Semi-quantum technology based two-party key negotiation method and system
A key agreement, semi-quantum technology, applied in transmission systems, digital transmission systems, key distribution
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
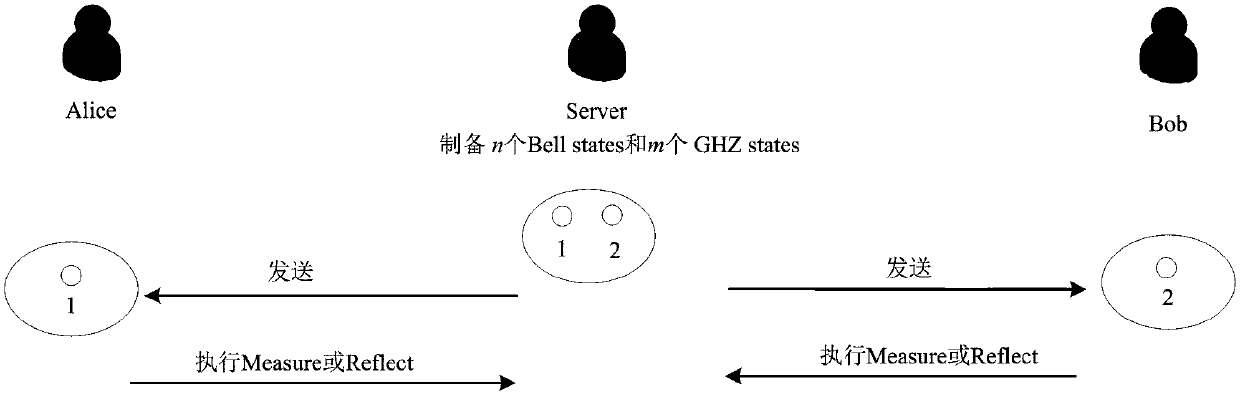
[0102] See figure 1 , this embodiment includes two parties who negotiate the key, the first negotiated key user and the second negotiated key user, and a semi-trusted third party and a semi-trusted third party.
[0103] The semi-trusted third party sends the particle sequence to the first negotiated key user and the second negotiated key user respectively, and the first negotiated key user and the second negotiated key user randomly select one of the two operations of Measure and Reflect implement.
Embodiment 2
[0105] See figure 2 , the using method of embodiment 1, comprises the following steps:
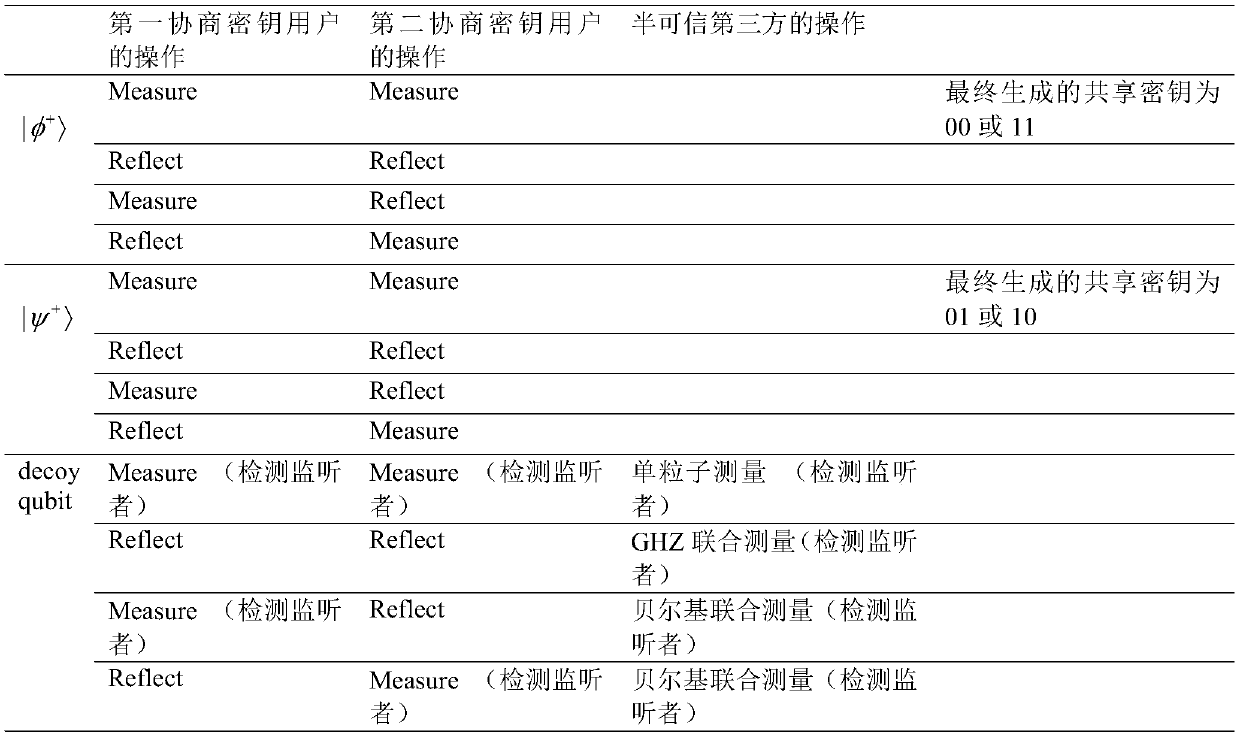
[0106] 1) If it is listening to detect particles.
[0107] Both the first negotiated key user and the second negotiated key user perform Measure, and the semi-trusted third party also performs single event measurement, and finds the listener according to the measurement results of the three parties.
[0108] Both the first negotiated key user and the second negotiated key user execute Reflect, and the semi-trusted third party conducts GHZ joint measurement of the two received particles and the corresponding particle in its own hands, and finds the listener according to the measurement results.
[0109] The first negotiating key user and the second negotiating key user execute Measure and Reflect respectively, then the semi-trusted third party conducts Belkey joint measurement of the reflected particles and the particles at the corresponding positions in their own hands, and finds the l...
Embodiment 3
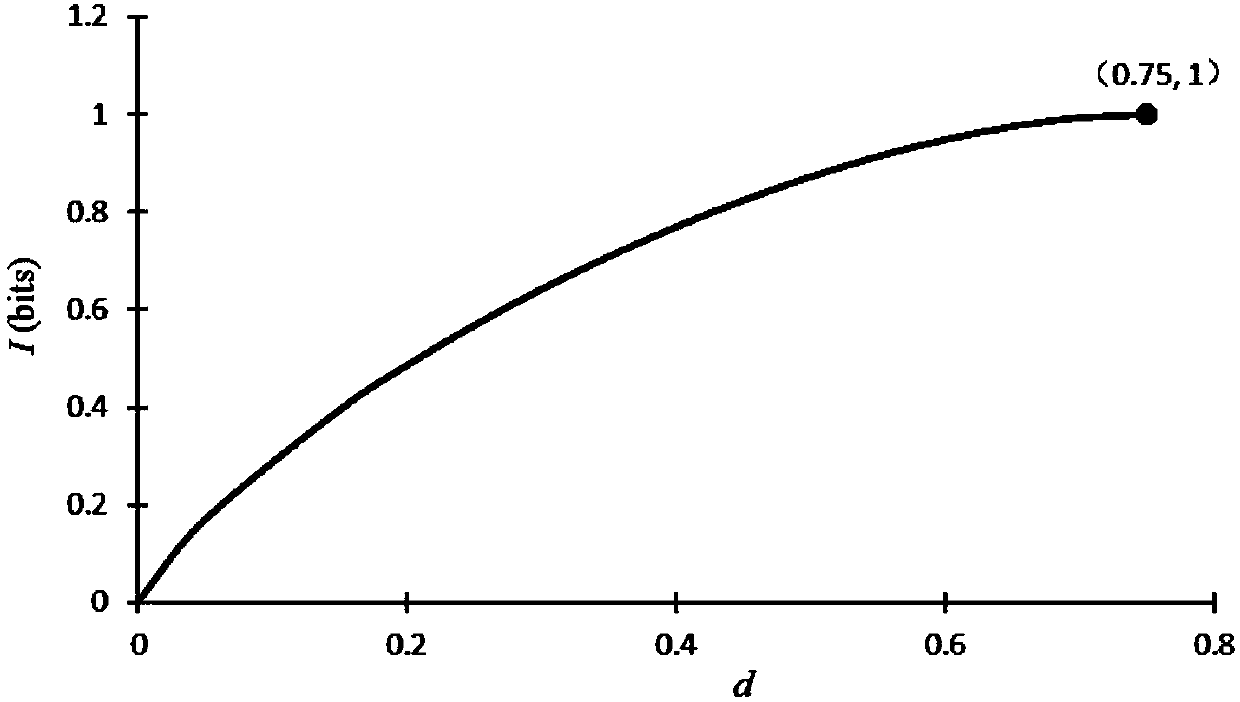
[0112] See image 3 , the usage method of embodiment 1, 2, if the listener wants to obtain complete information, the probability of being detected is 0.75%.
[0113] The present invention needs to be executed in a quantum communication network environment, so the participating computers have quantum functions, and a quantum network is required for transmission.
[0114] In the above embodiments, all or part of them may be implemented by software, hardware, firmware or any combination thereof. When implemented wholly or partly in the form of a computer program product, said computer program product comprises one or more computer instructions. When the computer program instructions are loaded or executed on the computer, the processes or functions according to the embodiments of the present invention will be generated in whole or in part. The computer needs to be equipped with a quantum device. The computer instructions may be stored in or transmitted from one computer-readab...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com