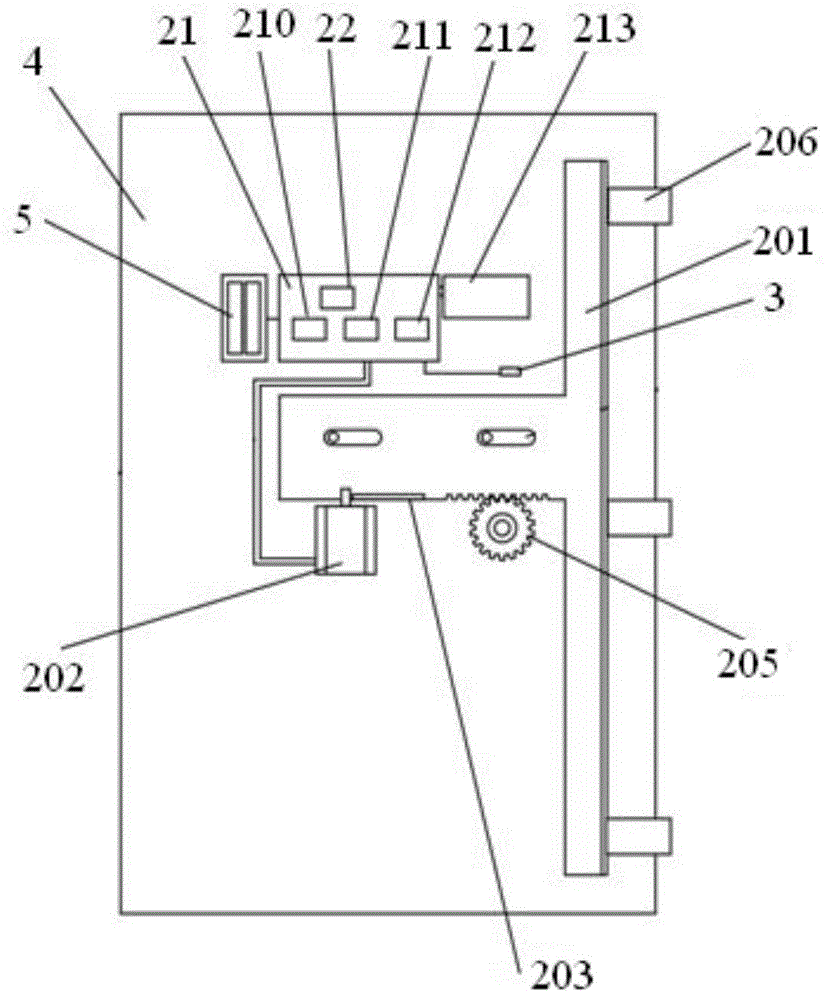
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
57 results about "Default password" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Where a device needs a username and/or password to log in, a default password is usually provided that allows the device to be accessed during its initial setup, or after resetting to factory defaults.
Method for quickly spreading registration among broad community of users in network system
InactiveCN101697538AAvoid randomnessImprove login success rateTransmissionNetworked systemUser identifier
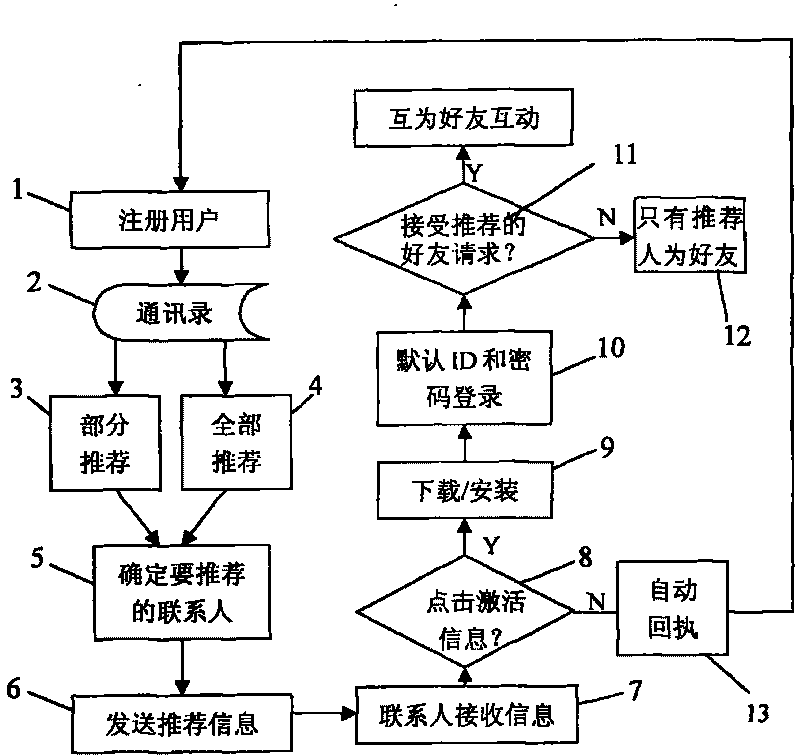
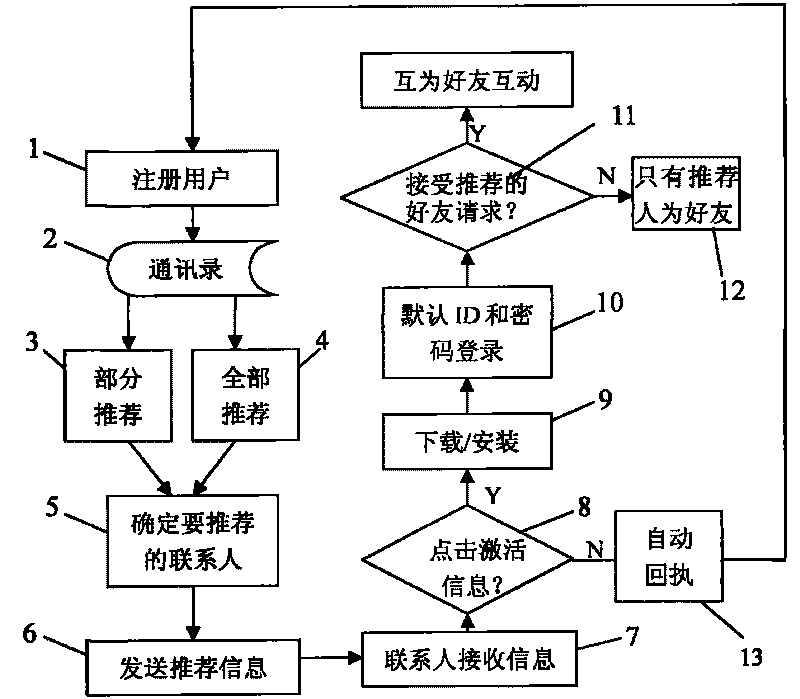
The invention discloses a method for quickly spreading registration among a broad community of users in a network system, which comprises that: registered users of the network system select a recommended mode and transmit recommended information to contact persons; after receiving the information, the contact persons download and install the system; the system automatically takes information receiving IDs of the contact persons as accounts and allocates default passwords; and the contact persons can log in the system instantly when clicking OK. In the method, the quick spreading of registration is realized through trust determined among the users and the contact persons in address lists of the users and the registration steps are simple; the IDs of the users receiving the information are automatically taken as the login IDs, which avoids the registration randomness of the users and improves the success ratio of the login of the users; when recommending the contact persons, the registered users can select a partially-recommending mode and a fully-recommending mode and also can select whether the users and the recommended contact persons are friends or not, and then the contact persons accept the recommendation according to the mode and can see a friend list after the login, thus the contact persons are avoided from adding the friends one by one; and when the IDs of the users are changed, histories of the old IDs can be synchronized to new IDs, thus user viscosity is improved.
Owner:SHENZHEN TEMOBI SCI &TECH
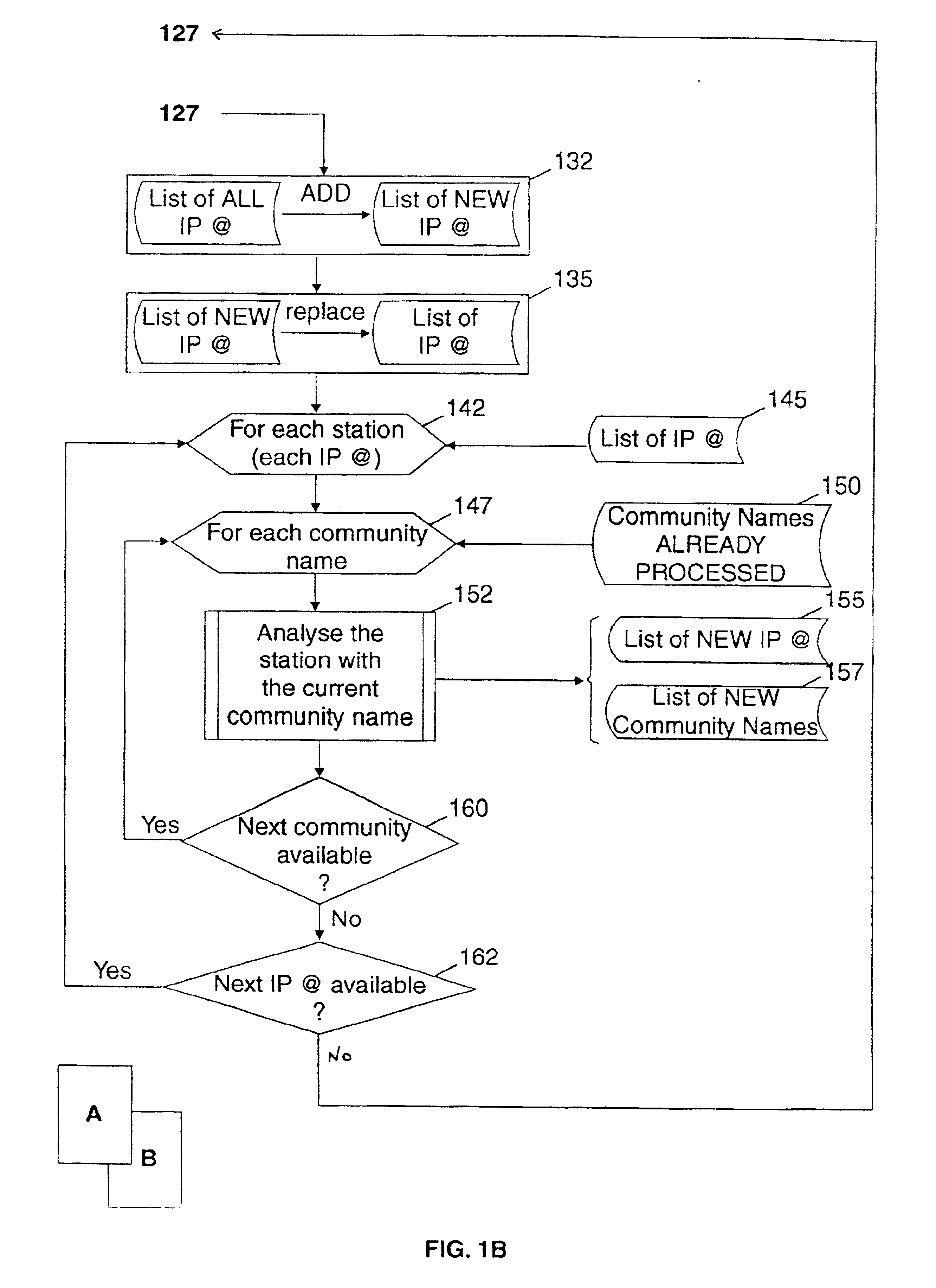
Method and system for evaluating network security
InactiveUS6895436B1Multiple digital computer combinationsData switching networksIp addressNetwork security policy
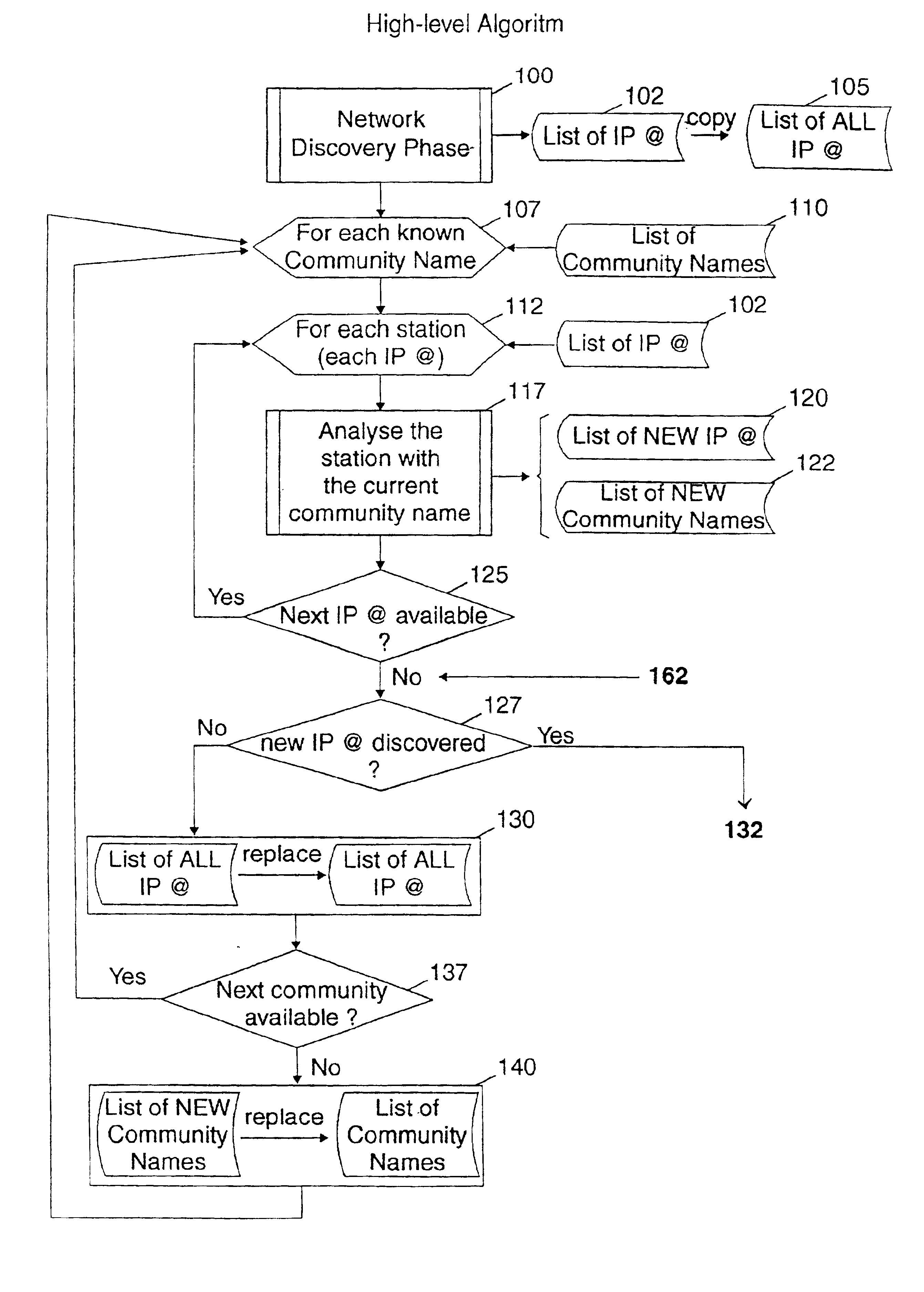
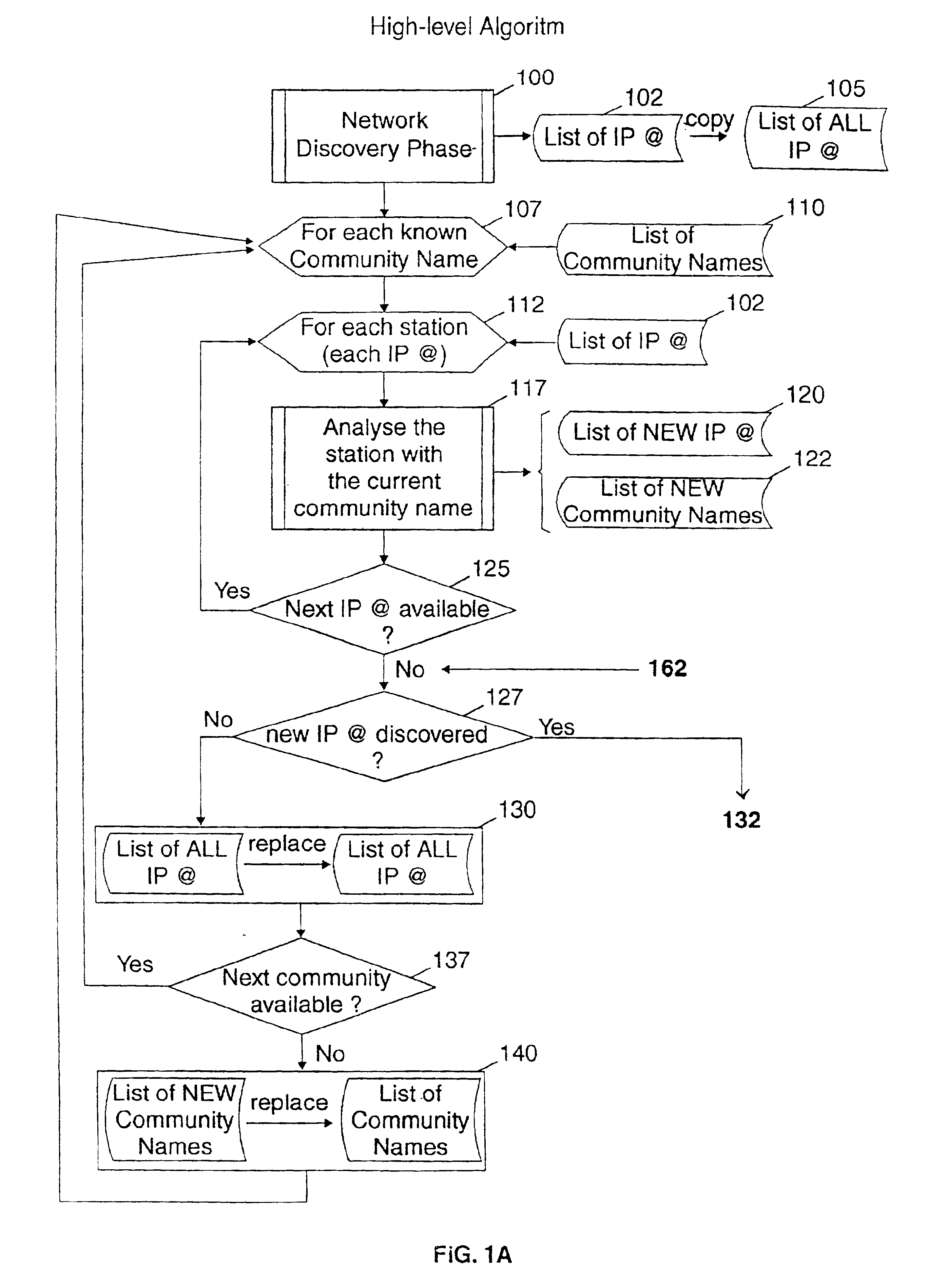
A method for automatically identifying from an ordinary station connected to a TCP / IP network, the network components managed by a network management station for which it is possible to read or write over the confidential network data they store. Starting from the list of the default passwords protecting the network data and the IP addresses of the network components communicating with the ordinary station, the method allows by repeating the IP address discovery process, to discover step by step the passwords used in all the network components managed by the network management station and try to use them in reading or writing network information.The method allows detecting the lack of protection by password which usually occurs in campus networks and thus auditing such networks against intrusion from one of the stations of the network.
Owner:IBM CORP
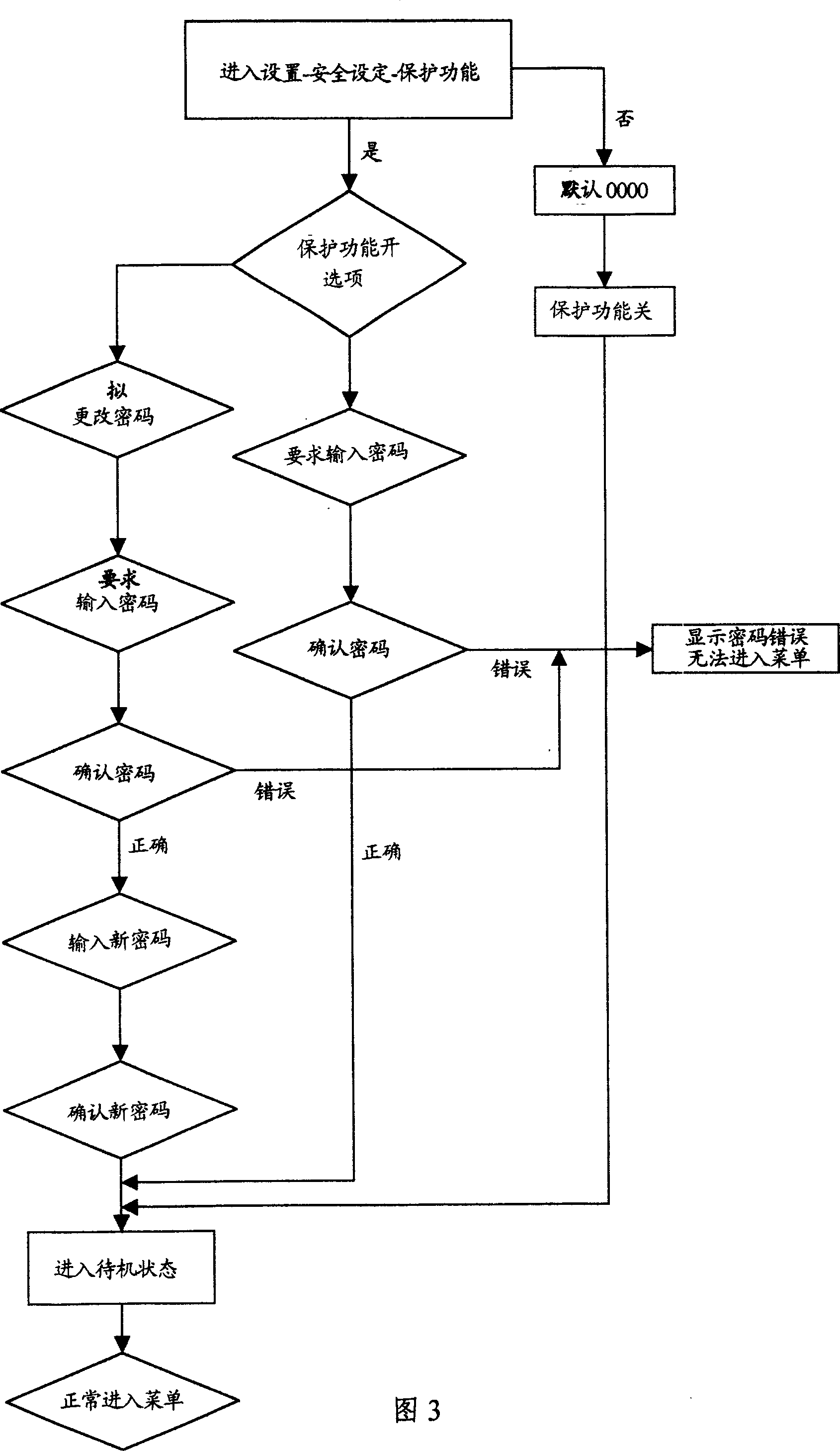
Mobile phone with enciphered short message, conversation recording and telephone directory menu
InactiveCN1426262AEasy to useEasy to operateEncryption apparatus with shift registers/memoriesRadio/inductive link selection arrangementsDefault passwordMobile phone
A mobile telephone with encrypted menu of short message and message registration and telephone book, in which the system module is composed of a ULYSSE17UBGA circuit connected with a KSA3240VTA memory, comprises a keyboard for input setting-safety detecting-protecting, a setting program for inputting default password when it doesn't need to encrypt, a program for inputting menu options of the short message and message registration and telephone book when need to encrypt, a program for inputting updating or not updating the password, an inputting confirming program when not need to update, a program for inputting a new password and confirming the new password when need to update the password, a program for inputting requested password for entering the menu of setting and confirming the password.
Owner:HAIER GRP CORP +1
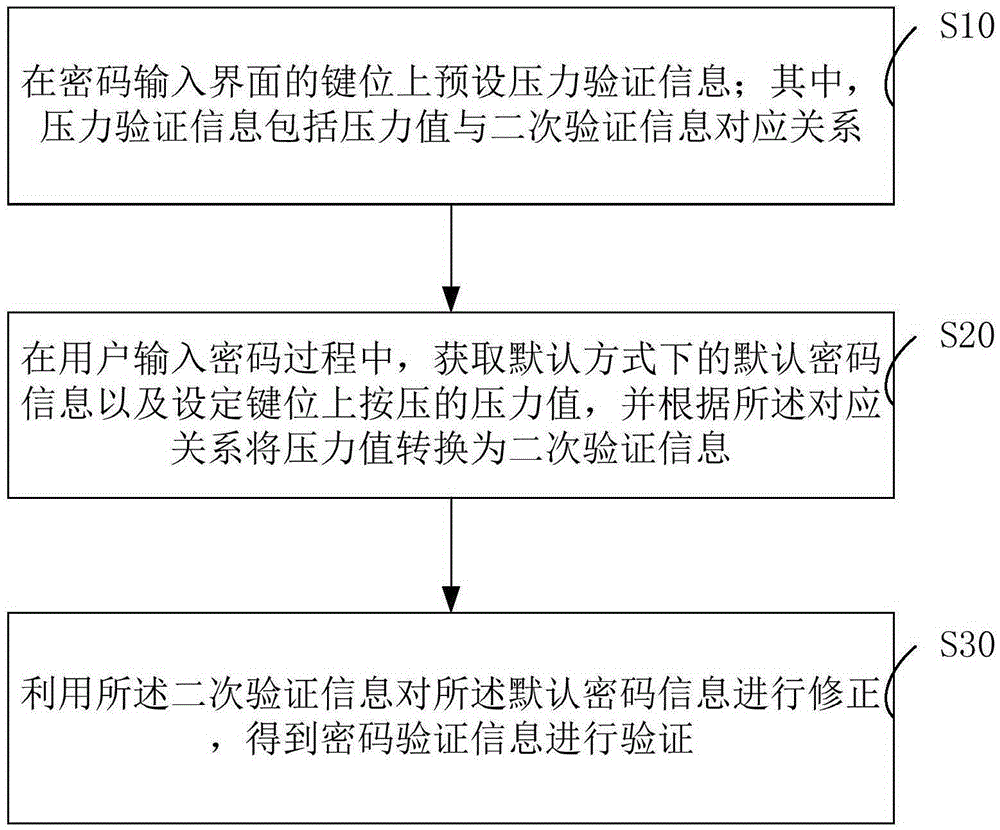
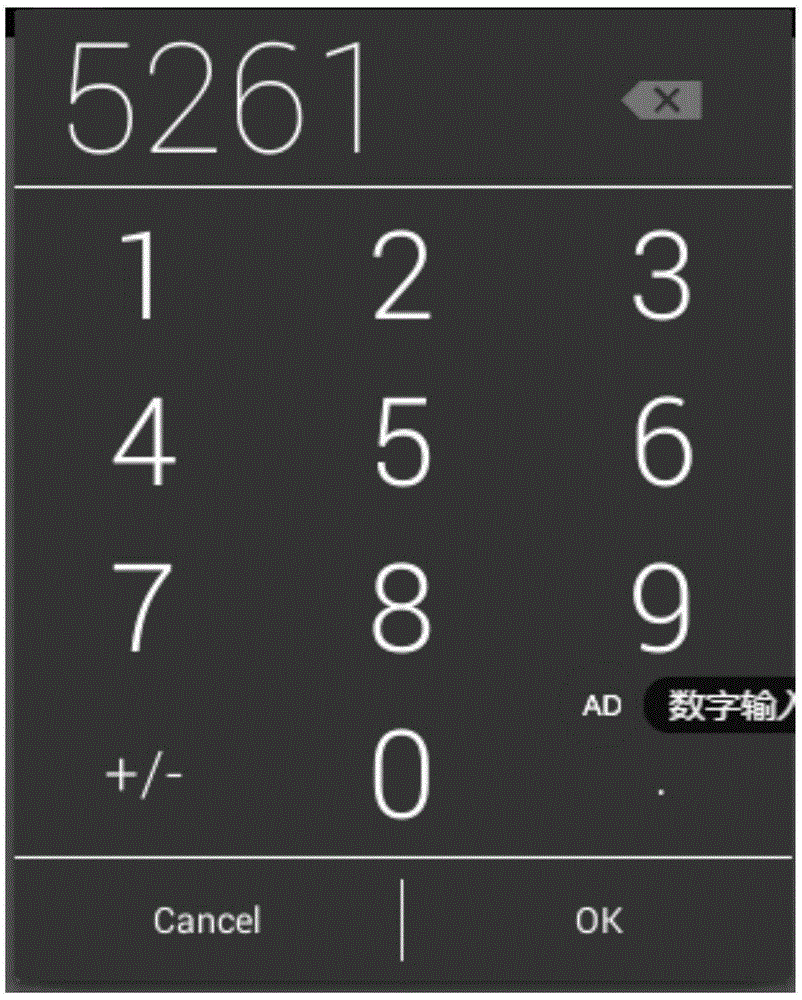
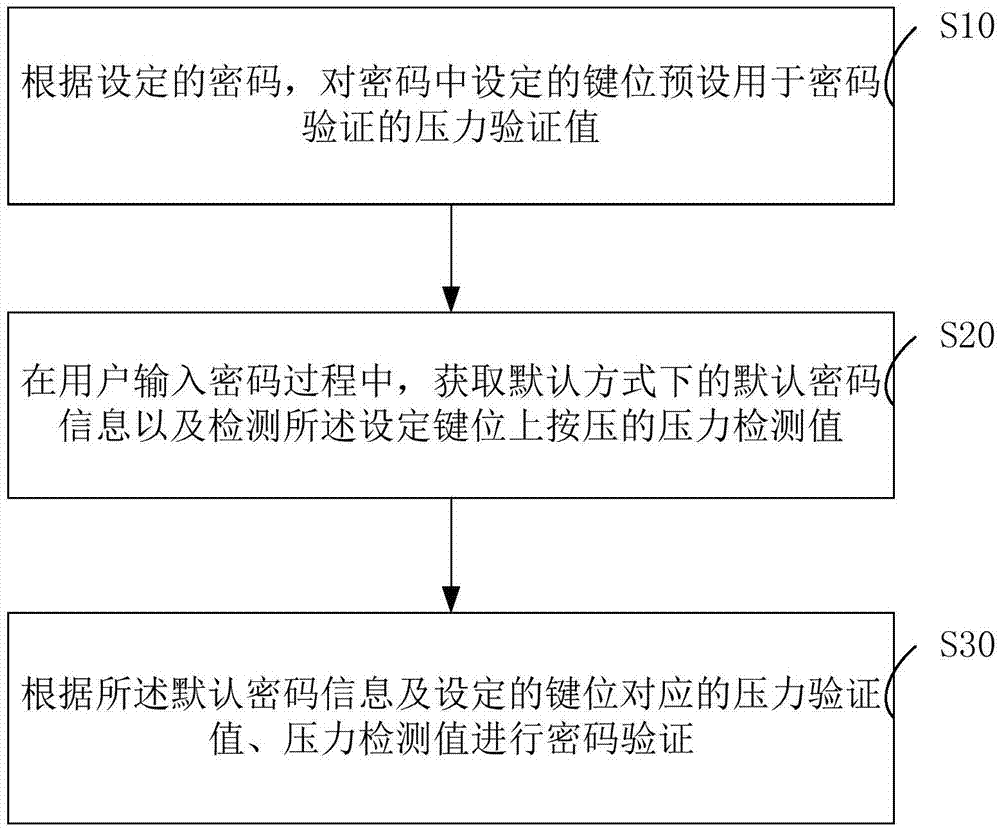
Password input verification method and system
ActiveCN105354458AImplement two-factor authenticationReduce theftDigital data authenticationValidation methodsUser input
The present invention relates to a password input verification method and system.The method comprises: presetting pressure verification information on keys of a password input interface, wherein the pressure verification information comprises a correspondence between a pressure value and secondary verification information; when a user inputs a password, acquiring default password information of a default mode and a pressure value of pressing on set keys, and converting the pressure value into the secondary verification information according to the correspondence; and using the secondary verification information to correct the default password information, so as to acquire password verification information and perform verification. According to the technical scheme provided by the present invention, two-factor verification is achieved; and only a default input mode during the password input process can be watched by a bystander, so that the password of a user cannot be cracked even though the password is leaked, thereby reducing the possibility that user privacy is stolen and improving security.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
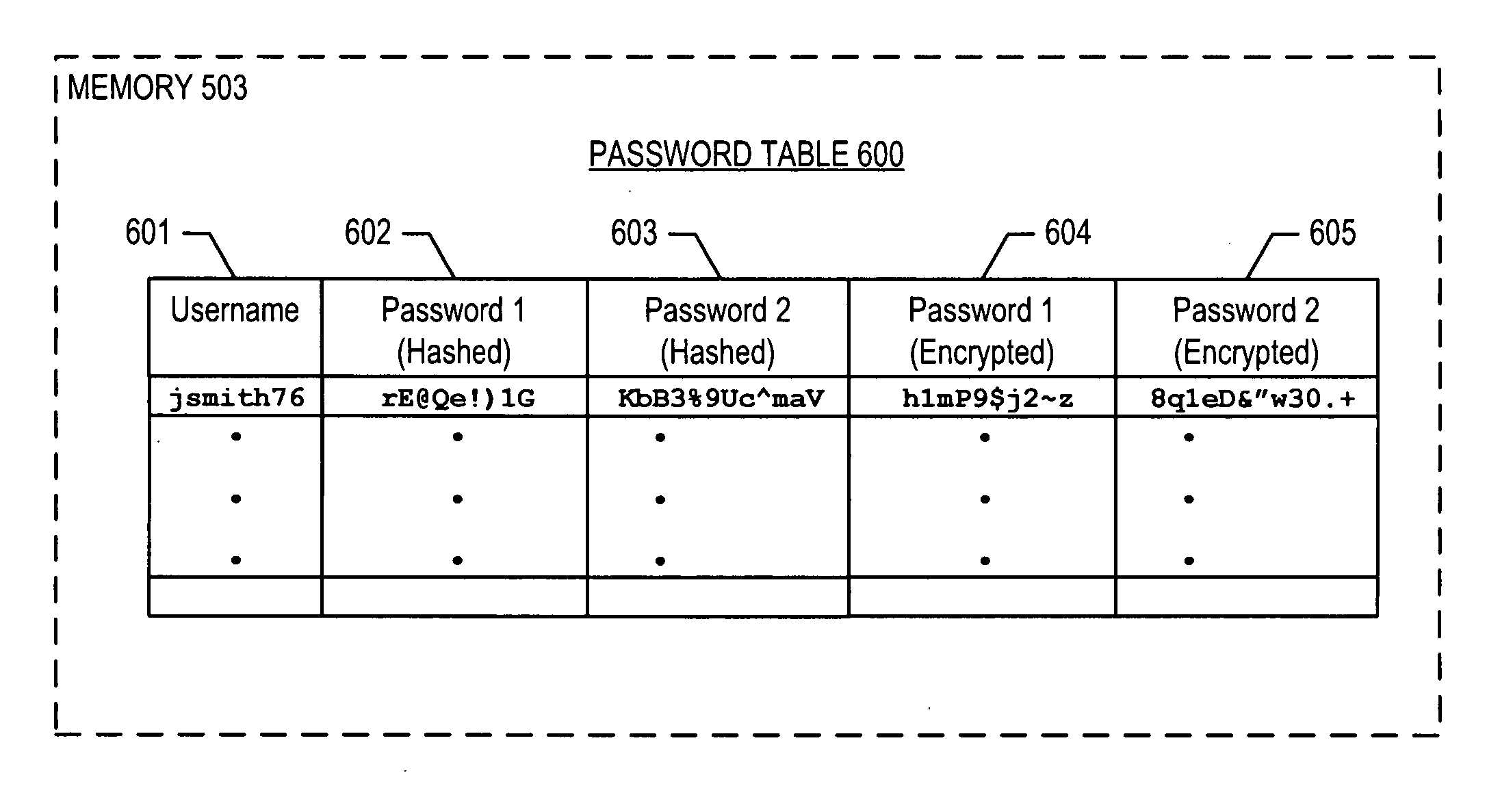
Secure recoverable passwords
InactiveUS20070079143A1Compromise safetyUnauthorized memory use protectionHardware monitoringDefault passwordCipher
A method and apparatus are disclosed that enable a user who forgets one of his two passwords to securely recover the forgotten password. After a user logs in using one of his two passwords, the illustrative embodiment reveals the other password to the user. The passwords are stored in a persistent table in both hashed and encrypted forms, but not in their original forms. The illustrative embodiment is advantageous over the prior art, where forgotten passwords are reset to a default value, in two ways. First, it avoids the inconvenience of a user having to log in using the default password, think up a new string that would make a good password, and change the password from the default to the new string. Second, it avoids the use of default-value passwords that might compromise security.
Owner:AVAYA INC
Encryption method and system based on white box
ActiveCN106506158AProtection securityProtect privacy and securityKey distribution for secure communicationBrute forceUser input
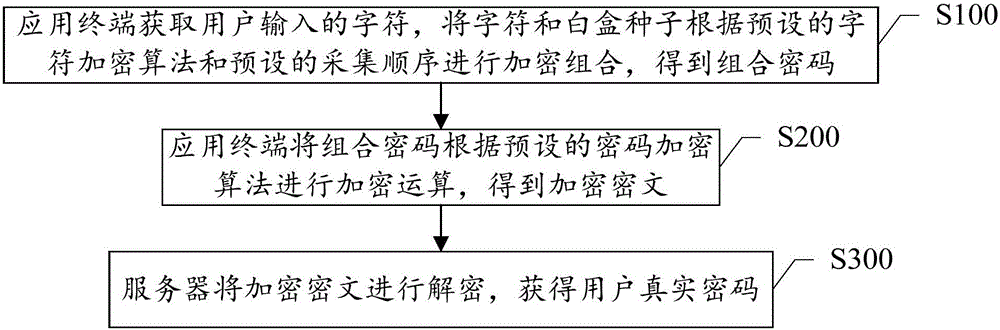
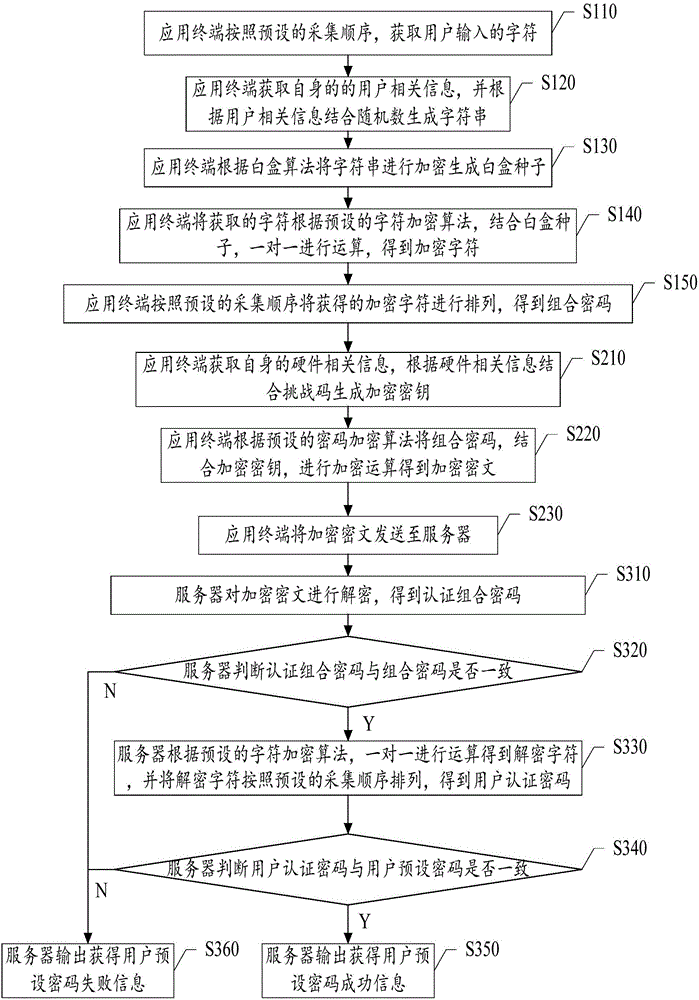
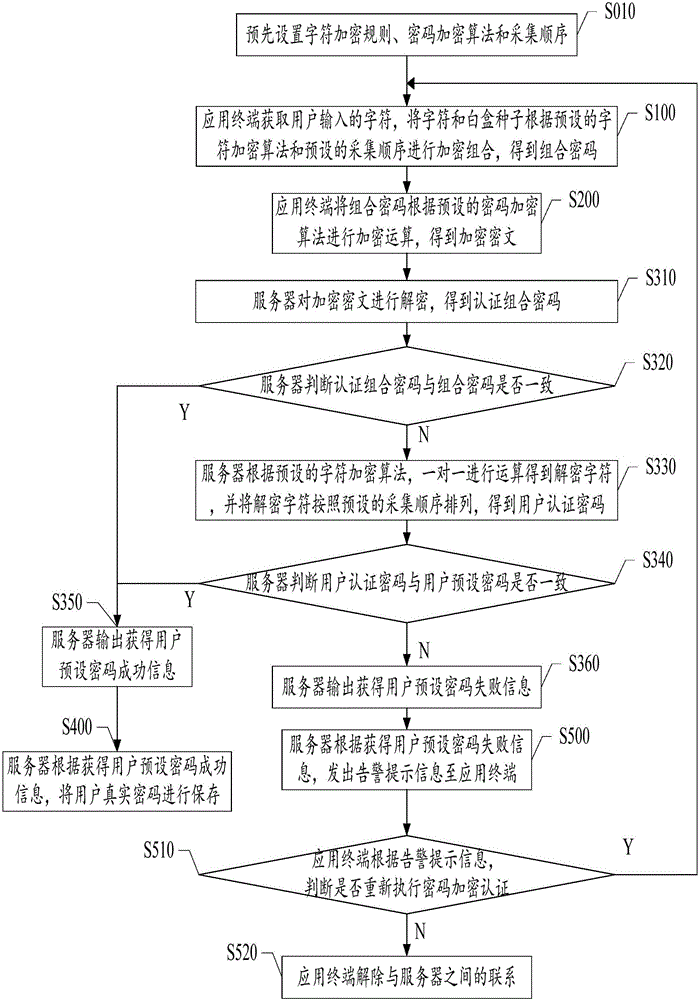
The invention discloses an encryption method and system based on a white box. The method comprises the following steps: S100, an application terminal acquires characters input by a user, and implements encryption combination on the characters and white box seeds in accordance with a preset character encryption algorithm and a preset acquisition sequence to obtain a combined password; S200, the application terminal implements encryption operation on the combined password according to a preset password encryption algorithm to obtain an encrypted ciphertext; and S300, a server decrypts the encrypted ciphertext to obtain a user default password. According to the encryption method and system disclosed by the invention, the characters input by the user can be obtained by clicking or touching a software simulation keyboard through a mouse, a white box cryptography is applied to a password keyboard of the application terminal to enable that the characters input by the user are firstly separately encrypted and then integrally encrypted, so that the way of obtaining the password through brute force can be better prevented.
Owner:SHANGHAI PEOPLENET SECURITY TECH
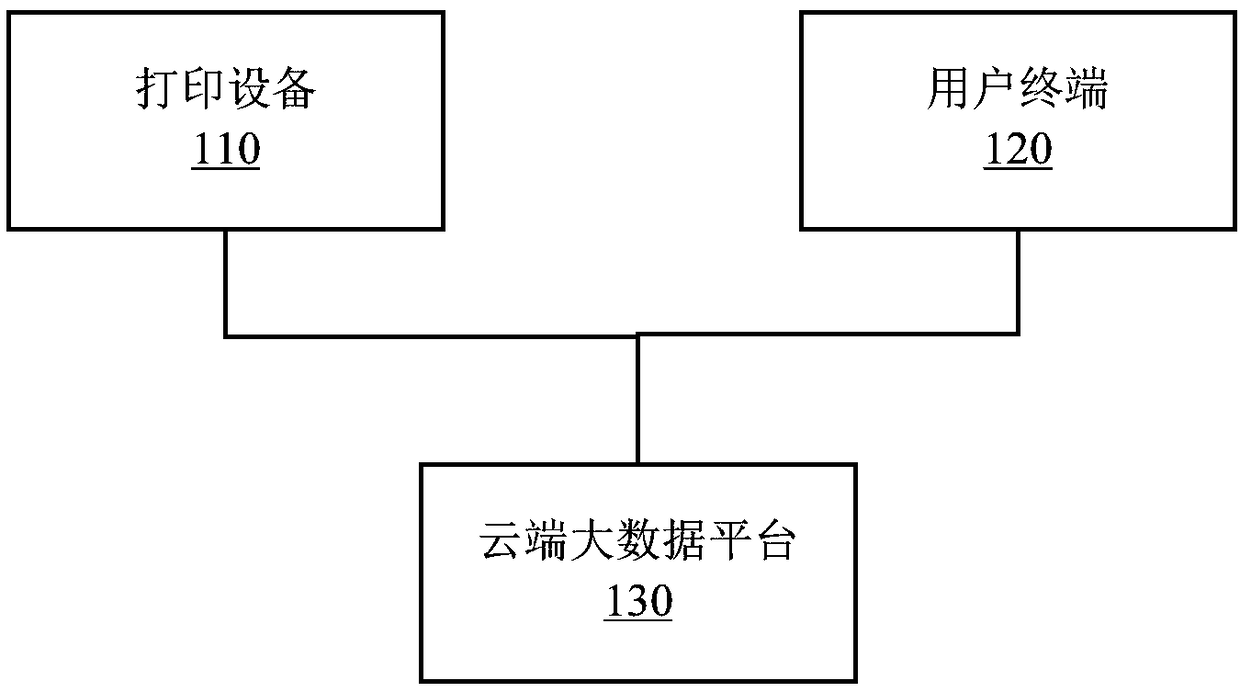
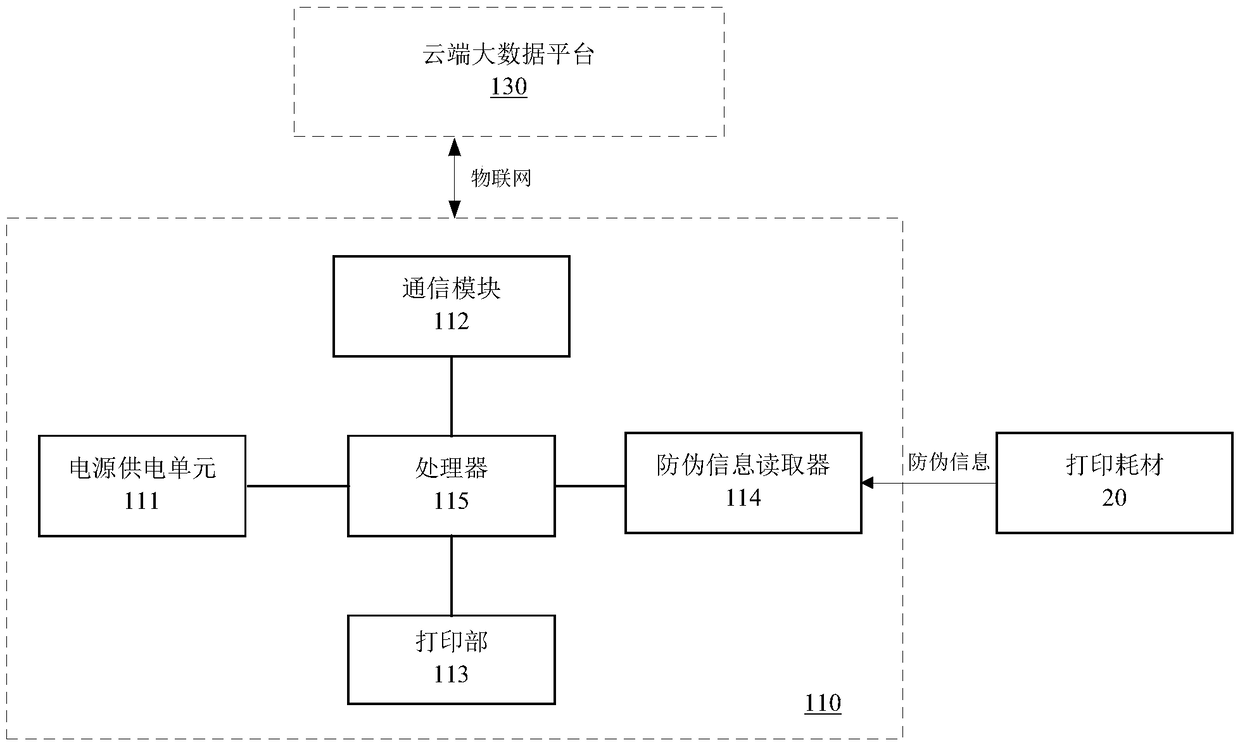
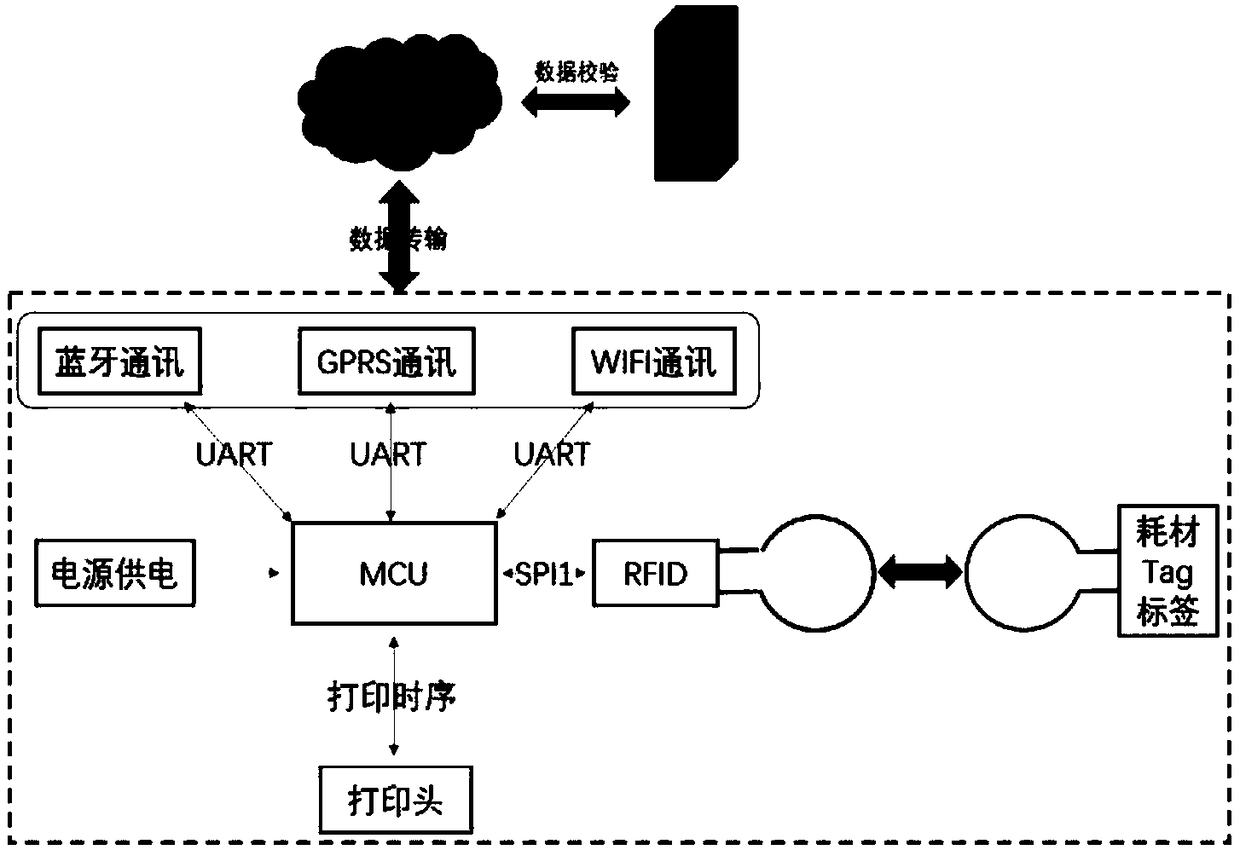
A printing system
PendingCN109298843AEffectively maintain interestsAvoid damageCo-operative working arrangementsDigital output to print unitsComputer moduleInformation transfer
The invention discloses a printing system, wherein the printing device comprises: an anti-counterfeit information reader which reads the anti-counterfeit information of printing consumables; The processor performs preliminary verification on the anti-counterfeit information read by the anti-counterfeit information reader and sends a printing instruction after the secondary verification passes; Thecommunication module transmits the anti-counterfeit information to the cloud end big data platform for completing the secondary check after the initial check passes, and receives the print data sentby the user terminal after the secondary check passes; A printing unit that receives a printing instruction transmitted from the processor and prints print data transmitted from the user terminal. Theinvention can prevent the user from carrying out consumption material anti-counterfeit cracking by simply changing the mechanical structure, and can also prevent the RFID electronic tag from being cracked by cracking means such as using default password attack, authentication vulnerability attack and violent attack so as to forge the corresponding anti-counterfeit tag to realize continuous printing.
Owner:ZHUHAI QUIN TECH CO LTD
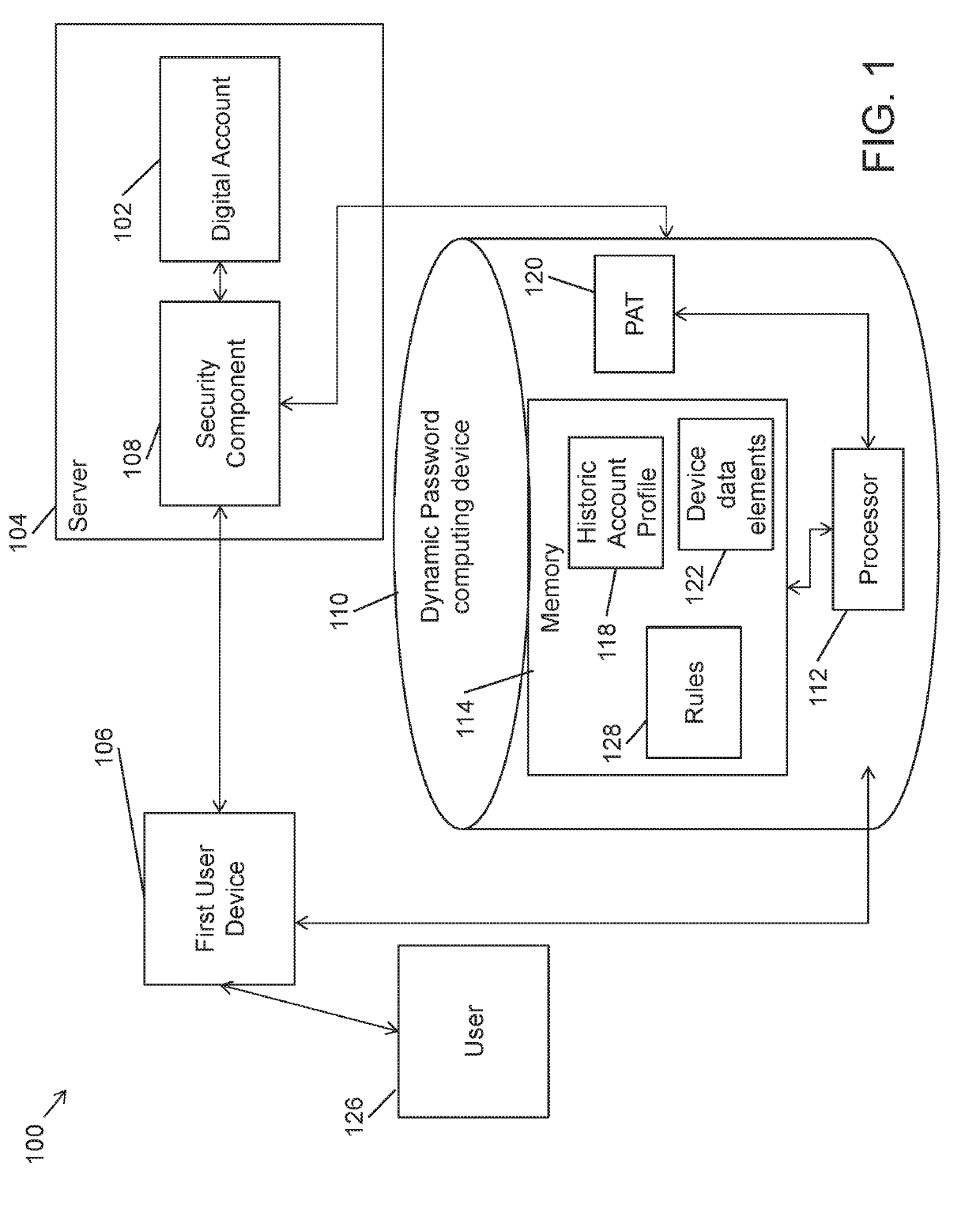
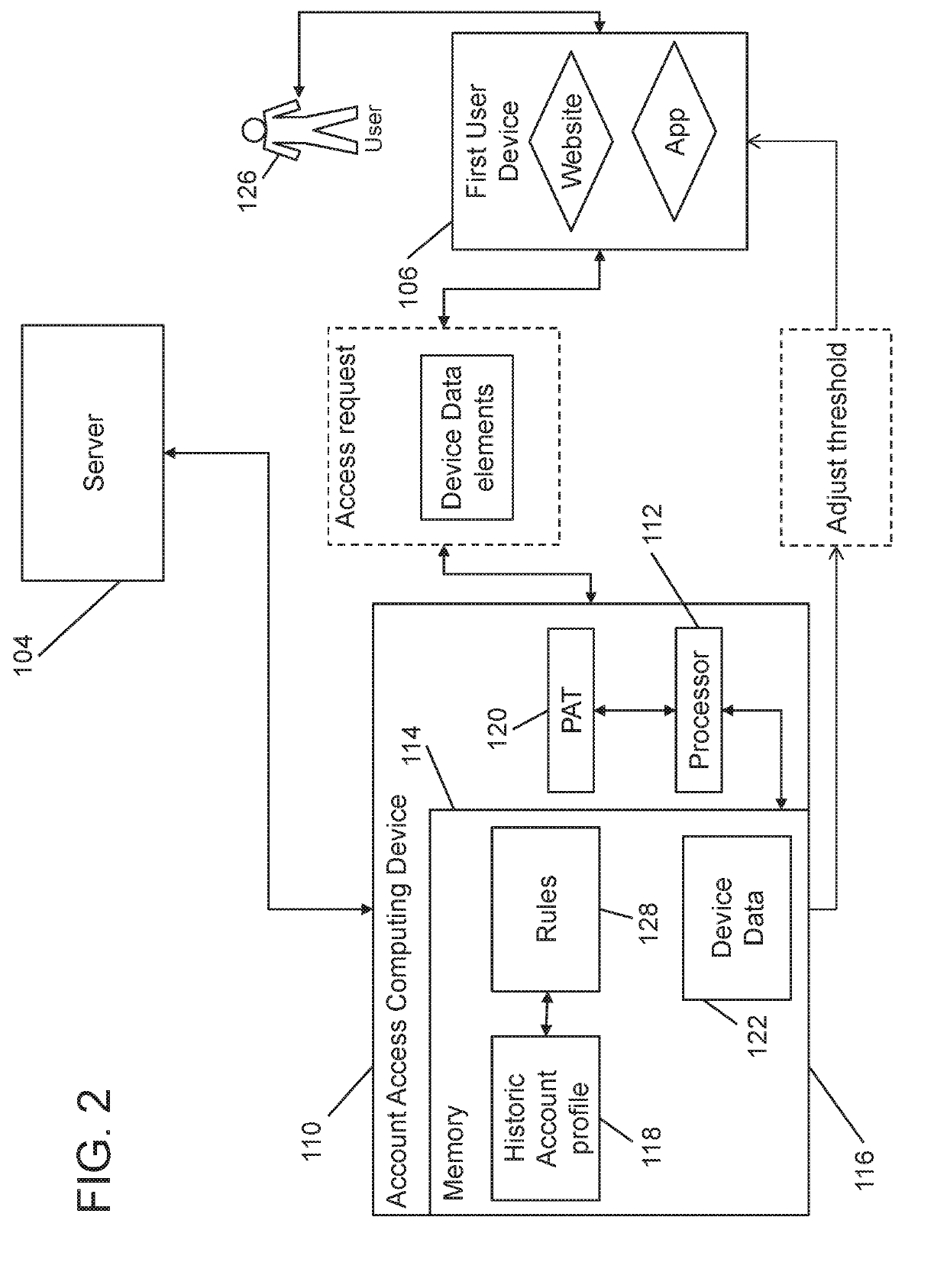
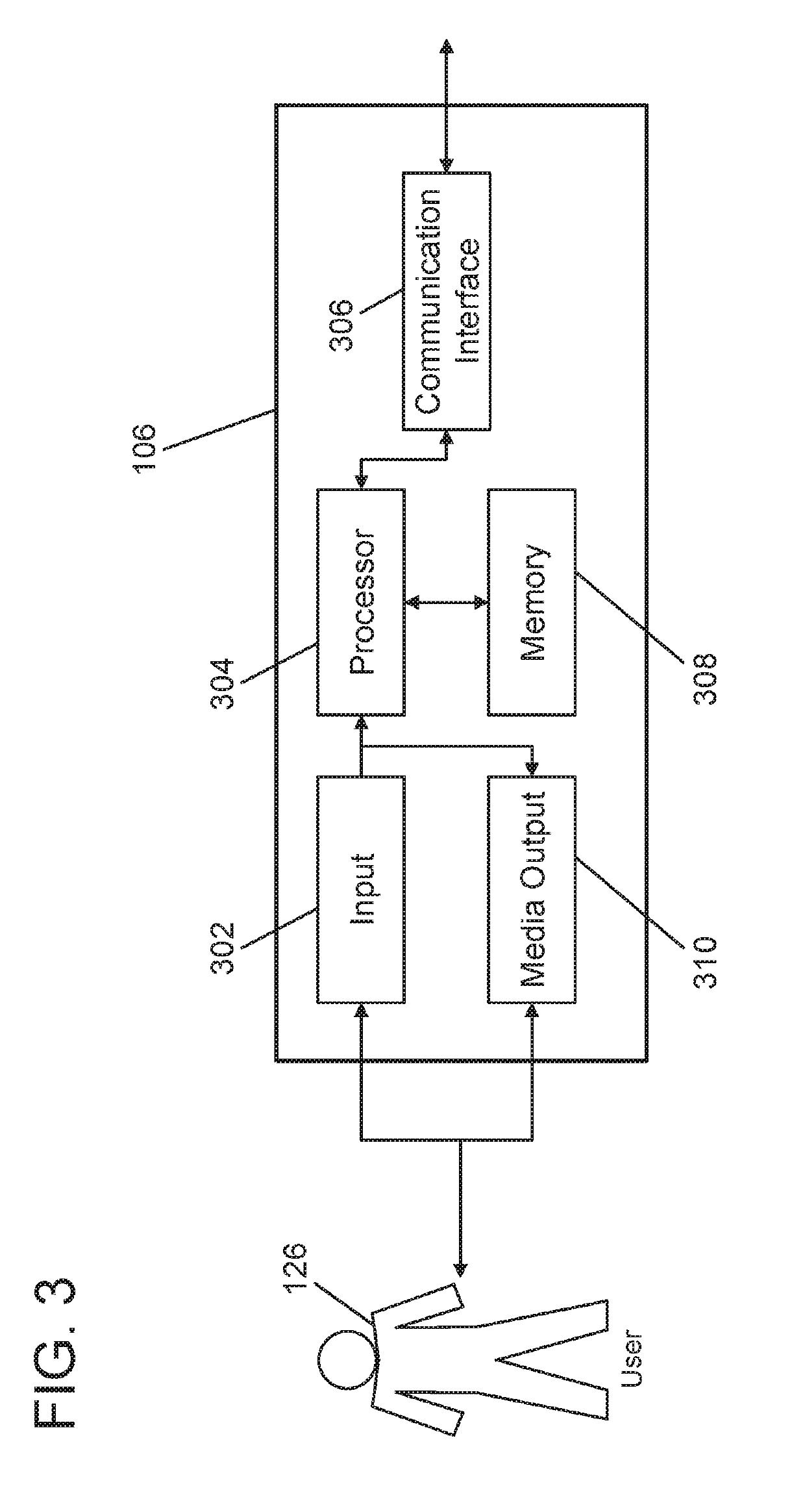
Systems and methods for dynamically adjusting a password attempt threshold
A system for dynamically adjusting a default password attempt threshold is provided. The system includes a server for storing the digital account, and a dynamic password computing device for controlling access to the server. The dynamic password computing device is configured to receive an access request from a user using a first user device for accessing the digital account wherein the access request includes first user device data elements and an account ID, retrieve a historical account profile of the user that includes user device data elements for one or more user devices used by the user to access the digital account, compare the first user device elements from the access request to the historical account profile of the user, determine a likelihood that the user submitting the access request is a legitimate account holder, and adjust the default password attempt threshold stored within the memory based on the determination.
Owner:MASTERCARD INT INC
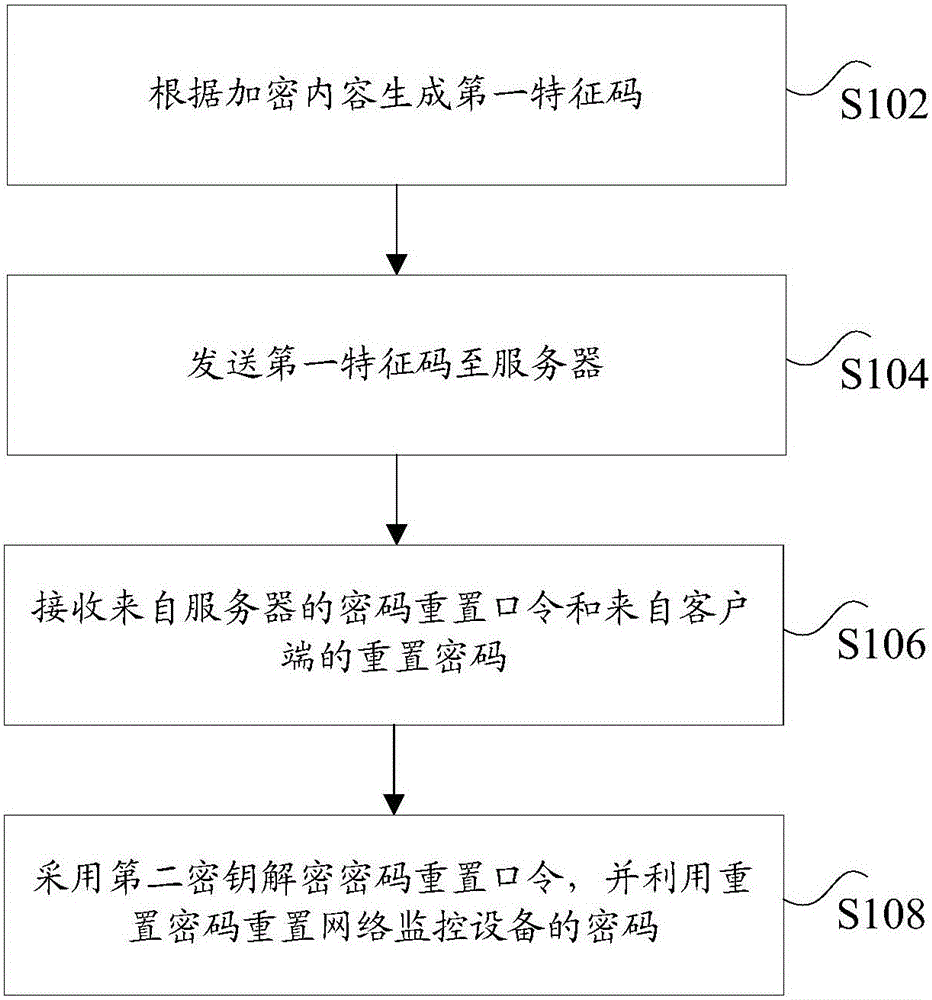
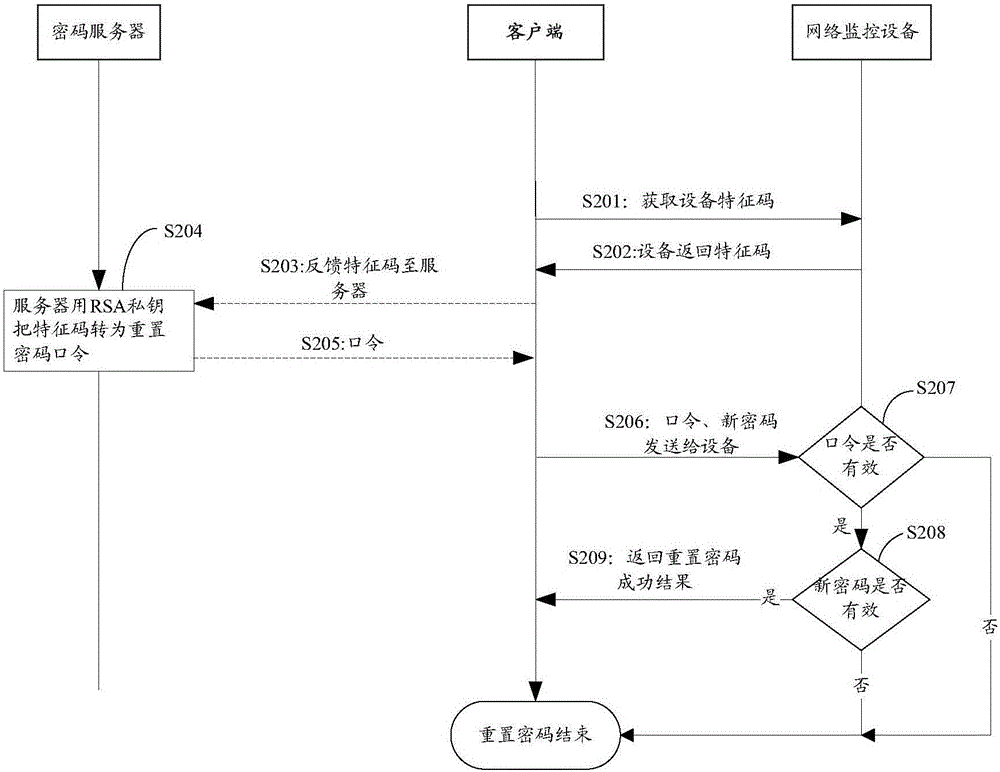
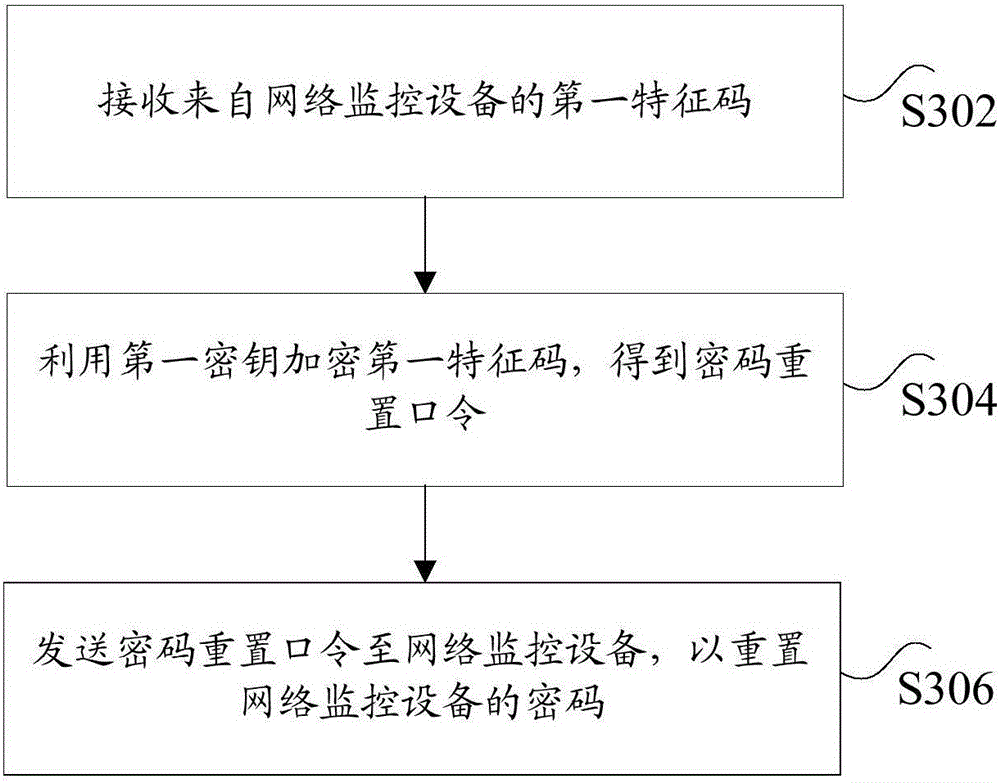
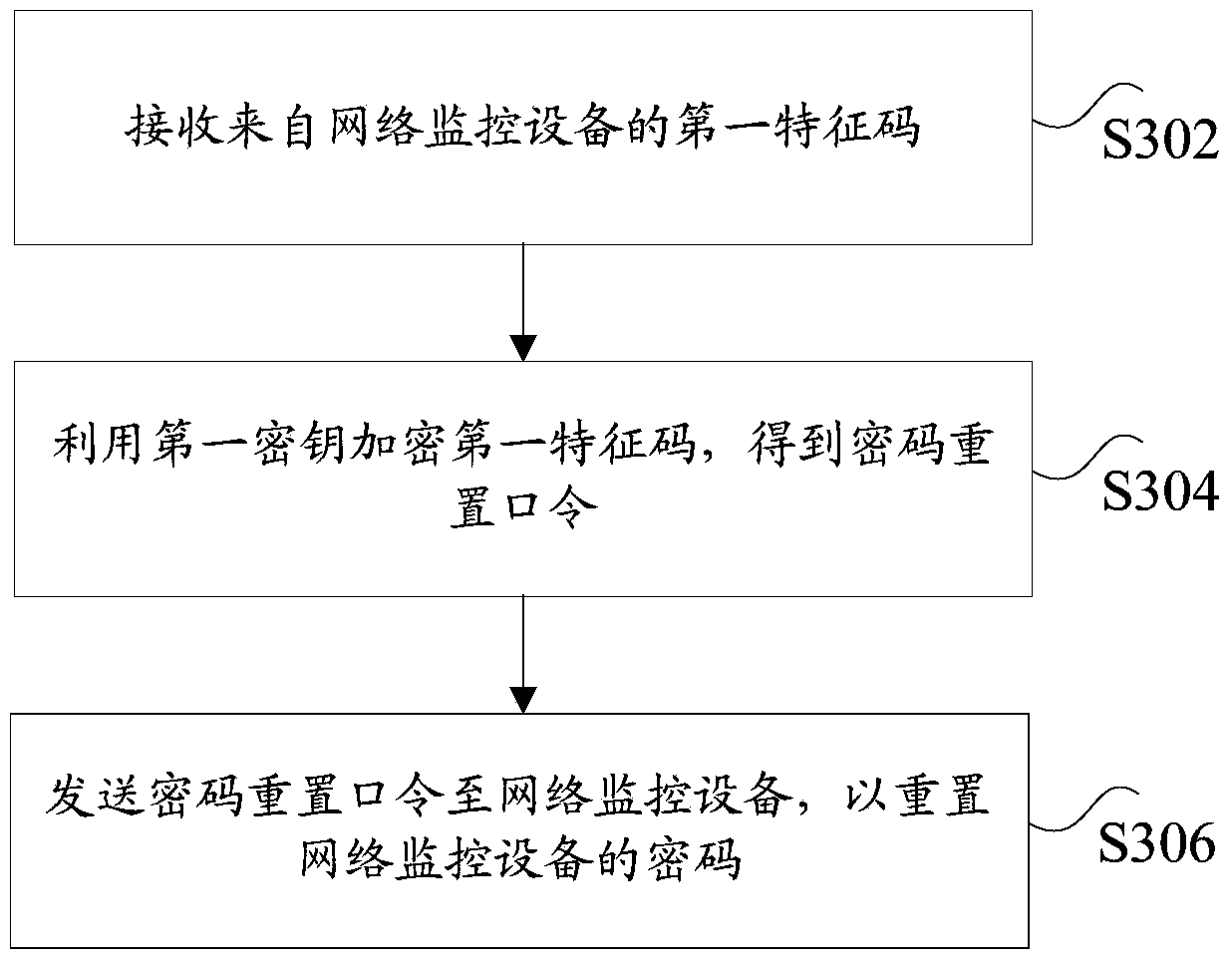
Method, device and system for resetting password of network monitoring equipment, server and network monitoring equipment
ActiveCN106302335AEnsure safetyImprove securityMultiple keys/algorithms usagePublic key for secure communicationMonitor equipmentClient-side
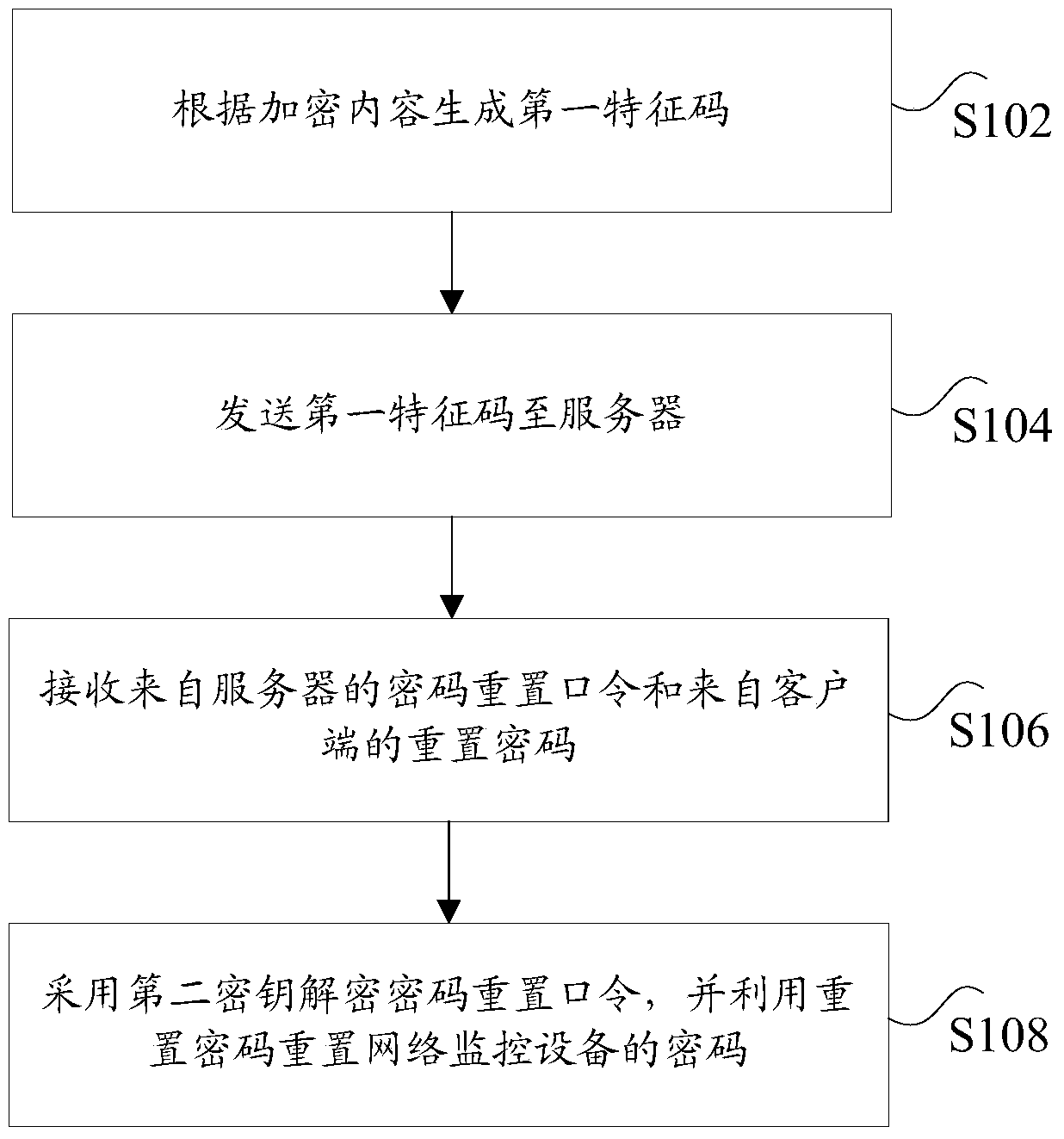
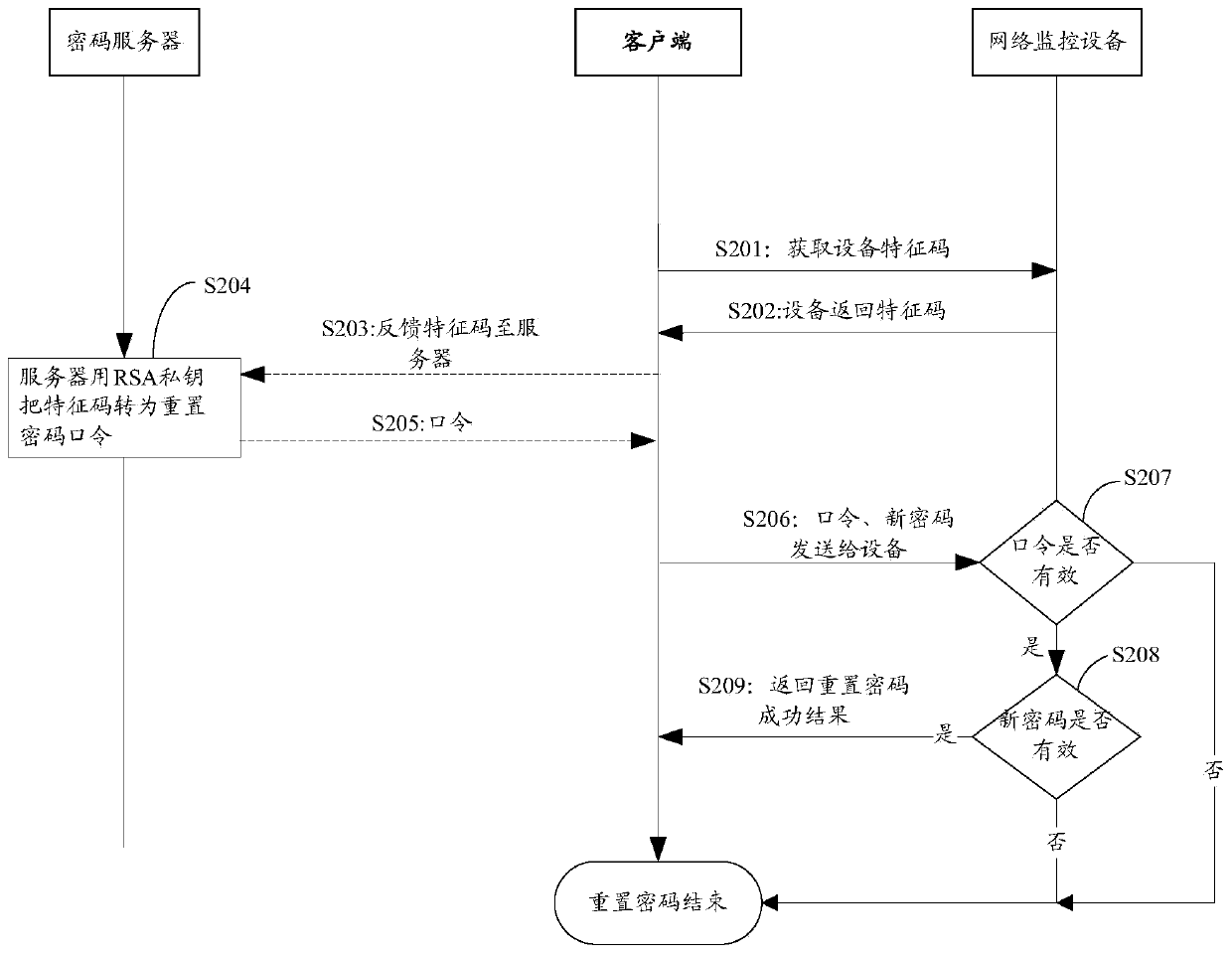
The invention discloses a method, device and system for resetting a password of network monitoring equipment, a server and network monitoring equipment. The method for resetting the password of the network monitoring equipment comprises the steps of: according to encrypted contents, generating a first feature code; sending the first feature code to the server; receiving a password resetting command from the server and a reset password from a client, wherein after the server receives the first feature code, the first feature code is encrypted by adopting a first secret key to obtain the password resetting command, and the password resetting command is returned; and decrypting the password resetting command by adopting a second secret key, and resetting the password of the network monitoring equipment by utilizing the reset password, wherein the first secret key and the second secret key are a pair of secret keys in an asymmetric cryptographic algorithm. By the method, device and system for resetting the password of the network monitoring equipment, the server and the network monitoring equipment which are disclosed by the invention, the problem of low security in the process of recovering a default password and resetting the password in the prior art is solved, so that an effect of improving security of the network monitoring equipment is achieved.
Owner:HANGZHOU HIKVISION DIGITAL TECH
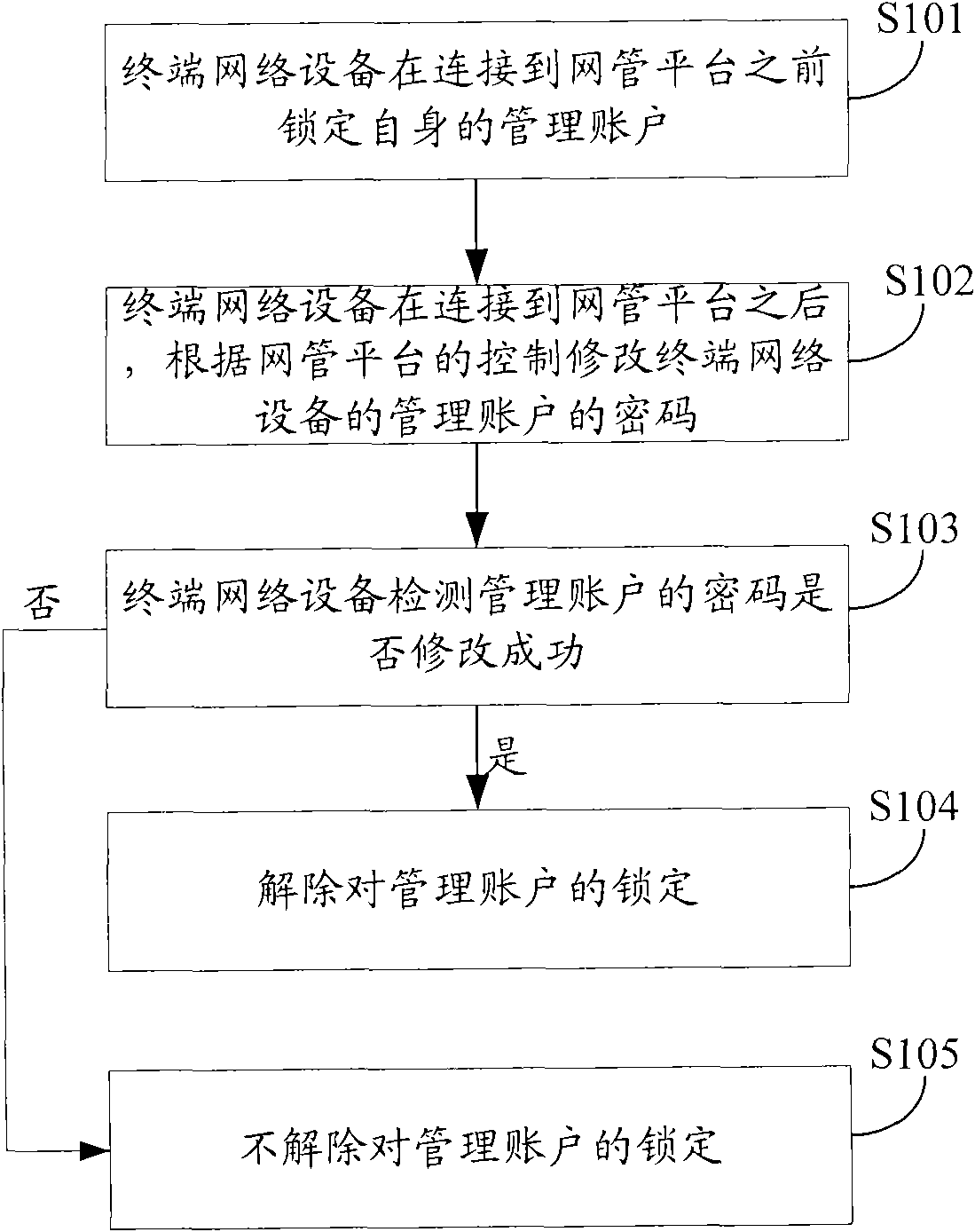
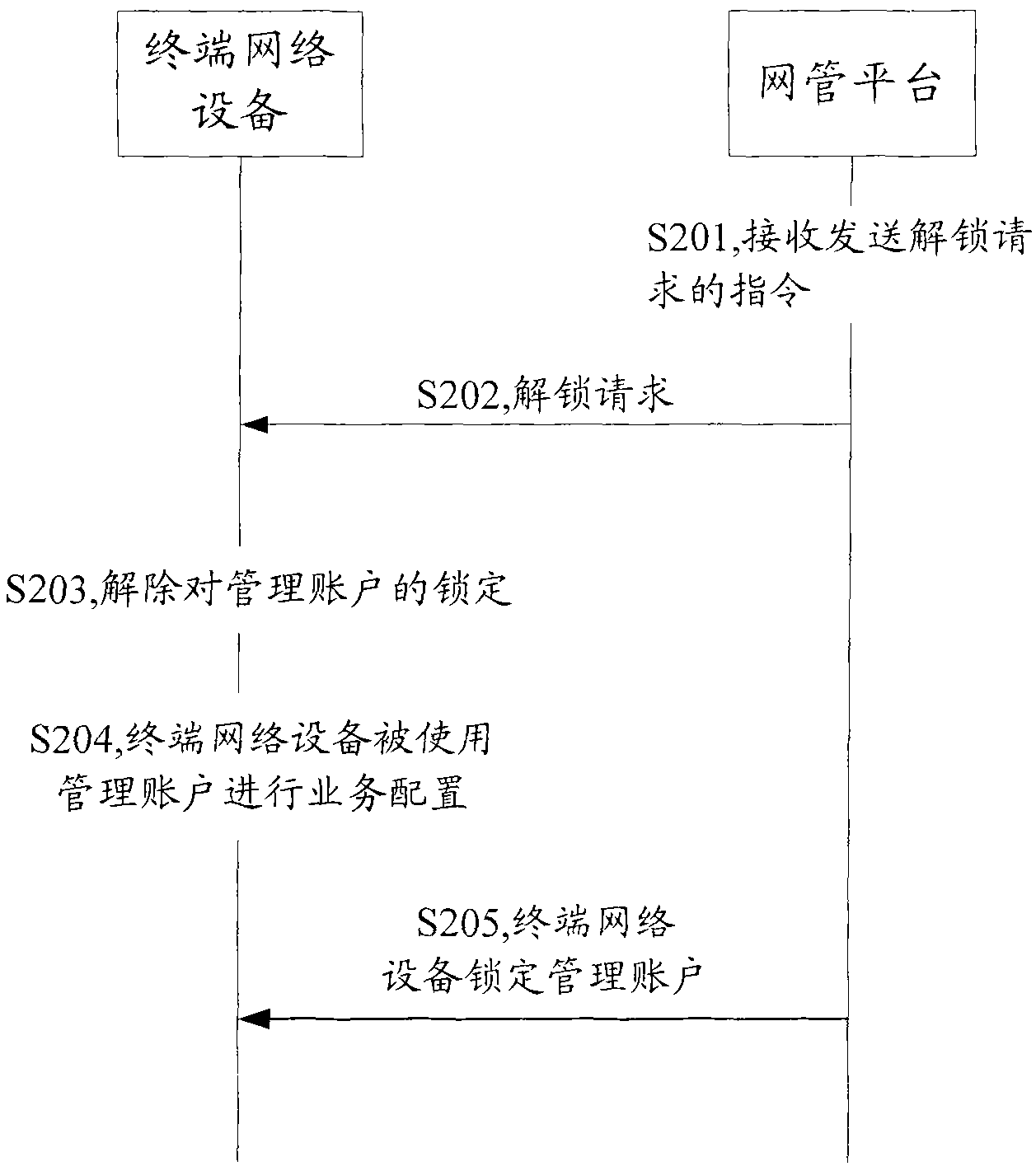
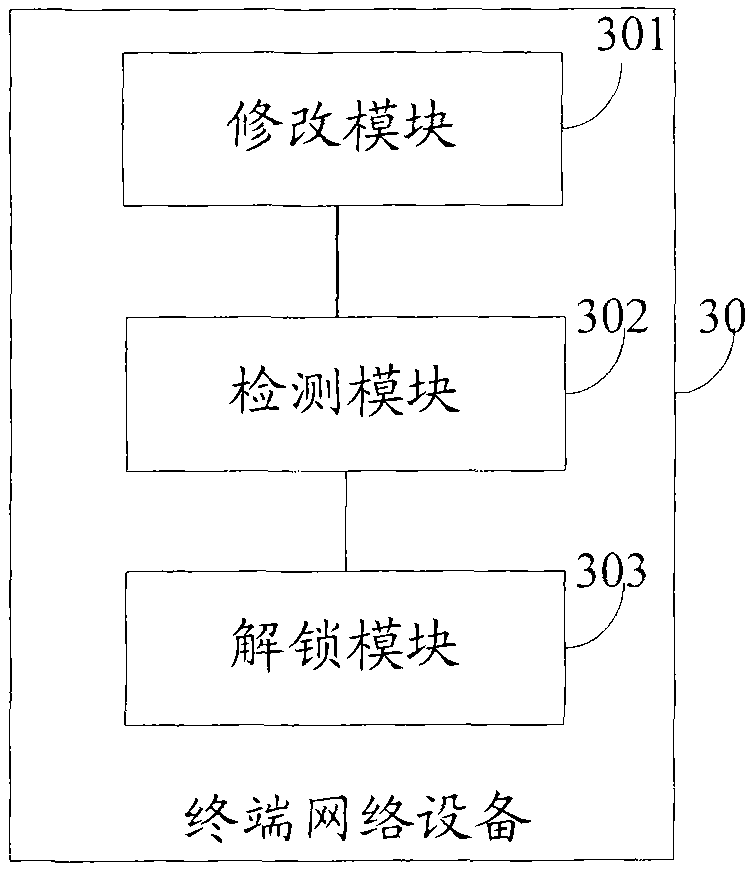
Terminal network device and method and system for controlling access to administrator account thereof
ActiveCN101783730AReduce distressReduce lossesUser identity/authority verificationData switching networksNetwork managementAccess control
The invention provides a terminal network device and a method and a system for controlling the access to the administrator account thereof, so as to solve the problems that the default password for the administrator account of the terminal network device is leak-prone in the prior art, thereby causing the undue use of the administrator account and influencing the normal operation of the terminal network device. The method comprises the following steps: changing the password for the administrator account of the terminal network device on the basis of the control of a network management platform after the terminal network device is connected to the network management platform; and unlocking the administrator account which is locked before the terminal network device is connected to the network management platform when detecting that the password for the administrator account is successfully changed. The technical scheme of the invention can greatly reduce the possibility that the administrator account is accessed freely by a user having only the general authority and further reduce the troubles and damage to the operation of the terminal network device.
Owner:HUAWEI DEVICE (SHENZHEN) CO LTD
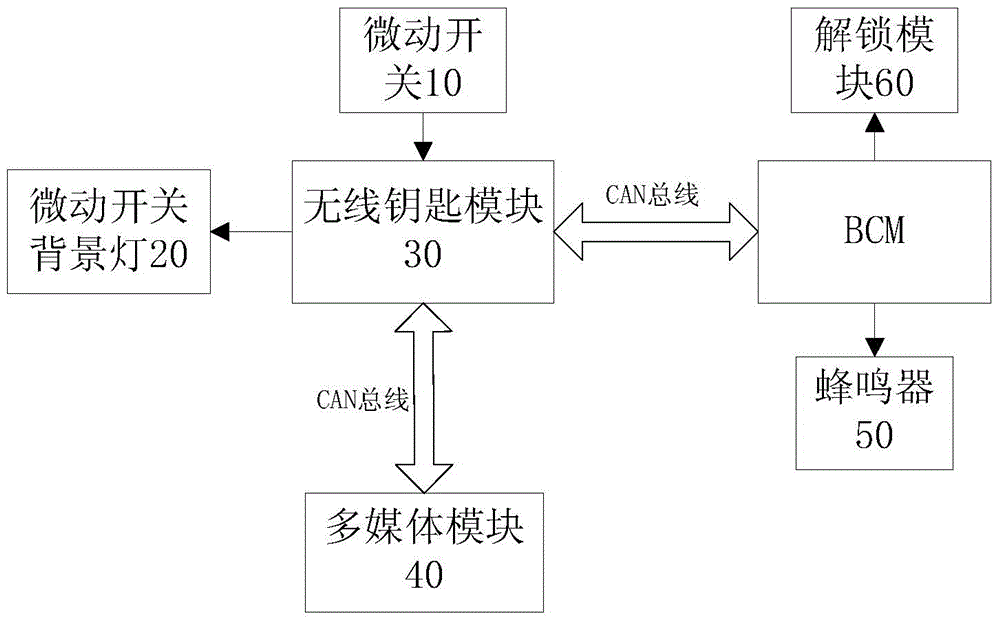
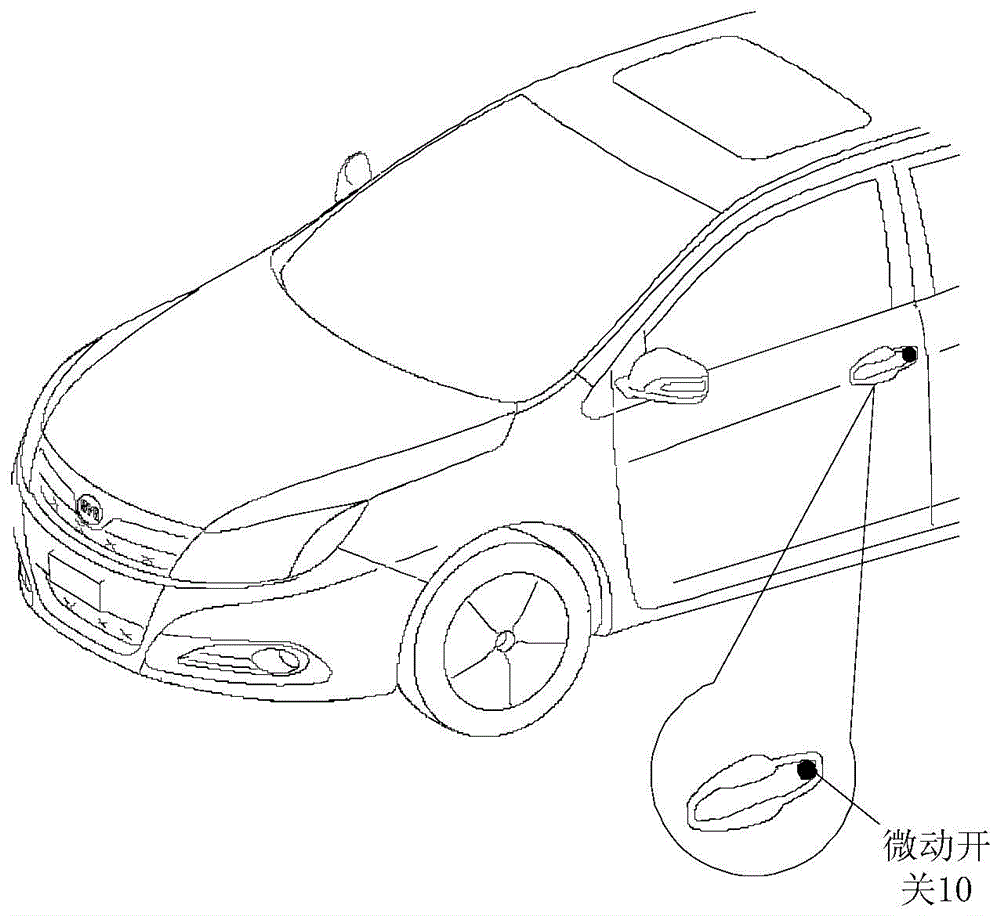
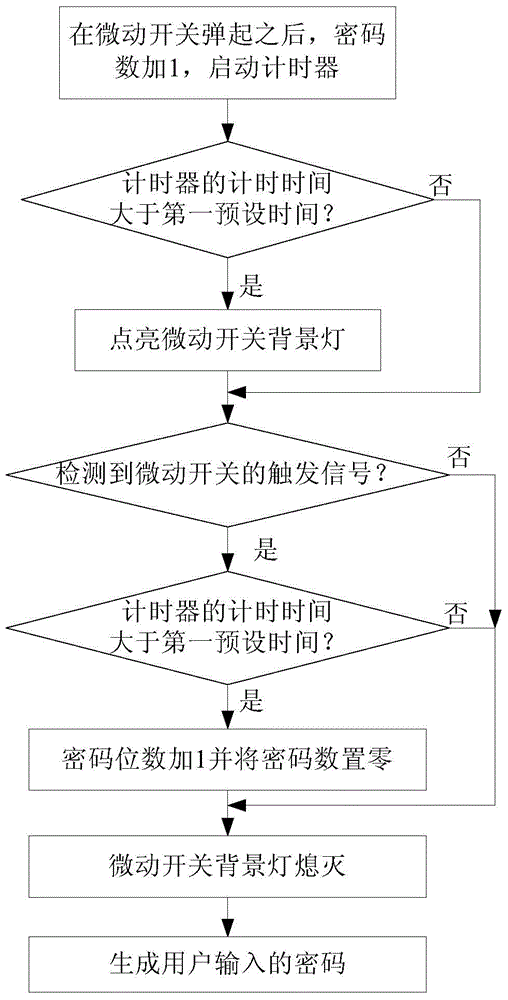
Automobile, wireless key system thereof and control method of wireless key system
The invention discloses a wireless key system of an automobile. The system comprises a microswitch, a microswitch background lamp, a body control module BCM and a wireless key module. The microswitch is arranged on an automobile body and used for producing trigger signals according to trigger of a user. The wireless key module is used for detecting trigger signals produced by the microswitch, controlling the microswitch background lamp according to the trigger signals so that the microswitch background lamp gives an input prompt to the user, generating a password input by the user according to the trigger signals produced by the microswitch, and carrying out unlocking through the BCM when the password input by the user coincides with a default password. By means of the wireless key system, the user can unlock, start and lock the automobile when having no entity key, and great convenience is brought to the user. The invention further discloses the automobile and a control method of the wireless key system of the automobile.
Owner:BYD CO LTD
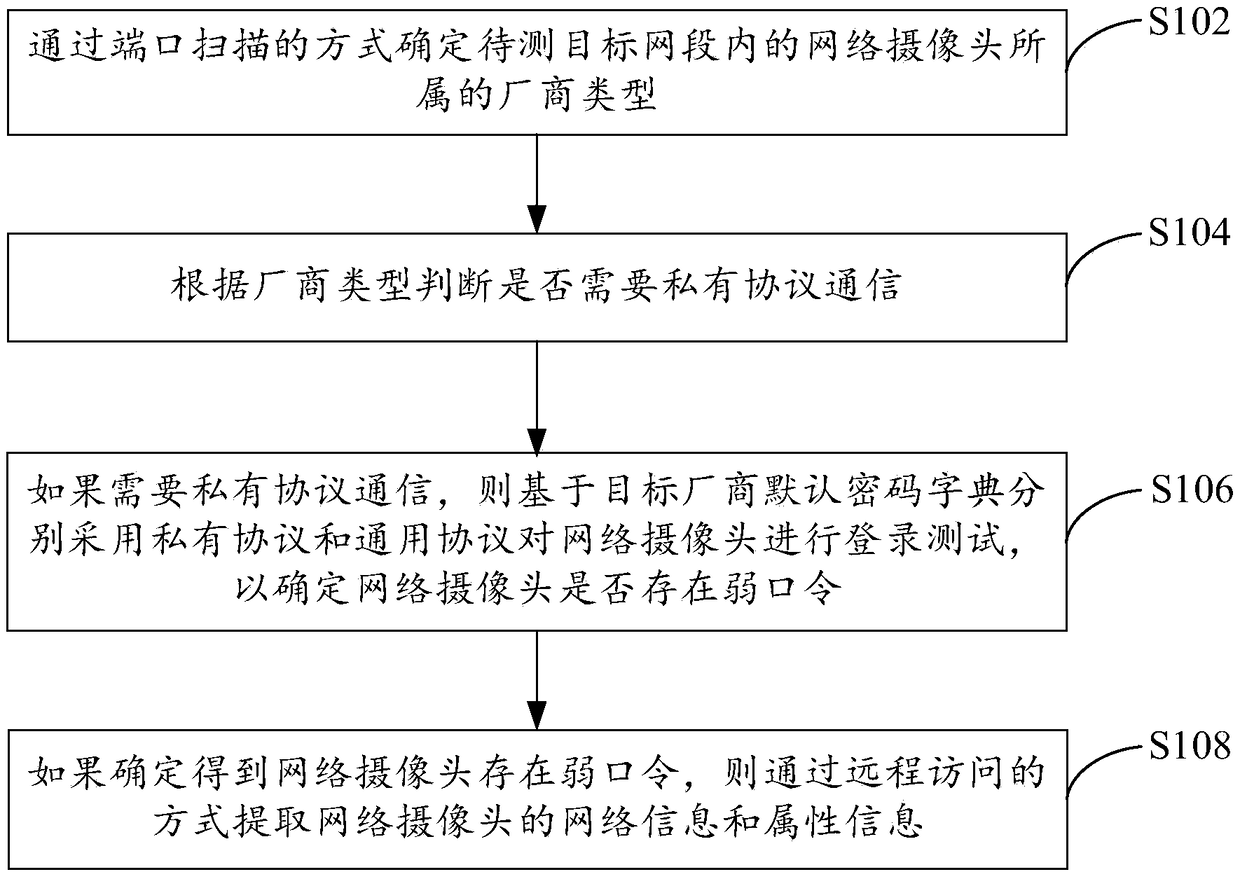
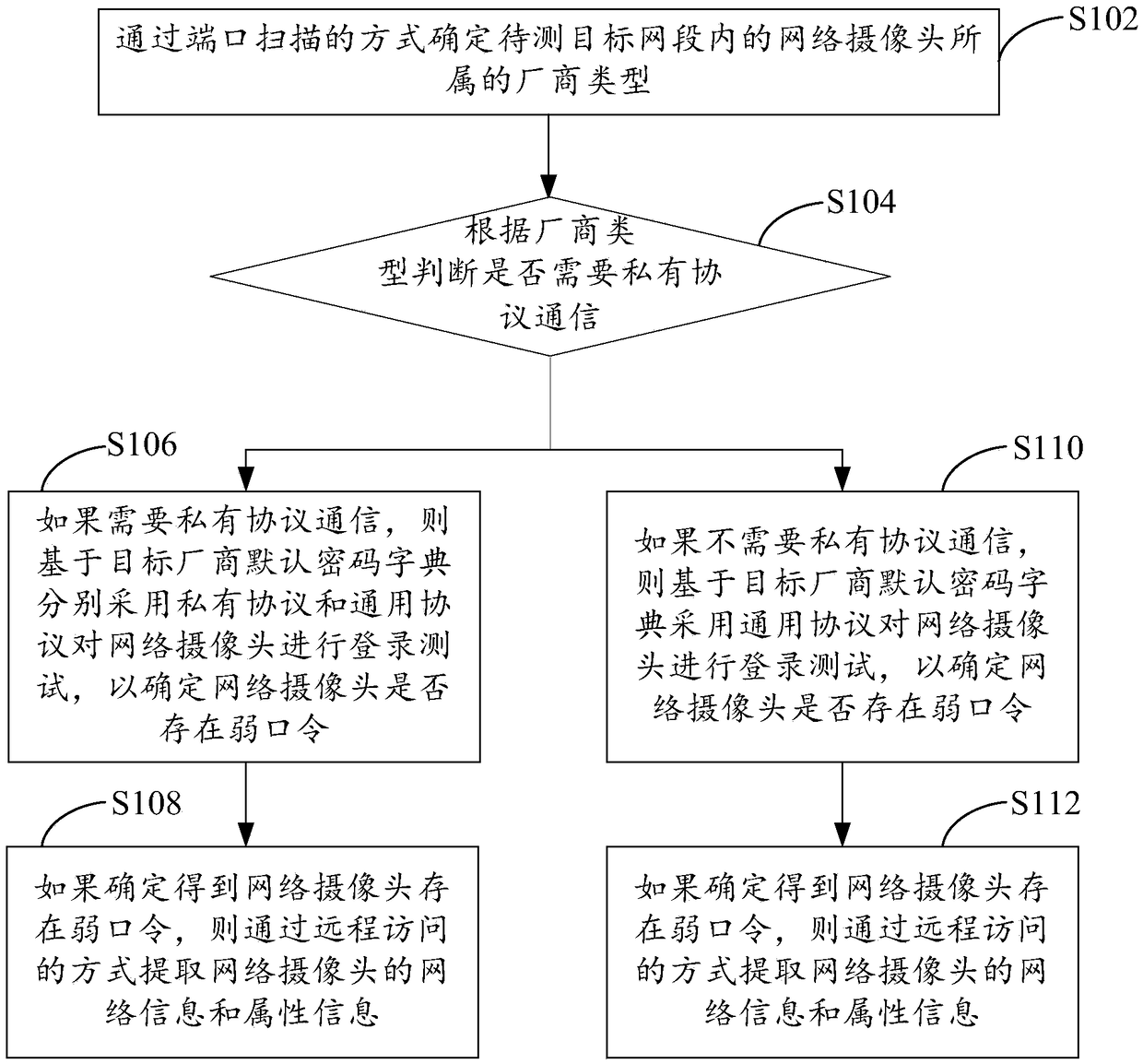
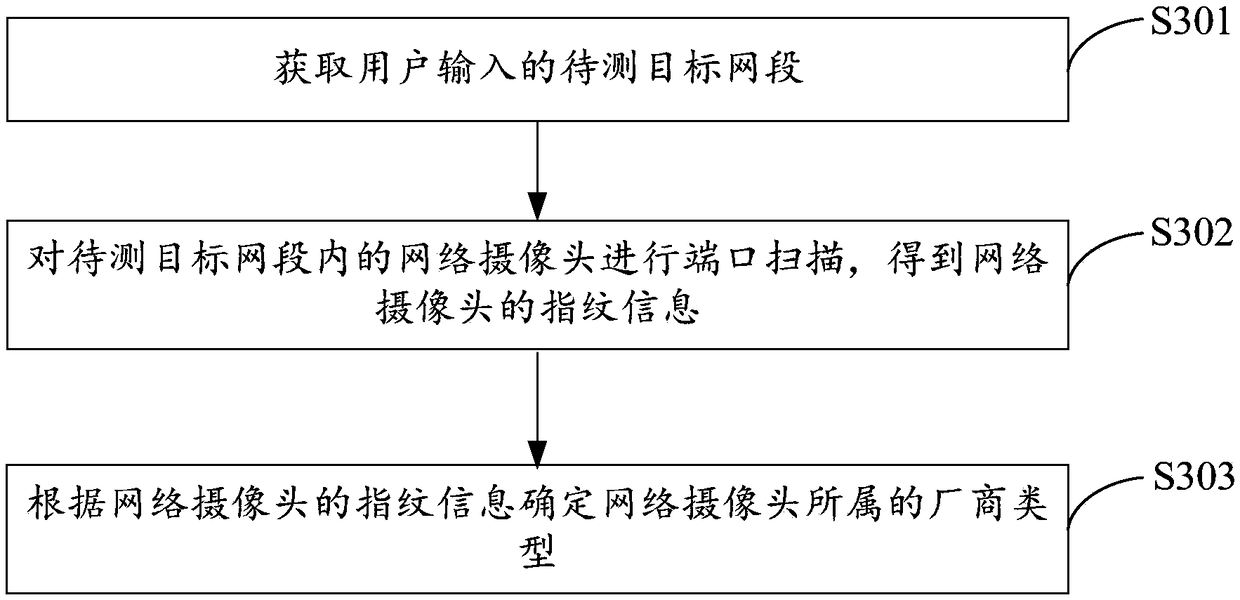
Webcam weak password detecting method and system
ActiveCN108833447AQuick checkAccurate detectionDigital data authenticationData switching networksNetwork segmentDefault password
The invention provides a webcam weak password detecting method and system. The method comprises determining the manufacturer type of a webcam in a target network segment to be tested by using a port scanning mode; determining whether private protocol communication is required according to the manufacturer type; if so, performing login tests on the webcam by using a private protocol and a general protocol separately based on the default password dictionary of a target manufacturer in order to determine whether the webcam has a weak password; and if it is determined that the webcam has a weak password, extracting the network information and the attribute information of the webcam. The method is compatible with the manufacturer's private protocol and the general protocol, automatically completes a detection process by a program, improves detection efficiency, achieves good intellectualization degree, can quickly, accurately and reliably detect whether the webcam has a weak password, and solves the technical problem that an existing webcam weak password detecting method is low in efficiency, poor in intellectualization, and poor in detection effect.
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
Method and password verifying device for verifying an input password, and computer system including the password verifying device
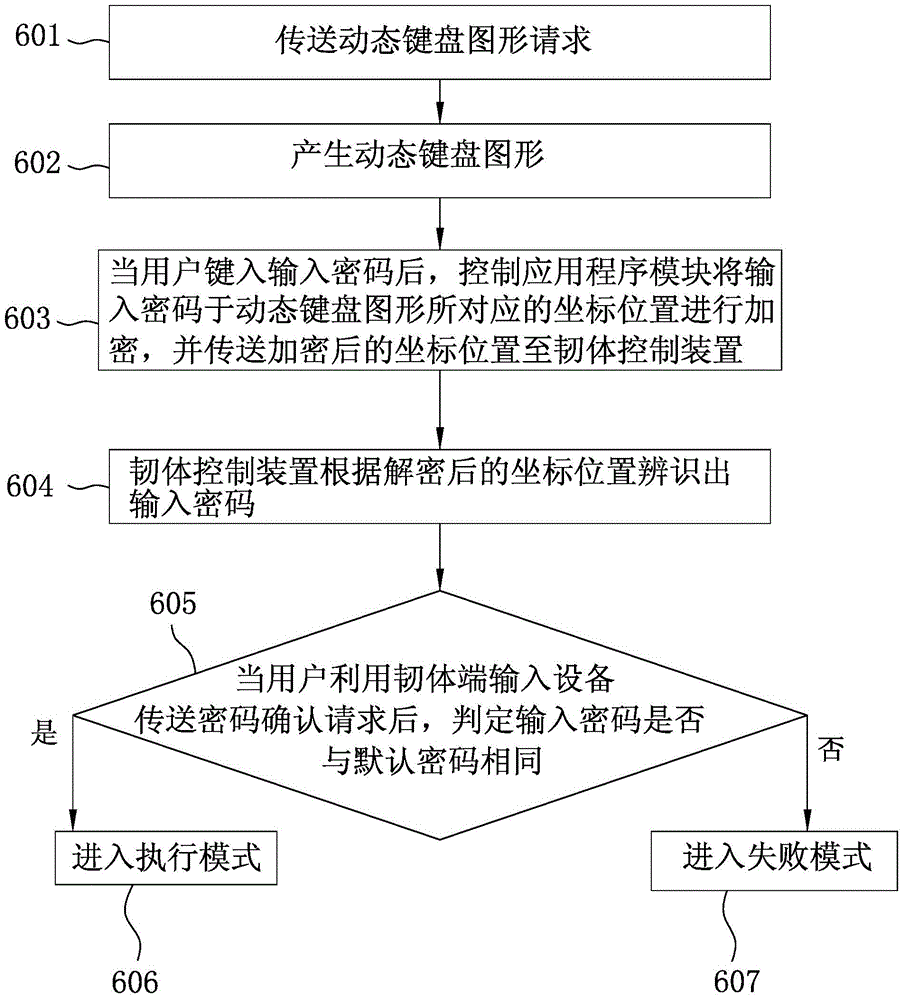
InactiveCN104978512AAvoid Malicious OperationsInternal/peripheral component protectionDigital data authenticationGraphicsSecret code
In a method for verifying an input password, a password verifying device coupled between a electronic device and an input device is configured to: in response to a password input request (601) from the electronic device, generating image data associated with a virtual keyboard and transmitting the image data to the electronic device; in response to password data from the electronic device, composing (604) an input password according to the password data; and in response to a password confirm request from the input device (4), comparing (606) the input password and a preset password stored therein.
Owner:周宏建
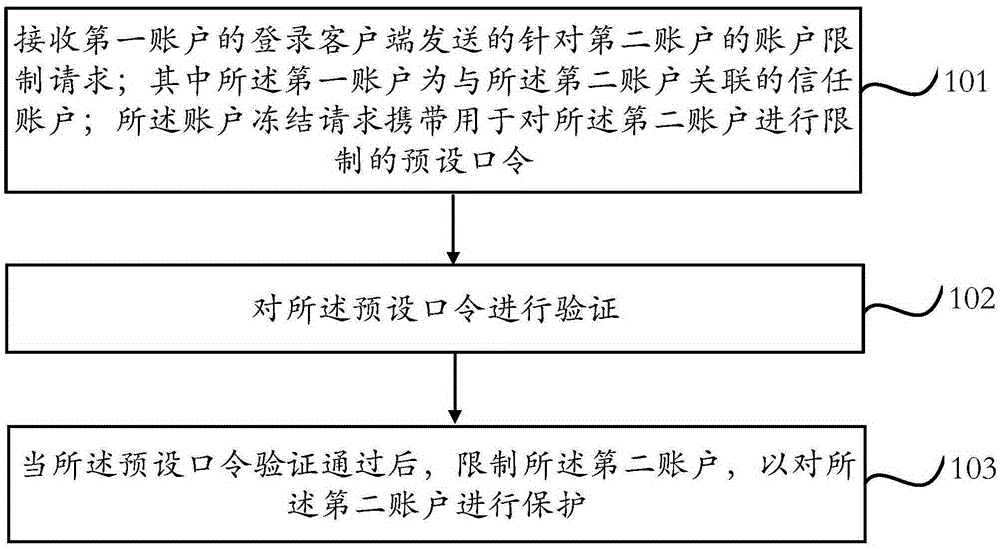
Account protection method and device
The invention provides an account protection method. The method comprises the steps that an account restriction request which is sent by the login client of a first account for a second account is received, wherein the first account is a trust account associated with the second account; the account restriction request carries a default password for restricting the second account; the default password is verified; after the default password is verified, the second account is restricted to protect the second account. According to the invention, when the account of a user is abnormal, the current account can be quickly restricted by the trust account of the third party; and the security of the account can be enhanced.
Owner:ADVANCED NEW TECH CO LTD
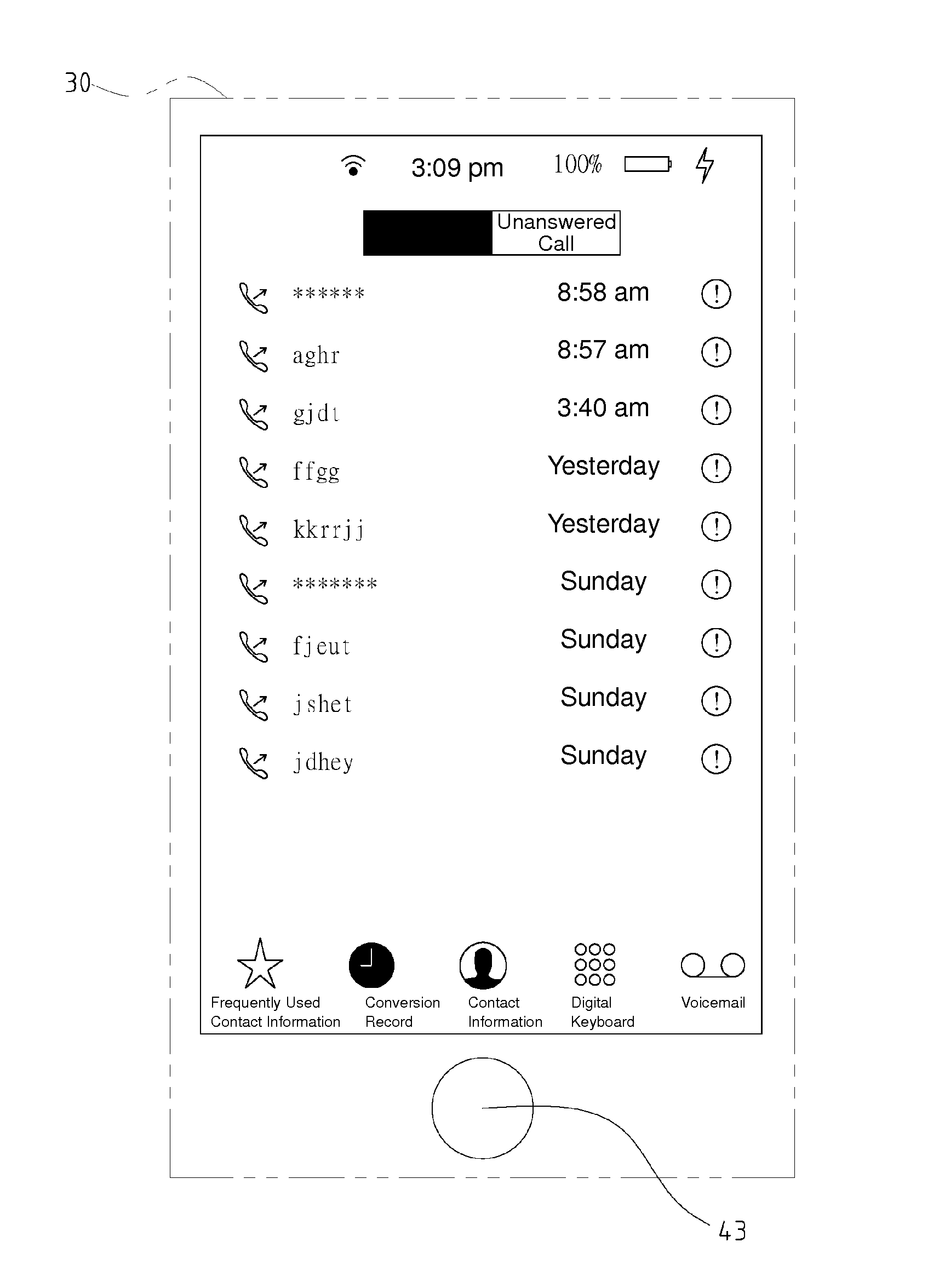
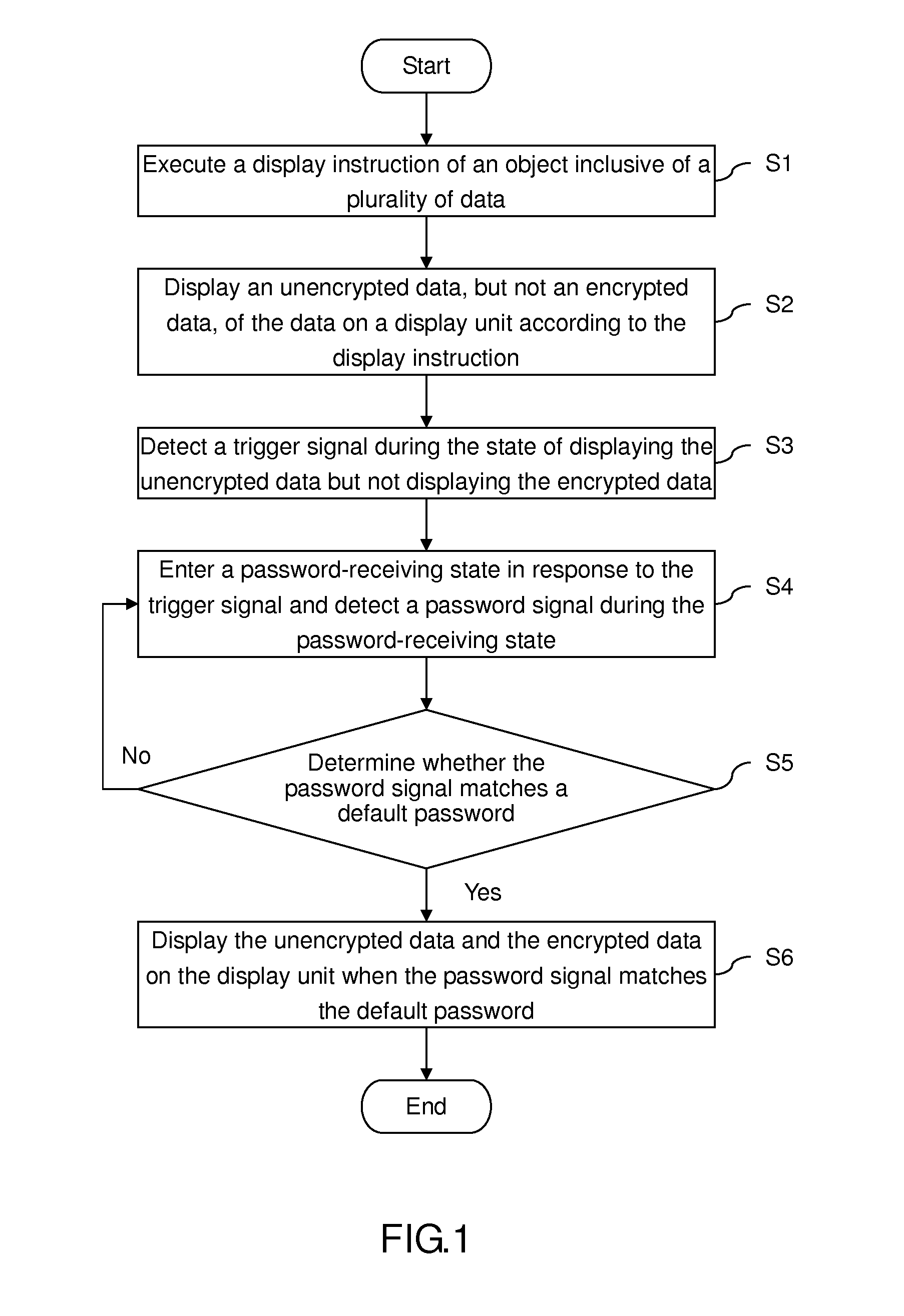
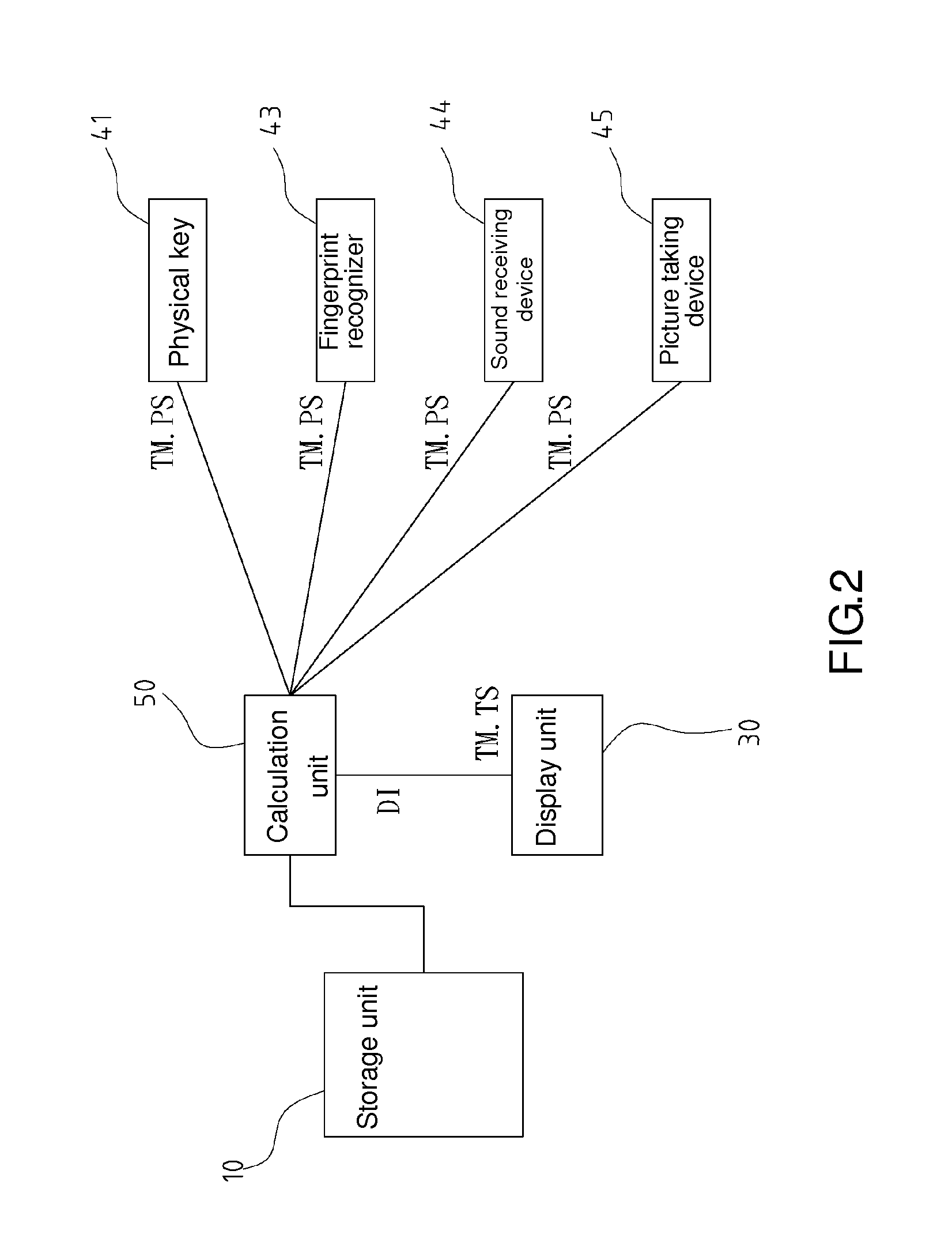
Decryption method for use in displaying data
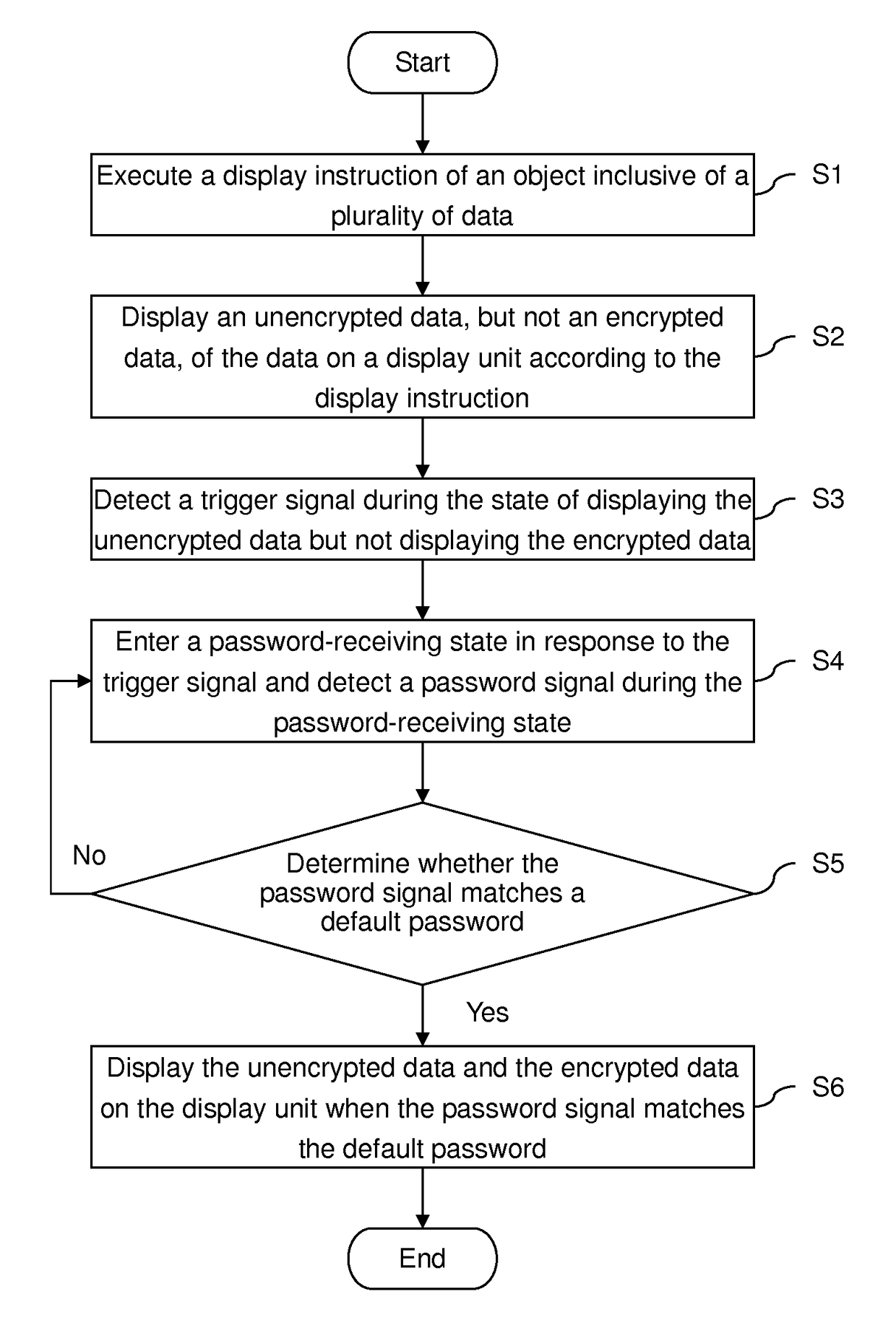
ActiveUS20160314304A1Prevent steppingImprove confidentialityDigital data protectionComputer hardwareDefault password
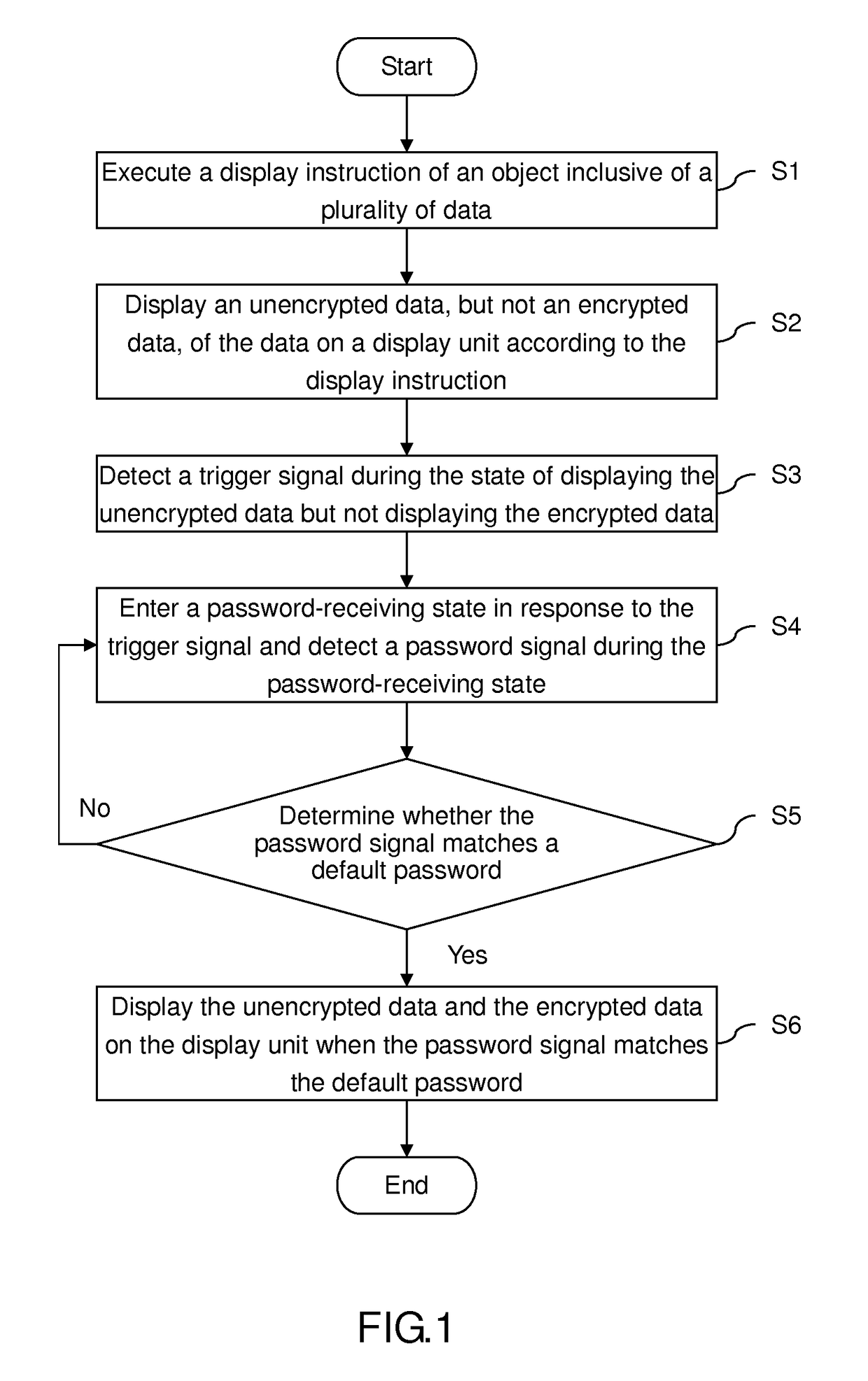
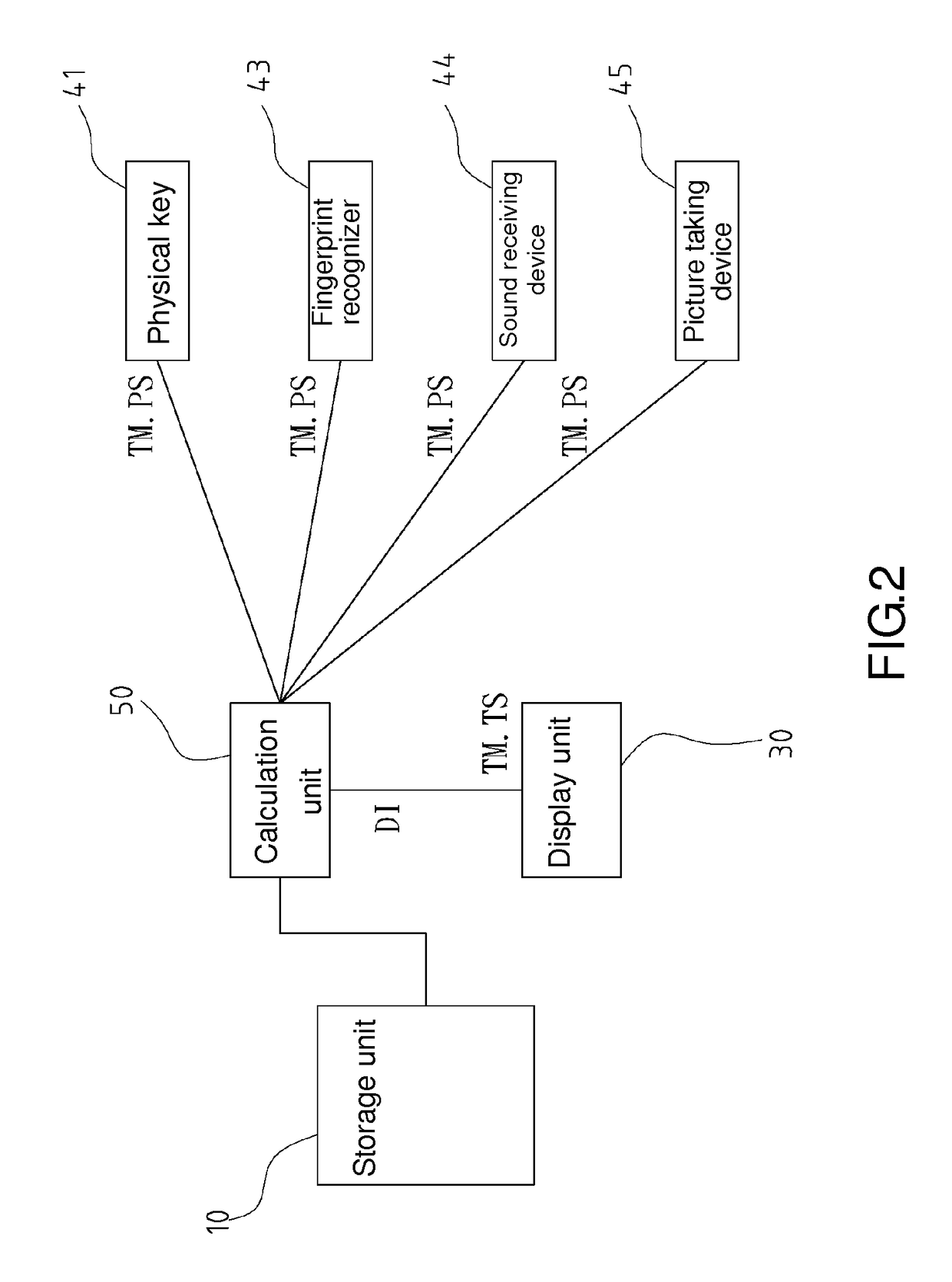
A decryption method for use in displaying data includes the steps of executing a display instruction of an object inclusive of a plurality of data, displaying an unencrypted data, but not an encrypted data, of the data on a display unit according to the display instruction, detecting a trigger signal during the state of displaying the unencrypted data but not displaying the encrypted data, entering a password-receiving state in response to the trigger signal and detecting a password signal during the password-receiving state, determining whether the password signal matches a default password, and displaying the unencrypted data and the encrypted data on the display unit when the password signal matches the default password. Therefore, with the decryption method, no person other than the object owner is aware of the encrypted data.
Owner:GETAC TECH CORP
Bluetooth-control-based intelligent lock system
InactiveCN104103108ARealize encrypted unlockingRealize closed controlIndividual entry/exit registersBluetoothData transmission
The invention discloses a bluetooth-control-based intelligent lock system including a bluetooth intelligent mobile terminal for a user to input a default password, and a lock arranged on an application object, the lock comprises an unlocking device, a main control chip and a bluetooth receiving module; the bluetooth intelligent mobile terminal transfers default password data to the bluetooth receiving module by a wireless communication manner, the bluetooth receiving module can receive the default password data and transfers the default password data to the main control chip, the main control chip performs analysis, encryption processing and validation on the default password data, and controls the unlocking device for unlocking; through the effective combination of the bluetooth intelligent mobile terminal and the lock, encryption unlocking and closing control of the lock can be achieved by operation of the bluetooth intelligent mobile terminal, and the bluetooth-control-based intelligent lock system has the advantages of simple structure, low cost, high safety, strong function, and use convenience.
Owner:魏孔明
Password input authentication method and system
ActiveCN105447353AImplement two-factor authenticationReduced Chances of PrivacyDigital data authenticationValidation methodsUser input
The present invention relates to a password input authentication method and system. The method comprises: according to a set password, for a set key in the password, presetting a pressure authentication value used for password authentication; when a user inputs a password, acquiring default password information in a default way and detecting a pressure detection value pressed on the set key; and performing password authentication according to the default password information, and the pressure authentication value and the pressure detection value that are corresponding to the set key. According to the technical scheme provided by the present invention, dual authentication is achieved, so that a bystander can only directly watch the default input way in the password input process and can not break the password of the user in spite of password leakage, thereby reducing probability of user privacy stealing and improving security.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
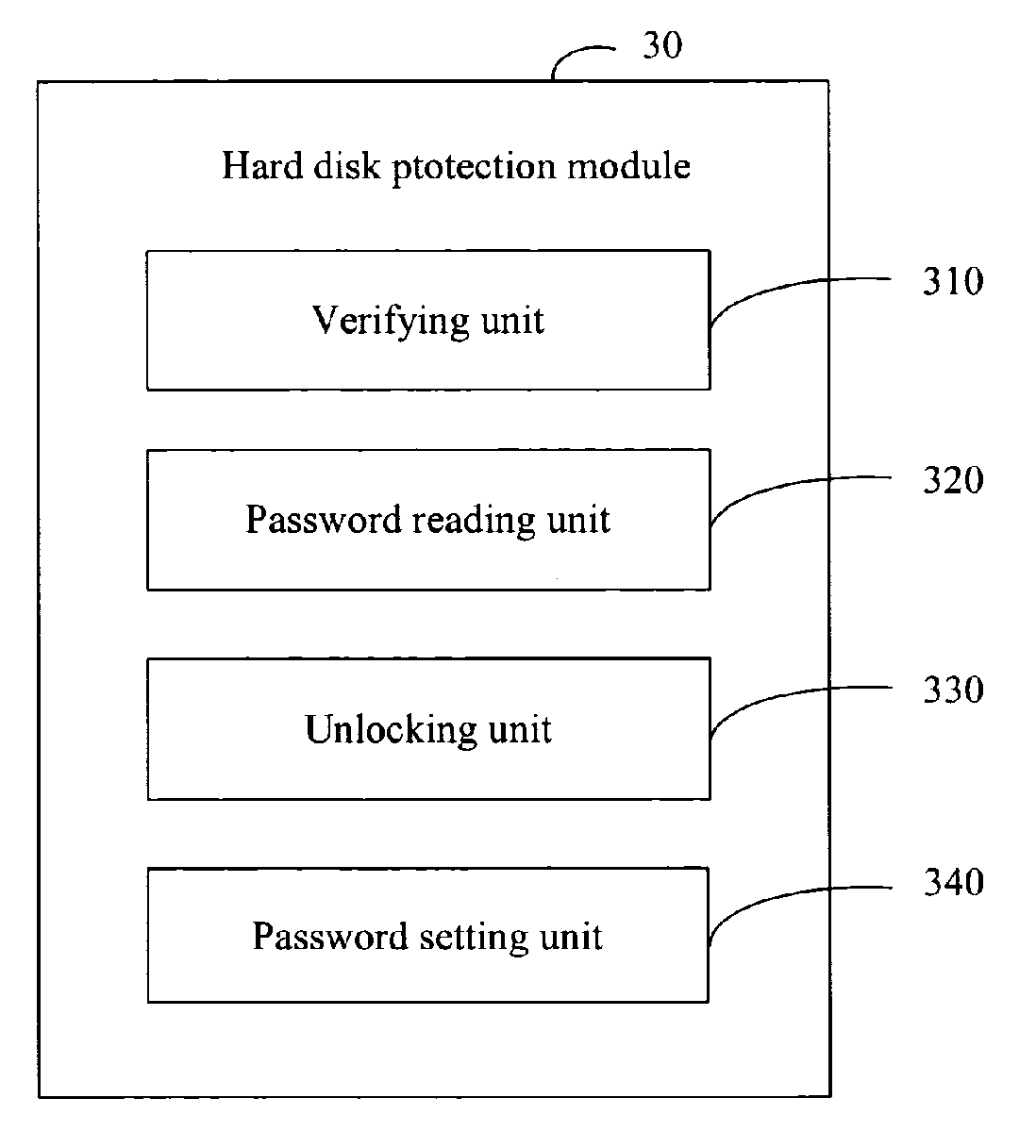
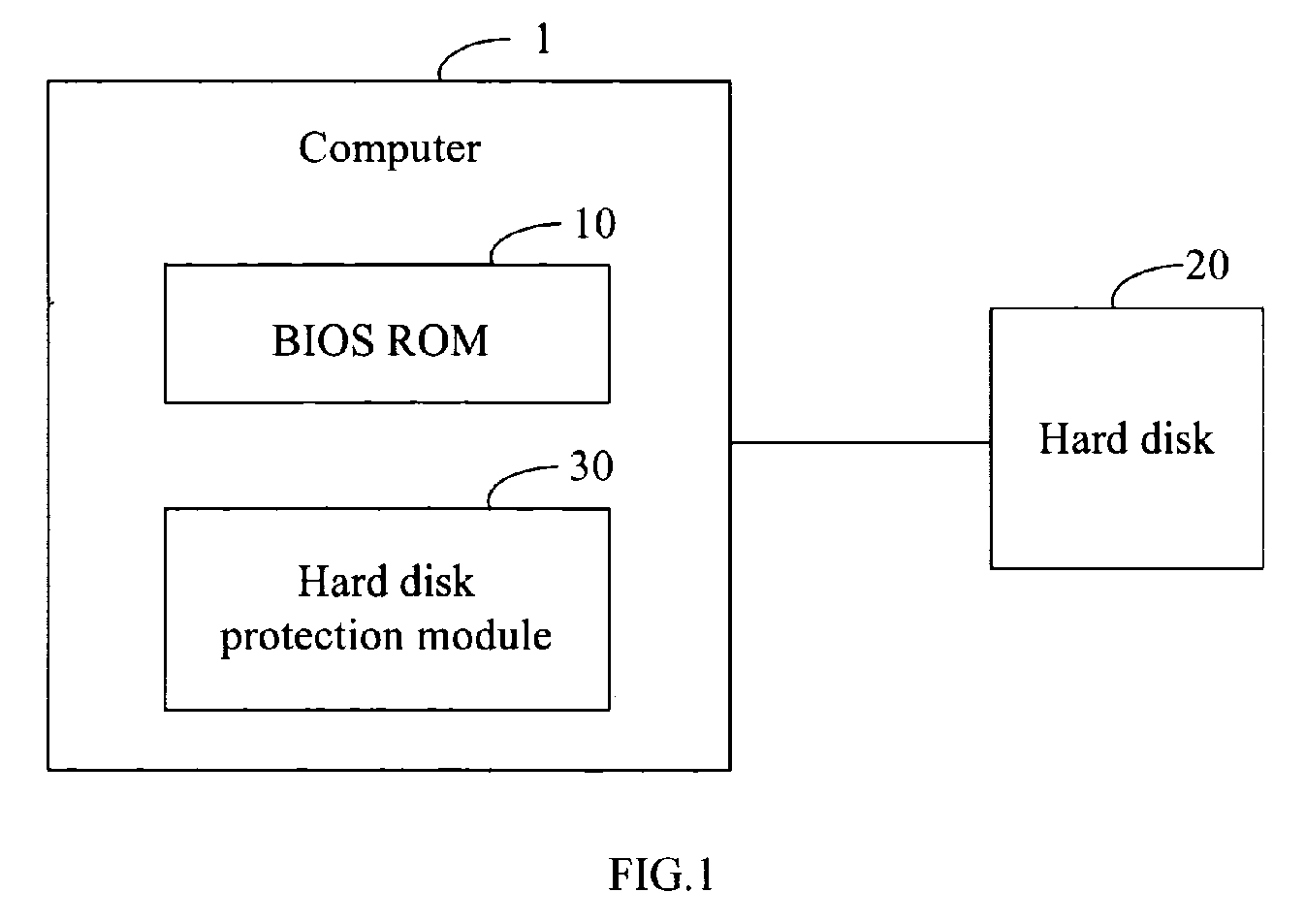
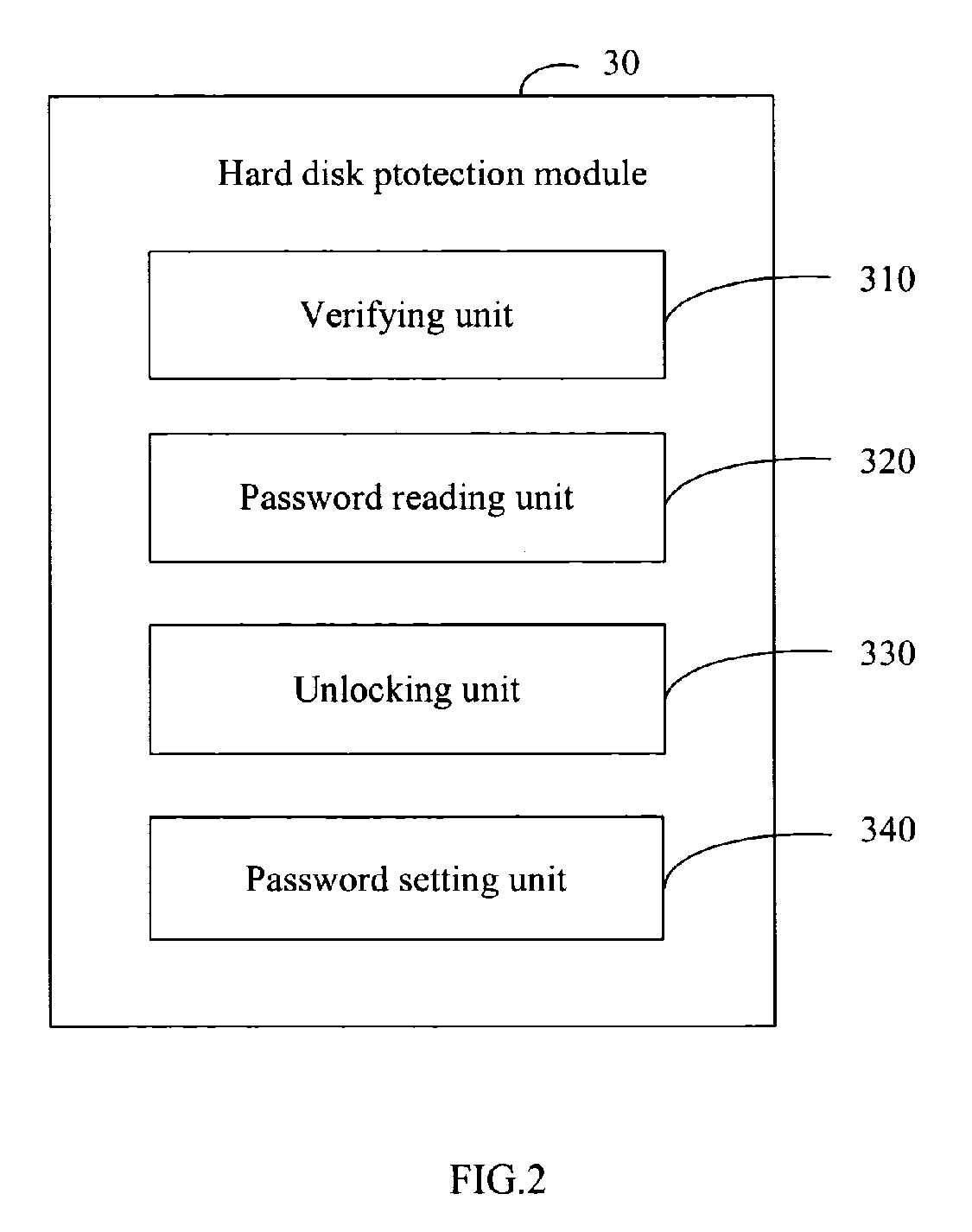
System and method for hard disk protection
InactiveUS20070089169A1Not easy to be stolenData can be securedDigital data processing detailsUnauthorized memory use protectionBIOSProtection system
A system for hard disk protection includes a computer. The computer includes a hard disk protection module, which includes: a verifying unit for determining whether a hard disk linked to the computer is locked, determining whether there is a generated password in a BIOS ROM of the computer, and determining whether an hard disk password setting in the hard disk is identical with the generated password or a factory default password stored in the BIOS ROM; a password reading unit for reading a factory default password or the generated password stored in the BIOS ROM, and reading an hard disk password setting in the hard disk; an unlocking unit for sending a request of unlocking the hard disk by the generated password or by the factory default password; and a password setting unit for writing the generated password to the hard disk to replace the hard disk password setting.
Owner:HON HAI PRECISION IND CO LTD
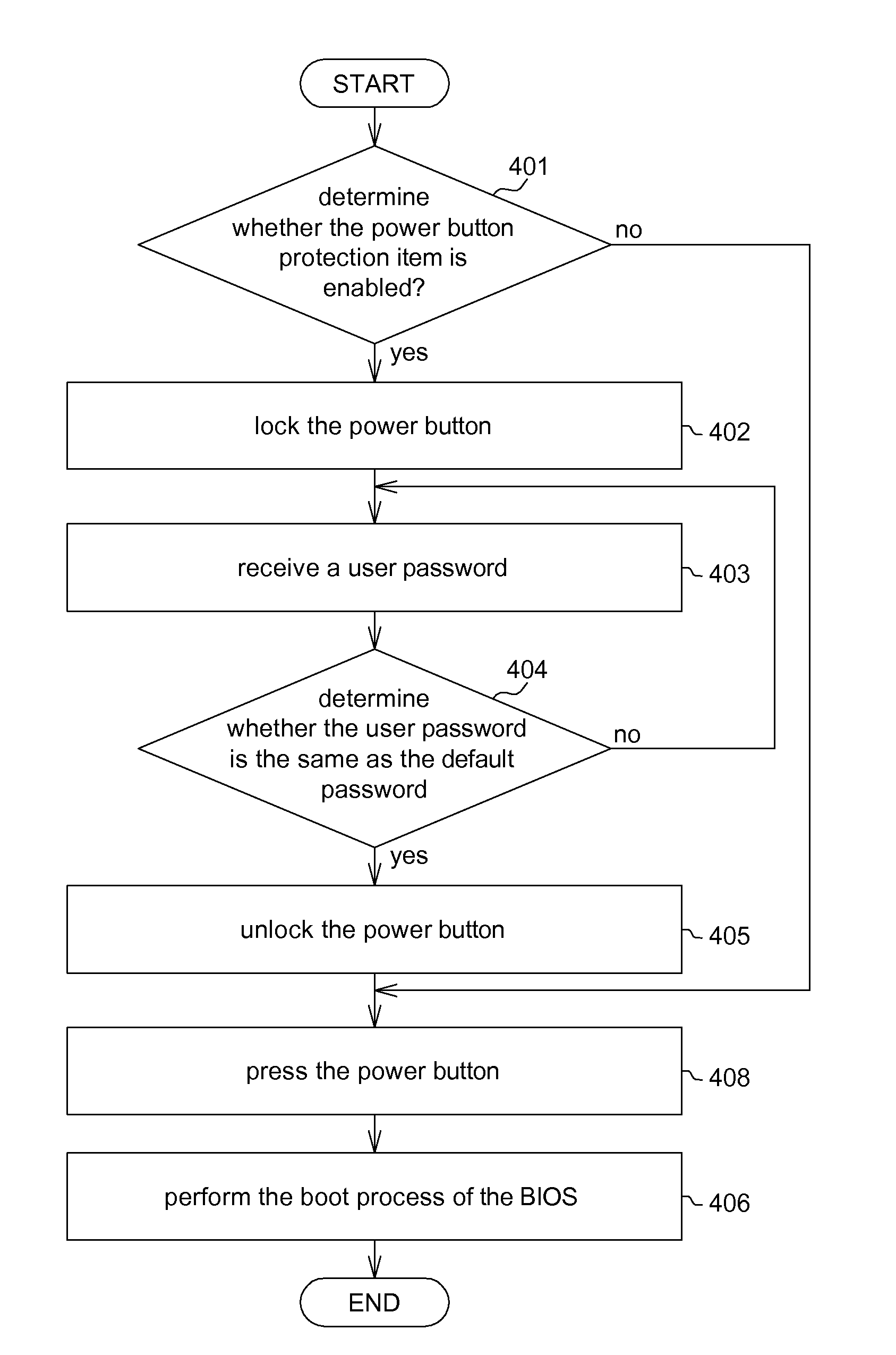
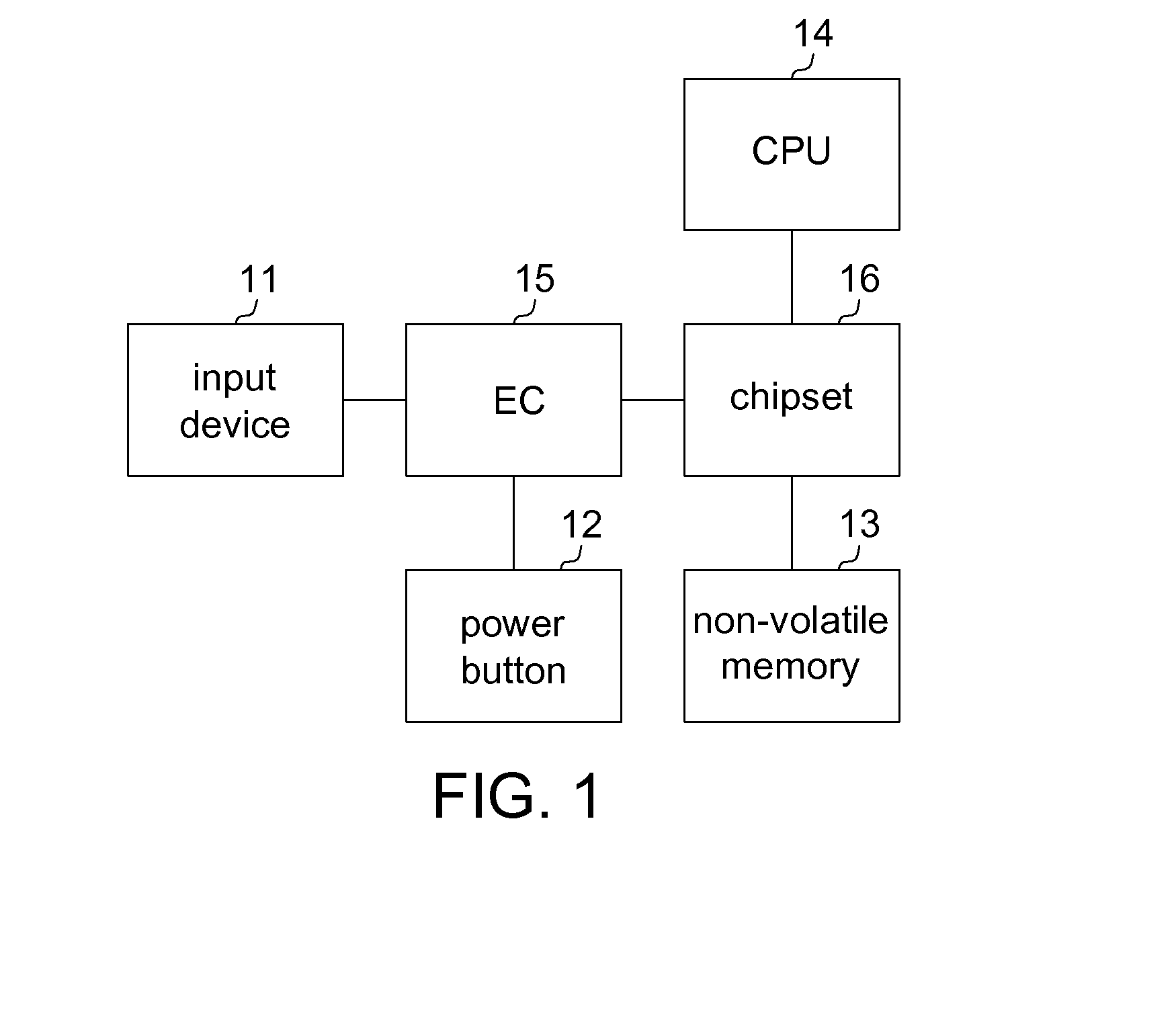
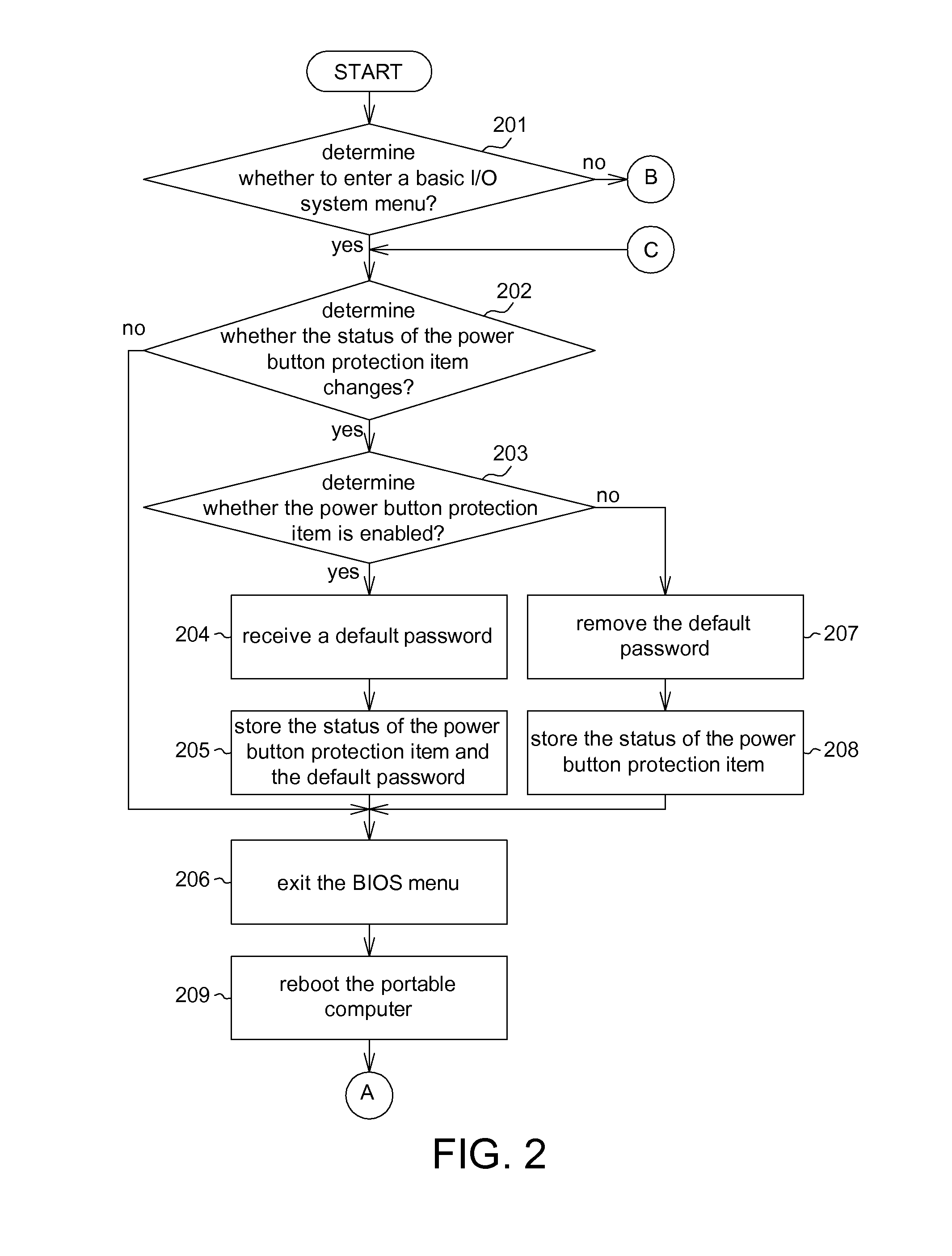
Portable computer and operating method thereof
A portable computer and an operating method thereof are provided. The portable computer comprises an input device, a power button, a non-volatile memory, a central processing unit (CPU), an embedded controller (EC), and a chipset. The input device inputs a user password, and the non-volatile memory stores a default password. The EC, in a soft off status, determines whether the power button protection item is enabled. The EC locks the power button if the power button protection item is enabled. The EC determines whether the user password is the same as the default password. The EC unlocks the power button if the user password is the same as the default password. The chipset is coupled to the non-volatile memory, the CPU and the EC.
Owner:QUANTA COMPUTER INC
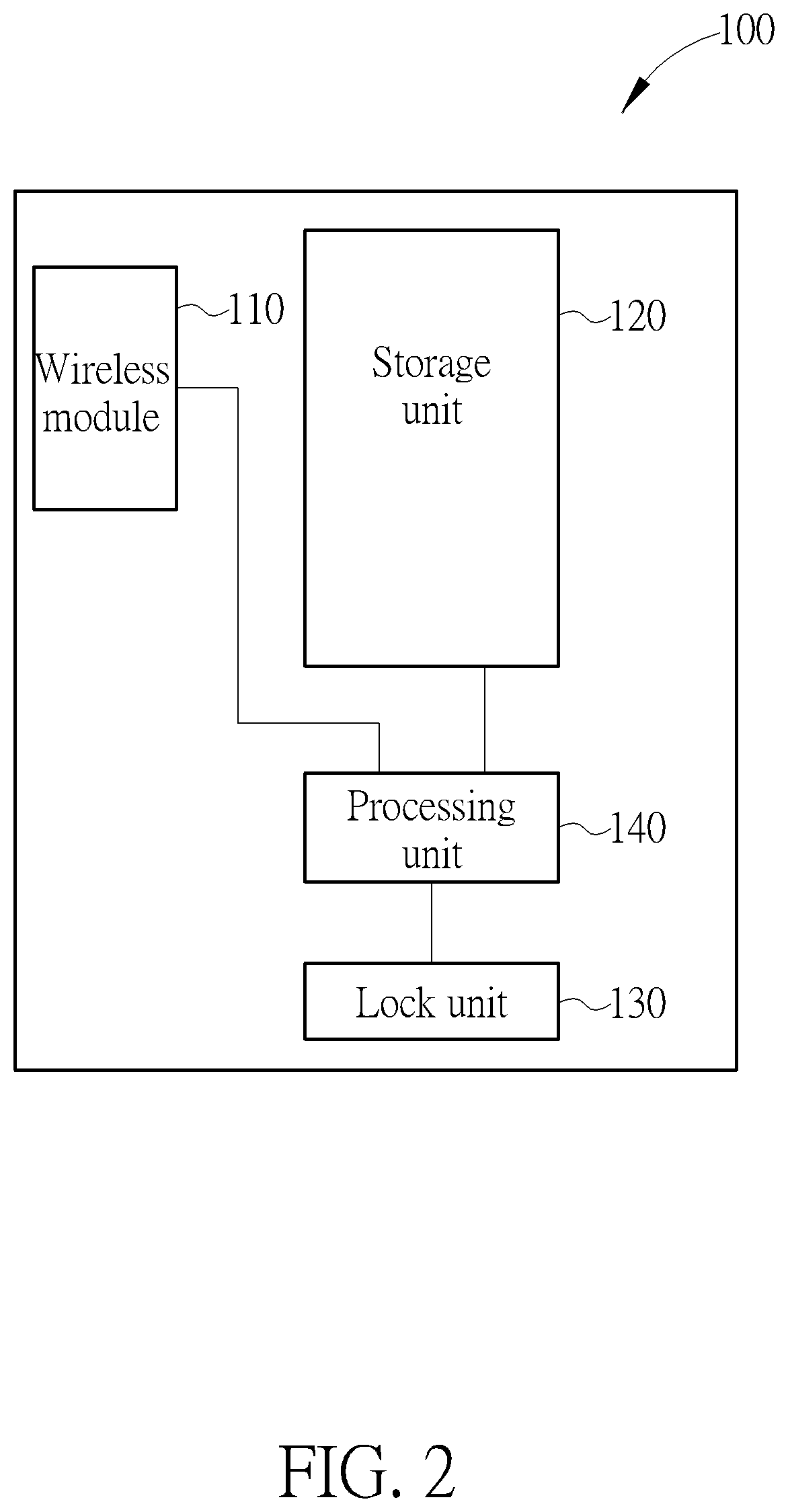
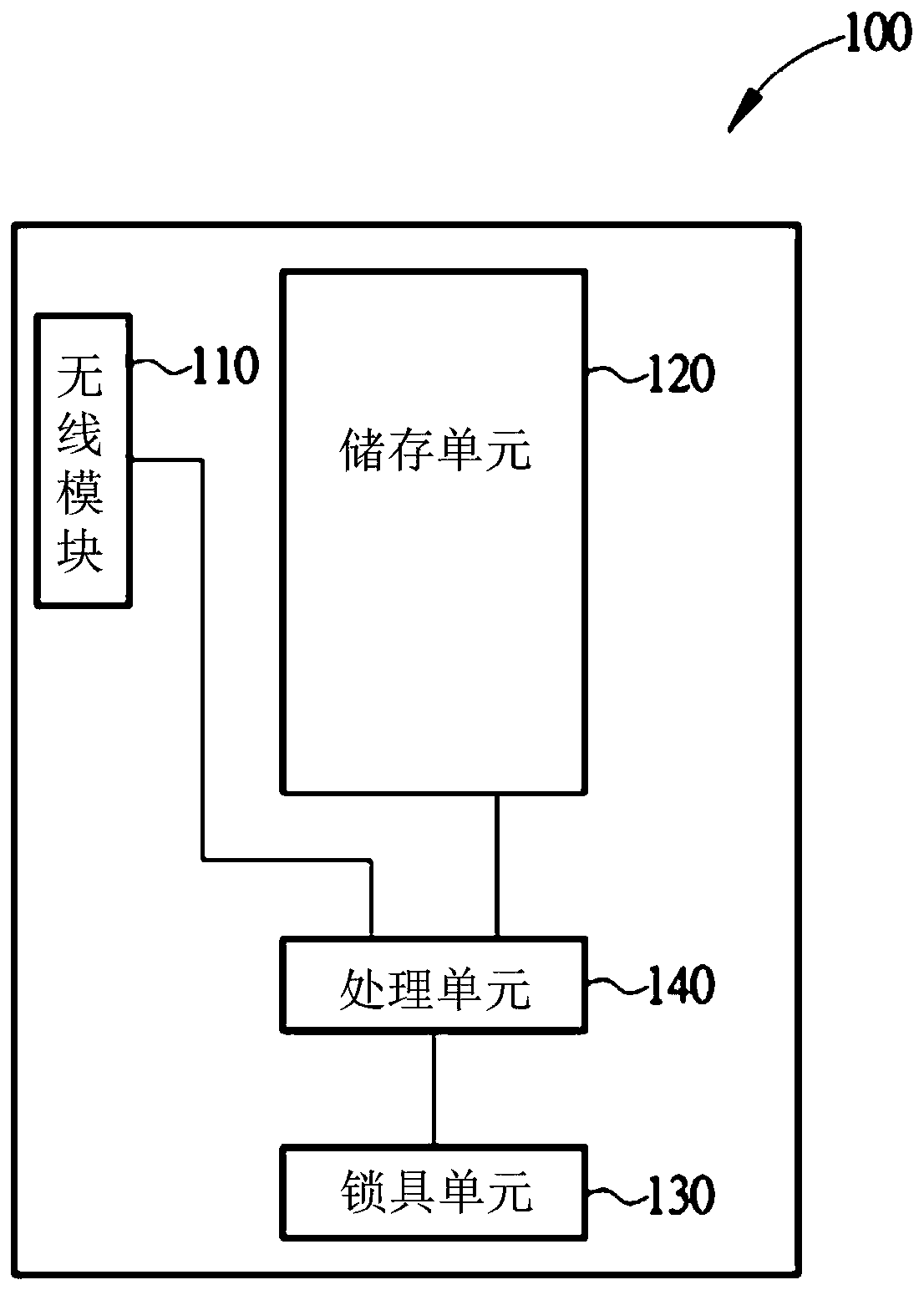
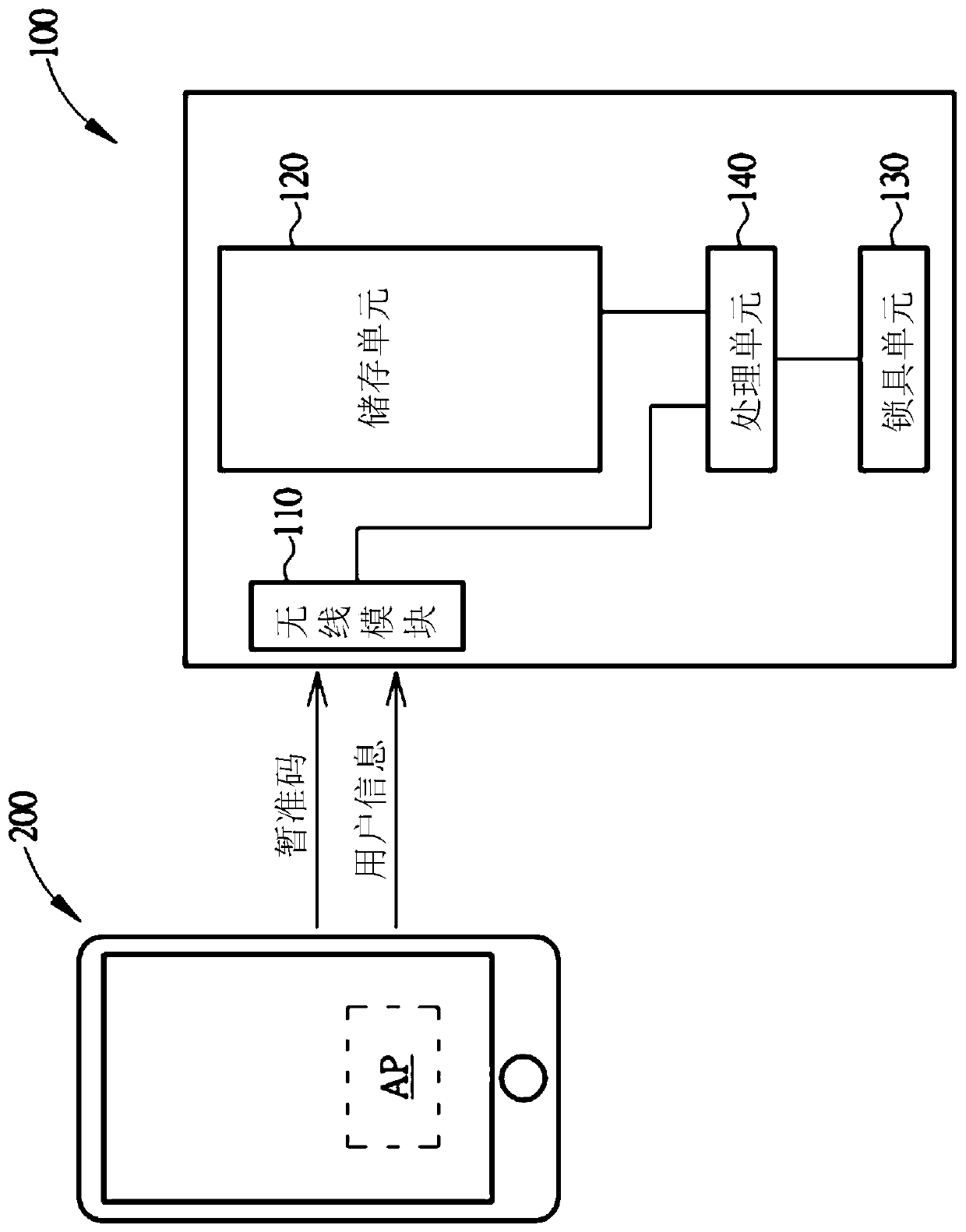
Electric lock and method for adding a user of the same
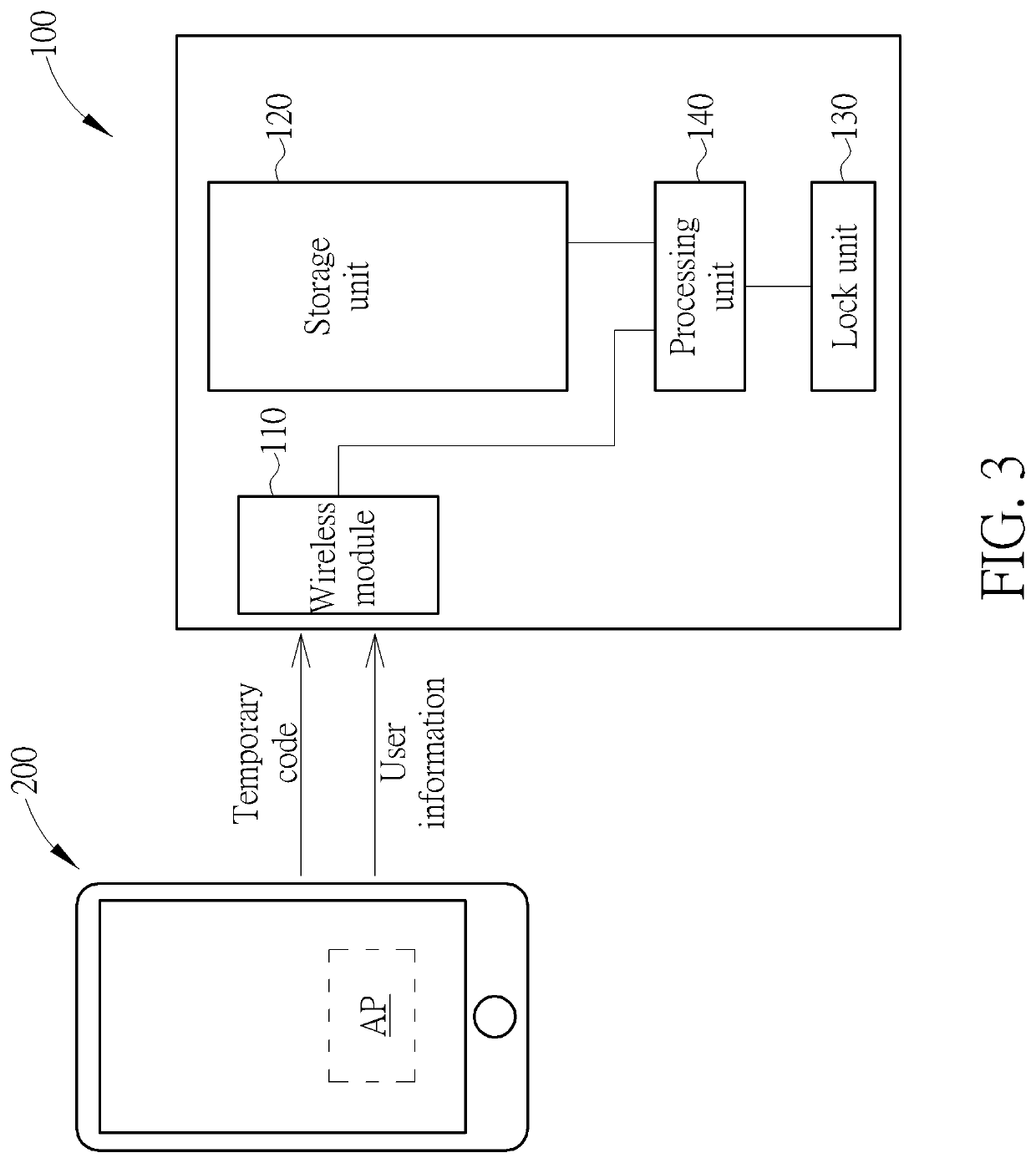
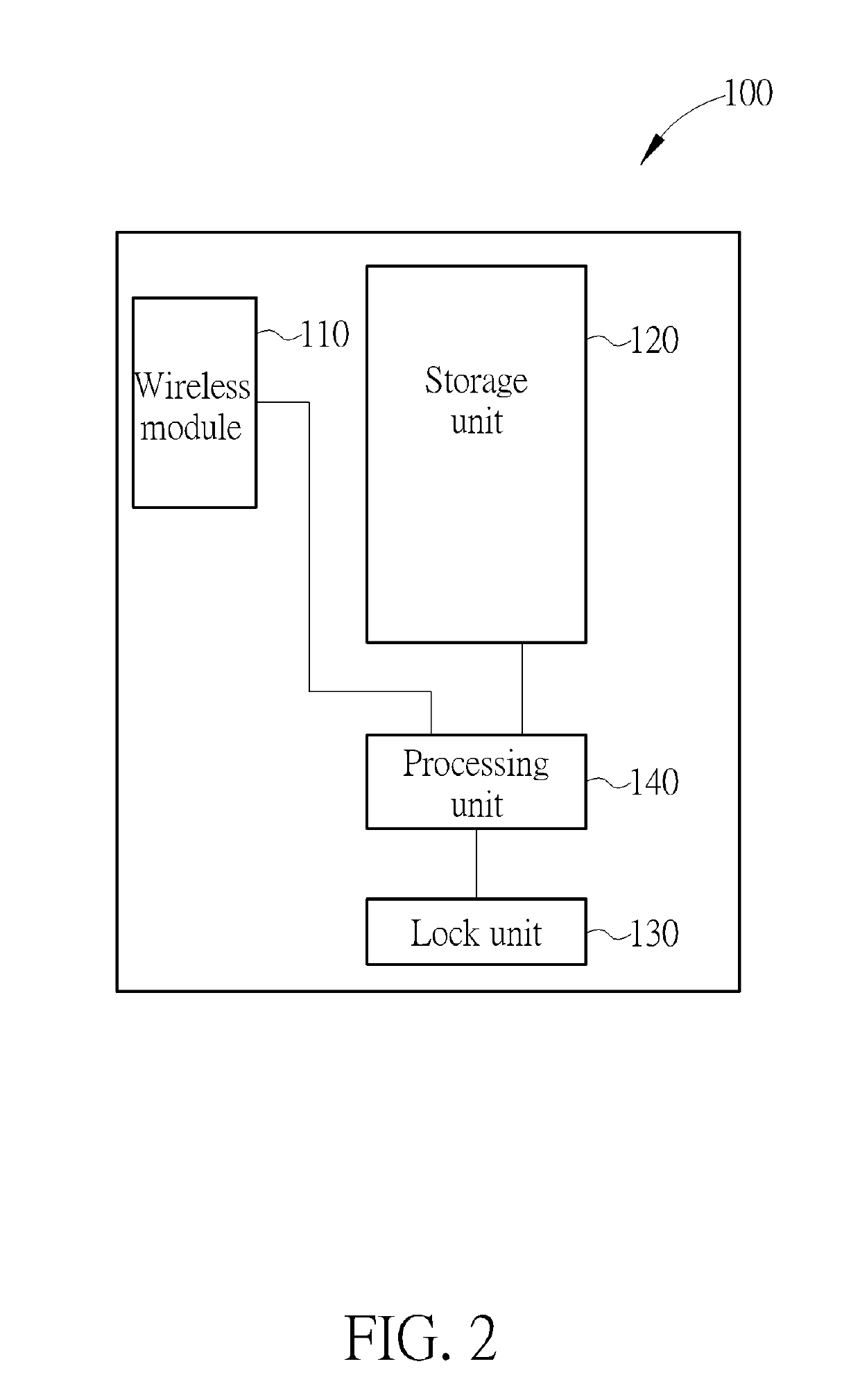
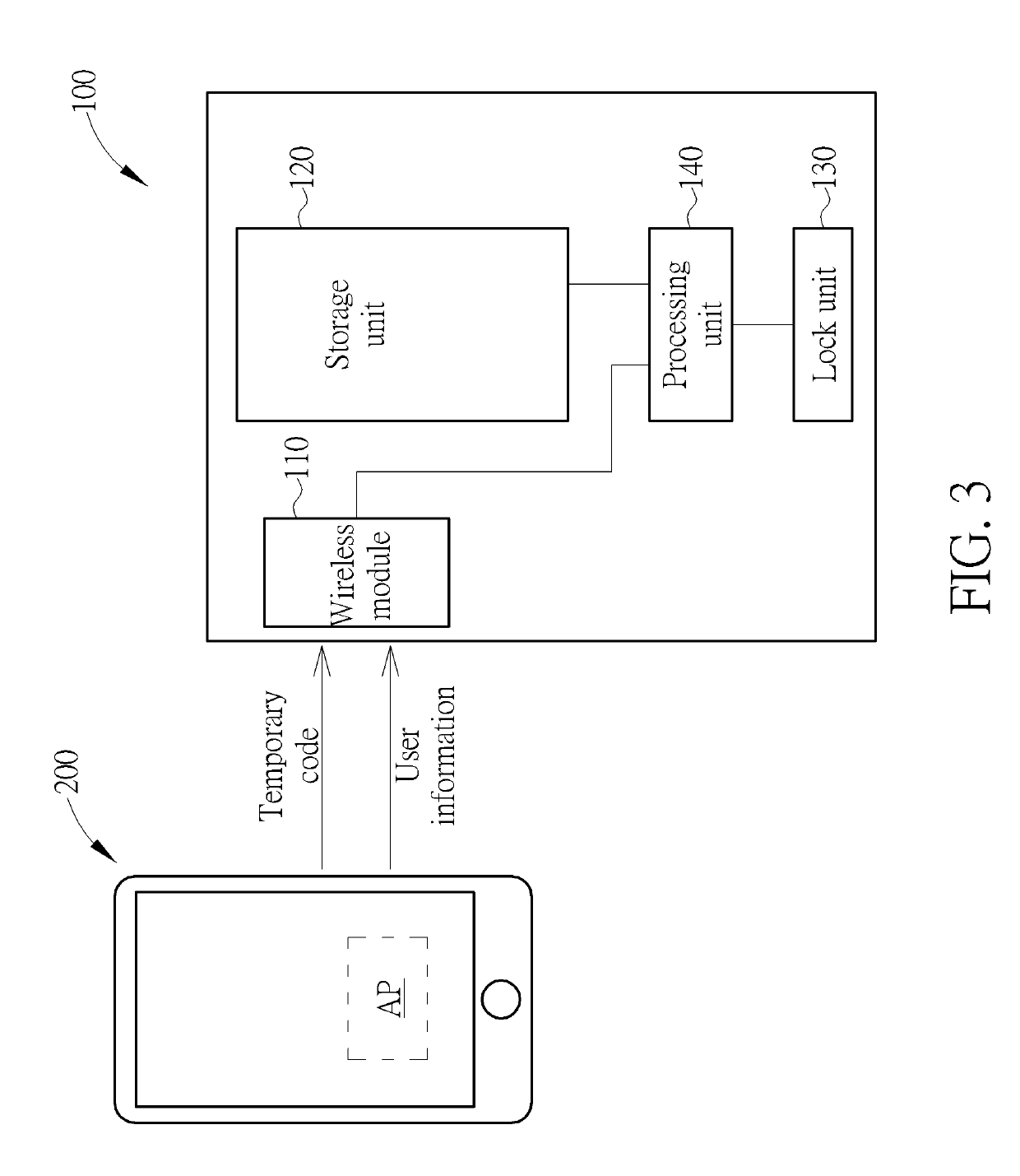
A method for adding a user of an electric lock includes receiving a temporary code; establishing a connection between a portable device of the user and the electric lock; inputting and transmitting the temporary code to the electric lock via the portable device; the electric lock determining if the temporary code matches a default password; inputting a user information of the portable device via the portable device when the temporary code matches the default password; and storing the user information in the electric lock, so that the portable device is allowed to drive the electric lock to perform an action.
Owner:TAIWAN FU HSING INDAL
Method of data access preventing decryption
ActiveCN101324866ARead-only memoriesUnauthorized memory use protectionComputer hardwareAccess method
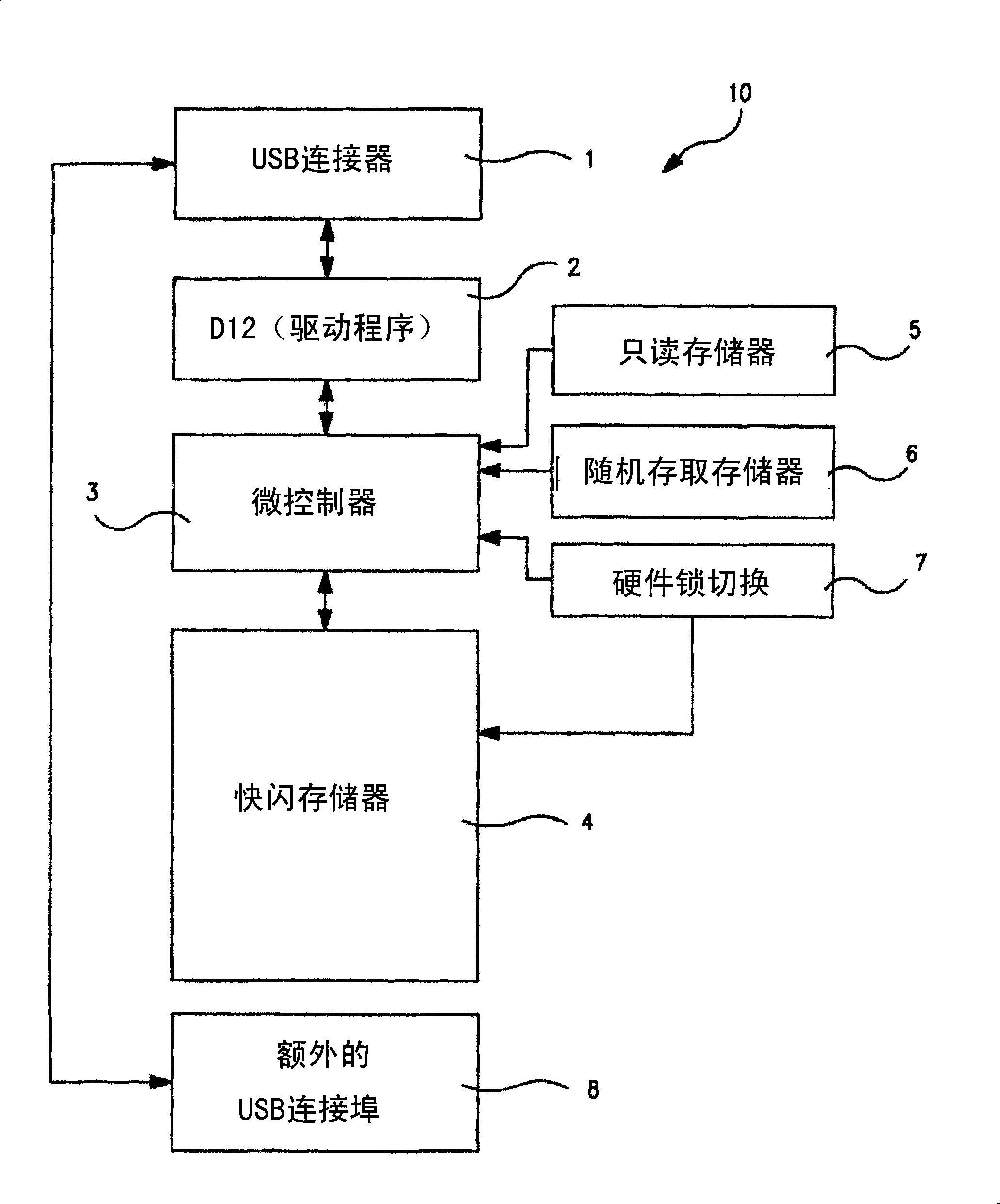
The invention discloses a data access method of a data storage device applied to a data read / write device and provided with at least one NAND flash memory. The method comprises the following steps: default passwords are established; a first encryption key is generated; data encryption is performed through the first encryption key; a prompt for password input is provided after an access request is received; headers stored in the NAND flash memory are decoded through the passwords input by a user; the headers are detected to determine whether the passwords input by the user are correctly corresponding to the first encryption key or not; and after the passwords input by the user are correctly corresponding to the first encryption key, decryption and data output are performed through the encryption key.
Owner:PHISON ELECTRONICS
Network access authentication method and system based on quantum key
ActiveCN108768640AAbsolute securityImprove securityKey distribution for secure communicationDigest access authenticationComputer terminal
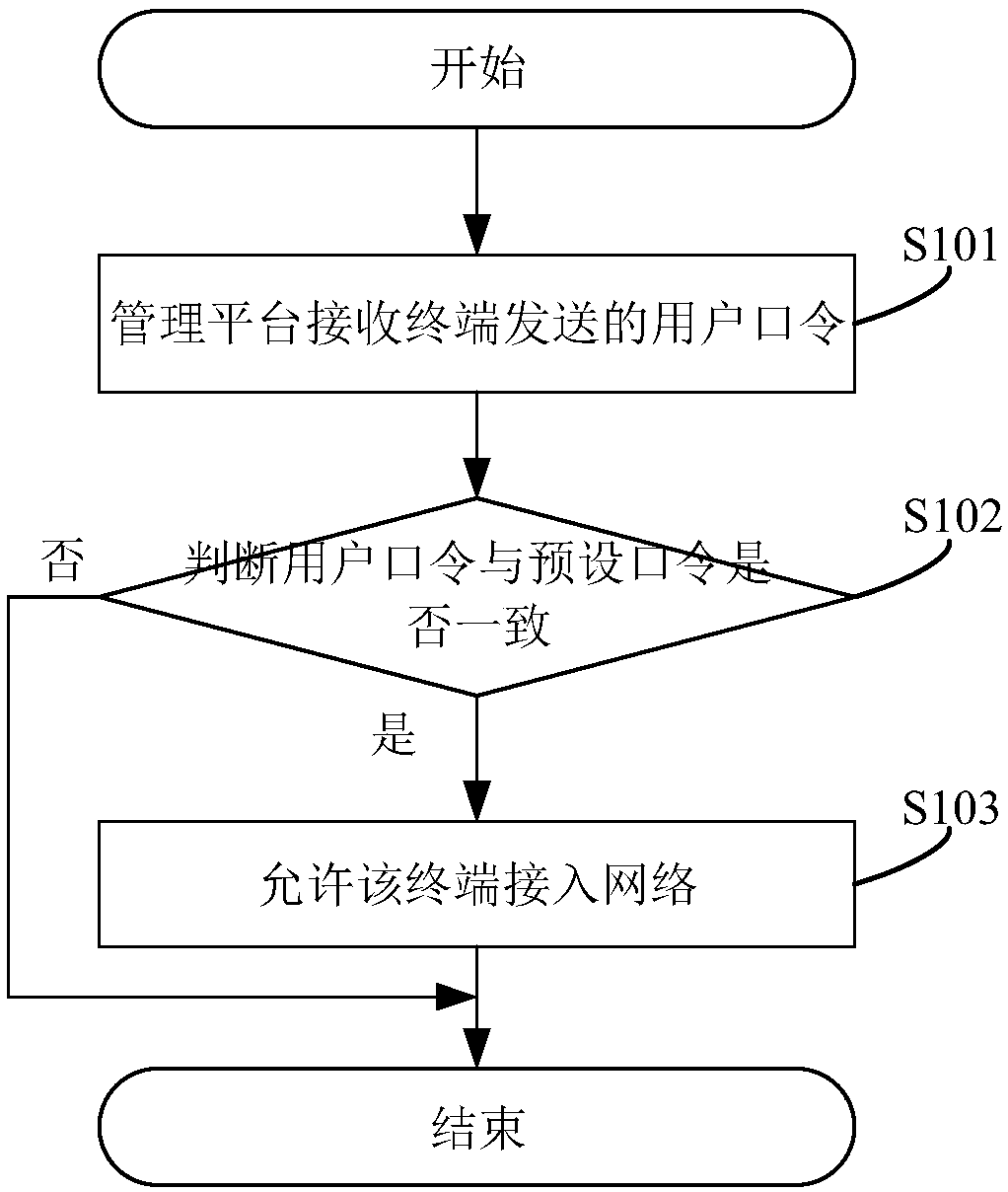
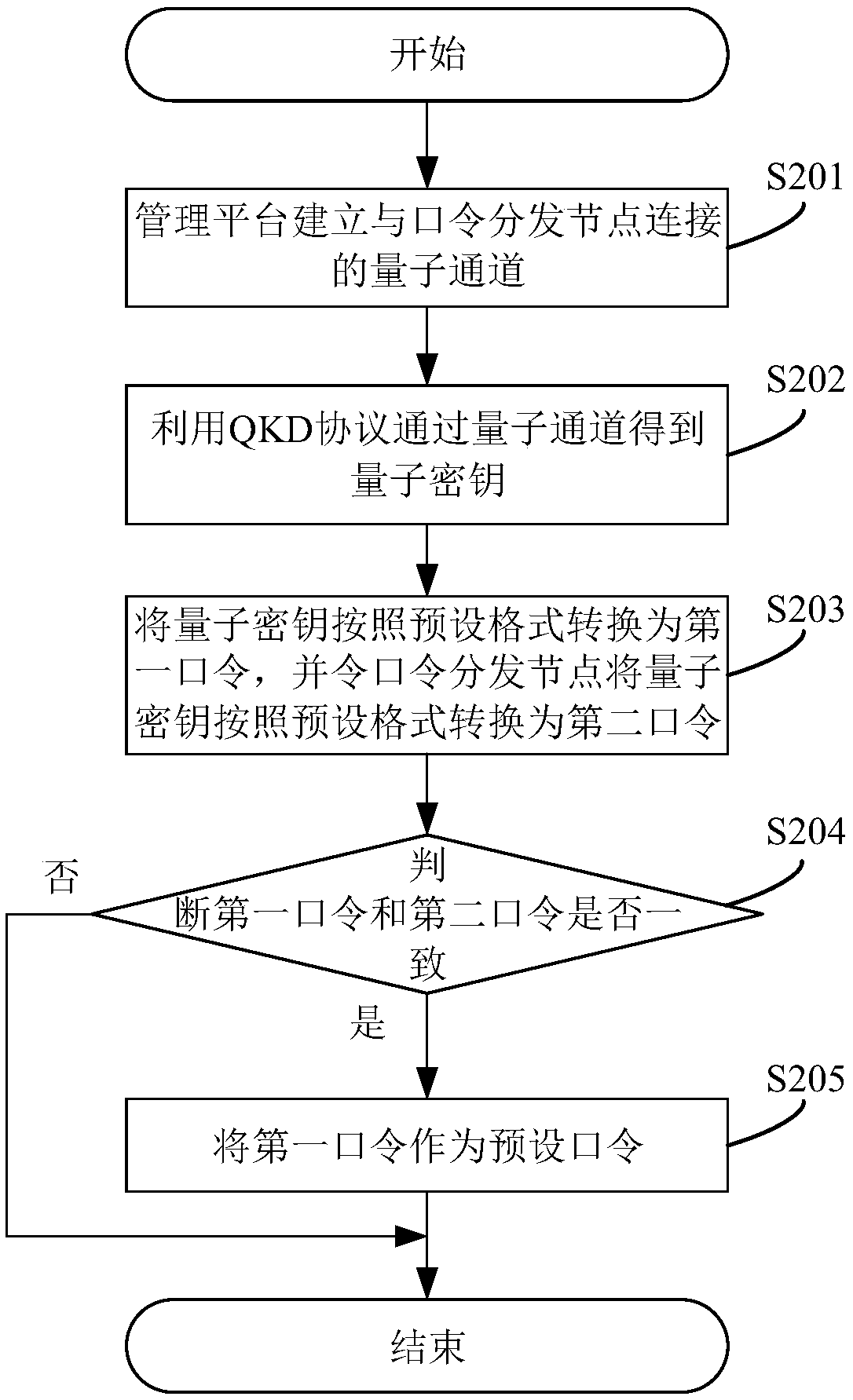
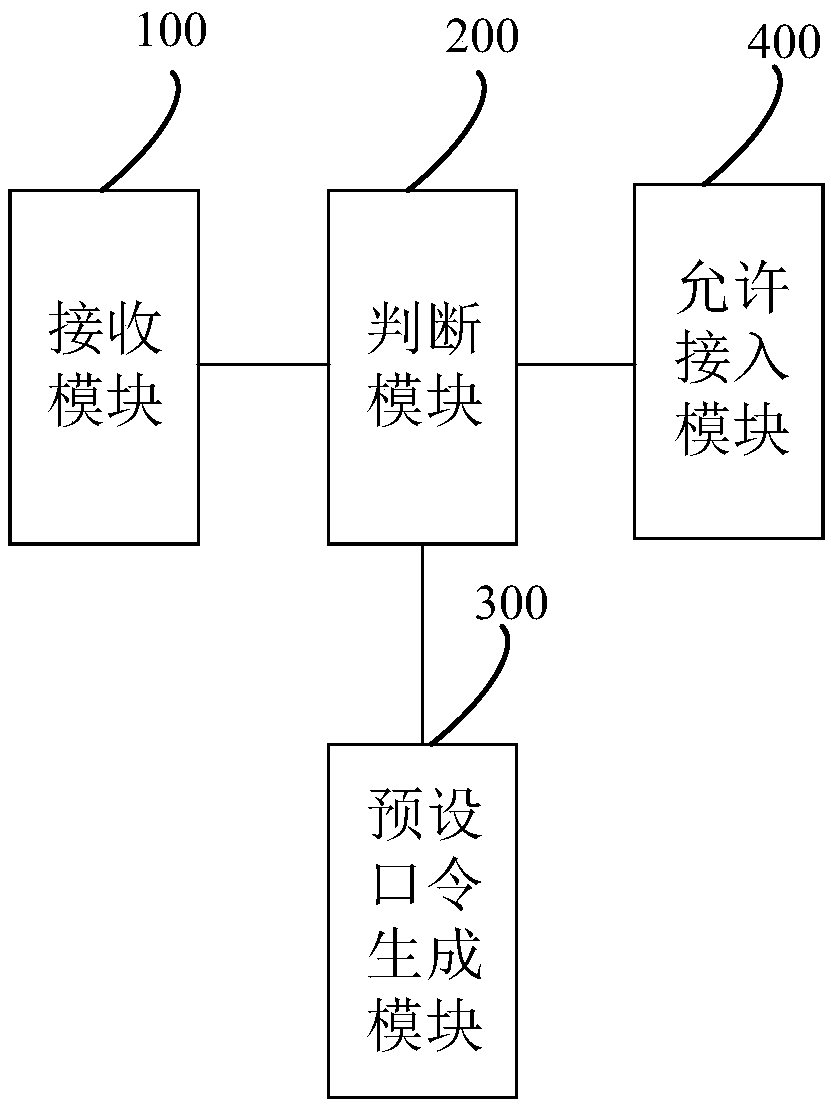
The application discloses a network access authentication method based on a quantum key. The method includes the following steps: enabling a management platform to receive a user password sent by a terminal; determining whether the user password is consistent with a default password, wherein the default password is a password generated according to a quantum key that is obtained by the managementplatform and a password distribution node by using a QKD protocol; and if yes, allowing the terminal to access the network. According to the technical scheme provided by the application, the default password is generated according to the quantum key that is obtained by the management platform and the password distribution node by using the QKD protocol, since the quantum key has absolute securityand cannot be duplicated, the default password generated according to the quantum key can also have absolute security, and the security of network access authentication can be greatly improved. The application also provides a network access authentication system based on the quantum key, a server and a computer readable storage medium, which have the above beneficial effects.
Owner:KEHUA DATA CO LTD
Asymmetric-algorithm-based certificate medium online-formatting and unlocking methods
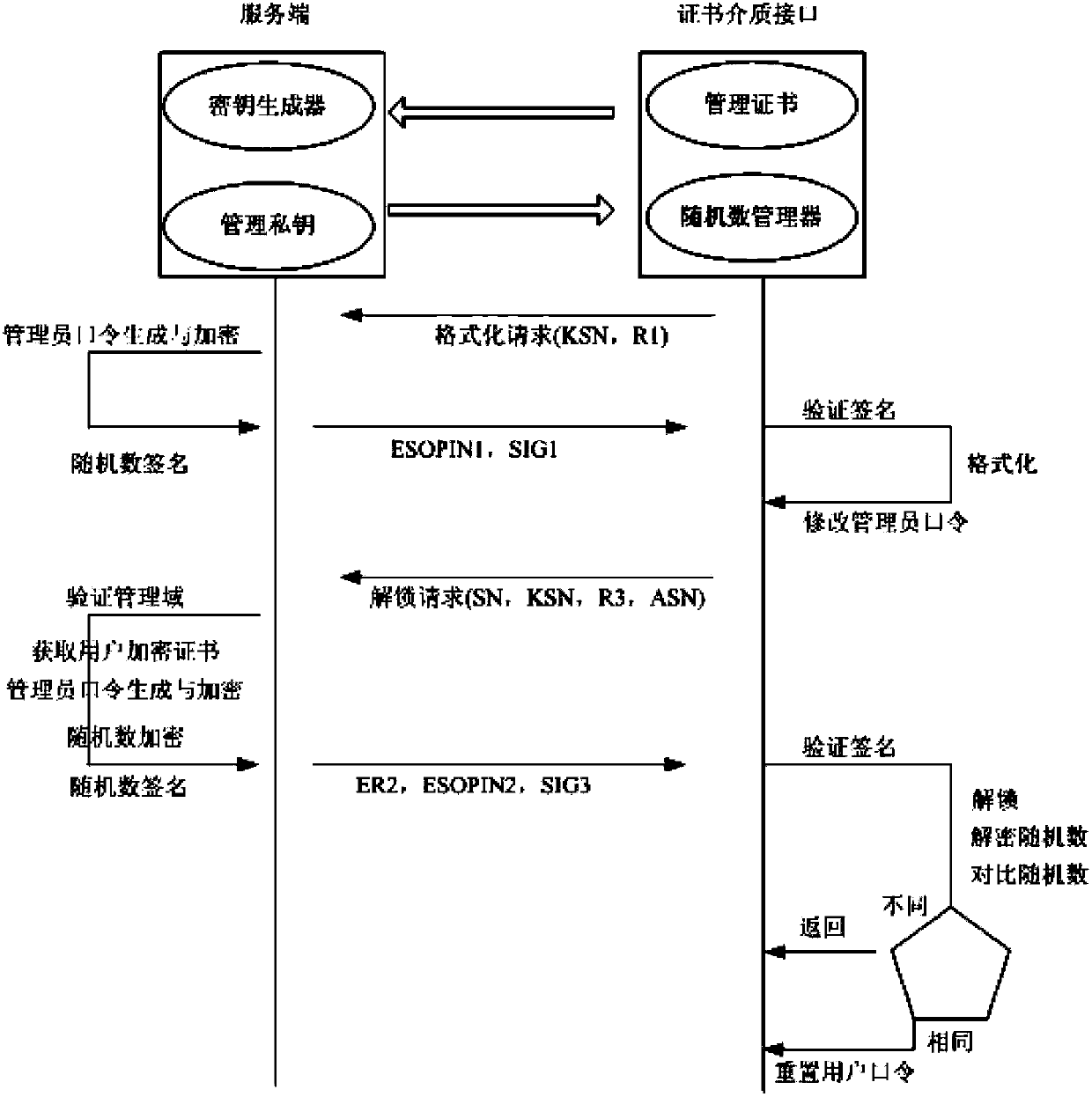
ActiveCN103873249AEnsure safetyKeep Passwords SafePublic key for secure communicationUser identity/authority verificationDefault passwordPublic key infrastructure
The invention discloses an asymmetric-algorithm-based certificate medium online-formatting method and an asymmetric-algorithm-based certificate medium online-locking method. The formatting method comprises the following steps that a medium management interface generates a one-time random code R1 and a medium sequence number KSN, a server acquires a corresponding management password SOPIN1 of a medium according to the KSN, performs encryption and signature, and transmits a result to a client, and the client verifies and decrypts the result to finish formatting. The unlocking method comprises the following steps that the medium management interface acquires a signed certificate sequence number SN and the medium sequence number KSN, and generates a one-time random code R3; the server acquires the management password SOPIN1 by using the KSN, encrypts and signs received data, and transmits the data to the client; the medium management interface performs signature verification and decryption, compares a decryption result, and resets a user password to be a default password if the one-time random code R3 is the same as the decryption result. According to the methods, the password security of the certificate medium can be ensured in large-scale public key infrastructures.
Owner:KOAL SOFTWARE CO LTD
Electric lock and method for adding a user of the same
ActiveUS20190206167A1Improve convenienceIndividual entry/exit registersEmbedded systemDefault password
A method for adding a user of an electric lock includes receiving a temporary code; establishing a connection between a portable device of the user and the electric lock; inputting and transmitting the temporary code to the electric lock via the portable device; the electric lock determining if the temporary code matches a default password; inputting a user information of the portable device via the portable device when the temporary code matches the default password; and storing the user information in the electric lock, so that the portable device is allowed to drive the electric lock to perform an action.
Owner:TAIWAN FU HSING INDAL
Password clearing method and system
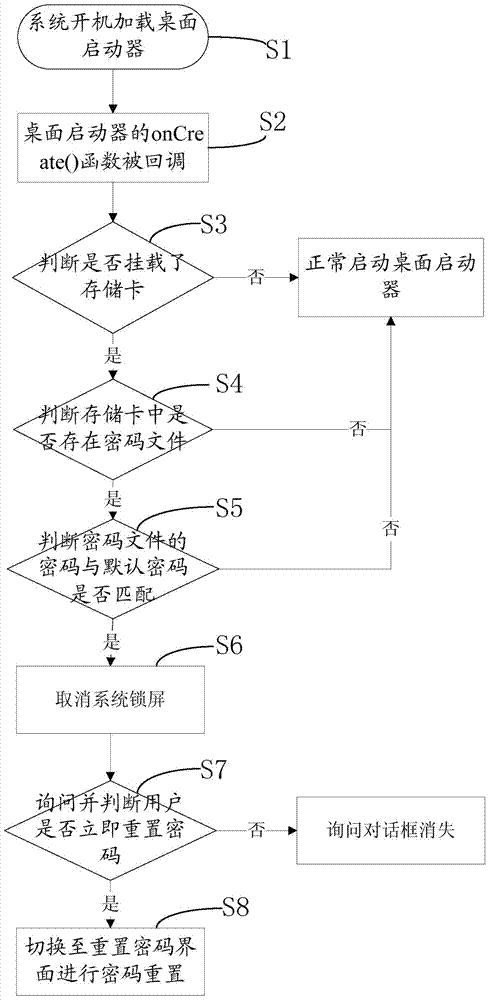
InactiveCN103886271AEasy to useEasy to removeInternal/peripheral component protectionDigital data authenticationDefault password
The invention provides a password clearing method. The password clearing method comprises the following steps that A. whether a storage card is mounted or not is judged, if yes, the step B is executed, and if not, a tabletop starter is started normally; B. whether a password file exists in the storage card or not is judged, if yes, the step C is executed, and if not, the tabletop starter is started normally; C. whether the password of the password file is matched with a default password or not is judged, if yes, the step D is executed, and if not, the tabletop starter is started normally; D. system screen locking is eliminated. The password clearing method and system have the advantages of clearing the password conveniently, rapidly and safely, and bringing convenience to use by users.
Owner:深圳市阿龙电子有限公司
Decryption method for use in displaying data
ActiveUS10025945B2Improve confidentialityPrevent steppingDigital data protectionComputer hardwareHuman–machine interface
A decryption method for use in displaying data includes the steps of executing a display instruction of an object inclusive of a plurality of data, displaying an unencrypted data, but not an encrypted data, of the data on a display unit according to the display instruction, detecting a trigger signal during the state of displaying the unencrypted data but not displaying the encrypted data, entering a password-receiving state in response to the trigger signal and detecting a password signal during the password-receiving state, determining whether the password signal matches a default password, and displaying the unencrypted data and the encrypted data on the display unit when the password signal matches the default password. Therefore, with the decryption method, no person other than the object owner is aware of the encrypted data.
Owner:GETAC TECH CORP
Network monitoring equipment and method, device and system for resetting its password, and server
ActiveCN106302335BEnsure safetyImprove securityMultiple keys/algorithms usagePublic key for secure communicationMonitor equipmentNetwork monitoring
Owner:HANGZHOU HIKVISION DIGITAL TECH
Password input method and device
InactiveCN104573445AImprove securityReduce construction costsDigital data authenticationInput/output processes for data processingLimited resourcesStart up
The invention relates to password input methods and devices, in particularly to a password input method and device capable of preventing peeping. The method password input method is characterized by including the steps of setting a default password; inputting the password; determining whether the input password is correct or not; starting up a machine if the input password is correct. The password input method can greatly enhance the password security, does not need to set an isolation unit during password inputting due to the good safety performance, greatly reduces construction costs, protects limited resources and is environmentally friendly.
Owner:陆忠敏
Electric lock and method for adding a user of the same
PendingCN110021099AImprove management convenienceLow operating environment requirementsIndividual entry/exit registersEmbedded systemDefault password
A method for adding a user of an electric lock includes receiving a temporary code; establishing a connection between a portable device of the user and the electric lock; inputting and transmitting the temporary code to the electric lock via the portable device; the electric lock determining if the temporary code matches a default password; inputting a user information of the portable device via the portable device when the temporary code matches the default password; and storing the user information in the electric lock, so that the portable device is allowed to drive the electric lock to perform an action. The electric lock is also disclosed.
Owner:TAIWAN FU HSING INDAL
Lock
InactiveCN111287581AEasy to operateImprove intelligenceElectric permutation locksIndividual entry/exit registersMultiple inputEmbedded system
The invention discloses a lock. The lock comprises a control mainboard, a motherboard, a son-board, a fingerprint recognition module, a driving component and a locking head. The control mainboard stores a default password and fingerprint information. The son-board is rotationally arranged on the motherboard. When a second induction component on the son-board is matched with one of first inductioncomponents on the motherboard, the control mainboard can receive password numbers corresponding to the first induction component and compares the password numbers with the default password, and can receive a fingerprint recognized by the fingerprint recognition module and compares the fingerprint with the fingerprint information. The control mainboard can control the driving component to drive thelocking head to move so that the lock can be switched between an unlocked state and a locked state. The control mainboard is configured to control the son-board to be switched to a rotating state from a locked state when the received fingerprint is matched with the fingerprint information and to control the driving component to drive the locking head to move when the multiple input password numbers are matched with the default password so that the lock can be switched to the unlocked state. The lock provided by the invention is low in manufacturing cost and high in intelligence level and meets current market requirements.
Owner:BYD SEMICON CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com