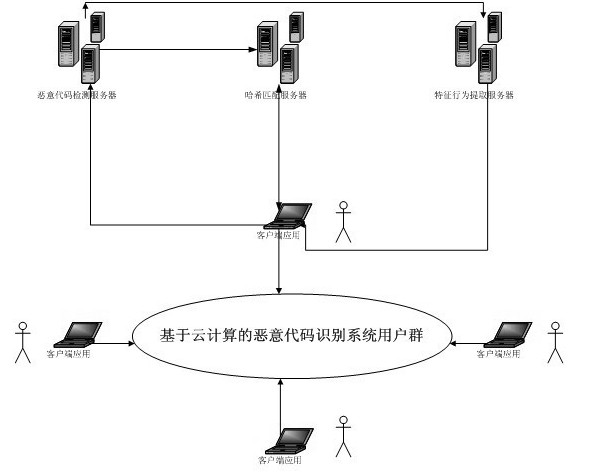
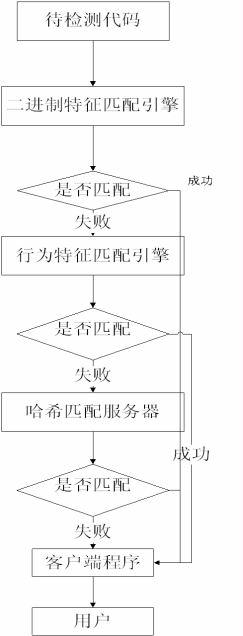
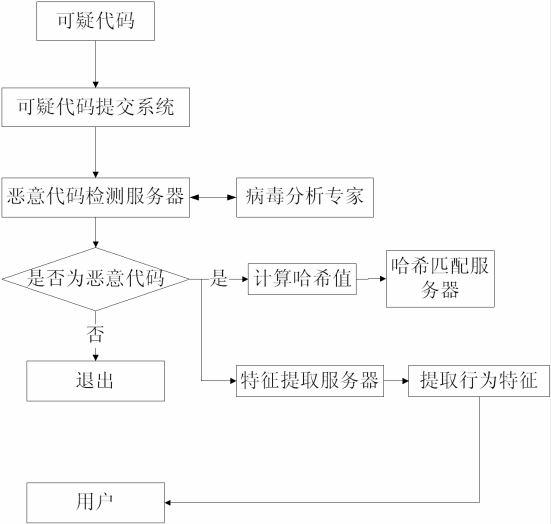
Malicious code recognition method based on cloud computing
A malicious code, malicious code detection technology, applied in the field of virus detection and protection, can solve problems such as accuracy decline
Inactive Publication Date: 2012-09-12
NANJING UNIV OF POSTS & TELECOMM
View PDF3 Cites 9 Cited by
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
As a result, the accuracy of traditional signature
Method used
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
View moreImage
Smart Image Click on the blue labels to locate them in the text.
Smart ImageViewing Examples
Examples
Experimental program
Comparison scheme
Effect test
 Login to View More
Login to View More PUM
 Login to View More
Login to View More Abstract
The invention discloses a malicious code recognition method based on cloud computing. The technical problems needed to be solved includes: firstly, variation of current malicious codes is quickened, encryption keys are changed continuously to enable generated code bodies to be extremely low in similarity by the aid of an encryption mechanism of the malicious codes, and traditional detection engines based on feature codes cannot recognize the malicious codes, so that searching and killing rate decreases continuously; and secondly, with development of technology, more self-protection technologies are added into the malicious codes and especially withstand currently popular virtual machine searching and killing mechanisms, and the analysis process of codes which are quite simple in the real environment is extremely complex in virtual machines of antivirus engines, so that the malicious codes are finally unrecognized. Obviously, new feasible schemes are needed to solve the problem of malicious code recognition in the current environment so as to defend effectively.
Description
technical field [0001] The present invention is a solution for identifying malicious codes based on a cloud computing platform, which mainly solves the problems that current malicious codes mutate more and more quickly, and traditional virus database updates cannot achieve timely detection and killing, and belongs to the field of virus detection and protection. Background technique [0002] With the development of computer technology, especially the rapid development of computer networks, the number of malicious codes has an exponential growth trend. Early malicious codes did not adopt too many self-protection mechanisms, and all had fixed signatures. Therefore, anti-virus software can easily detect virus programs hidden in the system by using virus signature matching. However, with the development of technology, malicious codes have adopted self-protection techniques against anti-virus detection engines. As a result, the accuracy of traditional signature-based antivirus e...
Claims
the structure of the environmentally friendly knitted fabric provided by the present invention; figure 2 Flow chart of the yarn wrapping machine for environmentally friendly knitted fabrics and storage devices; image 3 Is the parameter map of the yarn covering machine
Login to View More Application Information
Patent Timeline
 Login to View More
Login to View More IPC IPC(8): H04L29/06G06F21/00G06F21/56
Inventor 王汝传雷迟骏韩志杰付雄季一木戴华孙力娟
Owner NANJING UNIV OF POSTS & TELECOMM
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com