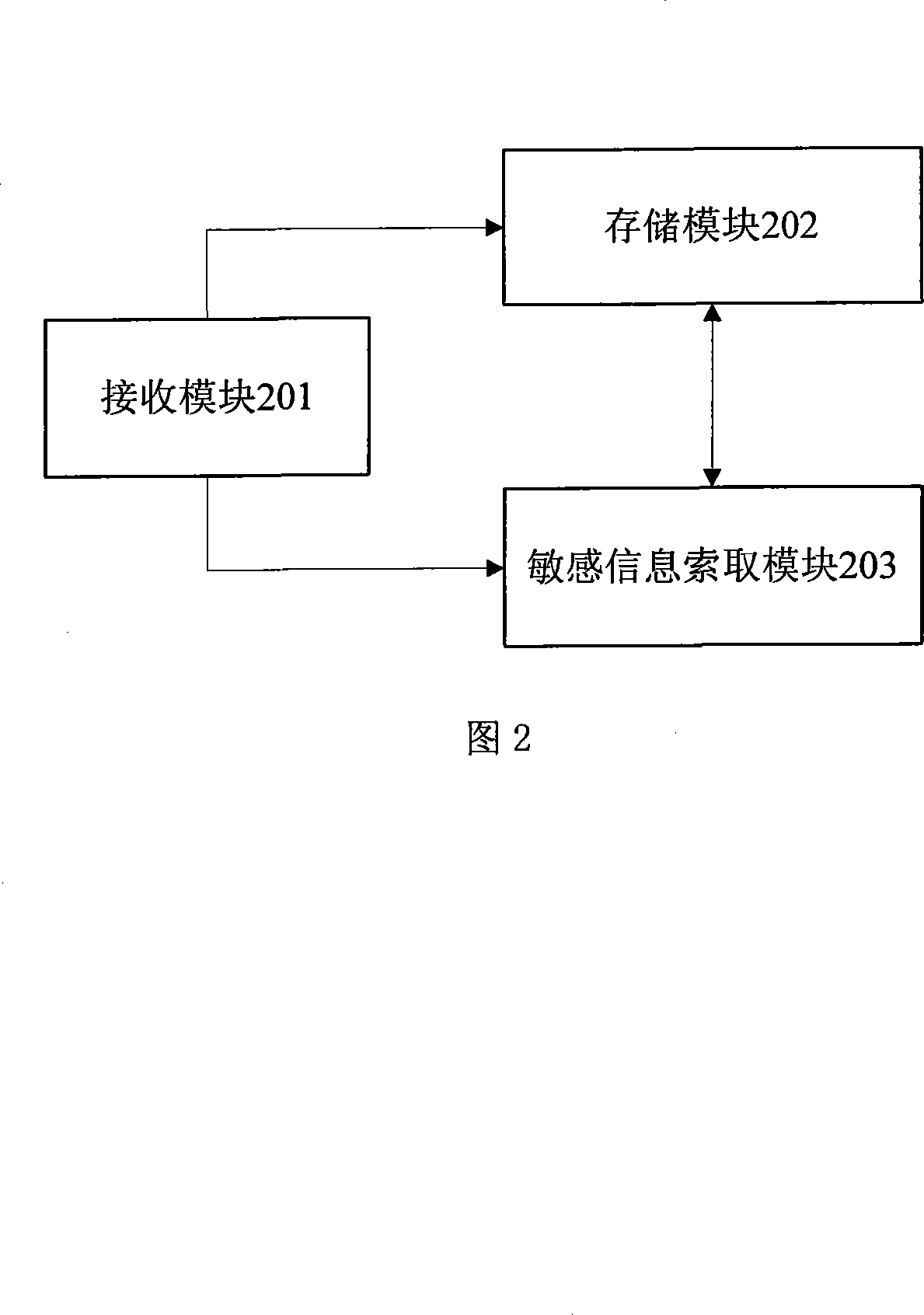
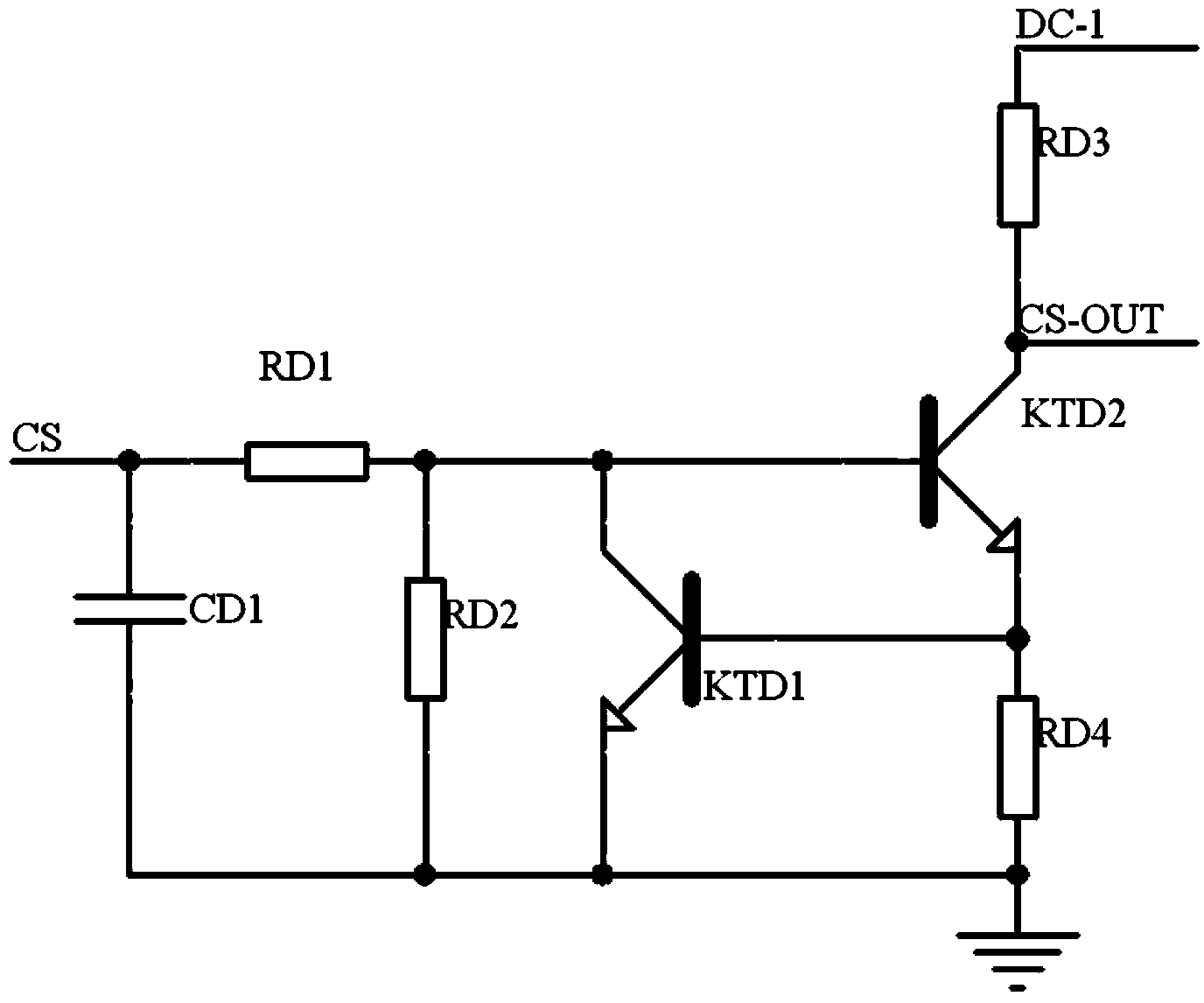
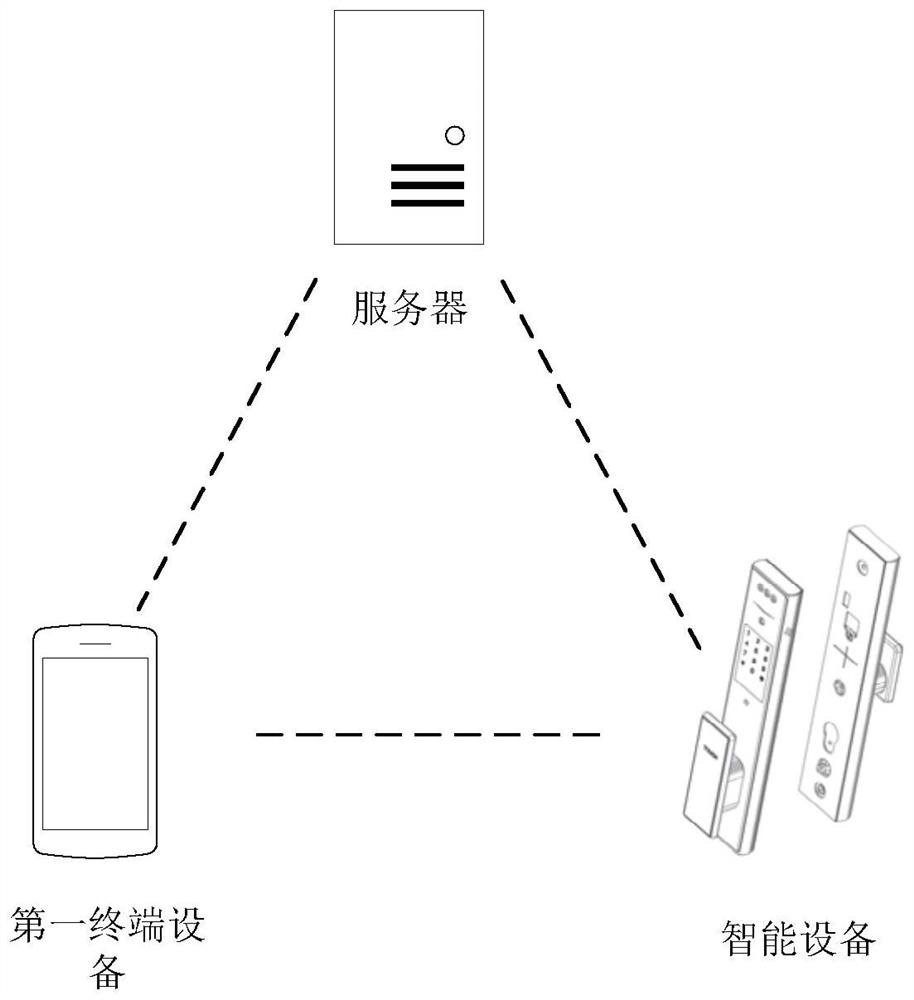
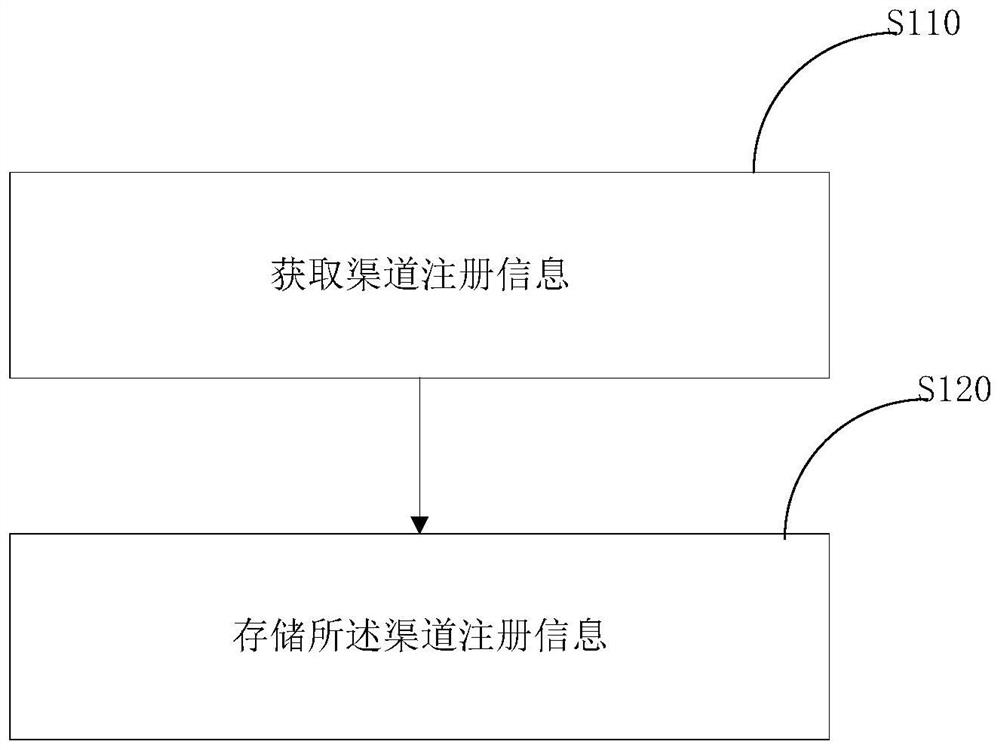
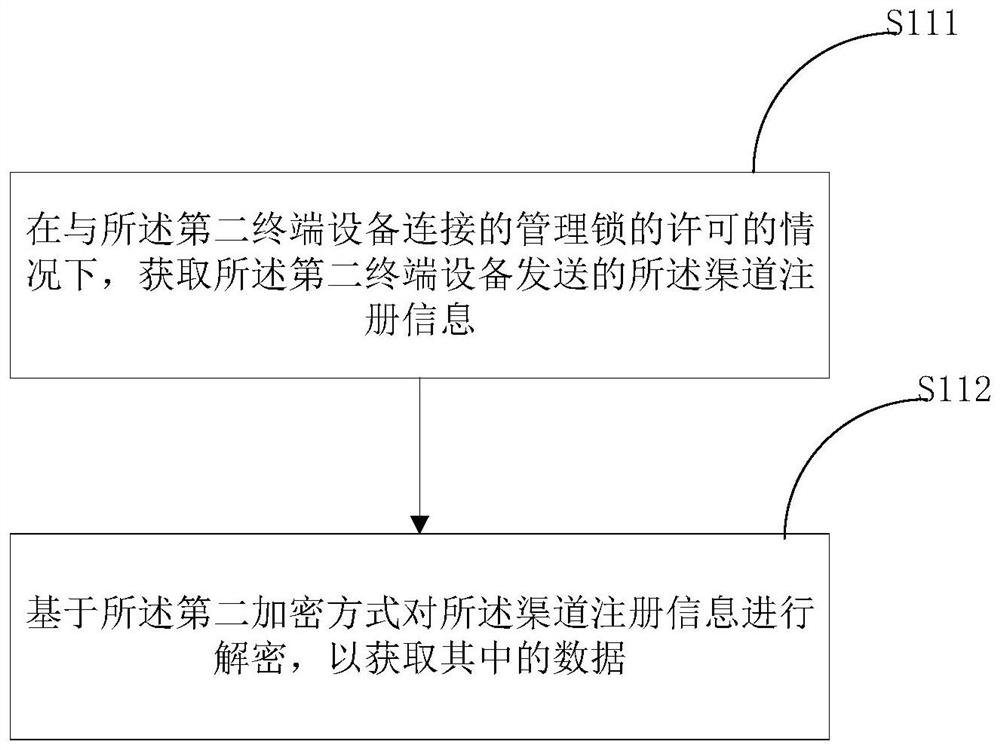
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
72results about How to "Protection of legitimate interests" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
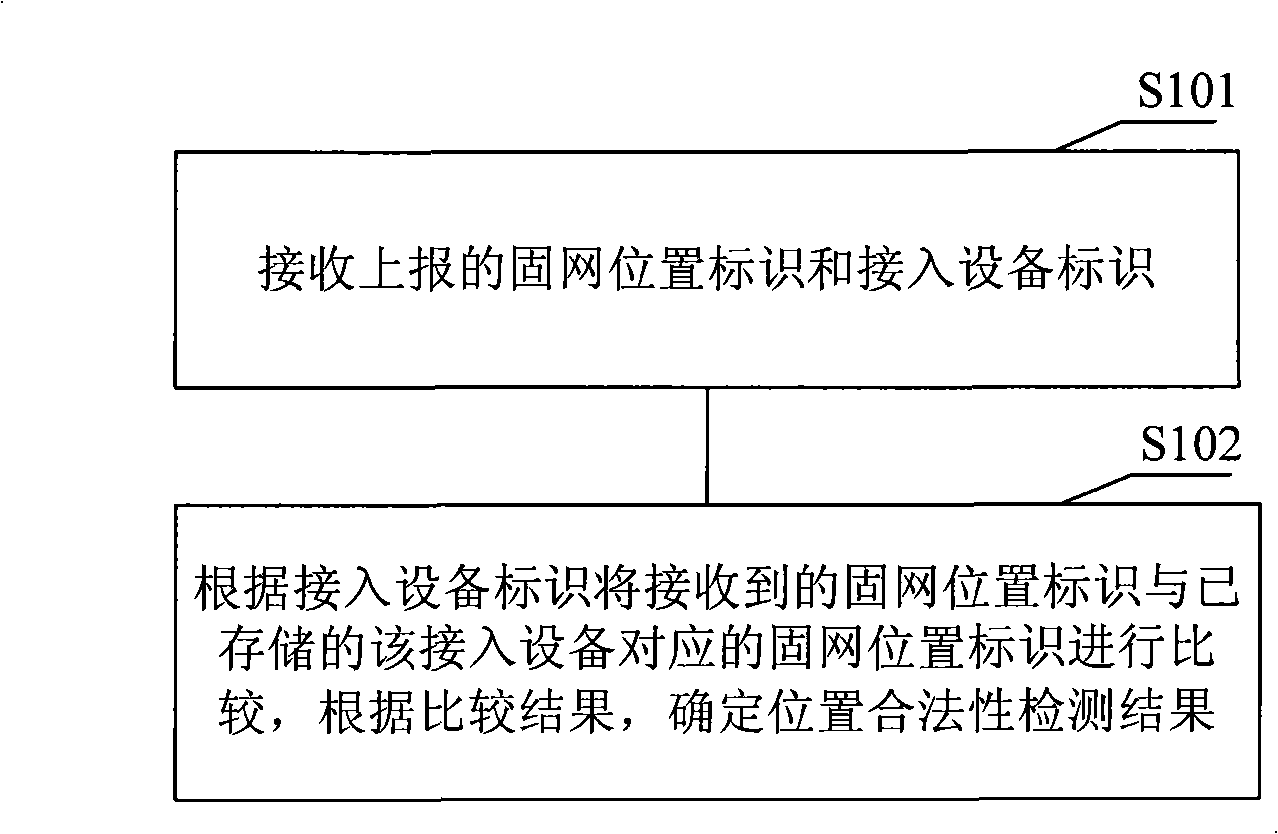
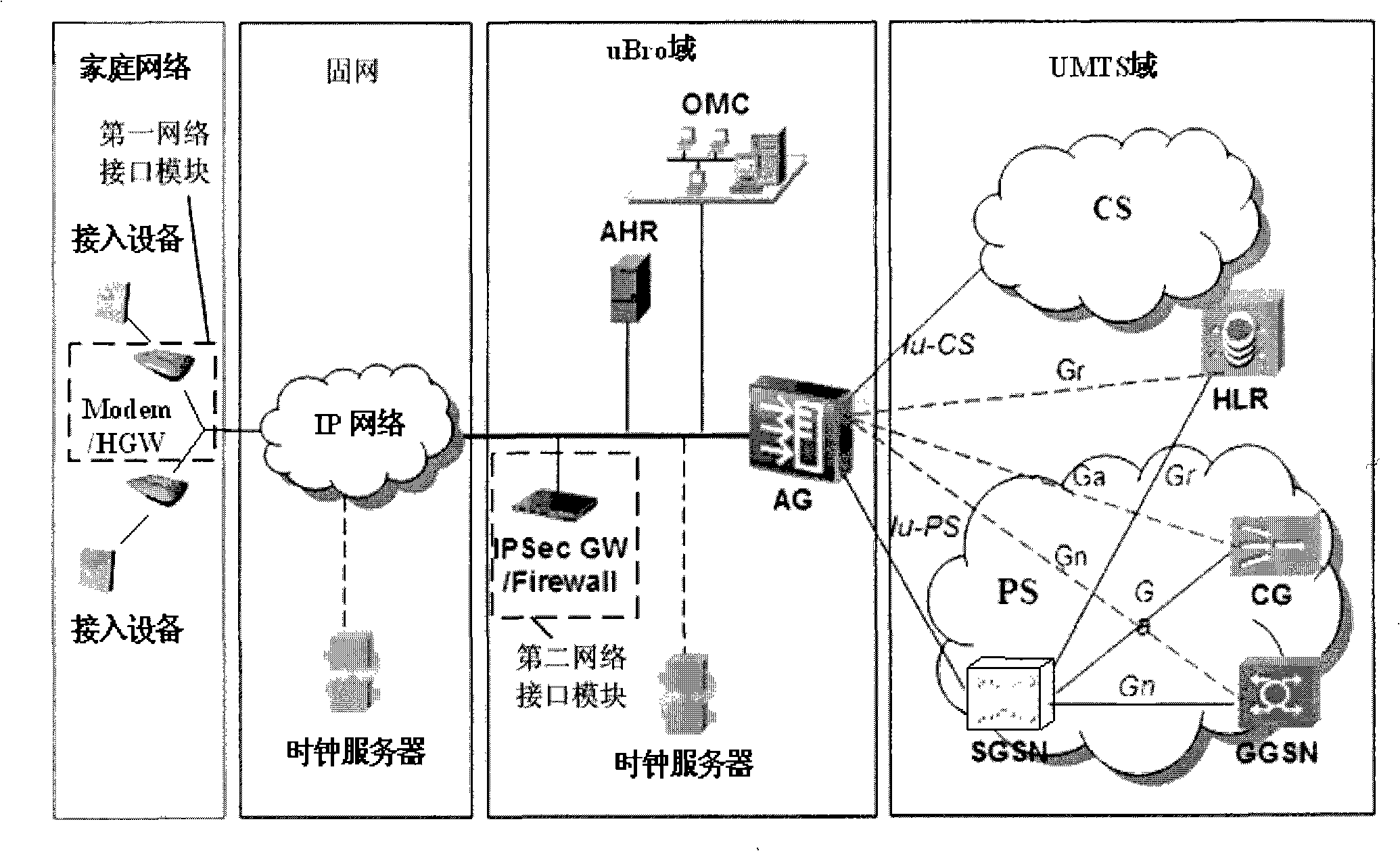
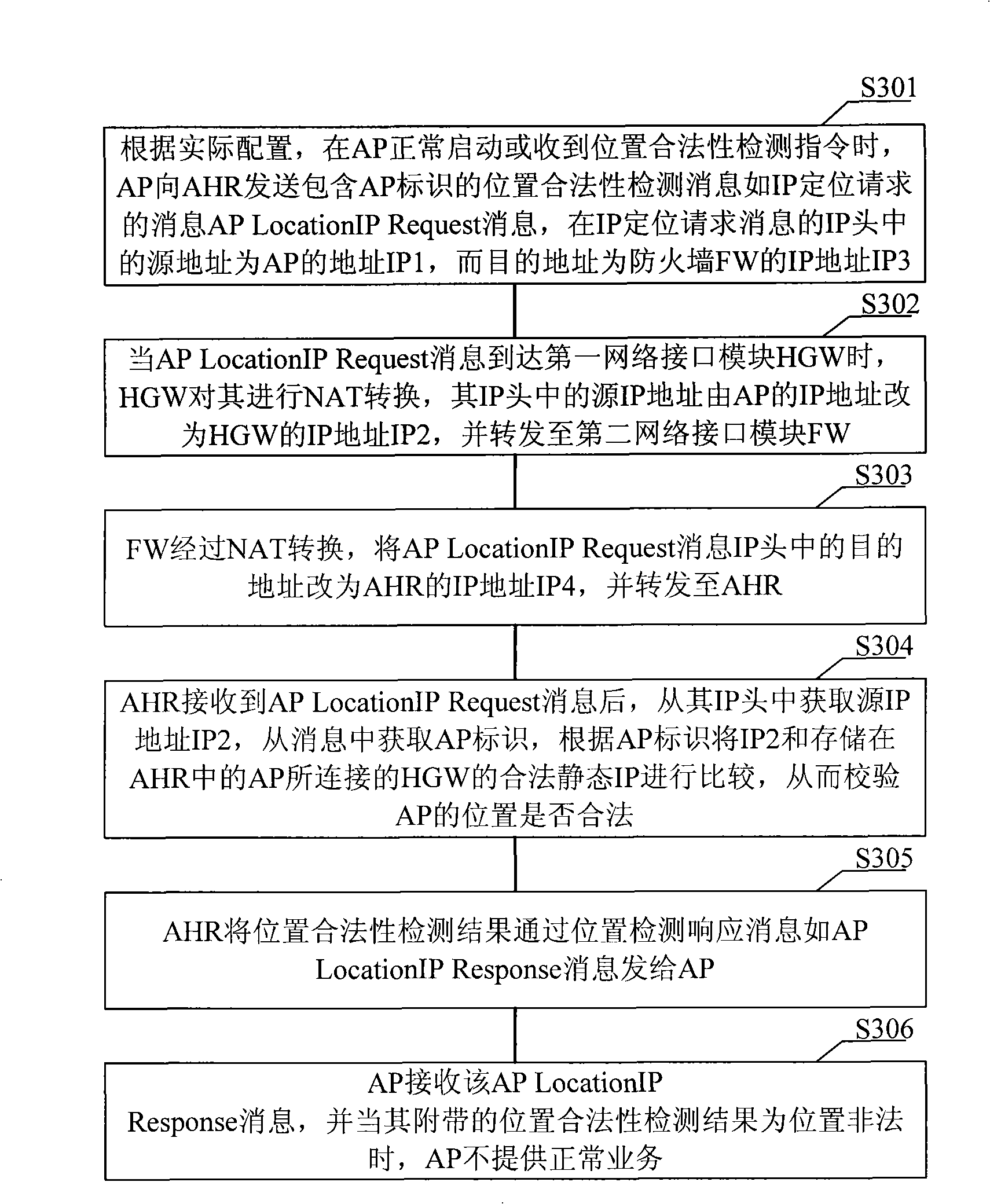
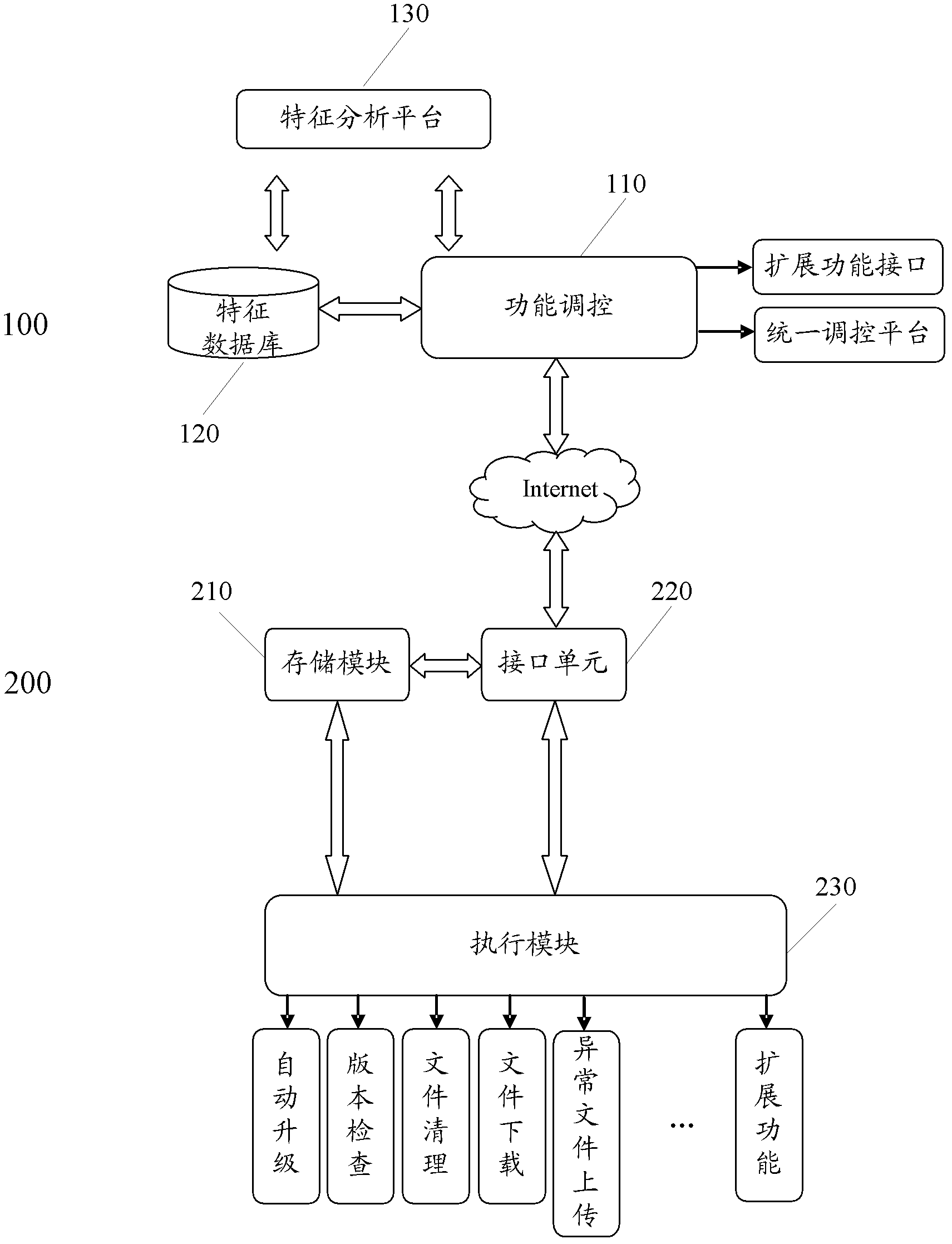
Method for position validity detection, communication system, access equipment and top management network element
ActiveCN101345673AProtection of legitimate interestsEasy to detectData switching by path configurationNetwork elementGeolocation
An embodiment of the invention discloses a method of detecting position legality and a system, comprising: receiving the reported fixed network position identification and access device identification, comparing the received fixed network position identification with that corresponding to the stored access device, or after converting the received network position identification into geographic position information, comparing the geographic position information obtained through conversion with that corresponding to the stored access device according to the access device, when any comparing result is inconsistent, determining the detecting result of position legality as position legality of the access device. According to the method of detecting position legality and the device and the system provided by the embodiment of the invention, position detection and legality judgment on the access device are realized, causing the operator to manage usage on the access device such as an access point AP, ensuring legal interest of the operator.
Owner:HUAWEI TECH CO LTD
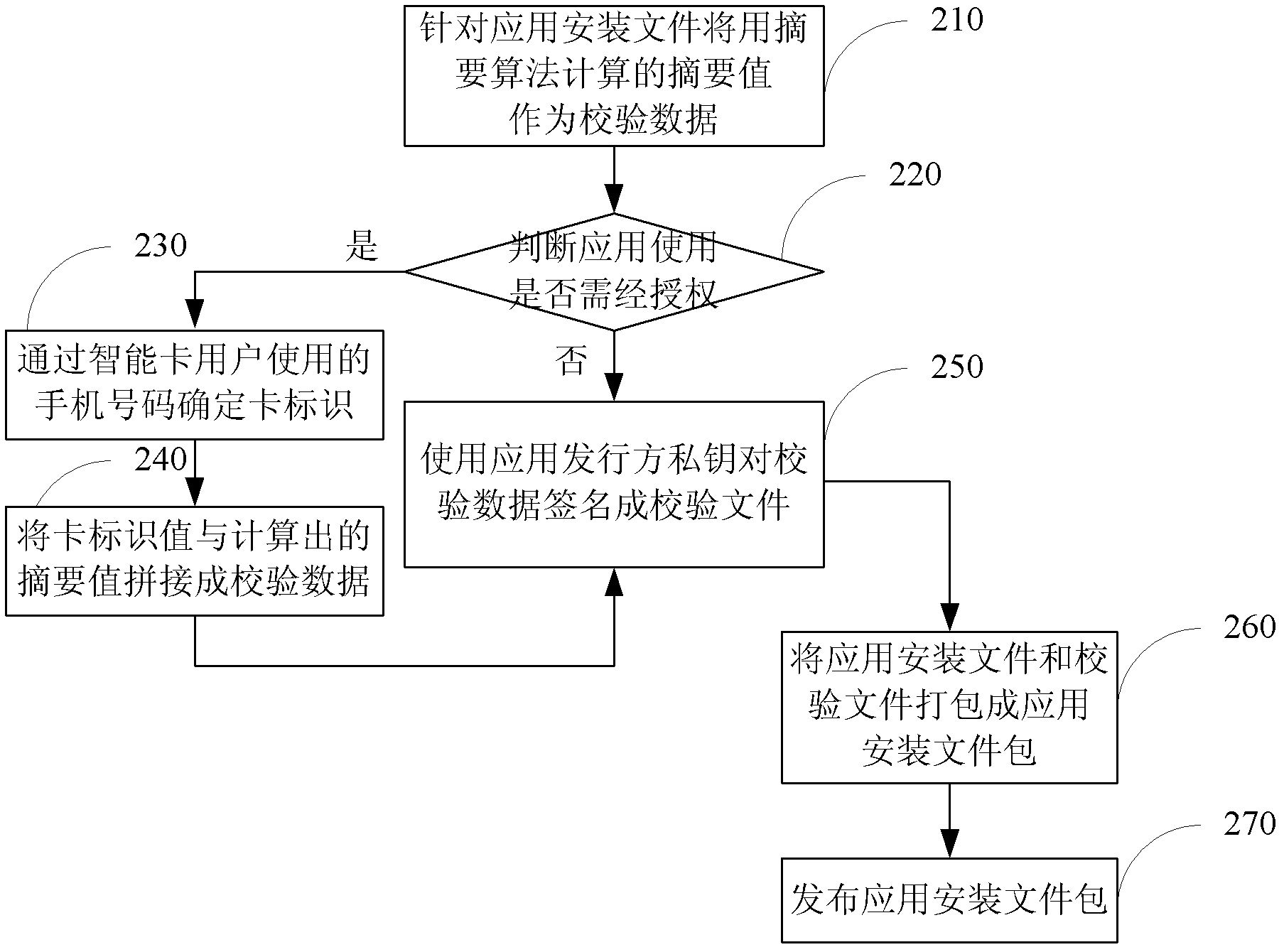
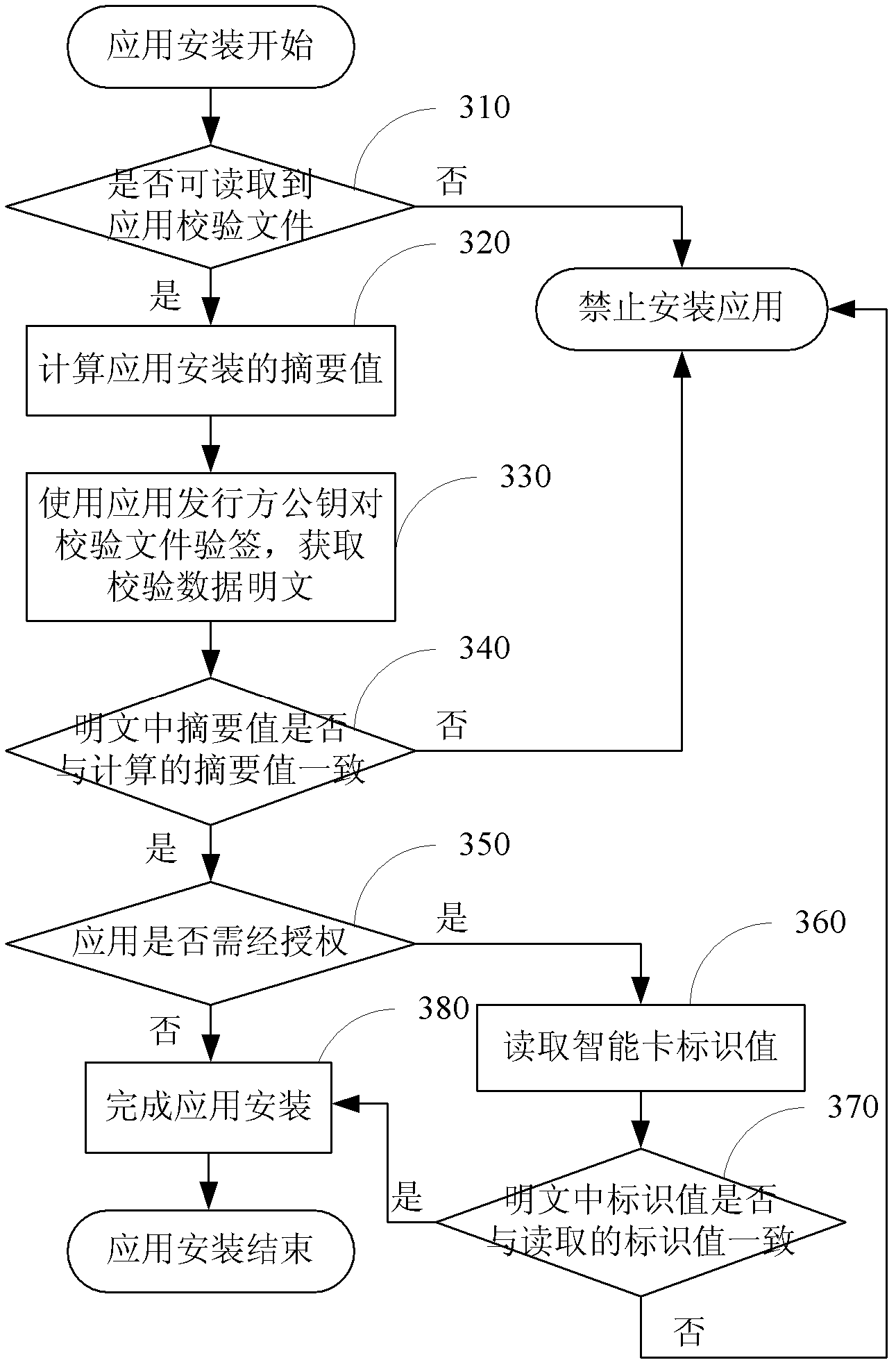
Method and system for realizing smart card application and deployment
InactiveCN102663292AVerify integrityProtection of legitimate interestsUser identity/authority verificationComputer security arrangementsPlaintextSmart card
The invention discloses a method and a system for realizing smart card application and deployment, wherein the method comprises that application installation documents and checking documents are packed as an application installation document wrap to be published when application is published. When the application is installed, if the application installation document wrap is checked out without a checking document wrap, or the calculated abstract value is not consistent with the abstract value of the checking data plaintext decrypted from the checking documents, or users which need to be authorized are unauthorized, the application installation must be prohibited, otherwise, the installation is allowed. The method and the system have the advantages of guaranteeing the legitimate interests of application suppliers effectively, prohibiting installation of all the incomplete or tampered application by means of checking the completeness of the application, and supporting the authorized application installation, so that the legitimate interests of the installation suppliers and the authorized users are guaranteed in the meanwhile.
Owner:DATANG MICROELECTRONICS TECH CO LTD
Android simulator detecting method and device
InactiveCN107102886AAchieve separationProtection of legitimate interestsSoftware simulation/interpretation/emulationSimulationApplication software
Owner:BEIJING BANGCLE TECH CO LTD
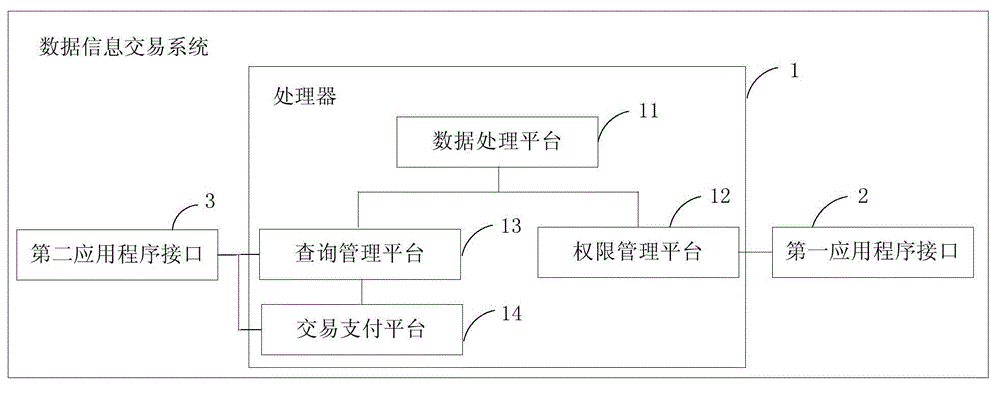
Data information transaction method and system
ActiveCN105302845AGuaranteed validitySearch results are accurateDatabase queryingDigital data protectionData informationFinancial transaction
The invention provides a data information transaction method and system. The method comprises the following steps: a server receives a query request, wherein the query request is sent from a data requester terminal and carries a query condition and the user characteristic identifier of a digital human which needs to meet the query condition, and the user characteristic identifier is a characteristic category identifier obtained through the classification of each piece of user characteristic information contained in the digital human; determining the digital human user characteristic information corresponding to the query condition and the user characteristic identifier to obtain a query result, and sending the query result to the data requester terminal; and receiving a purchase request sent from the data requester terminal, and finishing a transaction according to the purchase request. In the digital human, according to the query condition and the user characteristic identifier, the user characteristic information is queried, so that the query result is more accurate, and query efficiency is improved. Meanwhile, the user characteristic information is obtained in a transaction purchase way so as to be favorable for guaranteeing the legitimate interests and the information security of a practical terminal user.
Owner:HUAWEI TECH CO LTD
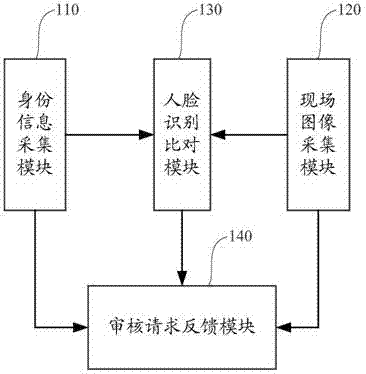
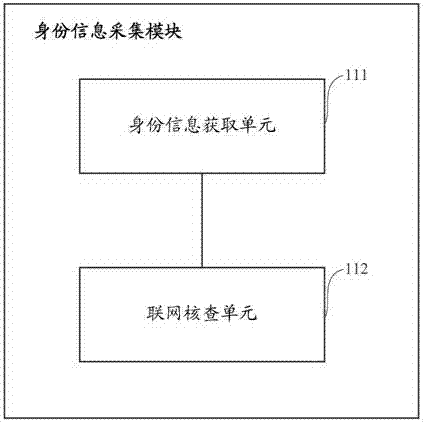
Self-service card distributing device and identity authentication system there and identity authentication method therefor
InactiveCN105447367AImprove rigorImprove securityFinanceDigital data authenticationAuthentication systemSelf-service
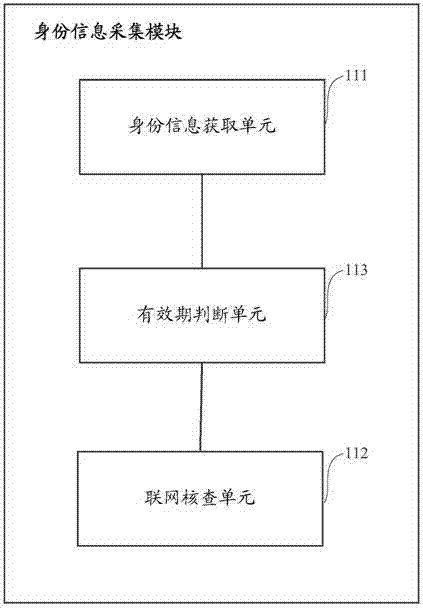
The present invention dscloses a self-service card distributing device, and an identity authentication system and an identity authentication method therefor. The identity authentication system comprises: an identity information acquisition module, for acquiring effective identity information of a customer; a live image acquisition module, for acquiring facial image information of the customer; a face recognition and comparison module, for comparing image information of the effective identity information of the customer with the acquired facial image information, and obtaining a face recognition and comparison result; and an auditing request feedback module, for requiring to audit the effective identity information of the customer, obtaining the facial image information and the face recognition and comparing result, and obtaining an examination result. According to the self-service card distributing device and the identity authentication system and identity authentication method therefor disclosed by the present invention, the interference and influence of artificial examination are greatly reduced by automatically obtaining the effective identity information of the customer and comparing facial image of the customer, preciseness and security of opening accounts by the customer are significantly enhanced, thereby protecting legal benefits of the customer and banks.
Owner:CHINA CONSTRUCTION BANK
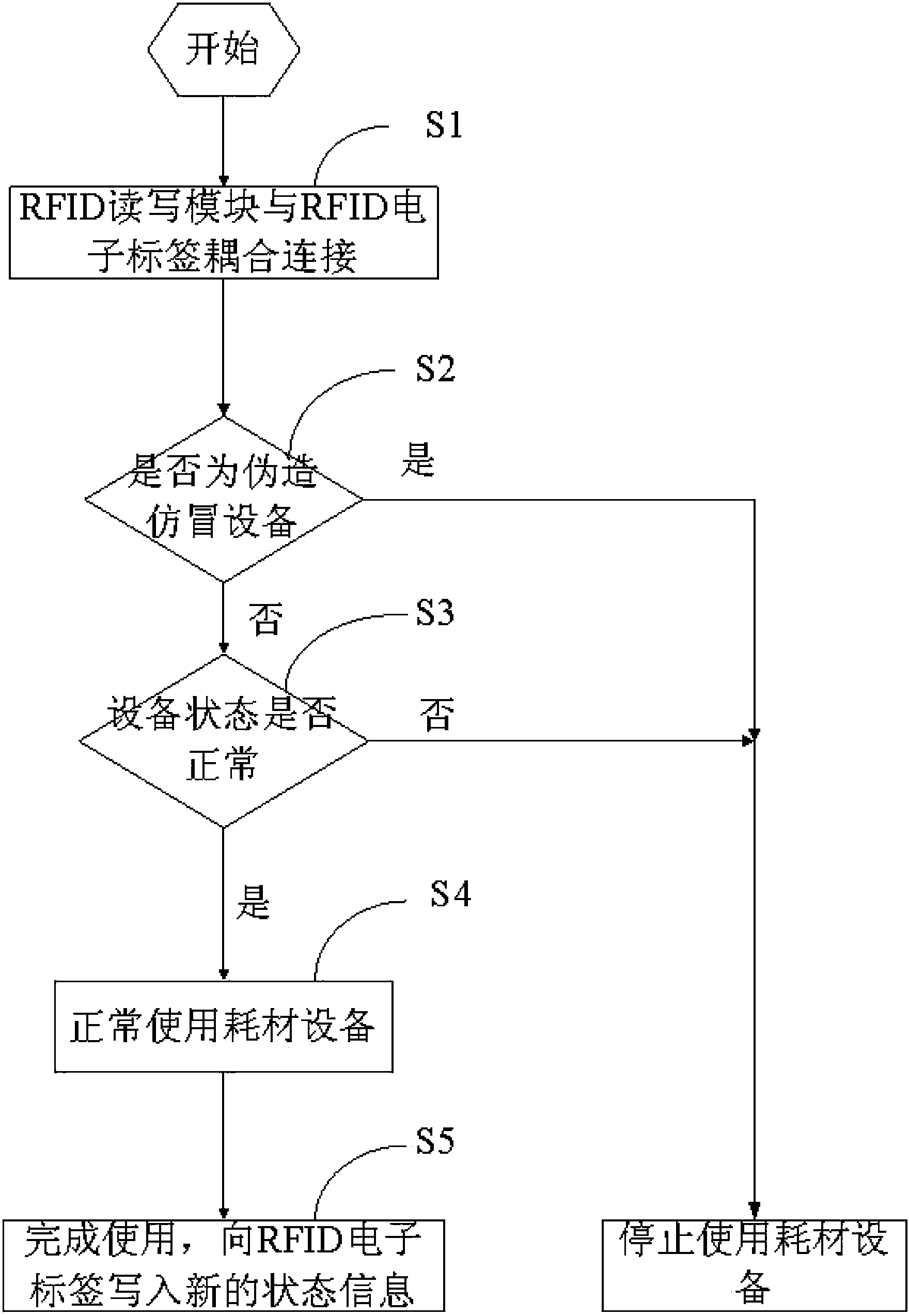
Anti-fake printing method and system
InactiveCN103513943AProtection of legitimate interestsIncrease viscosityPattern printingTypewritersElectricityComputer engineering
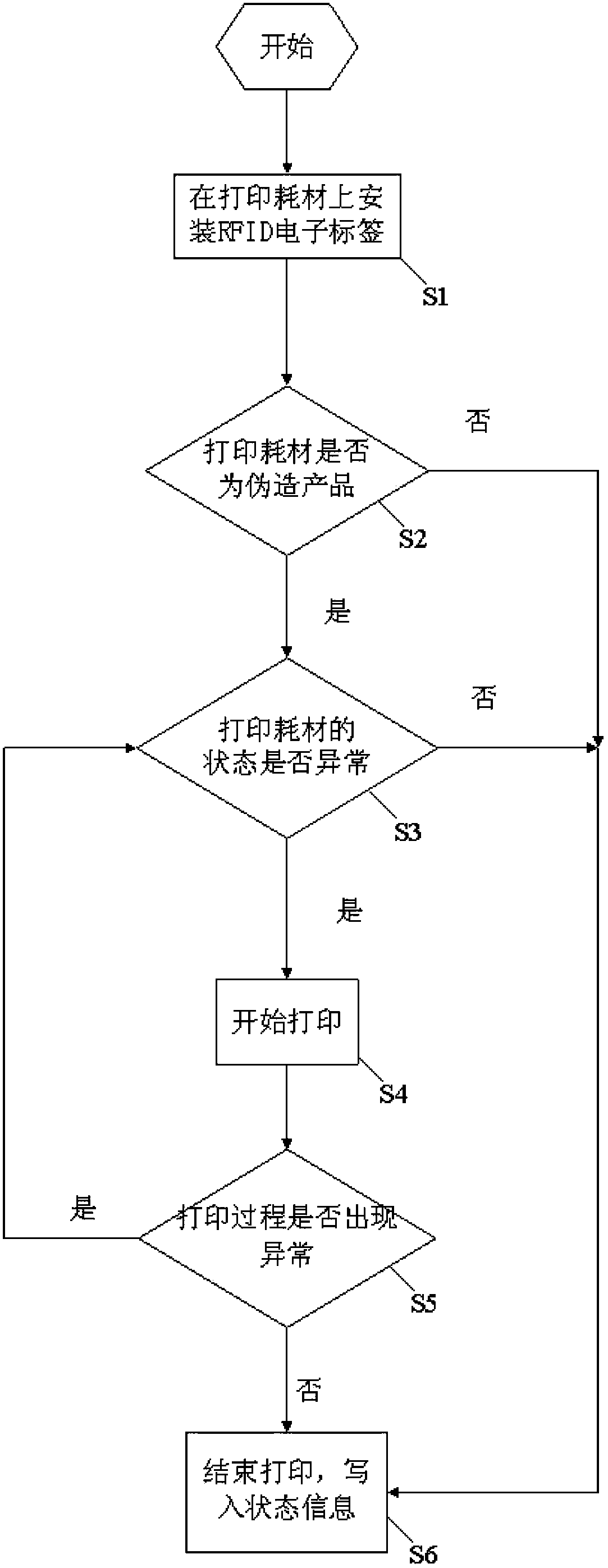
The invention relates to an anti-fake printing method and system. The anti-fake printing method comprises the following steps that printing supplies with a preset RFID electronic tag are installed on printing equipment; the printing equipment reads encrypted information on the RFID electronic tag when powered on and verifies whether the printing supplies are legal; if yes, state information of the printing supplies on the RFID electronic tag is read; printing work is started; when the printing process is abnormal or printing work is finished, the current state information of the printing supplies is written in the RFID electronic tag. By means of the anti-fake printing method and system, the authenticity of the printing supplies can be judged, and legitimate interests of producers and users are guaranteed.
Owner:POSTEK ELECTRONICS
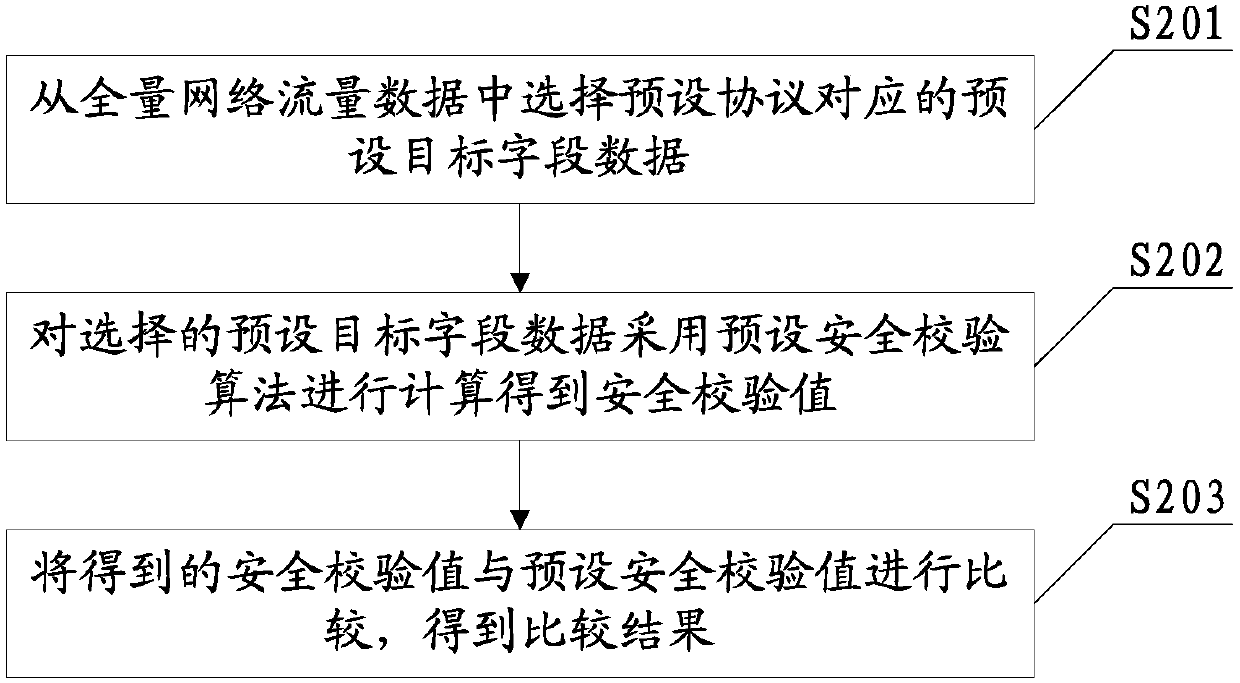
Content delivery network security detection method and system
InactiveCN109561051AImplement security detectionProtection of legitimate interestsTransmissionSecurity analysisContent delivery network
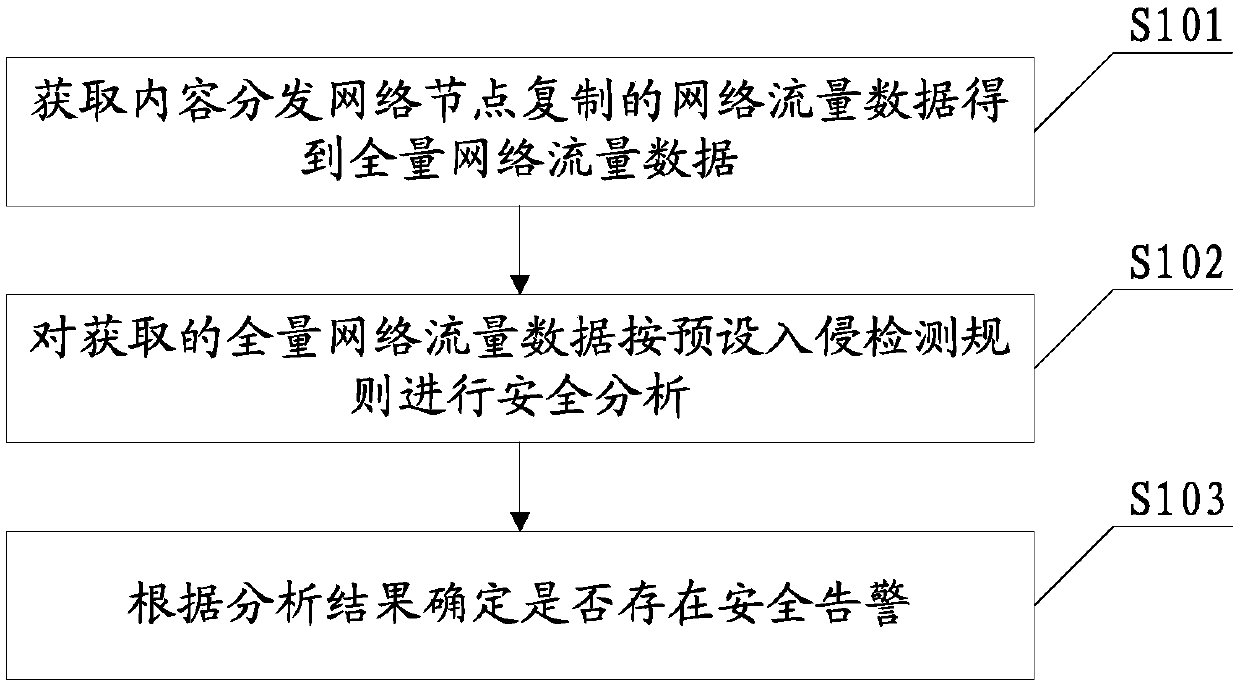
The embodiment of the invention provides a content delivery network security detection method and system. A content delivery network node replicates all the traffic, the network traffic data replicated by the content delivery network node can further be acquired, and full content network traffic data are obtained; then, the acquired network traffic data are subjected to security analysis accordingto a preset intrusion detection rule; and according to an analysis result, whether security warning exists is determined, and security detection on the content delivery network is realized. The traffic forwarded by the content delivery network node is analyzed, the analysis result is accurate and reliable, potential security threats can be timely and effectively detected, the legitimate interestsof a user and a service provider are protected, the security is enhanced, and the security risks are reduced.
Owner:ZTE CORP
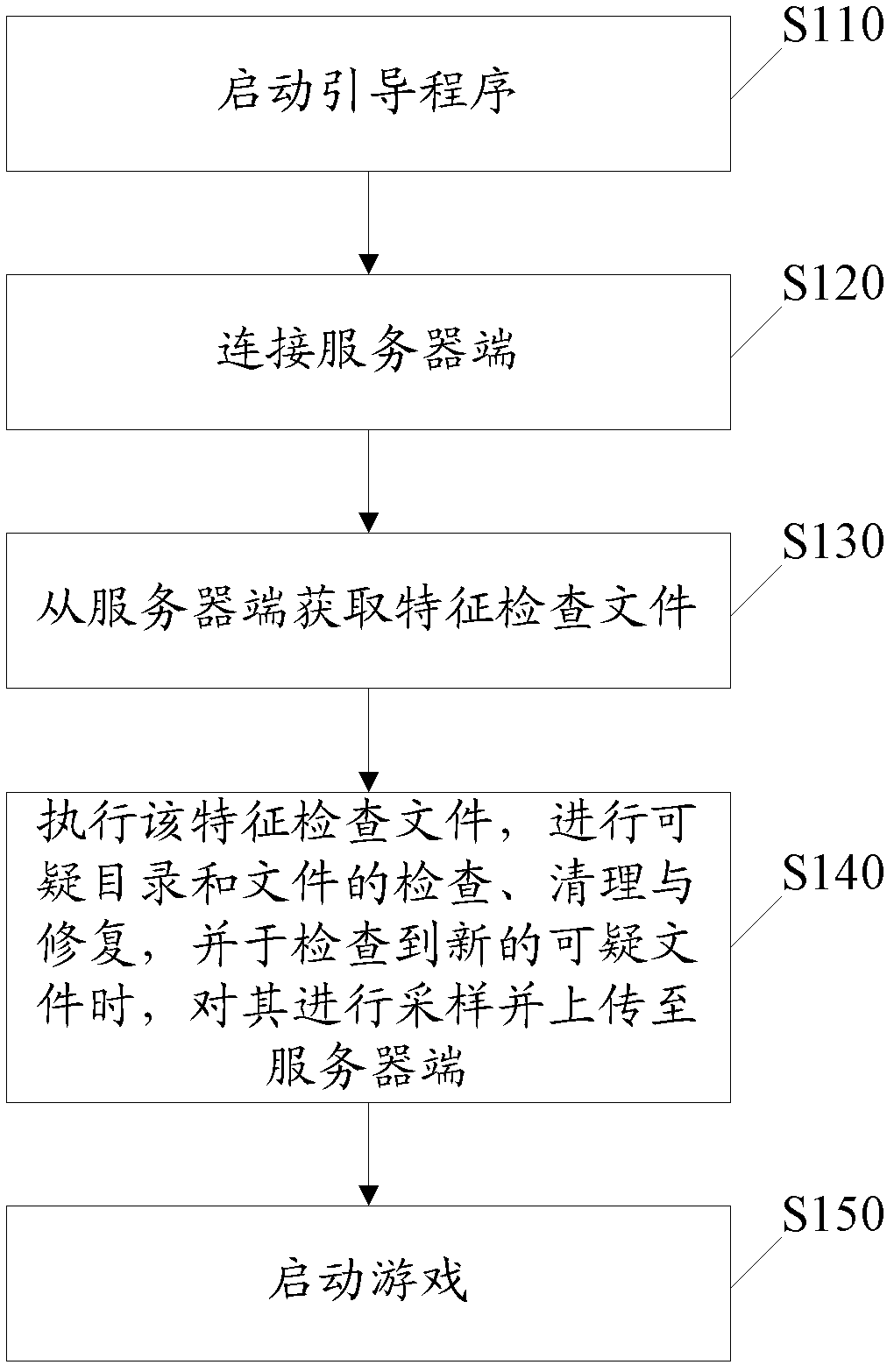
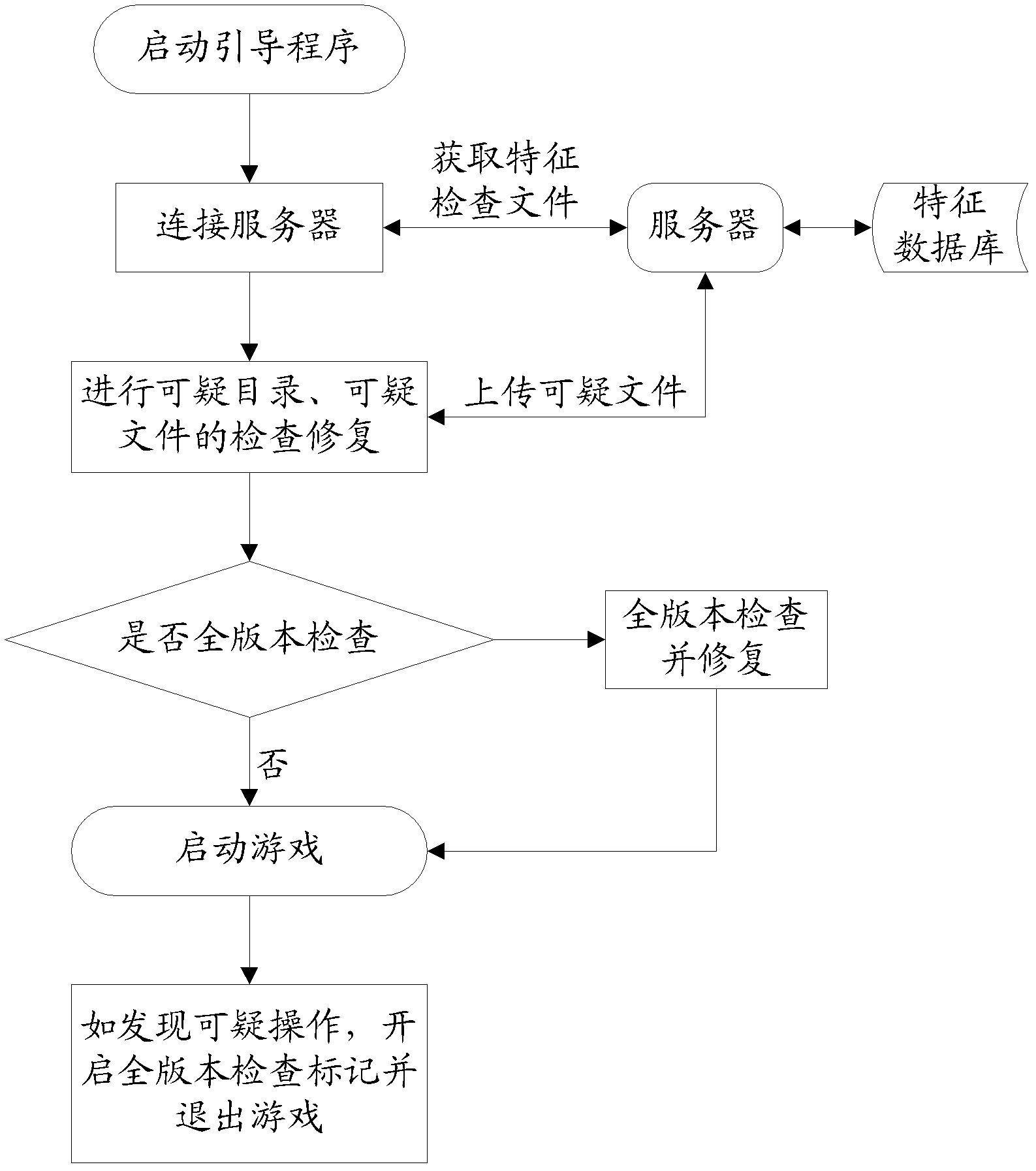
Method, device and system for preventing game cheating
InactiveCN103020415AProtection of legitimate interestsPlatform integrity maintainanceSpecial data processing applicationsOperating system
The invention discloses a method, a device and a system for preventing game cheating. The method comprises the following steps of: acquiring feature checking files from a server end by a client end when a game is started or updated; executing the feature checking files, checking, clearing and repairing suspicious directories and files, and when new suspicious files are checked, sampling the suspicious files and uploading to the server end; and starting the game. According to the invention, the specific game cheating actions are logically concentrated on layers of the files to be analyzed from a client perspective; and the game cheating actions are uniformly abstracted as modification, adding and deleting operations of client end files, so that the game cheating shielding function is realized, and the files and directories related to the game cheating are repaired so as to effectively reduce the hazard of cheating on the games.
Owner:SHENGQU INFORMATION TECH SHANGHAI
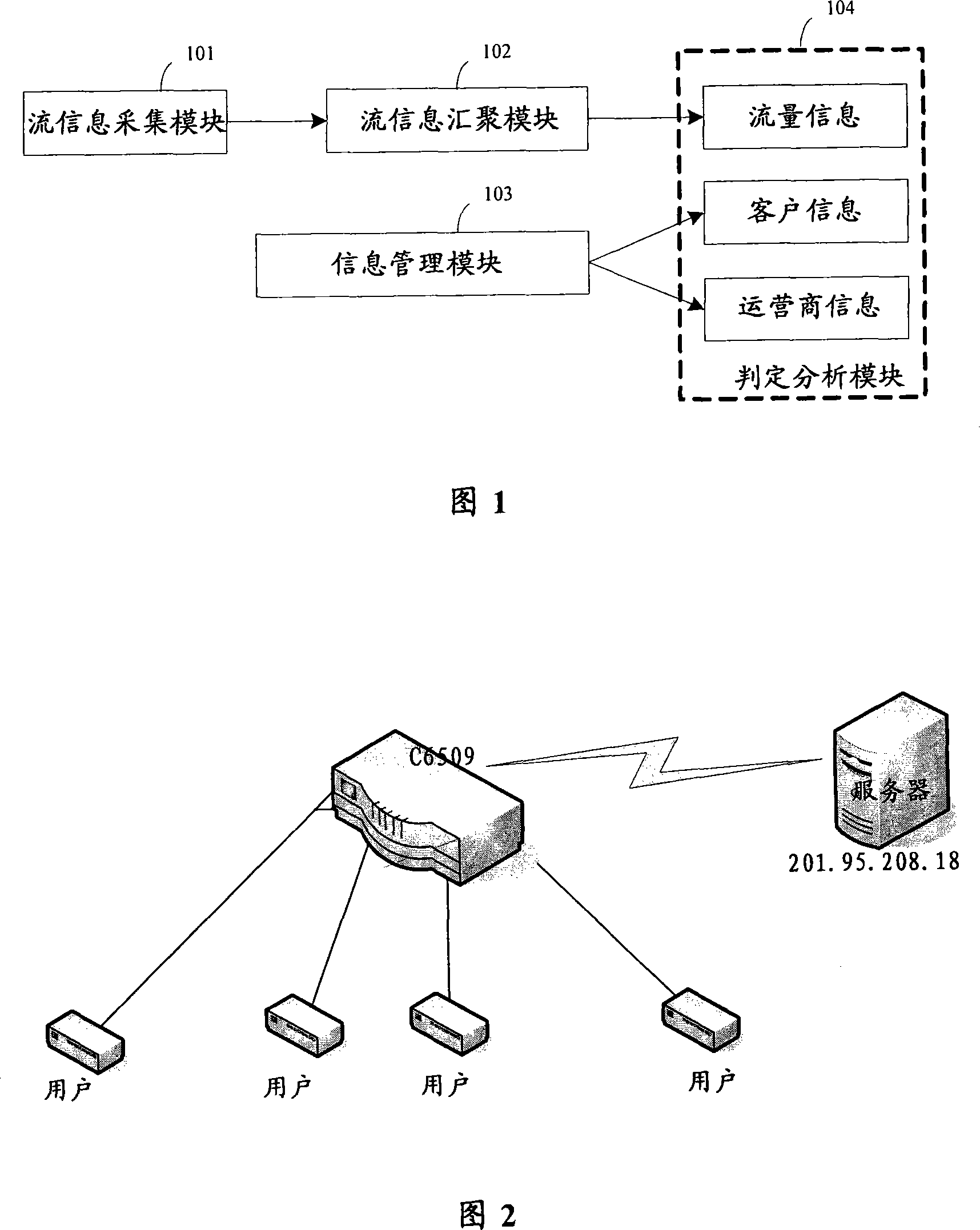
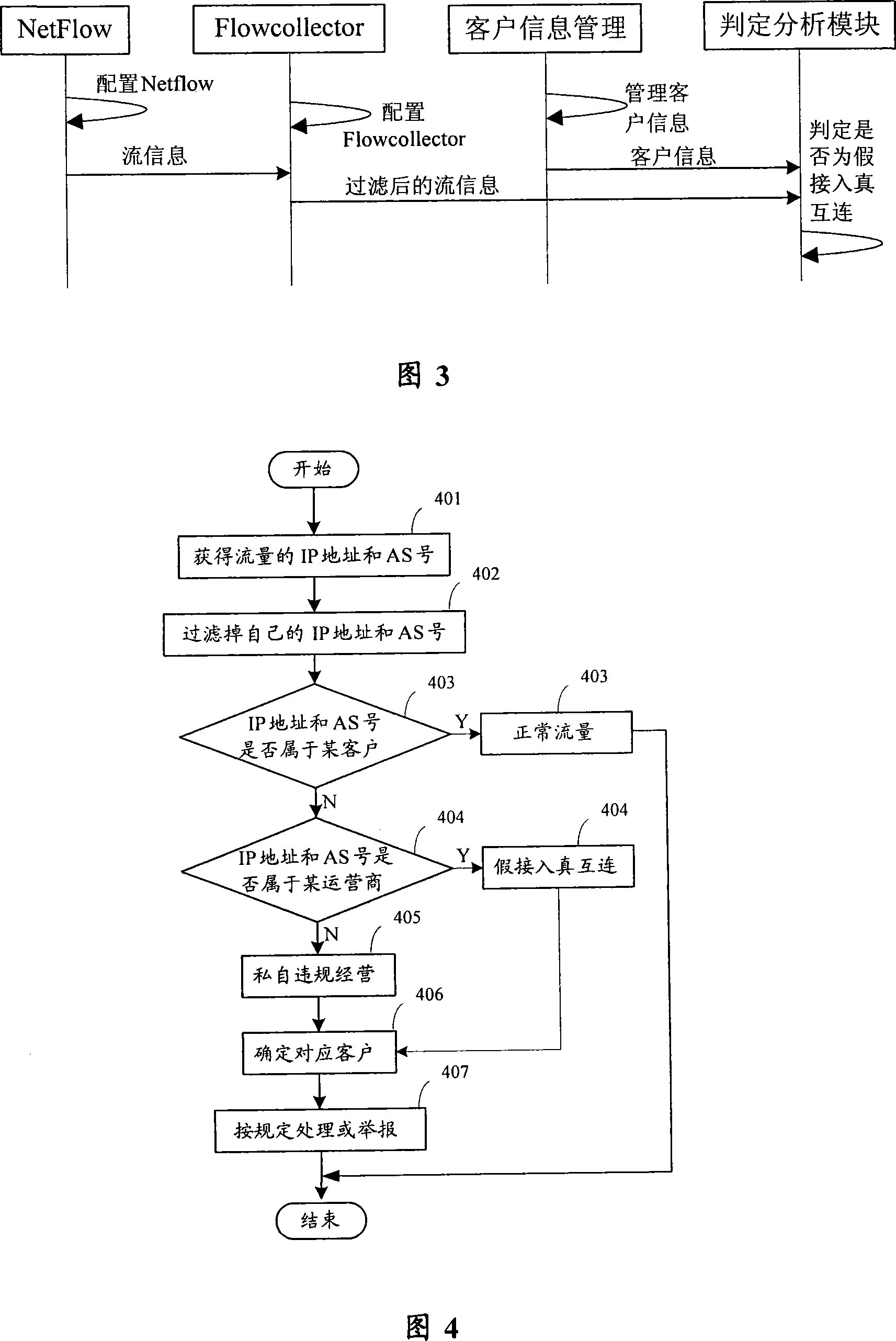
System and method for detecting illegal access
InactiveCN101159636AGuaranteed experienceProtection of legitimate interestsData switching by path configurationTraffic capacityNetwork packet
The invention discloses a system for detecting illegal access and a method thereof. The system comprises a flow information acquisition module for sampling local flow data and sending the acquired data packet to a stream information convergence module; a flow information convergence module for extracting flow data from the data packet acquired from the stream information acquisition module and merging the same flow information; a information management module for storing and maintaining the information of legal user; and a decision analysis module for judging and filtering the information belonging to the user of operator from the flow information converged from the flow information convergence module. The rest information after filtering is compared with the information of legal user in the information management module, if yes, the user is judged as normal flow user, and if not, the user is judged as illegal access user. The invention can automatically find illegal access user.
Owner:CHINA TELECOM CORP LTD
Network gene recognition method based on entity self characteristics in information space
InactiveCN102594807ASolving the Trusted Identity ProblemEnhance the substantive functionTransmissionPattern recognitionInformation space
The invention discloses a network gene recognition method based on entity self characteristics in an information space. In the information space, a consistent identifier based on self characteristics is realized by using the physical or virtual objective attribute information of a cyber entity itself. The identifier is a unique structural data rule processed in the information space based on cyber entity self natural attribute and is used as a network gene identification and recognition method of an entity. With the adoption of the network gene recognition method, unique identification and unique mapping of the entity in a PS (Physical Space) and a CS (Cyber Space) can be realized, i.e. a self real name of the cyber entity in the CS, a real name in the CS and an anonymous name in the CS or the real name in the PS existing in anonymous name in the in the CS can be realized; and meanwhile, the switch and the mapping between the real name and the anonymous name are a principle and a mechanism uniquely corresponding to the cyber entity, so that any cyber entity possesses of a trusted identity.
Owner:JIANGSU DIGITAL DNA TECH CO LTD
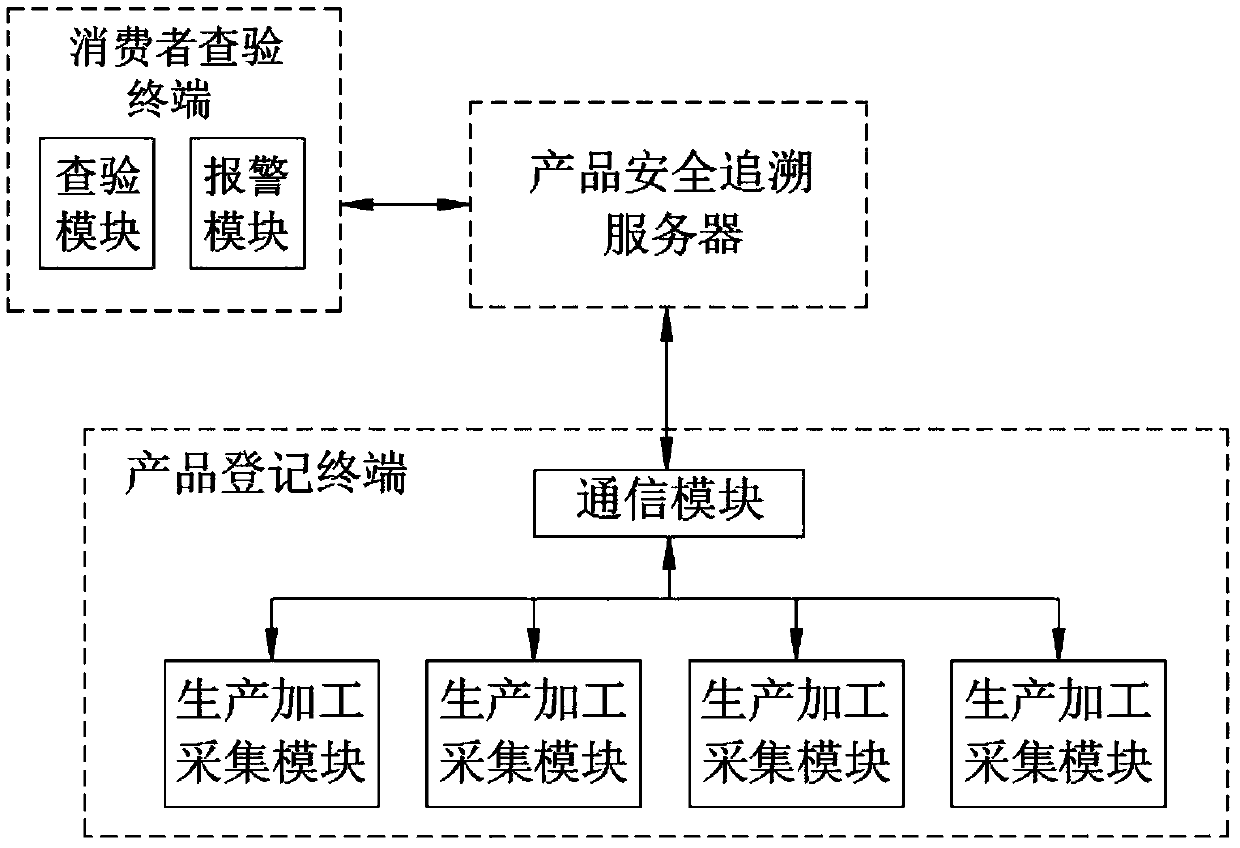
A tamper-proofing product quality safety tracing system and method based on blockchain encryption
PendingCN109685534AProtect interestsEasy to distinguishPayment protocolsCommerceElectricityTamper resistance
The invention discloses a tamper-proofing product quality safety traceability system based on blockchain encryption, comprising a protection system, a product registration terminal and a product safety traceability server which are connected, and the product registration terminal is connected with the product safety traceability server and is used for sending various data of a product to the product safety traceability server; Wherein the product registration terminal comprises a communication module, and a production and processing acquisition module, a logistics distribution acquisition module and a product sales acquisition module which are electrically connected with the communication module, and the communication module is connected with the product safety tracing server. According tothe invention, all related data are recorded in the block chain; In the blockchain auditing system, all the blocks are encrypted and stored in each node, so that anyone cannot tamper product information, and when the quality problem of the product occurs, all the information is traced and can be followed, real and credible, the production and distribution process is monitored more seriously, andthe legitimate interests of consumers are ensured.
Owner:江苏哩咕信息科技有限公司
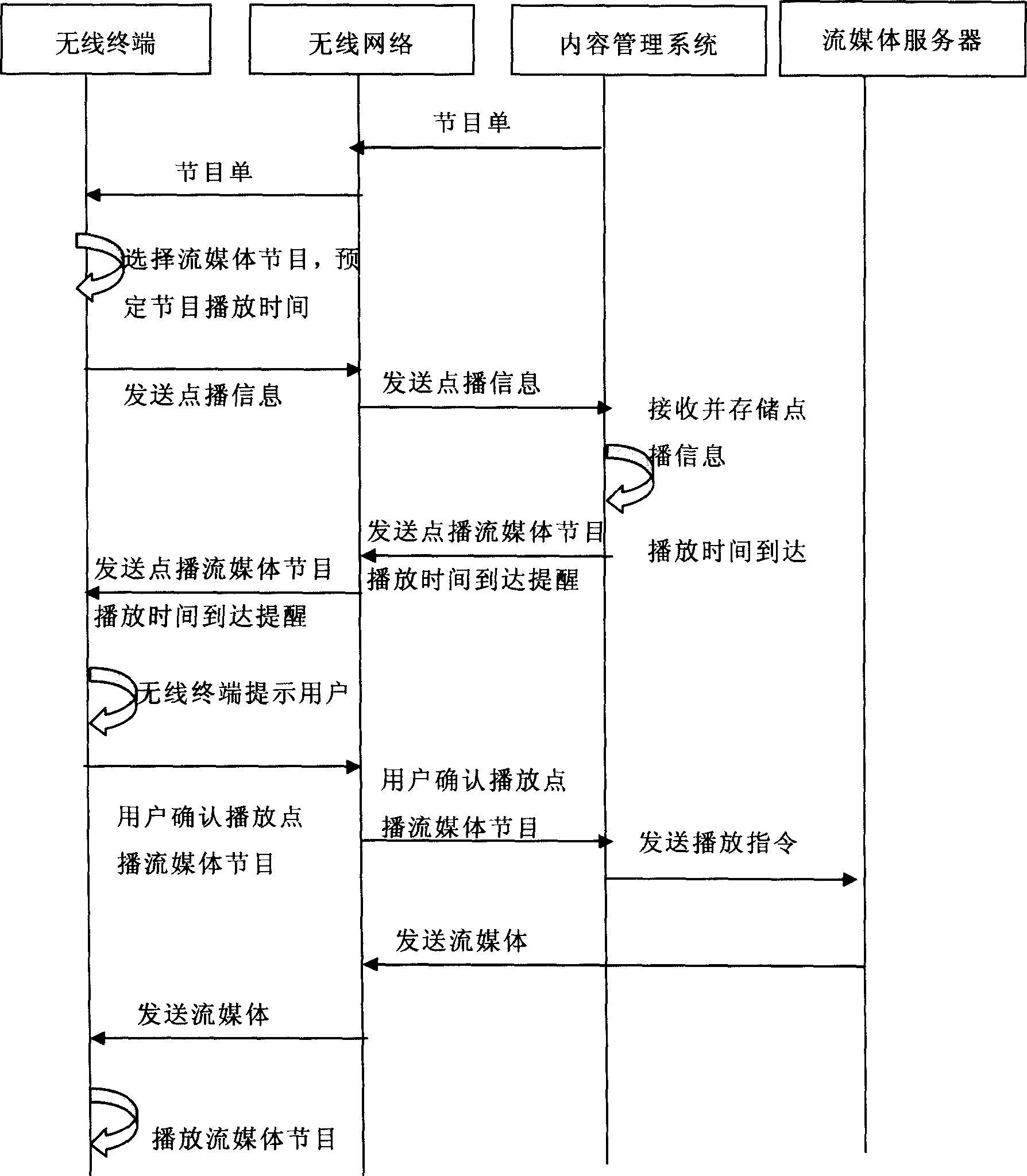
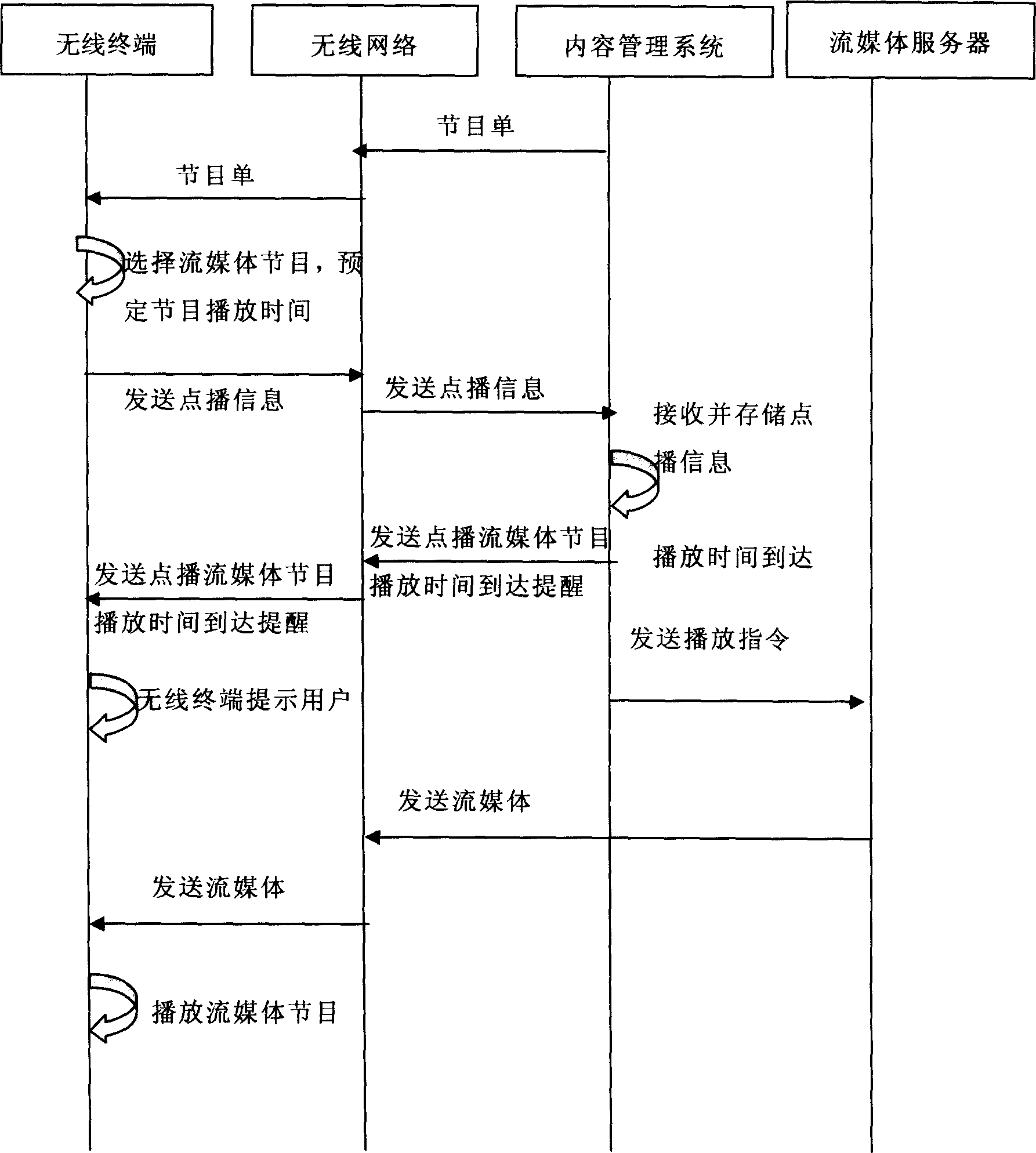
Flow-medium performance ordering method
ActiveCN1852424ASave storage spaceDoes not take up storage spacePulse modulation television signal transmissionError preventionComputer terminalMedia server
The method includes steps: through wireless terminal, user requests a pointed stream program to be displayed, and sending the information of request to content management system; content management system receives the request; when display time reaches, the content management system sends prompt to wireless terminal; wireless terminal prompts user to play stream program requested; based on the information of request, the content management system sends command of playing back the pointed stream program to designated terminal at pointed time to stream server; after receiving the command, stream server sends stream media to the wireless terminal; the wireless terminal plays stream program. Advantages are: user is not restricted by time of playing stream program; saving storage space; making network server safer; protecting legal interest of content provider.
Owner:HUAWEI TECH CO LTD
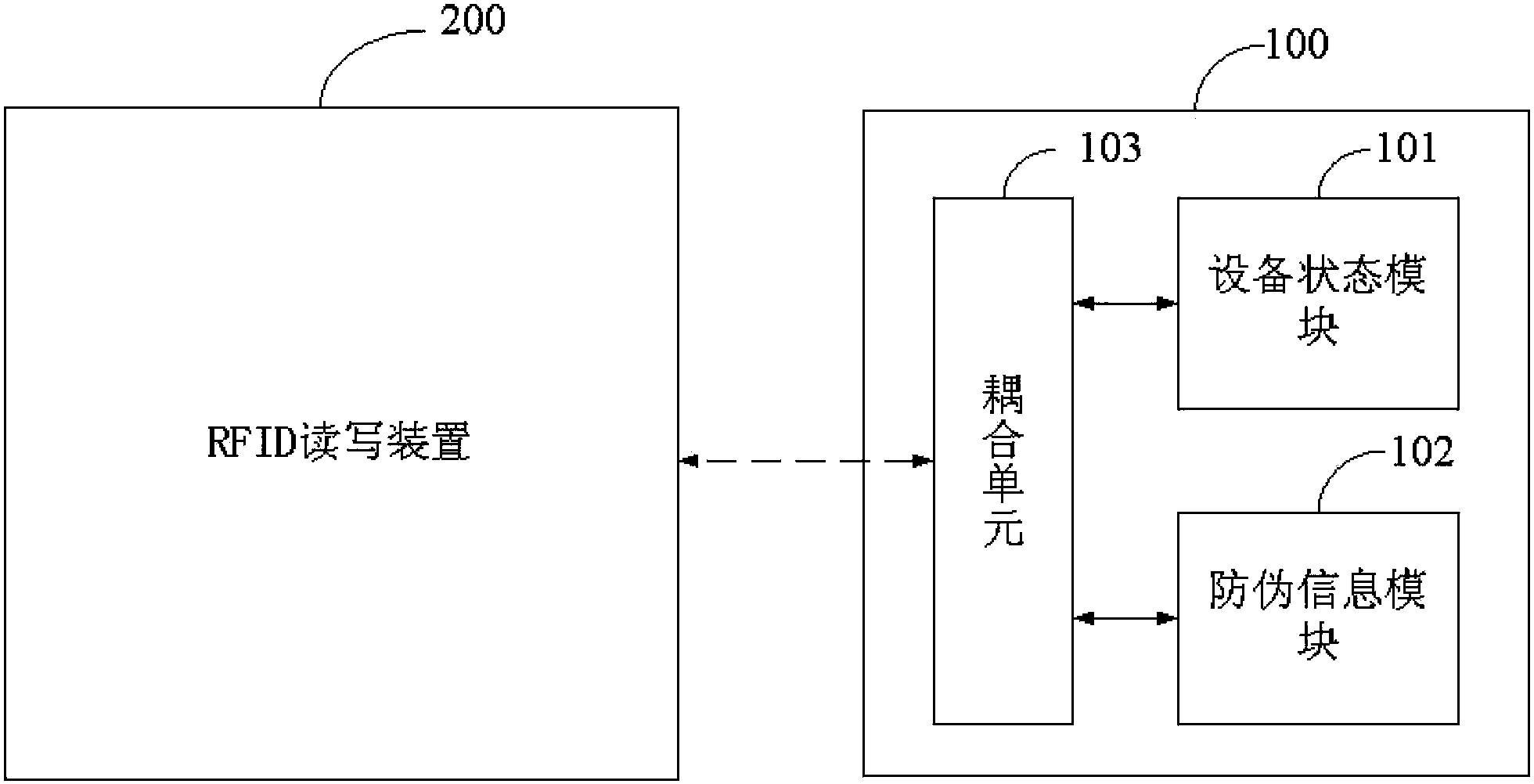
Anti-fake consumable item and application method thereof
InactiveCN103514470ASave steps in setting up print templatesAvoid damageCo-operative working arrangementsRecord carriers used with machinesElectricityComputer science
The invention relates to an anti-fake consumable item and an application method thereof. The anti-fake consumable item comprises a consumable item main body, and an RFID electronic tag arranged on the consumable item. The RFID electronic tag comprises a device state module which can be read and written repeatedly and an anti-fake information module which can be written once. A coupling unit which is electrically connected with the device state module and the anti-fake information module is further comprised. By implementing the anti-fake consumable item and an application method thereof of the invention, anti-fake detection is performed before the consumable item is used, when a fake consumable item is detected, the system stops using the fake consumable item so as to avoid the damage on other hardware equipment, so that legal advantages of users and manufacturers can be ensured.
Owner:POSTEK ELECTRONICS
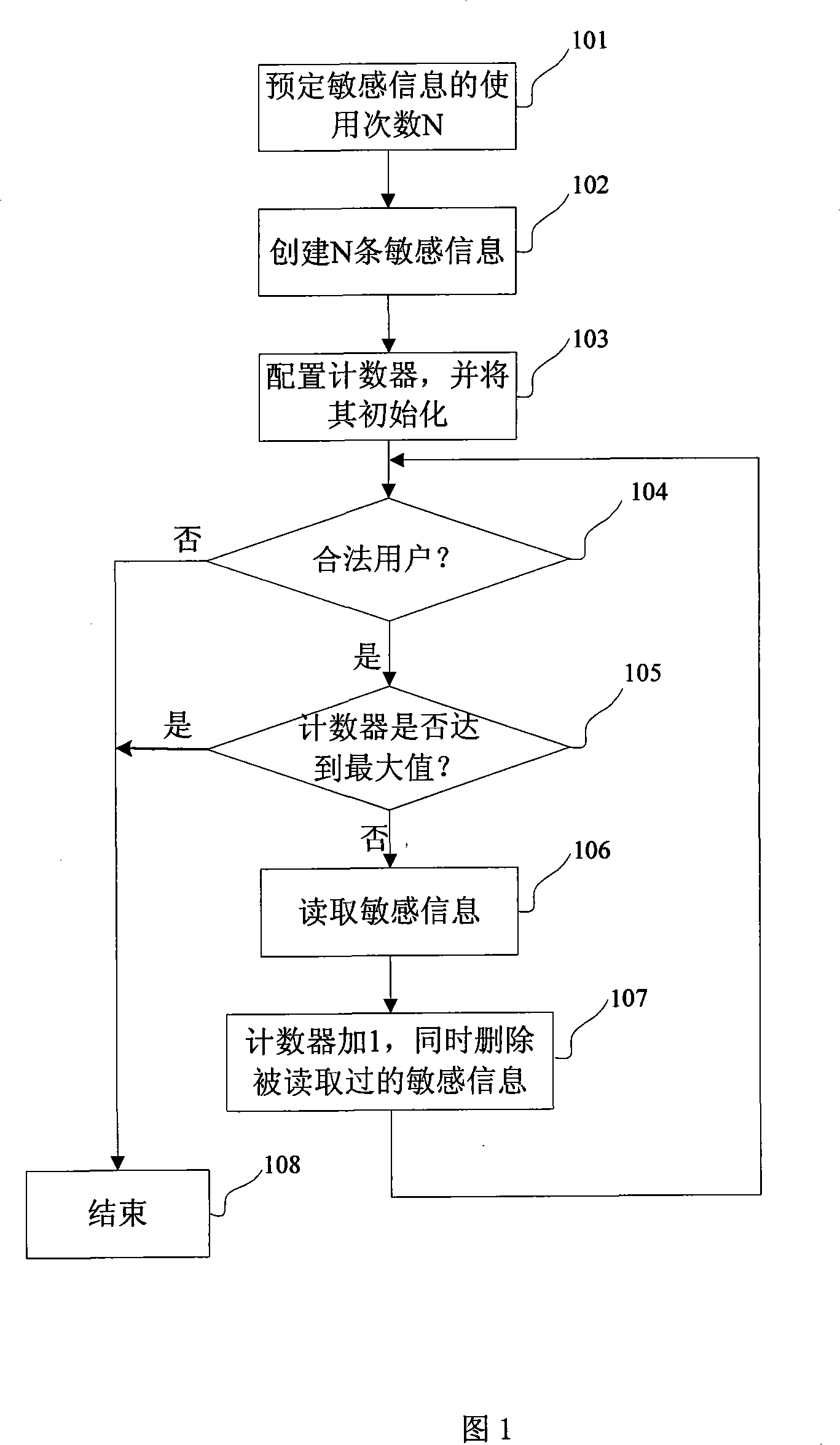
Method and storage device for limiting read of sensitive information
InactiveCN101079009APrevent theftImprove securityUnauthorized memory use protectionRecord carriers used with machinesInternet privacyInformation security
The invention discloses a method to limiting read sensitization information and storing device in information safe technical domain, which is characterized by the following: writing several strip sensitive information into storing device; receiving collected instrument; reading one sensitive information in the storing device; deleting the reading sensitive information; setting the storing device as receiving module, storing module and sensitive information collecting module. This invention avoids the sensitive information pilfered, intensifies the safety of data and improves safety in reading course.
Owner:FEITIAN TECHNOLOGIES
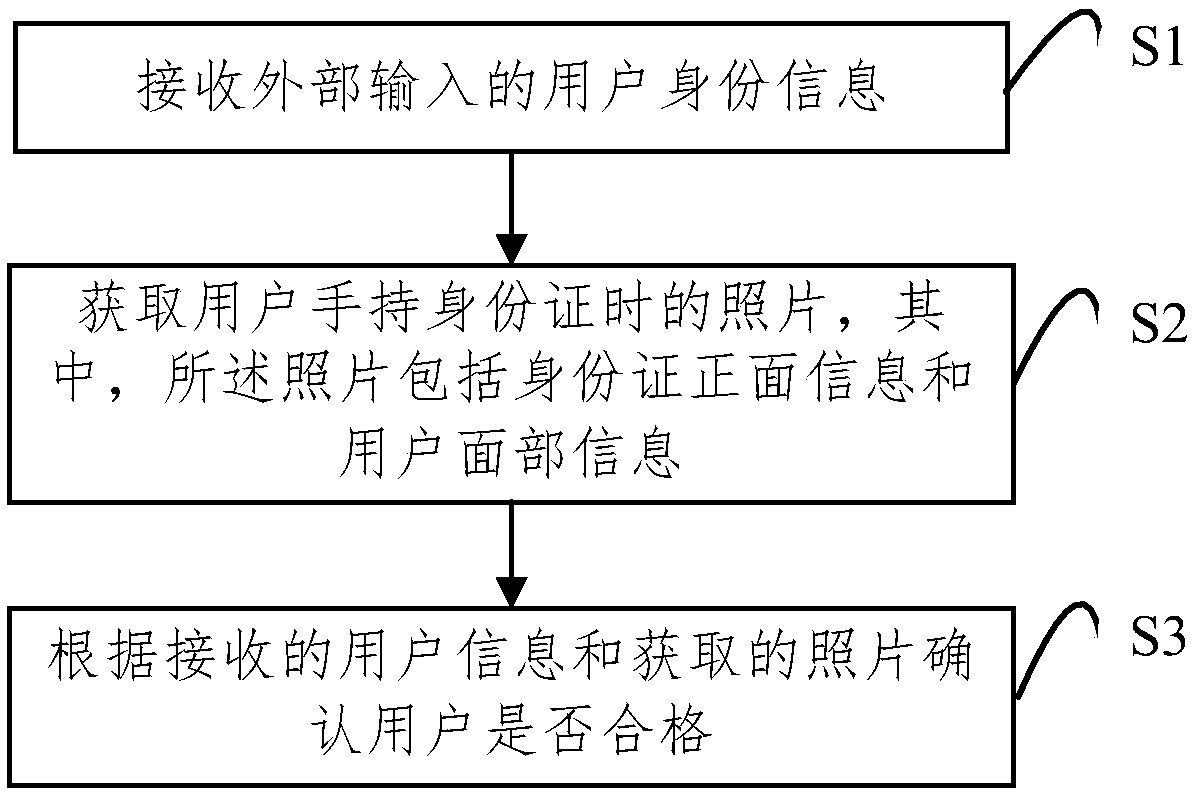
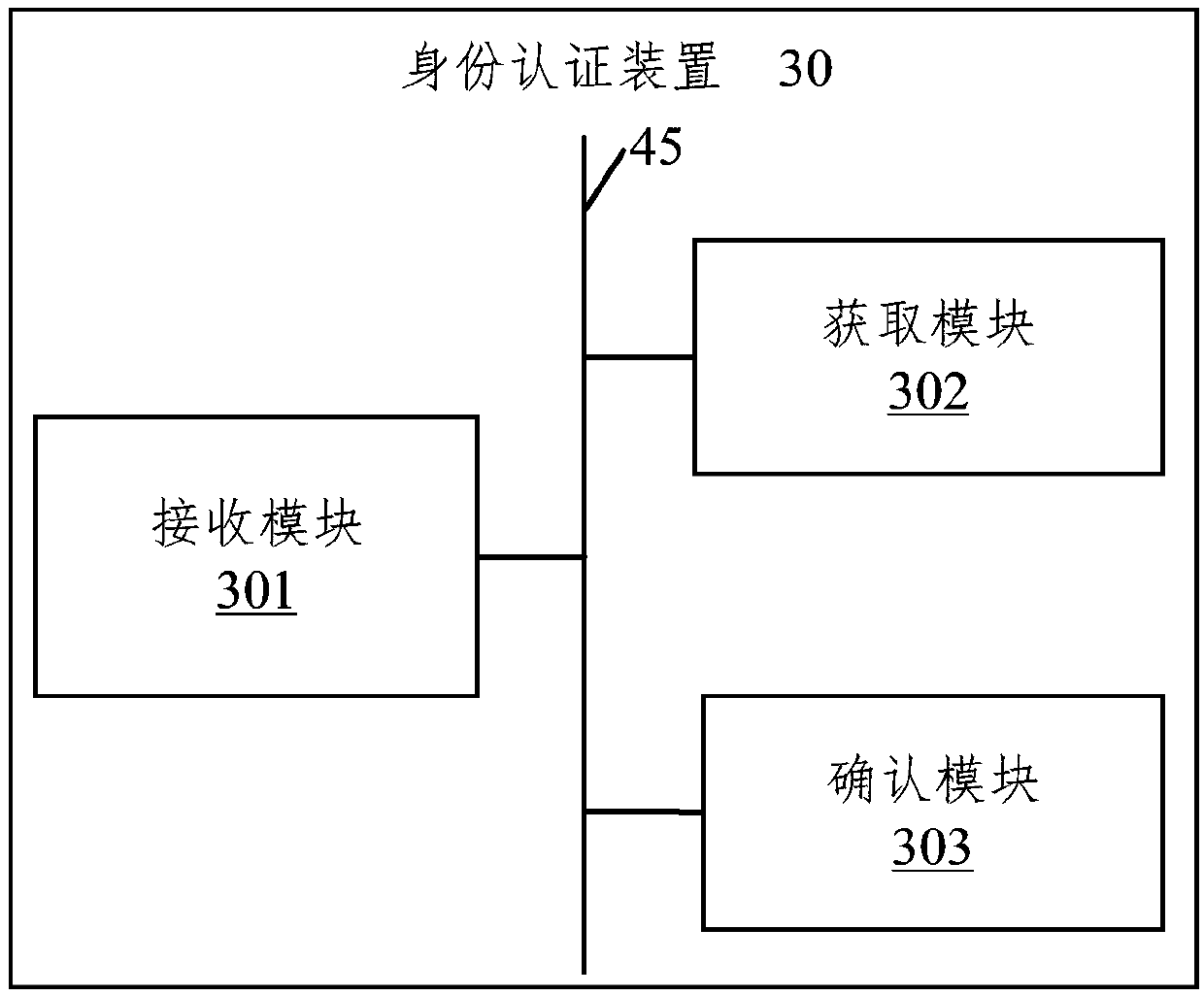
Identity authentication method and apparatus, terminal device, and storage medium
PendingCN109543507AImprove rigorImprove securityFinanceCharacter and pattern recognitionInternet privacyTerminal equipment
An identity authentication method includes receiving externally inputted user identity information, wherein the user identity information includes a name and an identity card number; acquiring a photograph of the user holding an identity card, wherein the photograph comprises positive information of the identity card and facial information of the user; and confirming whether the user is qualifiedaccording to the received user identity information and the obtained photograph, and receiving an account opening application when the user is confirmed to be qualified. The invention also provides anidentity authentication device, a terminal device and a storage medium. The invention authenticates the user identity based on the face recognition and the OCR recognition, which can obviously enhance the rigor and the security of the user opening an account, and protects the legitimate interests of the user and the bank.
Owner:ONE CONNECT SMART TECH CO LTD SHENZHEN
Real-time dispatching method for heating through abandoned wind power
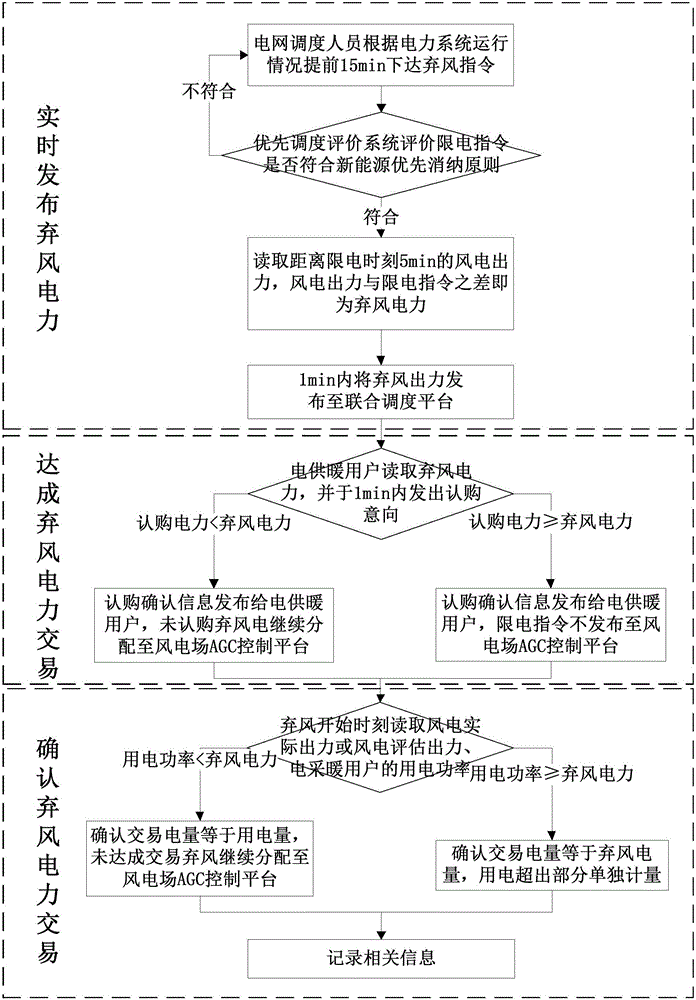
ActiveCN106026081AImprove the level of comprehensive utilizationImprove economySingle network parallel feeding arrangementsWind energy generationElectricitySimulation
The invention provides a real-time dispatching method for heating through abandoned wind power. The real-time dispatching method comprises the following steps of performing real-time publication of abandoned wind power; concluding the transaction of the abandoned wind power; and determining the transaction of the abandoned wind power. According to the real-time dispatching method, the randomness and fluctuation property of the wind power are taken into consideration; the wind power actual output or the wind power assessment output is read in real time, so that the abandoned wind power which can be used for electric heating can be evaluated accurately in real time, and then the abandoned wind power transaction can be performed; the condition that the unreasonable abandoned wind power is used for electric heating can be avoided; the utilization rate of the wind power can be increased; and reasonable benefits of all parties can be guaranteed.
Owner:CHINA ELECTRIC POWER RES INST +3
Gas flow collection device based on temperature and pressure intensity compensation
The invention discloses a gas flow collection device based on temperature and pressure intensity compensation. The gas flow collection device based on temperature and pressure intensity compensation comprises a temperature sensor, a pressure sensor, a flow collection module, a display module, a clock module, a control module and a storage module, wherein the flow collection module is used for collecting the gas volume in a working condition state; the temperature sensor is used for collecting temperature information of the gas supply environment; the pressure sensor is used for collecting pressure information of gas under the working condition state; the clock module is used for providing clock information; the control module is used for carrying out compensation calculation on the gas volume collected by the flow collection module according to the received temperature information and pressure information, obtains the gas volume corresponding to a standard state, and controls the storage module for storing the gas volume and the display module for displaying the gas volume. The gas flow collection device is simple in structure, convenient to use and accurate in calculation, eliminates the interference factors of temperature and pressure intensity in the working condition state, and ensures legal interests of users.
Owner:苏州市英富美欣科技有限公司
Visual ship searching and monitoring system
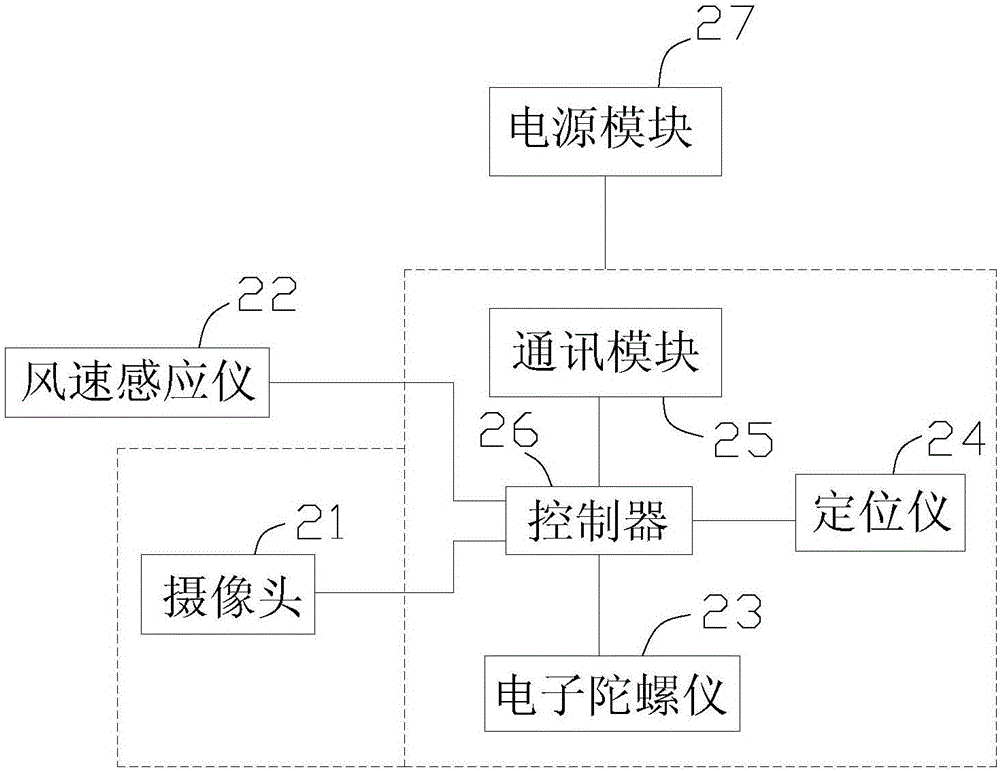
InactiveCN106815797AProtection of legitimate interestsReduce casualtiesMarine craft traffic controlLogisticsGyroscopeMonitoring system
The invention discloses a visual ship searching and monitoring system, which comprises a background server, a monitoring and early-warning device and a searching and monitoring platform. The monitoring and early-warning device is equipped with a camera, a wind speed inductance gauge, an electronic gyroscope, a position finder and a communication module. The navigation live information of a ship is transmitted to the background server through the communication module. The owner of the ship checks the navigation live information of the ship after searching the parameter information of the registered ship through the monitoring platform and connecting with the background server. The owner of goods finds a matched ship and checks the navigation live information of the ship through searching the monitoring platform. According to the technical scheme of the invention, the problem in the prior art that the conventional goods and ship searching operation is low in efficiency and not accurate in result can be effectively solved. Meanwhile, the navigation live information of the ship can be monitored in real time, so that the legitimate interests of the owners of ships and goods can be fully protected. Historical data can be stored, so that evidences are provided for the settlement of claims. Before and after the occurrence of an accident, the early warning and reaction can be automatically conducted by the system. Therefore, the rescue speed of the maritime square is effectively accelerated and the degree of casualties is reduced.
Owner:安徽彦思信息科技有限公司
Generation method for electronic attached sheets in circulation domain
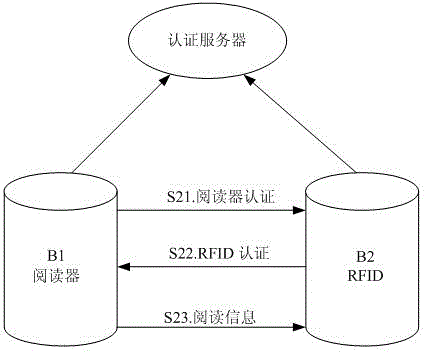
InactiveCN103559434AIncrease authenticityImprove securityCo-operative working arrangementsDigital data authenticationEngineeringAuthentication server
The invention relates to a generation method for electronic attached sheets in a circulation domain based on a hardware environment comprising an authentication server and multiple authentication parties. Each authentication party is a software entity comprising an RFID (radio frequency identification device) and a reader. The method includes an encryption authentication method and a decryption authentication method, and the decryption authentication method preferably includes a pre-step of mutual authentication of both the authentication parties. By the generation method for the electronic attached sheets in the circulation domain, authenticity and security of information in the electronic attached sheets in the circulation domain are improved, authenticity of data information is guaranteed, and legitimate interests of consumers, producers and retailers are guaranteed by applying the method to commodity production and sales processes.
Owner:SICHUAN UNIV +1
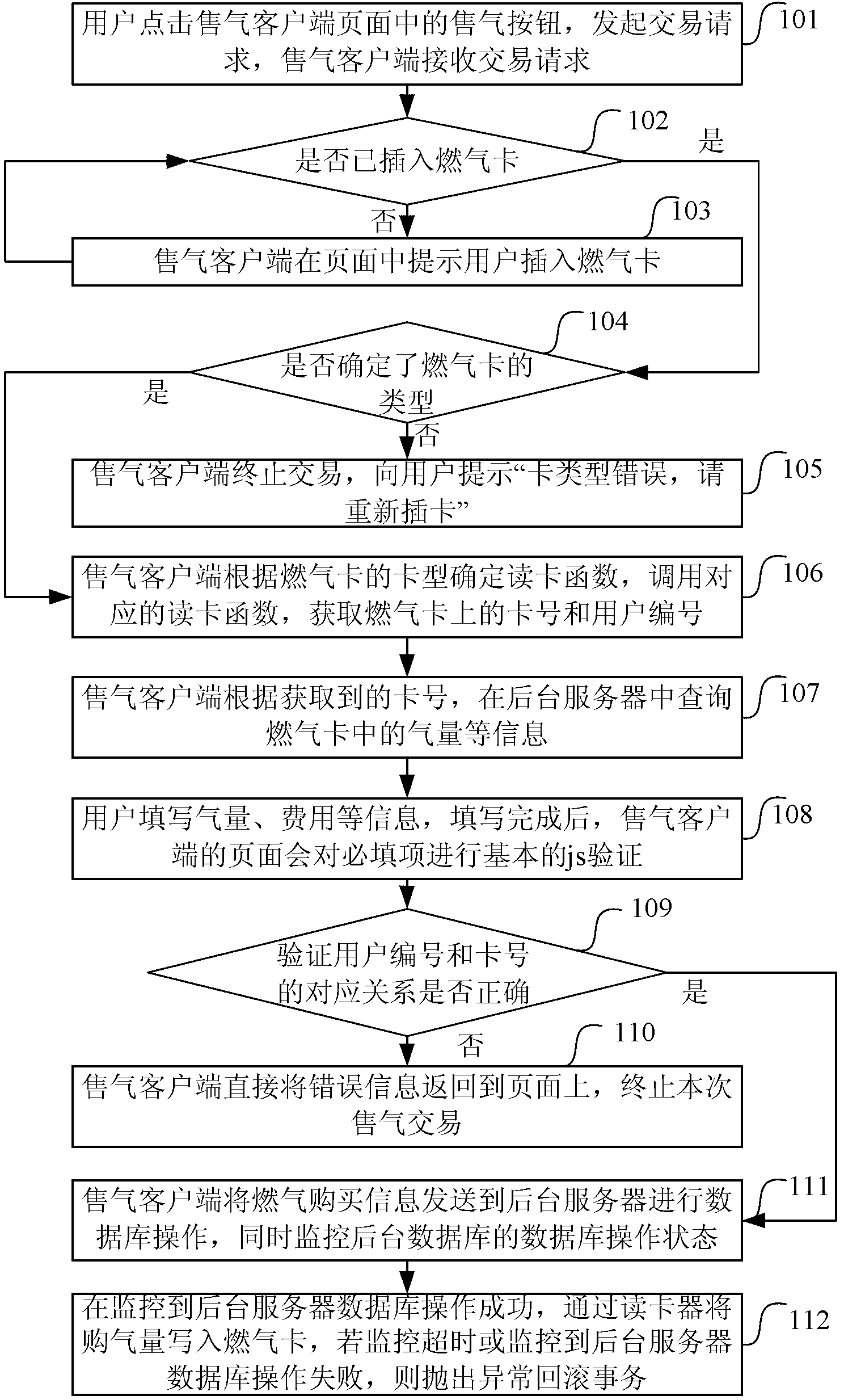
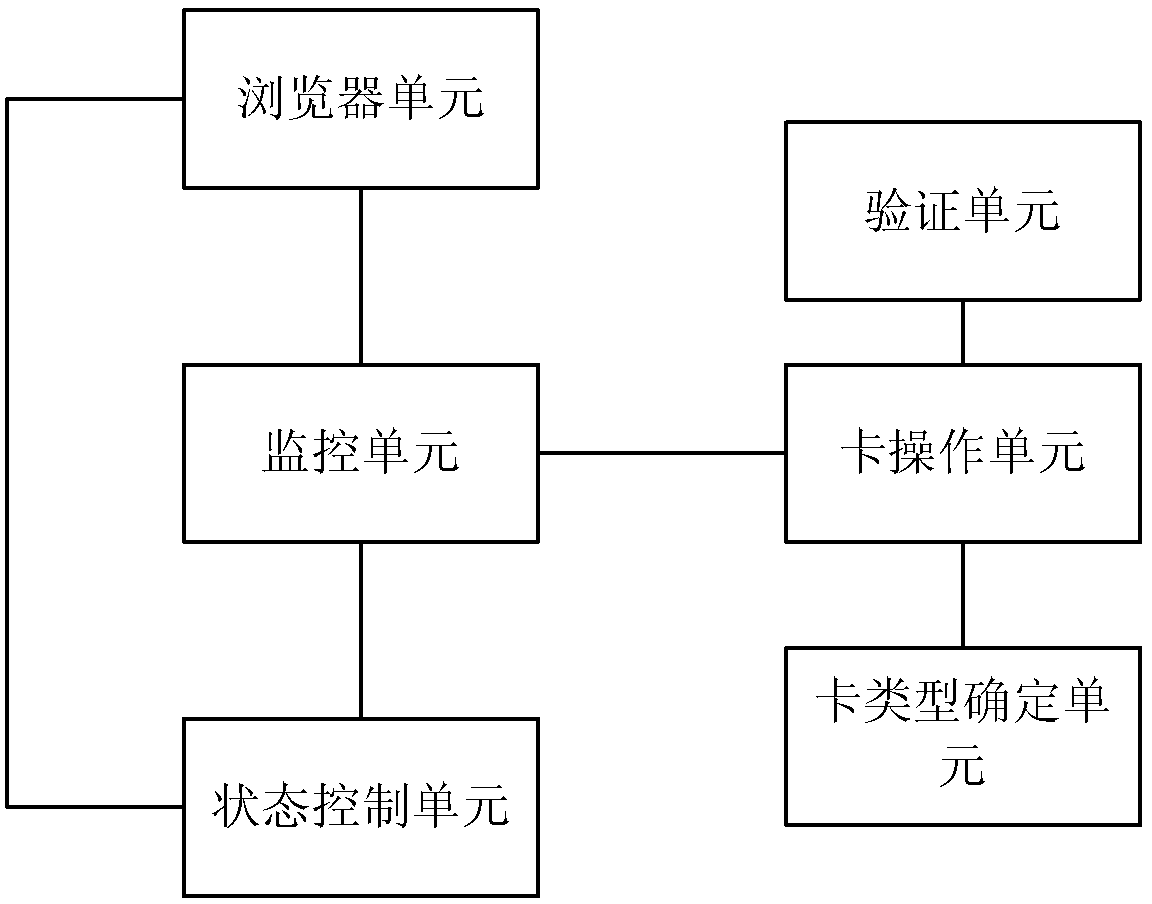
Fuel gas sale transaction method and gas sale client
InactiveCN103327086ASafe gas sales transactionAvoid administrative loopholesData processing applicationsTransmissionCard readerComputer science
The invention discloses a fuel gas sale transaction method and a gas sale client. The method includes the steps that in the process that a user buys fuel gas, the gas sale client sends fuel gas purchase information to a background server for database operation, the database operation state of the background server is monitored, and after the situation that the database operation of the background server is successful is monitored, gas purchase amount is written into a fuel gas card of the user through a card reader; when the monitoring is over time or the situation that the database operation of the background server fails, an abnormal roll-back event is executed to roll back to the state before a transaction request initiated by the user is received. The method can effectively avoid the problems that an incomplete transaction is caused by network failure or man-made network outage and thus card supplement and fuel cheating happen, can avoid management loopholes existing in a fuel card system and a fuel card table to the maximum, ensures that a fuel sale transaction of the fuel gas card is completed safely and effectively ensures legal interests of a fuel gas company.
Owner:BEYONDWINET INFORMATION TECH
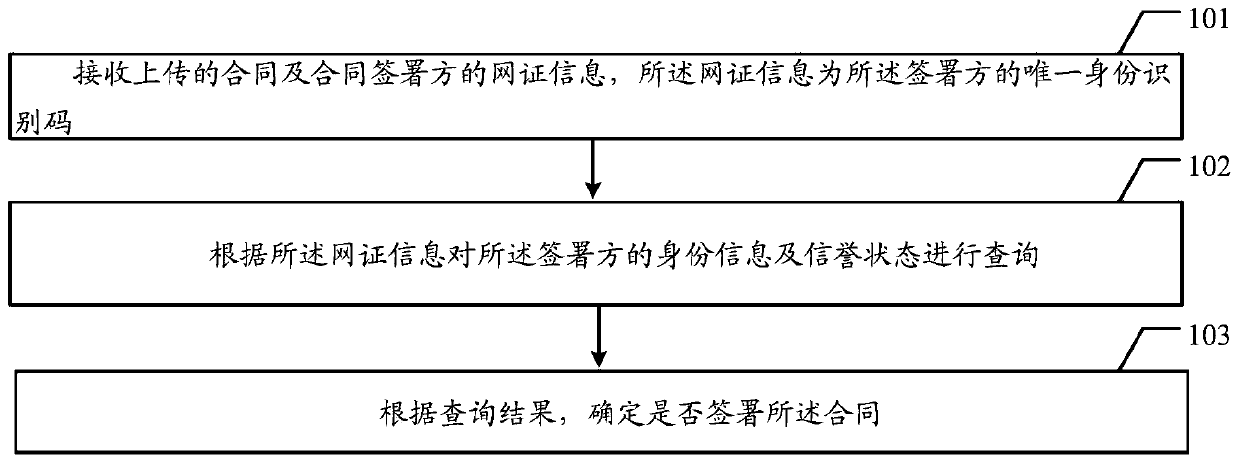
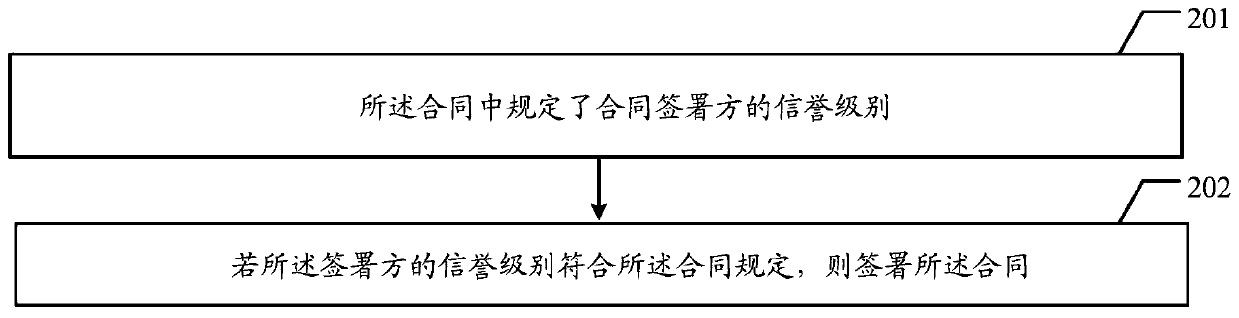
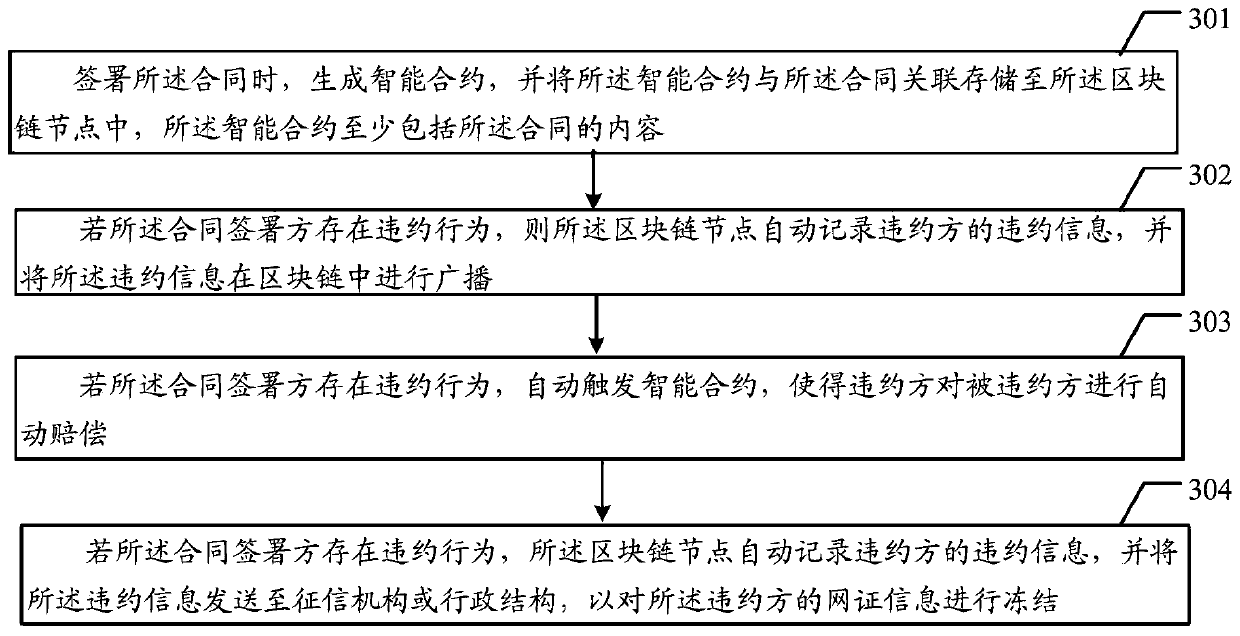
Contract signing method and block chain node equipment
ActiveCN109960919AGuarantee authenticityProtection of legitimate interestsDigital data protectionDigital data authenticationBlockchain
The embodiment of the invention provides a contract signing method and block chain node equipment, which are used for carrying out query confirmation on the identity authenticity and the reputation state of a contract signer during contract signing so as to ensure the legitimate interests of the contract signer. The method disclosed by the embodiment of the invention comprises the following steps:receiving an uploaded contract and network certificate information of a contract signer, wherein the network certificate information is a unique identity identification code of the signer; querying the identity information and the reputation state of the signer according to the network certificate information; and determining whether to sign the contract according to a query result.
Owner:LAUNCH TECH CO LTD
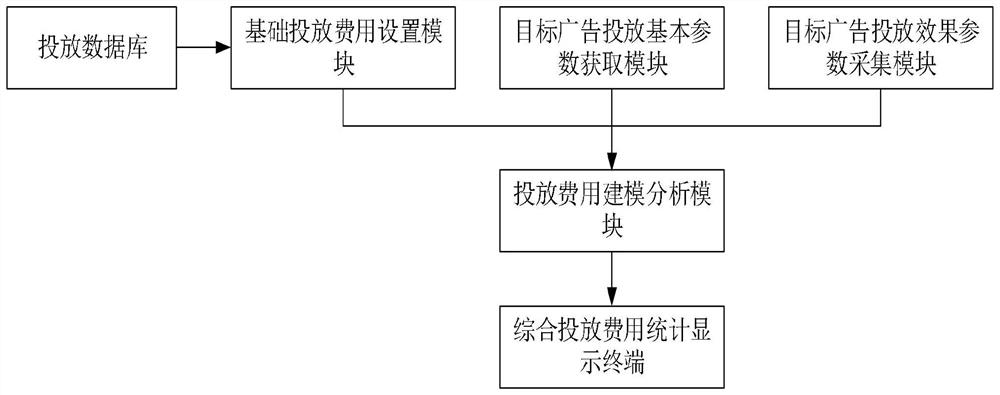
Electronic screen advertisement intelligent charging management system based on data analysis
PendingCN114708018AHigh precisionProtection of legitimate interestsAdvertisementsAlgorithmDelivery cost
The invention discloses an electronic screen advertisement intelligent billing management system based on data analysis, which comprises a basic putting cost setting module, a target advertisement putting basic parameter acquisition module, a target advertisement putting effect parameter acquisition module, a putting database, a putting cost modeling analysis module and a comprehensive putting cost statistical display terminal, basic putting parameters corresponding to a target advertisement and putting effect parameters corresponding to each time of putting in each putting day are acquired, and the parameters are imported into a putting cost algorithm model to calculate putting cost of the target advertisement in a putting position dimension, a putting time dimension and a putting effect dimension corresponding to each time of putting in each putting day; therefore, the comprehensive delivery cost corresponding to the target advertisement is counted by combining the delivery cost of each dimension, the multi-dimensional delivery cost calculation corresponding to the subway display screen advertisement is realized, and the defect that the charging dimension is too uniformed in the current subway display screen advertisement delivery cost management mode is greatly overcome.
Owner:武汉万驰机械设备租赁有限公司
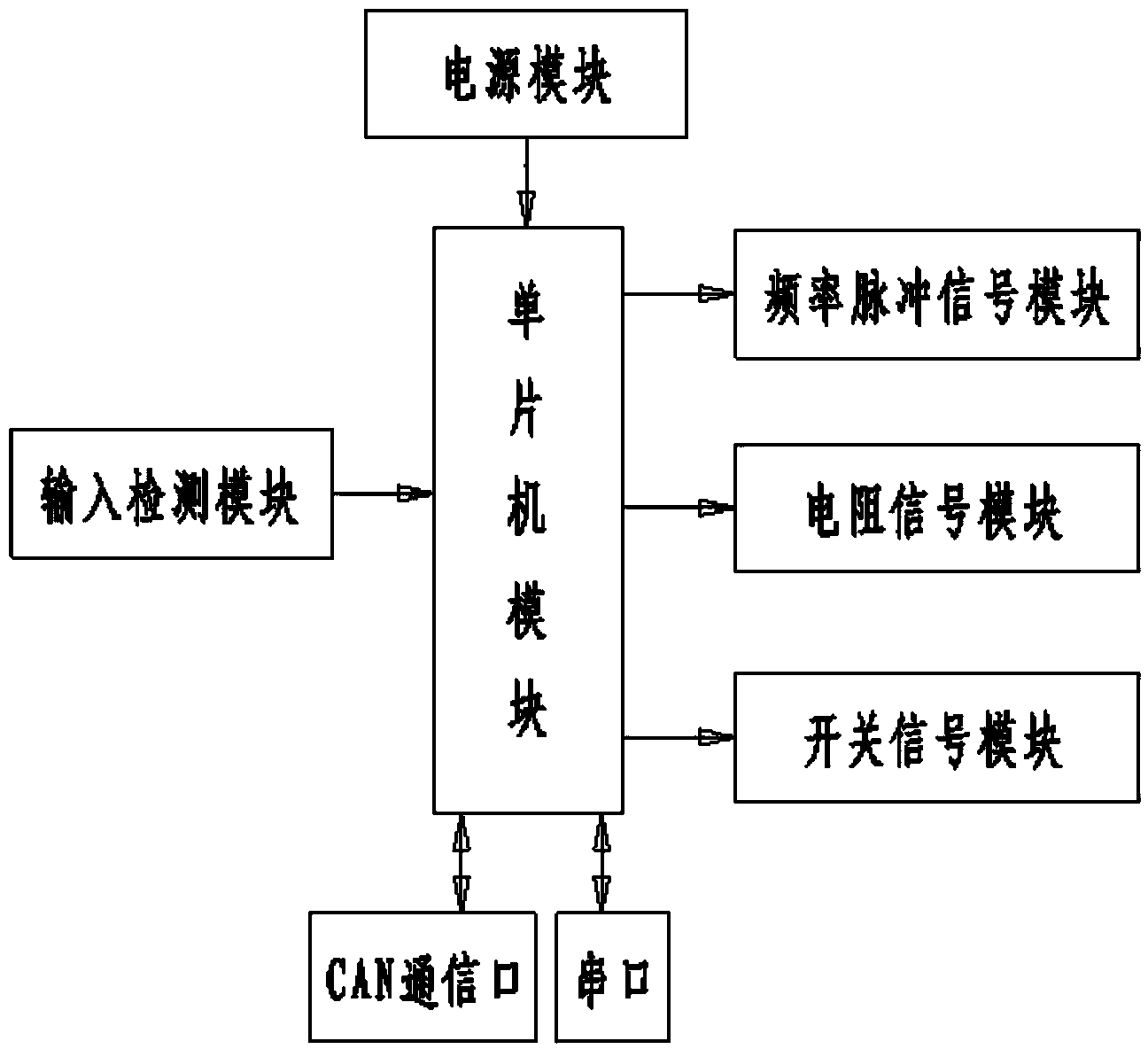
Universal automobile combination instrument function detection device
ActiveCN103644932AImprove general performanceIncrease productivityInstrumentsInstrument functionMicrocontroller
The invention discloses a universal automobile combination instrument function detection device and relates to a tester. The universal automobile combination instrument function detection device comprises a power module, an input detection module, a single-chip microcomputer module, a frequency pulse signal module, a resistor signal module, a switch signal module, a CAN communication port and a serial port, wherein the power module supplies power to the single-chip microcomputer module, the input detection module detects whether input data is correct and inputs detected input data to the single-chip microcomputer module, and the single-chip microcomputer module respectively outputs corresponding data signals; and the frequency pulse signal module, after receiving pulse signals outputted by the single-chip microcomputer module, outputs corresponding frequency signals to an instrument, the resistor signal module, after receiving resistor signals outputted by the single-chip microcomputer module, outputs corresponding resistor signals to the instrument, and the switch signal module outputs switch signals outputted by the single-chip microcomputer module to switches. The universal automobile combination instrument function detection device has the advantages of high versatility, lightness, convenience, low cost, high production efficiency and the like, thereby being applied to various occasions including production, examination, service after sale and the like of an automobile combination instrument.
Owner:LIUZHOU HANGSHENG TECH
Electronic device hardware verification method
InactiveCN107273255AProtection of legitimate interestsProtection securityVersion controlDetecting faulty computer hardwareComputer hardwareValidation methods
The present invention relates to the field of hardware verification of equipment, in particular to the field of hardware verification of electronic equipment. The present invention provides a hardware verification method of electronic equipment. All main components of electronic equipment are equipped with unique numbers, and a configuration is generated from the set of numbers. file, store the configuration file on the network or in a certain part of the device. When a part of the electronic device is replaced, hardware detection will be started. When the hardware number does not match the configuration file, the device will be restricted or stopped Operation, thereby restricting the installation of components from illegal sources in electronic equipment, and ensuring the legitimate rights and interests of consumers and manufacturers.
Owner:维乐思启(北京)科技有限公司
Management method of intelligent equipment and server
ActiveCN114298724AProtection of legitimate interestsImprove management efficiencyCommerceTotal factory controlTerminal equipmentEngineering
The invention discloses an intelligent device management method and a server, and the method comprises the steps: obtaining a device serial number of an intelligent device and activation information of a first terminal device, the first terminal device being a device used for activating the intelligent device to communicate with the server; determining a first sales address of the intelligent device based on the device serial number, and determining an activation operation address of the first terminal device based on activation information of the first terminal device, the first sales address being associated with a sales channel of the intelligent device; and managing a sales channel of the intelligent device based on the first sales address and the activation operation address. According to the management method, the abnormity of the sales channels can be monitored, the management of the abnormal sales channels can be enhanced correspondingly, the management efficiency and accuracy are improved, the legitimate interests of all the sales channels are ensured, and then the legitimate interests of manufacturers are protected.
Owner:BEIJING SENSESHIELD TECH
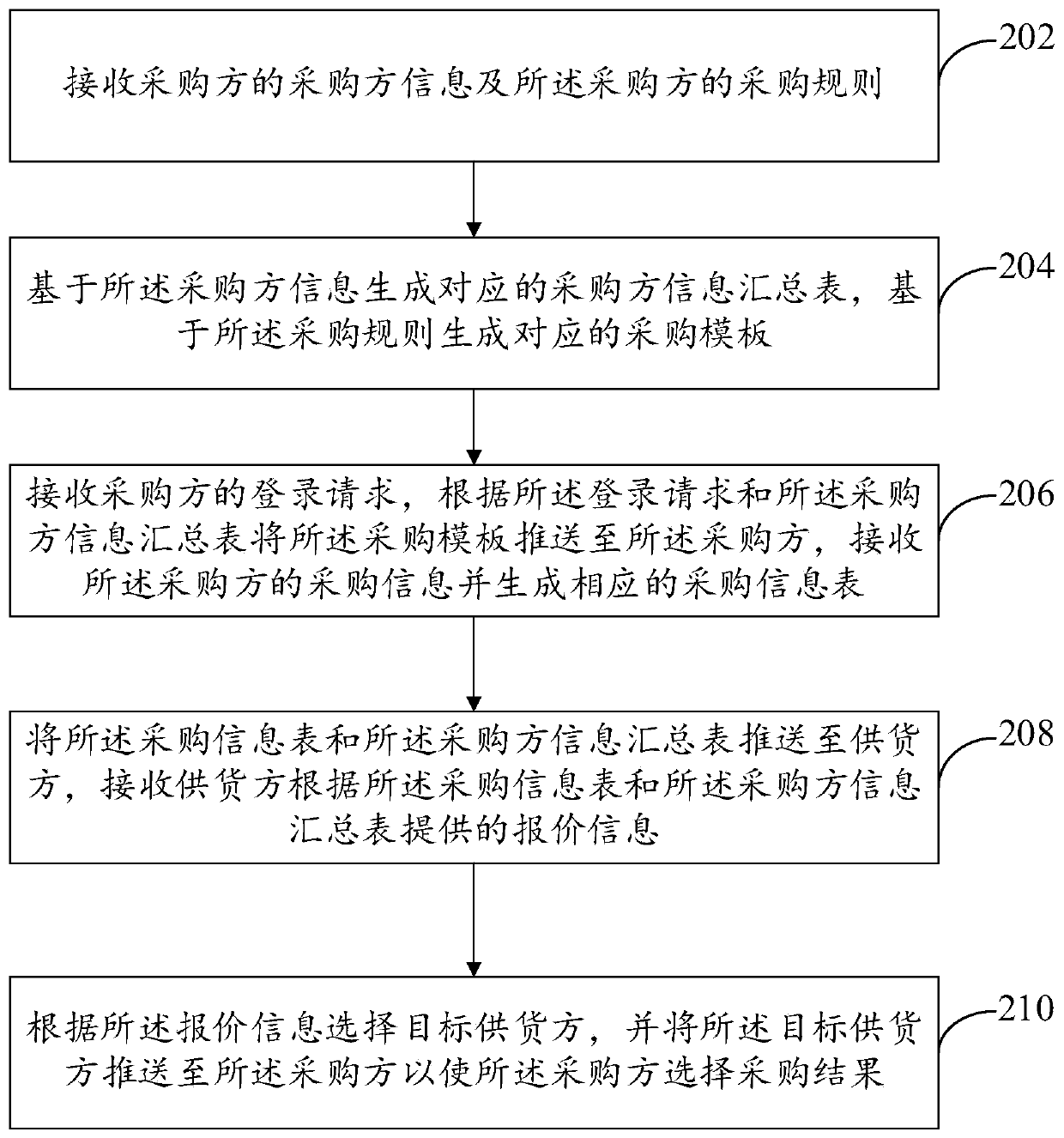
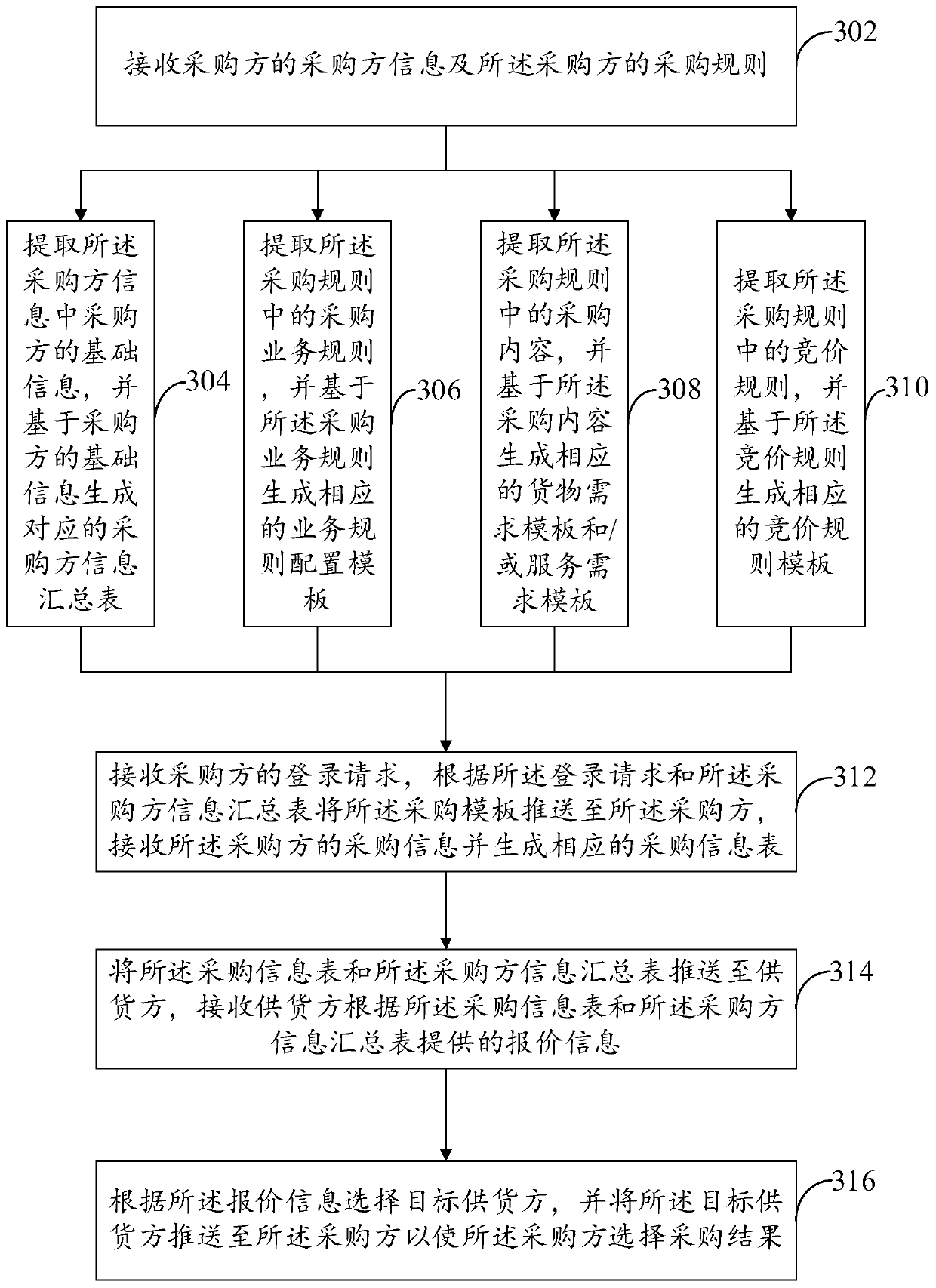
Differentiated purchasing method and device
ActiveCN110428309AStrengthen supervisionImprove procurement efficiencyBuying/selling/leasing transactionsTemplate basedPurchasing
The invention provides a differentiated purchasing method and a device, and the method is used for a system platform, and comprises the steps: receiving the purchaser information of a purchaser and the purchasing rule of the purchaser; generating a corresponding purchaser information summary sheet based on the purchaser information, and generating a corresponding purchase template based on the purchase rule; receiving a login request of the purchaser, pushing the purchasing template to the purchaser according to the login request and the purchaser information summary table, receiving purchasing information of the purchaser and generating a corresponding purchasing information table; pushing the purchase information table and the purchaser information summary table to a supplier, and receiving quotation information provided by the supplier according to the purchase information table and the purchaser information summary table; and selecting a target supplier according to the quotation information, and pushing the target supplier to the purchaser to enable the purchaser to select a purchasing result.
Owner:政采云有限公司
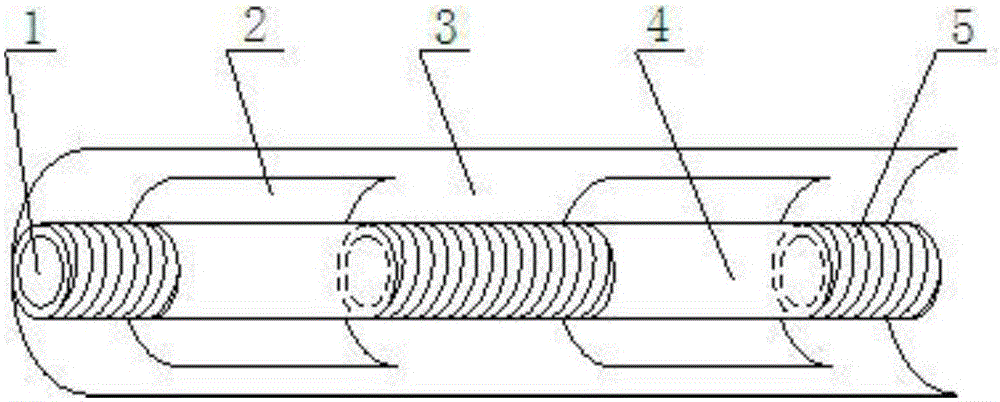
Composite filter stick wound with spice-containing threads and preparation method of composite filter stick
InactiveCN105962414AWiden the functional spaceSolve the problem of not being able to carry more flavor spicesGeometric CADTobacco smoke filtersFiberPolymer science
The invention discloses a composite filter stick wound with spice-containing threads and a preparation method of the composite filter stick. Cellulose acetate fiber filter stick sections and spice-containing thread filter stick sections are wrapped with an outer wrapping layer to form a round stick, and the composite filter stick wound with the spice-containing threads is prepared, wherein each spice-containing thread filter stick section is formed by winding and wrapping a cellulose acetate fiber core stick with one or more spice-containing threads, and the cellulose acetate fiber filter stick sections are wrapped with an inner wrapping layer. According to the composite filter stick wound with the spice-containing threads and the preparation method of the composite filter stick, the spice-containing threads serving as carriers of various spices also have the function of wrapping tow, aroma enhancing substances with various flavors are rich, the taste of cigarettes during smoking is improved, and the spice-containing threads replace shaping paper, have more functions and better aroma enhancement effect and have an anti-counterfeiting effect.
Owner:CHINA TOBACCO YUNNAN IND
Method and device for identifying user identity of SIM card
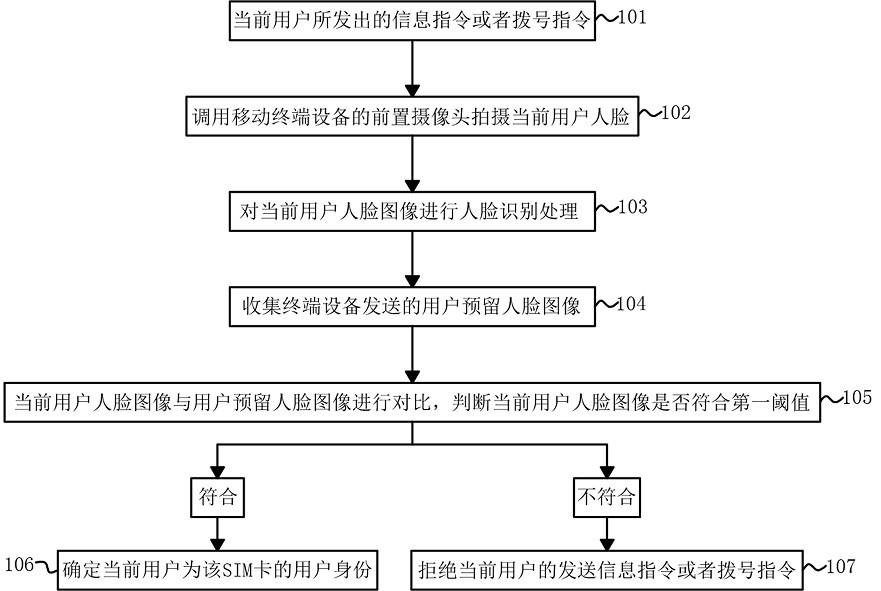
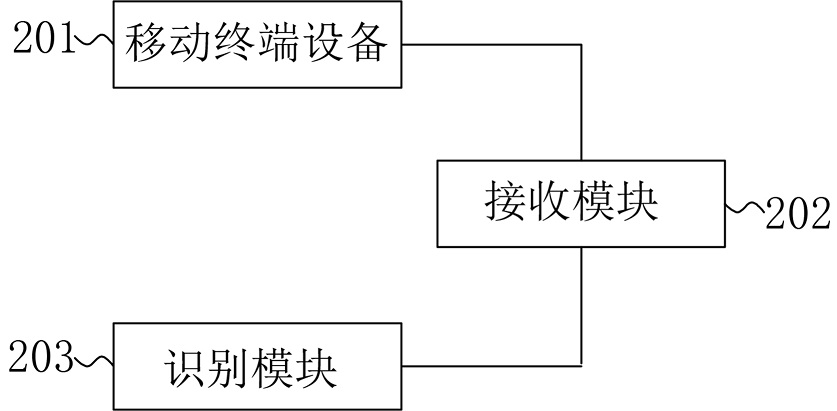
PendingCN112528261AProtection of legitimate interestsPrevent forgeryCharacter and pattern recognitionDigital data authenticationTerminal equipmentEngineering
The invention discloses a method and a device for identifying the user identity of an SIM card, and the method comprises the steps: calling a front camera of mobile terminal equipment to shoot the face of a current user when an information instruction or a dialing instruction is transmitted by the current user, and starting to carry out the face recognition of a face image of the current user; receiving a user reserved face image sent by the collection terminal device; and comparing the face image of the current user with the face image reserved by the user, judging whether the face image of the current user conforms to a first threshold value, if yes, determining that the current user is the user identity of the SIM card, and if not, refusing the current user to send an information instruction or a dialing instruction. According to the method of the invention, before the sending information of the current user or the instruction of dialing to contact other people is executed, whetherthe current user is the user identity which does not belong to the SIM card is identified, so that the legal interests of the user of the SIM card are protected, and illegal persons are prevented fromstealing the SIM of other people and counterfeiting the identity of other persons.
Owner:GUANGDONG CHUTIAN DRAGON SMART CARD
Beidou GNSS/DR integrated navigation taxi metering and timing system and running method thereof
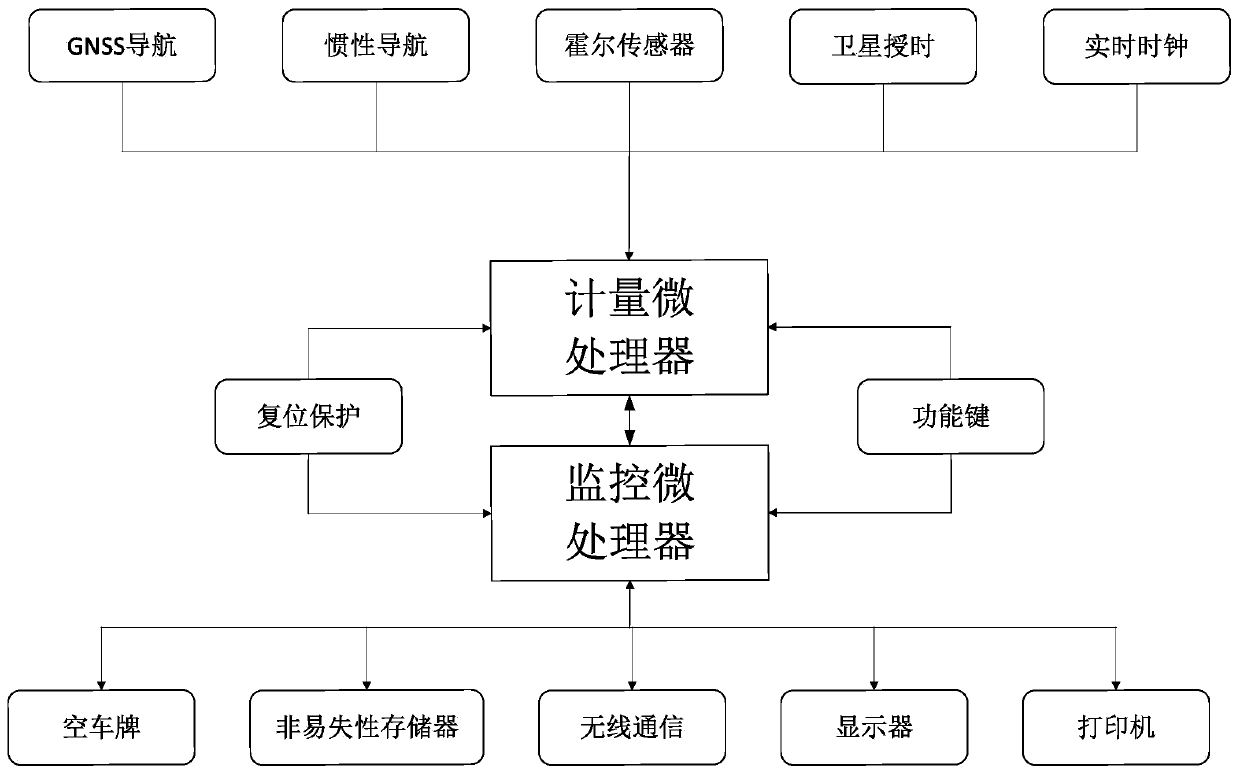
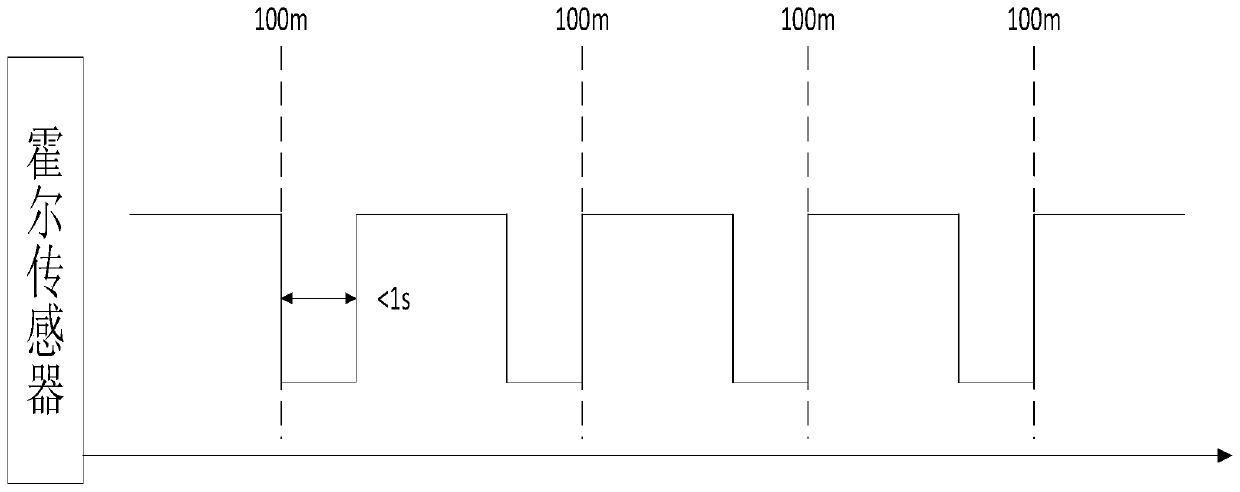
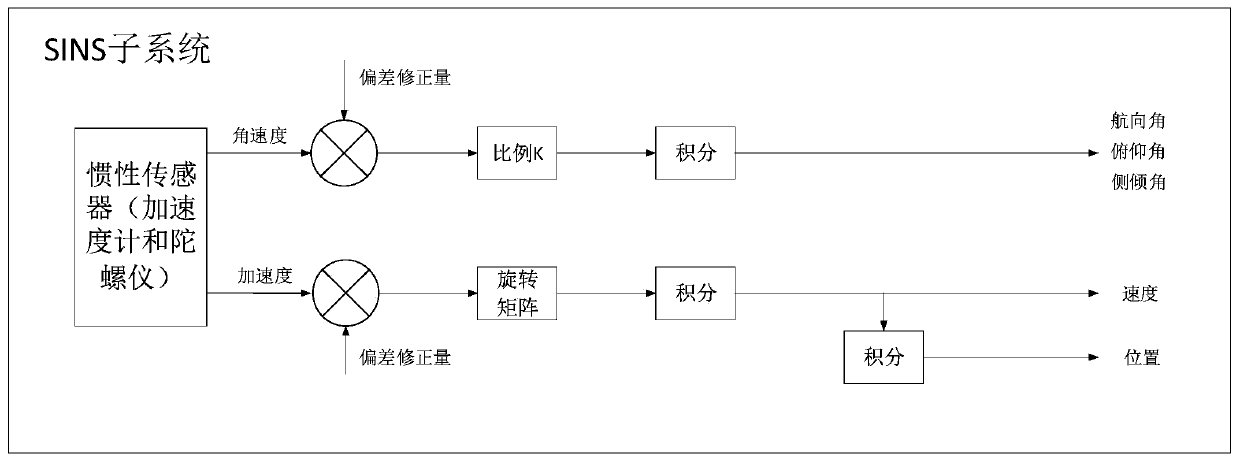
ActiveCN110189421AHigh positioning accuracyAvoid meter problemsRegistering/indicating working of vehiclesParticular environment based servicesCanyonEngineering
The invention relates to a Beidou GNSS / DR integrated navigation taxi metering and timing system and a running method thereof, and the system comprises a GNSS navigation unit, an inertial navigation unit, a satellite timing unit, a reset protection unit, a Hall sensor, a function key, an empty license plate, a real-time clock, a metering microprocessor, a monitoring microprocessor, a non-volatile memory and a wireless communication unit. The Beidou GNSS / DR integrated navigation taxi metering and timing system and the running method thereof provided by the invention avoid metering problems of the traditional satellite navigation without navigation signals or under an environment of weak navigation signals such as section of tunnels, viaducts and urban canyons by metering the taxi with the Beidou GNSS / DR integrated navigation technology, achieve the sub-meter positioning accuracy by utilizing the GNSS ground enhancement technology and the optimized navigation algorithm, and solve the positioning problem in the complex environment with the DR technology, thereby finally making the vehicle trajectory continuous without breakpoints.
Owner:SHANDONG UNIV
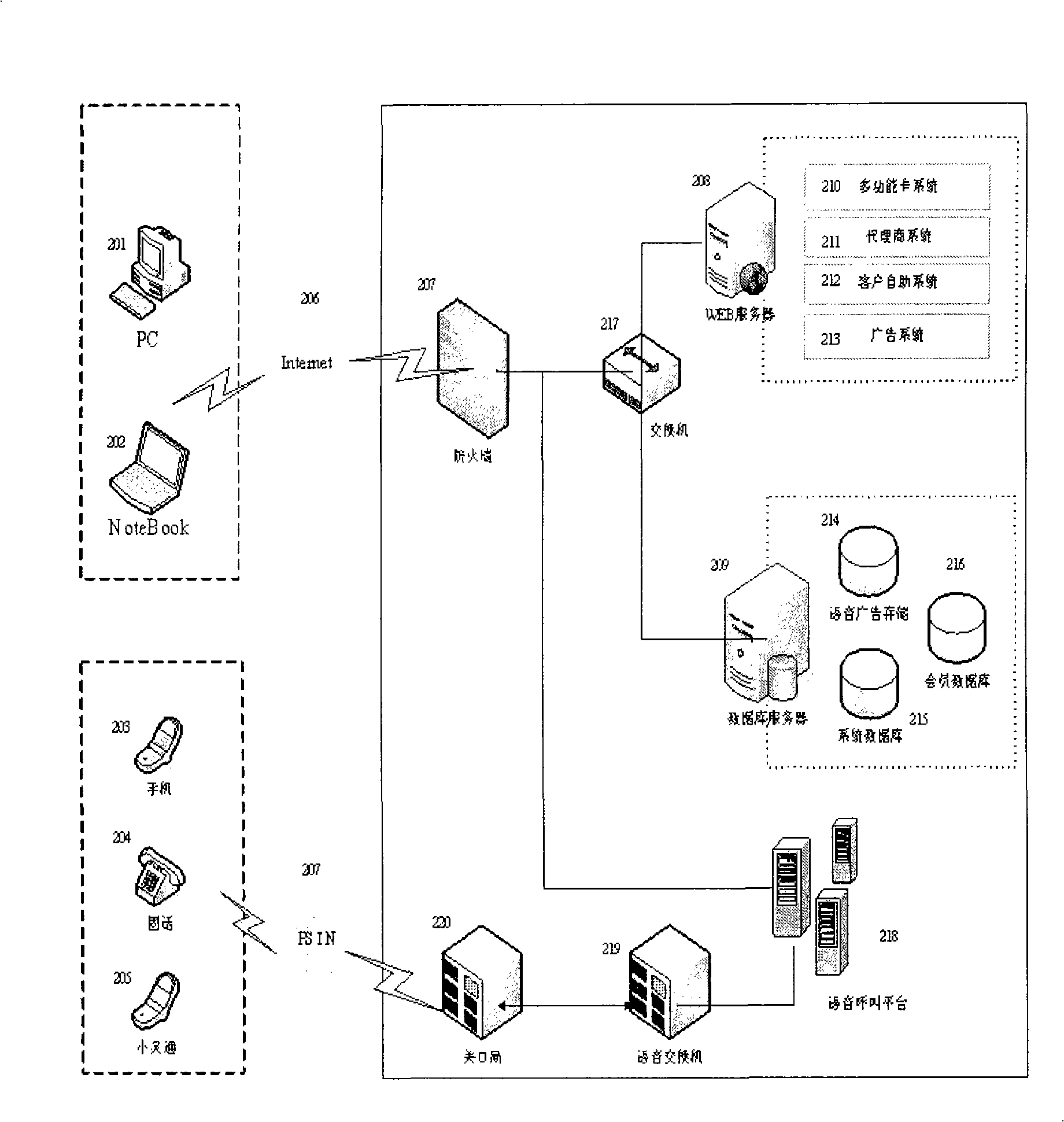
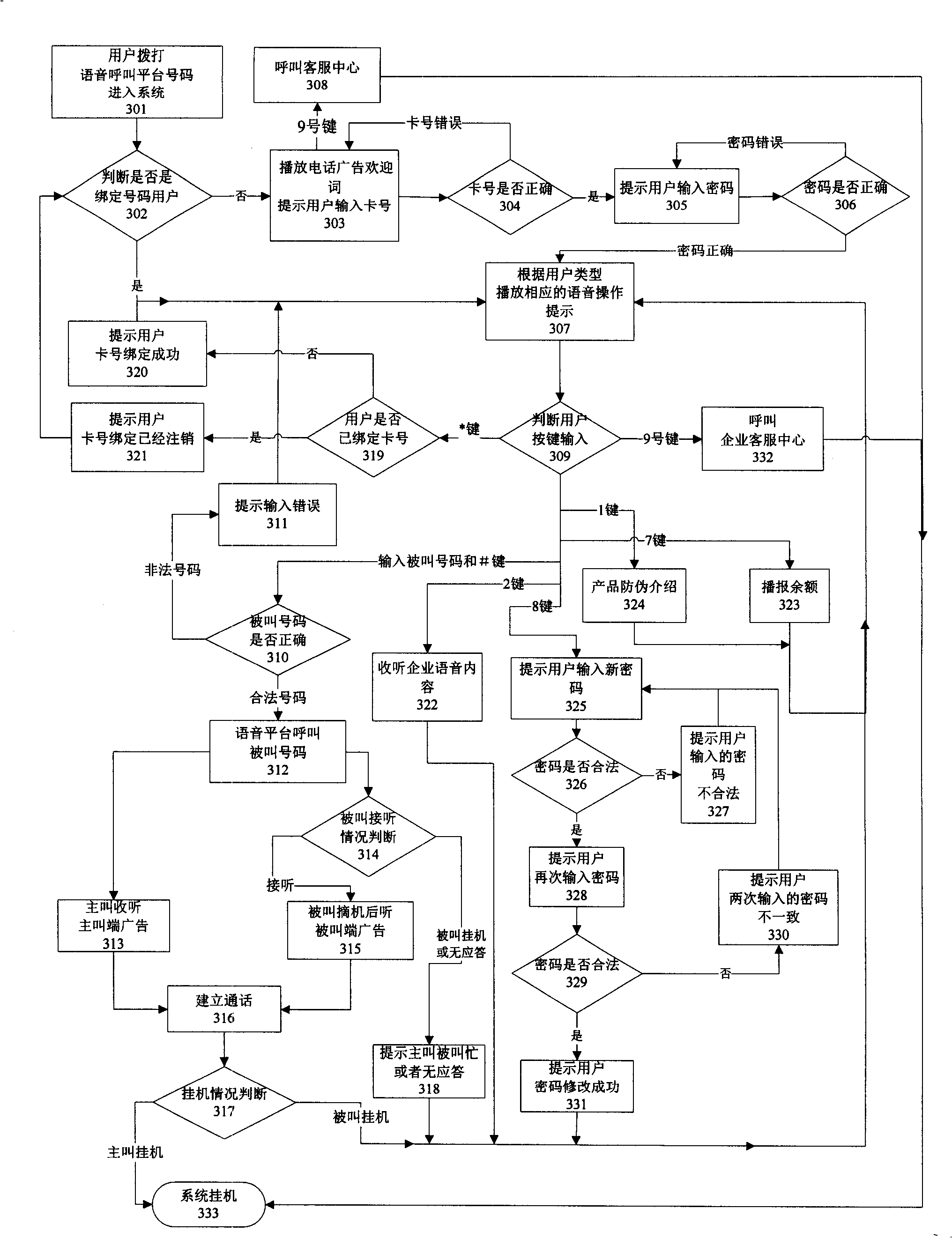
Method for providing bidirectional voice advertisement to calling and called party using voice calling platform
InactiveCN101335791AProtection of legitimate interestsTaking into account different needsSpecial service for subscribersSelection arrangementsVoice communicationSpeech sound
The invention discloses a voice communication technology, specifically to a method using the existing communication platform to publish bidirectional voice advertisement. The invention uses the existing communication technology platform to set up voice numbers, stores advertisement, calling party tariff card information content, and the like, in a database of a voice call platform in advance. When the calling party calls the voice numbers, the calling party checks up according to the voice prompt and the automatic request of the voice call platform, and then calls the numbers of called party, simultaneously the calling party can hear the advertisement of commercial units in the waiting process after dialing, and the telephone tariff of the calling party is paid by the advertiser, while the called party can hear the advertisement before answering the telephone, and the play of advertisements to both parties is stopped for normalized talking. The invention possesses the advantages of fully utilizing standby time of prior art platform, realizing a big commerce object. The invention can be widely applied in the existing telephone system and is provided with wide market outlook.
Owner:杭州天量通信技术有限公司 +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com