Webcam weak password detecting method and system
A network camera and weak password technology, which is applied in the field of network camera weak password detection methods and systems, can solve problems such as low efficiency, poor detection effect, poor intelligence, etc., and achieves high intelligence, improved detection efficiency, and reliable detection. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
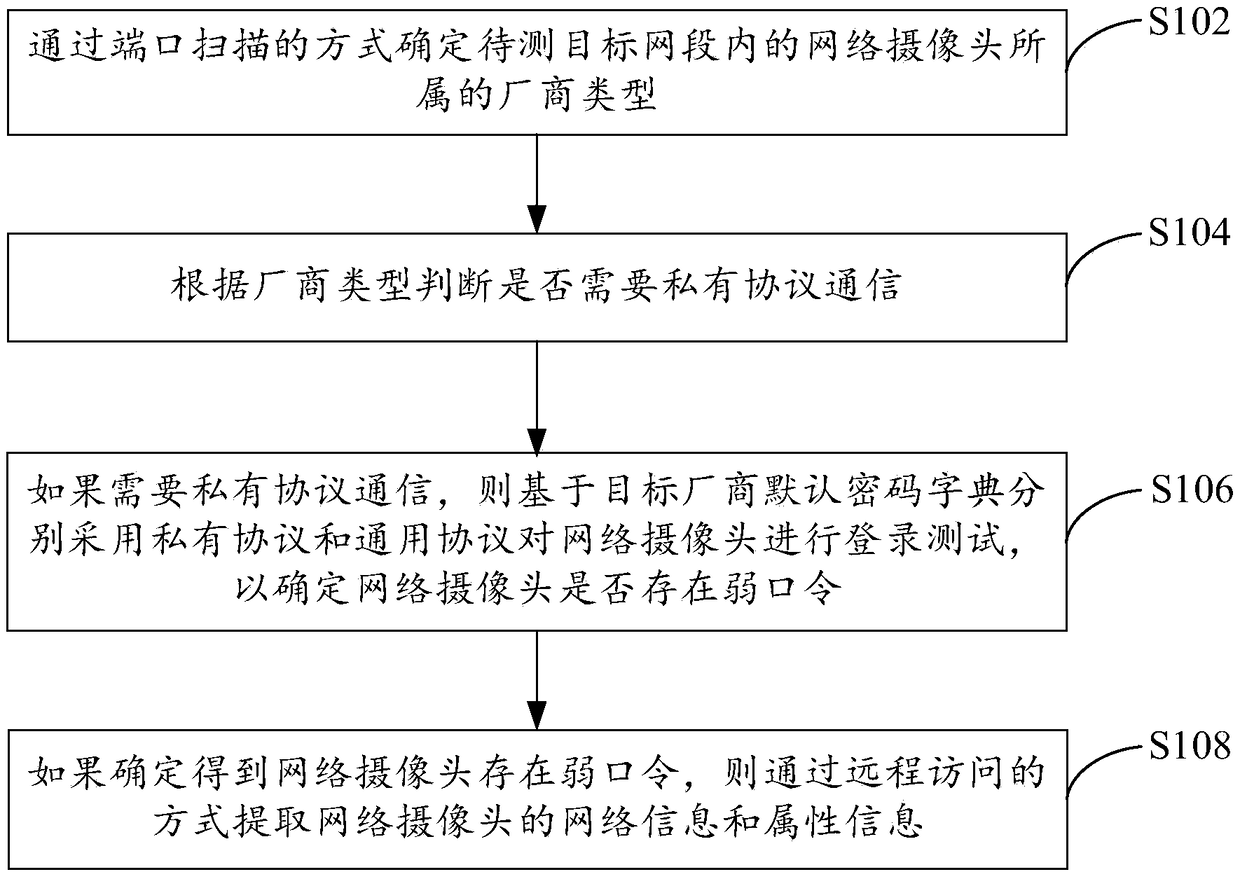
[0054] A method for detecting weak passwords of network cameras, refer to figure 1 , the method includes:
[0055] S102. Determine the manufacturer type of the network camera in the target network segment to be tested by means of port scanning;
[0056] Generally, most network cameras are installed with the manufacturer's own private protocol when leaving the factory, especially the equipment of Hikvision and Dahua. If the private protocol stack is not packaged, it cannot communicate with the service interface on the device. Therefore, the method of the present invention solves the problem of weak password detection of the network camera under the environment of multi-vendor coexistence under the complex network by being compatible with the private communication protocol of the manufacturer.
[0057] When performing detection, first determine the manufacturer type of the network camera in the target network to be tested by means of port scanning. The specific process will be...
Embodiment 2
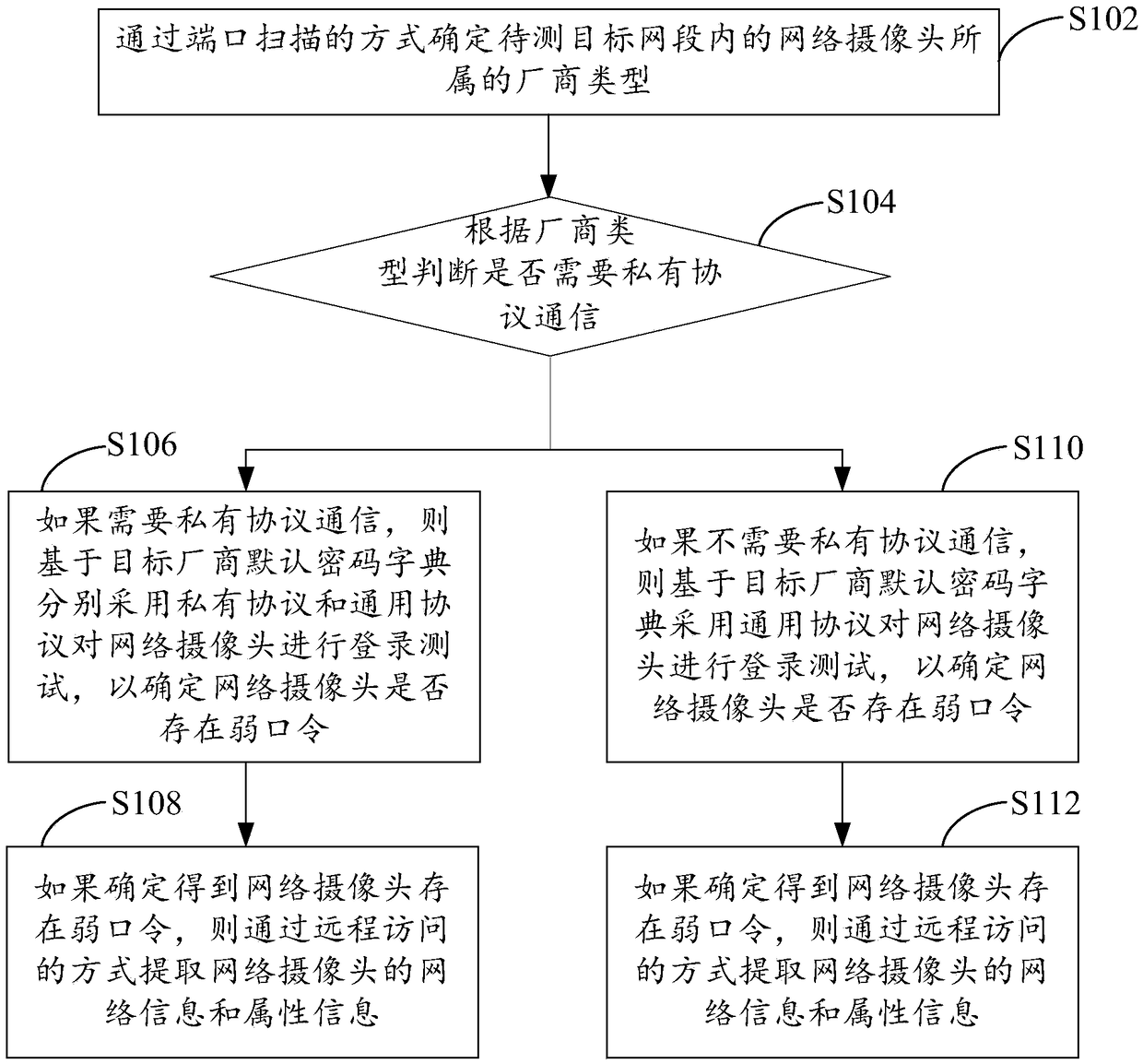
[0099] A network camera weak password detection system, refer to Figure 4 , the system consists of:
[0100] Determining module 11, is used for determining the vendor type that the network camera in the target network segment to be tested belongs to by the mode of port scanning;
[0101] Judging module 12, used to judge whether private protocol communication is needed according to the manufacturer type;
[0102] The first login test module 13, if private protocol communication is required, then based on the default password dictionary of the target manufacturer, respectively adopts a private protocol and a general protocol to carry out a login test to the network camera to determine whether there is a weak password in the network camera, wherein the default password dictionary of the target manufacturer Contains the factory default password corresponding to the manufacturer type, and the preset weak password;
[0103] The first extraction module 14, if it is determined that...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com