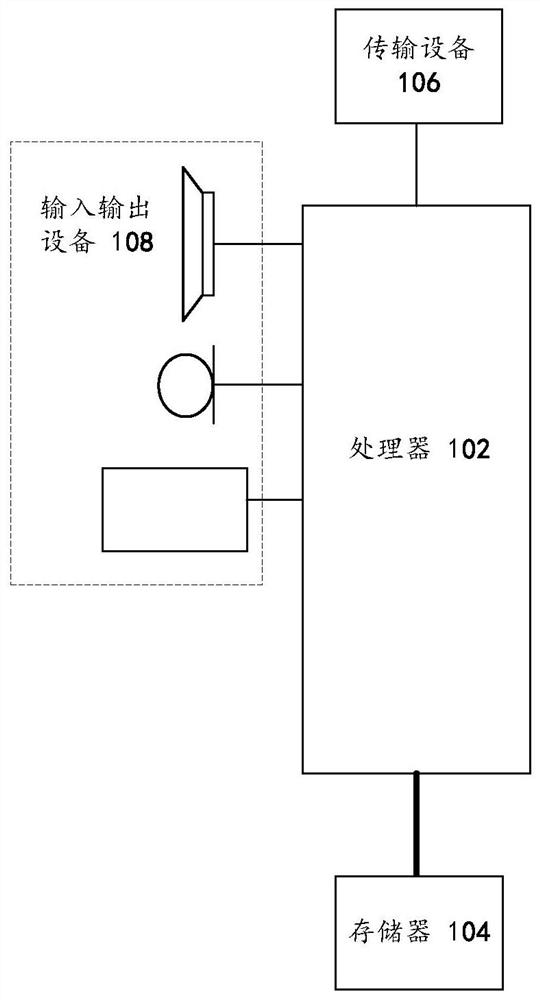
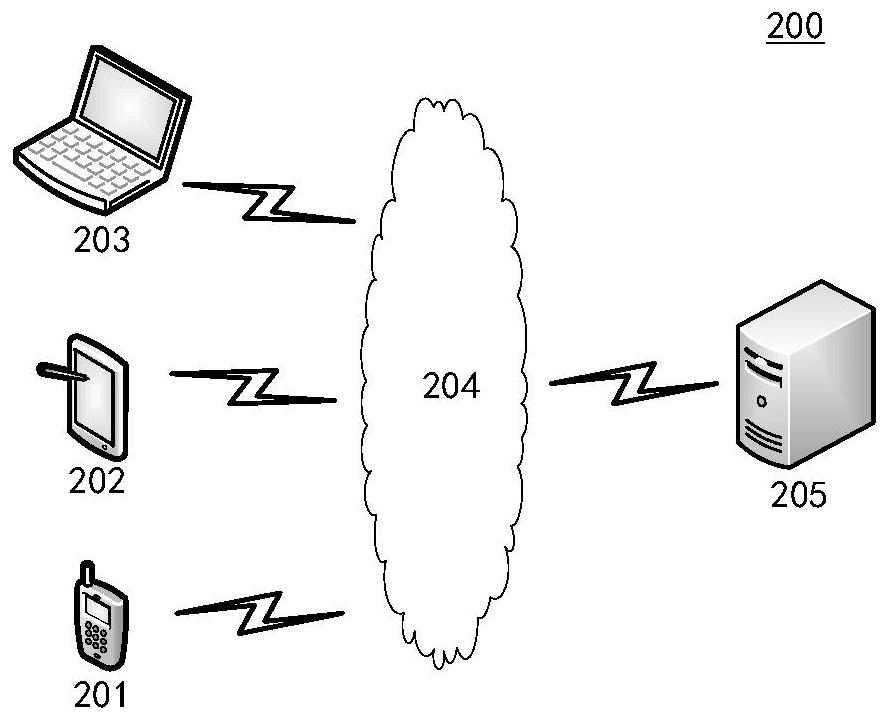
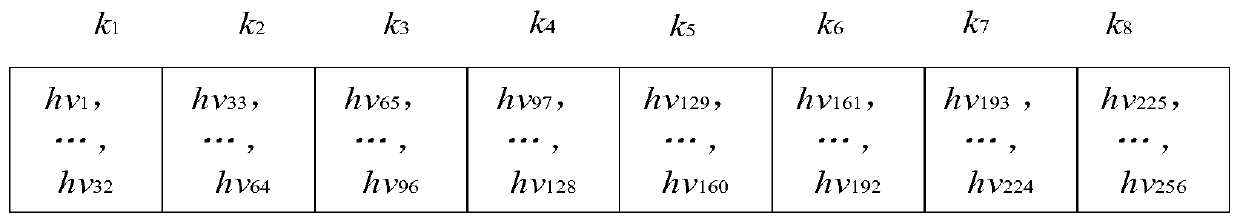Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
77results about How to "Solve the problem of low security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Intelligent electric control seal system
InactiveCN101704319ASolve the problem of low securityVersatileStampingKey pressingCommunication interface
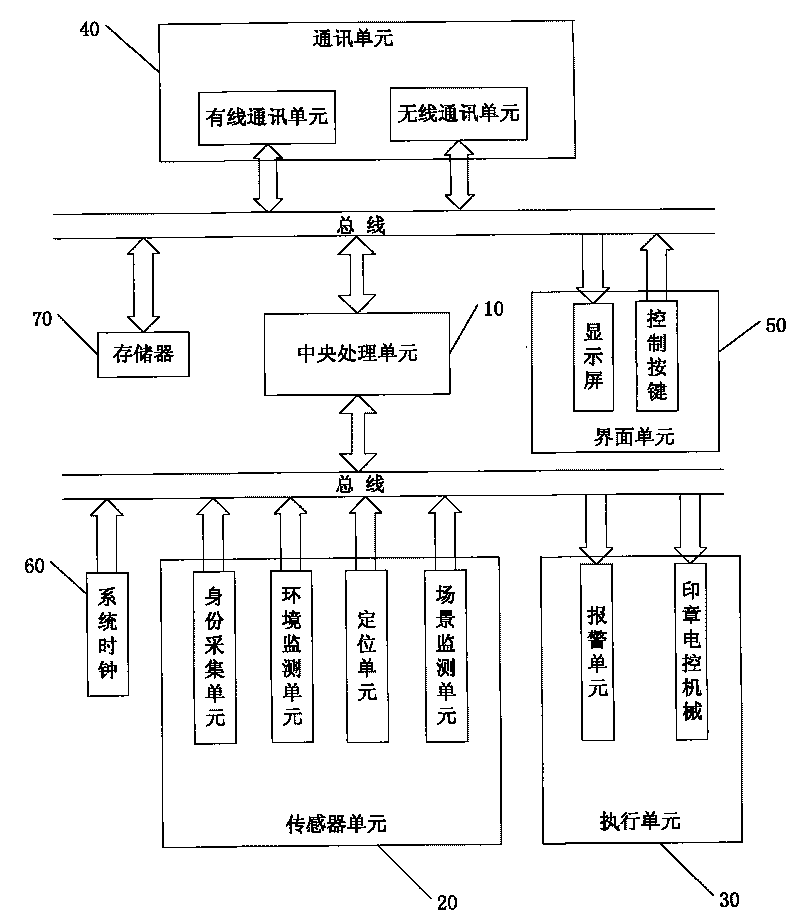
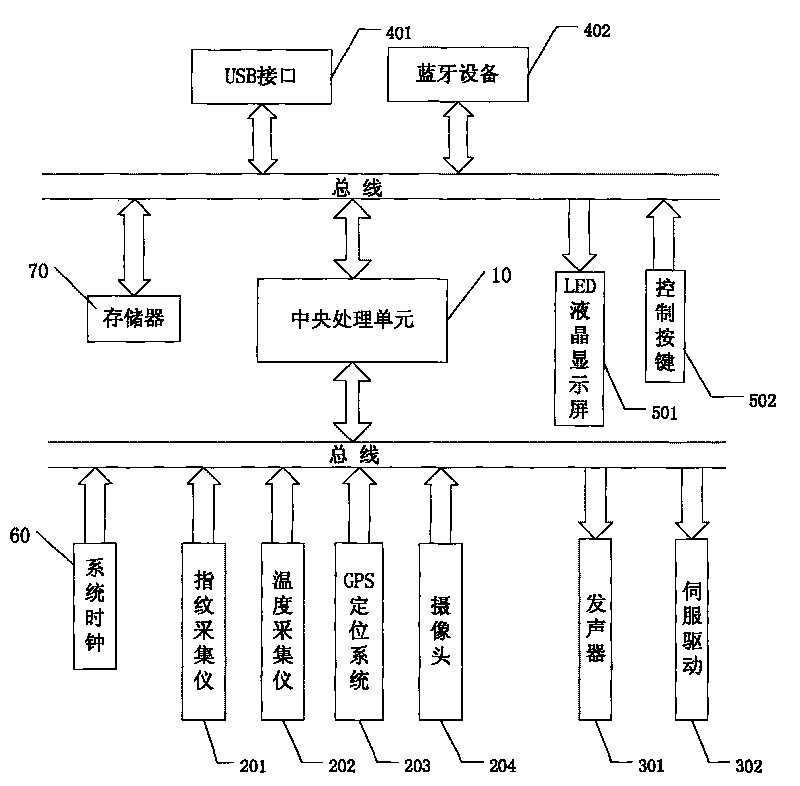
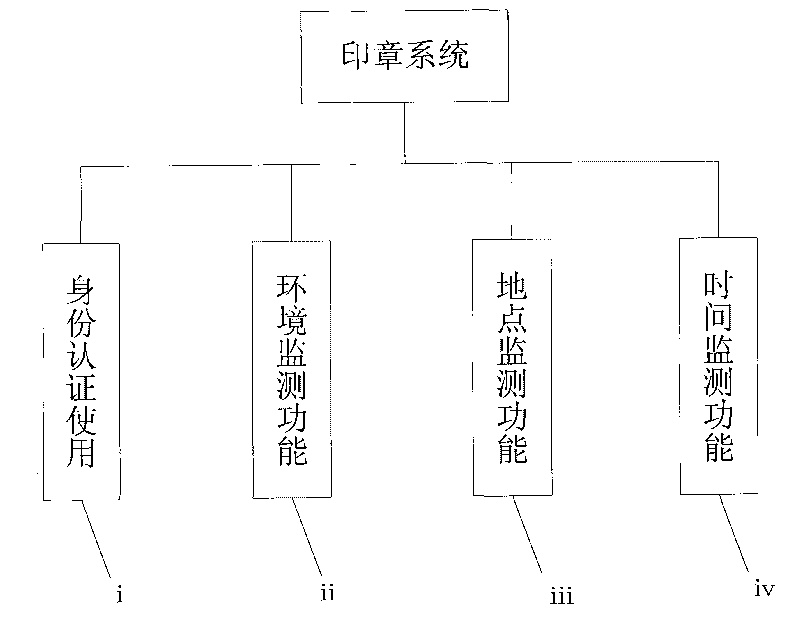
The invention provides an intelligent electric control seal system. The system comprises a central processing unit, a sensor unit, an execution unit, a communication unit, an interface unit, a system clock and a memory, wherein the sensor unit, the execution unit, the communication unit, the interface unit, the system clock and the memory are connected with the central processing unit by buses; the sensor unit comprises an identification acquisition unit, an environment monitoring unit, a positioning unit and a scene monitoring unit; the execution unit comprises an alarming unit and a seal electrically controlling machine; the communication unit comprises a wire communication interface and a wireless communication interface; and the interface unit comprises a display screen and control keys. The intelligent electric control seal system solves the problem of poor safety existing in the conventional seal, and can strictly limit users and record the seal-using process in detail.
Owner:CHENGDU FINCHOS ELECTRONICS
Data encryption method, device, equipment and system and data decryption method, device, equipment and system
ActiveCN104601325ASolve the problem of low securityImprove securityUser identity/authority verificationDigital data protectionXML EncryptionData decryption
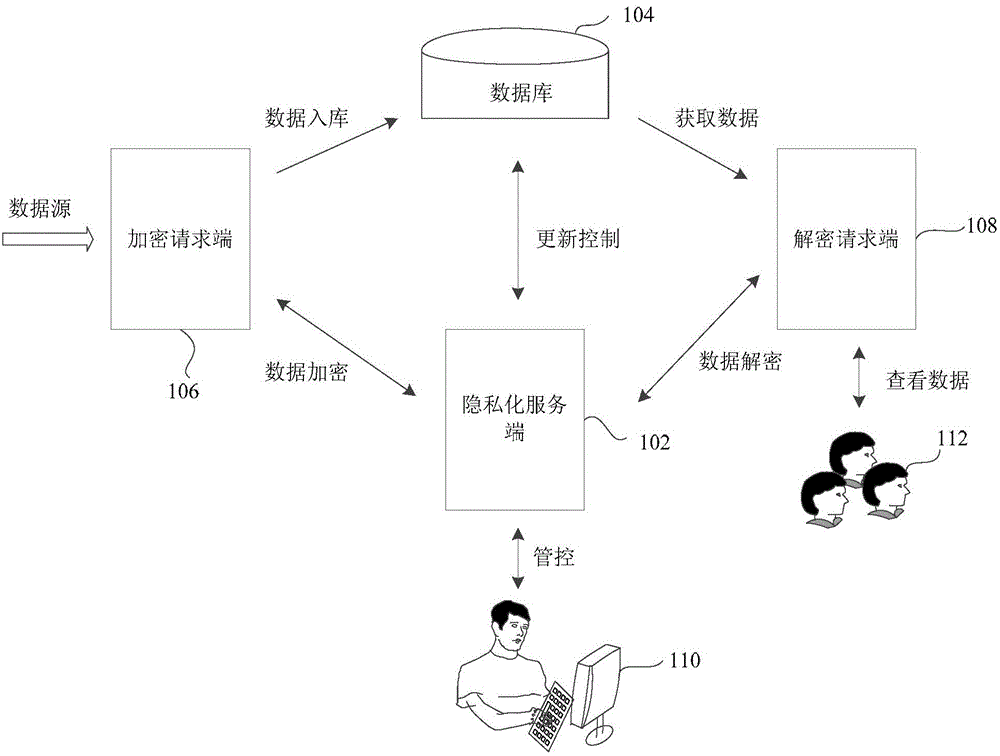
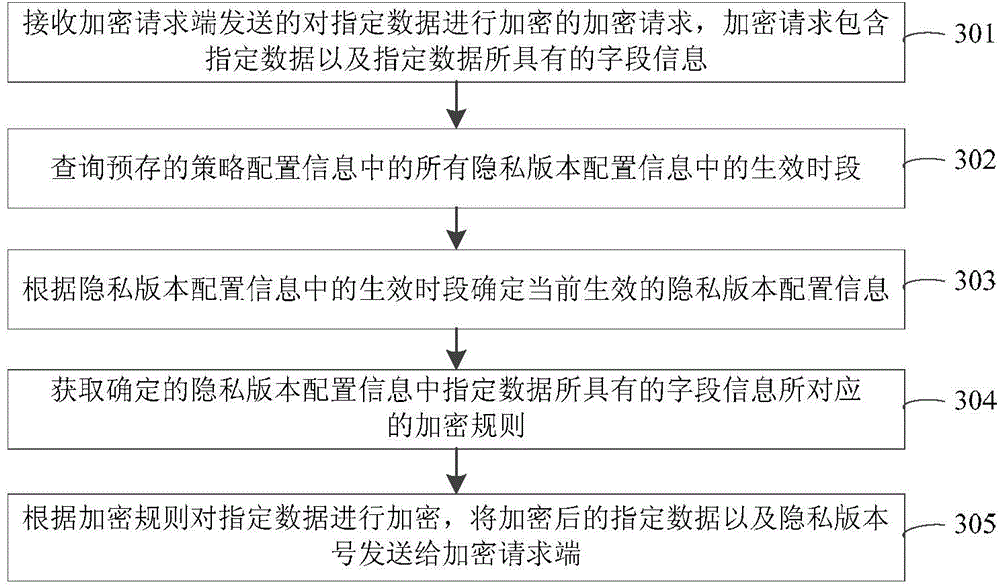
The embodiment of the invention provides a data encryption method, device, equipment and system and a data decryption method, device, equipment and system, and relates to the field of data security. The data encryption method comprises the following steps: receiving an encryption request for encrypting specified data; acquiring an encryption rule corresponding to field information in pre-stored currently-effective privacy version configuration information; and encrypting the specified data according to the searched encryption rule. The specified data is encrypted through the preconfigured currently-effective privacy version configuration information. The problem of low security of encryption and decryption methods provided in the prior art is solved. The effective privacy version configuration information is updated automatically along with time, so that the probability of forced cracking of encrypted data can be lowered to a great extent, and the security during data encryption or decryption can be enhanced greatly.
Owner:HUAWEI TECH CO LTD
Data encryption method and device and data decryption method and device
ActiveCN106850220AIncrease the difficultyImprove securityMultiple keys/algorithms usageComputer hardwareData decryption
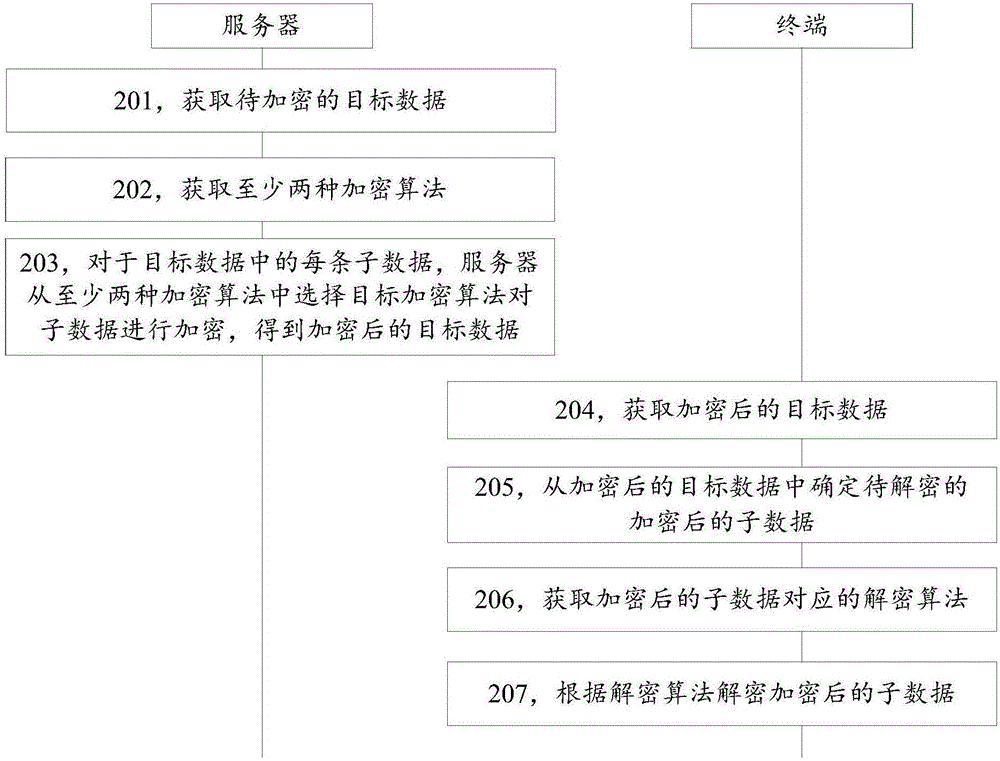
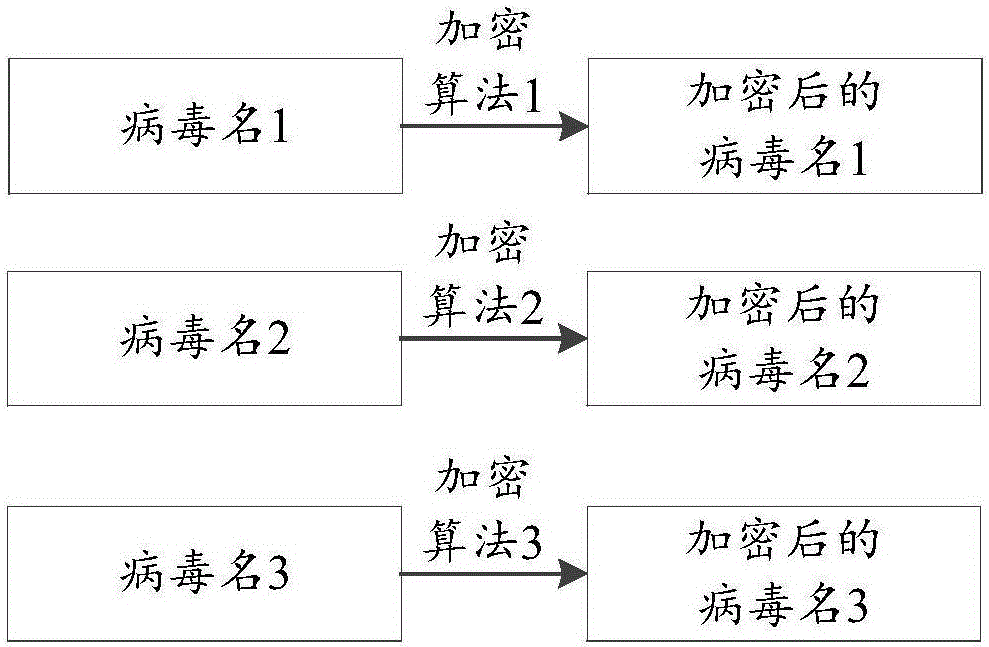
The invention discloses a data encryption method and device and a data decryption method and device, belonging to the technical field of computers. The method comprises the following steps: obtaining target data to be encrypted, wherein the target data includes at least two pieces of sub data; obtaining at least two encryption algorithms; and for each piece of sub data in the target data, encrypting the sub data by a target encryption algorithm which is selected from the at least two encryption algorithms to obtain encrypted target data. According to the invention, the problems that the cracking difficulty of the encrypted target data is low for malicious personnel, and the security of the encrypted target data is not high when a server encrypts the target data as a whole by using a single encryption algorithm are solved; and the cracking difficulty of the encrypted target data is increased for the malicious personnel, and the security of the encrypted target data is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
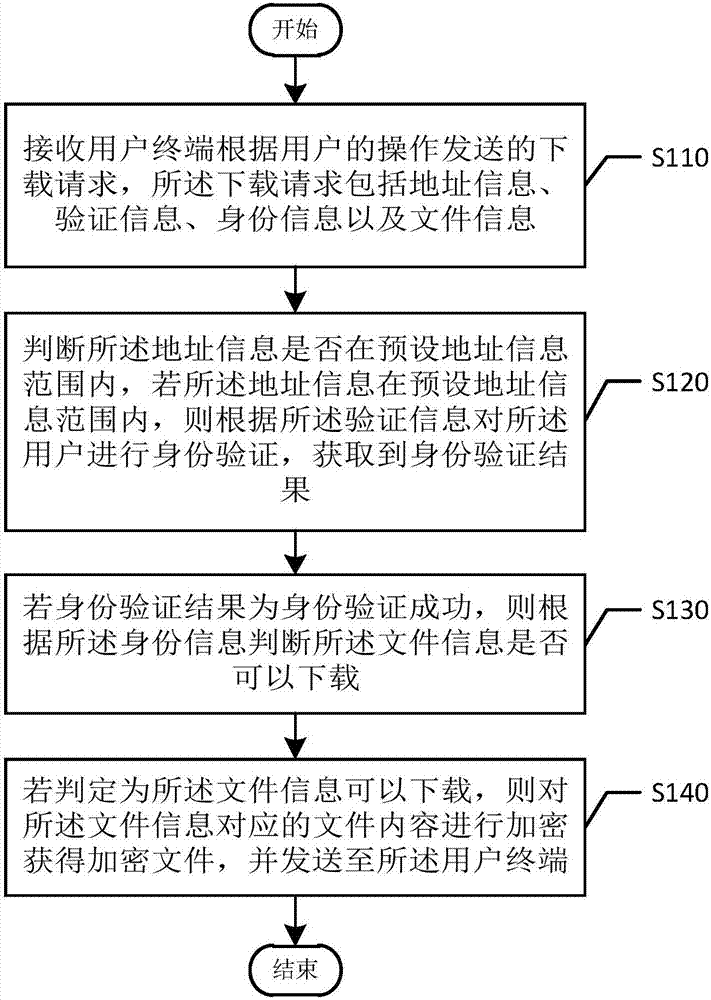
File downloading method and device
ActiveCN107241364AImprove securitySolve the problem of low securityKey distribution for secure communicationThe InternetAuthentication
The invention provides a file downloading method and device, and relates to the technical field of the internet. The file downloading method is applied to the server of a file downloading system, and includes the steps of receiving download requests sent by a user terminal according to the operations of a user, wherein the download requests include address information, verification information, identity information and file information; judging whether or not the address information is within the range of preset address information, and if yes, authenticating the user according to the verification information to obtain an authentication result; if the authentication result shows that the authentication is successful, judging whether or not the file information can be downloaded according to the identity information; if yes, encrypting file contents corresponding to the file information to obtain encrypted files, and sending the encrypted files to the user terminal. The file downloading method has strong security and reliability.
Owner:广州杰之良软件有限公司
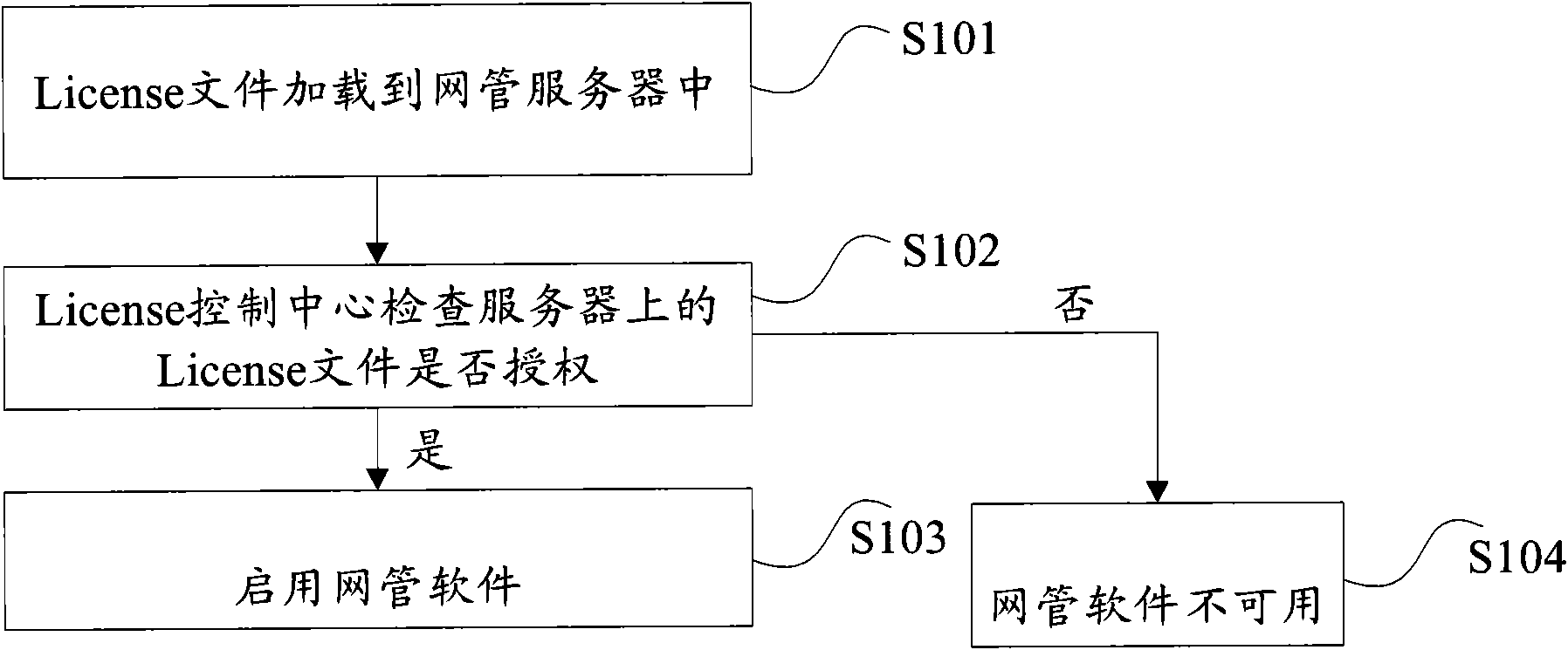
Protection method permitted by webmaster and device therefor
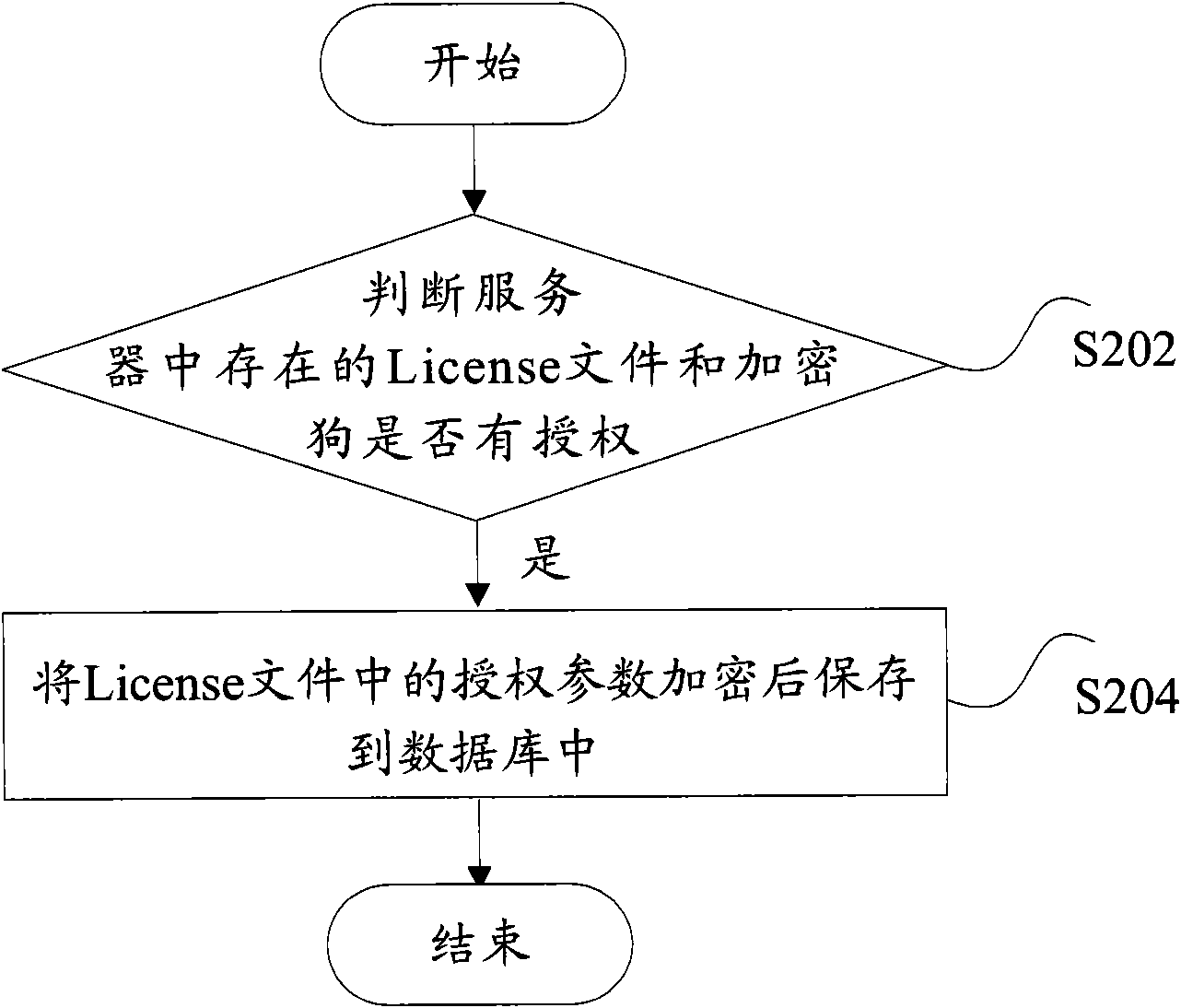
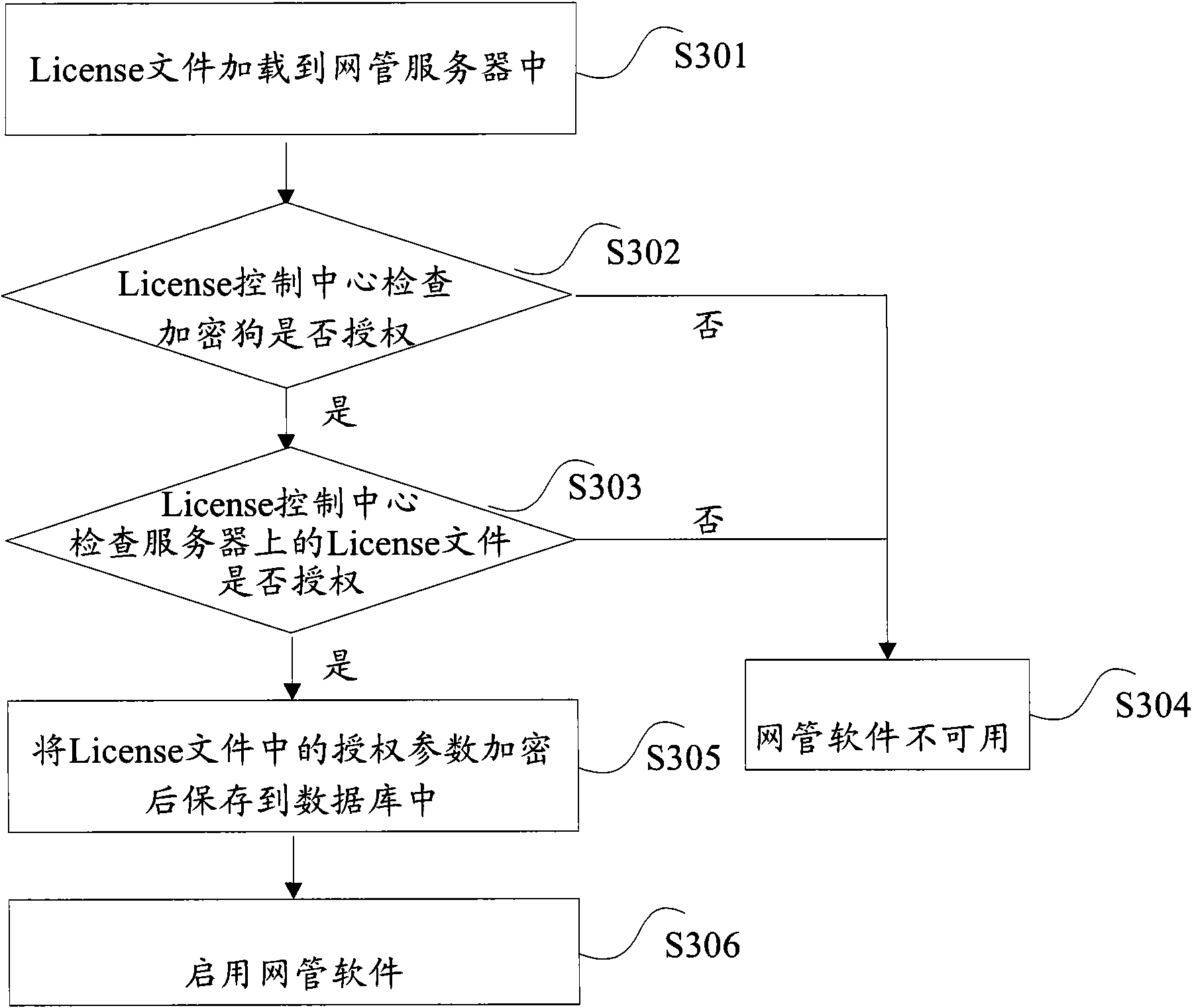
ActiveCN101667239ASolve the problem of low securityImprove securityDigital data protectionLicenseAuthentication
The invention discloses a protection method permitted by a webmaster and a device therefor. The method comprises: judging whether a license file and a softdog which exist in a server are whetheris authorized; if being authorized, resolving authentication parameter in the license file, and encrypting and then storing the authentication parameter into a data base of the server. The invention effectively improves the safety of webmaster software, thus better protecting the benefit of the software provider.
Owner:ZTE CORP
Wireless parameter sending and receiving method and device
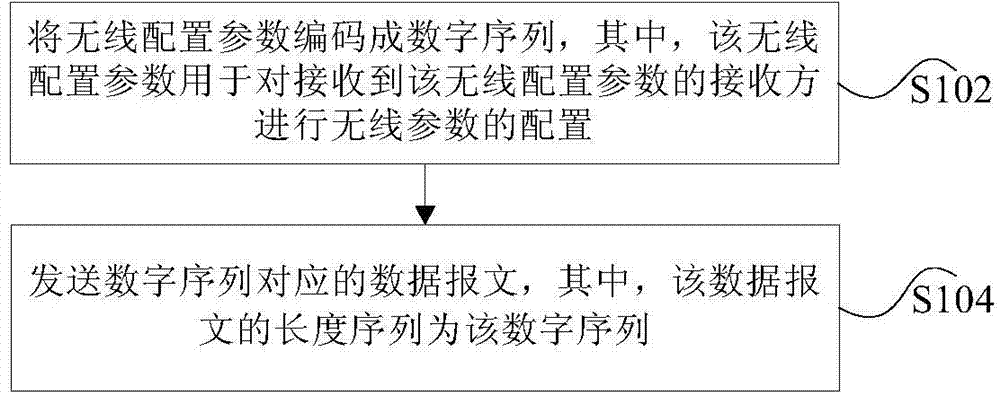
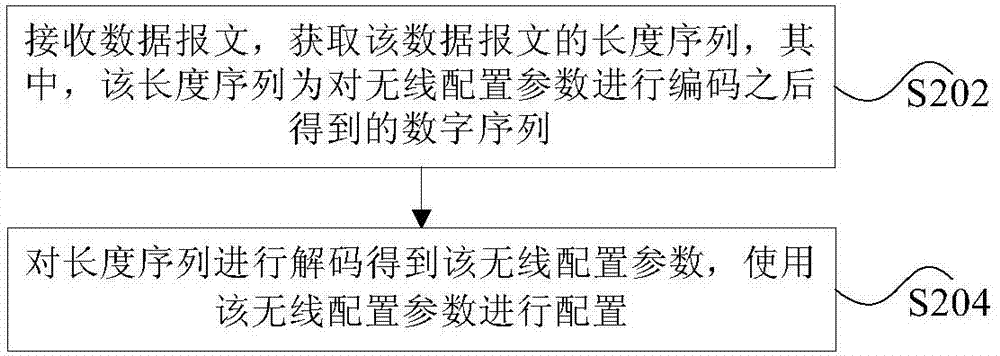
InactiveCN104754565ALow costSolve the problem of needing to add hardware and low securityError preventionAssess restrictionComputer scienceWireless
Disclosed are a method and device for sending and receiving a radio parameter. The method comprises: encoding a radio configuration parameter into a digital sequence, wherein the radio configuration parameter is used for conducting radio parameter configuration on a receiver receiving the radio configuration parameter; and sending a data packet corresponding to the digital sequence, wherein the length sequence of the data packet is the digital sequence. By means of the present invention, the problem of low security due to the fact that hardware is required to be added when a radio configuration parameter in a wireless local area network is sent and received is solved, thereby reducing hardware costs and improving the sending and receiving security.
Owner:ZTE CORP
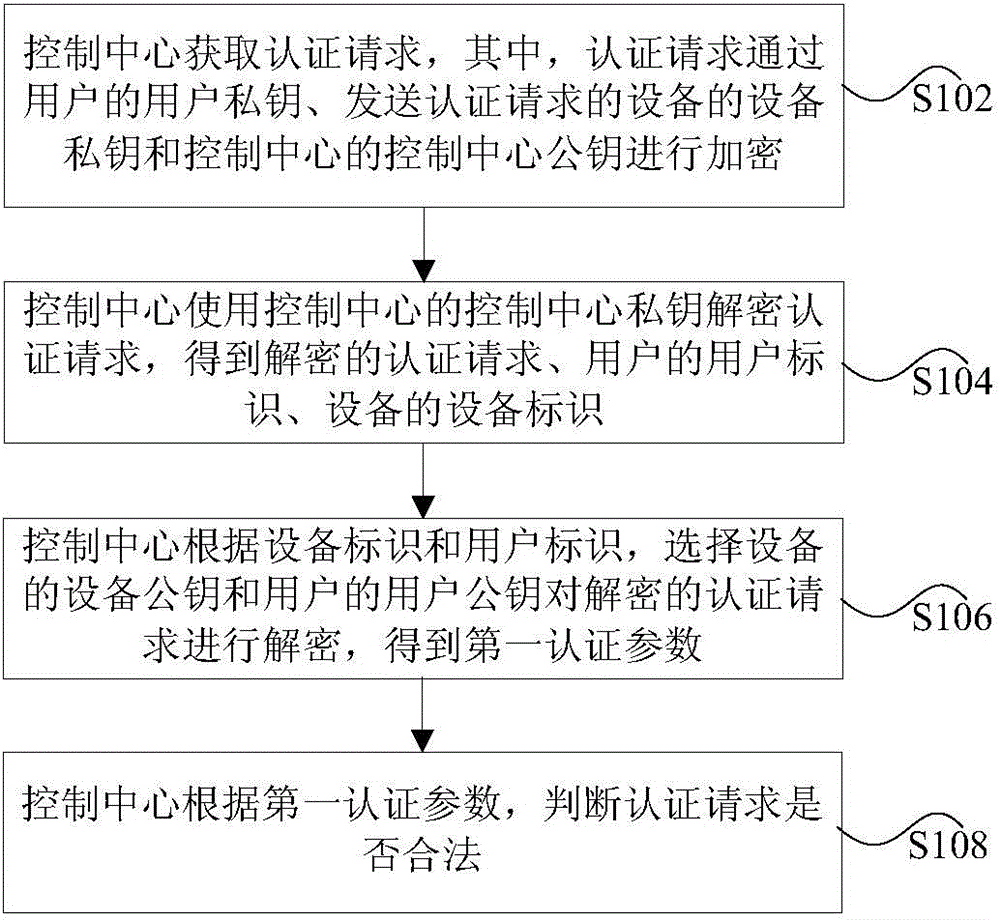
Identity authentication method, device and system
ActiveCN106330442ASolve the problem of low securityImprove securityUser identity/authority verificationTotal factory controlUser identifierAuthentication
The invention provides an identity authentication method, device and system. The method comprises the following steps: a control center obtains an authentication request, wherein the authentication request is encrypted by a user private key of a user, an equipment private key of equipment sending the authentication request and a control center public key of the control center; the control center decrypts the authentication request by using a control center private key of the control center to obtain a decrypted authentication request, a user identifier of the user and an equipment identifier of the equipment; the control center selects an equipment public key of the equipment and a user public key of the user according to the equipment identifier and the user identifier to decrypt the decrypted authentication request to obtain a first authentication parameter; and the control center judges whether the authentication request is legitimate according to the first authentication parameter. By adopting the identity authentication method, device and system provided by the invention, the problem of low security of the single authentication mode of identity authentication is solved, and the security of the identity authentication is improved.
Owner:ZTE CORP
Ciphertext generation method, ciphertext decryption method and encryption/ decryption device
ActiveCN103873250ASolve the problem of low securityUser identity/authority verificationComputer hardwarePlaintext
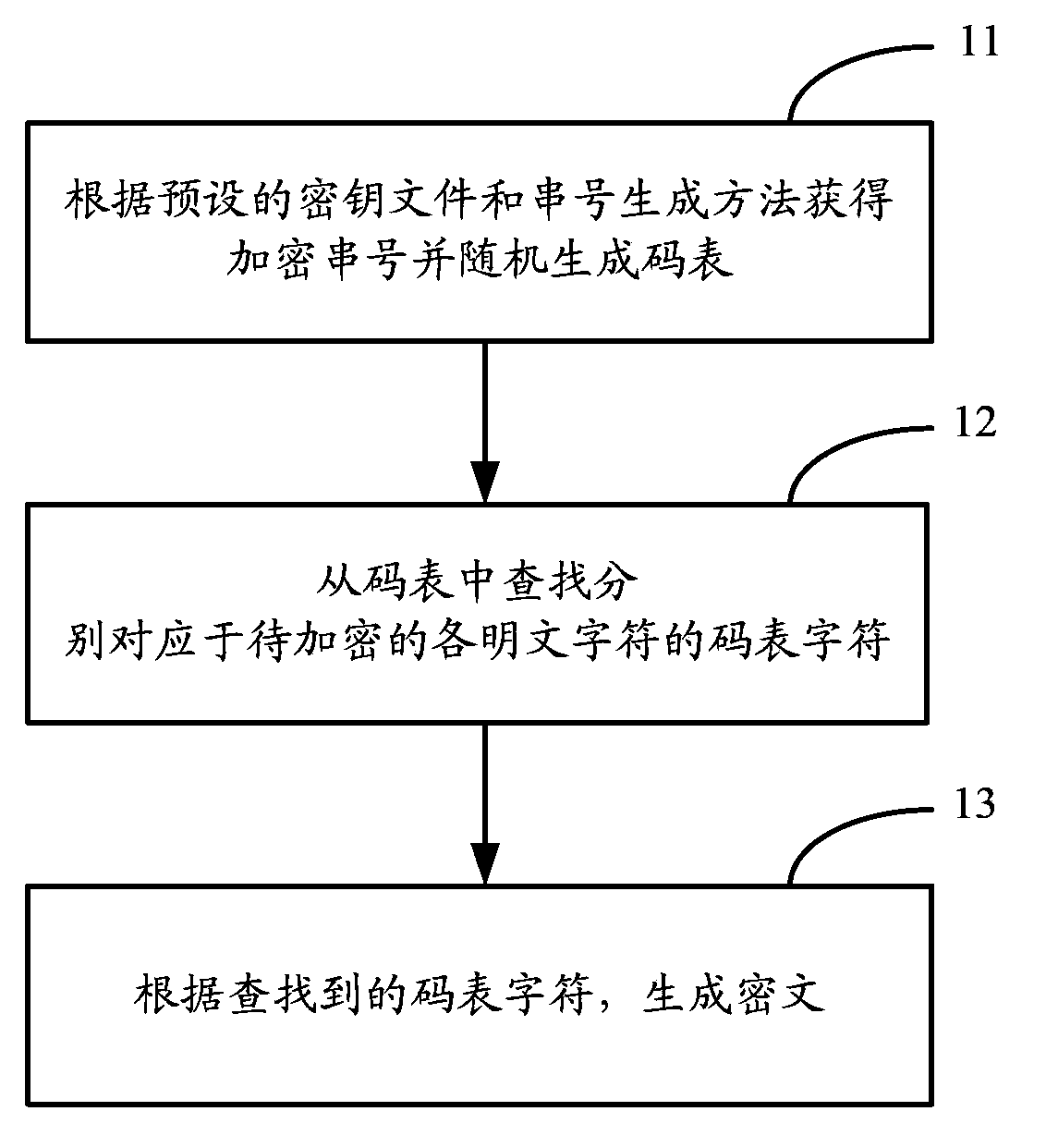
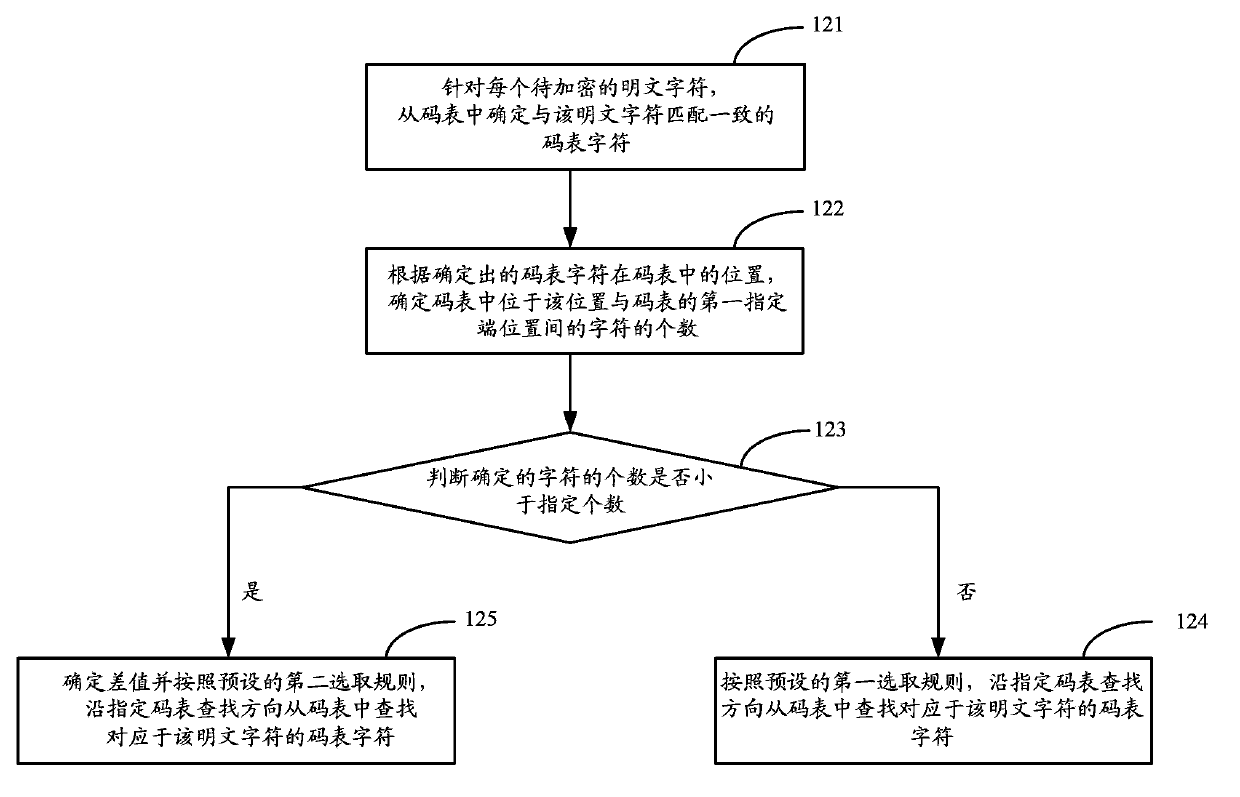
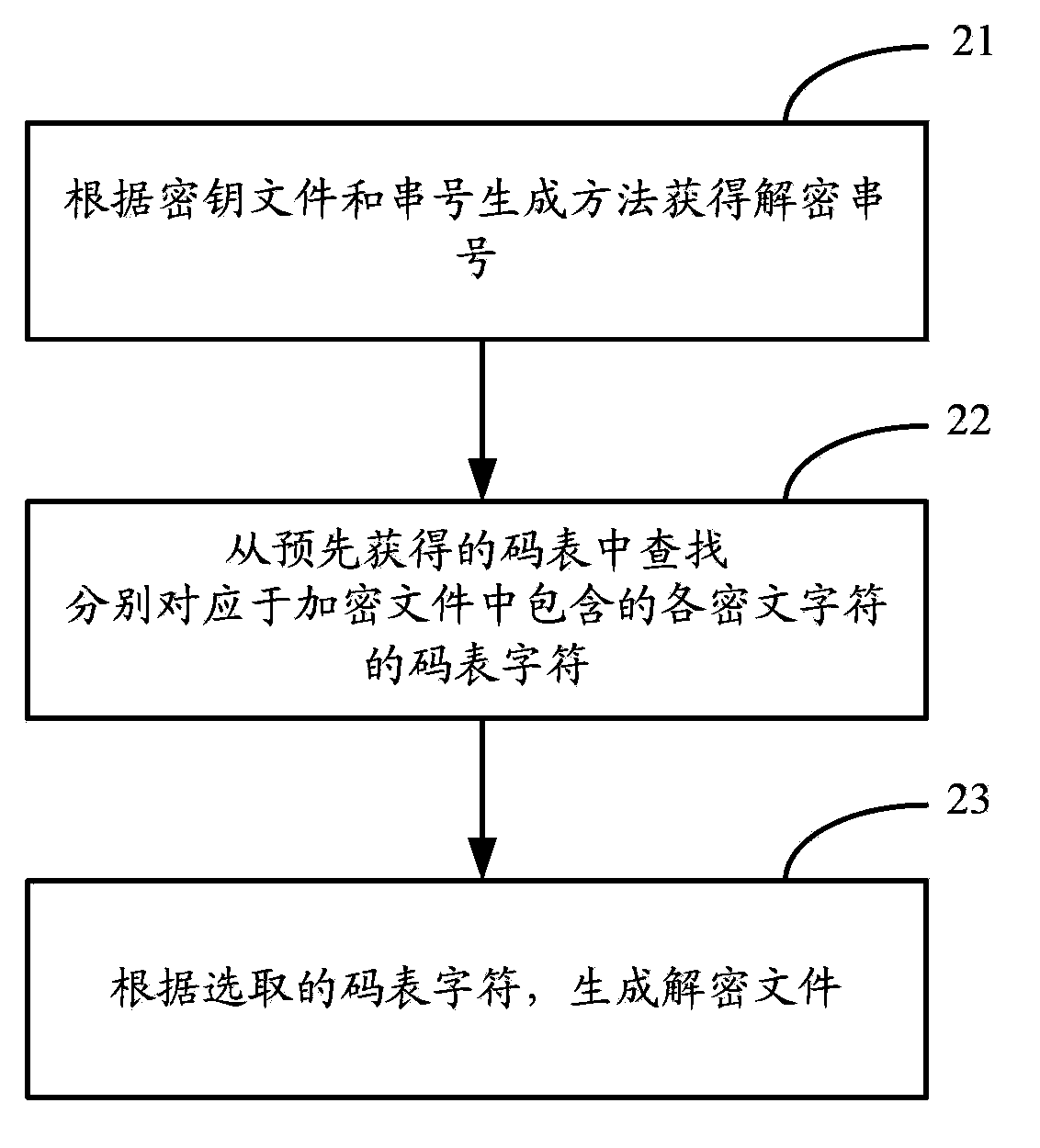
The invention discloses a ciphertext generation method, a ciphertext decryption method and an encryption / decryption device, and is used for solving the problem of poor safety when a ground-up encryption algorithm of the Java language is used for carrying out encryption transmission on a cross-system password or information in the prior art. The ciphertext generation method comprises the following steps: according to a preset key file and an identification number generation method, obtaining an encrypted identification number, and randomly generating a code table comprising a plurality of characters; according to the obtained encrypted identification number and each plaintext character to be encrypted, looking up a code table character respectively corresponding to each plaintext character to be encrypted from the generated rate table along an appointed code table lookup direction; according to the found code table character, generating a ciphertext. Therefore, the safety of the ciphertext not only depends on the encryption algorithm but also depends on the preset key file and the randomly-generated code table, and the ciphertext can not be accurately decrypted even if a decryption algorithm is obtained only by using different key files and code tables to carry out encryption processing on the plaintext.
Owner:XINYANG BRANCH HENAN CO LTD OF CHINA MOBILE COMM CORP
Positioning method and device and user terminal
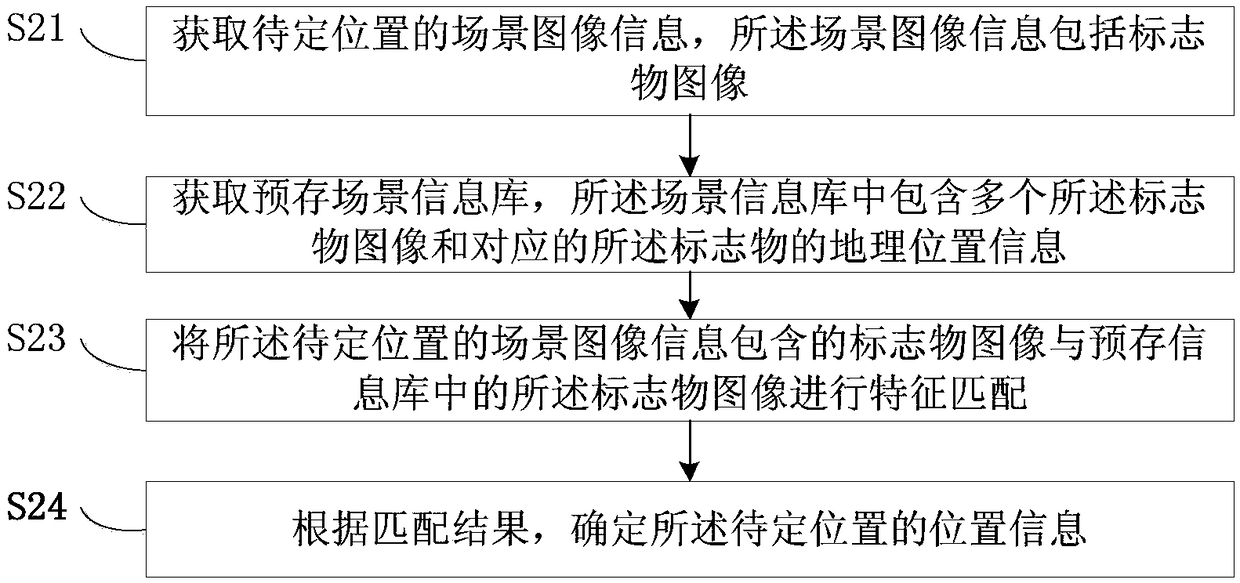
InactiveCN108646280ASolve the problem of low securityThe positioning result is accurateNavigational calculation instrumentsSubstation equipmentInformation repositoryGeolocation
A positioning method and device, and a user terminal are disclosed. The positioning method is applied to the user terminal, and includes acquiring scene image information of a to-be-determined position, wherein the scene image information includes a marker image; acquiring a pre-stored scene information library, wherein the scene information library includes a plurality of the marker images and corresponding geographic location information of the markers; performing character matching on the marker image included in the scene image information of the to-be-determined position and the marker images in the pre-stored information library; determining the location information of the to-be-determined position according to the matching result. The problem that the existing positioning mode is poor in security can be solved.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
Business approval method and device
ActiveCN110365662AEnsure safetySolve the problem of low securityUser identity/authority verificationDigital data protectionInformation securityPayload
The invention provides a business approval method and device, and the method comprises: a server receiving a payload transmitted by a first account, decrypting the payload to obtain to-be-approved contents and an approval account public key, and verifying a first signature; after the first signature passes the verification, encrypting the payload by using the approval account public key to obtainfirst information, and sending the first information to each approval account; receiving feedback content of a second account in the approval accounts for the to-be-approved content. By adoption of the scheme, the server synchronously sends the approval content to the plurality of approval accounts, so that the approval speed is increased, the information security is ensured, the approval processcannot be tampered, and the problem of low information security caused by easy tampering of the business approval process in related technologies is solved.
Owner:北京思源理想控股集团有限公司
Configurable third-party message callback method and device, server and storage medium
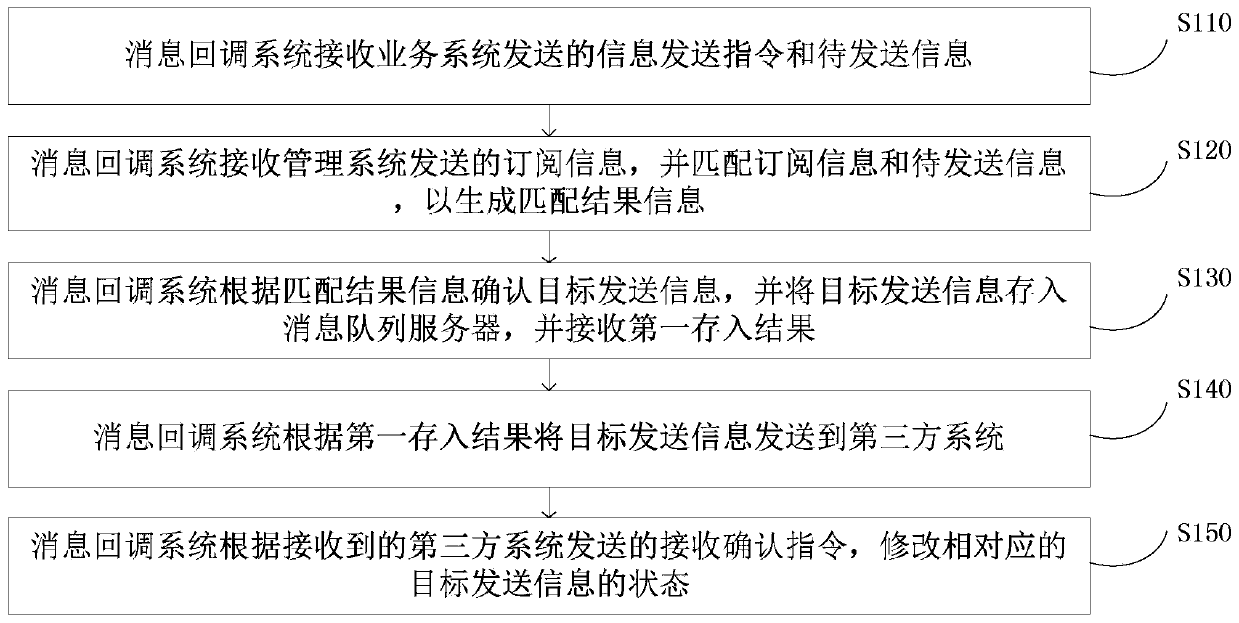
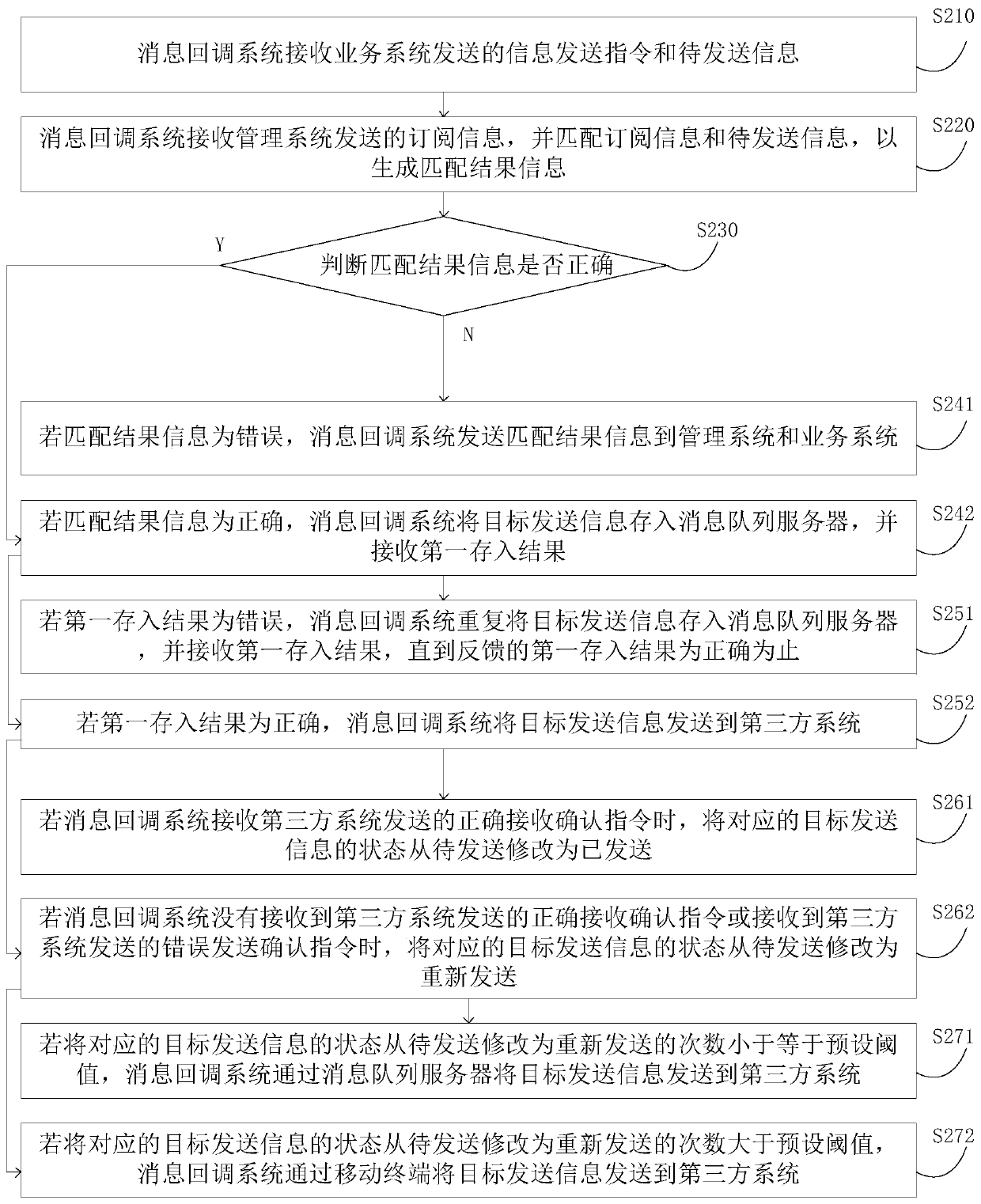
ActiveCN110413424ASolve the problem of low securityInterprogram communicationThird partyCommunications security
The invention discloses a configurable third-party message callback method and device, a server and a storage medium. The method comprises the following steps: a message callback system receives an information sending instruction and to-be-sent information sent by a service system; the message callback system receives the subscription information sent by the management system and matches the subscription information with the to-be-sent information to generate matching result information; the message callback system confirms target sending information according to the matching result information, stores the target sending information into a message queue server and receives a first storage result; and the message callback system sends the target sending information to the third-party systemaccording to the first storage result. According to the invention, the third-party system of the access party is managed through the management system, and the corresponding service message is sent according to the requirements of the customer, so that the problem of low communication security caused by incapability of flexibly providing a subscribed message for the partner in the prior art is solved.
Owner:SHENZHEN LEXIN SOFTWARE TECH CO LTD
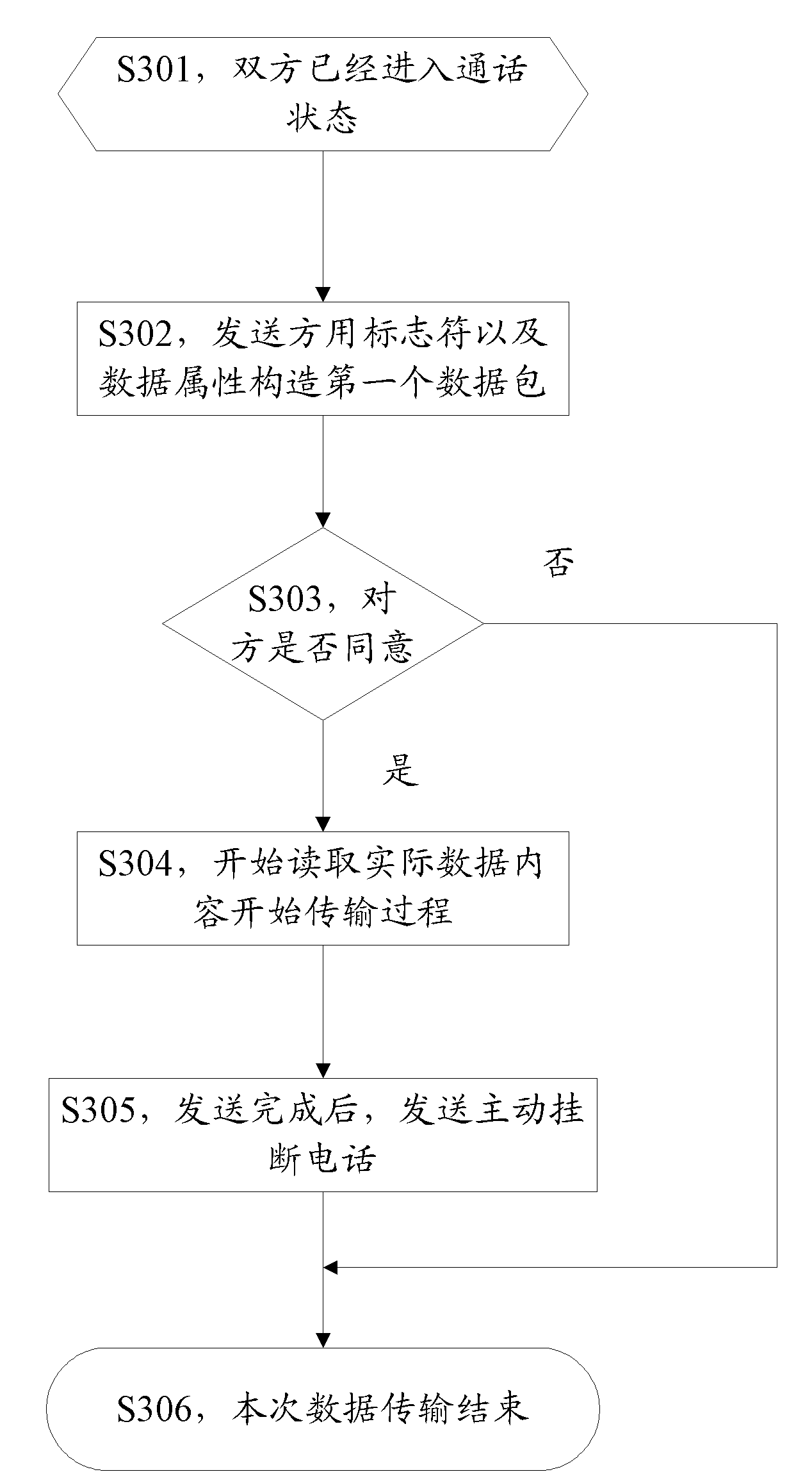
Method, system and terminal for transmitting data
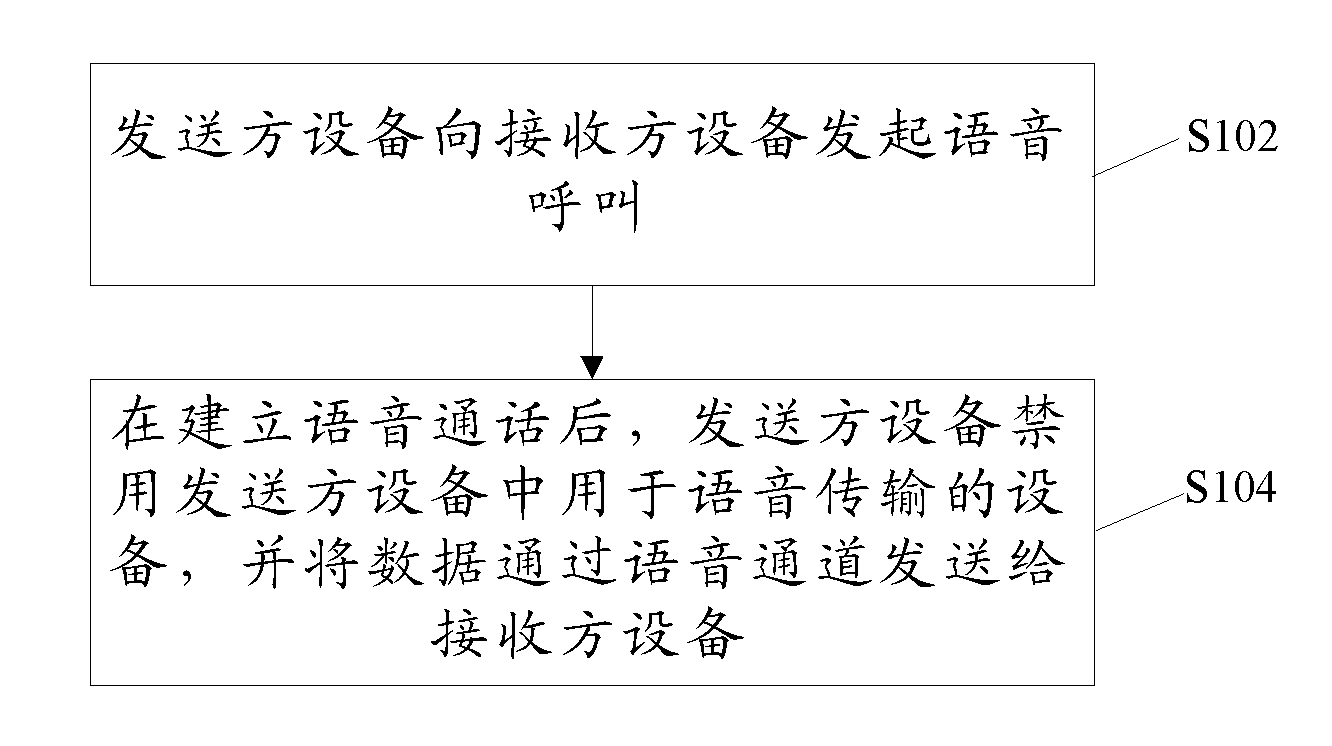
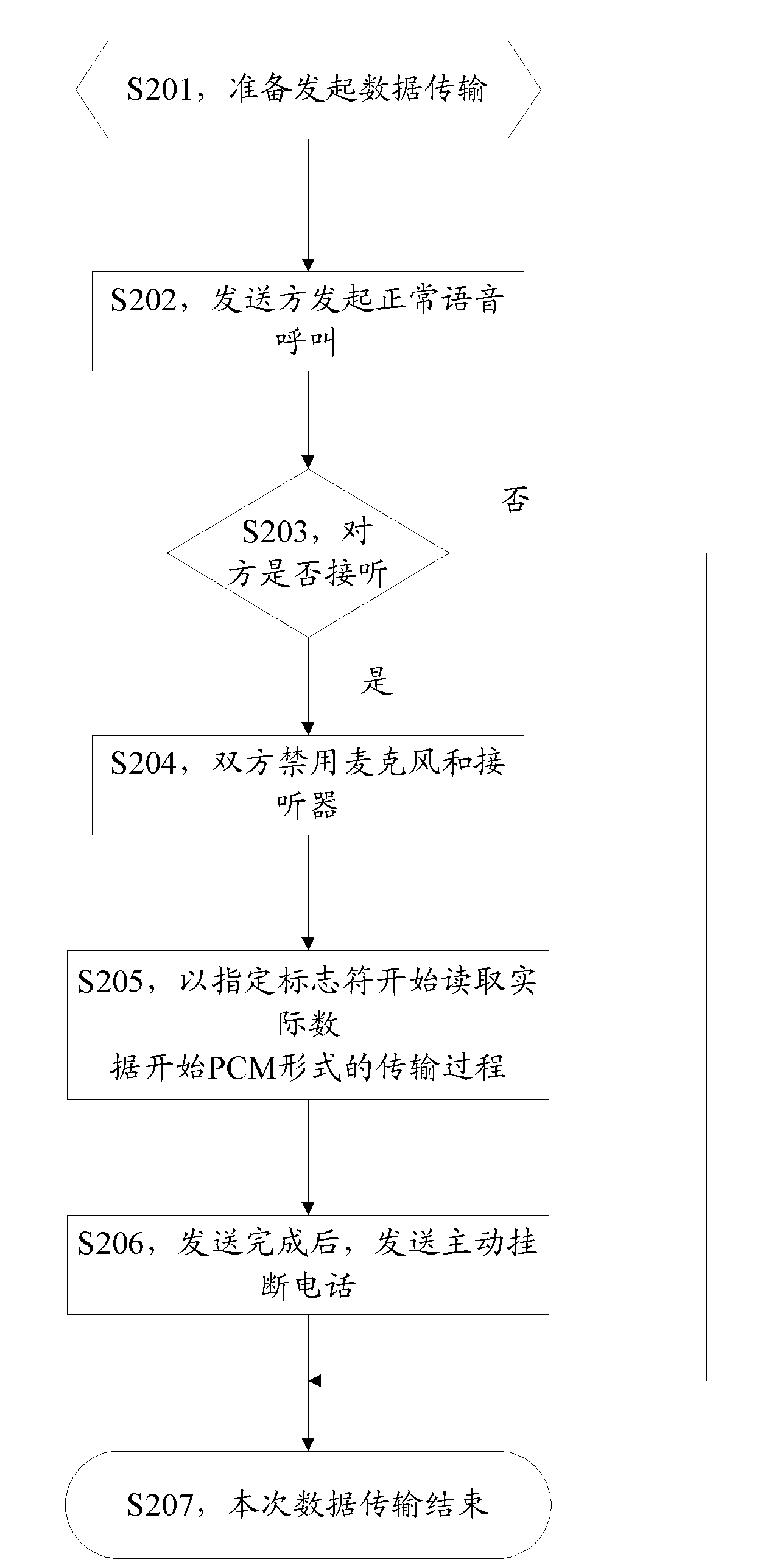
InactiveCN101980518ASolve the problem of low securityImprove securityInterconnection arrangementsConnection managementComputer terminalData transmission
The invention discloses a method, a system and a terminal for transmitting data. The method comprises that: transmitter equipment initiates a voice call to receiver equipment; after establishing the voice call; the transmitter equipment forbids the use of voice transmission equipment in the transmitter equipment and sends the data to the receiver equipment through a voice channel. In the invention, the safety of data transmission is improved.
Owner:ZTE CORP
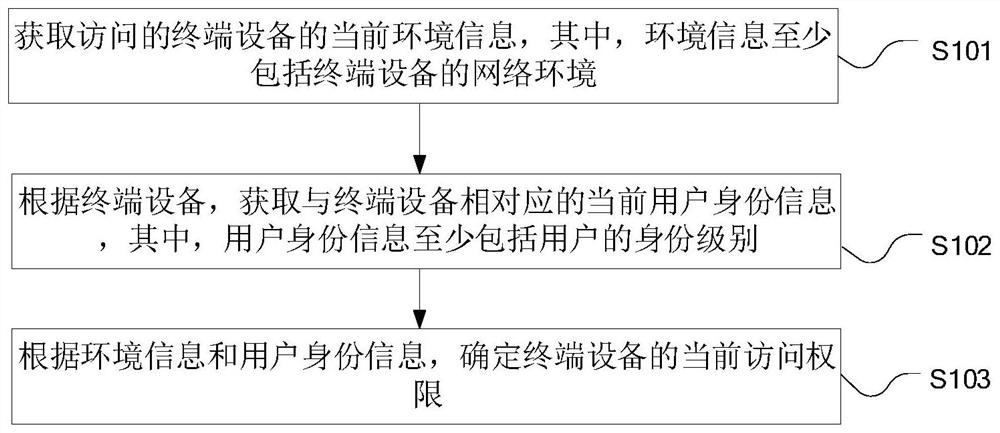
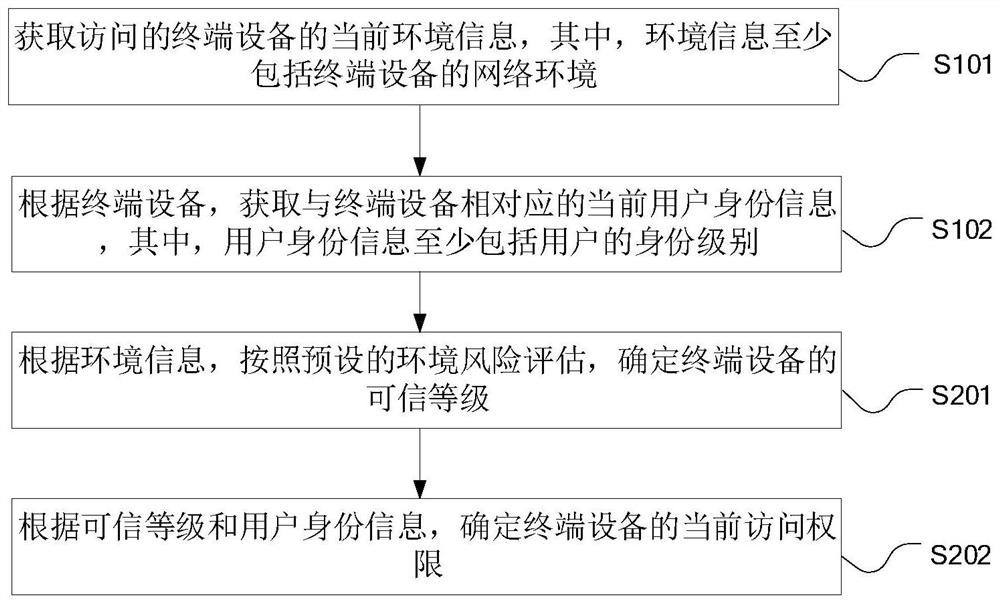
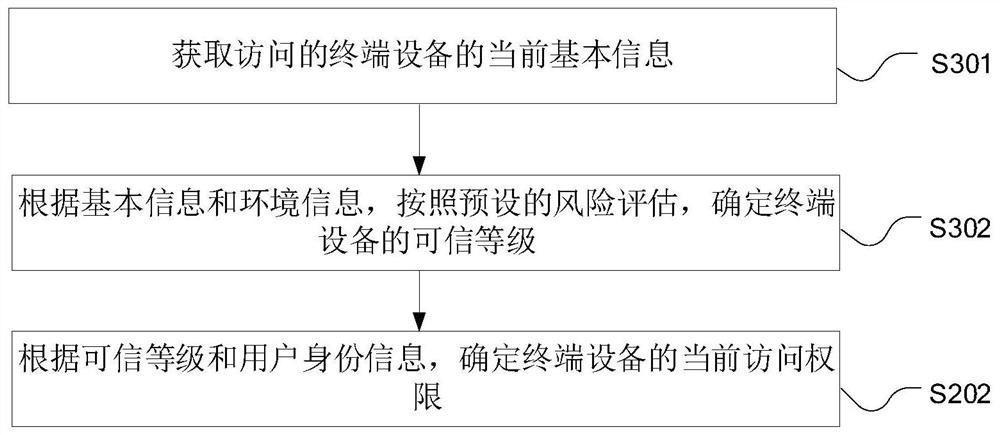
Zero-trust dynamic authorization method and device and computer equipment
PendingCN112165461AImprove securitySolve the problem of low securityTransmissionComputer equipmentWeb environment
The invention relates to a zero-trust dynamic authorization method and device and computer equipment, and the method comprises the steps: obtaining the current environment information of accessed terminal equipment, wherein the environment information at least comprises the network environment of the terminal equipment; according to the terminal equipment, obtaining current user identity information corresponding to the terminal equipment, wherein the user identity information at least comprises the identity level of the user; and determining the current access authority of the terminal equipment according to the environment information and the user identity information. According to the method, the low security of authority management of an operation and maintenance auditing system due tothe fact that the operation and maintenance auditing system uses a pre-configured resource access management model in the prior art is solved, and the security of authority management of the operation and maintenance auditing system is improved.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
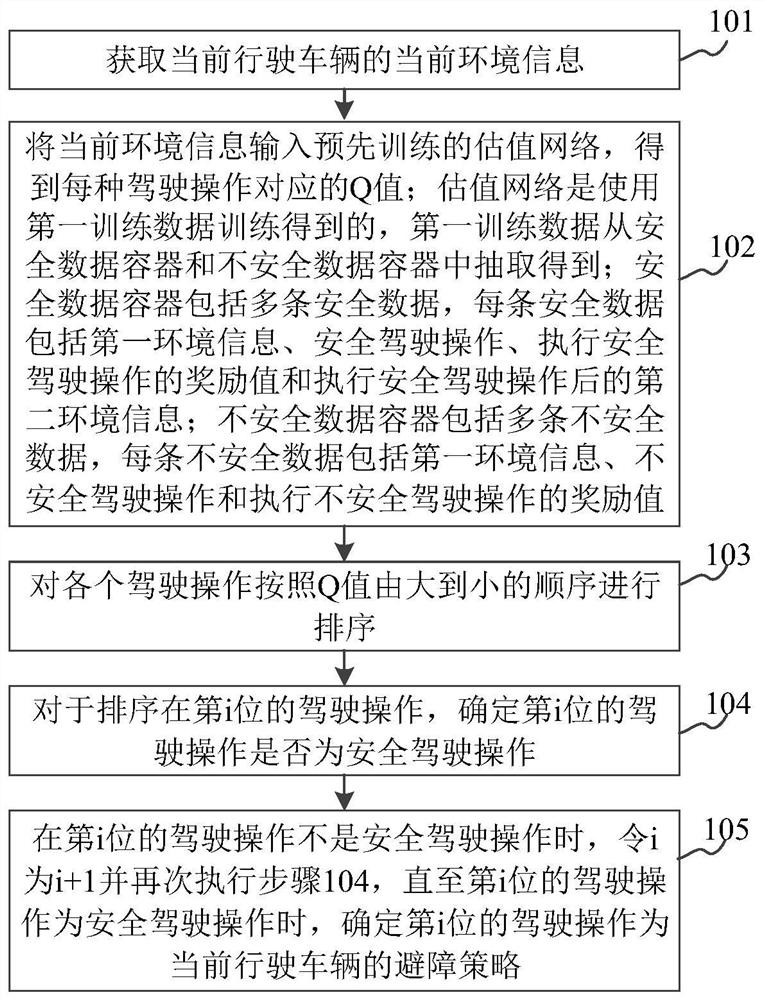
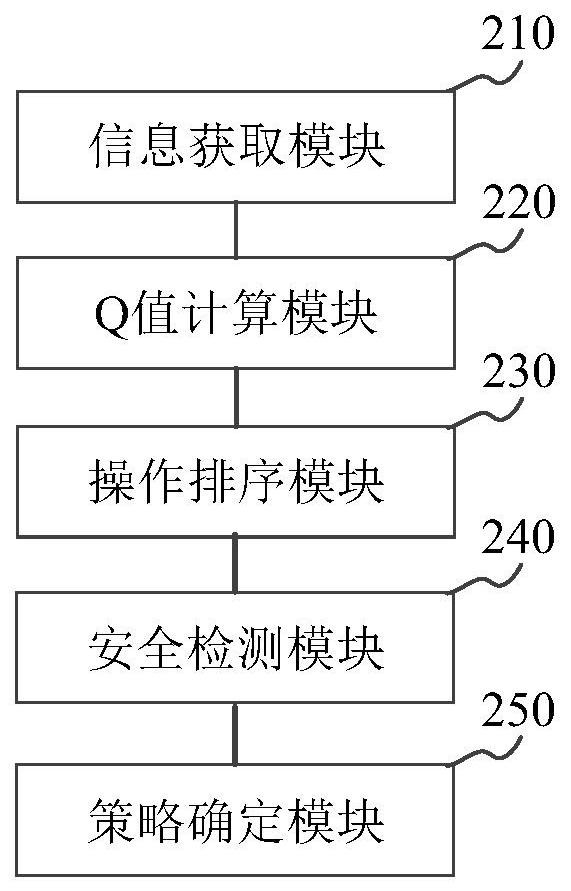
Obstacle avoidance strategy determination method and device and storage medium
ActiveCN111731326ASolve the problem of low securityImprove securityExternal condition input parametersObstacle avoidanceSafe driving
The invention relates to an obstacle avoidance strategy determination method and a device and a storage medium, and belongs to the technical field of computers. The method comprises the steps: inputting the current environment information of a current driving vehicle into an estimation network, and obtaining a Q value corresponding to each driving operation, wherein the estimation network is obtained through training by using first training data, and the first training data is extracted from a secure data container and an unsecure data container; sorting the driving operations according to thedescending order of the Q values; for the driving operation sorted at the i position, determining whether the driving operation at the i position is a safe driving operation; if the driving operation of the i position is not the safe driving operation, setting i to be i+1 until the driving operation of the i position is the safe driving operation, determining the driving operationof the i position to be an obstacle avoidance strategy of the current running vehicle; thereof the problem that an obstacle avoidance strategy determined based on rules is not high in safety canbe solved, and the safety of the determined obstacle avoidance strategy is improved.
Owner:知行汽车科技(苏州)股份有限公司
Modularly-designed fuse safety insurance mechanism
ActiveCN112525022AGuaranteed processing securityQuestions Guaranteed to AnswerAmmunition fuzesCantilevered beamExplosive train
The invention discloses a modularly-designed fuse safety insurance mechanism which is composed of three times of safety insurances, the first time of safety insurance is a recoil insurance; the secondtime of safety insurance is a centrifugal insurance; the third time of insurance is a long-distance insurance; and the three times of insurances and an explosion-proof sliding block form a main bodyof the safety insurance mechanism. At ordinary times, the explosion-proof sliding block is clamped by a recoil safety device composed of a cantilever beam mass block and a centrifugal safety device composed of a spring mass block, an explosion propagation sequence is separated, and the safety of a fuse is guaranteed. In the launching state, the safety insurance mechanism sequentially relieves thethree times of insurances by recognizing recoil force, centrifugal force and other environmental force, the explosive-proof sliding block relieves corresponding constraints, locking is completed, a detonating hole is aligned, and the safety insurance mechanism relieves the insurances. Based on the three-dimensional additive manufacturing technology, the size and the complexity of the safety insurance mechanism can be effectively reduced, the mechanism is convenient to assemble due to the modular design principle, and meanwhile the workload of optimization design of the mechanism in the futureis greatly reduced.
Owner:NANJING UNIV OF SCI & TECH
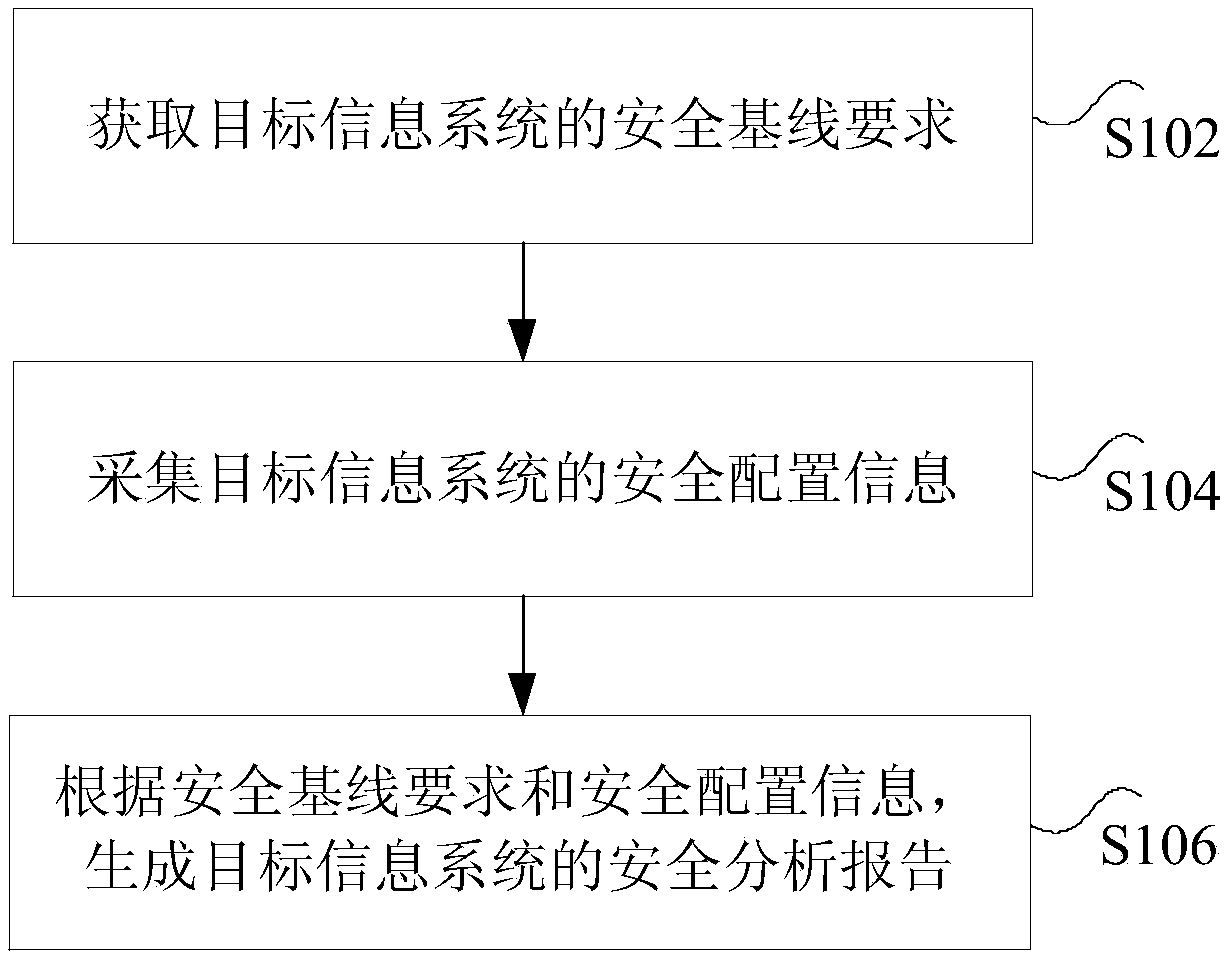
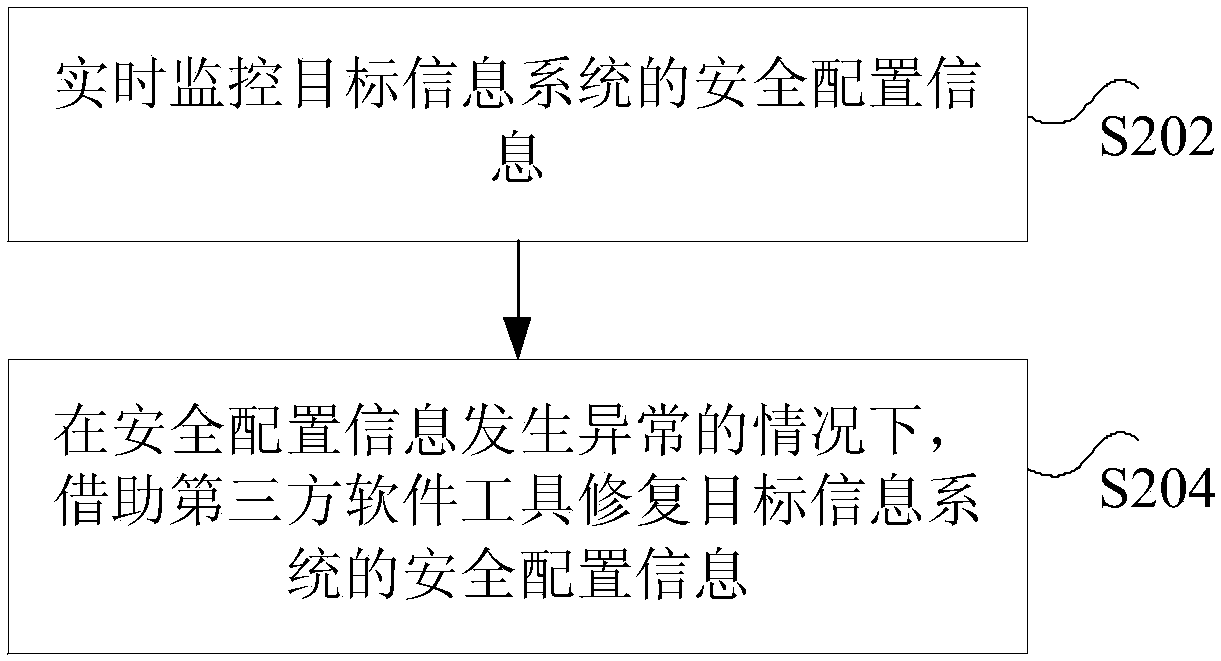
Power information system monitoring method and device
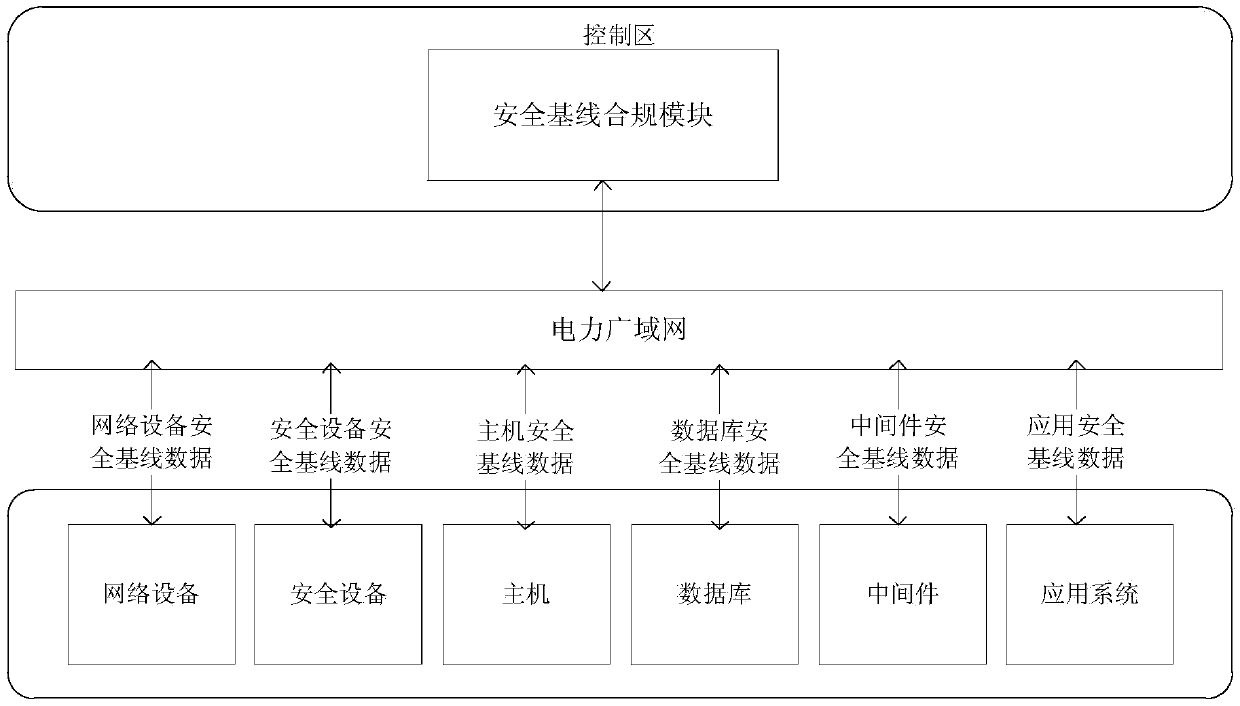
InactiveCN107689954AImprove monitoring efficiencySolve the problem of low securityTransmissionObjective informationSecurity analysis
The invention discloses a power information system monitoring method and device. The method comprises the steps of obtaining a security baseline demand of a target information system; collecting security configuration information of the target information system, wherein the security configuration information comprises at least one of the following information: first security configuration information of a network device, second security configuration information of a security device, third security configuration information of a host, fourth security configuration information of a database, fifth security configuration information of middleware and sixth security configuration information of an application system; and generating a security analysis report of the target information systemaccording to the security baseline demand and the security configuration information. According to the method and the device, the technical problem that in the prior art, the security is low due to the fact that a platform for monitoring the power information system does not exist is solved.
Owner:STATE GRID CORP OF CHINA +2
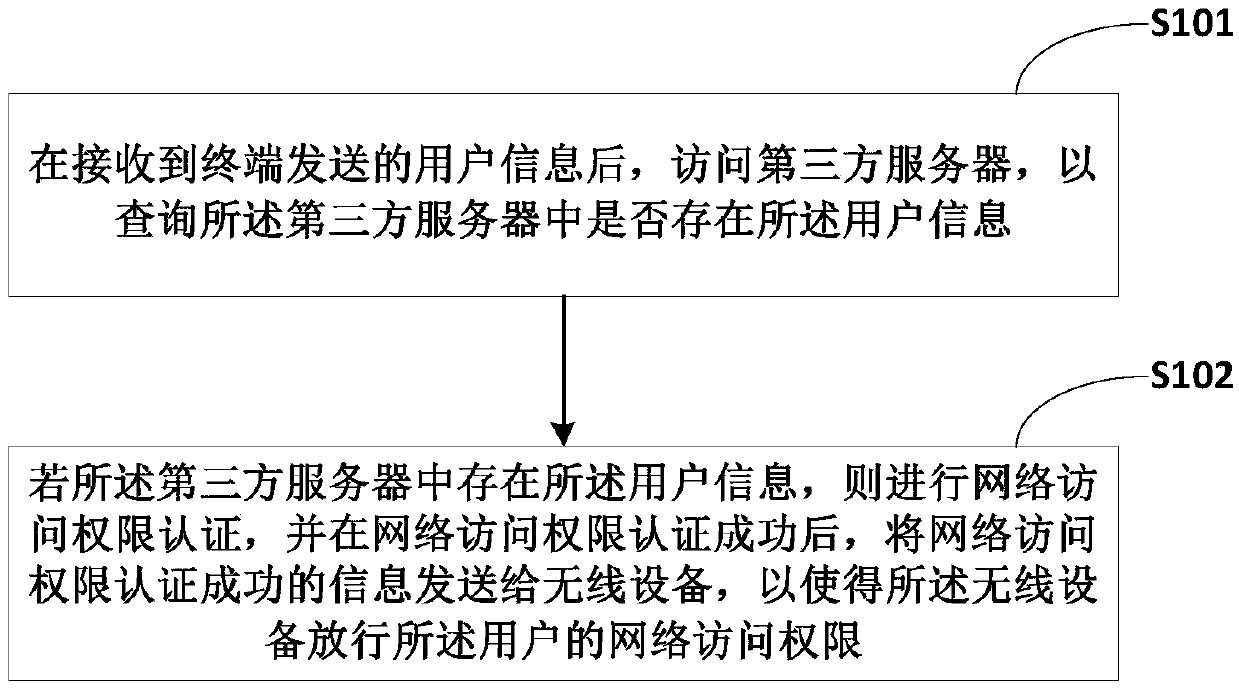
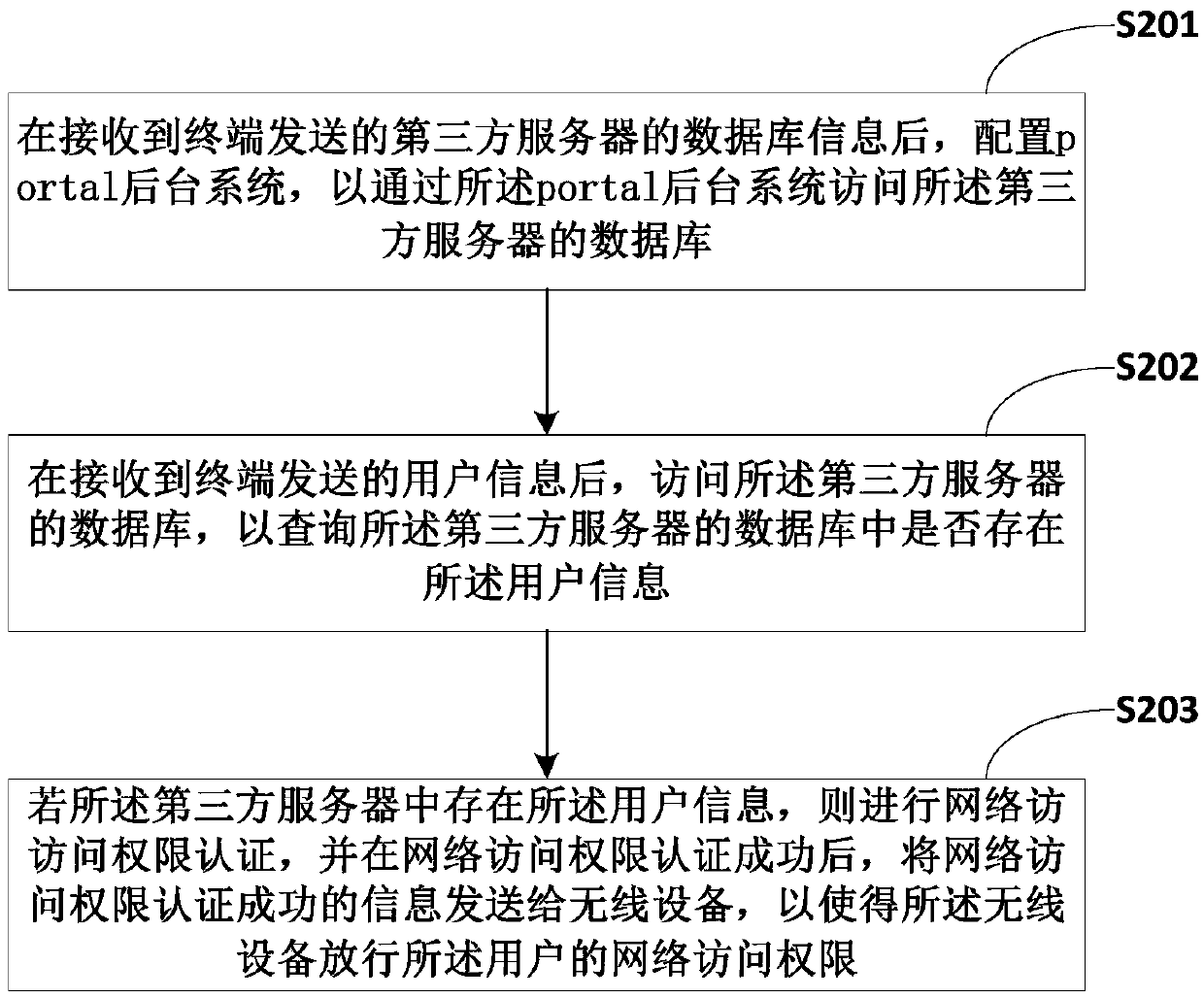
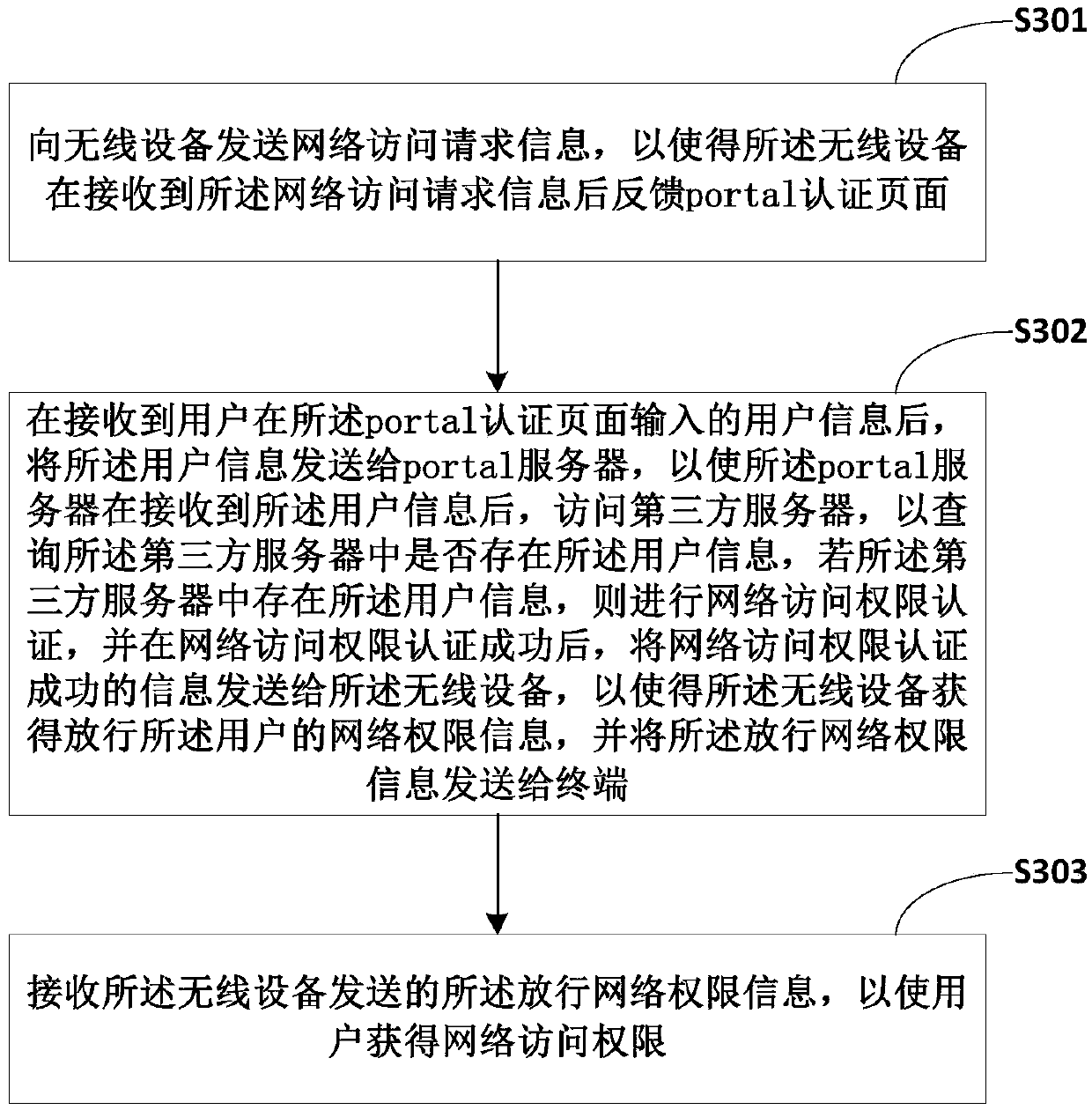
Portal authentication method, portal server and terminal
InactiveCN105516124ASolve the problem of low securityImprove securitySecuring communicationThird partyInternet privacy
The invention belongs to the technical field of the Internet, and provides a portal authentication method, a portal server and a terminal. The portal authentication method comprises the steps of after receiving user information sent by a terminal, accessing a third-party server to query that whether the user information exists in the third-party server; if the user information exists in the third-party server, authenticating network access authority, and after the authentication of the network access authority is successful, sending information about successful authentication of the network access authority to a wireless device to allow the wireless device to release the network access authority of the user. According to the portal authentication method, the user information is manually recorded for registering is avoided before portal authentication, the problem that the security of the user information is not high due to the fact that the user information is authenticated in the portal server is solved, and the security of the user information is improved while the user obtains the network access authority.
Owner:CHINA COMM TECH CO LTD +1
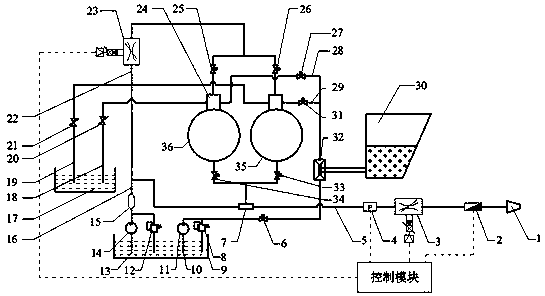
Grinding material continuous and automatic feed device capable of achieving pressure stabilization and flow stabilization
ActiveCN110125814AStrong pressure resistanceImprove pressure resistanceAbrasive feedersAbrasive machine appurtenancesBall valveAbrasive water jet
The invention discloses a grinding material continuous and automatic feed device capable of achieving pressure stabilization and flow stabilization. The device comprises a control module, dual spherical high-pressure grinding material tanks, high-pressure water pipelines, low-pressure water pipelines, feeding pipelines, a grinding material water jet pipeline, valves and sensors, wherein the valvesand the sensors are arranged on the pipelines. Valve seats of the dual spherical grinding material tanks are connected with the feeding pipelines, the high-pressure water pipelines and the low-pressure water pipelines. Water pumps are connected with above function devices through high-pressure pipelines, overflow valves, a main proportional flow valve, a bypass proportional flow valve, pneumaticball valves and high-pressure ball valves are arranged in the pipelines, and various functions are achieved through valve on-off combined control. In the device, operation of pure water jet and continuous and automatic grinding material water jet is achieved through system valve on-off combination; meanwhile, through cooperation of the sensors connected to the control module, an energy accumulatorand the flow valves, pressure stabilization and flow stabilization can be achieved, and automatic adjustment of the grinding material concentration and overpressure alarm can be achieved. The deviceis high in safety, simple in operation and capable of being used widely.
Owner:中国平煤神马控股集团有限公司 +2
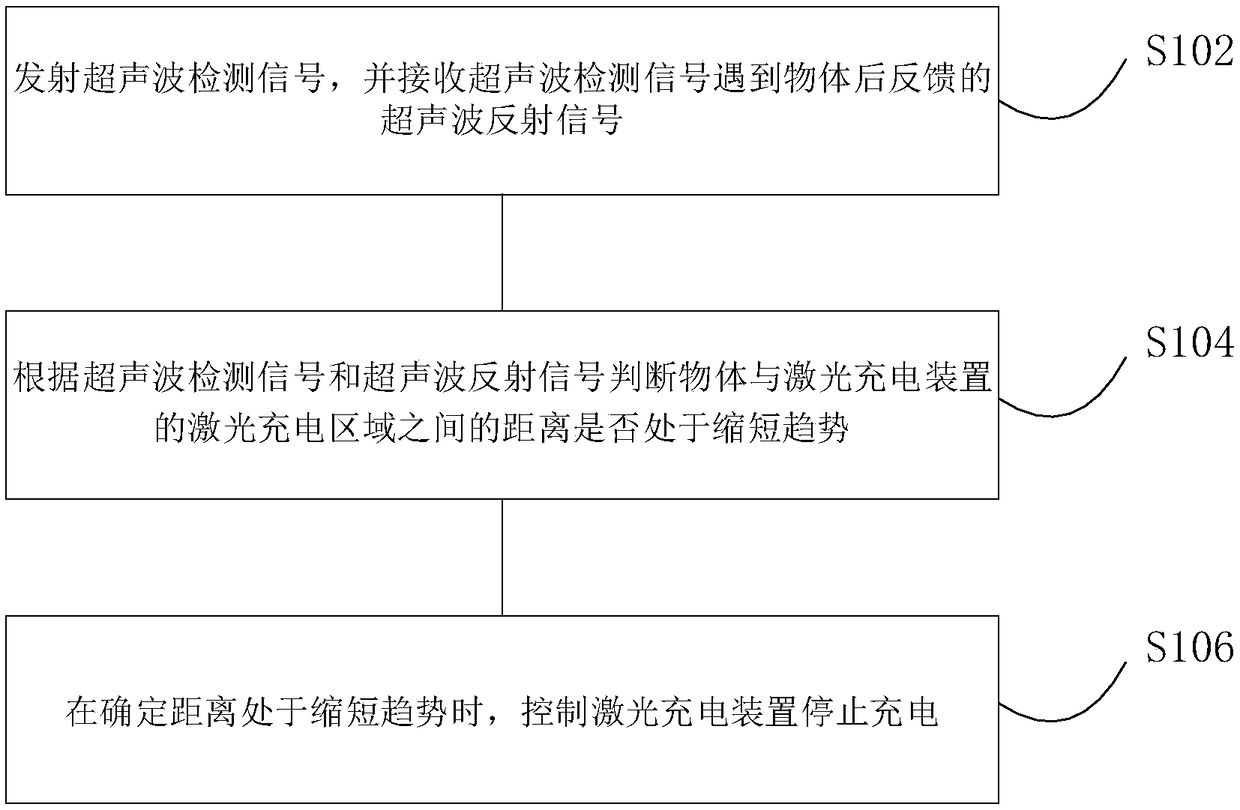
Laser charging protection method and device
ActiveCN108631452ASolve the problem of low securityImprove securityElectric powerBattery disconnect circuitsLaserUltrasound
The invention discloses a laser charging protection method and device. The method comprises the following steps of transmitting an ultrasonic detection signal, and receiving an ultrasonic reflected signal fed back after the ultrasonic detection signal encounters an object; judging whether a distance between the object and a laser charging area of a laser charging device is in a shortened trend ornot according to the ultrasonic detection signal and the ultrasonic reflected signal; and controlling the laser charging device to stop charging when the distance is determined to be in the shortenedtrend. According to the method and the device, a problem that the safety of the laser charging device is not high in the prior art is solved, and the safety of the laser charging device is improved.
Owner:GREE ELECTRIC APPLIANCES INC
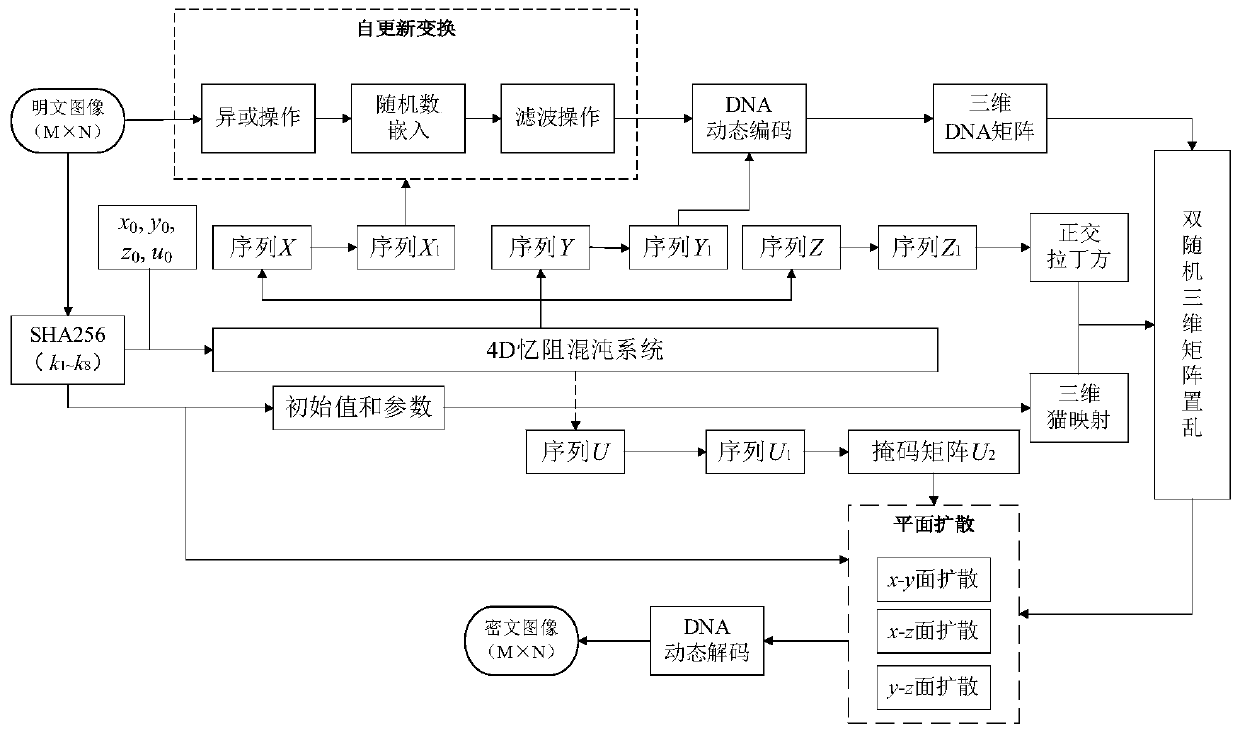
Image encryption method based on self-updating transformation, double random three-dimensional matrix scrambling and DNA calculation
ActiveCN111294481AImplement changesSolve the problem of low securitySecuring communication by chaotic signalsPictoral communicationAlgorithmCiphertext
The invention provides an image encryption method based on self-updating transformation, double random three-dimensional matrix scrambling and DNA calculation. The method comprises the following steps: giving an initial value of a 4D memristor chaotic system to generate a chaotic sequence, and calculating a hash value of a plaintext image; selecting elements from the chaotic sequence according tothe hash value to form a new chaotic sequence; performing self-updating transformation on the plaintext image P (M*N) to obtain a self-updating transformed image P3; carrying out DNA dynamic coding onthe image P3 by utilizing the DNA coding rule sequence to obtain a DNA sequence P5, and converting the DNA sequence P5 into a three-dimensional DNA matrix P6; generating a three-dimensional orthogonal Latin cube Lz1 and a three-dimensional cat mapping sequence Mp, constructing a double random three-dimensional matrix scrambling rule, and scrambling the three-dimensional DNA matrix P6 to obtain ascrambled three-dimensional matrix P7; carrying out plane diffusion on a to-be-diffused plane in the three-dimensional matrix P7 to obtain a diffused three-dimensional DNA matrix P8; performing DNA dynamic decoding on the three-dimensional DNA matrix P8, and then converting the three-dimensional DNA matrix P8 into a two-dimensional matrix with the size of M * N to serve as a ciphertext image C.
Owner:HENAN UNIVERSITY
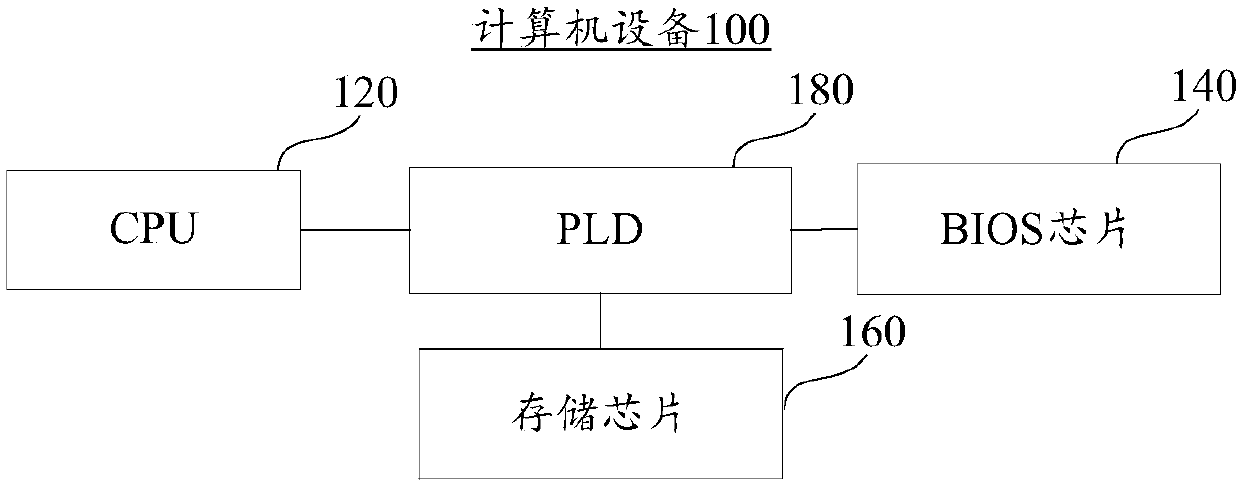
Computer device, program writing method and program reading method
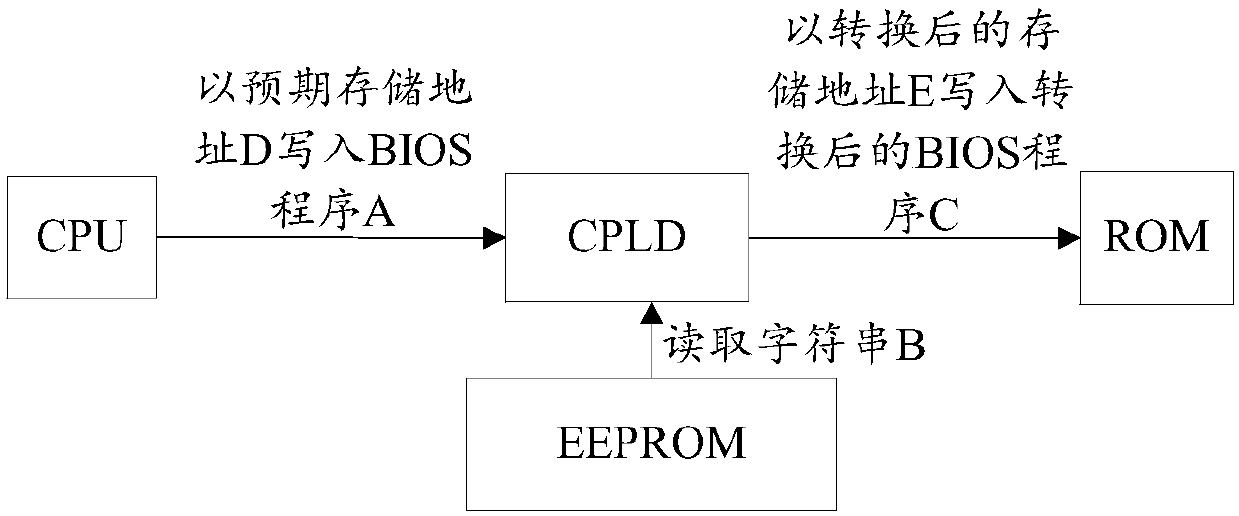
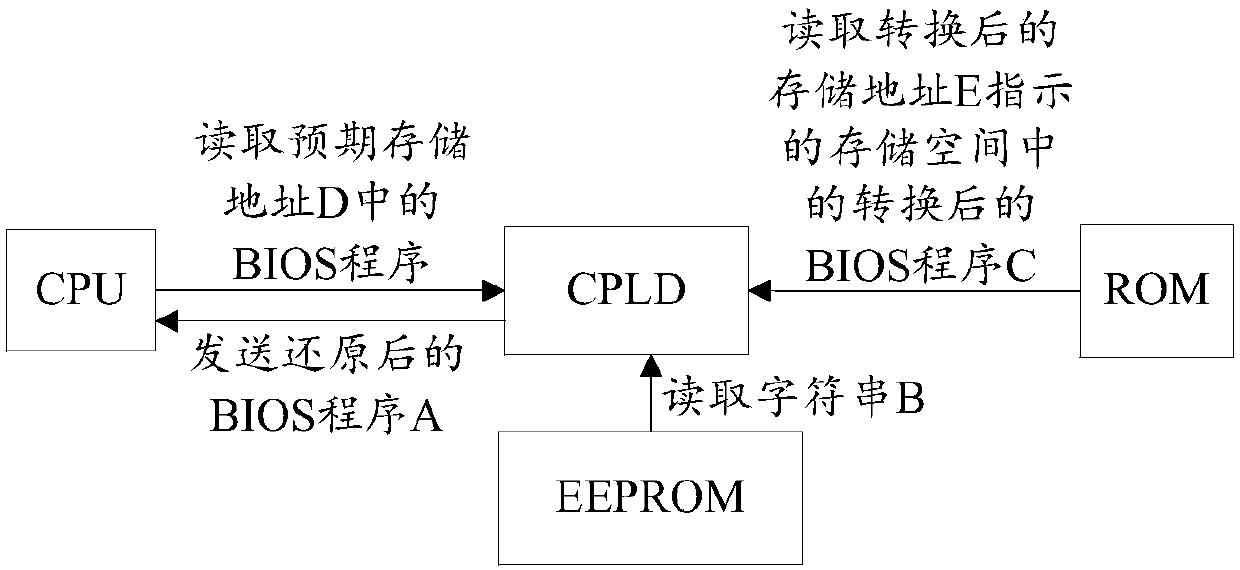
ActiveCN107832086ASolve the problem of low securityImprove securityBootstrappingProgrammable logic deviceBIOS
The invention discloses a computer device, a program writing method and a program reading method, and belongs to the technical field of computers. The computer device comprises a central processing unit (CPU), a basic input / output system (BIOS) chip, a storage chip and a programmable logic device (PLD), wherein the CPU is connected with the BIOS chip through the PLD, and the storage chip is connected with the PLD; the PLD is used for receiving a BIOS program sent by the CPU; a character string stored in the storage chip is read; the BIOS program is converted according to the character string so as to obtain a converted BIOS program, the converted BIOS program is stored into the BIOS chip, and the converted BIOS program is different from the BIOS program before conversion. The problem thatthe original BIOS program is stored in the BIOS chip, and accordingly the safety of the original BIOS program is low is solved, and the effect of improving the safety of the BIOS program in the BIOS chip is achieved.
Owner:SUZHOU YUDESHUI ELECTRIC TECH CO LTD
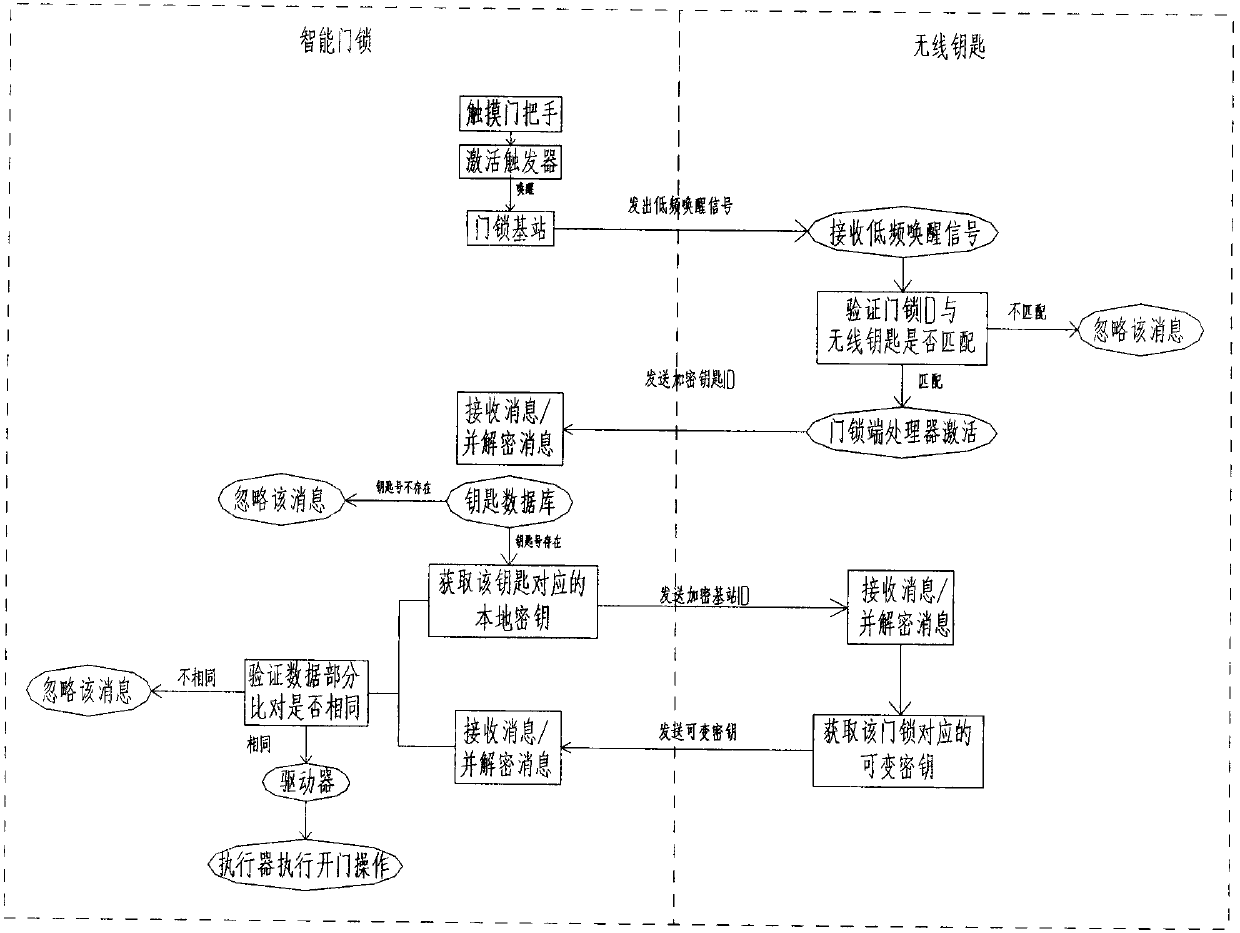
Wireless communication method of wireless intelligent door lock
InactiveCN110246239ASolve the problem of low securityImprove securityIndividual entry/exit registersSecurity arrangementCommunications securityCiphertext
The invention discloses a wireless communication method of a wireless intelligent door lock. According to the method, a key end processor is woken up by a low-frequency wake-up signal, a key ID is sent to a door lock base station by a high-frequency signal, the door lock base station performs decryption to obtain a local key, the encrypted door lock base station ID is sent to the key end by the high-frequency signal, the key end obtains the door lock base station ID after performing decryption and obtains a variable key according to the ID, the variable key is sent to the door lock base station through high frequency, and the lock base station compares the local key with the variable key, and then controls an actuator to open the door after confirming the match. By adopting the wireless communication method disclosed by the invention, the problem that the communication security of the wireless intelligent electronic door lock is not high is solved, the variable key can be formed by a rolling code and the local key, meanwhile since the rolling code is added to the encrypted data, the decrypted data and the variable key are both dynamically variable, each encrypted message encrypted by a double encryption algorithm has uniqueness, and the repetition probability of the encrypted message is infinitely close to zero, thereby effectively preventing a ciphertext from being recorded or cracked.
Owner:阳卓昆
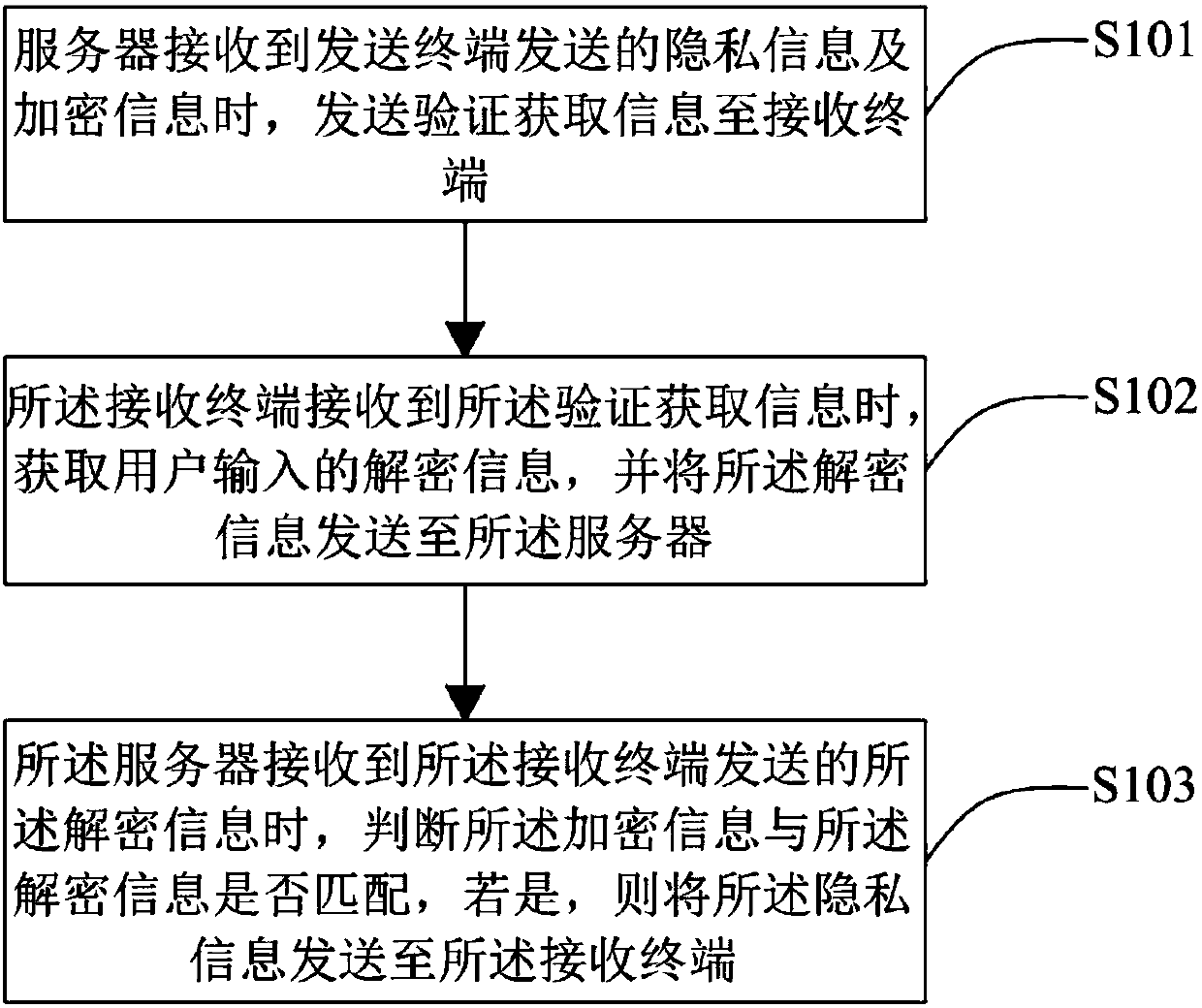
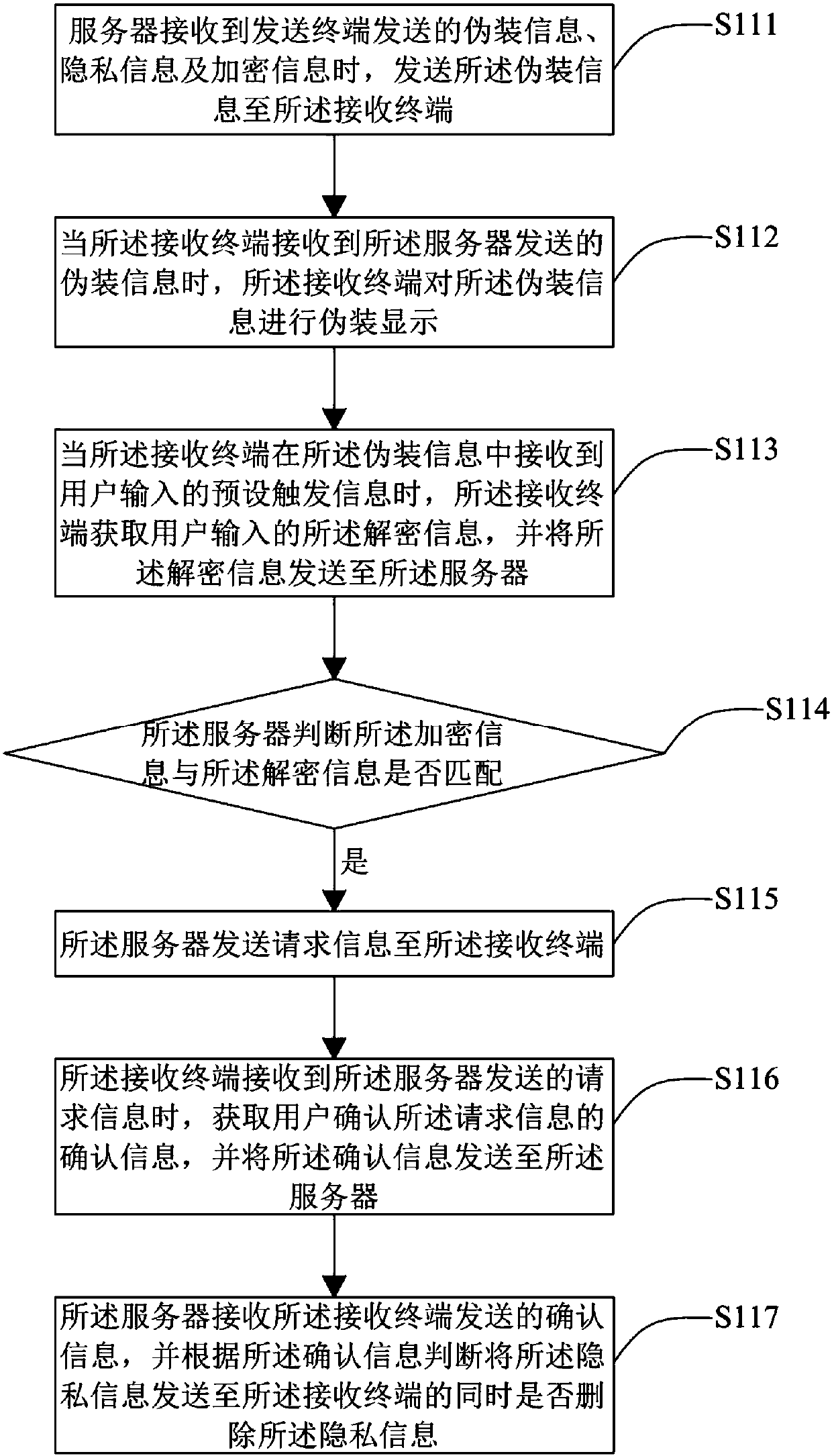
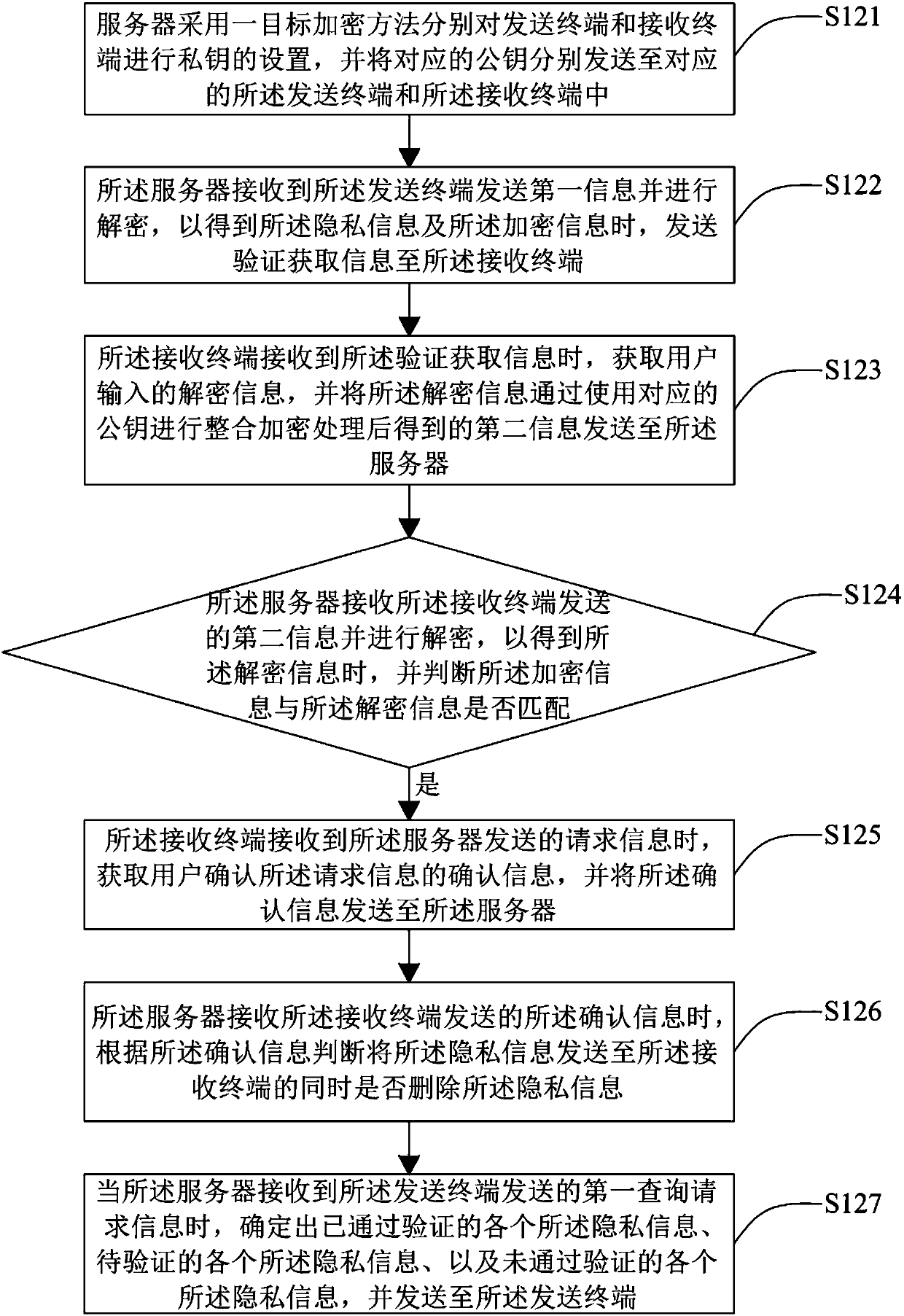
Privacy information protection method and system, server and receiving terminal
InactiveCN107786566AImprove securitySolve the problem of low securityTransmissionUser inputInternet privacy
The invention discloses a privacy information protection method and system, a server and a receiving terminal. The method is applicable to the server. The method comprises the steps that when privacyinformation and encrypted information sent by a sending terminal are received, verification acquisition information is sent to the receiving terminal, so that when the receiving terminal receives theverification acquisition information, decrypted information input by a user is received; the decrypted information sent by the receiving terminal is received; whether or not the encrypted informationis matched with the decrypted information is judged, and if yes, the privacy information is sent to the receiving terminal. According to the privacy information protection method, the server is arranged to store the privacy information, and when it is determined that the decrypted information is matched with the encrypted information, the privacy information is sent to the receiving terminal, so that the problem is solved that in the prior art, the safety is not high when the privacy information is protected.
Owner:QIKU INTERNET TECH SHENZHEN CO LTD
Verification code image generation method and device and electronic equipment
InactiveCN105323227AImprove securitySolve the problem of low securityUser identity/authority verificationElectronic equipmentComputer architecture
The invention discloses a verification code image generation method and device and electronic equipment, which belongs to the field of information safety. The method comprises the steps that the operation information of a client is acquired; according to the operation information, the difficulty level of a verification code corresponding to the client is determined, wherein the difficulty level of the verification code is one of at least two preset verification code difficulty levels; and an verification code image corresponding to the verification code difficulty level is generated. According to the invention, the operation information of the client is acquired; according to the operation information, the difficulty level of the generated verification code image is determined; the verification code image corresponding to the difficulty level is generated; different parts of the verification code image are acquired; the corresponding verification code image is generated according to the difficulty level determined by the operation information of the client; and the safety of the verification code is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
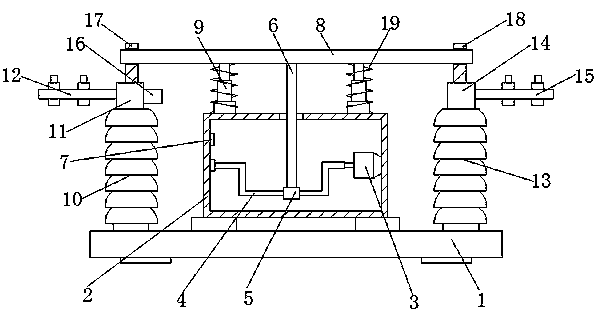
Outdoor high voltage isolation switch
The invention discloses an outdoor high voltage isolation switch. The switch comprises a steel groove base plate. The top of the steel groove base plate is fixedly connected to a box body through a support seat. The right side of the inner cavity of the box body is fixedly connected to a micro motor. The output shaft of the micro motor is fixedly connected to a concave frame. The left side of theconcave frame is movably connected to the inner wall of the box body through a bearing pedestal. A sliding sleeve sleeves the surface of the concave frame. In the invention, through the cooperation ofthe micro motor, the concave frame, the sliding sleeve, a support rod, a single chip microcomputer, a telescopic rod, a first insulating pillar, a first contact body, a first binding post, a second insulating pillar, a second contact body, a second binding post and a temperature sensor, a switch blade plate leaves a first elastic clamping sheet and a second elastic clamping sheet so that outage and energization effects are reached, the safety of a contact point is high, the safety of an isolation switch is guaranteed and the service life of the isolation switch is prolonged.
Owner:许昌亿源电气有限公司
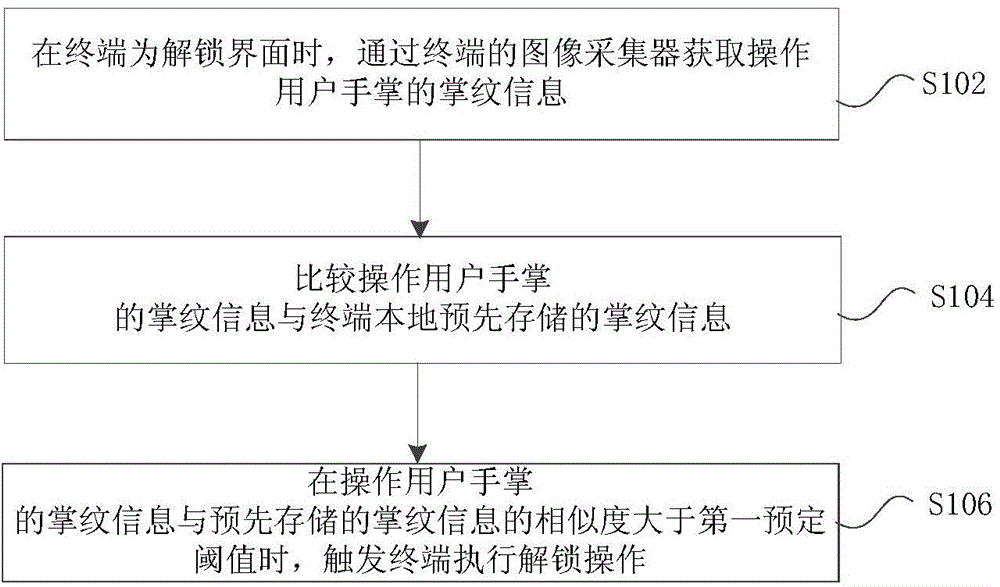
Unlocking method and device based on palm prints and terminal
InactiveCN106156570AEasy access and identificationSolve the problem of low securityDigital data authenticationSubstation equipmentPalm printComputer science
The invention provides an unlocking method and device based on palm prints and a terminal. The method includes the steps that when the terminal is an unlock interface, palm print information of the palm of an operation user is obtained through an image collector of the terminal; the palm print information of the palm of the operation user is compared with palm print information locally pre-stored in the terminal; when the similarity of the palm print information of the palm of the operation user and the pre-stored palm print information is larger than a first preset threshold, the terminal is triggered to execute unlocking operation. By means of the method and device and the terminal, the problems that in the prior art, an unlocking method of the terminal is low in safety and low in recognition rate are solved, and the effect of improving user experience is achieved.
Owner:ZTE CORP
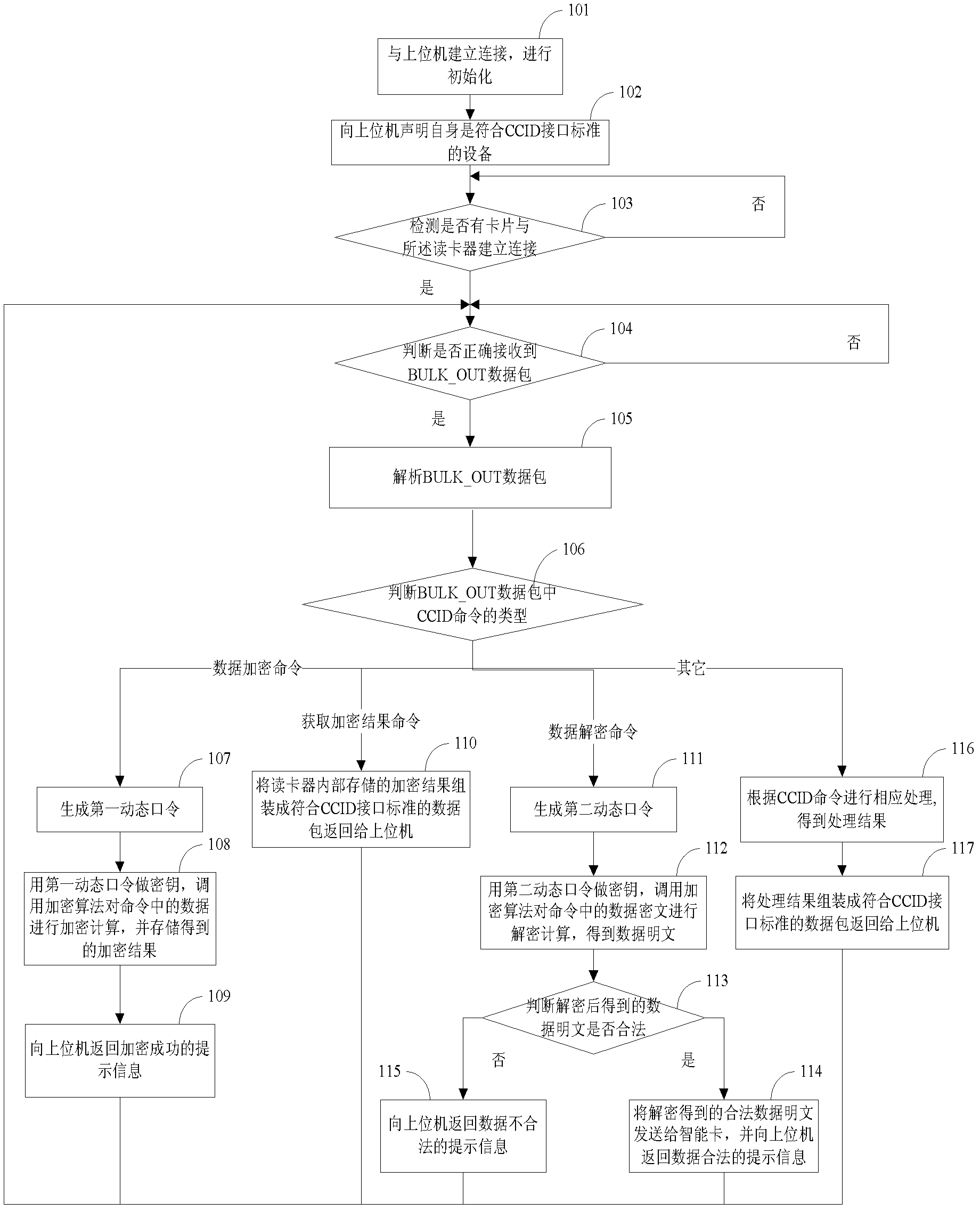
Data processing device and data processing method thereof
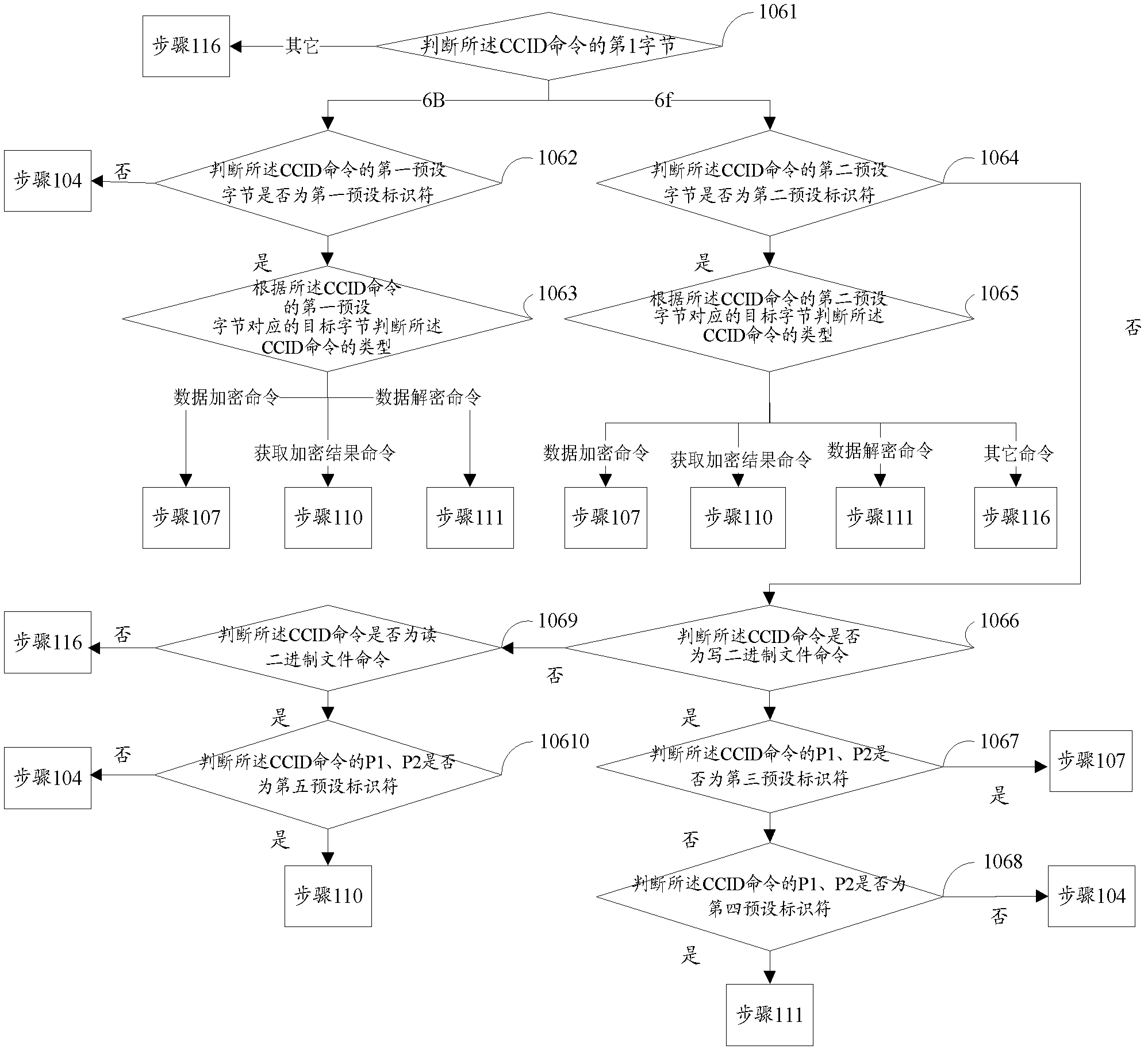
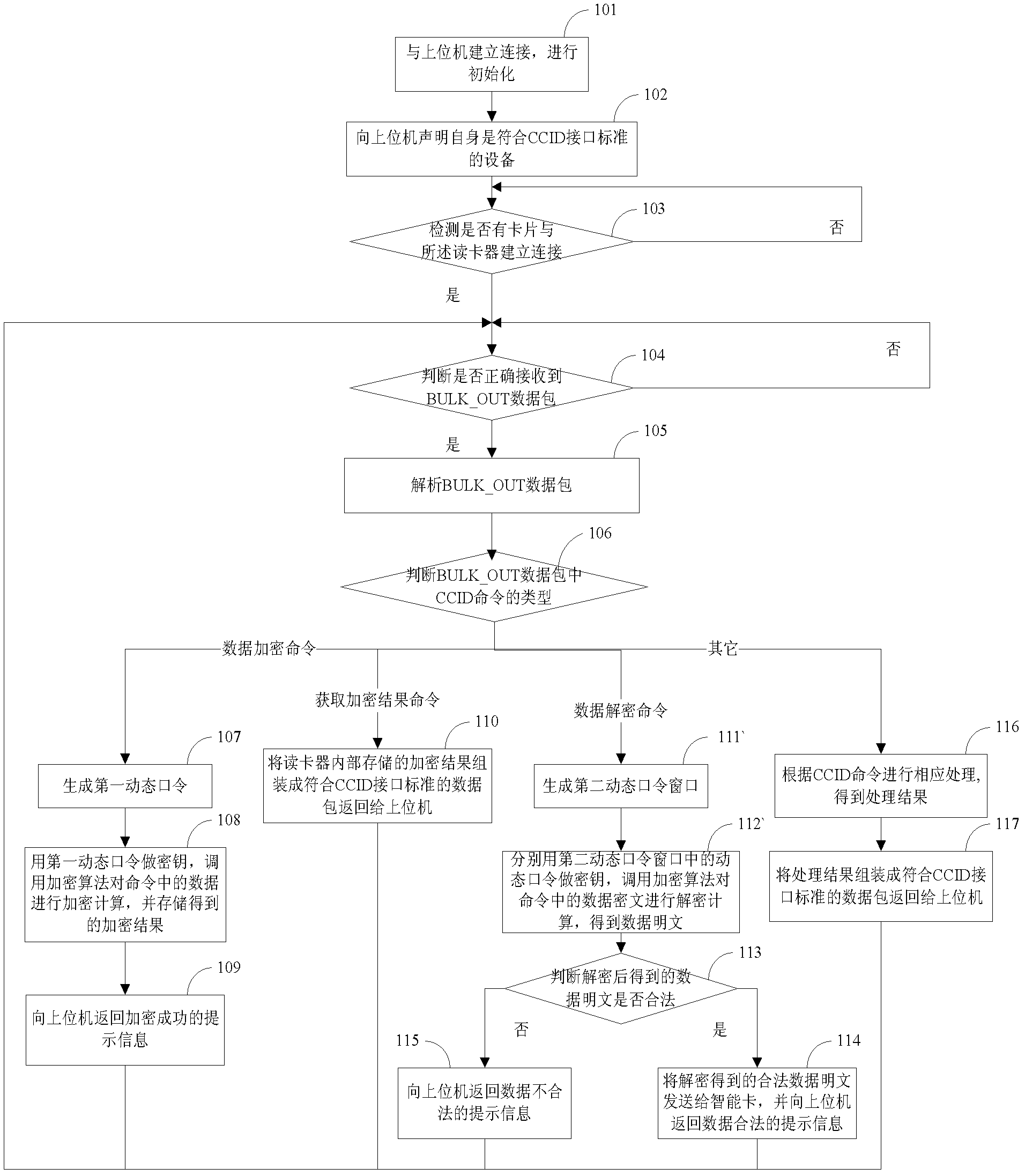
InactiveCN102307100AEnsure safetySolve the problem of low securityUser identity/authority verificationNetwork packetInterface standard
The invention discloses a data processing device and a data processing method thereof, belonging to the field of information security. The data processing device comprises an interface module, a receiving module, an acquisition module, an encryption sending module, a generation sending module, a decryption module, a card slot module and a power supply module. The working method comprises the steps of: establishing a connection between the device and an upper computer; declaring to the upper computer that the device is in accordance with the CCID (chip card interface device) interface standard; receiving a BULK_OUT data packet; acquiring the types of a CCID command according to the byte of the CCID command in the BULK_OUT data packet, wherein the types of the CCID command comprise a data encryption command, an acquisition encryption result command and a data decryption command; executing the corresponding operation according to the types of the CCID command; and returning the corresponding response to the upper computer.
Owner:FEITIAN TECHNOLOGIES
Door sheet pressing device for vehicle-mounted toilet machining and application method thereof
The invention discloses a door sheet pressing device for vehicle-mounted toilet machining. The device comprises a support base; two sets of support feet are mounted on the side near the top of the support base in parallel; cushion plates are welded at the two ends of the top of the support base; two sets of support columns are mounted at the top of each cushion plate in parallel; and positioning plates are arranged at the tops of the support columns. The device is provided with cover plates, and the cover plates are fixed with connecting plates and fixed feet through rotating shafts, so that the overturning of the cover plates is realized, and the pressing operation of the whole device is convenient; driving rods are arranged at the tops of the cushion plates for driving transmission rods,and the support columns are driven by rotation of the transmission rods for lifting cooperation with jacking cylinders, so that the positioning plates can be lifted; through cooperation with pressingof pressing plates, the door sheet pressing efficiency is improved; and through arrangement of fixing pieces, the bottoms of door sheets placed on the positioning plates can be fixed to prevent movement during pressing of the door sheets, so that the door sheet pressing accuracy is improved.
Owner:ANHUI JINCEN COMPOSITES
Convenient-to-operate charging equipment for new energy automobile
InactiveCN111923769ASolve the problem of inconvenient use and low safety of charging equipmentSolve the problem of low securityCharging stationsNon-rotating vibration suppressionNew energyStructural engineering
The invention belongs to the technical field of new energy, in particular to convenient-to-operate charging equipment for a new energy automobile. In view of the problems that the existing new energyautomobile charging equipment is inconvenient to use and the safety of charging equipment is not high, the convenient-to-operate charging equipment for a new energy automobile comprises a pile body; abase is fixedly mounted at the lower end of the pile body; idler wheels are movably installed behind the lower end of the base. Supporting legs are fixedly mounted in front of the lower end of the base. Fixing rods are fixedly mounted on the outer surfaces of the two ends of the base correspondingly. A stop rod is fixedly connected to one end of the fixing rod, a mounting rod is fixedly mounted on the outer surface of the rear end of the pile body, a positioning rod is fixedly connected to the rear end of the mounting rod, a handle is fixedly connected to the upper end of the positioning rod,and a mounting base is fixedly mounted on the outer surface of the lower end of the base. The charging equipment can be conveniently moved and fixed by utilizing the idler wheels and the supporting legs, so that the charging equipment is convenient to use, and the safety of the charging equipment during use can be improved.
Owner:吴报飞
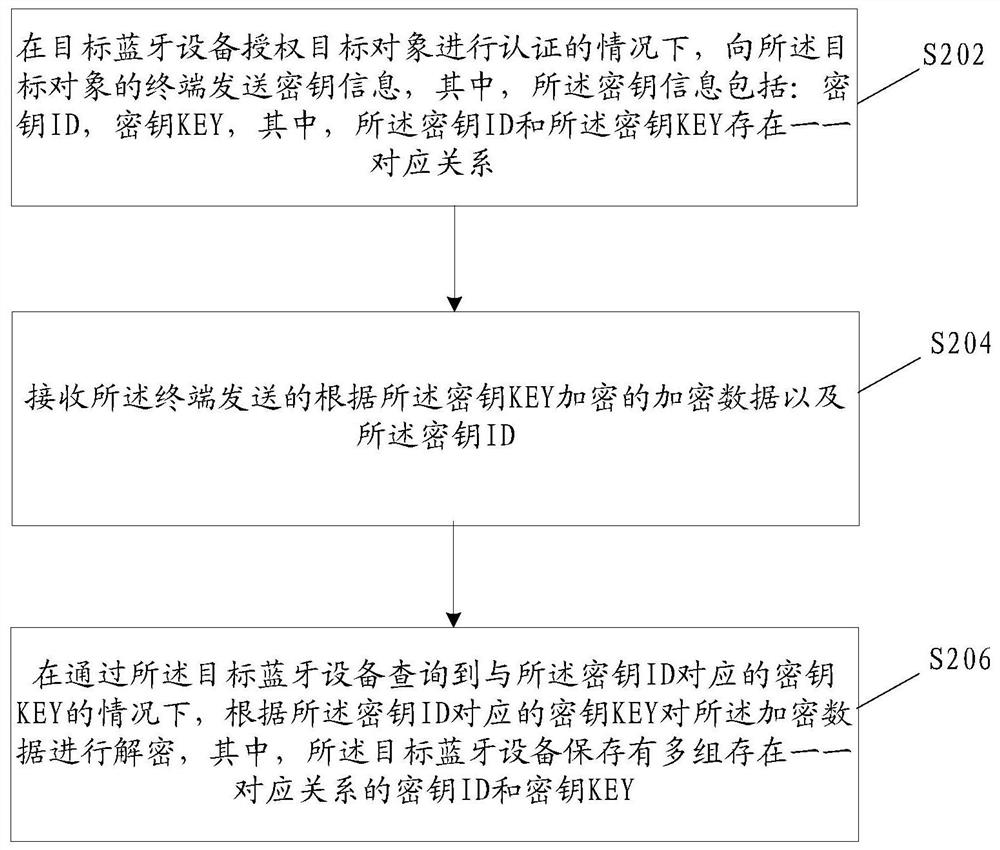
Equipment control data acquisition method and device, storage medium and electronic device
PendingCN111787514ASolve the problem of low securityImprove securityShort range communication serviceSecurity arrangementControl dataData acquisition
The invention provides an equipment control data acquisition method and device, a storage medium and an electronic device. The method comprises the steps of: under the condition that a target Bluetooth device authorizes a target object to conduct authentication, sending secret key information to a terminal of the target object, wherein the secret key information comprises secret key IDs and secretkey KEYs, and the secret key IDs and the secret key KEYs have a one-to-one correspondence relation; receiving encrypted data encrypted according to the key KEY and sent by the terminal and the key ID; under the condition that the key KEY corresponding to the key ID is inquired through the target Bluetooth device, sending the key ID to the target Bluetooth device; and decrypting the encrypted dataaccording to the key KEY corresponding to the key ID, wherein the target Bluetooth device stores a plurality of groups of secret key IDs and secret key KEYs which are in one-to-one correspondence, and the problems that in the prior art, when data plaintext authentication is carried out based on BLE GATEE, safety is low and the like are solved.
Owner:HAIER YOUJIA INTELLIGENT TECH BEIJING CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com