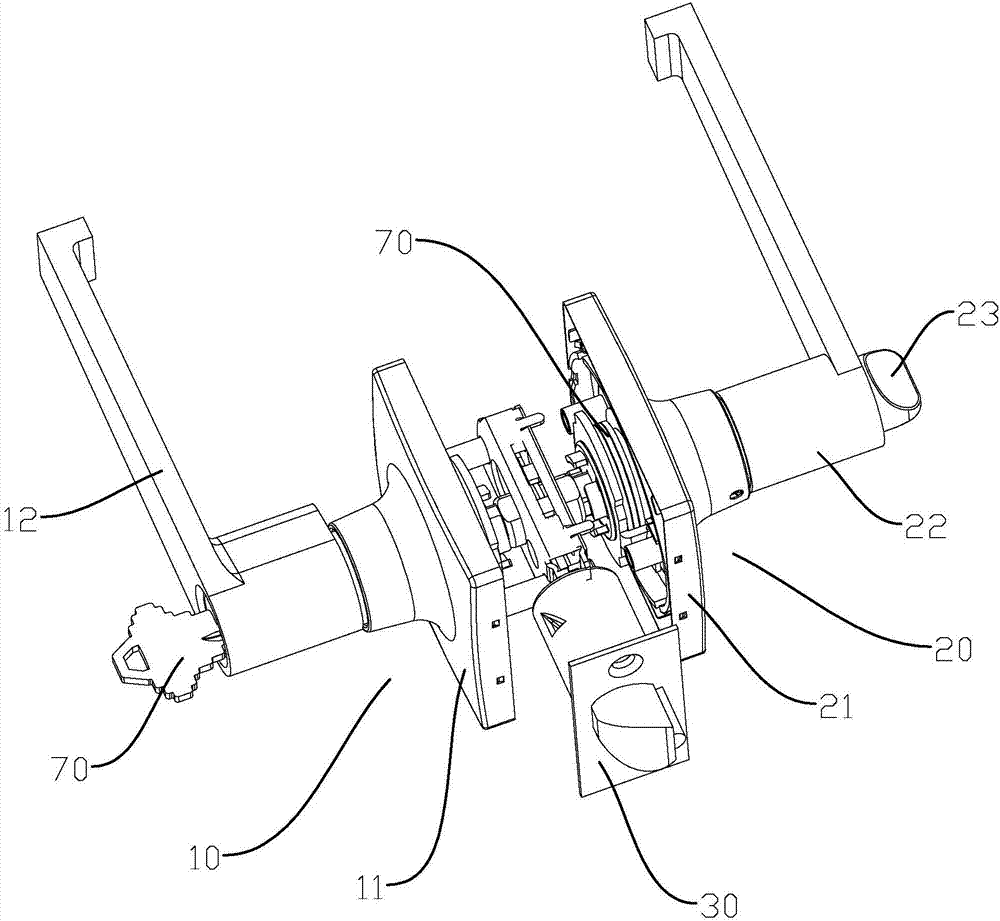
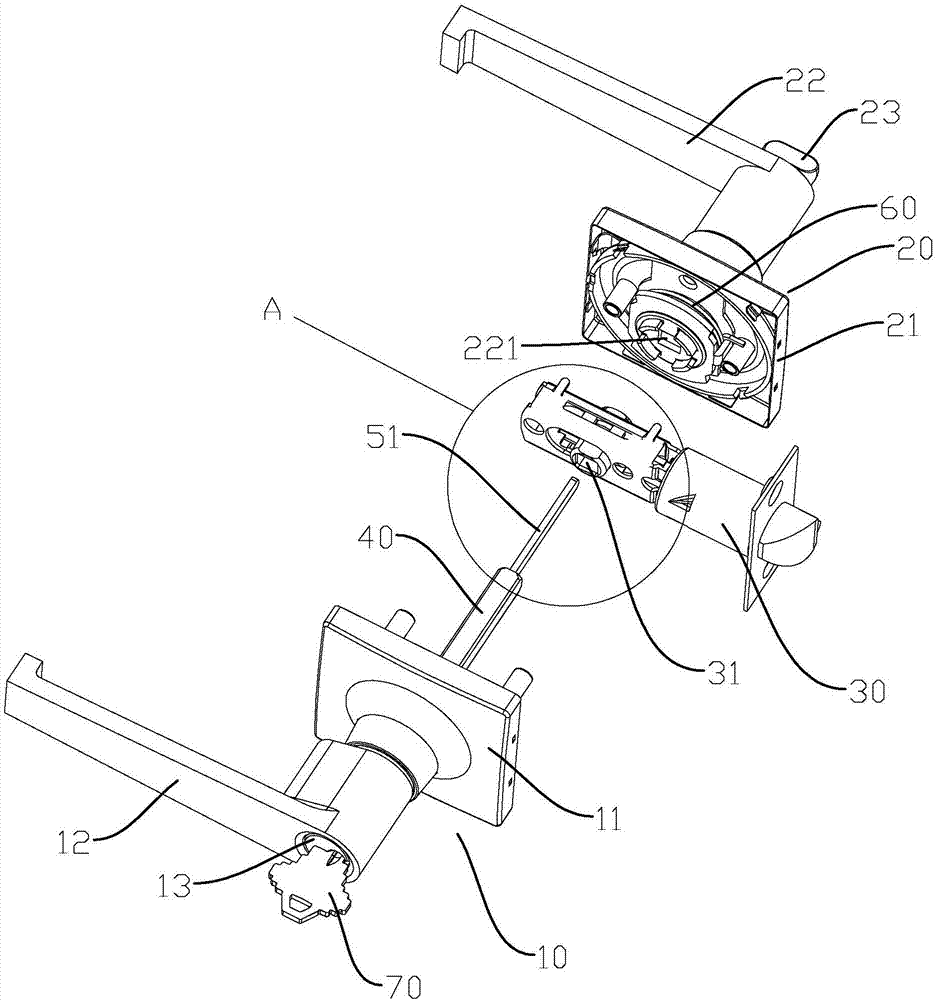
Idle safety door lock
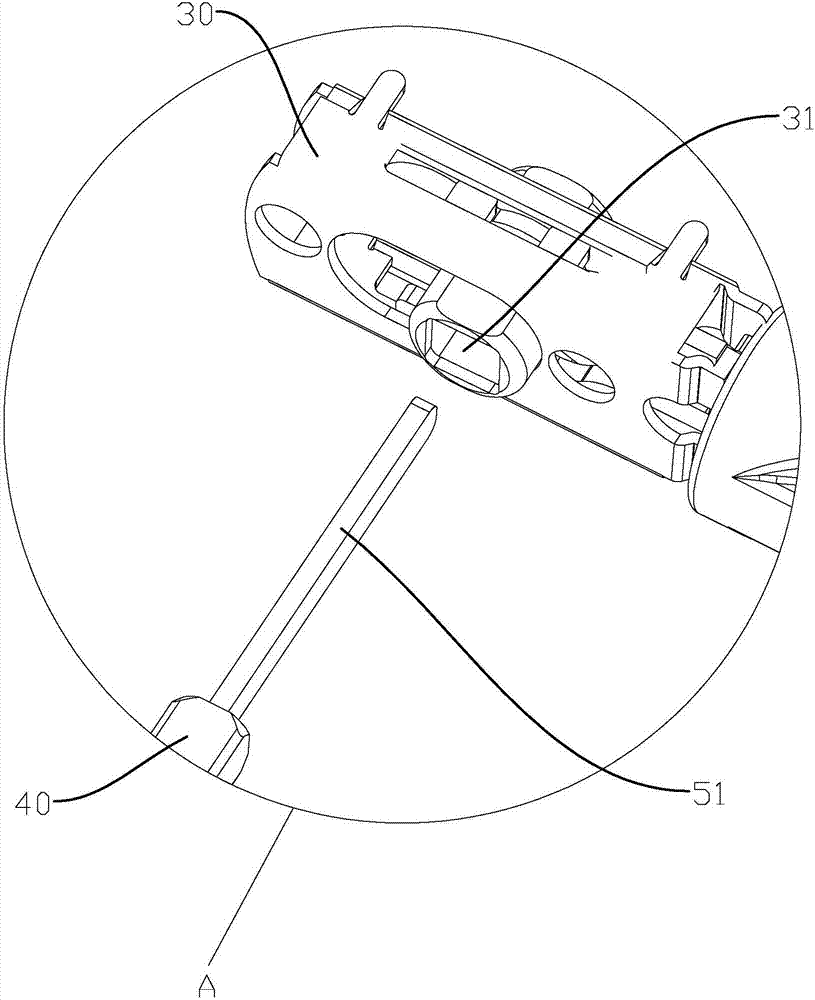
PendingCN107119990APrevent looseningAvoid damageLock casingsHandle fastenersSeparated stateStructural engineering
The invention discloses an idle safety door lock which comprises a front face plate assembly, a rear face plate assembly, a lock body and a transmission part. The front face plate assembly comprises a front base and a front lever handle arranged on the front base in a rotating manner. The rear face plate assembly comprises a rear base and a rear lever handle arranged on the rear base in a rotating manner. The transmission part is arranged on the front face plate assembly and / or the rear face plate assembly in a rotating manner. The transmission part is connected with the lock body. The front lever handle and the rear lever handle can drive the transmission part to rotate so as to control unlocking and locking action of the lock body when rotating. The front face plate assembly is provided with a lock cylinder. The front lever handle is connected with the transmission part through a clutch mechanism. The lock cylinder can switch the combination state and the separation state between the front lever handle and the transmission part through the clutch mechanism. According to the idle safety door lock, the situation that all parts of the door lock are loosened and damaged can be effectively avoided, the service life is prolonged, the violent cracking way of screwing the front lever forcibly to damage the front face plate assembly can be prevented, safety antitheft performance of the door lock is effectively improved, and use is facilitated.
Owner:胡淳龙
Authentication method and device
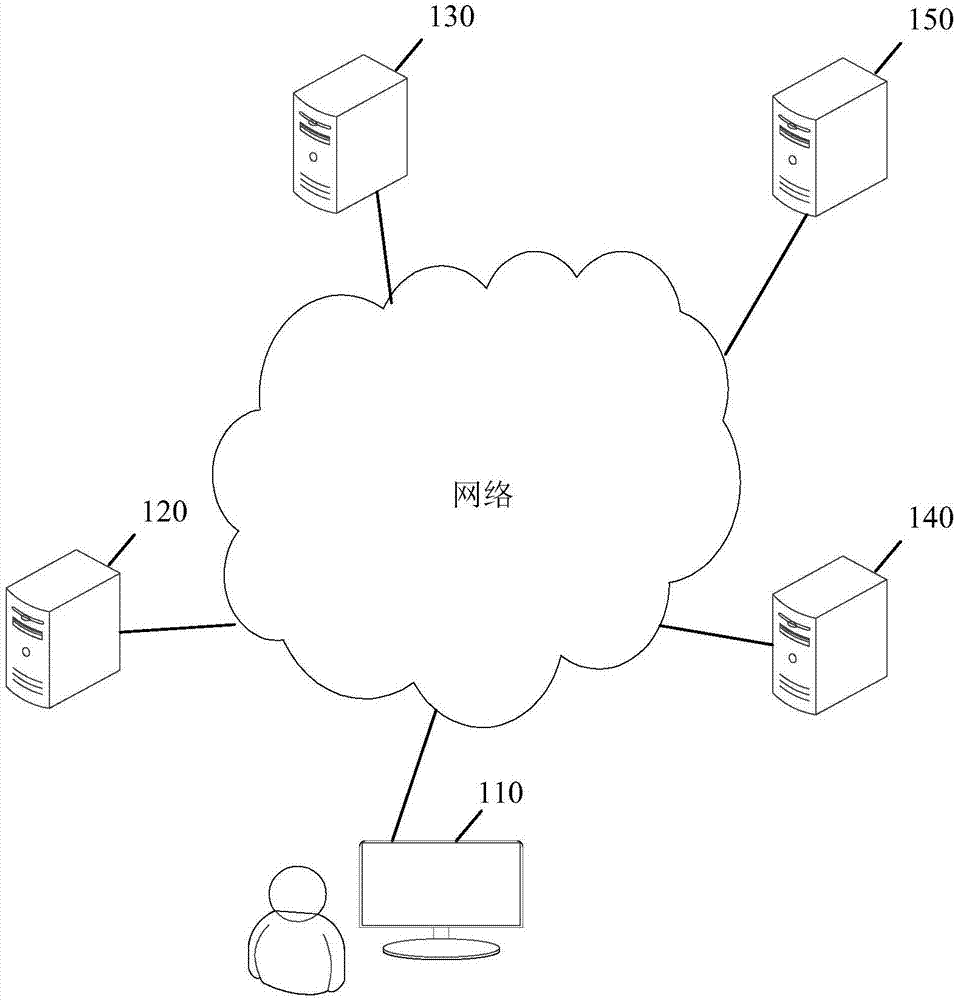
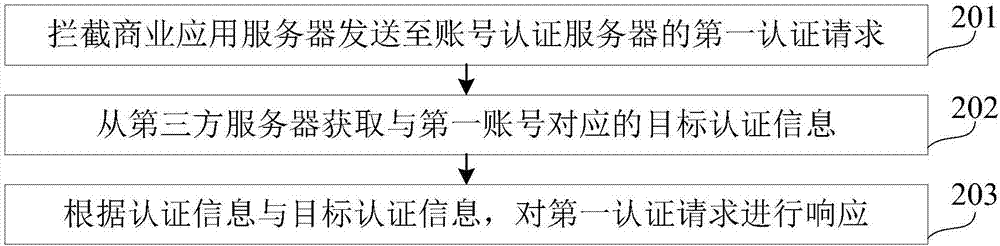
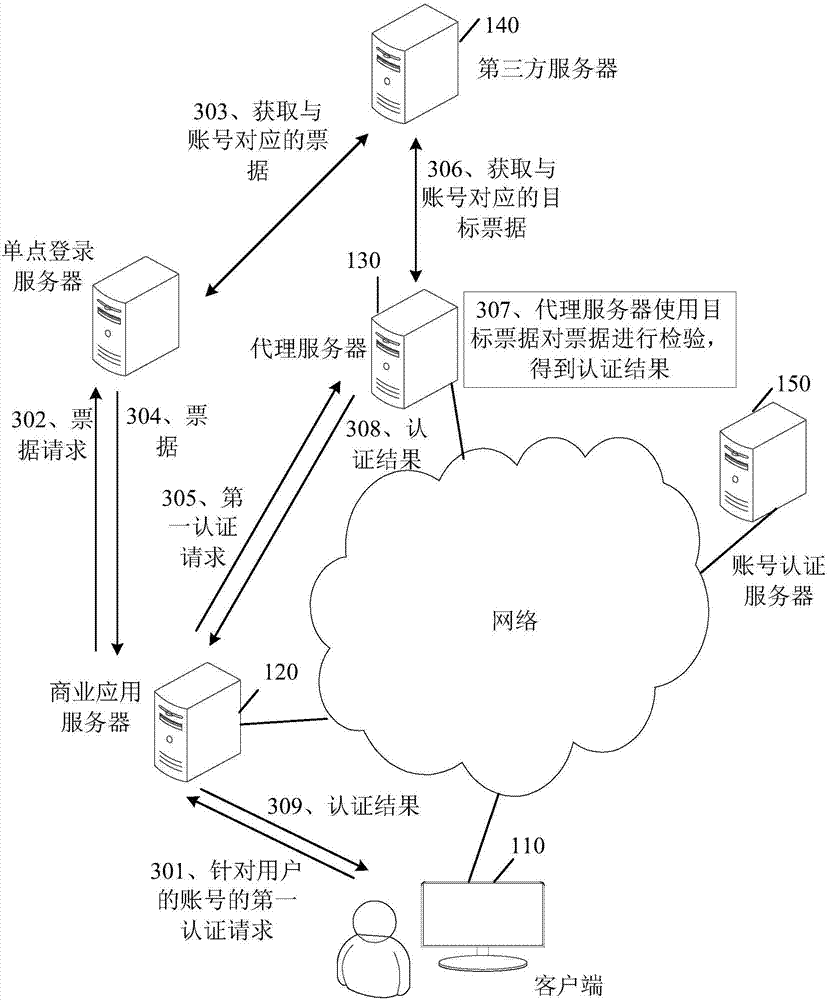
ActiveCN107395566AImprove experiencePrevent brute force crackingUser identity/authority verificationThird partyApplication server
The invention discloses an authentication method and a device. The method comprises the following steps: intercepting a first authentication request sent to an account authentication server by a business application server, wherein the first authentication request comprises an account and the authentication information; acquiring the target authentication information corresponding to the account from the third-party server; and responding to the first authentication request according to the authentication information and the target authentication information. The technical scheme disclosed by the invention can realize the account authentication based on the third party, and the risk of password leakage is lowered.
Owner:BEIJING XIAOMI MOBILE SOFTWARE CO LTD
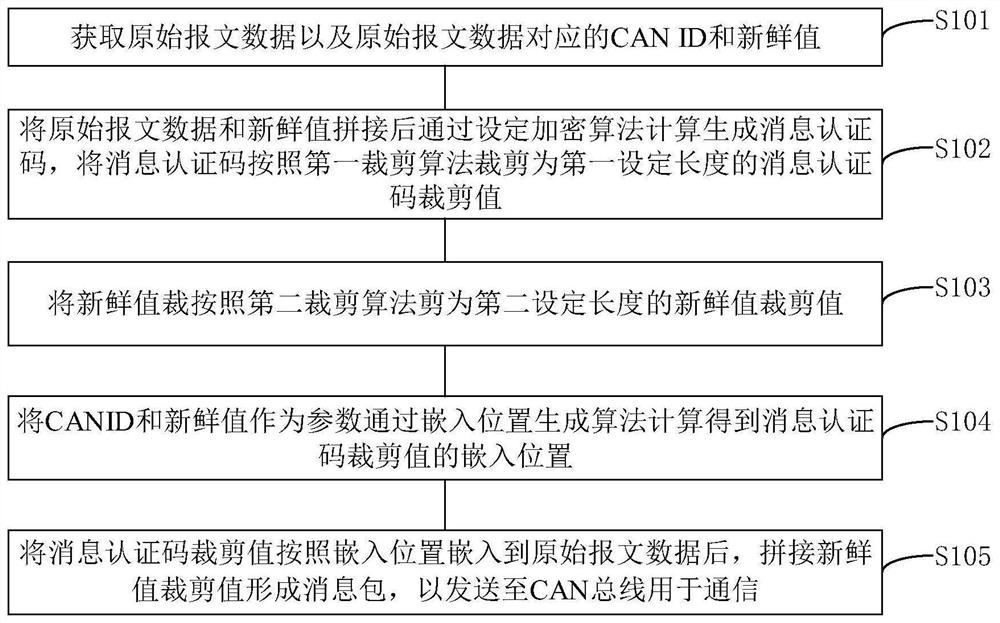
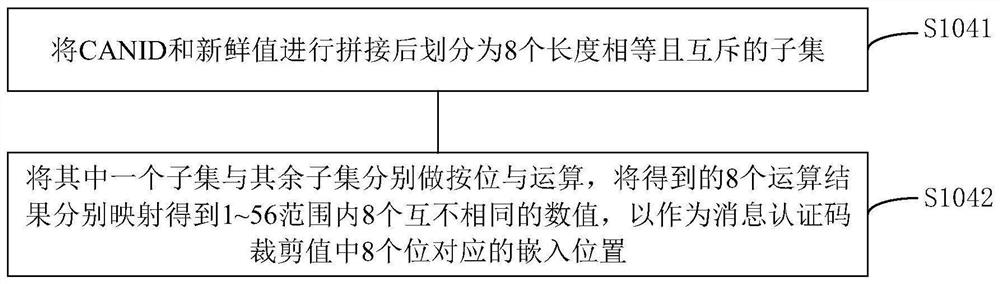
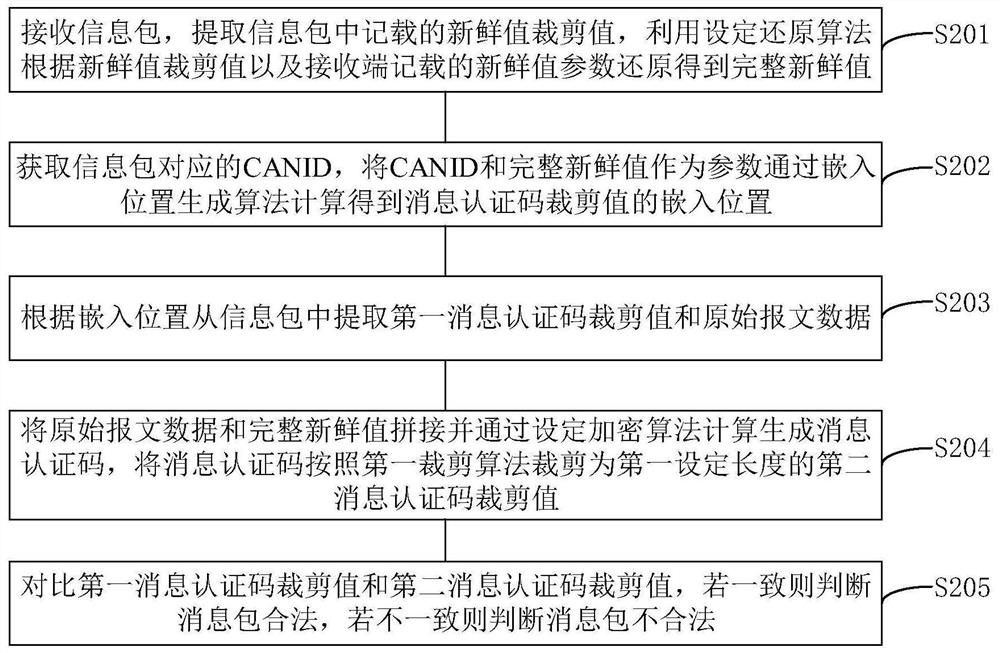
In-vehicle network safety communication sending and receiving method and device
ActiveCN112134702APrevent brute force crackingPreventing the Threat of Replay AttacksKey distribution for secure communicationUser identity/authority verificationSecure communicationMessage authentication code
The invention provides an in-vehicle network safety communication sending and receiving method and device. The method comprises the steps that a sending end generates a message authentication code according to original message data and a fresh value, and carries out the cutting of the message authentication code to obtain a message authentication code cutting value; and the message authenticationcode cutting value is embedded into the original message data based on the embedding position generated by the CAN ID and the fresh value, and the message authentication code cutting value is splicedwith the fresh value cutting value to obtain a to-be-sent message packet. The receiving end extracts a fresh value cutting value from the message packet, supplements the fresh value cutting value according to a first fresh value of a previous message recorded by the receiving end and a second fresh value of a counter of the receiving end to obtain a complete fresh value, calculates an embedded position according to the fresh value and the CAN ID, and extracts a first message authentication code cutting value and original message data; and a message authentication code is calculated according to the original message data and the fresh value, and cut to obtain a second cutting value for comparing and verifying the legality of the message. The method can effectively prevent the cutting valueof the message authentication code from being violently cracked, and prevent the threat of a replay attack.
Owner:BEIJING UNIV OF POSTS & TELECOMM
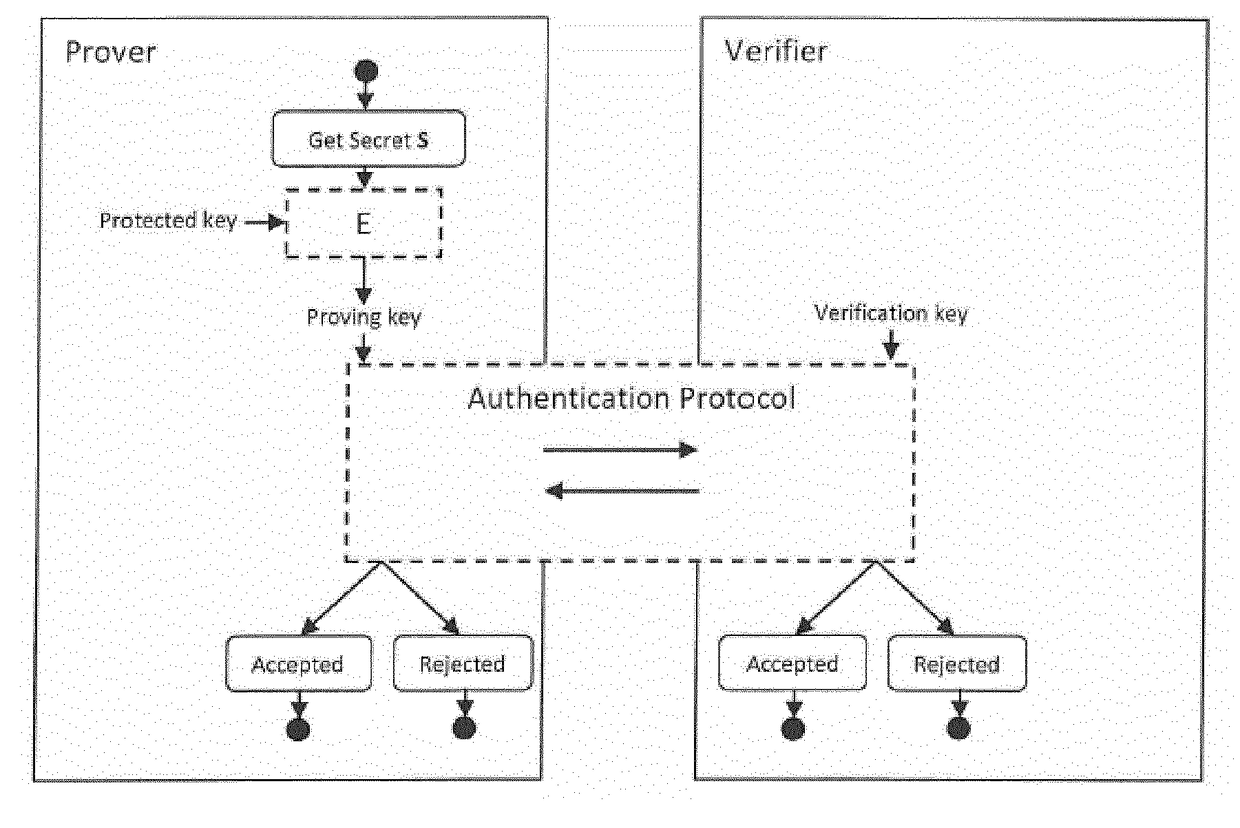
A method and device for authentication
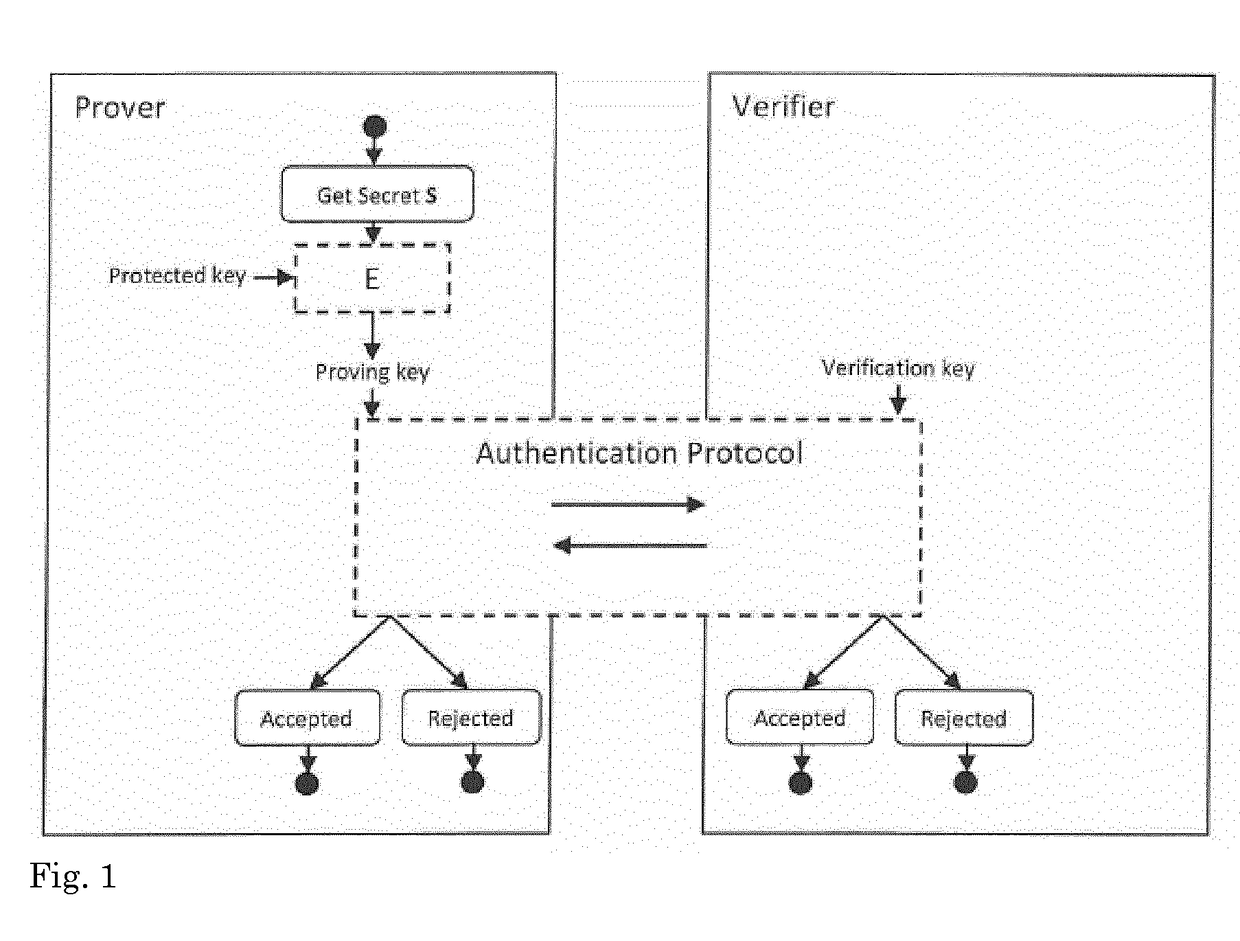
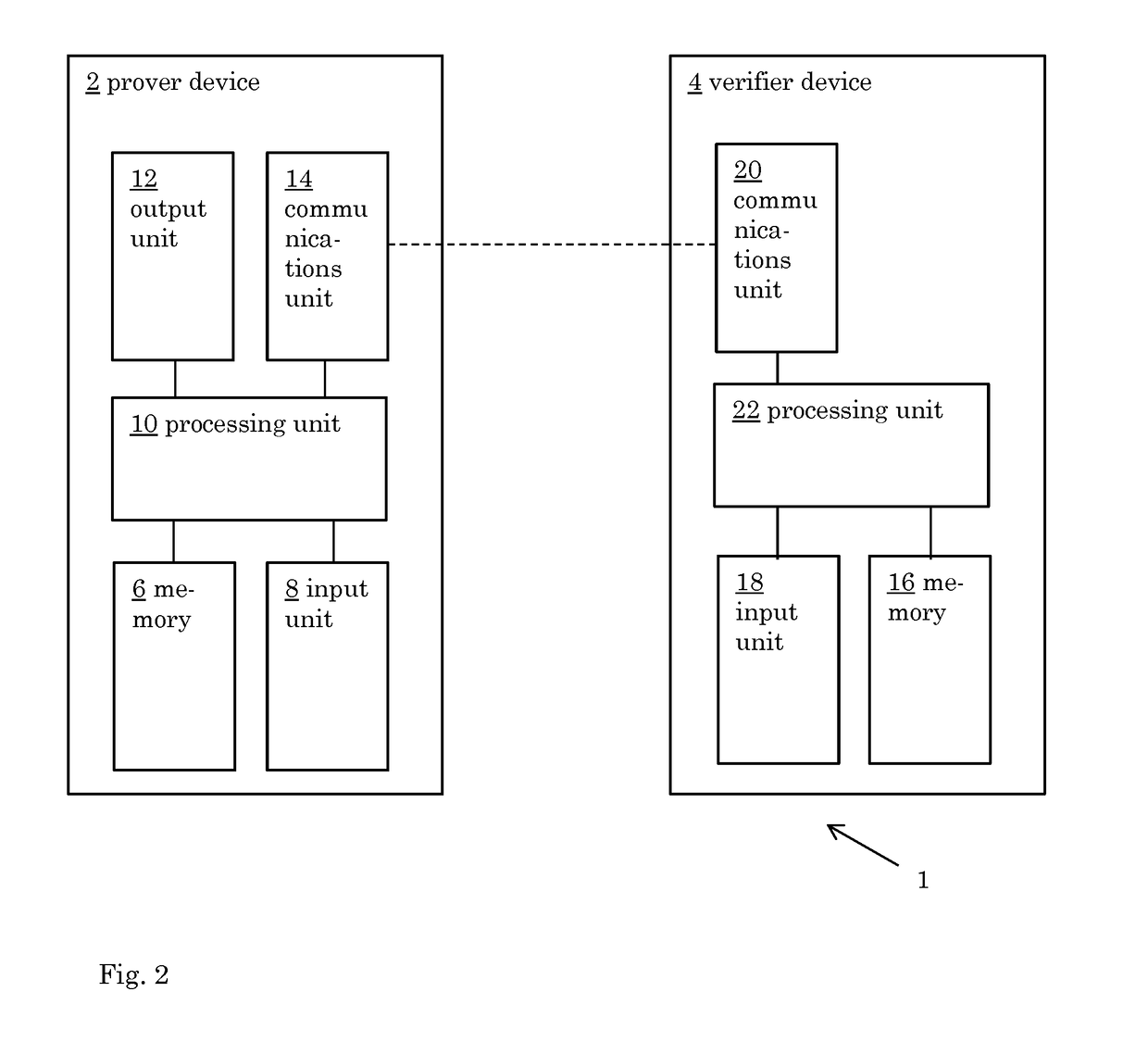
ActiveUS20170331631A1Prevent brute force crackingAvoid recoveryKey distribution for secure communicationUser identity/authority verificationAuthentication
A method for authenticating a prover to a verifier, the prover being provided with a proving key paired to a verification key registered with the verifier, wherein the proving key can be obtained by transforming a protected key and a secret (S) using a transformation (E), characterized in that the prover stores the protected key and does not store the corresponding proving key nor the corresponding verification key in clear, with the exception of storage in transient memory.
Owner:NEXTAUTH NV
Oil well antitheft box set
InactiveCN105239951ADoes not affect daily wellhead operationsPrevent brute force crackingBuilding locksSealing/packingOil wellWellhead
The invention relates to the technical field of burglary prevention of oil fields, and in particular, discloses an oil well antitheft box set. Antitheft boxes are mounted on an oil transmission pipe, and comprise a union antitheft box, a pressure gauge antitheft box and a sampling antitheft box; the union antitheft box and the pressure gauge antitheft box comprise upper shells and lower shells; the lower shells comprise left shells and right shells; locking structures are arranged between the left shells and the right shells; the sampling antitheft box comprises a plug shell and a sample port shell; the plug shell comprises a left shell and a right shell; a locking structure is arranged between the left shell and the right shell; and novel columnar locks are distributed between the left shells and the right shells, between the upper shells and the lower shells and between the plug shell and the sample port shell. The oil well antitheft box set has the following advantages: the antitheft boxes can effectively use the actual shape of a well mouth for protecting the well mouth under the condition of smallest volume to prevent crude oil from being stolen, and are matched with the novel columnar locks as an antitheft lock for use to prevent violent break by cutting nippers and hacksaws.
Owner:陈亮
Intelligent low-speed electric vehicle anti-theft device
The invention discloses an intelligent low-speed electric vehicle anti-theft device which comprise a main control module is used for monitoring and controlling a low-speed electric vehicle intelligent anti-theft device body, a battery control module capable of controlling the on / off of the battery output, a reset module determining a starting working state of the main control module, a crystal oscillator module providing a clock signal for the main control module, a keyboard input module and a display module for a user to input a password and to carry out interaction, a loudspeaker alarm module connected with the main control module and a honking device of a low-speed electric vehicle and a GSM alarm module, wherein the loudspeaker alarm module can receive a signal of the main control module to emit an alarm sound, and the GSM alarm module can receive the signal of the main control module to send information to the user. According to the object of the intelligent low-speed electric vehicle anti-theft device, different modules of the low-speed electric vehicle intelligent anti-theft device is accurately controlled according to the state of different low-speed electric vehicles, and an early warning is made through the different modules.
Owner:JILIN UNIV +1
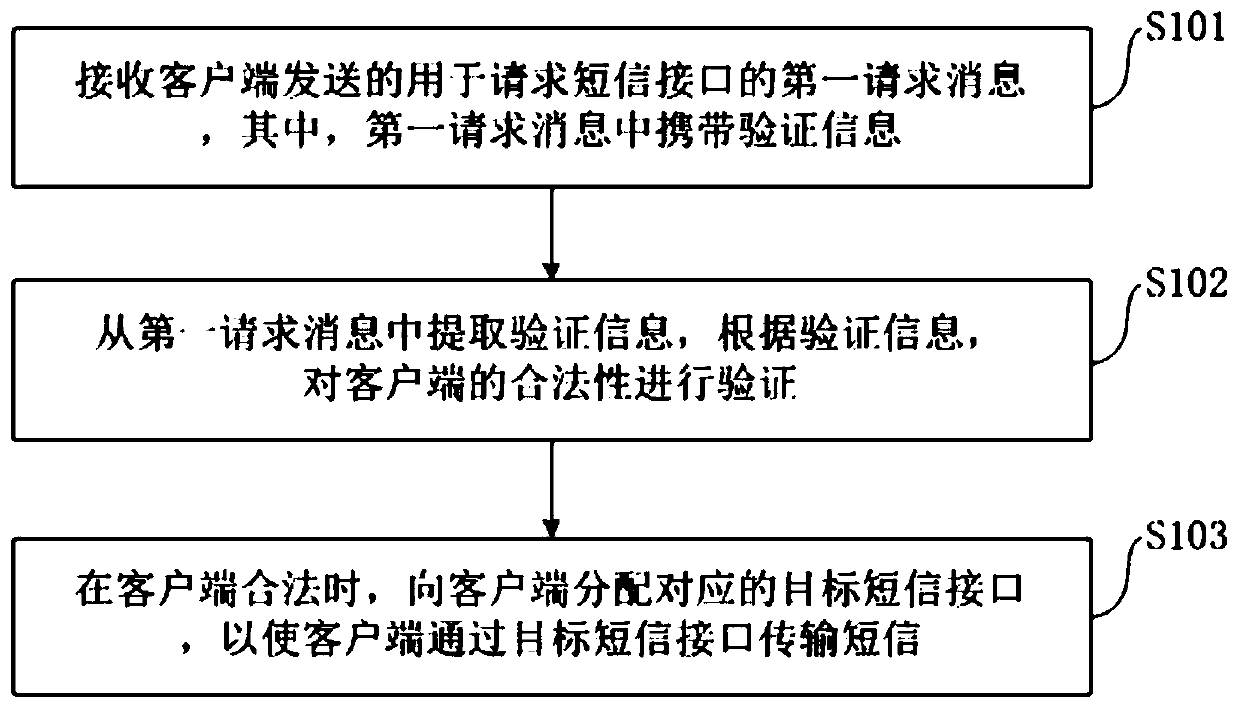
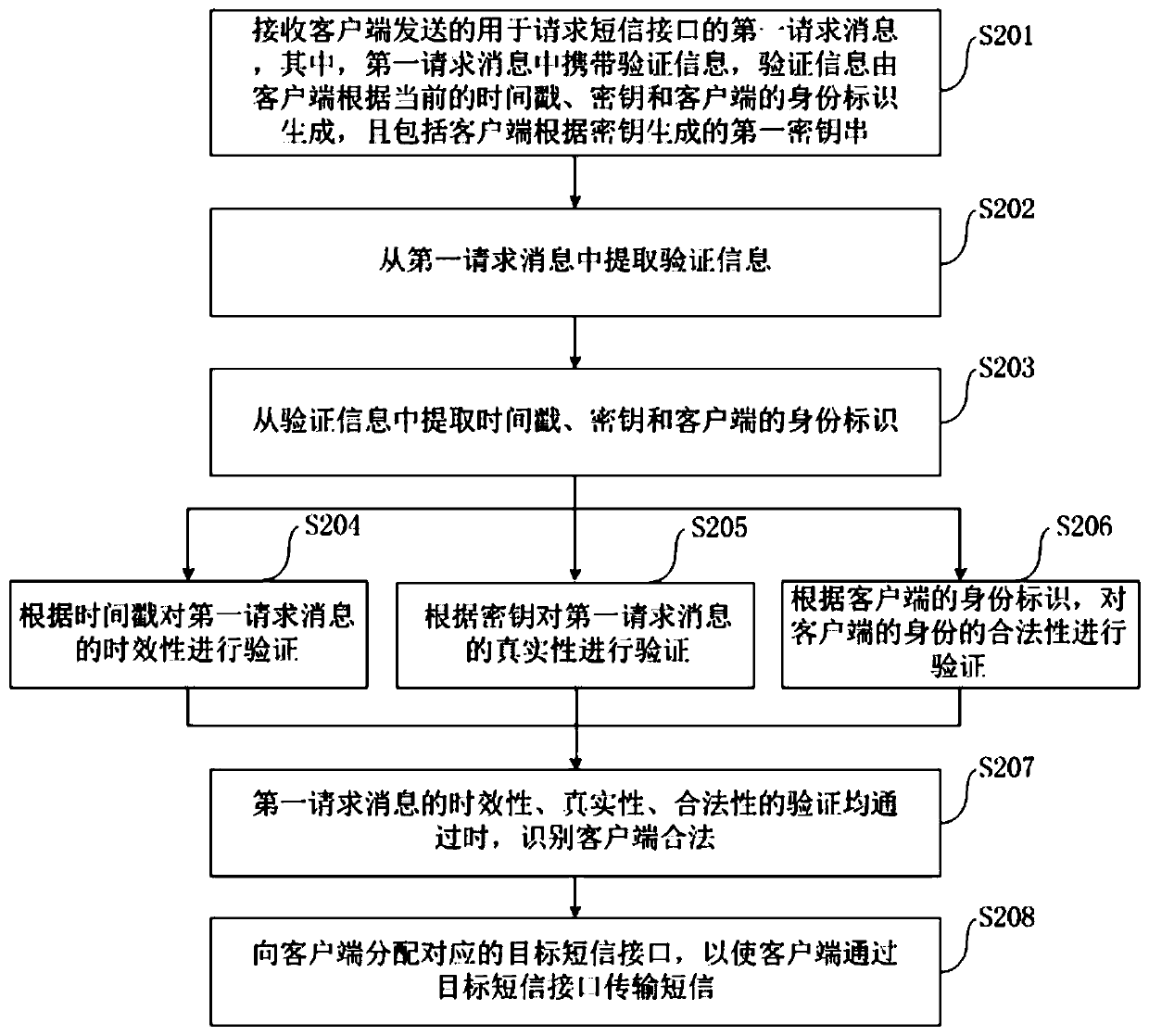
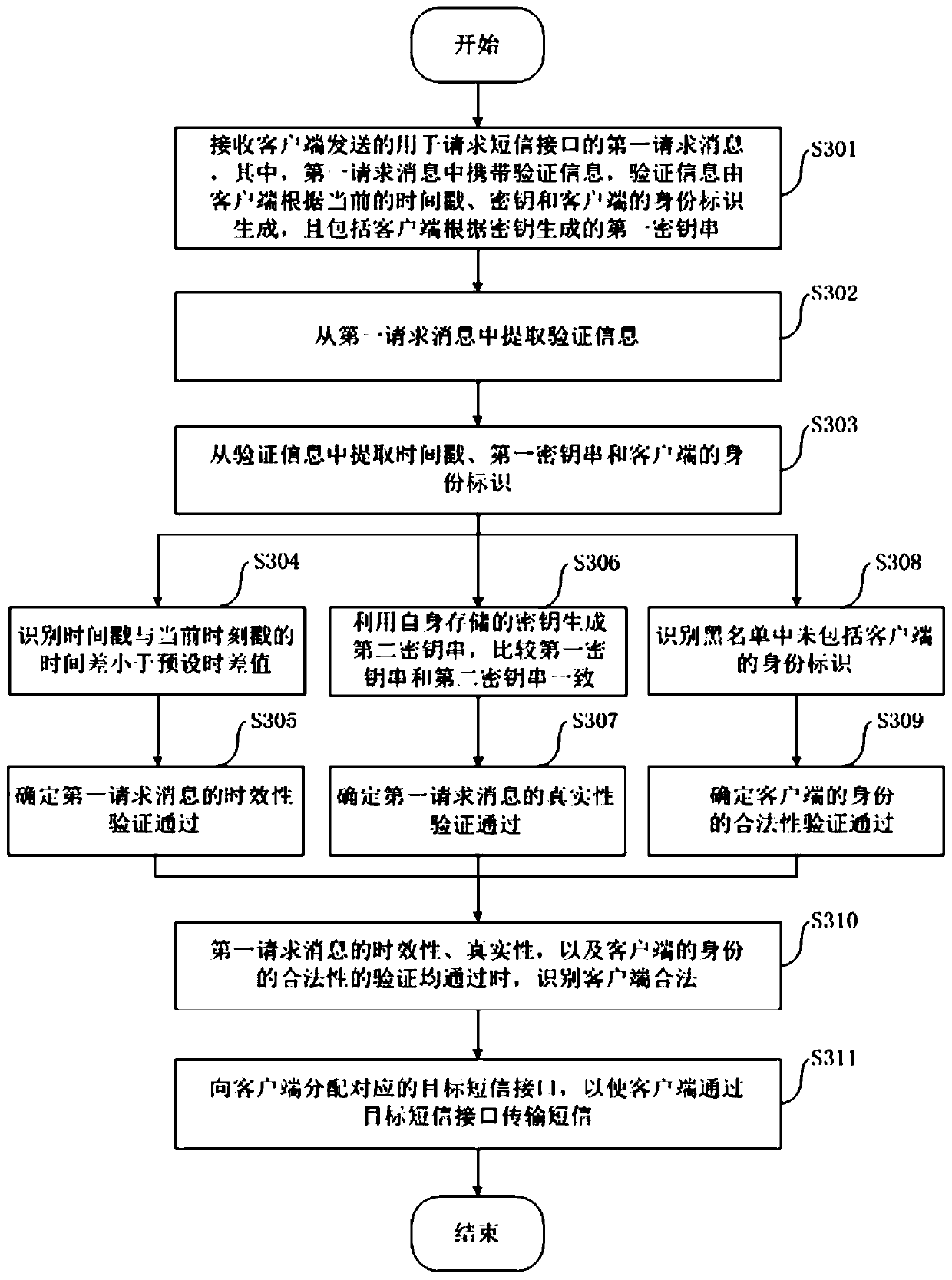
Short message interface distribution method, server, client and system
InactiveCN110891249APrevent brute force crackingImprove securityMessaging/mailboxes/announcementsSecurity arrangementDistribution methodEngineering
The invention discloses a short message interface distribution method, a server, a client and a system. The method comprises the following steps of receiving a first request message which is sent by aclient and used for requesting a short message interface wherein the first request message carries verification information; extracting the verification information from the first request message, and verifying the legality of the client according to the verification information; and when the client is legal, allocating a corresponding target short message interface to the client, so that the client transmits a short message through the target short message interface. The server can extract the verification information from the request message which is sent by the client and used for requesting the short message interface, verifies the legality of the client according to the verification information, and distributes the corresponding short message interface to the client when the clientis legal, so that violent cracking of the short message interface can be effectively prevented, and the safety and reliability of the short message interface are improved.
Owner:HEFEI MIDEA INTELLIGENT TECH CO LTD
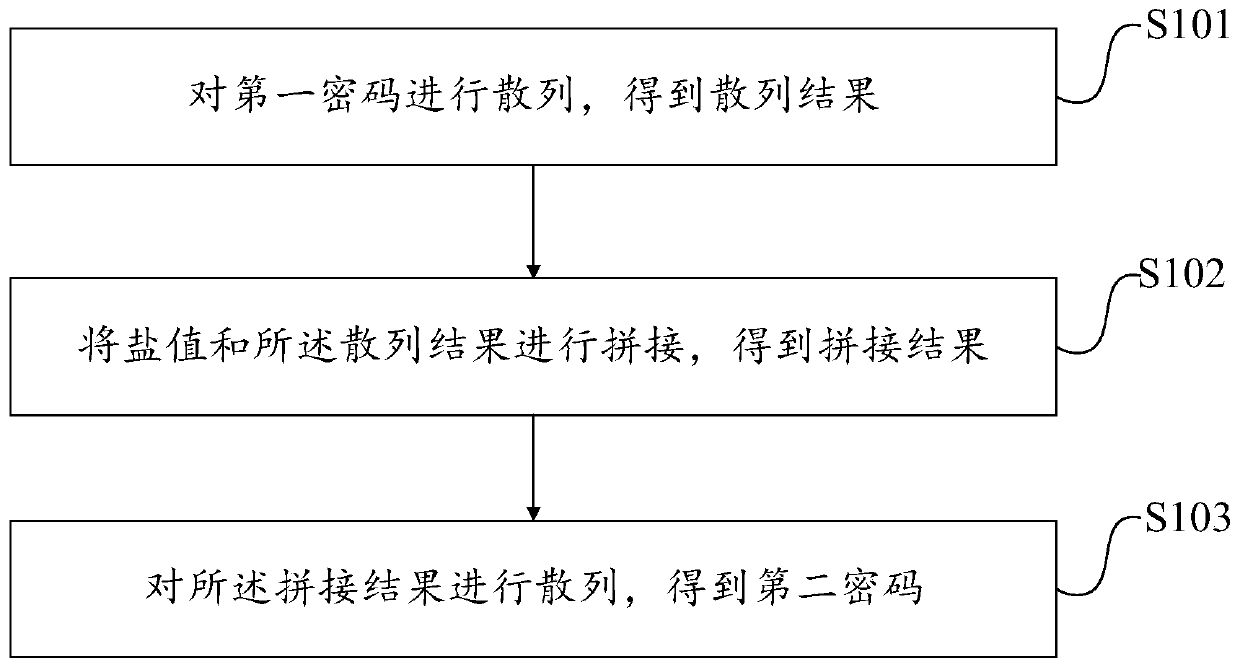
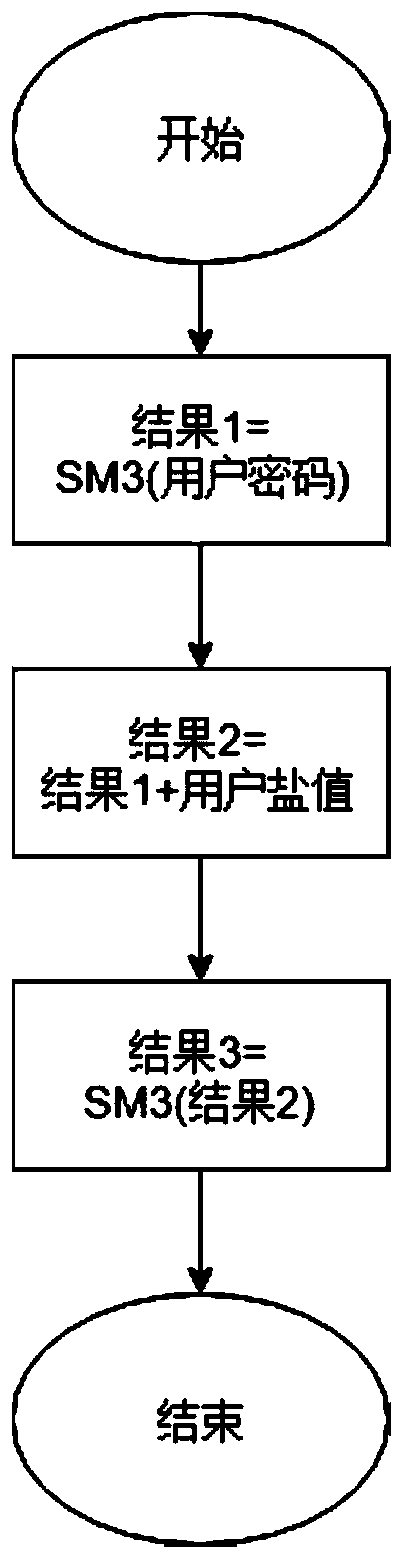
Password generation and authentication method and device, electronic equipment and medium
PendingCN111181714APrevent brute force crackingImprove securityKey distribution for secure communicationEncryption apparatus with shift registers/memoriesPasswordSecret code
The embodiment of the invention discloses a password generation and authentication method and device, electronic equipment and a medium. The password generation method comprises the steps of hashing afirst password to obtain a hash result; splicing the salt value and the hash result to obtain a splicing result; and hashing the splicing result to obtain a second password. The password is hashed through the salt value to serve as a variable generated by the password, and the hash result of the password and the salt value serves as a new secret key, and therefore the purposes of preventing bruteforce cracking and improving secret key safety are achieved.
Owner:AEROSPACE INFORMATION
Invitation code generation method and device, terminal equipment and storage medium
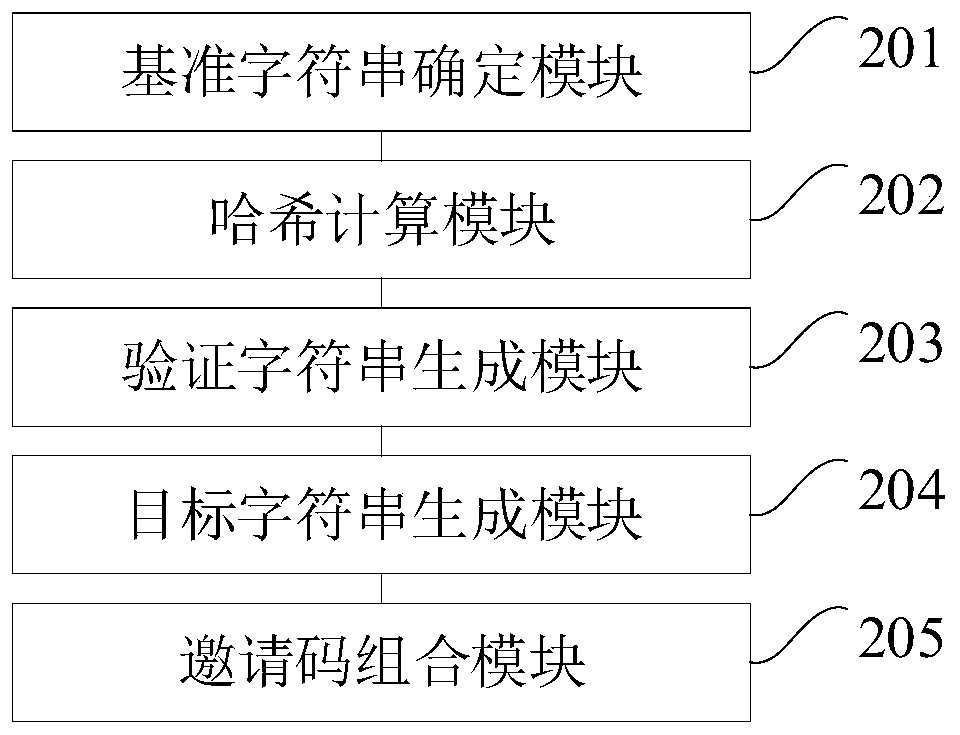
ActiveCN110489466AImprove securityEnsure safetyDatabase management systemsOther databases indexingGeneration processArray data structure
The embodiment of the invention is suitable for the technical field of information, and provides an invitation code generation method and device, terminal equipment and a storage medium, and the method comprises the steps: determining a reference character string for generating an invitation code; performing hash calculation on the reference character string to generate an MD5 value; generating ahash array according to the reference character string and the MD5 value, and converting the hash array into a verification character string according to a preset rule; performing position transformation on the reference character string by adopting the hash array to generate a target character string; and combining the verification character string and the target character string into an invitation code. In the generation process of the embodiment, hash calculation only needs to be executed once, and the efficiency of generating the invitation code is high; the verification character string in the generated invitation code can irregularly follow, and the invitation code cannot be cracked by modifying a certain character, so that the safety of the invitation code is improved.
Owner:PING AN SECURITIES CO LTD
Method and system for improving data transmission security
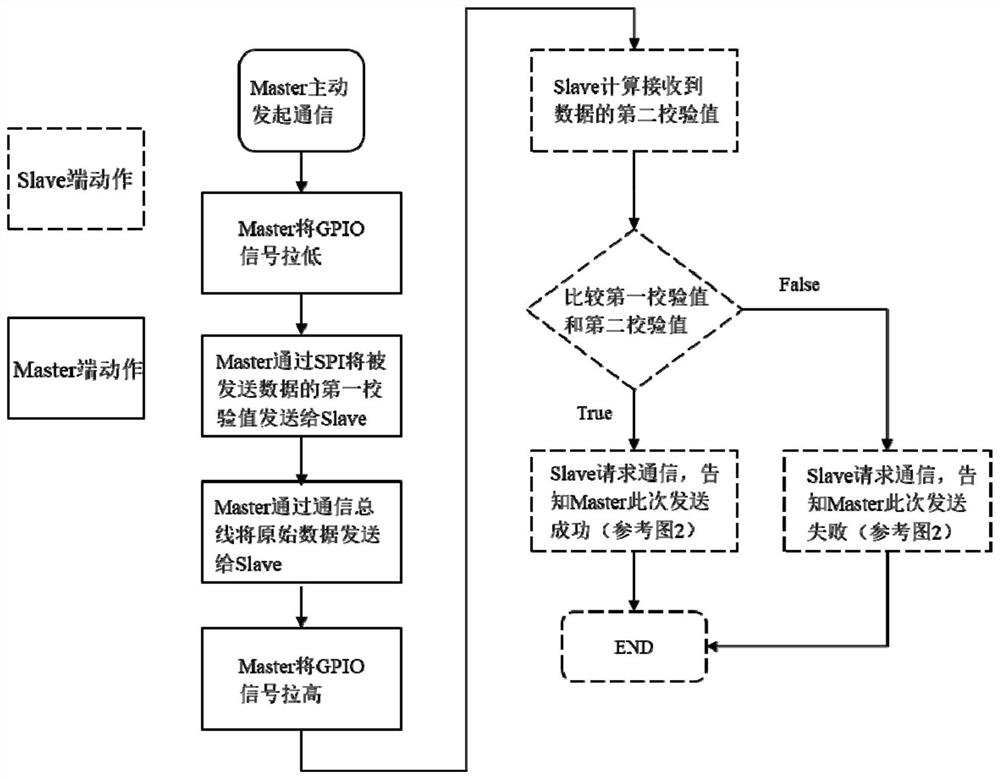
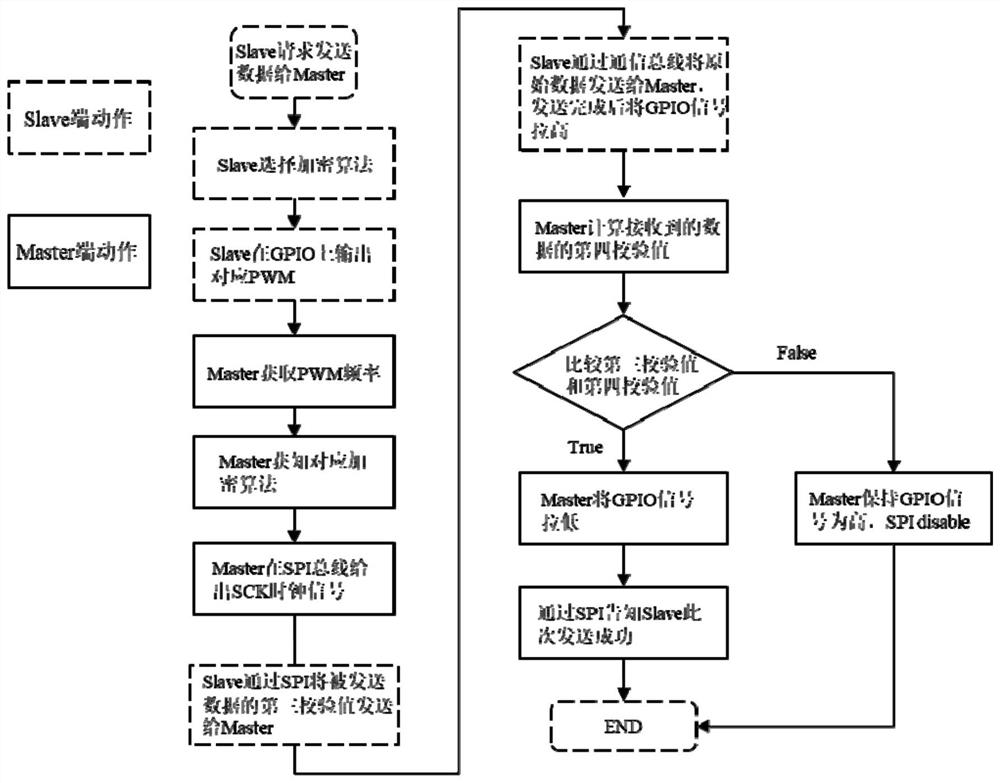
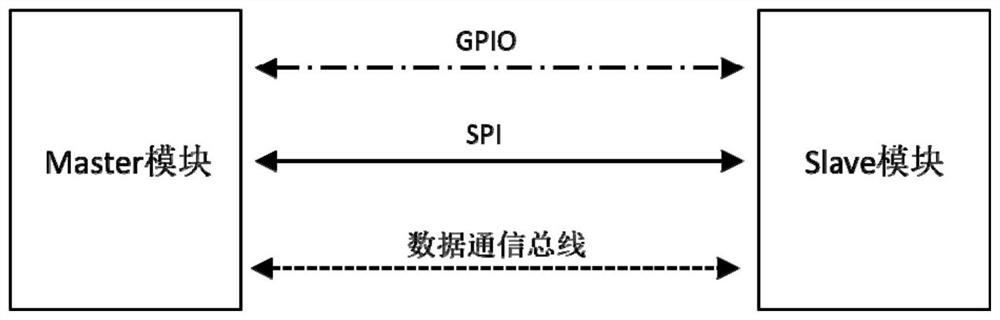
The invention discloses a method and a system for improving data transmission security. The method comprises the following steps of: connecting a Master end and a Slave end through GPIO (General Purpose Input / Output) and SPI (Serial Peripheral Interface) buses and a data communication bus; pulling down a GPIO (General Purpose Input / Output) signal of the Master end, actively initiating communication by the Master end, and transmitting interaction data and a corresponding check value to the Slave end; transmitting interaction data through a data communication bus, and transmitting a verification value through an SPI bus; enabling the Slave end to judge a transmission result of the data based on the received interaction data and the verification value; and outputting a PWM (Pulse Width Modulation) signal on a GPIO (General Purpose Input / Output) interface of the Slave end, requesting to initiate communication by the Slave end, and informing the Master end of the transmission result. According to the method, the validity of communication data is verified through GPIO and SPI buses, so that the security of data transmission is improved; and meanwhile, the verification value and the interaction data are sent through different buses, so that the security of data transmission is improved.
Owner:SUZHOU ZHIJIA SCI & TECH CO LTD
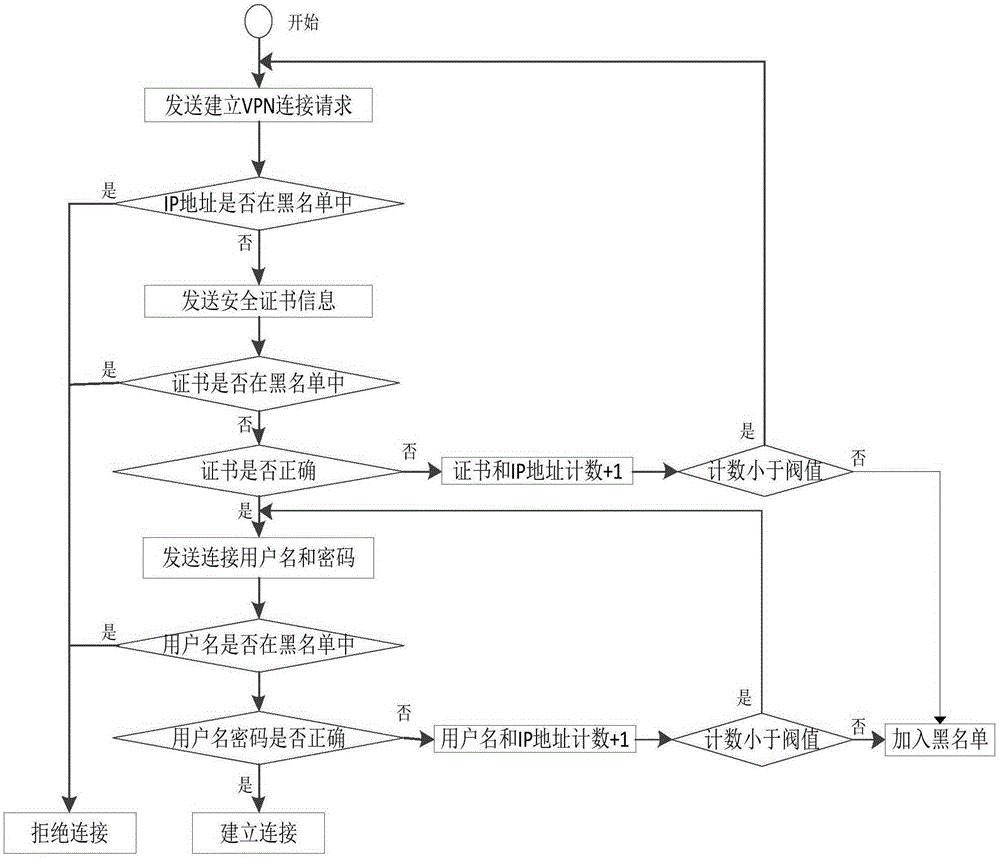
VPN (Virtual Private Network) connection method and system based on blacklist mechanism
The invention provides a VPN (Virtual Private Network) connection method based on a blacklist mechanism. The method comprises the following steps: when a request instruction of establishing VPN connection is received, acquiring feature information of a client performing VPN connection, wherein the feature information includes an IP address, a digital certificate summary, a user name and a password; judging whether the IP address, the digital certificate summary and the user name conform to corresponding information in a blacklist or not in sequence; if one of the IP address, the digital certificate summary and the user name conforms to the corresponding information in the blacklist, rejecting the VPN connection; and if all the IP address, the digital certificate summary and the user name do not conform to the corresponding information in the blacklist, and the digital certificate summary and the password are matched with a preset digital certificate summary and a preset password respectively, establishing the VPN connection. Through combination of VPN verification and the blacklist mechanism, hacker behaviors such as flooding attacks and brute force attacks can be prevented effectively.
Owner:INSPUR BEIJING ELECTRONICS INFORMATION IND
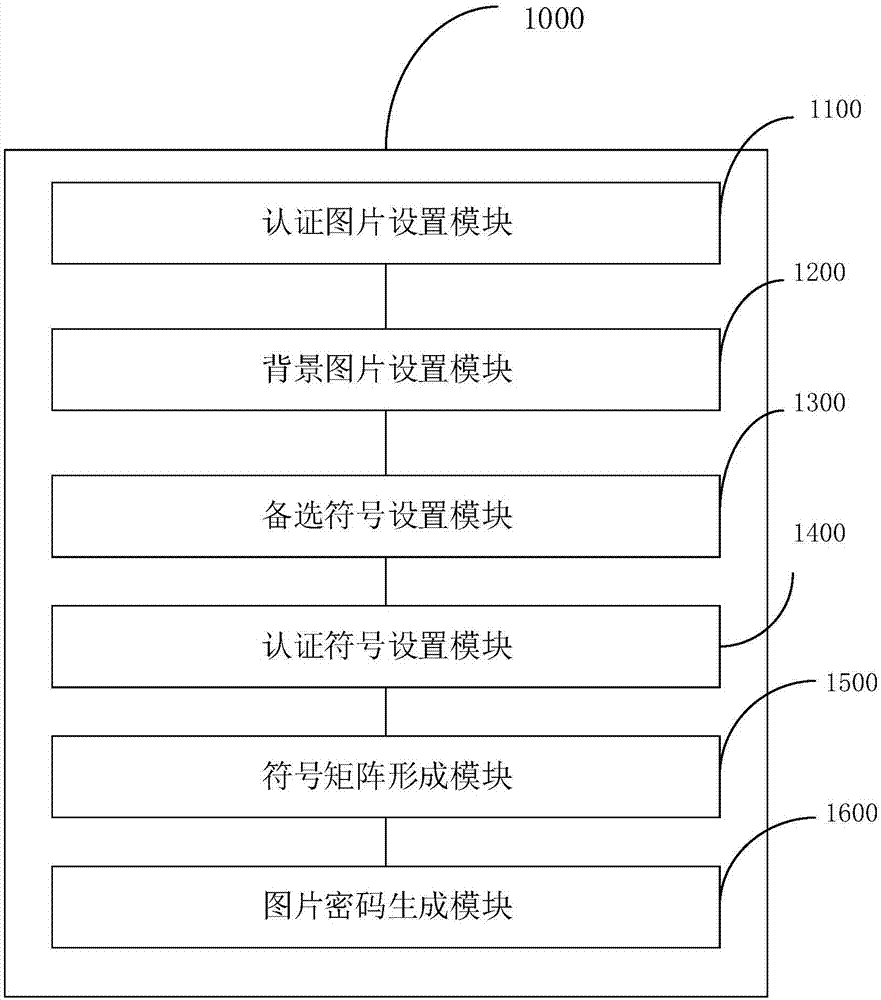
Image password generation method and image password generation device
ActiveCN107169341ATo prevent theftNo chance of being stolenDigital data protectionDigital data authenticationPasswordBackground image
The invention relates to an image password generation method and an image password generation device. The image password generation method comprises following steps: setting a user-selected image as an authentication image or selecting an authentication image directly from images of a system; setting a background image by means of the authentication image; requiring the user to select a symbol as a backup symbol; setting the symbol selected by the user from the backup symbols as an authentication symbol; generating a symbol matrix using symbols that contain the backup symbol and making the symbol matrix overlap on the background image and protrudingly displaying one authentication symbol; making the user drag the symbol matrix so that the highlighted authentication symbol is located at a desired position in the background picture to generate a picture password. The image password generated by this method is highly reliable.
Owner:SECBOOT INFORMATION TECH CO LTD
A login control method and device capable of preventing violent cracking
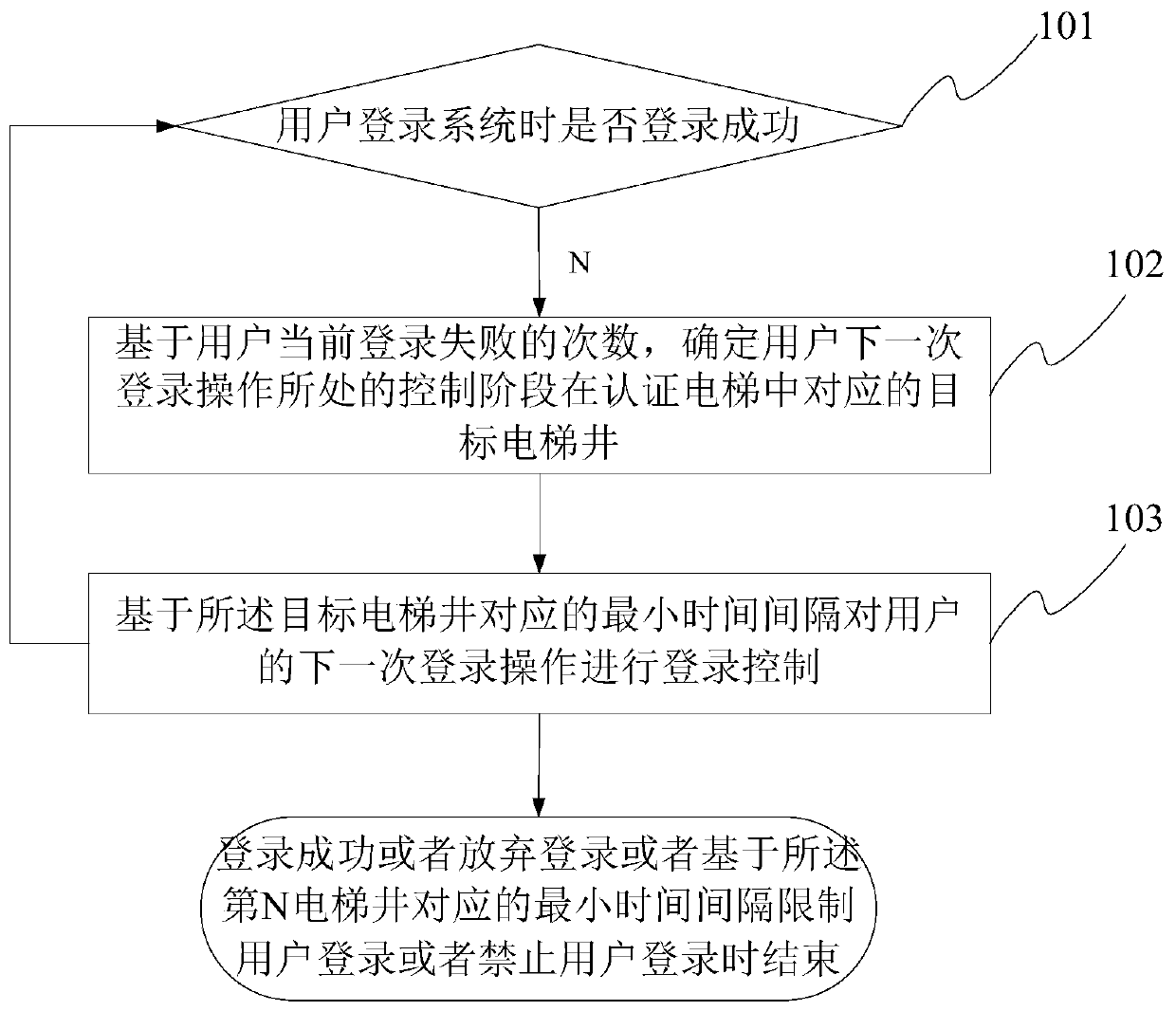
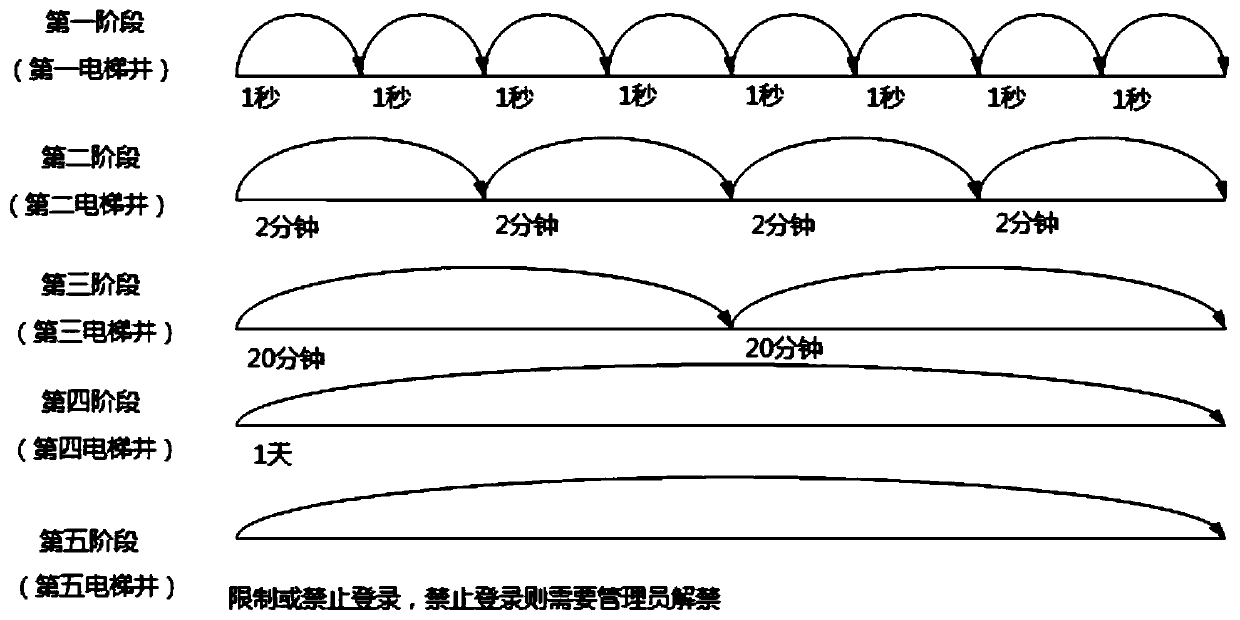
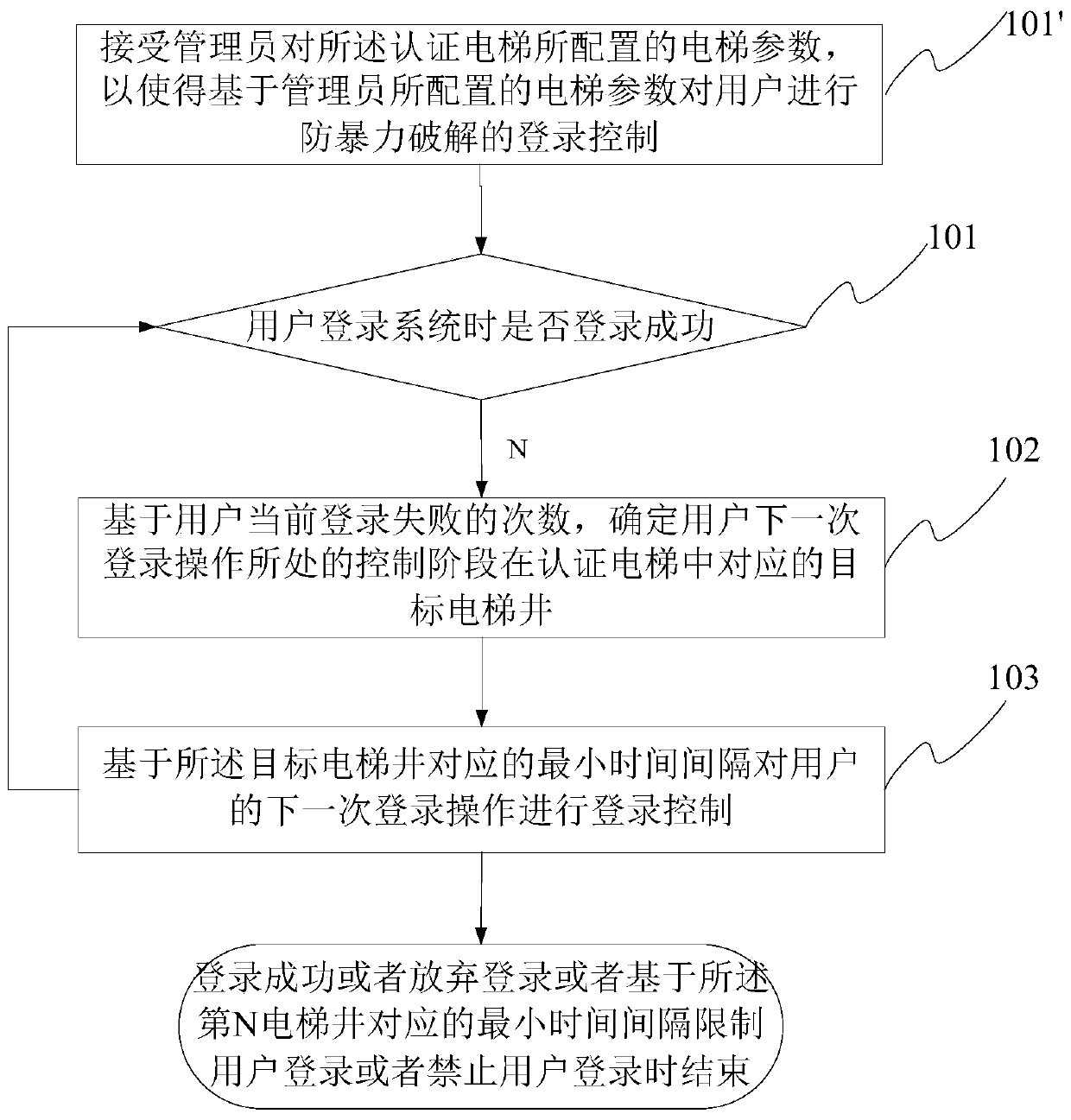
ActiveCN109714149APrevent brute force crackingImprove experienceSecuring communicationAuthorizationAuthentication
The invention discloses a login control method and device capable of preventing violent cracking. Violent cracking of a login authentication and authorization system is realized. According to the scheme of the invention, Continuous multiple login operations in the violent cracking process can be controlled based on authentication of all elevator shafts from the first to the Nth in the elevator; and finally, login operation of violent cracking can be limited or login of the violent cracking can be completely forbidden based on long limiting time required by the Nth elevator shaft. Therefore, violent cracking of the login authentication and authorization system can be effectively prevented by utilizing the scheme of the invention; In addition, relevant parameters for authenticating the elevator are configurable; a dynamic login attack prevention function is realized; Meanwhile, compared with a conventional verification mode based on a verification code, a verification picture and the like in the prior art, the method focuses on using an intelligent authentication means based on an authentication elevator at a system end to prevent attacks, a user does not need to execute complex interactive operation, the intelligent degree is high, and the user experience is effectively improved.
Owner:蓝卓数字科技有限公司
Privacy protection method of sensing information virtual service in Internet of Things
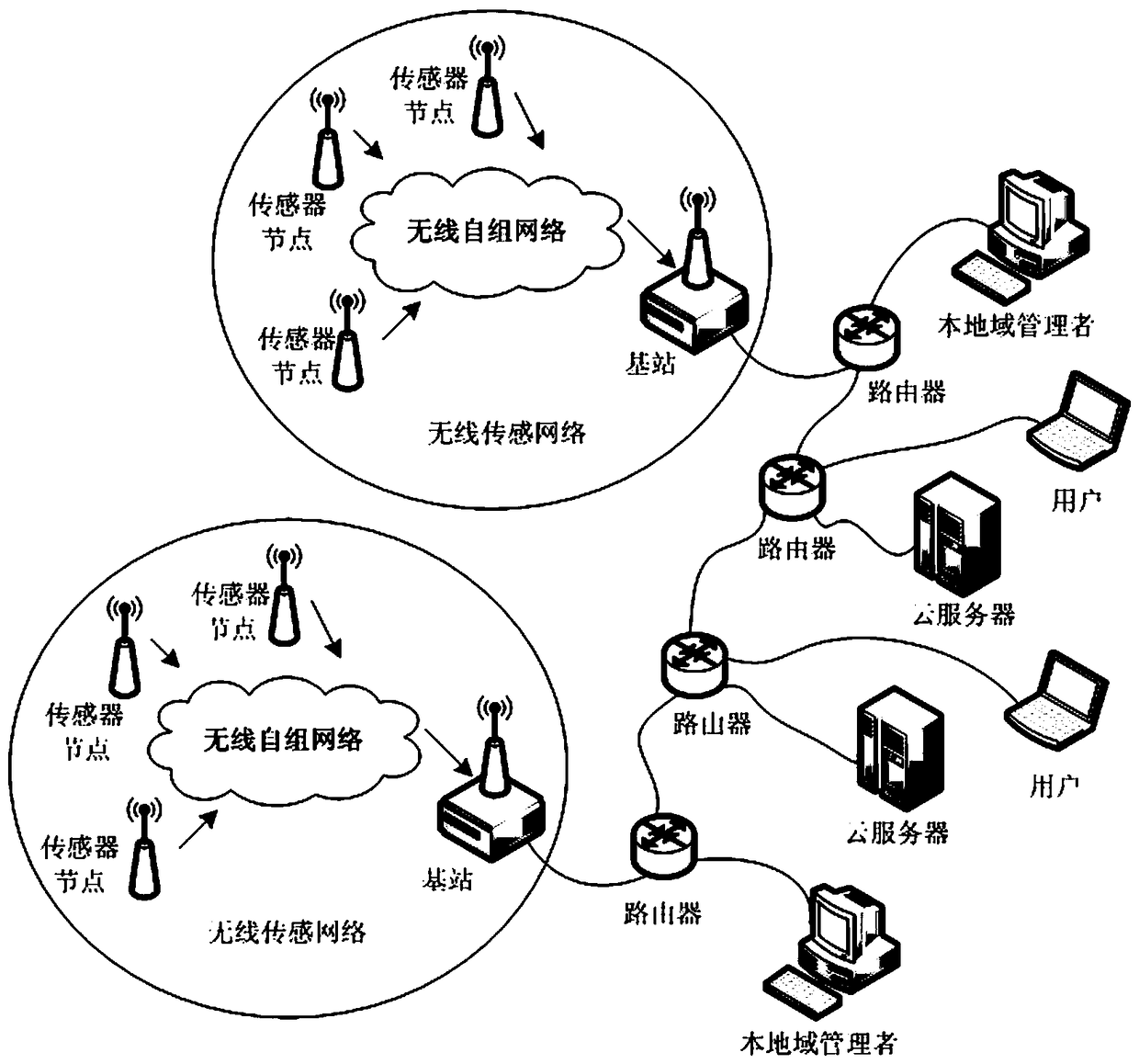
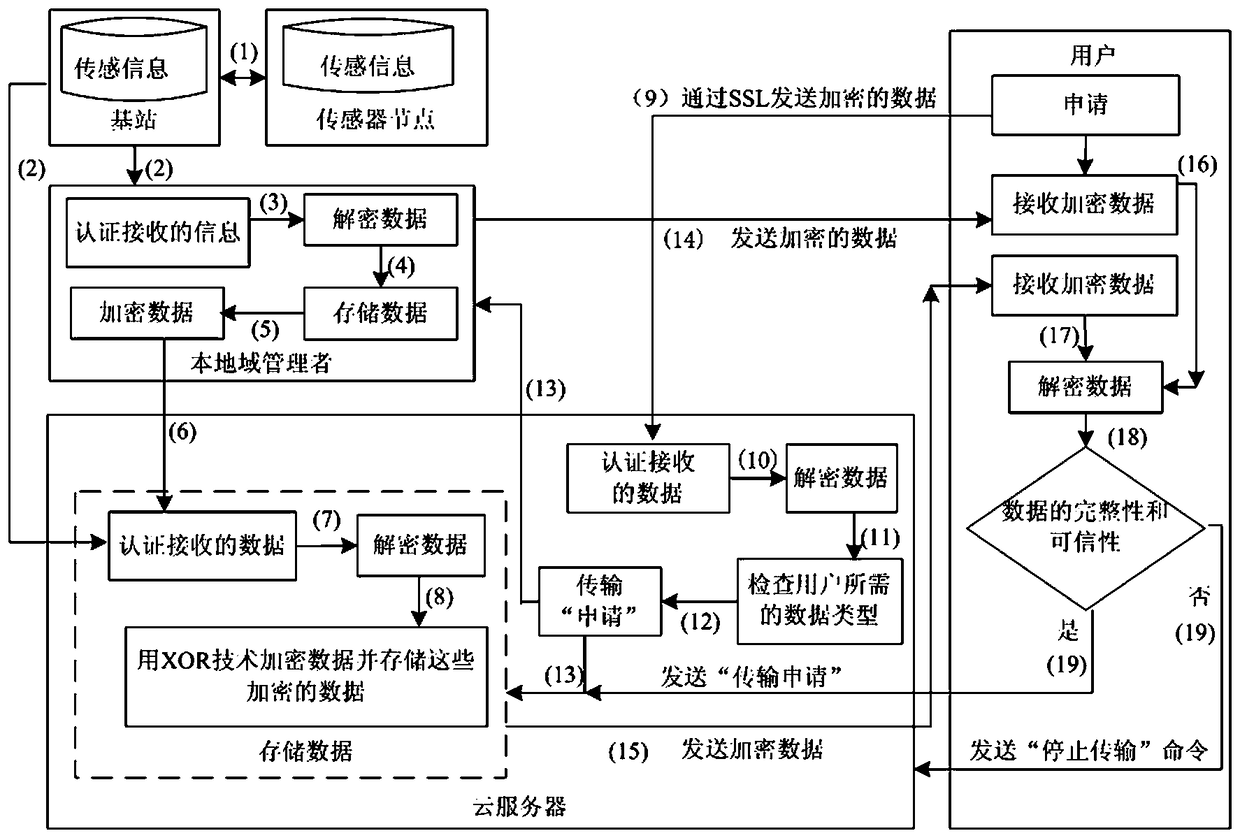
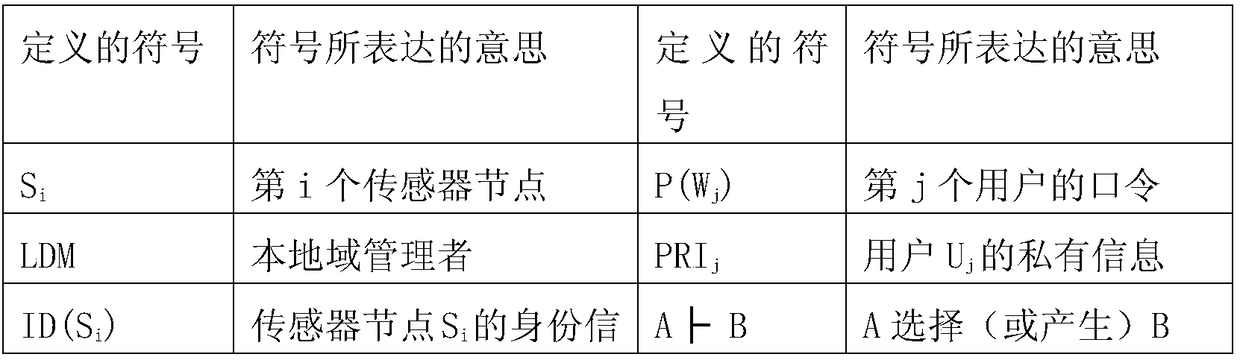
InactiveCN108512856AImprove adaptabilityImprove versatilityNetwork topologiesTransmissionSensing dataData privacy protection
The invention discloses a privacy protection method of sensing information virtual service in Internet of Things. Sensor sensing data, a cloud server, a local domain manager, and a user are provided.By aiming at generating of sensing information in a wireless sensing network and during a virtual service process in cloud computation, the data privacy protection strategy of the cloud computation virtual service is divided into two parts: (1) the sensing information is transmitted in the network, and is stored in the cloud server; (2) the sensing data stored in the cloud server is used to provide service for a user. By aiming at each of the safety problems faced by the abovementioned two parts, a safety protection algorithm is provided, and therefore the safety storage algorithm of the sensing information and the safety access algorithm of the data stored in the cloud server are provided.
Owner:HANGZHOU DIANZI UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com