Method and storage device for limiting read of sensitive information
A technology for sensitive information and storage devices, applied in the field of information security to achieve the effect of overcoming illegal use, avoiding theft, and protecting legitimate interests
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
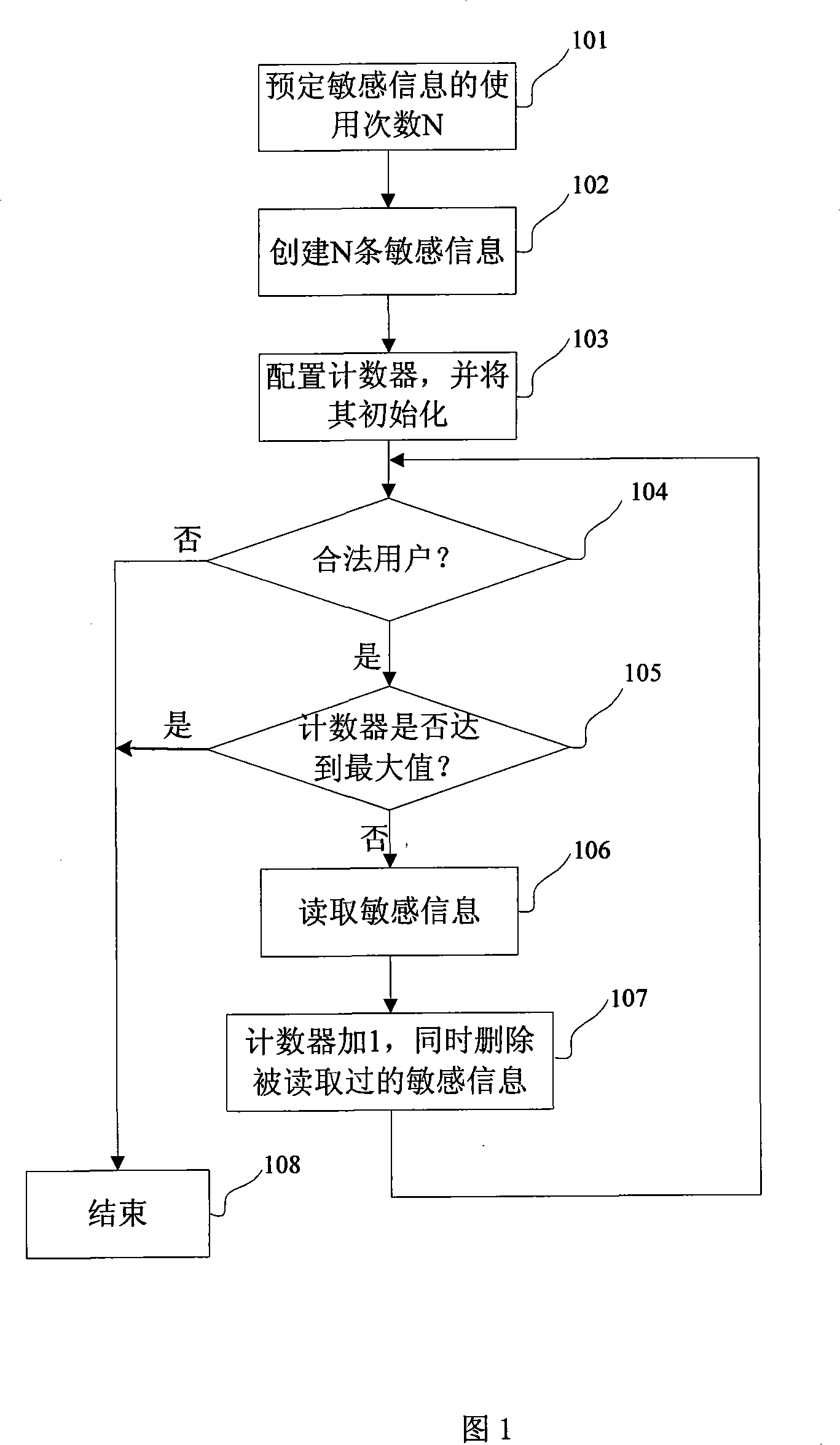
[0046] This embodiment provides a method for restricting the use of sensitive information, see Figure 1, the specific steps are as follows:
[0047] Step 101: The customer pre-defines the number N of uses of sensitive information.
[0048] Step 102: Create N pieces of sensitive information.
[0049] Sensitive information includes codes, keys, serial numbers, user passwords, user names, certificates, user identifiers, user rights, etc., and the sensitive information in this embodiment is keys and serial numbers. The carrier for storing sensitive information may be a smart card chip, a non-smart card chip or a storage chip, and the smart card chip is selected for storage in this embodiment. The content of each piece of sensitive information may be completely the same or different. For example, multiple pieces of sensitive information may all have the same key and serial number, or different keys and serial numbers.
[0050] In the production management process, the smart card ...
Embodiment 2
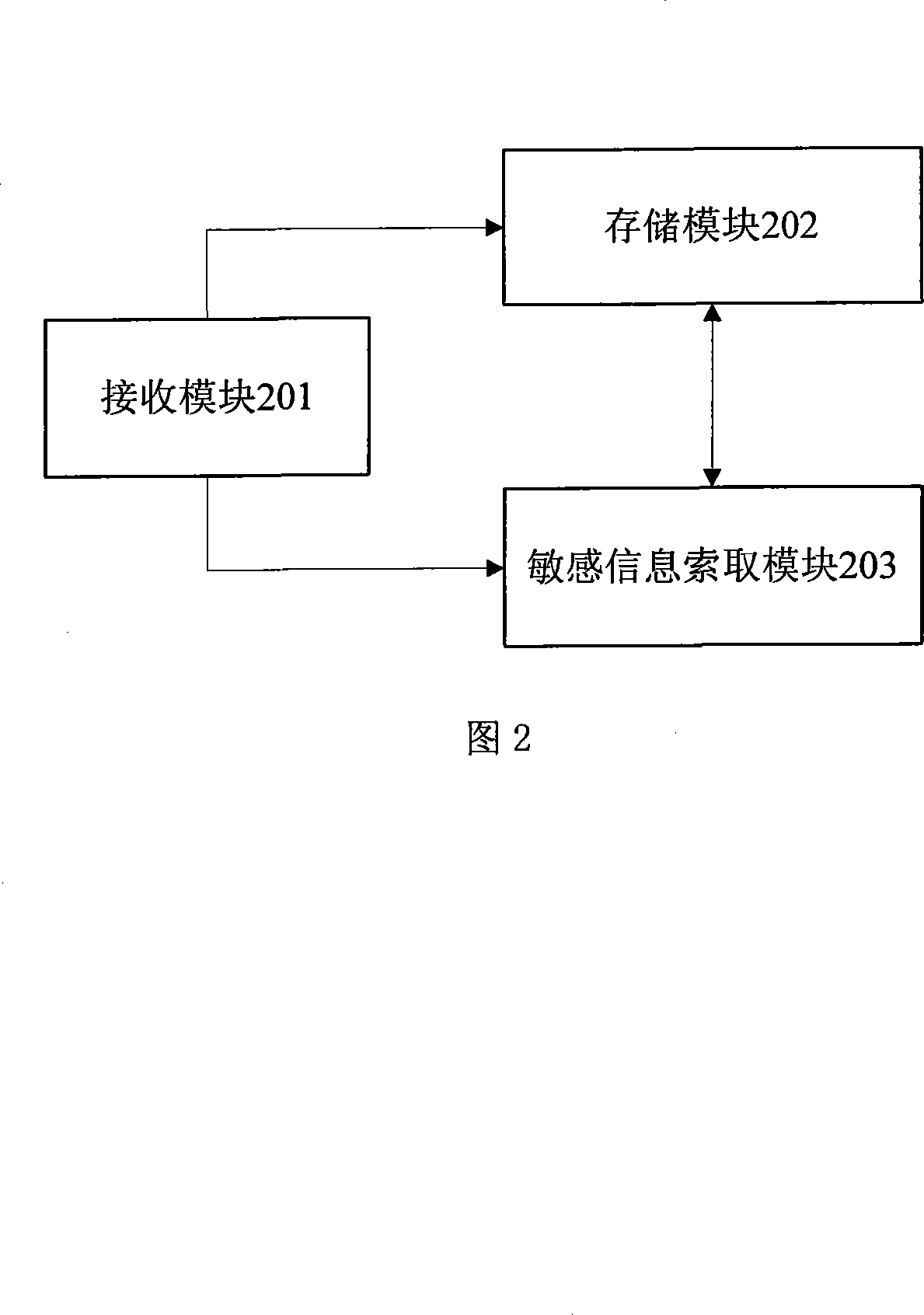
[0082] This embodiment provides a storage device that restricts reading of sensitive information. As shown in FIG. 2, the storage device includes:
[0083] The receiving module 201 is configured to receive instructions and forward the received instructions to corresponding modules;
[0084] The storage module 202 is configured to store the sensitive information in the instruction after receiving the instruction to write the sensitive information forwarded by the receiving module 201;
[0085] The sensitive information requesting module 203 is configured to read a piece of sensitive information from the storage module 202 after receiving the requesting instruction forwarded by the receiving module 201, and delete the read sensitive information.
[0086] The sensitive information is specifically one or more of codes, keys, serial numbers, user passwords, user identifications, and user permissions. The content of each piece of sensitive information may be completely the same or ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com