Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
80results about How to "Not attacked" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
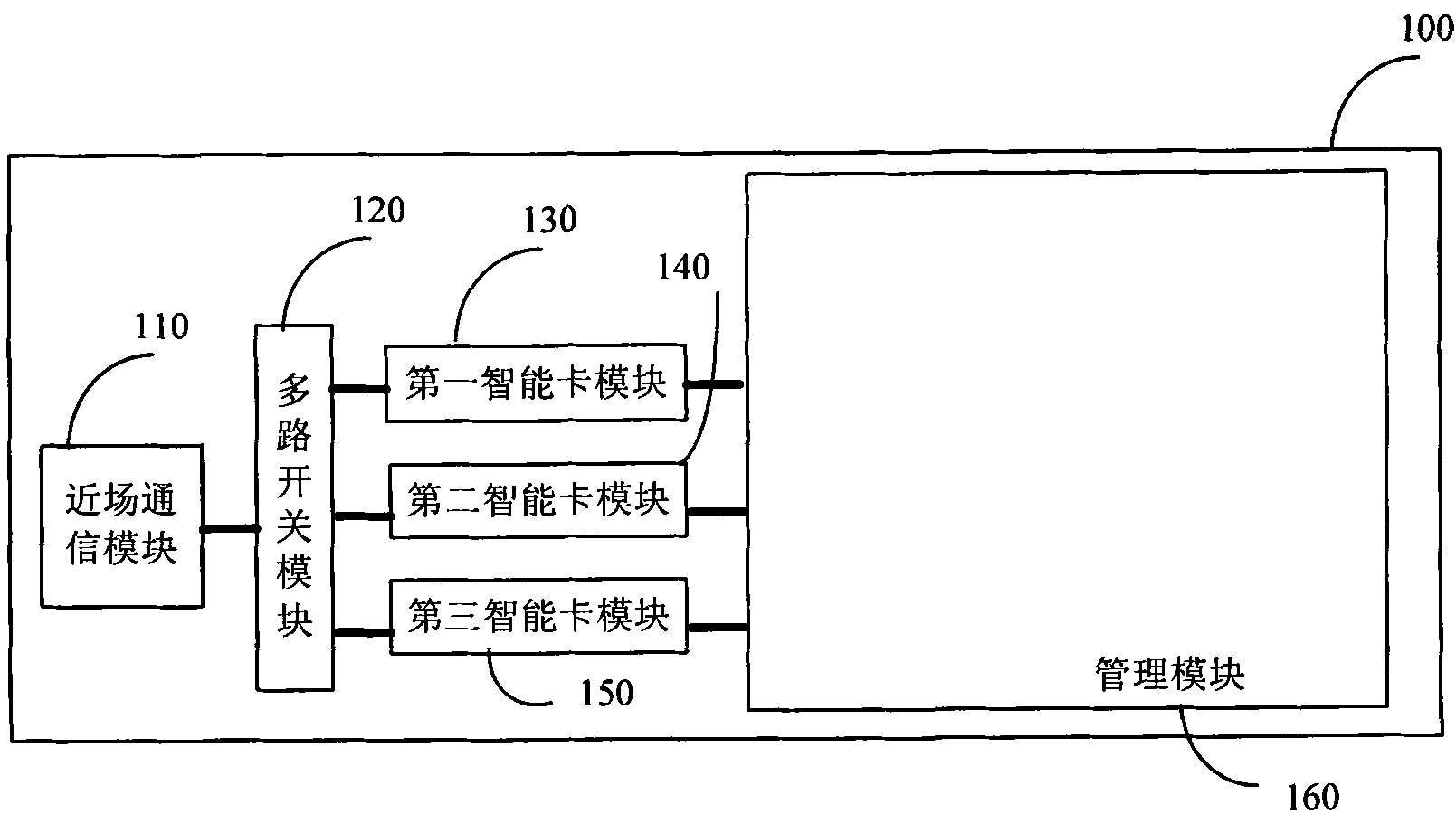
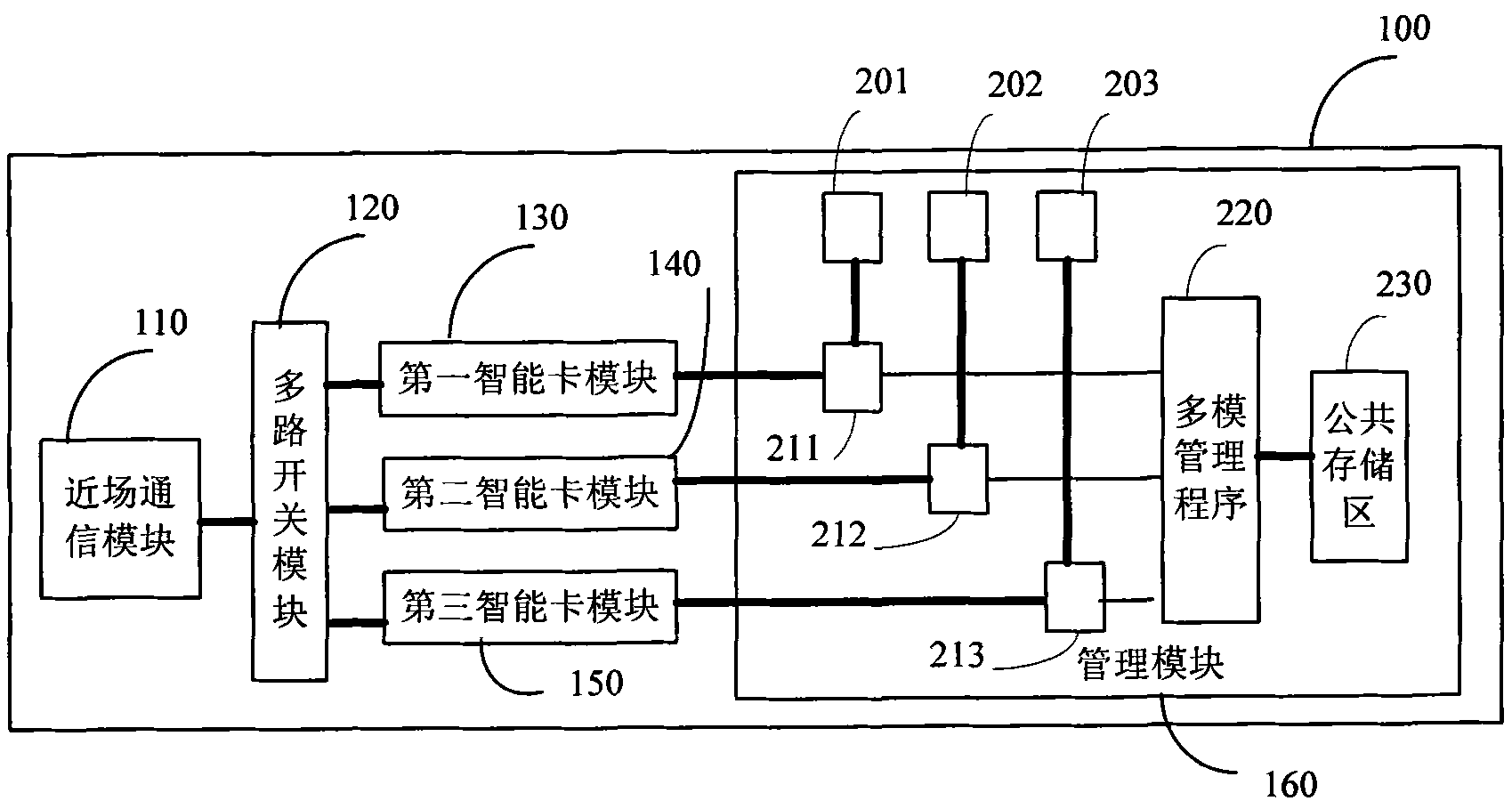
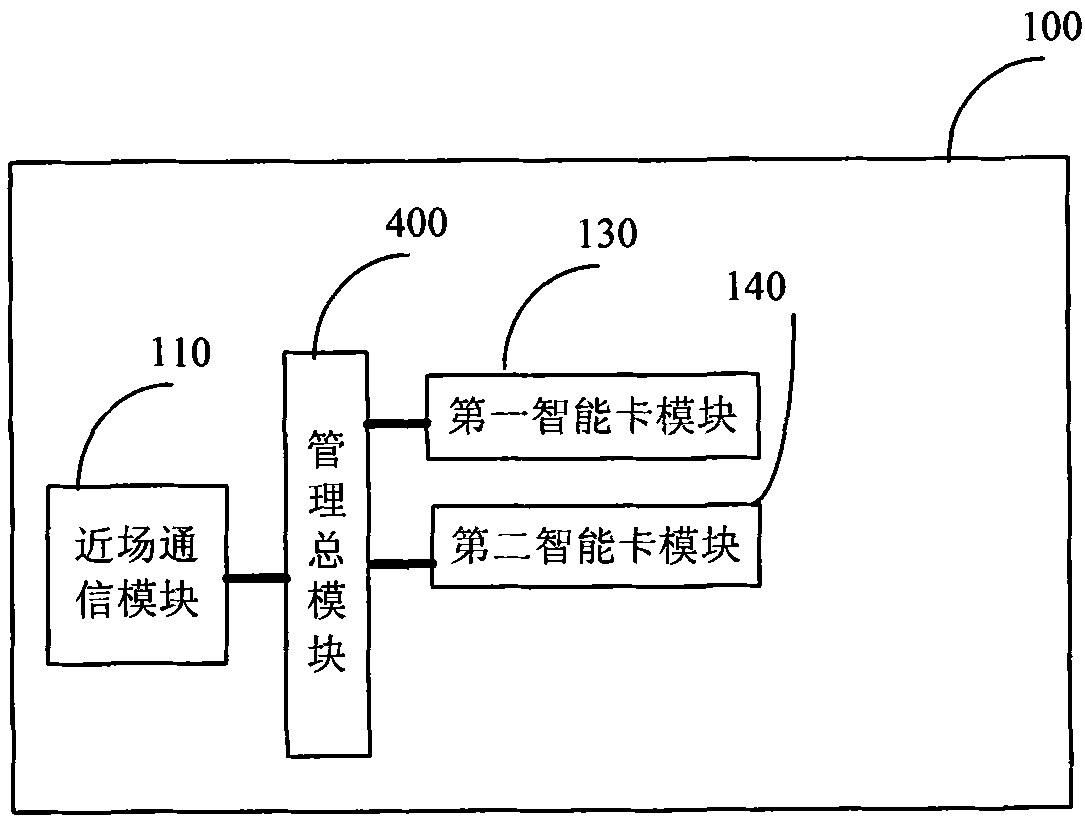
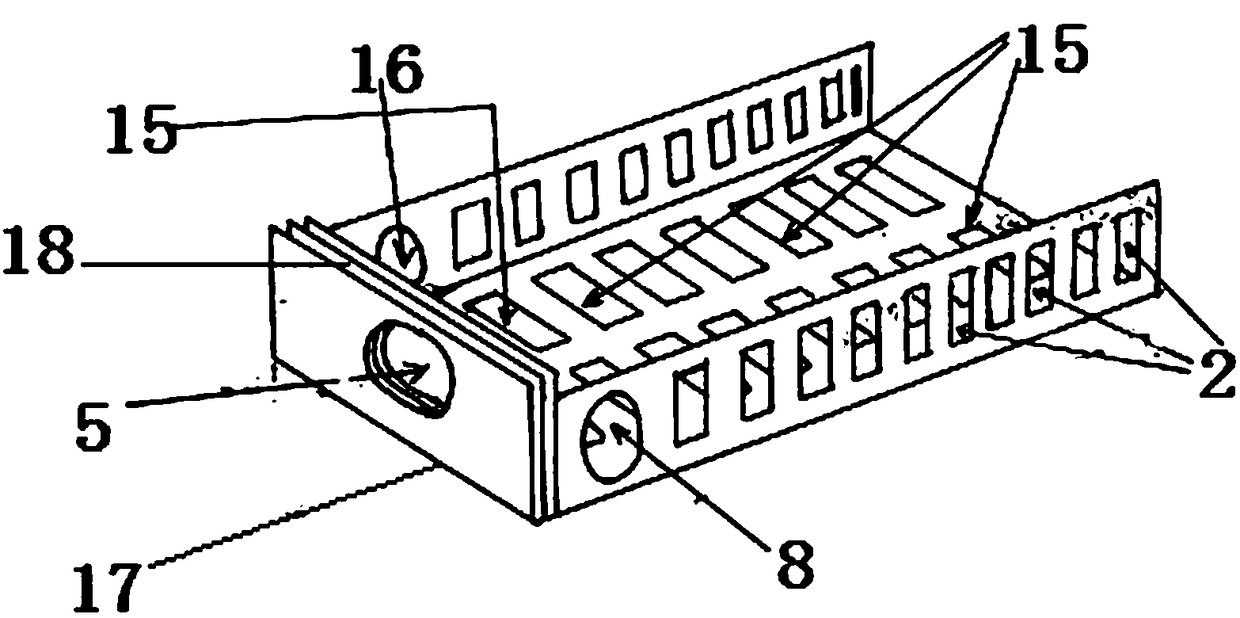
Mobile terminal and method for near-field communication thereof
ActiveCN101771754AImplementation supportAchieve integrationSubstation equipmentWireless communicationSmart cardNear field communication
The embodiment of the invention provides a mobile terminal and a method for near-field communication thereof. The mobile terminal comprises a near-field communication module, a first intelligent card module, a second intelligent card module and a management module. The near-field communication module is used for transmitting near-field communication data, the first intelligent card module is used for providing a first working mode of the mobile terminal according to the type of a first intelligent card, and the second intelligent card module is used for providing a second working mode of the mobile terminal according to the type of a second intelligent card. The management module is used for switching the connection between the near-field communication module and the first intelligent card module to the connection between the near-field communication module and the second intelligent card module, so as to lead the mobile terminal to be switched from the first working mode to the second working mode. The embodiment of the invention not only can be compatible to NFC intelligent cards in various modes, but also can ensure independence and safety of the various modes.
Owner:LENOVO SOFTWARE
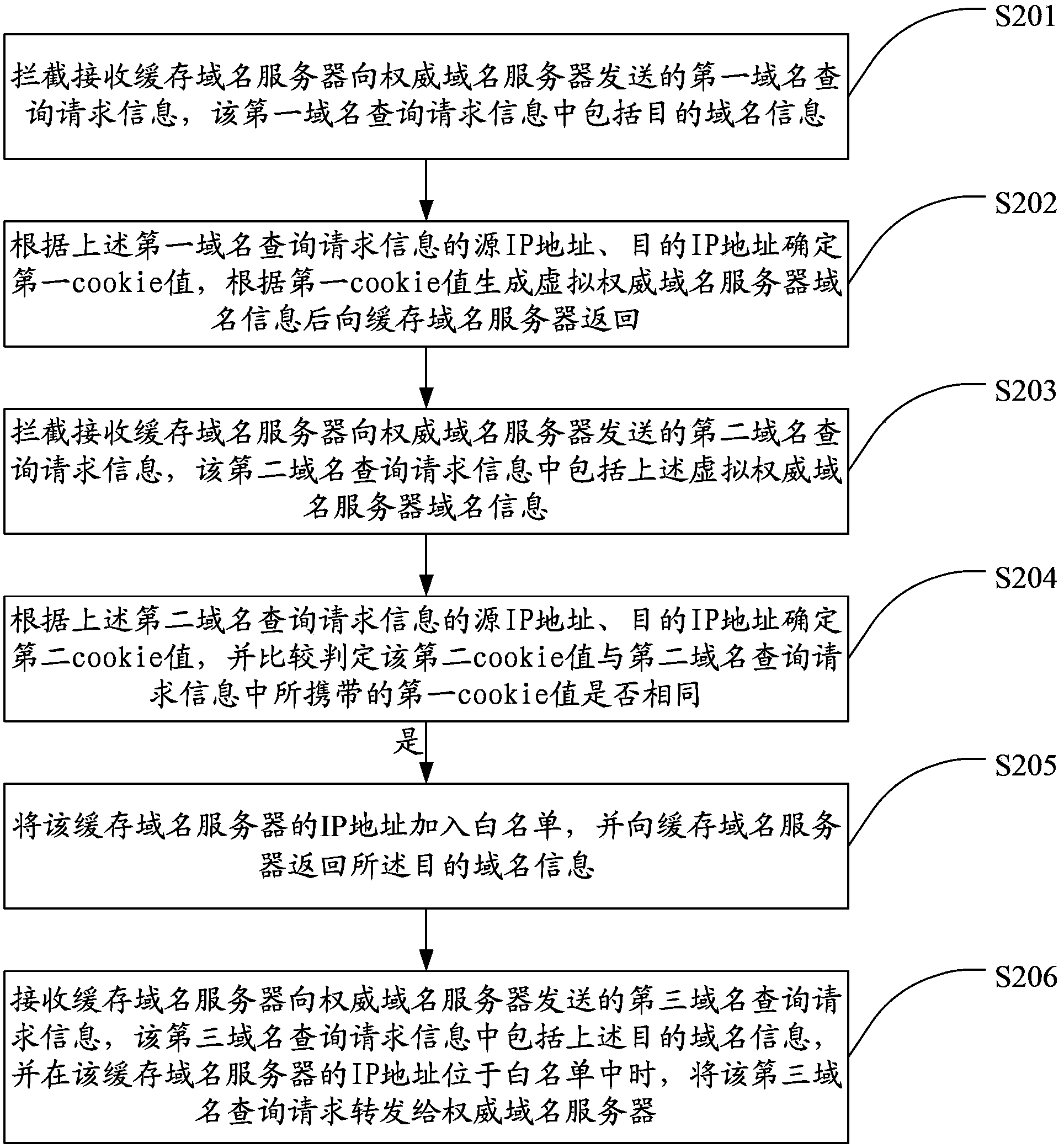
Method and system for detecting false attack sources
The invention provides a method and system for detecting false attack sources. The method includes the steps that first domain name query request information sent by a cache domain name server to an authoritative domain name server is intercepted and received; a first cookie value is determined according to the source IP address and the destination IP address of the first domain name query request information, and virtual domain name information of the authoritative domain name server is generated according to the first cookie value and then sent back to the cache domain name server; second domain name query request information sent by the cache domain name server to the authoritative domain name server is intercepted and received; a second cookie value is determined according to the source IP address and the destination IP address of the second domain name query request information, and the second cookie value is compared with the first cookie value carried by the second domain name query request information. According to the method and system for detecting false attack sources, the false attack sources can be accurately recognized, the authoritative domain name server can be effectively protected from attack by false IP sources and can normally work, and normal domain name query requests can not be affected.
Owner:SHENZHEN TENCENT COMP SYST CO LTD
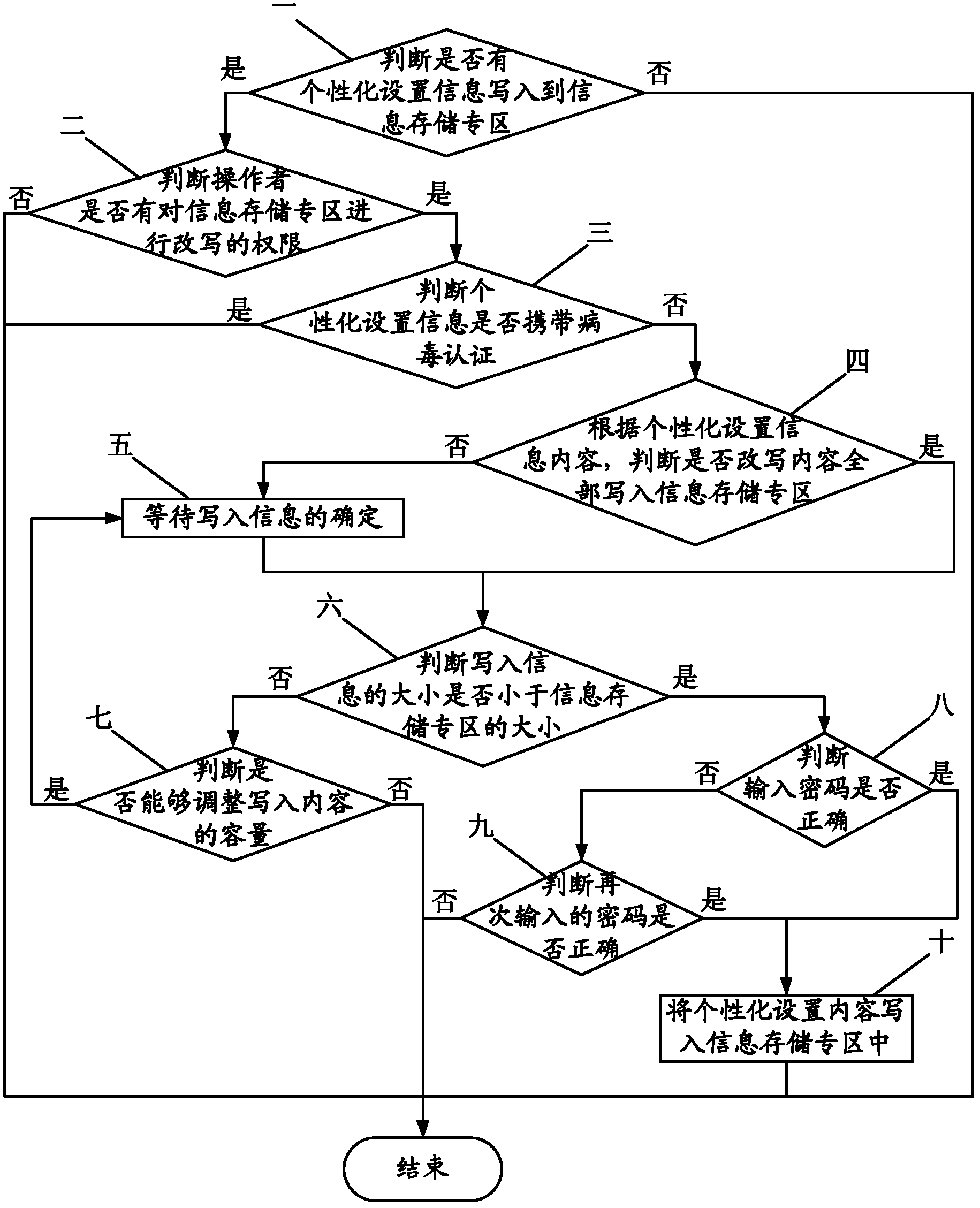
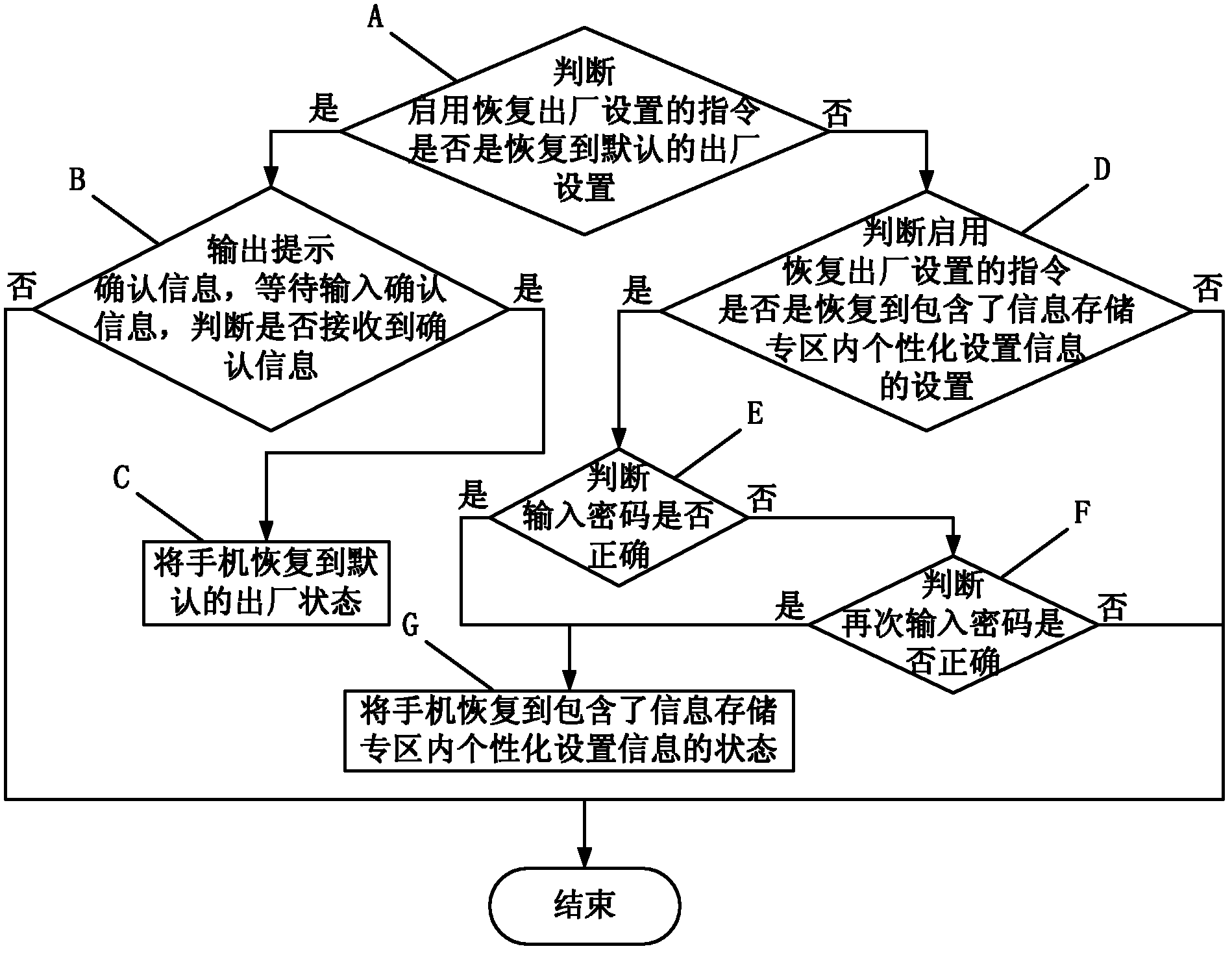
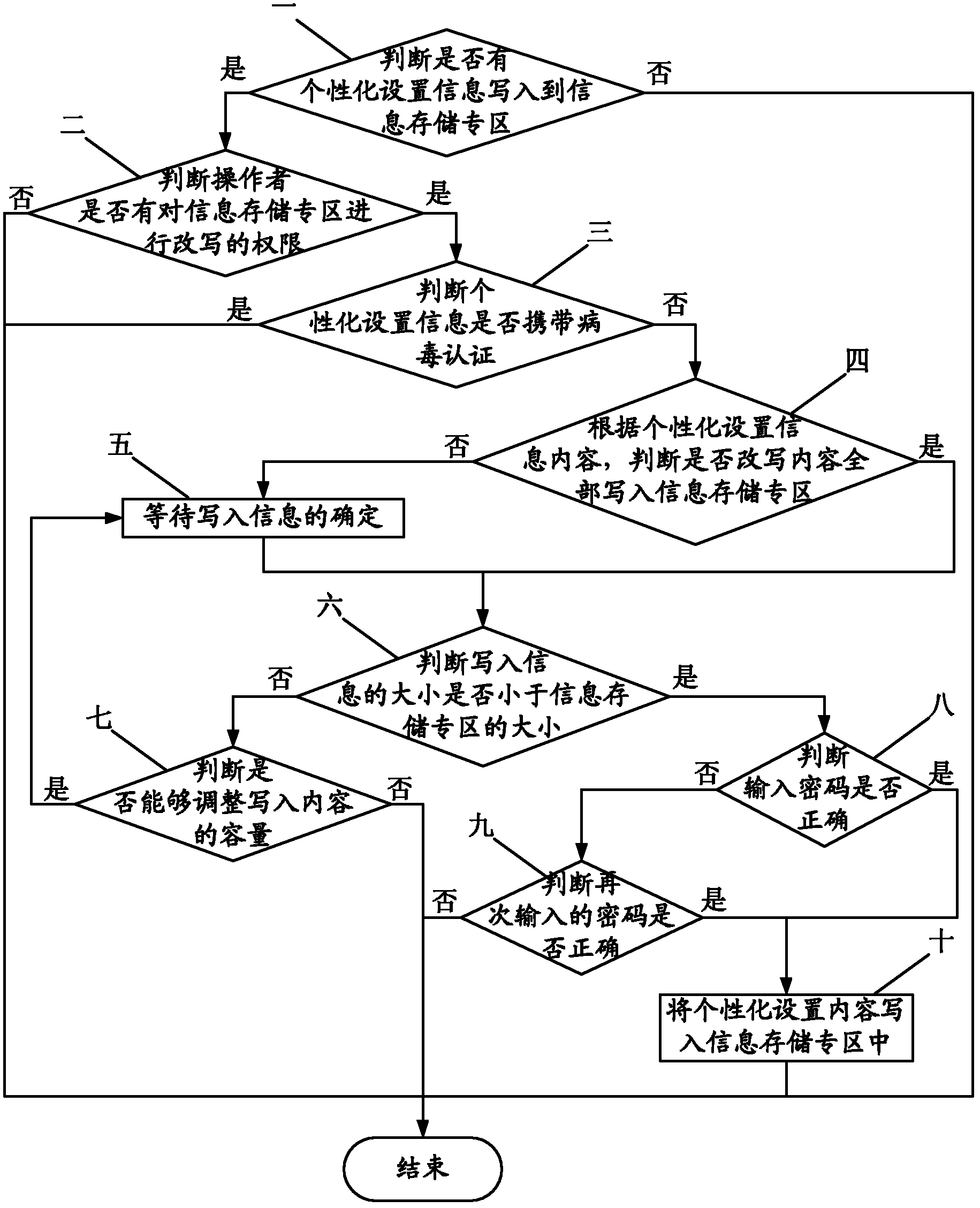
Method for personably customizing restore factory setting of mobile phone
InactiveCN102223441AEnsure safetyNot attackedUser identity/authority verificationSubstation equipmentPersonalizationPassword
The invention relates to the technical field of communication, in particular to a method for personably customizing the restore factory setting of a mobile phone, which aims at furthest reducing the trouble and the loss of the restore factory setting operation of the mobile phone to a mobile phone user. The method comprises the following steps that a special information memory area is set in a flash memory or a memory medium of the mobile phone; when a written-in personalized setting exists, the user has the right to set information content according to personalization under the condition that viruses are not carried, all the rewritten contents are written into the personalized setting memory area, the size of the personalized setting information content is adjusted, a password is determined to be correct, and then, the personalized setting content is written in the special information memory area; and finally, the restore factory setting operation is started on the mobile phone, and two choices of restore default factory setting and restore the setting containing the personalized setting information in the special information memory area are provided. The method disclosed by the invention can remain the personalized customized content when ensuring that the viruses can be thoroughly eliminated.
Owner:李海军
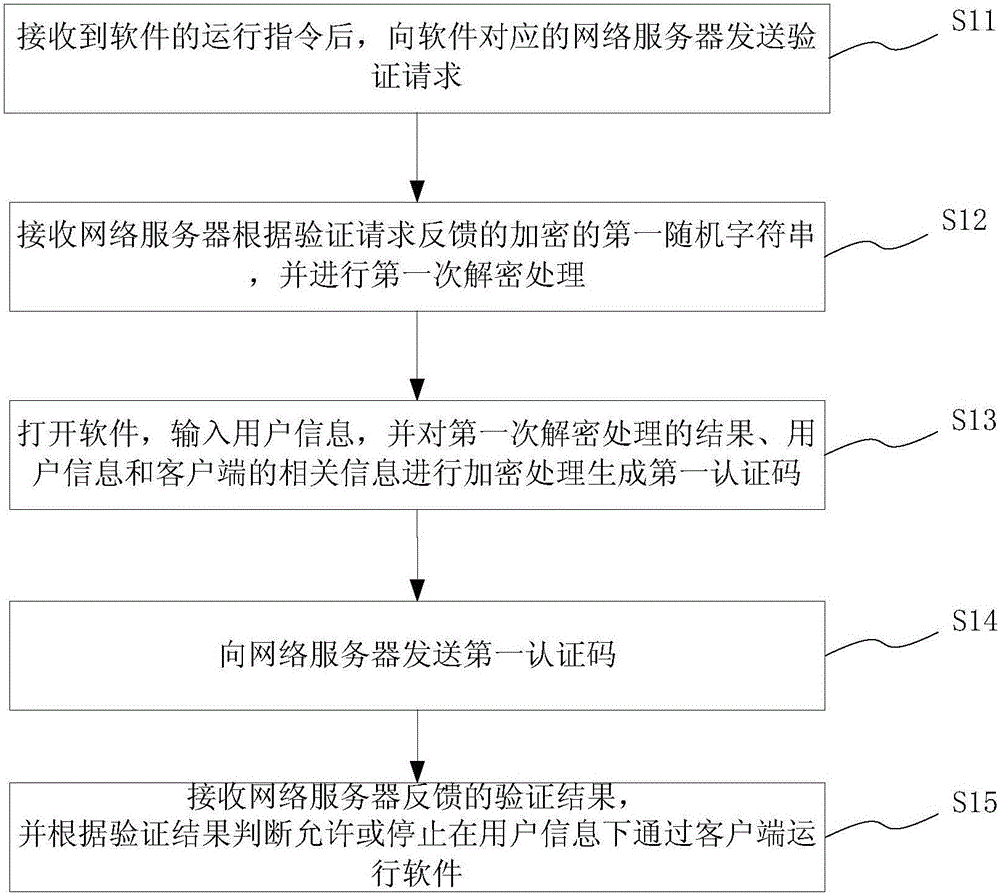
Software network authentication binding method and system
The present invention provides a software network authentication binding method and system, which are executed by the cooperation of the client and the network server: when the software is running on the client, it sends a verification request to the network server; according to the verification request, the network server randomly generates the first Random character strings, encrypted and fed back to the client; the client performs the first decryption process, and encrypts the decryption result, user information and client machine code to generate the first authentication code, and sends the first authentication code to the network Server; the network server performs a second decryption process on the first authentication code, and verifies the result of the second decryption process, and feeds back the verification result to the client. Run the software through the client. The invention not only protects the network server from the attack of the pirated software, but also protects the software from the attack of the counterfeit server, and improves the reliability of the legal authentication of the software.
Owner:MEDELI ELECTRONICS SHANGHAI
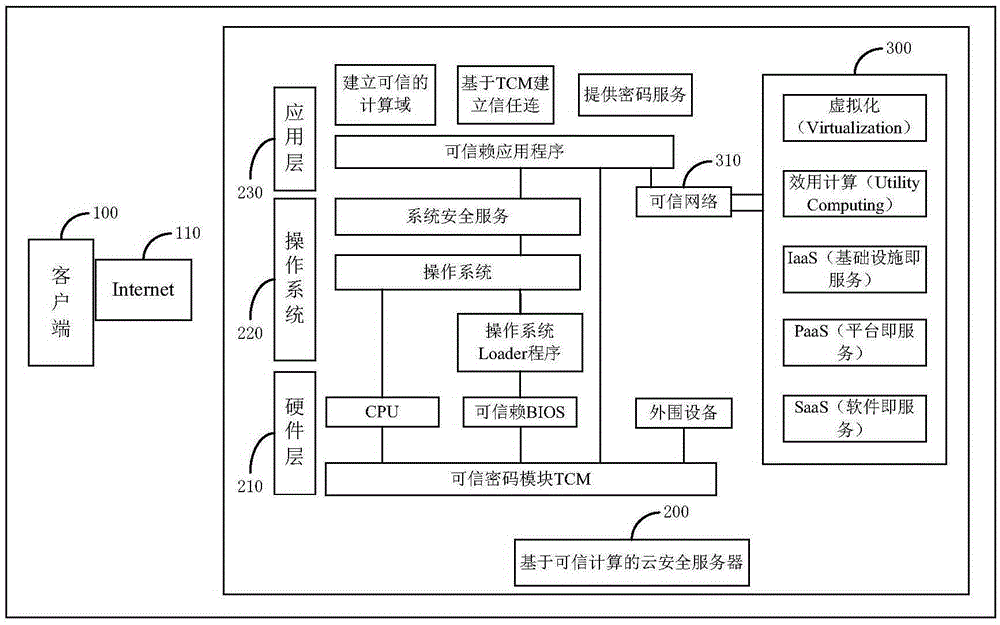
Cloud security server based on trusted computing
InactiveCN106656915ANot attackedImmune to malicious alterationTransmissionTerminal equipmentTrusted Computing
The invention combines a trusted computing technology, and aims at security holes of an existing server, proposes a cloud security server based on trusted computing. The cloud security server includes two parts, i.e., a Trusted Cryptography Module (TCM) and a cloud security server. In various service modes of cloud computing, through the TCM which adopts trusted computing, security of software and hardware environment is measured, and a server system is guaranteed from not being attached by Trojan and viruses and from not being maliciously modified by a hacker; the TCM can also be used for a secret key for protection, storage and data security encryption, thereby performing encrypted protection; and the TCM can also be used for information of identify authentication and attribute authentication, and when a terminal device accesses the cloud security server, the TCM is used for attribute information of identity authentication.
Owner:深圳耀东安全科技有限公司
Fire rescue and extinguishing system for super high-rise building
ActiveCN107261347AEffective rescueEffective diversion avoidanceFire rescueBuilding rescueRadiation sensorEngineering
The invention relates to a fire rescue and extinguishing system for a super high-rise building. A window cleaning machine is arranged on the super high-rise building needing rescue. The window cleaning machine is connected with a window cleaning machine basket which is connected with a pedestrian pedal and a stabilizing rod. The window cleaning machine basket is provided with a smoke flow guide plate. The bottom of the smoke flow guide pipe is provided with a center drainage hole, a water distributor, a radiation sensor and a temperature sensor. The super high-rise building needing rescue is provided with an underground fire water pool which is connected with a fire water monitor and a roof fire water tank. The roof fire water tank is connected with an electric control water mist spray head which is connected with the radiation sensor and the temperature sensor. Trapped persons can be effectively rescued; the fire water monitor, the electric control water mist spray head, a fire water supply connector, the temperature and radiation sensors, the water distributor and other safety protection measures and arranged, and therefore safety, fire control and fire extinguishing are ensured; high-temperature smoke can be guided and avoided, and it is ensured that an evacuation exit is not invaded by smoke; and a buffer facility is arranged to prevent persons from falling and used as a rescue air cushion.
Owner:CHINA RAILWAY CONSTR GROUP +1
Attenuated Salmonella pullorum and application thereof
InactiveCN102154184ALow toxicityImproving immunogenicityAntibacterial agentsBacteriaHorizontal transmissionMicroorganism
The invention discloses an attenuated Salmonella pullorum and application thereof. By using gene knockout technology, the in vivo colonization gene and the main virulence gene of Salmonella pullorum are deleted, thus obtaining an dual-gene-deleted attenuated Salmonella pullorum SM091-DED strain; and the microbiological preservation number of the strain is CGMCC NO.4604. The virulence of the attenuated Salmonella pullorum disclosed by the invention is obviously reduced, and the in vivo colonization time is short after the attenuated Salmonella pullorum is inoculated into a host; the herd infection test shows that the attenuated Salmonella pullorum has no horizontal transmission capability; the attenuated Salmonella pullorum provides full cross protection for homotype and allotype high-virulence Salmonella pullorum; and after SPF (Specific Pathogen Free) chicks are immunized, the infection of the high-virulence strain can be effectively eliminated, and the herd infection can not be caused. Thus, the invention provides a safe, fine-immunogenicity and low-virulence Salmonellosis avium attenuated live vaccine for preventing Salmonellosis avium.
Owner:HARBIN VETERINARY RES INST CHINESE ACADEMY OF AGRI SCI
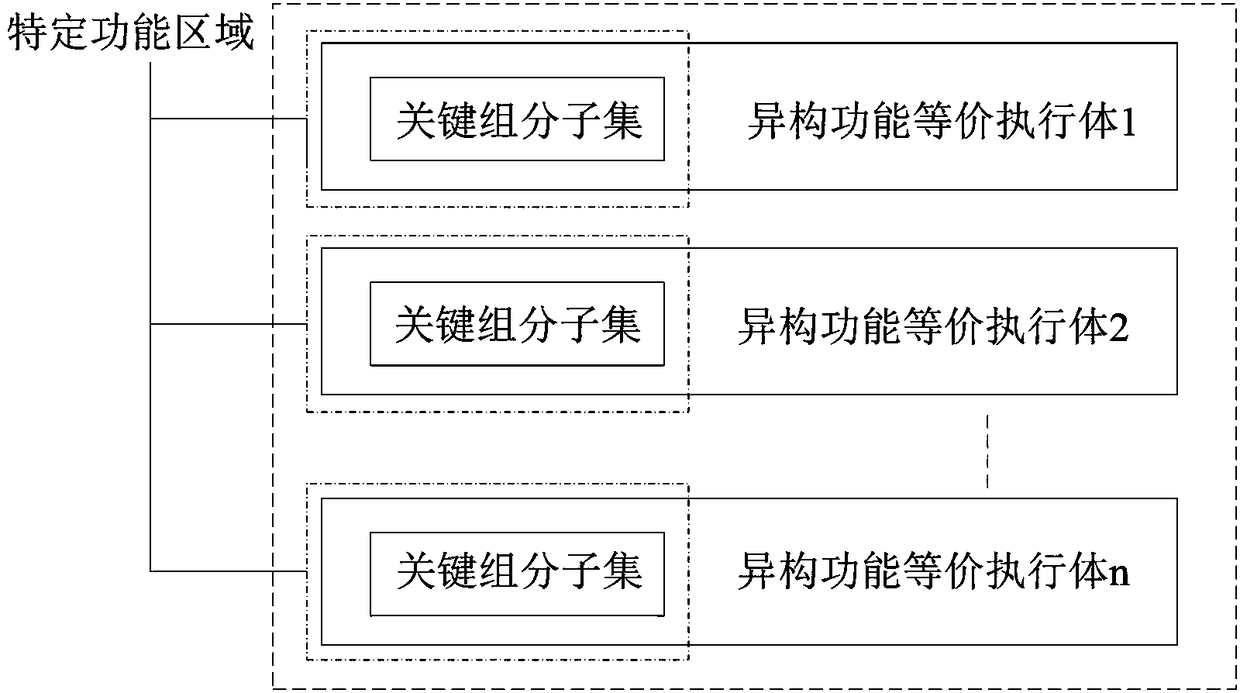
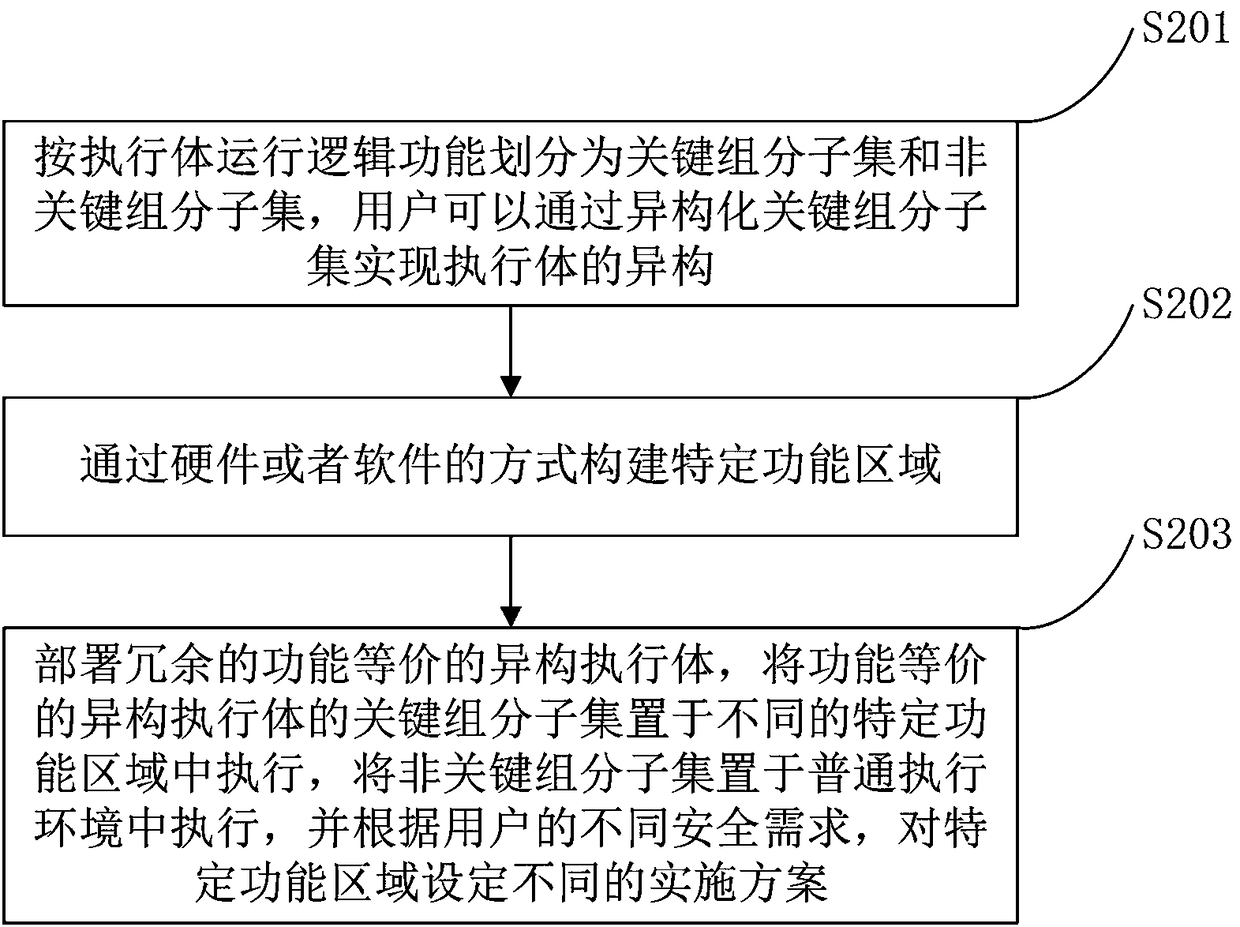
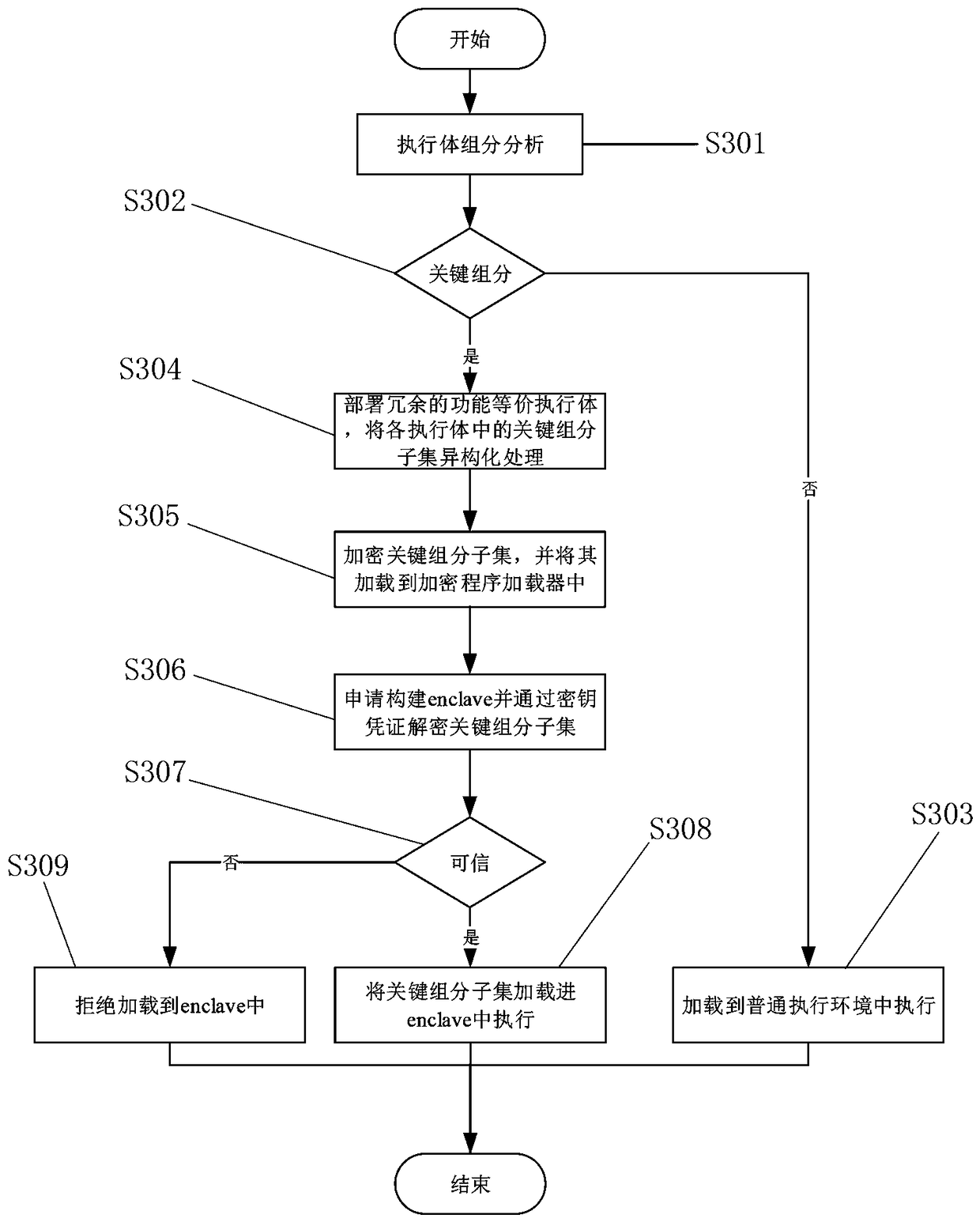
Implementation method for isomerizing function-equivalent executers
ActiveCN108366049AReduce the cost of isomerization implementationNot attackedTransmissionComputer architectureSpecific function
The invention belongs to the technical field of network security, and particularly relates to an implementation method for isomerizing function-equivalent executers. The implementation method comprises the steps that firstly, key component subsets, non key component subsets and isomerized key component subsets are obtained through partitioning according to the operation logic functions of the executer; secondly, specific function areas are constructed through a hardware or software mode; and finally, redundant function-equivalent isomerized executers are deployed, the key component subsets ofthe function-equivalent isomerized executers are placed in different specific function areas to be executed, and different implementation schemes are set for the specific function areas according to different security requirements of users. The method is suitable for the executer scenes with the simple function structure and particularly suitable for the executer scenes with the complex function structure and can protect the executers from being attacked by malicious software.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
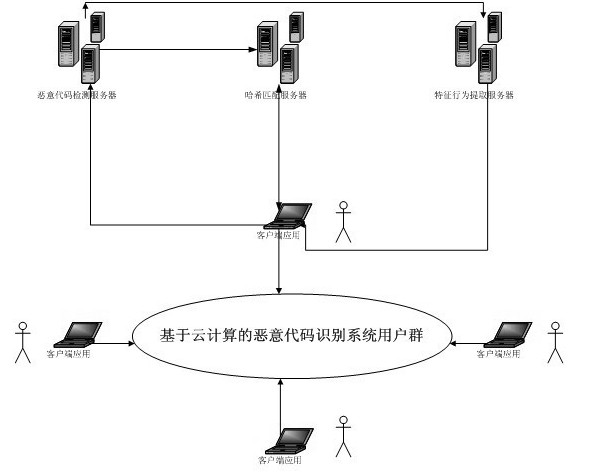
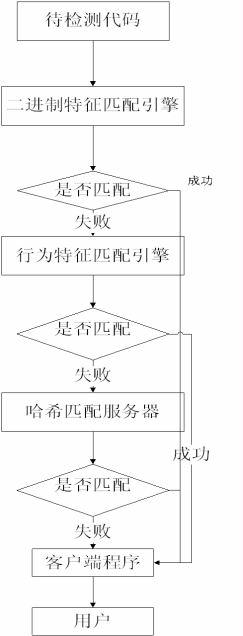
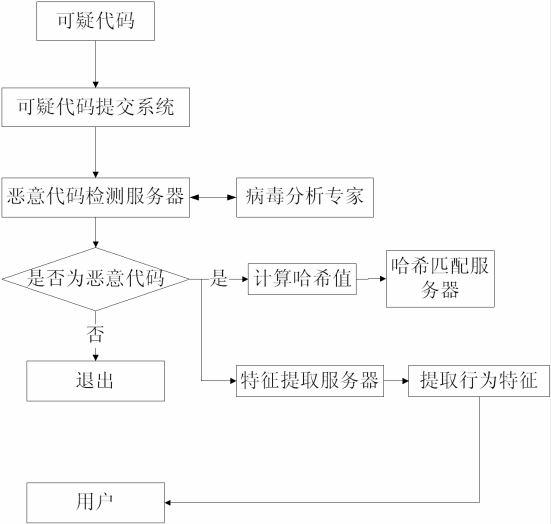
Malicious code recognition method based on cloud computing
InactiveCN102664884AReduce false alarm rateAccurate identificationPlatform integrity maintainanceTransmissionCloud computingFeature code
Owner:NANJING UNIV OF POSTS & TELECOMM
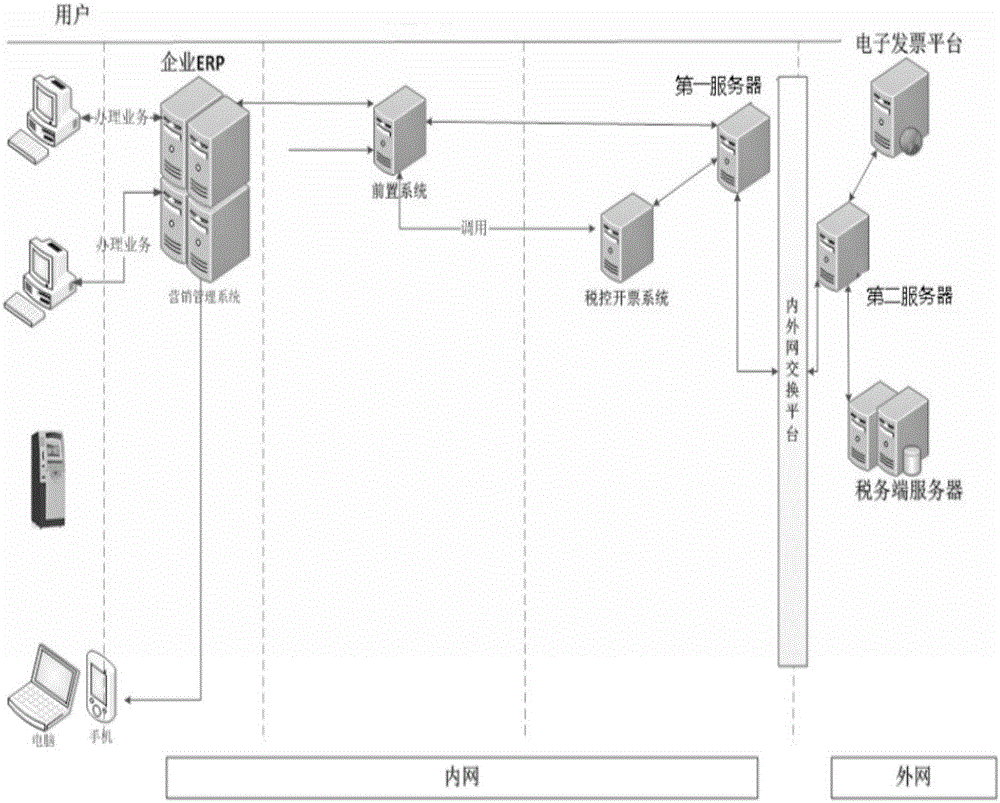
System and method for safely transmitting electronic invoice from ERP (enterprise resource planning) system to internet
InactiveCN106779891AStable deliveryAchieve deliveryDigital data protectionBilling/invoicingInformation transmissionInvoice
The invention discloses a system and a method for safely transmitting an electronic invoice from an ERP (enterprise resource planning) system to an internet. The system is used between the ERP system and a proxy server, the ERP system is used for transmitting billing information to a front system, the front system is used for checking received data and transmitting the data to a data exchange platform, the data are decrypted by a data root standard protocol and transmitted to the proxy server, the data are decrypted by the proxy server and then transmitted to an extranet, data returned from the extranet are received by the proxy server, and the electronic invoice is finally returned to the ERP system in an original route mode. Electronic invoice transmitting rapidness and convenience are improved, the billing link of the electronic invoice needs to be performed from an intranet to the extranet, and the problem of incapability of ensuring safety of transmitting the data from the intranet to the extranet is solved.
Owner:GUIZHOU POWER GRID INFORMATION & TELECOMM
Liquid-type dentifrice composition contained silver particles and mousse-type dentifrice using the same
InactiveCN101547679AImprove aestheticsQuality improvementCosmetic preparationsToilet preparationsBrush toothSucrose
Disclosed are a liquid type dentifrice composition primarily containing silver particles which is drawn out in foam state when used to brush teeth to prevent the liquid dentifrice from flowing down during tooth-brushing, resulting in effective and convenient tooth-brushing function and exhibit bactericidal action and protect mouth and teeth from periodontal disease and other mouth diseases because of original properties of silver ingredients in the dentifrice composition; and, in addition to, a mousse type dentifrice formulation using the same that improves aesthetic property and product quality thereof. The inventive dentifrice composition primarily containing silver particles useful for mouthwash comprises: at least one surfactant selected from a group consisting of 0.5 to 3% by weight of SQdium lauryl sulfate, 0.05 to 1% by weight of sodium sarcosine laurate, 0.5 to 5% by weight of alkyl polyglucoside and 0.5 to 3% by weight of sucrose fatty acid ester; at least one wetting agent selected from a group consisting of 30 to 80% by weight of sorbitol solution and 0.5 to 5% by weight of glycerine; at least one solubilizing agent selected from a group consisting of 0.1 to 1% by weight of hydrogenated polyoxyethylene caster oil and 0.1 to 1% by weight of polyoxyethylene sorbitan monolaurate effective to solubilize flavor and active ingredients; 0.01 to 10% by weight of silver particles with bactericidal action; and the balance of purified water relative to total weight of the composition. The inventive mousse type dentifrice formulation comprising the above liquid dentifrice composition is prepared by steps of: introducing the dentifrice composition comprising silver particles as essential ingredient into a foam generating receptacle with constant capacity; and drawing the composition in foam form through outlet of the receptacle in order to brush teeth.
Owner:金基暎
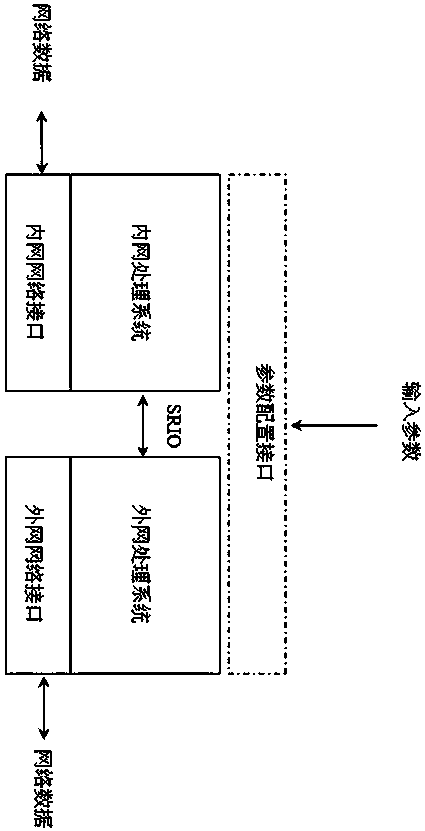
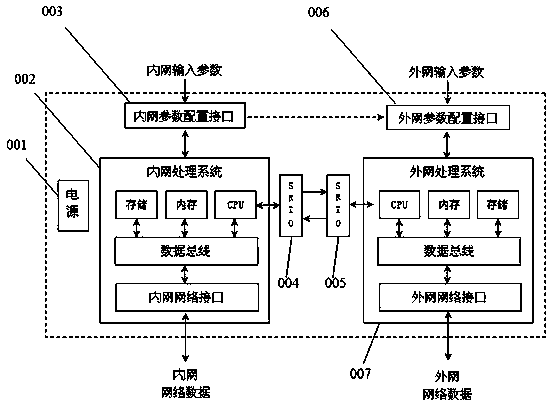
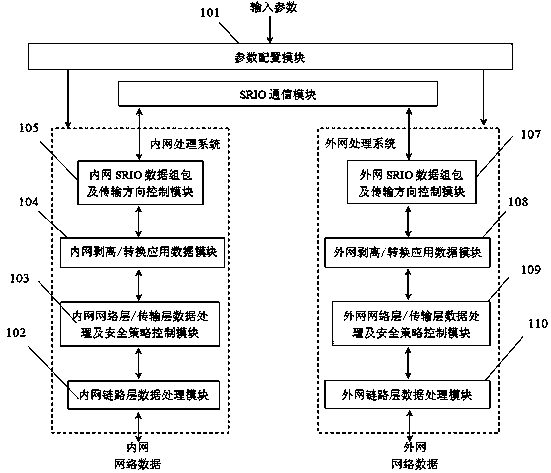
Dual-processing system network safety isolation method based on SRIO interface technology
ActiveCN108055244AAchieve security isolationAvoid Penetrating LinksTransmissionTraffic capacityHigh bandwidth
The invention aims at providing a dual-processing system network safety isolation method which is simple in structure, safe and reliable, high in transmission efficiency, enough in bandwidth and capable of realizing one-way or two-way safety isolation and based on the SRIO interface technology. The method comprises the following steps: unloading a network protocol stack to completely eradicate thepenetrability link of a network protocol, thereby realizing the one-way data safety isolation transmission or controllable two-way data safety isolation transmission of the network regions in different safety levels; since the SRIO technology supports the chip direct interconnection way, the logic layer supports the direct IO / DMA and message transfer, thereby obviously lightening the CPU load, and greatly improving the network data transmission efficiency , and the data safety isolation communication with 10G bandwidth can be realized. The method is suitable for the network boundary of the one-way or two-way safety isolation with high bandwidth traffic requirement, and is applied to the technical field of the computer network safety isolation.
Owner:珠海市鸿瑞信息技术股份有限公司
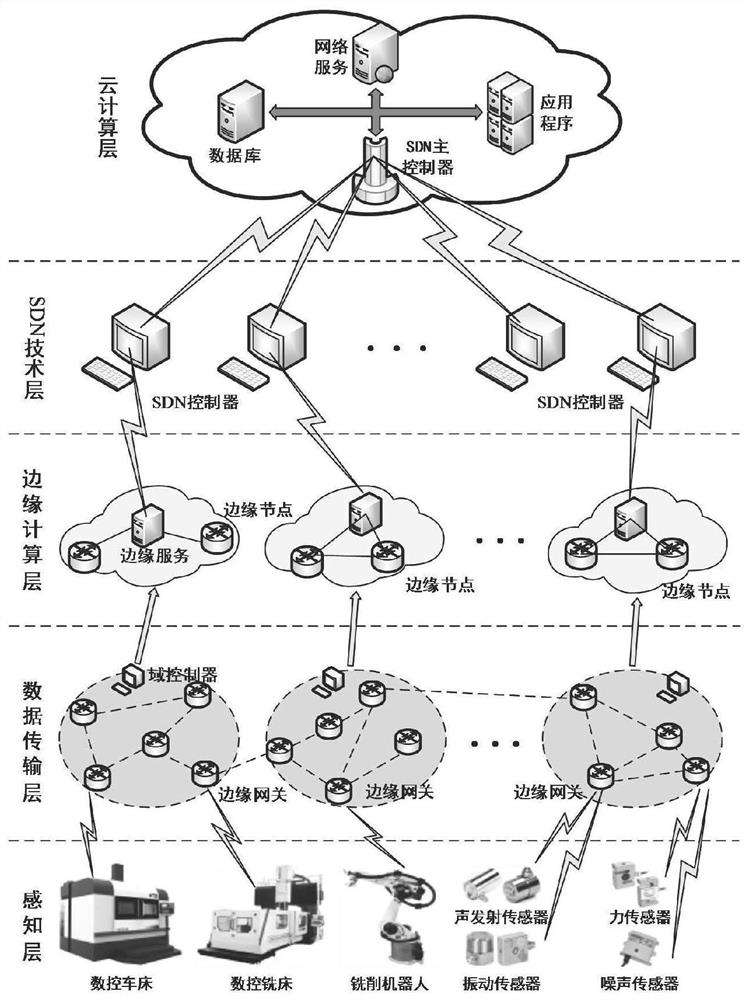
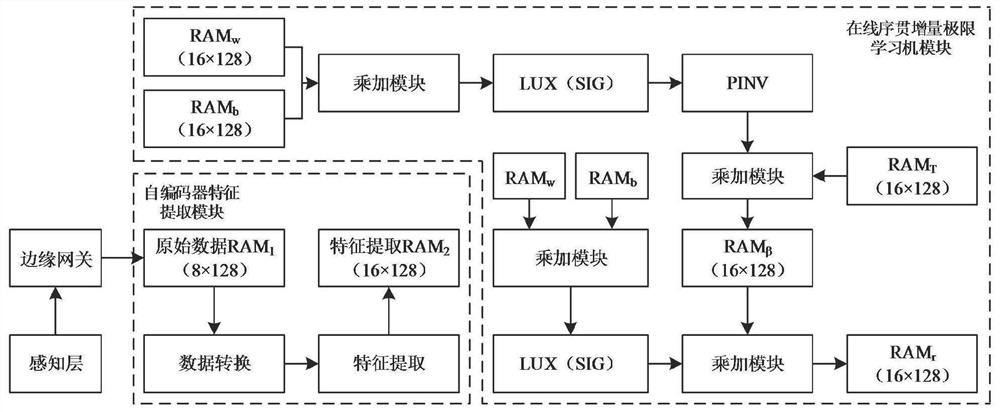
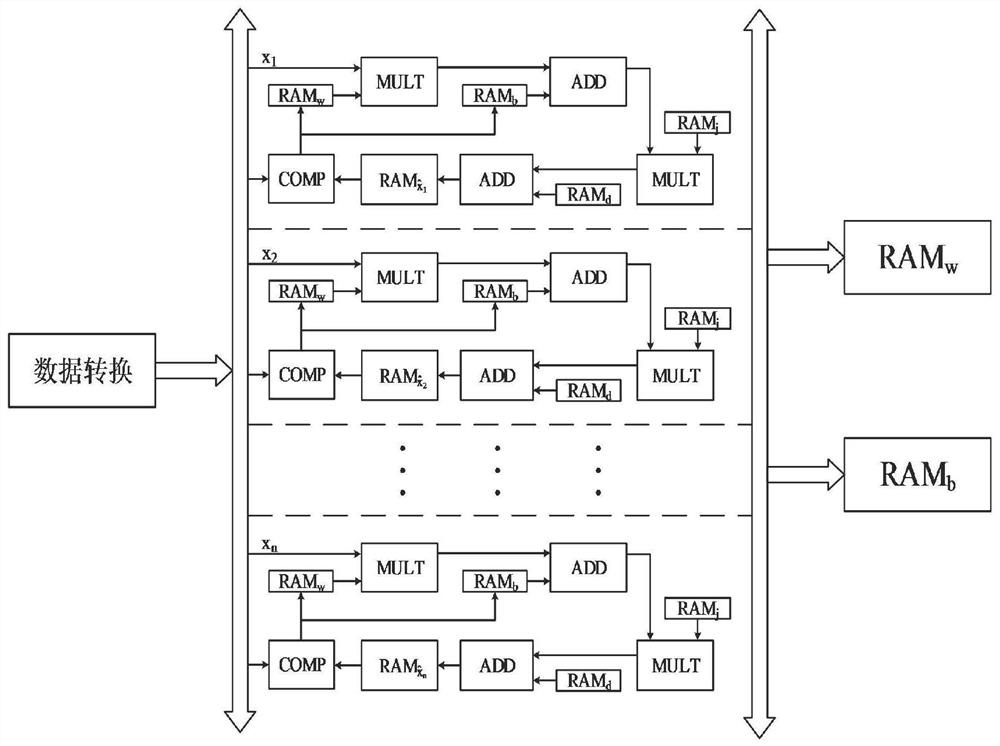
Cutting state edge intelligent monitoring method based on online incremental wear evolution model
ActiveCN111890127AImprove processing speedIncrease transfer speedMeasurement/indication equipmentsNeural architecturesLearning machineGate array
The technology discloses a cutting state edge intelligent monitoring method based on an online incremental wear evolution model. A tool edge intelligent monitoring system is used for acquiring cuttingforce signals, vibration signals and acoustic emission signals in the machining process of machining equipment in real time; a wireless data transmission network is established, a data transmission path is controlled with a domain controller, and finally data is transmitted from a sensing layer to an edge computing layer; the data is preprocessed with a Field Programmable Gate Array (FPGA) hardware system of the edge computing layer to obtain a training sample, an internal topological structure of an online sequential increment extreme learning machine is determined by combining the feature number and the sample number of the training sample, and finally the data acquired by a sensor is transmitted to the trained edge computing layer under the same working condition; a real-time monitoring result is sent to a cloud computing layer by utilizing an SDN technology layer in the tool edge intelligent monitoring system; and a tool wear monitoring result is applied by using an application service in the cloud computing layer. The technology has high real-time performance, good accuracy and strong data processing capability.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
Queen bee cage
The invention relates to the technical field of bee breeding and discloses a queen bee cage. The queen bee cage comprises a box and a baseplate; a worker bee inlet and a queen bee outlet are formed inthe side face or / and top face of the box, and the bottom of the box can be buckled on a honey comb; the baseplate comprises a movable baseplate body in drawer-type connection with the box and a fixedbaseplate body which is fixed to the bottom of the box and provided with a feeding channel, and a worker bee inlet, a queen bee outlet and a feeding channel are formed in the movable baseplate body and coincide and intersect with the worker bee inlet and a queen bee inlet of the box and the feeding channel in the fixed baseplate body; side grooves for the movable baseplate body to slide in are formed in the two side walls in the box, and side groove clamping ports are formed in the side grooves and matched with tap positions on the movable baseplate body through clamping. By arranging the positions of the side groove clamping ports and the number of side grooves, multiple sets of variable models are formed, in and out of worker bees and a queen bee are controlled, and the queen bee is controlled to eat honey on the comb. According to the queen bee cage, multiple functions of locking, introduction and transportation are integrated, and the queen bee cage is easy to operate.
Owner:雷秋雨
Connection device and data transmission method
ActiveCN108040082ANot attackedMeet reading needsBus networksProgrammable logic deviceProgrammable logic controller
The invention provides a connection device comprising an offline downloading module, a vehicle CAN bus reading module, a programmable logic module and an open CAN protocol module, wherein the vehicleCAN bus reading module is connected with a vehicle CAN bus and the programmable logic module, the open CAN protocol module is connected with the programmable logic module and an Internet of Vehicles terminal, and the offline downloading module is connected with the programmable logic module. A vehicle-mounted terminal and the vehicle CAN bus physically isolated to overcome the information securityproblem resulting from the fact that the existing Internet of Vehicles terminal directly reads CAN bus messages, and the CAN bus data are isolated and protected while the Internet of Vehicles terminal reads the CAN bus data.
Owner:CHANGAN UNIV
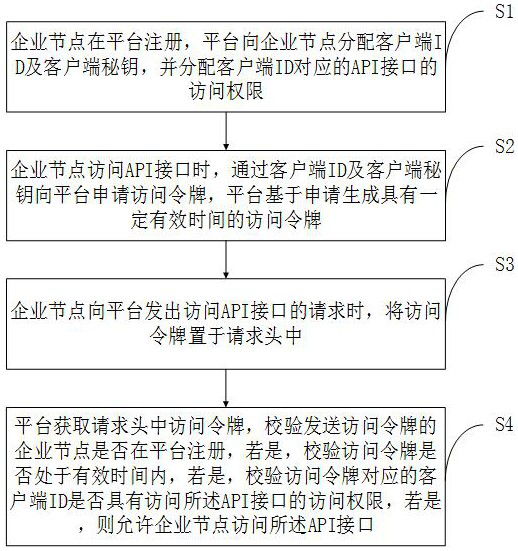
Method for analyzing data authority control based on Handle identification
ActiveCN112417511AEnsure platform securityGuaranteed confidentialityDigital data protectionDigital data authenticationComputer securityEngineering
The invention discloses a method for analyzing data authority control based on Handle identification, which comprises the following steps that: a platform allocates a client ID (Identity) and a clientsecret key to an enterprise node, and allocates access authority of an API (Application Program Interface) corresponding to the client ID; the enterprise node applies for an access token to the platform through the client ID and the client key; when the enterprise node sends a request for accessing the API to the platform, the access token is placed in the request header; and the platform acquires the access token in the request header, verifies whether the enterprise node sending the access token is registered in the platform or not, verifies whether the access token is in effective time ornot if the access token is registered in the platform, verifies whether the client ID corresponding to the access token has the access permission to access the API or not if the access token is registered in the platform, and allows the enterprise node to access the API if the access token is registered. According to the invention, when the enterprise node accesses the identification data throughthe platform open interface, identity recognition needs to be carried out on the accessed enterprise node, so that the platform security is ensured and the enterprise data is prevented from being attacked.
Owner:重庆忽米网络科技有限公司
Automatic ventilation plant
InactiveCN107166617AEasy to useNot attackedSpace heating and ventilation safety systemsLighting and heating apparatusAutomatic controlControl engineering
The invention discloses an automatic ventilation plant. The automatic ventilation plant comprises a plant body. A plurality of ventilation devices capable of ascending and descending are arranged on a roof of the plant body. Each ventilation device comprises a ventilation pipe body, wherein a filtering and dust removing interlayer is arranged in the middle of the ventilation pipe body, the ventilation pipe body is arranged in a through hole of the roof, a step face is arranged above the through hole, annular bosses are arranged at the two ends of the ventilation pipe body, an air inlet / air outlet is formed in the upper end of the ventilation pipe body, and an air outlet / air inlet is formed in the lower end of the ventilation pipe body. A control device is arranged on the side wall of the plant body, the control device controls opening of the air inlets and the air outlets in the ventilation pipe bodies, and a pressure sensor is arranged below each ventilation pipe body. According to the automatic ventilation plant, the top of the plant body is provided with the multiple ventilation devices capable of ascending and descending for ventilation, the ventilation devices are automatically controlled according to the pressure, the temperature and the like in the plant, and the automatic ventilation plant is very convenient to use.
Owner:ZHENJIANG JUNENG ELECTRICAL
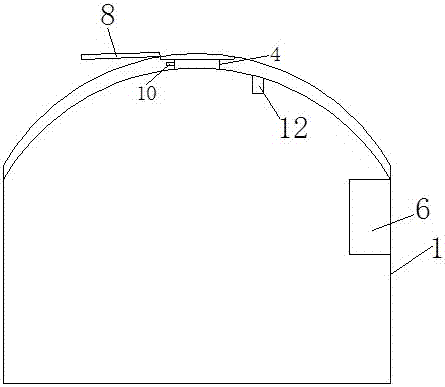
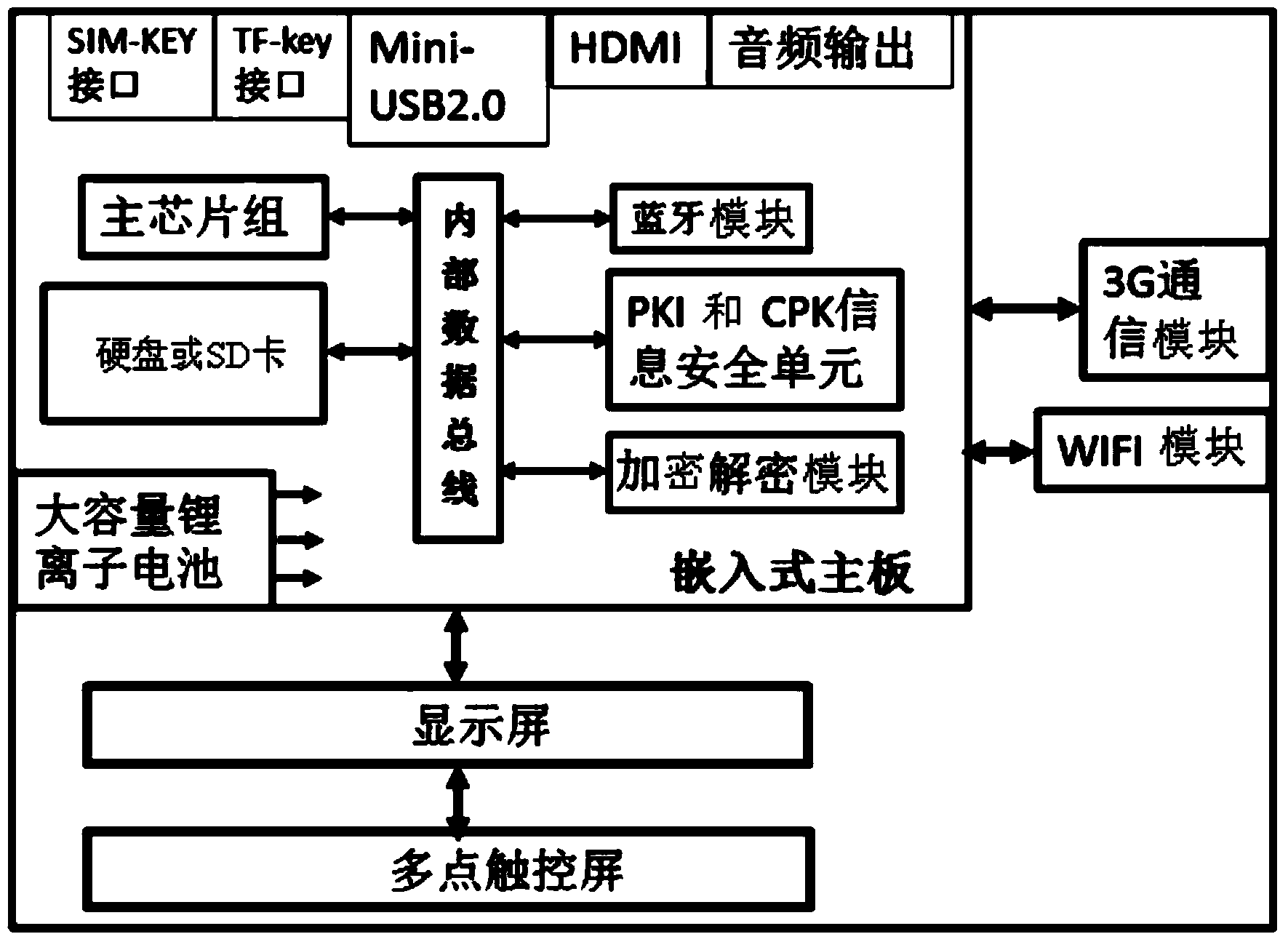
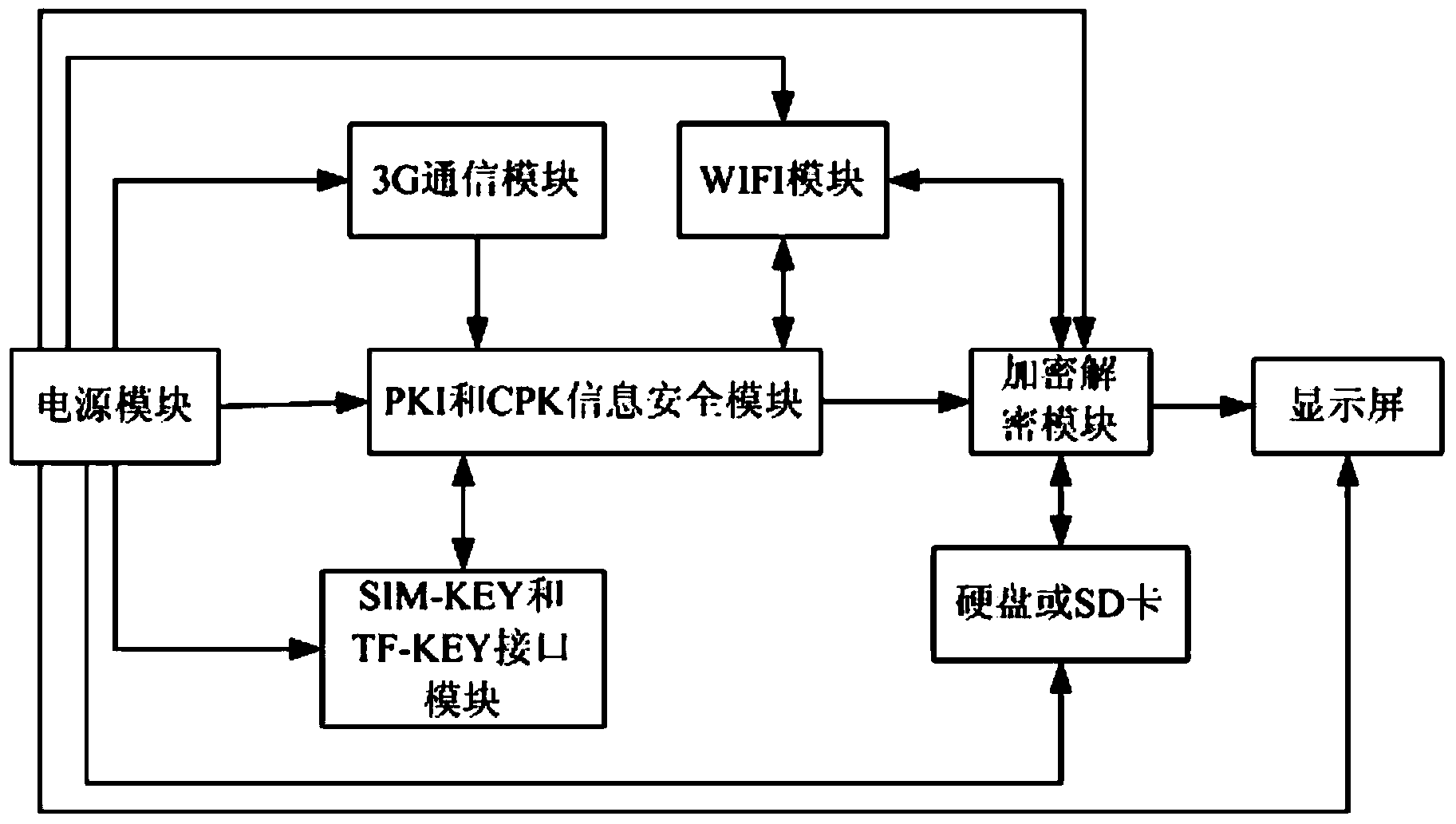
Intelligent PAD with information safety mechanism
InactiveCN103491530AEnsure safetyImplement data encryption and decryption applicationsDigital data processing detailsSecurity arrangementDigital signatureThird generation
The invention relates to an intelligent terminal, in particular to an intelligent PAD with information safety mechanism. The problem that existing intelligent equipment has no information safety mechanism or a digital certificate signature or verification so that during application, information safety cannot be guaranteed is solved. The intelligent PAD comprises a 3G communication module, a PKI and CPK information safety module, an encryption-decryption module, an SIM-KEY and TF-KEY interface module, a touch screen, a display screen and a power supply module. The 3G communication module is connected with an embedded type main board. The power supply module provides power for the modules. The intelligent PAD has information safety mechanism, and the intelligent terminal has safety guarantee on the Internet and in the process of communication and document mail processing. Internet attacking resistance is achieved, a digital certificate is achieved, the digital signature and verification are achieved, and information safety is guaranteed.
Owner:LIAONING XINCHANGCHENG INFORMATION TECH RES & DEV
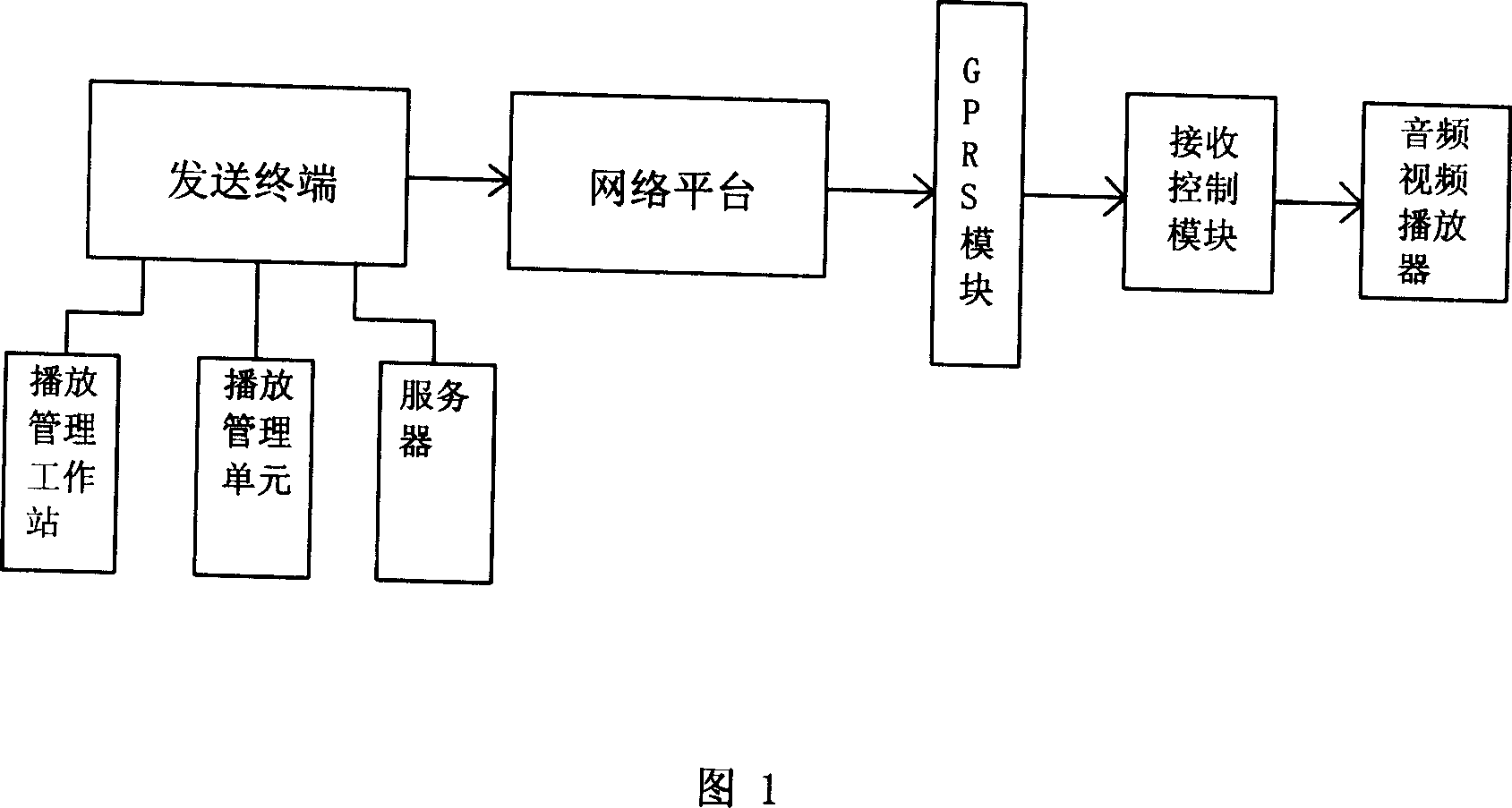
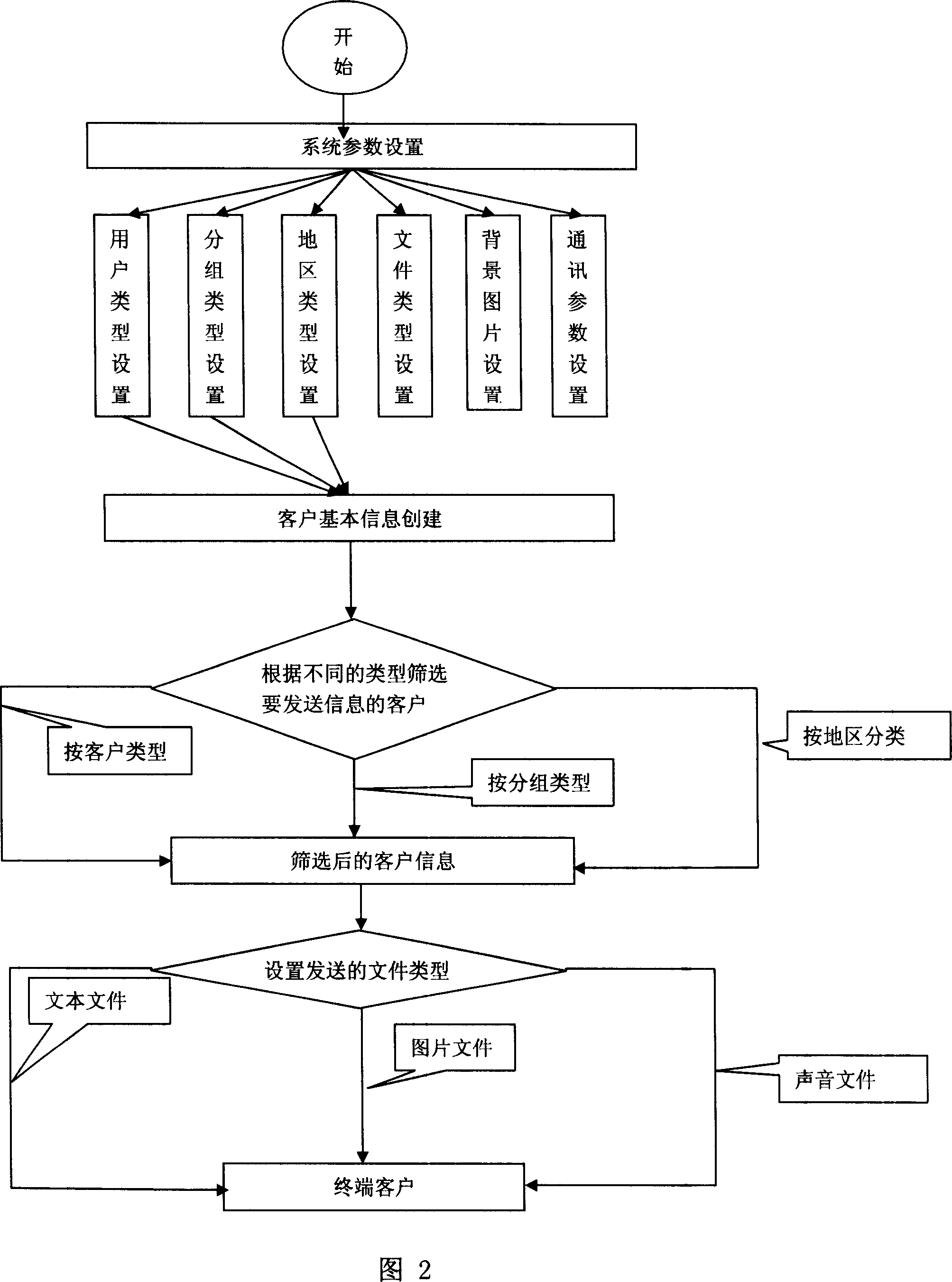
Public information publishing system based on the GRPS network platform
InactiveCN101018143AEasy to manageEasy to integrateSpecial service provision for substationRadio/inductive link selection arrangementsVideo playerManagement unit
The related public information distribution system based on GPRS platform comprises: a transmission client including a display management workstation, a server and a display management unit to decode and distribute audio and video data; a network platform to transmit audio and video signal, and a receiving terminal including a GPRS module, a receiving control module, a audio and video displayer. This invention can apply remote wireless network control.
Owner:金贵铜
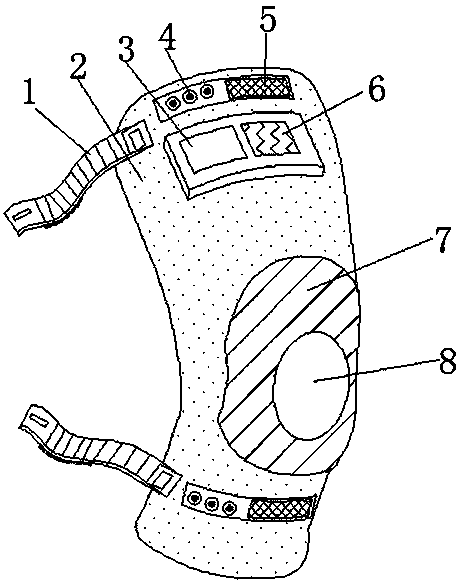
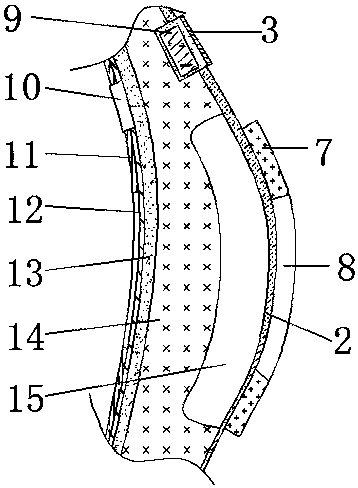
Sports knee cap with thermal insulation function
InactiveCN107752167AEffectively keep warmNot attackedGarment special featuresProtective garmentThermal insulationKnee protector
The invention discloses a sports knee pad with the function of keeping warm, which comprises a waterproof shell, and the outer walls of the waterproof shell near the top end and the bottom end are all sewn with tightening devices, and the tightening device includes a base and a fixing seat, and the base and the fixing seat The seats are all sewed on one side of the outer wall of the waterproof casing, the outer wall of the top top of the base is sewed with a cocklebur seat and three buttons distributed equidistantly, the outer wall of the top of the fixing seat is sewed with an elastic band, and one end of the elastic band There are buttonholes on the side outer wall, and the buttonholes are located on the side away from the waterproof casing. There is a groove on one side of the outer wall of the waterproof casing, and a patch battery is embedded in the groove, and the groove is far away from the outer wall of the patch battery. Sewn with fixed disc. The invention has a novel structure and good thermal performance, can protect the user's knees from the cold when exercising at a low temperature, is convenient to wear, and has good safety, which can prevent the knee pads from falling off and knee injuries during exercise .
Owner:江苏名欧高分子科技有限公司
Rearranged bacterial virus bacteriolysis gene, perforating vector thereof and use in vaccine preparation
InactiveCN101503694AImprove punching effectHole punching worksAntibacterial agentsMicroorganism based processesCrabtreellaSalmonella
The invention discloses a rearranged phage bacteriolytic gene, as well as a perforation vector and application thereof in vaccine preparation. The rearranged phage bacteriolytic gene has a nucleotide sequence shown in SEQ ID NO:1. An efficient perforation vector can be obtained by operationally connecting the rearranged phage bacteriolytic gene with a prokaryotic expression vector. The perforation vector is transformed into avian salmonella and then added with value; the expression of the rearranged phage bacteriolytic gene is induced; and formed bacterial ghosts are collected so as to obtain avian salmonella bacterial-ghost vaccine. The bacterial-ghost vaccine prepared in the invention can be applied without concentration. The avian salmonella bacterial-ghost vaccine is good in safety. After chicks are inoculated with the avian salmonella bacterial-ghost vaccine, the content of antibodies in every immune chick can be remarkably increased, so that every immune chick can be effectively protected against attacking toxins of avian salmonella, which shows that the avian salmonella bacterial-ghost vaccine has good immune protection effect.
Owner:HARBIN VETERINARY RES INST CHINESE ACADEMY OF AGRI SCI
Intrusion tolerant cloud storage data auditing method
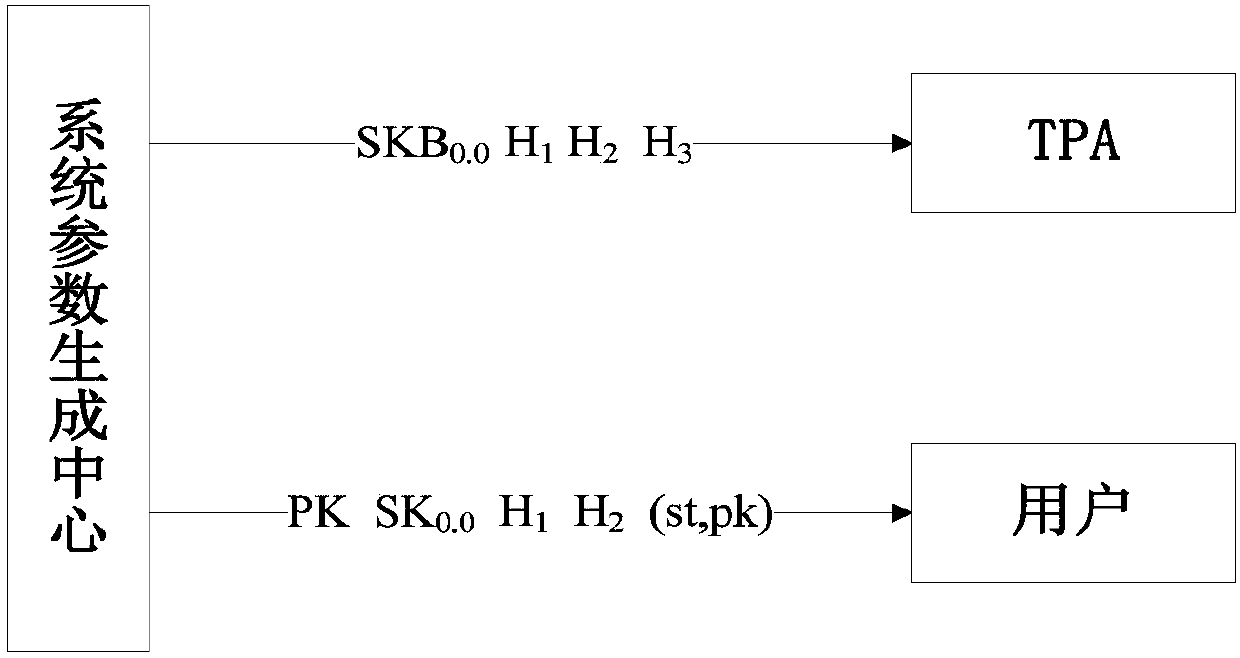
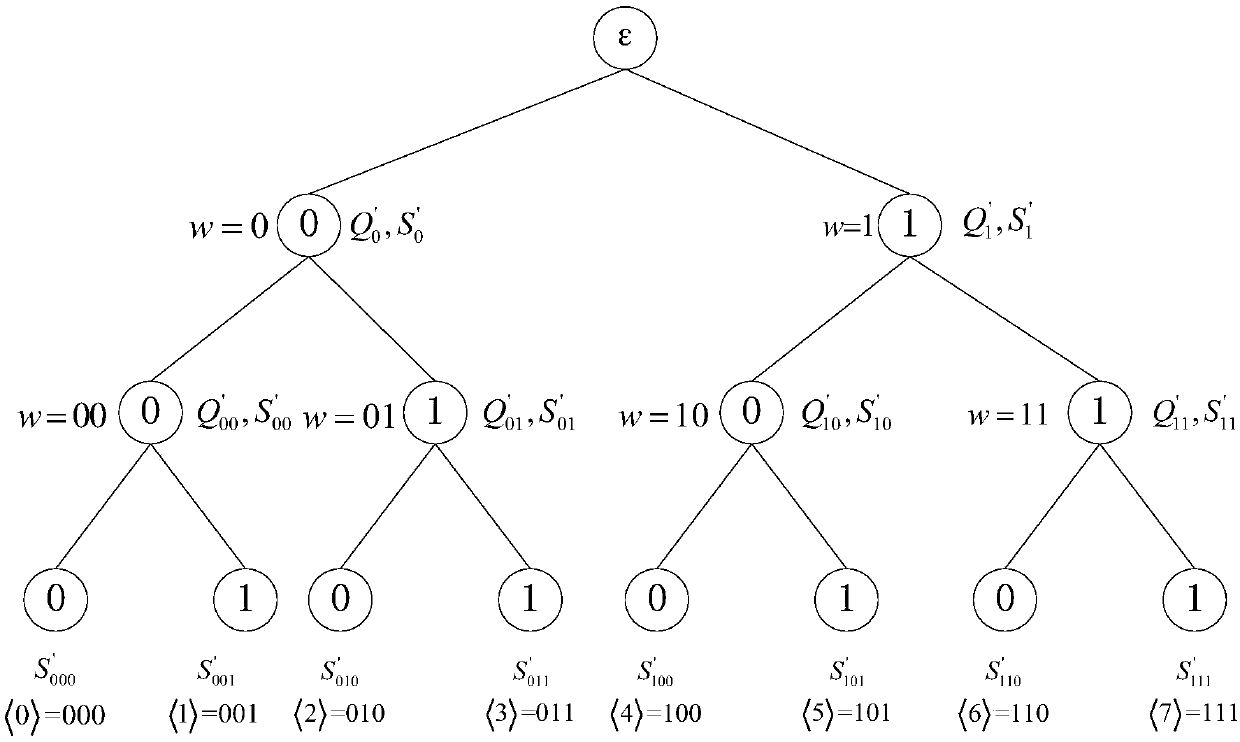
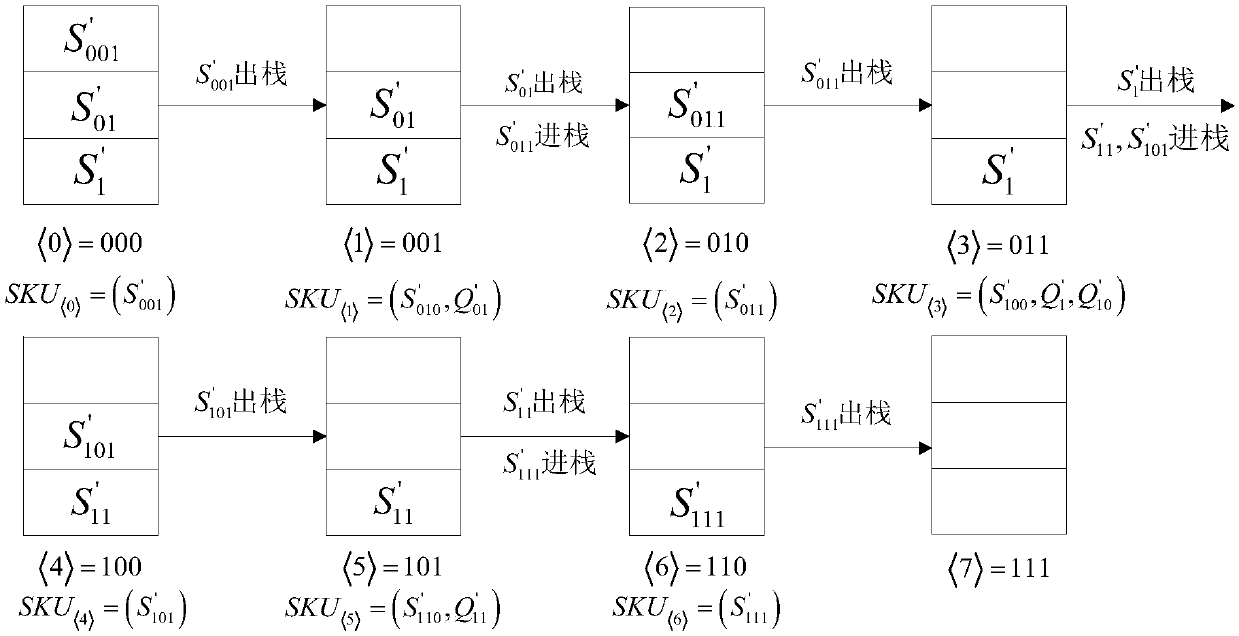
ActiveCN107046465ADoes not affect audit efficiencyImprove audit efficiencyKey distribution for secure communicationUser identity/authority verificationThird partyCloud storage
The invention discloses an intrusion tolerant cloud storage data auditing method and data auditing system. The method comprises a system parameter generation step of generating various system parameters by a system parameter generation center; a key updating step of assisting a user in updating an auditing key periodically through a TPA (Third-party Auditor); a key refreshing step of assisting the user in refreshing an auditing key in each period through the TPA; and a data uploading and auditing step of generating a verification tag for a file by the user, uploading the file and the verification tag to a cloud server and auditing the file by the TPA to verify whether the file is completely stored in the cloud server or not. According to the method, the third-party auditor TPA is introduced for carrying out auditing operation, and moreover, the user is assisted in carrying out periodic key updating and key refreshing operation in each time period. Even if the keys of the user and the TPA are leaked for many times, the data auditing of any other period except the periods in which a user side key is leaked is still secure.
Owner:ANHUI UNIVERSITY
Animal biogen special for pigs and preparation method thereof
ActiveCN102669487AImprove nutrient metabolismImprove biological activityFood processingAnimal feeding stuffMedicinal herbsBiotechnology
The invention discloses animal biogen special for pigs and a preparation method thereof. The animal biogen comprises the following raw materials: feed-grade fulvic acid, total dandelion flavonoids and bitter bean pulp fermentation culture; the bitter bean pulp fermentation culture comprises bitter bean pulp substrate and inoculation liquid, wherein the bitter bean pulp substrate comprises bitter bean pulp, corn meal and beet molasses; and the inoculation liquid comprises saccharomyces cerevisiae, lactobacillus plantarum, bacillus subtillis and living bacillus licheniformis. The animal biogen is prepared from probiotics such as lactobacillus plantarum and fulvic acid serving as raw materials, multiple Chinese medicinal herbs capable of improving the functions of intestines and stomach and improving the immune functions of animals and other nutritional substances by scientific compatibility and compounding. The animal biogen is a natural green product with the effects of promoting growth, improving the immunity, preventing and resisting diseases and improving the quality of an animal product by repairing, regulating and exciting the digestive systems and the immune system of an animal.
Owner:内蒙古永业农丰生物科技有限责任公司
Safety structure of all-around protecting mobile proxy network management application
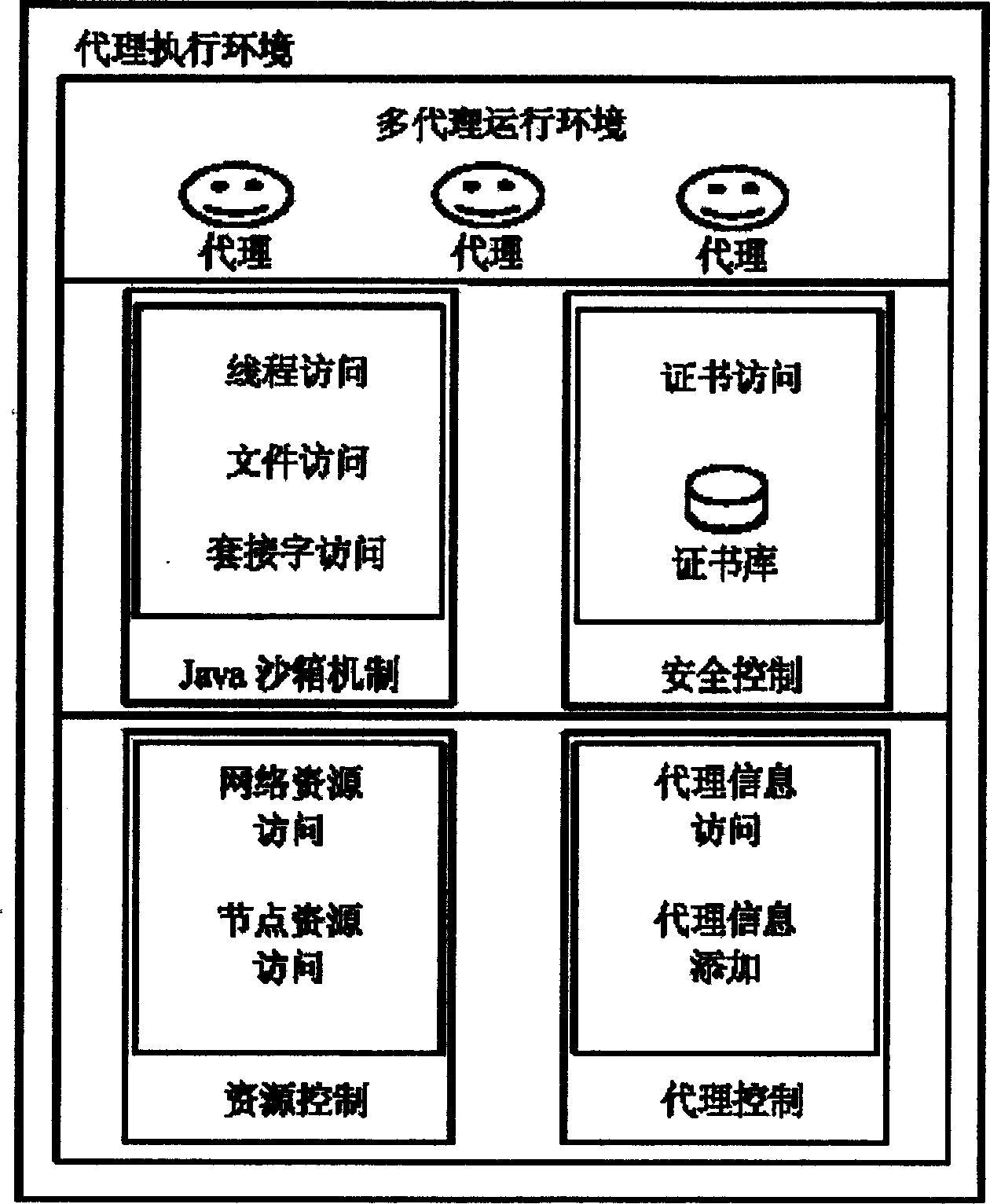
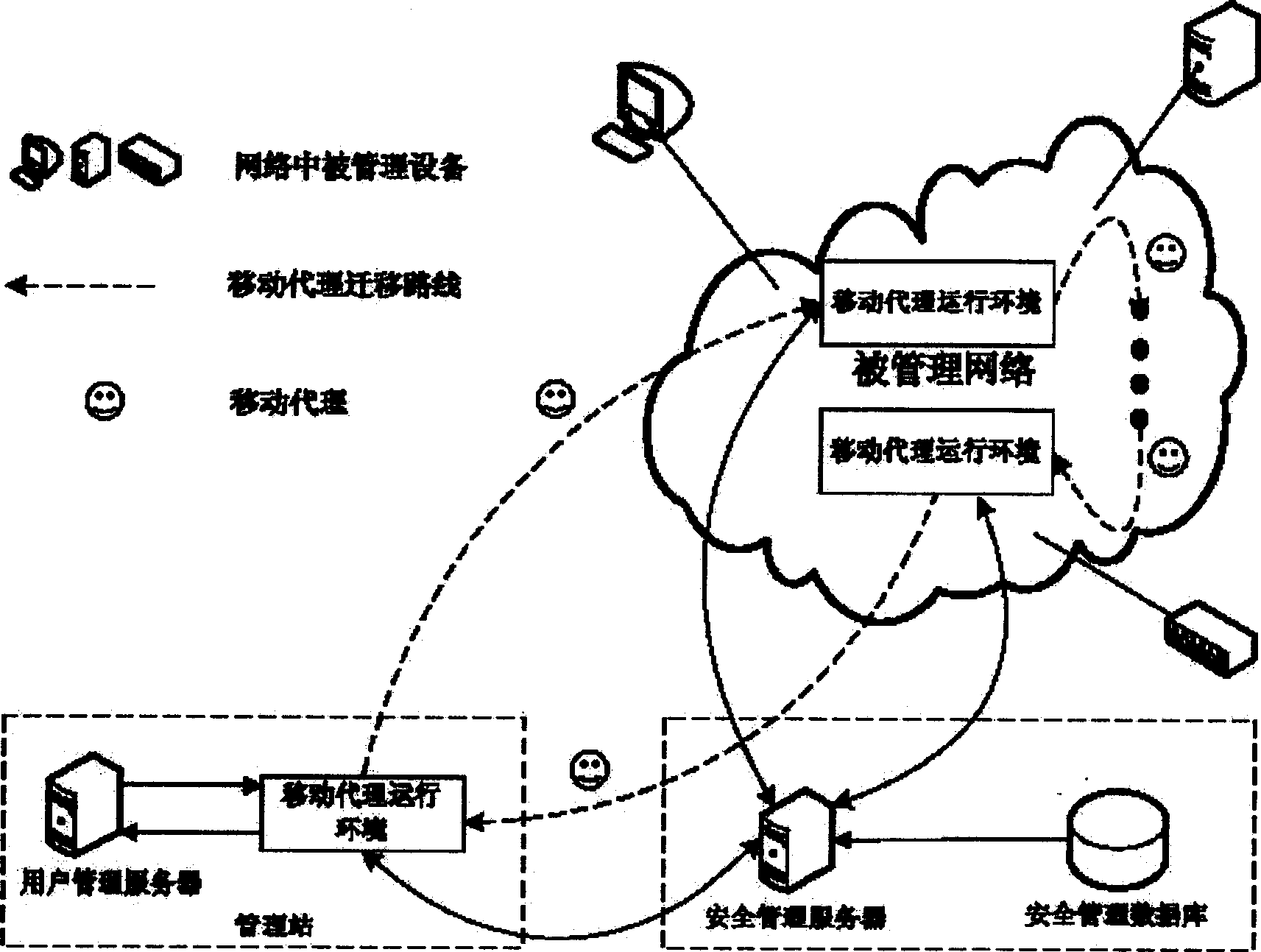
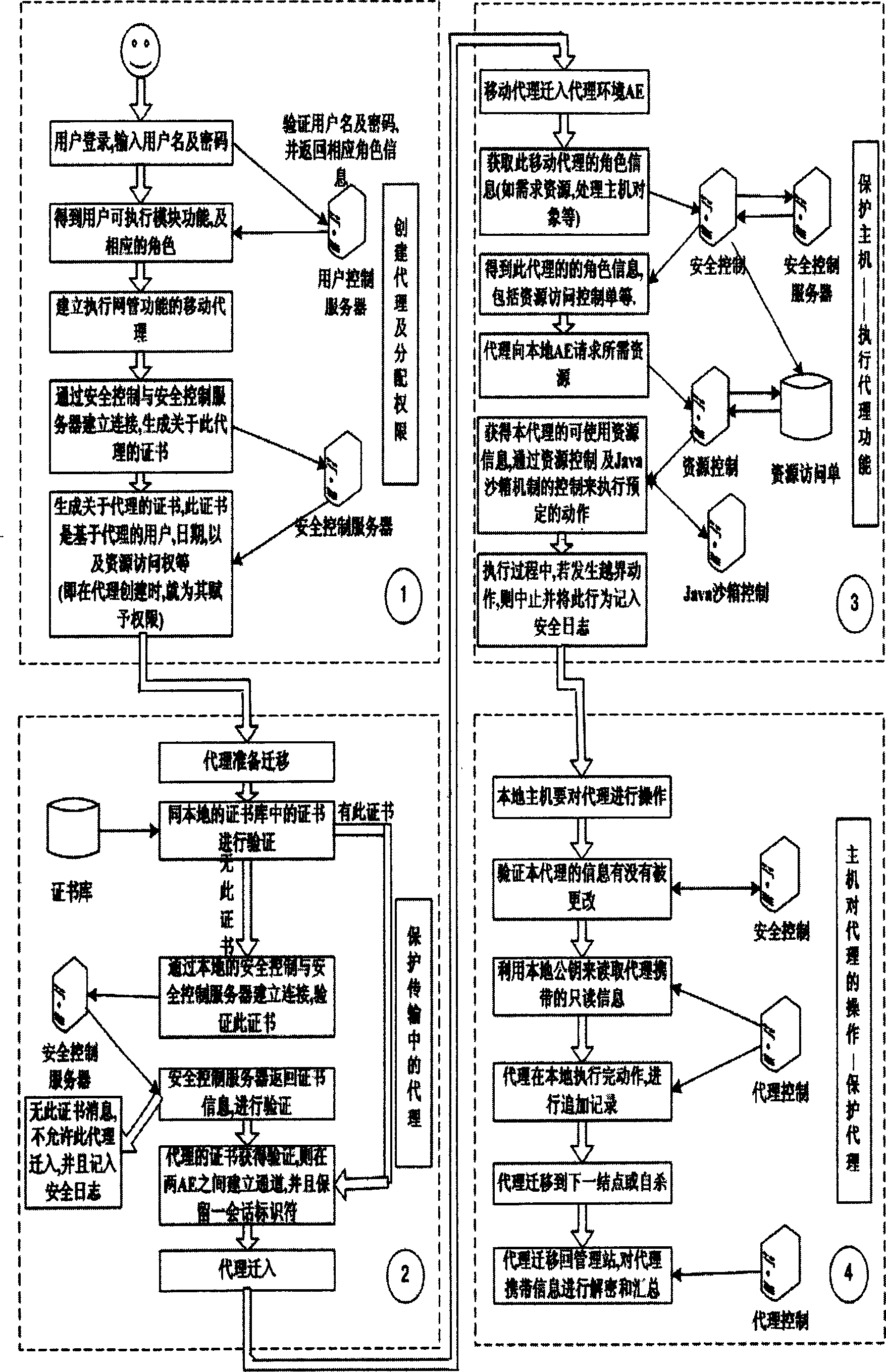
InactiveCN1845508AAvoid complexityIncrease flexibilityData switching networksExtensibilityNetwork management application
The security framework to protect mobile agent network manage application fully comprises: user logs on agent running environment to create mobile agent and assign right according to task request; the agent transfers the protection to be transmission to the target host for execution; while, it should prevent host resource from malicious destroy as well as the agent from malicious host attack. This invention improves network management security, and reduces protection difficulty and source consumption.
Owner:NANJING UNIV OF POSTS & TELECOMM
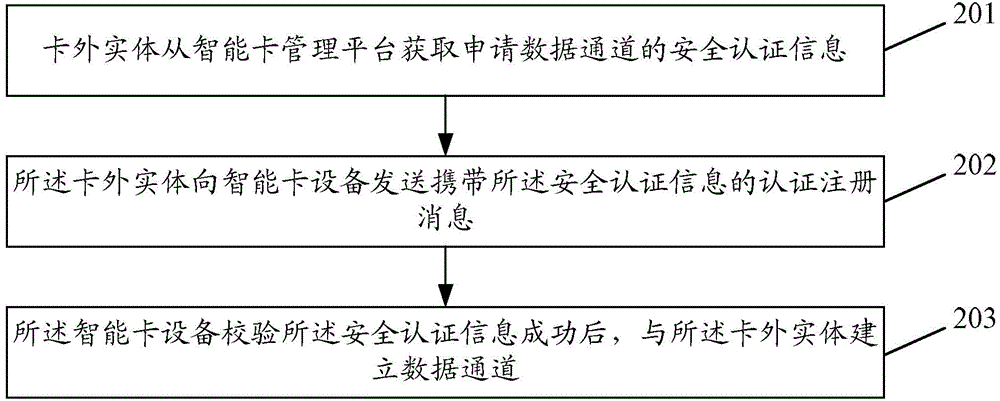
Method and system for building data channel and related devices
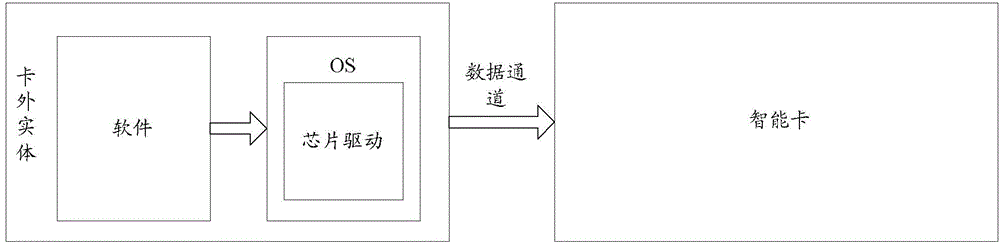
ActiveCN105790946ANot attackedNot hurtUser identity/authority verificationSmart cardSecurity authentication
The invention discloses a method for building a data channel. The method comprises an off-card entity obtains security authentication information for applying the data channel from an intelligent card management platform; the off-card entity sends an authentication registering message carrying the security authentication information to the intelligent card management platform; and after the intelligent card management platform verifies the security authentication information successfully, the intelligent card management platform builds the data channel with the off-card entity. The invention also discloses the off-card entity, the intelligent card management platform, an intelligent card device and a system for building the data channel.
Owner:CHINA MOBILE COMM GRP CO LTD +1
Fastening device for fastening a measuring pressure sensor, in particular tyre pressure sensor
InactiveCN104995045APrevent kinkingReduce imbalanceTyre measurementsFriction grip releasable fasteningsCommercial vehiclePressure sensor
The invention relates to a fastening device for fastening a measuring sensor, such as a tyre pressure sensor within a tyre cavity to a vehicle rim, in particular utility vehicle rim, comprising a clamping strap which is in the form of a band and carries a receiving device for the measuring sensor. The invention is characterized in that the clamping strap has an eyelet at a first end for the passage of a second end opposite the first end and, starting from the second end and at a distance from the first end, two textile fields are positioned consecutively on the surface of the clamping strap in the longitudinal direction of the clamping strap, of which textile fields one is provided with barbs and the other with loops for the joint formation of a touch and close fastener after the textile fields are folded over onto each other.
Owner:ALLIGATOR VENTILFAB BESCHRANKTER
Alternate distributing system for intelligent pretreatment of scarce resources by discrete directional broadcasting
The invention relates to an alternate distributing system for the intelligent pretreatment of scarce resources by discrete directional broadcasting, which is used for distributing scarce resources according to a distributing rule of alternate distributing probability by adopting a mode of establishing an exclusive identification code and hand-shaking code data according to an advance requirement and informing a selected person of receiving and selecting the scarce resources by a convenient and rapid communication mode. According to the alternate distributing system for the intelligent pretreatment of the scarce resources by the discrete directional broadcasting, the social cost generated by man-made noise is avoided, and the aim of equitable distribution is realized. According to the alternate distributing system for the intelligent pretreatment of the scarce resources by the discrete directional broadcasting, the system can be greatly simplified; the system has higher safety and lower developing and running cost; and meanwhile, the system also has very extensive application range.
Owner:赵永频
Silicon etchant composition having low selection ratio (Si (100)/Si (111)) for two crystal lattice directions and low silica etching rate
ActiveCN110003911ANot attackedProtects against etchSurface treatment compositionsChemical compoundAmmonium hydroxide
The present invention is directed to a special silicon etchant composition having a low selectivity ratio (Si(100) / Si(111)) for two lattice directions and a low silicon oxide etch rate, which is suitable for use in a semiconductor manufacturing process, and includes From about 0.5% by weight to about 5% by weight, based on the total weight of the etchant composition, of at least one quaternary ammonium hydroxide, from about 5% by weight to about 55% by weight of at least one primary amine compound, about 15% by weight to 80% by weight of at least one polyol compound, and from about 10% to 35%by weight of an aqueous medium. The composition preferentially etches silicon present on the substrate as compared to the silica present on the substrate.
Owner:C J TECH
Digital recording and processing device for mass data of audio and video
InactiveCN104270410ARealize collection recordPerfect surgeTransmissionSelective content distributionDigital recordingAnalog front-end
The present invention discloses a digital recording and processing device for mass data of audio and video. The digital recording and processing device is characterized by including a multimedia processor, an analog front end circuit, a DDR memory, a power source, a power source protective circuit, a Beidou module, a 3G module, an audio and video input circuit and a communication circuit, wherein an output end of the power source is connected to an input end of the power source protective circuit, an output end of the power source protective circuit is connected to an input end of the multimedia processor, an information output end of the DDR memory is connected to an information input end of the multimedia processor, a signal output end of the Beidou module is connected to the input end of the multimedia processor, a signal input end of the audio and video input circuit is connected to a signal input end of the analog front end circuit, a signal output end of the analog front end circuit is connected to the input end of the multimedia processor, a signal output end of the 3G module is connected to the input end of the multimedia processor, and the communication circuit is connected to the input end of the multimedia processor.
Owner:CHONGQING HUILIAN INFORMATION TECH
Identity authentication method and device, terminal, storage medium and program product
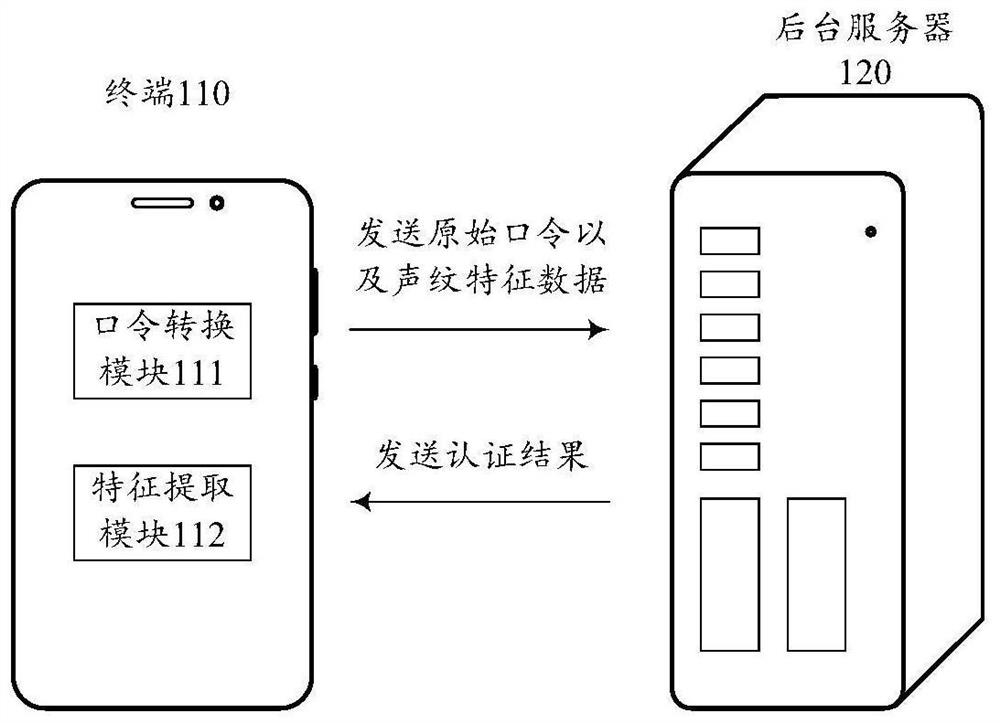
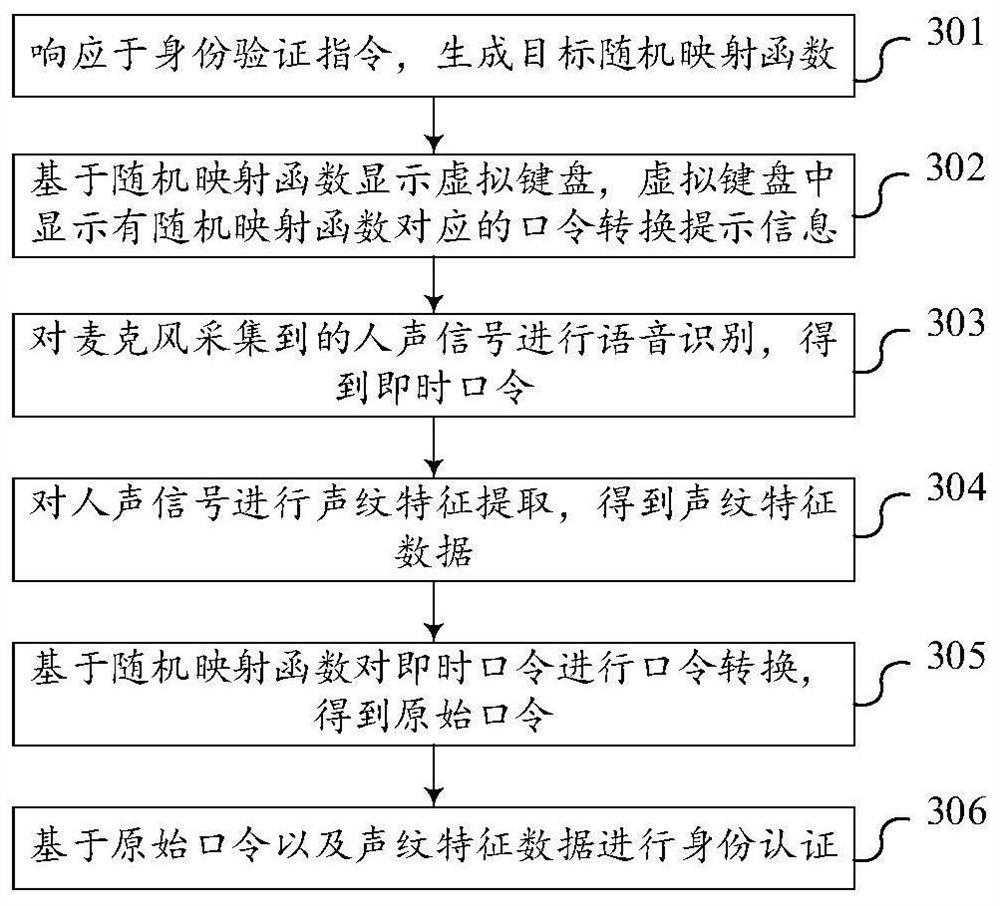
PendingCN114467283ASimplify the identity verification processImprove efficiencySpeech recognitionSecuring communicationFeature extractionPassword
The invention discloses an identity authentication method and device, a terminal, a storage medium and a program product, and belongs to the technical field of cloud security. The method comprises: in response to an identity verification instruction, displaying password conversion prompt information (201); performing voice recognition on the human voice signal acquired by the microphone to obtain an instant password (202); performing voiceprint feature extraction on the human voice signal to obtain voiceprint feature data (203); performing password conversion on the instant password based on a password character conversion mode to obtain an original password (204); and performing identity authentication based on the original password and the voiceprint feature data (205). By adopting the method, the device, the terminal, the storage medium and the program product, a user identity authentication process can be simplified, a user password is ensured not to be leaked in a voice input stage, and voiceprint verification is protected from being attacked by forged voiceprints.
Owner:BIGO TECH PTE LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com