Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
39results about How to "Absolute security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
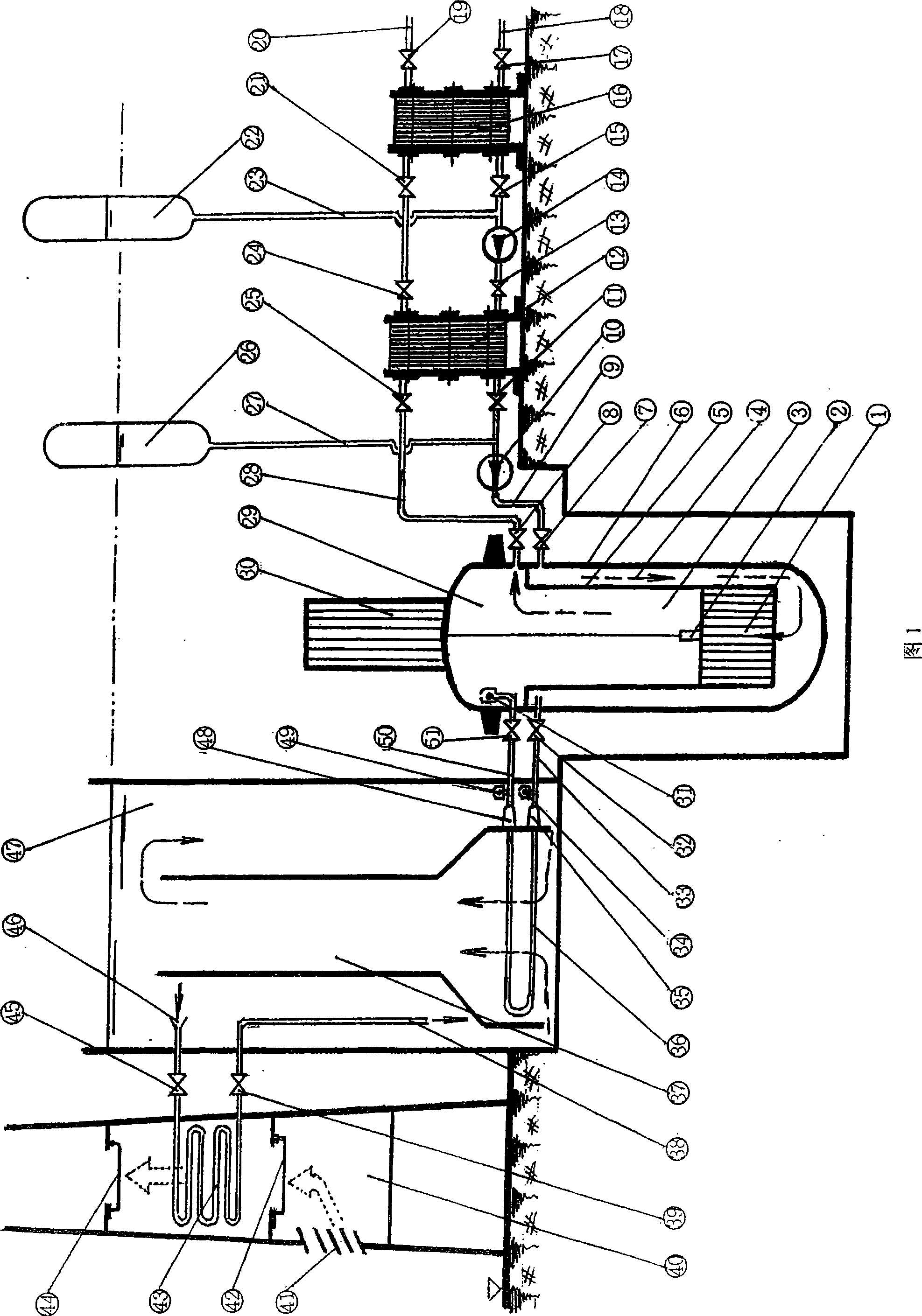
Inherent safety pool case combination low-temperature stack nuclear heating station apparatus and operational procedure thereof
InactiveCN101441902AIncreased average volume specific powerReduce initial loadIntegral reactorsNuclear energy generationInherent safetyPressurized water reactor
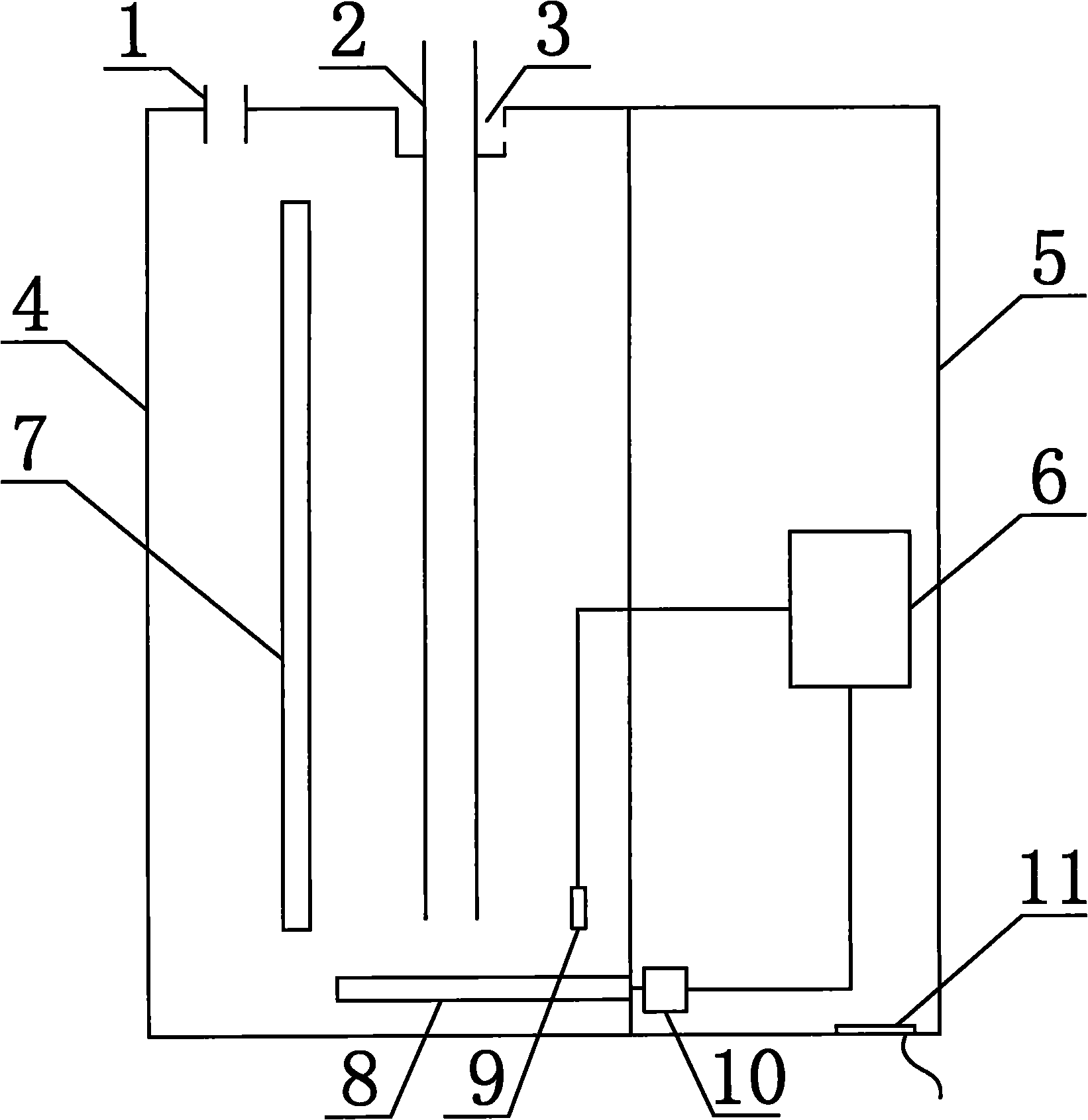
The present invention provides an inherent security pool-shell combination low temperature nuclear heating device and an operation program thereof, which belongs to nuclear energy centralized heat-supply field. The invention mainly comprises the following procedures: adopting separated layout, forced circulation and high effective small temperature difference heat exchange in primary loop of reactor; under the precondition that parameter requirements of centralized heat-supply by big cities heat supply network satisfied, reducing work temperature of shell-type heating reactor as far as possible; meanwhile optimized layout of equipment, and organic combination of normal pressure pool in large volume (47) and shell-style heating reactor(29) remove accident possibility of water loss and coldness loss of reactor core (1). Complete inherent safety principle is carried out in the invention. Thus, absolute security of nuclear heating can be guaranteed by using mature pressurized water reactor technology, and enterprises have develop nuclear station pressurized water reactor experience can possibly jump over research and develop stage and enter into nuclear heating market directly, and make a real contribution for energy-saving and emission-reduction and improving country energy structure.
Owner:肖宏才
Fresh bamboo shoot coating preservative prepared by edible material
InactiveCN101744045AAbsolute securityNo harmFruits/vegetable preservation by coatingPreservativeAtmospheric temperature
The invention relates to fresh bamboo shoot coating preservative prepared by edible materials, belonging to the technical field of fruit and vegetable freshness preservation. The preservative mainly comprises one kind or more of substances such as natural plant gum, polysaccharose, natural macromolecular substances, stabilizing agent, bacteriostatic agent and the like. In the process of preparation, components are dissolved in certain proportion, the obtain solution is agitated and heated to accelerate dissolution, and the obtained solution is prepared into water solution or colloidal solution after being cooled. The preservative can be used under atmospheric temperature. The coating preservative prepared through the invention belongs to natural preservative and has the advantages that the cost is low, the effectiveness is high, the environment is protected, the activity of the cellulose synthase and other enzymes is effectively inhibited, the weight loss of bamboo shoots is reduced, the low-temperature damage is avoided and the quality guarantee period of the fresh bamboo shoots is greatly improved.
Owner:JIANGNAN UNIV
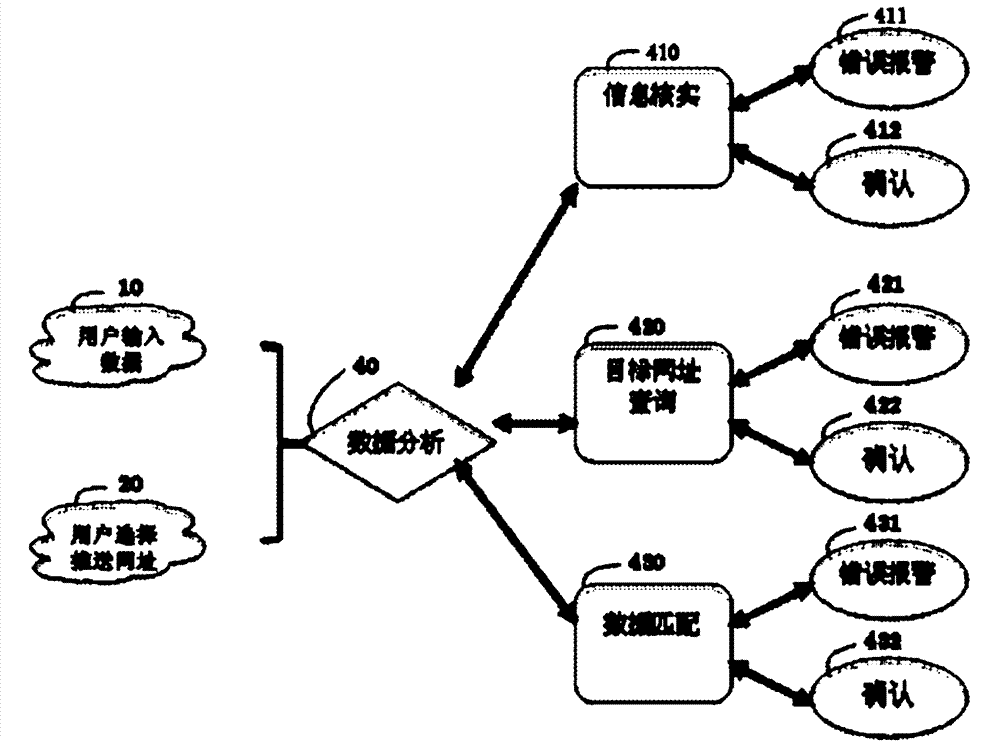
Automatic screening and propelling method and system with high matching degree for managing user and confidential information
InactiveCN103034671APrevent leakageTop secret protection achievedSpecial data processing applicationsMarketingCentral databaseScreening tool
The invention provides an automatic screening and propelling method and system with a high matching degree for managing a user and confidential information. The method comprises the following steps: a step A: self-defining and screening out a target option to be screened according to a screening model of the target option; a step B, establishing a first scoring mechanism of the screening model for scoring the target option to be screened; a step C: capturing the information associated with the target option from a first database according to the scored result, and showing the scored information from high to low in sequence according to the scores; and a step D: propelling the user information to the selected target option according to the self-defined propelling mechanism. According to the automatic screening and propelling method and system provided by the invention, the conational screening tool is improved; the user-defining and quantifying function is additionally added; self-defining treatment to a plurality of objects on the basis of protecting information privacy is carried out; and all operation processes and data are stored in the central database of the system. The automatic screening and propelling method and system are suitable for high-precision matching of market development, company merger and acquisition, investment banking and commercial procurement, and even a plurality of fields such as personal employment and education, marriage dating and the like.
Owner:GEBO INFORMATION TECH SUZHOU
True random password generation device based on vertical cavity surface emitting laser
ActiveCN106301754ACreate a new field of applicationAvoid the "Electronic Speed Bottleneck" ProblemKey distribution for secure communicationDigital data processing detailsVertical-cavity surface-emitting laserDriving current
The invention provides a true random password generation device based on a vertical cavity surface emitting laser. A driving current source loads a periodic electric signal to the vertical cavity surface laser, and the vertical cavity surface laser is periodically turned on and off to acquire a periodic laser signal. A noise signal source loads a noise signal to the vertical cavity surface emitting laser to form weak perturbation on the periodic electrical signal amplitude. The vertical cavity surface emitting laser periodically and randomly keeps in an x or y polarization mode. Random polarization laser emitted by the vertical cavity surface emitting laser enters a polarization beam splitter through a polarization controller. The polarization controller is adjusted, so that the polarization laser coincides with two orthogonal base vector directions of a crystal in the polarization beam splitter. The polarization laser is divided into two ways by taking two orthogonal base vector directions as reference, wherein x polarization laser is output in one way, and y polarization laser is output in the other way. Two laser signals in a single polarization mode are two complementary true random password sequences. The response time of the device is up to 100 fs. The device has the ability to produce true random passwords of dozens or even hundreds of Gbit / s in real time to ensure the safety of digital communication.
Owner:TAIYUAN UNIV OF TECH
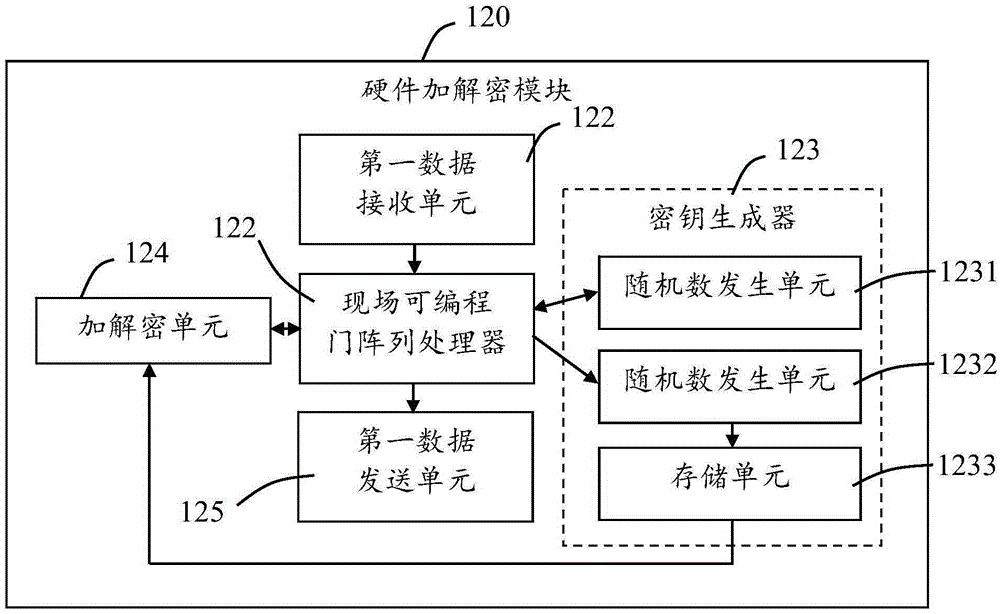
Router with hardware encryption and decryption function and encryption and decryption method of router
ActiveCN105357218AHigh speed and efficient forwardingEncryption and decryption high speedSecuring communicationComputer hardwarePlaintext
The invention provides a router with a hardware encryption and decryption function and an encryption and decryption method of the router. The router includes a routing function module and a field programming gate array-based hardware encryption and decryption module, wherein the routing function module and the field programming gate array-based hardware encryption and decryption module are connected with each other; the hardware encryption and decryption module encrypts plaintexts received by the routing function module from the outside or decrypts ciphertexts received by the routing function module from the outside; and the routing function module transmits out encrypted data generated by the encryption of the hardware encryption and decryption module or decrypted data generated by the decryption of the hardware encryption and decryption module through a wireless channel. In a work process, the routing function module of the router is not utilized to encrypt or decrypt the received plaintexts or ciphertexts, but the hardware encryption and decryption module is utilized to realize encryption and decryption, and therefore, the router can perform high-speed safe hardware encryption on the received plaintexts or ciphertexts, and at the same time, high-speed and effective forwarding of the encrypted data and the decrypted data of the router can be ensured.
Owner:台州市吉吉知识产权运营有限公司
One-way rotation type device capable of trapping mice continuously
A one-way rotation type device capable of trapping mice continuously comprises a base plate, a center shaft, a fixing stop bar, a rotating grating wheel, a one-way bearing and a partition plate. The center shaft is fixed in the center of the base plate, a mouse inlet is formed in the side wall of the base plate, the fixing stop bar is fixedly arranged on the inner wall of the base plate, the one-way bearing is arranged on the rotating grating wheel, the center shaft is sleeved with the rotating grating wheel which can only rotate inside the base plate in one direction, and the partition plate is arranged on the base plate. The one-way rotation type device capable of trapping the mice continuously has the advantages of being simple in structure, low in cost, easy and convenient to operate, absolutely safe, suitable for being used in various environment places and different seasons and climates, very high in trapping success rate, capable of trapping the mice continuously and the like, and the device is friendly to the environment.
Owner:王黎和
Quantum entanglement teleportation-based spinal cord injury nerve signal relay system and method
InactiveCN103357112AEfficient solutionThe method is matureDiagnostic recording/measuringSensorsNeuronHuman body
The invention discloses a quantum entanglement teleportation-based spinal cord injury nerve signal relay system and a quantum entanglement teleportation-based spinal cord injury nerve signal relay method, and mainly solves the problem that the spinal cord injury of a human body is not easy to repair. The method comprises the following implementation steps: irradiating pumping light on barium metaborate crystals to generate an entanglement photon pair consisting of a first photon (2) and a second photon (3), and respectively distributing the entanglement photon pair to an upper breaking point J of a spinal cord injury and a lower breaking point K of the spinal cord injury; and performing Bell states measurement on a damaged neuron cell state |phi)>1 and the first photon (2) to obtain the quantum state |phi<+>>12 of a Bell state 1, the quantum state |phi<->>12 of a Bell state 2, the quantum state |psi<+>>12 of a Bell state 3 and the quantum state |psi<->>12 of a Bell state 4, wherein a completely repaired damaged neuron cell is obtained by transmitting any quantum state to the lower breaking point K of the spinal cord injury and performing unitary transformation on the second photon (3) according to the transmitted quantum state, so that spinal cord injury nerve signals are relayed. The system and the method are convenient to operate and high in safety, and can be used for repairing the spinal cord injury nerve signals of the human body.
Owner:XIAN UNIV OF POSTS & TELECOMM
Back clamping type facing wallboard locking device
InactiveCN107893518AOutstanding and Beneficial Technical EffectsControllable securityCovering/liningsEngineeringFriction force
The invention belongs to the technical field of facing wallboard installation, in particular to a back clamping type facing wallboard locking device. The back clamping type facing wallboard locking device comprises an upper clamping element and a lower clamping element; the outer end of the upper clamping element is folded to the side of the facing wallboard to form an upper interleaf, and the upper interleaf is embedded in an upper groove of a reverse side of the facing wallboard; the outer end of the lower clamping element is folded to the side of the facing wallboard to form a lower interleaf, and the lower interleaf is embedded in an lower groove of a reverse side of the facing wallboard; the upper clamping element and the lower clamping element are fixed by a bolt; the upper interleafis matched with the lower interleaf to clamp the facing wallboard. A back clamping mode is adopted by the back clamping type facing wallboard locking device, short grooves are formed in the back of an ornament, two short grooves are correspondingly constitute two parallel surfaces or wedges, a clamp enters into the short grooves, and the pulling force is formed by the friction force produced by clamping force of the clamp and the safety of the ornament is ensured.
Owner:杨义生 +1
Temperature control type water feeder for ultrasonic endoscope detection
InactiveCN101828936AStable water temperatureSafe and stable useEnemata/irrigatorsSurgeryTemperature controlEngineering
The invention relates to a temperature control type water feeder for ultrasonic endoscope detection, which belongs to the technical field of medical appliances and comprises a water tank with a water inlet, a water outlet pipe and an air injection inlet. The temperature control type water feeder for ultrasonic endoscope detection is characterized by also comprising a heater, a temperature detector and a temperature controller, wherein the heater is used for heating water in the water tank, the temperature detector detects the temperature of water in the water tank, and the temperature controller is connected with the heater and the temperature detector. The water tank filled with water is heated by the heater, and the temperature is controlled by the temperature controller, and water can be heated to a set temperature and then heating is stopped. When the temperature is gradually lower than the set temperature as time goes on, the temperature controller restarts the heater to heat so that water is supplied at the set temperature and can keep a stable temperature during detection for a long time.
Owner:张国新
Skiing implement having a simplified structure
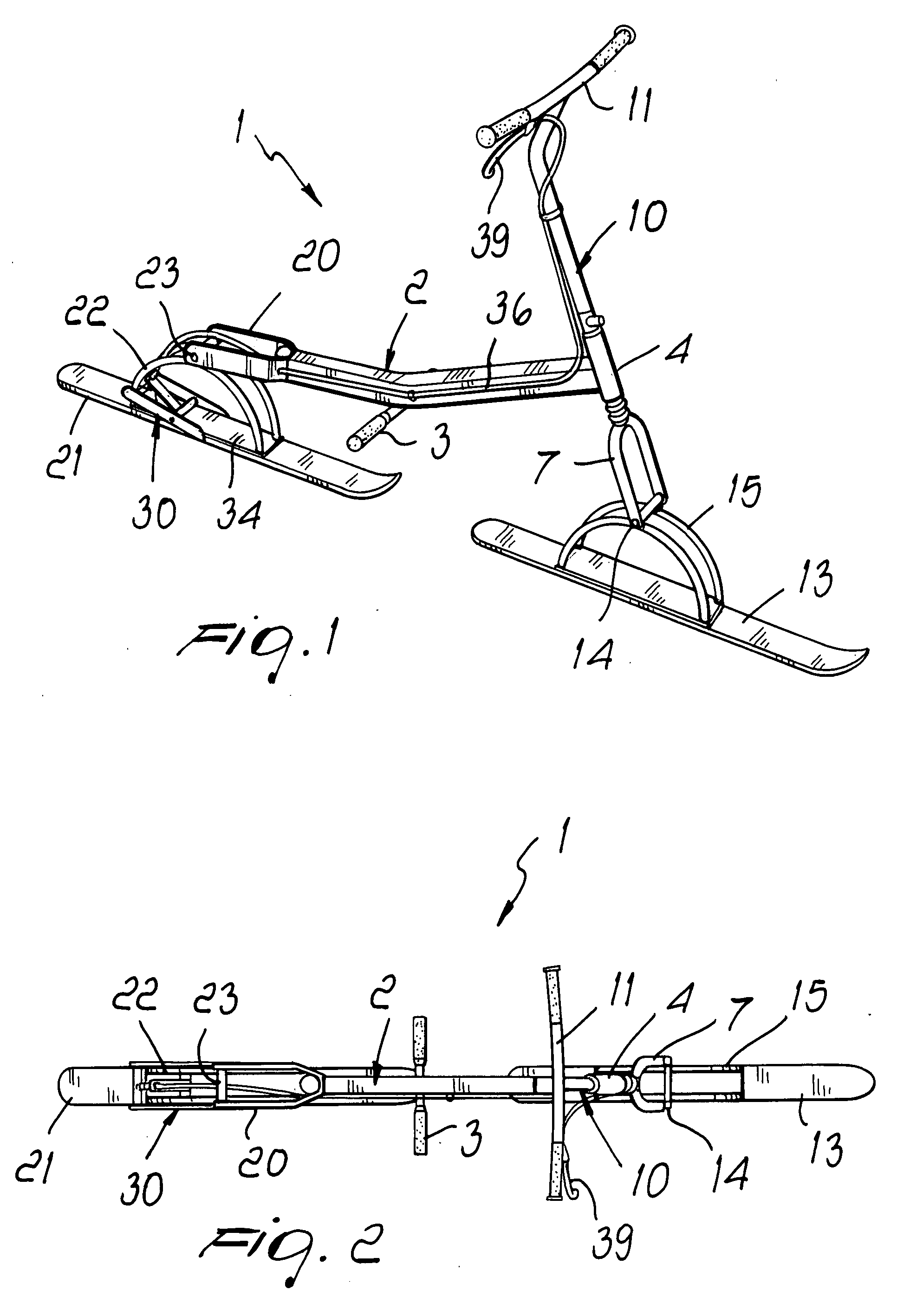
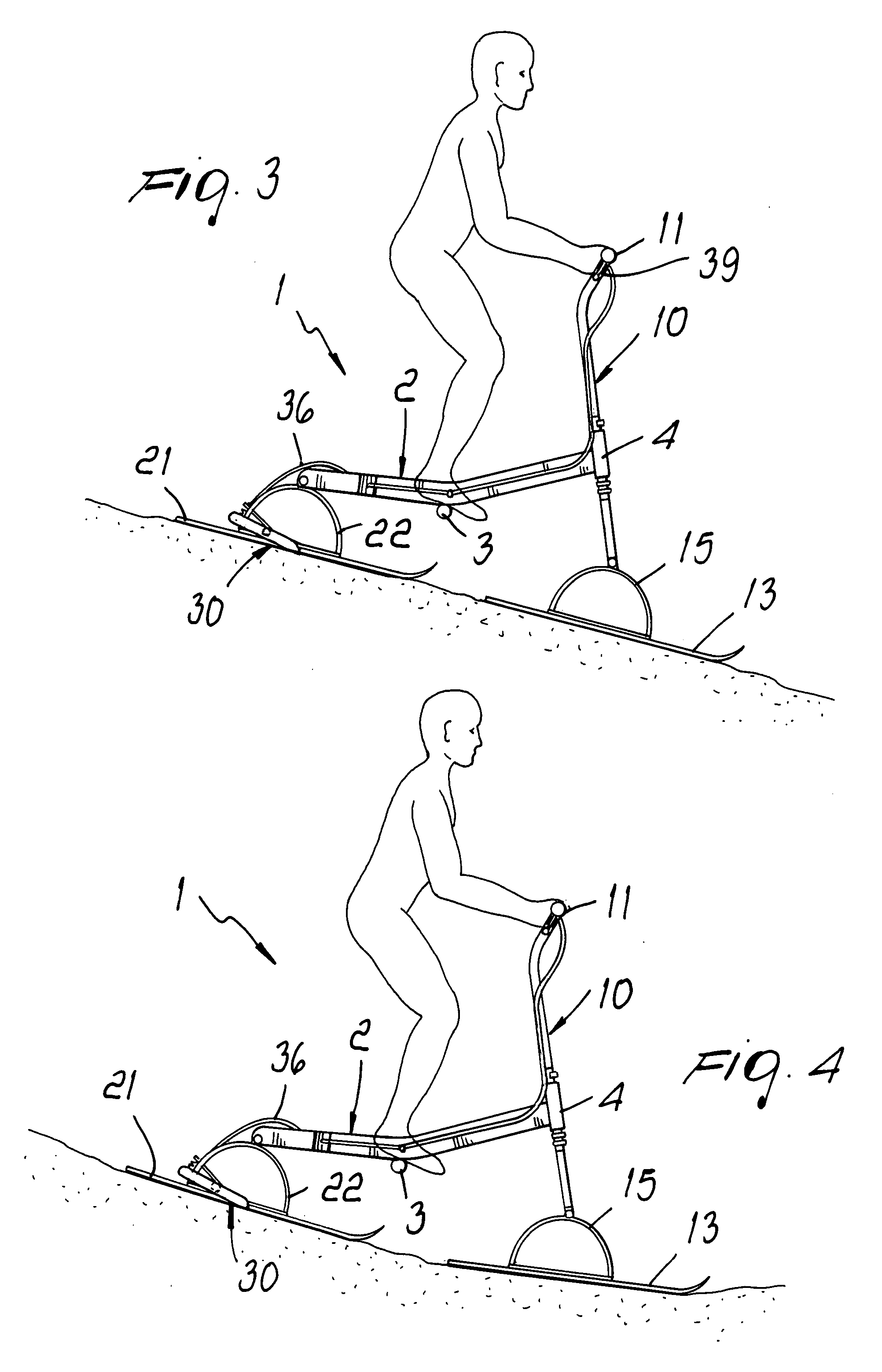
InactiveUS20090033047A1Simple structureAbsolute securityCarriage/perambulator accessoriesSledgesEngineeringHorizontal axis
A skiing implement having a simplified structure, comprising an elongated frame which defines, in a central portion, supports for the feet of a user and, at the front end, a head tube for rotary engagement with a steering column; there are also provided a front ski, which is connected to the lower end of the column, and a rear ski, which is connected to the rear end of the frame; the skis are connected so that they can oscillate about substantially horizontal axes.
Owner:EASY SKI BIKE
Network real-name authentication method and system
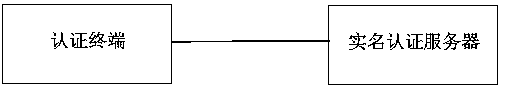
InactiveCN111200617AAccurately judge the authenticity of identityAccurate verification of identity authenticityUser identity/authority verificationEngineeringInformation security
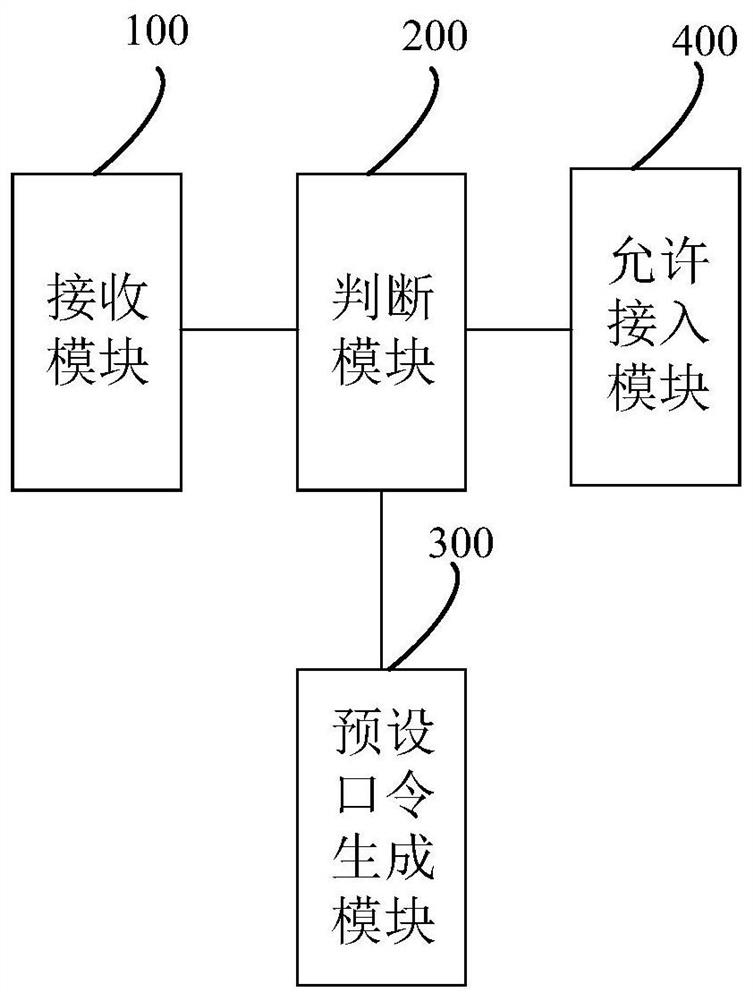
The invention relates to the field of network and information security, and in particular relates to a network real-name authentication method and system in the field of network and information security. The network real-name authentication system disclosed by the invention comprises an authentication terminal and a real-name authentication server, wherein the authentication terminal is used for compiling a password for an identity authentication digital signature, and the real-name authentication server is used for controlling access of remote network resources and providing comprehensive real-name authentication and auditing services. According to the invention, the authentication terminal is provided with a microprocessor for receiving a dynamic password sent by the real-name authentication server; the method comprises an operation rule key, a fingerprint key, a memory identity identification rule key and identity authentication fingerprint identity authentication; an instruction secret key signature module and a dynamic password operation digital signature compile a password, and send the password to the real-name authentication server to decrypt and restore the dynamic password, so as to accurately confirm the mutual identity authenticity real-name authentication of the operation rule key and the fingerprint key network activity personnel, and ensure the absolute securityof network resource authorized access.
Owner:BEIJING PASSWORD TECH
Computer information safety control system
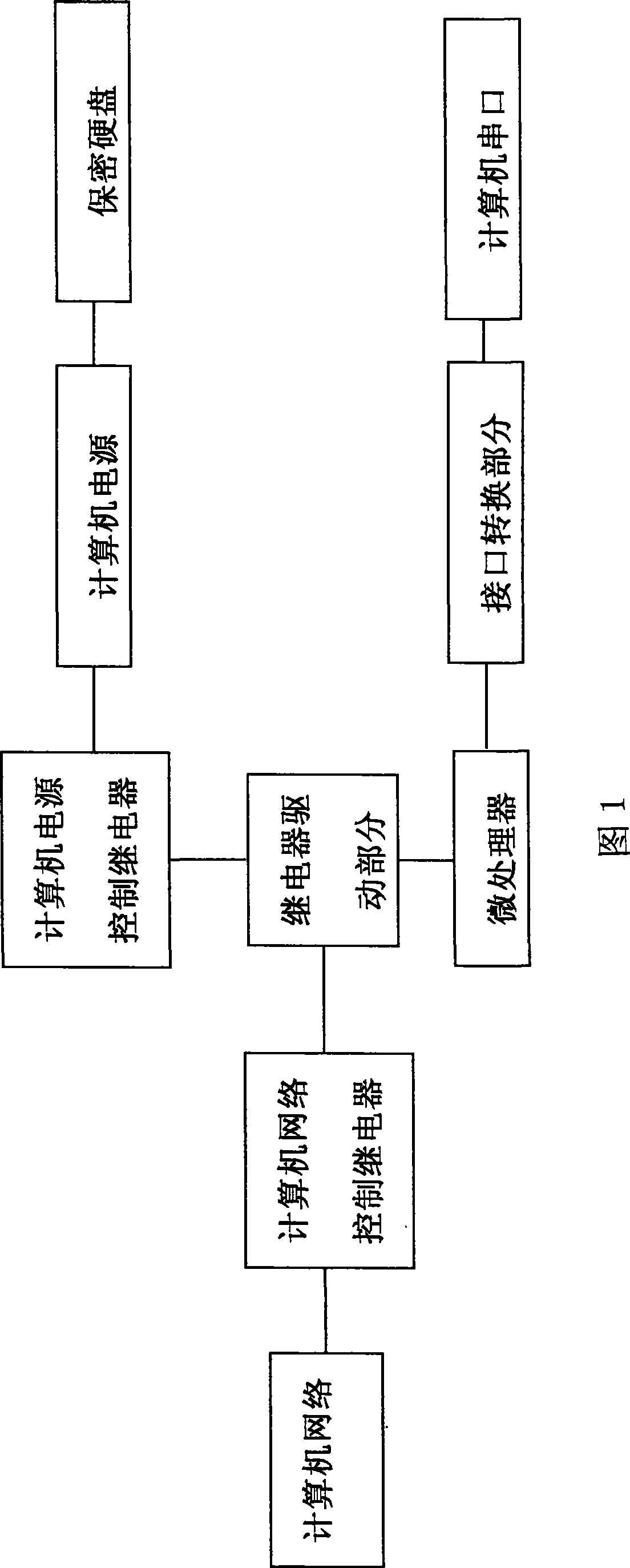
InactiveCN101414336AAbsolute securitySolve the problem of mutual control between applicationsInternal/peripheral component protectionSecuring communicationPower controlEncryption
The invention belongs to the field of computer information security control, and more particularly relates to a computer information security control system which comprises a relay drive part, a computer network control relay, a computer power control relay, a computer power, a microprocessor and an interface conversion part; one circuit of the output port of the microprocessor is connected with a user computer by the interface conversion part; another circuit of the output port of the microprocessor is connected with the input port of the relay drive part; one circuit of the output port of the relay drive part is connected with the input port of the computer network control relay and another circuit of the output port of the relay drive part is connected with the input port of the computer power control relay; the computer power control relay is used for controlling the encryption on the secret HD of the computer; the computer network control relay is used for controlling the on-off of a computer network. The computer information security control system can effectively ensure the absolute security of the information of the user computer.
Owner:吴晓明
Fingerprint identity recognition system and method for finger print image setting and verification
InactiveCN101478635AAbsolute securityEasy to operateTelevision system detailsCharacter and pattern recognitionFingerprintFingerprint image
The present invention discloses a fingerprint identity recognizing system and a setting and recognizing method of fingerprint identity image thereof. The recognizing method comprises the following steps: activating power source for entering a fingerprint identity recognition reminding information interface; sensing the fingerprint by a fingerprint recognizing sensor for obtaining fingerprint image information; comparing the fingerprint image information with fingerprint identity recognizing image information, confirming the matching of fingerprint image information and the fingerprint identity recognizing image information with each other, and finishing the identity recognizing. The fingerprint identity recognizing method provided by the invention guarantees the absolute safety of user in using the electronic product and has the advantage of simple operation through adopting a mode which comprises the following steps: sensing the fingerprint with the fingerprint recognizing sensor for obtaining fingerprint image information; comparing the fingerprint image information with fingerprint identity recognizing image information, confirming the matching of fingerprint image information and the fingerprint identity recognizing image information with each other, and finishing the identity recognizing.
Owner:KONKA GROUP
Medical image data processing method, device and system and storage medium
PendingCN112542229AHigh riskImprove securityStill image data indexingMedical imagesMedical imaging dataData acquisition
The invention relates to a medical image data processing method, device and system and a storage medium. The method comprises the steps that a terminal collects medical image data and a human face image of a target main body, binds the medical image data and the human face image of the target main body to obtain a mapping relation between the medical image data and the human face image, and storesthe medical image data, the human face image and the mapping relation of the target main body. According to the method, medical image data and face images of a target main body are acquired by data acquisition equipment based on the same terminal, and the medical image data and the face images are stored in an associated manner, so that the stored face images are in one-to-one correspondence withthe medical image data of the target main body; when the target main body subsequently retrieves and accesses the medical image data, the medical image data can be authenticated and acquired throughthe face image, so that the anti-risk capability and the safety of the medical image data of the target main body are improved, and the absolute safety of the medical image data of the target main body is effectively guaranteed.
Owner:WUHAN UNITED IMAGING HEALTHCARE CO LTD
Device for aircraft simulation catapulting test
The invention relates to the field of aircraft simulation catapulting tests, specifically to a device for an aircraft simulation catapulting test. The device for the aircraft simulation catapulting test comprises a control cabinet, a test frame and a platform truck, wherein the control cabinet is used for controlling; the test frame is matched with the control cabinet; the platform truck is arranged at the lower end of the test frame; a hooking device used for hooking an aircraft is arranged on the test frame; a simulation device used for realizing the aircraft simulation catapulting test is also arranged on the test frame; and a hydraulic system and a pneumatic system which are used for realizing hydraulic and pneumatic functions are embedded in the control cabinet. A foundation bolt is poured with ground cement to realize the stability of the test frame during testing; and meanwhile, the stability is improved under the coordination of a shock absorption mechanism so that the absolutesafety in the testing process is guaranteed; in order to limit the contracting velocity of an acting cylinder, the stability, safety and reliability of the acting cylinder in the whole contracting process can be guaranteed under the coordination of a throttle valve.
Owner:芜湖航翼集成设备有限公司
Network security controller of computer
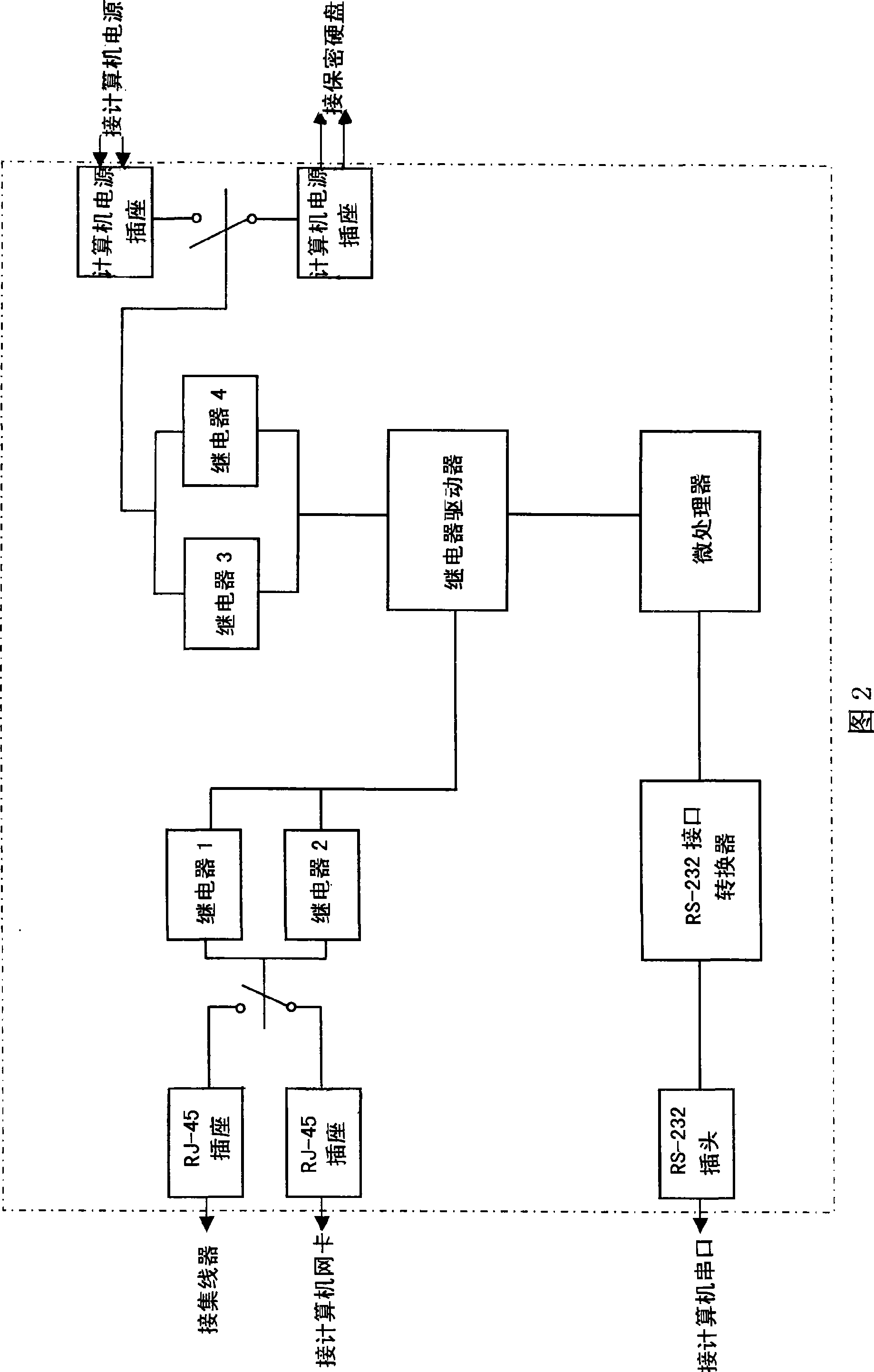
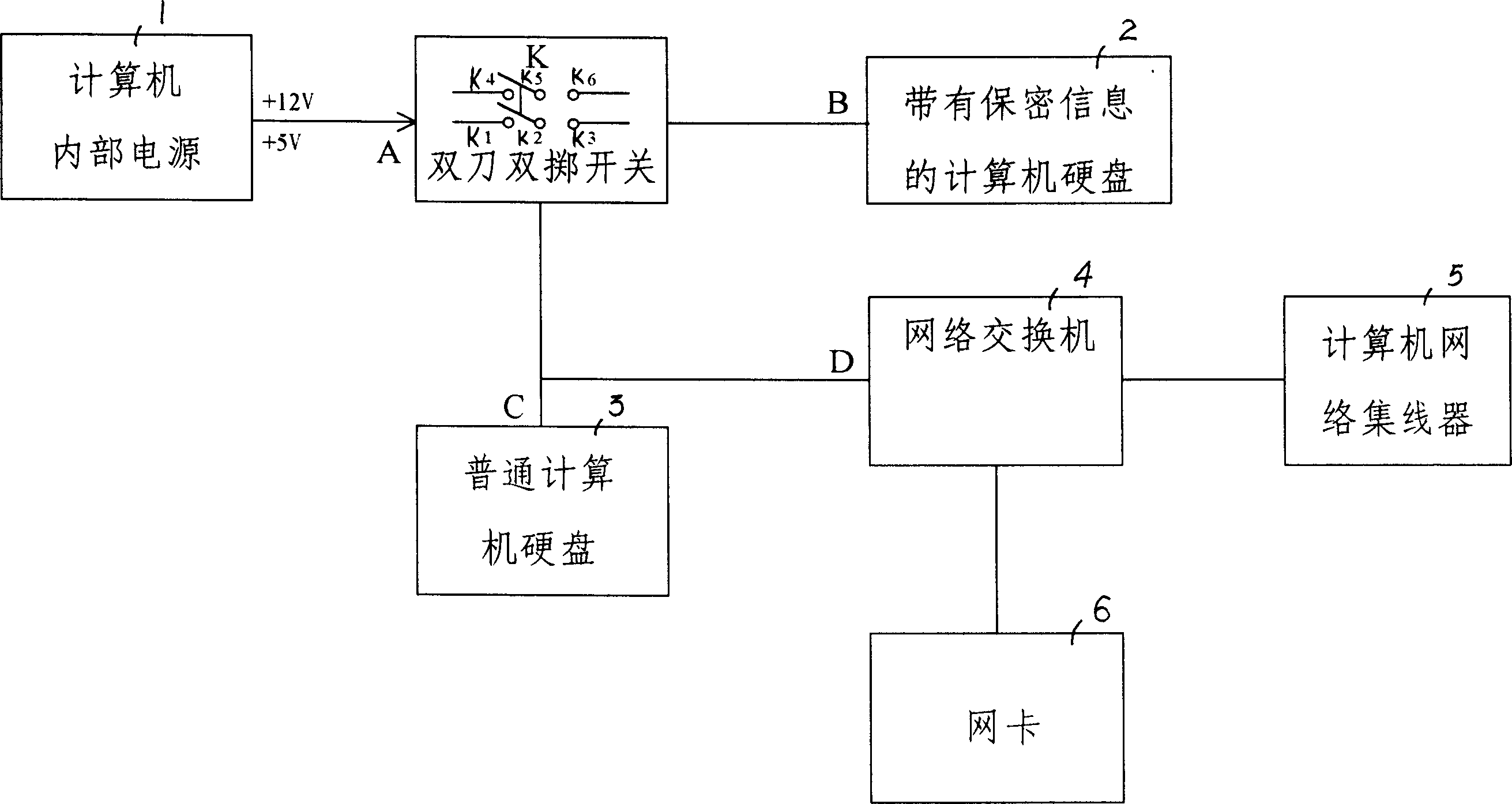
InactiveCN1779593AAbsolutely safeProtection securityDigital data processing detailsData switching networksHardware structureNetwork switch
A safety controller of computer network consists of computer internal power supply, computer hard disc with secret information, normal computer hard disc, network switching board, computer network concentrator, network card and double ¿C point double ¿C throw switch. It is featured as connecting normal computer hard disc to network card, computer network concentrator separately through network switching board, connecting computer internal power supply to normal computer hard disc through one double port of double ¿C point double ¿C throw switch and connecting another double port to computer hard disc with secret information.
Owner:吴晓明
Onboard platform supporting system for heading machine
InactiveCN112253203ADo not block the line of sightSmall space ratioMine roof supportsAnchoring boltsSupporting systemControl engineering
The invention belongs to the technical field of excavating equipment, and discloses an onboard platform supporting system for a heading machine. The onboard platform supporting system for the headingmachine is provided with an onboard platform supporting device and a platform pushing and conveying structure, wherein the onboard platform supporting device is fixedly arranged at the upper part of acutting part; and the platform pushing and conveying structure is movably arranged at the lower end of the onboard platform supporting device and is used for achieving movement of the onboard platform supporting device. The platform supporting device is retracted and folded to be placed above the cutting part; the space occupation ratio is very small; during operation, edge scraping is avoided, and the vision of a driver is not hindered; the platform supporting device can move along with heading equipment to achieve an onboard effect; and practicability is high. The function requirement of building an operation platform in the air is met, and the operation can be fast realized; and large-area coverage is achieved in front and lateral sides of the cutting part of the heading machine, and the adaptability is high.
Owner:山西晟特恒采矿工程机械有限公司
Real estate data encryption system based on quantum communication
PendingCN107579822AAbsolute securityPrevent accidental releaseKey distribution for secure communicationClient-sideComputer security
The invention relates to the technical field of quantum communication, particularly a real estate data encryption system based on the quantum communication. The system comprises an information collection and transmission module and a data storage management and control module. The information collection and transmission module comprises a collection tool, a database server and a quantum server. The collection tool and the quantum server are connected through two channels. The quantum server is connected with the database server. The data storage management and control module comprises a KMS quantum key management server, the quantum server and a client side for searching real estate information. The database server and the client side are connected through the two channels. Quantum gateways are connected with the KMS quantum key management server. The quantum gateways are connected with the quantum server. According to the real estate data encryption system based on the quantum communication, the information is prevented from being leaked unconsciously and accidently, and if the information is artificially leaked, tracing can be carried out after the event, and a person in charge can be confirmed.
Owner:浙江神州量子通信技术有限公司
Blow-Fill-Seal Fully Automatic Aseptic Production Process for Water Needle Injection
ActiveCN105291406BDoes not affect taking medicineImprove the shortcomings of not being easy to punctureBottle-handling machinesLiquid bottlingPunchingBottle
The invention discloses a full-automatic aseptic production technology for blowing, filling and sealing of a water needle injection medicament. The full-automatic aseptic production technology comprises the production technology steps that firstly, raw materials are sterilized; secondly, impurity removing is conducted on the raw materials; thirdly, material melting is conducted; fourthly, filling and forming are conducted; fifthly, die opening is conducted; sixthly, punching and slitting are conducted; and seventhly checking is conducted. The materials are sterilized and disinfected in the heating step and the material melting step in the production technology, and the use risk of the materials is lowered; during forming and filling, extruding, bottle blowing, local cooling, filling, sealing and die opening are conducted, blowing, filling and sealing are combined, the bottle forming time is short, pollution to liquid medicine from microorganisms and particles in air in a sealed environment is avoided, and especially the defect of a traditional mode is overcome through the ultra-low-temperature filling technology. Meanwhile, aseptic air is used in the whole process, pollution of microorganisms in air is effectively avoided, and medicine quality is ensured greatly.
Owner:HUBEI KELUN PHARMA
Back-clamp-type facing wallboard locking device
PendingCN109537842AOutstanding and Beneficial Technical EffectsAbsolute securityCovering/liningsSupport pointFriction force
The invention belongs to the technical field of facing wallboard installing, and particularly discloses a back-clamp-type facing wallboard locking device. The back-clamp-type facing wallboard lockingdevice comprises an upper clamping piece and a lower clamping piece, the outer end of the upper clamping piece is turned towards one side of a facing wallboard or straightly extends to form an upper clamping sheet, and the upper clamping sheet is embedded into an upper groove in the back face of the facing wallboard; the outer end of the lower clamping piece is turned towards one side of the facing wallboard or straightly extends to form a lower clamping sheet, and the lower clamping sheet is embedded into a lower groove of the back face of the facing wallboard; the upper clamping piece and the lower clamping piece are fixed with a bolt through a structural supporting point, and the upper clamping sheet is matched with the lower clamping sheet to clamp the facing wallboard. The back-clam-type facing wallboard locking device adopts a back-clamp mode, short grooves are formed in the back face of a decorating material, and correspond to form two parallel faces or wedge-shaped, the clamping sheets enter the grooves, anti-drawing force is formed through friction force generated by clamping force of the clamping pieces, and the safety of the decorating material is guaranteed.
Owner:杨义生 +1
Special network security supervision system for enterprises
InactiveCN110708340AImprove securityComprehensive strategyData switching networksPrivate networkInformation resource
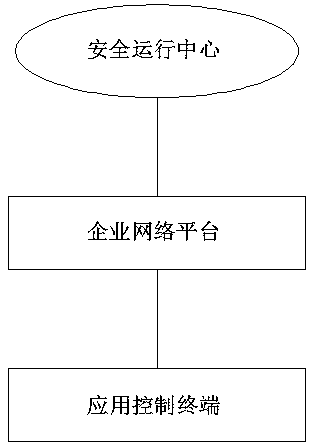
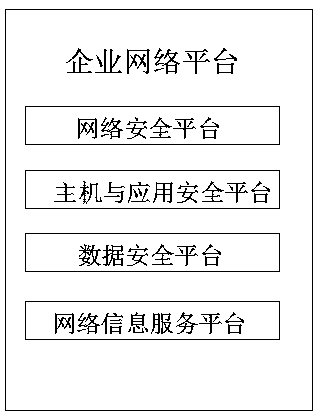
The invention discloses a special network security supervision system for enterprises, which is characterized by comprising a security operation center, an enterprise network platform and an application control terminal, the safety operation center can formulate comprehensive safety configuration and strategies for enterprises, reasonably plan and use information resources and monitor an enterprise network in real time, and the enterprise network platform can monitor all operation data information in the enterprise private network in real time. In the present invention, the enterprise special-purpose network safety supervision system adopts a structure system of one center, four platforms and five control terminals. The supervision effect of step-by-step permeation of the enterprise private network is realized; relatively unified network supervision of the enterprise private network is also realized, abnormal transmission and exchange of data in the network and in the network can be prevented through real-time monitoring of various network access devices and control terminals in the enterprise private network, and data loss or leakage caused by loopholes of the enterprise private network is prevented.
Owner:深圳市高德信通信股份有限公司
Intelligent government affair service analysis platform based on big data technology
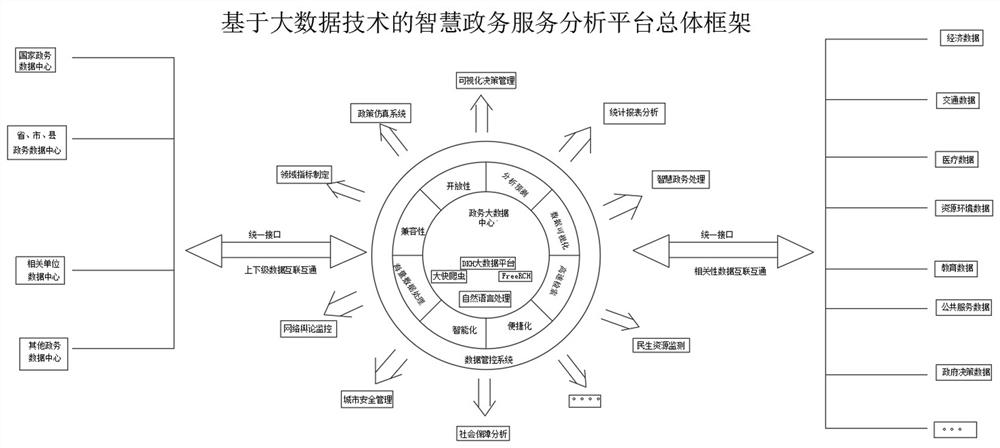
PendingCN114756567AEasy to manageEasy to masterData processing applicationsDatabase management systemsAnalysis dataData acquisition
The invention discloses an intelligent government affair service analysis platform based on a big data technology. The intelligent government affair service analysis platform based on the big data technology is a comprehensive government affair big data analysis platform integrating government affair big data processing, online analysis, data mining, data model and visual display. An OLPA visual analysis function based on Hadoop storage, a data cube and calculation is provided, so that a user can complete multi-dimensional and all-around data analysis within a sub-second time through simple operation of dragging, and an analysis result is displayed in various visual modes. The platform mainly comprises a data acquisition and sharing unit, a mass data storage and management unit, a data calculation and analysis unit, a data association and concentration unit, a big data analysis and mining unit, an enterprise / personal atlas unit and an application demand development unit. The intelligent government affair service analysis platform based on the big data technology has the advantages of high safety, convenience, rapidness and high working efficiency.
Owner:宁夏希望信息产业股份有限公司
Nanometer biological antistaling agent and preparation method thereof
InactiveCN1864493ANo pollutionNo pollution in the processBiocideAnimal repellantsPreservativeBiology
The present invention is one kind of nanometer biological preservative and its preparation process, and the nanometer biological preservative as one kind of green preservative is used mainly for preservation of grains and may be also used for medicine, books, filings, cultural relic, etc. The nanometer biological preservative may be used in ensuring the safety effectively and has wide application range.
Owner:张永锋
Network real-name authentication method and system
InactiveCN111245865AAccurately judge the authenticity of identityAccurate verification of identity authenticityUser identity/authority verificationInternet privacyDigital signature
The invention relates to the field of network and information security, in particular to a network real-name authentication method and system in the field of network and information security. The system used by the network real-name authentication method disclosed by the invention comprises an authentication terminal and a real-name authentication server. The method comprises the following operation steps: an identity identification rule secret key operation step; a step of identity authentication fingerprint operation; a step of human behavior operation; and a step of performing network real-name authentication operation through a identity identification rule key, an identity authentication fingerprint and human behaviors. According to the invention, an identity identification rule key, an identity authentication fingerprint and human behaviors are adopted, rule keys and a fingerprint key of the authentication terminal, a memory identity identification rule key, identity certificate fingerprint identity authentication and a dynamic password digital signature compilation cipher are operated, the cipher is sent to the real-name authentication server to decrypt and restore a dynamicpassword to perform real-name authentication, and absolute security of network resource authorized access is effectively guaranteed.
Owner:BEIJING PASSWORD TECH
A high-performance web image loading and display system based on html5
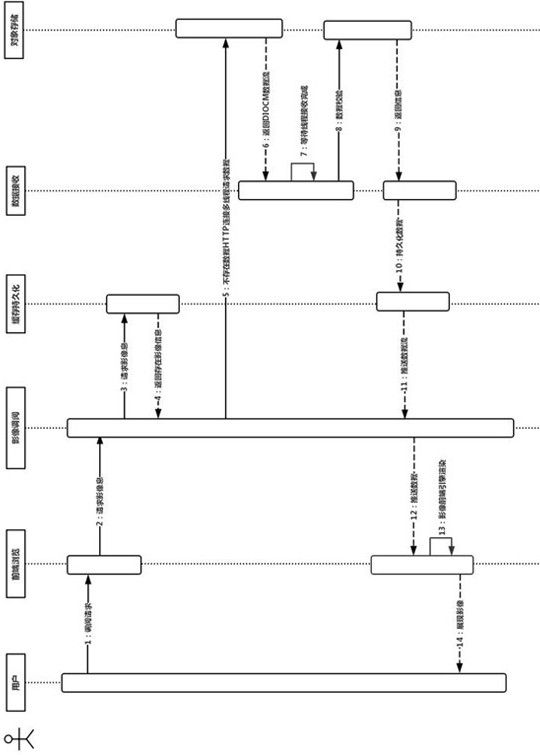
The invention relates to medical image loading and display technology, in particular to a high-performance Html5-based Web image loading and display system. The present invention realizes the efficient loading of DICOM data from the cloud to the front-end browser page through multiple loading methods. Different loading modes have their own advantages, which can meet the data retrieval requirements in different scenarios, and can also improve the efficiency of data loading through mixed methods. , The image archiving module realizes the ability of DICOM data transmission and sharing, completes the quick access to data, and can realize the sharing of image data, which is convenient for the integration of other third-party hospital systems.
Owner:中电万维信息技术有限责任公司
Method and system for network access authentication based on quantum key
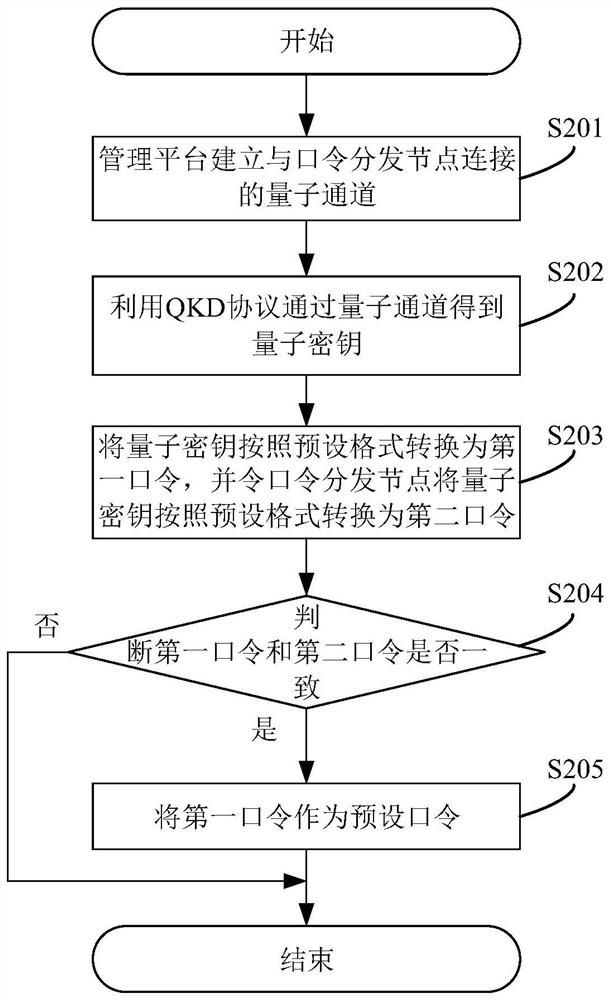
ActiveCN108768640BAbsolute securityImprove securityKey distribution for secure communicationAccess networkPassword
This application discloses a method for network access authentication based on quantum keys, including: the management platform receives the user password sent by the terminal; judging whether the user password is consistent with the preset password; wherein, the preset password is based on the management platform and the password The password generated by the distribution node using the quantum key obtained by the QKD protocol; if so, the terminal is allowed to access the network. In the technical solution provided by this application, the preset password is generated by using the quantum key obtained by the management platform and the password distribution node using the QKD protocol. Since the quantum key has absolute security and cannot be copied, the quantum key is generated based on the quantum key. The preset password is also absolutely safe, which greatly improves the security of network access authentication. At the same time, the present application also provides a quantum key-based network access authentication system, server and computer-readable storage medium, which have the above-mentioned beneficial effects.
Owner:KEHUA DATA CO LTD
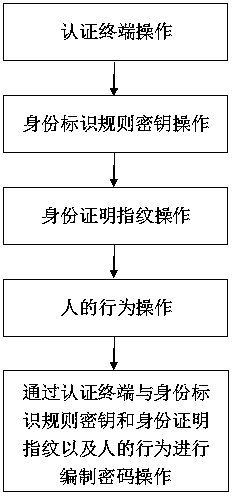
Password compiling method based on authentication terminal
InactiveCN111200616AAuthentic and reliable authenticationAbsolute securityUser identity/authority verificationFingerprintInternet privacy
The invention relates to the field of network and information security, and in particular relates to a password compiling method based on an authentication terminal in the field of network and information security. The method comprises the operation steps of authenticating terminal operation, identity identification rule secret key operation, identity authentication fingerprint operation, human behavior operation, and password compiling through the authentication terminal, the identity identification rule key, the identity certificate fingerprint and the behavior of the person. According to the password compiling method based on the authentication terminal, which is provided by the invention, the authentication terminal compiles a password based on the operation rule key and the fingerprint key through a microprocessor, the memory identity identification rule key and the identity certification fingerprint identity authentication and dynamic password digital signature; mutual identity authenticity of network activity personnel who compile the password operation rule key and the fingerprint key can be accurately confirmed; real and reliable identity authentication is realized; and absolute security of network resource authorized access is guaranteed.
Owner:BEIJING PASSWORD TECH
One-way rotation type device capable of trapping mice continuously
A one-way rotation type device capable of trapping mice continuously comprises a base plate, a center shaft, a fixing stop bar, a rotating grating wheel, a one-way bearing and a partition plate. The center shaft is fixed in the center of the base plate, a mouse inlet is formed in the side wall of the base plate, the fixing stop bar is fixedly arranged on the inner wall of the base plate, the one-way bearing is arranged on the rotating grating wheel, the center shaft is sleeved with the rotating grating wheel which can only rotate inside the base plate in one direction, and the partition plate is arranged on the base plate. The one-way rotation type device capable of trapping the mice continuously has the advantages of being simple in structure, low in cost, easy and convenient to operate, absolutely safe, suitable for being used in various environment places and different seasons and climates, very high in trapping success rate, capable of trapping the mice continuously and the like, and the device is friendly to the environment.
Owner:王黎和
Anti-slipping type yoga floor mat
The invention relates to a non-slip yoga floor mat, which comprises the following components in parts by weight: 90-100 parts of neoprene rubber; 9-18 parts of natural rubber; 3-7 parts of sodium bicarbonate; 1-4 parts of zinc borate 2-7 parts of zinc oxide; 1-3 parts of stearic acid; 3-8 parts of white carbon black; 0.2-0.5 parts of antioxidant; 1-1.5 parts of accelerator; 30-89 parts of polyether polyol; talcum powder 50‑80 parts; 0.1‑0.2 parts of diphenyldichlorosilane; 3‑8 parts of butanediol. The advantages of the present invention are: the present invention can significantly improve the flame-retardant performance of the existing neoprene floor mat, provide absolute safety and resilience, and good elasticity can play a good role in protecting the leg joints of athletes. It effectively avoids sports injuries, has strong wear resistance and better anti-slip performance, has the functions of stabilizing the size of the field and prolonging the service life, and the performance is more stable.
Owner:南通绿美佳塑胶有限公司
Drawing-out computer hardware interface with dust-proof and short-circuit-proof functions
InactiveCN109494518AEasy to useGuaranteed cooling effectCouplings bases/casesComputer periphery connectorsEngineeringComputer engineering
The invention discloses a drawing-out computer hardware interface with dust-proof and short-circuit-proof functions, which comprises an interface main body and a computer baseboard, wherein the interface body is composed of a shell arranged on the side surface of the interface main body and a fixing plate arranged on the side surface of the shell; and the fixing plate is nested in the shell. According to the drawing-out computer hardware interface with dust-proof and short-circuit-proof functions, as a sliding groove and a slider are arranged, the slider moves easily in the sliding groove to draw out the hardware interface, residual dust can be cleaned conveniently, and thorough circuit inspection is also facilitated; as a dust-proof cover is arranged, entering of dust can be effectively reduced, normal use and cooling of the interface are ensured, radiation is reduced, and the body health of a user is maintained; and as a fuse and a protective sheath are arranged, short circuit can beprevented, and the absolute safety of the interface and the user is ensured.
Owner:古天华
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com