Password compiling method based on authentication terminal
A terminal and password technology, which is applied in the field of network and information security, can solve problems such as the inability to confirm the identity authenticity of network activity personnel, and achieve the effect of accurately confirming identity authenticity, ensuring authenticity, and ensuring absolute security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
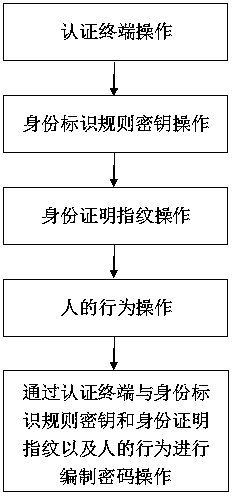
[0015] A process of creating a password method based on an authentication terminal is as follows: figure 1 As shown, the running steps are:
[0016] The step of authenticating the terminal operation, the authentication terminal is the authentication terminal authorized by the authentication system for the network active personnel, and the authentication system administrator binds the authentication terminal with the identity of the network active personnel to ensure the uniqueness of the authentication terminal and the identity of the network active personnel; The authentication terminal operation interface is equipped with regular keys and fingerprint keys, including regular keys for addition, regular keys for subtraction, regular keys for multiplication, regular keys for misplacement, regular keys for carry, regular keys for abdication, regular keys for numbers 1, and regular keys for 2 Number regular key, number regular key of 3, number regular key of 4, number regular key ...
Embodiment 2
[0027] This embodiment is an improvement in the steps of creating a password based on the authentication terminal described in the first embodiment, using the authentication terminal, the identification rule key, the identity certification fingerprint, and human behavior. figure 2 shown.
[0028] The sub-steps in the step of creating a password by authenticating the terminal and identity identification rule key and identity proof fingerprint and human behavior include:
[0029] The sub-steps of operating the authentication terminal rule key and fingerprint key to create a password through the identity identification rule key and identity certification fingerprint and human behavior;
[0030] The authentication terminal is based on the operation rule key and fingerprint key of the network active personnel. Through the microprocessor and memory, the identity identification rule key and identity certificate fingerprint identification is correct. The instruction key signature mod...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com