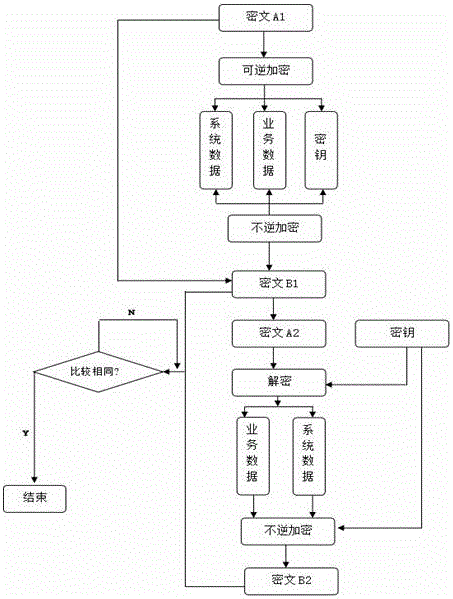
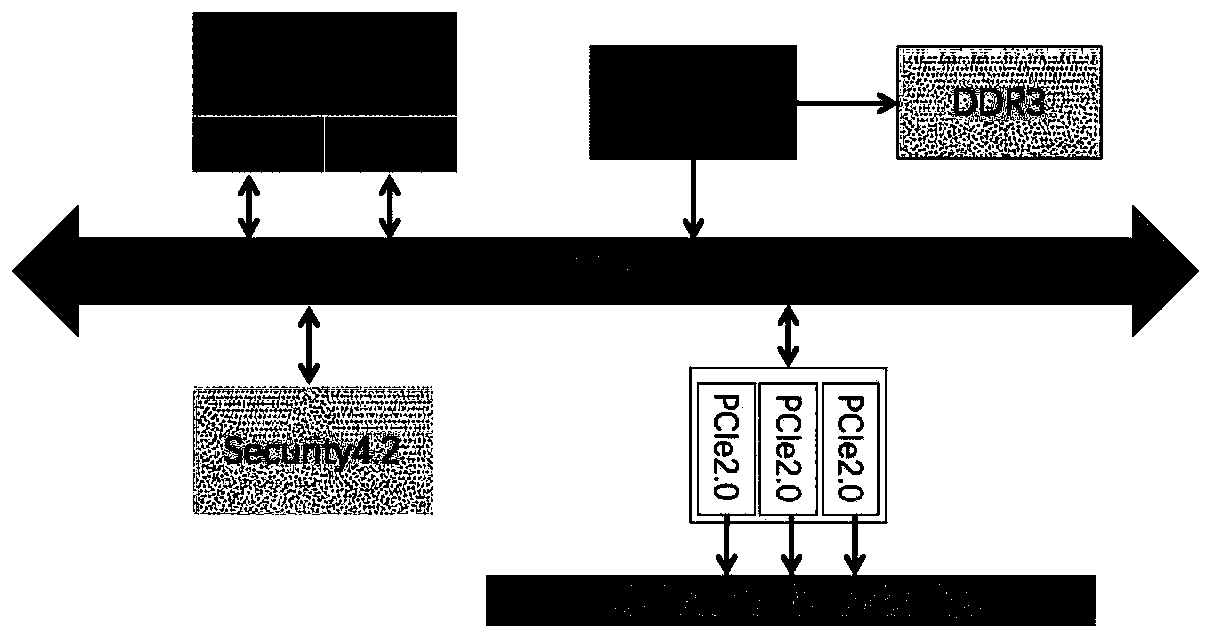
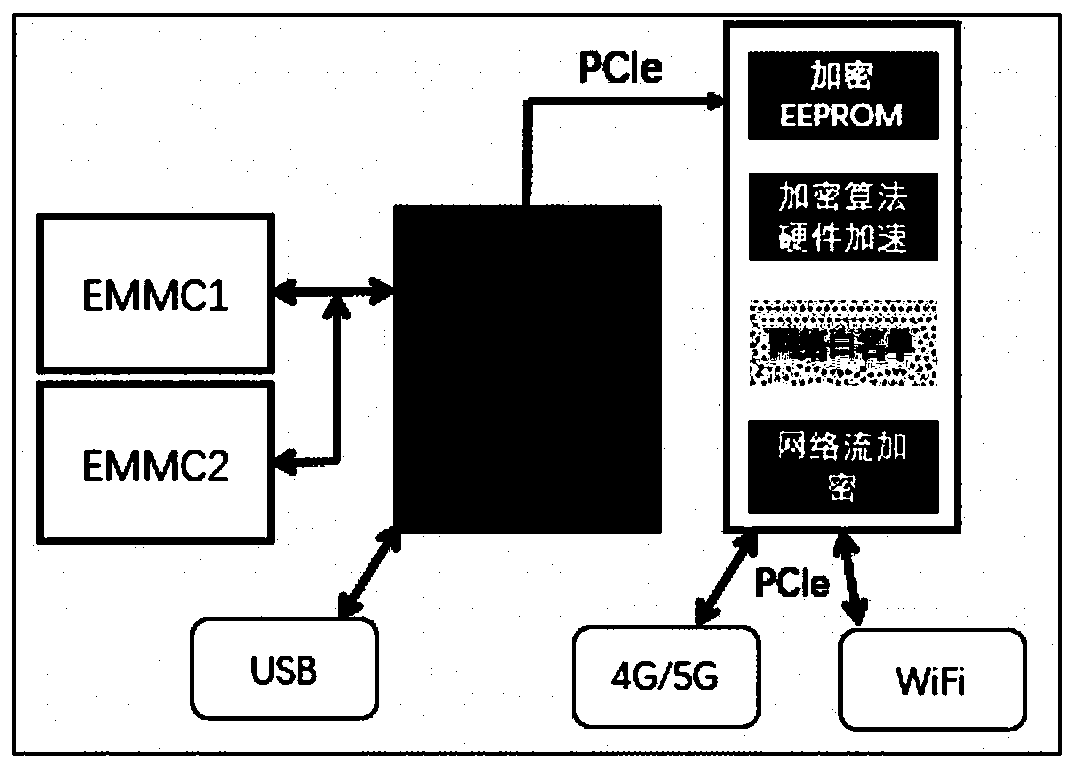
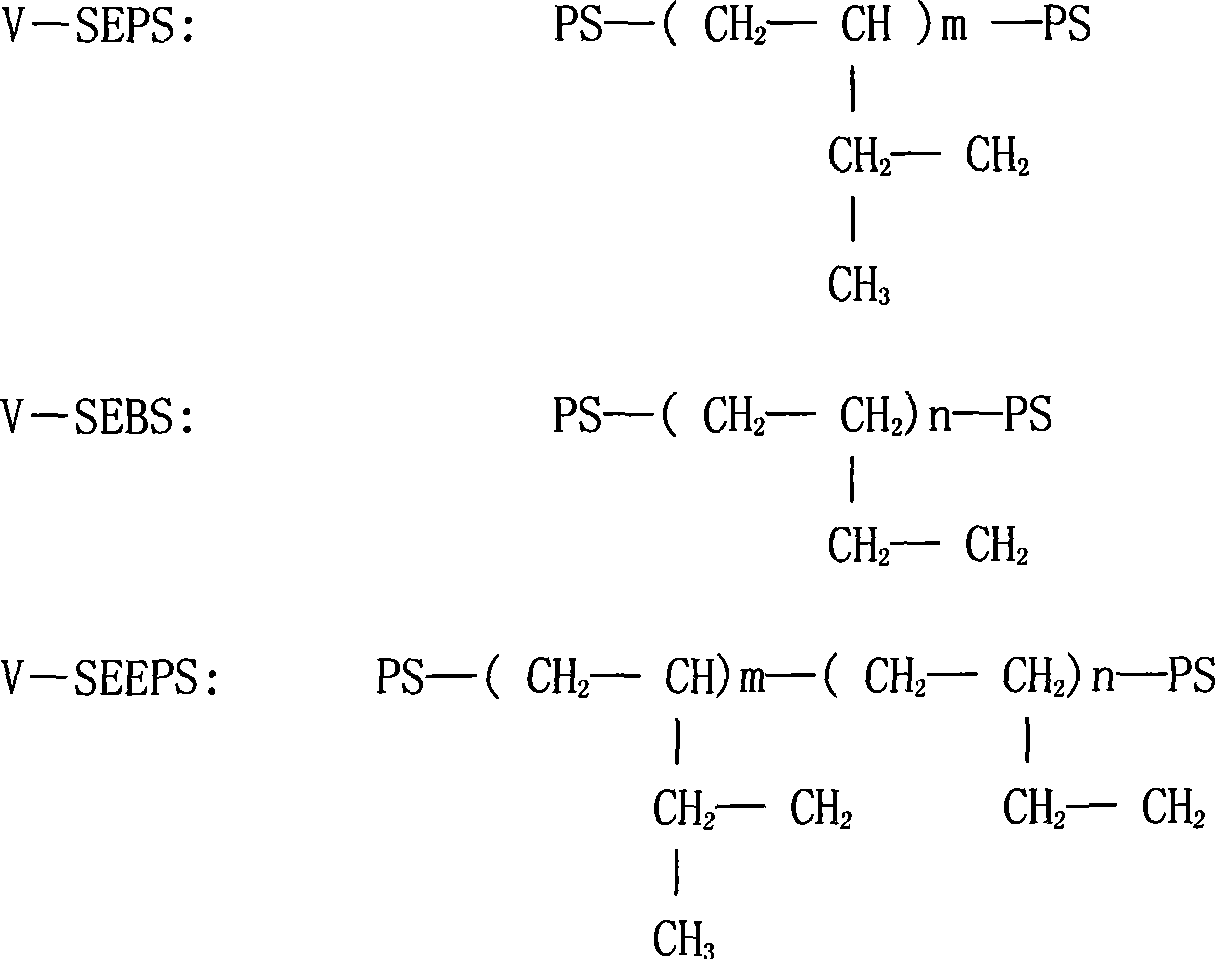Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
226results about How to "Absolutely safe" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Artificial intelligent training platform for intelligent networking vehicle plan decision-making module
InactiveCN107506830AImprove generalization abilitySafe and "Real Training Scenarios"Mathematical modelsMachine learningFrame basedReinforcement learning algorithm
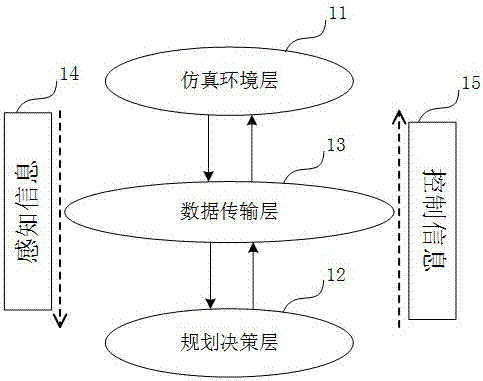
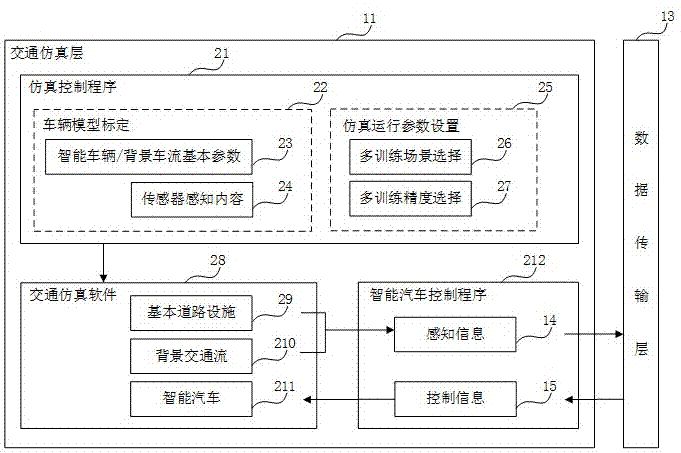
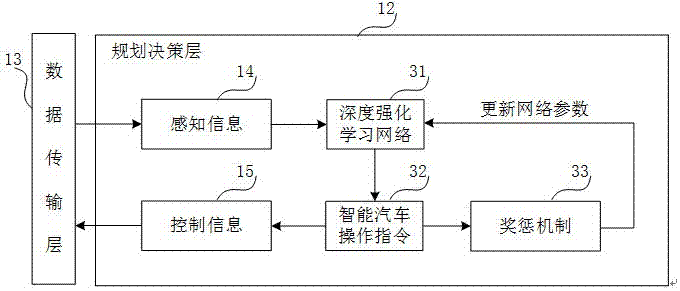
The invention, which relates to the technical field of an intelligent vehicle automatic driving and traffic simulation, relates to an artificial intelligent training platform for an intelligent networking vehicle plan decision-making module and aims at improving the intelligent level of the intelligent vehicle plan decision-making module based on enriched and vivid traffic scenes. The artificial intelligent training platform comprises a simulation environment layer, a data transmission layer, and a plan decision-making layer. The simulation environment layer is used for generating a true traffic scene based on a traffic simulation module and simulating sensing and reaction situations to the environment by an intelligent vehicle, thereby realizing multi-scene loading. The plan decision-making layer outputs a decision-making behavior of the intelligent vehicle by using environment sensing information as an input based on a deep reinforcement learning algorithm, thereby realizing training optimization of network parameters. And the data transmission layer connects the traffic environment module with a deep reinforcement learning frame based on a TCP / IP protocol to realize transmission of sensing information and vehicle control information between the simulated environment layer and the plan decision-making layer.
Owner:TONGJI UNIV
Multi-row micro-differential roadbed deep hole blasting construction method
The invention relates to a multi-row micro-differential roadbed deep hole blasting construction method, which comprises the following steps of: (1) selecting blasting parameters; (2) calculating security; (3) arranging a stair and a free face; (4) distributing holes and drilling holes; and (5) blasting. The blasting method is a multi-row deep hole millisecond micro-differential blasting method; and the blasting is performed by pull trough blasting and side slope blasting in a roadbed sequentially, wherein the pull trough blasting is loose blasting and the side slope blasting is precraking blasting. In the method, a shock conducting tube non-electric priming system micro-differential control blasting technology, a comprehensive blasting construction scheme of loose blasting, the deep hole millisecond micro-differential blasting technology and the roadbed side slope precraking blasting technology, and a wide-pitch and low-resistance hole distribution mode are adopted, so that explosivesand detonators are saved, the drilling mechanization degree is enhanced, the labor cost is reduced, the blasting effect is enhanced, the large rate of blast rocks is reduced, the material abandoning rate is reduced and harms of blasting vibration, impact waves, flying stones and the like are reduced; furthermore, when the blasting effect is enhanced and the stability of the blast roadbed side slope rocks is guaranteed, the absolute safety of blasting can be guaranteed.
Owner:HUITONG ROAD & BRIDGE CONSTR GROUP
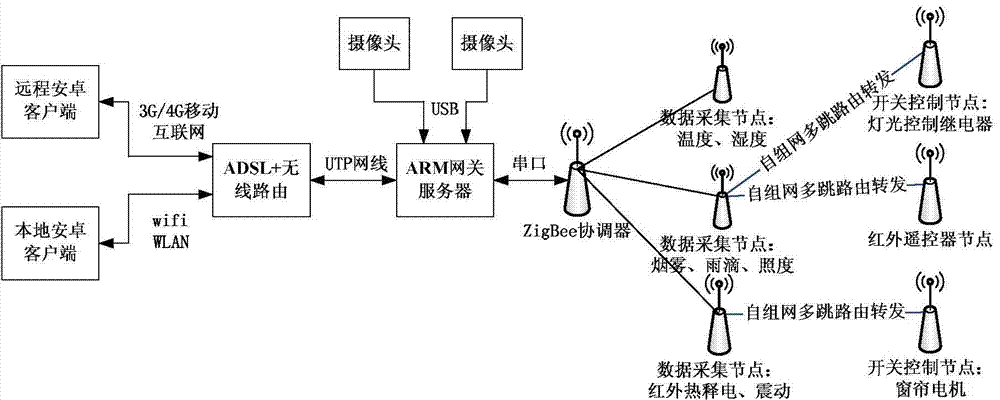
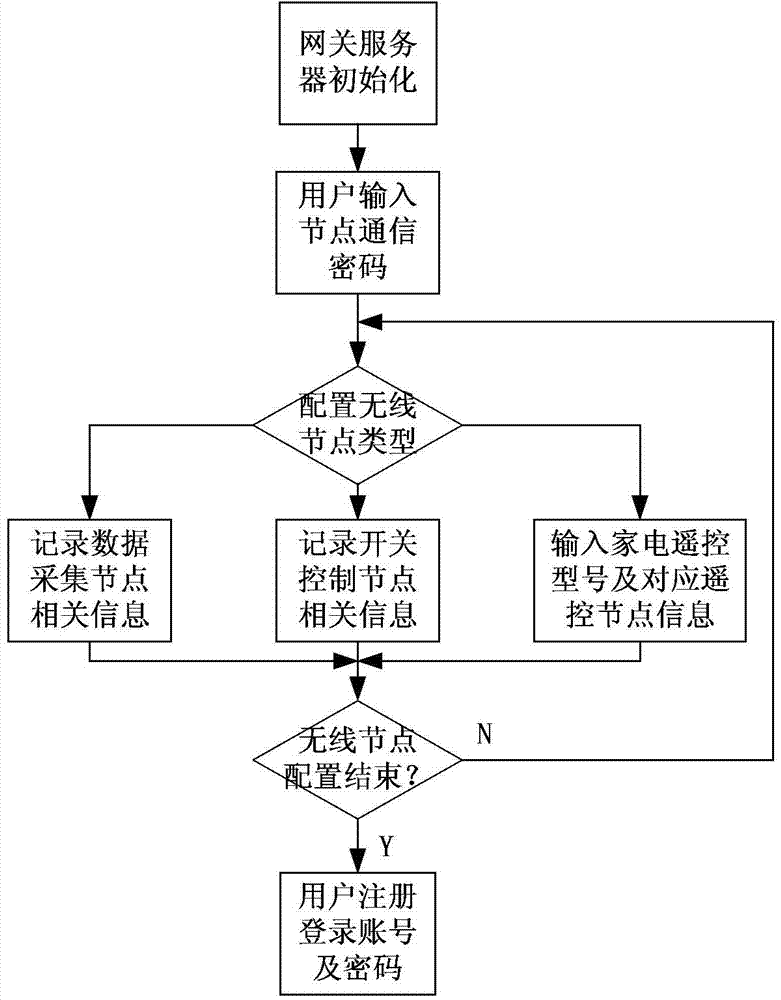
Intelligent housing system and control method
InactiveCN104125125AEasy to installEasy to install and maintainNetwork topologiesData switching by path configurationWireless routerModem device
The invention discloses an intelligent housing system and a control method. The intelligent housing system is mainly composed of a gateway server, a client, a modulator-demodulator, a wireless router, a wireless coordinator and at least one wireless node, wherein the wireless router is connected with the Internet through the modulator-demodulator; the client is connected with the wireless router, and the wireless router is connected with the gateway server through a network cable and / or a mobile Internet; the gateway server is connected with the wireless coordinator through a serial port; the wireless coordinator is wirelessly connected with all the wireless nodes. The intelligent housing system disclosed by the invention has the characteristics of being convenient to install and maintain, low in cost, capable of realizing dynamic management for a housing control node, convenient to operate the client, high in system safety, stable, efficient, energy-saving and environment-friendly, and the like.
Owner:GUILIN UNIV OF ELECTRONIC TECH
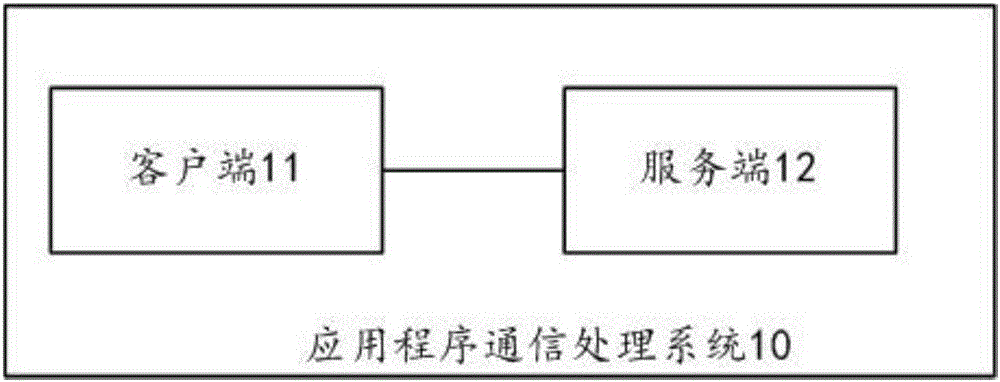
Application program communication processing system, an application program communication processing device, an application program communication processing apparatus and an application program communication processing method
InactiveCN105915342AImprove securityAbsolutely safeKey distribution for secure communicationGeneration processClient-side
The invention discloses an application program communication processing system, an application program communication processing device, an application program communication processing apparatus and an application program communication processing method. The application program communication processing system comprises a client and a server, wherein the client generates a request message including request information, signature information and a session key, carries out the signature and encryption by utilizing a client private key certificate, a session key and a server public key certificate in the generation process, transmits the request message to the server and receives a response message transmitted by the server after the request message is parsed; the server parses the received request message transmitted by the client and transmits the response message to the client, wherein the server performs the decryption and verification by utilizing a server private key certificate and a client public key certificate in the process of parsing the request message. By adopting the scheme provided by the invention, the application program communication safety can be improved.
Owner:GUANGZHOU AIJIUYOU INFORMATION TECH
Method and system for constructing modular medical instrument based on USB HUB
InactiveCN101536900AIndependent AD conversionFunction independentUltrasonic/sonic/infrasonic diagnosticsHeart defibrillatorsSpecific detectionUSB hub
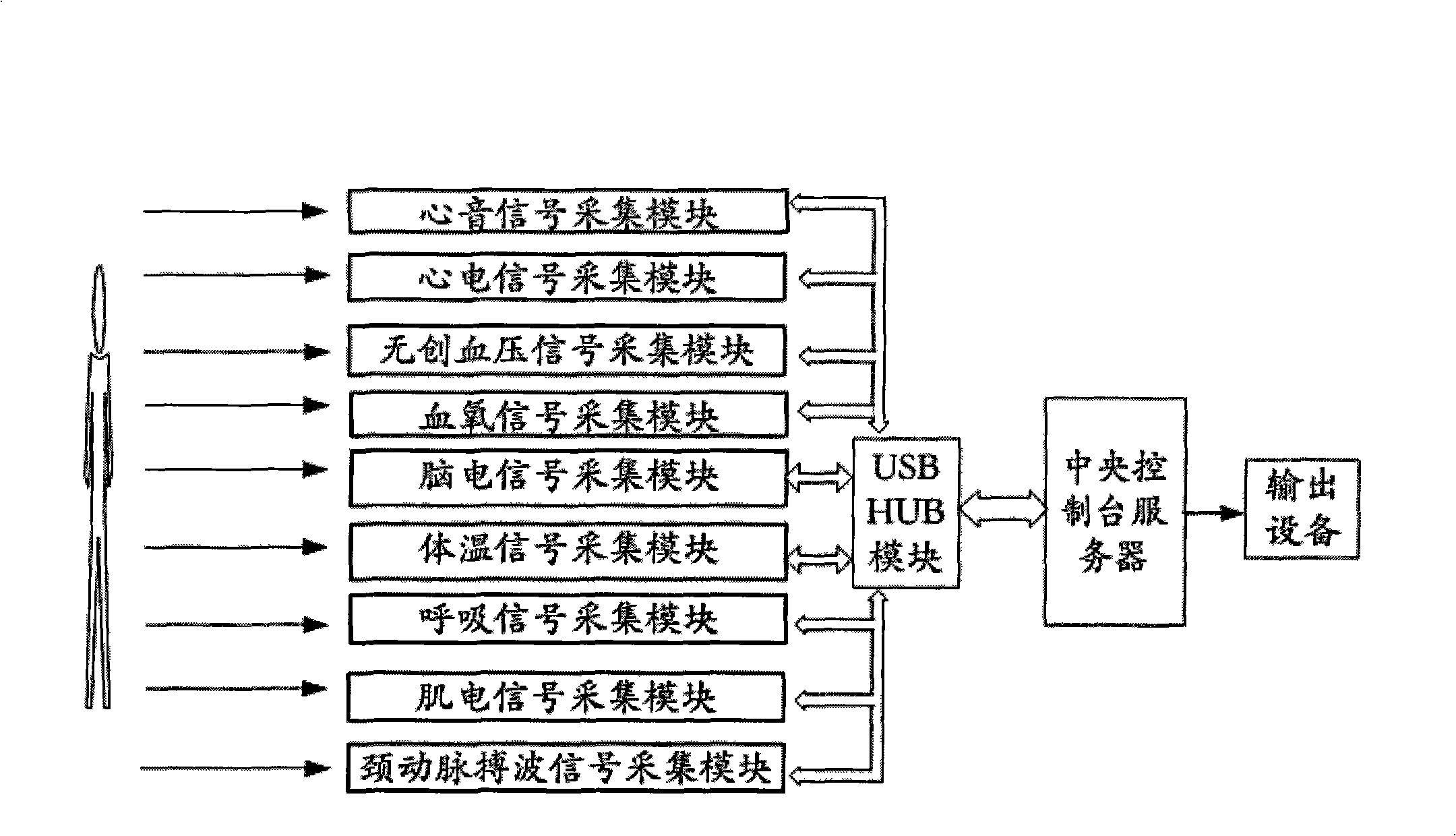
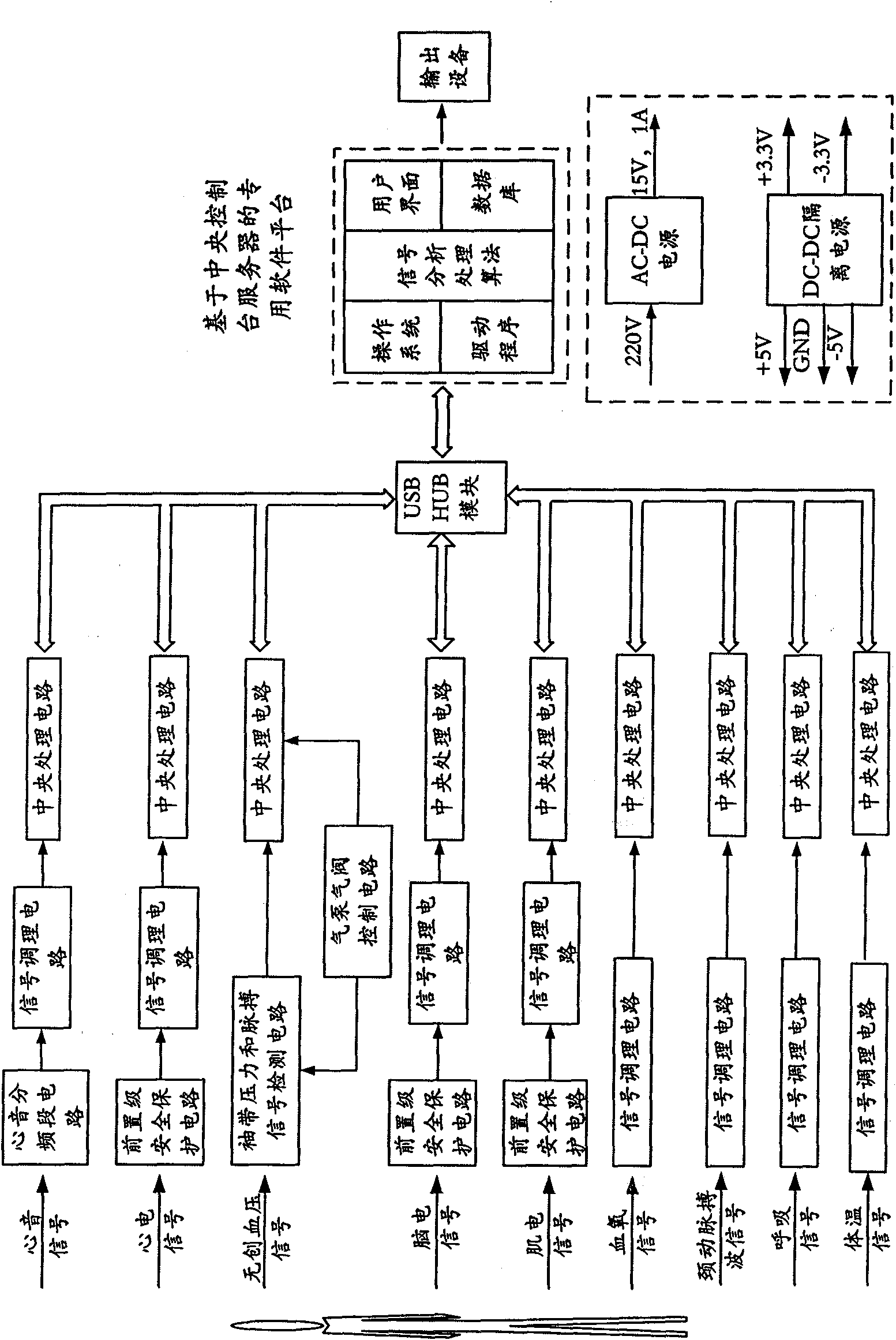
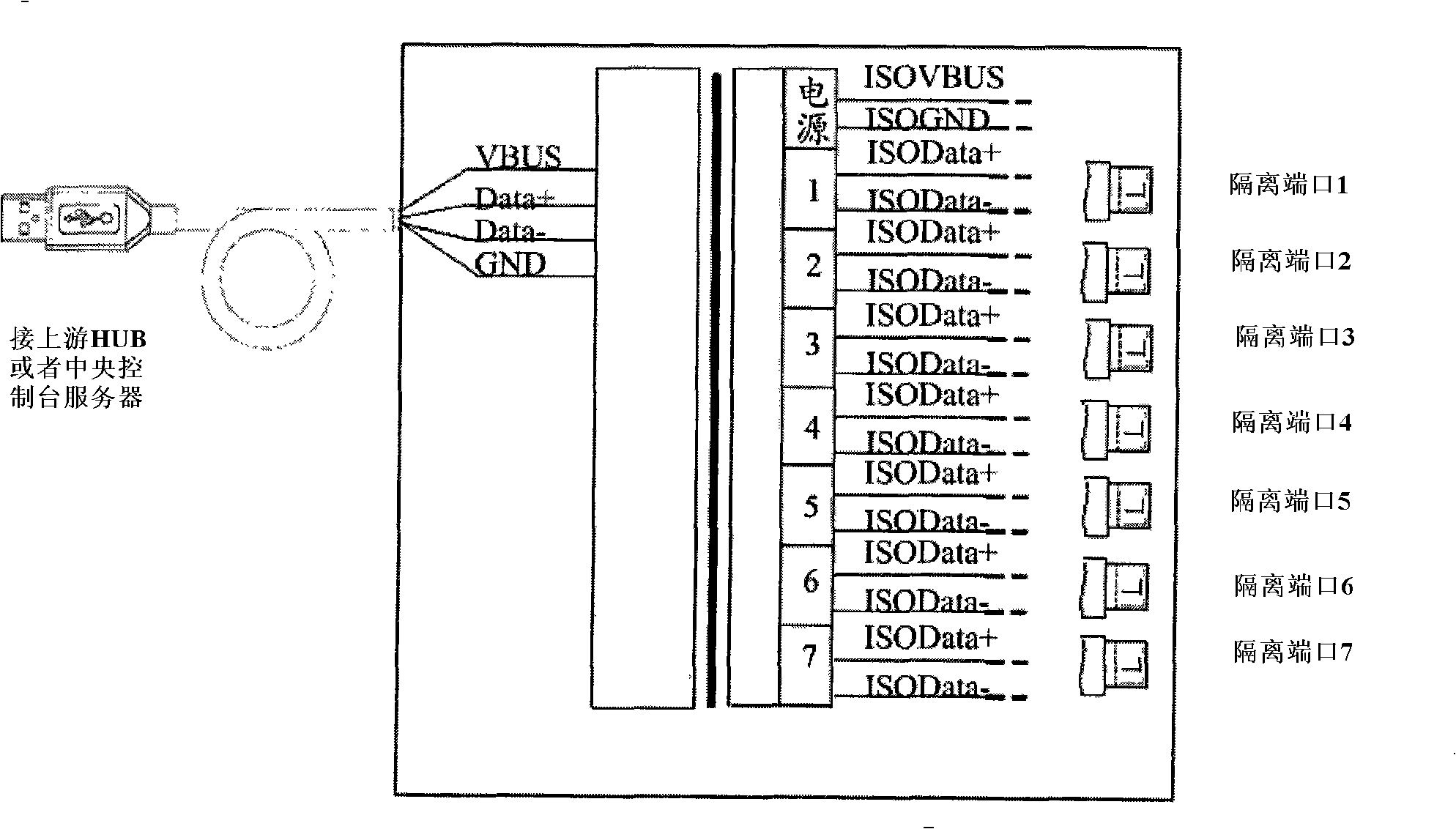
The invention relates to a method and a system for constructing a modular medical instrument based on USB HUB. The method comprises the following steps: each functional circuit adopts modular design, independently adopts a microprocessor and has the functions of independent AD conversion and USB communication control; each functional module is connected with a USB HUB module which has an electrical safety isolation function through a USB bus; and the USB HUB module is connected with a central console (PC) or server hardware through the USB bus, and connected with a special software platform based on the PC to form a complete medical instrument system. The method can realize high reliability and easy maintenance of the medical instrument, and the flexible expandability of the functions of the medical instrument, change the mode that the functions of the medical instrument are set by manufactures and can not be modified by a user, lead the user to be capable of randomly combining (increase or decrease) the functional modules according to specific detection requirements, and realize the personalized physiological parameter detection function and the function expansion of the medical instrument by USB topological structure.
Owner:CHONGQING UNIV
Intelligent portable safety fence
InactiveCN103669997AWith trespassAbsolutely safeFencingBurglar alarmEmbedded systemReliability engineering
The invention relates to an intelligent portable safety fence which comprises a plurality of stand columns connected through extensible belts. The extensible belts are wound in the stand columns, extend out when being pulled and automatically rewinds into the stand columns when not pulled. The intelligent portable safety fence is characterized in that the stand columns are provided with pyroelectric sensors and alarms, the pyroelectric sensors are provided with switches and electrically connected with the alarms, and the pyroelectric sensors are used for receiving and magnifying infrared radiation generated by movement of people and driving the alarms to send alarming signals. The intelligent portable safety fence is simple in structure, has the functions of automatically detecting mistaken intrusion of people, alarming in advance, striking warning marks and the like, can protect absolute security of people and equipment in high-voltage testing sites and can improve safety of the high-voltage testing sites.
Owner:STATE GRID CORP OF CHINA +2
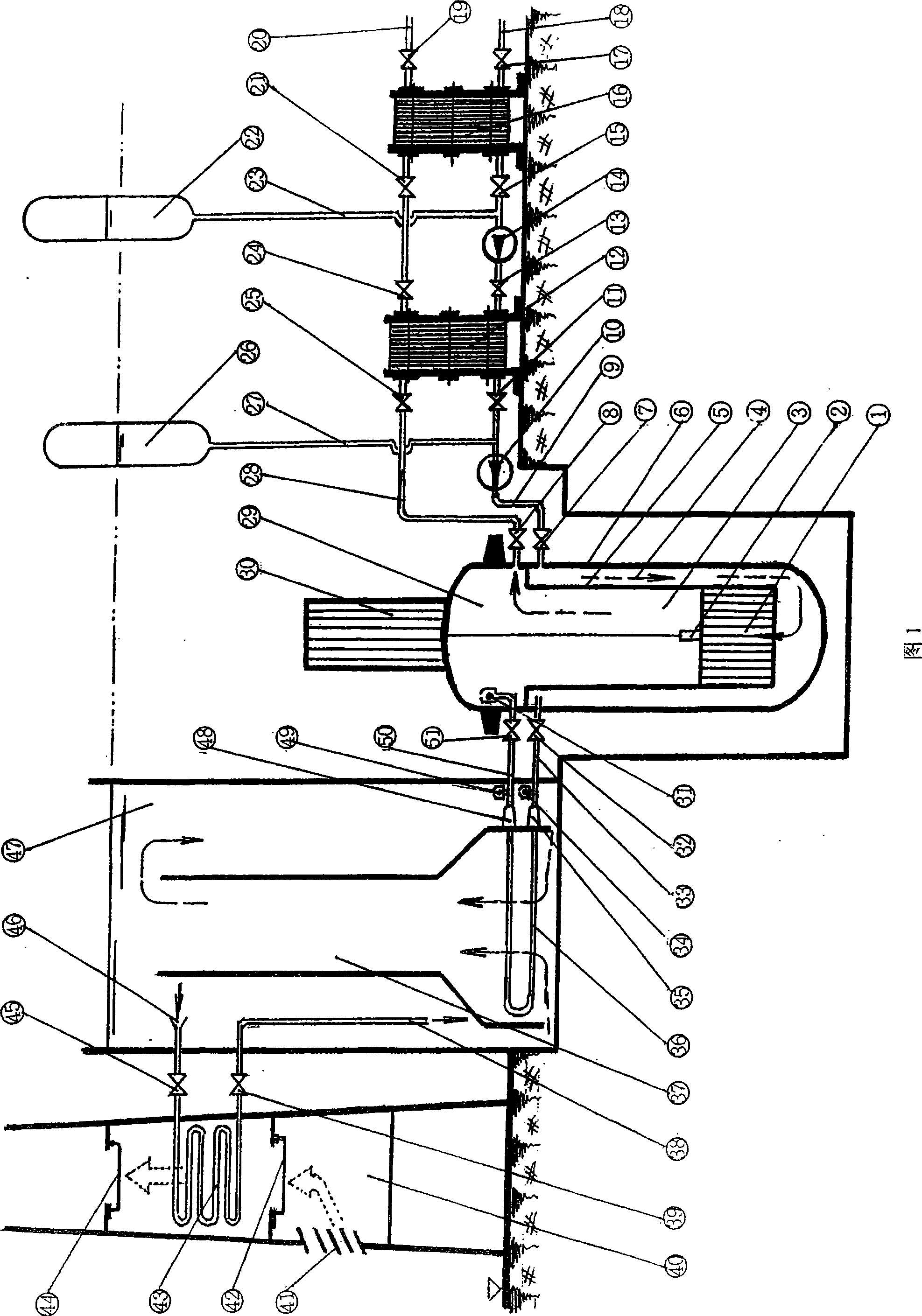
Inherent safety pool case combination low-temperature stack nuclear heating station apparatus and operational procedure thereof
InactiveCN101441902AIncreased average volume specific powerReduce initial loadIntegral reactorsNuclear energy generationInherent safetyPressurized water reactor
The present invention provides an inherent security pool-shell combination low temperature nuclear heating device and an operation program thereof, which belongs to nuclear energy centralized heat-supply field. The invention mainly comprises the following procedures: adopting separated layout, forced circulation and high effective small temperature difference heat exchange in primary loop of reactor; under the precondition that parameter requirements of centralized heat-supply by big cities heat supply network satisfied, reducing work temperature of shell-type heating reactor as far as possible; meanwhile optimized layout of equipment, and organic combination of normal pressure pool in large volume (47) and shell-style heating reactor(29) remove accident possibility of water loss and coldness loss of reactor core (1). Complete inherent safety principle is carried out in the invention. Thus, absolute security of nuclear heating can be guaranteed by using mature pressurized water reactor technology, and enterprises have develop nuclear station pressurized water reactor experience can possibly jump over research and develop stage and enter into nuclear heating market directly, and make a real contribution for energy-saving and emission-reduction and improving country energy structure.
Owner:肖宏才
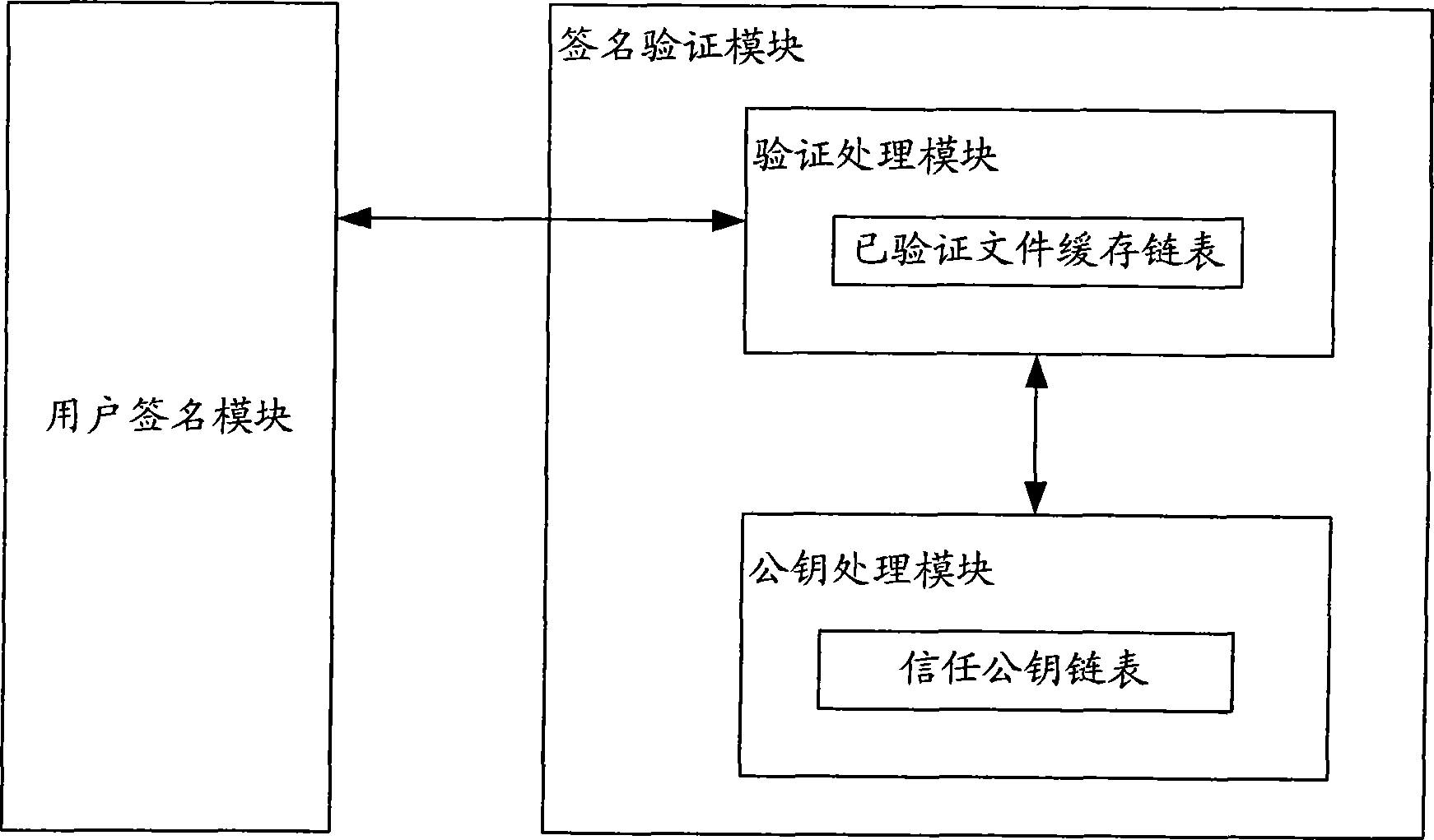
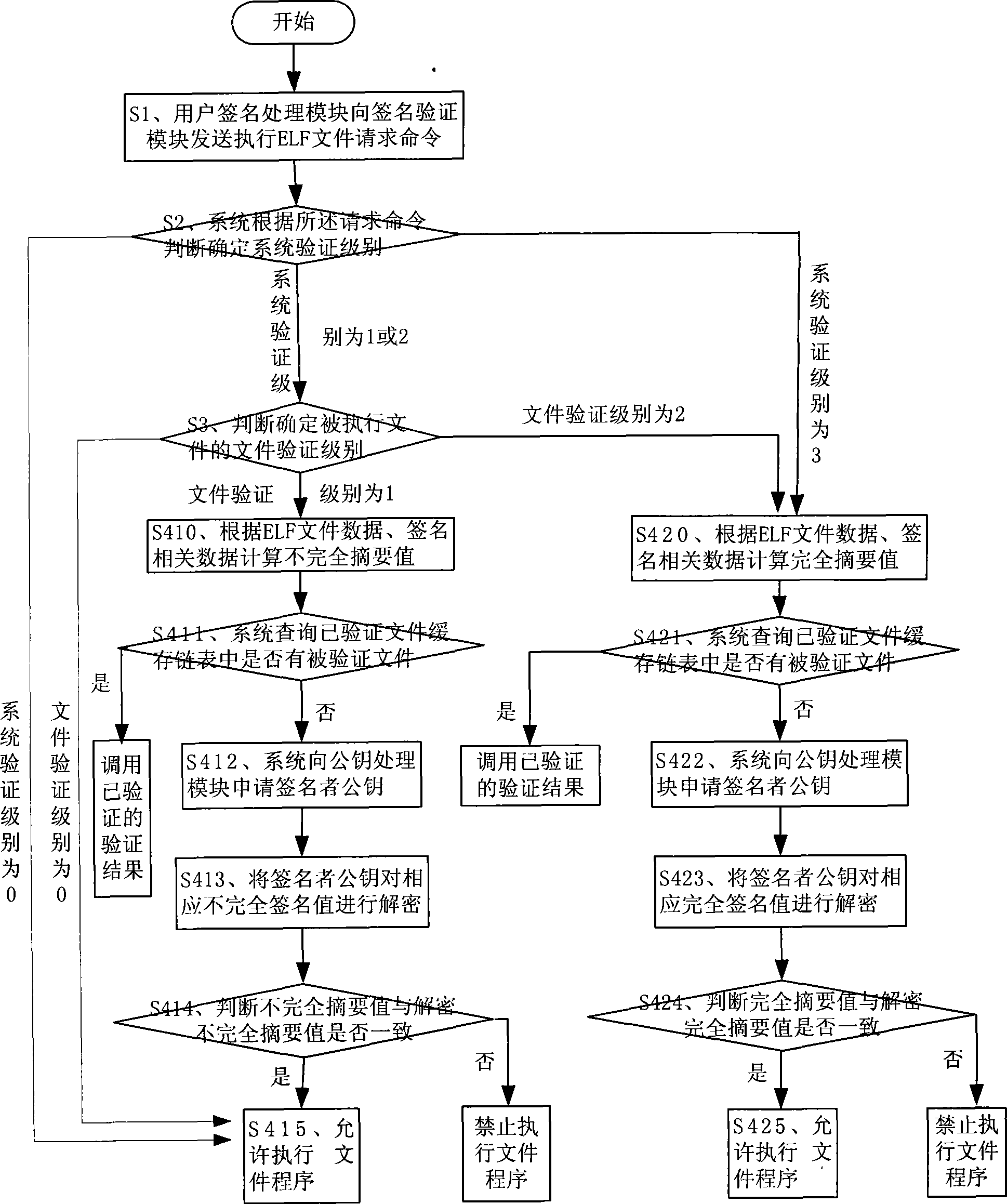
System and method for verifying file code signature
InactiveCN101520832AAbsolutely safePrevent intrusionPlatform integrity maintainanceVirusComputer security
The invention discloses a system and a method for verifying a file code signature. The system comprises a user signing module and a signature verifying module, and the user signing module is connected with the signature verifying module in a communication way. The system is characterized in that the signature verifying module comprises a verification processing module and a public key processing module; the verification processing module is connected with the user signing module and the public key processing module in the communication way respectively; the verification processing module is used for controlling to execute verification of a signature value; and the public key processing module is used for controlling to process a trust public key. The method for verifying the file code signature compares a complete summary value with a decrypting complete summary value and confirms whether to execute a mode of a file program according to the comparison result so as to effectively prevent virus programs and Trojan-horse programs entering, ensure the absolute safety of file programs, and improve verifying efficiency and operation flexibility at the same time.
Owner:KONKA GROUP
Household fresh air purifying full-air-conditioning system
ActiveCN107228428ASmall temperature fluctuationsRealize the function of air conditioningMechanical apparatusSpace heating and ventilation safety systemsVapor–liquid separatorFresh air
The invention discloses a household fresh air purifying full-air-conditioning system which comprises a fresh air purifying air-conditioning unit, a circulation water route and an outdoor unit. The fresh air purifying air-conditioning unit comprises a pipe section with a fresh air inlet and a return air inlet. Fresh air fed from the fresh air inlet and return air fed from the return air inlet are mixed in a mixing section and filtered through a low-efficiency filter, and enter a surface type heat exchanger to exchange heat with freezing or cooling water for dehumidification, and air treated by the surface type heat exchanger enters a high-efficiency filter to be filtered again under the drive of an air feeder and then is fed into a room through an air feeding inlet. An outdoor unit comprises a compressor. The compressor is connected with an air cooling heat exchanger, a water cooling heat exchanger, a gas-liquid separator and the like through a four-way reversing valve. A freezing or cooling water inlet of the surface type heat exchanger is connected with a heat exchange water outlet of the water cooling heat exchanger, a freezing or cooling water outlet of the surface type heat exchanger is connected with a heat exchange water inlet of the water cooling heat exchanger, and therefore the circulation water route is formed. Indoor environment is adjusted and controlled in winter, summer and transition seasons, and a comfortable and healthy natural environment is simulated.
Owner:XI'AN UNIVERSITY OF ARCHITECTURE AND TECHNOLOGY
Preparation method of novel all-solid-state lithium ion battery
ActiveCN110233298AReduce interface impedanceWeaken polarizationCell electrodesFinal product manufactureSolid-state batteryChemistry
The invention relates to a preparation method of a novel all-solid-state lithium ion battery, belonging to the technical field of lithium ion batteries. The preparation method comprises the steps of:mixing and uniformly dispersing a cathode active substance, a conductive agent and Li3OX as a cathode ingredient; mixing and uniformly dispersing an anode active substance, the conductive agent and Li3OX as an anode ingredient; mixing and uniformly dispersing a main body solid electrolyte and Li3OX as a solid electrolyte layer ingredient; coating the cathode ingredient on a cathode current collector, coating the anode ingredient on the anode current collector, stacking the anode current collector, the anode ingredient, the solid electrolyte layer ingredient, the cathode ingredient and the cathode current collector in order layer by layer to form a solid battery laminated cell, performing sintering of the solid battery laminated cell at a temperature of 282-400 DEG C while applying the pressure to the solid battery laminated cell, packaging the sintered solid battery laminated cell by adopting a battery membrane shell to obtain a novel all-solid-state lithium ion battery. The preparation method is simple, friendly in preparation environment, and is suitable for large-scale production.
Owner:ZHUHAI COSMX BATTERY CO LTD
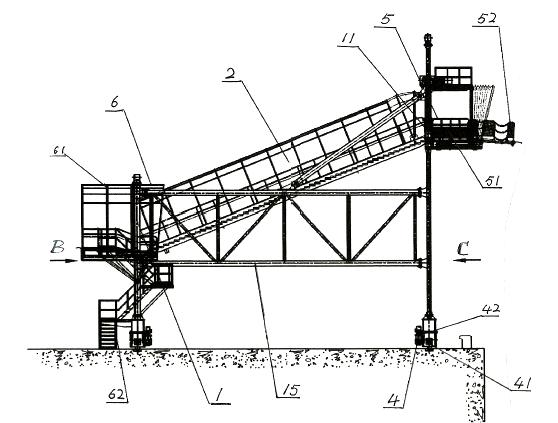
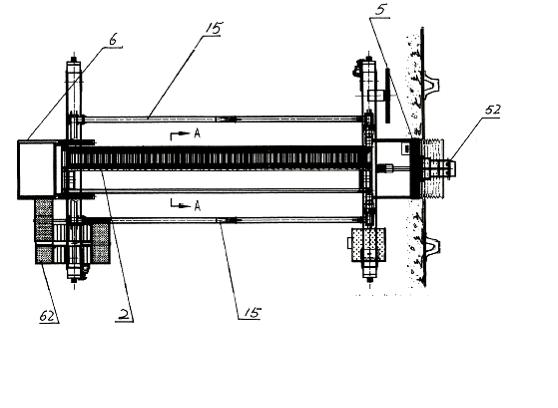
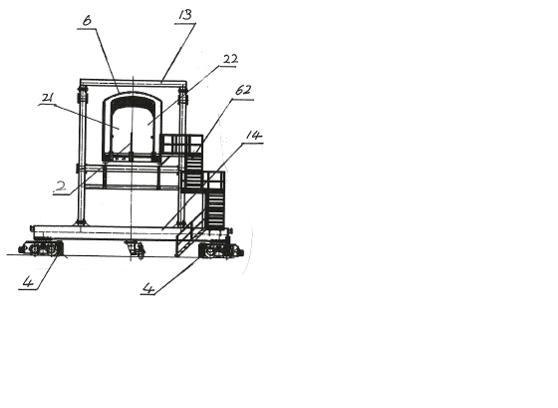
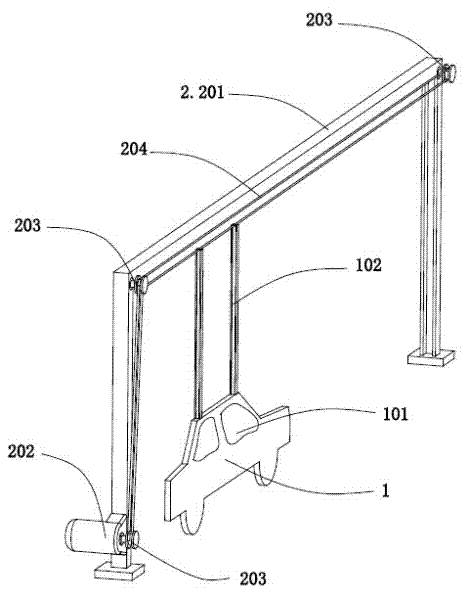
Two-passage passenger boarding bridge
The invention relates to a two-passage passenger boarding bridge, which mainly consists of a portal frame structure (1), a two-passage passenger passage (2), an elevation mechanism (3), a traveling mechanism (4), a connecting port (5), a land-side fixed platform (6), a control device and control cabinet (7), an illumination device (8), a warning device (9), a safe auxiliary device (10) and a malfunction emergency evacuation device (11). Due to the adoption of the two-passage passenger boarding bridge, passengers and personnel can safely, conveniently, comfortably and quickly come and go between a passenger liner and a waiting building, which is realized mainly through the two-passage passenger passage (2). The two-passage passenger passage (2) consists of two independent parallel passages, wherein one passage is an inclinable staircase-type stepping passage which is used when the passage is seriously pitched, the other passage is a flat board-type horizontally stepping passage, and when the pitch of the passage is smaller than 1:10, the two passages can be simultaneously used to realize the functions of the two passages. The two-passage passenger boarding bridge is an innovated product in the world, has a reasonable structure and powerful functions, is convenient to operate, is safe to use, and has fashionable appearance.
Owner:CHINA WATERBORNE TRANSPORT RES INST
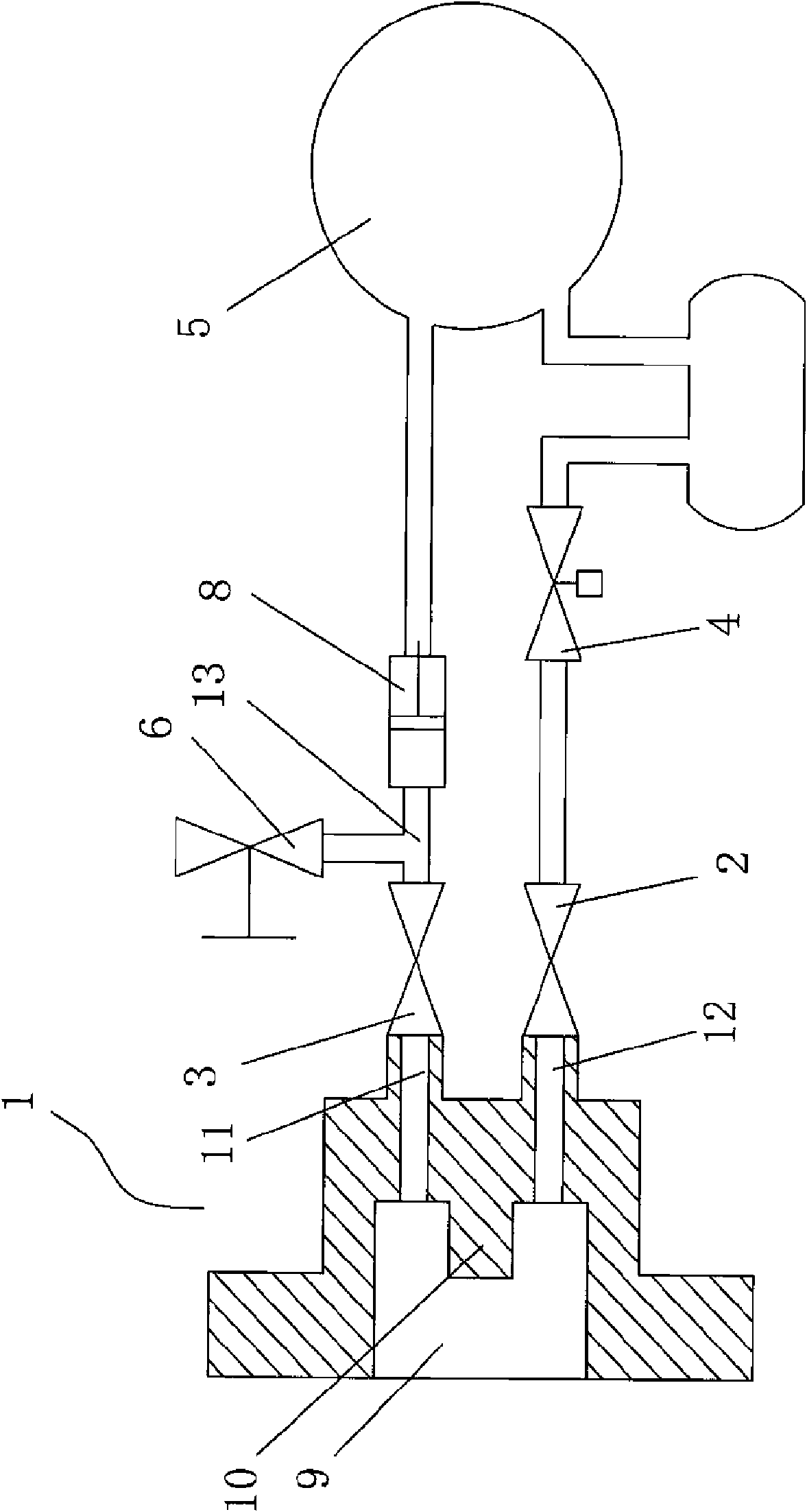
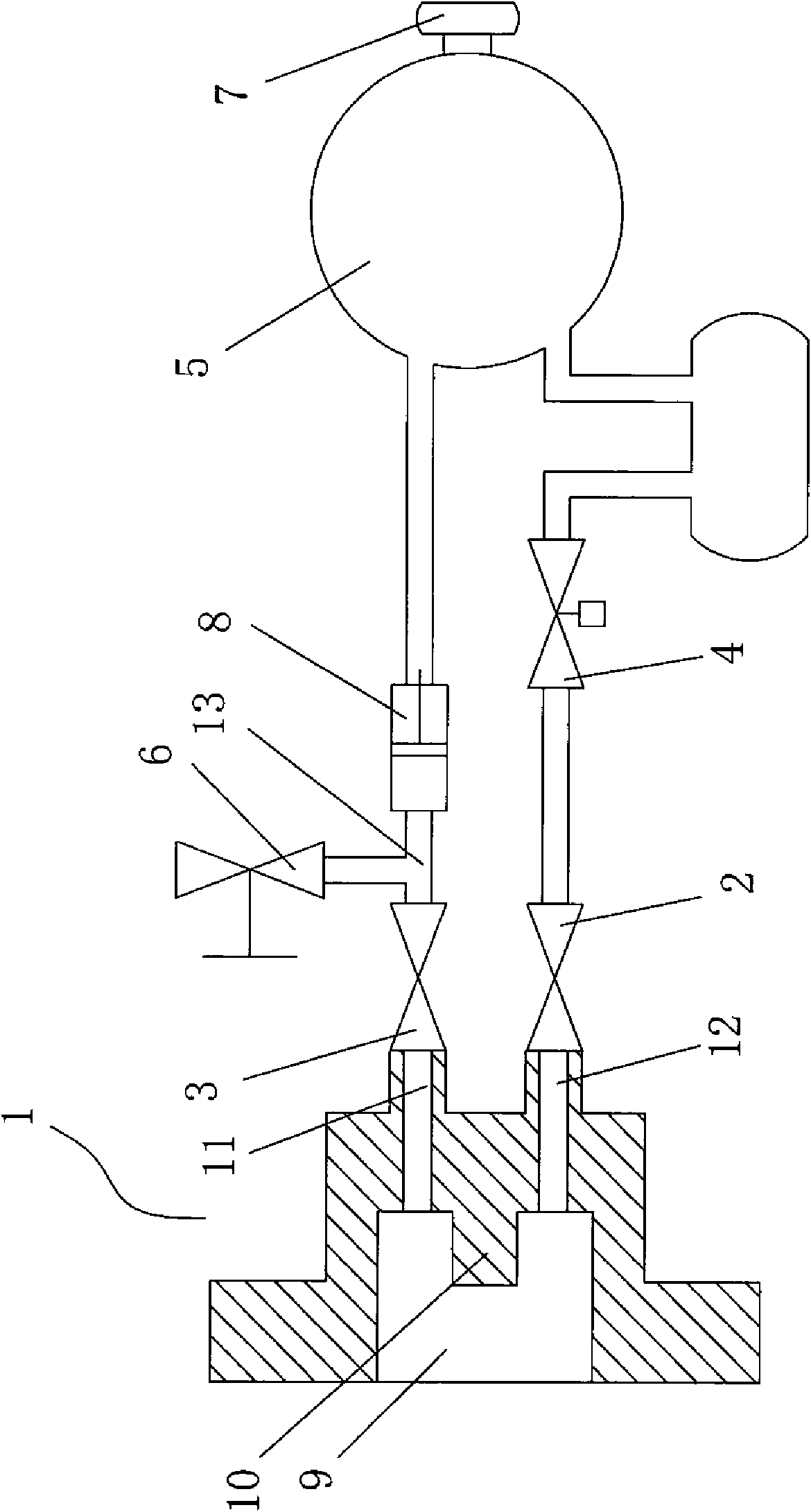
Sealing gas sampling apparatus
InactiveCN101587031AConducive to environmental protectionAvoid economic lossWithdrawing sample devicesEngineeringElectromagnetic valve
The invention discloses a sealing gas sampling apparatus, including an adapter, a first electromagnetic valve, a second electromagnetic valve, a gas container, a vent valve and a minisize high-pressure air pump. One end of the adapter is provided with a connecting column and a convex column and the other end is provided with an air inlet and an air outlet. The air outlet of the adapter is connected with the inlet of the first electromagnetic valve. The outlet of the gas container is connected with the inlet of the minisize high-pressure air pump. The outlet of the minisize high-pressure air pump is respectively connected with the inlet of the second electromagnetic valve and the vent valve via a tee joint. The outlet of the second electromagnetic valve is connected with the air inlet of the adapter. An interface is arranged on the gas container. The sealing gas sampling apparatus can sample the sealing gas. The gas passing through the sampling and analysis instrument can be charged to the electrical apparatus or the gas tank timely to realize the effective sampling of the measured gas, thus benefiting environmental protection and avoiding the economic loss.
Owner:施宏
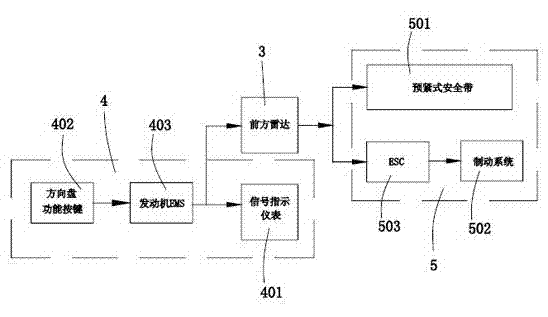
Test method and device for calibrating lateral coming vehicle by head-on collision prevention system
InactiveCN102564719AAbsolutely safeWide speed adjustment rangeVehicle testingWave based measurement systemsHead-on collisionControl system
The invention discloses a test device for calibrating a lateral coming vehicle by a head-on collision prevention system. The head-on collision prevention system comprises a control system, a radar arranged on a test vehicle and a vehicle passive safety control device; the test device comprises a simulated object positioned at the periphery of the test vehicle; the control system is provided with at least four control stages, namely a normal stage, a tracking stage, a prewarning stage and a collision buffering stage, and at least four corresponding instruction signals; the simulated object is a lateral coming vehicle simulation plate; the size of the simulation plate is the same as that of an actual vehicle; a vehicle lateral image is arranged on the surface of the simulation plate; and the simulation plate does motion along a direction vertical to a running direction of the test vehicle right in front of the test vehicle under the driving of a driving device. Therefore, the simulation plate can be effectively used for simulating the front lateral coming vehicle, so that traffic accidents easily caused by calibration by using a real vehicle and a real person are avoided, and the safety of testers is guaranteed effectively.
Owner:ZHEJIANG GEELY AUTOMOBILE RES INST CO LTD +1
Manipulator of high-altitude live working vehicle
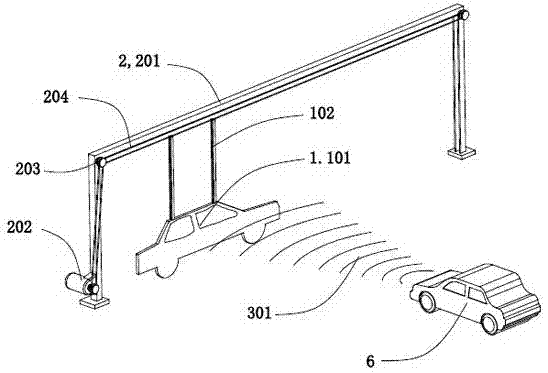
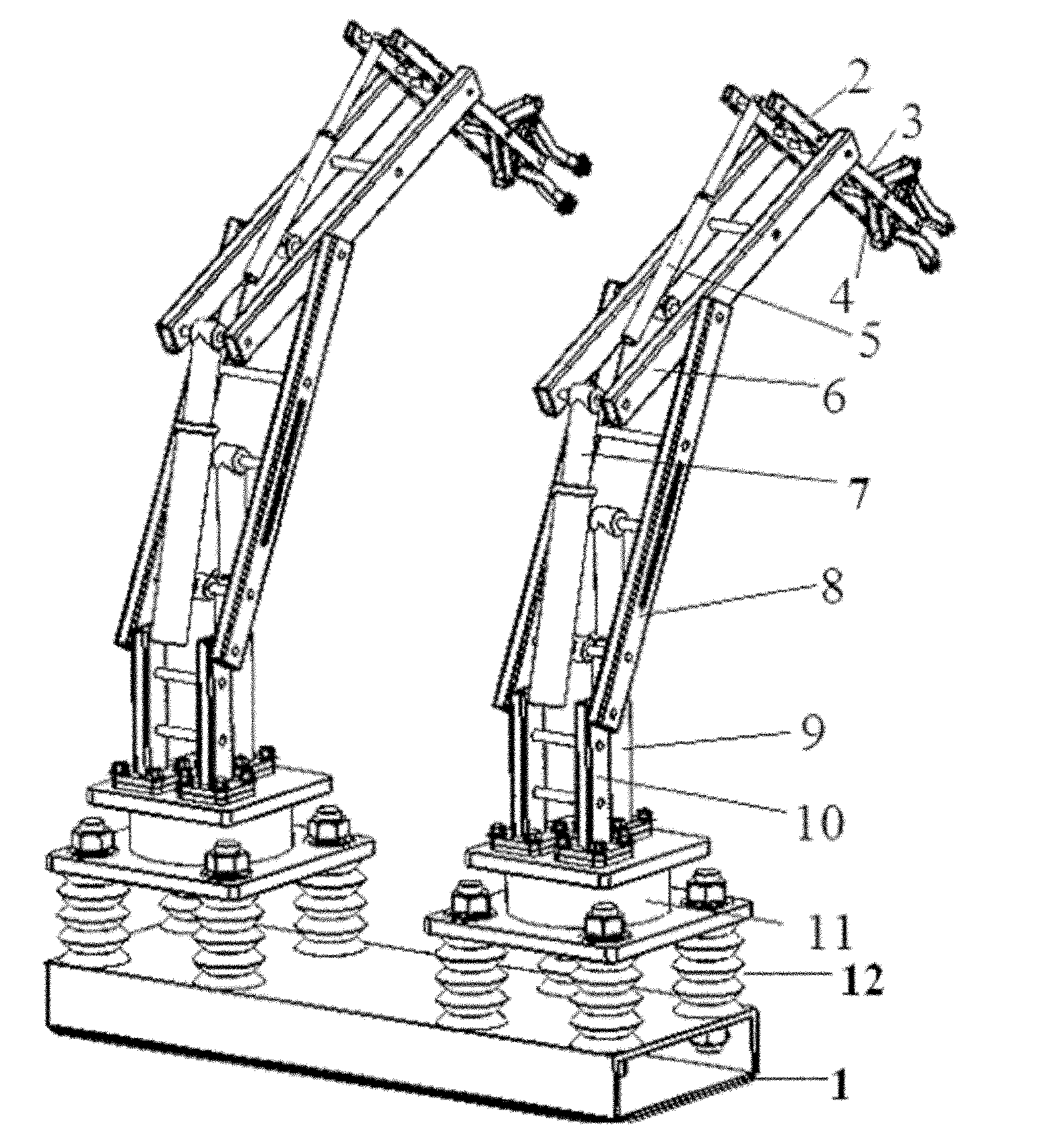
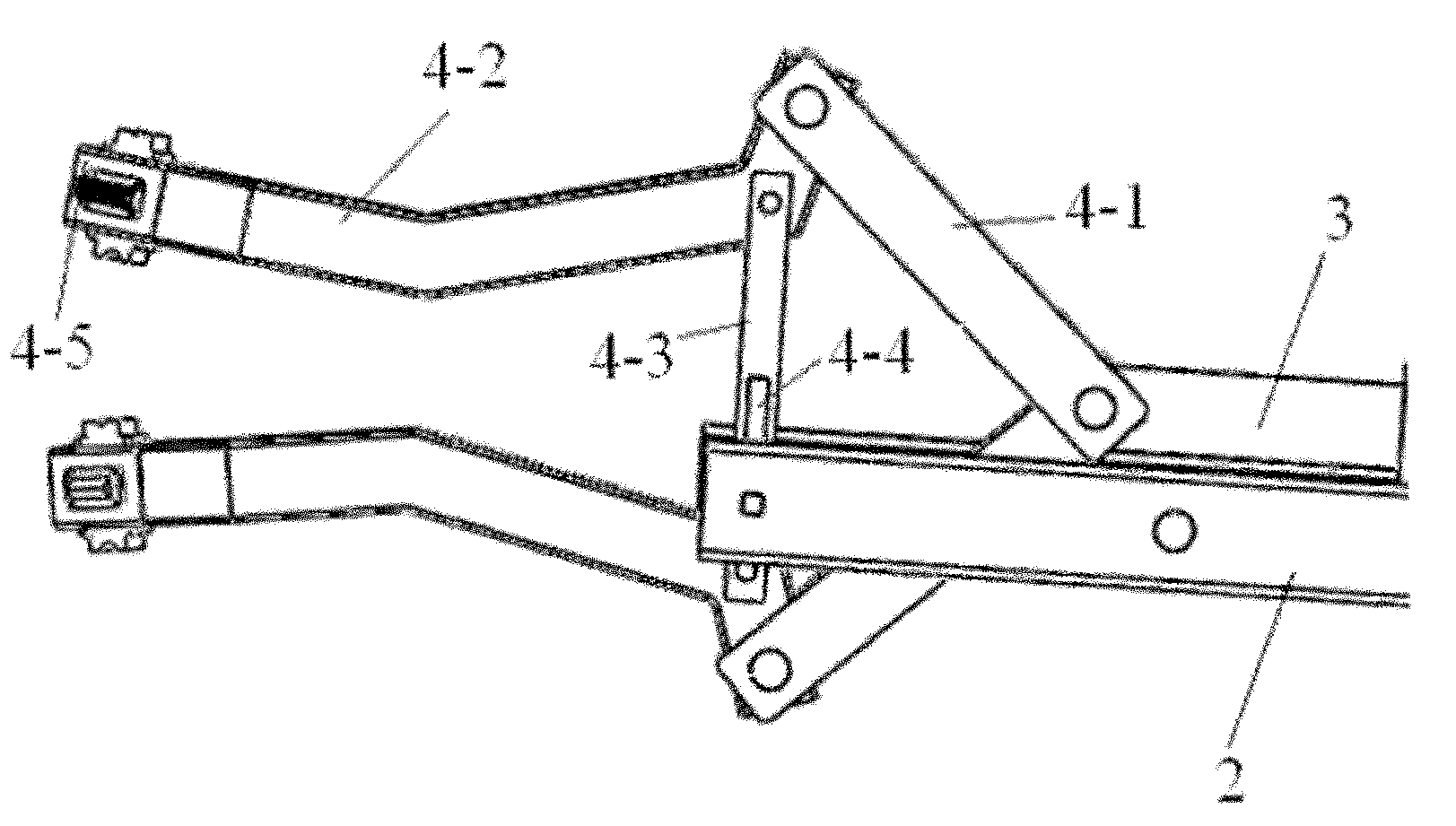
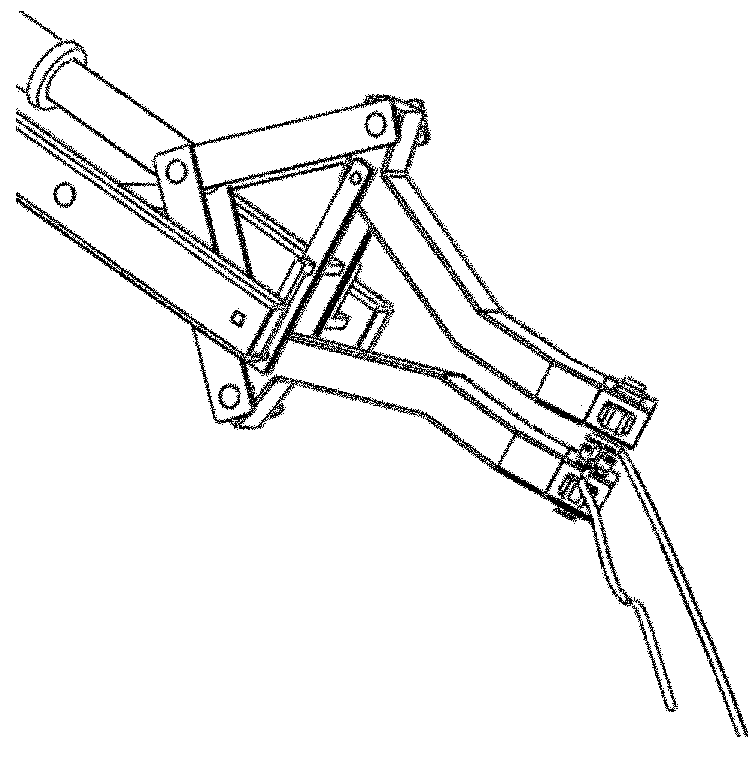
InactiveCN102152292AAbsolutely safeReliable insulation safety protection measuresProgramme-controlled manipulatorRotary stageHydraulic cylinder
The invention relates to a manipulator of a high-altitude live working vehicle, which belongs to the field of special vehicles. The manipulator comprises a base and two manipulators, wherein each manipulator comprises a rotating platform, an insulation part, a lower arm, a middle arm, an upper arm, a small arm, a tail end mechanism, and hydraulic cylinders of the middle arm, the upper arm, the small arm, and the tail end mechanism; the lower arm and the middle arm, as well as the middle arm and the upper arm, and the upper arm and the small arm are hinged; the small arm is connected with the tail end mechanism; the hydraulic cylinder of the middle arm is fixed on the rotating platform and is hinged with the middle arm; the hydraulic cylinder of the upper arm is hinged with the middle arm and the upper arm; the hydraulic cylinder of the small arm is hinged with the upper arm and the small arm; and the hydraulic cylinder of the tail end mechanism is connected with the small arm and the tail end mechanism. The tail end mechanism comprises a connecting bar, a paw, a crossbeam, a square dowel, and pincers mounted on the paw for taking, pressing and cutting wires, wherein the connecting bar is hinged with the hydraulic cylinder of the tail end mechanism and the paw; the paw is hinged with the crossbeam; and the square dowel is connected with the crossbeam and the small arm. When the manipulator is used for implementing high-altitude live working, the working safety can be guaranteed and the automation level can be improved.
Owner:TSINGHUA UNIV
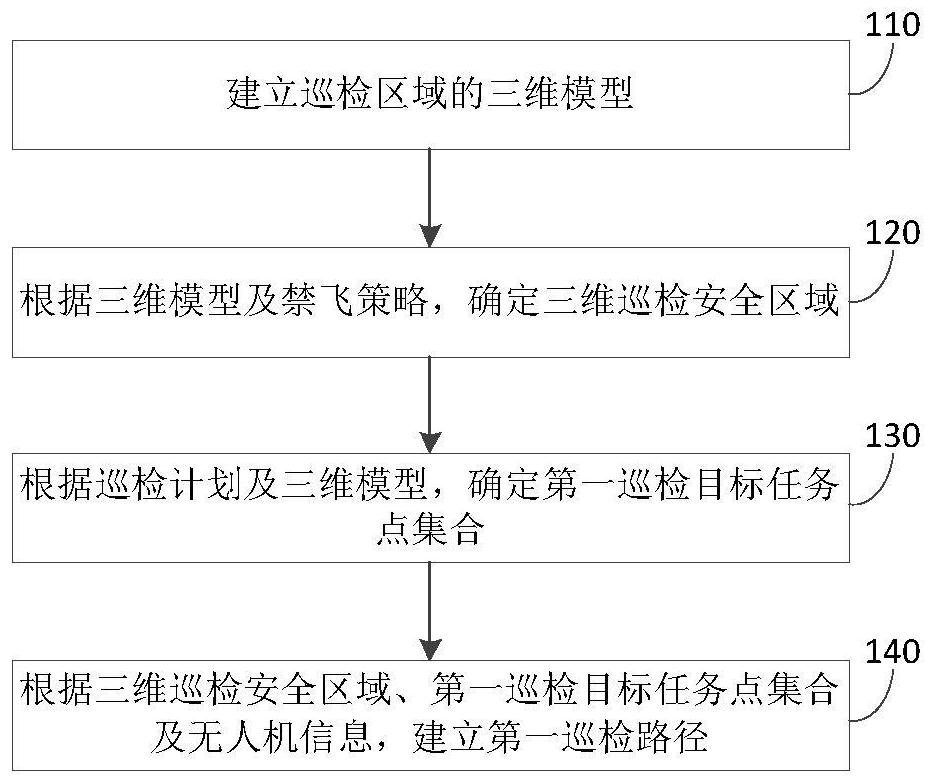
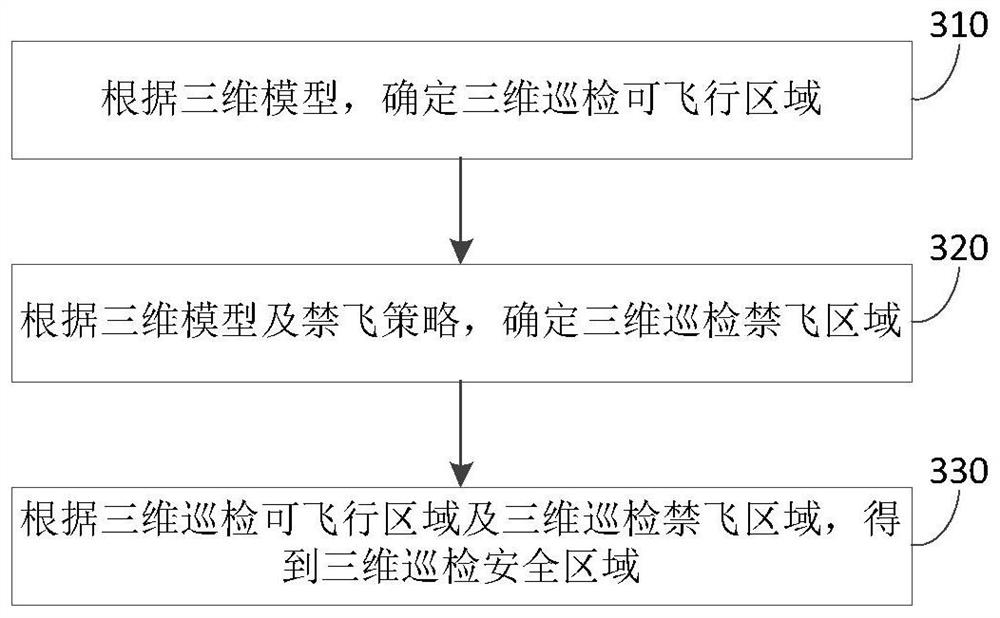
Unmanned aerial vehicle autonomous obstacle avoidance inspection path planning method and device
ActiveCN112327920AAbsolutely safeImprove flight safetyInternal combustion piston enginesPosition/course control in three dimensionsPoint cloudUncrewed vehicle
The invention provides an unmanned aerial vehicle autonomous obstacle avoidance inspection path planning method and device, and belongs to the field of unmanned aerial vehicle inspection, and the unmanned aerial vehicle inspection path planning method comprises the steps: building a three-dimensional model of an inspection region, wherein the three-dimensional model comprises the point cloud dataof equipment in the inspection region; determining a three-dimensional inspection safety area according to the three-dimensional model and a no-fly strategy; determining a first inspection target taskpoint set according to the inspection plan and the three-dimensional model; and establishing a first inspection path according to the three-dimensional inspection safety area, the first inspection target task point set and the unmanned aerial vehicle information. According to the embodiment, absolute safety of the unmanned aerial vehicle during inspection can be guaranteed, the method has the characteristic of small calculation amount, the inspection path can be planned quickly, accurately and automatically, so that the unmanned aerial vehicle is feasible in the inspection area, obstacles areprevented from being collided, and flight safety and flight efficiency of inspection operation of the unmanned aerial vehicle in the inspection area are improved.
Owner:MAINTENANCE COMPANY OF STATE GRID XINJIANG ELECTRIC POWER COMPANY +1
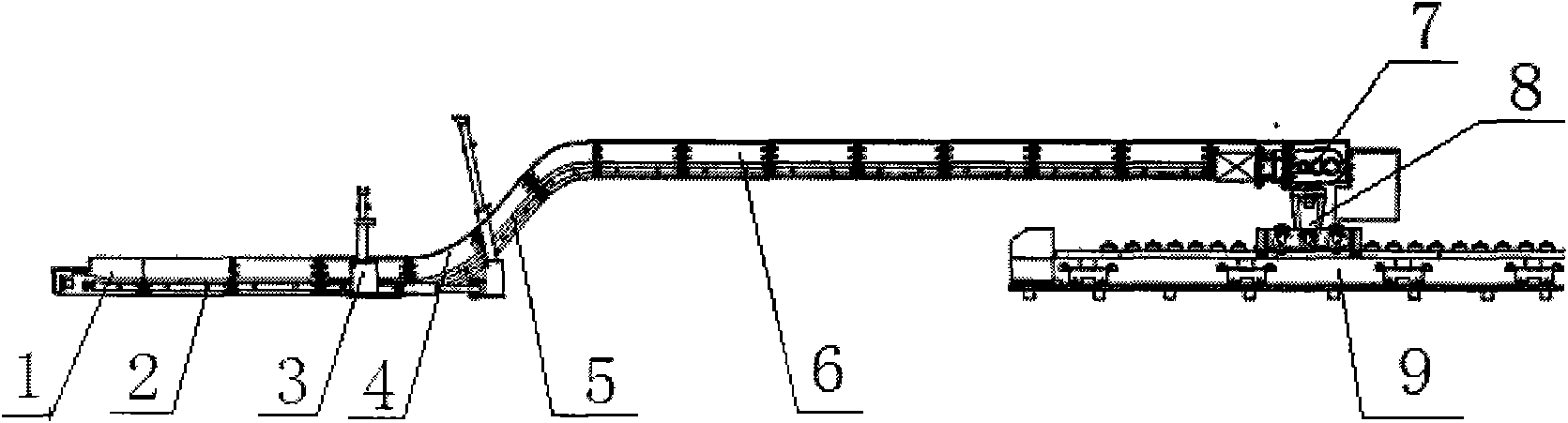
Self-moving type reversed loader for coal mine
ActiveCN101775993AWith automatic forward abilityNot easy to fall offEarth drilling and miningUnderground transportCoal
The invention relates to a coal cutting machine, in particular to a self-moving type reversed loader for a coal mine, which solves the problems of the waste and poor effect of large-scale mechanized devices used in the coal cutting process in some mine areas. The self-moving type reversed loader for the coal mine comprises a machine tail assembly, a bottom plate, a lower bend groove, an upper bend groove, a bridge part and a handpiece of the bridge part which are connected with one another sequentially, wherein the bottom plate consists of a coal groove and a plurality of transportation grooves; the bridge part consists of a plurality of transportation grooves; a paddled conveyor chain is arranged on the transportation groove between the machine tail assembly and the handpiece; a traveling trolley is arranged below the handpiece connected with the bridge part and connected with a coal receiving device; the traveling trolley and the coal receiving device are arranged on a transportation frame; and automatic push devices are arranged on two sides of the bottom plate. The self-moving type reversed loader is provided with a capability of automatically moving forward and a totally-closed floor, non-broken paddled conveyor chain and a totally-closed machine tail cover so as to ensure the absolute security of personnel passing through. The self-moving type reversed loader is also provided with higher left and right coal baffle plates, so the coal does not fall off on the ground during transportation, the number of workers for sweeping coal is reduced and the standardization of the coal quality can be ensured.
Owner:SHANXI JINCHENG ANTHRACITE COAL MINING GRP CO LTD
Method for constructing STPM of android system
ActiveCN103530578AImplement secure bootAchieve securityDigital data protectionInternal/peripheral component protectionHardware architectureTrusted Platform Module
The invention discloses a method for constructing an STPM of an android system. According to the dependable computing conception, on the basis that an existing handheld device hardware architecture is not changed, the TPM technology idea and the divide-and-conquer conception are adopted, and the functions of dependable storage, dependable measurement, three-layer key management and the like of the STPM are respectively achieved in the android system; the STPM is constructed to provide a basis for secondary safe development on mobile devices, and on the basis, developers can further achieve the development of various safety functions such as safe start of the system, measurement on start of upper-layer application programs and protection on private data of users. The method provides the basis for system safety of the mobile devices and privacy of the private data of the users from the bottom layer of the system. The method mainly has the advantage that the construction of the STPM overcomes the defect that the existing mobile devices lack a TPM and provides the basis for safe development of the mobile devices.
Owner:WUHAN UNIV
Physical unclonable function based wireless sensor network and realizing method thereof
InactiveCN102523579AEnsure safetySolve the copy attack problemNetwork topologiesTransmissionMobile wireless sensor networkWireless mesh network
The invention discloses a physical unclonable function based wireless sensor network, which comprises a plurality of terminals and a server. The server is connected with the terminals. The invention further discloses an application method of the physical unclonable function based wireless sensor network. By the physical unclonable function based wireless sensor network, the defect of singularity of safety technology of the existing wireless sensor network is overcome, safety of the integral network and data of the terminals is guaranteed by synthetizing multiple technologies, a complete system is formed, high safety and reliability of the architecture of the physical unclonable function based wireless sensor network are guaranteed, and the physical unclonable function based wireless sensor network has wide prospect of application of the internet of things.
Owner:SOUTHEAST UNIV
Thermoplastic elastomer, preparation method and use thereof
The invention relates to a thermoplastic elastomer, which comprises the following compositions by gross weight percentage: A. 5 to 85 percent of polypropylene; B. 5 to 90 percent of vinylated styrene hydrogen / conjugated diolefine segmented copolymer; and C. 5 to 90 percent of polyolefin thermoplastic elastomer. The preparation method is to physically mix mixture of various compositions for manufacturing transparent coating materials and so on. The thermoplastic elastomer has the advantages that the thermoplastic elastomer has good transparency, does not contain plasticizer such as processing oil and so on, so that emigration of the thermoplastic elastomer during the use process is avoided, thereby guaranteeing the absolute safety of the thermoplastic elastomer when applied to products such as foodpack, medical appliances and so on; the product is soft; the shore A rigidity is between 0 and 95; the flow rate of fused masses is between 0.1 and 100 grams per 10 minutes; and the thermoplastic elastomer has good weathering resistance, chemical resistance and solvent resistance.
Owner:KURARAY SHANGHAI
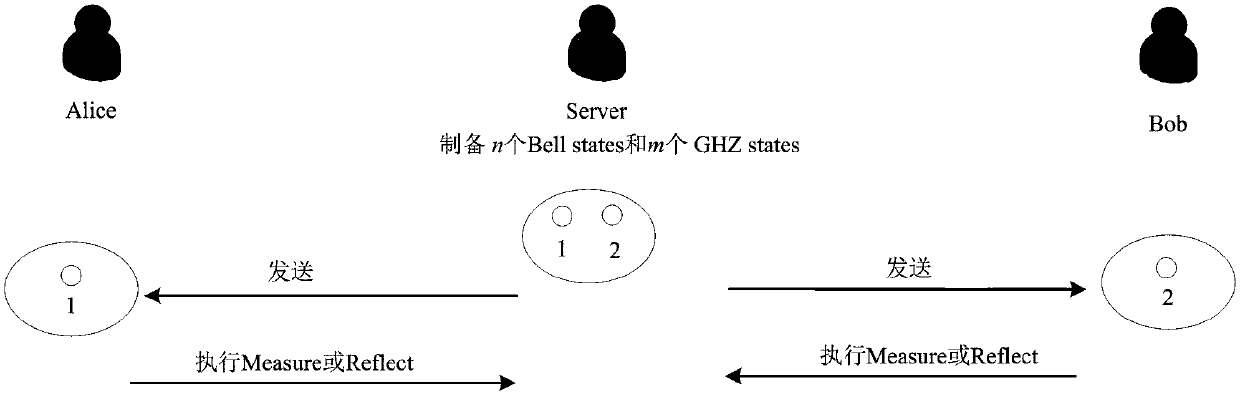
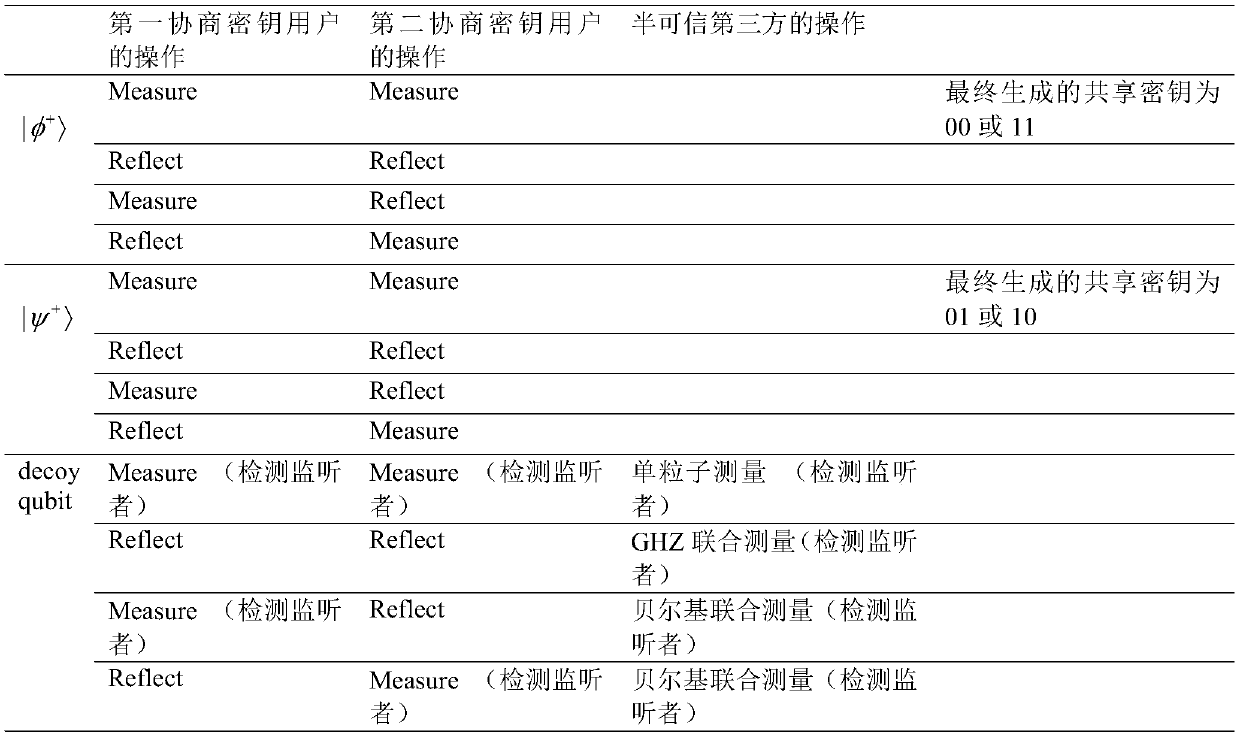
Semi-quantum technology based two-party key negotiation method and system
ActiveCN108173654AAbsolutely safeMeet fairnessKey distribution for secure communicationThird partySecure communication
The invention belongs to the field of quantum technology based secure communication, and discloses a semi-quantum technology based two-party key negotiation method and system. Three users participatein execution of this protocol, wherein the users include two users who negotiate keys and a semi-trusted third party; the two users only need to have two basic quantum functions, specifically: measurement: using a classical base {|0), |1)} to measure a quantum, generating a new quantum |0) or |1), and sending the new quantum out; reflection: directly sending the quantum to a sender without any modification after the quantum is received. The third party has advanced quantum functions, can prepare quantum states, can use various bases to measure quantum states, and have a quantum storage function. The invention discloses a semi-quantum technology based two-party key negotiation system at the same time. The protocol proposed by the invention is a quantum technology based two-party key agreement protocol, and the fairness of the protocol is also satisfied under the premise of ensuring the absolute security of the key.
Owner:CHENGDU UNIV OF INFORMATION TECH
Security pre-encoding method of multi-user opposite end-to-end relay system
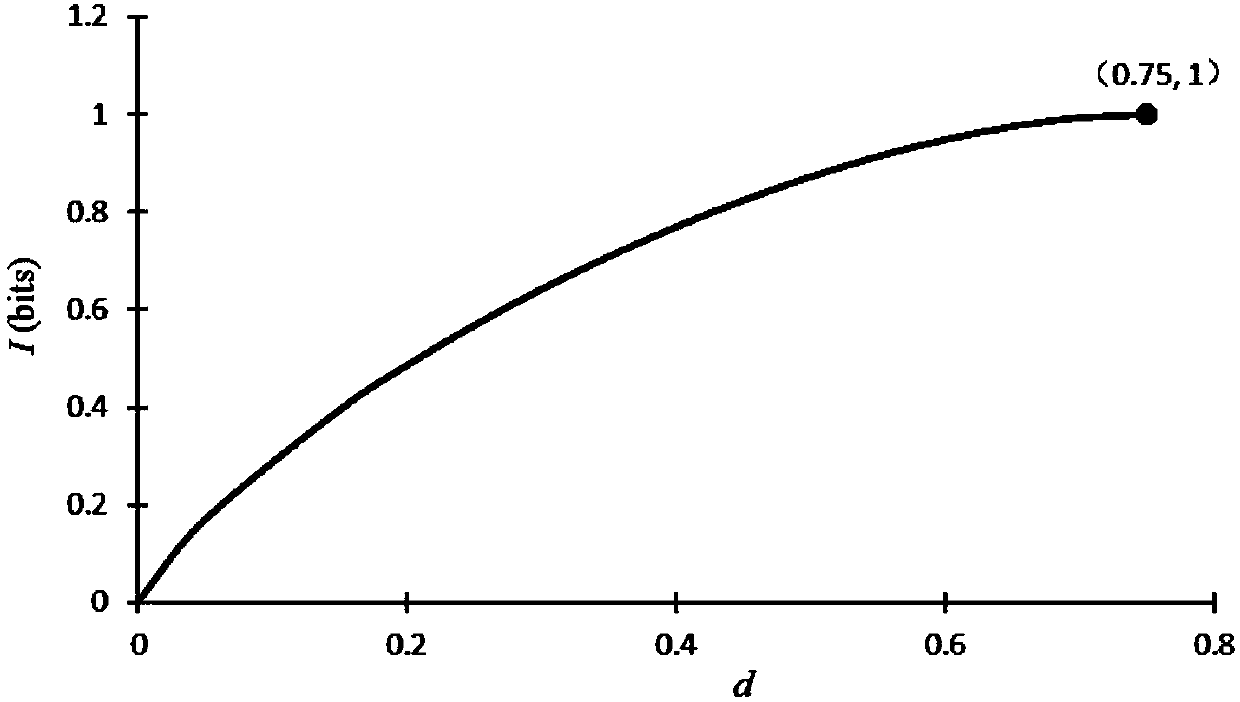
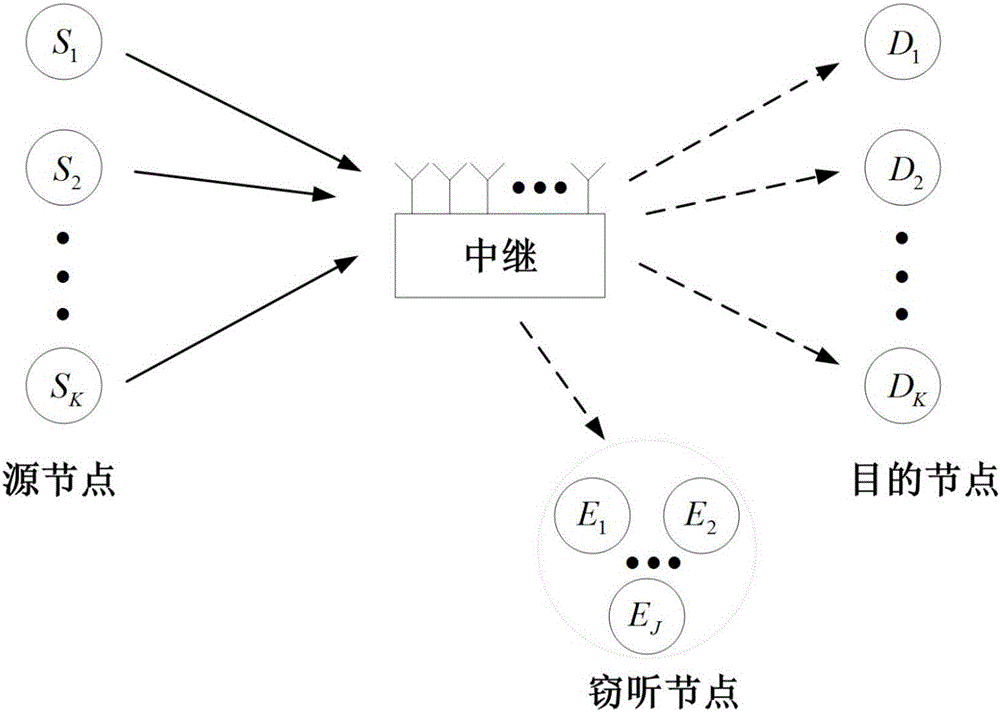
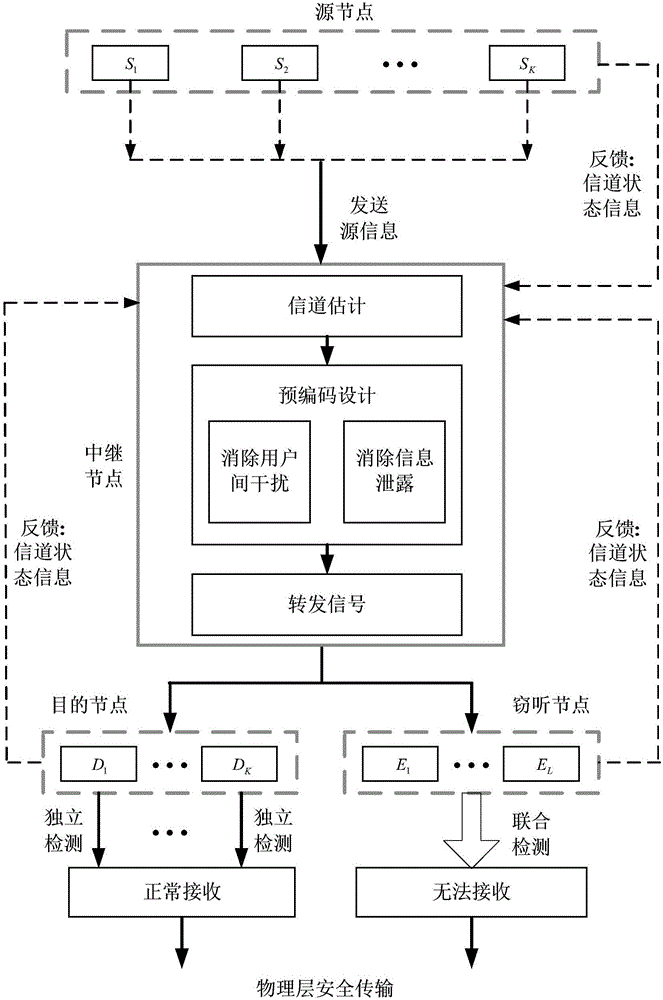
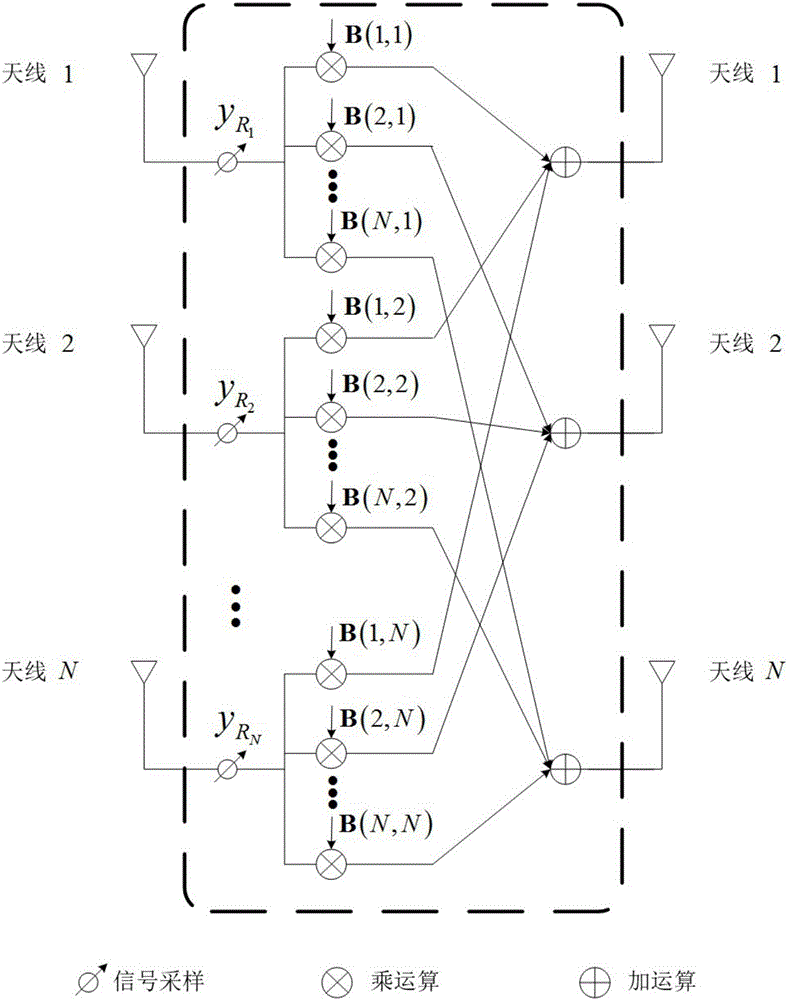
ActiveCN106788643AAbsolutely safeAdd dimensionRadio transmissionChannel estimationComputer hardwarePrecoding
The invention discloses a security pre-encoding method of a multi-user opposite end-to-end relay system. Multi-user interference can be eliminated from corresponding target nodes of relay nodes by virtue of differences of channels by using a pre-encoding signal processing techniques, and zero-forcing processing is implemented in an eavesdrop node direction, so that information security transmission is achieved. On the other hand, multi-user interference is eliminated, information disclosure is prevented, detection complexity of a target node receiver is degraded, and security transmission of information is ensured. On the other hand, main complexity is integrated in a fixed facility relay, hardware requirements of a mobile user is simplified, moreover, as only simple addition and multiplication operation is implemented by the relay nodes to received signals, the security pre-encoding method is simple in hardware achievement and relatively good in practicability.
Owner:PLA UNIV OF SCI & TECH
Method for processing suspension top by medium-deep hole blasting on upper and lower shoes
ActiveCN102337893AAbsolutely safeSimple construction organizationUnderground miningSurface miningDetonatorEngineering
The invention relates to a method for processing suspension top by medium-deep hole blasting on upper and lower shoes, comprising the steps of: simultaneously tunneling two drilling connection tunnels, on a tunnel upper shoe and a tunnel lower shoe of an electric shovel discharging tunnel, perpendicularly passing through a mineral vein; after the drilling connection tunnels pass through the mineral vein, tunneling two medium-deep hole drilling tunnels which is in parallel with the electric shovel discharging tunnel, faces towards the direction of the suspension top part, and is perpendicularly connected with the drilling connection tunnel, wherein the medium-deep hole drilling tunnels are tunneled exceed the suspension top part; performing construction of medium-deep holes in the two drilling tunnels towards the suspension top part according to the data for ore bring-down through blasting, such as row distance of 1-1.5m and hole bottom distance of 1-1.5m; drilling holes in each row; loading explosive in the medium-deep holes by a explosive loading machine; performing millisecond blasting by a millisecond detonator; and thereby breaking the suspension top by one-time blasting. Themethod for processing suspension top by medium-deep hole blasting on upper and lower shoes has the advantages that the deslagging is performed by the electric shovel, so that the labor intensity is small and the construction efficiency is high; operation is not performed on the tops of gobs so that the operation is ensured to be absolutely safe.
Owner:ANSTEEL GRP MINING CO LTD
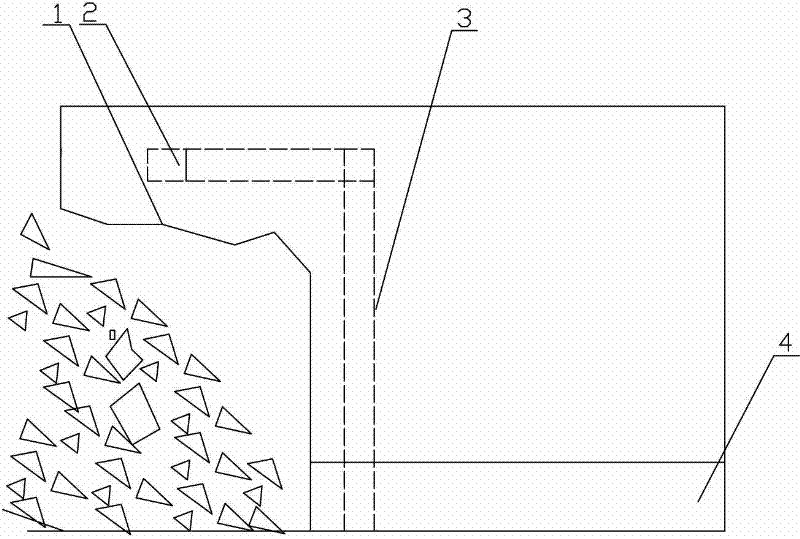
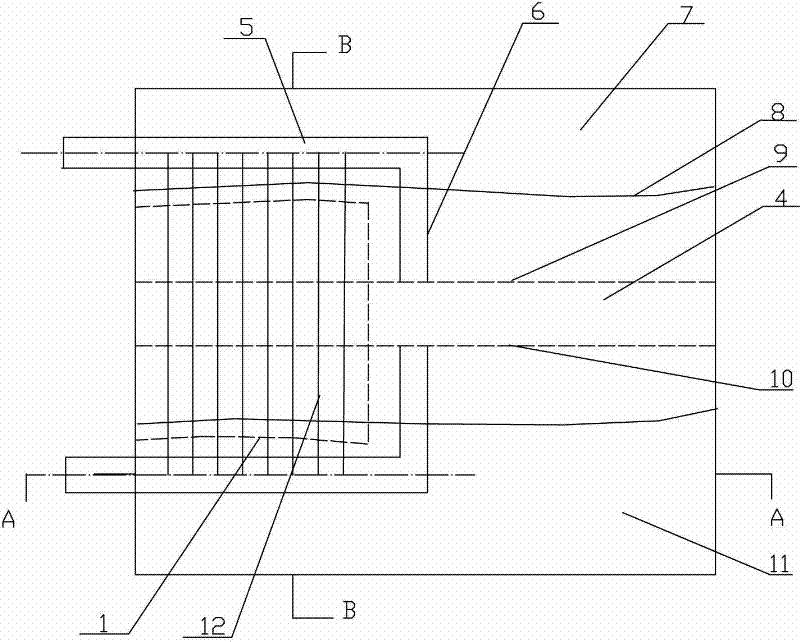
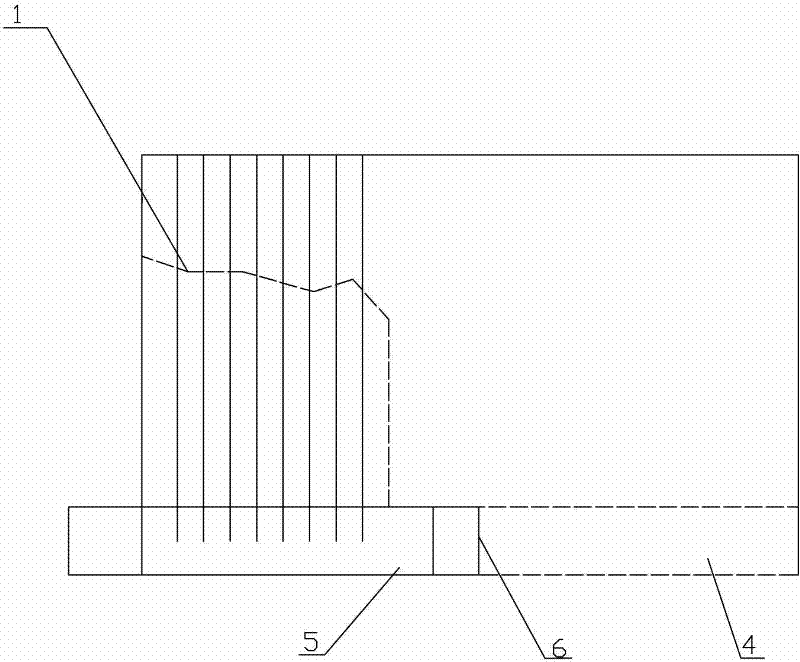
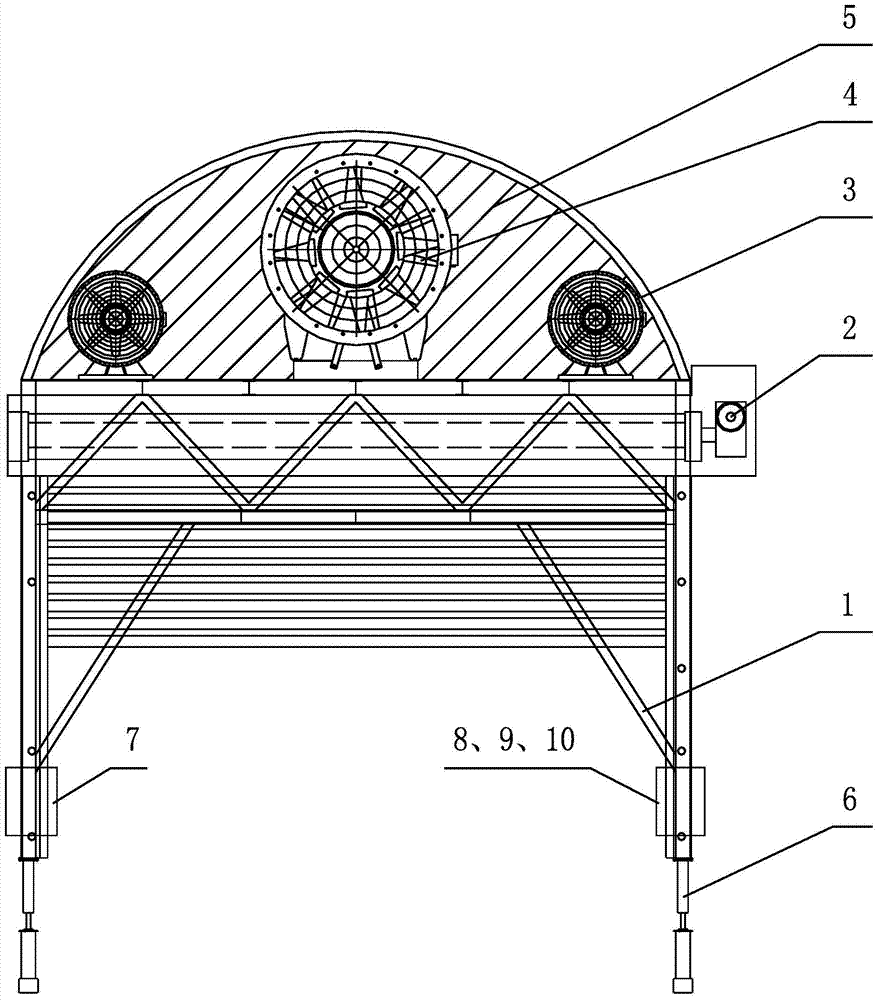
Rapid ventilation and smoke exhausting device and method for construction period of long-distance tunnel
ActiveCN104500123AGuaranteed structural strengthEasy to operateDust removalFire preventionElectric machineryPollutant
The invention provides a rapid ventilation and smoke exhausting device for a construction period of a long-distance tunnel. The rapid ventilation and smoke exhausting device comprises a gantry bracket, a fixed wind door and a movable wind door, an axial flow ventilator and a jet flow draught fan, and a motor control system, wherein the fixed wind door is arranged at the upper end of the gantry bracket and the movable wind door is arranged on one side of the gantry bracket; the axial flow ventilator and the jet flow draught fan penetrate through the fixed wind door; the fixed wind door is matched with the unfolded movable wind door so that the axial wind flow in the tunnel is separated; a wind inlet of the axial flow ventilator and a wind outlet of the jet flow draught fan are formed in one side, which is close to a working surface, of the fixed wind door; the wind outlet of the axial flow ventilator is connected with a flexible wind barrel; the wind outlet of the flexible wind barrel extends to the outer part of the tunnel. According to a ventilation and smoke exhausting method provided by the invention, the wind doors for separating the axial wind flow are arranged in the tunnel; a safe space and a closed polluted space are formed on the two sides of the wind doors respectively, and pollutants in the polluted space can be discharged out of a hole along an airflow through a closed exhausting channel by using ventilation equipment; blasting equipment is used for blasting wind into the polluted space from the safe space so that the pollutants rapidly flows towards the inlet of the ventilation equipment.
Owner:中国葛洲坝集团第三工程有限公司
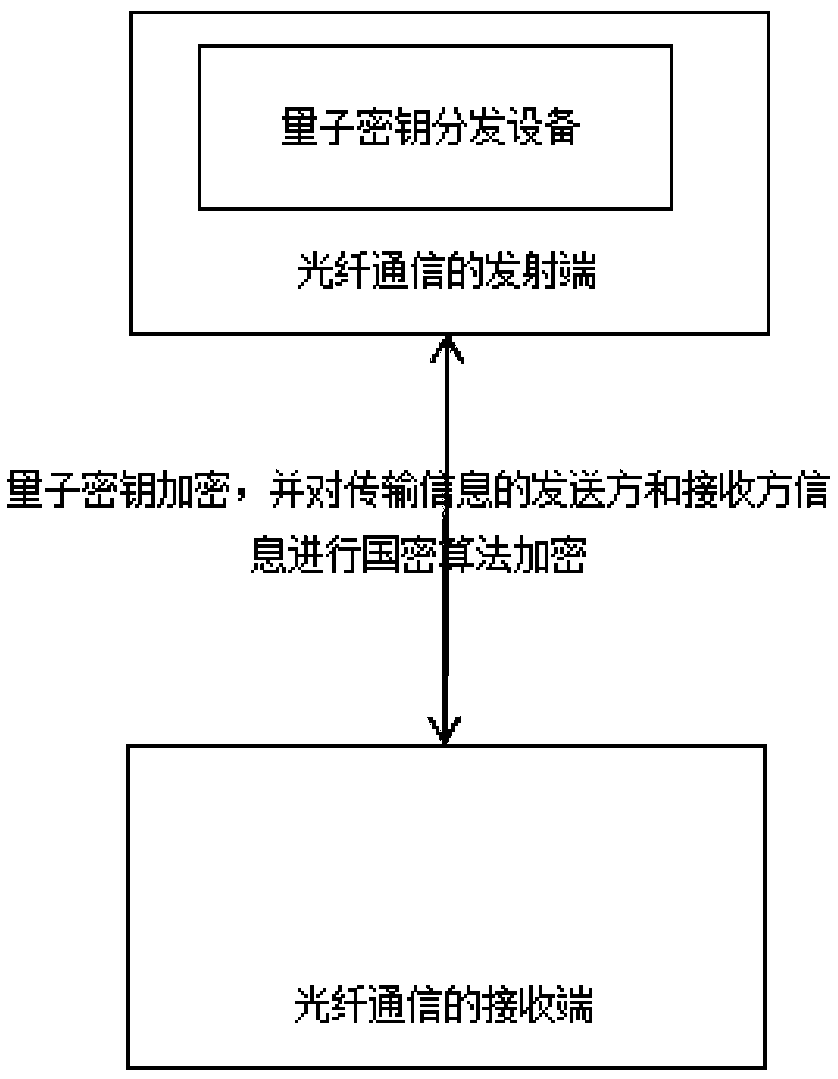
Information transmission encryption method based on combination of national secret algorithm and quantum communication technology
InactiveCN109462471ALarge transmission capacityIncrease transfer rateKey distribution for secure communicationEncryption apparatus with shift registers/memoriesInformation transmissionFiber-optic communication
The invention discloses an information transmission encryption method based on combination of a national secret algorithm and a quantum communication technology. The method comprises the steps that: the encryption method is realized based on an optical communication network; a quantum key distribution device is arranged at the optical communication transmitting end; data transmitted by optical communication is subjected to quantum key encryption through the quantum key distribution device; furthermore, sender and receiver information of transmission information is subjected to national secretalgorithm encryption; sender address information decryption is carried out at first when a receiver decrypts the received information; and, a quantum key decryption channel is provided for transmission data decryption after sender information is decrypted. According to the method in the invention, transmission information encryption is carried out by adoption of the quantum key; the sender and thereceiver can perform secret communication; this is the first layer of encryption; furthermore, communication address information of the sender and the receiver is subjected to national secret algorithm encryption; stealing of local data after source data is tracked and the receiver receives information can be avoided; and thus, the secret information data transmission security is ensured better.
Owner:有份儿智慧科技股份有限公司
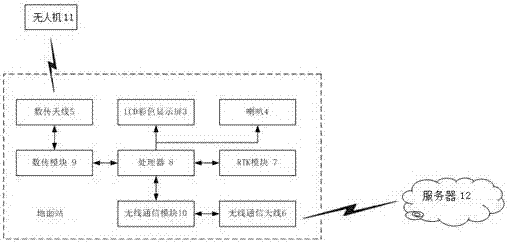
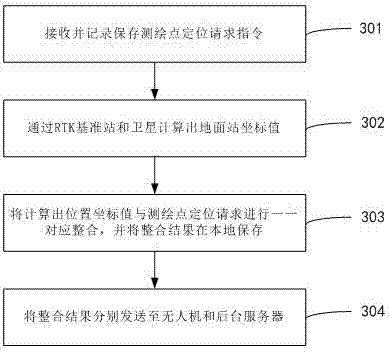
Hand-held ground station for unmanned aerial vehicle and surveying and mapping and positioning method thereof
PendingCN106932801AHigh positioning accuracyHigh precisionSatellite radio beaconingUncrewed vehicleGround station
The invention provides a hand-held ground station for an unmanned aerial vehicle and a surveying and mapping and positioning method thereof. The method comprises the following steps: receiving a surveying and mapping point positioning request instruction, and recording and keeping the surveying and mapping point positioning request instruction; according to the surveying and mapping point positioning request instruction, calculating a ground station coordinate through an RTK base station and a satellite, wherein the ground station coordinate is a surveying and mapping point position coordinate; carrying out one-to-one correspondence integration on the calculated position coordinates and surveying and mapping point positioning requests and keeping the integration results locally; and sending the integration results to the unmanned aerial vehicle and a background server. According to the unmanned aerial vehicle ground station, through RTK positioning, positioning accuracy of the surveying and mapping point, a landing point when the unmanned aerial vehicle returns and safety distance during flight is improved; and besides, through surveying and mapping of the ground station, the ground station can carry out pre-spray surveying and mapping instead of a conventional hand-held surveying and mapping rod, and plant protection work can be finished without uploading the surveying and mapping result to the background server, thereby reducing requirement for an environment network.
Owner:JIAGUTECH CO LTD
Information protection method and device
InactiveCN104579685AAbsolutely safeNo maintenance issuesUser identity/authority verificationTrust levelComputer science
The invention provides an information protection method and device. The method comprises the steps that false contact person information is generated; the trusted levels of all applications are set, the applications are at least classified to be the trusted applications and the non-trusted applications, and the authority of accessing the false contact person information is given to the non-trusted applications; whether the applications which request to access the contact person information are the non-trusted applications or not is judged; if yes, the false contact person information is provided for the non-trusted applications. The information protection device comprises a generation module, a setting module and a processing module. According to the information protection method and device, the false contact person information is provided for the non-trusted applications, the effects of confusing the public and lulling opponents are achieved, no chance of breaking is given to the opponents, and the absolute safety of privacy-sensitive information is guaranteed. The false contact person information generated by the method and device can be repeatedly used, compared with an existing encryption scheme, the system overhead is lowered to a great extent, and the maintaining problem of keys is solved.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
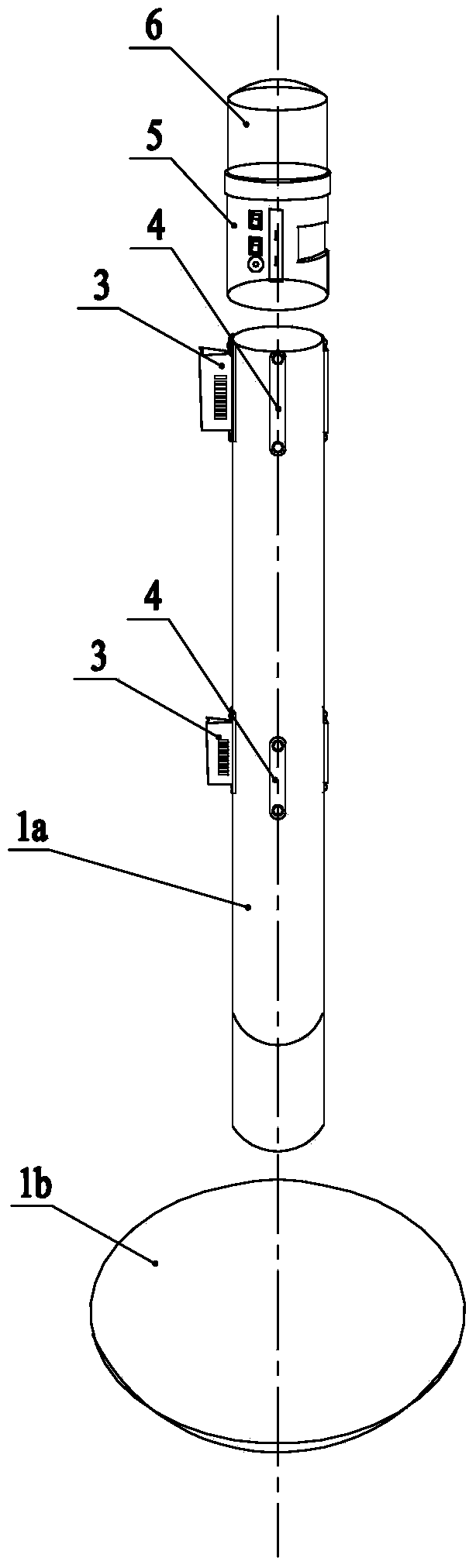
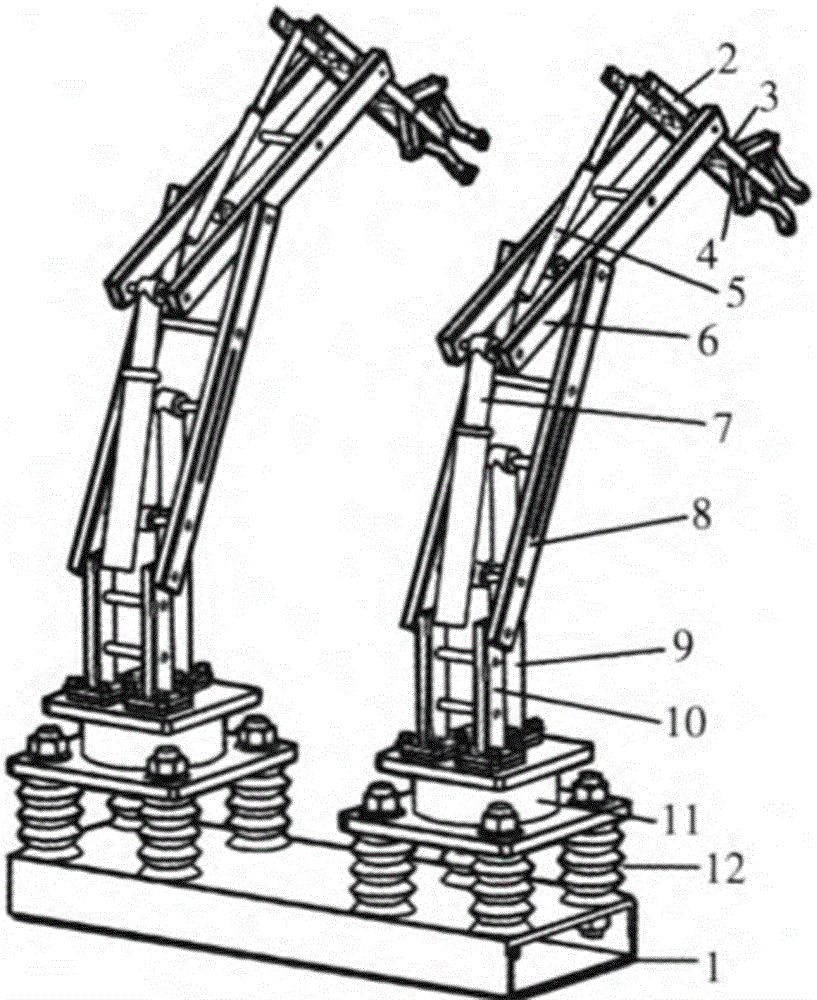
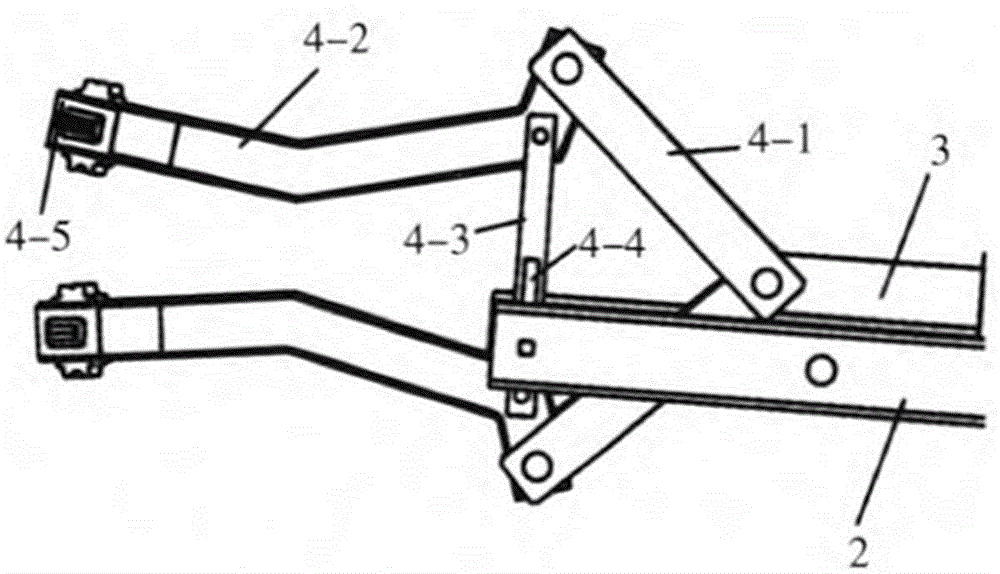
Mechanical hand of high-altitude electrified operating vehicle
InactiveCN106541384AAbsolutely safeCompact designManipulatorApparatus for overhead lines/cablesRotary stageWork content
Owner:褚秀清
Data encryption method based on NFC chip security authentication
ActiveCN106357404APrevent malicious tamperingAbsolutely safeMultiple keys/algorithms usageTimestampPassword
The invention relates to a data encryption method based on NFC chip security authentication. The method comprises the following steps: 1. The correct user name and password are entered by the user through the mobile terminal to verify the login; 2. After the login of the user is confirmed to be successful, a secret key in character string format is generated through the irreversible encryption of the user name, password and timestamp. To prevent the interactive data between the APP mobile terminal (NFC mobile phone) and the server (cloud server) is maliciously tampered with, cross-use of the 'reversible encryption' and the 'irreversible encryption' algorithms is adopted to ensure that interactive data between the mobile and the server terminals is absolutely safe.
Owner:北京小样科技有限公司
Angle variable slope for Mars land surface simulated environment
InactiveCN109708899AImprove conversion operation efficiencyShorten the development cycleVehicle testingCosmonautic condition simulationsEnvironment of AlbaniaSlope angle
The invention discloses an angle variable slope for the Mars land surface simulated environment. The slope comprises a horizontal platform, an inclined elevation platform, a horizontal elevation platform, a hydraulic device, a control device and a safety protection device, the inclined elevation platform is arranged between the horizontal platform and the horizontal elevation platform, and the three platforms forms a slope device of a flat-slope-flat structure. According to an instruction of the control device, the slope angle is adjusted, and after adjustment, the safety protection device isfastened to ensure that the slope angle is not changed due to accidents as oil leakage. The slope can bear large area of Mars soil, is reasonable and complete in structure, high in automatic degree and convenient to adjust the angle.
Owner:BEIJING INST OF SPACECRAFT ENVIRONMENT ENG
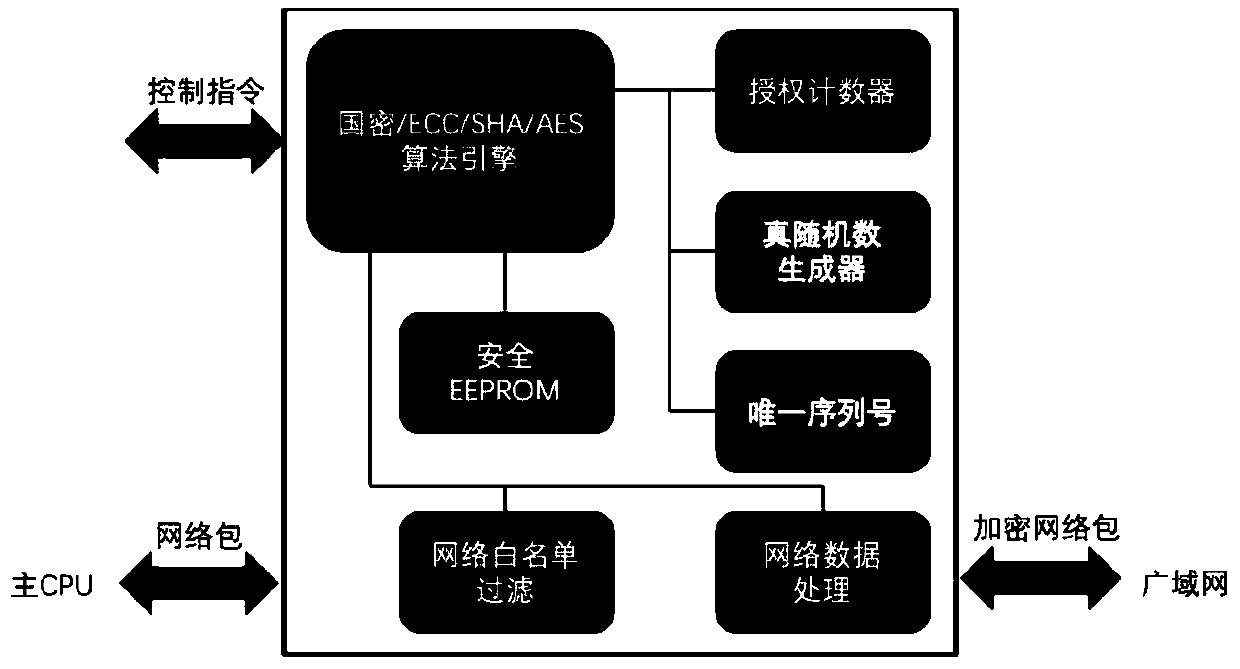
Security chip for protecting network security system and network security system using same
InactiveCN110430178AHigh speed encryptionHigh speed recoveryKey distribution for secure communicationUser identity/authority verificationCommunications securityData stream
A security chip for protecting a network security system comprises a data security part for providing a secure encryption and decryption algorithm and an interaction protocol, wherein the data security part mainly comprises an encryption and decryption algorithm control engine, an authorization counter, a true random number generator, a unique serial number and a secure EEPROM; and a network security part composed of a network white list filtering module and a network data processing module. The encryption and decryption algorithm control engine comprises private key security storage for supporting private key ECDH operation and ECDSA signature authentication. The mainstream national password and commercial password encryption and decryption algorithms perform high-speed encryption and reduction on the data stream so as to adapt to the security requirements of different scenes. The chip safety management supplies power, manages the read-write ROM on the chip, allows special equipment to write, and allows remote erasure but does not allow reading. The invention also provides a network security system using the security chip. The sensitive data communication security can be protectedfrom the hardware level, and the efficiency can be greatly improved while the system security is improved.
Owner:XI AN JIAOTONG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com