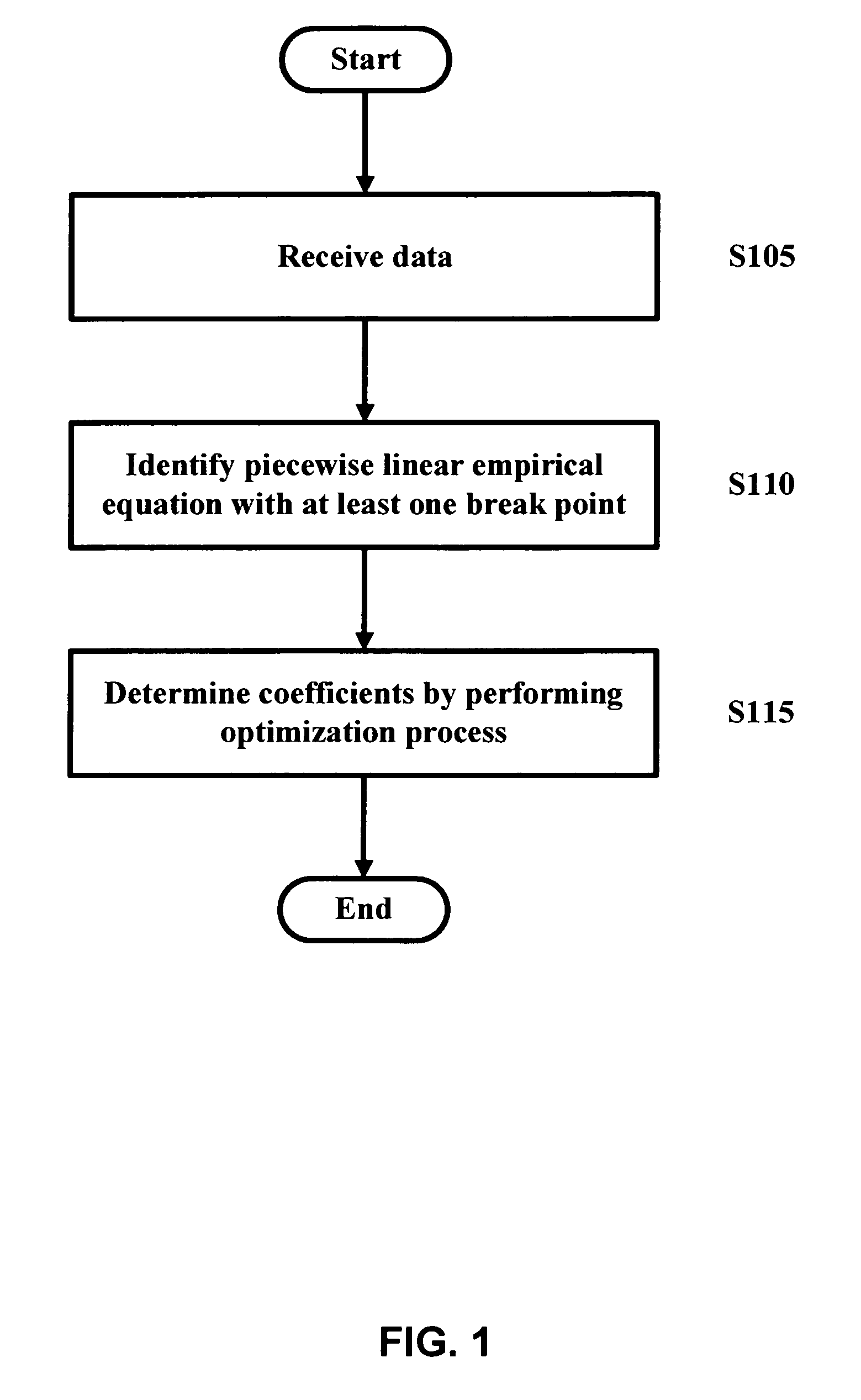
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
1414 results about "Breaking point" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
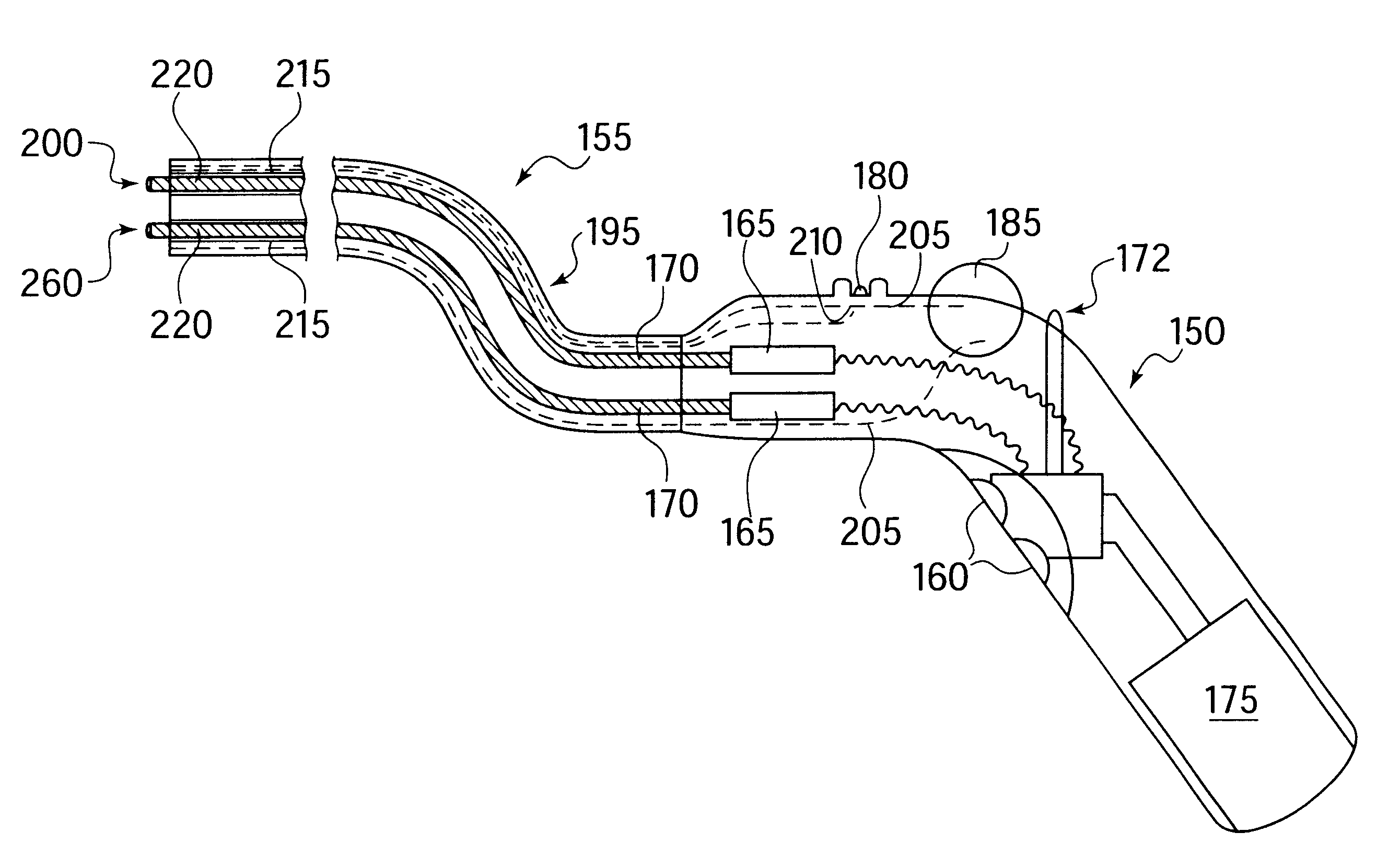
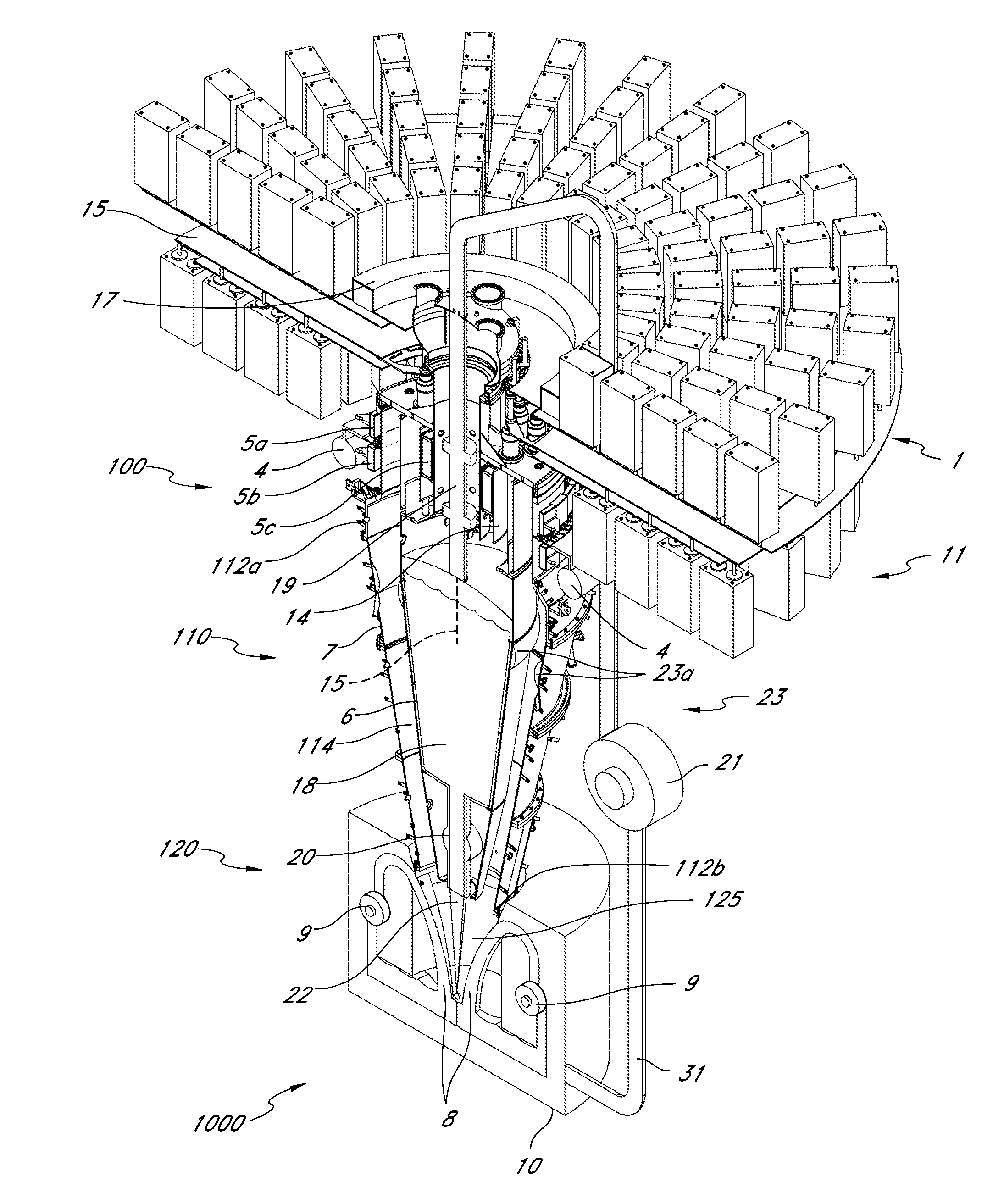
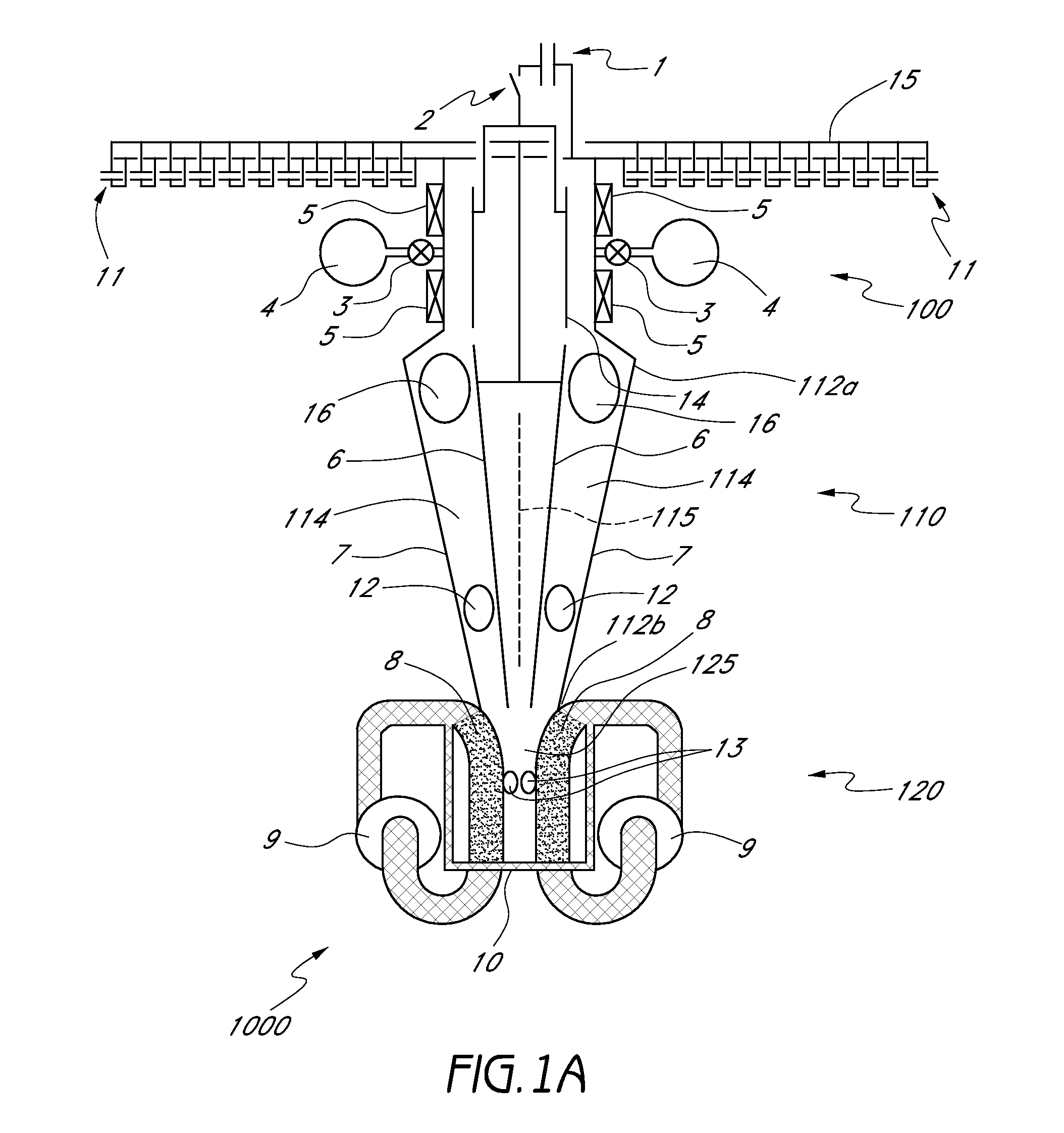
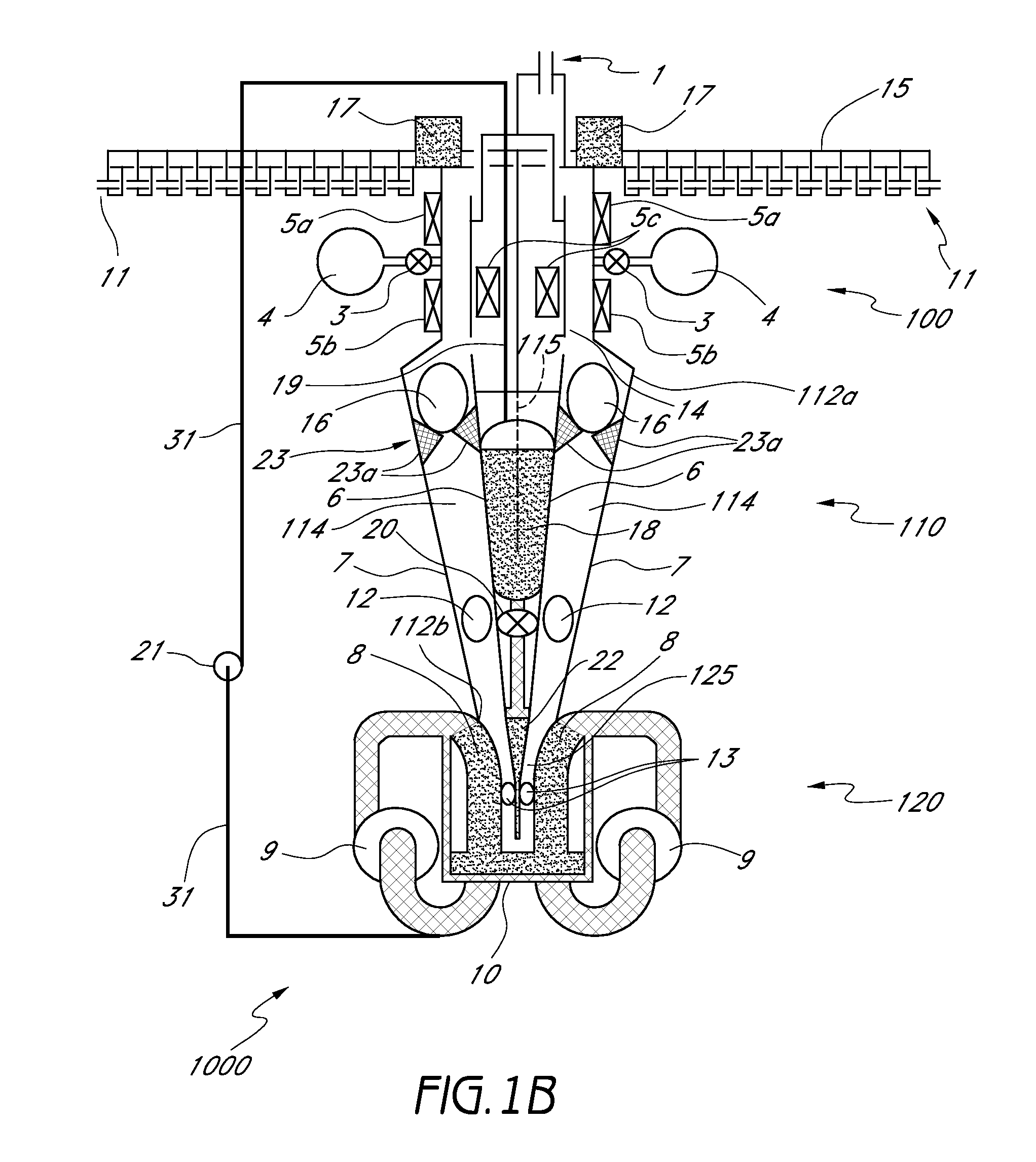
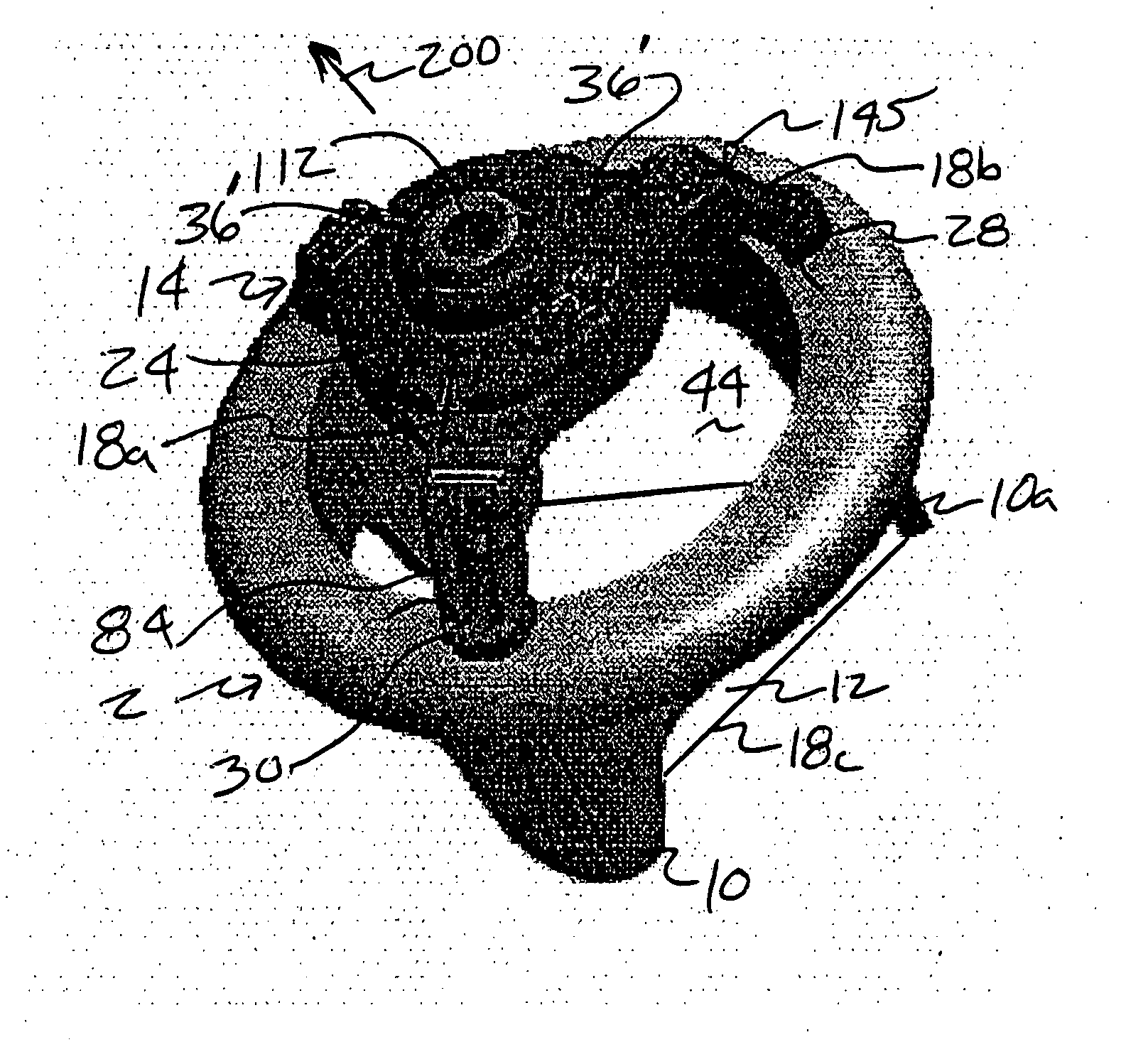
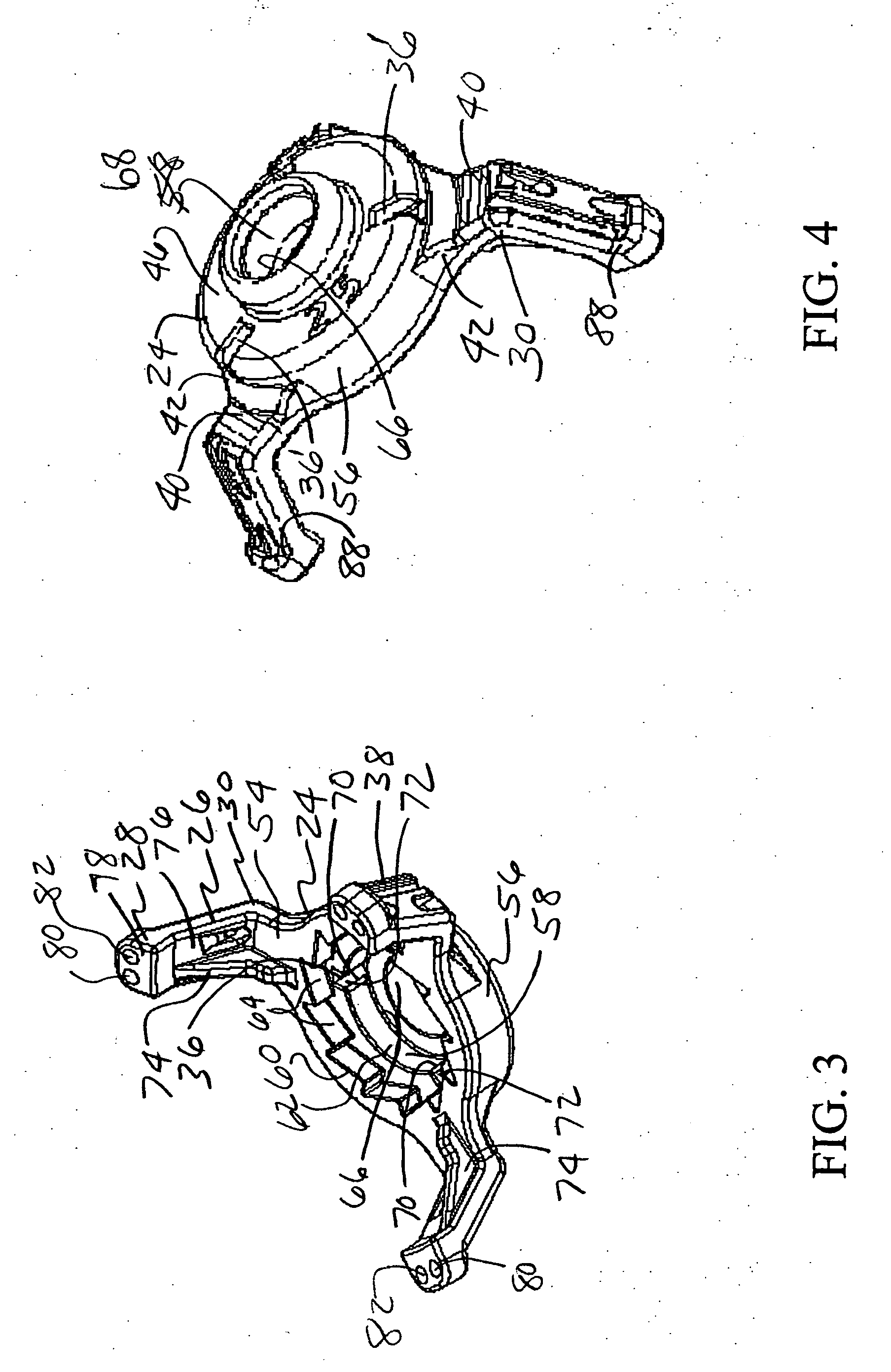
Fluid delivery device for use with anastomosing resecting and stapling instruments
A fibrin injection mechanism for use in combination with an anastomosing and stapling attachment for an electromechanical device driver comprises a cylindrical dispensing chamber adjacent the cylindrical blade of the attachment and containing a sac filled with fibrin, a plurality of channels extending within the blade communicating between the dispensing chamber and the cutting edge of the blade, such that when the turning drive shaft is activated, the staple driver of the attachment moves forward to push a plurality of staples through corresponding staple ports and against the anvil of the attachment to pass through and staple together the target tissue, while the blade driver of the attachment moves forward to cut the unwanted residual tissue (post stapling), while a plunger (delivery) driver moves forward through the dispensing chamber to compress the sac to its break point, releasing the fluid medication into the dispensing chamber, and eventually pushing the medication though the channels to deliver the fibrin to the cutting edge of the blade and thus to the site of the newly stapled target tissue to accelerate the healing process.
Owner:DORROS GERALD M D
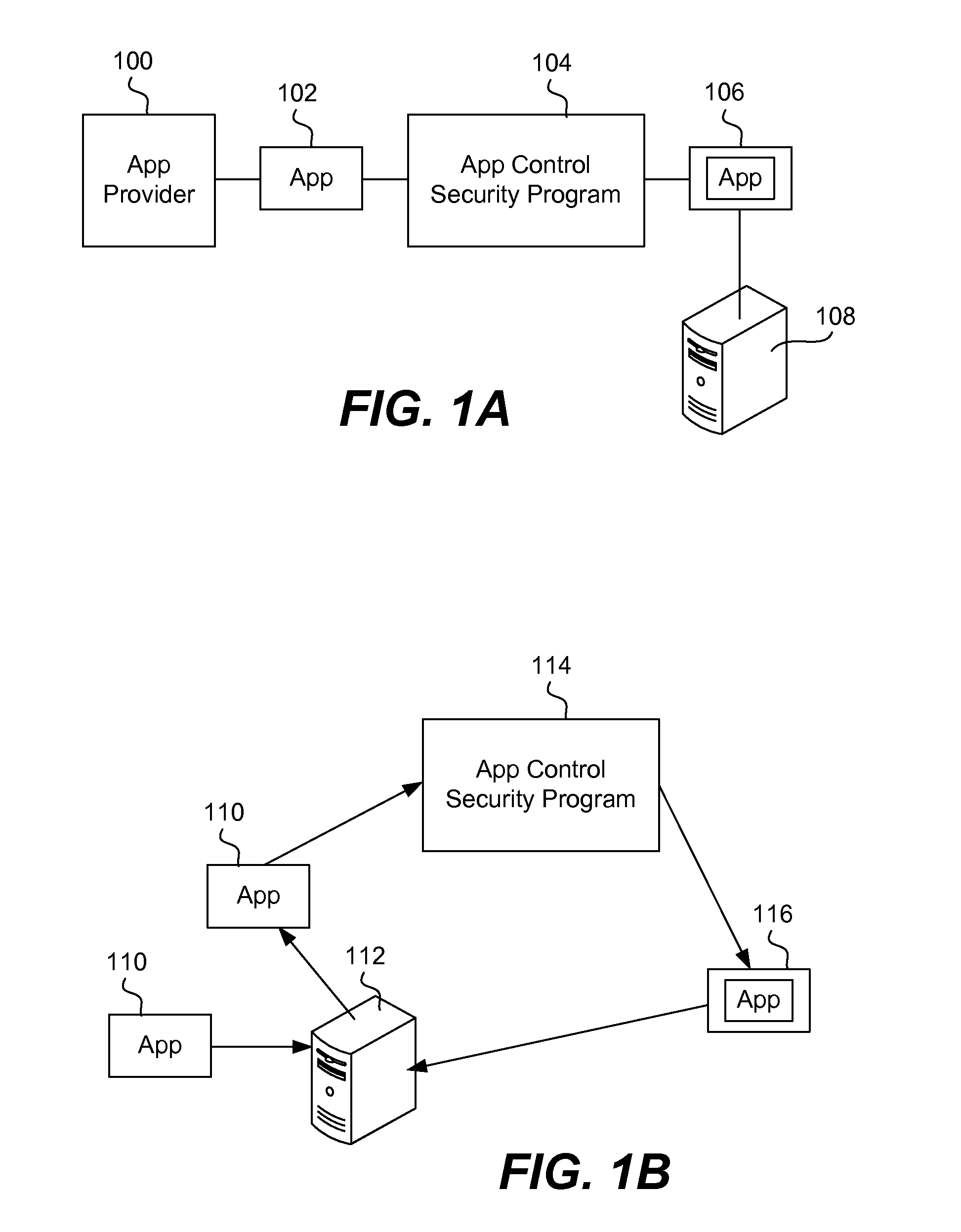
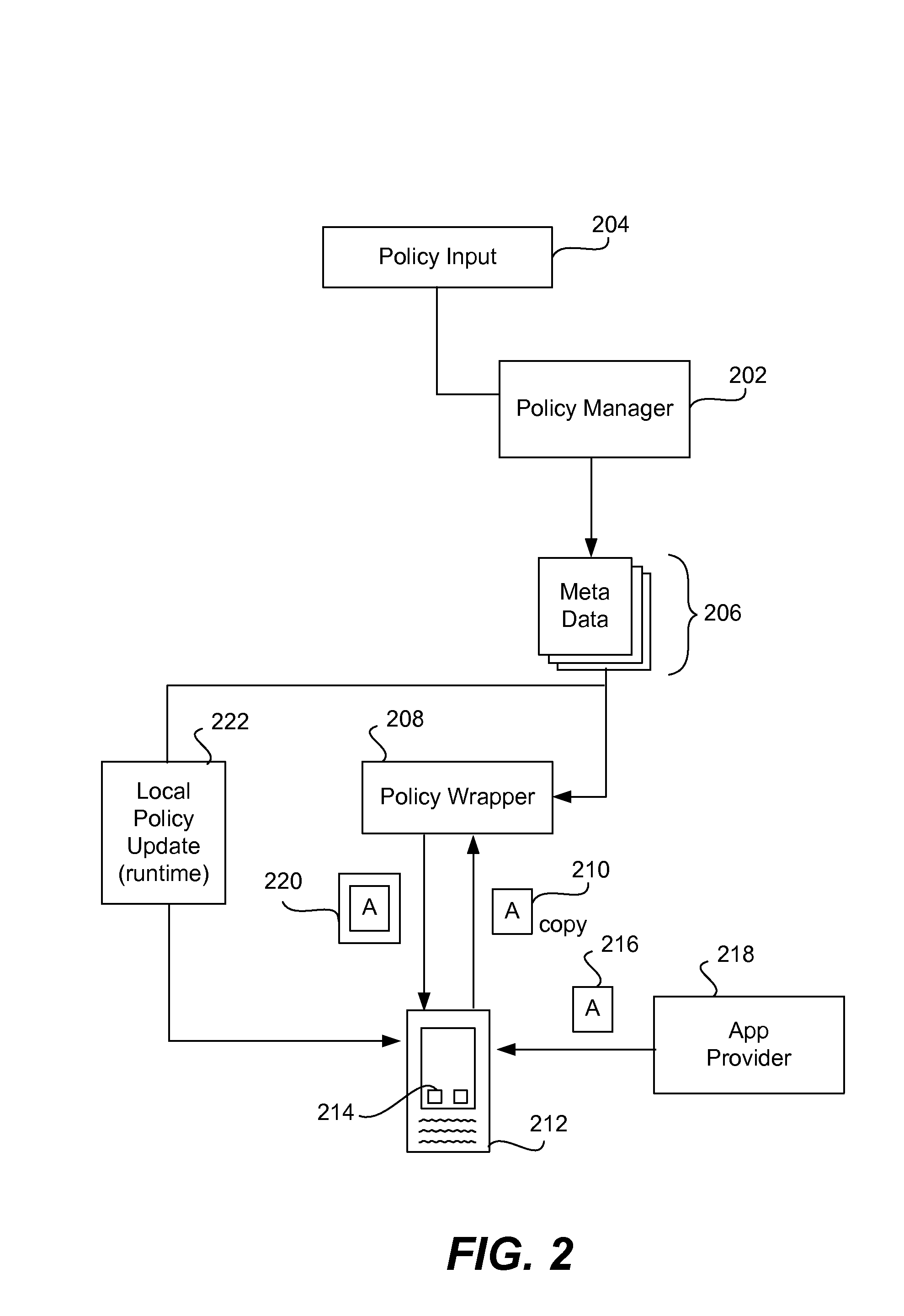
Secure execution of unsecured apps on a device
ActiveUS20120304310A1Digital data processing detailsAnalogue secracy/subscription systemsSecurity functionBreaking point
An app is secured on a mobile device by being deconstructed or unbundled into multiple modules, where a module is a segment of app code that performs a particular function. It is then determined which modules from the multiple modules perform some type of security function, for example, a function dealing with confidential or security-related data. These modules, forming a group of modules, are loaded into a trusted execution environment. The app is then re-bundled so that it has the first plurality of modules and the second plurality of modules. The app executes in a manner where the high security functions execute so that break points cannot be inserted into the app code. The re-bundling is done automatically in an app security wrapping process. Security constraints are added to the app.
Owner:BLUE CEDAR NETWORKS INC
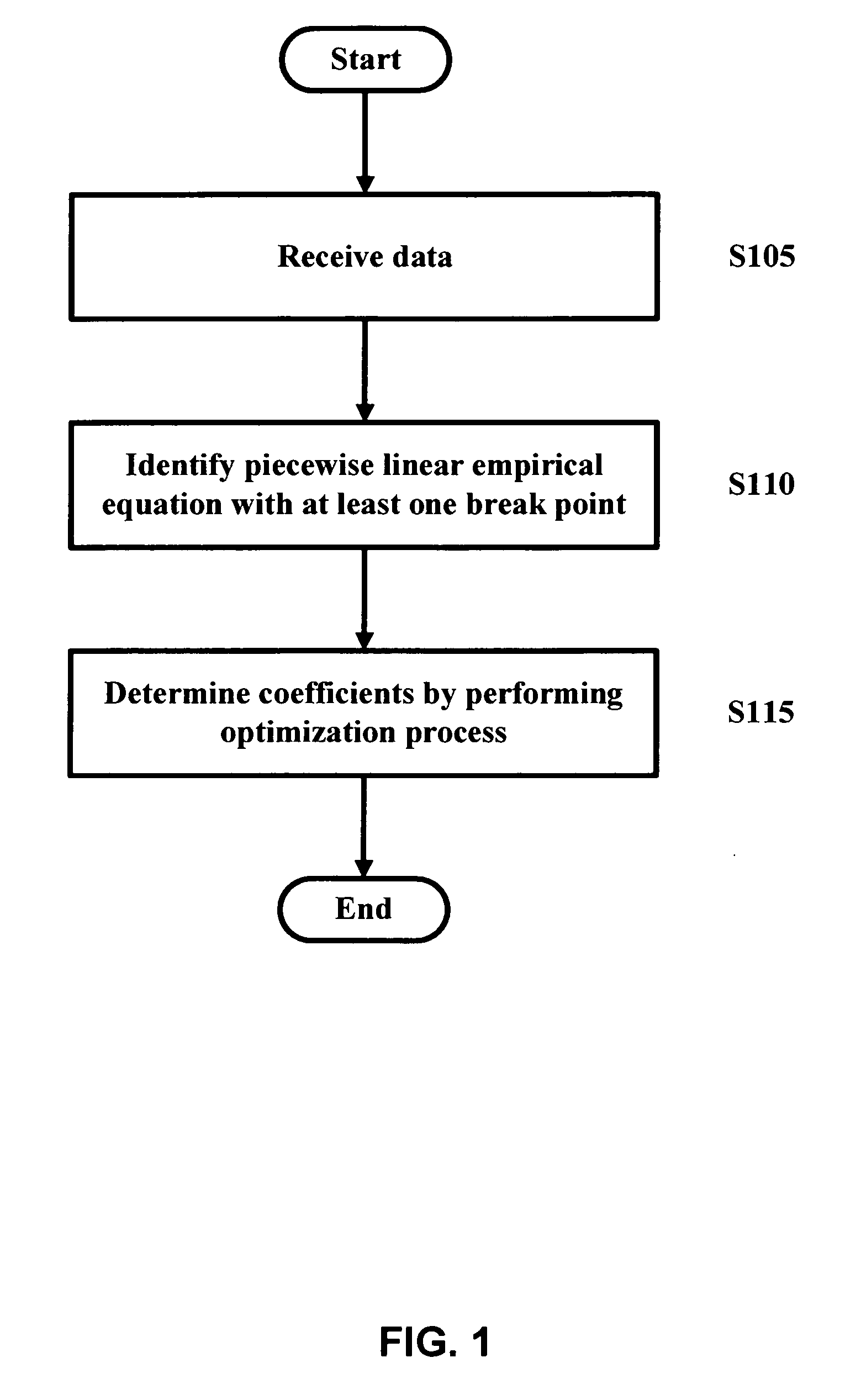
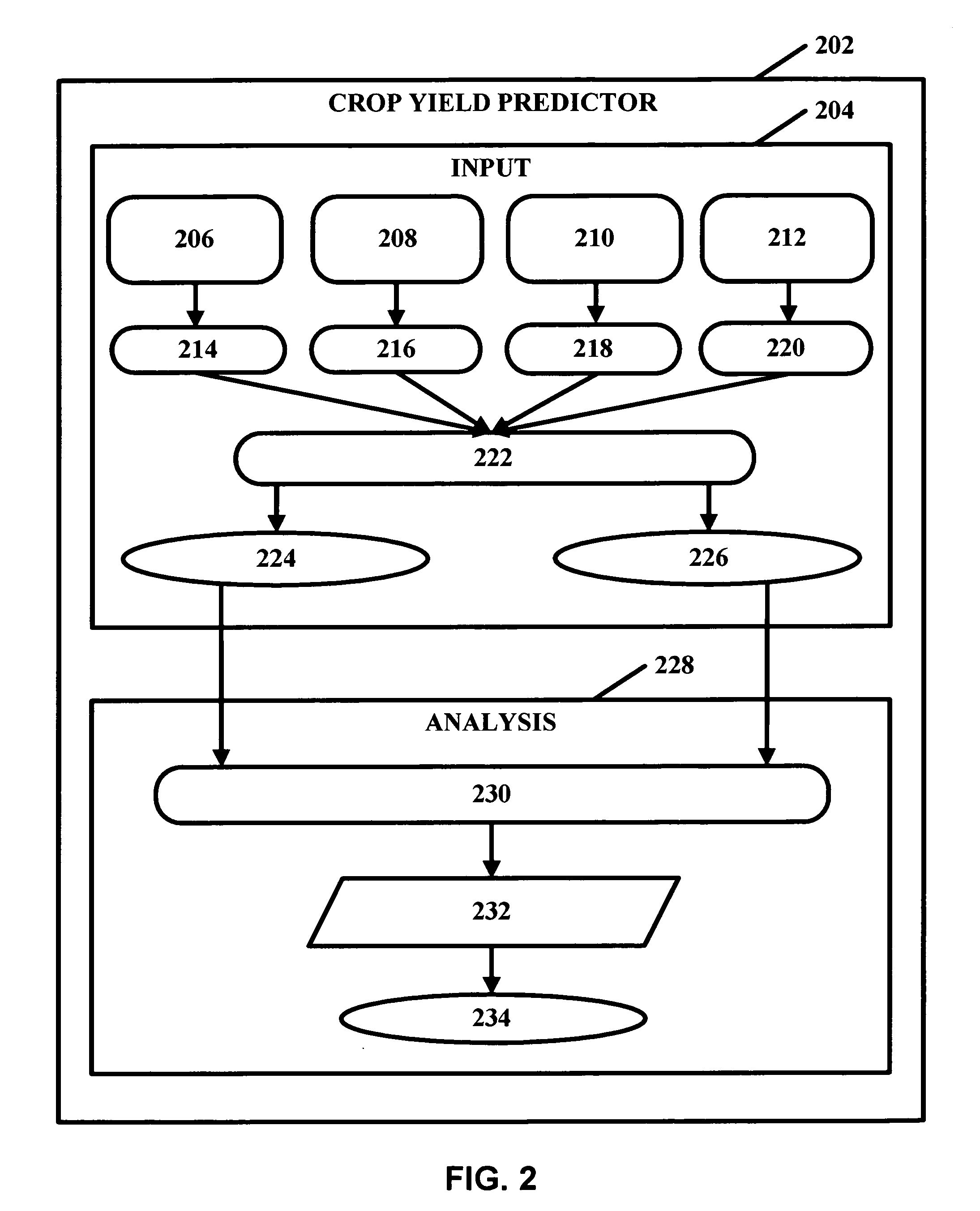
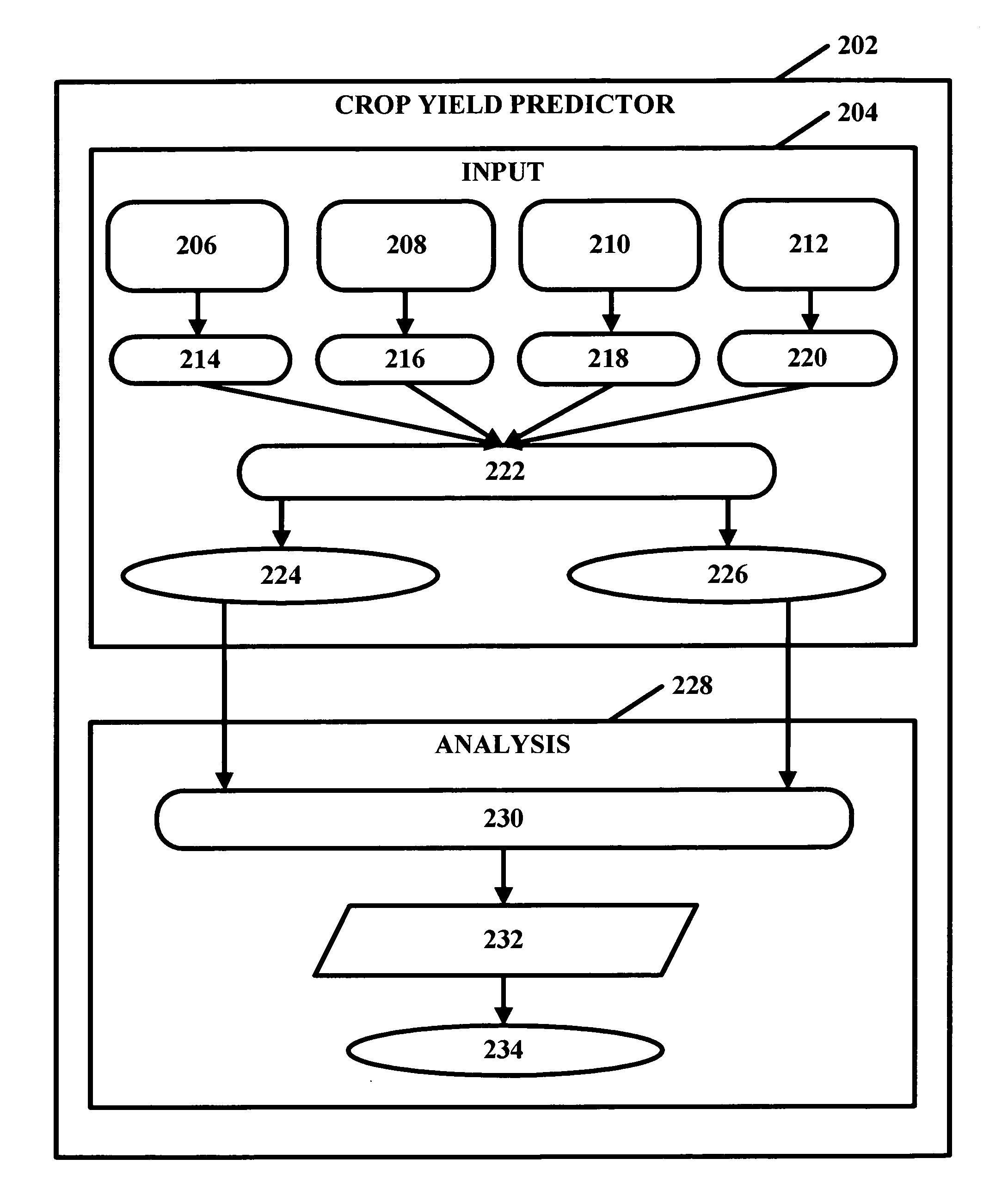
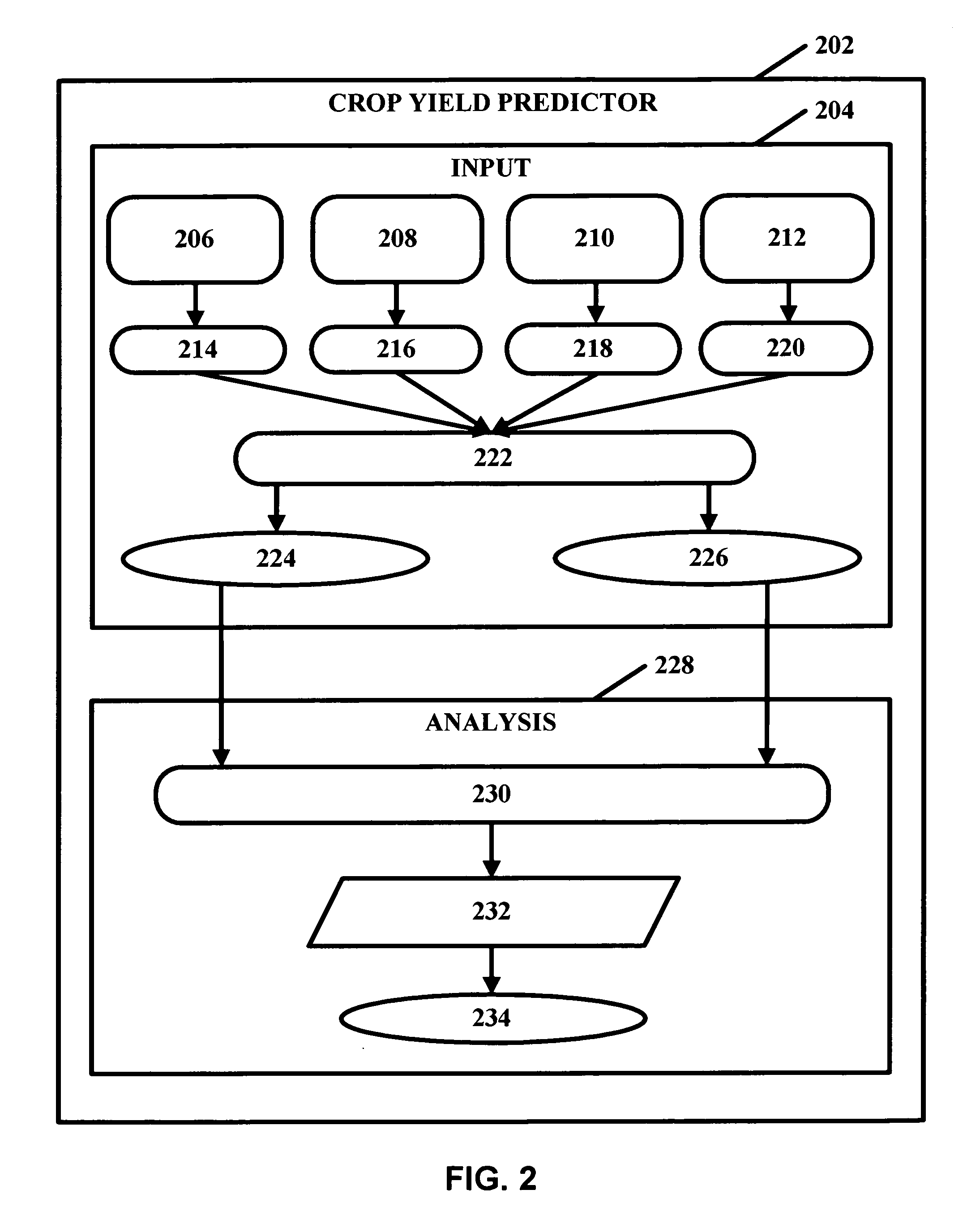
Crop yield prediction
InactiveUS20050234691A1Climate change adaptationAnalogue computers for chemical processesNon linear methodsEngineering
Crop yield may be assessed and predicted using a piecewise linear regression method with break point and various weather and agricultural parameters, such as NDVI, surface parameters (soil moisture and surface temperature) and rainfall data. These parameters may help aid in estimating and predicting crop conditions. The overall crop production environment can include inherent sources of heterogeneity and their nonlinear behavior. A non-linear multivariate optimization method may be used to derive an empirical crop yield prediction equation. Quasi-Newton method may be used in optimization for minimizing inconsistencies and errors in yield prediction. Minimization of least square loss function through iterative convergence of pre-defined empirical equation can be based on piecewise linear regression method with break point. This non-linear method can achieve acceptable lower residual values with predicted values very close to the observed values. The present invention can be modified and tailored for different crops worldwide.
Owner:GEORGE MASON INTPROP INC
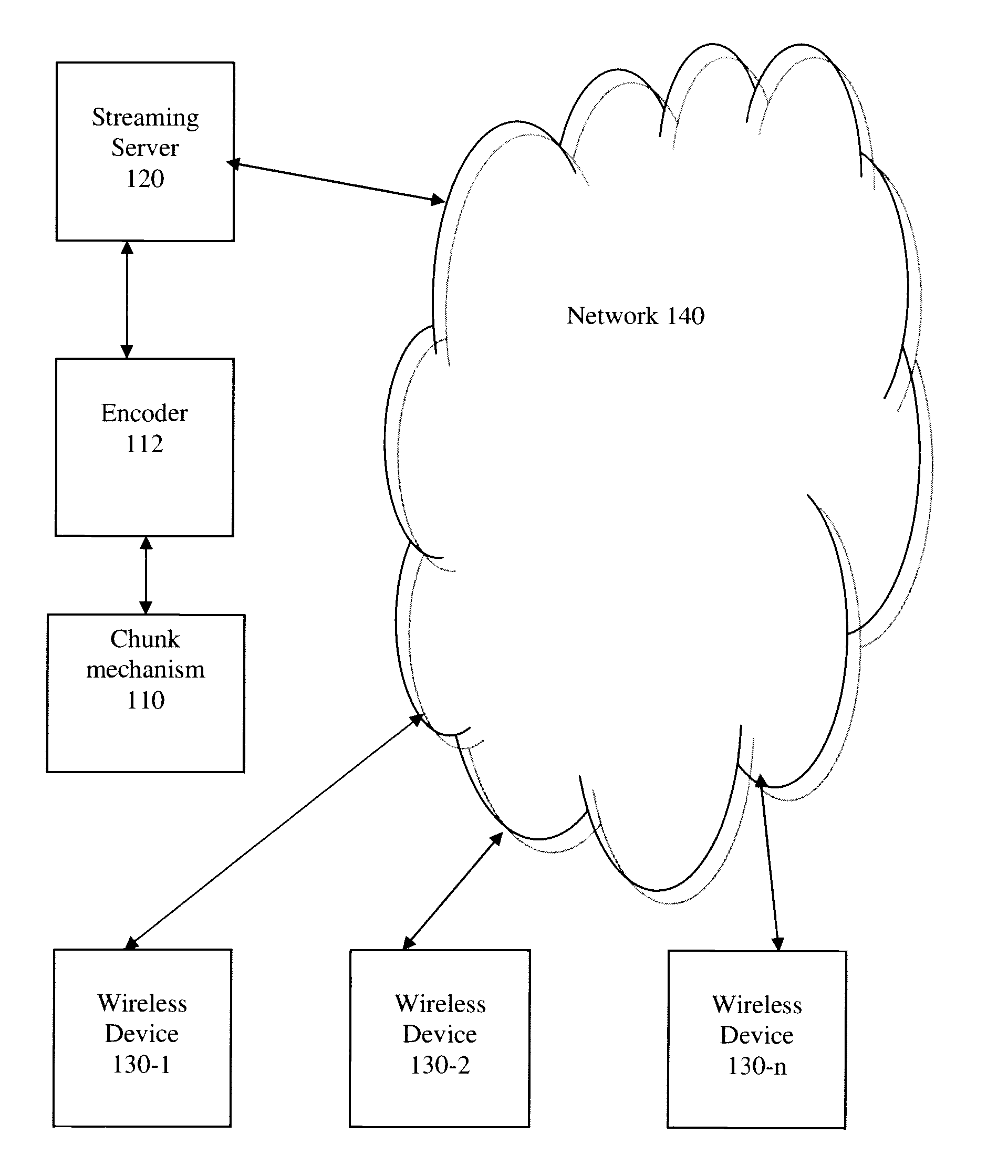
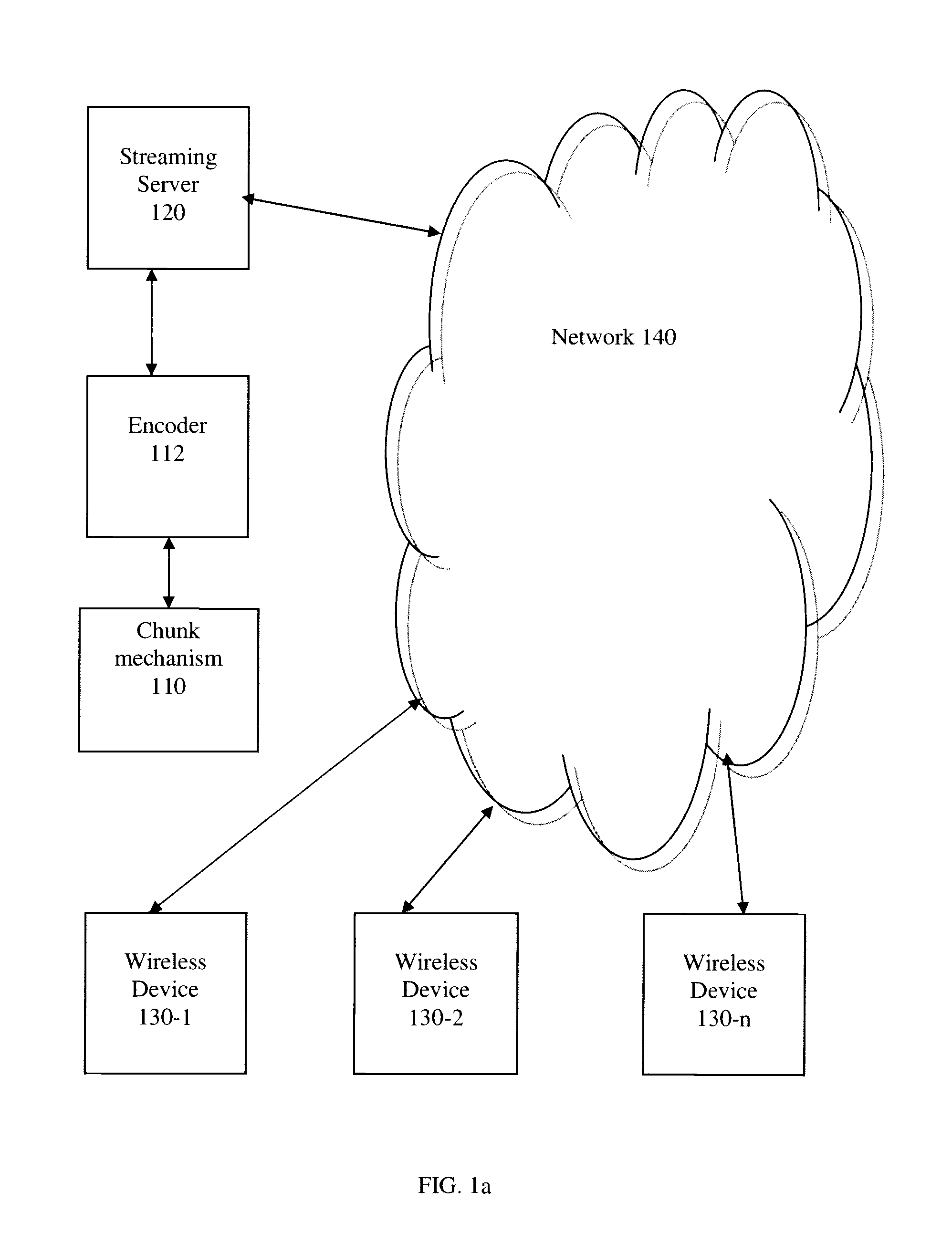
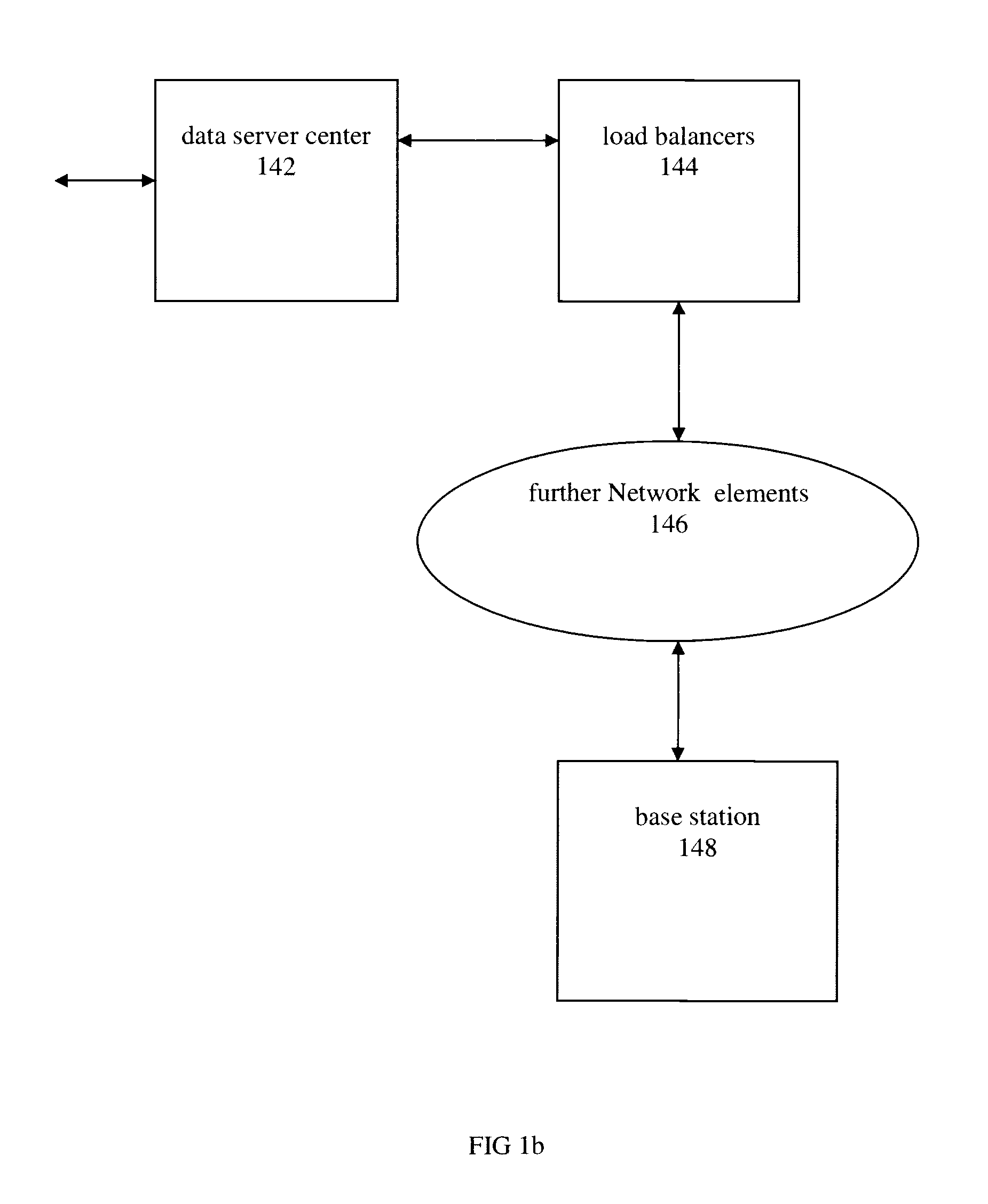
Method and apparatus for streaming media to a plurality of adaptive client devices
InactiveUS20080133766A1Network traffic/resource managementMultiple digital computer combinationsCellular telephoneBreaking point
The present invention relates to a method and apparatus for streaming media to a plurality of adaptive client devices. In one aspect there is provided a method of providing a media stream over data channel of a best effort transmission network that includes a wireless path to a plurality of client devices. In another aspect there is provided a method of encoding a stream of data into chunks, whereby the chunks are obtained by determining a break point between them that corresponds to a silence point. In another aspect, there is provided a method for creating a library of encoded media for a media stream and linking the library to a plurality of cell phone devices.
Owner:GLOBSTREAM
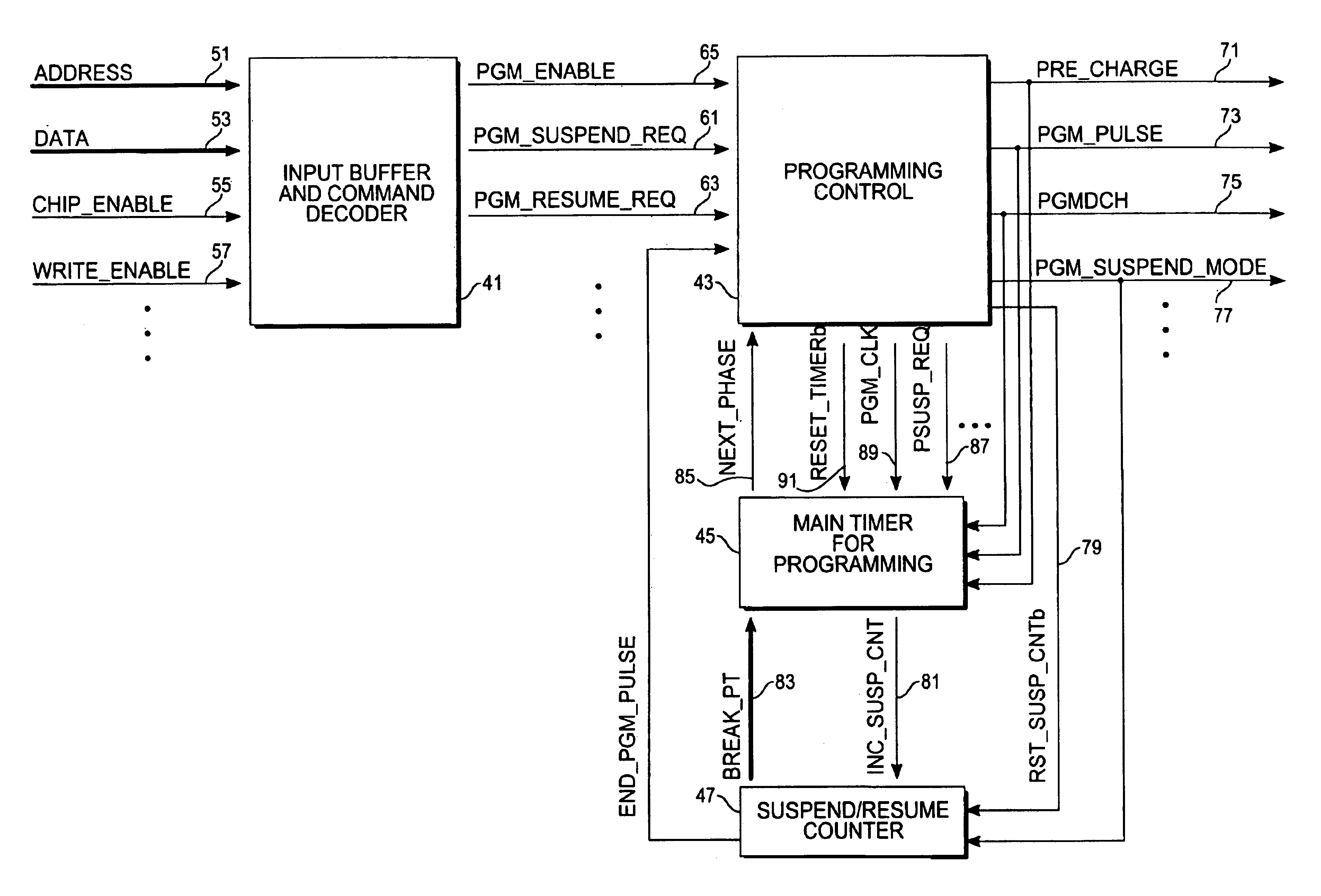
Suspend-resume programming method for flash memory
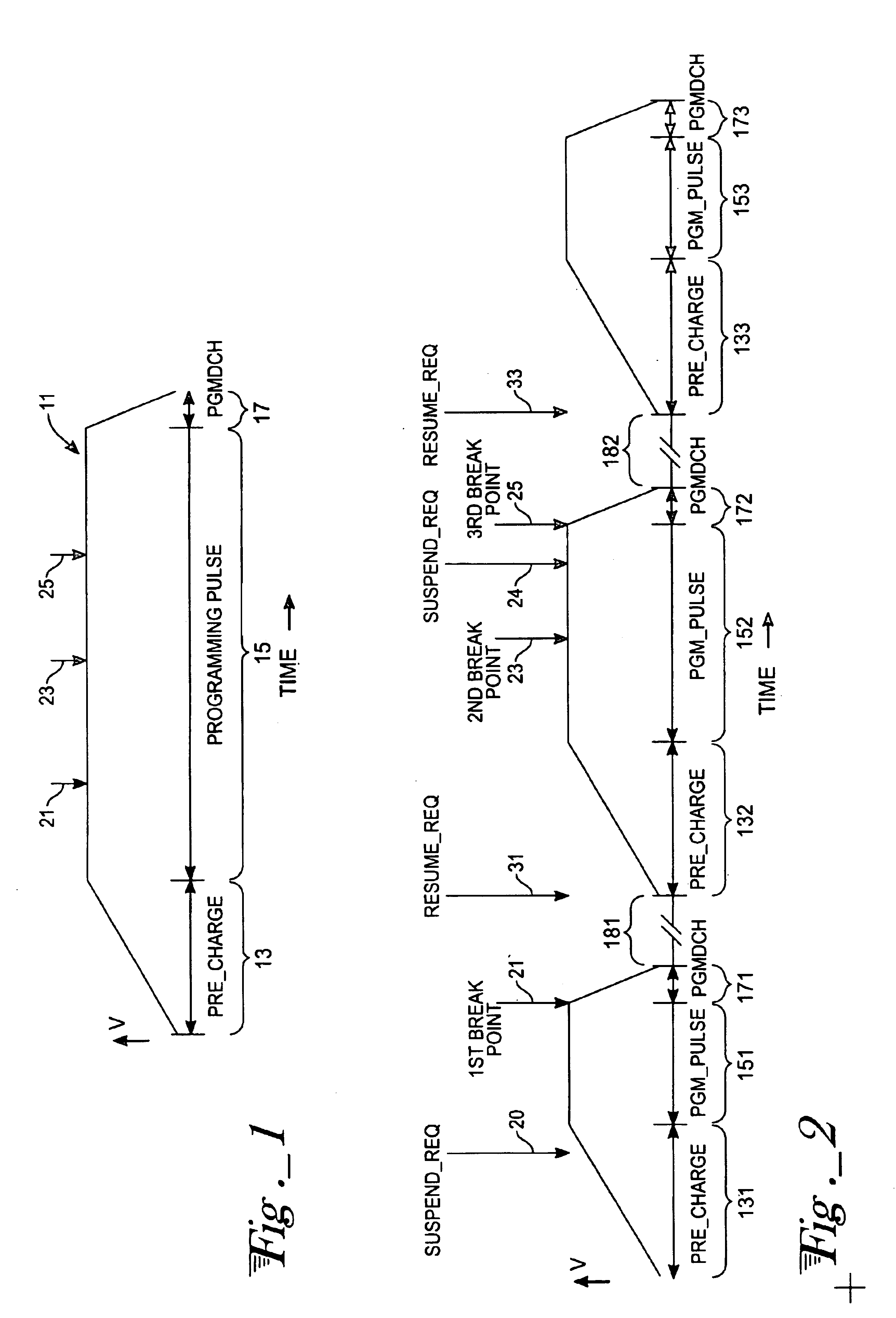
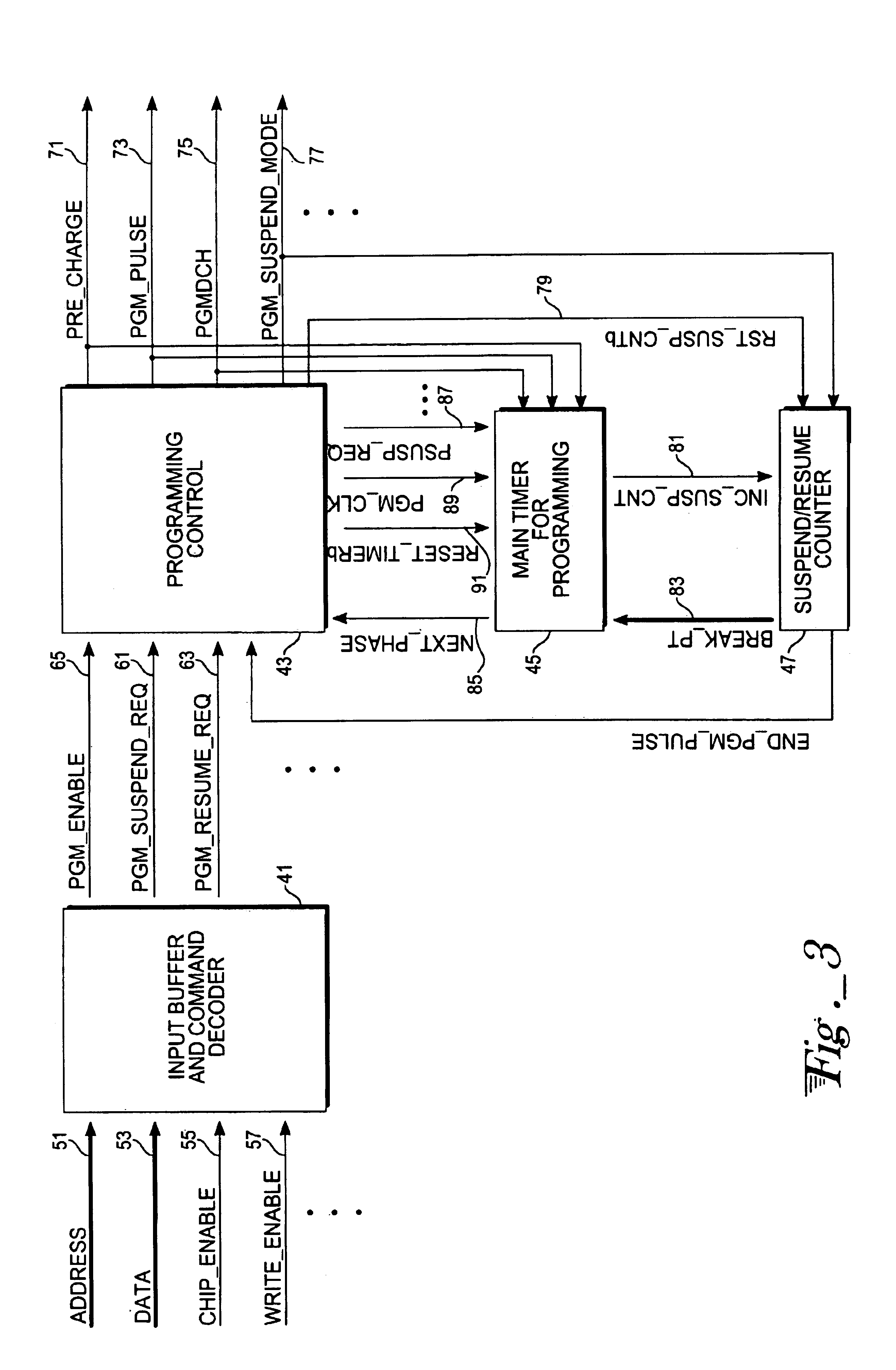
In a non-volatile memory, a programming cycle consists of the following phases: high voltage charging up, programming pulse, and discharge. The actual programming process only takes place in the programming pulse phase. Several break points are defined relative to elapsed time and introduced in the programming pulse phase. Upon receiving a suspend request, the programming operation will advance to the next break point, then discharge the high programming voltage and go to a suspend state. A separate counter is used to monitor the break points so that elapsed non-programming time can be deducted from the total programming pulse time when the programming operation is resumed. By doing so, the device can handle frequent suspend and resume requests. Since the total time duration in the programming pulse phase is equal for the programming operation with and without suspend and resume requests, the programming proceeds efficiently to completion.
Owner:ATMEL CORP
Self-upgrade method for equipment in remote online monitoring system
ActiveCN102314369AResolve escalationSolve problemsProgram loading/initiatingTransmissionGeneral Packet Radio ServiceSelf maintenance
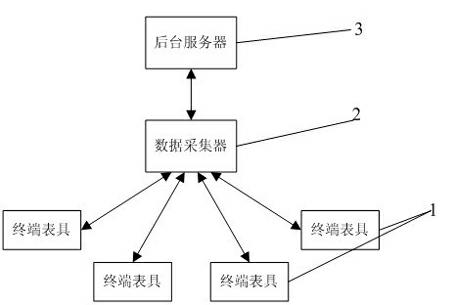
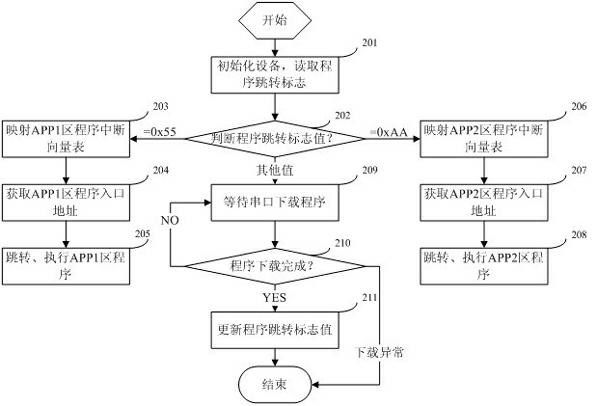
The invention belongs to the field of wireless communication, and particularly relates to a self-upgrade method for equipment in a remote online monitoring system. The method is characterized in that: each piece of terminal equipment performs self-upgrade and self-maintenance through the remote online monitoring system consisting of a terminal table tool, a data acquisition unit and a background server based on a GPRS (General Packet Radio Service). The method mainly comprises the following steps that: the background server manages an application program and version information; the data acquisition unit periodically inquires a version log and downloads a new version program; the data acquisition unit realizes self-upgrade and upgrades the terminal table tool; and after the new version program is updated successfully, skipping is performed and an old version program is still kept for later use. In the method, the GPRS, storage space management, a file sub-package mechanism, a transmission response mechanism, a mode for continuous transmission at break-points and an IAP (Internet Access Provider) program programming mode are combined, and the accuracy and reliability of data transmission are ensured; and under the condition of not influencing normal use of a user, the equipment upgrading and maintaining problems of large quantity and wide distribution are solved quickly and efficiently.
Owner:杭州先锋电子技术股份有限公司
Analytical aid
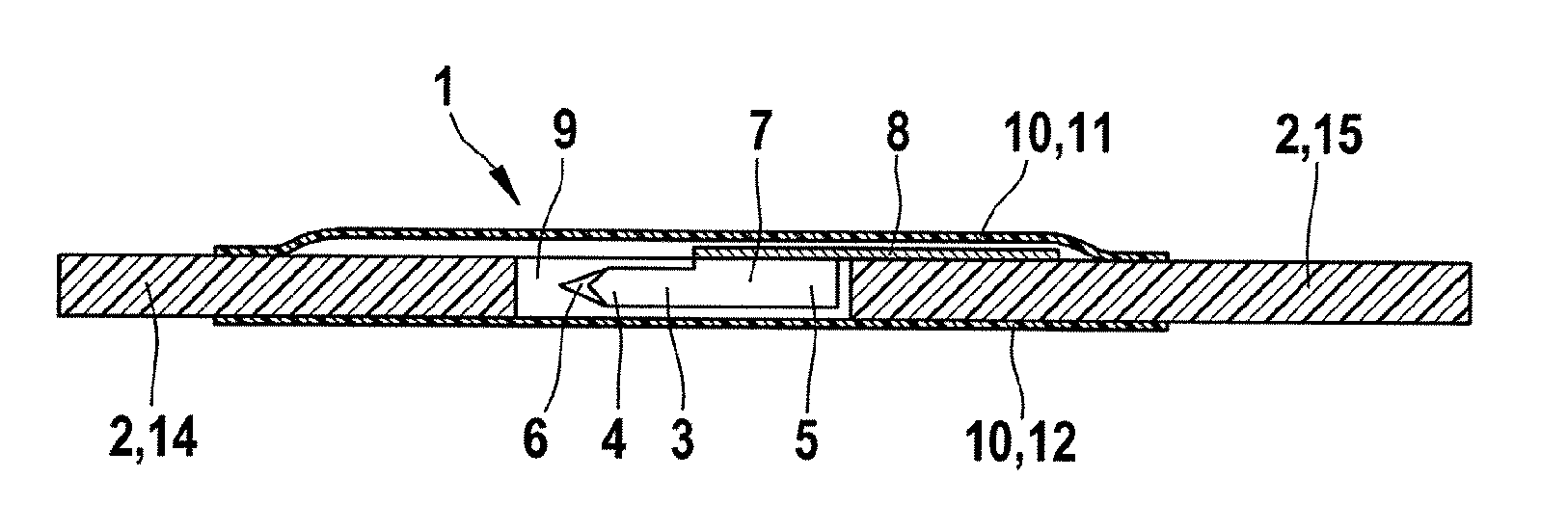
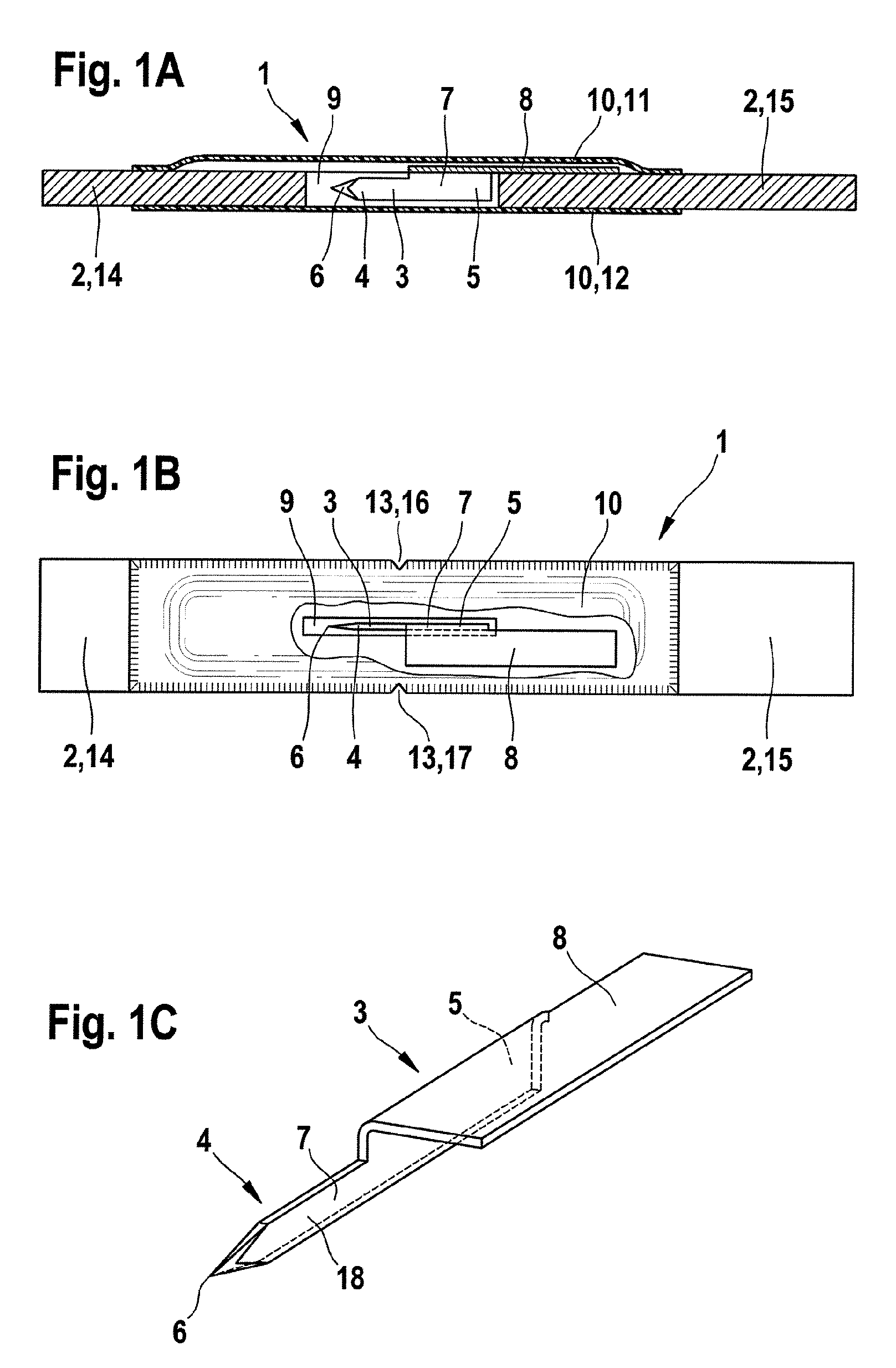
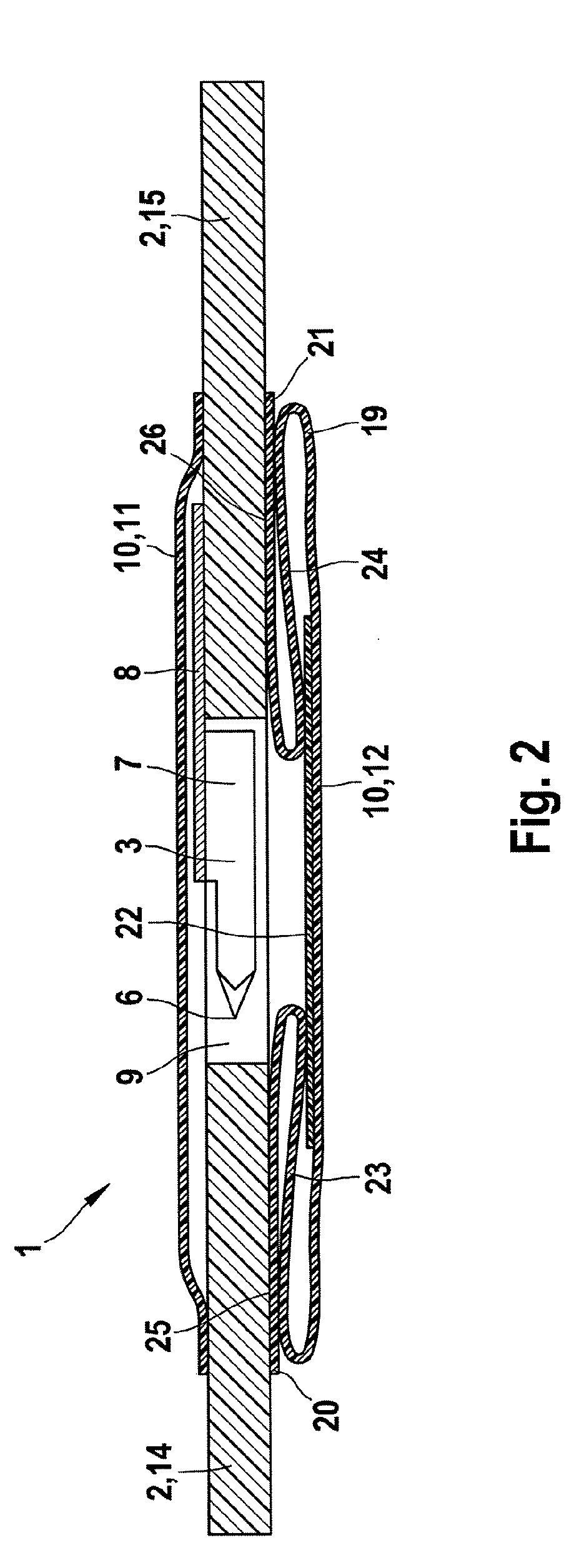
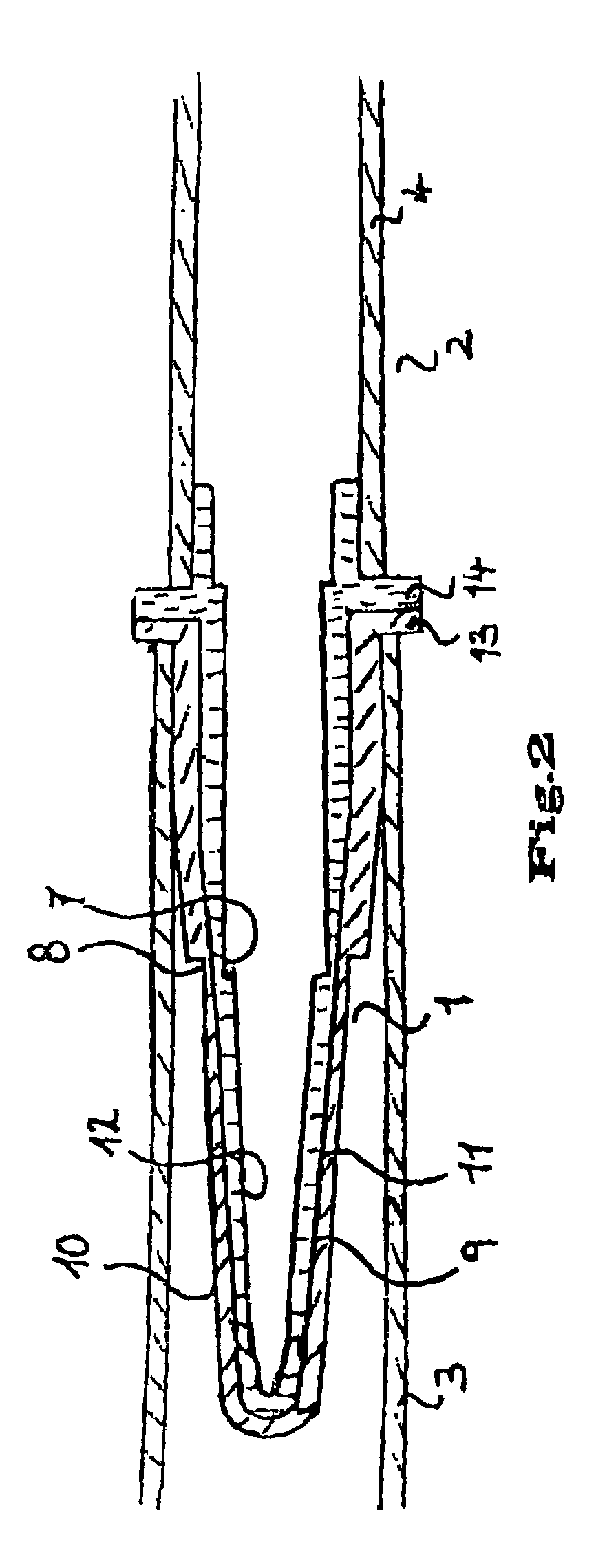
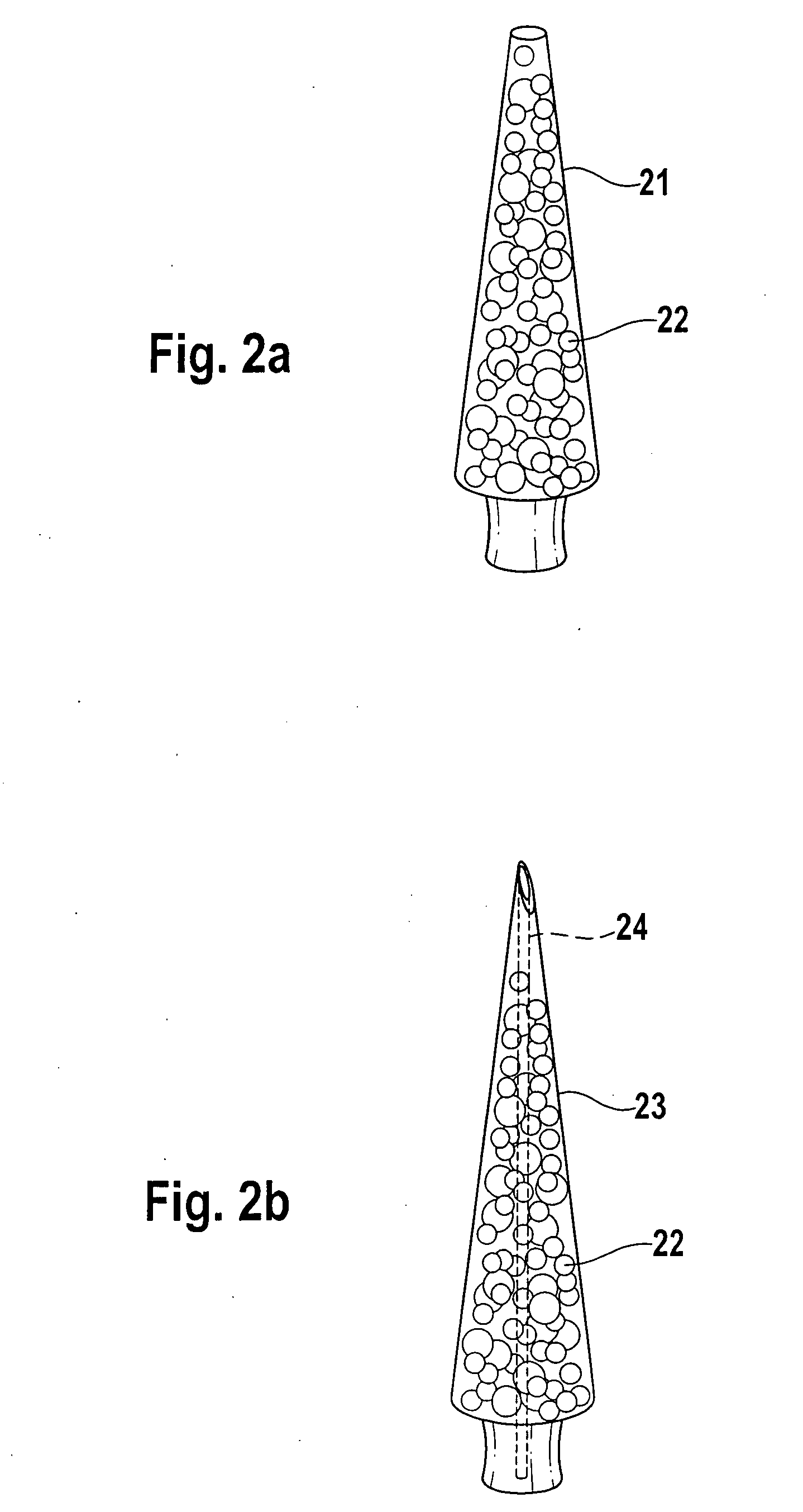
An analytical aid including a base, a lancet and a test element. The lancet includes a lancet point and a distal end of the lancet can be attached to the base. At least the lancet point is located in a recess in the base and the recess can be closed by a cover as long as the analytical aid is in an unused state. The base includes a predetermined breaking point or position, at which the base is broken into two segments when stress is applied. The predetermined breaking point is arranged such that the lancet point is exposed for use when the base breaks at the predetermined breaking point. A test element is attached to the base.
Owner:ROCHE DIABETES CARE INC +1
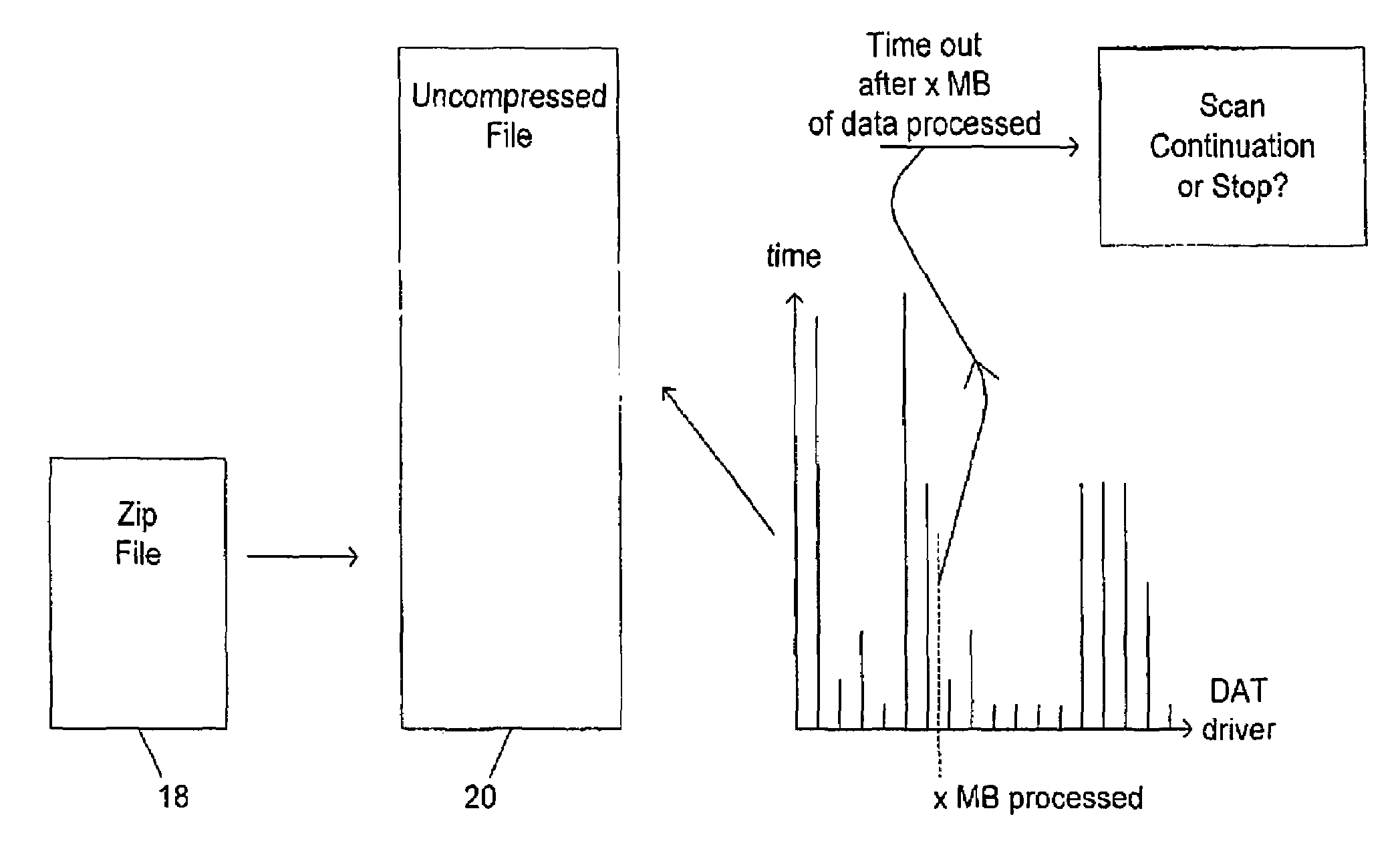
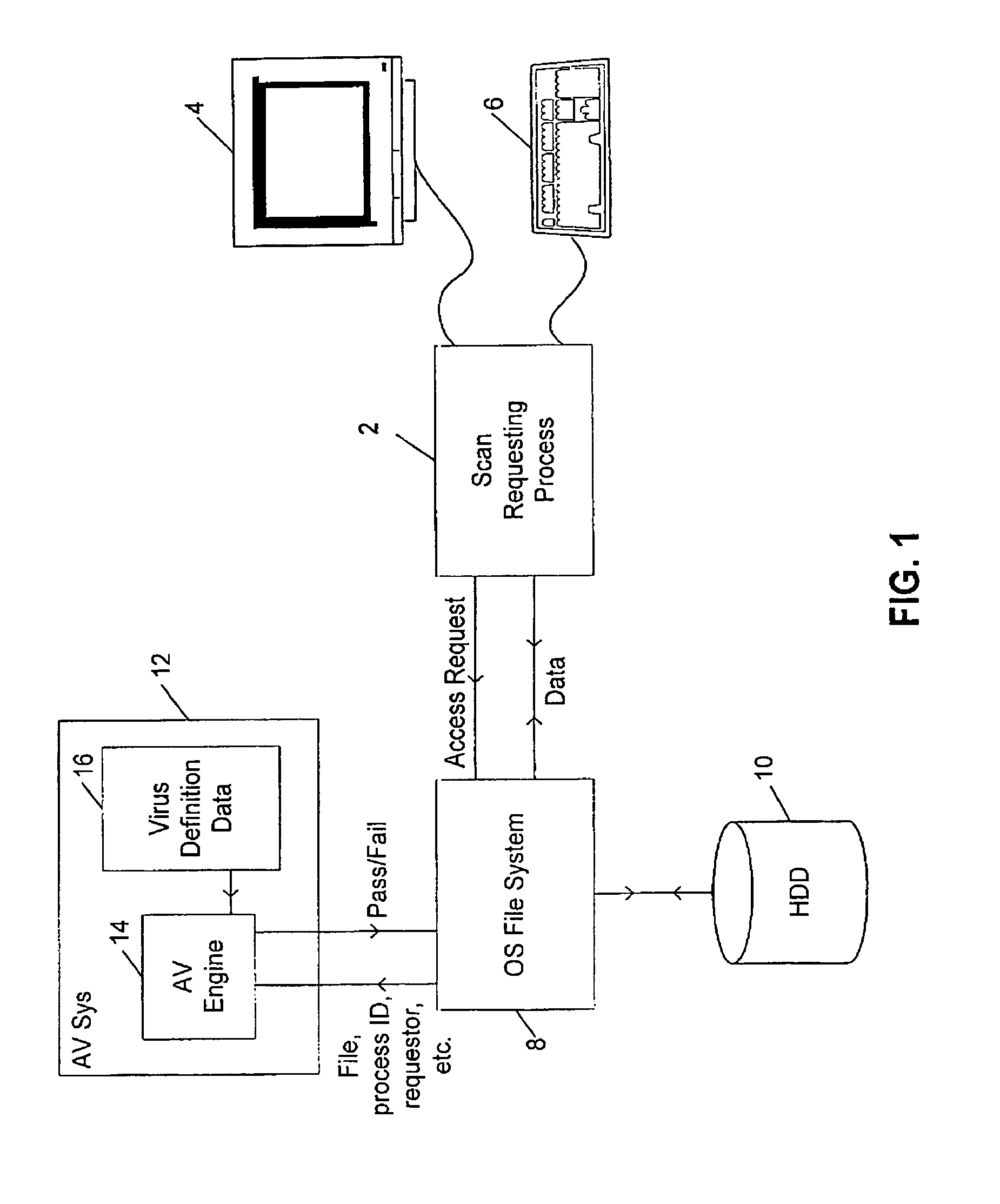
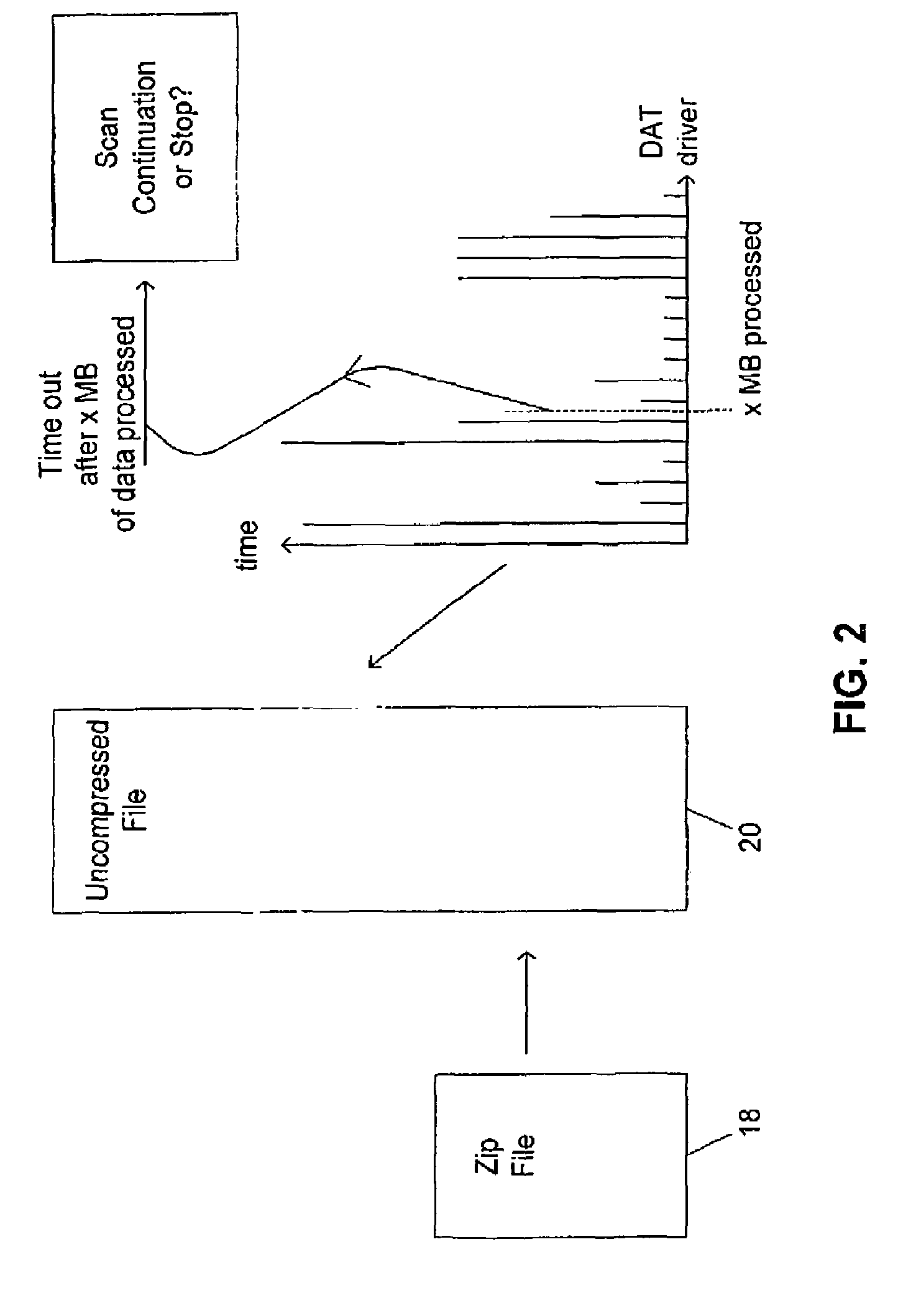
Providing break points in a malware scanning operation
InactiveUS6968461B1Increased complexityLow complexity valueMemory loss protectionUser identity/authority verificationMalwareData treatment
A computer virus scanning system is described in which during the scanning operation a measurement value indicative of the amount of data processing performed is calculated and this measurement value used to trigger breaks in the virus scanning operation. The triggered breaks can be used to perform a determination as to whether or not the virus scanning operations should be early terminated. One possibility is to measure the total size of the data processed during the virus scanning operation and calculate a ratio of this compared to the size of the computer file being virus scanned. If this calculated ratio exceeds a predetermined threshold, then virus scanning may be terminated. Another possibility is to associate a complexity value with each of a plurality of tests applied in the virus scanning operation. A total for these complexity values may be used to trigger the breaks and also to trigger early termination upon exceeding of respective threshold levels.
Owner:MCAFEE LLC
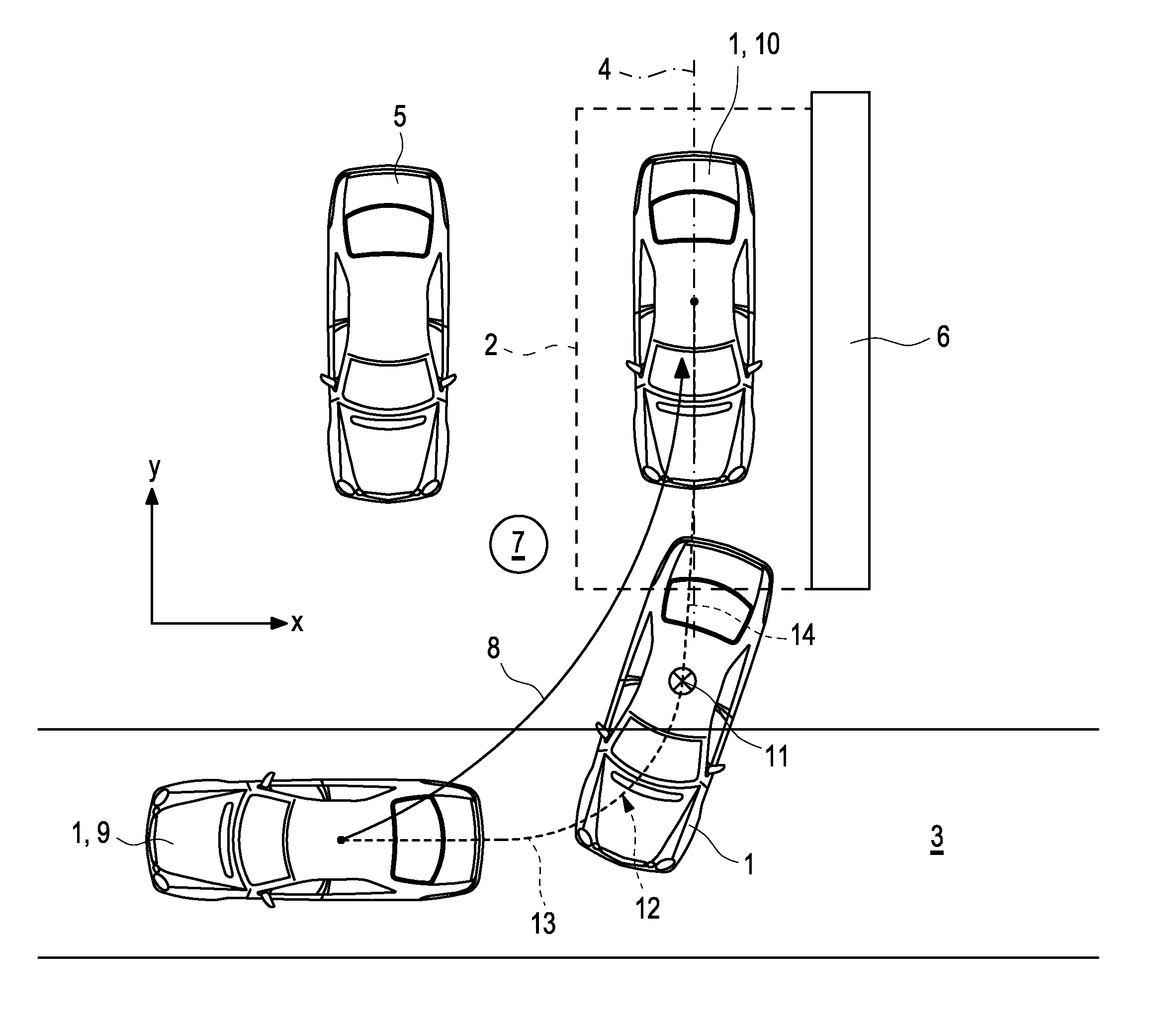
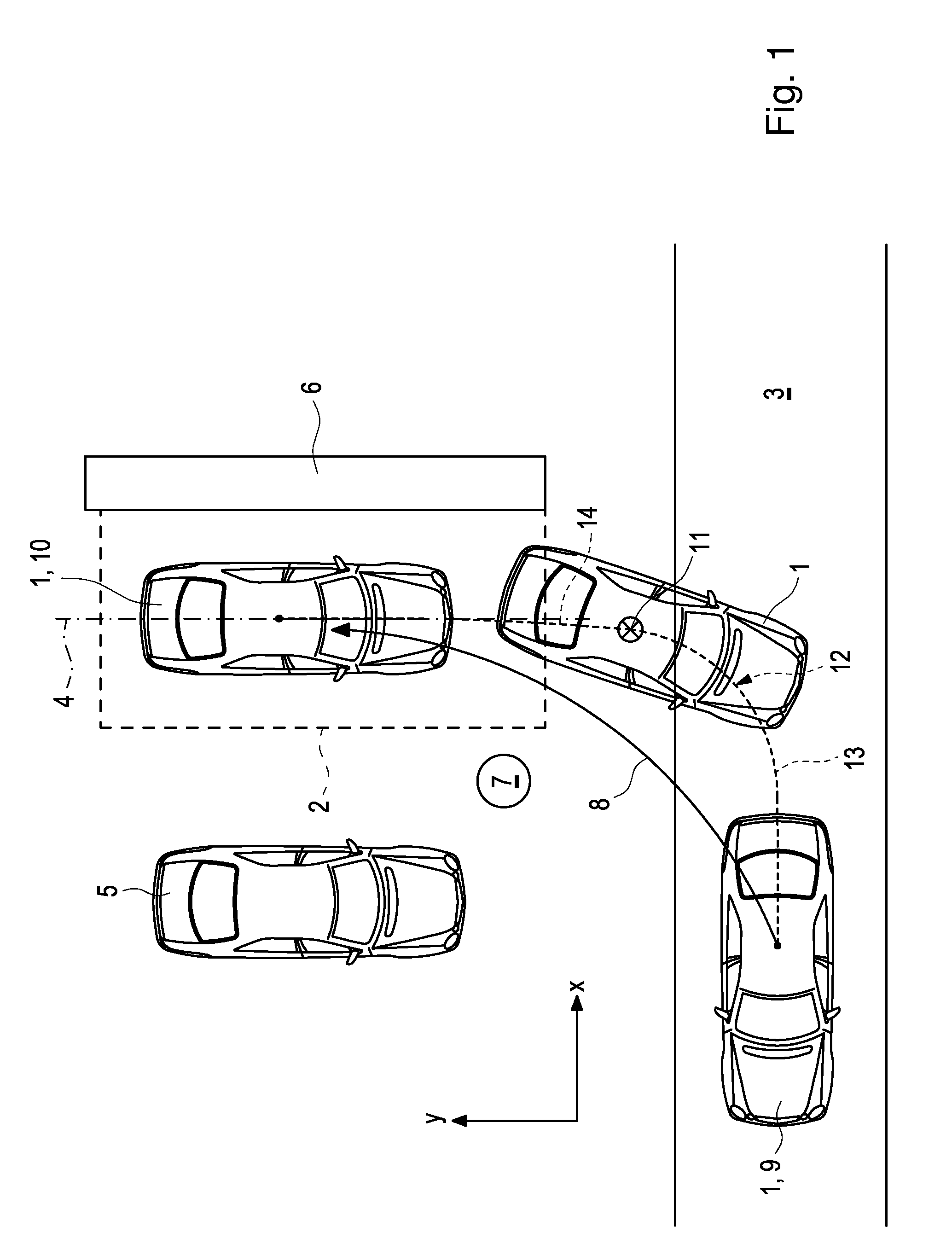
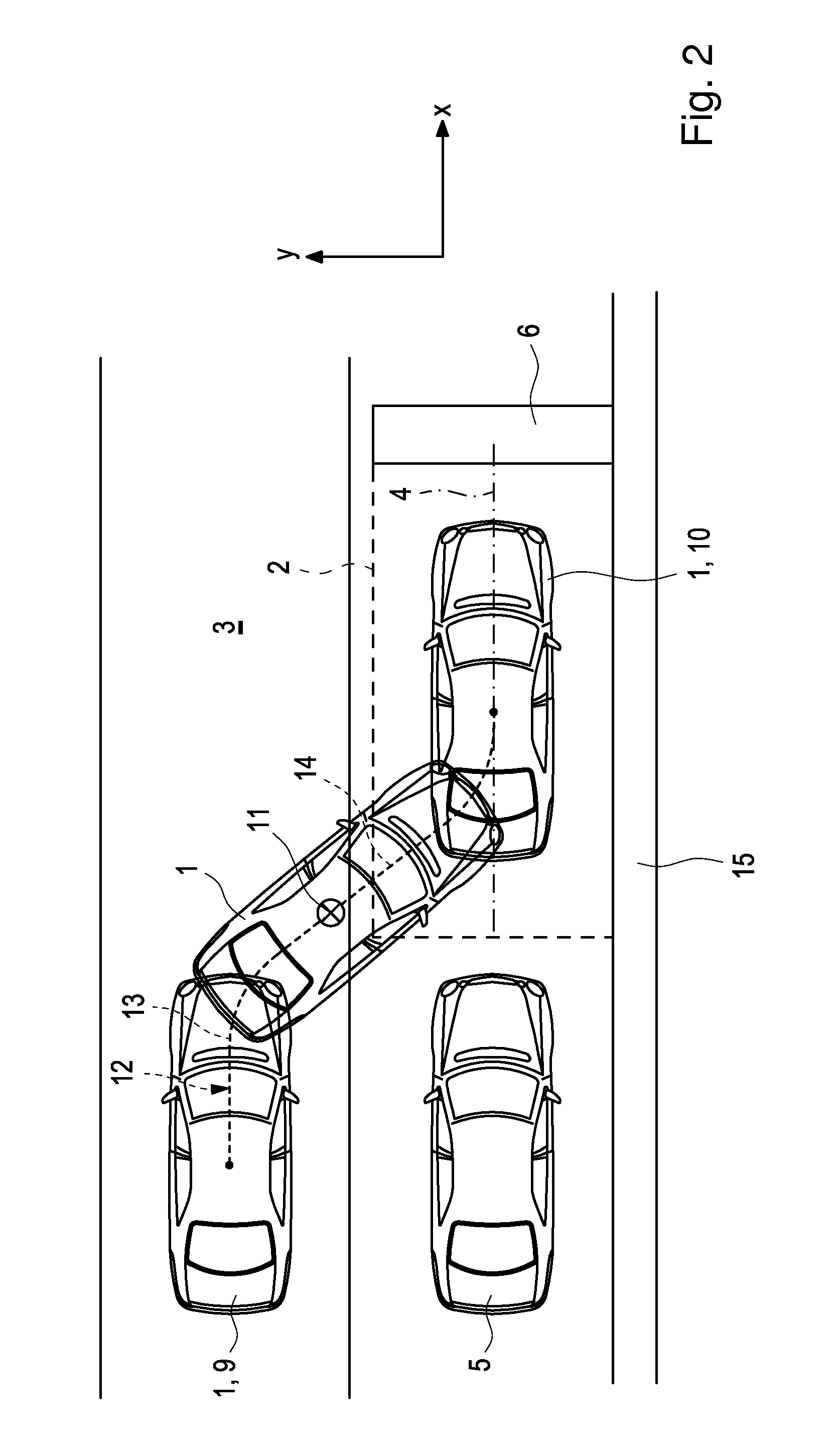
Method for Carrying Out a Process of Parking a Vehicle by Means of a Driver Assistance System
InactiveUS20150203111A1Simple processEasy to monitorSteering partsVehicle position/course/altitude controlEngineeringBreaking point
A method for performing an automatic parking process of a vehicle involves offering a user a selection between at least two parking maneuver for implementing by a driver assistance system in the vehicle. The first parking maneuver is a direct parking maneuver in which an automatic parking process is performed from the start position directly to the target position along the trajectory. The second parking maneuver involves providing a break point the parking trajectory so that a user can disembark the vehicle at the break point and prior to the target position.
Owner:DAIMLER AG
Sterility-maintaining connection system for medical systems and use thereof
A connection system including at least a male connecting element and a female connecting element which can be connected to each other, as well as the male connecting element and the female connecting element. The location of contact of the two connecting elements is preferably provided with a disinfecting adhesive so that an aseptic or sterile connection can be established. Therein both connecting elements have predetermined breaking points which in the connected state are arranged one above the other so that only one breaking point within the tube is obtained via which an aseptic fluid guidance through two tubes from one sterile system to another sterile system can be carried out. Thereby a particularly simple and cost-saving connection is created which fulfills the highest sterility requirements. Furthermore, also the use of such a connection system is described.
Owner:FRESENIUS AG
Method and apparatus for debugging optimized code
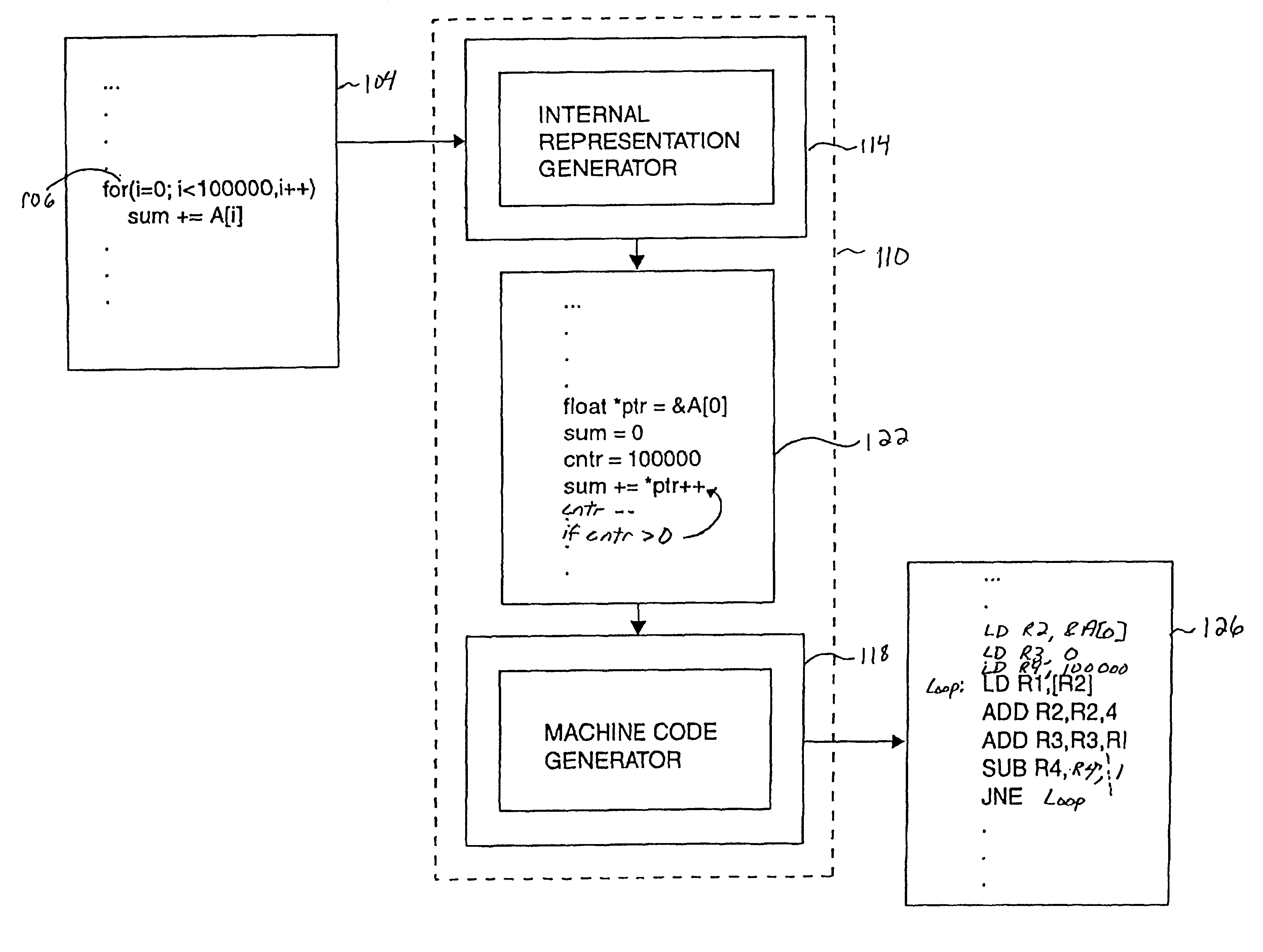
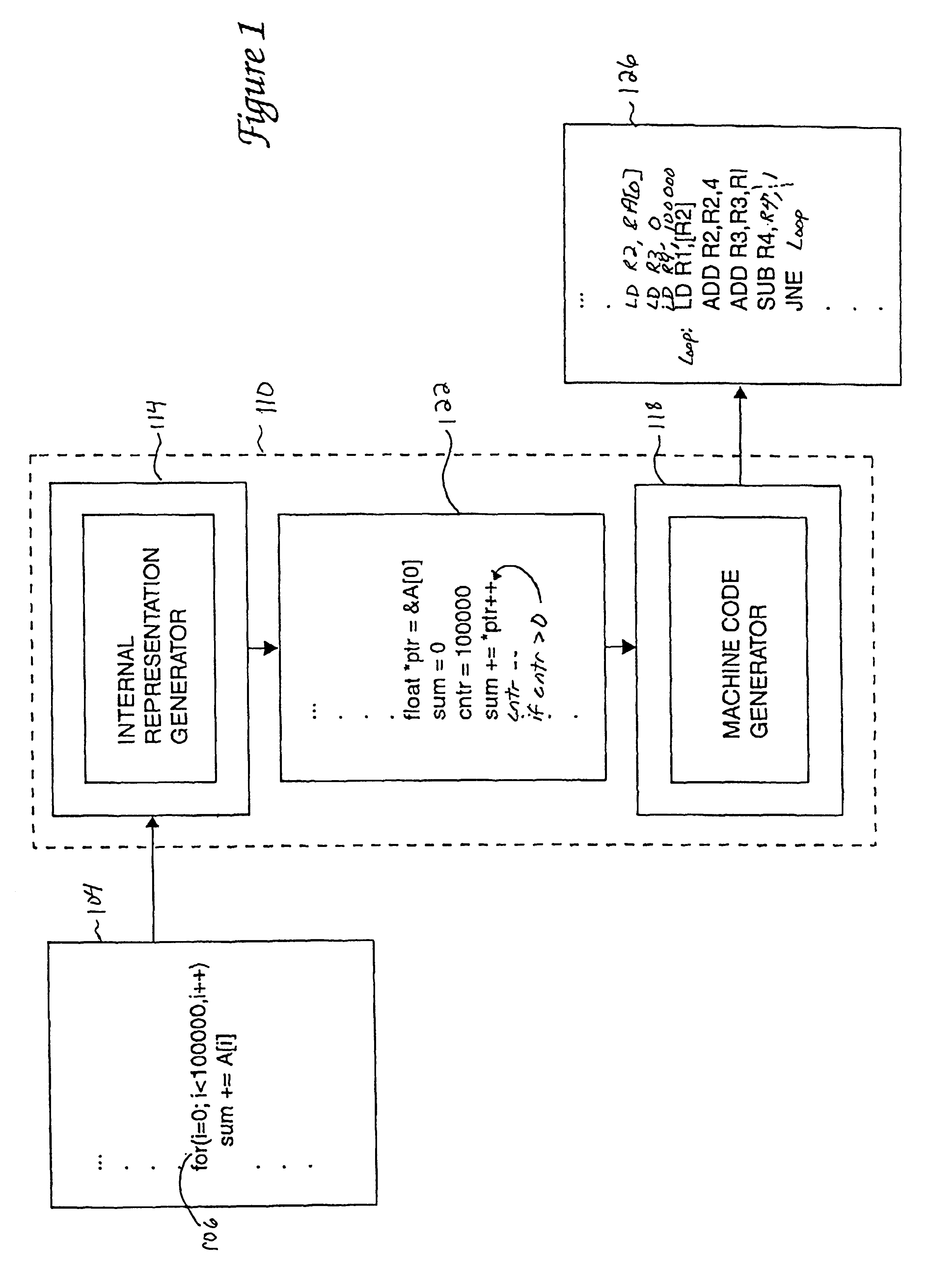
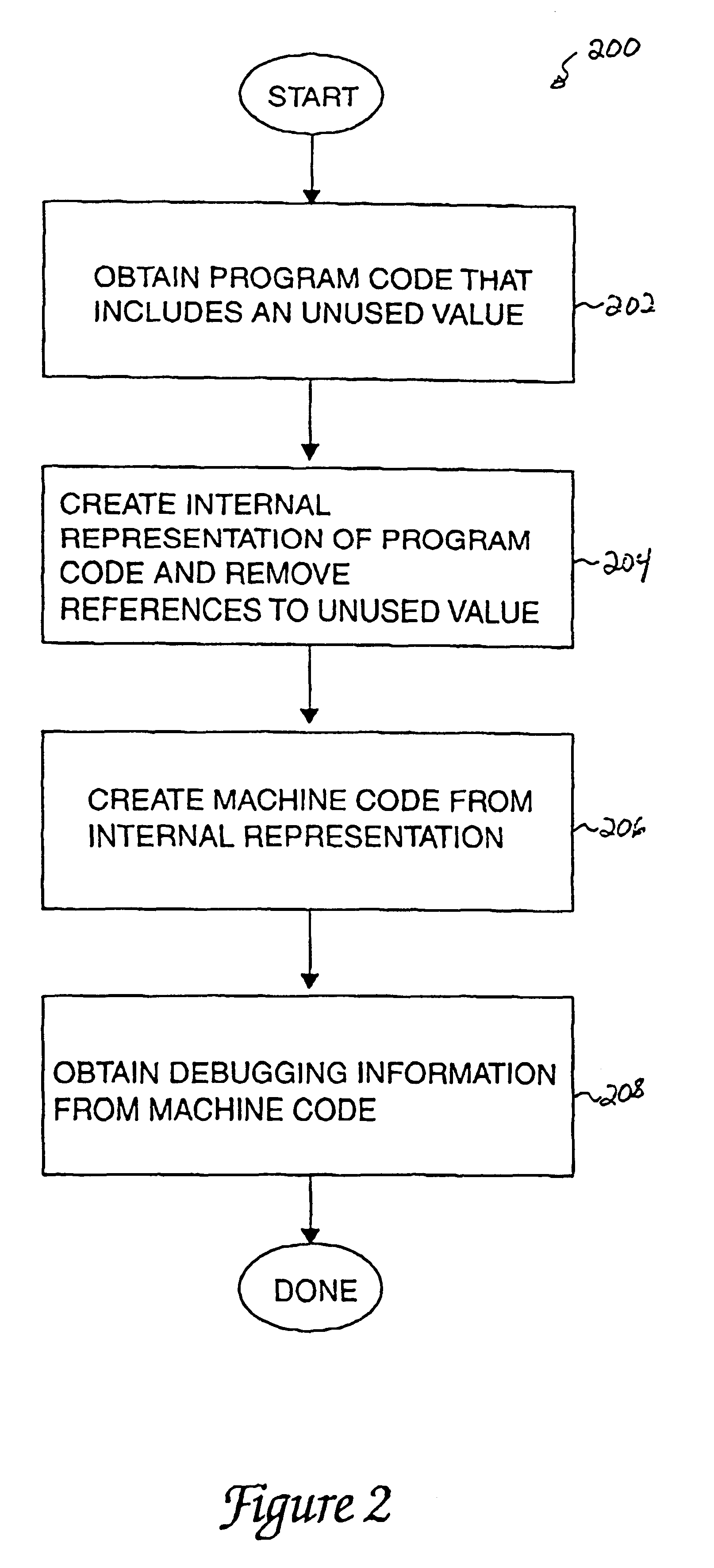
InactiveUS6553565B2Software testing/debuggingSpecific program execution arrangementsCode segmentBreak point
Methods and apparatus for providing a substantially full set of state information to a debugger, without significantly compromising system performance, in order to debug optimized computer program code are disclosed. According to one aspect of the present invention, a method for obtaining information associated with program code includes adding a segment of code, which includes a representation that is effectively not used after it is computed, to the program code. Debugging code is added in proximity to the segment of code, and machine code is generated from the program code. The machine code includes a break point that is associated with the debugging code, and includes an instruction at the breakpoint. Finally, the method includes replacing the instruction at the break point with a branch instruction that is arranged to cause the debugging code to execute.
Owner:ORACLE INT CORP
Systems and methods for compressing plasma
ActiveUS20110026657A1Sufficient reactionIncrease plasma densityNuclear energy generationLow temperature fusion reactorLiquid metalBreaking point
Embodiments of systems and methods for compressing plasma are described in which plasma pressures above the breaking point of solid material can be achieved by injecting a plasma into a funnel of liquid metal in which the plasma is compressed and / or heated.
Owner:GENERAL FUSION INC
File downloading method, system and terminal realizing breaker point continuous transmission
InactiveCN101291195AReduce download waiting timeBroadcast with distributionError preventionSoftware engineeringBroadcasting
The invention provides a method for downloading a document, realizing transmission resuming at break-points. The method can be applied to a unilateral broadcasting network which comprises a document transmitting terminal and a document receiving terminal, wherein, the document transmitting terminal sends down a document; the document receiving terminal records download state information of the document while downloading the document; when the download is interrupted and recovered once more, the document receiving terminal continues downloading from the download break-point according to the recorded download state information, thereby realizing the transmission resuming at break-points. The invention also provides a method, a system and a terminal for downloading the document capable of realizing the transmission resuming at break-points, thereby realizing the transmission resuming at break-points for document downloading after interruption during downloading the document in the unilateral broadcasting network.
Owner:ZTE CORP
Fluid delivery device for use with anastomosing stapling, and resecting instruments
Owner:COVIDIEN LP
System and method for distributed debugging and recording medium on which control programs are recorded
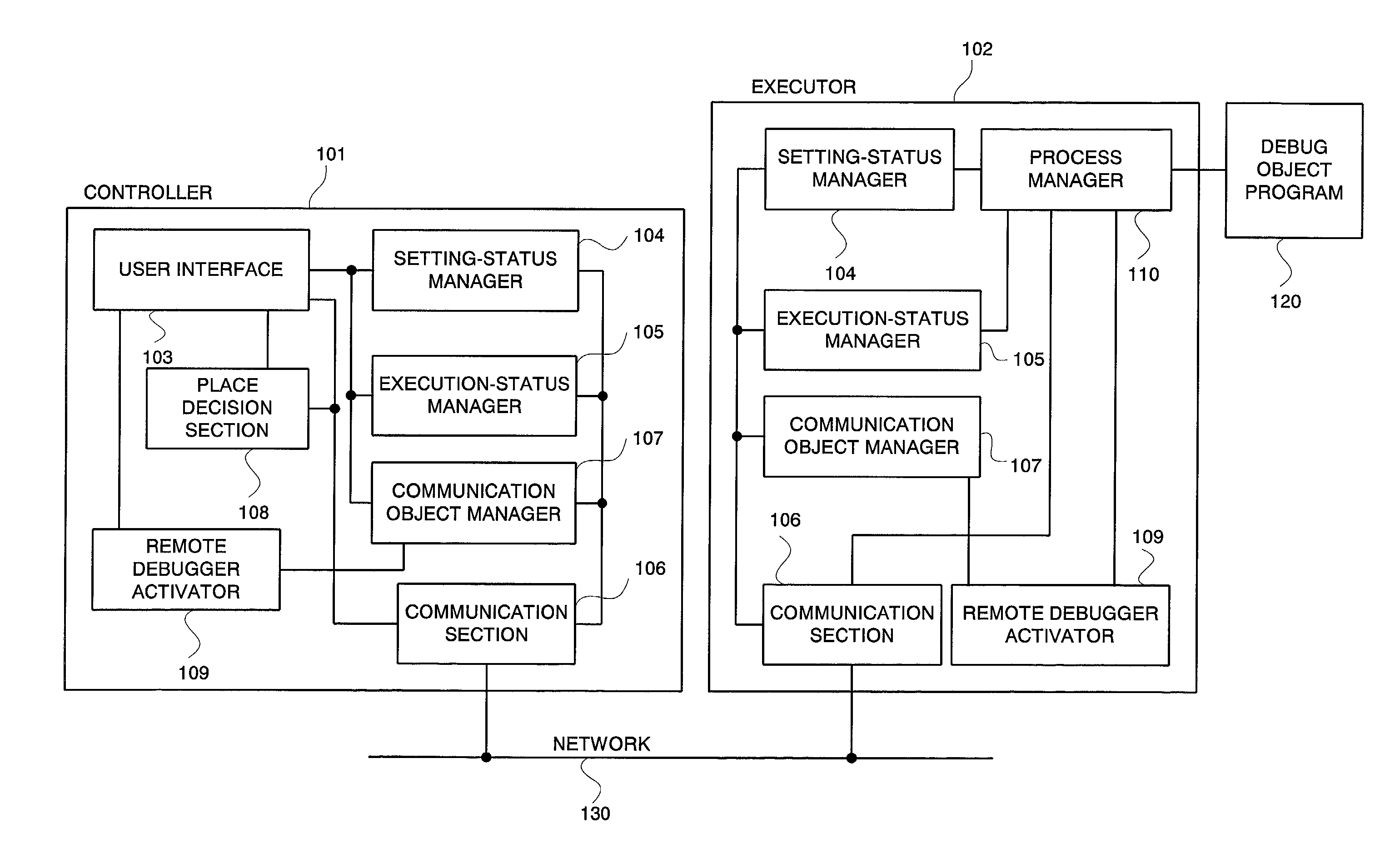
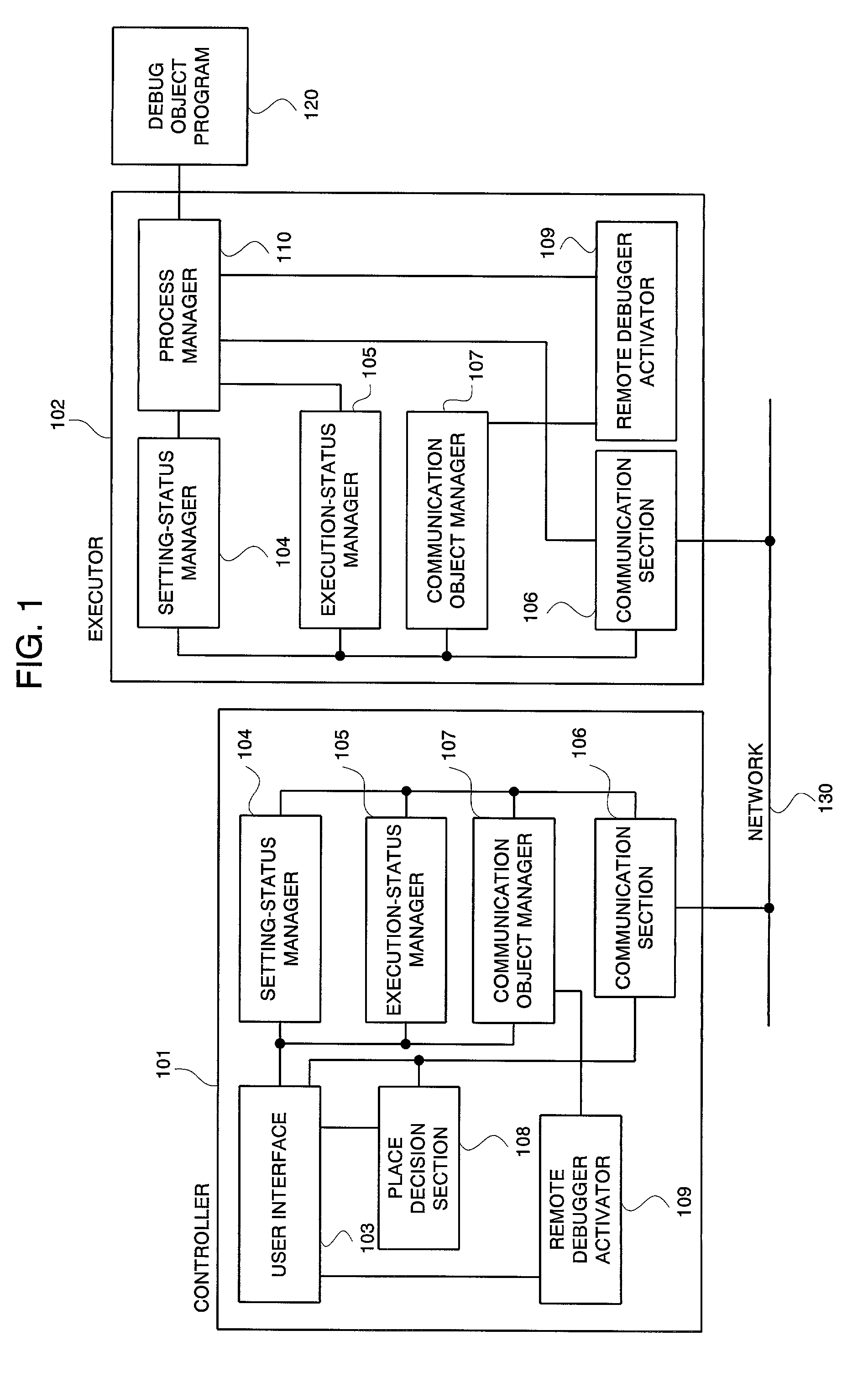
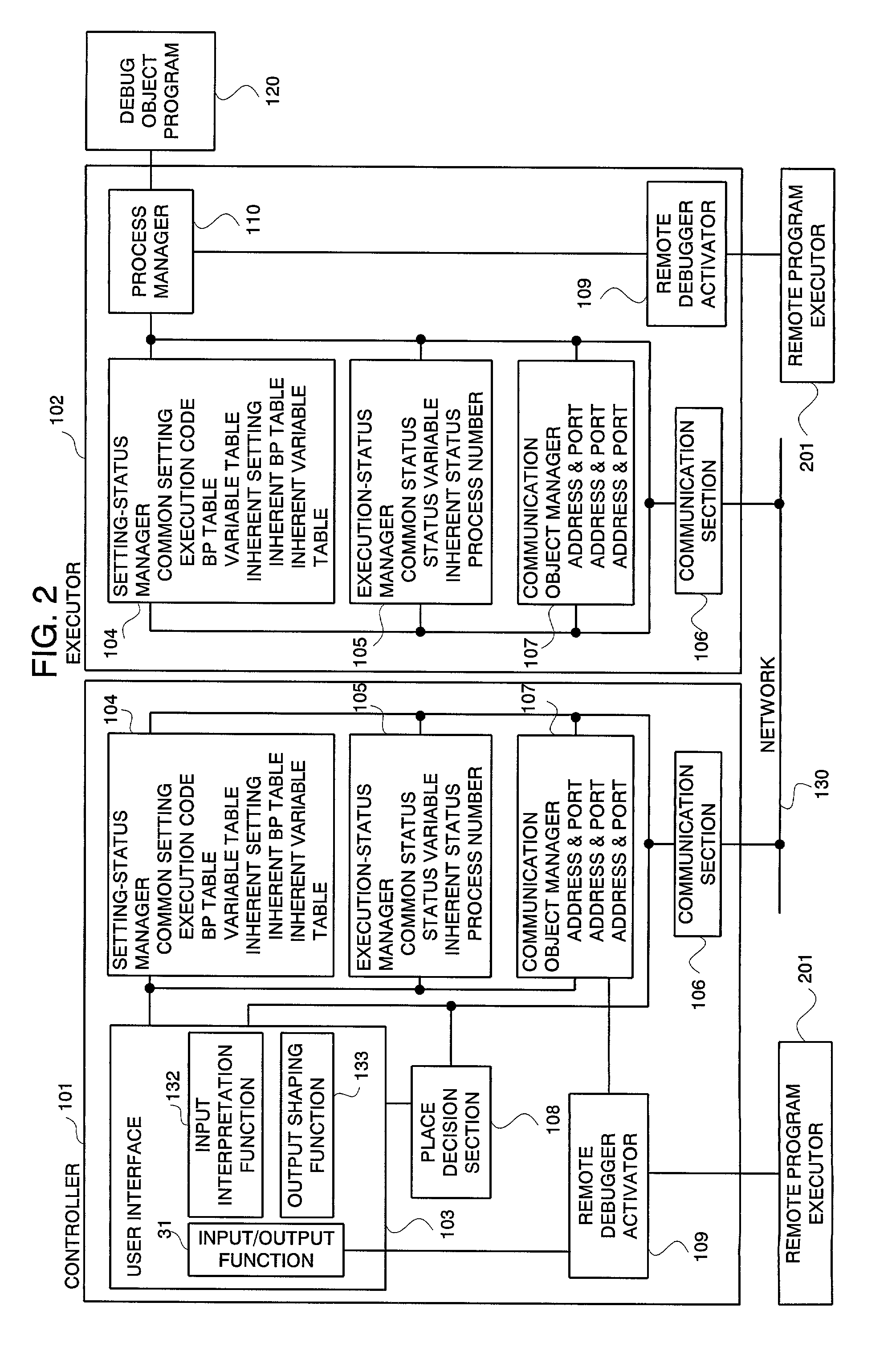
InactiveUS20010004766A1High distributed transparencyEasy to debugDigital computer detailsMultiprogramming arrangementsState managementContent management
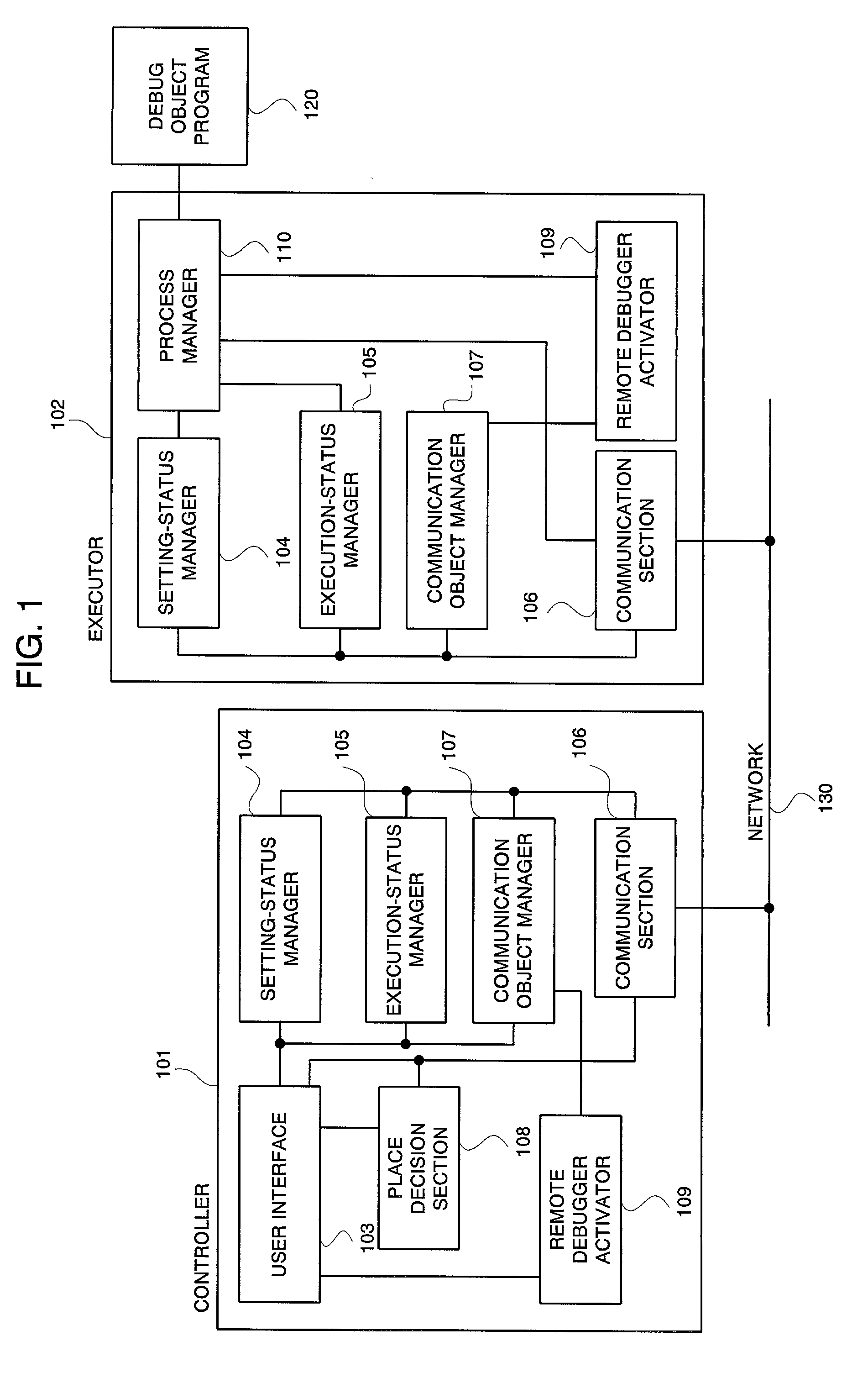
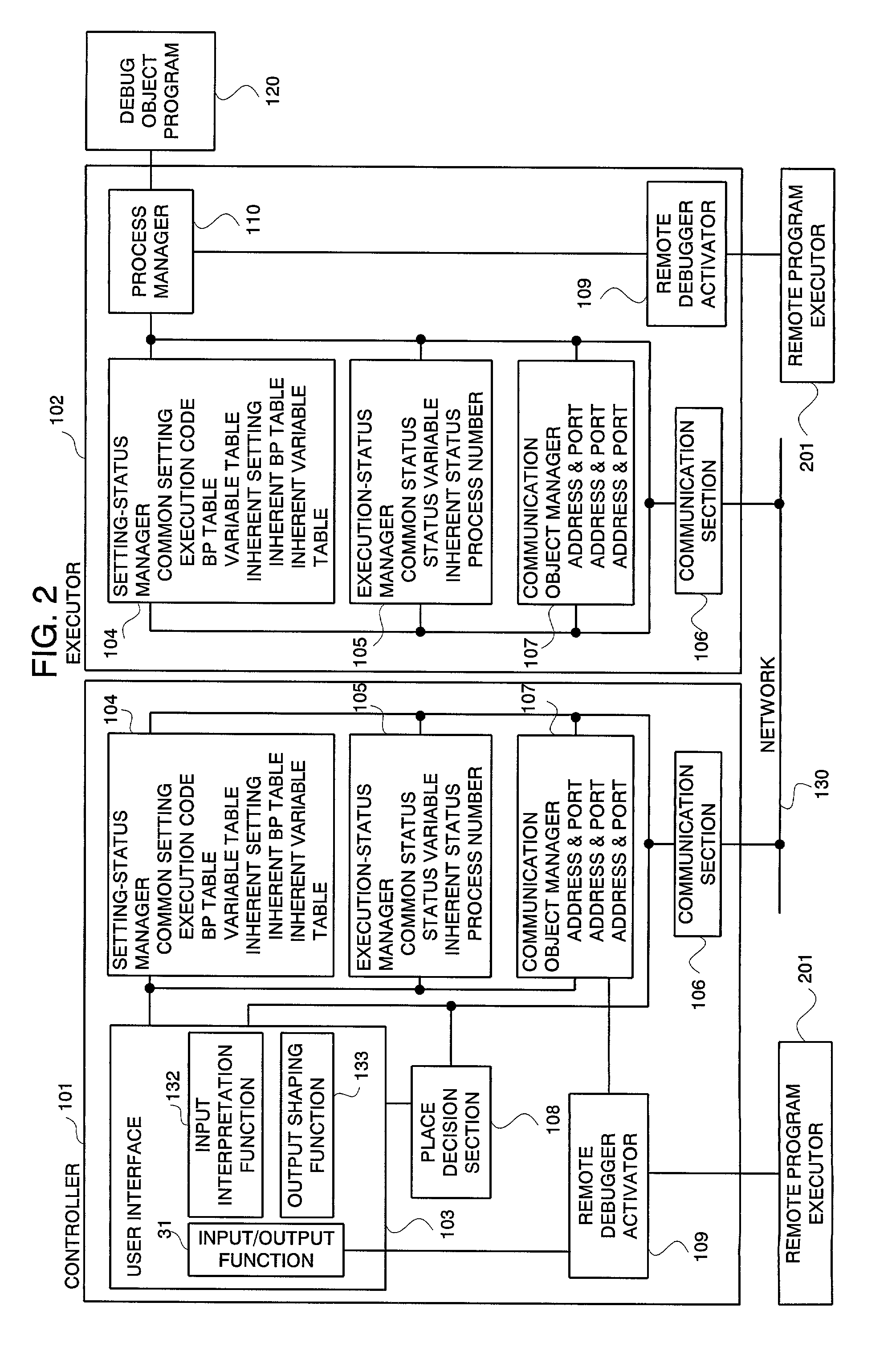
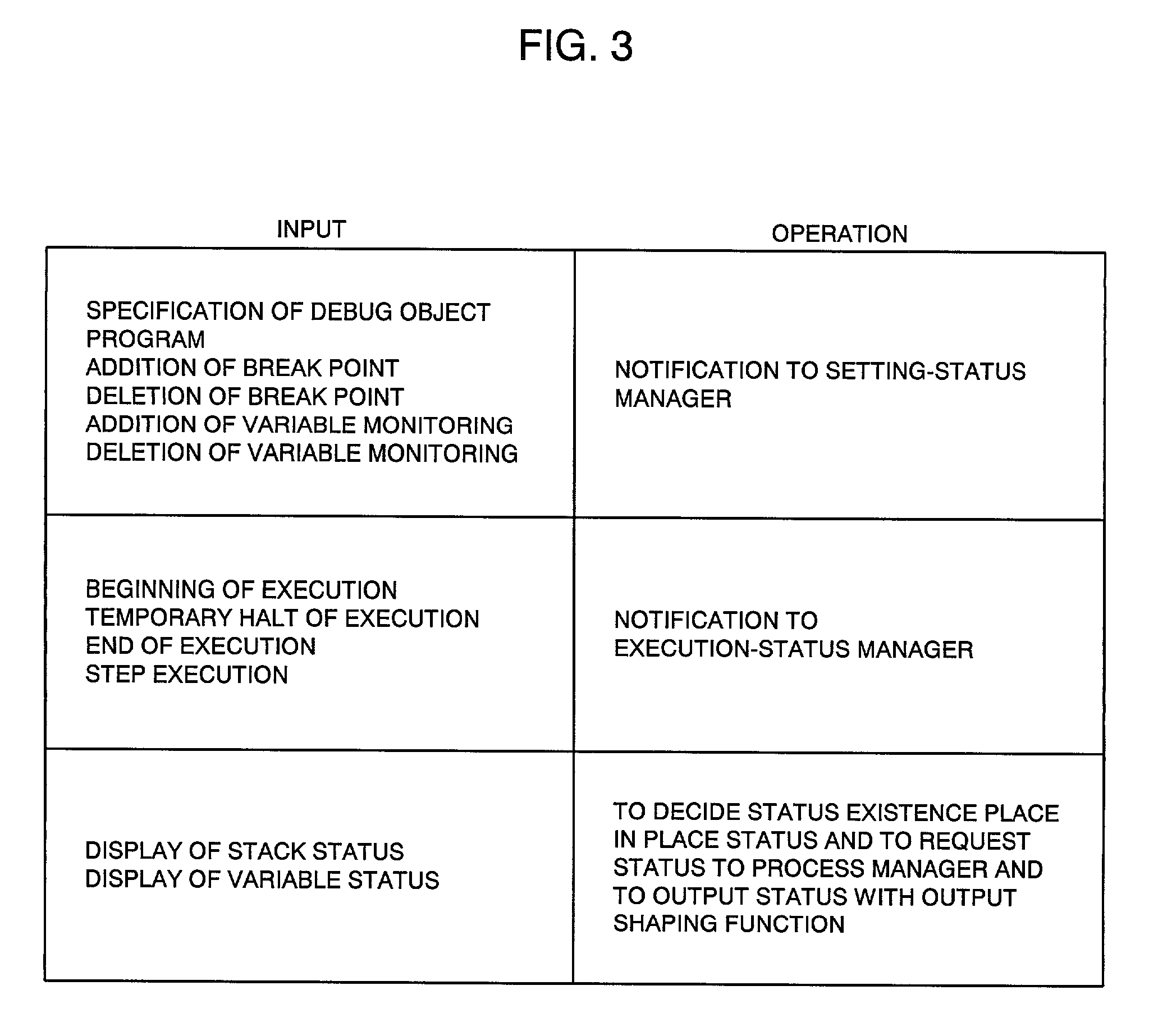
A distributed and transparent debugging environment is provided where, in order to debug a distributed system bridging over plural computers, settings or execution statuses which are respectively managed by debuggers operating on the computers are shared among the debuggers. The controller 101 and the executor 102, each which accepts operations from a user, are disposed on each of plural computers. Each of the controller 101 and the executor 102 has a setting-status manager 104 for managing the setting of a debugger and an execution-status manager 105 for managing the execution status of a debugger. In response to a status change, each of the controller 101 and the executor 102 notifies other computers of the content of the change via the network 130, thus sharing the status. The process manager 110 manages a debug object program according to the content of setting and sets a operation status change due to detection of a break point to the execution-status manager 105. Meanwhile, the process manager 110 changes its operation in response to a change in execution status sent from another computer.
Owner:NEC CORP
Microneedles to be placed in the skin for the transdermal application of pharhmaceuticals
InactiveUS20080167601A1Easy to operateLittle dangerPaper/cardboard articlesDecorative surface effectsActive agentToxin
An array for placement on the skin of a human or animal patient for the purpose of the transdermal application of pharmaceuticals, toxins or active agents, having microneedles that are situated on a carrier substrate, the microneedles having a preset breaking point in the area of the transition to the carrier substrate.
Owner:ROBERT BOSCH GMBH
Vehicle diagnostic tool
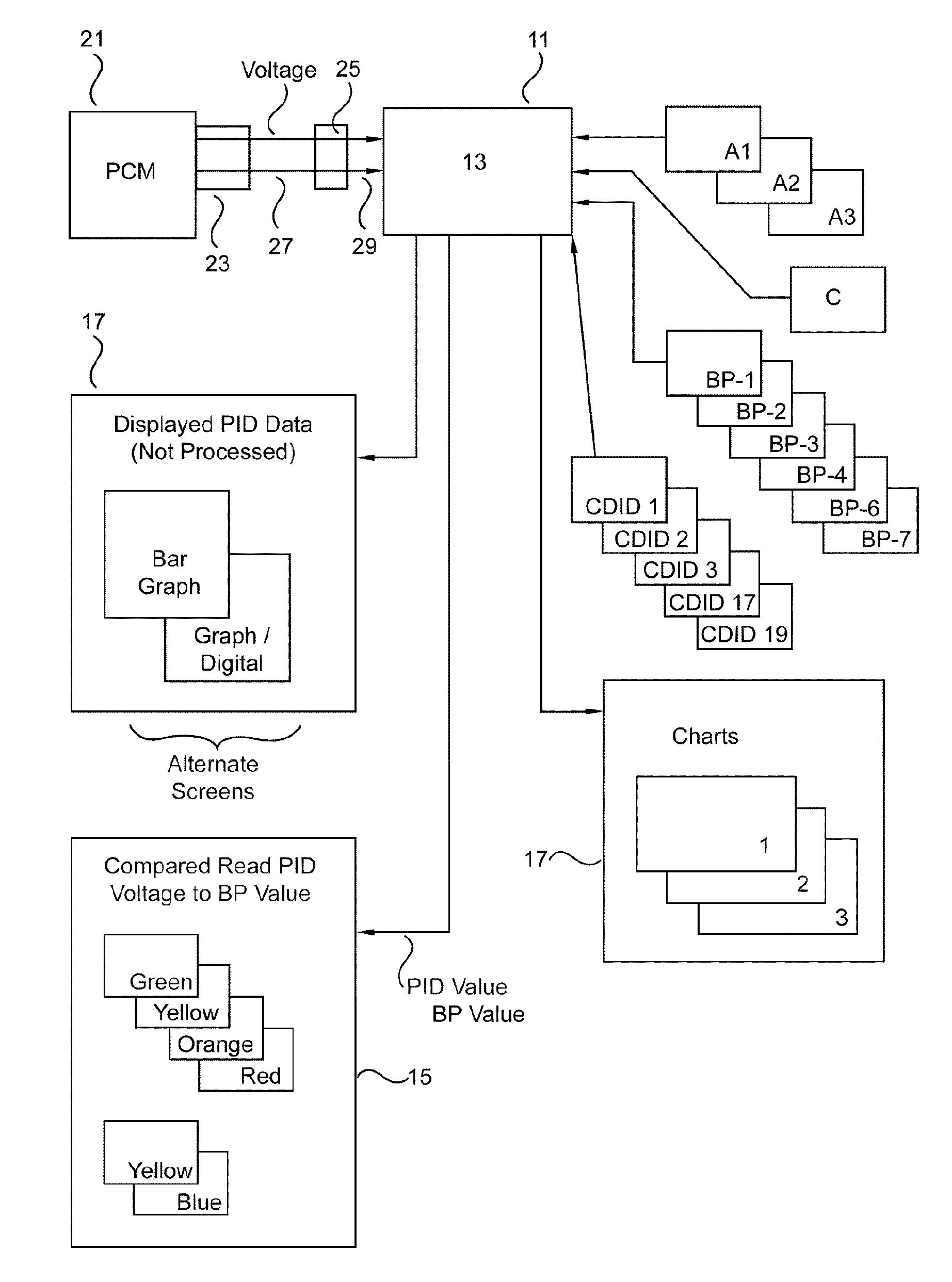
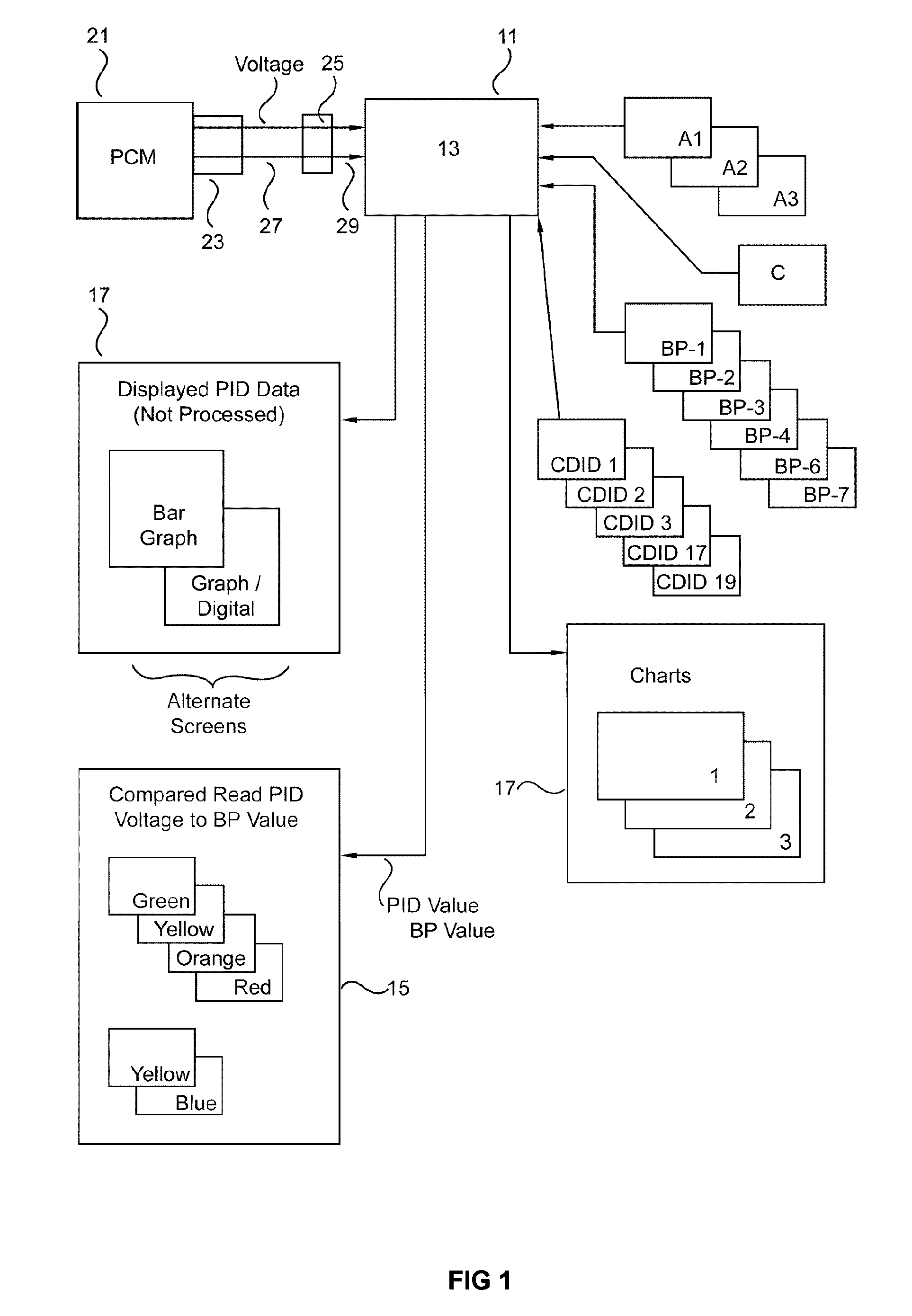
ActiveUS7953530B1Firmly connectedDiagnose the power plant systems quickly and accuratelyVehicle testingAnalogue computers for vehiclesReal-time dataComputer module
An analysis tool which extracts all the available parameter identifications (i.e. PIDS) from a vehicle's power train control module for diagnostic decisions. This is done by checking these PIDS and other information (e.g., calculated PIDS, Break Points, charts and algorithms) in three states; key on engine off, key on engine cranking, key on engine running. In all three modes the tool is comparing the live data from PIDS and voltage to the other information (e.g, Break Points). If any of this data are outside the programmed values a flag is assigned to the failure or control problem. The relationship between a particular PID and its associated preprogrammed value(s) may be indicated by a light. The depth of the problem (if any) is conveyed by the color of the light. Also included are tests / charts for fuel trim, engine volumetric efficiency, simulated injector, power, catalyst efficiency, and engine coolant range.
Owner:AUTOMOTIVE TEST SOLUTIONS
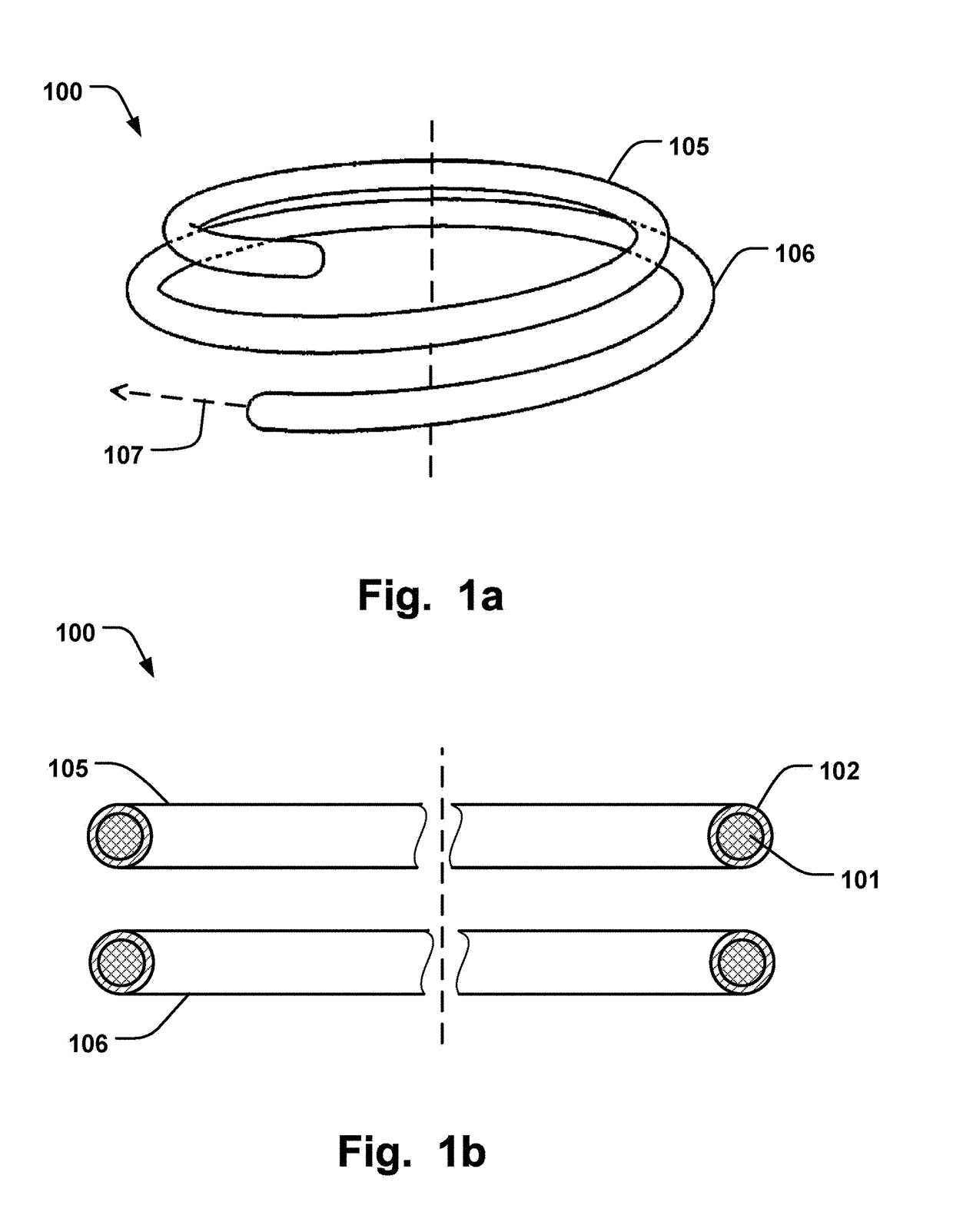
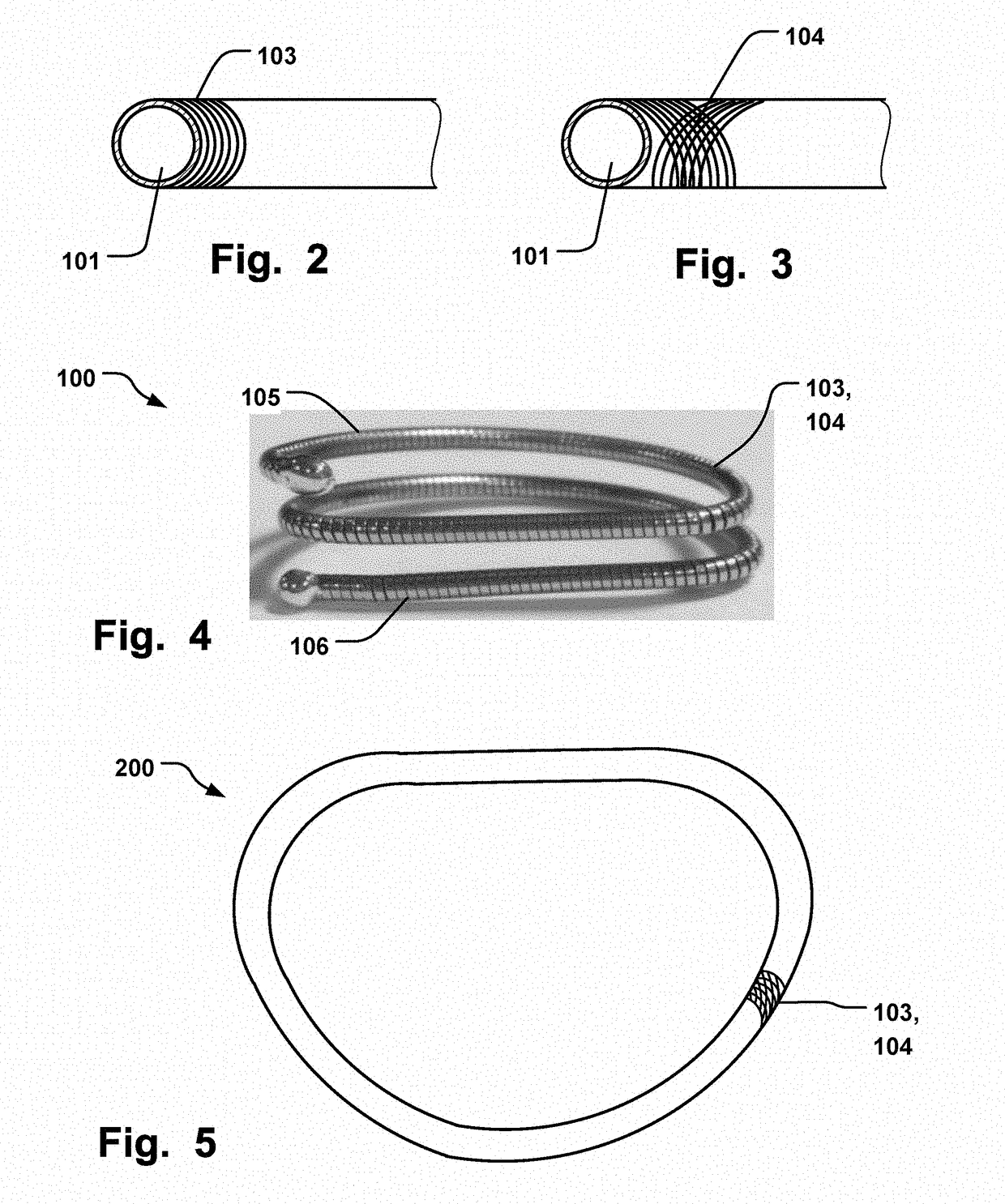
Annuloplasty Implant
InactiveUS20170273788A1Improve securityReduce deliveryAnnuloplasty ringsBreaking pointBiomedical engineering
An annuloplasty implant comprising an inner core of a shape memory material, an outer covering arranged radially outside said inner core material to cover at least part of said inner core, wherein said outer covering is resilient to conform to said inner core during movement of said shape memory material, wherein said outer covering comprises a material having surface properties to promote endothelialization. Two portions of the implant may be joined by a recess to be flexible with respect to each other by a bending motion at the recess. The two portions may also have a predefined breaking point at the recess.
Owner:MEDTENTIA INT LTD OY
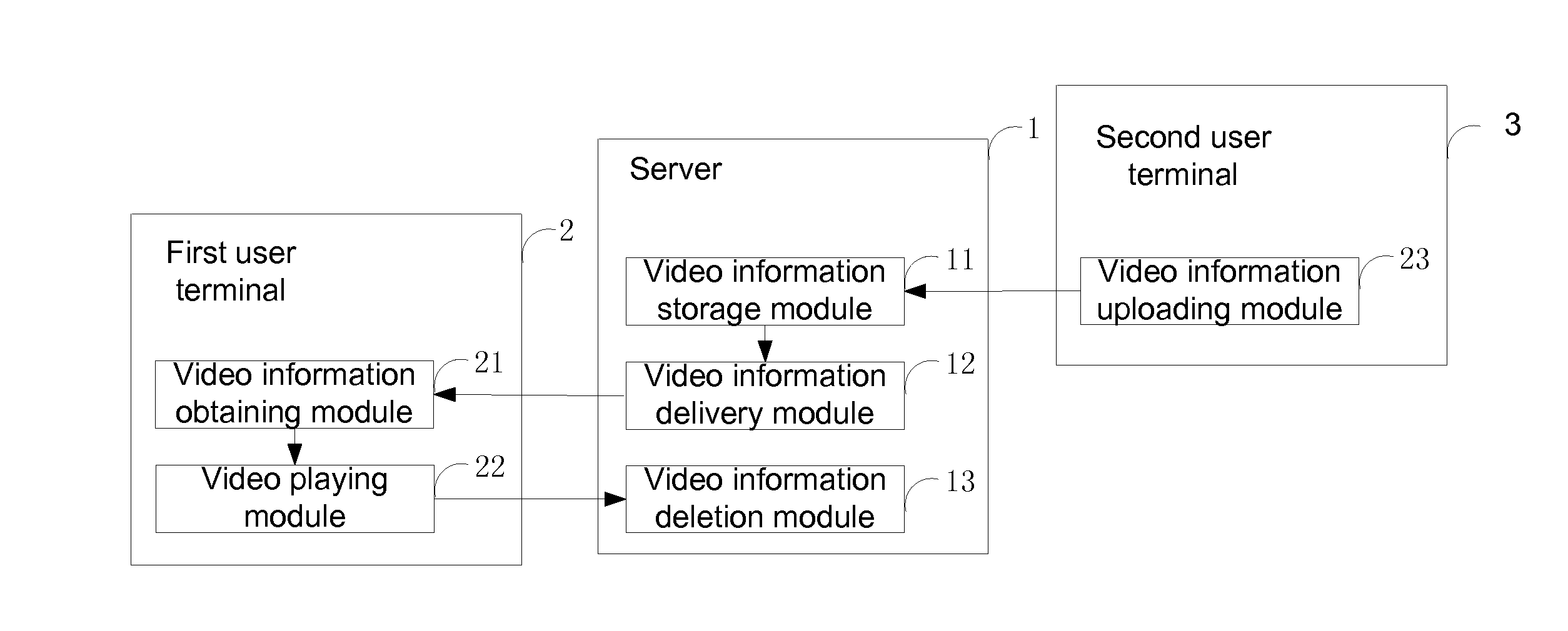
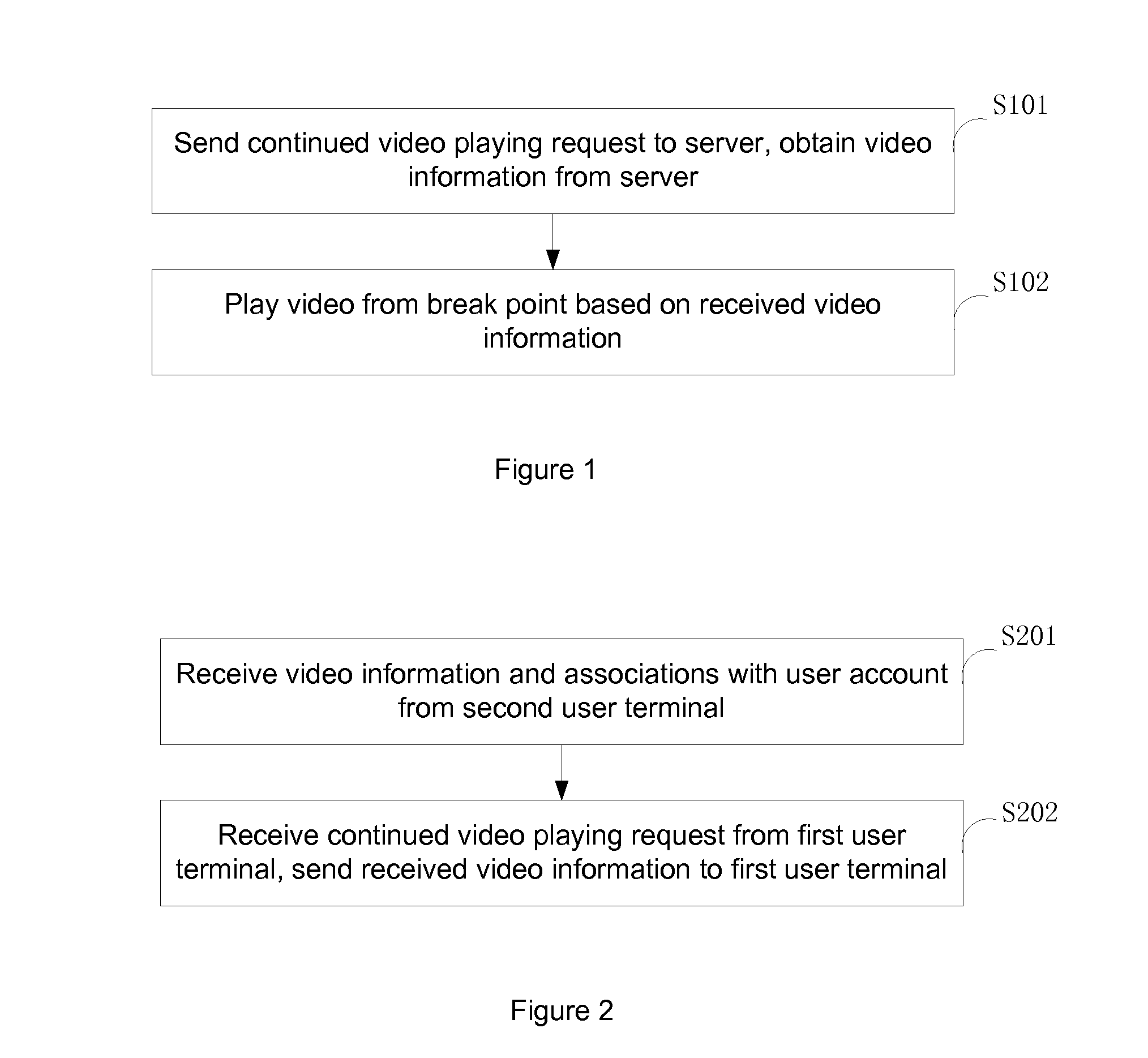
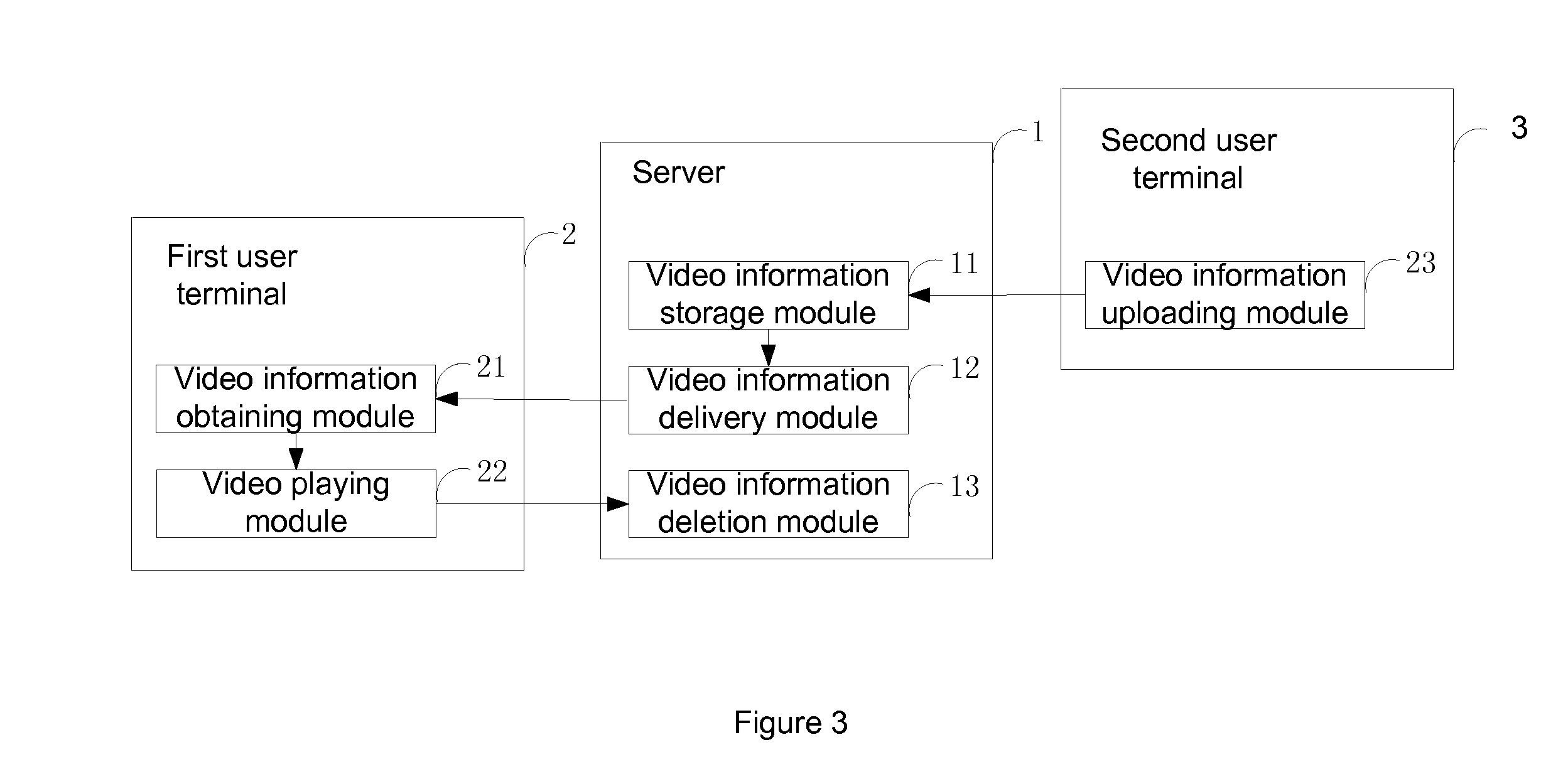
Methods and systems for playing video on multiple terminals
InactiveUS20140298395A1Improve user experienceEffective synchronizationTwo-way working systemsSelective content distributionBreak pointBreaking point
A method and system for synchronized video playing across multiple user terminals are disclosed. The method includes sending a continued video playing request to a server from a first user terminal to play a video from a break point, receiving video information from the server, the video information being submitted from a second user terminal, and playing the video from the break point based on the received video information. The method and system consistent with the present disclosure may improve a user's video watching experience by enabling a user to seamless switch between different user terminals.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Method and device for testing network cable failure
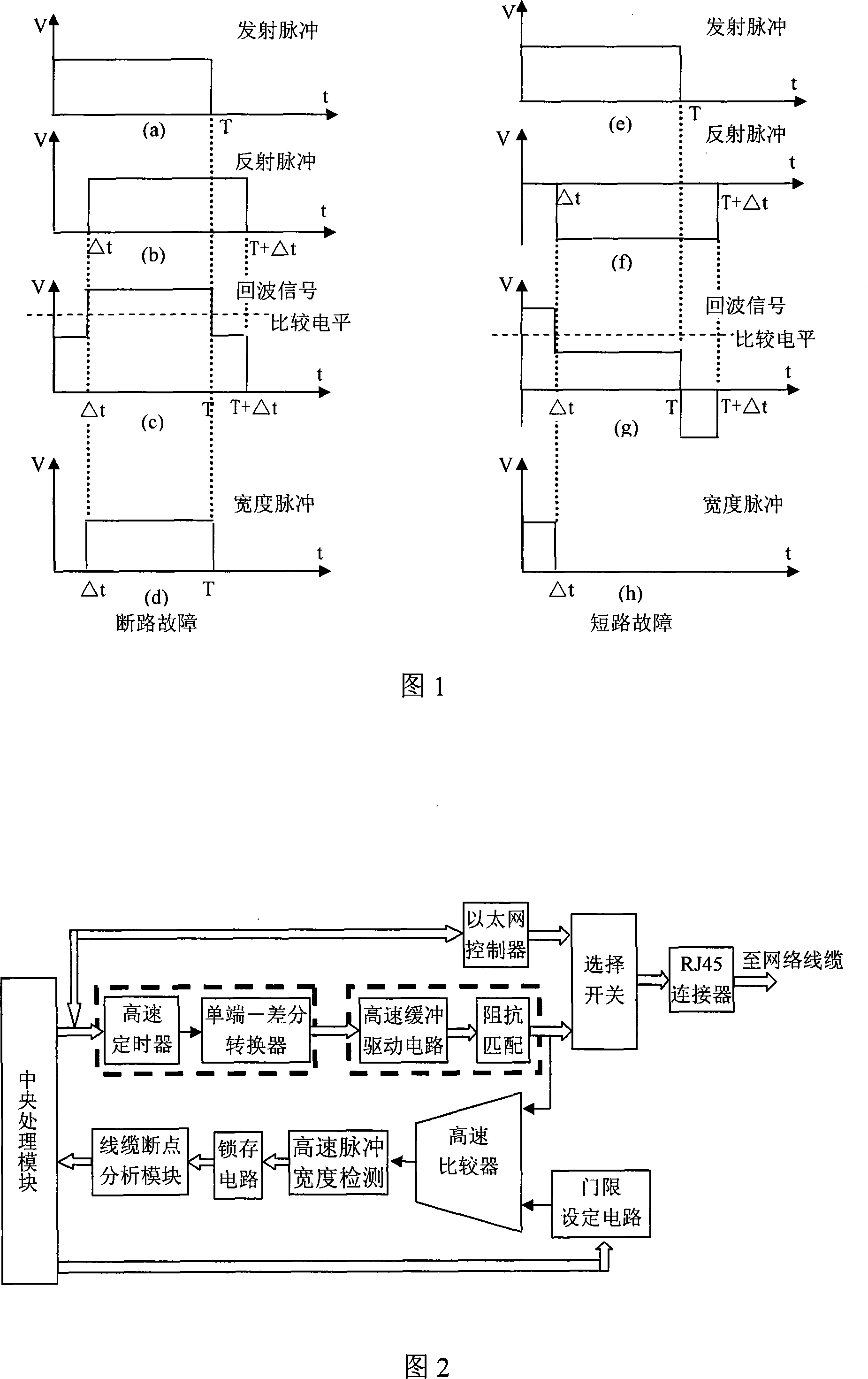
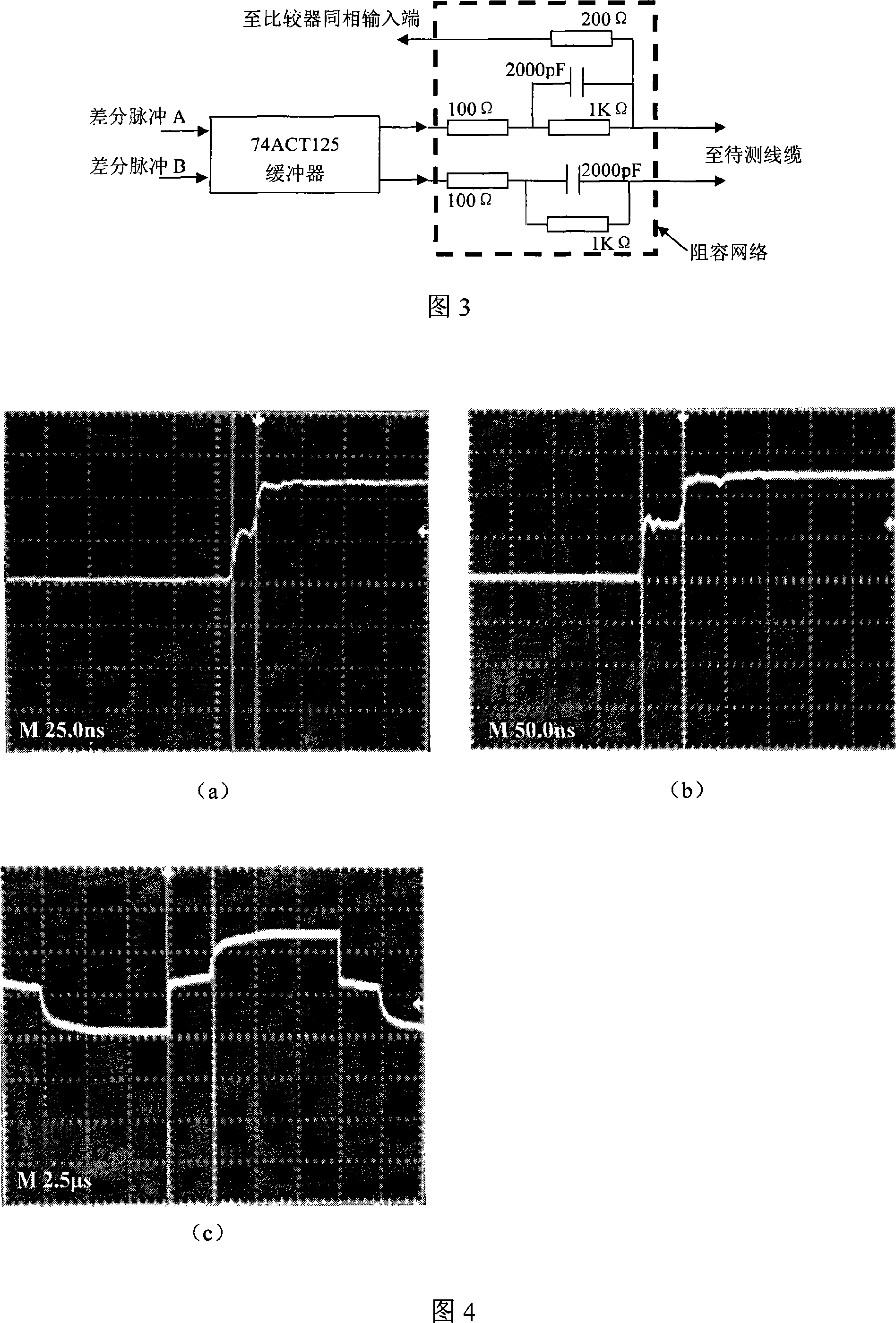
InactiveCN101127928AAccurate locationExact cause of failureFault locationSelection arrangementsCoaxial cableEnvironmental effect
The utility model provides a fault testing proposal over network cables. Wider differential detection pulses are sent out from a testing end. When encountering a break point on the cable, the detection pulses are reflected, and the reflected pulses are transmitted back to the sending end along the cable. The sending signal and the reflected signal are mutually superposed, and the time interval between the sending and reflected signals is calculated by measuring the time width of the superposed part; then the position and cause of the failure can be analyzed out. The proposal in the utility model also provides a relevant network cable tester. Four pairs of twisted network cables can be tested just by connecting any end of the network cable with the tester. The tester in the utility model has advantages of simple operation, high resolution and negligible environmental impact. Beside application in network cable fault testing, the testing proposal and device in the utility model can be also used in coaxial cable fault testing.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Crop yield prediction using piecewise linear regression with a break point and weather and agricultural parameters
InactiveUS7702597B2Climate change adaptationAnalogue computers for chemical processesMultivariable optimizationNon linear methods
Owner:GEORGE MASON INTPROP INC
Automatic grading method and automatic grading equipment for read questions in test of spoken English
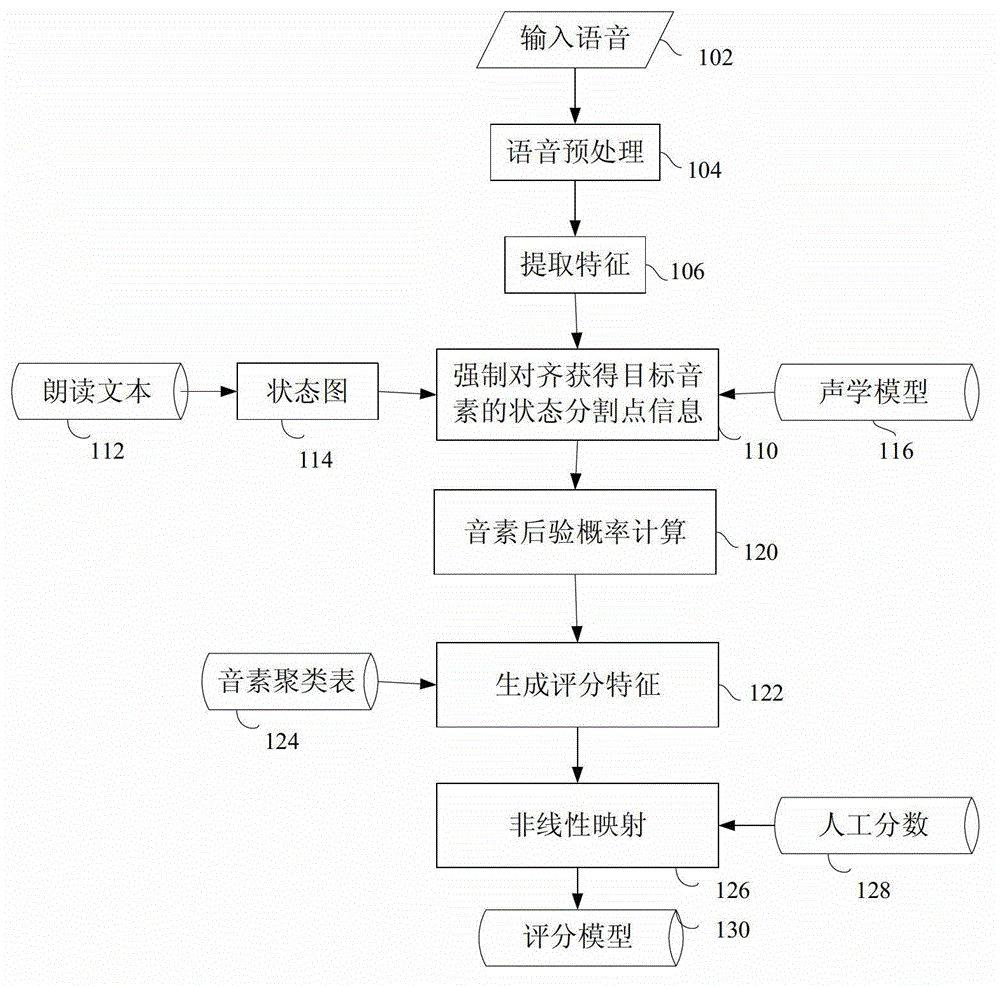
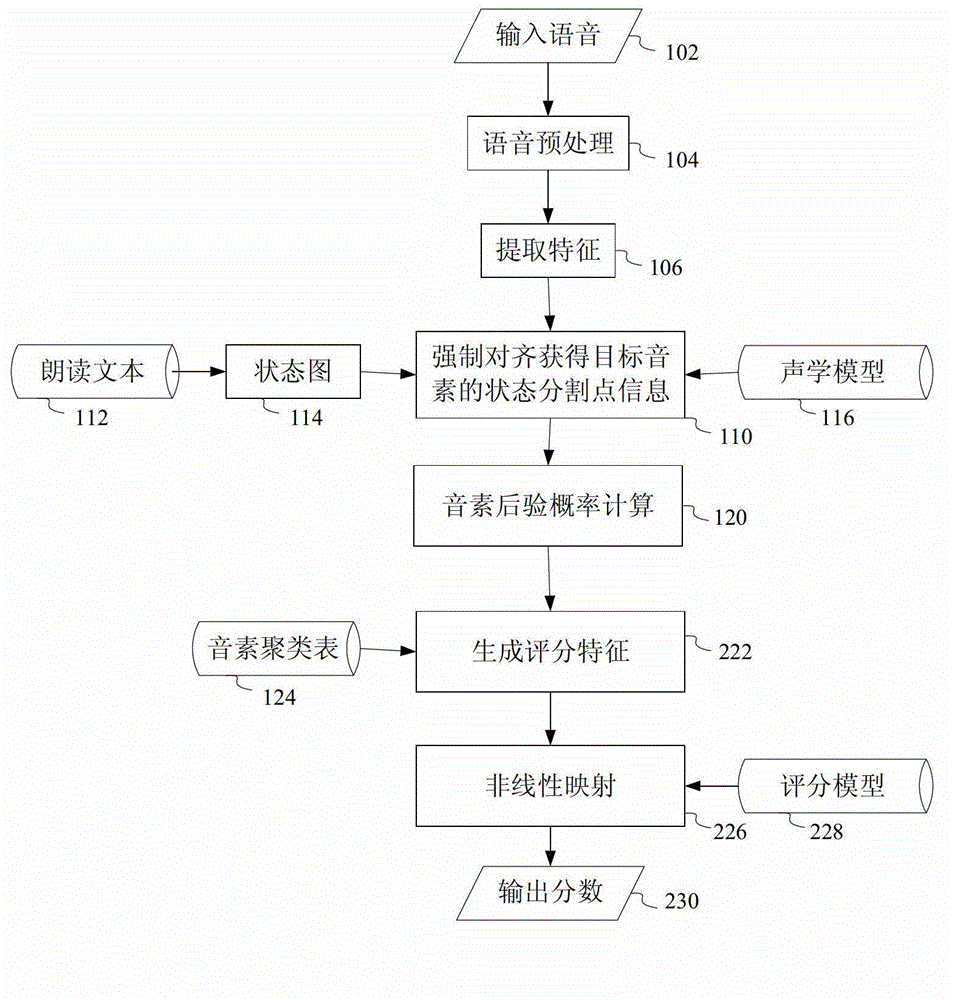
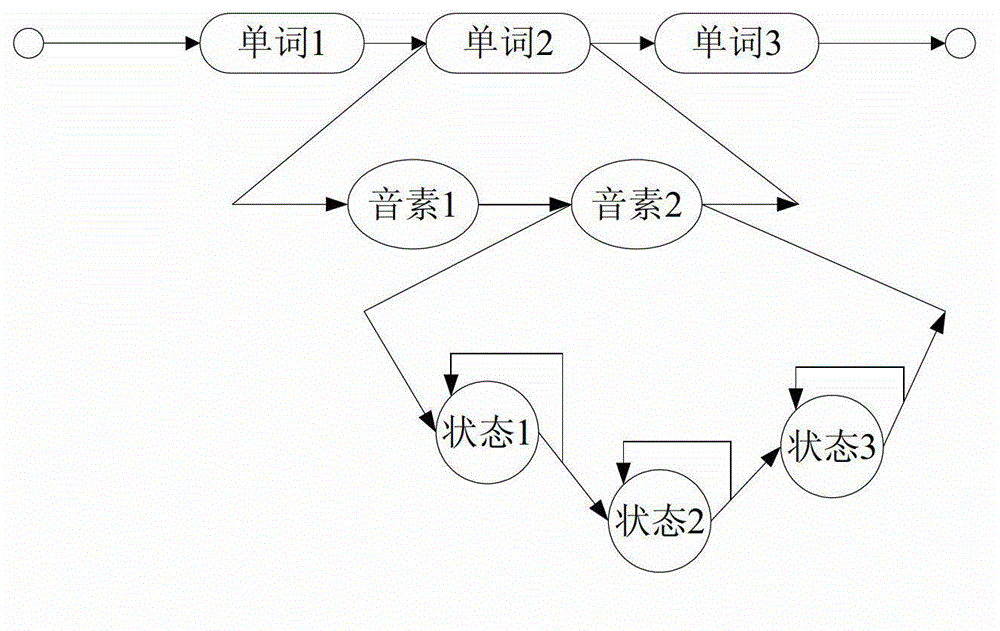
ActiveCN103065626ADoes not deviate from human scoringSpeech recognitionTeaching apparatusSpoken languageAlgorithm
The invention provides an automatic grading method and automatic grading equipment for read questions in a test of spoken English. According to the automatic grading method, preprocessing is carried out on input voice; the preprocessing comprises framing processing; phonetic feature is extracted from the preprocessed voice; by means of a linear grammar network and an acoustic model set up by reading texts, phonetic feature vector order is forcedly aligned to acquire information of the each break point of each phoneme; according to the information of the each break point of each phoneme, the posterior probability of each phoneme is calculated; based on the posterior probability of each phoneme, multi-dimensional grading characteristics are extracted; and based on the grading characteristics and manual grading information, a nonlinear regression model is trained by means of a support vector regression method, so that the nonlinear regression model is utilized to grade on reading of spoken English. The grading model is trained by means of expert scoring data, and therefore a result of machining grading is guaranteed not to deviate from a manual grading result in statistics, and the high simulation of a computer on the expert grading is achieved.
Owner:INST OF ACOUSTICS CHINESE ACAD OF SCI +1
System and method for distributed debugging and recording medium on which control programs are recorded
InactiveUS6961926B2High distributed transparencyEasy to debugDigital computer detailsMultiprogramming arrangementsState managementActuator
For a distributed and transparent debugging environment, a controller and an executor, each which accepts operations from a user, are disposed on each of plural computers. The controller and the executor each has a setting-status manager for managing the setting of a debugger and an execution-status manager for managing the execution status of a debugger. In response to a status change, the controller and the executor each notifies other computers of the content of the change via the network. A process manager manages a debug object program according to the content of setting and sets an operation status change due to detection of a break point to an execution-status manager. Meanwhile, the process manager changes its operation in response to a change in execution status sent from another computer.
Owner:NEC CORP
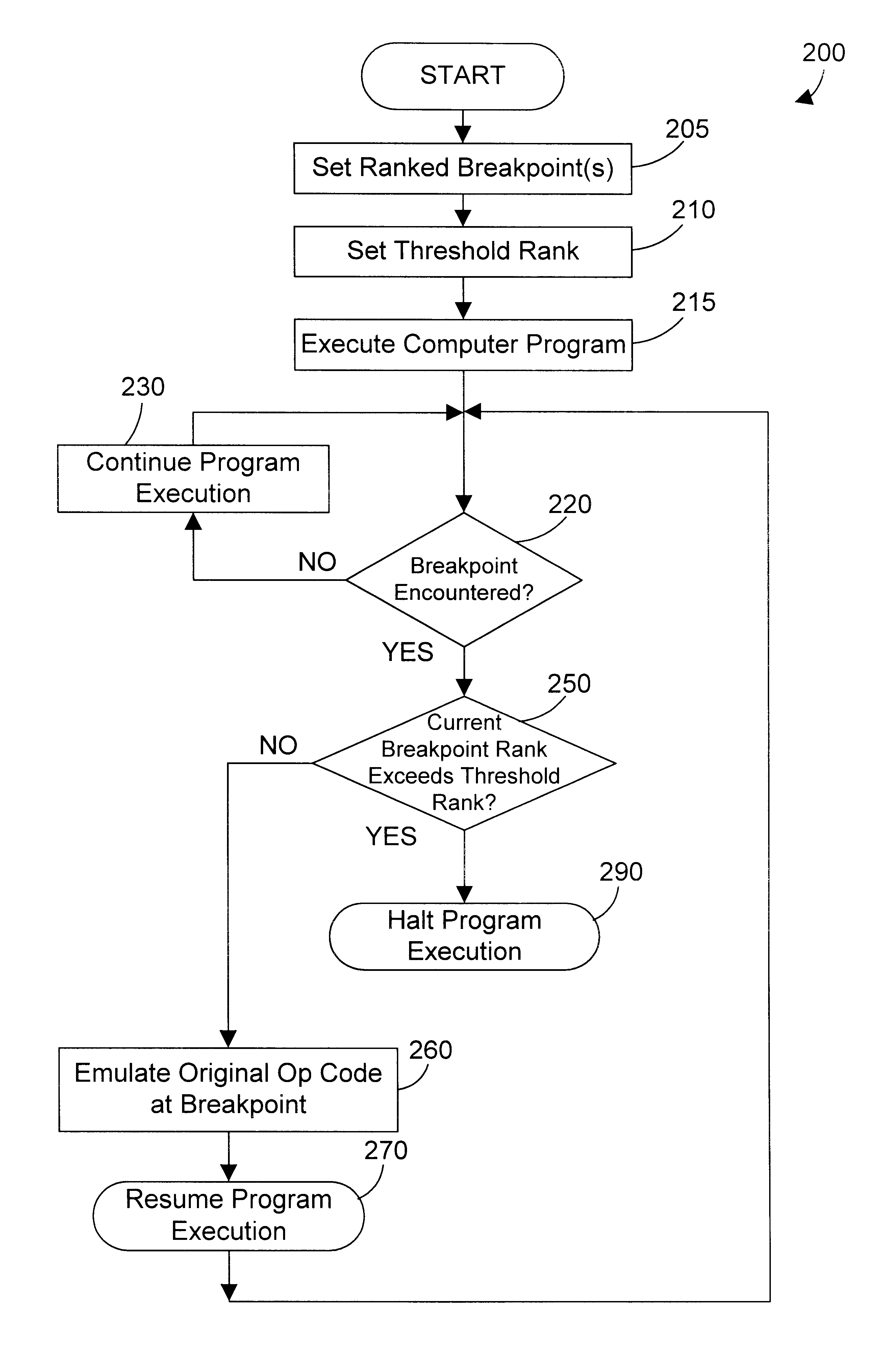
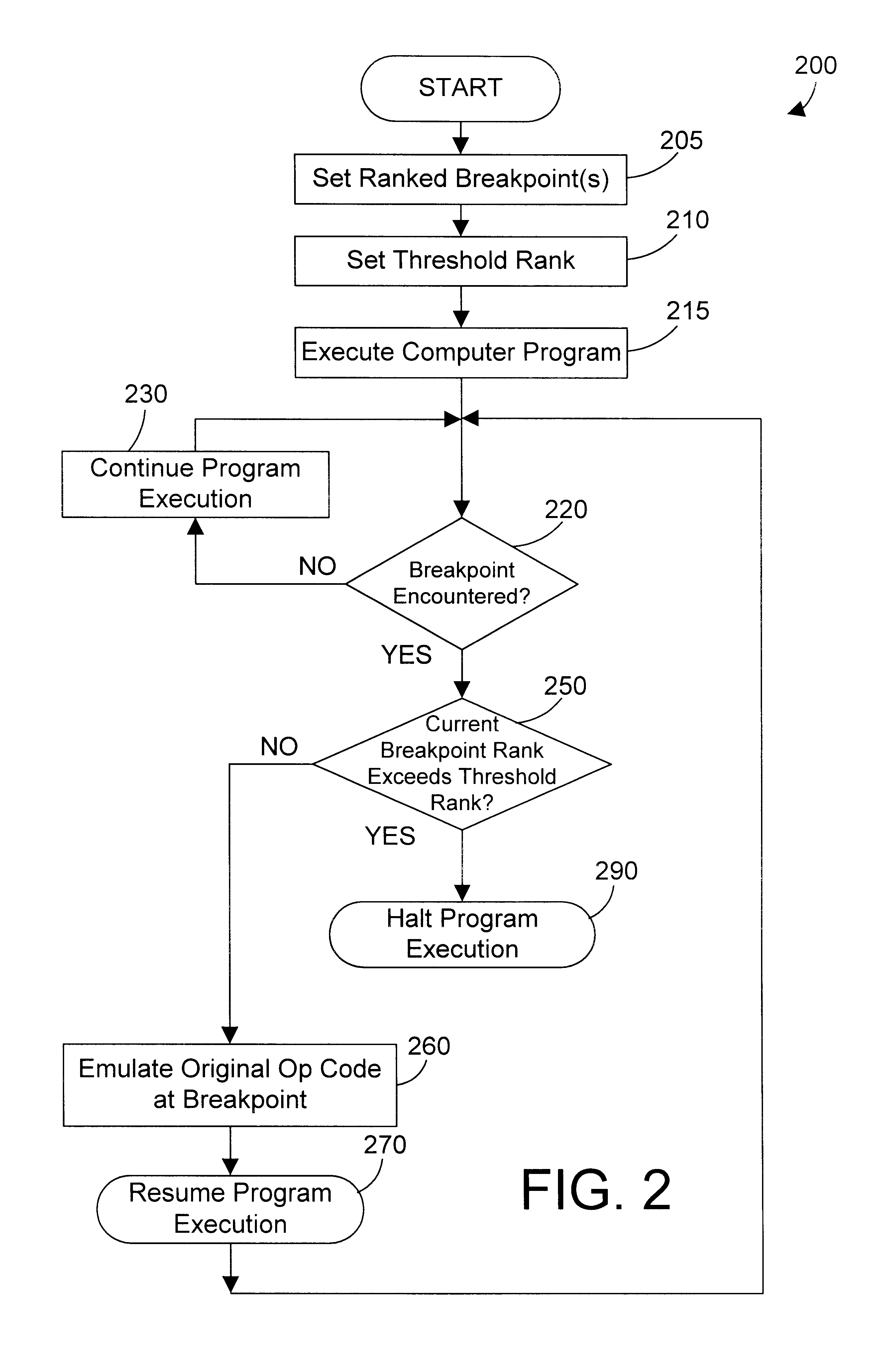
Ranked break points and method for debugging a computer program
InactiveUS6543049B1Software testing/debuggingSpecific program execution arrangementsBreaking pointDebugger
Ranked breakpoints are defined in a computer program that allow a debugger to determine whether or not to halt execution of the computer program when a ranked breakpoint is encountered based on the rank of the breakpoint compared to a threshold rank. In a preferred embodiment, the threshold rank is the rank of a RunTo function, and the ranked breakpoints only halt execution of the computer program if their rank is higher than the threshold rank of the RunTo function. The present invention thus provides a mechanism for ignoring some or all breakpoints in a computer program when performing debugger functions, such as a RunTo function.
Owner:IBM CORP
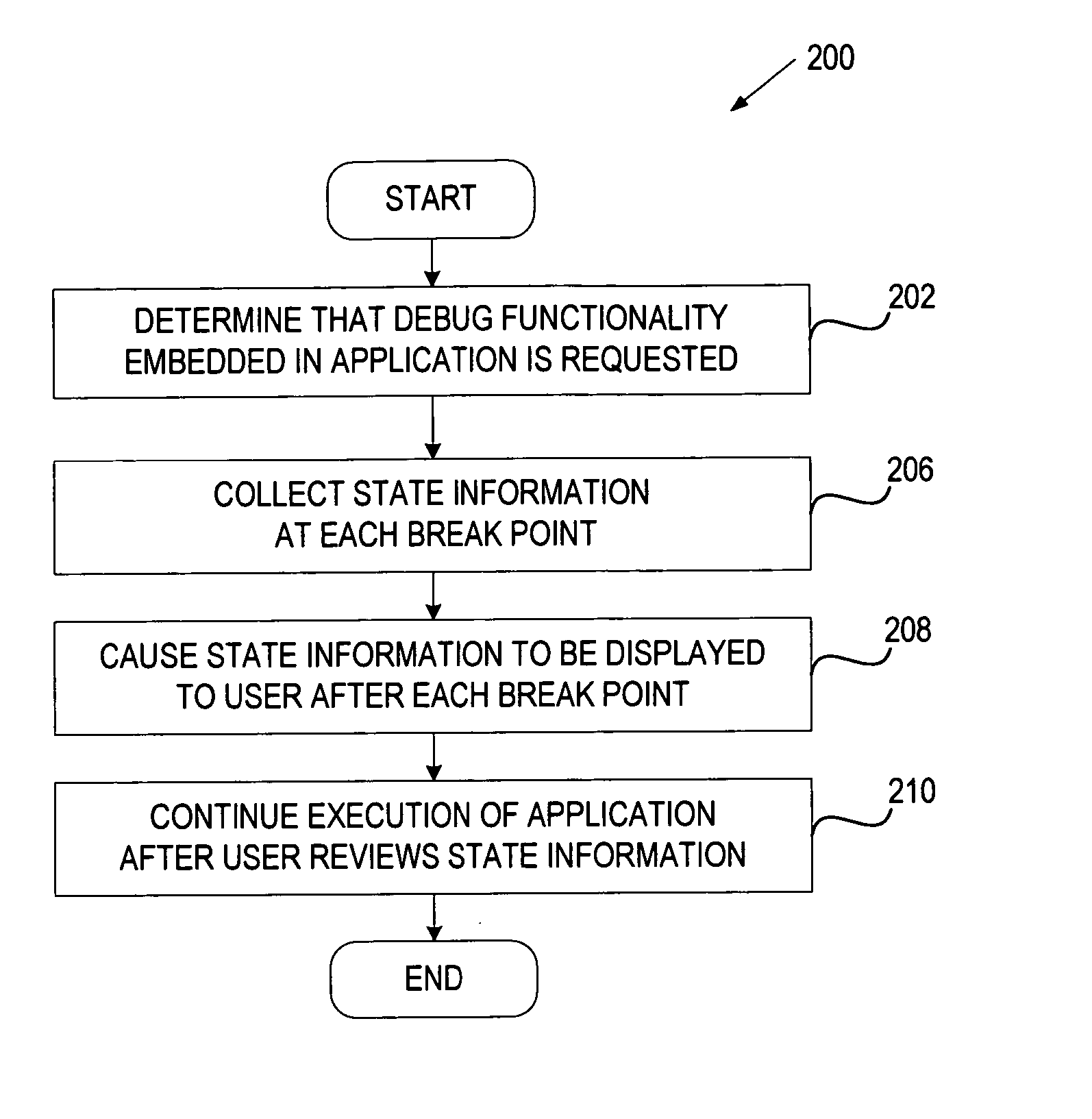
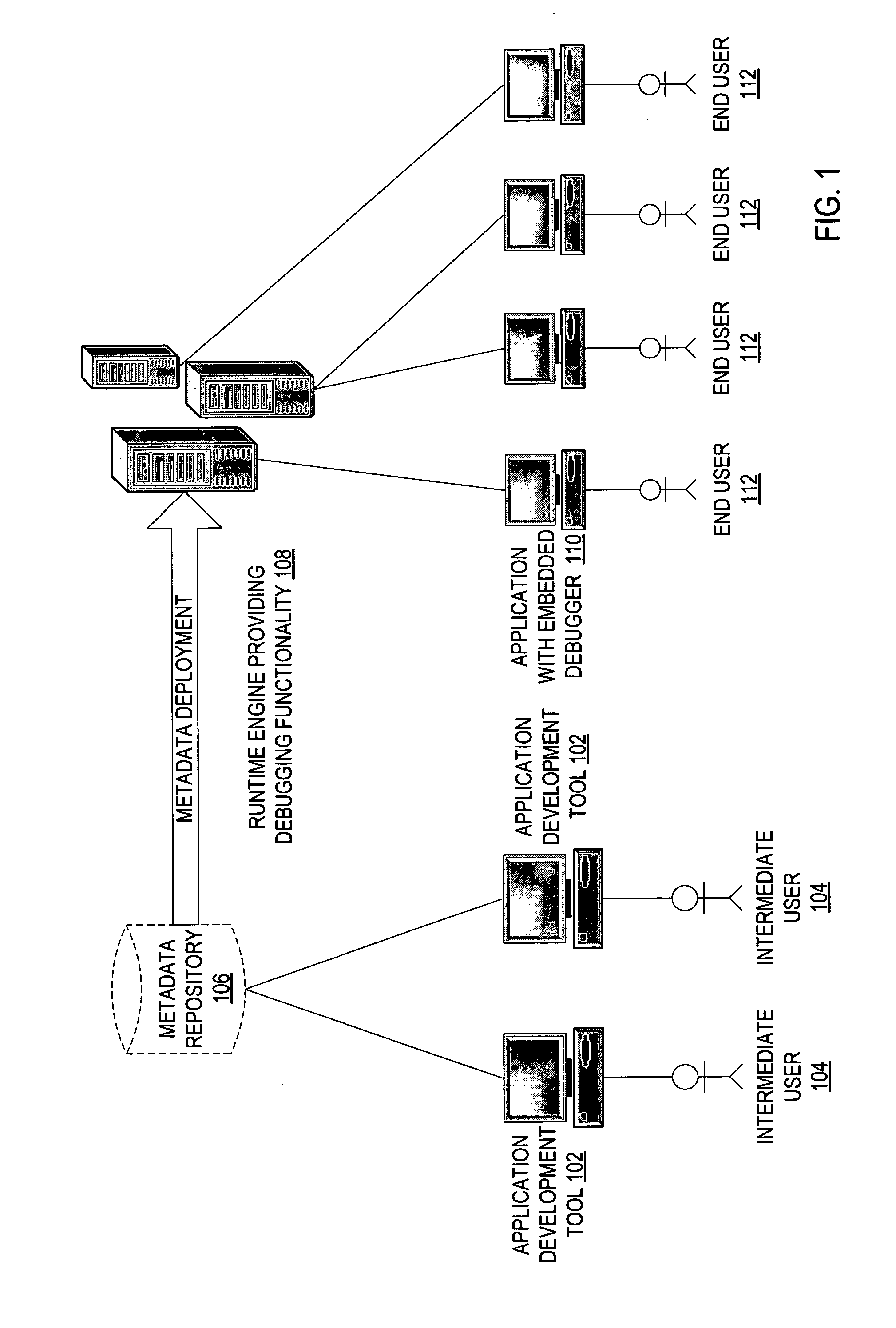
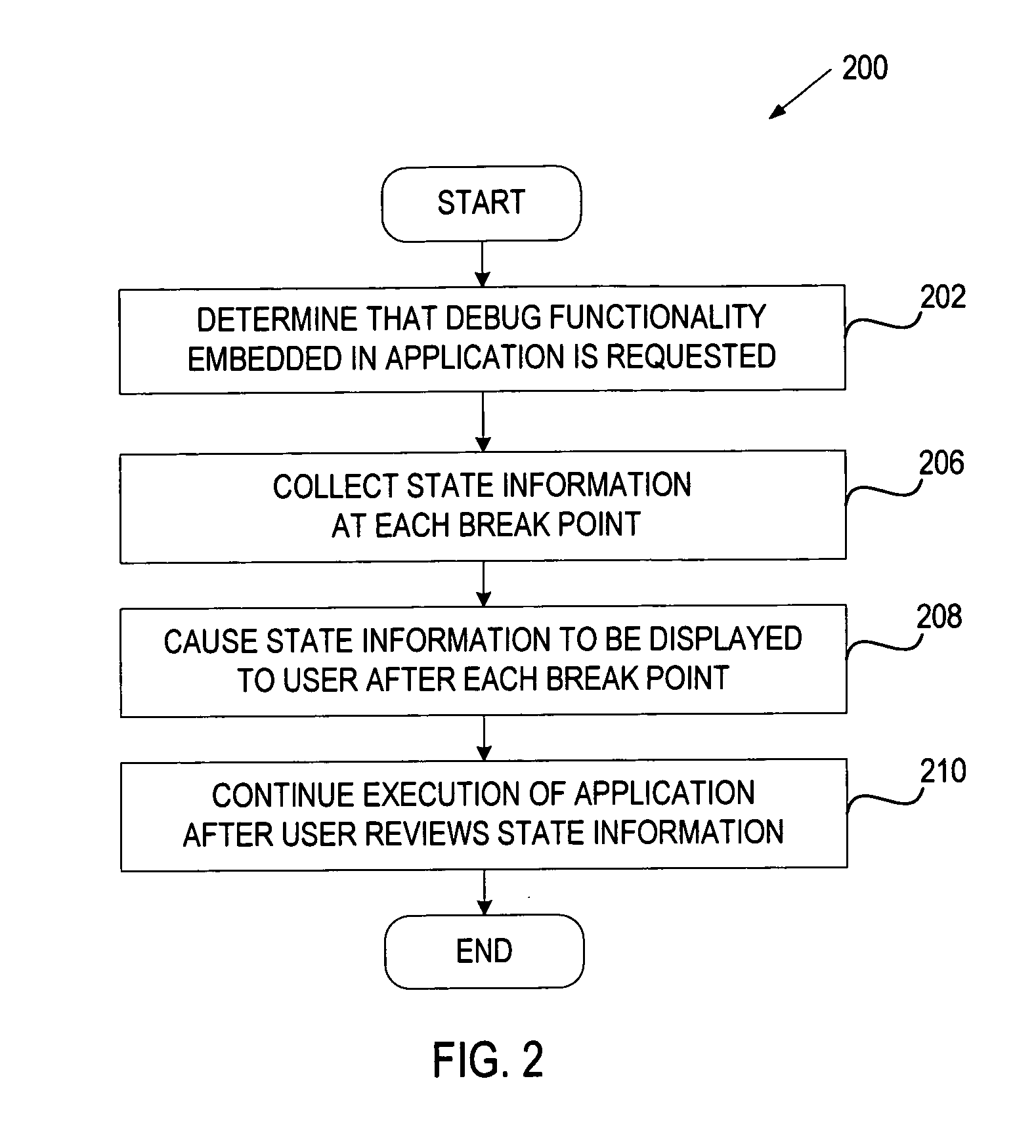
Debugging functionality embedded in an application
ActiveUS20070240125A1Hardware monitoringSpecific program execution arrangementsEmbedded systemBreaking point
In one embodiment, a method for providing a debugging functionality embedded in an application supporting an n-tiered architecture includes determining that the debugging functionality embedded in the application is requested, and causing current state information to be presented to a user at each break point in the production environment.
Owner:ORACLE CORPORATION +1
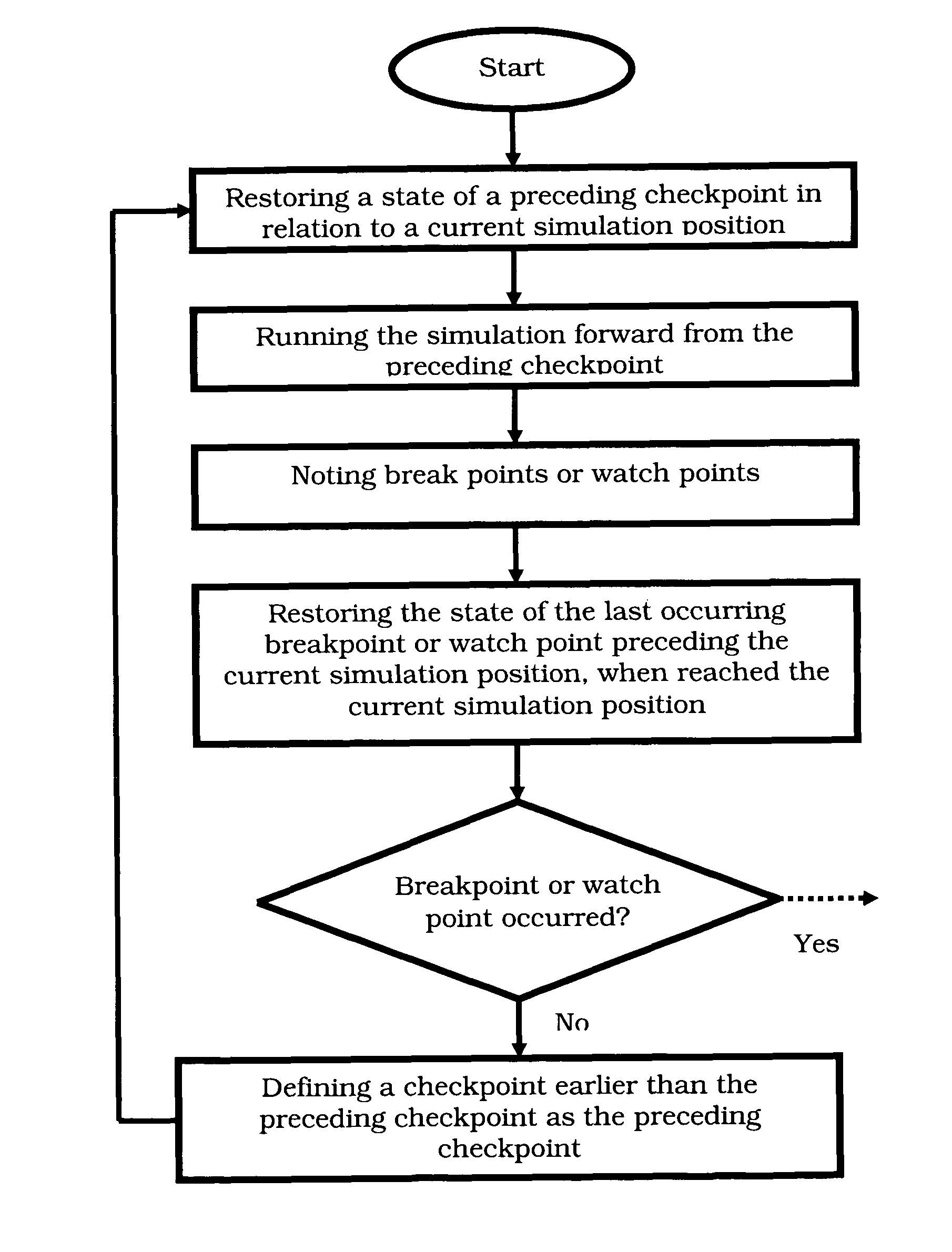
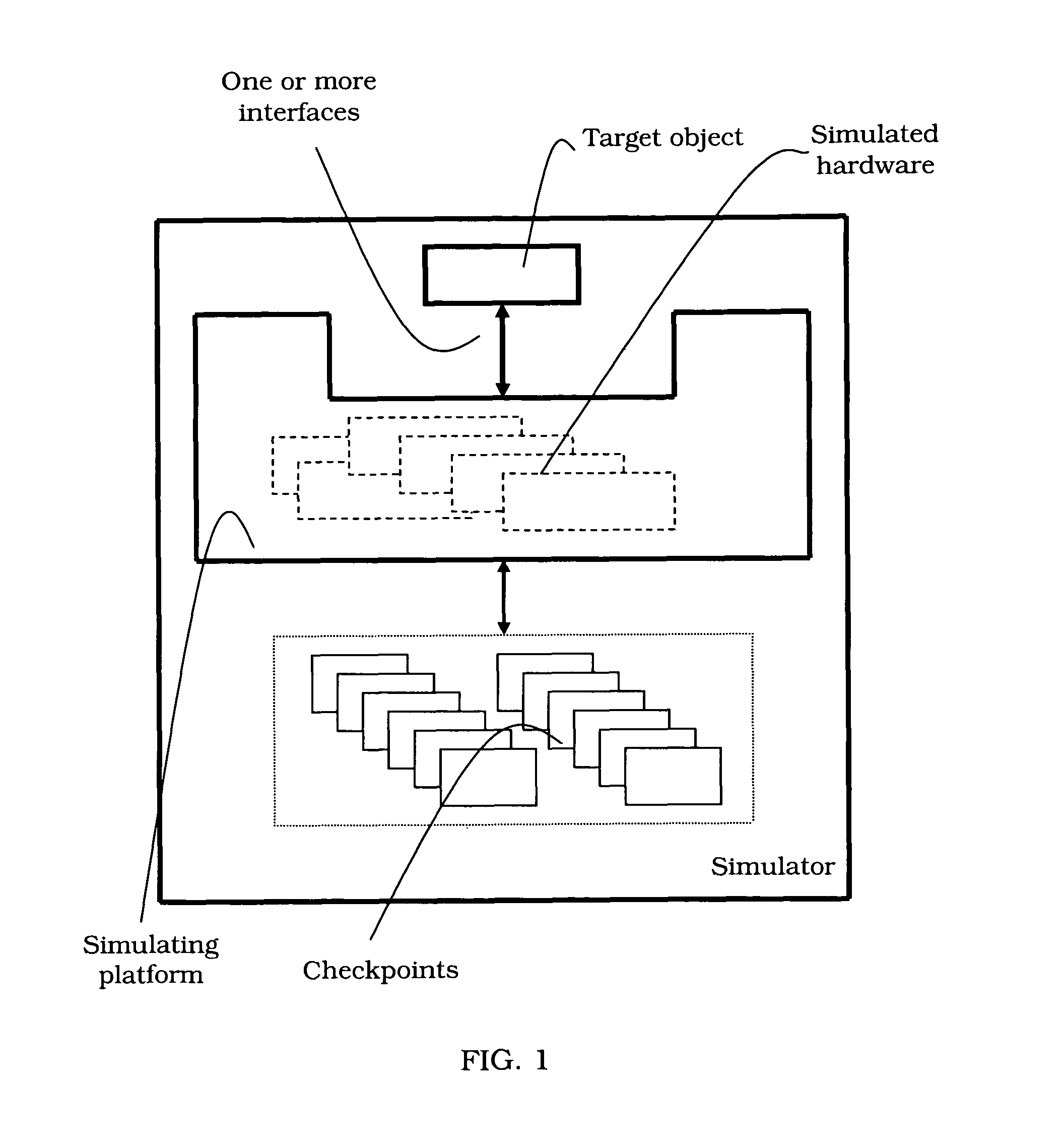
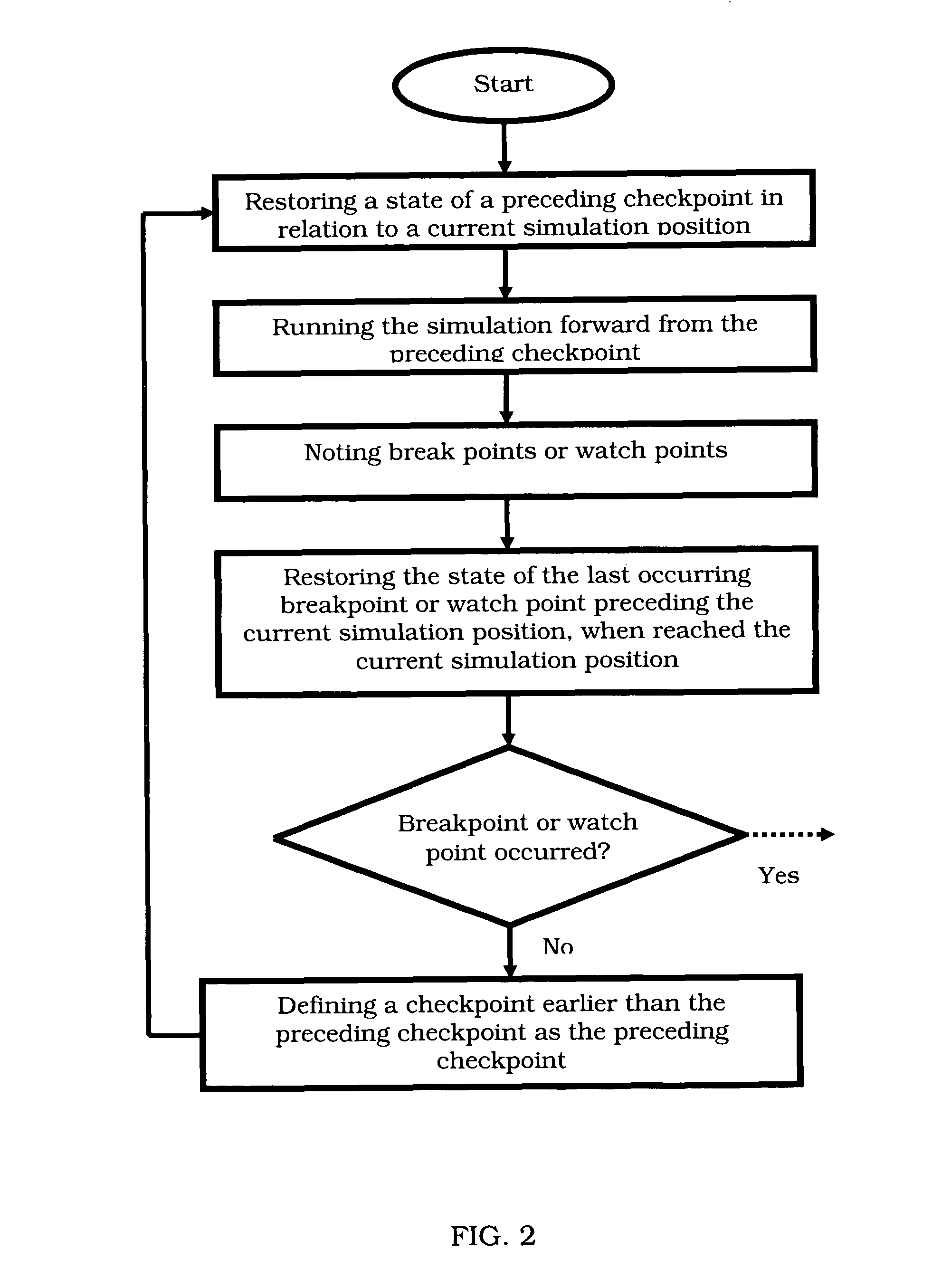
Devices, methods and computer program products for reverse execution of a simulation
InactiveUS7849450B1Error detection/correctionSpecific program execution arrangementsReverse executionObservation point
Devices, methods, and software program products for reverse execution of a simulation and / or tracing a value are provided. A state of a preceding checkpoint may be restored and a simulation may be run forward. Break points or watch points may be noted and the state of the last occurring breakpoint or watch point preceding the current simulation position may be restored. If no breakpoint or watch point occurred, an earlier checkpoint may be loaded and the previous steps may be repeated.
Owner:INTEL CORP
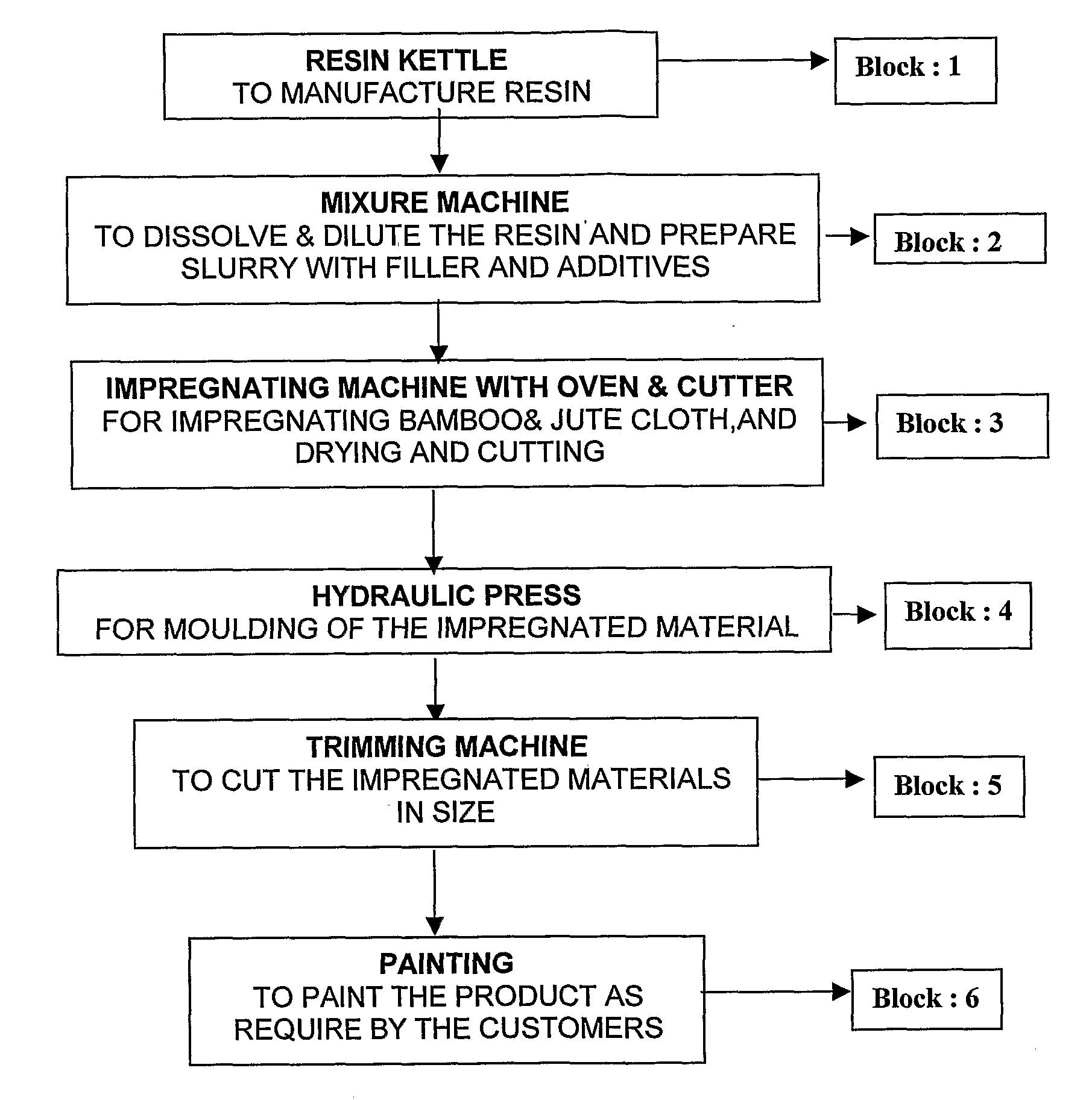
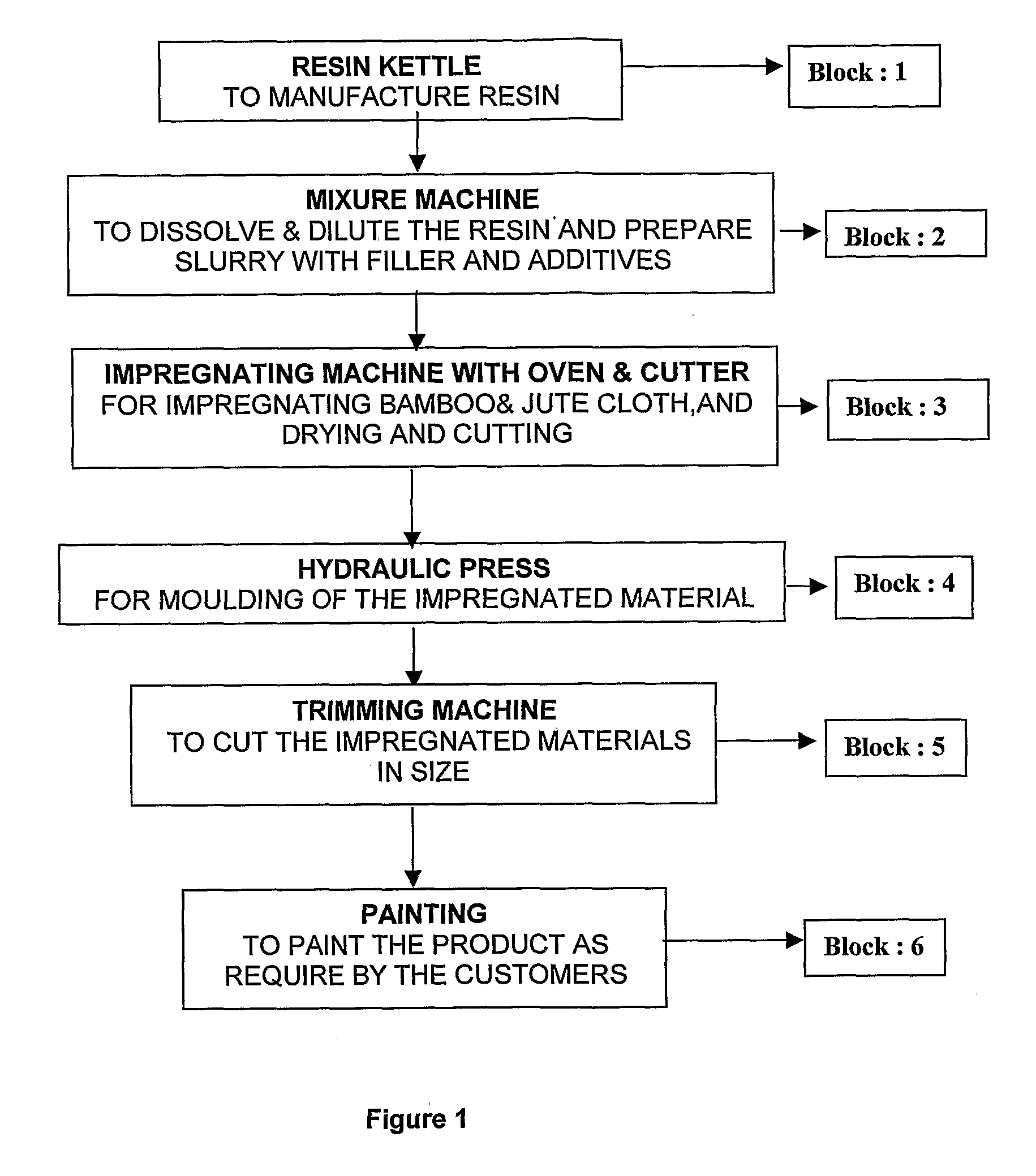
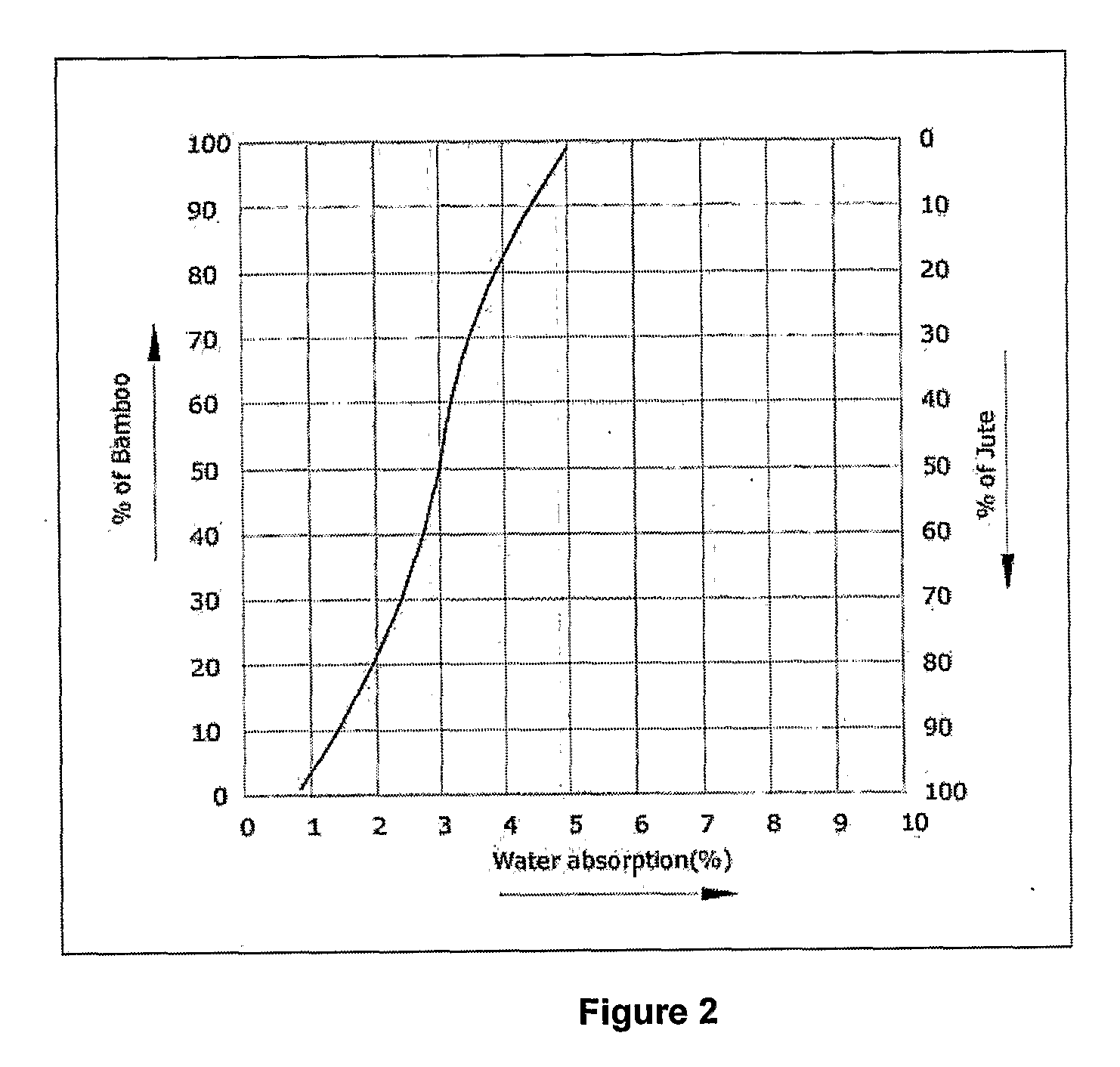
Natural Fibre Thermoset Composite Product and Method For Manufacturing the Same
InactiveUS20090130377A1High tensile strengthLow water absorptionLamination ancillary operationsLaminationDefinite periodSlurry
Owner:A B COMPOSITES PRIVATE
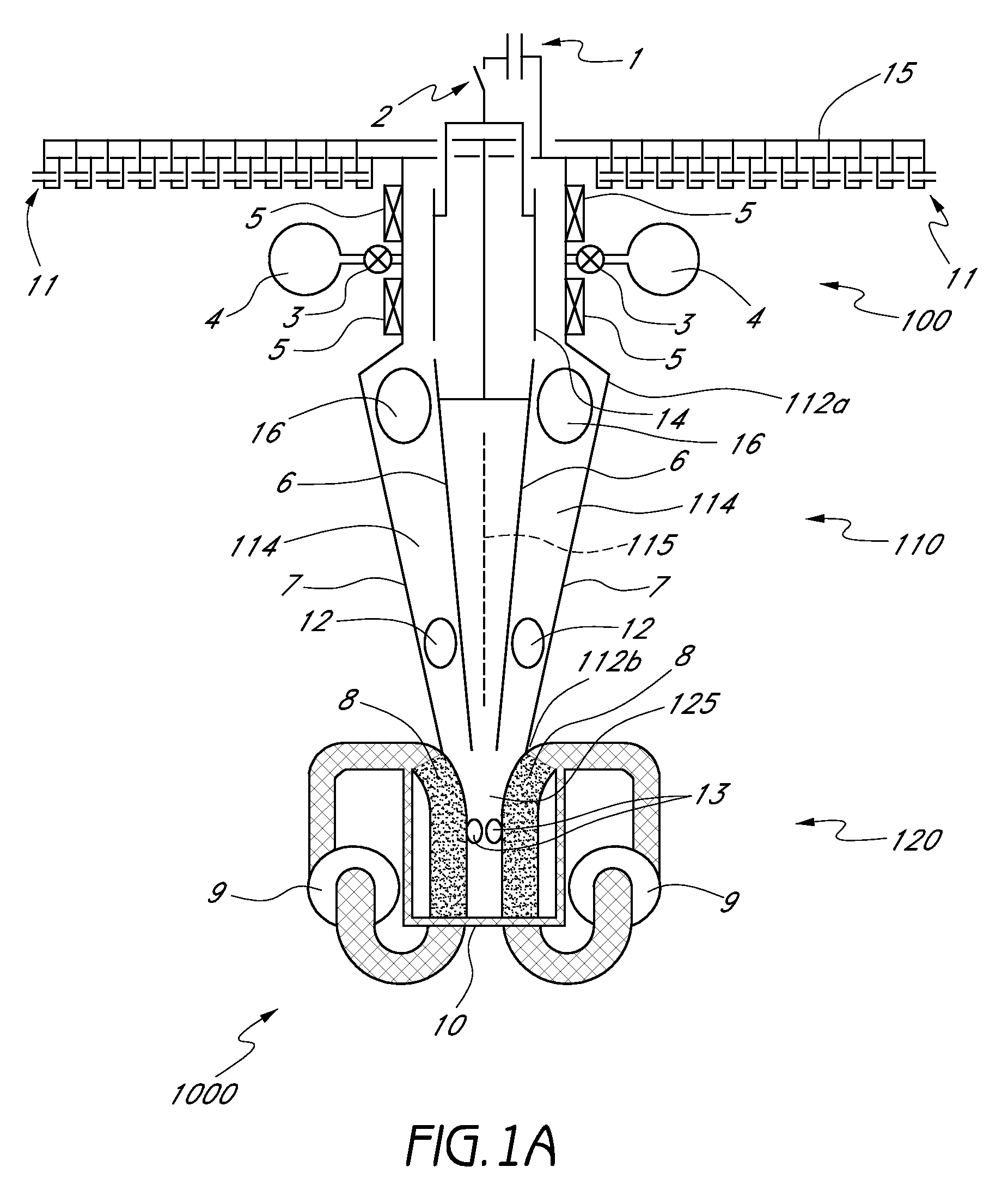
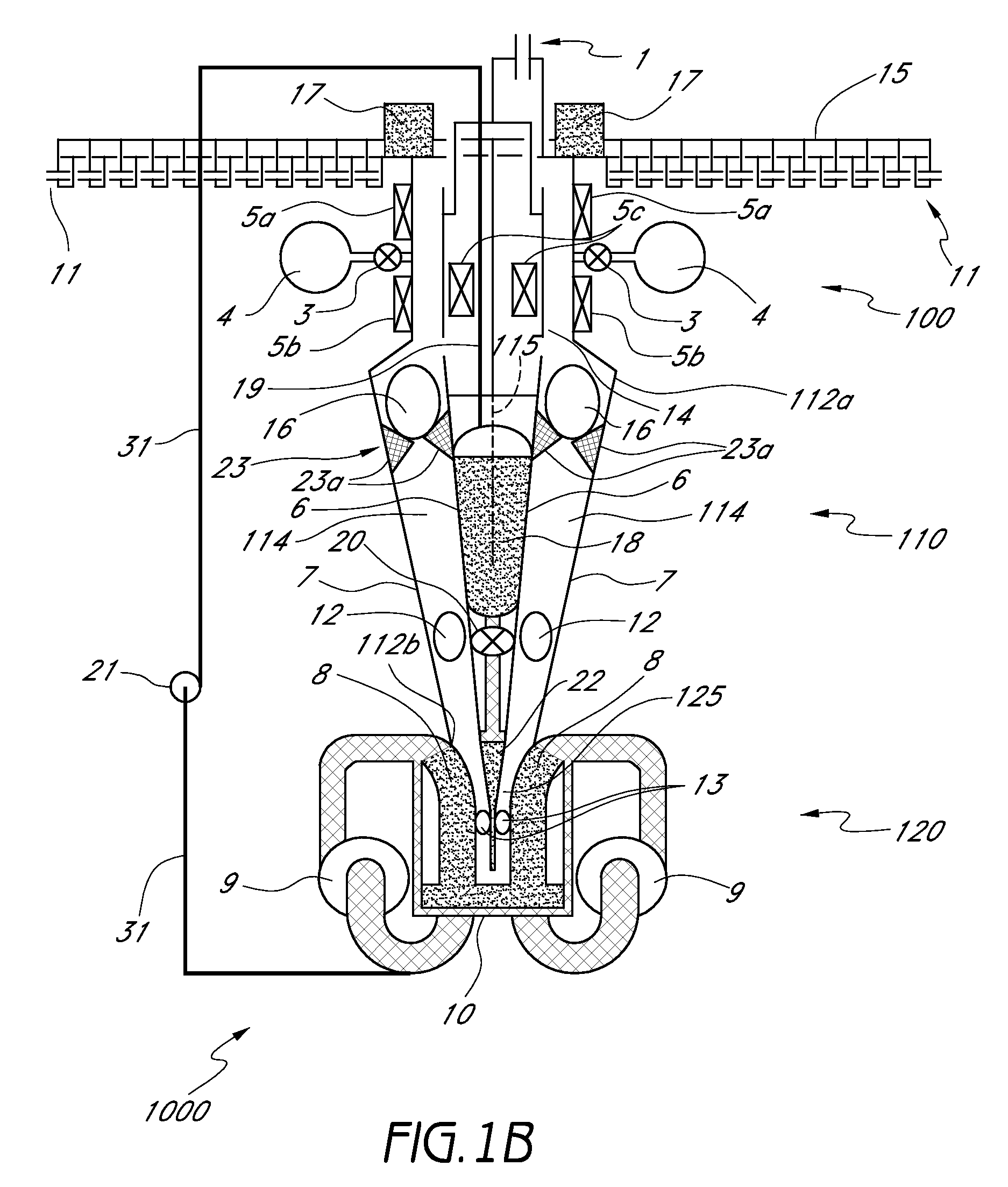
Valve holder
The present invention is an improved apparatus for holding and maneuvering a valve during preparation and attachment to patient. The present invention is particularly useful for increased visibility of the prosthetic valve and the sewing ring to prevent suture entanglement. The present invention is used most effectively with mitral valves having commissure posts on the outflow side of the valve structure but may be used with other valve configurations. The present invention spaces the handle attachment from the valve for improved visibility of the sewing ring and the outlet end of the valve during attachment. The present invention is adapted to safely bend the commissure posts inward at the tips while preventing crashing the commissure posts into each other causing damage. The new holder prevents suture remnants left in a patient by a designed break point for the holder suture. The present invention reduces the release force needed to remove the holder and unthread the holder sutures by an improved design and method of attachment to the prosthetic valve. The improved holder provides a kink free holder suture path to reduce suture entanglement and prevent damage to the implanted valve during holder removal by reducing the release force needed to remove the holder sutures by up to 30%.
Owner:MEDTRONIC INC
Systems and methods for compressing plasma
ActiveUS8537958B2Increase plasma densityNuclear energy generationLow temperature fusion reactorLiquid metalBreaking point
Embodiments of systems and methods for compressing plasma are described in which plasma pressures above the breaking point of solid material can be achieved by injecting a plasma into a funnel of liquid metal in which the plasma is compressed and / or heated.
Owner:GENERAL FUSION INC
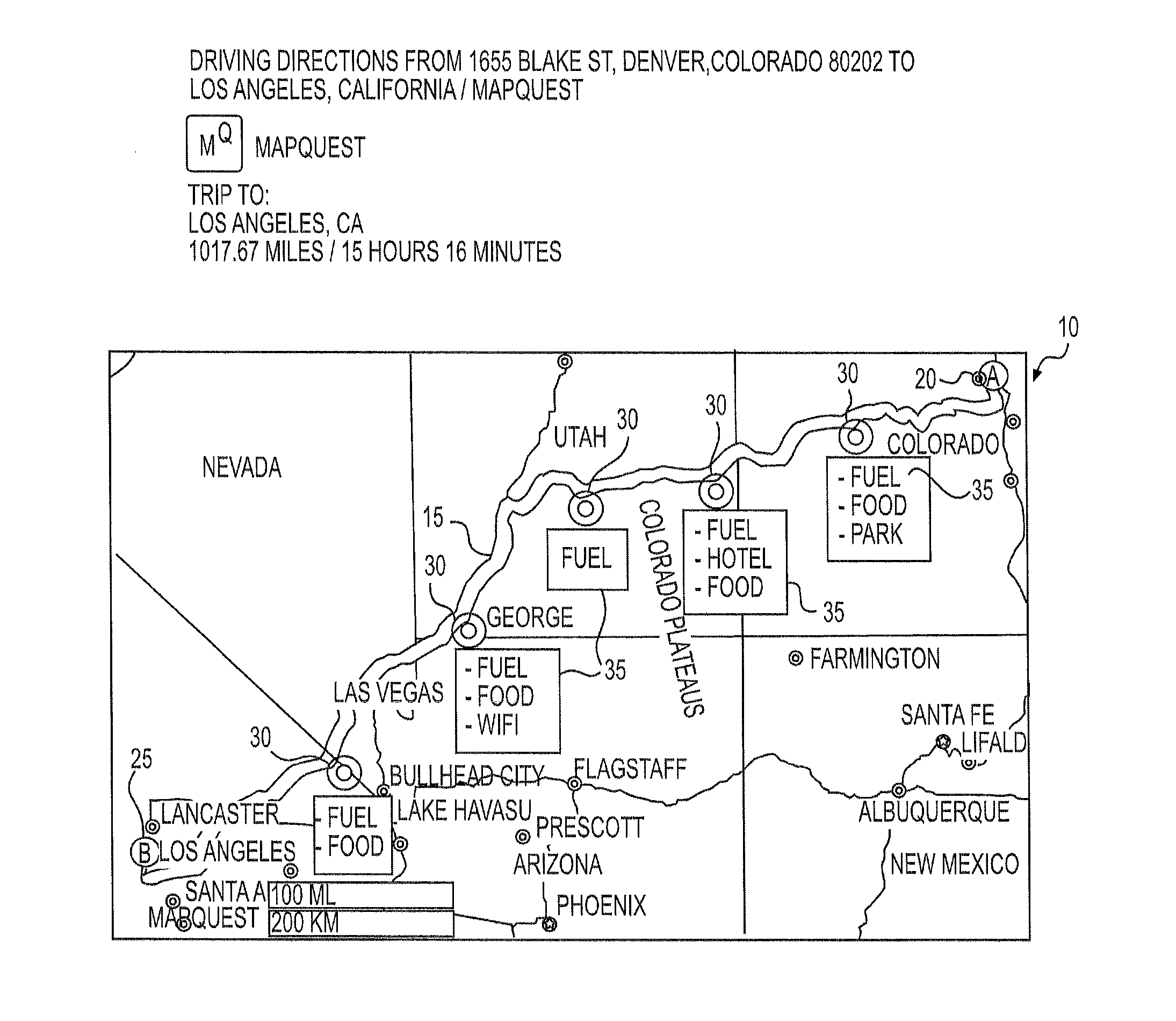
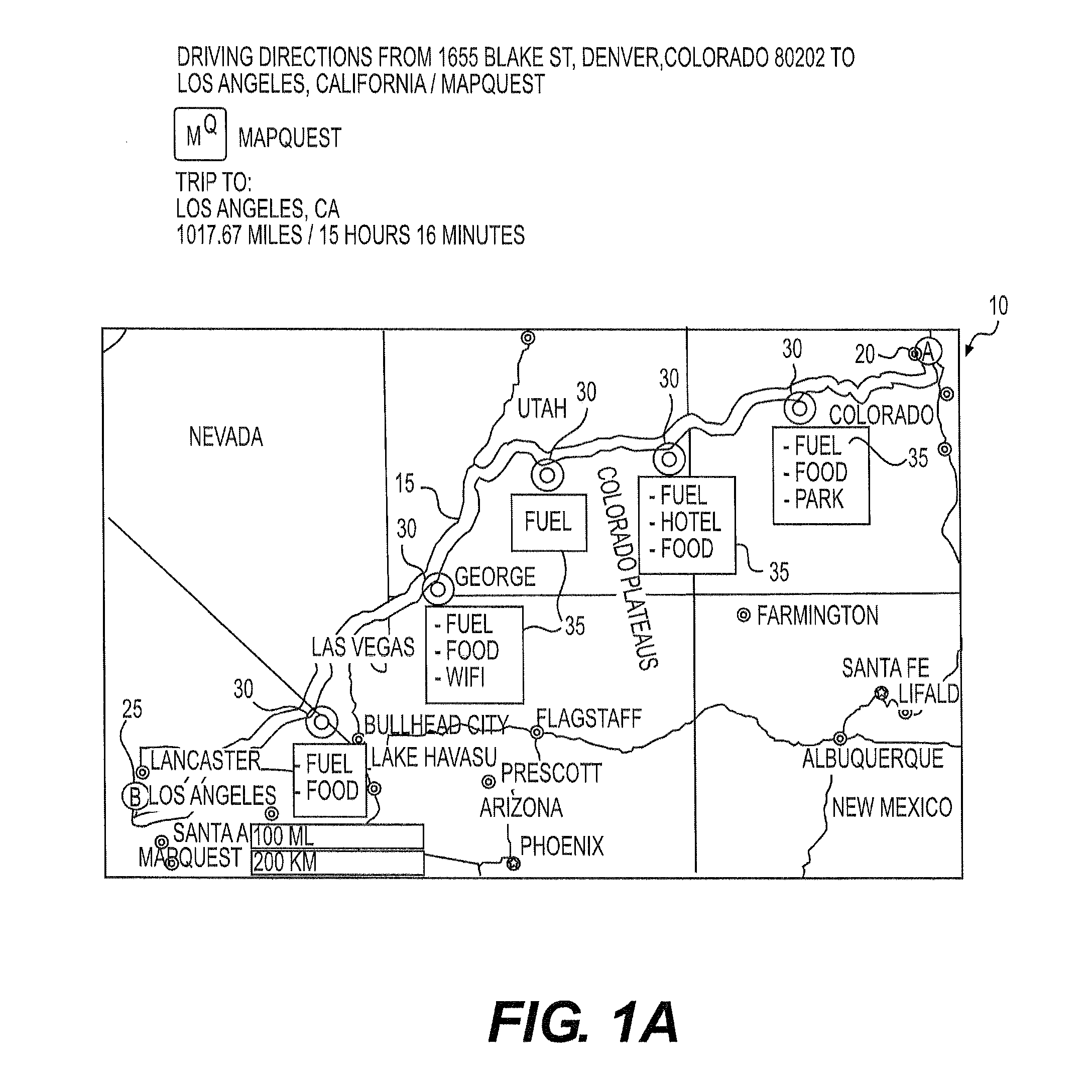
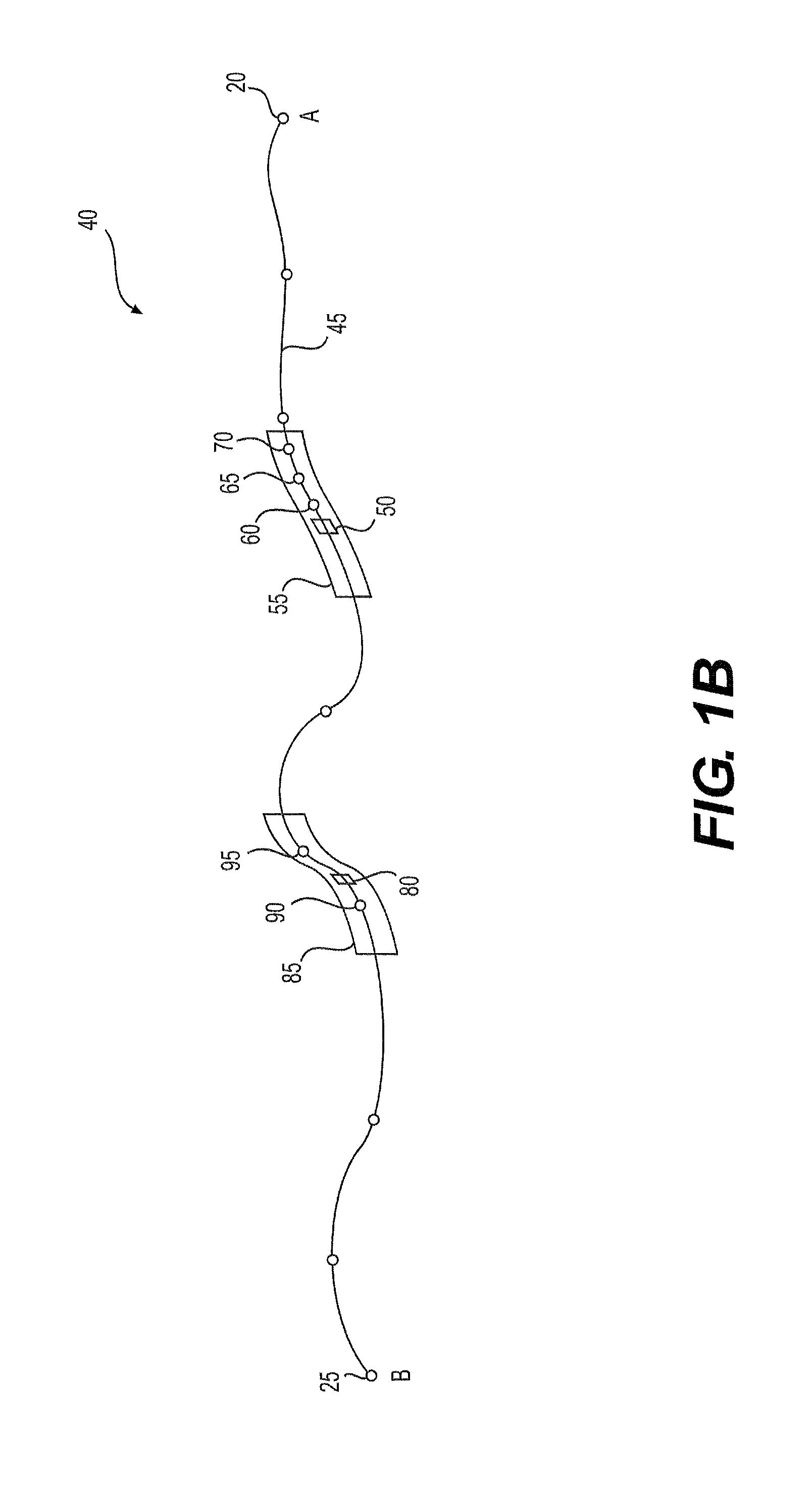
Systems and methods for providing mapping services including route break point recommendations
ActiveUS20150051829A1Quickly and easily addTrip planning convenient for the userInstruments for road network navigationNavigational calculation instrumentsUser inputBreaking point
Computer implemented methods are disclosed for providing geographical information to a user. One method may include receiving, from a user's electronic device and over a network, user input data including at least the destination location and a break point parameter and calculating one or more routes from the start location to the destination location, based on the user input data. The method may also include identifying one or more intermediate break point locations along the one or more routes based on the break point parameter received from the user and identifying a range extending around each intermediate break point location, and potential break points. A step may also be executed in which a density or type of points of interest within each potential break point may be evaluated by the electronic device and a recommended for a break point made.
Owner:VERIZON PATENT & LICENSING INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com